A brief history of Unicode
|
|
|
- Eric Weaver
- 9 years ago
- Views:
Transcription
1 A brief history of Unicode happens Alex Copyright (c) 2016, Alex Blewitt
2 What is Unicode? Unicode is an industry standard for representing text Defines a number of code points that map to characters Not all characters are visible (control characters) Not all characters are standalone (accents) Not all code points refer to characters (some are undefined) Does include all major ideographs from a variety of languages U+0041 == A, U+20AC == Pop quiz: what size are Unicode code points? 8-bit 16-bit 32-bit
3 Unicode: a 21-bit code point All characters in Unicode are logically 21-bits wide Not a great format for encoding data in computers! How did we end up with a 21-bit character set? To explain that, we have to look backwards in time Before Unicode Many variations of character sets with different meanings Single-byte ISO (CP-1252), ISO , ISO ASCII, EBCDIC Multi-byte ISO-2202-CN, ISO-2202-JP, ISO-2202-KR (CJK)
4 What does all of this mean? Character sets and code pages assigned meanings 0x41 = A 0xD0 =? ISO = Ð ISO = <missing> ISO = Ğ EBCDIC = } All based on ASCII (well, except EBCDIC ) Pop quiz: what size are ASCII code points? 8-bit 16-bit 32-bit
5 ASCII is a 7-bit code point Who needs power-of-two? American Standard Code for Information Interchange Defined to harmonise existing incompatible encodings ASCII was the Unicode of the telegraph era First 128 characters of ASCII are same as Unicode ISO (aka Latin-1) CP1252 (Windows) Where did ASCII come from?
6 ASCII Upper Lower Numbers Control Punctuation
7 ASCII control characters Many are now obsolete but stem from telegraph days XML disallows control characters other than CR, LF, HT Some were used for printer control mechanisms HT/VT horizontal or vertical tab (^I/^K) LF/FF line feed/form feed (^J/^L) CR carriage return (^M) Some are used for notification BEL ring the bell (^G is beep in Unix terminals) Some were used for notification ACK/NAK/STX/ETX/SYN ESC/NUL
8 Telegraphs and teletypes Telegraphs revolutionised communication Characters sent as an electric encoding of bits Various encoding supported characters Needed standardisation Teletype printers would print out punched paper tapes Paper tapes could be optically read /dev/tty in Unix stands for teletype /dev/ttys1 stands for teletype on serial port 1 Punched cards and tapes were common
9 Colossus computer Used to crack codes from the Lorenz telegraph with paper tape
10 Baudot, Murray and ITA2 Baudot created first fixed length 5-bit encoding Also gave name to baud as symbols-per-second (not bits) Became known as ITA1 Created ~ 1870 Murray encoding created ~ 1900 Modified patterns to minimise wear on punches Defined NUL as 0, introduced CR and LF, Backspace Evolved to ITA2 ~ 1930
11 Baudot, Murray and ITA2 Baudot created first fixed length 5-bit encoding Also gave name to baud as symbols-per-second (not bits) Became known as ITA1 Created ~ 1870 Sprocket drive holes Murray encoding created ~ 1900 Modified patterns to minimise wear on punches Defined NUL as 0, introduced CR and LF, Backspace Evolved to ITA2 ~
12 Shifting in Baudot code The astute of you will notice 5 bits isn t enough 26 letters + 10 digits > 2^5 (32) This was solved with the idea of a shift Based on idea of typewriters Meant that decoding was based on state Letter mode Hello World Figures mode 3))9 294)
13 Morse Code Morse code is a variable length encoding Dots or dashes to represent characters Initial encoding for radio with human operators Invented in ~1840 Practical for humans to hear and decode / send H e l l o W o r l d
14 Punched Cards Punched tape itself was an evolution of cards Each card represented a line, each column a letter Created by Herman Hollerith (IBM founder)
15 Punched Cards Punched tape itself was an evolution of cards Each card represented a line, each column a letter Created by Herman Hollerith (IBM founder)
16 When were punched cards used? When were punched cards first used? Jaquard Loom US Census 1890
17 Punched cards legacy Legacy of punched cards still with us Cards were 80 columns wide Led to early terminals having an 80 col display Some IDEs and text editors have a wrap at 80 8 characters were often used for numbering Fortran ignored characters in columns Some text editors will wrap /warn after column 72 Git commit messages should be wrapped at 72
18 Punched cards and line numbers Dropping a stack of cards was an expensive operation Radix sort of columns can be used to fix Or just put a diagonal line through them
19 0-9 in BCD is EBCDIC EBCDIC is the Extended BCD Interchange Code BCD is Binary Coded Decimal, e.g. 0x12 is 12 decimal
20 EBCDIC 0-9 in BCD is
21 EBCDIC challenges Not all was well with the EBCDIC character set Rarely used outside of IBM mainframes Different sort ordering to ASCII ASCII has 0-9, A-Z, a-z EBCDIC has a-z, A-Z, 0-9 (and not contiguous; a - z!= 25) Created around same time (1963) IBM s mainframes had peripherals using punched cards Easier to translate punched cards into EBCDIC Mainframes could be switched into ASCII but programs failed Shares similar control characters to ASCII Form Feed, Tab, Escape
22 Putting history together Telegraph Morse Code (1840) Baudot Code (1870) Murray/ITA2 (1900) Automation Jacquard Loom (1800) Hollerith Card (1890) Computing Fortran (1960) ASCII (1963) EBCDIC (1963) ISO-8859-* (1985) Unicode 1.0 (1991) 16 bit Unicode 2.0 (1996) 21bit
23 Why a 21 bit code, though? Unicode 1.x was a 16-bit code Not enough to store everything Needed to have additional planes Plane 0: Basic Multilingual Plane was most of 1.x Plane 1: Supplemental Multilingual Plane added Emoji Egyptian Hieroglyphs Graphics characters such as dominoes and playing cards Plane : Supplementary planes of various types
24 Still doesn t explain 21 bit To represent additional planes requires encoding Two main Unicode encodings are widely used UTF-8 UTF-16 (formerly UCS-2) Unicode Transformation Format says how to encode point Logical code point for is U+20AC May be written out in different ways 0x20 0xAC 0xAC 0x20 UTF-16 uses 2 octets (16-bits) to represent content UTF-8 uses octets (bytes/8-bit) to represent content
25 UTF-16 UTF-16 uses two octets to represent content Can be big endian or little endian 0x20 0xAC is big endian 0xAC 0x20 is little endian Byte Order Mark (BOM 0xFE 0xFF) often written out at front 0xFE 0xFF big endian UTF-16 BOM þÿ in ISO xFF 0xFE little endian UTF-16 BOM ÿþ in ISO Still only 16 bit how are planes represented? Surrogate pairs allow encoding 20 bits worth of data in 4 octets High surrogate pair (10 bits) Low surrogate pair (10 bits)
26 But != 21 No, but there s no need to use them for plane 0 (BMP) So, take away 1 and you have planes which is 4 bits 4 bits + 16 bits (65536 in each plane) = 20 bits Consider 7 o clock symbol U+1F556 (The leading 1 indicates it is in plane 1) Plane 1 is encoded as 0000 F5 is is UTF-16 for U+1F556 is == 0xD83D == 0xDD5A
27 UTF-8 stores 21 bits in 4 octets UTF-8 is a variable length encoding ASCII bytes (<= 127, <= U+007F) are encoded as one octet U U+07FF are encoded as two octets U U+FFFF are encoded as three octets U U+1FFFFF are encoded as four octets Single octets Always start with a 0 Multi octets Start with 11 Designed by Ken Thompson and Rob Pike Continuation octet starts with 10
