CYBERSITTER NAME. LLC/Solid Oak Software. Company. Version Client. Type of product. Computer. Devices supported
|
|
|
- Abner Garrison
- 10 years ago
- Views:
Transcription
1 NAME CYBERSITTER Company LLC/Solid Oak Software Version Type of product Devices supported Operating systems Client Computer Windows Vista (32/64 Bits) Windows 7 (32/64 Bits) Windows XP Windows 2000 Price* Up to 3 computers 1 year 30 Up to 3 computers 3 years 60 Up to 5 computers 1 year 38 Up to 5 computers 3 years 75 Language of interface English 12 years old users: 18/21 (points 1,43 out of 4) GLOBAL RANKING 13 years old users: 18/21 (points 1,54 out of 4) *Prices might change according to the latest company offers
2 FUNCTIONALITY The Internet Parental Control is able both to customize the webpage filtering and to manage the use of some applications. The parent can indicate specific URLs to be blocked (creation of a black list) or allowed (creation of a white list) by the filter despite the selected categories to be blocked/allowed. It is possible to block Streaming, Skype, MSN and P2P and applications by blocking the related software installed on the PC. The remote monitoring is possible if the parents ask for a specific add-in. It is possible to choose the page where users are redirected when a page is blocked. FUNCTIONALITY SCORE: 2,4 OUT OF 4 POINTS EFFECTIVENESS The overall effectiveness score is fair on adult content and very weak on other harmful content. There is no major difference in effectiveness between teenagers and children. There is no major difference in effectiveness between web and web 2.0. There is no major difference in effectiveness among the different languages. Effectiveness score with adult content filtering for 12 years old user: 2,2 Effectiveness score with other harmful content filtering for 12 years old user: 0,0 Effectiveness score with adult content filtering for 13 years old user: 2,4 Effectiveness score with other harmful content filtering for 13 years old user: 0,0 OVERALL SCORE FOR EFFECTIVENESS FOR 12 YEARS OLD USER: 1,1 OUT OF 4 POINTS OVERALL SCORE FOR EFFECTIVENESS FOR 13 YEARS OLD USER: 1,2 OUT OF 4 POINTS
3 USABILITY Installation of the tool: The installation process is mostly comprehensible, but the installation file name is not optimal. The installer does not provide advanced options and cannot be influenced with regard to kind or amount of information. The process is generally consistent, but it does not fully meet users' expectations as, for example, the installation button is not labelled adequately. Configuration of the tool: The configuration process is generally comprehensible and overall easy to learn. The process contains some inconsistencies and it does not always meet users' expectations. There are barely any options to individualise or influence the process. The design could be optimised to match the common standard. Usage of the tool: When a website has been blocked, the tool provides a button which leads the child to unknown 'child-friendly' websites without any further explanation. The alert message is child friendly and can be a little customised. The reporting is difficult to understand and uncomfortable to read. Usability of the installation process: 2,53 Usability of the configuration process: 2,45 Usability of the usage of the product: 1,83 OVERALL SCORE FOR USABILITY: 2,28 OUT OF 4 POINTS SECURITY The software allowed us to access some blacklisted webpages through the Google translation tool. It is also possible to by-pass the tool using IP adresses instead of URLs. No password for administration access is created by default. The parenthas to do it after having installed the software. OVERALL SCORE FOR SECURITY: 1 OUT OF 4 POINTS
4 DETAILED FUNCTIONALITY FICHE AREA OF NEED FUNCTIONALITY SPECIFIC ISSUE ASSESSMENT MGMNT FILTERING CUSTOMIZATION Management of users profile Monitoring Topics Urls White lists Create several profiles Remote access Customisation of filtering topics Restrict browsing to a white list Default white list Modification OR Creation Modification Creation Urls Black lists Creation of user s own black list Default black list KEYWORDS Keywords Default white list Creation of a user s black list Creation of a user s white list TIME BLOCKING MESSAGE Time limit settings Type Set a specific timeframe or web access duration Ask for unblocking to parents Redirect to safe resources Web Block access Monitor access Safe Search Availability Social Networks Block access Monitor usage Personal data provision Block Block the access Application - USAGE RESTRICTION Streaming P2P application Monitor the access to the application Block the application Monitor downloads Web - Block (chat, VoIP, Video-chat) Skype application Monitor the access Prevent from new contact Block the application MSN Monitor the access Prevent from new contact Block Client and/or web
5 DETAILED SECURITY FINDINGS The Tool prevents the user from by-passing the filter by: / Using the IP address instead of the URL Using an alternative browser Changing time and date settings* Disabling or uninstalling the software without a password* Closing the filtering tool trough the Task Manager Using a proxy instead of a direct connection to the Internet Accessing the web-pages through the Google Cache Reaching a website through translation sites Renaming a blocked application Using Safe Mode Changing the port of Peer-to-Peer application *As managed directly by the tool and not by the device. DETAILED USABILITY FINDINGS / I: installation in 3 steps or less I: choice of installation for beginners or advanced users C: different degrees of strength for the filtering C: different content criteria for the filtering C: option to transfer filter configurations between target users C: option to transfer filter configurations between devices C: altogether comprehensible configuration C: altogether in conformity with user expectations C: altogether easy to learn U: alert message in a child friendly language U: option to customise the reaction in case of blocking U: altogether easily operable and comprehensible reporting
MOBICIP NAME. Mobicip. Company. Version 1.3.0.12. Client. Type of product. Computer. Devices supported. Linux Ubuntu Windows 7 (Tested on Windows)
 NAME MOBICIP Company Mobicip Version 1.3.0.12 Type of product Devices supported Operating systems Client Computer Linux Ubuntu Windows 7 (Tested on Windows) Price* 1 year - 1 license: 7,75 Language of
