Enhancing Security Module to Prevent Data Hacking in Online Social Networks
|
|
|
- Jordan Stephens
- 10 years ago
- Views:
Transcription
1 184 JOURNAL OF EMERGING TECHNOLOGIES IN WEB INTELLIGENCE, VOL. 6, NO. 2, MAY 2014 Enhancing Security Module to Prevent Data Hacking in Online Social Networks M. Milton Joe Assistant Professor, Department of Computer Application, St. Jerome s College, Nagercoil, Tamilnadu, India. [email protected] Dr.B. Ramakrishan Associate Professor, Department of Computer Science and Research centre, S.T.Hindu College, Nagercoil, Tamilnadu, India. [email protected] Abstract Online Social Network (ONS) is the easiest platform to connect with one another. There are many Online Social Networking websites exist to bring up the reliable communication among the users. Facebook, Orkut, Google+, Twitter, MySpace, etc are some of the Online Social Networking websites. All the social networking websites provide the interface formally known as profile, to share their willingness with others. The users of these websites could share their feelings, photos, text file and even whatever the user wishes to provide. All the Online Social Networking websites bring the friends, family members and relatives together to share their desires in a fast track manner, however still it lacks in security module. The shared photos and information are freely open access to all the users of social networking websites. When the photos are freely available, the unauthorized users can easily access the photos of others and download it. Once the photo is downloaded, that image can be misused widely such as creation of fake profile and the photo can be sold to other nuisance websites. This kind of data hacking activities in online social networks even leads the life to death. In this paper, data hacking in online social network is considered and a novel mechanism is presented to prevent the data hacking. Index Terms Online Social Networks (OSNs), Internet, Security, Hacking, Data. I. INTRODUCTION Internet is the web based communication tool, which brings all the users together and forms network communication to share the information with one another. Internet is the fastest and easiest technology to connect with people for communication [1]. Social networking is a service offered to form a network or relation to exchange the ideas, thoughts, interests, activities, backgrounds and so on [1, 2]. The research development in web 2.0 was very much useful to develop this sort of network communication and founded the Online Social Networks (OSNs) [1, 3]. The existing social networking websites such as Facebook, Orkut, and Google Plus and so on allow its users to create profile to post their ideas, activities and photos on the social networking websites. This profile can be viewed by the others users. These social networking websites help a lot to communicate with one another and get back the response for the post from the other users at once. The registration to create a profile in the social networking websites could be done with the help of existing id [2]. Active users of social networking websites almost crossed more than one billion [2, 4, 5]. Though many social networking websites exist in the world, very few could stand among the people. One among them is the most popular social networking website Facebook, which crossed over one billion user during the month of September Most of the users use mobile device to access the social networking websites [6]. The recent survey says, the users of these websites by site wise as follows [7]: Facebook : 1150 M (1.15 Billion) Twitter : 500 M Google Plus : 500 M LinkedIn : 238 M Instagram : 130 M Pinterest : 70 M The Figure 1 shows the overall total number of users presents in the social networking websites. The figure indicates clearly that Facebook has the highest number of users compared with all the other social networking websites. Using all the social networking websites, the users can present their day to day activities, photos and their life styles in their profiles. Friends, Family members, Relatives and even others can have a look at these profiles and they can respond back as they wish. The growth of social networking websites are developed every day, since many users create new profile every day. Thus, online social networking websites are widely used as a communication medium to share and exchange information with one another. The users are very much interested and spend most of their valuable time in social websites to exchange the information in a fast track manner. doi: /jetwi
2 JOURNAL OF EMERGING TECHNOLOGIES IN WEB INTELLIGENCE, VOL. 6, NO. 2, MAY Figure 1 Total User of Social Network Websites II. RELATED WORK Online Social Networking is one of the major areas, where so many researches have been taken for the development of social networking websites. Some of the research works done on social networking medium are listed below: When all the information are posted on Online Social Networking websites, privacy must be provided by the OSN providers. Privacy settings can be set by the users, those who are aware of the security constraints in social networking websites [8, 1]. The growth of the Online Social Networking websites laid the foundation for the development of third party applications to access the social networking websites data to provide better performance to the users. Since user data are shared with third party applications, privacy to the user data must be provided. A separate framework was developed for third party applications for accessing the data from the user profile [3, 1]. That is, the user can set which data to be shared with third party applications [3, 1]. This framework set some sort of privacy to the user data in social networking websites. The concern of privacy on user data developed a new framework, which made both OSN providers and nonfriends to a particular user unable to access the user data [9]. Approach called FlyByNight employs the mechanism of cryptography, which never sends the data on social networking websites in an unencrypted format [10]. This FlyByNight brings up the data confidentiality over the online social networking websites [10]. Encryption techniques used to ensure the data confidentiality from the OSN provider in the approach of FaceCloak [11]. The FaceCloak mechanism provides equal access to all the friends of a particular user and no separate privacy is set for each friends of a particular user [11]. NOYB approach used cryptographic techniques to achieve the confidentiality from the OSN providers [12]. However the NOYB does not offer any tool for classifying the different permissions for each friend of a particular user [12]. Persona methodology offers a private OSN framework, which allows users to share their data with group of people securely defined by the user and Persona does not trust the OSN providers [13]. Lockr provides a new flexible data sharing method in a confidentiality manner in such a way the shared data cannot be accessed by the unauthorized users in Online Social Networking websites [14, 15]. All the social networking websites are threatened by the cyber criminals, who attack the social networking platform and breach the privacy of the users [16]. Socialbot is a software developed to control the attack on OSN platform [16]. Another vital challenge in Online Social Networking is preventing it from the worm propagation. The worm classified as muffle worm automatically propagates in the online social networking from one host to another host and infects it [17]. This muffle worm scans all the hosts in the social networking communication environment and identifies the vulnerable host among them [17, 18]. Once vulnerable host is identified the worm moves to that host and infects it and this process continues [17, 18]. The mechanism to detect such muffle worm and prevent the communication in online social networks securable is presented in the framework of muffle worm detection [17, 18]. All the above research works presented the mechanism of providing security to the user privacy and user data. III. PROBLEM STATEMENT The ideal growth of internet technologies developed Online Social Networks (OSNs) to communicate with others in an easiest manner. However to use the service of online social networks, user must register and create the profile. The user can post whatever he/she wants and the posted content is available to the other users. The other end user can view the post and reply back or comment on the post. Similarly most of the users post their original photographs on the social networking websites. Making the photographs available on the social networking websites are users own wish. As user s photographs are available on the websites, those photos can be easily hacked by the other users. These hacked photos are being misused widely, such as creation of fake profile, and for other bad activities. There are many ways to hack the data especially photographs on the social networking websites. So many people s life became a question mark because of the misuse of the photographs and even this lead to the death of lives. Prevention of this data hacking persists as a great challenge to the researchers
3 186 JOURNAL OF EMERGING TECHNOLOGIES IN WEB INTELLIGENCE, VOL. 6, NO. 2, MAY 2014 Figure 2 Ways of Hacking Photograph The Figure 2 depict the various ways of hacking a photograph on social networking websites. There are five ways to hack an image in the websites as shown in the Figure 2. However to enhancing the security to the users on the social networking, this data hacking ways must be prevented. This data hacking made many people not to use the facility of social networking websites and also many people are not at all aware of these kind of data hacking. This paper concentrates on data hacking in social networking websites and a novel mechanism is presented to prevent the data hacking. IV. PREVENTION OF DATA HACKING A. Disabling Right Click Option in OSNs One of the ways of hacking the photograph in social networking website is right click and save image option. This option is find open in most of the social networking websites, which is very easy to download and save the images of others. This option must be disabled on social networking websites, in order to provide good security to all the social networking website users. The above Figure 3 shows, how an image can be saved to the desktop in online social networking websites. It is a simple task to prevent the right click option in the social networking websites. The powerful Java script coding can be used to disable the right click option in the social networking websites. The Java script code described below disables the right click option in any web pages. However, right click option may be needed in the web pages for ease of service. This paper proposes that this Java script code Figure 3 Right click and Save image could be included in the social networking websites, in order to prevent the hacking of images without the knowledge of the intended user. Hence, inclusion of the Java script code enhance the security module in the social networking websites. Once security is improved, many people will make use the services of the social networking websites without any threat.