28 UTF-8 examples U+0041 A 0x41 U+1F556 U+1 is ï» is the UTF-8 encoded UTF-16 byte order mark Doesn't make sense Generated by Windows F5 is is Encoded as 4 octets 0xF09F == 0xF == 0x9F == 0x == 0x96 The number of bits in the first part shows number of bytes in code
29 Flags of all nations How are flags represented? #$% Extensible way without adding new data Regional indicator symbols A Z G B # U+1F1EC U+1F1E7 E U $ U+1F1EA U+1F1FA U S % U+1F1FA U+1F1F8 Symbols replaced with flag as standard font ligatures UTF-8: 0xF09F 87BA F09F 87B8 UTF-16: 0xFE FF D83C DDFA D83C DDF8
30 Unicode: a 21-bit code point Expanded from 16 bits with 1.x to 21 bits with 2.x Encodings for UTF-8 provide a way to store 21 bits Can scan through string to count code points Octets starting with 0 or 11 are start of character Octets starting with 10 are continuation characters Self synchronizing Encodings for UTF-16 use surrogate pairs Surrogate pairs can store 20 bits of data Define plane 0 to not use surrogate pairs and this gives 21 Evolving over the last 200 years
31 A brief history of Unicode happens Alex Copyright (c) 2016, Alex Blewitt
ASCII Code. Numerous codes were invented, including Émile Baudot's code (known as Baudot
 ASCII Code Data coding Morse code was the first code used for long-distance communication. Samuel F.B. Morse invented it in 1844. This code is made up of dots and dashes (a sort of binary code). It was
ASCII Code Data coding Morse code was the first code used for long-distance communication. Samuel F.B. Morse invented it in 1844. This code is made up of dots and dashes (a sort of binary code). It was
The use of binary codes to represent characters
 The use of binary codes to represent characters Teacher s Notes Lesson Plan x Length 60 mins Specification Link 2.1.4/hi Character Learning objective (a) Explain the use of binary codes to represent characters
The use of binary codes to represent characters Teacher s Notes Lesson Plan x Length 60 mins Specification Link 2.1.4/hi Character Learning objective (a) Explain the use of binary codes to represent characters
The ASCII Character Set
 The ASCII Character Set The American Standard Code for Information Interchange or ASCII assigns values between 0 and 255 for upper and lower case letters, numeric digits, punctuation marks and other symbols.
The ASCII Character Set The American Standard Code for Information Interchange or ASCII assigns values between 0 and 255 for upper and lower case letters, numeric digits, punctuation marks and other symbols.
The Unicode Standard Version 8.0 Core Specification
 The Unicode Standard Version 8.0 Core Specification To learn about the latest version of the Unicode Standard, see http://www.unicode.org/versions/latest/. Many of the designations used by manufacturers
The Unicode Standard Version 8.0 Core Specification To learn about the latest version of the Unicode Standard, see http://www.unicode.org/versions/latest/. Many of the designations used by manufacturers
URL encoding uses hex code prefixed by %. Quoted Printable encoding uses hex code prefixed by =.
 ASCII = American National Standard Code for Information Interchange ANSI X3.4 1986 (R1997) (PDF), ANSI INCITS 4 1986 (R1997) (Printed Edition) Coded Character Set 7 Bit American National Standard Code
ASCII = American National Standard Code for Information Interchange ANSI X3.4 1986 (R1997) (PDF), ANSI INCITS 4 1986 (R1997) (Printed Edition) Coded Character Set 7 Bit American National Standard Code
Symbols in subject lines. An in-depth look at symbols
 An in-depth look at symbols What is the advantage of using symbols in subject lines? The age of personal emails has changed significantly due to the social media boom, and instead, people are receving
An in-depth look at symbols What is the advantage of using symbols in subject lines? The age of personal emails has changed significantly due to the social media boom, and instead, people are receving
Chapter 4: Computer Codes
 Slide 1/30 Learning Objectives In this chapter you will learn about: Computer data Computer codes: representation of data in binary Most commonly used computer codes Collating sequence 36 Slide 2/30 Data
Slide 1/30 Learning Objectives In this chapter you will learn about: Computer data Computer codes: representation of data in binary Most commonly used computer codes Collating sequence 36 Slide 2/30 Data
BAR CODE 39 ELFRING FONTS INC.
 ELFRING FONTS INC. BAR CODE 39 This package includes 18 versions of a bar code 39 font in scalable TrueType and PostScript formats, a Windows utility, Bar39.exe, that helps you make bar codes, and Visual
ELFRING FONTS INC. BAR CODE 39 This package includes 18 versions of a bar code 39 font in scalable TrueType and PostScript formats, a Windows utility, Bar39.exe, that helps you make bar codes, and Visual
NVT (Network Virtual Terminal) description
 NVT (Network Virtual Terminal) description English version Czech version Communication with the TCP/IP device over the Ethernet network can be extended to more functions using NVT (Network Virtual Terminal)
NVT (Network Virtual Terminal) description English version Czech version Communication with the TCP/IP device over the Ethernet network can be extended to more functions using NVT (Network Virtual Terminal)
DATA COMMUNICATION (Basics of data communication, OSI layers.)
 DATA COMMUNICATION (Basics of data communication, OSI layers.) K.K.DHUPAR SDE (NP-II) ALTTC ALTTC/NP/KKD/Data Communication 1 Data Communications History 1838: Samuel Morse & Alfred Veil Invent Morse Code
DATA COMMUNICATION (Basics of data communication, OSI layers.) K.K.DHUPAR SDE (NP-II) ALTTC ALTTC/NP/KKD/Data Communication 1 Data Communications History 1838: Samuel Morse & Alfred Veil Invent Morse Code
Introduction to Unicode. By: Atif Gulzar Center for Research in Urdu Language Processing
 Introduction to Unicode By: Atif Gulzar Center for Research in Urdu Language Processing Introduction to Unicode Unicode Why Unicode? What is Unicode? Unicode Architecture Why Unicode? Pre-Unicode Standards
Introduction to Unicode By: Atif Gulzar Center for Research in Urdu Language Processing Introduction to Unicode Unicode Why Unicode? What is Unicode? Unicode Architecture Why Unicode? Pre-Unicode Standards
IBM Emulation Mode Printer Commands
 IBM Emulation Mode Printer Commands Section 3 This section provides a detailed description of IBM emulation mode commands you can use with your printer. Control Codes Control codes are one-character printer
IBM Emulation Mode Printer Commands Section 3 This section provides a detailed description of IBM emulation mode commands you can use with your printer. Control Codes Control codes are one-character printer
Encoding Text with a Small Alphabet
 Chapter 2 Encoding Text with a Small Alphabet Given the nature of the Internet, we can break the process of understanding how information is transmitted into two components. First, we have to figure out
Chapter 2 Encoding Text with a Small Alphabet Given the nature of the Internet, we can break the process of understanding how information is transmitted into two components. First, we have to figure out
How to represent characters?
