Remote Testing and Diagnosis of System-on-Chips Using Network Management Frameworks 1
|
|
|
- Grace Hart
- 10 years ago
- Views:
Transcription
1 Remote Testing and Diagnosis of System-on-Chips Using Network Management Frameworks 1 Oussama Laouamri & Chouki Aktouf DeFacTo Technologies, 167 rue de Mayoussard, Moirans, FRANCE Abstract This paper presents a new approach that allows remote testing and diagnosis of complex (Systems-on-Chip) and embedded IP cores. The approach extends both on-chip design-for-test (DFT) architectures and network management protocols to take full benefits from existing networking infrastructures. By running intensive experimentation on ITC 99 and ITC'02 design benchmarks, the efficiency of the proposed testing and diagnosis methodology is analyzed.. 1. Introduction The SoC design paradigm has been widely accepted and implemented in practice during the last few years as an enabling design methodology for the improvement of productivity and the increase of design functionality. The main issues to be faced when testing an SoC are essentially related to the new challenges offered by the growing design complexity. Semiconductor technology feature sizes are getting deep in the submicron area, thus allowing the integration of many complex cores within a single design. In the DSM (Deep Sub-Micron) arena, testing and diagnosis become a major concern for quality and cost. Testing costs are already significant part of the chips total production cost and represent a bottleneck in the successful completion of a design project and its final market success. Unlike other silicon manufacturing costs, the test cost has not benefited as much from the overall downward trend over time. The cost of large automated test equipments (ATE) have steadily risen to multimillion dollars for cutting-edge capabilities. The length and number of test vectors per design are increasing, resulting in each design consuming more time on the testers. The International Technology Roadmap for Semiconductors (ITRS) reported in its 2001 analysis that for some products in certain market segments, test may account for more than 70% of total manufacturing cost, or process technology. The solution to this predicament is reducing the reliance on big testers and instead utilizes more low-cost testers that are DFT-aware.1 1 This research work has been conducted under the support of the Institut National Polytechnique de Grenoble (INPG) Besides traditional manufacturing testing needs, diagnosis and silicon debug can be required at various stages in the lifecycle of an electronic product: during development, qualification, production ramp-up, or in maintenance-like activities. The root cause of the problem-to-be-debugged can lie in the technology used, as well as in the design implementation (or the combination of these); the debugging process has to cover both aspects. Although it is clear that software tools and DFT are gaining in importance, with the advent of SoC, diagnosis and physical debug methods have still an important role to play. Given an SoC which is already integrated within an electronic system, any mechanism that allows (i) remote application of test vectors for any of the SoC blocks and (ii) gathers related test results, is very beneficial. Beyond simplifying the access to CUT (Chip Under Test) blocks from external I/O pins, a remote access should be possible during an SoC live time. Only network infrastructure can allow such easy access. Making an SoC TCP/IP compliant extends testing and diagnosis possibilities. Such a compliance can take benefits from TCP/IP network management protocols such as SNMP (Simple Network Management Protocol). Today, available network infrastructures allow secure data transfer. Such infrastructure can serve as a powerful vehicle to drive test vectors from a test engine to chips and gather test results for a deep analysis. Furthermore, the large experience in network management of electronic and computer systems can assist the testing community in monitoring the behavior of chips during execution of reallife applications. Indeed, network management for local TCP/IP networks is mainstream. To maintain and deliver high service quality to end users, network performance and reliability must be constantly monitored. To date, several research works have addressed hardware-based solutions using network protocols and applications. In the Applied Research Lab (ARL) at Washington University, a set of hardware components for research in the field of networking, switching, routing and active networking have been developed [1]. However, hardware components of layered protocol wrappers (UDP/IP wrappers) [1] have been proposed which process Internet packets in reconfigurable hardware. Hence, several network applications which use this wrapper library [1] have been developed. For instance, an Internet router or a firewall are important applications that use the /DATE EDAA
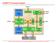
2 Bus Cor e 1 Core 2 Core 3 ID IP TEC TE ST WI R OI D WIP WIP WI P T A M (Te st Ac ce ss M ech a nis m) WIP W SO WI P WIP Agent PR OXY TEC TE ST TEC TE ST ID IP ID IP Wrapper UDP/IP Core 4 Core 4 wrapper library to route and filter packets [2, 3]. A single chip has been used to filter internet SPAM and to guard against several types of network intrusion. In such research, work has not addressed a hardware-based SNMP solution at the application layer. This is important since such a feature has to be considered at the chip level. SNMP is considered as an application layer protocol which uses a TCP/IP suite (in practice UDP is used). In this work, an SNMP agent is developed on a wrapper library described in [1]. This agent is developed within an SoC to help the external testing of the overall SoC. In this work, a new DFT methodology named SNMP/1500 which makes complex SoCs easily testable and diagnosable is presented. By using existing network infrastructure, the proposed methodology can interoperate with existing DFT methodologies and network technologies [4]. Using the IEEE 1500 DFT methodology [5, 6], test logic is extended and made compliant with SNMP TCP/IP management protocol. SNMP is known as a simple and a very powerful management protocol. It embeds a set of features that allow the management of heterogeneous and complex networks. In this research work, SNMP is considered within SoCs to allow either remote testing or real-time monitoring of embedded cores. IEEE 1500 standard [5, 6] enhances testability of SoCs. It helps isolating blocks or IP cores which allows targeting their individual test or monitoring. The proposed architecture embeds two kinds of interfaces. The first interface extends a traditional IEEE 1500 wrapper. The second interface embeds a SNMP proxy agent at the SoC level. Starting from SNMP requests sent by a test engine such as an ATE via TCP/IP network, the on-chip SNMP agent is made capable to perform IEEE 1500 boundary scan operations at the level of an embedded core. This allows support for testing, diagnosis and monitoring of an SoC or a block of an SoC with a full compliance to both the IEEE 1500 and SNMP standards. It is noteworthy that the proposed architecture reuses the existing Test Access Mechanism (TAM). The rest of the paper is organized as follows: Section 2 presents the SNMP/1500 compliant testing architecture. Section 3 presents software considerations that help implementing the proposed approach. In section 4, the main approach which combines both management and testing standards is presented. Section 5 summarizes the implementation results and performance evaluation on monitoring and testing operations. Finally, conclusions are given in section SNMP/1500 Test architecture In this architecture, IEEE 1500 wrappers are extended and represent SNMP agents. An SNMP agent which is illustrated in Figure 1.a is managed by a proxy agent. Test data is carried between IP cores and the proxy agent via a TAM. The proposed SNMP/1500 architecture is compliant with existing TAM structures. As previously detailed in [7, 8], such an architecture embeds new registers such as (IDentifier of IP core), TECTTEST (TECHnique of TEST) and (Object Identifier). The Wrapper Instruction Register () controls wrapper operations. Given control inputs, operations are directly controlled (WIP) by the proxy agent. Furthermore, is extended by new instructions such as WS_GETREQUEST and WS_SETREQUEST. Hence, a SNMP operation is indicated by two parameters: PDU (kind of operation: get-request, set-request...) and [9]. The same behavior is extrapolated at the level of the IP cores test interfaces (extended 1500 wrapper) which ensure a full compliance with the IEEE 1500 standard. During a SNMP operation, the semantics of a IEEE 1500 instruction is completed by a flattened, which is the equivalent to a hierarchical one. Functional Data Input Data Input From Gigabit Ethernet or SONET Line Card Bus Core 1 PROXY Agent Core 2 WIP WIP TAM (Test Access Mechanism) Extended 1500 Wrapper WIP UDP/IP Wrapper SoC : Wrapper Serial Input : Wrapper Serial Output WIP: Wrapper Interface Port : Object IDentifier (a) SNMP/1500 Architecture (i) Core 1 BIST WIP PROXY Agent UDP/IP Wrappers (Test controler) System-on-Chip TAM (ii) Core 2 Core 3 (iii) (b) Various types of IP cores compatible with SNMP/1500 architecture Fig. 1 Proposed SNMP/1500 architecture Functional Data Output Data output to Gigabit Ethernet or SONET Line Card Through the use of network layered protocol UDP/IP wrappers [1], a test operator has the ability to manage the SoC infrastructure by using an SNMP proxy agent module (Fig. 1.a). The proxy agent monitors and controls the embedded cores under test. The proxy agent is used to translate information between SNMP and IEEE std protocols. It provides a protocol conversion function which allows a management station to apply a consistent management framework to all SoC and IP cores infrastructures. The proxy agent can be considered as an IP core, which gets SNMP requests coming from the
