Connecting to a Database Using PHP. Prof. Jim Whitehead CMPS 183, Spring 2006 May 15, 2006
|
|
|
- Benedict Atkins
- 8 years ago
- Views:
Transcription
1 Connecting to a Database Using PHP Prof. Jim Whitehead CMPS 183, Spring 2006 May 15, 2006
2 Rationale Most Web applications: Retrieve information from a database to alter their on-screen display Store user data such as orders, tracking, address, credit card, etc. in a database Permits them to adapt to individual users, and provide fresh, changing content
3 PHP: Built-in Database Access PHP provides built-in database connectivity for a wide range of databases MySQL, PostgreSQL, Oracle, Berkeley DB, Informix, msql, Lotus Notes, and more Starting support for a specific database may involve PHP configuration steps Another advantage of using a programming language that has been designed for the creation of web apps. Support for each database is described in the PHP manual at:
4 MySQL and PHP Architecture diagram Logical Web Server OS proc. 1 Thread 1 OS proc. n Thread 1 Logical Database (MySQL) Thread 2 Thread n Thread 2 Thread n
5 Connecting to MySQL To connect to a database, need to create a connection At lowest level, this is a network connection Involves a login sequence (username/password) Since this is a relatively expensive step, web application environments: Share connections Have multiple connections Whether, and how many, are typical configuration items. In MySQL: Allow_persistent: whether to allow persistent connections Max_persistent: the maximum number of persistent connections Max_links: max number of connections, persistent and not Connection_timeout: how long the persistent connection is left open Can also use SSL to encrypt connection
6 High-Level Process of Using MySQL from PHP Create a database connection Select database you wish to use Perform a SQL query Do some processing on query results Close database connection
7 Creating Database Connection Use either mysql_connect or mysql_pconnect to create database connection mysql_connect: connection is closed at end of script (end of page) mysql_pconnect: creates persistent connection connection remains even after end of the page Parameters Server hostname of server Username username on the database Password password on the database New Link (mysql_connect only) reuse database connection created by previous call to mysql_connect Client Flags MYSQL_CLIENT_SSL :: Use SSL MYSQL_CLIENT_COMPRESS :: Compress data sent to MySQL
8 Security Note Username and password fields imply that database password is sitting there in the source code If someone gains access to source code, can compromise the database Servers are sometimes configured to view PHP source code when a resource is requested with.phps instead of.php One approach to avoid this: put this information in Web server config. File Then ensure the Web server config. file is not externally accessible
9 Selecting a Database mysql_select_db() Pass it the database name Related: mysql_list_dbs() List databases available Mysql_list_tables() List database tables available
10 Perform SQL Query Create query string $query = SQL formatted string $query = SELECT * FROM table Submit query to database for processing $result = mysql_query($query); For UPDATE, DELETE, DROP, etc, returns TRUE or FALSE For SELECT, SHOW, DESCRIBE or EXPLAIN, $result is an identifier for the results, and does not contain the results themselves $result is called a resource in this case A result of FALSE indicates an error If there is an error mysql_error() returns error string from last MySQL call
11 Process Results Many functions exist to work with database results mysql_num_rows() Number of rows in the result set Useful for iterating over result set mysql_fetch_array() Returns a result row as an array Can be associative or numeric or both (default) $row = mysql_fetch_array($result); $row[ column name ] :: value comes from database row with specified column name $row[0] :: value comes from first field in result set
12 Process Results Loop Easy loop for processing results: $result = mysql_query($qstring); $num_rows = mysql_num_rows($result); for ($i=0; $i<$num_rows; $i++) { $row = mysql_fetch_array($result); // take action on database results here }
13 Closing Database Connection mysql_close() Closes database connection Only works for connections opened with mysql_connect() Connections opened with mysql_pconnect() ignore this call Often not necessary to call this, as connections created by mysql_connect are closed at the end of the script anyway
7- PHP and MySQL queries
 7- PHP and MySQL queries Course: Cris*na Puente, Rafael Palacios 2010- 1 Introduc*on Introduc?on PHP includes libraries for communica*ng with several databases: MySQL (OpenSource, the use selected for
7- PHP and MySQL queries Course: Cris*na Puente, Rafael Palacios 2010- 1 Introduc*on Introduc?on PHP includes libraries for communica*ng with several databases: MySQL (OpenSource, the use selected for
A Brief Introduction to MySQL
 A Brief Introduction to MySQL by Derek Schuurman Introduction to Databases A database is a structured collection of logically related data. One common type of database is the relational database, a term
A Brief Introduction to MySQL by Derek Schuurman Introduction to Databases A database is a structured collection of logically related data. One common type of database is the relational database, a term
Server side scripting and databases
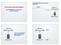 Three components used in typical web application Server side scripting and databases How Web Applications interact with server side databases Browser Web server Database server Web server Web server Apache
Three components used in typical web application Server side scripting and databases How Web Applications interact with server side databases Browser Web server Database server Web server Web server Apache
Web Programming Step by Step
 Web Programming Step by Step Chapter 11 Relational Databases and SQL References: SQL syntax reference, w3schools tutorial Except where otherwise noted, the contents of this presentation are Copyright 2009
Web Programming Step by Step Chapter 11 Relational Databases and SQL References: SQL syntax reference, w3schools tutorial Except where otherwise noted, the contents of this presentation are Copyright 2009
A table is a collection of related data entries and it consists of columns and rows.
 CST 250 MySQL Notes (Source: www.w3schools.com) MySQL is the most popular open-source database system. What is MySQL? MySQL is a database. The data in MySQL is stored in database objects called tables.
CST 250 MySQL Notes (Source: www.w3schools.com) MySQL is the most popular open-source database system. What is MySQL? MySQL is a database. The data in MySQL is stored in database objects called tables.
Database Extension 1.5 ez Publish Extension Manual
 Database Extension 1.5 ez Publish Extension Manual 1999 2012 ez Systems AS Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License,Version
Database Extension 1.5 ez Publish Extension Manual 1999 2012 ez Systems AS Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License,Version
The following steps detail how to prepare your database.