 Copyright Software Carpentry 2010 This work is licensed under the Creative Commons Attribution License See http://software-carpentry.org/license.html for more information. How to represent characters?
Copyright Software Carpentry 2010 This work is licensed under the Creative Commons Attribution License See http://software-carpentry.org/license.html for more information. How to represent characters?
Unicode Security. Software Vulnerability Testing Guide. July 2009 Casaba Security, LLC www.casabasecurity.com
 Unicode Security Software Vulnerability Testing Guide (DRAFT DOCUMENT this document is currently a preview in DRAFT form. Please contact me with corrections or feedback.) Software Globalization provides
Unicode Security Software Vulnerability Testing Guide (DRAFT DOCUMENT this document is currently a preview in DRAFT form. Please contact me with corrections or feedback.) Software Globalization provides
ASCII Characters. 146 CHAPTER 3 Information Representation. The sign bit is 1, so the number is negative. Converting to decimal gives
 146 CHAPTER 3 Information Representation The sign bit is 1, so the number is negative. Converting to decimal gives 37A (hex) = 134 (dec) Notice that the hexadecimal number is not written with a negative
146 CHAPTER 3 Information Representation The sign bit is 1, so the number is negative. Converting to decimal gives 37A (hex) = 134 (dec) Notice that the hexadecimal number is not written with a negative
Number Representation
 Number Representation CS10001: Programming & Data Structures Pallab Dasgupta Professor, Dept. of Computer Sc. & Engg., Indian Institute of Technology Kharagpur Topics to be Discussed How are numeric data
Number Representation CS10001: Programming & Data Structures Pallab Dasgupta Professor, Dept. of Computer Sc. & Engg., Indian Institute of Technology Kharagpur Topics to be Discussed How are numeric data
This is great when speed is important and relatively few words are necessary, but Max would be a terrible language for writing a text editor.
 Dealing With ASCII ASCII, of course, is the numeric representation of letters used in most computers. In ASCII, there is a number for each character in a message. Max does not use ACSII very much. In the
Dealing With ASCII ASCII, of course, is the numeric representation of letters used in most computers. In ASCII, there is a number for each character in a message. Max does not use ACSII very much. In the
Levent EREN [email protected] A-306 Office Phone:488-9882 INTRODUCTION TO DIGITAL LOGIC
 Levent EREN [email protected] A-306 Office Phone:488-9882 1 Number Systems Representation Positive radix, positional number systems A number with radix r is represented by a string of digits: A n
Levent EREN [email protected] A-306 Office Phone:488-9882 1 Number Systems Representation Positive radix, positional number systems A number with radix r is represented by a string of digits: A n
Representação de Caracteres
 Representação de Caracteres IFBA Instituto Federal de Educ. Ciencia e Tec Bahia Curso de Analise e Desenvolvimento de Sistemas Introdução à Ciência da Computação Prof. Msc. Antonio Carlos Souza Coletânea
Representação de Caracteres IFBA Instituto Federal de Educ. Ciencia e Tec Bahia Curso de Analise e Desenvolvimento de Sistemas Introdução à Ciência da Computação Prof. Msc. Antonio Carlos Souza Coletânea
Critical Values for I18n Testing. Tex Texin Chief Globalization Architect XenCraft
 Critical Values for I18n Testing Tex Texin Chief Globalization Architect XenCraft Abstract In this session, we recommend specific data values that are likely to identify internationalization problems in
Critical Values for I18n Testing Tex Texin Chief Globalization Architect XenCraft Abstract In this session, we recommend specific data values that are likely to identify internationalization problems in
Teletypewriter Communication Codes
 Teletypewriter Communication Codes Gil Smith [email protected] 2001 (Document Notes) Abstract Preliminary -- 5/01 gil smith Corrections or comments to [email protected] This information is
Teletypewriter Communication Codes Gil Smith [email protected] 2001 (Document Notes) Abstract Preliminary -- 5/01 gil smith Corrections or comments to [email protected] This information is
Model: LD1000 Series. USB Interface Customer Displays. 2 by 20 character display USER MANUAL. Rev 1.0
 Model: LD1000 Series USB Interface Customer Displays 2 by 20 character display USER MANUAL Rev 1.0 i NOTICE The manufacturer of the POS pole display makes no representations or warranties, either expressed
Model: LD1000 Series USB Interface Customer Displays 2 by 20 character display USER MANUAL Rev 1.0 i NOTICE The manufacturer of the POS pole display makes no representations or warranties, either expressed
Frequently Asked Questions on character sets and languages in MT and MX free format fields
 Frequently Asked Questions on character sets and languages in MT and MX free format fields Version Final 17 January 2008 Preface The Frequently Asked Questions (FAQs) on character sets and languages that
Frequently Asked Questions on character sets and languages in MT and MX free format fields Version Final 17 January 2008 Preface The Frequently Asked Questions (FAQs) on character sets and languages that
ELFRING FONTS UPC BAR CODES
 ELFRING FONTS UPC BAR CODES This package includes five UPC-A and five UPC-E bar code fonts in both TrueType and PostScript formats, a Windows utility, BarUPC, which helps you make bar codes, and Visual
ELFRING FONTS UPC BAR CODES This package includes five UPC-A and five UPC-E bar code fonts in both TrueType and PostScript formats, a Windows utility, BarUPC, which helps you make bar codes, and Visual
Count the Dots Binary Numbers
 Activity 1 Count the Dots Binary Numbers Summary Data in computers is stored and transmitted as a series of zeros and ones. How can we represent words and numbers using just these two symbols? Curriculum
Activity 1 Count the Dots Binary Numbers Summary Data in computers is stored and transmitted as a series of zeros and ones. How can we represent words and numbers using just these two symbols? Curriculum
Command Emulator STAR Line Mode Command Specifications
 Line Thermal Printer Command Emulator STAR Line Mode Command Specifications Revision 0.01 Star Micronics Co., Ltd. Special Products Division Table of Contents 1. Command Emulator 2 1-1) Command List 2
Line Thermal Printer Command Emulator STAR Line Mode Command Specifications Revision 0.01 Star Micronics Co., Ltd. Special Products Division Table of Contents 1. Command Emulator 2 1-1) Command List 2
Numeral Systems. The number twenty-five can be represented in many ways: Decimal system (base 10): 25 Roman numerals:
 Numeral Systems Which number is larger? 25 8 We need to distinguish between numbers and the symbols that represent them, called numerals. The number 25 is larger than 8, but the numeral 8 above is larger
Numeral Systems Which number is larger? 25 8 We need to distinguish between numbers and the symbols that represent them, called numerals. The number 25 is larger than 8, but the numeral 8 above is larger
Preservation Handbook
 Preservation Handbook Plain text Author Version 2 Date 17.08.05 Change History Martin Wynne and Stuart Yeates Written by MW 2004. Revised by SY May 2005. Revised by MW August 2005. Page 1 of 7 File: presplaintext_d2.doc
Preservation Handbook Plain text Author Version 2 Date 17.08.05 Change History Martin Wynne and Stuart Yeates Written by MW 2004. Revised by SY May 2005. Revised by MW August 2005. Page 1 of 7 File: presplaintext_d2.doc
plc numbers - 13.1 Encoded values; BCD and ASCII Error detection; parity, gray code and checksums
 plc numbers - 3. Topics: Number bases; binary, octal, decimal, hexadecimal Binary calculations; s compliments, addition, subtraction and Boolean operations Encoded values; BCD and ASCII Error detection;
plc numbers - 3. Topics: Number bases; binary, octal, decimal, hexadecimal Binary calculations; s compliments, addition, subtraction and Boolean operations Encoded values; BCD and ASCII Error detection;
Character Code Structure and Extension Techniques
 Standard ECMA-35 6th Edition - December 1994 Standardizing Information and Communication Systems Character Code Structure and Extension Techniques Phone: +41 22 849.60.00 - Fax: +41 22 849.60.01 - X.400:
Standard ECMA-35 6th Edition - December 1994 Standardizing Information and Communication Systems Character Code Structure and Extension Techniques Phone: +41 22 849.60.00 - Fax: +41 22 849.60.01 - X.400:
7-Bit coded Character Set
 Standard ECMA-6 6 th Edition - December 1991 Reprinted in electronic form in August 1997 Standardizing Information and Communication Systems 7-Bit coded Character Set Phone: +41 22 849.60.00 - Fax: +41
Standard ECMA-6 6 th Edition - December 1991 Reprinted in electronic form in August 1997 Standardizing Information and Communication Systems 7-Bit coded Character Set Phone: +41 22 849.60.00 - Fax: +41
Memory is implemented as an array of electronic switches
 Memory Structure Memory is implemented as an array of electronic switches Each switch can be in one of two states 0 or 1, on or off, true or false, purple or gold, sitting or standing BInary digits (bits)
Memory Structure Memory is implemented as an array of electronic switches Each switch can be in one of two states 0 or 1, on or off, true or false, purple or gold, sitting or standing BInary digits (bits)
San José, February 16, 2001
 San José, February 16, 2001 Feel free to distribute this text (version 1.4) including the author s e-mail address (mailto:[email protected]) and to contact him for corrections and additions. Please do not
San José, February 16, 2001 Feel free to distribute this text (version 1.4) including the author s e-mail address (mailto:[email protected]) and to contact him for corrections and additions. Please do not
Japanese Character Printers EPL2 Programming Manual Addendum
 Japanese Character Printers EPL2 Programming Manual Addendum This addendum contains information unique to Zebra Technologies Japanese character bar code printers. The Japanese configuration printers support
Japanese Character Printers EPL2 Programming Manual Addendum This addendum contains information unique to Zebra Technologies Japanese character bar code printers. The Japanese configuration printers support
Parallax Serial LCD 2 rows x 16 characters Non-backlit (#27976) 2 rows x 16 characters Backlit (#27977) 4 rows x 20 characters Backlit (#27979)
 599 Menlo Drive, Suite 100 Rocklin, California 95765, USA Office: (916) 624-8333 Fax: (916) 624-8003 General: [email protected] Technical: [email protected] Web Site: www.parallax.com Educational: www.stampsinclass.com
599 Menlo Drive, Suite 100 Rocklin, California 95765, USA Office: (916) 624-8333 Fax: (916) 624-8003 General: [email protected] Technical: [email protected] Web Site: www.parallax.com Educational: www.stampsinclass.com
Ecma/TC39/2013/NN. 4 th Draft ECMA-XXX. 1 st Edition / July 2013. The JSON Data Interchange Format. Reference number ECMA-123:2009
 Ecma/TC39/2013/NN 4 th Draft ECMA-XXX 1 st Edition / July 2013 The JSON Data Interchange Format Reference number ECMA-123:2009 Ecma International 2009 COPYRIGHT PROTECTED DOCUMENT Ecma International 2013
Ecma/TC39/2013/NN 4 th Draft ECMA-XXX 1 st Edition / July 2013 The JSON Data Interchange Format Reference number ECMA-123:2009 Ecma International 2009 COPYRIGHT PROTECTED DOCUMENT Ecma International 2013
Technical Reference DYMO LabelWriter SE450 Label Printer
 Technical Reference DYMO LabelWriter SE450 Label Printer Copyright 2010 Sanford, L.P. All rights reserved. Revised 7/26/2010. No part of this document or the software may be reproduced or transmitted in
Technical Reference DYMO LabelWriter SE450 Label Printer Copyright 2010 Sanford, L.P. All rights reserved. Revised 7/26/2010. No part of this document or the software may be reproduced or transmitted in
Windows Driver Manual Metapace T-4 Thermal Printer Rev. 1.00
 Manual Metapace T-4 Thermal Printer Rev. 1.00 http://www.metapace.com Table of Contents 1. Manual Information... 3 2. Operating System (OS) Environment... 3 3. Windows Driver Preparation... 3 4. Windows
Manual Metapace T-4 Thermal Printer Rev. 1.00 http://www.metapace.com Table of Contents 1. Manual Information... 3 2. Operating System (OS) Environment... 3 3. Windows Driver Preparation... 3 4. Windows
The programming language C. sws1 1
 The programming language C sws1 1 The programming language C invented by Dennis Ritchie in early 1970s who used it to write the first Hello World program C was used to write UNIX Standardised as K&C (Kernighan
The programming language C sws1 1 The programming language C invented by Dennis Ritchie in early 1970s who used it to write the first Hello World program C was used to write UNIX Standardised as K&C (Kernighan
Chapter 1. Introduction and Historical Background of Computer Networks. 1.1 Scope of Computer Networks
 Chapter 1 Introduction and Historical Background of Computer Networks 1.1 Scope of Computer Networks Perhaps the most significant change in computer science over the past twenty years has been the enormous
Chapter 1 Introduction and Historical Background of Computer Networks 1.1 Scope of Computer Networks Perhaps the most significant change in computer science over the past twenty years has been the enormous
Voyager 9520/40 Voyager GS9590 Eclipse 5145
