PGP Proof of Concept Completion Checklist
|
|
|
- David Chad Preston
- 10 years ago
- Views:
Transcription
1 Completion Checklist Updated as of November 7, 2008 Proof of Concept Start Date: September 23, 2008 Proof of Concept Completion Date: October 31, 2008 Proof of Concept Objectives Proof of Concept objectives defined and completed Defined in initial SGG Project Charter under Expected Deliverables and Timeline Proof of Concept Budget approved October 23, $55,000 Proof of Concept completed no later than October 31, 2008? Proof of Concept completed within Budget Go/No Go Decision made? Proof of Concept Initiation Key Participants identified and available to participate Acquire Initial Set of PGP licenses Mac/Win Project Manager Assigned Initial Testers volunteered and representative of the on-going support organizations Evaluation and Testing Objectives confirmation to participating testers on November 3, 2008 Expenses incomplete Estimated to be within approved budget Recommendation is to proceed with PGP for Stanford s Whole Disk Encryption Solution for Mac and Windows computers/platforms WST, Tier 2 Help Desk, CRC, PMO Purchase via PCard for initial licenses 10 Win, 10 Mac, 20 Universal Server Steve Loving Initial Test Whole Disk Encryption Stand Alone client Successful download of the client Identified 19 testers across WST, Storage, Integration, Tier 2 Help Desk, Desktop Systems Group, and CRC Significant struggle using the web download ability with all 20 licenses identified for Bruce Vincent. Brute force required. Impacted ~ 1/3 of testers who did not actively participate. NON ISSUE with Universal Server C_\Files+from+C\PGP2009\PGP+Proof+of+Concept+Completion+Checklist doc
2 Windows (XP, Vista) Intuitive login to Workstation Initiate and successfully complete Macintosh (MacIntel, 10.4+) Intuitive login to Workstation Initiate and successfully complete Installation and Configuration of Universal Server Identify Server for Proof of Concept Install and configure Universal Server appliance Intuitive Interface for Logging and Reporting Key Logging/Reporting Components available Intuitive Interface for Whole Disk Retrieval Token Key Retrieval Components available Ease of Integration with Active Directory intuitive. Can address by customizing initial PGP screen and providing directions. Sign in day and run throughout the evening. Recommend run on AC power, not battery. The encryption simply adds an intuitive. Not yet able to customize initial PGP screen and provide directions. Sign in day and run throughout the evening Must run on AC. Encryption stops on battery and requires Decryption and restarting of. The encryption simply adds an Stanford specific audit reports may be required Will need to be developed PGP Proof of Concept Completion Checklist Page 2
3 Ability to change key settings to meet Stanford s needs Ability for distributed IT Support groups to manage within Universal Server Initial Test Whole Disk Encryption with Universal Server Windows (XP, Vista) Installation of client via Universal Server process Intuitive login to Workstation Initiate and successfully complete Initial evaluation Whole Disk Encryption Workstation Backup/Recovery/Backup Size with both Mozy and Iron Mountain Macintosh (MacIntel, 10.4+) Installation of client via Universal Server process Intuitive login to Workstation Initiate and successfully complete PGP Proof of Concept Completion Checklist Page 3 Ability to not allow user to decrypt without Help Desk assistance Access to one system within Universal Server allows access to ALL systems and recovery tokens. Retain Universal Server access within IT Services intuitive. Can address by customizing initial PGP screen and providing directions. Sign in traditional login (installer modification required to enable secondary login requirement) platform (OS) and amount of disk. Suggest this be started towards end of the day and run throughout the evening. Recommend run on AC power, not battery, as battery power will pause encryption. Mozy and Iron Mountain appear to do an initial full backup, followed by incremental backups The encryption simply adds an intuitive. Not yet able to customize initial PGP screen; provide directions. Sign in day and run throughout the evening Must run on AC power. Encryption continues on battery power, but will require Decryption and restarting of if machine loses power during the Encryption process.
4 Initial evaluation Whole Disk Encryption Workstation Backup/Recovery/Backup Size with both Mozy and Iron Mountain Vendor Relationship Is the Vendor Relationship collaborative? Are skilled consultants available and able to participate in the success of this project Security and Architecture Review Initial review of PGP Architecture/Security with appropriate Stanford and PGP representatives Initial review of Architecture aligns with Stanford s current services and infrastructure Initial review of Security risks meet Stanford s acceptance level NOT COMPLETED Mozy appears to do an initial full backup, followed by incremental backups The encryption simply adds an Cooperative and collaborative to date Via PGP Resellers Held October 30, 2008 at PGP Design includes Master/Slave Servers. Decision will need to be made related to the potential risks of the users and the level of PGP Support Agreement we require. General Observations as a Result of the PGP Proof of Concept The general observations of the PGP Proof of Concept is that this is a viable solution for Stanford University s business need to provide encryption solutions to Windows, Macintosh and ultimately Linux desktops and laptops that may hold Prohibited, Restricted and/or Confidential data. The recommended solution is to use the PGP Whole Disk Encryption () solution leveraging the PGP Universal Server. There are decisions to make regarding: - Confirming Best Practices associated with this Encryption Offering to increase the confidence of the state of the data in the event a desktop/laptop and in the future PDA is lost/stolen - Licensing the software by User or by Device - Protecting Stanford owned equipment only or including any desktop/laptop used by anyone with SUNet id This PGP solution is the preferred solution at Yale, parts of Harvard, Baylor, and University of Colorado. The determining factor is predominantly a single solution for both Windows and Mac desktops/laptops. PGP Proof of Concept Completion Checklist Page 4