 Using databases in Second Life or Open Sim to enhance user experience Tom Connors, SciEthis Interactive 2012 Second Life and Open Sim each have a built in system for editing the virtual world that allows
Using databases in Second Life or Open Sim to enhance user experience Tom Connors, SciEthis Interactive 2012 Second Life and Open Sim each have a built in system for editing the virtual world that allows
MYSQL DATABASE ACCESS WITH PHP
 MYSQL DATABASE ACCESS WITH PHP Fall 2009 CSCI 2910 Server Side Web Programming Typical web application interaction Database Server 3 tiered architecture Security in this interaction is critical Web Server
MYSQL DATABASE ACCESS WITH PHP Fall 2009 CSCI 2910 Server Side Web Programming Typical web application interaction Database Server 3 tiered architecture Security in this interaction is critical Web Server
Security and Control Issues within Relational Databases
 Security and Control Issues within Relational Databases David C. Ogbolumani, CISA, CISSP, CIA, CISM Practice Manager Information Security Preview of Key Points The Database Environment Top Database Threats
Security and Control Issues within Relational Databases David C. Ogbolumani, CISA, CISSP, CIA, CISM Practice Manager Information Security Preview of Key Points The Database Environment Top Database Threats
Databases and SQL. The Bioinformatics Lab SS 2013 - Wiki topic 10. Tikira Temu. 04. June 2013
 Databases and SQL The Bioinformatics Lab SS 2013 - Wiki topic 10 Tikira Temu 04. June 2013 Outline 1 Database system (DBS) Definition DBS Definition DBMS Advantages of a DBMS Famous DBMS 2 Some facts about
Databases and SQL The Bioinformatics Lab SS 2013 - Wiki topic 10 Tikira Temu 04. June 2013 Outline 1 Database system (DBS) Definition DBS Definition DBMS Advantages of a DBMS Famous DBMS 2 Some facts about
MySQL Security for Security Audits
 MySQL Security for Security Audits Presented by, MySQL AB & O Reilly Media, Inc. Brian Miezejewski MySQL Principal Consultat Bio Leed Architect ZFour database 1986 Senior Principal Architect American Airlines
MySQL Security for Security Audits Presented by, MySQL AB & O Reilly Media, Inc. Brian Miezejewski MySQL Principal Consultat Bio Leed Architect ZFour database 1986 Senior Principal Architect American Airlines
INSTALLING, CONFIGURING, AND DEVELOPING WITH XAMPP
 INSTALLING, CONFIGURING, AND DEVELOPING WITH XAMPP by Dalibor D. Dvorski, March 2007 Skills Canada Ontario DISCLAIMER: A lot of care has been taken in the accuracy of information provided in this article,
INSTALLING, CONFIGURING, AND DEVELOPING WITH XAMPP by Dalibor D. Dvorski, March 2007 Skills Canada Ontario DISCLAIMER: A lot of care has been taken in the accuracy of information provided in this article,
Database 10g Edition: All possible 10g features, either bundled or available at additional cost.
 Concepts Oracle Corporation offers a wide variety of products. The Oracle Database 10g, the product this exam focuses on, is the centerpiece of the Oracle product set. The "g" in "10g" stands for the Grid
Concepts Oracle Corporation offers a wide variety of products. The Oracle Database 10g, the product this exam focuses on, is the centerpiece of the Oracle product set. The "g" in "10g" stands for the Grid
Using Apache Derby in the real world
 Apache Derby a 100% Java Open Source RDBMS Using Apache Derby in the real world Victorian AJUG, Australia 28 th August 2008 Chris Dance Chris Dance Introduction Director and Found of PaperCut Software
Apache Derby a 100% Java Open Source RDBMS Using Apache Derby in the real world Victorian AJUG, Australia 28 th August 2008 Chris Dance Chris Dance Introduction Director and Found of PaperCut Software
MySQL Quick Start Guide
 Fasthosts Customer Support MySQL Quick Start Guide This guide will help you: Add a MySQL database to your account. Find your database. Add additional users. Use the MySQL command-line tools through ssh.
Fasthosts Customer Support MySQL Quick Start Guide This guide will help you: Add a MySQL database to your account. Find your database. Add additional users. Use the MySQL command-line tools through ssh.
Supercharge your MySQL application performance with Cloud Databases
 Supercharge your MySQL application performance with Cloud Databases J.R. Arredondo Director Product Marketing Kelly Goolsby Sales Engineering Manager Daniel Morris Senior Product Manager Dave Fowler Founder
Supercharge your MySQL application performance with Cloud Databases J.R. Arredondo Director Product Marketing Kelly Goolsby Sales Engineering Manager Daniel Morris Senior Product Manager Dave Fowler Founder
Zend Framework Database Access
 Zend Framework Database Access Bill Karwin Copyright 2007, Zend Technologies Inc. Introduction What s in the Zend_Db component? Examples of using each class Using Zend_Db in MVC applications Zend Framework
Zend Framework Database Access Bill Karwin Copyright 2007, Zend Technologies Inc. Introduction What s in the Zend_Db component? Examples of using each class Using Zend_Db in MVC applications Zend Framework
Eurobackup PRO: Configuration Best Practices
 P a g e 1 Eurobackup PRO: Configuration Best Practices P a g e 2 Contents General Best Practices... 3 Installation... 3 Encryption... 3 Retention Policy... 3 Retention Policy (advanced)... 3 In-File Delta...
P a g e 1 Eurobackup PRO: Configuration Best Practices P a g e 2 Contents General Best Practices... 3 Installation... 3 Encryption... 3 Retention Policy... 3 Retention Policy (advanced)... 3 In-File Delta...
G563 Quantitative Paleontology. SQL databases. An introduction. Department of Geological Sciences Indiana University. (c) 2012, P.
