Attention windows of second level fixations. Input image. Attention window of first level fixation
|
|
|
- Everett Hunt
- 10 years ago
- Views:
Transcription
1 HandSegmentationUsingLearning-BasedPredictionand VericationforHandSignRecognition DepartmentofComputerScience YuntaoCuiandJohnJ.Weng mentationschemeusingattentionimagesfrommultiple Thispaperpresentsaprediction-and-vericationseg- EastLansing,MI48824,USA MichiganStateUniversity canhandlealargenumberofdierentdeformableobjectspresentedincomplexbackgrounds.theschemeingareferenceimageofthestaticbackground[8],or eachsequencerepresentsahandsign.theexperimen- a3%falserejectionrate. menthandsinthesequencesofintensityimages,where talresultshoweda95%correctsegmentationratewith 1Introduction vericationscheme.thesystemhasbeentestedtoseg-elsor2-dvelocity-eldmodels[2].thesecondtype extractingthemotionentitybasedon3-dmotionmod- (e.g.[9]).thesemodelstypicallyneedagoodinitial positiontoconverge.theyalsoneedarelativelyclean ofapproachestashapetodeformablemovingobjects imagegradient. backgroundsincetheexternalforcesaredenedbythe guidedbythepastknowledgethroughaprediction-and- xations.amajoradvantageofthisschemeisthatit isalsorelativelyecientsincethesegmentationis cultiesfacedbythevision-basedapproachissegmenta- tion(e.g.[1,3,4,7,11,13]).oneofthemajordi- amountofresearchonvision-basedhandsignrecognimanmachineinterface.recently,thereisasignicantionofthemovinghandfromsometimescomplexback- suchasuniformbackground. grounds.toavoidtheaboveproblem,someofthesys- temsrelyonmarkers.theothersuserestrictivesetups Theabilitytointerprethandsignsisessentialforhu- Inordertoovercomethedicultiesfacedbythesegmentationmethodsfordeformableobjectsmentionevironment,itisnotverydiculttoroughlydetermine thepositionofamovingobjectintheimageusingmotioninformation.however,itisnotsimpleifthetaskis toextractthecontouroftheobjectfromvariousbackgrounds.severalmotionsegmentationmethodshavefigure1:anillustrationoftwolevelxationsofaninput handimage. thattheobjectofinterestismovinginastationaryen- choiceofvisualcueforvisualattention.ifweassume ofanalyzingtemporalsequence,motionisanobvious toperformthetaskofhandsegmentation.inthecase Inthispaper,wepresentalearning-basedapproachbackgroundinterference. thereconstructionisnotabletofullygetridofthe positioninarectangularattentionimagetogetherwith thebackground.theattentionimagewentthrougha reconstructionbasedonlearningwhichcanreducethe backgroundinterferencetoacertaindegree.however, proach[5].inthatapproach,theobjectwasassumedto above,wehaveproposedaneigen-subspacelearningap- beenproposed.theseapproachesfallintotwocategories.approachesintherstcategoryaredesignedto ofapproachesachievesasegmentationbyeitherbuild- dealwithrigidmovingobjects(e.g.[2,8]).thistypesolvethesegmentationproblemcompletely.similar kindofmultiplexationshasahierarchalstructure.as showninfig.1,therstlevelofthexationconcentratesontheentirehand,whilethenextlevelofthe xationtakescareofdierentpartsofthehand.the tohumanvision,multiplexationsareneeded.this attentionwindowoftherstlevelxationusuallycontainsapartofthebackground.butaswecontinue Oneattentionwindowfromasinglexationcannot zoomingintheobjectfromdierentxations,theat- Input image Attention window of first level fixation Attention windows of second level fixations
2 tentionwindowsbecomefocusingondierentpartsof theobject.oneimportantfeatureoftheseattention windowsisthattheytypicallycontainmuchlessbackgroundthantheattentionwindowoftherstlevelxation.theseattentionimagesfrommultiplexations canbeusedasimportantvisualcuestosegmentthe objectofinterestfromtheinputimage.inthispaper, wepresentalearning-basedapproachwhicheciently utilizestheattentionimagesobtainedfromthemultiple xationsthroughaprediction-and-vericationscheme toperformthetaskofhandsegmentation. 2ValidSegmentation Inthissection,wedenetheverierftoevaluate thesegmentationusingfunctioninterpolationbasedon trainingsamples.givenaninputimage,wecanconstructanattentionimageofthehandasshowninfig. 2.Input image Attention image Extract and scale the hand Figure2:Theillustrationofconstructingattentionimages. 2.1TheMostExpressiveFeatures(MEF) LetanattentionimageFofmrowsandncolumns bean(mn)-dimensionalvector.forexample,theset ofimagepixelsff(i;j)j0i<m;0j<ng canbewrittenasavectorv=(v1;v2;;vd)where vmi+j=f(i;j)andd=mn.typicallydisvery large.thekarhunen-loeveprojection[12]isavery ecientwaytoreduceahigh-dimensionalspacetoa low-dimensionalsubspace.thevectorsproducedbythe Karhunen-Loeveprojectionaretypicallycalledtheprinciplecomponents.Wecallthesevectorsthemostexpressivefeatures(MEF)inthattheybestdescribethe samplepopulationinthesenseoflineartransform[4]. 2.2ApproximationasFunctionInterpolation AfterprojectinghandattentionimagestoalowdimensionalMEFspace,wearenowreadytoapproximatetheverierfusingfunctioninterpolation. Denition1GivenatrainingvectorXk;iofgesture kinthemefspace,agaussianbasisfunctionsiis si(x)=e?kx?xk;ik2,whereisapositivedampingfactor,andkkdenotestheeuclideandistance. Averysmalltendstoreducethecontributionof neighboringtrainingsamples. Denition2GivenasetofntrainingsamplesLk= fxk;1;xk;2;;xk;ngofgesturek,thecondencelevel oftheinputxbelongstoclasskisdenedas:gk(x)= Pni=1cisi(X),wherethesiisaGaussianbasisfunctionandthecoecientsci'saretobedeterminedbythe trainingsamples. Thecoecientsci'saredeterminedasfollows.Given ntrainingsamples,wehavenequations gk(xk;i)=nxi=1cisi(xk;i); (1) whicharelinearwithrespecttothecoecientsci's.if wesetgk(xk;i)equalto1,wecansolvetheaboveequationsforciusinggauss-jordaneliminationmethod. ThecondenceleveldenedinDenition2canbe usedtoverifyasegmentationresult. Denition3GivenasegmentationresultSandacon- dencelevell,theverierfoutputsvalidsegmentation forgesturekifgk(s)>l. Intuitively,asegmentationresultSisvalidifthereis atrainingsamplethatissucientlyclosetoit. 3PredicationforValidSegmentation Thissectioninvestigatestheproblemhowtonda validsegmentation.ourapproachistousetheattentionimagesfrommultiplexationsoftraininghandimages.givenahandattentionimage,axationimage isdeterminedbyitsxationposition(s;t)andascale r.fig.3showstheattentionimagesofthe19xations fromonetrainingsample. Figure3:Theattentionimagesfrom19xationsofa trainingsample.therstoneisthesameastheoriginal handattentionimage. 3.1Overview Givenatrainingset,weobtainasetofattention imagesfrommultiplexationsforeachimageintheset. Eachattentionimagefromaxationisassociatedwith thesegmentationmaskoforiginalhandattentionimage, thescalerandthepositionofthexation(s;t).these informationisnecessarytorecoverthesegmentationfor theentireobject. Duringthesegmentationstage,werstusethemotioninformationtoselectvisualattention.Then,we