5 Actions to address during PGP Whole Disk Encryption Deployment Project Action Item Determine implications to PGP user in the event the Master Universal Server is unavailable. Identify alternatives as needed. Determine if Business Continuity requires a second Master available on campus or in Livermore Scope Integration needs between Stanford s Active Directory and the Universal Server Determine who the target audience is for the PGP service. - any one who wants to use the service - require if Prohibited, Restricted and/or Confidential data on desktop/laptop - All Faculty? All Staff? Students? - Stanford equipment only or any device associated with an active Stanford SUNet ID member Clearly identify and document the expectations of the user of PGP s Whole Disk Encryption service Confirm if this service will be provided with or without a fee to the user or department organization Create Project Plan, Milestones, Cost Estimate/Resources and Charter PGP Proof of Concept Completion Checklist Page 5
PGP Whole Disk Encryption Training
 PGP Whole Disk Encryption Training Agenda WDE Overview Licensing Universal Server & Client Basics Installation Password Recovery OS Maintenance Support Questions 2 Whole Disk Encryption Protects against:
PGP Whole Disk Encryption Training Agenda WDE Overview Licensing Universal Server & Client Basics Installation Password Recovery OS Maintenance Support Questions 2 Whole Disk Encryption Protects against:
Using Mac OS X 10.7 Filevault with Centrify DirectControl
 Using Mac OS X 10.7 Filevault with Centrify DirectControl August 2011, Revision 2 OS X 10.7's Filevault has the ability to encrypt the entire disk. Full Disk Encryption is compatible with Centrify Active
Using Mac OS X 10.7 Filevault with Centrify DirectControl August 2011, Revision 2 OS X 10.7's Filevault has the ability to encrypt the entire disk. Full Disk Encryption is compatible with Centrify Active
Open Cloud Store. End-user manual. For
 Open Cloud Store - End-user manual For 1 Version control... 3 2 Introduction to BackupAgent... 4 3 Configuring BackupAgent... 5 3.1 Create a BackupAgent account... 5 3.2 Download and install the BackupAgent
Open Cloud Store - End-user manual For 1 Version control... 3 2 Introduction to BackupAgent... 4 3 Configuring BackupAgent... 5 3.1 Create a BackupAgent account... 5 3.2 Download and install the BackupAgent
How To Set Up Hopkins Wireless On Windows 7 On A Pc Or Mac Or Ipad (For A Laptop) On A Network Card (For Windows 7) On Your Computer Or Ipa (For Mac Or Mac) On An Ipa Or
 Wireless Configuration Guide: Windows 7 Additional hopkins wireless network instructions and requirements for Windows XP, Vista, 8, Mac OS X, Linux, and other Mobile versions can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
Wireless Configuration Guide: Windows 7 Additional hopkins wireless network instructions and requirements for Windows XP, Vista, 8, Mac OS X, Linux, and other Mobile versions can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
Transferring AIS to a different computer
 Transferring AIS to a different computer AIS can easily be transferred from one computer to another. There are several different scenarios for transferring AIS to another computer. Since AIS is designed
Transferring AIS to a different computer AIS can easily be transferred from one computer to another. There are several different scenarios for transferring AIS to another computer. Since AIS is designed
Product Brief. DC-Protect. Content based backup and recovery solution. By DATACENTERTECHNOLOGIES
 Product Brief DC-Protect Content based backup and recovery solution By DATACENTERTECHNOLOGIES 2002 DATACENTERTECHNOLOGIES N.V. All rights reserved. This document contains information proprietary and confidential
Product Brief DC-Protect Content based backup and recovery solution By DATACENTERTECHNOLOGIES 2002 DATACENTERTECHNOLOGIES N.V. All rights reserved. This document contains information proprietary and confidential
How To Restore Your Data On A Backup By Mozy (Windows) On A Pc Or Macbook Or Macintosh (Windows 2) On Your Computer Or Mac) On An Pc Or Ipad (Windows 3) On Pc Or Pc Or Micro
 Online Backup by Mozy Restore Common Questions Document Revision Date: June 29, 2012 Online Backup by Mozy Common Questions 1 How do I restore my data? There are five ways of restoring your data: 1) Performing
Online Backup by Mozy Restore Common Questions Document Revision Date: June 29, 2012 Online Backup by Mozy Common Questions 1 How do I restore my data? There are five ways of restoring your data: 1) Performing
Guidelines on use of encryption to protect person identifiable and sensitive information
 Guidelines on use of encryption to protect person identifiable and sensitive information 1. Introduction David Nicholson, NHS Chief Executive, has directed that there should be no transfers of unencrypted