4 JOURNAL OF EMERGING TECHNOLOGIES IN WEB INTELLIGENCE, VOL. 6, NO. 2, MAY B. Dragging the Image Another way of hacking the image is dragging. User can easily drag the image to the any location where he/she wants to save the image. This dragging of the image is found open in online social networking websites. Figure 4 represents how an image is dragged in Facebook social networking website. In the figure, we can find the same image in small size, when the image is being dragged. This dragged image can be dropped anywhere in the computer system for saving the image. This way of dragging an image must be disabled in order to tighten security constraint in social networking websites. The tag <img> is used to display the image files in the webpages. This <img> tag has the attribute draggable, which returns the Boolean value that is either true or false. By default the value of draggable attribute is true. If the value of draggable attribute set as false as shown in the above <img> coding, then the image cannot be dragged. Hence this coding prevents the image dragging in social networking web pages. C. Snipping Tool in Windows OS Windows operating System such as Windows 7 offers a tool called Snipping tool. This tool can be used to take a copy of the image from the social networking web pages and the image can be saved in the desired location. The Figure 5 depicts the snipping tool. In the snipping tool, when new option is chosen, the mouse pointer is enabled to crop the image. Once the image is cropped, then user can save the image in the desired location. Using this snipping tool any image can be cropped and saved. This snipping tool option needs to be eliminated to enhance the security modules in social networking websites. Figure 5 Snipping tool to save the image D. Combination of Keys Image can be hacked with combination of key such as Ctrl +A and Ctrl +S. Disabling right click will prevent the hacking from the mouse operation. However once mouse operation is disabled, it is still possible for the hackers to copy the image with the Ctrl +A and Ctrl +C keys. When the user presses the above mentioned key combination, the entire current working environment is get selected. Once the working environment is get selected the key combination Ctrl +C could be used to copy the entire page and that can be pasted with the key wherever the user wants. In order to prevent data hacking in online Social networking webpages this Ctrl +A must be disabled. Similarly the key combination Ctrl +S allows users to save the current viewing web page as it is. When a web page is saved, all the images of the web page are saved in a folder for the ease of the hackers. Hence, this combination of Ctrl +S keys must be disabled in online social networking websites to enhance the security module. Figure 4 Dragging the Image <img draggable="false" src="image.jpg" />
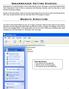
5 188 JOURNAL OF EMERGING TECHNOLOGIES IN WEB INTELLIGENCE, VOL. 6, NO. 2, MAY 2014 created, the same identifier must be assigned to it also. For instance let us consider the key 111 is assigned to all the social networking websites. The working principle of Print Screen button in Online Social Network websites are described below. When the PrntScr button is pressed, it will check for the website s identifier. If the identifiers is equals to 111, then the screen shot will be taken without capturing the images found in the webpage. That is, except the image file all the other information will be captured. Similarly if the identifier is not equal to 111, then no restriction is given and the PrntScr option will function as it is. That is, all the contents of the screen is captured. The above placed java script code should be added in all the social networking web pages. This java script code disables the Ctrl + A, Ctrl + S and all the other keys with combination of Ctrl key. Implementation of these codes in social networking web pages prevents the user data highly and users will be saved from the threat of data hacking. E. Print Screen Option Print Screen option in computer system s keyboard provides good facility to all the researchers and others to take the screen shot of the current desktop position as it is. Similarly this print screen button (PrntScr) can be used to capture the screen in the Online Social Networking websites. Once the social networking webpage is captured that can be saved and cropped to have the image separately. Enhancing security constraint in social networking websites this Print Screen operation in the computer system needs to be disabled. However the usage of Print Screen option is much needed to all the users of the computer system. Hence this feature cannot be disabled. Alternatively this paper provides the novel mechanism, when the Print Screen button is pressed to capture the screen. The novel mechanism is, assigning the same identifier to all the social networking websites. Similarly whenever a new social networking website is about to be These days the hackers are much clever. When the proposed scheme is implemented, hackers will open a small working environment near the social networking web pages and take the print screen of the desktop. Along with the active window the social networking web page is also captured, since the print screen button will check the identifier of the active window. The Figure 6 depicts how an online social networking web page can be captured by making another working environment as active window. This way of hacking must be prevented to tighten the security constraints. Additional intelligence should be given to the print screen button, when it is being pressed. Whenever the print screen button is pressed, it must check how many windows are maximized. If more than one window is maximized, then it must prompt to minimize all windows by keeping one window as active. This checking will keep only one window active at a time. Hence the proposed mechanism will work perfectly.