3 trydierentxationsontheinputimage.anattentionimagefromaxationofaninputimageisused toquerythetrainingset.thesegmentationmaskassociatedwiththequeryresultisthepredication.the predictedsegmentationmaskisthenappliedtotheinputimage.finally,weverifythesegmentationresult toseeiftheextractedsubimagecorrespondstoahand gesturethathasbeenlearned.iftheanswerisyes,we ndthesolution.thissolutioncanfurthergothrough arenementprocess.fig.4givestheoutlineofthe scheme. 3.2OrganizationofAttentionImagesfrom Fixations Inordertoachieveafastretrieval,webuildahierarchicalstructuretoorganizethedata. Denition4Ahierarchicalquasi-VoronoidiagramP ofsisasetofpartitionsp=fp1;p2;;pmg,where everypi=fpi;1;;pi;nig,i=1;2;;misapartitionofs.pi+1=fpi+1;1;;pi+1;ni+1gisaner VoronoidiagrampartitionofPiinthesensethatcorrespondingtoeveryelementPi;k2Pi,Pi+1containsa VoronoipartitionfPi+1;s;;Pi+1;tgofPi;k. 0,1 1,2 1,3 1,4 1,5 1,6 1,7 2,2 2,3 2,4 2,5 2,6 2,7 2,8 2,10 2,14 2,12 Figure5:A2-Dillustrationofahierarchicalquasi-Voronoi diagram. ThegraphicdescriptioninFig.5givesansimpli- edbutintuitiveexplanationofthehierarchicalquasi- Voronoidiagram.Thestructureisatree.Theroot correspondstotheentirespaceofallthepossibleinputs.thechildrenoftherootpartitionthespaceinto largecells,asshownbythicklinesinfig.5.thechildrenofaparentsubdividetheparent'scellfutureinto smallercells,andsoon. 3.3PredictionasQueryingtheTraining Set GivenatrainingsetL,ahierarchicalquasi-Voronoi diagramp=fp1;p2;;pngcorrespondingtoland aquerysamplex,thepredictionproblemistonda trainingsamplex02l,suchthatkx?x0kkx?x00k foranyx002lwithx006=x0.thetypeofquerymentionedaboveisanearestneighborproblem,alsoknown aspost-oceproblem[10].therestilllacksofecient solutionsforthecasewithdimensionhigherthanthree. Inthissection,wewillpresentanecientalgorithm whenthetrainingsetisd-supportiveasdenedbelow. Denition5LetSbeasetwhichcontainsallpossible samples.atrainingsetl=fl1;l2;;lngisadsupportivetrainingsetifforanytestsamplex2s, thereexistisuchthatkx?lik<d,wherekkisthe Euclideandistance. Nexttwotheoremsshowhowtoprunethesearch patheswhenthetrainingsetisd-supportive. Theorem1Wehaveasetofd-supportivetrainingset L=fL1;L2;;Lng,ahierarchicalquasi-VoronoidiagramP=fP1;P2;;PngcorrespondingtoLanda querysamplex2s.lettheithpartitionbepi= fpi;1;pi;2;;pi;nigandc=fc1;c2;;cnigbethe correspondingcentersofregionsinpi.assumec1be thecentertoxsuchthatkc1?xkkci?xkforany i6=1.letc2beanyothercenterandp1beaboundary hyperplanebetweenregionsrepresentedbyc1andc2as illustratedinfig.6.thentheregionofc2doesnot containthenearesttrainingsampletoxifthedistance betweenxandthehyperplanep1isgreaterthand. d a b e f boundary hyperplane M P1 P2 m C 1 C 2 X Figure6:A2Dillustrationofnearestneighborquerytheorems. Inordertoavoidtocalculatethepointtohyperplane distanceinahighdimensionalspace,wecanusefollowingequivalenttheorem. Theorem2LetkC1?C2k=r,f=r2,e=r2?d, kc1?xk=aandkc2?xk=basshowninfig.6. TheregionofC2doesnotcontainthenearesttraining sampletoxifa2?e2<b2?f2. FortheproofTheorem1andTheorem2,thereader isreferredto[6]. 4Experiments Wehaveappliedoursegmentationschemetothetask ofhandsegmentationintheexperiments.thenumber ofgesturesweusedinourexperimentis40.thesegestureshaveappearedinthesignswhichhavebeenused
4 input sequence Confident?Figure4:Overviewofthesegmentationscheme. Motion based visual attention Extractor attention images recalled mask from multiple fixations Information needed by the Verifier approximate function (e.g., illustratedinfig.7.thesizeofattentionwindowused coefficients) intheexperimentis3232pixels. totestthehandsignrecognitionsystem[4].theyareverierfforthatgesture.givenasetoftrainingsam- plesl=fx1;x2;;xngforgesturek,weempirically information for gesture k gesture 1 functionasfollows: pleswereusedtoobtainedtheapproximationofthe determinedthedampingfactorintheinterpolation Predictor gesture k gesture n no yes index Thesecondtypeoftrainingwastogeneratetheat- =0:2Pn?1 i=1kxi?xi+1k n?1 : (2) Discard Refinement proximationforverierfwhichwouldbeusedlater 4.1Training iments.thersttypeoftrainingistogettheap- tocheckthevalidationofthesegmentation.foreach gesture,anumberbetween(27and36)oftrainingsam- Twotypesoftrainingwereconductedintheexper- Figure7:40handgesturesusedintheexperiment. Thetotalnumberoftrainingattentionimagesis HandSegmentation presentedintheattentionwindowwouldbediscarded. tentionimageswithmorethan30%backgroundpixels ples.inthecurrentimplementation,theselectionofthe foreachtrainingsampleasshowninfig.3.theattentionimagesfrommultiplexationsoftrainingsammentationtaskfromatemporalsequenceofintensity xationsismechanical.totally19xationswereused images.eachsequencerepresentsacompletehandsign. Fig.8(a)showstwosamplesequences. weutilizemotioninformationtondamotionattention window.theattentionalgorithmcandetecttherough Thetrainedsystemwastestedtoperformtheseg- Inordertospeeduptheprocessofthesegmentation,
5 (a) (b) attentionareshownusingdarkrectangular;(c)theresultsofthesegmentationareshownaftermaskingothebackground. Figure8:Thesamplesoftheexperimentalresults.(a)Theinputtestingsequences;(b)Theresultsofmotion-basedvisual
6 positionofamovingobject,buttheaccuracyisnot guaranteedasshowninfig.8(b).wesolvethisproblembydoingsomelimitedsearchbasedonthemotion attentionwindow.inthecurrentimplementation,given amotionattentionwindowwithmrowsandncolumns, wetrythecandidateswithsizefrom(0:5m;0:5n)to (2m;2n)usingstepsize(0:5m;0:5n). Wetestedthesystemwith802images(161sequences)whichwerenotusedinthetraining.Aresult wasrejectedifthesystemcouldnotndavalidsegmentationwithacondencelevell.thesegmentation wasconsideredasacorrectoneifthecorrectgesture segmentationcwasretrievedandplacedintheright positionofthetestimage.forthecaseofl=0:2,we haveachieved95%correctsegmentationratewith3% falserejectionrate.fig.8(c)showssomesegmentationresults.wesummarizetheexperimentalresultsin Table1.ThetimewasobtainedonaSGI-INDIGO2 workstation. Table1:Summaryoftheexperimentaldata NumberofCorrect FalseTime testimagessegmentationrejectionperimage % 3%58.3sec. 5ConclusionsandFutureWork Asegmentationschemeusingattentionimagesfrom multiplexationsispresentedinthispaper.themajoradvantageofthisschemeisthatitcanhandlea largenumberofdierentdeformableobjectspresented invariouscomplexbackgrounds.theschemeisalso relativelyecientsincethesearchofthesegmentation isguidedbythepastknowledgethroughapredicationand-vericationscheme. Inthecurrentimplementation,thexationsaregeneratedmechanically.Thenumberofxationsandthe positionsofxationsarethesameregardlessofthetypes ofgestures.thisisnotveryecient.somegestures maybeverysimplesothatafewxationsareenough