 SQL databases An introduction AMP: Apache, mysql, PHP This installations installs the Apache webserver, the PHP scripting language, and the mysql database on your computer: Apache: runs in the background
SQL databases An introduction AMP: Apache, mysql, PHP This installations installs the Apache webserver, the PHP scripting language, and the mysql database on your computer: Apache: runs in the background
SQL Injection Vulnerabilities in Desktop Applications
 Vulnerabilities in Desktop Applications Derek Ditch (lead) Dylan McDonald Justin Miller Missouri University of Science & Technology Computer Science Department April 29, 2008 Vulnerabilities in Desktop
Vulnerabilities in Desktop Applications Derek Ditch (lead) Dylan McDonald Justin Miller Missouri University of Science & Technology Computer Science Department April 29, 2008 Vulnerabilities in Desktop
Package sjdbc. R topics documented: February 20, 2015
 Package sjdbc February 20, 2015 Version 1.5.0-71 Title JDBC Driver Interface Author TIBCO Software Inc. Maintainer Stephen Kaluzny Provides a database-independent JDBC interface. License
Package sjdbc February 20, 2015 Version 1.5.0-71 Title JDBC Driver Interface Author TIBCO Software Inc. Maintainer Stephen Kaluzny Provides a database-independent JDBC interface. License
"SQL Database Professional " module PRINTED MANUAL
 "SQL Database Professional " module PRINTED MANUAL "SQL Database Professional " module All rights reserved. No parts of this work may be reproduced in any form or by any means - graphic, electronic, or
"SQL Database Professional " module PRINTED MANUAL "SQL Database Professional " module All rights reserved. No parts of this work may be reproduced in any form or by any means - graphic, electronic, or
CSCI110 Exercise 4: Database - MySQL
 CSCI110 Exercise 4: Database - MySQL The exercise This exercise is to be completed in the laboratory and your completed work is to be shown to the laboratory tutor. The work should be done in week-8 but
CSCI110 Exercise 4: Database - MySQL The exercise This exercise is to be completed in the laboratory and your completed work is to be shown to the laboratory tutor. The work should be done in week-8 but
Final Design Document for Practicum Chat Program
 Final Design Document for Practicum Chat Program Prepared by: Team Members: Raymond Chamberglain William Mason Jerrad Allen Elh Barry Franklin University CS Practicum April 12, 2008 Page 1 Purpose: This
Final Design Document for Practicum Chat Program Prepared by: Team Members: Raymond Chamberglain William Mason Jerrad Allen Elh Barry Franklin University CS Practicum April 12, 2008 Page 1 Purpose: This
MySQL Quick Start Guide
 Quick Start Guide MySQL Quick Start Guide SQL databases provide many benefits to the web designer, allowing you to dynamically update your web pages, collect and maintain customer data and allowing customers
Quick Start Guide MySQL Quick Start Guide SQL databases provide many benefits to the web designer, allowing you to dynamically update your web pages, collect and maintain customer data and allowing customers
AVALANCHE MC 5.3 AND DATABASE MANAGEMENT SYSTEMS
 AVALANCHE MC 5.3 AND DATABASE MANAGEMENT SYSTEMS Avalanche Mobility Center (MC) offers support for other database management systems (DBMS) as alternatives to the built-in PostgreSQL DBMS. This was prompted
AVALANCHE MC 5.3 AND DATABASE MANAGEMENT SYSTEMS Avalanche Mobility Center (MC) offers support for other database management systems (DBMS) as alternatives to the built-in PostgreSQL DBMS. This was prompted
Install Guide - Hosted
 Install Guide - Hosted SelectSurvey.NET Install Guide for Hosted For more detailed instructions read the SelectSurveyNETInstallGuide.pdf located in same directory as this file. This install guide is for
Install Guide - Hosted SelectSurvey.NET Install Guide for Hosted For more detailed instructions read the SelectSurveyNETInstallGuide.pdf located in same directory as this file. This install guide is for
ORACLE DATABASE SECURITY. Keywords: data security, password administration, Oracle HTTP Server, OracleAS, access control.
 ORACLE DATABASE SECURITY Cristina-Maria Titrade 1 Abstract This paper presents some security issues, namely security database system level, data level security, user-level security, user management, resource
ORACLE DATABASE SECURITY Cristina-Maria Titrade 1 Abstract This paper presents some security issues, namely security database system level, data level security, user-level security, user management, resource
WordPress Security Scan Configuration
 WordPress Security Scan Configuration To configure the - WordPress Security Scan - plugin in your WordPress driven Blog, login to WordPress as administrator, by simply entering the url_of_your_website/wp-admin
WordPress Security Scan Configuration To configure the - WordPress Security Scan - plugin in your WordPress driven Blog, login to WordPress as administrator, by simply entering the url_of_your_website/wp-admin
HP OO 10.X - SiteScope Monitoring Templates
 HP OO Community Guides HP OO 10.X - SiteScope Monitoring Templates As with any application continuous automated monitoring is key. Monitoring is important in order to quickly identify potential issues,
HP OO Community Guides HP OO 10.X - SiteScope Monitoring Templates As with any application continuous automated monitoring is key. Monitoring is important in order to quickly identify potential issues,
How To Let A Lecturer Know If Someone Is At A Lecture Or If They Are At A Guesthouse
 Saya WebServer Mini-project report Introduction: The Saya WebServer mini-project is a multipurpose one. One use of it is when a lecturer (of the cs faculty) is at the reception desk and interested in knowing
Saya WebServer Mini-project report Introduction: The Saya WebServer mini-project is a multipurpose one. One use of it is when a lecturer (of the cs faculty) is at the reception desk and interested in knowing
Designing for Dynamic Content