3 management station. Such requests are converted into instructions in compliance with the extended 1500 standard. In a similar way, answers from the IP core are converted into an SNMP protocol representation (response). Finally, test results are sent to the ATE as SNMP messages. Figure 1.b shown various types of IP cores which are compliant with the proposed SNMP/1500 architecture. Figure 1.b.i shows an IP core including an internal Built- In-Self-Test (BIST) structure. The SNMP/1500 architecture operates also with the IP cores using the scan test infrastructure (Fig. 1.b.ii). To ensure hierarchical testing, any IP core can be considered as an SoC with a full compliance to the proposed SNMP/1500 architecture (Fig. 1.b.iii). 3. Software design considerations A MIB (Management Information Base) [9] data model represents a software interface between SNMP Framework and the design under test. Hence, a correspondence must exist between the MIB knowledge available to the manager (ATE) and what is really implemented within the agent (SoC). The manager can only carry out the operations which are envisaged in the MIB. Name Description socidentifier X SoC Identifier ipcoreidentifier techniquetest functionaltestvt extestvt X ipCoreIndex IPcore Identifier X ipCoreIndex test technique X ipCoreIndex Functional test X ipCoreIndex External test simplecoretestvt X ipCoreIndex Simple Internal test corebistenable X ipCoreIndex Built-In Self-test Tab. 1 Definition of main managed objects A MIB basic element [7, 8] is called mibsoctest. Any new module is identified by the X, for which X is a reference given by Internet Engineering Task Force (IETF). Given an IP core or an SoC under test, the MIB describes both features of the implemented test techniques which are associated to the IEEE 1500 wrapper and information related to the testing process. The MIB is divided into two parts: the information at the SoC level and those at the level of IP cores. The first part of the MIB is dedicated to the SoC: SoC identifier, configuration of basic components, etc. The second part of the MIB is dedicated to the IP cores. For instance, the table called ipcoreswrappedp1500table is related to the information regarding IEEE 1500 test architecture of each IP core. The index of this table is called ipcoreindex. It represents the logical address of IP cores in the SoC environment. The table 1 shows examples of managed objects. 4. Remote test protocol 4.1. Overview The proposed SNMP/1500 interface (UDP/IP wrapper and Proxy Agent) controls the internal and wrapper boundary scan (WBR of IEEE std. 1500) via the TCP/IP network. This interface assumes the connection of input and output terminals of the scan chains (including the boundary-scan chain), test control pins, and clock pins to ATE channels (managed by existing TCP/IP bandwidths). At the level of every IP core, the access to the rest of the functional pins is achieved via the IEEE 1500 wrapper boundary-scan chain. In this work, both the UDP/IP wrapper and the Proxy Agent constitute an SNMP/1500 wrapper around an SoC (fig. 1). In this case, the DFT for the SoC can be designed without even knowing about the target ATE. Later, by using the re-configurable logic, the number of scan chains and their length can be modified in the embedded cores according to the ATE specification. The basic idea behind the combination of DFT techniques and the SNMP standard is to provide remote access not only to the functional terminals, but also to the internal scan chains via the boundary-scan architecture (IEEE 1500 wrapper), in order to enable even greater scalability of the SoC-ATE interface. Given such an extension, the SoC becomes capable of understanding SNMP requests. SNMP requests (get-request, set-request ) retrieve or modify the value of any managed objects (e.g. IP core identifier, SoC identifier, test vector, tests techniques, etc.) at an SoC level. Our proposed SNMP/1500 wrapper around an IC truly converts the fixed number of external test inputs and outputs, which represent a TCP/IP network interface, into IEEE std dedicated internal test inputs and outputs. Clock Reset DataEn_IN Data_IN 1 0 get-request X (a succession of words (32bits) which constitutes SNMP get -request) DataEn_OUT Data_OUT Address a succession of words (32bits) which constitutes SNMP get -response It generates by proxy agent to TAM It generates by proxy agent to Wrapped IP core get-response X b (logical address of the considered IP core = <5>) (flattened = <7>) It generates by proxy agent to Wrapped IP core WS_GETREQUEST 1500 Instruction It generates by wrapped IP core to proxy agen The contents of register WIP (1500 controls generate by proxy agent to wrapped IP) Fig. 2 Functioning of SNMP/1500 architecture
4 The SNMP set-request message (set-request TV) applies test vectors on the IP cores where both object identifiers () and test vectors are specified. The distinguishes the type of the applied test. The SNMP getrequest message (get-request ) retrieves information of test or monitoring (e.g. IP core identifier, SoC identifier, tests techniques, monitoring registers, etc.) of either the IP core or the SoC by specifying the identity of an instance of the managed object SNMP-IEEE 1500 relationships The relationship between the SNMP requests and those of IEEE 1500 is implemented at the level of the proxy agent. The proxy agent converts SNMP requests into IEEE 1500 instructions. For example, the SNMP request get-request X is used to recover the contents of the register (4 bits which identify the used test technique). This request is converted into WS_GETREQUEST IEEE 1500 instruction (Fig. 2) with a flattened that equals 7. This flattened relates to the hierarchical X Given some IP cores, the last number (ipcoreindex) of the hierarchical represents the logical address (number 5 ) of the considered IP core. To distinguish the type of applied tests at the IP core level the flattened is considered instead of the hierarchical. This choice is motivated by the need for minimizing the processing logic of the hierarchical for each IP core. Figure 2 illustrates this example. In this figure, the data enable signals (DataEn_IN and DataEn_Out) indicate if 32 bit databusses Data_IN and Data_OUT are a valid payload of the SNMP message or not. 5. Simulation results The considered design flow is based on Synopsys tools. Using a 0.18 µ CMOS technology, implementation of a 200 MHz proxy agent requires gates. Given a million gate SoC f2126 from ITC 02 [10] that embeds four cores, 2% of the area overhead is estimated for the SNMP/1500 architecture adapted to this SoC benchmark. This seems reasonable knowing the number of added features. The proxy agent analyzes at 33 MHz to 100 MHz or 200 MHz, suited to the production lines of electronic component manufacturers, who require high throughput. Therefore, the proxy agent can operate on high-speed networks. The theoretical maximum network throughput that can be supported is 3.2 Gb/s for a 100 MHz proxy agent. However, several experimentations at IP core level have been conducted using twenty-two design benchmarks known as ITC 99 benchmarks (b01 to b22) for estimating the cost of area overhead of the extended IEEE std wrapper. In summary, the area cost of the extended wrapper depends on the size of the core, as well as the number of core terminals. We reported 1% additional silicon area for the extended wrapper at IP core level, on top of 4.5% area costs in order to make all cores fully testable with internal full scan. A queueing model is used in the performance analysis of the proposed approach. The OMNeT++ [11] is considered for analyzing the performance of both monitoring and testing. The implemented queueing network (Fig. 3) is the model M/G/1/N FIFO queue system. It has a Poisson arrival distribution, a general service time, a single server and a finite queue (N: system capacity). The service time is calculated for each SNMP request received starting from its contents. The parameters used in the calculation of the service time are: service type, test type, size of monitoring registers, size of test patterns, number of tests per message, chip speed (clock frequency of test architecture), length of each coreinternal scan chain, etc. The setting of these parameters typically influence the number of clock cycles needed to apply one test pattern or to recover one monitoring register. Fig. 3 Queueing network of the proposed approach As shown in figure 3, three main components are considered in the model that is proposed in this work: system under test or monitoring, the generator of SNMP requests and the system (sink) that processes and analyzes SNMP responses. These two last components constitute the testing station (ATE) Monitoring performance analysis Within larger digital systems, you often find a large number of hardware registers (monitoring registers). Generally, these kinds of registers control and monitor hardware functions within the system. It is common practice to spelling registers from the functional blocks (FB) of each IP cores, and interconnect them with the extended P1500 logic proposed in this approach. These facilities allow complete remote management and monitoring of the IP cores activities via simple SNMP requests (get-request, etc.). According to the size of monitoring registers that are embedded within the SoC, the monitoring performance has been estimated. The performance characteristics are evaluated in terms of the response time (delay), traffic intensity and loss rate. The proposed results also show the influence of system parameters such as: queueing capacity, chip speed and interarrival rate (1/λ, versus of arrival rate λ). As discussed earlier, an extensive simulation work has been conducted to show how many parameters for modeling are necessary to influence the performance of monitoring operations. For instance, let us assume that a mean arrival rate is λ=10000 SNMP messages per second, i.e. on average one message appears every 1/λ=1/10000= second. This implies that the interarrival times have an exponential distribution with an average interarrival time of second. Moreover, when the arrival rate λ increases the time of inter-arrival 1/λ