torecognizethem.nevertheless,inordertoachievethe optimalperformance,dierentgesturesmayrequiredifferentpositionsofxations.inthefuture,weplanto investigatethegenerationofthexationsalsobasedon learning.thepreviousxationsareusedtoguidethe nextaction.thenextactioncouldbe(a)termination oftheprocessofgeneratingxationifthegesturehas alreadybeenrecognized;or(b)ndingtheappropriate positionfornextxation. Acknowledgements TheauthorswouldliketothankYuZhong,Kal Rayes,DougNeal,andValerieBolsterformakingthemselvesavailablefortheexperiments.ThisworkwassupportedinpartbyNSFgrantNo.IRI andONR grantno.n References [1]A.BobickandA.Wilson,\Astate-basedtechnique forthesummarizationandrecognitionofgesture", inproc.5thint'lconf.computervision,pp ,boston,1995. [2]P.BouthemyandE.Francois,\Motionsegmentationandqualitativedynamicsceneanalysisfroman imagesequence",ininternationaljournalofcomputervision,vol.10,pp ,1993. [3]R.Cipolla,Y.OkamotoandY.Kuno,\Robust structurefrommotionusingmotionparallax",in IEEEConf.ComputerVisionandPatternRecog., pp ,1993. [4]Y.Cui,D.SwetsandJ.Weng,\Learning-based handsignrecognitionusingshoslif-m",inproc. 5thInt'lConf.ComputerVision,pp , Boston,1995. [5]Y.CuiandJ.Weng,"2Dobjectsegmentationfrom foveaimagesbasedoneigen-subspacelearning", Proc.IEEEInt'lSymposiumonComputerVision, CoralGables,FL,Nov.20-22,1995. [6]Y.CuiandJ.Weng,\Alearning-basedpredictionand-vericationsegmentationschemeforhandsign imagesequences",technicalreportcps-95-43, ComputerScienceDepartment,MichiganState University,Dec.,1995. [7]T.DarrellandA.Pentland,\Space-timegestures",inIEEEConf.ComputerVisionandPatternRecog.,pp ,1993. [8]G.W.Donohoe,D.R.HushandN.Ahmed, \Changedetectionfortargetdetectionandclassicationinvideosequences",inProc.Int'lConf. Acoust.,Speech,SignalProcessing,pp , [9]M.Kass,A.WitkinandD.Terzopoulos,\Snakes: activecontourmodels",inproc.1sticcv,pp ,1987. [10]D.Knuth,TheArtofComputerProgrammingIII: SortingandSearching,Addison-Wesley,Reading, Mass.,1973. [11]J.J.KuchandT.S.Huang,\Visionbasedhand modelingandtracking",inproc.international ConferenceonComputerVision,June,1995. [12]M.M.Loeve,ProbabilityTheory,Princeton,NJ: VanNostrand,1955. [13]T.E.StarnerandA.Pentland,\Visualrecognition ofamericansignlanguageusinghiddenmarkov models",inproc.internationalworkshoponautomaticface-andgesture-recognition",june1995.
hp calculators HP 12C Net Present Value Cash flow and NPV calculations Cash flow diagrams The HP12C cash flow approach Practice solving NPV problems
 Cash flow and NPV calculations Cash flow diagrams The HP12C cash flow approach Practice solving NPV problems How to modify cash flow entries Cash Flow and NPV calculations Cash flow analysis is an extension
Cash flow and NPV calculations Cash flow diagrams The HP12C cash flow approach Practice solving NPV problems How to modify cash flow entries Cash Flow and NPV calculations Cash flow analysis is an extension
ME6130 An introduction to CFD 1-1
 ME6130 An introduction to CFD 1-1 What is CFD? Computational fluid dynamics (CFD) is the science of predicting fluid flow, heat and mass transfer, chemical reactions, and related phenomena by solving numerically
ME6130 An introduction to CFD 1-1 What is CFD? Computational fluid dynamics (CFD) is the science of predicting fluid flow, heat and mass transfer, chemical reactions, and related phenomena by solving numerically
hp calculators HP 12C Internal Rate of Return Cash flow and IRR calculations Cash flow diagrams The HP12C cash flow approach
 Cash flow and IRR calculations Cash flow diagrams The HP12C cash flow approach Practice with solving cash flow problems related to IRR How to modify cash flow entries Cash Flow and IRR calculations Cash
Cash flow and IRR calculations Cash flow diagrams The HP12C cash flow approach Practice with solving cash flow problems related to IRR How to modify cash flow entries Cash Flow and IRR calculations Cash
Data Mining Techniques Chapter 6: Decision Trees
 Data Mining Techniques Chapter 6: Decision Trees What is a classification decision tree?.......................................... 2 Visualizing decision trees...................................................
Data Mining Techniques Chapter 6: Decision Trees What is a classification decision tree?.......................................... 2 Visualizing decision trees...................................................
Tutorial: Assigning Prelogin Criteria to Policies
 CHAPTER 4 This tutorial provides an overview of the CSD configuration sequence. The configuration chapters that follow provide detailed instructions on the attributes. The sections are as follows: Overview
CHAPTER 4 This tutorial provides an overview of the CSD configuration sequence. The configuration chapters that follow provide detailed instructions on the attributes. The sections are as follows: Overview
Quick Start. Creating a Scoring Application. RStat. Based on a Decision Tree Model
 Creating a Scoring Application Based on a Decision Tree Model This Quick Start guides you through creating a credit-scoring application in eight easy steps. Quick Start Century Corp., an electronics retailer,
Creating a Scoring Application Based on a Decision Tree Model This Quick Start guides you through creating a credit-scoring application in eight easy steps. Quick Start Century Corp., an electronics retailer,
Adabas Archiving. Mike Conena, Database Administrator Commonwealth of Massachusetts
 Adabas Archiving Mike Conena, Database Administrator Commonwealth of Massachusetts What is it? A tool to archive Data from Adabas Files What are the benefits? Minimizes only necessary data on primary databases
Adabas Archiving Mike Conena, Database Administrator Commonwealth of Massachusetts What is it? A tool to archive Data from Adabas Files What are the benefits? Minimizes only necessary data on primary databases
Purchase Agent Installation Guide
 Purchase Agent Installation Guide Before Installing Purchase Agent... 1 Installing Purchase Agent..... 2 Installing Purchase Agent Help Files... 8 Post Installation Getting Started... 13 BEFORE INSTALLING
Purchase Agent Installation Guide Before Installing Purchase Agent... 1 Installing Purchase Agent..... 2 Installing Purchase Agent Help Files... 8 Post Installation Getting Started... 13 BEFORE INSTALLING
5 Systems of Equations
 Systems of Equations Concepts: Solutions to Systems of Equations-Graphically and Algebraically Solving Systems - Substitution Method Solving Systems - Elimination Method Using -Dimensional Graphs to Approximate
