CHAPTER 1 INTRODUCTION
|
|
|
- Arleen Bennett
- 7 years ago
- Views:
Transcription
1 CHAPTER 1 INTRODUCTION 1.1 Motivations Vision is the process of discovering from images what is present in the world and where it is (Marr [88], p. 3). Due to the apparent simplicity of the action of seeing, however, the underlying difficulties of visual information processing had not been realized until Marr s pioneer work on computational vision. According to Marr, the ultimate task of any computer vision system is essentially to transform an array of input numerical values into meaningful description that a human normally perceives. Figure 1.1(a) shows an image which consists of two texture regions. However, the texture regions are not obvious at all from the numerical values, where a small portion is shown in Figure 1.1(c). While the true transformation employed by humans is not known, any algorithm for solving vision problems attempts to approximate the transformation based on different assumptions and constraints with respect to the problems to be solved. Existing approaches can thus be categorized according to the problems to be solved and their assumptions. Due to the complexities of the vision process, four problems are widely studied in computer vision relatively independently: edge detection, stereo 1
2 (a) (b) 67 6d a 73 6c 6a f 7b 7c 7d 7e 87 7b 86 bd a6 85 8e b4 8d 95 8c a d 69 6b 63 6f 6c 69 6b 6c 70 6e 6c 6b d 93 8b 7e 7f 81 b7 8f c9 a9 c d 80 7e 8e 7e 8d d 6b 71 6c 6e 6b 6e bb ee ac 81 b8 b6 9c 57 7a 8c 5d d0 8b ab b2 8d d0 bd 8f 84 7a 86 7c e a 6c 62 6d 6a 6d 6e 73 6c 69 b8 9e a6 6b 4e a a7 79 7e 59 ad 80 7e 7a 70 b9 7b d e d a b0 e5 ce 5c 8e 7d 64 6c 98 bd 88 9a e 3d 9b 8c cc 7d 85 7c 87 8d b 65 6a 6e 67 6c dd 9e e e 6b 87 b9 a4 ae 9b 9f b 92 5f a6 7f a8 ab 7c b 8a 8f 8d c a8 a7 a9 a2 5f a c a8 a0 97 9c a d 9d 8a 9f a7 ac b e 93 8b a0 73 6c 70 6b ef e7 d1 a5 82 8e c5 40 7f 9f 9f a2 a3 a6 a0 9d 9e 8f a ca c e e 72 6c 6c 6d dd e0 c6 c4 c2 b0 b6 8e f 9a 9f a3 99 a0 9d a1 70 8a 95 eb b9 7b 84 8a 82 8a b c 77 6e 6d fb d0 da 9f 8f be c0 a8 aa a0 9f a1 a4 9d 9e a d 9e ce 8e c d 9a 8f 96 9a 71 6f e3 e0 dd da c0 a4 d7 a1 a f 98 a0 af a5 9e a7 8b 4d 9c 86 a7 a e 8e d 6d c e6 cf d8 c8 da ad a1 ca b1 fb a4 5f 92 a2 b4 b5 a3 9b 7f 82 b2 4f dd dd ff 88 8d e f d f5 af e3 d0 c0 c2 b7 a7 b2 a2 a6 7f 79 c8 a5 a2 a6 a3 9a b6 d9 99 8a 8a e 9a 97 9a 71 6e 6b 6f fc f5 e0 b1 a3 cc a2 d0 a0 ae a0 93 8f ab be a5 a9 a1 a2 87 7e 8a b1 8f a 8d 8c d 6c 79 6f 6d 73 df d4 e2 9b 84 c0 b0 9d a0 ce 9b ac bb 9b ac aa 9a a c c 88 8c f 78 6d 6f c cf f3 ce bb a2 c0 94 c9 bf 94 9a 9d a0 ad ad b3 a6 ad a3 86 7f b7 92 7a c 8f 8c e 99 9a ec bd cb c5 d8 94 a7 a0 b c8 a7 ab a8 aa bb af bc 8d 94 6e dc 8c 8d 88 8f 8c a 6d 6d 6c c ff d9 df fa d2 b8 ad 8b b1 b7 cd c8 ad a8 b6 af b4 bd d 8a b4 8a 8b 8f 8c d 94 9b 99 6e 6c c 6e ff f4 f0 d8 c5 db 8f a1 b1 c3 f6 d5 95 a8 b5 aa b1 e9 e4 78 7d 8c f 93 8e c 6e 73 6a 71 6f 72 5e dd f4 ef d5 ba bb aa ab aa ae ae ae 96 ab c1 f9 90 c2 f3 ed c4 81 7f d 86 8a c e 6d 6c ff da e6 dc cc b4 ae b5 ae 9e d5 ae ba af 93 a4 b5 ea b1 d3 e7 ff e b 8b 8f 8b a a f f7 c1 97 d8 c4 bb ab ac a7 af a3 aa b1 c5 e8 c3 af 94 9e b2 d6 cd ee de f b d 63 5d e5 d8 cb bb b8 ae aa a9 a3 9b a9 ca e3 ff b5 b6 8f 9b af aa b6 eb c1 80 7e 87 8d 8b d cc d7 c0 b3 bf b6 b3 ad a6 92 a3 c8 de ff a7 bd b5 9b 9c 98 9b d0 a6 e a 8a e 6c 6e 6e 76 6c 6f ff e9 c5 b9 b4 b3 c8 c8 b0 98 a9 b9 d2 ff af aa d1 d9 7b e 87 8e e 6d 63 5f e1 c9 ba ba b3 f6 cd c2 b4 a4 b9 d3 e8 ff 7e 7e 7b 8a 8d 96 7f 9b b3 d3 d7 6e b 8d 8e 96 6c a 71 6b 76 6c 61 db bd b6 a6 ee d9 d4 c4 b5 ad ac c7 d9 ea a b5 8b a5 a8 ad c0 dc d d c c3 a9 a9 99 de e5 d5 bd ae a5 ab bb c8 d7 e3 80 7a 7a d2 b f a0 ad d9 7b 7b 7f d 6a 5b 58 5e 5c 59 5a 63 8f 9c 76 db de c0 bd b9 b0 a9 b1 c2 bd c9 d4 7a f e c2 ee 7a 7f f 5f 5b f e9 cf b5 b0 ae ae b6 b0 bd c6 bb c9 cb a 87 8e e ad d5 e3 7d a 5e d6 bd ba b3 aa af ad b4 b7 bd c3 b9 bf c5 d3 cc 75 8f 9a c 9d a9 dc f a d 5c 68 5d 8d d0 b9 ab a9 a7 ac af b5 c2 c3 bd b2 af b5 c2 c0 d2 d4 b7 b9 97 9a f ae ff a f 65 5c 5f 59 4f 6d c5 bd ae ab a0 a9 a3 b1 b7 b9 c2 c8 c0 a9 9c a5 ba c6 d4 dc da c1 c6 c8 8a b3 c7 ff 7d c 5c 5a cb be bb b8 ba aa a8 a2 92 9c 9a a1 bc ba c5 d5 b9 a0 93 a4 b6 c5 de ee ee de c1 cc d9 b2 b7 ac b2 c3 da bd 5f 5c 54 d0 bd b5 b1 ad a7 9f a3 9a 94 9b 8c 98 a5 b6 c7 d2 e6 c7 9c 8b 94 b4 c2 e2 fe f0 e5 dc e7 de df b4 c1 cc d4 f6 f d0 c1 b8 b2 a6 a4 9e 9b 9d 97 8e 8e ac b5 cc e4 ef c8 9e 8c 91 b1 c5 ef ff fd f1 e7 ee f1 dd d4 cf cc dc e5 e2 82 ca c4 ba ab a6 9e 9f 9b 99 9a 8e a1 b4 cc ea ff c ae c0 f5 ff f4 f6 e9 e6 e2 df d3 d9 dd e3 ea d5 d0 c3 b3 a6 b1 a2 a4 9b 94 8f f e b5 cf ee fb ce 98 8c 90 a7 c4 e9 ff f4 eb e4 d9 d0 d8 d1 d7 e2 d6 e6 d9 ce bd b7 ac a7 a0 a3 9a 92 8e a b 9d ba d7 f2 ff d4 9a a7 c6 e3 f9 f9 f9 e4 d9 d7 de de ec ee ea f3 e4 (c) Figure 1.1: A texture image and the corresponding numerical arrays. (a) A texture image with size (b) A small portion with size of (a) centered at pixel (64, 37), which is on the boundary between the two texture regions. (c) Numerical values of (b). To save space, the values are displayed in hexadecimal format. 2
3 matching and motion analysis, image segmentation and perceptual organization, and pattern recognition. Roughly speaking, the techniques for the first three problems are primarily data-driven, or called bottom-up processes, and pattern recognition is model-driven, or called top-down process. Early techniques with successful applications are classification techniques [25], which map a given input into one of the pre-defined classes according to a distance measure. However, all the possible classes and their variations we normally perceive are too gigantic to be implemented effectively in any system. The attention of computer vision was then shifted to derive more generic features for arbitrary images. From information and encoding theories, edges, i.e., discontinuities in images, carry more information and exhibit nice properties such as invariance to luminance changes. Motivated by neurophysiological findings [53], many edge detection algorithms were proposed and studied. Segmentation techniques try to solve the same problem by segmenting an image into homogeneous regions, where edges and region contours can be obtained straightforwardly and more robustly. These approaches were claimed to be unified [92] through what is called Mumford-Shah Segmentation energy functional [94] (See Chapters 4 and 5). Common to these approaches, the images are assumed to be piece-wise smooth regions with additive Gaussian noise, resulting in efficient algorithms. To improve the performance for real images, multiple scales are generally needed and linear and nonlinear scale spaces are thus proposed and studied. Chapter 2 studies segmentation for range images. Chapter 3 studies a new nonlinear smoothing algorithm and addresses some of problems in nonlinear scale spaces. Chapter 7 applies a nonlinear smoothing algorithm to hydrographic object extraction from remotely sensed images. 3