NAME MOBICIP Company Mobicip Version 1.3.0.12 Type of product Devices supported Operating systems Client Computer Linux Ubuntu Windows 7 (Tested on Windows) Price* 1 year - 1 license: 7,75 Language of
User's voice OPTENET WEBFILTER PC. Comprehensibility: Test user did not provide any comments. Look and Feel: Time to install and configure: 45 minutes
 NAME OPTENET WEBFILTER PC Company Optenet S.A. Version 10.09.69 Type of product Devices supported Operating systems Client Computer Windows XP Sp2 Windows Vista (32 and 64 bits) Windows 7 (32 and 64 bits)
NAME OPTENET WEBFILTER PC Company Optenet S.A. Version 10.09.69 Type of product Devices supported Operating systems Client Computer Windows XP Sp2 Windows Vista (32 and 64 bits) Windows 7 (32 and 64 bits)
How To Use Windows Live Family Safety On Windows 7 (32 Bit) And Windows Live Safety (64 Bit) On A Pc Or Mac Or Ipad (32)
 NAME Windows Live Family Safety Company Microsoft Version 2012 Type of product Devices supported Operating systems Price* Client Computer Windows 7 (32 or 64 bit edition) Windows Vista Service Pack 2 Windows
NAME Windows Live Family Safety Company Microsoft Version 2012 Type of product Devices supported Operating systems Price* Client Computer Windows 7 (32 or 64 bit edition) Windows Vista Service Pack 2 Windows
User's voice NET NANNY. Quite simple to install and configure. Improve messages and possible reactions when a page is blocked. Comprehensibility:
 NAME NET NANNY Company Content Watch Version 6.5.13.1 Type of product Devices supported Operating systems Client Computer Microsoft Windows 7 (32/64 bit) Microsoft Windows Vista (32/64 bit) Microsoft Windows,
NAME NET NANNY Company Content Watch Version 6.5.13.1 Type of product Devices supported Operating systems Client Computer Microsoft Windows 7 (32/64 bit) Microsoft Windows Vista (32/64 bit) Microsoft Windows,
Comprehensibility: Look and Feel: Time to install and configure: 130 minutes NAME PROFIL PARENTAL FILTER 2. Profil Technology. Company. Version 2.4.
 NAME PROFIL PARENTAL FILTER 2 Company Profil Technology Version 2.4.0 Type of product Devices supported Operating systems Client Computer Windows 7 (32/64 bit) Windows XP (32/64 bit) Windows Vista (32/64
NAME PROFIL PARENTAL FILTER 2 Company Profil Technology Version 2.4.0 Type of product Devices supported Operating systems Client Computer Windows 7 (32/64 bit) Windows XP (32/64 bit) Windows Vista (32/64
User's voice. Safe Eyes. User 1: I was surprised how the tool was easy to install and configure. Comprehensibility:
 NAME Safe Eyes Company McAfee Version 6.0.244 Type of product Devices supported Operating systems Client Computer Windows XP Windows 7 Vista Mac OS (with some limitations on functionalities) Price* 1 year,
NAME Safe Eyes Company McAfee Version 6.0.244 Type of product Devices supported Operating systems Client Computer Windows XP Windows 7 Vista Mac OS (with some limitations on functionalities) Price* 1 year,
Puresight Technologies Ltd. Arabic, Dutch, English, German, Greece, Russian. 12 years old users: 1/21 (points 2,67 out of 4)
 NAME PURESIGHT OWL Company Puresight Technologies Ltd. Version 2012.3.9081 Type of product Devices supported Operating systems Client Computer Windows Vista (32/64 bit) Windows XP (32/64 bit) Windows 7
NAME PURESIGHT OWL Company Puresight Technologies Ltd. Version 2012.3.9081 Type of product Devices supported Operating systems Client Computer Windows Vista (32/64 bit) Windows XP (32/64 bit) Windows 7
Configuring Your Gateman Proxy Server
 Configuring Your Gateman Proxy Server A proxy server acts as an intermediary between a workstation users and the Internet to ensure security, administrative control, distribution of bandwidth and caching
Configuring Your Gateman Proxy Server A proxy server acts as an intermediary between a workstation users and the Internet to ensure security, administrative control, distribution of bandwidth and caching
Safe internet for business use: Getting Started Guide
 Safe internet for business use: Getting Started Guide Table of Contents 1. Preface 1 2. Before You Install 2 2.1 Disabling Firewalls 2 2.2 About Accelerators 3 3. About Profiles 4 4. Installation and Initial
Safe internet for business use: Getting Started Guide Table of Contents 1. Preface 1 2. Before You Install 2 2.1 Disabling Firewalls 2 2.2 About Accelerators 3 3. About Profiles 4 4. Installation and Initial
Safe internet: Getting Started Guide
 Safe internet: Getting Started Guide Table of Contents 1. Preface 1 2. Before You Install 2 2.1 Disabling Firewalls 2 2.2 About Accelerators 3 3. About Profiles 4 4. Installation and Initial Configuration
Safe internet: Getting Started Guide Table of Contents 1. Preface 1 2. Before You Install 2 2.1 Disabling Firewalls 2 2.2 About Accelerators 3 3. About Profiles 4 4. Installation and Initial Configuration
OPTENET Security Suite / OPTENET PC Web Filter
 OPTENET Security Suite / OPTENET PC Web Filter Version 11.01 User Guide (rev 1.7) COPYRIGHT No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated
OPTENET Security Suite / OPTENET PC Web Filter Version 11.01 User Guide (rev 1.7) COPYRIGHT No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated
SecuraLive ULTIMATE SECURITY
 SecuraLive ULTIMATE SECURITY Home Edition for Windows USER GUIDE SecuraLive ULTIMATE SECURITY USER MANUAL Introduction: Welcome to SecuraLive Ultimate Security Home Edition. SecuraLive Ultimate Security
SecuraLive ULTIMATE SECURITY Home Edition for Windows USER GUIDE SecuraLive ULTIMATE SECURITY USER MANUAL Introduction: Welcome to SecuraLive Ultimate Security Home Edition. SecuraLive Ultimate Security
Cyclope Internet Filtering Proxy
 Cyclope Internet Filtering Proxy - Installation Guide - Cyclope-Series - 2010 - Table of contents 1. Overview - 3-2. Installation - 4-2.1. System requirements - 4-2.2. Cyclope Internet Filtering Proxy
Cyclope Internet Filtering Proxy - Installation Guide - Cyclope-Series - 2010 - Table of contents 1. Overview - 3-2. Installation - 4-2.1. System requirements - 4-2.2. Cyclope Internet Filtering Proxy
Release Notes for Websense Web Endpoint (32- and 64-bit OS)
 Release Notes for Websense Web Endpoint (32- and 64-bit OS) Updated: 8-Feb-2013 Applies To: Websense Cloud Web Security solutions Use the Release Notes to learn about: What s new in Websense Web Endpoint?