Systems of Equations Concepts: Solutions to Systems of Equations-Graphically and Algebraically Solving Systems - Substitution Method Solving Systems - Elimination Method Using -Dimensional Graphs to Approximate
Applied Biosystems Real-Time System Computer Setup Guide
 Applied Biosystems Real-Time System Computer Setup Guide Unpack the computer boxes and set the proper voltage. 1. Unpack the computer boxes and place the monitor, computer, keyboard, and mouse on the bench
Applied Biosystems Real-Time System Computer Setup Guide Unpack the computer boxes and set the proper voltage. 1. Unpack the computer boxes and place the monitor, computer, keyboard, and mouse on the bench
DYNAMICS AS A PROCESS, HELPING UNDERGRADUATES UNDERSTAND DESIGN AND ANALYSIS OF DYNAMIC SYSTEMS
 Session 2666 DYNAMICS AS A PROCESS, HELPING UNDERGRADUATES UNDERSTAND DESIGN AND ANALYSIS OF DYNAMIC SYSTEMS Louis J. Everett, Mechanical Engineering Texas A&M University College Station, Texas 77843 [email protected]
Session 2666 DYNAMICS AS A PROCESS, HELPING UNDERGRADUATES UNDERSTAND DESIGN AND ANALYSIS OF DYNAMIC SYSTEMS Louis J. Everett, Mechanical Engineering Texas A&M University College Station, Texas 77843 [email protected]
How-To Guide Importing a Portal Public Key into an ECC client
 How-To Guide Importing a Portal Public Key into an ECC client Shows how to import Portal Public Key Certificates and grant single sign on access to ECC clients using the imported key certificate. Wolfgang
How-To Guide Importing a Portal Public Key into an ECC client Shows how to import Portal Public Key Certificates and grant single sign on access to ECC clients using the imported key certificate. Wolfgang
PMLead. Project Management Professional. edition. Based on PMBOK Guide 4 th. www.pmlead.net
 PMLead Project Management Professional Based on PMBOK Guide 4 th edition www.pmlead.net SECTION II Chapter 3 Project Management Processes Chapter 3 Project Process Groups A process is a set of interrelated
PMLead Project Management Professional Based on PMBOK Guide 4 th edition www.pmlead.net SECTION II Chapter 3 Project Management Processes Chapter 3 Project Process Groups A process is a set of interrelated
DRAFT Standard Operating Procedure for Long-Term Archiving of PM 2.5 Filters and Extracts
 Page 1 of 6 DRAFT Standard Operating Procedure for Long-Term Archiving of PM 2.5 Filters and Extracts Environmental and Industrial Sciences Division Research Triangle Institute Research Triangle Park,
Page 1 of 6 DRAFT Standard Operating Procedure for Long-Term Archiving of PM 2.5 Filters and Extracts Environmental and Industrial Sciences Division Research Triangle Institute Research Triangle Park,
DataTrak 2.95.0 Release Notes
 The following is an overview of this release. Release Date: Thursday, Release Number: 2.95.0 Enhancements: In this release, we made the following enhancements: Billing Info - We improved validation of
The following is an overview of this release. Release Date: Thursday, Release Number: 2.95.0 Enhancements: In this release, we made the following enhancements: Billing Info - We improved validation of
A Cognitive Approach to Vision for a Mobile Robot
 A Cognitive Approach to Vision for a Mobile Robot D. Paul Benjamin Christopher Funk Pace University, 1 Pace Plaza, New York, New York 10038, 212-346-1012 [email protected] Damian Lyons Fordham University,
A Cognitive Approach to Vision for a Mobile Robot D. Paul Benjamin Christopher Funk Pace University, 1 Pace Plaza, New York, New York 10038, 212-346-1012 [email protected] Damian Lyons Fordham University,
International Journal of Computer Trends and Technology (IJCTT) volume 4 Issue 8 August 2013
 A Short-Term Traffic Prediction On A Distributed Network Using Multiple Regression Equation Ms.Sharmi.S 1 Research Scholar, MS University,Thirunelvelli Dr.M.Punithavalli Director, SREC,Coimbatore. Abstract:
A Short-Term Traffic Prediction On A Distributed Network Using Multiple Regression Equation Ms.Sharmi.S 1 Research Scholar, MS University,Thirunelvelli Dr.M.Punithavalli Director, SREC,Coimbatore. Abstract:
The Correlation Coefficient
 The Correlation Coefficient Lelys Bravo de Guenni April 22nd, 2015 Outline The Correlation coefficient Positive Correlation Negative Correlation Properties of the Correlation Coefficient Non-linear association
The Correlation Coefficient Lelys Bravo de Guenni April 22nd, 2015 Outline The Correlation coefficient Positive Correlation Negative Correlation Properties of the Correlation Coefficient Non-linear association
NOTE-TAKING. Rutgers School of Nursing
 NOTE-TAKING Rutgers School of Nursing WHEN TO TAKE NOTES BEFORE DURING AFTER I. Before Class: Preparation (mental and physical) Read Textbook BEFORE Class Start Taking Notes BEFORE Class The SQ3R Method
NOTE-TAKING Rutgers School of Nursing WHEN TO TAKE NOTES BEFORE DURING AFTER I. Before Class: Preparation (mental and physical) Read Textbook BEFORE Class Start Taking Notes BEFORE Class The SQ3R Method
USER GUIDE MANTRA WEB EXTRACTOR. www.altiliagroup.com
 USER GUIDE MANTRA WEB EXTRACTOR www.altiliagroup.com Page 1 of 57 MANTRA WEB EXTRACTOR USER GUIDE TABLE OF CONTENTS CONVENTIONS... 2 CHAPTER 2 BASICS... 6 CHAPTER 3 - WORKSPACE... 7 Menu bar 7 Toolbar
USER GUIDE MANTRA WEB EXTRACTOR www.altiliagroup.com Page 1 of 57 MANTRA WEB EXTRACTOR USER GUIDE TABLE OF CONTENTS CONVENTIONS... 2 CHAPTER 2 BASICS... 6 CHAPTER 3 - WORKSPACE... 7 Menu bar 7 Toolbar
June 2011. TerraSAR-X-based Flood Mapping Service
 June 2011 TerraSAR-X-based Flood Mapping Service Service TerraSAR-X-based Flood Mapping Product Flood extent map Product specifications Flood mask / water mask Input / output data Summary Content Date
June 2011 TerraSAR-X-based Flood Mapping Service Service TerraSAR-X-based Flood Mapping Product Flood extent map Product specifications Flood mask / water mask Input / output data Summary Content Date
Enhancing the SNR of the Fiber Optic Rotation Sensor using the LMS Algorithm
 1 Enhancing the SNR of the Fiber Optic Rotation Sensor using the LMS Algorithm Hani Mehrpouyan, Student Member, IEEE, Department of Electrical and Computer Engineering Queen s University, Kingston, Ontario,
1 Enhancing the SNR of the Fiber Optic Rotation Sensor using the LMS Algorithm Hani Mehrpouyan, Student Member, IEEE, Department of Electrical and Computer Engineering Queen s University, Kingston, Ontario,
Architectural Design Structured Design. Xin Feng
 Architectural Design Structured Design Xin Feng Structured Analysis Method Based on the Data Flow Diagrams Specification Data flow diagram Design Structured tree This is NOT an OO-Method!!! Data Flow Model