4 While there are useful applications of edge detection and segmentation algorithms, the underlying assumption limits their successes in dealing with natural images. As shown in Figure 1.1, texture regions neither are piece-wise smooth nor can be modeled with additive Gaussian noise. Figure 1.2 demonstrated that a pure linear system is not sufficient for natural image modeling [63], where the spatial relationships among pixels are more prominent in characterizing the texture regions than individual pixels. Clearly piece-wise smooth regions with additive Gaussian noise are not sufficient and more sophisticated models are needed to deal with texture images. Supported by neurophysiological and psychophysical experiments [12] [23], The early processes in the human vision system can be abstractly modeled by filtering with a set of frequency and orientation tuned filters. However, as demonstrated in Figure 1.2, purely linear filtering is not sufficient, nonlinearity beyond filtering must be incorporated [87]. Spectral histograms integrate the responses of a chosen bank of filters through marginal distributions [148] [149] [150] [147]. As demonstrated in Figure 1.2, spectral histograms are nonlinear. Chapters 4 and 5 apply spectral histograms to modeling [147], classification, and segmentation of texture as well as intensity images. While edge detection and segmentation techniques are very fruitful, there are perceptual phenomena that cannot be explained by purely data-driven processes. Classical examples include virtual contours, which are widely studied by Gestaltists. The long-range order grouping is known as perceptual organization. Chapter 6 studies perceptual organization through temporal dynamics. Because many of the meaningful objects cannot be characterized well using intensity values or even textures, such as a human face, the relationships among some 4
5 (a) (b) (c) Figure 1.2: Demonstration of nonlinearity for texture images. (a) A regular texture image. (b) The image in (a) was circularly shifted left and downward for 2 pixels at each direction. (c) The pixel-by-pixel average of (a) and (b). The relative variance defined in (3.20) between (a) and (b) is 137, and between (a) and (c) is 69. The distance between the spectral histograms defined in Chapter 4 between (a) and (b) is and between (a) and (c) is
6 primitives need to be modeled. This leads to the need of top-down processes such as recognition. Clearly, the four problems studied are sub-problems of vision process and the integration among them is critical for a complete vision system. The interaction between different modules is briefly discussed in Chapter Thesis Overview As discussed above, we study vision problems at different organizational levels in this dissertation. In Chapter 2, we study the segmentation problem for range images. Depth is most important cue for visual perception and range image segmentation has a wide range of applications. We propose a feature vector consisting of surface normal, mean and Gaussian curvatures and a similarity measure for range images. We implemented a system based on oscillatory correlation using a LEGION (locally excitatory globally inhibitory oscillator network) network. Experimental results demonstrate that our system is capable of handling different kinds of surfaces. With the unique properties of a temporal dynamic system, our approach may lead to a real-time approach for range image segmentation. In Chapter 3, we propose a new nonlinear smoothing algorithm by incorporating contextual information and geometrical constraints. Several nonlinear algorithms are derived as special cases of the proposed one. We have compared the temporal behavior and boundary detection results of several widely algorithms, including the proposed method. The proposed algorithm gives quantitatively good results and exhibits nice temporal behaviors such as quick convergence and robustness to noise. In Chapter 4, we propose spectral histograms as a generic statistic feature for texture as well as intensity images. We demonstrate the properties of spectral histograms 6
7 using image synthesis, image classification, and content-based image retrieval. We also compare with several widely used statistic features for textures and show that the distribution of local features is critically important for classification while mean and variance in general are not sufficient. We also propose a model for texture discrimination, which matches the existing psychophysical data well. Chapter 5 continues the work in Chapter 4. In Chapter 5, segmentation problem is studied extensively using spectral histograms. A new energy functional for segmentation is proposed by making explicit the homogeneity measures. An approximate algorithm is derived, implemented and studied under different assumptions. Satisfactory results have been obtained using natural texture images. Chapter 6 studies the problem of perceptual organization and long-range grouping, which is one level beyond the segmentation. By using a boundary-pair representation, we propose a figure-ground segregation network. Gestalt-like grouping rules are incorporated by modulating the connection weights in the network. The network can explain many perceptual phenomena such as modal and amodal completion, shape composition and perceptual grouping using a fixed set of parameters. Chapter 7 presents a computational framework for feature extraction from remote sensing images for map revision and geographic information extraction purposes. A multi-layer perceptron is used to learn the features to be extracted from examples. A locally coupled LEGION network is used to achieve accurate boundary localization. To increase the robustness of the system, a weight adaption method is used. Experimental results using DOQQ images show that our system can handle very large images efficiently and may have a wide range of applications. 7
8 Chapter 8 summarizes the contributions of the work presented in this dissertation and concludes this dissertation with discussions on the future work. 8
Visa Smart Debit/Credit Certificate Authority Public Keys
 CHIP AND NEW TECHNOLOGIES Visa Smart Debit/Credit Certificate Authority Public Keys Overview The EMV standard calls for the use of Public Key technology for offline authentication, for aspects of online
CHIP AND NEW TECHNOLOGIES Visa Smart Debit/Credit Certificate Authority Public Keys Overview The EMV standard calls for the use of Public Key technology for offline authentication, for aspects of online
SERVER CERTIFICATES OF THE VETUMA SERVICE
 Page 1 Version: 3.4, 19.12.2014 SERVER CERTIFICATES OF THE VETUMA SERVICE 1 (18) Page 2 Version: 3.4, 19.12.2014 Table of Contents 1. Introduction... 3 2. Test Environment... 3 2.1 Vetuma test environment...
Page 1 Version: 3.4, 19.12.2014 SERVER CERTIFICATES OF THE VETUMA SERVICE 1 (18) Page 2 Version: 3.4, 19.12.2014 Table of Contents 1. Introduction... 3 2. Test Environment... 3 2.1 Vetuma test environment...
SERVER CERTIFICATES OF THE VETUMA SERVICE
 Page 1 Version: 3.5, 4.11.2015 SERVER CERTIFICATES OF THE VETUMA SERVICE 1 (18) Page 2 Version: 3.5, 4.11.2015 Table of Contents 1. Introduction... 3 2. Test Environment... 3 2.1 Vetuma test environment...
Page 1 Version: 3.5, 4.11.2015 SERVER CERTIFICATES OF THE VETUMA SERVICE 1 (18) Page 2 Version: 3.5, 4.11.2015 Table of Contents 1. Introduction... 3 2. Test Environment... 3 2.1 Vetuma test environment...
Pattern Co. Monkey Trouble Wall Quilt. Size: 48" x 58"
 .............................................................................................................................................. Pattern Co..........................................................................................
.............................................................................................................................................. Pattern Co..........................................................................................