Guidelines on use of encryption to protect person identifiable and sensitive information 1. Introduction David Nicholson, NHS Chief Executive, has directed that there should be no transfers of unencrypted
ScoMIS Encryption Service
 Introduction This guide explains how to implement the ScoMIS Encryption Service for a secondary school. We recommend that the software should be installed onto the laptop by ICT staff; they will then spend
Introduction This guide explains how to implement the ScoMIS Encryption Service for a secondary school. We recommend that the software should be installed onto the laptop by ICT staff; they will then spend
Symantec PGP Whole Disk Encryption Hands-On Lab V 3.7
 Symantec PGP Whole Disk Encryption Hands-On Lab V 3.7 Description This hands-on lab session covers the hard drive encryption technologies from PGP. Students will administer a typical Whole Disk Encryption
Symantec PGP Whole Disk Encryption Hands-On Lab V 3.7 Description This hands-on lab session covers the hard drive encryption technologies from PGP. Students will administer a typical Whole Disk Encryption
Wireless @ Johns Hopkins
 Wireless Configuration Guide: Windows 7 Additional hopkins wireless network instructions and requirements for Windows XP, Vista, Mac OS X, and Linux can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
Wireless Configuration Guide: Windows 7 Additional hopkins wireless network instructions and requirements for Windows XP, Vista, Mac OS X, and Linux can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
University Systems Desktop Support Service Level Commitment
 University Systems Desktop Support Service Level Commitment The Purpose of this Service Level Commitment (SLC) is to formally define the level of service University Systems will provide to UVic faculty,
University Systems Desktop Support Service Level Commitment The Purpose of this Service Level Commitment (SLC) is to formally define the level of service University Systems will provide to UVic faculty,
Installation and User Guide. MQLink Version 3.0 (Java)
 Installation and User Guide MQLink Version 3.0 (Java) MQLink V3.0 (Java) User Guide Table of Contents 1 Introduction... 2 2 Installation... 2 2.1 Available from 2.2 Where to install 2.3 Installation Pre-requisites
Installation and User Guide MQLink Version 3.0 (Java) MQLink V3.0 (Java) User Guide Table of Contents 1 Introduction... 2 2 Installation... 2 2.1 Available from 2.2 Where to install 2.3 Installation Pre-requisites
Symantec Backup Exec.cloud
 Automatic, continuous, and secure protection that backs up data to the cloud, or via a hybrid approach combining on-premise and cloud-based backup. Data Sheet: Symantec.cloud Only 21 percent of SMBs are
Automatic, continuous, and secure protection that backs up data to the cloud, or via a hybrid approach combining on-premise and cloud-based backup. Data Sheet: Symantec.cloud Only 21 percent of SMBs are
Mobile Device Security and Encryption Standard and Guidelines
 Mobile Device Security and Encryption Standard and Guidelines University Mobile Computing and Device best practices are currently defined as follows: 1) The use of any sensitive or private data on mobile
Mobile Device Security and Encryption Standard and Guidelines University Mobile Computing and Device best practices are currently defined as follows: 1) The use of any sensitive or private data on mobile
Microsoft Agreement FAQ
 Microsoft Agreement FAQ 1. Why did the University of Utah seek to establish the Microsoft Campus Agreement? In years past, Microsoft has allowed the University to utilize multiple agreements (Select and
Microsoft Agreement FAQ 1. Why did the University of Utah seek to establish the Microsoft Campus Agreement? In years past, Microsoft has allowed the University to utilize multiple agreements (Select and
VMware Virtual Desktop Infrastructure (VDI) - The Best Strategy for Managing Desktop Environments Mike Coleman, VMware (mcoleman@vmware.
 VMware Virtual Desktop Infrastructure (VDI) - The Best Strategy for Managing Desktop Environments Mike Coleman, VMware ([email protected]) Copyright 2008 EMC Corporation. All rights reserved. Agenda
VMware Virtual Desktop Infrastructure (VDI) - The Best Strategy for Managing Desktop Environments Mike Coleman, VMware ([email protected]) Copyright 2008 EMC Corporation. All rights reserved. Agenda
REMOTELY ACCESS YOUR FILES WITH THE FLAGLER FILECONNECT SYSTEM
 REMOTELY ACCESS YOUR FILES WITH THE FLAGLER FILECONNECT SYSTEM This document explains the various ways to connect to your network files and group share data. In addition, staff and full-time faculty are
REMOTELY ACCESS YOUR FILES WITH THE FLAGLER FILECONNECT SYSTEM This document explains the various ways to connect to your network files and group share data. In addition, staff and full-time faculty are
Cloud Backup Service Service Description. PRECICOM Cloud Hosted Services
 Cloud Backup Service Service Description PRECICOM Cloud Hosted Services Table of Contents Table of Contents 2 1. Cloud Backup Service Service Summary 3 2. Cloud Backup Service Service Definition 4 2.1.
Cloud Backup Service Service Description PRECICOM Cloud Hosted Services Table of Contents Table of Contents 2 1. Cloud Backup Service Service Summary 3 2. Cloud Backup Service Service Definition 4 2.1.
Citrix Remote Access Work Instructions
 Work Instructions Version 1.0 15 January 2010 InTACT Shared Services Centre ACT Department of Treasury Quality Management System Service Management Tools Contents Introduction... 3 Purpose... 3 Scope...
Work Instructions Version 1.0 15 January 2010 InTACT Shared Services Centre ACT Department of Treasury Quality Management System Service Management Tools Contents Introduction... 3 Purpose... 3 Scope...