Release Notes for Websense Web Endpoint (32- and 64-bit OS) Updated: 8-Feb-2013 Applies To: Websense Cloud Web Security solutions Use the Release Notes to learn about: What s new in Websense Web Endpoint?
Server Requirements: Microsoft Windows Small Business Server 2011 Essentials*
 The Intel Small Business Manageability Add-in (Intel SBMA) for Windows Small Business Server 2011 Essentials allows you to access and manage the client PCs connected to your Windows Small Business Server
The Intel Small Business Manageability Add-in (Intel SBMA) for Windows Small Business Server 2011 Essentials allows you to access and manage the client PCs connected to your Windows Small Business Server
ProperSync 1.3 User Manual. Rev 1.2
 ProperSync 1.3 User Manual Rev 1.2 Contents Overview of ProperSync... 3 What is ProperSync... 3 What s new in ProperSync 1.3... 3 Getting Started... 4 Installing ProperSync... 4 Activating ProperSync...
ProperSync 1.3 User Manual Rev 1.2 Contents Overview of ProperSync... 3 What is ProperSync... 3 What s new in ProperSync 1.3... 3 Getting Started... 4 Installing ProperSync... 4 Activating ProperSync...
Thirtyseven4 Endpoint Security (EPS) Upgrading Instructions
 Thirtyseven4 Endpoint Security (EPS) Upgrading Instructions Disclaimer: As with any software upgrade or new release, it is strongly encouraged to fully test the new build within your environment prior
Thirtyseven4 Endpoint Security (EPS) Upgrading Instructions Disclaimer: As with any software upgrade or new release, it is strongly encouraged to fully test the new build within your environment prior
M86 Web Filter USER GUIDE for M86 Mobile Security Client. Software Version: 5.0.00 Document Version: 02.01.12
 M86 Web Filter USER GUIDE for M86 Mobile Security Client Software Version: 5.0.00 Document Version: 02.01.12 M86 WEB FILTER USER GUIDE FOR M86 MOBILE SECURITY CLIENT 2012 M86 Security All rights reserved.
M86 Web Filter USER GUIDE for M86 Mobile Security Client Software Version: 5.0.00 Document Version: 02.01.12 M86 WEB FILTER USER GUIDE FOR M86 MOBILE SECURITY CLIENT 2012 M86 Security All rights reserved.
BROWSER AND SYSTEM REQUIREMENTS
 BROWSER AND SYSTEM REQUIREMENTS Minimum and Recommended System Requirements To ensure that CSIU Student Information System performs seamlessly, please adhere to the requirements listed in the chart below:
BROWSER AND SYSTEM REQUIREMENTS Minimum and Recommended System Requirements To ensure that CSIU Student Information System performs seamlessly, please adhere to the requirements listed in the chart below:
Home Internet Filter User Guide
 Home Internet Filter User Guide TABLE OF CONTENTS About Home Internet Filter... 2 How Home Internet Filter help you?... 2 Setting up the Residential Gateway and accessing to SingTel Home Internet Filter
Home Internet Filter User Guide TABLE OF CONTENTS About Home Internet Filter... 2 How Home Internet Filter help you?... 2 Setting up the Residential Gateway and accessing to SingTel Home Internet Filter
PREDICTIVE DIALER AND REMOTE AGENT SETUP GUIDE
 PREDICTIVE DIALER AND REMOTE AGENT SETUP GUIDE RELEASE 7 VOICENT AGENTDIALER TM TABLE OF CONTENT I. Overview II. Install and Setup Server III. Test AgentDialer on the Server IV. Use a better headset V.
PREDICTIVE DIALER AND REMOTE AGENT SETUP GUIDE RELEASE 7 VOICENT AGENTDIALER TM TABLE OF CONTENT I. Overview II. Install and Setup Server III. Test AgentDialer on the Server IV. Use a better headset V.