USB HID to PS/2 Scan Code Translation Table
 Key Name HID Usage Page HID Usage ID PS/2 Set 1 Make* PS/2 Set 1 Break* PS/2 Set 2 Make PS/2 Set 2 Break System Power 01 81 E0 5E E0 DE E0 37 E0 F0 37 System Sleep 01 82 E0 5F E0 DF E0 3F E0 F0 3F System
Key Name HID Usage Page HID Usage ID PS/2 Set 1 Make* PS/2 Set 1 Break* PS/2 Set 2 Make PS/2 Set 2 Break System Power 01 81 E0 5E E0 DE E0 37 E0 F0 37 System Sleep 01 82 E0 5F E0 DF E0 3F E0 F0 3F System
Advanced Encryption Standard by Example. 1.0 Preface. 2.0 Terminology. Written By: Adam Berent V.1.7
 Written By: Adam Berent Advanced Encryption Standard by Example V.1.7 1.0 Preface The following document provides a detailed and easy to understand explanation of the implementation of the AES (RIJNDAEL)
Written By: Adam Berent Advanced Encryption Standard by Example V.1.7 1.0 Preface The following document provides a detailed and easy to understand explanation of the implementation of the AES (RIJNDAEL)
Advanced Encryption Standard by Example. 1.0 Preface. 2.0 Terminology. Written By: Adam Berent V.1.5
 Written By: Adam Berent Advanced Encryption Standard by Example V.1.5 1.0 Preface The following document provides a detailed and easy to understand explanation of the implementation of the AES (RIJNDAEL)
Written By: Adam Berent Advanced Encryption Standard by Example V.1.5 1.0 Preface The following document provides a detailed and easy to understand explanation of the implementation of the AES (RIJNDAEL)
0242-1. HSR TRAINING COURSE REQUIREMENTS HSR Training Course Guidance Booklet 2
 0242-1 HSR TRAINING COURSE REQUIREMENTS HSR Training Course Guidance Booklet 2 SafeWork SA 2 Contents Introduction... 4 Learning resources... 4 PART 1 UNDERPINNING PRINCIPLES FOR THE DEVELOPMENT OF A SAFEWORK
0242-1 HSR TRAINING COURSE REQUIREMENTS HSR Training Course Guidance Booklet 2 SafeWork SA 2 Contents Introduction... 4 Learning resources... 4 PART 1 UNDERPINNING PRINCIPLES FOR THE DEVELOPMENT OF A SAFEWORK
The ASCII Character Set
 The ASCII Character Set The American Standard Code for Information Interchange or ASCII assigns values between 0 and 255 for upper and lower case letters, numeric digits, punctuation marks and other symbols.
The ASCII Character Set The American Standard Code for Information Interchange or ASCII assigns values between 0 and 255 for upper and lower case letters, numeric digits, punctuation marks and other symbols.
SL-8800 HDCP 2.2 and HDCP 1.x Protocol Analyzer for HDMI User Guide
 SL-8800 HDCP 2.2 and HDCP 1.x Protocol Analyzer for HDMI Simplay-UG-02003-A July 2015 Contents 1. Overview... 4 1.1. SL-8800 HDCP Protocol Analyzer Test Equipment... 4 1.2. HDCP 2.2/HDCP 1.x Protocol Analyzer
SL-8800 HDCP 2.2 and HDCP 1.x Protocol Analyzer for HDMI Simplay-UG-02003-A July 2015 Contents 1. Overview... 4 1.1. SL-8800 HDCP Protocol Analyzer Test Equipment... 4 1.2. HDCP 2.2/HDCP 1.x Protocol Analyzer
How to create OpenDocument URL s with SAP BusinessObjects BI 4.0
 How to create OpenDocument URL s with SAP BusinessObjects BI 4.0 Creator: Twitter: Blog: Pieter Verstraeten http://www.twitter.com/pverstraeten http://www.pieterverstraeten.com/blog Hi, Thanks for downloading
How to create OpenDocument URL s with SAP BusinessObjects BI 4.0 Creator: Twitter: Blog: Pieter Verstraeten http://www.twitter.com/pverstraeten http://www.pieterverstraeten.com/blog Hi, Thanks for downloading
Luxembourg (Luxembourg): Trusted List
 Luxembourg (Luxembourg): Trusted List Institut Luxembourgeois de la Normalisation, de l'accréditation de la Sécurité et qualité des produits et services Scheme Information TSL Version 4 TSL Sequence Number
Luxembourg (Luxembourg): Trusted List Institut Luxembourgeois de la Normalisation, de l'accréditation de la Sécurité et qualité des produits et services Scheme Information TSL Version 4 TSL Sequence Number
CROSS REFERENCE. Cross Reference Index 110-122. Cast ID Number 110-111 Connector ID Number 111 Engine ID Number 112-122. 2015 Ford Motor Company 109
 CROSS REFERENCE Cross Reference Index 110-122 Cast ID Number 110-111 Connector ID Number 111 112-122 2015 Ford Motor Company 109 CROSS REFERENCE Cast ID Number Cast ID Ford Service # MC Part # Part Type
CROSS REFERENCE Cross Reference Index 110-122 Cast ID Number 110-111 Connector ID Number 111 112-122 2015 Ford Motor Company 109 CROSS REFERENCE Cast ID Number Cast ID Ford Service # MC Part # Part Type
KALE: A High-Degree Algebraic-Resistant Variant of The Advanced Encryption Standard
 KALE: A High-Degree Algebraic-Resistant Variant of The Advanced Encryption Standard Dr. Gavekort c/o Vakiopaine Bar Kauppakatu 6, 41 Jyväskylä FINLAND mjos@iki.fi Abstract. We have discovered that the
KALE: A High-Degree Algebraic-Resistant Variant of The Advanced Encryption Standard Dr. Gavekort c/o Vakiopaine Bar Kauppakatu 6, 41 Jyväskylä FINLAND mjos@iki.fi Abstract. We have discovered that the
3. April 2013 IT ZERTIFIKATE. Zertifizierungsstellen / Certification Center. IT Sicherheit UNTERNEHMENSBEREICH IT
 IT Sicherheit UNTERNEHMENSBEREICH IT IT ZERTIFIKATE 3. April 2013 Zertifizierungsstellen / Certification Center D-TRUST D-Trust Root Class 2 CA2007 Aussteller/Issuer: D-TRUST Root Class 2 CA 2007 Gültig
IT Sicherheit UNTERNEHMENSBEREICH IT IT ZERTIFIKATE 3. April 2013 Zertifizierungsstellen / Certification Center D-TRUST D-Trust Root Class 2 CA2007 Aussteller/Issuer: D-TRUST Root Class 2 CA 2007 Gültig
Community College of Philadelphia Calling Code 218 Employer Scan Client Approved: November 17, 2005 Region (CIRCLE) City MSA
 Community College of Philadelphia Calling Code 218 Employer Scan Client Approved: November 17, 2005 Region (CIRCLE) City MSA Zip V0 V1 V2 Month/ Day/ Year of Contact: Business Name: Address: V3 City: V4
Community College of Philadelphia Calling Code 218 Employer Scan Client Approved: November 17, 2005 Region (CIRCLE) City MSA Zip V0 V1 V2 Month/ Day/ Year of Contact: Business Name: Address: V3 City: V4
URL encoding uses hex code prefixed by %. Quoted Printable encoding uses hex code prefixed by =.