 Voyager 9520/40 Voyager GS9590 Eclipse 5145 Quick Start Guide Aller à www.honeywellaidc.com pour le français. Vai a www.honeywellaidc.com per l'italiano. Gehe zu www.honeywellaidc.com für Deutsch. Ir a
Voyager 9520/40 Voyager GS9590 Eclipse 5145 Quick Start Guide Aller à www.honeywellaidc.com pour le français. Vai a www.honeywellaidc.com per l'italiano. Gehe zu www.honeywellaidc.com für Deutsch. Ir a
The Answer to the 14 Most Frequently Asked Modbus Questions
 Modbus Frequently Asked Questions WP-34-REV0-0609-1/7 The Answer to the 14 Most Frequently Asked Modbus Questions Exactly what is Modbus? Modbus is an open serial communications protocol widely used in
Modbus Frequently Asked Questions WP-34-REV0-0609-1/7 The Answer to the 14 Most Frequently Asked Modbus Questions Exactly what is Modbus? Modbus is an open serial communications protocol widely used in
Binary Representation
 Binary Representation The basis of all digital data is binary representation. Binary - means two 1, 0 True, False Hot, Cold On, Off We must tbe able to handle more than just values for real world problems
Binary Representation The basis of all digital data is binary representation. Binary - means two 1, 0 True, False Hot, Cold On, Off We must tbe able to handle more than just values for real world problems
2- Electronic Mail (SMTP), File Transfer (FTP), & Remote Logging (TELNET)
 2- Electronic Mail (SMTP), File Transfer (FTP), & Remote Logging (TELNET) There are three popular applications for exchanging information. Electronic mail exchanges information between people and file
2- Electronic Mail (SMTP), File Transfer (FTP), & Remote Logging (TELNET) There are three popular applications for exchanging information. Electronic mail exchanges information between people and file
2011, The McGraw-Hill Companies, Inc. Chapter 3
 Chapter 3 3.1 Decimal System The radix or base of a number system determines the total number of different symbols or digits used by that system. The decimal system has a base of 10 with the digits 0 through
Chapter 3 3.1 Decimal System The radix or base of a number system determines the total number of different symbols or digits used by that system. The decimal system has a base of 10 with the digits 0 through
Bachelors of Computer Application Programming Principle & Algorithm (BCA-S102T)
 Unit- I Introduction to c Language: C is a general-purpose computer programming language developed between 1969 and 1973 by Dennis Ritchie at the Bell Telephone Laboratories for use with the Unix operating
Unit- I Introduction to c Language: C is a general-purpose computer programming language developed between 1969 and 1973 by Dennis Ritchie at the Bell Telephone Laboratories for use with the Unix operating
Digital System Design Prof. D Roychoudhry Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur
 Digital System Design Prof. D Roychoudhry Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture - 04 Digital Logic II May, I before starting the today s lecture
Digital System Design Prof. D Roychoudhry Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture - 04 Digital Logic II May, I before starting the today s lecture
BLUETOOTH SERIAL PORT PROFILE. iwrap APPLICATION NOTE
 BLUETOOTH SERIAL PORT PROFILE iwrap APPLICATION NOTE Thursday, 19 April 2012 Version 1.2 Copyright 2000-2012 Bluegiga Technologies All rights reserved. Bluegiga Technologies assumes no responsibility for
BLUETOOTH SERIAL PORT PROFILE iwrap APPLICATION NOTE Thursday, 19 April 2012 Version 1.2 Copyright 2000-2012 Bluegiga Technologies All rights reserved. Bluegiga Technologies assumes no responsibility for
Software Developer's Manual
 Software Developer's Manual ESC/P Command Reference QL-720NW Version 1.0 The Brother logo is a registered trademark of Brother Industries, Ltd. Brother is a registered trademark of Brother Industries,
Software Developer's Manual ESC/P Command Reference QL-720NW Version 1.0 The Brother logo is a registered trademark of Brother Industries, Ltd. Brother is a registered trademark of Brother Industries,
SMPP protocol analysis using Wireshark (SMS)
 SMPP protocol analysis using Wireshark (SMS) Document Purpose Help analyzing SMPP traffic using Wireshark. Give hints about common caveats and oddities of the SMPP protocol and its implementations. Most
SMPP protocol analysis using Wireshark (SMS) Document Purpose Help analyzing SMPP traffic using Wireshark. Give hints about common caveats and oddities of the SMPP protocol and its implementations. Most
2. What is the maximum value of each octet in an IP address? A. 128 B. 255 C. 256 D. None of the above
 1. How many bits are in an IP address? A. 16 B. 32 C. 64 2. What is the maximum value of each octet in an IP address? A. 128 B. 255 C. 256 3. The network number plays what part in an IP address? A. It
1. How many bits are in an IP address? A. 16 B. 32 C. 64 2. What is the maximum value of each octet in an IP address? A. 128 B. 255 C. 256 3. The network number plays what part in an IP address? A. It
Embedded Special Characters Kiran Karidi, Mahipal Vanam, and Sridhar Dodlapati
 PharmaSUG2010 - Paper CC19 Embedded Special Characters Kiran Karidi, Mahipal Vanam, and Sridhar Dodlapati ABSTRACT When the report generated from the clinical trial data requires to show lot of information
PharmaSUG2010 - Paper CC19 Embedded Special Characters Kiran Karidi, Mahipal Vanam, and Sridhar Dodlapati ABSTRACT When the report generated from the clinical trial data requires to show lot of information
Lexical Analysis and Scanning. Honors Compilers Feb 5 th 2001 Robert Dewar
 Lexical Analysis and Scanning Honors Compilers Feb 5 th 2001 Robert Dewar The Input Read string input Might be sequence of characters (Unix) Might be sequence of lines (VMS) Character set ASCII ISO Latin-1
Lexical Analysis and Scanning Honors Compilers Feb 5 th 2001 Robert Dewar The Input Read string input Might be sequence of characters (Unix) Might be sequence of lines (VMS) Character set ASCII ISO Latin-1
Systems I: Computer Organization and Architecture
 Systems I: Computer Organization and Architecture Lecture 2: Number Systems and Arithmetic Number Systems - Base The number system that we use is base : 734 = + 7 + 3 + 4 = x + 7x + 3x + 4x = x 3 + 7x
Systems I: Computer Organization and Architecture Lecture 2: Number Systems and Arithmetic Number Systems - Base The number system that we use is base : 734 = + 7 + 3 + 4 = x + 7x + 3x + 4x = x 3 + 7x
THREE YEAR DEGREE (HONS.) COURSE BACHELOR OF COMPUTER APPLICATION (BCA) First Year Paper I Computer Fundamentals
 THREE YEAR DEGREE (HONS.) COURSE BACHELOR OF COMPUTER APPLICATION (BCA) First Year Paper I Computer Fundamentals Full Marks 100 (Theory 75, Practical 25) Introduction to Computers :- What is Computer?