Cyclope Internet Filtering Proxy. - Installation Guide -
 Cyclope Internet Filtering Proxy - Installation Guide - 1. Overview 3 2. Installation 4 2.1 System requirements 4 2.2 Cyclope Internet Filtering Proxy Installation 4 2.3 Client Browser Configuration 6
Cyclope Internet Filtering Proxy - Installation Guide - 1. Overview 3 2. Installation 4 2.1 System requirements 4 2.2 Cyclope Internet Filtering Proxy Installation 4 2.3 Client Browser Configuration 6
How to Set Up Outlook 2007 and Outlook 2010 for Hosted Microsoft Exchange if the Program is Already Installed
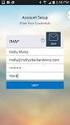 How to Set Up Outlook 2007 and Outlook 2010 for Hosted Microsoft Exchange if the Program is Already Installed 1. If you received your copy of Outlook from Cbeyond (via a CD or by downloading it from CbeyondOnline)
How to Set Up Outlook 2007 and Outlook 2010 for Hosted Microsoft Exchange if the Program is Already Installed 1. If you received your copy of Outlook from Cbeyond (via a CD or by downloading it from CbeyondOnline)
Norton Family Product Manual
 Norton TM Family Product Manual Care for our Environment; It's the right thing to do. Symantec has removed the cover from this manual to reduce the Environmental Footprint of our products. This manual
Norton TM Family Product Manual Care for our Environment; It's the right thing to do. Symantec has removed the cover from this manual to reduce the Environmental Footprint of our products. This manual
GFI Product Manual. Web security, monitoring and Internet access control. Administrator Guide
 GFI Product Manual Web security, monitoring and Internet access control Administrator Guide The information and content in this document is provided for informational purposes only and is provided "as
GFI Product Manual Web security, monitoring and Internet access control Administrator Guide The information and content in this document is provided for informational purposes only and is provided "as
Cloudfinder for Office 365 User Guide. November 2013
 1 Contents Getting started with Cloudfinder for Office 365 1... 3 Sign up New Cloudfinder user... 3 Sign up Existing Cloudfinder user... 4 Setting the Admin Impersonation... 4 Initial backup... 7 Inside
1 Contents Getting started with Cloudfinder for Office 365 1... 3 Sign up New Cloudfinder user... 3 Sign up Existing Cloudfinder user... 4 Setting the Admin Impersonation... 4 Initial backup... 7 Inside
Sharp Remote Device Manager (SRDM) Server Software Setup Guide
 Sharp Remote Device Manager (SRDM) Server Software Setup Guide This Guide explains how to install the software which is required in order to use Sharp Remote Device Manager (SRDM). SRDM is a web-based
Sharp Remote Device Manager (SRDM) Server Software Setup Guide This Guide explains how to install the software which is required in order to use Sharp Remote Device Manager (SRDM). SRDM is a web-based
Wireless Presentation System User s Manual
 Wireless Presentation System User s Manual (Model Name: WPS-Dongle) Version: 3.0 Date: August 19, 2009 Table of Contents 1. Overview...3 2. Quick Start...4 3. Windows Client Utility...7 3.1 Starting Program...7
Wireless Presentation System User s Manual (Model Name: WPS-Dongle) Version: 3.0 Date: August 19, 2009 Table of Contents 1. Overview...3 2. Quick Start...4 3. Windows Client Utility...7 3.1 Starting Program...7
USER GUIDE. Ethernet Configuration Guide (Lantronix) P/N: 2900-300321 Rev 6
 KRAMER ELECTRONICS LTD. USER GUIDE Ethernet Configuration Guide (Lantronix) P/N: 2900-300321 Rev 6 Contents 1 Connecting to the Kramer Device via the Ethernet Port 1 1.1 Connecting the Ethernet Port Directly
KRAMER ELECTRONICS LTD. USER GUIDE Ethernet Configuration Guide (Lantronix) P/N: 2900-300321 Rev 6 Contents 1 Connecting to the Kramer Device via the Ethernet Port 1 1.1 Connecting the Ethernet Port Directly
Campus VPN. Version 1.0 September 22, 2008
 Campus VPN Version 1.0 September 22, 2008 University of North Texas 1 9/22/2008 Introduction This is a guide on the different ways to connect to the University of North Texas Campus VPN. There are several
Campus VPN Version 1.0 September 22, 2008 University of North Texas 1 9/22/2008 Introduction This is a guide on the different ways to connect to the University of North Texas Campus VPN. There are several
Release Notes for Websense Email Security v7.2
 Release Notes for Websense Email Security v7.2 Websense Email Security version 7.2 is a feature release that includes support for Windows Server 2008 as well as support for Microsoft SQL Server 2008. Version
Release Notes for Websense Email Security v7.2 Websense Email Security version 7.2 is a feature release that includes support for Windows Server 2008 as well as support for Microsoft SQL Server 2008. Version
Network Connect Installation and Usage Guide
 Network Connect Installation and Usage Guide I. Installing the Network Connect Client..2 II. Launching Network Connect from the Desktop.. 9 III. Launching Network Connect Pre-Windows Login 11 IV. Installing
Network Connect Installation and Usage Guide I. Installing the Network Connect Client..2 II. Launching Network Connect from the Desktop.. 9 III. Launching Network Connect Pre-Windows Login 11 IV. Installing
Cloud Services MDM. ios User Guide
 Cloud Services MDM ios User Guide 10/24/2014 CONTENTS Overview... 3 Supported Devices... 3 System Capabilities... 3 Enrollment and Activation... 4 Download the Agent... 4 Enroll Your Device Using the Agent...
Cloud Services MDM ios User Guide 10/24/2014 CONTENTS Overview... 3 Supported Devices... 3 System Capabilities... 3 Enrollment and Activation... 4 Download the Agent... 4 Enroll Your Device Using the Agent...