 ASCII = American National Standard Code for Information Interchange ANSI X3.4 1986 (R1997) (PDF), ANSI INCITS 4 1986 (R1997) (Printed Edition) Coded Character Set 7 Bit American National Standard Code
ASCII = American National Standard Code for Information Interchange ANSI X3.4 1986 (R1997) (PDF), ANSI INCITS 4 1986 (R1997) (Printed Edition) Coded Character Set 7 Bit American National Standard Code
ASCII CODES WITH GREEK CHARACTERS
 ASCII CODES WITH GREEK CHARACTERS Dec Hex Char Description 0 0 NUL (Null) 1 1 SOH (Start of Header) 2 2 STX (Start of Text) 3 3 ETX (End of Text) 4 4 EOT (End of Transmission) 5 5 ENQ (Enquiry) 6 6 ACK
ASCII CODES WITH GREEK CHARACTERS Dec Hex Char Description 0 0 NUL (Null) 1 1 SOH (Start of Header) 2 2 STX (Start of Text) 3 3 ETX (End of Text) 4 4 EOT (End of Transmission) 5 5 ENQ (Enquiry) 6 6 ACK
HTML Codes - Characters and symbols
 ASCII Codes HTML Codes Conversion References Control Characters English version Versión español Click here to add this link to your favorites. HTML Codes - Characters and symbols Standard ASCII set, HTML
ASCII Codes HTML Codes Conversion References Control Characters English version Versión español Click here to add this link to your favorites. HTML Codes - Characters and symbols Standard ASCII set, HTML
Service Instruction. 1.0 SUBJECT: ECi Accessory Cases for Lycoming 4-Cylinder engines with single magneto configurations and TITAN 361 Engines
 Title: Service Instruction ECi Accessory Cases Installed on Engines S.I. No.: 03-1 Page: 1 of 7 Issued: 2/28/2003 Revision: 2 (4/13/2009) Technical Portions are FAA DER Approved. 1.0 SUBJECT: ECi Accessory
Title: Service Instruction ECi Accessory Cases Installed on Engines S.I. No.: 03-1 Page: 1 of 7 Issued: 2/28/2003 Revision: 2 (4/13/2009) Technical Portions are FAA DER Approved. 1.0 SUBJECT: ECi Accessory
EMV (Chip-and-PIN) Protocol
 EMV (Chip-and-PIN) Protocol Märt Bakhoff December 15, 2014 Abstract The objective of this report is to observe and describe a real world online transaction made between a debit card issued by an Estonian
EMV (Chip-and-PIN) Protocol Märt Bakhoff December 15, 2014 Abstract The objective of this report is to observe and describe a real world online transaction made between a debit card issued by an Estonian
Modelling, Extraction and Description of Intrinsic Cues of High Resolution Satellite Images: Independent Component Analysis based approaches
 Modelling, Extraction and Description of Intrinsic Cues of High Resolution Satellite Images: Independent Component Analysis based approaches PhD Thesis by Payam Birjandi Director: Prof. Mihai Datcu Problematic
Modelling, Extraction and Description of Intrinsic Cues of High Resolution Satellite Images: Independent Component Analysis based approaches PhD Thesis by Payam Birjandi Director: Prof. Mihai Datcu Problematic
NEOSHO COUNTY COMMUNITY COLLEGE MASTER COURSE SYLLABUS. Medical Administrative Aspects
 NEOSHO COUNTY COMMUNITY COLLEGE MASTER COURSE SYLLABUS COURSE IDENTIFICATION Course Code/Number: ALMA 120 Course Title: Medical Administrative Aspects Division: Applied Science (AS) Liberal Arts (LA) Workforce
NEOSHO COUNTY COMMUNITY COLLEGE MASTER COURSE SYLLABUS COURSE IDENTIFICATION Course Code/Number: ALMA 120 Course Title: Medical Administrative Aspects Division: Applied Science (AS) Liberal Arts (LA) Workforce
Digital image processing
 746A27 Remote Sensing and GIS Lecture 4 Digital image processing Chandan Roy Guest Lecturer Department of Computer and Information Science Linköping University Digital Image Processing Most of the common
746A27 Remote Sensing and GIS Lecture 4 Digital image processing Chandan Roy Guest Lecturer Department of Computer and Information Science Linköping University Digital Image Processing Most of the common
Rijndael Encryption implementation on different platforms, with emphasis on performance
 Rijndael Encryption implementation on different platforms, with emphasis on performance KAFUUMA JOHN SSENYONJO Bsc (Hons) Computer Software Theory University of Bath May 2005 Rijndael Encryption implementation
Rijndael Encryption implementation on different platforms, with emphasis on performance KAFUUMA JOHN SSENYONJO Bsc (Hons) Computer Software Theory University of Bath May 2005 Rijndael Encryption implementation
Visibility optimization for data visualization: A Survey of Issues and Techniques
 Visibility optimization for data visualization: A Survey of Issues and Techniques Ch Harika, Dr.Supreethi K.P Student, M.Tech, Assistant Professor College of Engineering, Jawaharlal Nehru Technological
Visibility optimization for data visualization: A Survey of Issues and Techniques Ch Harika, Dr.Supreethi K.P Student, M.Tech, Assistant Professor College of Engineering, Jawaharlal Nehru Technological
COUNCIL OF INTERNATIONAL SCHOOLS (CIS) SCHOOL IMPROVEMENT THROUGH ACCREDITATION
 COUNCIL OF INTERNATIONAL SCHOOLS (CIS) SCHOOL IMPROVEMENT THROUGH ACCREDITATION Guide to School Evaluation and Accreditation - 8 th Edition (Version 8.2) STANDARDS AND INDICATORS SECTION A SCHOOL GUIDING
COUNCIL OF INTERNATIONAL SCHOOLS (CIS) SCHOOL IMPROVEMENT THROUGH ACCREDITATION Guide to School Evaluation and Accreditation - 8 th Edition (Version 8.2) STANDARDS AND INDICATORS SECTION A SCHOOL GUIDING
DATING YOUR GUILD 1952-1960
 DATING YOUR GUILD 1952-1960 YEAR APPROXIMATE LAST SERIAL NUMBER PRODUCED 1953 1000-1500 1954 1500-2200 1955 2200-3000 1956 3000-4000 1957 4000-5700 1958 5700-8300 1959 12035 1960-1969 This chart displays
DATING YOUR GUILD 1952-1960 YEAR APPROXIMATE LAST SERIAL NUMBER PRODUCED 1953 1000-1500 1954 1500-2200 1955 2200-3000 1956 3000-4000 1957 4000-5700 1958 5700-8300 1959 12035 1960-1969 This chart displays
Parallax Serial LCD 2 rows x 16 characters Non-backlit (#27976) 2 rows x 16 characters Backlit (#27977) 4 rows x 20 characters Backlit (#27979)
 599 Menlo Drive, Suite 100 Rocklin, California 95765, USA Office: (916) 624-8333 Fax: (916) 624-8003 General: info@parallax.com Technical: support@parallax.com Web Site: www.parallax.com Educational: www.stampsinclass.com
599 Menlo Drive, Suite 100 Rocklin, California 95765, USA Office: (916) 624-8333 Fax: (916) 624-8003 General: info@parallax.com Technical: support@parallax.com Web Site: www.parallax.com Educational: www.stampsinclass.com
Assessment. Presenter: Yupu Zhang, Guoliang Jin, Tuo Wang Computer Vision 2008 Fall
 Automatic Photo Quality Assessment Presenter: Yupu Zhang, Guoliang Jin, Tuo Wang Computer Vision 2008 Fall Estimating i the photorealism of images: Distinguishing i i paintings from photographs h Florin
Automatic Photo Quality Assessment Presenter: Yupu Zhang, Guoliang Jin, Tuo Wang Computer Vision 2008 Fall Estimating i the photorealism of images: Distinguishing i i paintings from photographs h Florin
NEOSHO COUNTY COMMUNITY COLLEGE MASTER COURSE SYLLABUS. Medical Professional Issues
 NEOSHO COUNTY COMMUNITY COLLEGE MASTER COURSE SYLLABUS COURSE IDENTIFICATION Course Code/Number: ALMA 110 Course Title: Medical Professional Issues Division: Applied Science (AS) Liberal Arts (LA) Workforce
NEOSHO COUNTY COMMUNITY COLLEGE MASTER COURSE SYLLABUS COURSE IDENTIFICATION Course Code/Number: ALMA 110 Course Title: Medical Professional Issues Division: Applied Science (AS) Liberal Arts (LA) Workforce
"HIGHER EDUCATION VALUES AND OPINIONS SURVEY" ADVANCED PLACEMENT TEACHERS and GUIDANCE COUNSELORS May-June 1994
 "HIGHER EDUCATION VALUES AND OPINIONS SURVEY" ADVANCED PLACEMENT TEACHERS and GUIDANCE COUNSELORS May-June 1994 VARIABLE SURVEY ANSWER NAME QUESTION CATEGORIES Facsimile the original mail questionnaire
"HIGHER EDUCATION VALUES AND OPINIONS SURVEY" ADVANCED PLACEMENT TEACHERS and GUIDANCE COUNSELORS May-June 1994 VARIABLE SURVEY ANSWER NAME QUESTION CATEGORIES Facsimile the original mail questionnaire
COMPARISON OF OBJECT BASED AND PIXEL BASED CLASSIFICATION OF HIGH RESOLUTION SATELLITE IMAGES USING ARTIFICIAL NEURAL NETWORKS
 COMPARISON OF OBJECT BASED AND PIXEL BASED CLASSIFICATION OF HIGH RESOLUTION SATELLITE IMAGES USING ARTIFICIAL NEURAL NETWORKS B.K. Mohan and S. N. Ladha Centre for Studies in Resources Engineering IIT
COMPARISON OF OBJECT BASED AND PIXEL BASED CLASSIFICATION OF HIGH RESOLUTION SATELLITE IMAGES USING ARTIFICIAL NEURAL NETWORKS B.K. Mohan and S. N. Ladha Centre for Studies in Resources Engineering IIT
A DIVISION OF THE MENO. Meno proposes a question: whether virtue can be taught. Three conversations or discussions following question
 A DIVISION OF THE MENO 70A 70B-100B Meno proposes a question: whether virtue can be taught Three conversations or discussions following question 70B-80D Conversation on a question before Meno's: what is
A DIVISION OF THE MENO 70A 70B-100B Meno proposes a question: whether virtue can be taught Three conversations or discussions following question 70B-80D Conversation on a question before Meno's: what is
Environmental Remote Sensing GEOG 2021
 Environmental Remote Sensing GEOG 2021 Lecture 4 Image classification 2 Purpose categorising data data abstraction / simplification data interpretation mapping for land cover mapping use land cover class
Environmental Remote Sensing GEOG 2021 Lecture 4 Image classification 2 Purpose categorising data data abstraction / simplification data interpretation mapping for land cover mapping use land cover class
MAC Address Management
 D MAC Address Management Contents Overview.................................................... D-2.................................. D-3 Menu: Viewing the Switch s MAC Addresses.................... D-4
D MAC Address Management Contents Overview.................................................... D-2.................................. D-3 Menu: Viewing the Switch s MAC Addresses.................... D-4
SOFTWARE ENGINEERING PROGRAM ASSESSMENT PLAN
 SOFTWARE ENGINEERING PROGRAM ASSESSMENT PLAN Version 3.0 October 5, 2010 Version 2.6 November 6, 2009 Version 2.5 September 16, 2008 Version 2.4 February 29, 2008 Version 2.3 January 12, 2007 Version 2.2
SOFTWARE ENGINEERING PROGRAM ASSESSMENT PLAN Version 3.0 October 5, 2010 Version 2.6 November 6, 2009 Version 2.5 September 16, 2008 Version 2.4 February 29, 2008 Version 2.3 January 12, 2007 Version 2.2
Elements of Abstract Group Theory
 Chapter 2 Elements of Abstract Group Theory Mathematics is a game played according to certain simple rules with meaningless marks on paper. David Hilbert The importance of symmetry in physics, and for
Chapter 2 Elements of Abstract Group Theory Mathematics is a game played according to certain simple rules with meaningless marks on paper. David Hilbert The importance of symmetry in physics, and for
The Role of SPOT Satellite Images in Mapping Air Pollution Caused by Cement Factories
 The Role of SPOT Satellite Images in Mapping Air Pollution Caused by Cement Factories Dr. Farrag Ali FARRAG Assistant Prof. at Civil Engineering Dept. Faculty of Engineering Assiut University Assiut, Egypt.