Architectural Design Structured Design Xin Feng Structured Analysis Method Based on the Data Flow Diagrams Specification Data flow diagram Design Structured tree This is NOT an OO-Method!!! Data Flow Model
THE PROCESS APPROACH IN ISO 9001:2015
 International Organization for Standardization BIBC II, Chemin de Blandonnet 8, CP 401, 1214 Vernier, Geneva, Switzerland Tel: +41 22 749 01 11, Web: www.iso.org THE PROCESS APPROACH IN ISO 9001:2015 Purpose
International Organization for Standardization BIBC II, Chemin de Blandonnet 8, CP 401, 1214 Vernier, Geneva, Switzerland Tel: +41 22 749 01 11, Web: www.iso.org THE PROCESS APPROACH IN ISO 9001:2015 Purpose
Simulation of processes in a mining enterprise with Tecnomatix Plant Simulation
 Simulation of processes in a mining enterprise with Tecnomatix Plant Simulation Vladimir Medvedev Simulation of ore extraction on the open mountain works Page 2 Simulation objective To verify current control
Simulation of processes in a mining enterprise with Tecnomatix Plant Simulation Vladimir Medvedev Simulation of ore extraction on the open mountain works Page 2 Simulation objective To verify current control
Copyright 2013 CTB/McGraw-Hill LLC. 1
 TerraNova, Third Edition Science and Social Studies Joan Buzick DRC/CTB Assessment Consultant Organizing for Assessment Success Today s Webinar Objectives Why test Science and Social Studies with TerraNova3
TerraNova, Third Edition Science and Social Studies Joan Buzick DRC/CTB Assessment Consultant Organizing for Assessment Success Today s Webinar Objectives Why test Science and Social Studies with TerraNova3
SQLFlow: PL/SQL Multi-Diagrammatic Source Code Visualization
 SQLFlow: PL/SQL Multi-Diagrammatic Source Code Visualization Samir Tartir Department of Computer Science University of Georgia Athens, Georgia 30602 USA Email: [email protected] ABSTRACT: A major problem
SQLFlow: PL/SQL Multi-Diagrammatic Source Code Visualization Samir Tartir Department of Computer Science University of Georgia Athens, Georgia 30602 USA Email: [email protected] ABSTRACT: A major problem
INTERNATIONAL JOURNAL OF COMPUTER ENGINEERING & TECHNOLOGY (IJCET)
 INTERNATIONAL JOURNAL OF COMPUTER ENGINEERING & TECHNOLOGY (IJCET) International Journal of Computer Engineering and Technology (IJCET), ISSN 0976 6367(Print), ISSN 0976 6367(Print) ISSN 0976 6375(Online)
INTERNATIONAL JOURNAL OF COMPUTER ENGINEERING & TECHNOLOGY (IJCET) International Journal of Computer Engineering and Technology (IJCET), ISSN 0976 6367(Print), ISSN 0976 6367(Print) ISSN 0976 6375(Online)
Intelligent Learning Content Management System based on SCORM Standard. Dr. Shian-Shyong Tseng
 Intelligent Learning Content Management System based on SCORM Standard Dr. Shian-Shyong Tseng Department of Computer Science, National Chiao Tung University (NCTU), Taiwan (R.O.C) 2008 Researching Topics
Intelligent Learning Content Management System based on SCORM Standard Dr. Shian-Shyong Tseng Department of Computer Science, National Chiao Tung University (NCTU), Taiwan (R.O.C) 2008 Researching Topics
Data Masking Secure Sensitive Data Improve Application Quality. Becky Albin Chief IT Architect [email protected]
 Data Masking Secure Sensitive Data Improve Application Quality Becky Albin Chief IT Architect [email protected] Data Masking for Adabas The information provided in this PPT is entirely subject
Data Masking Secure Sensitive Data Improve Application Quality Becky Albin Chief IT Architect [email protected] Data Masking for Adabas The information provided in this PPT is entirely subject
ABAQUS Tutorial. 3D Modeling
 Spring 2011 01/21/11 ABAQUS Tutorial 3D Modeling This exercise intends to demonstrate the steps you would follow in creating and analyzing a simple solid model using ABAQUS CAE. Introduction A solid undergoes
Spring 2011 01/21/11 ABAQUS Tutorial 3D Modeling This exercise intends to demonstrate the steps you would follow in creating and analyzing a simple solid model using ABAQUS CAE. Introduction A solid undergoes
Value Engineering VE with Risk Assessment RA
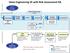 Preparation Conclude & Report Value Engineering VE with Risk Assessment RA yes START Plan for VE and RA Value Engineering Job Plan 1 2 Function Information Analysis 3 Creative 4 Evaluation 5 Develop recommendations
Preparation Conclude & Report Value Engineering VE with Risk Assessment RA yes START Plan for VE and RA Value Engineering Job Plan 1 2 Function Information Analysis 3 Creative 4 Evaluation 5 Develop recommendations
Notecard Question & Answer Technique
 Academic Resources Notecard Question & Answer Technique To succeed in college, important ideas from lectures and textbooks must be identified, organized, recorded, practiced and stored in long term memory
Academic Resources Notecard Question & Answer Technique To succeed in college, important ideas from lectures and textbooks must be identified, organized, recorded, practiced and stored in long term memory
CHAPTER 1. Introduction to CAD/CAM/CAE Systems
 CHAPTER 1 1.1 OVERVIEW Introduction to CAD/CAM/CAE Systems Today s industries cannot survive worldwide competition unless they introduce new products with better quality (quality, Q), at lower cost (cost,
CHAPTER 1 1.1 OVERVIEW Introduction to CAD/CAM/CAE Systems Today s industries cannot survive worldwide competition unless they introduce new products with better quality (quality, Q), at lower cost (cost,
Modelling, Extraction and Description of Intrinsic Cues of High Resolution Satellite Images: Independent Component Analysis based approaches
 Modelling, Extraction and Description of Intrinsic Cues of High Resolution Satellite Images: Independent Component Analysis based approaches PhD Thesis by Payam Birjandi Director: Prof. Mihai Datcu Problematic
Modelling, Extraction and Description of Intrinsic Cues of High Resolution Satellite Images: Independent Component Analysis based approaches PhD Thesis by Payam Birjandi Director: Prof. Mihai Datcu Problematic
PROCESS DOCKET - PRINT CHECKS
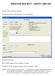 PROCESS DOCKET - PRINT CHECKS Docket > Process Docket (Normal) The Process Docket - Specifications screen will display. Enter the following: RUN TYPE: Toggle to Trial (default) or Normal. EXTRACT TYPE:
PROCESS DOCKET - PRINT CHECKS Docket > Process Docket (Normal) The Process Docket - Specifications screen will display. Enter the following: RUN TYPE: Toggle to Trial (default) or Normal. EXTRACT TYPE:
In mathematics, there are four attainment targets: using and applying mathematics; number and algebra; shape, space and measures, and handling data.