5 decreases. The system capacity (N) represents the number of SNMP messages supported. Cq is the capacity of the queue, therefore N=Cq+1. Figure 4 shows the end-to-end response time (monitoring time) of the system according to the size of monitoring register during the time. Response time (monitoring time) (µs) Size of m onitoring register (bit) Size(t+1) = Size(t) + 4 (a) λ=10000, Speed=100MHz and Cq=1 enhancing the monitoring performance of the proposed SNMP/1500 architecture Testing performance analysis Several simulations have been conducted using several ITC 02 SoC Test Benchmarks [10]. The proposed results also show the influence of system parameters such as: queueing capacity (Cq), chip speed (clock frequency of test architecture) and interarrival rate (SNMP messages per second). Response time (monitoring time) (µs) Size of m onitoring register (bit) Size(t+1) = Size(t) (b) λ=10000, Speed=100MHz and Cq=2 (a) λ =10000, Frequency=100MHz, Cq = 1 response time (monitoring time) (µs) Size of m onitoring regis ter (bit) Size(t+1) = Size(t) + 4 (c) λ=10000, Speed=300MHz and Cq=2 Figure 4 -End-to-end response time(µs) analysis Figure 4 shows high and intensive peaks which explain the progression of the occupancy rate of the SoC under monitoring. If a new message arrives at the input ports of an occupied SoC, then the considered message is placed at the tail of its queue from where it will possibly be withdrawn. The latency between arrival and service is that which constitutes the peaks shown in figure 4. When the arrival rate λ increase, the number of peaks explodes. Also, the monitoring register lengths are a determining factor to regularize the occupancy rate of the SoC. Each time the length of the monitoring registers grow, the SoC load increases which causes increasingly higher latencies. Note that the second curve (Fig. 4.b) presents peaks higher than the first curve. This is due to the waiting capacity Cq. With an increased capacity for waiting, there is less loss, giving higher response times. In figure 4.c, the clock frequency of the on-chip DFT is increased to 300MHz. Note that the intensity of the specific peaks decreases by a third which is why the clock frequency constitutes an important parameter in (c) λ =10000, Frequency =200MHz, Cq = 1 Fig. 5 Instantaneous testing time for SoC d695 (Duke University) In figure 5, the instantaneous testing time is shown according to characteristic of SoC test benchmark d695 (number of test patterns, number and length of scan chains, etc.). The test of the SoC d695 is not complex and its traffic intensity converges towards zero because it does not use very long scan chains. Simulations of figure 5 show specific peaks of differing intensity. Such peaks express the latency of the messages during the functioning of the on-chip DFT. The clock frequency of the architecture influences considerably the performance of the test processes (Fig. 5.a and 5.b). Traffic intensity is
6 a measure of the congestion of the system. If it is near to zero then there is very little queueing, and in general as the traffic intensity increases (to near 1 or even greater than 1) the amount of queueing increases. Table 2 gives simulation results of three ITC 02 SOC Test Benchmarks: u226, p22810, p This table is organized as follows. Column 1 gives the names of the SoCs. In Column 2, the number of modules is listed. Column 3 shows the total number of input/output terminals in the SoC; this is the sum of input/output counts for all modules. Column 4 shows the total number of scan flip-flops in the SoC; this is the sum of scan chain lengths of all modules. Column 5 lists the sum of test pattern counts of all tests. Column 6 gives the test data volume (in Kbytes) generated by the ATE; this is the data volume which is needed for a 100% faults coverage, etc. The next columns give the results in two cases: SoC without a queue (Cq=0) and SoC with a queue where its capacity is only one SNMP message (Cq=1). Column 7 presents the rates of test vectors processed by the SoCs under test. The fault coverage can be deduced from the number of test vectors processed. The testing time (in ms) is given in the last column. It is noteworthy that the benchmarks used have differing test complexities. It is clear that a high pattern count does not directly imply a large test time. The testing time is dependent on the total test pattern time (the number of clock cycles that it takes to load and unload one test pattern). Some tests have fewer test patterns, but utilize very long scan chains, whereas other test have many patterns, but do not use scan chains at all. 6. Conclusion A new approach to remote testing, diagnosis and monitoring of System on Chips and their embedded IP cores is presented. The approach is based on an implementation of a hardware-based network management application called a proxy agent. The proxy agent is a part of a hybrid testing/management solution that is based on a combination of the SNMP and a DFT standard called IEEE Through the use of network layered protocol wrappers, a test operator has the ability to manage and precisely test the activities of embedded cores (IP cores) by using existing TCP/IP networks. The approach was analyzed at the levels of both the IP core and the SoC. In future research SNMPv3 capabilities will be used where the approach will consider authentication and privacy features to improve management critical hardware applications. A more extensive validation of the approach is also planned. References [1] F. Braun, J. W. Lockwood and M. Waldvogel, Layered Protocol Wrappers for Internet Packet Processing in Reconfigurable Hardware, Proc. of Hot Interconnects 9 (HotI-9), pp , California, USA, Aug [2] J. W. Lockwood, C. E. Neely, C. K. Zuver, J. Moscola, S. Dharmapurikar and D. Lim, An Extensible, System-On- Programmable-Chip, Content-Aware Internet Firewall, Field-Programmable Logic and Applications (FPL 03), pp , Lisbon, Portugal, October [3] J. Moscola, J. W. Lockwood, R. P. Loui and M. Pachos, Implementation of a Content-Scanning Module for an Internet Firewall, 11th Annual IEEE Symposium on Field- Programmable Custom Computing Machines (FCCM 03), pp , California, USA, April [4] L. Miclea, Sz. Enyedi, G. Toderean, A. Benso and P. Prinetto, Agent Based DBIST / DBISR and its Web / Wireless Management, International Test Conference 2003, Charlotte, NC, USA, pp , October [5] E. J. Marinissen and Y. Zorian, Challenges in Testing Core-Based System ICs, IEEE Communication Magazine, Vol. 37, No. 6, pp , June [6] E.J Marinissen, R.Kapur, M. Lausberg, T. McLaurin, M. Ricchetti, and Y. Zorian, On IEEE P1500 s Standard for Embedded Core Test, Journal of Electronic Testing: Theory and Applications, vol. 18, no. 4-5, pp , August-October [7] O. Laouamri and C. Aktouf, Enhancing Testability of System on Chips Using Network Management Protocols, In Proc. of IEEE Design Automation and Test in Europe (DATE 04), pp , Paris, France, February [8] O. Laouamri and C. Aktouf, Towards a More Precise Network Management Through Electronic Design, In Proc. of IEEE 3rd International Conference on Networking, (ICN 04), pp , Guadeloupe, France, February [9] D. Harrington, R. Presuhn and B. Wijnen, An Architecture for Describing Simple Network Management Protocol (SNMP) Management Frameworks, RFC 3411, STD 62, Category Standards Track, December [10] E.J. Marinissen, V. Iyengar and K. ChAkrabarty, A Set of Benchmarks for Modular Testing of SOCs, In Proc. of IEEE International Test Conference (ITC 02), pp , Baltimore, MD, October [11] OMNeT++ object-orie:nted discrete event simulation system. URL reference: SoC Test vectors processed (%) Testing time (ms) #IP cores I/Os SFFs Test Patterns ATE Test data (Ko) Cq = 0 Cq=1 Cq = 0 Cq=1 u p p Tab. 2 Performances analysis of testing operations for λ=10000, Clock frequency =100MHz
Testing of Digital System-on- Chip (SoC)
 Testing of Digital System-on- Chip (SoC) 1 Outline of the Talk Introduction to system-on-chip (SoC) design Approaches to SoC design SoC test requirements and challenges Core test wrapper P1500 core test
Testing of Digital System-on- Chip (SoC) 1 Outline of the Talk Introduction to system-on-chip (SoC) design Approaches to SoC design SoC test requirements and challenges Core test wrapper P1500 core test
What is a System on a Chip?