The Role of SPOT Satellite Images in Mapping Air Pollution Caused by Cement Factories Dr. Farrag Ali FARRAG Assistant Prof. at Civil Engineering Dept. Faculty of Engineering Assiut University Assiut, Egypt.
3 An Illustrative Example
 Objectives An Illustrative Example Objectives - Theory and Examples -2 Problem Statement -2 Perceptron - Two-Input Case -4 Pattern Recognition Example -5 Hamming Network -8 Feedforward Layer -8 Recurrent
Objectives An Illustrative Example Objectives - Theory and Examples -2 Problem Statement -2 Perceptron - Two-Input Case -4 Pattern Recognition Example -5 Hamming Network -8 Feedforward Layer -8 Recurrent
The University of the State of New York REGENTS HIGH SCHOOL EXAMINATION GEOMETRY. Thursday, August 16, 2012 8:30 to 11:30 a.m.
 GEOMETRY The University of the State of New York REGENTS HIGH SCHOOL EXAMINATION GEOMETRY Thursday, August 16, 2012 8:30 to 11:30 a.m., only Student Name: School Name: Print your name and the name of your
GEOMETRY The University of the State of New York REGENTS HIGH SCHOOL EXAMINATION GEOMETRY Thursday, August 16, 2012 8:30 to 11:30 a.m., only Student Name: School Name: Print your name and the name of your
Colorado School of Mines Computer Vision Professor William Hoff
 Professor William Hoff Dept of Electrical Engineering &Computer Science http://inside.mines.edu/~whoff/ 1 Introduction to 2 What is? A process that produces from images of the external world a description
Professor William Hoff Dept of Electrical Engineering &Computer Science http://inside.mines.edu/~whoff/ 1 Introduction to 2 What is? A process that produces from images of the external world a description
Geometry Handout 2 ~ Page 1
 1. Given: a b, b c a c Guidance: Draw a line which intersects with all three lines. 2. Given: a b, c a a. c b b. Given: d b d c 3. Given: a c, b d a. α = β b. Given: e and f bisect angles α and β respectively.
1. Given: a b, b c a c Guidance: Draw a line which intersects with all three lines. 2. Given: a b, c a a. c b b. Given: d b d c 3. Given: a c, b d a. α = β b. Given: e and f bisect angles α and β respectively.
Future Trends in Airline Pricing, Yield. March 13, 2013
 Future Trends in Airline Pricing, Yield Management, &AncillaryFees March 13, 2013 THE OPPORTUNITY IS NOW FOR CORPORATE TRAVEL MANAGEMENT BUT FIRST: YOU HAVE TO KNOCK DOWN BARRIERS! but it won t hurt much!
Future Trends in Airline Pricing, Yield Management, &AncillaryFees March 13, 2013 THE OPPORTUNITY IS NOW FOR CORPORATE TRAVEL MANAGEMENT BUT FIRST: YOU HAVE TO KNOCK DOWN BARRIERS! but it won t hurt much!
WHITE PAPER. Methods for Measuring Flat Panel Display Defects and Mura as Correlated to Human Visual Perception
 Methods for Measuring Flat Panel Display Defects and Mura as Correlated to Human Visual Perception Methods for Measuring Flat Panel Display Defects and Mura as Correlated to Human Visual Perception Abstract
Methods for Measuring Flat Panel Display Defects and Mura as Correlated to Human Visual Perception Methods for Measuring Flat Panel Display Defects and Mura as Correlated to Human Visual Perception Abstract
Application Note RMF Magic 5.1.0: EMC Array Group and EMC SRDF/A Reporting. July 2009
 Application Note RMF Magic 5.1.0: EMC Array Group and EMC SRDF/A Reporting July 2009 Summary: This Application Note describes the new functionality in RMF Magic 5.1 that enables more effective monitoring
Application Note RMF Magic 5.1.0: EMC Array Group and EMC SRDF/A Reporting July 2009 Summary: This Application Note describes the new functionality in RMF Magic 5.1 that enables more effective monitoring
Transparency and Occlusion
 Transparency and Occlusion Barton L. Anderson University of New South Wales One of the great computational challenges in recovering scene structure from images arises from the fact that some surfaces in
Transparency and Occlusion Barton L. Anderson University of New South Wales One of the great computational challenges in recovering scene structure from images arises from the fact that some surfaces in
QA Framework. Process Control Objectives Toolkit
 QA Framework Process Control Objectives Toolkit Contents 1. Introduction 2. Purpose and Scope 3. Context 4. Existing Guidance and Assumptions 5. Process Overview 6. How to use the toolkit 7. Framework
QA Framework Process Control Objectives Toolkit Contents 1. Introduction 2. Purpose and Scope 3. Context 4. Existing Guidance and Assumptions 5. Process Overview 6. How to use the toolkit 7. Framework
Texture. Chapter 7. 7.1 Introduction
 Chapter 7 Texture 7.1 Introduction Texture plays an important role in many machine vision tasks such as surface inspection, scene classification, and surface orientation and shape determination. For example,
Chapter 7 Texture 7.1 Introduction Texture plays an important role in many machine vision tasks such as surface inspection, scene classification, and surface orientation and shape determination. For example,
Bernice E. Rogowitz and Holly E. Rushmeier IBM TJ Watson Research Center, P.O. Box 704, Yorktown Heights, NY USA
 Are Image Quality Metrics Adequate to Evaluate the Quality of Geometric Objects? Bernice E. Rogowitz and Holly E. Rushmeier IBM TJ Watson Research Center, P.O. Box 704, Yorktown Heights, NY USA ABSTRACT
Are Image Quality Metrics Adequate to Evaluate the Quality of Geometric Objects? Bernice E. Rogowitz and Holly E. Rushmeier IBM TJ Watson Research Center, P.O. Box 704, Yorktown Heights, NY USA ABSTRACT
Open Access A Facial Expression Recognition Algorithm Based on Local Binary Pattern and Empirical Mode Decomposition
 Send Orders for Reprints to reprints@benthamscience.ae The Open Electrical & Electronic Engineering Journal, 2014, 8, 599-604 599 Open Access A Facial Expression Recognition Algorithm Based on Local Binary
Send Orders for Reprints to reprints@benthamscience.ae The Open Electrical & Electronic Engineering Journal, 2014, 8, 599-604 599 Open Access A Facial Expression Recognition Algorithm Based on Local Binary
Taking Inverse Graphics Seriously
 CSC2535: 2013 Advanced Machine Learning Taking Inverse Graphics Seriously Geoffrey Hinton Department of Computer Science University of Toronto The representation used by the neural nets that work best
CSC2535: 2013 Advanced Machine Learning Taking Inverse Graphics Seriously Geoffrey Hinton Department of Computer Science University of Toronto The representation used by the neural nets that work best
Calculation of Valu-Trac Statuses
 Calculation of Intrinsic Value Yield Latest Cash Earnings (Net Income + Depreciation and Amortization) (put aside) Dividend (subtract) Provision for Depreciation (Net Assets x Inflation Rate) (subtract)
Calculation of Intrinsic Value Yield Latest Cash Earnings (Net Income + Depreciation and Amortization) (put aside) Dividend (subtract) Provision for Depreciation (Net Assets x Inflation Rate) (subtract)
Common Licensing Technology Overview
 Common Licensing Technology Overview Siemens PLM Software has developed a common license technology in response to customer requests for consistent licensing and a common license file as well as the Siemens
Common Licensing Technology Overview Siemens PLM Software has developed a common license technology in response to customer requests for consistent licensing and a common license file as well as the Siemens
Part-Based Recognition
 Part-Based Recognition Benedict Brown CS597D, Fall 2003 Princeton University CS 597D, Part-Based Recognition p. 1/32 Introduction Many objects are made up of parts It s presumably easier to identify simple
Part-Based Recognition Benedict Brown CS597D, Fall 2003 Princeton University CS 597D, Part-Based Recognition p. 1/32 Introduction Many objects are made up of parts It s presumably easier to identify simple
Face detection is a process of localizing and extracting the face region from the
 Chapter 4 FACE NORMALIZATION 4.1 INTRODUCTION Face detection is a process of localizing and extracting the face region from the background. The detected face varies in rotation, brightness, size, etc.