Proxies. Chapter 4. Network & Security Gildas Avoine
 Proxies Chapter 4 Network & Security Gildas Avoine SUMMARY OF CHAPTER 4 Generalities Forward Proxies Reverse Proxies Open Proxies Conclusion GENERALITIES Generalities Forward Proxies Reverse Proxies Open
Proxies Chapter 4 Network & Security Gildas Avoine SUMMARY OF CHAPTER 4 Generalities Forward Proxies Reverse Proxies Open Proxies Conclusion GENERALITIES Generalities Forward Proxies Reverse Proxies Open
Magaya Software Installation Guide
 Magaya Software Installation Guide MAGAYA SOFTWARE INSTALLATION GUIDE INTRODUCTION Introduction This installation guide explains the system requirements for installing any Magaya software, the steps to
Magaya Software Installation Guide MAGAYA SOFTWARE INSTALLATION GUIDE INTRODUCTION Introduction This installation guide explains the system requirements for installing any Magaya software, the steps to
Manual for configuring NIC VPN in Windows OS
 Manual for configuring NIC VPN in Windows OS NIC is introducing a new web based VPN interface to allow s to connect to NICNET through VPN. Apart from existing Client based VPN service, this new interface
Manual for configuring NIC VPN in Windows OS NIC is introducing a new web based VPN interface to allow s to connect to NICNET through VPN. Apart from existing Client based VPN service, this new interface
Burst Technology. bt-webfilter User Guide
 Burst Technology presents bt-webfilter User Guide Burstek TM 9240 Bonita Beach Road Bonita Springs, FL 34135 Telephone: (239) 495-5900 or toll free (800) 709-2551 Visit the Burstek Website at http://www.burstek.com
Burst Technology presents bt-webfilter User Guide Burstek TM 9240 Bonita Beach Road Bonita Springs, FL 34135 Telephone: (239) 495-5900 or toll free (800) 709-2551 Visit the Burstek Website at http://www.burstek.com
Access to Kozminski University library databases from home
 Access to Kozminski University library databases from home All students and staff at Kozminski University can benefit from special, purchased by the Library of ALK, databases containing many interesting
Access to Kozminski University library databases from home All students and staff at Kozminski University can benefit from special, purchased by the Library of ALK, databases containing many interesting
Identifying the Number of Visitors to improve Website Usability from Educational Institution Web Log Data
 Identifying the Number of to improve Website Usability from Educational Institution Web Log Data Arvind K. Sharma Dept. of CSE Jaipur National University, Jaipur, Rajasthan,India P.C. Gupta Dept. of CSI
Identifying the Number of to improve Website Usability from Educational Institution Web Log Data Arvind K. Sharma Dept. of CSE Jaipur National University, Jaipur, Rajasthan,India P.C. Gupta Dept. of CSI
How To Set Up Ops Cser.Com (Pros) For A Pc Or Mac) With A Microsoft Powerbook (Proos) (Prosecco) (Powerbook) (Pros) And Powerbook.Com/
 PROS CS (Client-Server) Installation and Basic-configuration Guide Contents PROS CS (Client-Server)... 1 Installation and Basic-configuration Guide... 1 1. Overview... 2 2. Intro... 3 3. UPGRADING from
PROS CS (Client-Server) Installation and Basic-configuration Guide Contents PROS CS (Client-Server)... 1 Installation and Basic-configuration Guide... 1 1. Overview... 2 2. Intro... 3 3. UPGRADING from
www.novell.com/documentation User Guide Novell iprint 1.1 March 2015
 www.novell.com/documentation User Guide Novell iprint 1.1 March 2015 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of this documentation, and specifically
www.novell.com/documentation User Guide Novell iprint 1.1 March 2015 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of this documentation, and specifically
Controlling Risk, Conserving Bandwidth, and Monitoring Productivity with Websense Web Security and Websense Content Gateway
 Controlling Risk, Conserving Bandwidth, and Monitoring Productivity with Websense Web Security and Websense Content Gateway Websense Support Webinar January 2010 web security data security email security
Controlling Risk, Conserving Bandwidth, and Monitoring Productivity with Websense Web Security and Websense Content Gateway Websense Support Webinar January 2010 web security data security email security
Access the UTHSCSA Palo Alto Networks (PAN) VPN using Global Protect VPN client and Two Factor Authentication (2FA)
 Access the UTHSCSA Palo Alto Networks (PAN) VPN using Global Protect VPN client and Two Factor Authentication (2FA) Table of Contents Introduction. 1 Determine your Windows Operating System (for software
Access the UTHSCSA Palo Alto Networks (PAN) VPN using Global Protect VPN client and Two Factor Authentication (2FA) Table of Contents Introduction. 1 Determine your Windows Operating System (for software
Configure Web Conference Parameters Through The Web Conference Administration User Interface.
 Configure Web Conference Parameters Through The Web Conference Administration User Interface. Once the ShoreTel Service Appliance 100 has been installed and configured in ShoreTel Director, the Web Conference
Configure Web Conference Parameters Through The Web Conference Administration User Interface. Once the ShoreTel Service Appliance 100 has been installed and configured in ShoreTel Director, the Web Conference
User's Guide. Copyright 2012 Bitdefender
 User's Guide Copyright 2012 Bitdefender Bitdefender Parental Control User's Guide Publication date 2012.06.05 Copyright 2012 Bitdefender Legal Notice All rights reserved. No part of this book may be reproduced
User's Guide Copyright 2012 Bitdefender Bitdefender Parental Control User's Guide Publication date 2012.06.05 Copyright 2012 Bitdefender Legal Notice All rights reserved. No part of this book may be reproduced
FAQ. How does the new Big Bend Backup (powered by Keepit) work?
 FAQ How does the new Big Bend Backup (powered by Keepit) work? Once you establish which of the folders on your hard drive you ll be backing up, you ll log into myaccount.bigbend.net and from your control
FAQ How does the new Big Bend Backup (powered by Keepit) work? Once you establish which of the folders on your hard drive you ll be backing up, you ll log into myaccount.bigbend.net and from your control
Get Started Guide - PC Tools Internet Security
 Get Started Guide - PC Tools Internet Security Table of Contents PC Tools Internet Security... 1 Getting Started with PC Tools Internet Security... 1 Installing... 1 Getting Started... 2 iii PC Tools
Get Started Guide - PC Tools Internet Security Table of Contents PC Tools Internet Security... 1 Getting Started with PC Tools Internet Security... 1 Installing... 1 Getting Started... 2 iii PC Tools
F-Secure Mobile Security. Android
 F-Secure Mobile Security Android F-Secure Mobile Security TOC 2 Contents Chapter 1: Installation...4 1.1 Installing...5 1.2 Activating...6 1.3 Configuring the product...7 1.4 Uninstalling the product from
F-Secure Mobile Security Android F-Secure Mobile Security TOC 2 Contents Chapter 1: Installation...4 1.1 Installing...5 1.2 Activating...6 1.3 Configuring the product...7 1.4 Uninstalling the product from
ONLINE ACCOUNTABILITY FOR EVERY DEVICE. Quick Reference Guide V1.0
 ONLINE ACCOUNTABILITY FOR EVERY DEVICE Quick Reference Guide V1.0 TABLE OF CONTENTS ACCOUNT SET UP Creating an X3watch account DOWNLOADING AND INSTALLING X3WATCH System Requirements How to install on a
ONLINE ACCOUNTABILITY FOR EVERY DEVICE Quick Reference Guide V1.0 TABLE OF CONTENTS ACCOUNT SET UP Creating an X3watch account DOWNLOADING AND INSTALLING X3WATCH System Requirements How to install on a
Webmail Instruction Guide
 Webmail Instruction Guide This document is setup to guide your through the use of the many features of our Webmail system. You may either visit www.safeaccess.com or webmail.safeaccess.com to login with
Webmail Instruction Guide This document is setup to guide your through the use of the many features of our Webmail system. You may either visit www.safeaccess.com or webmail.safeaccess.com to login with
Portal Recipient Guide
 Portal Recipient Guide Lindenhouse Software Limited 2015 Contents 1 Introduction... 4 2 Account Activation... 4 3 Forgotten Password... 9 4 Document signing... 12 5 Authenticating your Device & Browser...