 Designing for Dynamic Content Course Code (WEB1005M) James Todd Web Design BA (Hons) Summary This report will give a step-by-step account of the relevant processes that have been adopted during the construction
Designing for Dynamic Content Course Code (WEB1005M) James Todd Web Design BA (Hons) Summary This report will give a step-by-step account of the relevant processes that have been adopted during the construction
Video Administration Backup and Restore Procedures
 CHAPTER 12 Video Administration Backup and Restore Procedures This chapter provides procedures for backing up and restoring the Video Administration database and configuration files. See the following
CHAPTER 12 Video Administration Backup and Restore Procedures This chapter provides procedures for backing up and restoring the Video Administration database and configuration files. See the following
SQL Injection. The ability to inject SQL commands into the database engine through an existing application
 SQL Injection The ability to inject SQL commands into the database engine through an existing application 1 What is SQL? SQL stands for Structured Query Language Allows us to access a database ANSI and
SQL Injection The ability to inject SQL commands into the database engine through an existing application 1 What is SQL? SQL stands for Structured Query Language Allows us to access a database ANSI and
Accessing Your Database with JMP 10 JMP Discovery Conference 2012 Brian Corcoran SAS Institute
 Accessing Your Database with JMP 10 JMP Discovery Conference 2012 Brian Corcoran SAS Institute JMP provides a variety of mechanisms for interfacing to other products and getting data into JMP. The connection
Accessing Your Database with JMP 10 JMP Discovery Conference 2012 Brian Corcoran SAS Institute JMP provides a variety of mechanisms for interfacing to other products and getting data into JMP. The connection
ADO and SQL Server Security
 ADO and SQL Server Security Security is a growing concern in the Internet/intranet development community. It is a constant trade off between access to services and data, and protection of those services
ADO and SQL Server Security Security is a growing concern in the Internet/intranet development community. It is a constant trade off between access to services and data, and protection of those services
Oracle Database Security
 breaking through barriers to progress By Raman Jathar an award winning '2004 Future 50 Company' 18650 W. Corporate Drive Suite 120 Brookfield, WI 53045 262.792.0200 Database Security Lately, database security
breaking through barriers to progress By Raman Jathar an award winning '2004 Future 50 Company' 18650 W. Corporate Drive Suite 120 Brookfield, WI 53045 262.792.0200 Database Security Lately, database security
MatriXay Database Vulnerability Scanner V3.0
 MatriXay Database Vulnerability Scanner V3.0 (DAS- DBScan) - - - The best database security assessment tool 1. Overview MatriXay Database Vulnerability Scanner (DAS- DBScan) is a professional tool with
MatriXay Database Vulnerability Scanner V3.0 (DAS- DBScan) - - - The best database security assessment tool 1. Overview MatriXay Database Vulnerability Scanner (DAS- DBScan) is a professional tool with
Technical. Overview. ~ a ~ irods version 4.x
 Technical Overview ~ a ~ irods version 4.x The integrated Ru e-oriented DATA System irods is open-source, data management software that lets users: access, manage, and share data across any type or number
Technical Overview ~ a ~ irods version 4.x The integrated Ru e-oriented DATA System irods is open-source, data management software that lets users: access, manage, and share data across any type or number
SQL - QUICK GUIDE. Allows users to access data in relational database management systems.
 http://www.tutorialspoint.com/sql/sql-quick-guide.htm SQL - QUICK GUIDE Copyright tutorialspoint.com What is SQL? SQL is Structured Query Language, which is a computer language for storing, manipulating
http://www.tutorialspoint.com/sql/sql-quick-guide.htm SQL - QUICK GUIDE Copyright tutorialspoint.com What is SQL? SQL is Structured Query Language, which is a computer language for storing, manipulating
Chapter 2: Interactive Web Applications
 Chapter 2: Interactive Web Applications 2.1! Interactivity and Multimedia in the WWW architecture 2.2! Server-Side Scripting (Example PHP, Part I) 2.3! Interactivity and Multimedia for Web Browsers 2.4!
Chapter 2: Interactive Web Applications 2.1! Interactivity and Multimedia in the WWW architecture 2.2! Server-Side Scripting (Example PHP, Part I) 2.3! Interactivity and Multimedia for Web Browsers 2.4!
Thick Client Application Security
 Thick Client Application Security Arindam Mandal (arindam.mandal@paladion.net) (http://www.paladion.net) January 2005 This paper discusses the critical vulnerabilities and corresponding risks in a two
Thick Client Application Security Arindam Mandal (arindam.mandal@paladion.net) (http://www.paladion.net) January 2005 This paper discusses the critical vulnerabilities and corresponding risks in a two
SQL Injection January 23, 2013
 Web-based Attack: SQL Injection SQL Injection January 23, 2013 Authored By: Stephanie Reetz, SOC Analyst Contents Introduction Introduction...1 Web applications are everywhere on the Internet. Almost Overview...2
Web-based Attack: SQL Injection SQL Injection January 23, 2013 Authored By: Stephanie Reetz, SOC Analyst Contents Introduction Introduction...1 Web applications are everywhere on the Internet. Almost Overview...2
USING MYWEBSQL FIGURE 1: FIRST AUTHENTICATION LAYER (ENTER YOUR REGULAR SIMMONS USERNAME AND PASSWORD)
 USING MYWEBSQL MyWebSQL is a database web administration tool that will be used during LIS 458 & CS 333. This document will provide the basic steps for you to become familiar with the application. 1. To
USING MYWEBSQL MyWebSQL is a database web administration tool that will be used during LIS 458 & CS 333. This document will provide the basic steps for you to become familiar with the application. 1. To
SQL Injection. SQL Injection. CSCI 4971 Secure Software Principles. Rensselaer Polytechnic Institute. Spring 2010 ...