THREE YEAR DEGREE (HONS.) COURSE BACHELOR OF COMPUTER APPLICATION (BCA) First Year Paper I Computer Fundamentals Full Marks 100 (Theory 75, Practical 25) Introduction to Computers :- What is Computer?
Digital codes. Resources and methods for learning about these subjects (list a few here, in preparation for your research):
 Digital codes This worksheet and all related files are licensed under the Creative Commons Attribution License, version 1.0. To view a copy of this license, visit http://creativecommons.org/licenses/by/1.0/,
Digital codes This worksheet and all related files are licensed under the Creative Commons Attribution License, version 1.0. To view a copy of this license, visit http://creativecommons.org/licenses/by/1.0/,
Using a Laptop Computer with a USB or Serial Port Adapter to Communicate With the Eagle System
 Using a Laptop Computer with a USB or Serial Port Adapter to Communicate With the Eagle System ECU DB9 USB 20-060_A.DOC Page 1 of 18 9/15/2009 2009 Precision Airmotive LLC This publication may not be copied
Using a Laptop Computer with a USB or Serial Port Adapter to Communicate With the Eagle System ECU DB9 USB 20-060_A.DOC Page 1 of 18 9/15/2009 2009 Precision Airmotive LLC This publication may not be copied
Electronic Data Interchange
 Data Interchange plc Electronic Data Interchange Issued: 14 March 2006 Copyright Data Interchange Plc Peterborough, England, September 2005. All rights reserved. No part of this document may be disclosed
Data Interchange plc Electronic Data Interchange Issued: 14 March 2006 Copyright Data Interchange Plc Peterborough, England, September 2005. All rights reserved. No part of this document may be disclosed
Bluetooth HID Profile
 RN-WIFLYCR-UM-.01 RN-HID-UM Bluetooth HID Profile 2012 Roving Networks. All rights reserved. Version 1.0r 1/17/2012 USER MANUAL www.rovingnetworks.com 1 OVERVIEW Roving Networks Bluetooth modules support
RN-WIFLYCR-UM-.01 RN-HID-UM Bluetooth HID Profile 2012 Roving Networks. All rights reserved. Version 1.0r 1/17/2012 USER MANUAL www.rovingnetworks.com 1 OVERVIEW Roving Networks Bluetooth modules support
SYMETRIX SOLUTIONS: TECH TIP August 2015
 String Output Modules The purpose of this document is to provide an understanding of operation and configuration of the two different String Output modules available within SymNet Composer. The two different
String Output Modules The purpose of this document is to provide an understanding of operation and configuration of the two different String Output modules available within SymNet Composer. The two different
DPP-250 Thermal Printer User Manual
 1 DATECS DPP-250 Thermal Printer User Manual The information in this document cannot be reproduced in any mechanical, electrical or electronic way and under any circumstances without the written consent
1 DATECS DPP-250 Thermal Printer User Manual The information in this document cannot be reproduced in any mechanical, electrical or electronic way and under any circumstances without the written consent
Pemrograman Dasar. Basic Elements Of Java
 Pemrograman Dasar Basic Elements Of Java Compiling and Running a Java Application 2 Portable Java Application 3 Java Platform Platform: hardware or software environment in which a program runs. Oracle
Pemrograman Dasar Basic Elements Of Java Compiling and Running a Java Application 2 Portable Java Application 3 Java Platform Platform: hardware or software environment in which a program runs. Oracle
Internationalizing JavaScript Applications Norbert Lindenberg. Norbert Lindenberg 2013. All rights reserved.
 Internationalizing JavaScript Applications Norbert Lindenberg Norbert Lindenberg 2013. All rights reserved. Agenda Unicode support Collation Number and date/time formatting Localizable resources Message
Internationalizing JavaScript Applications Norbert Lindenberg Norbert Lindenberg 2013. All rights reserved. Agenda Unicode support Collation Number and date/time formatting Localizable resources Message
Instruction Set Architecture (ISA)
 Instruction Set Architecture (ISA) * Instruction set architecture of a machine fills the semantic gap between the user and the machine. * ISA serves as the starting point for the design of a new machine
Instruction Set Architecture (ISA) * Instruction set architecture of a machine fills the semantic gap between the user and the machine. * ISA serves as the starting point for the design of a new machine
ESC/POS Command Specifications
 Hybrid Printer ESC/POS Command Specifications Revision 0.00 Star Micronics Co., Ltd. Special Products Operating Division Contents 1) GENERAL DESCRIPTION 1-1 2) COMMAND FUNCTION LIST 2-1 3) COMMAND DETAILS
Hybrid Printer ESC/POS Command Specifications Revision 0.00 Star Micronics Co., Ltd. Special Products Operating Division Contents 1) GENERAL DESCRIPTION 1-1 2) COMMAND FUNCTION LIST 2-1 3) COMMAND DETAILS
Digital Systems Based on Principles and Applications of Electrical Engineering/Rizzoni (McGraw Hill
 Digital Systems Based on Principles and Applications of Electrical Engineering/Rizzoni (McGraw Hill Objectives: Analyze the operation of sequential logic circuits. Understand the operation of digital counters.
Digital Systems Based on Principles and Applications of Electrical Engineering/Rizzoni (McGraw Hill Objectives: Analyze the operation of sequential logic circuits. Understand the operation of digital counters.