6 JOURNAL OF EMERGING TECHNOLOGIES IN WEB INTELLIGENCE, VOL. 6, NO. 2, MAY F. Print Preview and Save Figure 6 Screenshot of the web page by keeping another working environment as active window Print preview option enables users to view the document s appearance before it is being printed. This option allows users to save the print preview appearance of the document to the computer system as pdf file. In the same way, this option can be used in the social networking websites to save the webpage as the pdf file. Similarly the webpage that contains user s photo can be saved using the print preview option. After saving the file to the computer system, then the image alone can be cropped and can be misused. In order protect the user data in the social networking websites, this print preview Figure 6 Print Preview and save the image in social networking webpage and then save option must be disabled. For the same, this paper proposes the same identifier key matching, which is used in the Print Screen option section. That is when the print preview option is chosen, it must check the identifier. If the identifier is equal to 111 then print preview of the current webpage is displayed but the save option must be disabled. If the identifier is not equal to 111, then normal operation of print preview can be used. The Figure 6 represents the working process of Print Preview option in online social networking webpages. As shown in the image, left top corner we can find the save
7 190 JOURNAL OF EMERGING TECHNOLOGIES IN WEB INTELLIGENCE, VOL. 6, NO. 2, MAY 2014 option, which enables the user to save the page as the pdf file. This form of image hacking can be eliminated in the propose model. G. Temporary Internet Folder Every browser keeps a folder in the local drive called temporary internet folder, which is used to store the caches. When a web page is loaded, the browser keeps the copy of the content of the web page in the temporary internet folder. This helps a lot, when the user loads the same web page again in future. That is, the content of the web page is directly loaded from the temporary internet folder, while downloading the new contents alone from the web server. The mechanism of caching provides the fast loading of the web pages in the client machine. As the name implies it is not really temporary internet folder. As long as the user clears the temporary internet folder manually, all the contents remain inside the folder. This temporary internet folder leads to privacy issue. Temporary internet folder can be opened easily by anyone, who has access to the machine and can copy all the images and other details. In our case, when the hackers load online social networking web page in their local machine, all the images are stored in temporary internet folder. Once the images are downloaded to the hacker s local machine, those images can be used as hacker wishes. The ultimate aim of this paper is prevent the image hacking in online social networking web pages. The caching of web pages provide fast loading and viewing of the websites in client machine. In order to prevent the data hacking, this paper proposes an alternative method of storing caches of web pages. Temporary internet folder should contain a sub folder and it should be highly secured. This sub folder should not be open access, so that the user cannot open the secured sub folder. As discussed in the previous section all the social networking websites are alerted with the same identifier that is 111. When the user loads a website, the browser must check the identifier of the website. If the identifier is equal to 111, the content of the website must be cached to the sub folder. If the identifier is not equal to 111, then the content can be stored in the normal temporary internet folder. Once the content of the social networking websites are stored in the secured sub folder the images cannot be hacked by the hackers, since the sub folder cannot be opened by the user. V. CONCLUSION In this paper, the entire characteristics of Online Social Networking websites are studied and found the present security mechanism to the user data especially to user s photographs are not trust worthy. The user s photographs can be hacked in various ways. This limitation must be avoided to provide good quality of service to the users of Online Social Networking websites. This paper identified the various ways of hacking the user data in social networking websites and novel alternative mechanisms are presented to tighten the security constraints in Online Social Networking websites. The proposed methodologies are applicable only to the social networking websites, however if needed the same techniques can be implemented in other webpages also. Modeling of this paper makes sure, that security constraints of social networking websites are enhanced. Proposed architecture provides much better Quality of Service to all the users of Online Social Networking websites. The proposed methodologies and ideas are in the hand of operating system developers and the browser developers. The developers of both must consider the above mentioned factors, and develop their product accordingly to enhancing the security constraints in social networking websites. REFERENCES [1] M. Milton Joe, Dr. B. Ramakrishnan, Dr. R.S. Shaji Prevention of Losing User Account by Enhancing Security Module: A Facebook Case, Journal of Emerging Technologies in Web Intelligence, Vol. 5, No. 3, August 2013, Page No: [2] [3] Mohamed Shehab a, Anna Squicciarini b, Gail-Joon Ahn c, Irini Kokkinou Access control for online social networks third party applications Elsevier- Computers & Security 31 (2012) [4] Facebook, Facebook Statistics, March < [5] Twitter, Twitter Numbers, March < [6] Facebook, [7] tatistics/ [8] Gorrell P. Cheek, Mohamed Shehab "Policy-by-Example for Online Social Networks" SACMATO 12 JUNE 20-22, 2012 NEWARK, NEW JERSY, USA, ACM YEAR [9] Fatemeh Raji, Ali Miri, Mohammad Davarpanah Jazi, CP2: Cryptographic privacy protection framework for online social networks, Computers and Electrical Engineering Volume 39, issue 7, October 2013, Pages: [10] Lucas MM, Borisov N. FlyByNight: mitigating the privacy risks of social networking. In: 7th ACM workshop on privacy in the electronic society (WPES 08); p [11] Luo W, Xie Q, Hengartner U. FaceCloak: an architecture for user privacy on social networking sites. In: IEEE international conference on privacy, security, risk and trust (PASSAT-09). Vancouver, Canada; p [12] Guha S, Tang K, Francis P. NOYB: privacy in online social networks. In: First workshop on online social networks (WOSP 08); p [13] Baden R, Bender A, Spring N, Bhattacharjee B, Starin D. Persona: an online social network with user defined privacy, and scholarship. In: Annual conference on special interest group on data communications (ACM SIGCOMM); p [14] Tootoonchian A, Gollu KK, Saroiu S, Ganjali Y, Wolman A. Lockr: social access control for web 2.0. In: The first ACM SIGCOMM workshop on online social networks (WOSN). Seattle, WA; p [15] Tootoonchian A, Saroiu S, Ganjali Y, Wolman A. Lockr: better privacy for social networks. In: The 5th ACM international conference on emerging networking experiments and technologies (CoNEXT). Rome, Italy; p
8 JOURNAL OF EMERGING TECHNOLOGIES IN WEB INTELLIGENCE, VOL. 6, NO. 2, MAY [16] Yazan Boshmaf, Ildar Muslukhov, Konstantin Beznosov, Matei Ripeanu, Design and analysis of a social botnet, Computer Networks 57 (2013) [17] M. Milton Joe, R.S. Shaji, F. Ramesh Dhanaseelan Detection of M-Worm to Provide Secure Computing In Social Networks Elixir International Journal September -50 (2012) [18] Wei Yu, Xun Wang, Prasad Calyam, Dong Xuan and Wei Zhao, Modeling and Detection of Camouflaging Worm, IEEE Transactions on Dependable and Secure Computing, Vol.8, No.3, May-June Mr. M. Milton Joe received his B.Sc Computer Science degree from Bharathidasan University, India and MCA degree from Anna University, India. Presently he is working as Assistant Professor at St. Jerome s College in Nagercoil, India. He has three years of research experience and authored nine research papers in reputed international journals. His research interests include Web Security, Web Communication, Vehicular Network and Social Network Security. Dr. B. Ramakrishnan is currently working as Associate Professor in the Department of Computer Science and research Centre in S.T. Hindu College, Nagercoil. He received his M.Sc degree from Madurai Kamaraj University, Madurai and received Mphil (Comp. Sc.) from Alagappa University Karikudi. He earned his Doctorate degree in the field of Computer Science from Manonmaniam Sundaranar University, Tirunelveli. He has a teaching experience of 26 years. He has twelve years of research experience and published more than twenty five international journals. His research interests lie in the field of Vehicular networks, mobile network and communication, Cloud computing, Green computing, Ad-hoc networks and Network security.
FORBIDDEN - Ethical Hacking Workshop Duration
 Workshop Course Module FORBIDDEN - Ethical Hacking Workshop Duration Lecture and Demonstration : 15 Hours Security Challenge : 01 Hours Introduction Security can't be guaranteed. As Clint Eastwood once
Workshop Course Module FORBIDDEN - Ethical Hacking Workshop Duration Lecture and Demonstration : 15 Hours Security Challenge : 01 Hours Introduction Security can't be guaranteed. As Clint Eastwood once
Secure Mail Registration and Viewing Procedures
 Secure Mail Registration and Viewing Procedures May 2011 For External Secure Mail Recipients Contents This document provides a brief, end user oriented overview of the Associated Banc Corp s Secure Email
Secure Mail Registration and Viewing Procedures May 2011 For External Secure Mail Recipients Contents This document provides a brief, end user oriented overview of the Associated Banc Corp s Secure Email
Secure Cross Border File Protection & Sharing for Enterprise Product Brief CRYPTOMILL INC
 C NNECTED Circles of Trust Secure Cross Border File Protection & Sharing for Enterprise Product Brief www.cryptomill.com product overview OVERVIEW Connected Circles of Trust is an endpoint data security
C NNECTED Circles of Trust Secure Cross Border File Protection & Sharing for Enterprise Product Brief www.cryptomill.com product overview OVERVIEW Connected Circles of Trust is an endpoint data security
CSIS Security Research and Intelligence Research paper: Threats when using Online Social Networks Date: 16/05-2007
 CSIS Security Research and Intelligence Research paper: Threats when using Online Social Networks Date: 16/05-2007 Written by Dennis Rand [email protected] http://www.csis.dk Table of contents Table of contents...