 SQL Injection CSCI 4971 Secure Software Principles Rensselaer Polytechnic Institute Spring 2010 A Beginner s Example A hypothetical web application $result = mysql_query(
SQL Injection CSCI 4971 Secure Software Principles Rensselaer Polytechnic Institute Spring 2010 A Beginner s Example A hypothetical web application $result = mysql_query(
FileMaker Security Guide The Key to Securing Your Apps
 FileMaker Security Guide The Key to Securing Your Apps Table of Contents Overview... 3 Configuring Security Within FileMaker Pro or FileMaker Pro Advanced... 5 Prompt for Password... 5 Give the Admin Account
FileMaker Security Guide The Key to Securing Your Apps Table of Contents Overview... 3 Configuring Security Within FileMaker Pro or FileMaker Pro Advanced... 5 Prompt for Password... 5 Give the Admin Account
Release: 1. ICADBS601A Build a data warehouse
 Release: 1 ICADBS601A Build a data warehouse ICADBS601A Build a data warehouse Modification History Release Release 1 Comments This Unit first released with ICA11 Information and Communications Technology
Release: 1 ICADBS601A Build a data warehouse ICADBS601A Build a data warehouse Modification History Release Release 1 Comments This Unit first released with ICA11 Information and Communications Technology
Connecting to your Database!... 3
 Connecting to your Database!... 3 Connecting to Access Databases!... 3 Connecting to SQL Server!... 8 Connecting to Oracle!... 10 Connecting to MySQL!... 11 Connecting to Sybase!... 12 Connecting to IBM
Connecting to your Database!... 3 Connecting to Access Databases!... 3 Connecting to SQL Server!... 8 Connecting to Oracle!... 10 Connecting to MySQL!... 11 Connecting to Sybase!... 12 Connecting to IBM
1. Building Testing Environment
 The Practice of Web Application Penetration Testing 1. Building Testing Environment Intrusion of websites is illegal in many countries, so you cannot take other s web sites as your testing target. First,
The Practice of Web Application Penetration Testing 1. Building Testing Environment Intrusion of websites is illegal in many countries, so you cannot take other s web sites as your testing target. First,
Smart Home Security System Based on Microcontroller Using Internet and Android Smartphone
 International Conference on Materials, Electronics & Information Engineering, ICMEIE-205 05-06 June, 205, Faculty of Engineering, University of Rajshahi, Bangladesh www.ru.ac.bd/icmeie205/proceedings/
International Conference on Materials, Electronics & Information Engineering, ICMEIE-205 05-06 June, 205, Faculty of Engineering, University of Rajshahi, Bangladesh www.ru.ac.bd/icmeie205/proceedings/
How to configure your Desktop Computer and Mobile Devices post migrating to Microsoft Office 365
 How to configure your Desktop Computer and Mobile Devices post migrating to Microsoft Office 365 1 Contents Purpose... 3 Office 365 Mail Connections... 3 Finding IMAP server... 3 Desktop computers... 4
How to configure your Desktop Computer and Mobile Devices post migrating to Microsoft Office 365 1 Contents Purpose... 3 Office 365 Mail Connections... 3 Finding IMAP server... 3 Desktop computers... 4
PHP Tutorial From beginner to master
 PHP Tutorial From beginner to master PHP is a powerful tool for making dynamic and interactive Web pages. PHP is the widely-used, free, and efficient alternative to competitors such as Microsoft's ASP.
PHP Tutorial From beginner to master PHP is a powerful tool for making dynamic and interactive Web pages. PHP is the widely-used, free, and efficient alternative to competitors such as Microsoft's ASP.
Configuring Nex-Gen Web Load Balancer
 Configuring Nex-Gen Web Load Balancer Table of Contents Load Balancing Scenarios & Concepts Creating Load Balancer Node using Administration Service Creating Load Balancer Node using NodeCreator Connecting
Configuring Nex-Gen Web Load Balancer Table of Contents Load Balancing Scenarios & Concepts Creating Load Balancer Node using Administration Service Creating Load Balancer Node using NodeCreator Connecting
SQL Server. 2012 for developers. murach's TRAINING & REFERENCE. Bryan Syverson. Mike Murach & Associates, Inc. Joel Murach
 TRAINING & REFERENCE murach's SQL Server 2012 for developers Bryan Syverson Joel Murach Mike Murach & Associates, Inc. 4340 N. Knoll Ave. Fresno, CA 93722 www.murach.com murachbooks@murach.com Expanded
TRAINING & REFERENCE murach's SQL Server 2012 for developers Bryan Syverson Joel Murach Mike Murach & Associates, Inc. 4340 N. Knoll Ave. Fresno, CA 93722 www.murach.com murachbooks@murach.com Expanded
Synchronization Agent Configuration Guide
 SafeNet Authentication Service Synchronization Agent Configuration Guide 1 Document Information Document Part Number 007-012476-001, Revision A Release Date July 2014 Trademarks All intellectual property
SafeNet Authentication Service Synchronization Agent Configuration Guide 1 Document Information Document Part Number 007-012476-001, Revision A Release Date July 2014 Trademarks All intellectual property
Automate Your BI Administration to Save Millions with Command Manager and System Manager
 Automate Your BI Administration to Save Millions with Command Manager and System Manager Presented by: Dennis Liao Sr. Sales Engineer Date: 27 th January, 2015 Session 2 This Session is Part of MicroStrategy
Automate Your BI Administration to Save Millions with Command Manager and System Manager Presented by: Dennis Liao Sr. Sales Engineer Date: 27 th January, 2015 Session 2 This Session is Part of MicroStrategy
Various Load Testing Tools
 Various Load Testing Tools Animesh Das May 23, 2014 Animesh Das () Various Load Testing Tools May 23, 2014 1 / 39 Outline 3 Open Source Tools 1 Load Testing 2 Tools available for Load Testing 4 Proprietary
Various Load Testing Tools Animesh Das May 23, 2014 Animesh Das () Various Load Testing Tools May 23, 2014 1 / 39 Outline 3 Open Source Tools 1 Load Testing 2 Tools available for Load Testing 4 Proprietary
Ordering Offsite Backups
 Introduction The purpose of this Startup Guide is to familiarize you with Own Web Now's Offsite Backup offering and show you how to purchase, deploy and manage the service. Offsite Backup offering is an
Introduction The purpose of this Startup Guide is to familiarize you with Own Web Now's Offsite Backup offering and show you how to purchase, deploy and manage the service. Offsite Backup offering is an
1. Please login to the Own Web Now Support Portal (https://support.ownwebnow.com) with your email address and a password.