Backups. Backup Plan. How to use the Backup utility to back up files and folders in Windows XP Home Edition
 Backups Backups are your insurance against data loss. Most organizations have an Information Technology Department (IT) which may be responsible for backing up organizational data and that is handled well
Backups Backups are your insurance against data loss. Most organizations have an Information Technology Department (IT) which may be responsible for backing up organizational data and that is handled well
Disaster Recovery Strategies: Business Continuity through Remote Backup Replication
 W H I T E P A P E R S O L U T I O N : D I S A S T E R R E C O V E R Y T E C H N O L O G Y : R E M O T E R E P L I C A T I O N Disaster Recovery Strategies: Business Continuity through Remote Backup Replication
W H I T E P A P E R S O L U T I O N : D I S A S T E R R E C O V E R Y T E C H N O L O G Y : R E M O T E R E P L I C A T I O N Disaster Recovery Strategies: Business Continuity through Remote Backup Replication
Eduroam wireless network Apple Mac OSX 10.4
 Eduroam wireless network Apple Mac OSX 0.4 How to configure laptop computers to connect to the eduroam wireless network Contents university for the creative arts Contents Introduction Prerequisites Instructions
Eduroam wireless network Apple Mac OSX 0.4 How to configure laptop computers to connect to the eduroam wireless network Contents university for the creative arts Contents Introduction Prerequisites Instructions
Sage Grant Management System Requirements
 Sage Grant Management System Requirements You should meet or exceed the following system requirements: One Server - Database/Web Server The following system requirements are for Sage Grant Management to
Sage Grant Management System Requirements You should meet or exceed the following system requirements: One Server - Database/Web Server The following system requirements are for Sage Grant Management to
Centralized Mac Home Directories On Windows Servers: Using Windows To Serve The Mac
 Making it easy to deploy, integrate and manage Macs, iphones and ipads in a Windows environment. Centralized Mac Home Directories On Windows Servers: Using Windows To Serve The Mac 2011 ENTERPRISE DEVICE
Making it easy to deploy, integrate and manage Macs, iphones and ipads in a Windows environment. Centralized Mac Home Directories On Windows Servers: Using Windows To Serve The Mac 2011 ENTERPRISE DEVICE
Remote Infrastructure Support Services & Managed IT Services
 Remote Infrastructure Support Services & Managed IT Services Remote Desktop Services are designed to optimize the customers IT resource utilization and provide a standardized end-user environment. The
Remote Infrastructure Support Services & Managed IT Services Remote Desktop Services are designed to optimize the customers IT resource utilization and provide a standardized end-user environment. The
Every organization has critical data that it can t live without. When a disaster strikes, how long can your business survive without access to its
 DISASTER RECOVERY STRATEGIES: BUSINESS CONTINUITY THROUGH REMOTE BACKUP REPLICATION Every organization has critical data that it can t live without. When a disaster strikes, how long can your business
DISASTER RECOVERY STRATEGIES: BUSINESS CONTINUITY THROUGH REMOTE BACKUP REPLICATION Every organization has critical data that it can t live without. When a disaster strikes, how long can your business
Online back-up. 1. Install the software from MRJ-COMPUTERS to your PC, notebook or server - 1 -
 Online back-up What will happen with your important data during a fire, water damage, theft or a computercrash? Prevent the risk and choose for MRJ Online back-up from MRJ-COMPUTERS. Safe storage of your
Online back-up What will happen with your important data during a fire, water damage, theft or a computercrash? Prevent the risk and choose for MRJ Online back-up from MRJ-COMPUTERS. Safe storage of your
Yale Software Library
 e/ Yale Software Library http://www.yale.edu/its/software/ For assistance contact the ITS Help Desk 432-9000 or [email protected] Installation PGP Desktop for Windows Operating Systems Preparing your computer:
e/ Yale Software Library http://www.yale.edu/its/software/ For assistance contact the ITS Help Desk 432-9000 or [email protected] Installation PGP Desktop for Windows Operating Systems Preparing your computer:
Eaton NetWatch v5.0 NetWatch on Microsoft Hyper-V server 2008 Installation and configuration guide
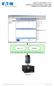 Eaton NetWatch v5.0 NetWatch on Microsoft Hyper-V server 2008 Installation and configuration guide Hyper-V 6.0 NetWatch Main operating system: 2008 Enterprise x64 (hosting Hyper-V) Eaton UPS Eaton NetWatch
Eaton NetWatch v5.0 NetWatch on Microsoft Hyper-V server 2008 Installation and configuration guide Hyper-V 6.0 NetWatch Main operating system: 2008 Enterprise x64 (hosting Hyper-V) Eaton UPS Eaton NetWatch
ScoMIS Encryption Service
 Introduction This guide explains how to install the ScoMIS Encryption Service Software onto a laptop computer. There are three stages to the installation which should be completed in order. The installation
Introduction This guide explains how to install the ScoMIS Encryption Service Software onto a laptop computer. There are three stages to the installation which should be completed in order. The installation
Figure 1: Restore Tab
 Apptix Online Backup by Mozy Restore How do I restore my data? There are five ways of restoring your data: 1) Performing a Restore Using the Restore Tab You can restore files from the Apptix Online Backup
Apptix Online Backup by Mozy Restore How do I restore my data? There are five ways of restoring your data: 1) Performing a Restore Using the Restore Tab You can restore files from the Apptix Online Backup
Xerox DocuShare Security Features. Security White Paper
 Xerox DocuShare Security Features Security White Paper Xerox DocuShare Security Features Businesses are increasingly concerned with protecting the security of their networks. Any application added to a
Xerox DocuShare Security Features Security White Paper Xerox DocuShare Security Features Businesses are increasingly concerned with protecting the security of their networks. Any application added to a
For your eyes only - Encryption and DLP Erkko Skantz
 For your eyes only - Encryption and DLP Erkko Skantz Symantec Finland 1 USER PRODUCTIVITY INFORMATION MANAGEMENT DATA CENTER SECURITY 2 Focus on information 3 Today's System-Centric Enterprise Data Center
For your eyes only - Encryption and DLP Erkko Skantz Symantec Finland 1 USER PRODUCTIVITY INFORMATION MANAGEMENT DATA CENTER SECURITY 2 Focus on information 3 Today's System-Centric Enterprise Data Center
Enterprise Backup Solution Vendor Questions
 Enterprise Backup Solution Vendor Questions What is the size of a single full back up? If Backups comprise 28% of the 19TB, can we assume that a single full (not compressed) is approximately 6TB? The approximate
Enterprise Backup Solution Vendor Questions What is the size of a single full back up? If Backups comprise 28% of the 19TB, can we assume that a single full (not compressed) is approximately 6TB? The approximate
Online Backup Service Frequently Asked Questions. 13 September 2010 Version 1.0
 Online Backup Service Frequently Asked Questions 13 September 2010 Version 1.0 1 Content 1 Content... 2 2 FAQ... 3 2.1 How much online backup space do I need?... 3 2.2 What operating systems are supported?...
Online Backup Service Frequently Asked Questions 13 September 2010 Version 1.0 1 Content 1 Content... 2 2 FAQ... 3 2.1 How much online backup space do I need?... 3 2.2 What operating systems are supported?...