CSIS Security Research and Intelligence Research paper: Threats when using Online Social Networks Date: 16/05-2007 Written by Dennis Rand [email protected] http://www.csis.dk Table of contents Table of contents...
Store & Share Quick Start
 Store & Share Quick Start What is Store & Share? Store & Share is a service that allows you to upload all of your content (documents, music, video, executable files) into a centralized cloud storage. You
Store & Share Quick Start What is Store & Share? Store & Share is a service that allows you to upload all of your content (documents, music, video, executable files) into a centralized cloud storage. You
Mikogo User Guide Mac Version
 Mikogo User Guide Mac Version Table of Contents Registration... 3 Download & Installation... 4 Start a Session... 5 Join a Session... 5 Features... 6 Participant List... 6 Switch Presenter... 7 Remote
Mikogo User Guide Mac Version Table of Contents Registration... 3 Download & Installation... 4 Start a Session... 5 Join a Session... 5 Features... 6 Participant List... 6 Switch Presenter... 7 Remote
High Speed Internet - User Guide. Welcome to. your world.
 High Speed Internet - User Guide Welcome to your world. 1 Welcome to your world :) Thank you for choosing Cogeco High Speed Internet. Welcome to your new High Speed Internet service. When it comes to a
High Speed Internet - User Guide Welcome to your world. 1 Welcome to your world :) Thank you for choosing Cogeco High Speed Internet. Welcome to your new High Speed Internet service. When it comes to a
Loophole+ with Ethical Hacking and Penetration Testing
 Loophole+ with Ethical Hacking and Penetration Testing Duration Lecture and Demonstration: 15 Hours Security Challenge: 01 Hours Introduction Security can't be guaranteed. As Clint Eastwood once said,
Loophole+ with Ethical Hacking and Penetration Testing Duration Lecture and Demonstration: 15 Hours Security Challenge: 01 Hours Introduction Security can't be guaranteed. As Clint Eastwood once said,
BeamYourScreen User Guide Mac Version
 BeamYourScreen User Guide Mac Version Table of Contents Registration 3 Download & Installation 4 Start a Session 5 Join a Session 6 Features 7 Participant List 7 Switch Presenter 8 Remote Control 8 Whiteboard
BeamYourScreen User Guide Mac Version Table of Contents Registration 3 Download & Installation 4 Start a Session 5 Join a Session 6 Features 7 Participant List 7 Switch Presenter 8 Remote Control 8 Whiteboard
McAfee Internet Security Suite Quick-Start Guide
 Enjoy a Worry Free Online Experience McAfee Internet Security Suite protects your PC, identity and online experience. It also includes PC and network tools, plus McAfee SiteAdvisor for safe surfing. Internet
Enjoy a Worry Free Online Experience McAfee Internet Security Suite protects your PC, identity and online experience. It also includes PC and network tools, plus McAfee SiteAdvisor for safe surfing. Internet
An Insight into Cookie Security
 An Insight into Cookie Security Today most websites and web based applications use cookies. Cookies are primarily used by the web server to track an authenticated user or other user specific details. This
An Insight into Cookie Security Today most websites and web based applications use cookies. Cookies are primarily used by the web server to track an authenticated user or other user specific details. This
An Intelligent Approach for Data Fortification in Cloud Computing
 An Intelligent Approach for Data Fortification in Cloud Computing Supriya Mandhare 1, Prof. A. K. Sen 2, Asso. Prof. Rajkumar Shende 3 1,3 Department of Computer Engineering, St. Francis Institute of Technology,
An Intelligent Approach for Data Fortification in Cloud Computing Supriya Mandhare 1, Prof. A. K. Sen 2, Asso. Prof. Rajkumar Shende 3 1,3 Department of Computer Engineering, St. Francis Institute of Technology,
Banking Security using Honeypot
 Banking Security using Honeypot Sandeep Chaware D.J.Sanghvi College of Engineering, Mumbai [email protected] Abstract New threats are constantly emerging to the security of organization s information
Banking Security using Honeypot Sandeep Chaware D.J.Sanghvi College of Engineering, Mumbai [email protected] Abstract New threats are constantly emerging to the security of organization s information
XpoLog Center Suite Log Management & Analysis platform
 XpoLog Center Suite Log Management & Analysis platform Summary: 1. End to End data management collects and indexes data in any format from any machine / device in the environment. 2. Logs Monitoring -
XpoLog Center Suite Log Management & Analysis platform Summary: 1. End to End data management collects and indexes data in any format from any machine / device in the environment. 2. Logs Monitoring -
3 Easy Steps to Get Started
 Quick Start Guide Contents 1. What is icafe Manager?... 4 1.1. Server... 4 1.2. Client Terminal... 4 2. Downloading, Registering & Activating Cafe Code... 5 2.1. Downloading icafe Manager:... 5 2.2. Registering
Quick Start Guide Contents 1. What is icafe Manager?... 4 1.1. Server... 4 1.2. Client Terminal... 4 2. Downloading, Registering & Activating Cafe Code... 5 2.1. Downloading icafe Manager:... 5 2.2. Registering
ONLINE MARKETING CENTER. User Guide
 ONLINE MARKETING CENTER User Guide 1 Online Marketing Center User Guide Introduction 2 Home Page 2 Getting Started 4 Business Information 5 Creating a Project 7 Designs 7 Projects 9 Step 1: Project Info
ONLINE MARKETING CENTER User Guide 1 Online Marketing Center User Guide Introduction 2 Home Page 2 Getting Started 4 Business Information 5 Creating a Project 7 Designs 7 Projects 9 Step 1: Project Info
Frequently Asked Questions (FAQ)
 Your personal information and account security is important to us. This product employs a Secure Sign On process that includes layers of protection at time of product log in to mitigate risk, and thwart
Your personal information and account security is important to us. This product employs a Secure Sign On process that includes layers of protection at time of product log in to mitigate risk, and thwart
SecuraLive ULTIMATE SECURITY
 SecuraLive ULTIMATE SECURITY Home Edition for Windows USER GUIDE SecuraLive ULTIMATE SECURITY USER MANUAL Introduction: Welcome to SecuraLive Ultimate Security Home Edition. SecuraLive Ultimate Security
SecuraLive ULTIMATE SECURITY Home Edition for Windows USER GUIDE SecuraLive ULTIMATE SECURITY USER MANUAL Introduction: Welcome to SecuraLive Ultimate Security Home Edition. SecuraLive Ultimate Security
Mikogo User Guide Windows Version
 Mikogo User Guide Windows Version Table of Contents Registration 3 Download & Installation 4 Start a Session 4 Join a Session 5 Features 6 Participant List 6 Switch Presenter 7 Remote Control 7 Whiteboard
Mikogo User Guide Windows Version Table of Contents Registration 3 Download & Installation 4 Start a Session 4 Join a Session 5 Features 6 Participant List 6 Switch Presenter 7 Remote Control 7 Whiteboard
Mikogo User Guide Linux Version
 Mikogo User Guide Linux Version Table of Contents Registration 3 Downloading & Running the Application 4 Start a Session 5 Join a Session 6 Features 7 Participant List 7 Switch Presenter 8 Remote Control
Mikogo User Guide Linux Version Table of Contents Registration 3 Downloading & Running the Application 4 Start a Session 5 Join a Session 6 Features 7 Participant List 7 Switch Presenter 8 Remote Control
UPC Online Back-Up. UPC WebTáros DOCUMENTATION
 UPC Online Back-Up UPC WebTáros DOCUMENTATION 1 Table of contents 1 Online Storage - general... 3 1.1 What is UPC Online Storage?... 3 1.2 What is Online Storage capable of?... 3 1.2.1 Secure your digital
UPC Online Back-Up UPC WebTáros DOCUMENTATION 1 Table of contents 1 Online Storage - general... 3 1.1 What is UPC Online Storage?... 3 1.2 What is Online Storage capable of?... 3 1.2.1 Secure your digital
