A Low-Cost Solution for Protecting IPs Against Scan-Based Side-Channel Attacks
|
|
|
- Emory Moody
- 7 years ago
- Views:
Transcription
1 A Low-Cost Solution for Protecting IPs Against Scan-Based Side-Channel Attacks Jeremy Lee, Mohammad Tehranipoor, and Jim Plusquellic Department of CSEE University of Maryland Baltimore County Abstract Scan designs used for testing also provide an easily accessible port for hacking. In this paper, we present a new lowcost secure scan design that is effective against scan-based sidechannel attacks. By integrating a test key into test vectors that are scanned into the chip, testing and accessing scan chains are guaranteed to be allowed only by an authorized user. Any attempt to use the scan chain without a verified test vector will result in a randomized output preventing potential side-channel attacks. The proposed technique has a negligible area overhead, has no negative impact on chip performance, and places several levels of security over the scan chain protecting it from potential attacks. I. INTRODUCTION Design for testability (DFT) has greatly eased manufacturing testing with an efficient method of yielding a high fault coverage. Scan test has contributed greatly to the success of DFT, but recently it has also been used to assist in non-invasive attacks to steal important information such as intellectual property (IP) or secret keys [1][2]. The scan-based side-channel attacks have added to an already growing customer concern of hardware security [3][4][5]. As more information security measures are implemented on chip and more companies would like to keep their designs or IP protected, additional security measures must be implemented to defend from the multitude of intrusive and side-channel attacks that exist. Scan test provides extensive controllability and observability over a chip. While beneficial for testing purposes, these properties also make reverse engineering the chip much easier. Testability and security inherently contradict each other. The higher degree of controllability and observability allowed, the easier it is to test the circuit under test (CUT). Security of a chip attempts to limit controllability and observability in order to protect and obscure any important information from any unauthorized persons. Most security measures implemented in hardware have been used to protect information, but if these measures are leaking information through side-channels, which has become the case for scan-based testing, additional hardware measures must be taken to prevent such events from occurring. If the designer does not consider testability when designing for security, he may lose the efficient and reliable test mechanism. However, if security is overlooked in favor of testability, too much information may be too easily accessible. In order to find a solution, the designer must also consider the hacker and the expected skill set of the hacker [6]. A proper balance of all these factors is necessary when considering an appropriate solution. A. Prior Work Hardware security has been receiving a lot of attention with the increased use of cryptochips in various applications like smart cards and other embedded systems [7][8]. Much of the discussion has been focused on tamper resistant designs in order to prevent intrusive and side-channel attacks [3][4][9]. But with all this attention towards security, scan chains have only recently been shown to be just as dangerous [2]. A traditional method of scan security has been to place polysilicon fuses near the pin connections and blow them after manufacturing testing or completely cut off the test interface with a wafer saw [7]. This however eliminates any possibility for in-field testing. Many have gotten around the concern by using BIST to test the entire design [1] or a hybrid method that uses BIST on sensitive portions and scan on the remainder [11]. Although a viable solution, the fault coverage still does not reach the levels of scan and ATPG. There has recently been an increased focus to secure scan designs without completely destroying access to the test interface. An encoding/decoding security scheme has been presented as a potential solution but have not been fully developed yet [12][13]. To prevent finding secret key information, a simple solution proposed is to use a second register, called the mirror key register (MKR), to prevent any critical data from entering the scan chain when in test mode [1]. Although effective, application of this solution is fairly limited since this approach can only protect information and not the actual IP the chip may contain. Scan scrambling was presented in [14], which divides the scan chain into subchains and uses logic and a random number generator to randomly reconnect the subchains together again and internally scramble data. Using this strategy with a large number of subchains yield a high complexity, but also begins to create significant area and timing overhead. Another technique checks a golden signature after a well defined consistent system reset to ensure secure switching between system and test modes [15]. A lock & key technique was developed in [6], which also divides the scan chain into subchains, but rather than connecting all of the subchains back together, all the subchains are independent of each other. By using a randomly seeded LFSR, one subchain at a time would be randomly enabled to scan-in and scan-out while all other subchains are left unaffected. This technique also has the disadvantage of scaling poorly for a very large number of subchains. B. Contribution and Paper Organization We propose a low-cost secure scan solution that can be used to prevent scan-based side-channel attacks while maintaining the testability features of scan. By allowing for varying levels of security, our solution is flexible and can easily be integrated into the scan insertion flow. This low-cost solution requires that a test key be included into all test vectors that are to be