Portal Recipient Guide Lindenhouse Software Limited 2015 Contents 1 Introduction... 4 2 Account Activation... 4 3 Forgotten Password... 9 4 Document signing... 12 5 Authenticating your Device & Browser...
Internet Filtering Appliance. User s Guide VERSION 1.2
 Internet Filtering Appliance User s Guide VERSION 1.2 User s Guide VERSION 1.2 InternetSafety.com, Inc 3979 South Main Street Suite 230 Acworth, GA 30101 Phone 678 384 5300 Fax 678 384 5299 1 Table of
Internet Filtering Appliance User s Guide VERSION 1.2 User s Guide VERSION 1.2 InternetSafety.com, Inc 3979 South Main Street Suite 230 Acworth, GA 30101 Phone 678 384 5300 Fax 678 384 5299 1 Table of
Using the ScoMIS Remote Access Service (VPN Gateway) to access the ScoMIS SIMS.net Terminal Server Service.
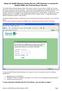 Using the ScoMIS Remote Access Service (VPN Gateway) to access the ScoMIS SIMS.net Terminal Server Service. The ScoMIS Remote Access Gateway offers a convenient method to connect direct to SIMS.net Terminal
Using the ScoMIS Remote Access Service (VPN Gateway) to access the ScoMIS SIMS.net Terminal Server Service. The ScoMIS Remote Access Gateway offers a convenient method to connect direct to SIMS.net Terminal
How To Use A Pvpn On A Pc Or Mac Or Ipad (For Pc) With A Password Protected (For Mac) On A Network (For Windows) On Your Computer (For Ipad) On An Ipad Or Ipa
 VPN User Guide For PC System Requirements Operating System: Windows XP, Windows Vista, or Windows 7. (Windows 8 is not officially supported, but does work for some users.) Internet Browser: Internet Explorer
VPN User Guide For PC System Requirements Operating System: Windows XP, Windows Vista, or Windows 7. (Windows 8 is not officially supported, but does work for some users.) Internet Browser: Internet Explorer
What s New with Salesforce for Outlook?
 What s New with Salesforce for Outlook? Available in: Contact Manager, Group, Professional, Enterprise, Unlimited, and Developer Editions Salesforce for Outlook v2.1.2 New Supported Operating System We
What s New with Salesforce for Outlook? Available in: Contact Manager, Group, Professional, Enterprise, Unlimited, and Developer Editions Salesforce for Outlook v2.1.2 New Supported Operating System We
User Manual. Onsight Management Suite Version 5.1. Another Innovation by Librestream
 User Manual Onsight Management Suite Version 5.1 Another Innovation by Librestream Doc #: 400075-06 May 2012 Information in this document is subject to change without notice. Reproduction in any manner
User Manual Onsight Management Suite Version 5.1 Another Innovation by Librestream Doc #: 400075-06 May 2012 Information in this document is subject to change without notice. Reproduction in any manner
TENVIS Technology Co., Ltd. User Manual. For H.264 Cameras. Version 2.0.0
 TENVIS Technology Co., Ltd User Manual For H.264 Cameras Version 2.0.0 Catalogue Basic Operation... 3 Hardware Installation... 3 Search Camera... 3 Get live video... 5 Camera Settings... 8 System... 8
TENVIS Technology Co., Ltd User Manual For H.264 Cameras Version 2.0.0 Catalogue Basic Operation... 3 Hardware Installation... 3 Search Camera... 3 Get live video... 5 Camera Settings... 8 System... 8
Setting up the Swann HD IP cameras
 Setting up the Swann HD IP cameras Connecting the cameras to the network The Swann IP cameras are connected to the network with Category 5/5E/6 cables. The cameras feature Power over Ethernet for ease
Setting up the Swann HD IP cameras Connecting the cameras to the network The Swann IP cameras are connected to the network with Category 5/5E/6 cables. The cameras feature Power over Ethernet for ease
Section 1.0 Getting Started with the Vālant EMR. Contents
 Section 1.0 Getting Started with the Vālant EMR Contents Getting Started with the Valant EMR application:... 2 Hardware Requirements for the Vālant EMR:... 3 Software Requirements for the Vālant EMR:...
Section 1.0 Getting Started with the Vālant EMR Contents Getting Started with the Valant EMR application:... 2 Hardware Requirements for the Vālant EMR:... 3 Software Requirements for the Vālant EMR:...