 What is a System on a Chip? Integration of a complete system, that until recently consisted of multiple ICs, onto a single IC. CPU PCI DSP SRAM ROM MPEG SoC DRAM System Chips Why? Characteristics: Complex
What is a System on a Chip? Integration of a complete system, that until recently consisted of multiple ICs, onto a single IC. CPU PCI DSP SRAM ROM MPEG SoC DRAM System Chips Why? Characteristics: Complex
ITEC310 Computer Networks II
 ITEC310 Computer Networks II Chapter 28 Network Management: Department of Information Technology Eastern Mediterranean University Objectives 2/60 After completing this chapter you should be able to do
ITEC310 Computer Networks II Chapter 28 Network Management: Department of Information Technology Eastern Mediterranean University Objectives 2/60 After completing this chapter you should be able to do
An Extensible, System-On-Programmable-Chip, Content-Aware Internet Firewall
 An Extensible, System-On-Programmable-Chip, Content-Aware Internet Firewall John W. Lockwood, Christopher Neely, Christopher Zuver, James Moscola, Sarang Dharmapurikar, and David Lim Applied Research Laboratory
An Extensible, System-On-Programmable-Chip, Content-Aware Internet Firewall John W. Lockwood, Christopher Neely, Christopher Zuver, James Moscola, Sarang Dharmapurikar, and David Lim Applied Research Laboratory
Top-Down Network Design
 Top-Down Network Design Chapter Nine Developing Network Management Strategies Copyright 2010 Cisco Press & Priscilla Oppenheimer 29 Network Management Design A good design can help an organization achieve
Top-Down Network Design Chapter Nine Developing Network Management Strategies Copyright 2010 Cisco Press & Priscilla Oppenheimer 29 Network Management Design A good design can help an organization achieve
High-Performance IP Service Node with Layer 4 to 7 Packet Processing Features
 UDC 621.395.31:681.3 High-Performance IP Service Node with Layer 4 to 7 Packet Processing Features VTsuneo Katsuyama VAkira Hakata VMasafumi Katoh VAkira Takeyama (Manuscript received February 27, 2001)
UDC 621.395.31:681.3 High-Performance IP Service Node with Layer 4 to 7 Packet Processing Features VTsuneo Katsuyama VAkira Hakata VMasafumi Katoh VAkira Takeyama (Manuscript received February 27, 2001)
SNMP Network Management Concepts
 SNMP Network Management Concepts Chu-Sing Yang Department of Electrical Engineering National Cheng Kung University Outline Background Basic Concepts Summary The Origins of TCP/IP Starts at 1969, and founded
SNMP Network Management Concepts Chu-Sing Yang Department of Electrical Engineering National Cheng Kung University Outline Background Basic Concepts Summary The Origins of TCP/IP Starts at 1969, and founded
A Guide to Understanding SNMP
 A Guide to Understanding SNMP Read about SNMP v1, v2c & v3 and Learn How to Configure SNMP on Cisco Routers 2013, SolarWinds Worldwide, LLC. All rights reserved. Share: In small networks with only a few
A Guide to Understanding SNMP Read about SNMP v1, v2c & v3 and Learn How to Configure SNMP on Cisco Routers 2013, SolarWinds Worldwide, LLC. All rights reserved. Share: In small networks with only a few
Serial port interface for microcontroller embedded into integrated power meter
 Serial port interface for microcontroller embedded into integrated power meter Mr. Borisav Jovanović, Prof. dr. Predrag Petković, Prof. dr. Milunka Damnjanović, Faculty of Electronic Engineering Nis, Serbia
Serial port interface for microcontroller embedded into integrated power meter Mr. Borisav Jovanović, Prof. dr. Predrag Petković, Prof. dr. Milunka Damnjanović, Faculty of Electronic Engineering Nis, Serbia
Implementation Details
 LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
Extensible Network Configuration and Communication Framework
 Extensible Network Configuration and Communication Framework Todd Sproull and John Lockwood Applied Research Laboratory Department of Computer Science and Engineering: Washington University in Saint Louis
Extensible Network Configuration and Communication Framework Todd Sproull and John Lockwood Applied Research Laboratory Department of Computer Science and Engineering: Washington University in Saint Louis
Introduction to Network Management
 Introduction to Network Management Chu-Sing Yang Department of Electrical Engineering National Cheng Kung University Outline Introduction Network Management Requirement SNMP family OSI management function
Introduction to Network Management Chu-Sing Yang Department of Electrical Engineering National Cheng Kung University Outline Introduction Network Management Requirement SNMP family OSI management function
ARM Ltd 110 Fulbourn Road, Cambridge, CB1 9NJ, UK. *[email protected]
 Serial Wire Debug and the CoreSight TM Debug and Trace Architecture Eddie Ashfield, Ian Field, Peter Harrod *, Sean Houlihane, William Orme and Sheldon Woodhouse ARM Ltd 110 Fulbourn Road, Cambridge, CB1
Serial Wire Debug and the CoreSight TM Debug and Trace Architecture Eddie Ashfield, Ian Field, Peter Harrod *, Sean Houlihane, William Orme and Sheldon Woodhouse ARM Ltd 110 Fulbourn Road, Cambridge, CB1
Design and Implementation of an On-Chip timing based Permutation Network for Multiprocessor system on Chip
 Design and Implementation of an On-Chip timing based Permutation Network for Multiprocessor system on Chip Ms Lavanya Thunuguntla 1, Saritha Sapa 2 1 Associate Professor, Department of ECE, HITAM, Telangana
Design and Implementation of an On-Chip timing based Permutation Network for Multiprocessor system on Chip Ms Lavanya Thunuguntla 1, Saritha Sapa 2 1 Associate Professor, Department of ECE, HITAM, Telangana
Lecture 4: Introduction to Computer Network Design
 Lecture 4: Introduction to Computer Design Prof. Shervin Shirmohammadi SITE, University of Ottawa Prof. Shervin Shirmohammadi CEG 4185 4-1 Computer s Prof. Shervin Shirmohammadi CEG 4185 4-2 1 Background
Lecture 4: Introduction to Computer Design Prof. Shervin Shirmohammadi SITE, University of Ottawa Prof. Shervin Shirmohammadi CEG 4185 4-1 Computer s Prof. Shervin Shirmohammadi CEG 4185 4-2 1 Background
Simple Network Management Protocol (SNMP) Primer
 Xerox Multifunction Devices July 22, 2003 for the user Simple Network Management Protocol (SNMP) Primer Purpose This document introduces the history, purpose, basic functionality and common uses of SNMP
Xerox Multifunction Devices July 22, 2003 for the user Simple Network Management Protocol (SNMP) Primer Purpose This document introduces the history, purpose, basic functionality and common uses of SNMP
DESIGN AND VERIFICATION OF LSR OF THE MPLS NETWORK USING VHDL
 IJVD: 3(1), 2012, pp. 15-20 DESIGN AND VERIFICATION OF LSR OF THE MPLS NETWORK USING VHDL Suvarna A. Jadhav 1 and U.L. Bombale 2 1,2 Department of Technology Shivaji university, Kolhapur, 1 E-mail: [email protected]
IJVD: 3(1), 2012, pp. 15-20 DESIGN AND VERIFICATION OF LSR OF THE MPLS NETWORK USING VHDL Suvarna A. Jadhav 1 and U.L. Bombale 2 1,2 Department of Technology Shivaji university, Kolhapur, 1 E-mail: [email protected]
Network Management and Monitoring Software
 Page 1 of 7 Network Management and Monitoring Software Many products on the market today provide analytical information to those who are responsible for the management of networked systems or what the
Page 1 of 7 Network Management and Monitoring Software Many products on the market today provide analytical information to those who are responsible for the management of networked systems or what the
White Paper Abstract Disclaimer
 White Paper Synopsis of the Data Streaming Logical Specification (Phase I) Based on: RapidIO Specification Part X: Data Streaming Logical Specification Rev. 1.2, 08/2004 Abstract The Data Streaming specification
White Paper Synopsis of the Data Streaming Logical Specification (Phase I) Based on: RapidIO Specification Part X: Data Streaming Logical Specification Rev. 1.2, 08/2004 Abstract The Data Streaming specification
A New Programmable RF System for System-on-Chip Applications
 Vol. 6, o., April, 011 A ew Programmable RF System for System-on-Chip Applications Jee-Youl Ryu 1, Sung-Woo Kim 1, Jung-Hun Lee 1, Seung-Hun Park 1, and Deock-Ho Ha 1 1 Dept. of Information and Communications
Vol. 6, o., April, 011 A ew Programmable RF System for System-on-Chip Applications Jee-Youl Ryu 1, Sung-Woo Kim 1, Jung-Hun Lee 1, Seung-Hun Park 1, and Deock-Ho Ha 1 1 Dept. of Information and Communications
packet retransmitting based on dynamic route table technology, as shown in fig. 2 and 3.