Data Acquisition Module with I2C interface «I2C-FLEXEL» User s Guide
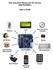 Data Acquisition Module with I2C interface «I2C-FLEXEL» User s Guide Sensors LCD Real Time Clock/ Calendar DC Motors Buzzer LED dimming Relay control I2C-FLEXEL PS2 Keyboards Servo Motors IR Remote Control
Data Acquisition Module with I2C interface «I2C-FLEXEL» User s Guide Sensors LCD Real Time Clock/ Calendar DC Motors Buzzer LED dimming Relay control I2C-FLEXEL PS2 Keyboards Servo Motors IR Remote Control
Tibetan For Windows - Software Development and Future Speculations. Marvin Moser, Tibetan for Windows & Lucent Technologies, USA
 Tibetan For Windows - Software Development and Future Speculations Marvin Moser, Tibetan for Windows & Lucent Technologies, USA Introduction This paper presents the basic functions of the Tibetan for Windows
Tibetan For Windows - Software Development and Future Speculations Marvin Moser, Tibetan for Windows & Lucent Technologies, USA Introduction This paper presents the basic functions of the Tibetan for Windows
Chapter 1: Digital Systems and Binary Numbers
 Chapter 1: Digital Systems and Binary Numbers Digital age and information age Digital computers general purposes many scientific, industrial and commercial applications Digital systems telephone switching
Chapter 1: Digital Systems and Binary Numbers Digital age and information age Digital computers general purposes many scientific, industrial and commercial applications Digital systems telephone switching
QuickScan i. QD2100 Barcode Imager. Product Reference Guide
 QuickScan i QD2100 Barcode Imager Product Reference Guide Configuring the Interface KEYBOARD FEATURES AT, PS/2 25-286, 30-286, 50, 50Z, 60, 70, 80, 90 & 95 w/standard Key Encoding Select KBD-AT Keyboard
QuickScan i QD2100 Barcode Imager Product Reference Guide Configuring the Interface KEYBOARD FEATURES AT, PS/2 25-286, 30-286, 50, 50Z, 60, 70, 80, 90 & 95 w/standard Key Encoding Select KBD-AT Keyboard
Today s topics. Digital Computers. More on binary. Binary Digits (Bits)
 Today s topics! Binary Numbers! Brookshear.-.! Slides from Prof. Marti Hearst of UC Berkeley SIMS! Upcoming! Networks Interactive Introduction to Graph Theory http://www.utm.edu/cgi-bin/caldwell/tutor/departments/math/graph/intro
Today s topics! Binary Numbers! Brookshear.-.! Slides from Prof. Marti Hearst of UC Berkeley SIMS! Upcoming! Networks Interactive Introduction to Graph Theory http://www.utm.edu/cgi-bin/caldwell/tutor/departments/math/graph/intro
Intel Hexadecimal Object File Format Specification Revision A, 1/6/88
 Intel Hexadecimal Object File Format Specification Revision A, 1/6/88 DISCLAIMER Intel makes no representation or warranties with respect to the contents hereof and specifically disclaims any implied warranties
Intel Hexadecimal Object File Format Specification Revision A, 1/6/88 DISCLAIMER Intel makes no representation or warranties with respect to the contents hereof and specifically disclaims any implied warranties
Chapter 6. Inside the System Unit. What You Will Learn... Computers Are Your Future. What You Will Learn... Describing Hardware Performance
 What You Will Learn... Computers Are Your Future Chapter 6 Understand how computers represent data Understand the measurements used to describe data transfer rates and data storage capacity List the components
What You Will Learn... Computers Are Your Future Chapter 6 Understand how computers represent data Understand the measurements used to describe data transfer rates and data storage capacity List the components
Allen-Bradley. Bar Code. 2-D Hand-Held. Programming Guide. Bar Code. Scanners. (Cat. No. 2755-HTG-4)
 Allen-Bradley 2-D Hand-Held Bar Code Scanners Bar Code Programming Guide (Cat. No. 2755-HTG-4) Important User Information The illustrations, charts, sample programs and layout examples shown in this guide
Allen-Bradley 2-D Hand-Held Bar Code Scanners Bar Code Programming Guide (Cat. No. 2755-HTG-4) Important User Information The illustrations, charts, sample programs and layout examples shown in this guide
Binary, Hexadecimal, Octal, and BCD Numbers
 23CH_PHCalter_TMSETE_949118 23/2/2007 1:37 PM Page 1 Binary, Hexadecimal, Octal, and BCD Numbers OBJECTIVES When you have completed this chapter, you should be able to: Convert between binary and decimal
23CH_PHCalter_TMSETE_949118 23/2/2007 1:37 PM Page 1 Binary, Hexadecimal, Octal, and BCD Numbers OBJECTIVES When you have completed this chapter, you should be able to: Convert between binary and decimal
Mail 2 ZOS FTPSweeper
 Mail 2 ZOS FTPSweeper z/os or OS/390 Release 1.0 February 12, 2006 Copyright and Ownership: Mail2ZOS and FTPSweeper are proprietary products to be used only according to the terms and conditions of sale,
Mail 2 ZOS FTPSweeper z/os or OS/390 Release 1.0 February 12, 2006 Copyright and Ownership: Mail2ZOS and FTPSweeper are proprietary products to be used only according to the terms and conditions of sale,
NØGSG DMR Contact Manager
 NØGSG DMR Contact Manager Radio Configuration Management Software for Connect Systems CS700 and CS701 DMR Transceivers End-User Documentation Version 1.24 2015-2016 Tom A. Wheeler [email protected] Terms
NØGSG DMR Contact Manager Radio Configuration Management Software for Connect Systems CS700 and CS701 DMR Transceivers End-User Documentation Version 1.24 2015-2016 Tom A. Wheeler [email protected] Terms
Hexadecimal Object File Format Specification
 Hexadecimal Object File Format Specification Revision A January 6, 1988 This specification is provided "as is" with no warranties whatsoever, including any warranty of merchantability, noninfringement,
Hexadecimal Object File Format Specification Revision A January 6, 1988 This specification is provided "as is" with no warranties whatsoever, including any warranty of merchantability, noninfringement,
Unicode Enabling Java Web Applications
 Internationalization Report: Unicode Enabling Java Web Applications From Browser to DB Provided by: LingoPort, Inc. 1734 Sumac Avenue Boulder, Colorado 80304 Tel: +1.303.444.8020 Fax: +1.303.484.2447 http://www.lingoport.com
Internationalization Report: Unicode Enabling Java Web Applications From Browser to DB Provided by: LingoPort, Inc. 1734 Sumac Avenue Boulder, Colorado 80304 Tel: +1.303.444.8020 Fax: +1.303.484.2447 http://www.lingoport.com
NiceLabel Automation Version 1.5 Release Notes. Rev-1602
 NiceLabel Automation Version 1.5 Release Notes Rev-1602 Table of Contents What is New in NiceLabel Automation?...2 New Label Template Features...2 Batch Printing Support...2 Support for Codabar Barcode
NiceLabel Automation Version 1.5 Release Notes Rev-1602 Table of Contents What is New in NiceLabel Automation?...2 New Label Template Features...2 Batch Printing Support...2 Support for Codabar Barcode
Barcode Labels Feature Focus Series. POSitive For Windows
 Barcode Labels Feature Focus Series POSitive For Windows Inventory Label Printing... 3 PFW System Requirement for Scanners... 3 A Note About Barcode Symbologies... 4 An Occasional Misunderstanding... 4
Barcode Labels Feature Focus Series POSitive For Windows Inventory Label Printing... 3 PFW System Requirement for Scanners... 3 A Note About Barcode Symbologies... 4 An Occasional Misunderstanding... 4
Technical Support Bulletin Nr.18 Modbus Tips
 Technical Support Bulletin Nr.18 Modbus Tips Contents! Definitions! Implemented commands! Examples of commands or frames! Calculating the logical area! Reading a signed variable! Example of commands supported
Technical Support Bulletin Nr.18 Modbus Tips Contents! Definitions! Implemented commands! Examples of commands or frames! Calculating the logical area! Reading a signed variable! Example of commands supported
WORKING DRAFT. ISO/IEC International Standard International Standard 10646. ISO/IEC 10646 1 st Edition + Amd1
 ISO/IEC JC1/SC2/WG2 N2937 ISO/IEC International Standard International Standard 10646 ISO/IEC 10646 1 st Edition + Amd1 Information technology Universal Multiple-Octet Coded Character Set (UCS) Architecture
ISO/IEC JC1/SC2/WG2 N2937 ISO/IEC International Standard International Standard 10646 ISO/IEC 10646 1 st Edition + Amd1 Information technology Universal Multiple-Octet Coded Character Set (UCS) Architecture
TELOCATOR ALPHANUMERIC PROTOCOL (TAP)
 TELOCATOR ALPHANUMERIC PROTOCOL (TAP) Version 1.8 February 4, 1997 TABLE OF CONTENTS 1.0 Introduction...1 2.0 TAP Operating Environment...1 3.0 Recommended Sequence Of Call Delivery From An Entry Device...2
TELOCATOR ALPHANUMERIC PROTOCOL (TAP) Version 1.8 February 4, 1997 TABLE OF CONTENTS 1.0 Introduction...1 2.0 TAP Operating Environment...1 3.0 Recommended Sequence Of Call Delivery From An Entry Device...2
Fingerprint Based Biometric Attendance System
 Fingerprint Based Biometric Attendance System Team Members Vaibhav Shukla Ali Kazmi Amit Waghmare Ravi Ranka Email Id [email protected] [email protected] Contact Numbers 8097031667 9167689265
Fingerprint Based Biometric Attendance System Team Members Vaibhav Shukla Ali Kazmi Amit Waghmare Ravi Ranka Email Id [email protected] [email protected] Contact Numbers 8097031667 9167689265
Virtual Integrated Design Getting started with RS232 Hex Com Tool v6.0
 Virtual Integrated Design Getting started with RS232 Hex Com Tool v6.0 Copyright, 1999-2007 Virtual Integrated Design, All rights reserved. 1 Contents: 1. The Main Window. 2. The Port Setup Window. 3.