Eduroam wireless network Apple Mac OSX 10.5
 Eduroam wireless network Apple Mac OSX 0. How to configure laptop computers to connect to the eduroam wireless network Contents university for the creative arts Contents Introduction Prerequisites Instructions
Eduroam wireless network Apple Mac OSX 0. How to configure laptop computers to connect to the eduroam wireless network Contents university for the creative arts Contents Introduction Prerequisites Instructions
Novell Archive and Version Services Administration Guide
 www.novell.com/documentation Novell Archive and Version Services Administration Guide Open Enterprise Server 11 SP2 January 2014 Legal Notices Novell, Inc., makes no representations or warranties with
www.novell.com/documentation Novell Archive and Version Services Administration Guide Open Enterprise Server 11 SP2 January 2014 Legal Notices Novell, Inc., makes no representations or warranties with
Introweb Remote Backup Client for Mac OS X User Manual. Version 3.20
 Introweb Remote Backup Client for Mac OS X User Manual Version 3.20 1. Contents 1. Contents...2 2. Product Information...4 3. Benefits...4 4. Features...5 5. System Requirements...6 6. Setup...7 6.1. Setup
Introweb Remote Backup Client for Mac OS X User Manual Version 3.20 1. Contents 1. Contents...2 2. Product Information...4 3. Benefits...4 4. Features...5 5. System Requirements...6 6. Setup...7 6.1. Setup
Total Backup Recovery 7
 7 TM 7 Enhance business functionality and productivity with guaranteed protection from 7 Server 7 Server is a total backup and recovery solution for Windows. With support for all operating systems, 7 Server
7 TM 7 Enhance business functionality and productivity with guaranteed protection from 7 Server 7 Server is a total backup and recovery solution for Windows. With support for all operating systems, 7 Server
Web-Based Data Backup Solutions
 "IMAGINE LOSING ALL YOUR IMPORTANT FILES, IS NOT OF WHAT FILES YOU LOSS BUT THE LOSS IN TIME, MONEY AND EFFORT YOU ARE INVESTED IN" The fact Based on statistics gathered from various sources: 1. 6% of
"IMAGINE LOSING ALL YOUR IMPORTANT FILES, IS NOT OF WHAT FILES YOU LOSS BUT THE LOSS IN TIME, MONEY AND EFFORT YOU ARE INVESTED IN" The fact Based on statistics gathered from various sources: 1. 6% of
CBH Provider EDI Browser Manual
 CBH Provider EDI Browser Manual Table of Contents PGP Software Installation Windows XP 2 PGP Software Installation Windows 7 9 Main Screen 16 Log In Screen 19 Report: Authorizations 21 Decryption Instructions
CBH Provider EDI Browser Manual Table of Contents PGP Software Installation Windows XP 2 PGP Software Installation Windows 7 9 Main Screen 16 Log In Screen 19 Report: Authorizations 21 Decryption Instructions
Total Backup Recovery 7
 7 TM 7 Automat backup and restore management for all networked laptops & workstations from a centralized administrating console 7 Advanced Workstation assures that critical business information is well
7 TM 7 Automat backup and restore management for all networked laptops & workstations from a centralized administrating console 7 Advanced Workstation assures that critical business information is well
VMware Horizon DaaS: Desktop as a Cloud Service (DaaS)
 VMware Horizon DaaS: Desktop as a Cloud Service (DaaS) 1 43% of workforce using 3+ devices 74% of employees use consumer technologies, due to a lack of alternatives from IT 2010 The year the number of
VMware Horizon DaaS: Desktop as a Cloud Service (DaaS) 1 43% of workforce using 3+ devices 74% of employees use consumer technologies, due to a lack of alternatives from IT 2010 The year the number of
Designing a Windows Server 2008 Applications Infrastructure
 Designing a Windows Server 2008 Applications Infrastructure Course 6437A : Three days; Instructor-Led Introduction This three day course will prepare IT professionals for the role of Enterprise Administrator.
Designing a Windows Server 2008 Applications Infrastructure Course 6437A : Three days; Instructor-Led Introduction This three day course will prepare IT professionals for the role of Enterprise Administrator.
File Management and File Storage
 File Management and File Storage http://training.usask.ca Information Technology Services Division Table of Contents File Management at the University of Saskatchewan...3 Introduction...3 Creating Files
File Management and File Storage http://training.usask.ca Information Technology Services Division Table of Contents File Management at the University of Saskatchewan...3 Introduction...3 Creating Files
A Nemaris Company. Formal Privacy & Security Assessment For Surgimap version 2.2.6 and higher
 A Nemaris Company Formal Privacy & Security Assessment For Surgimap version 2.2.6 and higher 306 East 15 th Street Suite 1R, New York, New York 10003 Application Name Surgimap Vendor Nemaris Inc. Version
A Nemaris Company Formal Privacy & Security Assessment For Surgimap version 2.2.6 and higher 306 East 15 th Street Suite 1R, New York, New York 10003 Application Name Surgimap Vendor Nemaris Inc. Version
Other documents in this series are available at: servernotes.wazmac.com
 Wazza s Snow Leopard Server QuickStart 14. Win XP - Workgroup Setup About the Document This document is the fourteenth in a series of documents describing the process of installing and configuring a Mac
Wazza s Snow Leopard Server QuickStart 14. Win XP - Workgroup Setup About the Document This document is the fourteenth in a series of documents describing the process of installing and configuring a Mac
Storage Guardian Remote Backup Restore and Archive Services
 Storage Guardian Remote Backup Restore and Archive Services Storage Guardian is the unique alternative to traditional backup methods, replacing conventional tapebased backup systems with a fully automated,
Storage Guardian Remote Backup Restore and Archive Services Storage Guardian is the unique alternative to traditional backup methods, replacing conventional tapebased backup systems with a fully automated,
Administration Quick Start
 www.novell.com/documentation Administration Quick Start ZENworks 11 Support Pack 3 February 2014 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of
www.novell.com/documentation Administration Quick Start ZENworks 11 Support Pack 3 February 2014 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of
FAQ. How does the new Big Bend Backup (powered by Keepit) work?