 Implementation of an Emulation Environment for Large Scale Network Security Experiments Cui Yimin, Liu Li, Jin Qi, Kuang Xiaohui National Key Laboratory of Science and Technology on Information System
Implementation of an Emulation Environment for Large Scale Network Security Experiments Cui Yimin, Liu Li, Jin Qi, Kuang Xiaohui National Key Laboratory of Science and Technology on Information System
Chapter 2 - The TCP/IP and OSI Networking Models
 Chapter 2 - The TCP/IP and OSI Networking Models TCP/IP : Transmission Control Protocol/Internet Protocol OSI : Open System Interconnection RFC Request for Comments TCP/IP Architecture Layers Application
Chapter 2 - The TCP/IP and OSI Networking Models TCP/IP : Transmission Control Protocol/Internet Protocol OSI : Open System Interconnection RFC Request for Comments TCP/IP Architecture Layers Application
AERONAUTICAL COMMUNICATIONS PANEL (ACP) ATN and IP
 AERONAUTICAL COMMUNICATIONS PANEL (ACP) Working Group I - 7 th Meeting Móntreal, Canada 2 6 June 2008 Agenda Item x : ATN and IP Information Paper Presented by Naoki Kanada Electronic Navigation Research
AERONAUTICAL COMMUNICATIONS PANEL (ACP) Working Group I - 7 th Meeting Móntreal, Canada 2 6 June 2008 Agenda Item x : ATN and IP Information Paper Presented by Naoki Kanada Electronic Navigation Research
Architectural Level Power Consumption of Network on Chip. Presenter: YUAN Zheng
 Architectural Level Power Consumption of Network Presenter: YUAN Zheng Why Architectural Low Power Design? High-speed and large volume communication among different parts on a chip Problem: Power consumption
Architectural Level Power Consumption of Network Presenter: YUAN Zheng Why Architectural Low Power Design? High-speed and large volume communication among different parts on a chip Problem: Power consumption
How To Configure Voice Vlan On An Ip Phone
 1 VLAN (Virtual Local Area Network) is used to logically divide a physical network into several broadcast domains. VLAN membership can be configured through software instead of physically relocating devices
1 VLAN (Virtual Local Area Network) is used to logically divide a physical network into several broadcast domains. VLAN membership can be configured through software instead of physically relocating devices
TABLE OF CONTENTS. xiii List of Tables. xviii List of Design-for-Test Rules. xix Preface to the First Edition. xxi Preface to the Second Edition
 TABLE OF CONTENTS List of Figures xiii List of Tables xviii List of Design-for-Test Rules xix Preface to the First Edition xxi Preface to the Second Edition xxiii Acknowledgement xxv 1 Boundary-Scan Basics
TABLE OF CONTENTS List of Figures xiii List of Tables xviii List of Design-for-Test Rules xix Preface to the First Edition xxi Preface to the Second Edition xxiii Acknowledgement xxv 1 Boundary-Scan Basics
Network System Design Lesson Objectives
 Network System Design Lesson Unit 1: INTRODUCTION TO NETWORK DESIGN Assignment Customer Needs and Goals Identify the purpose and parts of a good customer needs report. Gather information to identify network
Network System Design Lesson Unit 1: INTRODUCTION TO NETWORK DESIGN Assignment Customer Needs and Goals Identify the purpose and parts of a good customer needs report. Gather information to identify network
Chapter 1 Reading Organizer
 Chapter 1 Reading Organizer After completion of this chapter, you should be able to: Describe convergence of data, voice and video in the context of switched networks Describe a switched network in a small
Chapter 1 Reading Organizer After completion of this chapter, you should be able to: Describe convergence of data, voice and video in the context of switched networks Describe a switched network in a small
UPPER LAYER SWITCHING
 52-20-40 DATA COMMUNICATIONS MANAGEMENT UPPER LAYER SWITCHING Gilbert Held INSIDE Upper Layer Operations; Address Translation; Layer 3 Switching; Layer 4 Switching OVERVIEW The first series of LAN switches
52-20-40 DATA COMMUNICATIONS MANAGEMENT UPPER LAYER SWITCHING Gilbert Held INSIDE Upper Layer Operations; Address Translation; Layer 3 Switching; Layer 4 Switching OVERVIEW The first series of LAN switches
s@lm@n CompTIA Exam N10-006 CompTIA Network+ certification Version: 5.1 [ Total Questions: 1146 ]
![s@lm@n CompTIA Exam N10-006 CompTIA Network+ certification Version: 5.1 [ Total Questions: 1146 ] s@lm@n CompTIA Exam N10-006 CompTIA Network+ certification Version: 5.1 [ Total Questions: 1146 ]](/thumbs/27/9611247.jpg) s@lm@n CompTIA Exam N10-006 CompTIA Network+ certification Version: 5.1 [ Total Questions: 1146 ] Topic break down Topic No. of Questions Topic 1: Network Architecture 183 Topic 2: Network Operations 149
s@lm@n CompTIA Exam N10-006 CompTIA Network+ certification Version: 5.1 [ Total Questions: 1146 ] Topic break down Topic No. of Questions Topic 1: Network Architecture 183 Topic 2: Network Operations 149
10/100/1000Mbps Ethernet MAC with Protocol Acceleration MAC-NET Core with Avalon Interface
 1 Introduction Ethernet is available in different speeds (10/100/1000 and 10000Mbps) and provides connectivity to meet a wide range of needs from desktop to switches. MorethanIP IP solutions provide a
1 Introduction Ethernet is available in different speeds (10/100/1000 and 10000Mbps) and provides connectivity to meet a wide range of needs from desktop to switches. MorethanIP IP solutions provide a
Using SNMP for Remote Measurement and Automation
 Using SNMP for Remote Measurement and Automation Nikolay Kakanakov, Elena Kostadinova Department of Computer Systems and Technologies, Technical University of Sofia, branch Plovdiv, 61 St. Petersburg Blvd.,
Using SNMP for Remote Measurement and Automation Nikolay Kakanakov, Elena Kostadinova Department of Computer Systems and Technologies, Technical University of Sofia, branch Plovdiv, 61 St. Petersburg Blvd.,
Seamless Congestion Control over Wired and Wireless IEEE 802.11 Networks
 Seamless Congestion Control over Wired and Wireless IEEE 802.11 Networks Vasilios A. Siris and Despina Triantafyllidou Institute of Computer Science (ICS) Foundation for Research and Technology - Hellas
Seamless Congestion Control over Wired and Wireless IEEE 802.11 Networks Vasilios A. Siris and Despina Triantafyllidou Institute of Computer Science (ICS) Foundation for Research and Technology - Hellas
Performance Evaluation of Linux Bridge
 Performance Evaluation of Linux Bridge James T. Yu School of Computer Science, Telecommunications, and Information System (CTI) DePaul University ABSTRACT This paper studies a unique network feature, Ethernet
Performance Evaluation of Linux Bridge James T. Yu School of Computer Science, Telecommunications, and Information System (CTI) DePaul University ABSTRACT This paper studies a unique network feature, Ethernet
G. Squillero, M. Rebaudengo. Test Techniques for Systems-on-a-Chip
 G. Squillero, M. Rebaudengo Test Techniques for Systems-on-a-Chip December 2005 Preface Fast innovation in VLSI technologies makes possible the integration a complete system into a single chip (System-on-Chip,
G. Squillero, M. Rebaudengo Test Techniques for Systems-on-a-Chip December 2005 Preface Fast innovation in VLSI technologies makes possible the integration a complete system into a single chip (System-on-Chip,
Computer Network. Interconnected collection of autonomous computers that are able to exchange information
 Introduction Computer Network. Interconnected collection of autonomous computers that are able to exchange information No master/slave relationship between the computers in the network Data Communications.
Introduction Computer Network. Interconnected collection of autonomous computers that are able to exchange information No master/slave relationship between the computers in the network Data Communications.