 Offsite Backups Introduction The purpose of this Startup Guide is to familiarize you with Own Web Now's Offsite Backup offering and show you how to purchase, deploy and manage the service. Offsite Backup
Offsite Backups Introduction The purpose of this Startup Guide is to familiarize you with Own Web Now's Offsite Backup offering and show you how to purchase, deploy and manage the service. Offsite Backup
Connect to MySQL or Microsoft SQL Server using R
 Connect to MySQL or Microsoft SQL Server using R 1 Introduction Connecting to a MySQL database or Microsoft SQL Server from the R environment can be extremely useful. It allows a research direct access
Connect to MySQL or Microsoft SQL Server using R 1 Introduction Connecting to a MySQL database or Microsoft SQL Server from the R environment can be extremely useful. It allows a research direct access
Perceptive Intelligent Capture Solution Configration Manager
 Perceptive Intelligent Capture Solution Configration Manager Installation and Setup Guide Version: 1.0.x Written by: Product Knowledge, R&D Date: February 2016 2015 Lexmark International Technology, S.A.
Perceptive Intelligent Capture Solution Configration Manager Installation and Setup Guide Version: 1.0.x Written by: Product Knowledge, R&D Date: February 2016 2015 Lexmark International Technology, S.A.
Application note: SQL@CHIP Connecting the IPC@CHIP to a Database
 Application note: SQL@CHIP Connecting the IPC@CHIP to a Database 1. Introduction This application note describes how to connect an IPC@CHIP to a database and exchange data between those. As there are no
Application note: SQL@CHIP Connecting the IPC@CHIP to a Database 1. Introduction This application note describes how to connect an IPC@CHIP to a database and exchange data between those. As there are no
DIPLOMA IN WEBDEVELOPMENT
 DIPLOMA IN WEBDEVELOPMENT Prerequisite skills Basic programming knowledge on C Language or Core Java is must. # Module 1 Basics and introduction to HTML Basic HTML training. Different HTML elements, tags
DIPLOMA IN WEBDEVELOPMENT Prerequisite skills Basic programming knowledge on C Language or Core Java is must. # Module 1 Basics and introduction to HTML Basic HTML training. Different HTML elements, tags
1. Open the preferences screen by opening the Mail menu and selecting Preferences...
 Using TLS encryption with OS X Mail This guide assumes that you have already created an account in Mail. If you have not, you can use the new account wizard. The new account wizard is in the Accounts window
Using TLS encryption with OS X Mail This guide assumes that you have already created an account in Mail. If you have not, you can use the new account wizard. The new account wizard is in the Accounts window
Software Architecture Document
 Software Architecture Document Project Management Cell 1.0 1 of 16 Abstract: This is a software architecture document for Project Management(PM ) cell. It identifies and explains important architectural
Software Architecture Document Project Management Cell 1.0 1 of 16 Abstract: This is a software architecture document for Project Management(PM ) cell. It identifies and explains important architectural
Web Development using PHP (WD_PHP) Duration 1.5 months
 Duration 1.5 months Our program is a practical knowledge oriented program aimed at learning the techniques of web development using PHP, HTML, CSS & JavaScript. It has some unique features which are as
Duration 1.5 months Our program is a practical knowledge oriented program aimed at learning the techniques of web development using PHP, HTML, CSS & JavaScript. It has some unique features which are as
To use MySQL effectively, you need to learn the syntax of a new language and grow
 SESSION 1 Why MySQL? Session Checklist SQL servers in the development process MySQL versus the competition To use MySQL effectively, you need to learn the syntax of a new language and grow comfortable
SESSION 1 Why MySQL? Session Checklist SQL servers in the development process MySQL versus the competition To use MySQL effectively, you need to learn the syntax of a new language and grow comfortable
Web Application Security Part 1
 Web Application Security Part 1 Author : Treasure Priyamal Site : www.treasuresec.com E-mail : treasure@treasuresec.com Twitter :http://twitter.com/treasure_sec Introduction Today we are going to talk
Web Application Security Part 1 Author : Treasure Priyamal Site : www.treasuresec.com E-mail : treasure@treasuresec.com Twitter :http://twitter.com/treasure_sec Introduction Today we are going to talk
Role Based Access Control. Using PHP Sessions
 Role Based Access Control Using PHP Sessions Session Developed in PHP to store client data on the web server, but keep a single session ID on the client machine (cookie) The session ID : identifies the
Role Based Access Control Using PHP Sessions Session Developed in PHP to store client data on the web server, but keep a single session ID on the client machine (cookie) The session ID : identifies the
Welcome to Collage (Draft v0.1)
 Welcome to Collage (Draft v0.1) Table of Contents Welcome to Collage (Draft v0.1)... 1 Table of Contents... 1 Overview... 2 What is Collage?... 3 Getting started... 4 Searching for Images in Collage...
Welcome to Collage (Draft v0.1) Table of Contents Welcome to Collage (Draft v0.1)... 1 Table of Contents... 1 Overview... 2 What is Collage?... 3 Getting started... 4 Searching for Images in Collage...
MySQL for Beginners Ed 3
 Oracle University Contact Us: 1.800.529.0165 MySQL for Beginners Ed 3 Duration: 4 Days What you will learn The MySQL for Beginners course helps you learn about the world's most popular open source database.
Oracle University Contact Us: 1.800.529.0165 MySQL for Beginners Ed 3 Duration: 4 Days What you will learn The MySQL for Beginners course helps you learn about the world's most popular open source database.
Installation Tutorial Script: The Real Estate Script. 1. Please login to download script. On PHP Classifieds Script web site.