Chapter 4 FACE NORMALIZATION 4.1 INTRODUCTION Face detection is a process of localizing and extracting the face region from the background. The detected face varies in rotation, brightness, size, etc.
ON-BOARDING TOOL USER GUIDE. HKEx Orion Market Data Platform Securities Market & Index Datafeed Products Mainland Market Data Hub (MMDH)
 ON-BOARDING TOOL USER GUIDE HKEx Orion Market Data Platform Securities Market & Index Datafeed Products Mainland Market Data Hub (MMDH) Version 1.1 27 May 2013 Document History DOCUMENT HISTORY Distribution
ON-BOARDING TOOL USER GUIDE HKEx Orion Market Data Platform Securities Market & Index Datafeed Products Mainland Market Data Hub (MMDH) Version 1.1 27 May 2013 Document History DOCUMENT HISTORY Distribution
1 Symmetries of regular polyhedra
 1230, notes 5 1 Symmetries of regular polyhedra Symmetry groups Recall: Group axioms: Suppose that (G, ) is a group and a, b, c are elements of G. Then (i) a b G (ii) (a b) c = a (b c) (iii) There is an
1230, notes 5 1 Symmetries of regular polyhedra Symmetry groups Recall: Group axioms: Suppose that (G, ) is a group and a, b, c are elements of G. Then (i) a b G (ii) (a b) c = a (b c) (iii) There is an
Online EFFECTIVE AS OF JANUARY 2013
 2013 A and C Session Start Dates (A-B Quarter Sequence*) 2013 B and D Session Start Dates (B-A Quarter Sequence*) Quarter 5 2012 1205A&C Begins November 5, 2012 1205A Ends December 9, 2012 Session Break
2013 A and C Session Start Dates (A-B Quarter Sequence*) 2013 B and D Session Start Dates (B-A Quarter Sequence*) Quarter 5 2012 1205A&C Begins November 5, 2012 1205A Ends December 9, 2012 Session Break
Data Mining mit der JMSL Numerical Library for Java Applications
 Data Mining mit der JMSL Numerical Library for Java Applications Stefan Sineux 8. Java Forum Stuttgart 07.07.2005 Agenda Visual Numerics JMSL TM Numerical Library Neuronale Netze (Hintergrund) Demos Neuronale
Data Mining mit der JMSL Numerical Library for Java Applications Stefan Sineux 8. Java Forum Stuttgart 07.07.2005 Agenda Visual Numerics JMSL TM Numerical Library Neuronale Netze (Hintergrund) Demos Neuronale
T360 Barbecue. Assembly Manual. 85-3052-6 (G30531) Propane 1 YEAR LIMITED WARRANTY
 T360 Barbecue Assembly Manual 85-3052-6 (G30531) Propane 1 YEAR LIMITED WARRANTY READ AND SAVE MANUAL FOR FUTURE REFERENCE. If pre-assembled, leave this manual with unit for consumer s future reference.
T360 Barbecue Assembly Manual 85-3052-6 (G30531) Propane 1 YEAR LIMITED WARRANTY READ AND SAVE MANUAL FOR FUTURE REFERENCE. If pre-assembled, leave this manual with unit for consumer s future reference.
More Local Structure Information for Make-Model Recognition
 More Local Structure Information for Make-Model Recognition David Anthony Torres Dept. of Computer Science The University of California at San Diego La Jolla, CA 9093 Abstract An object classification
More Local Structure Information for Make-Model Recognition David Anthony Torres Dept. of Computer Science The University of California at San Diego La Jolla, CA 9093 Abstract An object classification
Recognizing Cats and Dogs with Shape and Appearance based Models. Group Member: Chu Wang, Landu Jiang
 Recognizing Cats and Dogs with Shape and Appearance based Models Group Member: Chu Wang, Landu Jiang Abstract Recognizing cats and dogs from images is a challenging competition raised by Kaggle platform
Recognizing Cats and Dogs with Shape and Appearance based Models Group Member: Chu Wang, Landu Jiang Abstract Recognizing cats and dogs from images is a challenging competition raised by Kaggle platform
Appendix C: Keyboard Scan Codes
 Thi d t t d ith F M k 4 0 2 Appendix C: Keyboard Scan Codes Table 90: PC Keyboard Scan Codes (in hex) Key Down Up Key Down Up Key Down Up Key Down Up Esc 1 81 [ { 1A 9A, < 33 B3 center 4C CC 1! 2 82 ]
Thi d t t d ith F M k 4 0 2 Appendix C: Keyboard Scan Codes Table 90: PC Keyboard Scan Codes (in hex) Key Down Up Key Down Up Key Down Up Key Down Up Esc 1 81 [ { 1A 9A, < 33 B3 center 4C CC 1! 2 82 ]
COMPUTING CLOUD MOTION USING A CORRELATION RELAXATION ALGORITHM Improving Estimation by Exploiting Problem Knowledge Q. X. WU
 COMPUTING CLOUD MOTION USING A CORRELATION RELAXATION ALGORITHM Improving Estimation by Exploiting Problem Knowledge Q. X. WU Image Processing Group, Landcare Research New Zealand P.O. Box 38491, Wellington
COMPUTING CLOUD MOTION USING A CORRELATION RELAXATION ALGORITHM Improving Estimation by Exploiting Problem Knowledge Q. X. WU Image Processing Group, Landcare Research New Zealand P.O. Box 38491, Wellington
Feature Tracking and Optical Flow
 02/09/12 Feature Tracking and Optical Flow Computer Vision CS 543 / ECE 549 University of Illinois Derek Hoiem Many slides adapted from Lana Lazebnik, Silvio Saverse, who in turn adapted slides from Steve
02/09/12 Feature Tracking and Optical Flow Computer Vision CS 543 / ECE 549 University of Illinois Derek Hoiem Many slides adapted from Lana Lazebnik, Silvio Saverse, who in turn adapted slides from Steve
Identification algorithms for hybrid systems
 Identification algorithms for hybrid systems Giancarlo Ferrari-Trecate Modeling paradigms Chemistry White box Thermodynamics System Mechanics... Drawbacks: Parameter values of components must be known
Identification algorithms for hybrid systems Giancarlo Ferrari-Trecate Modeling paradigms Chemistry White box Thermodynamics System Mechanics... Drawbacks: Parameter values of components must be known
Determining optimal window size for texture feature extraction methods
 IX Spanish Symposium on Pattern Recognition and Image Analysis, Castellon, Spain, May 2001, vol.2, 237-242, ISBN: 84-8021-351-5. Determining optimal window size for texture feature extraction methods Domènec
IX Spanish Symposium on Pattern Recognition and Image Analysis, Castellon, Spain, May 2001, vol.2, 237-242, ISBN: 84-8021-351-5. Determining optimal window size for texture feature extraction methods Domènec
Masters research projects. 1. Adapting Granger causality for use on EEG data.