 MATHEMATICS: THE LEVEL DESCRIPTIONS In mathematics, there are four attainment targets: using and applying mathematics; number and algebra; shape, space and measures, and handling data. Attainment target
MATHEMATICS: THE LEVEL DESCRIPTIONS In mathematics, there are four attainment targets: using and applying mathematics; number and algebra; shape, space and measures, and handling data. Attainment target
Multi-factor Authentication in Banking Sector
 Multi-factor Authentication in Banking Sector Tushar Bhivgade, Mithilesh Bhusari, Ajay Kuthe, Bhavna Jiddewar,Prof. Pooja Dubey Department of Computer Science & Engineering, Rajiv Gandhi College of Engineering
Multi-factor Authentication in Banking Sector Tushar Bhivgade, Mithilesh Bhusari, Ajay Kuthe, Bhavna Jiddewar,Prof. Pooja Dubey Department of Computer Science & Engineering, Rajiv Gandhi College of Engineering
UML TUTORIALS THE USE CASE MODEL
 UML TUTORIALS THE USE CASE MODEL www.sparxsystems.com.au Sparx Systems 2004 Page 1/5 describes the proposed functionality of the new system. A Use Case represents a discrete unit of interaction between
UML TUTORIALS THE USE CASE MODEL www.sparxsystems.com.au Sparx Systems 2004 Page 1/5 describes the proposed functionality of the new system. A Use Case represents a discrete unit of interaction between
Large Scale Systems Design G52LSS
 G52LSS Refine Requirements Lecture 13 Use Case Analysis Use Case Diagrams and Use Cases Steps of Use Case Analysis Example: University Registration System Learning outcomes: understand the importance of
G52LSS Refine Requirements Lecture 13 Use Case Analysis Use Case Diagrams and Use Cases Steps of Use Case Analysis Example: University Registration System Learning outcomes: understand the importance of
Quantitative market research for incremental improvement innovations. Professor Eric von Hippel MIT Sloan School of Management
 Quantitative market research for incremental improvement innovations Professor Eric von Hippel MIT Sloan School of Management Incremental innovation is important. Quantitative market research can identify
Quantitative market research for incremental improvement innovations Professor Eric von Hippel MIT Sloan School of Management Incremental innovation is important. Quantitative market research can identify
EXTENDED ANGEL: KNOWLEDGE-BASED APPROACH FOR LOC AND EFFORT ESTIMATION FOR MULTIMEDIA PROJECTS IN MEDICAL DOMAIN
 EXTENDED ANGEL: KNOWLEDGE-BASED APPROACH FOR LOC AND EFFORT ESTIMATION FOR MULTIMEDIA PROJECTS IN MEDICAL DOMAIN Sridhar S Associate Professor, Department of Information Science and Technology, Anna University,
EXTENDED ANGEL: KNOWLEDGE-BASED APPROACH FOR LOC AND EFFORT ESTIMATION FOR MULTIMEDIA PROJECTS IN MEDICAL DOMAIN Sridhar S Associate Professor, Department of Information Science and Technology, Anna University,
IST722 Data Warehousing
 IST722 Data Warehousing Components of the Data Warehouse Michael A. Fudge, Jr. Recall: Inmon s CIF The CIF is a reference architecture Understanding the Diagram The CIF is a reference architecture CIF
IST722 Data Warehousing Components of the Data Warehouse Michael A. Fudge, Jr. Recall: Inmon s CIF The CIF is a reference architecture Understanding the Diagram The CIF is a reference architecture CIF
ORIENTATIONS INVENTORY
 ORIENTATIONS INVENTORY Instructions for questions (1-18 and 20-26): Place a check mark in the blank next to the statement that is more true for you or true most of the time. 1. When planning the activities
ORIENTATIONS INVENTORY Instructions for questions (1-18 and 20-26): Place a check mark in the blank next to the statement that is more true for you or true most of the time. 1. When planning the activities
SN54165, SN54LS165A, SN74165, SN74LS165A PARALLEL-LOAD 8-BIT SHIFT REGISTERS
 The SN54165 and SN74165 devices SN54165, SN54LS165A, SN74165, SN74LS165A PRODUCTION DATA information is current as of publication date. Products conform to specifications per the terms of Texas Instruments
The SN54165 and SN74165 devices SN54165, SN54LS165A, SN74165, SN74LS165A PRODUCTION DATA information is current as of publication date. Products conform to specifications per the terms of Texas Instruments
Next Generation of Global Production Management Using Sensing and Analysis Technology
 Hitachi Review Vol. 65 (2016), No. 5 47 Featured Articles Next Generation of Global Production Management Using Sensing and Analysis Technology Hideya Isaka Hiroto Nagayoshi Hiroshi Yoshikawa Toshihiro
Hitachi Review Vol. 65 (2016), No. 5 47 Featured Articles Next Generation of Global Production Management Using Sensing and Analysis Technology Hideya Isaka Hiroto Nagayoshi Hiroshi Yoshikawa Toshihiro
Client Security Risk Assessment Questionnaire
 Select the appropriate answer from the drop down in the column, and provide a brief description in the section. 1 Do you have a member of your organization with dedicated information security duties? 2
Select the appropriate answer from the drop down in the column, and provide a brief description in the section. 1 Do you have a member of your organization with dedicated information security duties? 2
Building Information Modelling (BIM); How it Improves Building Performance. R.P. Kumanayake Lecturer, Department of Civil Engineering
 Building Information Modelling (BIM); How it Improves Building Performance R.P. Kumanayake Lecturer, Department of Civil Engineering R.M.P.S. Bandara Lecturer, Department of Mechanical Engineering Faculty
Building Information Modelling (BIM); How it Improves Building Performance R.P. Kumanayake Lecturer, Department of Civil Engineering R.M.P.S. Bandara Lecturer, Department of Mechanical Engineering Faculty
SpotCell Automatic Dialer System
 Application Note 108 11-Jun-00 SpotCell Automatic Dialer System Overview All SpotCell adaptive repeaters now come equipped with built-in alarming capabilities which have been designed to be compatible
Application Note 108 11-Jun-00 SpotCell Automatic Dialer System Overview All SpotCell adaptive repeaters now come equipped with built-in alarming capabilities which have been designed to be compatible
Customer Training Material. Lecture 2. Introduction to. Methodology ANSYS FLUENT. ANSYS, Inc. Proprietary 2010 ANSYS, Inc. All rights reserved.
 Lecture 2 Introduction to CFD Methodology Introduction to ANSYS FLUENT L2-1 What is CFD? Computational Fluid Dynamics (CFD) is the science of predicting fluid flow, heat and mass transfer, chemical reactions,
Lecture 2 Introduction to CFD Methodology Introduction to ANSYS FLUENT L2-1 What is CFD? Computational Fluid Dynamics (CFD) is the science of predicting fluid flow, heat and mass transfer, chemical reactions,
Software Specification and Architecture 2IW80
 Software Specification and Architecture 2IW80 Julien Schmaltz (slides partly from M. Mousavi and A. Serebrenik) Lecture 03: Use Cases Before we start The system shall give access to the database to any
Software Specification and Architecture 2IW80 Julien Schmaltz (slides partly from M. Mousavi and A. Serebrenik) Lecture 03: Use Cases Before we start The system shall give access to the database to any
Physics 9e/Cutnell. correlated to the. College Board AP Physics 1 Course Objectives
 Physics 9e/Cutnell correlated to the College Board AP Physics 1 Course Objectives Big Idea 1: Objects and systems have properties such as mass and charge. Systems may have internal structure. Enduring
Physics 9e/Cutnell correlated to the College Board AP Physics 1 Course Objectives Big Idea 1: Objects and systems have properties such as mass and charge. Systems may have internal structure. Enduring
Procedure for obtaining Biometric Device Certification (Authentication)
 Procedure for obtaining Biometric Device Certification (Authentication) (BDCS(A)-03-02) ISSUE 1 STQC - IT Services STQC Directorate, Department of Information Technology, Ministry of Communications & Information
Procedure for obtaining Biometric Device Certification (Authentication) (BDCS(A)-03-02) ISSUE 1 STQC - IT Services STQC Directorate, Department of Information Technology, Ministry of Communications & Information
Media Cloud Service with Optimized Video Processing and Platform
 Media Cloud Service with Optimized Video Processing and Platform Kenichi Ota Hiroaki Kubota Tomonori Gotoh Recently, video traffic on the Internet has been increasing dramatically as video services including