Chapter 6 Using Network Monitoring Tools
 Chapter 6 Using Network Monitoring Tools This chapter describes how to use the maintenance features of your Wireless-G Router Model WGR614v9. You can access these features by selecting the items under
Chapter 6 Using Network Monitoring Tools This chapter describes how to use the maintenance features of your Wireless-G Router Model WGR614v9. You can access these features by selecting the items under
Archive Add-in Administrator Guide
 Archive Add-in Administrator Guide RESTRICTION ON USE, PUBLICATION, OR DISCLOSURE OF PROPRIETARY INFORMATION Copyright 2011 McAfee, Inc. This document contains information that is proprietary and confidential
Archive Add-in Administrator Guide RESTRICTION ON USE, PUBLICATION, OR DISCLOSURE OF PROPRIETARY INFORMATION Copyright 2011 McAfee, Inc. This document contains information that is proprietary and confidential
Connecting to the Staff Desktop Service
 Connecting to the Staff Desktop Service Access your programs and files just like you were in the office Get Setup The first step to use our Remote Connection service is to check that you have the free
Connecting to the Staff Desktop Service Access your programs and files just like you were in the office Get Setup The first step to use our Remote Connection service is to check that you have the free
Option nv, Gaston Geenslaan 14, B-3001 Leuven Tel +32 16 317 411 Fax +32 16 207 164 http://www.option.com Page 1 of 14
 Page 1 of 14 ! " #!"#$ % &&' Page 2 of 14 1 INTRODUCTION One of the highly desirable features of the GlobeSurfer III device is the ability to network together Printers and External Hard Disk drives (aka
Page 1 of 14 ! " #!"#$ % &&' Page 2 of 14 1 INTRODUCTION One of the highly desirable features of the GlobeSurfer III device is the ability to network together Printers and External Hard Disk drives (aka
Technical Brief for Windows Home Server Remote Access
 Technical Brief for Windows Home Server Remote Access Microsoft Corporation Published: October, 2008 Version: 1.1 Abstract This Technical Brief provides an in-depth look at the features and functionality
Technical Brief for Windows Home Server Remote Access Microsoft Corporation Published: October, 2008 Version: 1.1 Abstract This Technical Brief provides an in-depth look at the features and functionality
Managing Qualys Scanners
 Q1 Labs Help Build 7.0 Maintenance Release 3 [email protected] Managing Qualys Scanners Managing Qualys Scanners A QualysGuard vulnerability scanner runs on a remote web server. QRadar must access
Q1 Labs Help Build 7.0 Maintenance Release 3 [email protected] Managing Qualys Scanners Managing Qualys Scanners A QualysGuard vulnerability scanner runs on a remote web server. QRadar must access
How To Watch A Live Webcast On A Pc Or Mac Or Ipad (For Pc Or Ipa)
 FAQ Welcome to the F.A.Q. (Frequently Asked Questions). You may be connecting to the internet through a network that has restrictions on the type of content which can be viewed. This can occur in any network
FAQ Welcome to the F.A.Q. (Frequently Asked Questions). You may be connecting to the internet through a network that has restrictions on the type of content which can be viewed. This can occur in any network
IntraVUE Plug Scanner/Recorder Installation and Start-Up
 IntraVUE Plug Scanner/Recorder Installation and Start-Up The IntraVUE Plug is a complete IntraVUE Hardware/Software solution that can plug directly into any network to continually scan and record details
IntraVUE Plug Scanner/Recorder Installation and Start-Up The IntraVUE Plug is a complete IntraVUE Hardware/Software solution that can plug directly into any network to continually scan and record details
M2Web - Browser-Based Mobile Remote Access
 Application User Guide M2Web - Browser-Based Mobile Remote Access AUG 058 / Rev. 1.2 This application guide describes how to use the M2Web interface for mobile remote access. support.ewon.biz Table of
Application User Guide M2Web - Browser-Based Mobile Remote Access AUG 058 / Rev. 1.2 This application guide describes how to use the M2Web interface for mobile remote access. support.ewon.biz Table of
Select Correct USB Driver
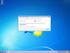 Select Correct USB Driver Windows often installs updated drivers automatically, and defaults to this latest version. Not all of these drivers are compatible with our software. If you are experiencing communications
Select Correct USB Driver Windows often installs updated drivers automatically, and defaults to this latest version. Not all of these drivers are compatible with our software. If you are experiencing communications
Employee PC and Server Activity Monitoring Solution
 Employee PC and Server Activity Monitoring Solution Employee PC and Server Activity Monitoring Ever dreamed of a software tool to track your network activity in real time? Ever thought of how useful it
Employee PC and Server Activity Monitoring Solution Employee PC and Server Activity Monitoring Ever dreamed of a software tool to track your network activity in real time? Ever thought of how useful it
How to set up popular firewalls to work with Web CEO
 How to set up popular firewalls to work with Web CEO Contents How to set up popular firewalls to work with Web CEO... 1 Setting up Agnitum Outpost Firewall 2.5... 2 Setting up Black ICE 3... 6 Setting
How to set up popular firewalls to work with Web CEO Contents How to set up popular firewalls to work with Web CEO... 1 Setting up Agnitum Outpost Firewall 2.5... 2 Setting up Black ICE 3... 6 Setting
System Log Setup (RTA1025W Rev2)
 System Log Setup (RTA1025W Rev2) System Log As shown on the web page, you can view the system log and configure system log whenever you want. To view the system log, you must configure system log first.
System Log Setup (RTA1025W Rev2) System Log As shown on the web page, you can view the system log and configure system log whenever you want. To view the system log, you must configure system log first.