Architecture of distributed network processors: specifics of application in information security systems
 Architecture of distributed network processors: specifics of application in information security systems V.Zaborovsky, Politechnical University, Sait-Petersburg, Russia [email protected] 1. Introduction Modern
Architecture of distributed network processors: specifics of application in information security systems V.Zaborovsky, Politechnical University, Sait-Petersburg, Russia [email protected] 1. Introduction Modern
Study of Network Performance Monitoring Tools-SNMP
 310 Study of Network Performance Monitoring Tools-SNMP Mr. G.S. Nagaraja, Ranjana R.Chittal, Kamod Kumar Summary Computer networks have influenced the software industry by providing enormous resources
310 Study of Network Performance Monitoring Tools-SNMP Mr. G.S. Nagaraja, Ranjana R.Chittal, Kamod Kumar Summary Computer networks have influenced the software industry by providing enormous resources
VLSI Design Verification and Testing
 VLSI Design Verification and Testing Instructor Chintan Patel (Contact using email: [email protected]). Text Michael L. Bushnell and Vishwani D. Agrawal, Essentials of Electronic Testing, for Digital,
VLSI Design Verification and Testing Instructor Chintan Patel (Contact using email: [email protected]). Text Michael L. Bushnell and Vishwani D. Agrawal, Essentials of Electronic Testing, for Digital,
IP SLAs Overview. Finding Feature Information. Information About IP SLAs. IP SLAs Technology Overview
 This module describes IP Service Level Agreements (SLAs). IP SLAs allows Cisco customers to analyze IP service levels for IP applications and services, to increase productivity, to lower operational costs,
This module describes IP Service Level Agreements (SLAs). IP SLAs allows Cisco customers to analyze IP service levels for IP applications and services, to increase productivity, to lower operational costs,
4 Internet QoS Management
 4 Internet QoS Management Rolf Stadler School of Electrical Engineering KTH Royal Institute of Technology [email protected] September 2008 Overview Network Management Performance Mgt QoS Mgt Resource Control
4 Internet QoS Management Rolf Stadler School of Electrical Engineering KTH Royal Institute of Technology [email protected] September 2008 Overview Network Management Performance Mgt QoS Mgt Resource Control
A Study of Network Security Systems
 A Study of Network Security Systems Ramy K. Khalil, Fayez W. Zaki, Mohamed M. Ashour, Mohamed A. Mohamed Department of Communication and Electronics Mansoura University El Gomhorya Street, Mansora,Dakahlya
A Study of Network Security Systems Ramy K. Khalil, Fayez W. Zaki, Mohamed M. Ashour, Mohamed A. Mohamed Department of Communication and Electronics Mansoura University El Gomhorya Street, Mansora,Dakahlya
Product Overview. Product Family. Product Features. Powerful intrusion detection and monitoring capacity
 NIP IDS Product Overview The Network Intelligent Police (NIP) Intrusion Detection System (IDS) is a new generation of session-based intelligent network IDS developed by Huaweisymantec. Deployed in key
NIP IDS Product Overview The Network Intelligent Police (NIP) Intrusion Detection System (IDS) is a new generation of session-based intelligent network IDS developed by Huaweisymantec. Deployed in key
How To Understand Network Performance Monitoring And Performance Monitoring Tools
 http://www.cse.wustl.edu/~jain/cse567-06/ftp/net_traffic_monitors2/ind... 1 of 11 SNMP and Beyond: A Survey of Network Performance Monitoring Tools Paul Moceri, [email protected] Abstract The growing
http://www.cse.wustl.edu/~jain/cse567-06/ftp/net_traffic_monitors2/ind... 1 of 11 SNMP and Beyond: A Survey of Network Performance Monitoring Tools Paul Moceri, [email protected] Abstract The growing
Block based, file-based, combination. Component based, solution based
 The Wide Spread Role of 10-Gigabit Ethernet in Storage This paper provides an overview of SAN and NAS storage solutions, highlights the ubiquitous role of 10 Gigabit Ethernet in these solutions, and illustrates
The Wide Spread Role of 10-Gigabit Ethernet in Storage This paper provides an overview of SAN and NAS storage solutions, highlights the ubiquitous role of 10 Gigabit Ethernet in these solutions, and illustrates
This topic lists the key mechanisms use to implement QoS in an IP network.
 IP QoS Mechanisms QoS Mechanisms This topic lists the key mechanisms use to implement QoS in an IP network. QoS Mechanisms Classification: Each class-oriented QoS mechanism has to support some type of
IP QoS Mechanisms QoS Mechanisms This topic lists the key mechanisms use to implement QoS in an IP network. QoS Mechanisms Classification: Each class-oriented QoS mechanism has to support some type of
NETASQ & PCI DSS. Is NETASQ compatible with PCI DSS? NG Firewall version 9
 NETASQ & PCI DSS Is NETASQ compatible with PCI DSS? We have often been asked this question. Unfortunately, even the best firewall is but an element in the process of PCI DSS certification. This document
NETASQ & PCI DSS Is NETASQ compatible with PCI DSS? We have often been asked this question. Unfortunately, even the best firewall is but an element in the process of PCI DSS certification. This document
Network Monitoring. Chu-Sing Yang. Department of Electrical Engineering National Cheng Kung University
 Network Monitoring Chu-Sing Yang Department of Electrical Engineering National Cheng Kung University Outline Introduction Network monitoring architecture Performance monitoring Fault monitoring Accounting
Network Monitoring Chu-Sing Yang Department of Electrical Engineering National Cheng Kung University Outline Introduction Network monitoring architecture Performance monitoring Fault monitoring Accounting
A NOVEL RESOURCE EFFICIENT DMMS APPROACH
 A NOVEL RESOURCE EFFICIENT DMMS APPROACH FOR NETWORK MONITORING AND CONTROLLING FUNCTIONS Golam R. Khan 1, Sharmistha Khan 2, Dhadesugoor R. Vaman 3, and Suxia Cui 4 Department of Electrical and Computer
A NOVEL RESOURCE EFFICIENT DMMS APPROACH FOR NETWORK MONITORING AND CONTROLLING FUNCTIONS Golam R. Khan 1, Sharmistha Khan 2, Dhadesugoor R. Vaman 3, and Suxia Cui 4 Department of Electrical and Computer
Network Virtualization for Large-Scale Data Centers
 Network Virtualization for Large-Scale Data Centers Tatsuhiro Ando Osamu Shimokuni Katsuhito Asano The growing use of cloud technology by large enterprises to support their business continuity planning
Network Virtualization for Large-Scale Data Centers Tatsuhiro Ando Osamu Shimokuni Katsuhito Asano The growing use of cloud technology by large enterprises to support their business continuity planning
Tutorial on Network Management and Measurements. Tasos Alexandridis [email protected]
 Tutorial on Network Management and Measurements Tasos Alexandridis [email protected] Network management Simple Network Management Protocol (SNMP) AP s SYSLOG messages Network Measurements and Analysis
Tutorial on Network Management and Measurements Tasos Alexandridis [email protected] Network management Simple Network Management Protocol (SNMP) AP s SYSLOG messages Network Measurements and Analysis
Huawei One Net Campus Network Solution
 Huawei One Net Campus Network Solution 2 引 言 3 园 区 网 面 临 的 挑 战 4 华 为 园 区 网 解 决 方 案 介 绍 6 华 为 园 区 网 解 决 方 案 对 应 产 品 组 合 6 结 束 语 Introduction campus network is an internal network of an enterprise or organization,
Huawei One Net Campus Network Solution 2 引 言 3 园 区 网 面 临 的 挑 战 4 华 为 园 区 网 解 决 方 案 介 绍 6 华 为 园 区 网 解 决 方 案 对 应 产 品 组 合 6 结 束 语 Introduction campus network is an internal network of an enterprise or organization,
A Framework for End-to-End Proactive Network Management
 A Framework for End-to-End Proactive Network Management S. Hariri, Y. Kim, P. Varshney, Department of Electrical Engineering and Computer Science Syracuse University, Syracuse, NY 13244 {hariri, yhkim,varshey}@cat.syr.edu
A Framework for End-to-End Proactive Network Management S. Hariri, Y. Kim, P. Varshney, Department of Electrical Engineering and Computer Science Syracuse University, Syracuse, NY 13244 {hariri, yhkim,varshey}@cat.syr.edu
IP SAN Best Practices
 IP SAN Best Practices A Dell Technical White Paper PowerVault MD3200i Storage Arrays THIS WHITE PAPER IS FOR INFORMATIONAL PURPOSES ONLY, AND MAY CONTAIN TYPOGRAPHICAL ERRORS AND TECHNICAL INACCURACIES.
IP SAN Best Practices A Dell Technical White Paper PowerVault MD3200i Storage Arrays THIS WHITE PAPER IS FOR INFORMATIONAL PURPOSES ONLY, AND MAY CONTAIN TYPOGRAPHICAL ERRORS AND TECHNICAL INACCURACIES.
Cisco Bandwidth Quality Manager 3.1
 Cisco Bandwidth Quality Manager 3.1 Product Overview Providing the required quality of service (QoS) to applications on a wide-area access network consistently and reliably is increasingly becoming a challenge.
Cisco Bandwidth Quality Manager 3.1 Product Overview Providing the required quality of service (QoS) to applications on a wide-area access network consistently and reliably is increasingly becoming a challenge.