Internet threats: steps to security for your small business
 Internet threats: 7 steps to security for your small business Proactive solutions for small businesses A restaurant offers free WiFi to its patrons. The controller of an accounting firm receives a confidential
Internet threats: 7 steps to security for your small business Proactive solutions for small businesses A restaurant offers free WiFi to its patrons. The controller of an accounting firm receives a confidential
Cyber Security Presentation Cyber Security Month Curtis McNay, Director of IT Security
 Cyber Security Presentation Cyber Security Month Curtis McNay, Director of IT Security The IT Security Office (ITSO) What We Do? Risk Assessment Network and System Security Monitoring Vulnerability Scanning
Cyber Security Presentation Cyber Security Month Curtis McNay, Director of IT Security The IT Security Office (ITSO) What We Do? Risk Assessment Network and System Security Monitoring Vulnerability Scanning
Enabling Public Accountability and Data Sharing for Storage Security in Cloud Computing
 VOLUME 1, NUMBER 1, JUNE 2014 OPEN JOURNAL OF INFORMATION SECURITY AND APPLICATIONS Enabling Public Accountability and Data Sharing for Storage Security in Cloud Computing K. Mohammed Aaqib Ameen, A. Anny
VOLUME 1, NUMBER 1, JUNE 2014 OPEN JOURNAL OF INFORMATION SECURITY AND APPLICATIONS Enabling Public Accountability and Data Sharing for Storage Security in Cloud Computing K. Mohammed Aaqib Ameen, A. Anny
How Much Space? New SkyDrive accounts offer 7GB of cloud storage. Older users of the service were able to reclaim more free space (25 GB).
 What is SkyDrive? The short answer is that SkyDrive is a free service offered by Microsoft to host files in the cloud. SkyDrive also allows you to store, sync, and share files with other people and devices
What is SkyDrive? The short answer is that SkyDrive is a free service offered by Microsoft to host files in the cloud. SkyDrive also allows you to store, sync, and share files with other people and devices
IJREAT International Journal of Research in Engineering & Advanced Technology, Volume 1, Issue 1, March, 2013 ISSN: 2320-8791 www.ijreat.
 Intrusion Detection in Cloud for Smart Phones Namitha Jacob Department of Information Technology, SRM University, Chennai, India Abstract The popularity of smart phone is increasing day to day and the
Intrusion Detection in Cloud for Smart Phones Namitha Jacob Department of Information Technology, SRM University, Chennai, India Abstract The popularity of smart phone is increasing day to day and the
MacScan. MacScan User Guide. Detect, Isolate and Remove Spyware
 MacScan MacScan User Guide Detect, Isolate and Remove Spyware Part 1 1.1 Introduction MacScan is a spyware detection utility for Macintosh OS X that finds and removes spyware and other Internet files
MacScan MacScan User Guide Detect, Isolate and Remove Spyware Part 1 1.1 Introduction MacScan is a spyware detection utility for Macintosh OS X that finds and removes spyware and other Internet files
Thanks for showing interest in Vortex IIT Delhi & What After College (WAC) Ethical Hacking Workshop.
 Thanks for showing interest in Vortex IIT Delhi & What After College (WAC) Ethical Hacking Workshop. Our aim is to address the students apprehensions and anxieties regarding their career prospects in Ethical
Thanks for showing interest in Vortex IIT Delhi & What After College (WAC) Ethical Hacking Workshop. Our aim is to address the students apprehensions and anxieties regarding their career prospects in Ethical
Securing the endpoint and your data
 #SymVisionEmea #SymVisionEmea Securing the endpoint and your data Piero DePaoli Sr. Director, Product Marketing Marcus Brownell Sr. Regional Product Manager Securing the Endpoint and Your Data 2 Safe harbor
#SymVisionEmea #SymVisionEmea Securing the endpoint and your data Piero DePaoli Sr. Director, Product Marketing Marcus Brownell Sr. Regional Product Manager Securing the Endpoint and Your Data 2 Safe harbor
Final Year Project Interim Report
 2013 Final Year Project Interim Report FYP12016 AirCrypt The Secure File Sharing Platform for Everyone Supervisors: Dr. L.C.K. Hui Dr. H.Y. Chung Students: Fong Chun Sing (2010170994) Leung Sui Lun (2010580058)
2013 Final Year Project Interim Report FYP12016 AirCrypt The Secure File Sharing Platform for Everyone Supervisors: Dr. L.C.K. Hui Dr. H.Y. Chung Students: Fong Chun Sing (2010170994) Leung Sui Lun (2010580058)
Presented by Evan Sylvester, CISSP
 Presented by Evan Sylvester, CISSP Who Am I? Evan Sylvester FAST Information Security Officer MBA, Texas State University BBA in Management Information Systems at the University of Texas Certified Information
Presented by Evan Sylvester, CISSP Who Am I? Evan Sylvester FAST Information Security Officer MBA, Texas State University BBA in Management Information Systems at the University of Texas Certified Information
IDRBT Working Paper No. 11 Authentication factors for Internet banking
 IDRBT Working Paper No. 11 Authentication factors for Internet banking M V N K Prasad and S Ganesh Kumar ABSTRACT The all pervasive and continued growth being provided by technology coupled with the increased
IDRBT Working Paper No. 11 Authentication factors for Internet banking M V N K Prasad and S Ganesh Kumar ABSTRACT The all pervasive and continued growth being provided by technology coupled with the increased
Mac OS X User Manual Version 2.0
 Mac OS X User Manual Version 2.0 Welcome to ncrypted Cloud! ncrypted Cloud is a Privacy, Security, and Collaboration application that uses Industry Standard Encryption Technology (AES-256 bit encryption)
Mac OS X User Manual Version 2.0 Welcome to ncrypted Cloud! ncrypted Cloud is a Privacy, Security, and Collaboration application that uses Industry Standard Encryption Technology (AES-256 bit encryption)
AVOIDING ONLINE THREATS CYBER SECURITY MYTHS, FACTS, TIPS. ftrsecure.com
 AVOIDING ONLINE THREATS CYBER SECURITY MYTHS, FACTS, TIPS ftrsecure.com Can You Separate Myths From Facts? Many Internet myths still persist that could leave you vulnerable to internet crimes. Check out
AVOIDING ONLINE THREATS CYBER SECURITY MYTHS, FACTS, TIPS ftrsecure.com Can You Separate Myths From Facts? Many Internet myths still persist that could leave you vulnerable to internet crimes. Check out
ARP and DNS. ARP entries are cached by network devices to save time, these cached entries make up a table
 ARP and DNS Both protocols do conversions of a sort, but the distinct difference is ARP is needed for packet transfers and DNS is not needed but makes things much easier. ARP Address Resolution Protocol
ARP and DNS Both protocols do conversions of a sort, but the distinct difference is ARP is needed for packet transfers and DNS is not needed but makes things much easier. ARP Address Resolution Protocol
The Case of Decentralized Online Social Networks
 The Case of Decentralized Online Social Networks Rammohan Narendula School of Computer and Communication Sciences, EPFL, Switzerland Abstract As the Online Social Networks (OSNs) amass unprecedented amounts
The Case of Decentralized Online Social Networks Rammohan Narendula School of Computer and Communication Sciences, EPFL, Switzerland Abstract As the Online Social Networks (OSNs) amass unprecedented amounts
Welcome to EMP Monitor (Employee monitoring system):
 Welcome to EMP Monitor (Employee monitoring system): Overview: Admin End. User End. 1.0 Admin End: Introduction to Admin panel. Admin panel log in. Introduction to UI. Adding an Employee. Getting and editing
Welcome to EMP Monitor (Employee monitoring system): Overview: Admin End. User End. 1.0 Admin End: Introduction to Admin panel. Admin panel log in. Introduction to UI. Adding an Employee. Getting and editing