 Installation Tutorial Script: The Real Estate Script Thank you for your purchase of The Real Estate Script. This tutorial will guide you threw the installation process. In this install example we use CPanel
Installation Tutorial Script: The Real Estate Script Thank you for your purchase of The Real Estate Script. This tutorial will guide you threw the installation process. In this install example we use CPanel
Oracle Database 10g: Introduction to SQL
 Oracle University Contact Us: 1.800.529.0165 Oracle Database 10g: Introduction to SQL Duration: 5 Days What you will learn This course offers students an introduction to Oracle Database 10g database technology.
Oracle University Contact Us: 1.800.529.0165 Oracle Database 10g: Introduction to SQL Duration: 5 Days What you will learn This course offers students an introduction to Oracle Database 10g database technology.
Eylean server deployment guide
 Eylean server deployment guide Contents 1 Minimum software and hardware requirements... 2 2 Setting up the server using Eylean.Server.Setup.exe wizard... 2 3 Manual setup with Windows authentication -
Eylean server deployment guide Contents 1 Minimum software and hardware requirements... 2 2 Setting up the server using Eylean.Server.Setup.exe wizard... 2 3 Manual setup with Windows authentication -
Real SQL Programming 1
 Real 1 We have seen only how SQL is used at the generic query interface an environment where we sit at a terminal and ask queries of a database. Reality is almost always different: conventional programs
Real 1 We have seen only how SQL is used at the generic query interface an environment where we sit at a terminal and ask queries of a database. Reality is almost always different: conventional programs
WSO2 Business Process Server Clustering Guide for 3.2.0
 WSO2 Business Process Server Clustering Guide for 3.2.0 Throughout this document we would refer to WSO2 Business Process server as BPS. Cluster Architecture Server clustering is done mainly in order to
WSO2 Business Process Server Clustering Guide for 3.2.0 Throughout this document we would refer to WSO2 Business Process server as BPS. Cluster Architecture Server clustering is done mainly in order to
Configuring and Monitoring Database Servers
 Configuring and Monitoring Database Servers eg Enterprise v5.6 Restricted Rights Legend The information contained in this document is confidential and subject to change without notice. No part of this
Configuring and Monitoring Database Servers eg Enterprise v5.6 Restricted Rights Legend The information contained in this document is confidential and subject to change without notice. No part of this
ESET Secure Authentication Java SDK
 ESET Secure Authentication Java SDK Getting Started Guide Document Version 1.0 ESET Secure Authentication Java SDK 2 Introduction This document details what is required to add a second authentication factor
ESET Secure Authentication Java SDK Getting Started Guide Document Version 1.0 ESET Secure Authentication Java SDK 2 Introduction This document details what is required to add a second authentication factor
HIPAA Compliance Use Case
 Overview HIPAA Compliance helps ensure that all medical records, medical billing, and patient accounts meet certain consistent standards with regard to documentation, handling, and privacy. Current Situation
Overview HIPAA Compliance helps ensure that all medical records, medical billing, and patient accounts meet certain consistent standards with regard to documentation, handling, and privacy. Current Situation
External Vulnerability Assessment. -Technical Summary- ABC ORGANIZATION
 External Vulnerability Assessment -Technical Summary- Prepared for: ABC ORGANIZATI On March 9, 2008 Prepared by: AOS Security Solutions 1 of 13 Table of Contents Executive Summary... 3 Discovered Security
External Vulnerability Assessment -Technical Summary- Prepared for: ABC ORGANIZATI On March 9, 2008 Prepared by: AOS Security Solutions 1 of 13 Table of Contents Executive Summary... 3 Discovered Security
IBM Campaign and IBM Silverpop Engage Version 1 Release 2 August 31, 2015. Integration Guide IBM
 IBM Campaign and IBM Silverpop Engage Version 1 Release 2 August 31, 2015 Integration Guide IBM Note Before using this information and the product it supports, read the information in Notices on page 93.
IBM Campaign and IBM Silverpop Engage Version 1 Release 2 August 31, 2015 Integration Guide IBM Note Before using this information and the product it supports, read the information in Notices on page 93.
Intunex Oy Skillhive Service Description 1 / 6
 Intunex Oy Skillhive Service Description 1 / 6 About Skillhive Skillhive is a social business application designed for connecting and sharing expertise within organizations. Skillhive enables employees
Intunex Oy Skillhive Service Description 1 / 6 About Skillhive Skillhive is a social business application designed for connecting and sharing expertise within organizations. Skillhive enables employees
INFORMATION BROCHURE Certificate Course in Web Design Using PHP/MySQL
 INFORMATION BROCHURE OF Certificate Course in Web Design Using PHP/MySQL National Institute of Electronics & Information Technology (An Autonomous Scientific Society of Department of Information Technology,
INFORMATION BROCHURE OF Certificate Course in Web Design Using PHP/MySQL National Institute of Electronics & Information Technology (An Autonomous Scientific Society of Department of Information Technology,
Oracle EXAM - 1Z0-528. Oracle Database 11g Security Essentials. Buy Full Product. http://www.examskey.com/1z0-528.html
 Oracle EXAM - 1Z0-528 Oracle Database 11g Security Essentials Buy Full Product http://www.examskey.com/1z0-528.html Examskey Oracle 1Z0-528 exam demo product is here for you to test the quality of the
Oracle EXAM - 1Z0-528 Oracle Database 11g Security Essentials Buy Full Product http://www.examskey.com/1z0-528.html Examskey Oracle 1Z0-528 exam demo product is here for you to test the quality of the
Seamless Web Data Entry for SAS Applications D.J. Penix, Pinnacle Solutions, Indianapolis, IN
 Seamless Web Data Entry for SAS Applications D.J. Penix, Pinnacle Solutions, Indianapolis, IN ABSTRACT For organizations that need to implement a robust data entry solution, options are somewhat limited
Seamless Web Data Entry for SAS Applications D.J. Penix, Pinnacle Solutions, Indianapolis, IN ABSTRACT For organizations that need to implement a robust data entry solution, options are somewhat limited
Web Application Report
 Web Application Report This report includes important security information about your Web Application. Security Report This report was created by IBM Rational AppScan 8.5.0.1 11/14/2012 8:52:13 AM 11/14/2012
Web Application Report This report includes important security information about your Web Application. Security Report This report was created by IBM Rational AppScan 8.5.0.1 11/14/2012 8:52:13 AM 11/14/2012
news from Tom Bacon about Monday's lecture
 ECRIC news from Tom Bacon about Monday's lecture I won't be at the lecture on Monday due to the work swamp. The plan is still to try and get into the data centre in two weeks time and do the next migration,
ECRIC news from Tom Bacon about Monday's lecture I won't be at the lecture on Monday due to the work swamp. The plan is still to try and get into the data centre in two weeks time and do the next migration,
Database Security. Principle of Least Privilege. DBMS Security. IT420: Database Management and Organization. Database Security.