 Masters research projects 1. Adapting Granger causality for use on EEG data. Background. Granger causality is a concept introduced in the field of economy to determine which variables influence, or cause,
Masters research projects 1. Adapting Granger causality for use on EEG data. Background. Granger causality is a concept introduced in the field of economy to determine which variables influence, or cause,
What is Visualization? Information Visualization An Overview. Information Visualization. Definitions
 What is Visualization? Information Visualization An Overview Jonathan I. Maletic, Ph.D. Computer Science Kent State University Visualize/Visualization: To form a mental image or vision of [some
What is Visualization? Information Visualization An Overview Jonathan I. Maletic, Ph.D. Computer Science Kent State University Visualize/Visualization: To form a mental image or vision of [some
Montgomery GI Bill Selected Reserve (MGIB-SR) Command/Servicing Personnel Office Review
 Overview Montgomery GI Bill Selected Reserve (MGIB-SR) Command/Servicing Personnel Office Review Introduction This transaction is used to record a Reserve member s Montgomery GI Bill-SR (MGIB-SR) eligibility
Overview Montgomery GI Bill Selected Reserve (MGIB-SR) Command/Servicing Personnel Office Review Introduction This transaction is used to record a Reserve member s Montgomery GI Bill-SR (MGIB-SR) eligibility
SUCCESSFUL PREDICTION OF HORSE RACING RESULTS USING A NEURAL NETWORK
 SUCCESSFUL PREDICTION OF HORSE RACING RESULTS USING A NEURAL NETWORK N M Allinson and D Merritt 1 Introduction This contribution has two main sections. The first discusses some aspects of multilayer perceptrons,
SUCCESSFUL PREDICTION OF HORSE RACING RESULTS USING A NEURAL NETWORK N M Allinson and D Merritt 1 Introduction This contribution has two main sections. The first discusses some aspects of multilayer perceptrons,
Acceptance Page 2. Revision History 3. Introduction 14. Control Categories 15. Scope 15. General Requirements 15
 Acceptance Page 2 Revision History 3 Introduction 14 Control Categories 15 Scope 15 General Requirements 15 Control Category: 0.0 Information Security Management Program 17 Objective Name: 0.01 Information
Acceptance Page 2 Revision History 3 Introduction 14 Control Categories 15 Scope 15 General Requirements 15 Control Category: 0.0 Information Security Management Program 17 Objective Name: 0.01 Information
Section 8.8. 1. The given line has equations. x = 3 + t(13 3) = 3 + 10t, y = 2 + t(3 + 2) = 2 + 5t, z = 7 + t( 8 7) = 7 15t.
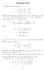 . The given line has equations Section 8.8 x + t( ) + 0t, y + t( + ) + t, z 7 + t( 8 7) 7 t. The line meets the plane y 0 in the point (x, 0, z), where 0 + t, or t /. The corresponding values for x and
. The given line has equations Section 8.8 x + t( ) + 0t, y + t( + ) + t, z 7 + t( 8 7) 7 t. The line meets the plane y 0 in the point (x, 0, z), where 0 + t, or t /. The corresponding values for x and
PCL PC -8. PCL Symbol Se t: 12G Unicode glyph correspondence table s. Contact:help@redtitan.com http://pcl.to
 PCL PC-8 Page 1 of 5 PCL Symbol Se t: 12G Unicode glyph correspondence table s. Contact:help@redtitan.com http://pcl.to -- -- -- -- $90 U00C9 Ê Uppercase e acute $21 U0021 Ë Exclamation $91 U00E6 Ì Lowerc
PCL PC-8 Page 1 of 5 PCL Symbol Se t: 12G Unicode glyph correspondence table s. Contact:help@redtitan.com http://pcl.to -- -- -- -- $90 U00C9 Ê Uppercase e acute $21 U0021 Ë Exclamation $91 U00E6 Ì Lowerc
The colors in the Federal Standard set have no official names, just five-digit numbers. Any names given below are generic.
 Federal Standard 595 Paint Spec Information The following information is made available to our customers as a reference point only. See below for how to request the 595 specification from the US Government.
Federal Standard 595 Paint Spec Information The following information is made available to our customers as a reference point only. See below for how to request the 595 specification from the US Government.
Information visualization examples
 Information visualization examples 350102: GenICT II 37 Information visualization examples 350102: GenICT II 38 Information visualization examples 350102: GenICT II 39 Information visualization examples
Information visualization examples 350102: GenICT II 37 Information visualization examples 350102: GenICT II 38 Information visualization examples 350102: GenICT II 39 Information visualization examples
Image Segmentation and Registration
 Image Segmentation and Registration Dr. Christine Tanner (tanner@vision.ee.ethz.ch) Computer Vision Laboratory, ETH Zürich Dr. Verena Kaynig, Machine Learning Laboratory, ETH Zürich Outline Segmentation
Image Segmentation and Registration Dr. Christine Tanner (tanner@vision.ee.ethz.ch) Computer Vision Laboratory, ETH Zürich Dr. Verena Kaynig, Machine Learning Laboratory, ETH Zürich Outline Segmentation
Security of Online Social Networks
 Security of Online Social Networks Lehrstuhl IT-Sicherheitsmanagment Universität Siegen April 19, 2012 Lehrstuhl IT-Sicherheitsmanagment 1/36 Overview Lesson 02 Authentication Web Login Implementation
Security of Online Social Networks Lehrstuhl IT-Sicherheitsmanagment Universität Siegen April 19, 2012 Lehrstuhl IT-Sicherheitsmanagment 1/36 Overview Lesson 02 Authentication Web Login Implementation
US Code (Unofficial compilation from the Legal Information Institute)
 US Code (Unofficial compilation from the Legal Information Institute) TITLE 26 - INTERNAL REVENUE CODE Subtitle D - Miscellaneous Excise Taxes CHAPTER 43 QUALIFIED PENSION, ETC., PLANS Please Note: This
US Code (Unofficial compilation from the Legal Information Institute) TITLE 26 - INTERNAL REVENUE CODE Subtitle D - Miscellaneous Excise Taxes CHAPTER 43 QUALIFIED PENSION, ETC., PLANS Please Note: This
Public Key Infrastructure. Certificates Standard X509v3
 Public Key Infrastructure Certificates Standard X509v3 Certificate and Certification Authority Problem. Make a subject s public key available to others so that they can verifiy the key authenticity and
Public Key Infrastructure Certificates Standard X509v3 Certificate and Certification Authority Problem. Make a subject s public key available to others so that they can verifiy the key authenticity and
DIGITAL IMAGE PROCESSING AND ANALYSIS
 DIGITAL IMAGE PROCESSING AND ANALYSIS Human and Computer Vision Applications with CVIPtools SECOND EDITION SCOTT E UMBAUGH Uffi\ CRC Press Taylor &. Francis Group Boca Raton London New York CRC Press is
DIGITAL IMAGE PROCESSING AND ANALYSIS Human and Computer Vision Applications with CVIPtools SECOND EDITION SCOTT E UMBAUGH Uffi\ CRC Press Taylor &. Francis Group Boca Raton London New York CRC Press is
WATER BODY EXTRACTION FROM MULTI SPECTRAL IMAGE BY SPECTRAL PATTERN ANALYSIS
 WATER BODY EXTRACTION FROM MULTI SPECTRAL IMAGE BY SPECTRAL PATTERN ANALYSIS Nguyen Dinh Duong Department of Environmental Information Study and Analysis, Institute of Geography, 18 Hoang Quoc Viet Rd.,
WATER BODY EXTRACTION FROM MULTI SPECTRAL IMAGE BY SPECTRAL PATTERN ANALYSIS Nguyen Dinh Duong Department of Environmental Information Study and Analysis, Institute of Geography, 18 Hoang Quoc Viet Rd.,
Draft Martin Doerr ICS-FORTH, Heraklion, Crete Oct 4, 2001
 A comparison of the OpenGIS TM Abstract Specification with the CIDOC CRM 3.2 Draft Martin Doerr ICS-FORTH, Heraklion, Crete Oct 4, 2001 1 Introduction This Mapping has the purpose to identify, if the OpenGIS
A comparison of the OpenGIS TM Abstract Specification with the CIDOC CRM 3.2 Draft Martin Doerr ICS-FORTH, Heraklion, Crete Oct 4, 2001 1 Introduction This Mapping has the purpose to identify, if the OpenGIS