VMWARE WHITE PAPER 1
 1 VMWARE WHITE PAPER Introduction This paper outlines the considerations that affect network throughput. The paper examines the applications deployed on top of a virtual infrastructure and discusses the
1 VMWARE WHITE PAPER Introduction This paper outlines the considerations that affect network throughput. The paper examines the applications deployed on top of a virtual infrastructure and discusses the
Linear Motion and Assembly Technologies Pneumatics Service. Industrial Ethernet: The key advantages of SERCOS III
 Electric Drives and Controls Hydraulics Linear Motion and Assembly Technologies Pneumatics Service profile Drive & Control Industrial Ethernet: The key advantages of SERCOS III SERCOS III is the open,
Electric Drives and Controls Hydraulics Linear Motion and Assembly Technologies Pneumatics Service profile Drive & Control Industrial Ethernet: The key advantages of SERCOS III SERCOS III is the open,
CCNA R&S: Introduction to Networks. Chapter 5: Ethernet
 CCNA R&S: Introduction to Networks Chapter 5: Ethernet 5.0.1.1 Introduction The OSI physical layer provides the means to transport the bits that make up a data link layer frame across the network media.
CCNA R&S: Introduction to Networks Chapter 5: Ethernet 5.0.1.1 Introduction The OSI physical layer provides the means to transport the bits that make up a data link layer frame across the network media.
AdSec: A System for Adaptive Network Security
 AdSec: A System for Adaptive Network Security Kihong Park Network Systems Lab & CERIAS Dept. of Computer Sciences Purdue University [email protected] Joint: E. Spafford (co-pi), M. Tripunitara, G. Nalawade
AdSec: A System for Adaptive Network Security Kihong Park Network Systems Lab & CERIAS Dept. of Computer Sciences Purdue University [email protected] Joint: E. Spafford (co-pi), M. Tripunitara, G. Nalawade
SNMP Extensions for a Self Healing Network
 SNMP Extensions for a Self Healing Network Background Patent 6,088,141: This is a self healing network depending on additional hardware. It requires a second ring of connection to handle recovery operations.
SNMP Extensions for a Self Healing Network Background Patent 6,088,141: This is a self healing network depending on additional hardware. It requires a second ring of connection to handle recovery operations.
C101:IntroductiontotheCommunications ProtocolsandTheirUsesin ITSApplications(K)
 C101:IntroductiontotheCommunications ProtocolsandTheirUsesin ITSApplications(K) C101: Introduction to Communications Protocols and Their Table of Contents Introduction/Purpose... 2 NTCIP Framework... 3
C101:IntroductiontotheCommunications ProtocolsandTheirUsesin ITSApplications(K) C101: Introduction to Communications Protocols and Their Table of Contents Introduction/Purpose... 2 NTCIP Framework... 3
Lecture Objectives. Lecture 07 Mobile Networks: TCP in Wireless Networks. Agenda. TCP Flow Control. Flow Control Can Limit Throughput (1)
 Lecture Objectives Wireless and Mobile Systems Design Lecture 07 Mobile Networks: TCP in Wireless Networks Describe TCP s flow control mechanism Describe operation of TCP Reno and TCP Vegas, including
Lecture Objectives Wireless and Mobile Systems Design Lecture 07 Mobile Networks: TCP in Wireless Networks Describe TCP s flow control mechanism Describe operation of TCP Reno and TCP Vegas, including
Network Considerations for IP Video
 Network Considerations for IP Video H.323 is an ITU standard for transmitting voice and video using Internet Protocol (IP). It differs from many other typical IP based applications in that it is a real-time
Network Considerations for IP Video H.323 is an ITU standard for transmitting voice and video using Internet Protocol (IP). It differs from many other typical IP based applications in that it is a real-time
Design of Hospital EMR Management System
 International Journal of u-and e-service, Science and Technology, pp.341-348 http://dx.doi.org/10.14257/ijunnesst.2014.7.5.30 Design of Hospital EMR Management System Hongfeng He and Yixin Yan * Harbin
International Journal of u-and e-service, Science and Technology, pp.341-348 http://dx.doi.org/10.14257/ijunnesst.2014.7.5.30 Design of Hospital EMR Management System Hongfeng He and Yixin Yan * Harbin
Low-Overhead Hard Real-time Aware Interconnect Network Router
 Low-Overhead Hard Real-time Aware Interconnect Network Router Michel A. Kinsy! Department of Computer and Information Science University of Oregon Srinivas Devadas! Department of Electrical Engineering
Low-Overhead Hard Real-time Aware Interconnect Network Router Michel A. Kinsy! Department of Computer and Information Science University of Oregon Srinivas Devadas! Department of Electrical Engineering
Know the signs of potential problems. Prevent problems before they occur. This unit contains the following three lessons:
 Unit 6 Router Management Overview Description With today s networks growing exponentially, management is a key to quality of network performance. People depend on their networks and performance issues
Unit 6 Router Management Overview Description With today s networks growing exponentially, management is a key to quality of network performance. People depend on their networks and performance issues
Smart Queue Scheduling for QoS Spring 2001 Final Report
 ENSC 833-3: NETWORK PROTOCOLS AND PERFORMANCE CMPT 885-3: SPECIAL TOPICS: HIGH-PERFORMANCE NETWORKS Smart Queue Scheduling for QoS Spring 2001 Final Report By Haijing Fang([email protected]) & Liu Tang([email protected])
ENSC 833-3: NETWORK PROTOCOLS AND PERFORMANCE CMPT 885-3: SPECIAL TOPICS: HIGH-PERFORMANCE NETWORKS Smart Queue Scheduling for QoS Spring 2001 Final Report By Haijing Fang([email protected]) & Liu Tang([email protected])
A Generic Network Interface Architecture for a Networked Processor Array (NePA)
 A Generic Network Interface Architecture for a Networked Processor Array (NePA) Seung Eun Lee, Jun Ho Bahn, Yoon Seok Yang, and Nader Bagherzadeh EECS @ University of California, Irvine Outline Introduction
A Generic Network Interface Architecture for a Networked Processor Array (NePA) Seung Eun Lee, Jun Ho Bahn, Yoon Seok Yang, and Nader Bagherzadeh EECS @ University of California, Irvine Outline Introduction
Introduction. Background
 Introduction By far, the most widely used networking technology in Wide Area Networks (WANs) is SONET/SDH. With the growth of Ethernet now into Metropolitan Area Networks (MANs) there is a growing need
Introduction By far, the most widely used networking technology in Wide Area Networks (WANs) is SONET/SDH. With the growth of Ethernet now into Metropolitan Area Networks (MANs) there is a growing need
Comparison of SNMP. Versions 1, 2 and 3
 Comparison of SNMP 1 Comparison of SNMP Versions 1, 2 and 3 Eddie Bibbs Brandon Matt ICTN 4600-001 Xin Tang April 17, 2006 Comparison of SNMP 2 During its development history, the communities of researchers,
Comparison of SNMP 1 Comparison of SNMP Versions 1, 2 and 3 Eddie Bibbs Brandon Matt ICTN 4600-001 Xin Tang April 17, 2006 Comparison of SNMP 2 During its development history, the communities of researchers,
Internet Concepts. What is a Network?
 Internet Concepts Network, Protocol Client/server model TCP/IP Internet Addressing Development of the Global Internet Autumn 2004 Trinity College, Dublin 1 What is a Network? A group of two or more devices,
Internet Concepts Network, Protocol Client/server model TCP/IP Internet Addressing Development of the Global Internet Autumn 2004 Trinity College, Dublin 1 What is a Network? A group of two or more devices,
Network Management - SNMP
 Network Management - SNMP Simple Network Management Protocol Networks are indispensable More complexity makes failure more likely Require automatic network management tools Standards required to allow
Network Management - SNMP Simple Network Management Protocol Networks are indispensable More complexity makes failure more likely Require automatic network management tools Standards required to allow
Cisco PIX vs. Checkpoint Firewall
 Cisco PIX vs. Checkpoint Firewall Introduction Firewall technology ranges from packet filtering to application-layer proxies, to Stateful inspection; each technique gleaning the benefits from its predecessor.
Cisco PIX vs. Checkpoint Firewall Introduction Firewall technology ranges from packet filtering to application-layer proxies, to Stateful inspection; each technique gleaning the benefits from its predecessor.