Virtual Integrated Design Getting started with RS232 Hex Com Tool v6.0 Copyright, 1999-2007 Virtual Integrated Design, All rights reserved. 1 Contents: 1. The Main Window. 2. The Port Setup Window. 3.
EE 261 Introduction to Logic Circuits. Module #2 Number Systems
 EE 261 Introduction to Logic Circuits Module #2 Number Systems Topics A. Number System Formation B. Base Conversions C. Binary Arithmetic D. Signed Numbers E. Signed Arithmetic F. Binary Codes Textbook
EE 261 Introduction to Logic Circuits Module #2 Number Systems Topics A. Number System Formation B. Base Conversions C. Binary Arithmetic D. Signed Numbers E. Signed Arithmetic F. Binary Codes Textbook
DPP-350. ESC/POS Thermal Printer. Programmer s Manual 1 DATEC
 DPP-350 ESC/POS Thermal Printer Programmer s Manual 1 DATEC Introduction DATECS DPP-350 is a mobile ESC/POS thermal printer with 3-inch wide printing mechanism. It can be used in dynamic working conditions
DPP-350 ESC/POS Thermal Printer Programmer s Manual 1 DATEC Introduction DATECS DPP-350 is a mobile ESC/POS thermal printer with 3-inch wide printing mechanism. It can be used in dynamic working conditions
Bluetooth Installation
 Overview Why Bluetooth? There were good reasons to use Bluetooth for this application. First, we've had customer requests for a way to locate the computer farther from the firearm, on the other side of
Overview Why Bluetooth? There were good reasons to use Bluetooth for this application. First, we've had customer requests for a way to locate the computer farther from the firearm, on the other side of
Multi-lingual Label Printing with Unicode
 Multi-lingual Label Printing with Unicode White Paper Version 20100716 2009 SATO CORPORATION. All rights reserved. http://www.satoworldwide.com [email protected] 2009 SATO Corporation. All rights
Multi-lingual Label Printing with Unicode White Paper Version 20100716 2009 SATO CORPORATION. All rights reserved. http://www.satoworldwide.com [email protected] 2009 SATO Corporation. All rights
Elfring Fonts LaserJet Bar Codes & More
 Elfring Fonts LaserJet Bar Codes & More This package contains five separate types of bar code fonts, and two OCR fonts. These PCL bar code fonts can not be used unless you understand how each bar code
Elfring Fonts LaserJet Bar Codes & More This package contains five separate types of bar code fonts, and two OCR fonts. These PCL bar code fonts can not be used unless you understand how each bar code
Software Developer's Manual
 Software Developer's Manual ESC/P Command Reference RJ-3050/3150 Version 1.00 The rother logo is a registered trademark of rother Industries, Ltd. rother is a registered trademark of rother Industries,
Software Developer's Manual ESC/P Command Reference RJ-3050/3150 Version 1.00 The rother logo is a registered trademark of rother Industries, Ltd. rother is a registered trademark of rother Industries,
Kiwi SyslogGen. A Freeware Syslog message generator for Windows. by SolarWinds, Inc.
 Kiwi SyslogGen A Freeware Syslog message generator for Windows by SolarWinds, Inc. Kiwi SyslogGen is a free Windows Syslog message generator which sends Unix type Syslog messages to any PC or Unix Syslog
Kiwi SyslogGen A Freeware Syslog message generator for Windows by SolarWinds, Inc. Kiwi SyslogGen is a free Windows Syslog message generator which sends Unix type Syslog messages to any PC or Unix Syslog
Session ID: SPC251 Unicode Interfaces Data Exchange Between Unicode and non-unicode Systems
 Session ID: SPC251 Unicode Interfaces Data Exchange Between Unicode and non-unicode Systems Dr. Christian Hansen, SAP AG Agenda Introduction About Code Pages Communication: The Ideal Picture Communication:
Session ID: SPC251 Unicode Interfaces Data Exchange Between Unicode and non-unicode Systems Dr. Christian Hansen, SAP AG Agenda Introduction About Code Pages Communication: The Ideal Picture Communication:
BAR CODE 2 OF 5 INTERLEAVED
 ELFRING FONTS INC BAR CODE 2 OF 5 INTERLEAVED This package includes 25 bar code 2 of 5 interleaved fonts in TrueType and PostScript formats, a Windows utility, Bar25i.exe, to help make your bar codes,
ELFRING FONTS INC BAR CODE 2 OF 5 INTERLEAVED This package includes 25 bar code 2 of 5 interleaved fonts in TrueType and PostScript formats, a Windows utility, Bar25i.exe, to help make your bar codes,
Counting in base 10, 2 and 16
 Counting in base 10, 2 and 16 1. Binary Numbers A super-important fact: (Nearly all) Computers store all information in the form of binary numbers. Numbers, characters, images, music files --- all of these
Counting in base 10, 2 and 16 1. Binary Numbers A super-important fact: (Nearly all) Computers store all information in the form of binary numbers. Numbers, characters, images, music files --- all of these