Media Cloud Service with Optimized Video Processing and Platform Kenichi Ota Hiroaki Kubota Tomonori Gotoh Recently, video traffic on the Internet has been increasing dramatically as video services including
Express Introductory Training in ANSYS Fluent Lecture 1 Introduction to the CFD Methodology
 Express Introductory Training in ANSYS Fluent Lecture 1 Introduction to the CFD Methodology Dimitrios Sofialidis Technical Manager, SimTec Ltd. Mechanical Engineer, PhD PRACE Autumn School 2013 - Industry
Express Introductory Training in ANSYS Fluent Lecture 1 Introduction to the CFD Methodology Dimitrios Sofialidis Technical Manager, SimTec Ltd. Mechanical Engineer, PhD PRACE Autumn School 2013 - Industry
Unit I. Introduction
 Unit I Introduction Product Life Cycles Products also have life cycles The Systems Development Life Cycle (SDLC) is a framework for describing the phases involved in developing and maintaining information
Unit I Introduction Product Life Cycles Products also have life cycles The Systems Development Life Cycle (SDLC) is a framework for describing the phases involved in developing and maintaining information
Automatic Analysis of Browser-based Security Protocols
 Automatic Analysis of Browser-based Security Protocols Avinash Sudhodanan Alessandro Armando (FBK, coordinator) Roberto Carbone (FBK, tutor) Luca Compagna (SAP, tutor) FP7-PEOPLE-2012-ITN Outline Context
Automatic Analysis of Browser-based Security Protocols Avinash Sudhodanan Alessandro Armando (FBK, coordinator) Roberto Carbone (FBK, tutor) Luca Compagna (SAP, tutor) FP7-PEOPLE-2012-ITN Outline Context
A Study of Immersive Game Contents System Design and Modeling for Virtual Reality Technology
 , pp.411-418 http://dx.doi.org/10.14257/ijca.2014.7.10.38 A Study of Immersive Game Contents System Design and Modeling for Virtual Reality Technology Jung-Yoon Kim 1 and SangHun Nam 2 1 Graduate School
, pp.411-418 http://dx.doi.org/10.14257/ijca.2014.7.10.38 A Study of Immersive Game Contents System Design and Modeling for Virtual Reality Technology Jung-Yoon Kim 1 and SangHun Nam 2 1 Graduate School
The Scientific Data Mining Process
 Chapter 4 The Scientific Data Mining Process When I use a word, Humpty Dumpty said, in rather a scornful tone, it means just what I choose it to mean neither more nor less. Lewis Carroll [87, p. 214] In
Chapter 4 The Scientific Data Mining Process When I use a word, Humpty Dumpty said, in rather a scornful tone, it means just what I choose it to mean neither more nor less. Lewis Carroll [87, p. 214] In
Biometric Authentication using Online Signature
 University of Trento Department of Mathematics Outline Introduction An example of authentication scheme Performance analysis and possible improvements Outline Introduction An example of authentication
University of Trento Department of Mathematics Outline Introduction An example of authentication scheme Performance analysis and possible improvements Outline Introduction An example of authentication
EAP/GWL Rev. 1/2011 Page 1 of 5. Factoring a polynomial is the process of writing it as the product of two or more polynomial factors.
 EAP/GWL Rev. 1/2011 Page 1 of 5 Factoring a polynomial is the process of writing it as the product of two or more polynomial factors. Example: Set the factors of a polynomial equation (as opposed to an
EAP/GWL Rev. 1/2011 Page 1 of 5 Factoring a polynomial is the process of writing it as the product of two or more polynomial factors. Example: Set the factors of a polynomial equation (as opposed to an
Newton s Laws of Motion Project
 Newton s Laws of Motion Project Sir Isaac Newton lived during the 1s. Like all scientists, he made observations about the world around him. Some of his observations were about motion. His observations
Newton s Laws of Motion Project Sir Isaac Newton lived during the 1s. Like all scientists, he made observations about the world around him. Some of his observations were about motion. His observations
Region of Interest Access with Three-Dimensional SBHP Algorithm CIPR Technical Report TR-2006-1
 Region of Interest Access with Three-Dimensional SBHP Algorithm CIPR Technical Report TR-2006-1 Ying Liu and William A. Pearlman January 2006 Center for Image Processing Research Rensselaer Polytechnic
Region of Interest Access with Three-Dimensional SBHP Algorithm CIPR Technical Report TR-2006-1 Ying Liu and William A. Pearlman January 2006 Center for Image Processing Research Rensselaer Polytechnic
ELEC 3908, Physical Electronics, Lecture 15. BJT Structure and Fabrication
 ELEC 3908, Physical Electronics, Lecture 15 Lecture Outline Now move on to bipolar junction transistor (BJT) Strategy for next few lectures similar to diode: structure and processing, basic operation,
ELEC 3908, Physical Electronics, Lecture 15 Lecture Outline Now move on to bipolar junction transistor (BJT) Strategy for next few lectures similar to diode: structure and processing, basic operation,
Prospectus for the Essential Physics package.
 Prospectus for the Essential Physics package. Essential Physics is a new textbook and learning package aimed at the College Physics audience, covering the standard introductory physics topics without using
Prospectus for the Essential Physics package. Essential Physics is a new textbook and learning package aimed at the College Physics audience, covering the standard introductory physics topics without using
Evaluation & Validation: Credibility: Evaluating what has been learned
 Evaluation & Validation: Credibility: Evaluating what has been learned How predictive is a learned model? How can we evaluate a model Test the model Statistical tests Considerations in evaluating a Model
Evaluation & Validation: Credibility: Evaluating what has been learned How predictive is a learned model? How can we evaluate a model Test the model Statistical tests Considerations in evaluating a Model
Reviewed by Ok s a n a Afitska, University of Bristol
 Vol. 3, No. 2 (December2009), pp. 226-235 http://nflrc.hawaii.edu/ldc/ http://hdl.handle.net/10125/4441 Transana 2.30 from Wisconsin Center for Education Research Reviewed by Ok s a n a Afitska, University
Vol. 3, No. 2 (December2009), pp. 226-235 http://nflrc.hawaii.edu/ldc/ http://hdl.handle.net/10125/4441 Transana 2.30 from Wisconsin Center for Education Research Reviewed by Ok s a n a Afitska, University
Assessment Report Sample Candidate
 Assessment Report Sample Candidate Abstract Reasoning Aptitude-Rx Generated on: 27-Mar-2015 Page 2 2016 Willis Towers Watson. All rights reserved. Contents Introduction to Assessment Report...3 Total Score...4
Assessment Report Sample Candidate Abstract Reasoning Aptitude-Rx Generated on: 27-Mar-2015 Page 2 2016 Willis Towers Watson. All rights reserved. Contents Introduction to Assessment Report...3 Total Score...4
OFFICIAL SECURITY CHARACTERISTIC MOBILE DEVICE MANAGEMENT
 SECURITY CHARACTERISTIC MOBILE DEVICE MANAGEMENT Version 1.3 Crown Copyright 2015 All Rights Reserved 49358431 Page 1 of 12 About this document This document describes the features, testing and deployment
SECURITY CHARACTERISTIC MOBILE DEVICE MANAGEMENT Version 1.3 Crown Copyright 2015 All Rights Reserved 49358431 Page 1 of 12 About this document This document describes the features, testing and deployment
Search and Information Retrieval
 Search and Information Retrieval Search on the Web 1 is a daily activity for many people throughout the world Search and communication are most popular uses of the computer Applications involving search
Search and Information Retrieval Search on the Web 1 is a daily activity for many people throughout the world Search and communication are most popular uses of the computer Applications involving search
Technology in Music Therapy and Special Education. What is Special Education?
 Technology in Music Therapy and Special Education What is Special Education? Disabilities are categorized into the following areas: o Autism, visual impairment, hearing impairment, deaf- blindness, multiple
Technology in Music Therapy and Special Education What is Special Education? Disabilities are categorized into the following areas: o Autism, visual impairment, hearing impairment, deaf- blindness, multiple
Umbrella: A New Component-Based Software Development Model
 2009 International Conference on Computer Engineering and Applications IPCSIT vol.2 (2011) (2011) IACSIT Press, Singapore Umbrella: A New Component-Based Software Development Model Anurag Dixit and P.C.