 FAQ How does the new Big Bend Backup (powered by Keepit) work? Once you establish which of the folders on your hard drive you ll be backing up, you ll log into myaccount.bigbend.net and from your control
FAQ How does the new Big Bend Backup (powered by Keepit) work? Once you establish which of the folders on your hard drive you ll be backing up, you ll log into myaccount.bigbend.net and from your control
USING GENIE REMOTELY
 USING GENIE REMOTELY This document outlines the available options for using Genie in offsite logging mode (Genie single user) or remotely in real-time via a remote desktop (terminal services) connection.
USING GENIE REMOTELY This document outlines the available options for using Genie in offsite logging mode (Genie single user) or remotely in real-time via a remote desktop (terminal services) connection.
PGP Desktop Encrypting Removable Media. May 1 2012 Version 1.3
 PGP Desktop Encrypting Removable Media May 1 2012 Version 1.3 Table of Contents Introduction... 3 Installation Notes... 3 Encrypting Removable Media... 5 Adding and Deleting Users... 10 Changing a Passphrase...
PGP Desktop Encrypting Removable Media May 1 2012 Version 1.3 Table of Contents Introduction... 3 Installation Notes... 3 Encrypting Removable Media... 5 Adding and Deleting Users... 10 Changing a Passphrase...
CSG Windows Support Policy
 CSG Windows Support Policy This document describes the policies for service and support of computers running Microsoft Windows used by faculty and staff in the departments of Computer Science, Mathematics
CSG Windows Support Policy This document describes the policies for service and support of computers running Microsoft Windows used by faculty and staff in the departments of Computer Science, Mathematics
Security Tool Kit System Checklist Departmental Servers and Enterprise Systems
 Security Tool Kit System Checklist Departmental Servers and Enterprise Systems INSTRUCTIONS System documentation specifically related to security controls of departmental servers and enterprise systems
Security Tool Kit System Checklist Departmental Servers and Enterprise Systems INSTRUCTIONS System documentation specifically related to security controls of departmental servers and enterprise systems
Windows Symantec Encryption Desktop (PGP) Install Guide. Symantec Encryption Desktop (PGP) Windows system requirements
 Image not found https://it.ucsf.edu/sites/it.ucsf.edu/themes/custom/it_new/logo.png it.ucsf.edu Published on it.ucsf.edu (https://it.ucsf.edu) Home > Windows Symantec Encryption Desktop (PGP) Install Guide
Image not found https://it.ucsf.edu/sites/it.ucsf.edu/themes/custom/it_new/logo.png it.ucsf.edu Published on it.ucsf.edu (https://it.ucsf.edu) Home > Windows Symantec Encryption Desktop (PGP) Install Guide
TestNav 8 User Guide for PARCC
 TestNav 8 User Guide for PARCC Copyright 2014, Pearson Education, Inc. Published March 6, 2014 TestNav 8 User Guide for PARCC 1 TestNav 8 User Guide for PARCC Revision History What is TestNav? Technical
TestNav 8 User Guide for PARCC Copyright 2014, Pearson Education, Inc. Published March 6, 2014 TestNav 8 User Guide for PARCC 1 TestNav 8 User Guide for PARCC Revision History What is TestNav? Technical
[email protected] 2009 STREAM FRBC
 Virtualization ti Dave Balka [email protected] Examination Elements Architecture Management Processes Integrity Availability Security 2 Datacenter Consolidation 3 What is Virtualization A framework
Virtualization ti Dave Balka [email protected] Examination Elements Architecture Management Processes Integrity Availability Security 2 Datacenter Consolidation 3 What is Virtualization A framework
Total Backup Recovery
 Total Backup Recovery Ultimate Backup & Recovery Solution for Businesses & Organizations Total Backup Recovery 7 Series is a total backup and recovery solution for businesses and organizations. The series
Total Backup Recovery Ultimate Backup & Recovery Solution for Businesses & Organizations Total Backup Recovery 7 Series is a total backup and recovery solution for businesses and organizations. The series
BitLocker/Active Directory Encryption Procedure Department: Information Security Office Version: 1.0 Last Revised: 09/26/2011
 BitLocker/Active Directory Encryption Procedure Department: Information Security Office Version: 1.0 Last Revised: 09/26/2011 Purpose To provide a step-by-step procedure for encrypting installed laptop
BitLocker/Active Directory Encryption Procedure Department: Information Security Office Version: 1.0 Last Revised: 09/26/2011 Purpose To provide a step-by-step procedure for encrypting installed laptop
Alliance Key Manager A Solution Brief for Technical Implementers
 KEY MANAGEMENT Alliance Key Manager A Solution Brief for Technical Implementers Abstract This paper is designed to help technical managers, product managers, and developers understand how Alliance Key
KEY MANAGEMENT Alliance Key Manager A Solution Brief for Technical Implementers Abstract This paper is designed to help technical managers, product managers, and developers understand how Alliance Key
Implementing, Managing, and Maintaining a Microsoft Windows Server 2003 Network Infrastructure
 Question Number (ID) : 1 (jaamsp_mngnwi-025) Lisa would like to configure five of her 15 Web servers, which are running Microsoft Windows Server 2003, Web Edition, to always receive specific IP addresses
Question Number (ID) : 1 (jaamsp_mngnwi-025) Lisa would like to configure five of her 15 Web servers, which are running Microsoft Windows Server 2003, Web Edition, to always receive specific IP addresses
White Paper. BD Assurity Linc Software Security. Overview
 Contents 1 Overview 2 System Architecture 3 Network Settings 4 Security Configurations 5 Data Privacy and Security Measures 6 Security Recommendations Overview This white paper provides information about
Contents 1 Overview 2 System Architecture 3 Network Settings 4 Security Configurations 5 Data Privacy and Security Measures 6 Security Recommendations Overview This white paper provides information about
enicq 5 System Administrator s Guide
 Vermont Oxford Network enicq 5 Documentation enicq 5 System Administrator s Guide Release 2.0 Published November 2014 2014 Vermont Oxford Network. All Rights Reserved. enicq 5 System Administrator s Guide
Vermont Oxford Network enicq 5 Documentation enicq 5 System Administrator s Guide Release 2.0 Published November 2014 2014 Vermont Oxford Network. All Rights Reserved. enicq 5 System Administrator s Guide
Installation Overview
 Contents Installation Overview... 2 How to Install Ad-Aware Management Server... 3 How to Deploy the Ad-Aware Security Solutions... 5 General Deployment Conditions... 5 Deploying Ad-Aware Management Agent...