2014 Entry Form (Complete one for each entry.) Fill out the entry name exactly as you want it listed in the program.
 2014 Entry Form (Complete one for each entry.) Fill out the entry name exactly as you want it listed in the program. Entry Name HFA Submission Contact Phone Email Qualified Entries must be received by
2014 Entry Form (Complete one for each entry.) Fill out the entry name exactly as you want it listed in the program. Entry Name HFA Submission Contact Phone Email Qualified Entries must be received by
Security Practices for Online Collaboration and Social Media
 Cisco IT Best Practice Collaboration Security Cisco on Cisco Best Practice Security Practices for Online Collaboration and Social Media January 2012 2013 Cisco and/or its affiliates. All rights reserved.
Cisco IT Best Practice Collaboration Security Cisco on Cisco Best Practice Security Practices for Online Collaboration and Social Media January 2012 2013 Cisco and/or its affiliates. All rights reserved.
HomeNet. Gateway User Guide
 HomeNet Gateway User Guide Gateway User Guide Table of Contents HomeNet Gateway User Guide Gateway User Guide Table of Contents... 2 Introduction... 3 What is the HomeNet Gateway (Gateway)?... 3 How do
HomeNet Gateway User Guide Gateway User Guide Table of Contents HomeNet Gateway User Guide Gateway User Guide Table of Contents... 2 Introduction... 3 What is the HomeNet Gateway (Gateway)?... 3 How do
INROADS, INC. TRAINING AND DEVELOPMENT. Intern E- Learning Guide 2012 (rev. 4.2012)
 INROADS, INC. TRAINING AND DEVELOPMENT Intern E- Learning Guide 2012 (rev. 4.2012) 1 Introduction Welcome to another valuable piece of your INROADS development experience, e learning! If you are unfamiliar
INROADS, INC. TRAINING AND DEVELOPMENT Intern E- Learning Guide 2012 (rev. 4.2012) 1 Introduction Welcome to another valuable piece of your INROADS development experience, e learning! If you are unfamiliar
Bellevue University Cybersecurity Programs & Courses
 Undergraduate Course List Core Courses: CYBR 250 Introduction to Cyber Threats, Technologies and Security CIS 311 Network Security CIS 312 Securing Access Control CIS 411 Assessments and Audits CYBR 320
Undergraduate Course List Core Courses: CYBR 250 Introduction to Cyber Threats, Technologies and Security CIS 311 Network Security CIS 312 Securing Access Control CIS 411 Assessments and Audits CYBR 320
Policies & Procedures. Moat Community College E-Safety Policy
 Moat Community College E-Safety Policy Vision Statement Moat Community College embraces the positive impact and educational benefits that can be achieved through appropriate use of the Internet and associated
Moat Community College E-Safety Policy Vision Statement Moat Community College embraces the positive impact and educational benefits that can be achieved through appropriate use of the Internet and associated
Cisco on Cisco Best Practice Security Practices for Online Collaboration and Social Media
 January 2012 Cisco on Cisco Best Practice Security Practices for Online Collaboration and Social Media January 2012 All contents are Copyright 1992 2012 Cisco Systems, Inc. All rights reserved. This document
January 2012 Cisco on Cisco Best Practice Security Practices for Online Collaboration and Social Media January 2012 All contents are Copyright 1992 2012 Cisco Systems, Inc. All rights reserved. This document
Dreamweaver: Getting Started Website Structure Why is this relevant?
 Dreamweaver: Getting Started Dreamweaver is a Graphic Designer s tool to create websites as he or she designs. As part of the Adobe Creative Suite, Dreamweaver is able to work in conjunction with Photoshop,
Dreamweaver: Getting Started Dreamweaver is a Graphic Designer s tool to create websites as he or she designs. As part of the Adobe Creative Suite, Dreamweaver is able to work in conjunction with Photoshop,
Welcome to ncrypted Cloud!
 Welcome to ncrypted Cloud! ncrypted Cloud is a Privacy, Security, and Collaboration application that uses Industry Standard Encryption Technology (AES-256 bit encryption) to secure files stored in the
Welcome to ncrypted Cloud! ncrypted Cloud is a Privacy, Security, and Collaboration application that uses Industry Standard Encryption Technology (AES-256 bit encryption) to secure files stored in the
Business 360 Online - Product concepts and features
 Business 360 Online - Product concepts and features Version November 2014 Business 360 Online from Software Innovation is a cloud-based tool for information management. It helps you to work smarter with
Business 360 Online - Product concepts and features Version November 2014 Business 360 Online from Software Innovation is a cloud-based tool for information management. It helps you to work smarter with
Comodo Mobile Security for Android Software Version 3.0
 Comodo Mobile Security for Android Software Version 3.0 User Guide Guide Version 3.0.042115 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo Mobile
Comodo Mobile Security for Android Software Version 3.0 User Guide Guide Version 3.0.042115 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo Mobile
Last modified: November 22, 2013 This manual was updated for the TeamDrive Android client version 3.0.216
 Last modified: November 22, 2013 This manual was updated for the TeamDrive Android client version 3.0.216 2013 TeamDrive Systems GmbH Page 1 Table of Contents 1 Starting TeamDrive for Android for the First
Last modified: November 22, 2013 This manual was updated for the TeamDrive Android client version 3.0.216 2013 TeamDrive Systems GmbH Page 1 Table of Contents 1 Starting TeamDrive for Android for the First
MiraCosta College now offers two ways to access your student virtual desktop.