Session 5 Dissections and Proof
 Key Terms for This Session Session 5 Dissections and Proof Previously Introduced midline parallelogram quadrilateral rectangle side-angle-side (SAS) congruence square trapezoid vertex New in This Session
Key Terms for This Session Session 5 Dissections and Proof Previously Introduced midline parallelogram quadrilateral rectangle side-angle-side (SAS) congruence square trapezoid vertex New in This Session
Research On The Classification Of High Resolution Image Based On Object-oriented And Class Rule
 Research On The Classification Of High Resolution Image Based On Object-oriented And Class Rule Li Chaokui a,b, Fang Wen a,b, Dong Xiaojiao a,b a National-Local Joint Engineering Laboratory of Geo-Spatial
Research On The Classification Of High Resolution Image Based On Object-oriented And Class Rule Li Chaokui a,b, Fang Wen a,b, Dong Xiaojiao a,b a National-Local Joint Engineering Laboratory of Geo-Spatial
ASV Scan Report Vulnerability Details PRESTO BIZ
 ASV Scan Report Vulnerability Details PRESTO BIZ Scan Results Executive Summary PCI Compliance: Passing Scan Target: secure.prestomart.com Scan ID: 6060285 Start: 2015-03-14 05:00:01 Finish: 2015-03-14
ASV Scan Report Vulnerability Details PRESTO BIZ Scan Results Executive Summary PCI Compliance: Passing Scan Target: secure.prestomart.com Scan ID: 6060285 Start: 2015-03-14 05:00:01 Finish: 2015-03-14
Color Segmentation Based Depth Image Filtering
 Color Segmentation Based Depth Image Filtering Michael Schmeing and Xiaoyi Jiang Department of Computer Science, University of Münster Einsteinstraße 62, 48149 Münster, Germany, {m.schmeing xjiang}@uni-muenster.de
Color Segmentation Based Depth Image Filtering Michael Schmeing and Xiaoyi Jiang Department of Computer Science, University of Münster Einsteinstraße 62, 48149 Münster, Germany, {m.schmeing xjiang}@uni-muenster.de
Gameover Zeus Bad Guys and Backends
 Gameover Zeus Bad Guys and Backends Elliott Peterson, Michael Sandee, Tillmann Werner August 5, 2015 Cui Honorem, Honorem Dr. Brett Stone-Gross, Dell SecureWorks Frank Ruiz, Fox-IT Dr. Christian Rossow,
Gameover Zeus Bad Guys and Backends Elliott Peterson, Michael Sandee, Tillmann Werner August 5, 2015 Cui Honorem, Honorem Dr. Brett Stone-Gross, Dell SecureWorks Frank Ruiz, Fox-IT Dr. Christian Rossow,
Measuring Line Edge Roughness: Fluctuations in Uncertainty
 Tutor6.doc: Version 5/6/08 T h e L i t h o g r a p h y E x p e r t (August 008) Measuring Line Edge Roughness: Fluctuations in Uncertainty Line edge roughness () is the deviation of a feature edge (as
Tutor6.doc: Version 5/6/08 T h e L i t h o g r a p h y E x p e r t (August 008) Measuring Line Edge Roughness: Fluctuations in Uncertainty Line edge roughness () is the deviation of a feature edge (as
Euler Vector: A Combinatorial Signature for Gray-Tone Images
 Euler Vector: A Combinatorial Signature for Gray-Tone Images Arijit Bishnu, Bhargab B. Bhattacharya y, Malay K. Kundu, C. A. Murthy fbishnu t, bhargab, malay, murthyg@isical.ac.in Indian Statistical Institute,
Euler Vector: A Combinatorial Signature for Gray-Tone Images Arijit Bishnu, Bhargab B. Bhattacharya y, Malay K. Kundu, C. A. Murthy fbishnu t, bhargab, malay, murthyg@isical.ac.in Indian Statistical Institute,
Edge tracking for motion segmentation and depth ordering
 Edge tracking for motion segmentation and depth ordering P. Smith, T. Drummond and R. Cipolla Department of Engineering University of Cambridge Cambridge CB2 1PZ,UK {pas1001 twd20 cipolla}@eng.cam.ac.uk
Edge tracking for motion segmentation and depth ordering P. Smith, T. Drummond and R. Cipolla Department of Engineering University of Cambridge Cambridge CB2 1PZ,UK {pas1001 twd20 cipolla}@eng.cam.ac.uk
INCIDENCE-BETWEENNESS GEOMETRY
 INCIDENCE-BETWEENNESS GEOMETRY MATH 410, CSUSM. SPRING 2008. PROFESSOR AITKEN This document covers the geometry that can be developed with just the axioms related to incidence and betweenness. The full
INCIDENCE-BETWEENNESS GEOMETRY MATH 410, CSUSM. SPRING 2008. PROFESSOR AITKEN This document covers the geometry that can be developed with just the axioms related to incidence and betweenness. The full
 Tracking Moving Objects In Video Sequences Yiwei Wang, Robert E. Van Dyck, and John F. Doherty Department of Electrical Engineering The Pennsylvania State University University Park, PA16802 Abstract{Object
Tracking Moving Objects In Video Sequences Yiwei Wang, Robert E. Van Dyck, and John F. Doherty Department of Electrical Engineering The Pennsylvania State University University Park, PA16802 Abstract{Object
Modbus Register Map: Environmental Management System and Environmental Monitoring Unit 990-0589A 02/2005
 // Version 102 //Absolute Starting Register Number, (Hexadecimal) Modbus Register Map: Environmental Management System and Environmental Monitoring Unit 990-0589A 02/2005 Absolute Starting Register Number,
// Version 102 //Absolute Starting Register Number, (Hexadecimal) Modbus Register Map: Environmental Management System and Environmental Monitoring Unit 990-0589A 02/2005 Absolute Starting Register Number,
Big Data Text Mining and Visualization. Anton Heijs
 Copyright 2007 by Treparel Information Solutions BV. This report nor any part of it may be copied, circulated, quoted without prior written approval from Treparel7 Treparel Information Solutions BV Delftechpark
Copyright 2007 by Treparel Information Solutions BV. This report nor any part of it may be copied, circulated, quoted without prior written approval from Treparel7 Treparel Information Solutions BV Delftechpark
EMDX3 Multifunction meter Cat No. 146 69 ModbusTable LGR EN v1.01.xls
 GENERAL MODBUS TABLE ORGANIZATION Starting of the Starting of the Group s Group s System Version (Release) System Version (Build) Group Name (Text) Group Code Group Complexity Group Version 50512 C550
GENERAL MODBUS TABLE ORGANIZATION Starting of the Starting of the Group s Group s System Version (Release) System Version (Build) Group Name (Text) Group Code Group Complexity Group Version 50512 C550
Introduction to Machine Learning and Data Mining. Prof. Dr. Igor Trajkovski trajkovski@nyus.edu.mk
 Introduction to Machine Learning and Data Mining Prof. Dr. Igor Trakovski trakovski@nyus.edu.mk Neural Networks 2 Neural Networks Analogy to biological neural systems, the most robust learning systems
Introduction to Machine Learning and Data Mining Prof. Dr. Igor Trakovski trakovski@nyus.edu.mk Neural Networks 2 Neural Networks Analogy to biological neural systems, the most robust learning systems
Multiscale Object-Based Classification of Satellite Images Merging Multispectral Information with Panchromatic Textural Features
 Remote Sensing and Geoinformation Lena Halounová, Editor not only for Scientific Cooperation EARSeL, 2011 Multiscale Object-Based Classification of Satellite Images Merging Multispectral Information with
Remote Sensing and Geoinformation Lena Halounová, Editor not only for Scientific Cooperation EARSeL, 2011 Multiscale Object-Based Classification of Satellite Images Merging Multispectral Information with
DISPLAYING SMALL SURFACE FEATURES WITH A FORCE FEEDBACK DEVICE IN A DENTAL TRAINING SIMULATOR
 PROCEEDINGS of the HUMAN FACTORS AND ERGONOMICS SOCIETY 49th ANNUAL MEETING 2005 2235 DISPLAYING SMALL SURFACE FEATURES WITH A FORCE FEEDBACK DEVICE IN A DENTAL TRAINING SIMULATOR Geb W. Thomas and Li
PROCEEDINGS of the HUMAN FACTORS AND ERGONOMICS SOCIETY 49th ANNUAL MEETING 2005 2235 DISPLAYING SMALL SURFACE FEATURES WITH A FORCE FEEDBACK DEVICE IN A DENTAL TRAINING SIMULATOR Geb W. Thomas and Li