Contents Installation Overview... 2 How to Install Ad-Aware Management Server... 3 How to Deploy the Ad-Aware Security Solutions... 5 General Deployment Conditions... 5 Deploying Ad-Aware Management Agent...
White Paper. Anywhere, Any Device File Access with IT in Control. Enterprise File Serving 2.0
 White Paper Enterprise File Serving 2.0 Anywhere, Any Device File Access with IT in Control Like it or not, cloud- based file sharing services have opened up a new world of mobile file access and collaborative
White Paper Enterprise File Serving 2.0 Anywhere, Any Device File Access with IT in Control Like it or not, cloud- based file sharing services have opened up a new world of mobile file access and collaborative
activecho Frequently Asked Questions
 activecho Frequently Asked Questions What are the benefits of activecho? activecho allows your organization to provide an on-premise, managed and secure alternative to Dropbox and other file synching and
activecho Frequently Asked Questions What are the benefits of activecho? activecho allows your organization to provide an on-premise, managed and secure alternative to Dropbox and other file synching and
Service Level Agreement
 This document outlines the Service Level Agreement (SLA) between University Technology Services (UTS) and our Customers for the delivery of. The purpose of this agreement is threefold: 1. To clearly represent
This document outlines the Service Level Agreement (SLA) between University Technology Services (UTS) and our Customers for the delivery of. The purpose of this agreement is threefold: 1. To clearly represent
Cloudifile: Frequently Asked Questions
 Cloudifile: Frequently Asked Questions 1 Contents Cloudifile Compatibility... 3 Cloudifile Installation... 4 Cloudifile Account Registration... 5 Working with Cloudifile... 6 Cloudifile Functionality...
Cloudifile: Frequently Asked Questions 1 Contents Cloudifile Compatibility... 3 Cloudifile Installation... 4 Cloudifile Account Registration... 5 Working with Cloudifile... 6 Cloudifile Functionality...
Allidm.com. SSO Introduction. Discovering IAM Solutions. Leading the IAM Training. @aidy_idm facebook/allidm
 Discovering IAM Solutions Leading the IAM Training @aidy_idm facebook/allidm SSO Introduction Disclaimer and Acknowledgments The contents here are created as a own personal endeavor and thus does not reflect
Discovering IAM Solutions Leading the IAM Training @aidy_idm facebook/allidm SSO Introduction Disclaimer and Acknowledgments The contents here are created as a own personal endeavor and thus does not reflect
Hardware and Software Requirements. Release 7.5.x PowerSchool Student Information System
 Release 7.5.x PowerSchool Student Information System Released October 2012 Document Owner: Documentation Services This edition applies to Release 7.5.x of the PowerSchool software and to all subsequent
Release 7.5.x PowerSchool Student Information System Released October 2012 Document Owner: Documentation Services This edition applies to Release 7.5.x of the PowerSchool software and to all subsequent
Introduction to Stanford Box
 January 15, 2016 Tech Briefing Introduction to Stanford Box box.stanford.edu / stanford.box.com Don Cameron [email protected] (650) 736-0609 INTRODUCTION Agenda Box at Stanford Getting Started Managing
January 15, 2016 Tech Briefing Introduction to Stanford Box box.stanford.edu / stanford.box.com Don Cameron [email protected] (650) 736-0609 INTRODUCTION Agenda Box at Stanford Getting Started Managing
HIPAA COMPLIANCE REVIEW
 HIPAA COMPLIANCE REVIEW DRAGON MEDICAL V 10 CSC 3811 Turtle Creek Blvd Suite 2000 Dallas, TX 75219 Phone: 214.520.0555 TABLE OF CONTENTS 1.0 Introduction 1 2.0 Findings 1 2.1 Observations and Recommendations
HIPAA COMPLIANCE REVIEW DRAGON MEDICAL V 10 CSC 3811 Turtle Creek Blvd Suite 2000 Dallas, TX 75219 Phone: 214.520.0555 TABLE OF CONTENTS 1.0 Introduction 1 2.0 Findings 1 2.1 Observations and Recommendations
Symantec Endpoint Encryption Device Control Release Notes
 Symantec Endpoint Encryption Device Control Release Notes Symantec Endpoint Encryption Device Control 8.2.0 www.symantec.com About Symantec Endpoint Encryption Device Control Symantec Endpoint Encryption
Symantec Endpoint Encryption Device Control Release Notes Symantec Endpoint Encryption Device Control 8.2.0 www.symantec.com About Symantec Endpoint Encryption Device Control Symantec Endpoint Encryption
Administering FileVault 2 on OS X Lion with the Casper Suite. Technical Paper July 2012
 Administering FileVault 2 on OS X Lion with the Casper Suite Technical Paper July 2012 JAMF Software, LLC 2012 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that
Administering FileVault 2 on OS X Lion with the Casper Suite Technical Paper July 2012 JAMF Software, LLC 2012 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that
USB 2.0 Flash Drive User Manual
 USB 2.0 Flash Drive User Manual 1 INDEX Table of Contents Page 1. IMPORTANT NOTICES...3 2. PRODUCT INTRODUCTION...4 3. PRODUCT FEATURES...5 4. DRIVER INSTALLATION GUIDE...6 4.1 WINDOWS 98 / 98 SE... 6