Pearl Echo Installation Checklist
 Pearl Echo Installation Checklist Use this checklist to enter critical installation and setup information that will be required to install Pearl Echo in your network. For detailed deployment instructions
Pearl Echo Installation Checklist Use this checklist to enter critical installation and setup information that will be required to install Pearl Echo in your network. For detailed deployment instructions
Last modified on 03-01-2010 for application version 4.4.4
 Last modified on 03-01-2010 for application version 4.4.4 RemotePC User Manual Table of Contents Introduction... 3 Features... 3 Install the Remote Access Host application... 4 Install the Remote Access
Last modified on 03-01-2010 for application version 4.4.4 RemotePC User Manual Table of Contents Introduction... 3 Features... 3 Install the Remote Access Host application... 4 Install the Remote Access
FortKnox Personal Firewall
 FortKnox Personal Firewall User Manual Document version 1.4 EN ( 15. 9. 2009 ) Copyright (c) 2007-2009 NETGATE Technologies s.r.o. All rights reserved. This product uses compression library zlib Copyright
FortKnox Personal Firewall User Manual Document version 1.4 EN ( 15. 9. 2009 ) Copyright (c) 2007-2009 NETGATE Technologies s.r.o. All rights reserved. This product uses compression library zlib Copyright
Web-Access Security Solution
 WavecrestCyBlock Client Version 2.1.13 Web-Access Security Solution UserGuide www.wavecrest.net Copyright Copyright 1996-2014, Wavecrest Computing, Inc. All rights reserved. Use of this product and this
WavecrestCyBlock Client Version 2.1.13 Web-Access Security Solution UserGuide www.wavecrest.net Copyright Copyright 1996-2014, Wavecrest Computing, Inc. All rights reserved. Use of this product and this
ACCEPT THE SECURITY CERTIFICATE FOR THE WEB FILTER
 ACCEPT THE SECURITY CERTIFICATE FOR THE WEB FILTER ACCESS THE WEB FILTER VIA ITS LAN 1 IP ADDRESS ACCEPT THE SECURITY CERTIFICATE FOR THE WEB FILTER Access the Web Filter via its LAN 1 IP Address A. Launch
ACCEPT THE SECURITY CERTIFICATE FOR THE WEB FILTER ACCESS THE WEB FILTER VIA ITS LAN 1 IP ADDRESS ACCEPT THE SECURITY CERTIFICATE FOR THE WEB FILTER Access the Web Filter via its LAN 1 IP Address A. Launch
Comodo LoginPro Software Version 1.5
 Comodo LoginPro Software Version 1.5 User Guide Guide Version 1.5.030513 Comodo Security Solutions 1255 Broad Street STE 100 Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo LoginPro... 3 1.1.System
Comodo LoginPro Software Version 1.5 User Guide Guide Version 1.5.030513 Comodo Security Solutions 1255 Broad Street STE 100 Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo LoginPro... 3 1.1.System
Contents. Business Everywhere user guide. 1. Introduction. 2. Recommended configuration. 3. Administration Tool installation and start-up
 Contents 1. Introduction 2. Recommended configuration 3. Administration Tool installation and start-up 4. Configure your connection manager KitType Help window Secured networks Thresholds & Alerts 5. Save
Contents 1. Introduction 2. Recommended configuration 3. Administration Tool installation and start-up 4. Configure your connection manager KitType Help window Secured networks Thresholds & Alerts 5. Save
EINTE LAB EXERCISES LAB EXERCISE #5 - SIP PROTOCOL
 EINTE LAB EXERCISES LAB EXERCISE #5 - SIP PROTOCOL PREPARATIONS STUDYING SIP PROTOCOL The aim of this exercise is to study the basic aspects of the SIP protocol. Before executing the exercise you should
EINTE LAB EXERCISES LAB EXERCISE #5 - SIP PROTOCOL PREPARATIONS STUDYING SIP PROTOCOL The aim of this exercise is to study the basic aspects of the SIP protocol. Before executing the exercise you should
How To Create An Easybelle History Database On A Microsoft Powerbook 2.5.2 (Windows)
 Introduction EASYLABEL 6 has several new features for saving the history of label formats. This history can include information about when label formats were edited and printed. In order to save this history,
Introduction EASYLABEL 6 has several new features for saving the history of label formats. This history can include information about when label formats were edited and printed. In order to save this history,
Konica Minolta s Optimised Print Services (OPS)
 Konica Minolta s Optimised Print Services (OPS) Document Collection Agent (DCA) Detailed Installation Guide V1.6 Page 1 of 43 Table of Contents Notes... 4 Requirements... 5 Network requirements... 5 System
Konica Minolta s Optimised Print Services (OPS) Document Collection Agent (DCA) Detailed Installation Guide V1.6 Page 1 of 43 Table of Contents Notes... 4 Requirements... 5 Network requirements... 5 System
TECH NOTES. Minimum MLC 226 IP MediaLink Controller Firmware required Applies to
 Application Name: IP Intercom HelpDesk Software Current Version: 2.4.3 The following notes provide the revision history and a list of known software issues in the current release. For more information
Application Name: IP Intercom HelpDesk Software Current Version: 2.4.3 The following notes provide the revision history and a list of known software issues in the current release. For more information
MobileStatus Server Installation and Configuration Guide
 MobileStatus Server Installation and Configuration Guide Guide to installing and configuring the MobileStatus Server for Ventelo Mobilstatus Version 1.2 June 2010 www.blueposition.com All company names,
MobileStatus Server Installation and Configuration Guide Guide to installing and configuring the MobileStatus Server for Ventelo Mobilstatus Version 1.2 June 2010 www.blueposition.com All company names,
Magnet Voice Windows PC Softphone Installation
 Magnet Voice Windows PC Softphone Installation Contents 1. Introduction 3 2. Installation 3 Step 1: Install the Software on your PC 4 Step 2: Input your registration details 4 3. Connected State 6 6. Port
Magnet Voice Windows PC Softphone Installation Contents 1. Introduction 3 2. Installation 3 Step 1: Install the Software on your PC 4 Step 2: Input your registration details 4 3. Connected State 6 6. Port
E-Learning User Manual
 E-Learning User Manual 1 University of Puthisastra Lecturer Features Main Page 1 st Main Page Needs a proper login. 1. Select your preferred language from the list box (English or Khmer) 2. To go back
E-Learning User Manual 1 University of Puthisastra Lecturer Features Main Page 1 st Main Page Needs a proper login. 1. Select your preferred language from the list box (English or Khmer) 2. To go back
Seagate NAS OS 4 Reviewers Guide: NAS / NAS Pro / Business Storage Rackmounts
 Seagate NAS OS 4 Reviewers Guide: NAS / NAS Pro / Business Storage Rackmounts Seagate NAS OS 4 Reviewers Guide 2 Purpose of this guide Experience the most common use cases for the product, learn about
Seagate NAS OS 4 Reviewers Guide: NAS / NAS Pro / Business Storage Rackmounts Seagate NAS OS 4 Reviewers Guide 2 Purpose of this guide Experience the most common use cases for the product, learn about