 Database Security Rights Enforced IT420: Database Management and Organization Database Security Textbook: Ch 9, pg 309-314 PHP and MySQL: Ch 9, pg 217-227 Database security - only authorized users can
Database Security Rights Enforced IT420: Database Management and Organization Database Security Textbook: Ch 9, pg 309-314 PHP and MySQL: Ch 9, pg 217-227 Database security - only authorized users can
SQL. by Steven Holzner, Ph.D. ALPHA. A member of Penguin Group (USA) Inc.
 SQL by Steven Holzner, Ph.D. A ALPHA A member of Penguin Group (USA) Inc. Contents Part 1: Mastering the SQL Basics 1 1 Getting into SQL 3 Understanding Databases 4 Creating Tables Creating Rows and Columns
SQL by Steven Holzner, Ph.D. A ALPHA A member of Penguin Group (USA) Inc. Contents Part 1: Mastering the SQL Basics 1 1 Getting into SQL 3 Understanding Databases 4 Creating Tables Creating Rows and Columns
ICADBS504A Integrate database with a website
 ICADBS504A Integrate database with a website Release: 1 ICADBS504A Integrate database with a website Modification History Release Release 1 Comments This Unit first released with ICA11 Information and
ICADBS504A Integrate database with a website Release: 1 ICADBS504A Integrate database with a website Modification History Release Release 1 Comments This Unit first released with ICA11 Information and
Advanced Web Security, Lab
 Advanced Web Security, Lab Web Server Security: Attacking and Defending November 13, 2013 Read this earlier than one day before the lab! Note that you will not have any internet access during the lab,
Advanced Web Security, Lab Web Server Security: Attacking and Defending November 13, 2013 Read this earlier than one day before the lab! Note that you will not have any internet access during the lab,
IT360: Applied Database Systems. Database Security. Kroenke: Ch 9, pg 309-314 PHP and MySQL: Ch 9, pg 217-227
 IT360: Applied Database Systems Database Security Kroenke: Ch 9, pg 309-314 PHP and MySQL: Ch 9, pg 217-227 1 Database Security Rights Enforced Database security - only authorized users can perform authorized
IT360: Applied Database Systems Database Security Kroenke: Ch 9, pg 309-314 PHP and MySQL: Ch 9, pg 217-227 1 Database Security Rights Enforced Database security - only authorized users can perform authorized
FileMaker 12. ODBC and JDBC Guide
 FileMaker 12 ODBC and JDBC Guide 2004 2012 FileMaker, Inc. All Rights Reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker and Bento are trademarks of FileMaker, Inc.
FileMaker 12 ODBC and JDBC Guide 2004 2012 FileMaker, Inc. All Rights Reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker and Bento are trademarks of FileMaker, Inc.
TrueSight Operations Management Monitoring Studio
 USER DOCUMENTATION APPLICATIONS MONITORING TrueSight Operations Management Monitoring Studio Version 9.0.00 June 2015 Contacting BMC Software You can access the BMC Software Web site at http://www.bmc.com.
USER DOCUMENTATION APPLICATIONS MONITORING TrueSight Operations Management Monitoring Studio Version 9.0.00 June 2015 Contacting BMC Software You can access the BMC Software Web site at http://www.bmc.com.
Oracle Database 11g Security Essentials
 Oracle 1z0-528 Oracle Database 11g Security Essentials Version: 4.2 QUESTION NO: 1 Oracle 1z0-528 Exam Which of the following tasks is the first task to perform when implementing Oracle Database Vault?
Oracle 1z0-528 Oracle Database 11g Security Essentials Version: 4.2 QUESTION NO: 1 Oracle 1z0-528 Exam Which of the following tasks is the first task to perform when implementing Oracle Database Vault?
How-To: MySQL as a linked server in MS SQL Server
 How-To: MySQL as a linked server in MS SQL Server 1 Introduction... 2 2 Why do I want to do this?... 3 3 How?... 4 3.1 Step 1: Create table in SQL Server... 4 3.2 Step 2: Create an identical table in MySQL...
How-To: MySQL as a linked server in MS SQL Server 1 Introduction... 2 2 Why do I want to do this?... 3 3 How?... 4 3.1 Step 1: Create table in SQL Server... 4 3.2 Step 2: Create an identical table in MySQL...
Serious Threat. Targets for Attack. Characterization of Attack. SQL Injection 4/9/2010 COMP620 1. On August 17, 2009, the United States Justice
 Serious Threat SQL Injection COMP620 On August 17, 2009, the United States Justice Department tcharged an American citizen Albert Gonzalez and two unnamed Russians with the theft of 130 million credit
Serious Threat SQL Injection COMP620 On August 17, 2009, the United States Justice Department tcharged an American citizen Albert Gonzalez and two unnamed Russians with the theft of 130 million credit
DBMS / Business Intelligence, SQL Server
 DBMS / Business Intelligence, SQL Server Orsys, with 30 years of experience, is providing high quality, independant State of the Art seminars and hands-on courses corresponding to the needs of IT professionals.
DBMS / Business Intelligence, SQL Server Orsys, with 30 years of experience, is providing high quality, independant State of the Art seminars and hands-on courses corresponding to the needs of IT professionals.