USB 2.0 Flash Drive User Manual 1 INDEX Table of Contents Page 1. IMPORTANT NOTICES...3 2. PRODUCT INTRODUCTION...4 3. PRODUCT FEATURES...5 4. DRIVER INSTALLATION GUIDE...6 4.1 WINDOWS 98 / 98 SE... 6
Symantec Client Management Suite 7.6 powered by Altiris technology
 Symantec Client Management Suite 7.6 powered by Altiris technology IT flexibility. User freedom. Data Sheet: Endpoint Management Overview With so many new devices coming into the workplace and users often
Symantec Client Management Suite 7.6 powered by Altiris technology IT flexibility. User freedom. Data Sheet: Endpoint Management Overview With so many new devices coming into the workplace and users often
Acronis Backup & Recovery for Mac. Acronis Backup & Recovery & Acronis ExtremeZ-IP REFERENCE ARCHITECTURE
 Acronis Backup & Recovery for Mac Acronis Backup & Recovery & Acronis ExtremeZ-IP This document describes the technical requirements and best practices for implementation of a disaster recovery solution
Acronis Backup & Recovery for Mac Acronis Backup & Recovery & Acronis ExtremeZ-IP This document describes the technical requirements and best practices for implementation of a disaster recovery solution
Kaseya IT Automation Framework
 Kaseya Kaseya IT Automation Framework An Integrated solution designed for reducing complexity while increasing productivity for IT Professionals and Managed Service Providers. The powerful, web-based automation
Kaseya Kaseya IT Automation Framework An Integrated solution designed for reducing complexity while increasing productivity for IT Professionals and Managed Service Providers. The powerful, web-based automation
Data Backup and Restore (DBR) Overview... 2. Detailed Description... 3. Pricing... 5 SLAs... 5 Service Matrix... 6. Service Description
 Service Description Data Backup and Restore (DBR) Terremark s Data Backup & Restore provides secure, streamlined online-offsite data storage and retrieval that is highly scalable and easily customizable.
Service Description Data Backup and Restore (DBR) Terremark s Data Backup & Restore provides secure, streamlined online-offsite data storage and retrieval that is highly scalable and easily customizable.
Security Information/Event Management Security Development Life Cycle Version 5
 Security Information/Event Management Security Development Life Cycle Version 5 If your enterprise is like most, you are collecting logs from most every device with security relevance. The flood of events
Security Information/Event Management Security Development Life Cycle Version 5 If your enterprise is like most, you are collecting logs from most every device with security relevance. The flood of events
Vess A2000 Series HA Surveillance with Milestone XProtect VMS Version 1.0
 Vess A2000 Series HA Surveillance with Milestone XProtect VMS Version 1.0 2014 PROMISE Technology, Inc. All Rights Reserved. Contents Introduction 1 Purpose 1 Scope 1 Audience 1 What is High Availability?
Vess A2000 Series HA Surveillance with Milestone XProtect VMS Version 1.0 2014 PROMISE Technology, Inc. All Rights Reserved. Contents Introduction 1 Purpose 1 Scope 1 Audience 1 What is High Availability?
Hosted File Backup for business. Keep your data safe with our cloud backup service
 Hosted File Backup for business Keep your data safe with our cloud backup service Why choose Hosted File Backup? Your most important business asset is data. After all, without customer information, order
Hosted File Backup for business Keep your data safe with our cloud backup service Why choose Hosted File Backup? Your most important business asset is data. After all, without customer information, order
HELPDESK & SERVER MONITORING. Helpdesk HOURS OF COVER KEY FEATURES
 HELPDESK & SERVER MONITORING Organisations are under pressure to implement efficient, reliable and cost effective helpdesk And server monitoring service solutions. Our Helpdesk & Server Monitoring services
HELPDESK & SERVER MONITORING Organisations are under pressure to implement efficient, reliable and cost effective helpdesk And server monitoring service solutions. Our Helpdesk & Server Monitoring services
Cloud Services. Getting Started. with Cloud Services Admin Guide
 Cloud Services Getting Started with Cloud Services Admin Guide 3/12/2015 INTRODUCTION This is a planning guide. It is meant to walk the reader through the steps necessary to plan, configure, and activate
Cloud Services Getting Started with Cloud Services Admin Guide 3/12/2015 INTRODUCTION This is a planning guide. It is meant to walk the reader through the steps necessary to plan, configure, and activate
6. AUDIT CHECKLIST FOR NETWORK ADMINISTRATION AND SECURITY AUDITING
 6. AUDIT CHECKLIST FOR NETWORK ADMINISTRATION AND SECURITY AUDITING The following is a general checklist for the audit of Network Administration and Security. Sl.no Checklist Process 1. Is there an Information
6. AUDIT CHECKLIST FOR NETWORK ADMINISTRATION AND SECURITY AUDITING The following is a general checklist for the audit of Network Administration and Security. Sl.no Checklist Process 1. Is there an Information