2009 International Conference on Computer Engineering and Applications IPCSIT vol.2 (2011) (2011) IACSIT Press, Singapore Umbrella: A New Component-Based Software Development Model Anurag Dixit and P.C.
18-731 Midterm. Name: Andrew user id:
 18-731 Midterm 6 March 2008 Name: Andrew user id: Scores: Problem 0 (10 points): Problem 1 (10 points): Problem 2 (15 points): Problem 3 (10 points): Problem 4 (20 points): Problem 5 (10 points): Problem
18-731 Midterm 6 March 2008 Name: Andrew user id: Scores: Problem 0 (10 points): Problem 1 (10 points): Problem 2 (15 points): Problem 3 (10 points): Problem 4 (20 points): Problem 5 (10 points): Problem
Web Application Testing. Web Performance Testing
 Web Application Testing Web Performance Testing Objectives of Performance Testing Evaluate runtime compliance to performance requirements Check different properties such as throughput (bits/sec, packets/sec)
Web Application Testing Web Performance Testing Objectives of Performance Testing Evaluate runtime compliance to performance requirements Check different properties such as throughput (bits/sec, packets/sec)
COMP 150-04 Visualization. Lecture 11 Interacting with Visualizations
 COMP 150-04 Visualization Lecture 11 Interacting with Visualizations Assignment 5: Maps Due Wednesday, March 17th Design a thematic map visualization Option 1: Choropleth Map Implementation in Processing
COMP 150-04 Visualization Lecture 11 Interacting with Visualizations Assignment 5: Maps Due Wednesday, March 17th Design a thematic map visualization Option 1: Choropleth Map Implementation in Processing
Journal of Industrial Engineering Research. Adaptive sequence of Key Pose Detection for Human Action Recognition
 IWNEST PUBLISHER Journal of Industrial Engineering Research (ISSN: 2077-4559) Journal home page: http://www.iwnest.com/aace/ Adaptive sequence of Key Pose Detection for Human Action Recognition 1 T. Sindhu
IWNEST PUBLISHER Journal of Industrial Engineering Research (ISSN: 2077-4559) Journal home page: http://www.iwnest.com/aace/ Adaptive sequence of Key Pose Detection for Human Action Recognition 1 T. Sindhu
is in plane V. However, it may be more convenient to introduce a plane coordinate system in V.
 .4 COORDINATES EXAMPLE Let V be the plane in R with equation x +2x 2 +x 0, a two-dimensional subspace of R. We can describe a vector in this plane by its spatial (D)coordinates; for example, vector x 5
.4 COORDINATES EXAMPLE Let V be the plane in R with equation x +2x 2 +x 0, a two-dimensional subspace of R. We can describe a vector in this plane by its spatial (D)coordinates; for example, vector x 5
APPLICATION OF DATA MINING TECHNIQUES FOR BUILDING SIMULATION PERFORMANCE PREDICTION ANALYSIS. email [email protected]
 Eighth International IBPSA Conference Eindhoven, Netherlands August -4, 2003 APPLICATION OF DATA MINING TECHNIQUES FOR BUILDING SIMULATION PERFORMANCE PREDICTION Christoph Morbitzer, Paul Strachan 2 and
Eighth International IBPSA Conference Eindhoven, Netherlands August -4, 2003 APPLICATION OF DATA MINING TECHNIQUES FOR BUILDING SIMULATION PERFORMANCE PREDICTION Christoph Morbitzer, Paul Strachan 2 and
e-gateway SOLUTION OVERVIEW Financials HCM ERP e-gateway Web Applications Mobile Devices SharePoint Portal
 e-gateway SOLUTION OVERVIEW In an effort to manage mission critical information better, perform their daily tasks more efficiently, share information to key stakeholders more effectively, and ensure that
e-gateway SOLUTION OVERVIEW In an effort to manage mission critical information better, perform their daily tasks more efficiently, share information to key stakeholders more effectively, and ensure that
Management Information System Prof. B. Mahanty Department of Industrial Engineering & Management Indian Institute of Technology, Kharagpur
 (Refer Slide Time: 00:54) Management Information System Prof. B. Mahanty Department of Industrial Engineering & Management Indian Institute of Technology, Kharagpur Lecture - 18 Data Flow Diagrams - III
(Refer Slide Time: 00:54) Management Information System Prof. B. Mahanty Department of Industrial Engineering & Management Indian Institute of Technology, Kharagpur Lecture - 18 Data Flow Diagrams - III
The Sun: Our nearest star
 The Sun: Our nearest star Property Surface T Central T Luminosity Mass Lifetime (ms) Value 5500K 15x10 6 K 2 x 10 33 ergs 4 x 10 33 grams 10 billion years Solar Structure Build a model and find the central
The Sun: Our nearest star Property Surface T Central T Luminosity Mass Lifetime (ms) Value 5500K 15x10 6 K 2 x 10 33 ergs 4 x 10 33 grams 10 billion years Solar Structure Build a model and find the central
Factors and Products
 CHAPTER 3 Factors and Products What You ll Learn use different strategies to find factors and multiples of whole numbers identify prime factors and write the prime factorization of a number find square
CHAPTER 3 Factors and Products What You ll Learn use different strategies to find factors and multiples of whole numbers identify prime factors and write the prime factorization of a number find square
Factorising quadratics
 Factorising quadratics An essential skill in many applications is the ability to factorise quadratic expressions. In this unit you will see that this can be thought of as reversing the process used to
Factorising quadratics An essential skill in many applications is the ability to factorise quadratic expressions. In this unit you will see that this can be thought of as reversing the process used to
1000-Grid Banner Set. This Really Good Stuff product includes: 1000-Grid Banner Set This Really Good Stuff Activity Guide
 1000-Grid Banner Set This Really Good Stuff product includes: 1000-Grid Banner Set This Really Good Stuff Activity Guide Congratulations on your purchase of this Really Good Stuff 1000-Grid Banner Set
1000-Grid Banner Set This Really Good Stuff product includes: 1000-Grid Banner Set This Really Good Stuff Activity Guide Congratulations on your purchase of this Really Good Stuff 1000-Grid Banner Set
NEW CHALLENGES IN COLLABORATIVE VIRTUAL FACTORY DESIGN
 02 NEW CHALLENGES IN COLLABORATIVE VIRTUAL FACTORY DESIGN Stefano Mottura, Giampaolo Viganò, Luca Greci, Marco Sacco Emanuele Carpanzano Institute of Industrial Technologies and Automation National Research
02 NEW CHALLENGES IN COLLABORATIVE VIRTUAL FACTORY DESIGN Stefano Mottura, Giampaolo Viganò, Luca Greci, Marco Sacco Emanuele Carpanzano Institute of Industrial Technologies and Automation National Research
from Larson Text By Susan Miertschin
 Decision Tree Data Mining Example from Larson Text By Susan Miertschin 1 Problem The Maximum Miniatures Marketing Department wants to do a targeted mailing gpromoting the Mythic World line of figurines.
Decision Tree Data Mining Example from Larson Text By Susan Miertschin 1 Problem The Maximum Miniatures Marketing Department wants to do a targeted mailing gpromoting the Mythic World line of figurines.
(Refer Slide Time: 02:17)
 Internet Technology Prof. Indranil Sengupta Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture No #06 IP Subnetting and Addressing (Not audible: (00:46)) Now,
Internet Technology Prof. Indranil Sengupta Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture No #06 IP Subnetting and Addressing (Not audible: (00:46)) Now,