CISCO SMB CLASS MOBILITY AND WIRELESS SOLUTIONS: THE RESPONSIVE WORKFORCE
 CISCO SMB CLASS MOBILITY AND WIRELESS SOLUTIONS: THE RESPONSIVE WORKFORCE BLUEPRINT Cisco Small and Medium Business Class Solutions Cisco offers small and medium-sized business customers a suite of intelligent
CISCO SMB CLASS MOBILITY AND WIRELESS SOLUTIONS: THE RESPONSIVE WORKFORCE BLUEPRINT Cisco Small and Medium Business Class Solutions Cisco offers small and medium-sized business customers a suite of intelligent
MEASURING WORKLOAD PERFORMANCE IS THE INFRASTRUCTURE A PROBLEM?
 MEASURING WORKLOAD PERFORMANCE IS THE INFRASTRUCTURE A PROBLEM? Ashutosh Shinde Performance Architect [email protected] Validating if the workload generated by the load generating tools is applied
MEASURING WORKLOAD PERFORMANCE IS THE INFRASTRUCTURE A PROBLEM? Ashutosh Shinde Performance Architect [email protected] Validating if the workload generated by the load generating tools is applied
Frequently Asked Questions
 Frequently Asked Questions 1. Q: What is the Network Data Tunnel? A: Network Data Tunnel (NDT) is a software-based solution that accelerates data transfer in point-to-point or point-to-multipoint network
Frequently Asked Questions 1. Q: What is the Network Data Tunnel? A: Network Data Tunnel (NDT) is a software-based solution that accelerates data transfer in point-to-point or point-to-multipoint network
Hardware Implementation of Improved Adaptive NoC Router with Flit Flow History based Load Balancing Selection Strategy
 Hardware Implementation of Improved Adaptive NoC Rer with Flit Flow History based Load Balancing Selection Strategy Parag Parandkar 1, Sumant Katiyal 2, Geetesh Kwatra 3 1,3 Research Scholar, School of
Hardware Implementation of Improved Adaptive NoC Rer with Flit Flow History based Load Balancing Selection Strategy Parag Parandkar 1, Sumant Katiyal 2, Geetesh Kwatra 3 1,3 Research Scholar, School of
10/100/1000 Ethernet MAC with Protocol Acceleration MAC-NET Core
 1 Introduction The implements, in conjunction with a triple speed 10/100/1000 MAC, Layer 3 network acceleration functions, which are designed to accelerate the processing of various common networking protocols
1 Introduction The implements, in conjunction with a triple speed 10/100/1000 MAC, Layer 3 network acceleration functions, which are designed to accelerate the processing of various common networking protocols
Get the best performance from your LTE Network with MOBIPASS
 Get the best performance from your LTE Network with MOBIPASS The most powerful, user friendly and scalable enodeb test tools family for Network Equipement Manufacturers and Mobile Network Operators Network
Get the best performance from your LTE Network with MOBIPASS The most powerful, user friendly and scalable enodeb test tools family for Network Equipement Manufacturers and Mobile Network Operators Network
Chapter 3. TCP/IP Networks. 3.1 Internet Protocol version 4 (IPv4)
 Chapter 3 TCP/IP Networks 3.1 Internet Protocol version 4 (IPv4) Internet Protocol version 4 is the fourth iteration of the Internet Protocol (IP) and it is the first version of the protocol to be widely
Chapter 3 TCP/IP Networks 3.1 Internet Protocol version 4 (IPv4) Internet Protocol version 4 is the fourth iteration of the Internet Protocol (IP) and it is the first version of the protocol to be widely
Network Attached Storage. Jinfeng Yang Oct/19/2015
 Network Attached Storage Jinfeng Yang Oct/19/2015 Outline Part A 1. What is the Network Attached Storage (NAS)? 2. What are the applications of NAS? 3. The benefits of NAS. 4. NAS s performance (Reliability
Network Attached Storage Jinfeng Yang Oct/19/2015 Outline Part A 1. What is the Network Attached Storage (NAS)? 2. What are the applications of NAS? 3. The benefits of NAS. 4. NAS s performance (Reliability
The ABCs of SNMP. Info Sheet. The ABC of SNMP INTRODUCTION. SNMP Versions
 The ABCs of SNMP INTRODUCTION One of the numerous acronyms from the Internet world is SNMP which stands for Simple Network Management Protocol. Of course, anything termed simple is suspect. SNMP is an
The ABCs of SNMP INTRODUCTION One of the numerous acronyms from the Internet world is SNMP which stands for Simple Network Management Protocol. Of course, anything termed simple is suspect. SNMP is an
Network Simulation Traffic, Paths and Impairment
 Network Simulation Traffic, Paths and Impairment Summary Network simulation software and hardware appliances can emulate networks and network hardware. Wide Area Network (WAN) emulation, by simulating
Network Simulation Traffic, Paths and Impairment Summary Network simulation software and hardware appliances can emulate networks and network hardware. Wide Area Network (WAN) emulation, by simulating
The Boundary Scan Test (BST) technology
 The Boundary Scan Test () technology J. M. Martins Ferreira FEUP / DEEC - Rua Dr. Roberto Frias 42-537 Porto - PORTUGAL Tel. 35 225 8 748 / Fax: 35 225 8 443 ([email protected] / http://www.fe.up.pt/~jmf) Objectives
The Boundary Scan Test () technology J. M. Martins Ferreira FEUP / DEEC - Rua Dr. Roberto Frias 42-537 Porto - PORTUGAL Tel. 35 225 8 748 / Fax: 35 225 8 443 ([email protected] / http://www.fe.up.pt/~jmf) Objectives
SNMP I/O Devices Make Monitoring Environmental Conditions Easy. Austin Lin Product Manager Wayne Chen Technical Service Moxa Inc.
 SNMP I/O Devices Make Monitoring Environmental Conditions Easy Austin Lin Product Manager Wayne Chen Technical Service Moxa Inc. Overview According to the US Census Bureau s 2012 Statistical Abstract there
SNMP I/O Devices Make Monitoring Environmental Conditions Easy Austin Lin Product Manager Wayne Chen Technical Service Moxa Inc. Overview According to the US Census Bureau s 2012 Statistical Abstract there
Considerations In Developing Firewall Selection Criteria. Adeptech Systems, Inc.
 Considerations In Developing Firewall Selection Criteria Adeptech Systems, Inc. Table of Contents Introduction... 1 Firewall s Function...1 Firewall Selection Considerations... 1 Firewall Types... 2 Packet
Considerations In Developing Firewall Selection Criteria Adeptech Systems, Inc. Table of Contents Introduction... 1 Firewall s Function...1 Firewall Selection Considerations... 1 Firewall Types... 2 Packet
Tik-109/110.300 Telecommunications architectures:
 Tik-109/110.300 Telecommunications architectures: Network management Hannu H. KARI/Helsinki University of Technology (HUT) TML-laboratory/CS/HUT Tik-109/110.300 Fall 2000 Hannu H. Kari Page 1 Agenda Telecom
Tik-109/110.300 Telecommunications architectures: Network management Hannu H. KARI/Helsinki University of Technology (HUT) TML-laboratory/CS/HUT Tik-109/110.300 Fall 2000 Hannu H. Kari Page 1 Agenda Telecom
Internet Firewall CSIS 4222. Packet Filtering. Internet Firewall. Examples. Spring 2011 CSIS 4222. net15 1. Routers can implement packet filtering
 Internet Firewall CSIS 4222 A combination of hardware and software that isolates an organization s internal network from the Internet at large Ch 27: Internet Routing Ch 30: Packet filtering & firewalls
Internet Firewall CSIS 4222 A combination of hardware and software that isolates an organization s internal network from the Internet at large Ch 27: Internet Routing Ch 30: Packet filtering & firewalls
From Bus and Crossbar to Network-On-Chip. Arteris S.A.
 From Bus and Crossbar to Network-On-Chip Arteris S.A. Copyright 2009 Arteris S.A. All rights reserved. Contact information Corporate Headquarters Arteris, Inc. 1741 Technology Drive, Suite 250 San Jose,
From Bus and Crossbar to Network-On-Chip Arteris S.A. Copyright 2009 Arteris S.A. All rights reserved. Contact information Corporate Headquarters Arteris, Inc. 1741 Technology Drive, Suite 250 San Jose,
Implementing a Digital Answering Machine with a High-Speed 8-Bit Microcontroller
 Implementing a Digital Answering Machine with a High-Speed 8-Bit Microcontroller Zafar Ullah Senior Application Engineer Scenix Semiconductor Inc. Leo Petropoulos Application Manager Invox TEchnology 1.0
Implementing a Digital Answering Machine with a High-Speed 8-Bit Microcontroller Zafar Ullah Senior Application Engineer Scenix Semiconductor Inc. Leo Petropoulos Application Manager Invox TEchnology 1.0