 MiraCosta College now offers two ways to access your student virtual desktop. We now feature the new VMware Horizon View HTML access option available from https://view.miracosta.edu. MiraCosta recommends
MiraCosta College now offers two ways to access your student virtual desktop. We now feature the new VMware Horizon View HTML access option available from https://view.miracosta.edu. MiraCosta recommends
The Key to Secure Online Financial Transactions
 Transaction Security The Key to Secure Online Financial Transactions Transferring money, shopping, or paying debts online is no longer a novelty. These days, it s just one of many daily occurrences on
Transaction Security The Key to Secure Online Financial Transactions Transferring money, shopping, or paying debts online is no longer a novelty. These days, it s just one of many daily occurrences on
IS L06 Protect Servers and Defend Against APTs with Symantec Critical System Protection
 IS L06 Protect Servers and Defend Against APTs with Symantec Critical System Protection Description Lab flow At the end of this lab, you should be able to Discover how to harness the power and capabilities
IS L06 Protect Servers and Defend Against APTs with Symantec Critical System Protection Description Lab flow At the end of this lab, you should be able to Discover how to harness the power and capabilities
Security in an Increasingly Threatened World. SMS: A better way of doing Two Factor Authentication (2FA)
 Security in an Increasingly Threatened World SMS: A better way of doing Two Factor Authentication (2FA) January 2015 The Proliferation of The App World The revolution of the smart phone forever affected
Security in an Increasingly Threatened World SMS: A better way of doing Two Factor Authentication (2FA) January 2015 The Proliferation of The App World The revolution of the smart phone forever affected
Wireless Network Security
 Wireless Network Security Bhavik Doshi Privacy and Security Winter 2008-09 Instructor: Prof. Warren R. Carithers Due on: February 5, 2009 Table of Contents Sr. No. Topic Page No. 1. Introduction 3 2. An
Wireless Network Security Bhavik Doshi Privacy and Security Winter 2008-09 Instructor: Prof. Warren R. Carithers Due on: February 5, 2009 Table of Contents Sr. No. Topic Page No. 1. Introduction 3 2. An
10 best practice suggestions for common smartphone threats
 10 best practice suggestions for common smartphone threats Jeff R Fawcett Dell SecureWorks Security Practice Executive M Brandon Swain Dell SecureWorks Security Practice Executive When using your Bluetooth
10 best practice suggestions for common smartphone threats Jeff R Fawcett Dell SecureWorks Security Practice Executive M Brandon Swain Dell SecureWorks Security Practice Executive When using your Bluetooth
Facebook Smart Card FB 121211_1800
 Facebook Smart Card FB 121211_1800 Social Networks - Do s and Don ts Only establish and maintain connections with people you know and trust. Review your connections often. Assume that ANYONE can see any
Facebook Smart Card FB 121211_1800 Social Networks - Do s and Don ts Only establish and maintain connections with people you know and trust. Review your connections often. Assume that ANYONE can see any
Google Apps for Education: The Basics
 Google Apps for Education: The Basics You will learn how to get started with Google Drive by uploading and converting documents. You will also learn how to share your documents with others. Plus learn
Google Apps for Education: The Basics You will learn how to get started with Google Drive by uploading and converting documents. You will also learn how to share your documents with others. Plus learn
Comodo Mobile Security for Android Software Version 2.5
 Comodo Mobile Security for Android Software Version 2.5 User Guide Guide Version 2.5.111014 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Mobile
Comodo Mobile Security for Android Software Version 2.5 User Guide Guide Version 2.5.111014 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Mobile
Facebook and Social Networking Security
 Facebook and Social Networking Security By Martin Felsky November 2009 Table of Contents Introduction... 1 What is Facebook?... 2 Privacy Settings... 5 Friends... 7 Applications... 8 Twitter... 9 Should
Facebook and Social Networking Security By Martin Felsky November 2009 Table of Contents Introduction... 1 What is Facebook?... 2 Privacy Settings... 5 Friends... 7 Applications... 8 Twitter... 9 Should
Leonardo Hotels Group Page 1
 Privacy Policy The Leonardo Hotels Group, represented by Sunflower Management GmbH & Co.KG, respects the right to privacy of every individual who access and navigate our website. Leonardo Hotels takes
Privacy Policy The Leonardo Hotels Group, represented by Sunflower Management GmbH & Co.KG, respects the right to privacy of every individual who access and navigate our website. Leonardo Hotels takes
Neat Cloud Service + Mobile App
 Getting Started with Neat Cloud Service + Mobile App Neat transforms paper and electronic documents into organized digital files that are easy to find, use, and share. Neat Cloud Service and Mobile App
Getting Started with Neat Cloud Service + Mobile App Neat transforms paper and electronic documents into organized digital files that are easy to find, use, and share. Neat Cloud Service and Mobile App
Mikogo Web Conferencing & Remote Support. User Guide (Windows Version)
 Mikogo Web Conferencing & Remote Support User Guide (Windows Version) Table of Contents Register an Account... 3 Download the Software... 3 Start a Session... 4 Informing your Participants to Join the
Mikogo Web Conferencing & Remote Support User Guide (Windows Version) Table of Contents Register an Account... 3 Download the Software... 3 Start a Session... 4 Informing your Participants to Join the
U.S. Cellular Mobile Data Security. User Guide Version 00.01
 U.S. Cellular Mobile Data Security User Guide Version 00.01 Table of Contents Install U.S. Cellular Mobile Data Security...3 Activate U.S. Cellular Mobile Data Security...3 Main Interface...3 Checkup...4
U.S. Cellular Mobile Data Security User Guide Version 00.01 Table of Contents Install U.S. Cellular Mobile Data Security...3 Activate U.S. Cellular Mobile Data Security...3 Main Interface...3 Checkup...4
NYS OCFS CMS Contractor Manual
 NYS OCFS CMS Contractor Manual C O N T E N T S CHAPTER 1... 1-1 Chapter 1: Introduction to the Contract Management System... 1-2 CHAPTER 2... 2-1 Accessing the Contract Management System... 2-2 Shortcuts
NYS OCFS CMS Contractor Manual C O N T E N T S CHAPTER 1... 1-1 Chapter 1: Introduction to the Contract Management System... 1-2 CHAPTER 2... 2-1 Accessing the Contract Management System... 2-2 Shortcuts
A NOVEL APPROACH FOR MULTI-KEYWORD SEARCH WITH ANONYMOUS ID ASSIGNMENT OVER ENCRYPTED CLOUD DATA
 A NOVEL APPROACH FOR MULTI-KEYWORD SEARCH WITH ANONYMOUS ID ASSIGNMENT OVER ENCRYPTED CLOUD DATA U.Pandi Priya 1, R.Padma Priya 2 1 Research Scholar, Department of Computer Science and Information Technology,
A NOVEL APPROACH FOR MULTI-KEYWORD SEARCH WITH ANONYMOUS ID ASSIGNMENT OVER ENCRYPTED CLOUD DATA U.Pandi Priya 1, R.Padma Priya 2 1 Research Scholar, Department of Computer Science and Information Technology,
Secure Email Client Guide
 PRESIDIO BANK 33 Secure Email Client Guide THE BUSINESS BANK THAT WORKS 8/2013 Table of Contents Introduction.....3 Our Responsibility to Protect Confidential Information....4 Registering and Accessing
PRESIDIO BANK 33 Secure Email Client Guide THE BUSINESS BANK THAT WORKS 8/2013 Table of Contents Introduction.....3 Our Responsibility to Protect Confidential Information....4 Registering and Accessing
158.738. Implementation & Management of Systems Security. Amavax Project. Ethical Hacking Challenge. Group Project By
 158.738 Implementation & Management of Systems Security Amavax Project Ethical Hacking Challenge Group Project By Nawed Rajeh Mansour Kavin Khan Al Gamdi Al Harthi Palanavel The Amavax project required
158.738 Implementation & Management of Systems Security Amavax Project Ethical Hacking Challenge Group Project By Nawed Rajeh Mansour Kavin Khan Al Gamdi Al Harthi Palanavel The Amavax project required
1. What information do we collect?
 CHURNSPOTTER.IO PRIVACY POLICY Last updated: February 03, 2015 Welcome to the http://churnspotter.io Web site (the Site ) owned by PREDICSIS S.A.S, a corporation organized and existing under the laws of
CHURNSPOTTER.IO PRIVACY POLICY Last updated: February 03, 2015 Welcome to the http://churnspotter.io Web site (the Site ) owned by PREDICSIS S.A.S, a corporation organized and existing under the laws of
Upon Installation, Soda
 Upon Installation, Soda Prompts you to create your user profile to register for a new profile Note: Asks your for your particulars Prompts you to select a password. You would need to provide this password
Upon Installation, Soda Prompts you to create your user profile to register for a new profile Note: Asks your for your particulars Prompts you to select a password. You would need to provide this password
Getting started with Mendeley. Guide by ITC library
 Getting started with Mendeley Guide by ITC library January 2015 Table of Contents 1 Mendeley in not even 10 steps... 3 1.1 Go to www.mendeley.com and register... 3 1.2 Download Mendeley desktop... 3 1.3
Getting started with Mendeley Guide by ITC library January 2015 Table of Contents 1 Mendeley in not even 10 steps... 3 1.1 Go to www.mendeley.com and register... 3 1.2 Download Mendeley desktop... 3 1.3
Internet Security Priorities. Benenson Strategy Group and American Viewpoint December 20, 2013
 Internet Security Priorities Prepared for: Presented by: Benenson Strategy Group and American Viewpoint December 20, 2013 Methodology The Benenson Strategy Group and American Viewpoint conducted 1,000
Internet Security Priorities Prepared for: Presented by: Benenson Strategy Group and American Viewpoint December 20, 2013 Methodology The Benenson Strategy Group and American Viewpoint conducted 1,000
A briefing paper on the osconcert online ticketing system security issues, vulnerabilities and privacy concerns. OSCONCERT SECURITY AND PRIVACY.
 osconcert Security and Privacy. A briefing paper on the osconcert online ticketing system security issues, vulnerabilities and privacy concerns. Contents. OSCONCERT SECURITY AND PRIVACY. 1 CONTENTS. 1
osconcert Security and Privacy. A briefing paper on the osconcert online ticketing system security issues, vulnerabilities and privacy concerns. Contents. OSCONCERT SECURITY AND PRIVACY. 1 CONTENTS. 1
A Layered Signcryption Model for Secure Cloud System Communication
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 4, Issue. 6, June 2015, pg.1086
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 4, Issue. 6, June 2015, pg.1086
AN INVESTIGATION OF SECURITY THEME FOR CLOUD COMPUTING
 AN INVESTIGATION OF SECURITY THEME FOR CLOUD COMPUTING Mrs. J. Pavithra 1 Mr. A. Naveen 2 1 (MRIT, Hyderabad, India, [email protected]) 2 (Asst. Professor, MRIT, Hyderabad, India, [email protected])
AN INVESTIGATION OF SECURITY THEME FOR CLOUD COMPUTING Mrs. J. Pavithra 1 Mr. A. Naveen 2 1 (MRIT, Hyderabad, India, [email protected]) 2 (Asst. Professor, MRIT, Hyderabad, India, [email protected])
Network Security Web Security
 Network Security Web Security Anna Sperotto, Ramin Sadre Design and Analysis of Communication Systems Group University of Twente, 2012 Cross Site Scripting Cross Side Scripting (XSS) XSS is a case of (HTML)
Network Security Web Security Anna Sperotto, Ramin Sadre Design and Analysis of Communication Systems Group University of Twente, 2012 Cross Site Scripting Cross Side Scripting (XSS) XSS is a case of (HTML)
PROCEDURE TO JOIN WEBEX MEETING FOR REMOTE SUPPORT
 PROCEDURE TO JOIN WEBEX MEETING FOR REMOTE SUPPORT A. DISABLING UAC 1. Click Start button, type uac in the Search Box and click on Change User Account Control Settings, as shown in the figure below. 2.
PROCEDURE TO JOIN WEBEX MEETING FOR REMOTE SUPPORT A. DISABLING UAC 1. Click Start button, type uac in the Search Box and click on Change User Account Control Settings, as shown in the figure below. 2.
Reading an email sent with Voltage SecureMail. Using the Voltage SecureMail Zero Download Messenger (ZDM)
 Reading an email sent with Voltage SecureMail Using the Voltage SecureMail Zero Download Messenger (ZDM) SecureMail is an email protection service developed by Voltage Security, Inc. that provides email
Reading an email sent with Voltage SecureMail Using the Voltage SecureMail Zero Download Messenger (ZDM) SecureMail is an email protection service developed by Voltage Security, Inc. that provides email
Preventing Identity Theft using Shift Key mechanism and QR Code with Sudoku Puzzle
 DOI 10.4010/2014.282 ISSN-2321-3361 2014 IJESC Research Article Preventing Identity Theft using Shift Key mechanism and QR Code with Sudoku Puzzle R.Saisrikanth Department of Computer Science and Engineering
DOI 10.4010/2014.282 ISSN-2321-3361 2014 IJESC Research Article Preventing Identity Theft using Shift Key mechanism and QR Code with Sudoku Puzzle R.Saisrikanth Department of Computer Science and Engineering
Sync Security and Privacy Brief
 Introduction Security and privacy are two of the leading issues for users when transferring important files. Keeping data on-premises makes business and IT leaders feel more secure, but comes with technical
Introduction Security and privacy are two of the leading issues for users when transferring important files. Keeping data on-premises makes business and IT leaders feel more secure, but comes with technical
ONLINE QUICK REFERENCE CARD ENDNOTE
 QUICK REFERENCE CARD ENDNOTE ONLINE Access your password-protected reference library anywhere, at any time. Download references and full text from just about any online data source, such as PubMed, GoogleScholar
QUICK REFERENCE CARD ENDNOTE ONLINE Access your password-protected reference library anywhere, at any time. Download references and full text from just about any online data source, such as PubMed, GoogleScholar