2 used for scan test by inserting dummy flip-flops into the scan chains. By doing so, it verifies that all vectors scanned-in come from an authorized user and the correct response can be safely scanned-out after functional mode operation. If the correct key is not integrated into the vector, an unpredictable response will be scanned-out making analysis very difficult for an attack. By using an unpredictable response, a hacker would not be able to immediately realize that their intrusion has been detected as could be done if the CUT were to immediately reset [15]. Our approach to scan security requires little area overhead and does not negatively impact important aspects of the original design such as performance. We have organized the paper as followed. In Section II we present how an attack can be made using the scan chain. Section III presents our low-cost secure scan solution, which can be used to prevent scan-based attacks. Section IV provides an overview of how our solution can be integrated into the current scan insertion flow. Section V analyzes the impact on design and shows the implementation results. Finally, we conclude our discussion in Section VI. Normal Mode Operation Scan Mode Operation Input stimuli Input Pattern/ Take Snapshot Scan Mode Operation Generate New Input Generate New Input Snapshot Normal Mode Input Operation Pattern Take snapshot (a) (b) Analyze Scanned out Response Analyze Scanned out Response Collected Enough Data Collected Enough Data Steal IP/ Secret Key Steal IP/ Secret Key Figure 1. Summary of the steps necessary to perform a successful scan-based attacks: (a) Scan-based observability attack and (b) Scan-based controllability/observability attack. II. SCAN-BASED ATTACK CATEGORIZATION Developing a secure scan design is dependent on targeting both the type of attacker [6] and how they can potentially make the attack. We categorize the scan-based attacks into two types: scan-based observability and scan-based controllability/observability attacks. Each requires that a hacker has access to the test control (TC) pin. The type of attack depends on how a hacker decides to apply stimuli. The low-cost secure scan design we propose removes the hacker s ability to correlate test response data by creating a random response when an unauthorized user attempts access. A. Scan-Based Observability Attack A scan-based observability attack relies on a hackers ability to use the scan chain to take snapshots of the system at any time, which is a result of the observability from scan-based testing. Figure 1(a) diagrams the necessary steps to perform a scan-based observability attack. The hacker begins this attack by observing the position of critical registers in the scan chain. First, a known vector is placed on the primary input (PI) of the chip and the chip is allowed to run in functional mode until the targeted register is supposed to have data in it. At this point, the chip is placed into test mode using TC and the response in the scan chain is scanned-out. The chip is reset and a new vector that will cause a new response only in the targeted register is placed on PI. The chip again is run in functional mode for the specific number of cycles and then set into test mode. The new response is scanned-out and analyzed with the previous response. This process continues until there are enough responses to analyze where in the scan chain the targeted register is positioned. Once the targeted register is determined, a similar process can be used to either determine a secret key in the case of cryptochips or determine design secrets for a particularly innovative chip. B. Scan-Based Controllability/Observability Attack Scan-based controllability/observability attacks take a different approach to applying stimuli to the CUT, which is shown in Figure 1(b). Scan-based controllability/observability attacks begin by applying the stimuli directly into the scan chain as opposed to the PI. In order to mount an effective attack, the hacker must first determine the position of any critical registers as was done for the scan-based observability attack. Once located, the hacker can load the registers with any desired data during test mode. Next, the chip can be switched to functional mode using the vector the hacker scanned-in, potentially bypassing any information security measures. Finally, the chip can be switched back to test mode to allow the hacker a level of observability the system primary output (PO) would not provide otherwise. As opposed to using a known vector to scan in to the chain, hackers also have the opportunity to choose a random vector to induce a fault in the system. Based off of the fault-injection side-channel attack [16][17], by inducing a fault, the chip may malfunction potentially revealing critical data. The scan chain becomes an easily accessible entry point for inducing a fault and makes the attack easily repeatable. In order to protect from such side-channel attacks, additional hardware security measures must be included in the design. III. LOW-COST SECURE SCAN (LCSS) We propose a low-cost secure scan (LCSS) solution that provides flexibility in design and integrates smoothly with current scan insertion flow. After performing scan insertion, the testing process is minimally affected while not affecting functional mode operation. The state of the scan chain is dependent on a test key that is integrated into all test vectors. We define two possible states for the chain: secure and insecure. By integrating the key, all vectors scanned-in can be verified to be from a trustworthy source (secure). Without a correct key integrated into the test vector, when scanning in a new vector and out the response, the response will be randomly altered to prevent reverse engineering of critical data that is being stored in registers (insecure). By altering the response scanned out of the chain, both the scan-based observability and scan-based controllabil-
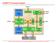
3 KCL (k to 1) FF secure secure random RBG LFSR (q bits) TC 2 SI 1 SO SI 2 SO2 SI m SOm l Figure 2. General architecture for low-cost secure scan design. To KCL To KCL from RBG SI 1 dff 1 dff SO TC Clk Figure 3. Example low-cost secure scan chain with integrated dummy flip-flops and random response network. ity/observability attacks are prevented since any attempt to correlate the responses from various input will prove unsuccessful due to the random altering of the data. The low-cost secure scan architecture is shown in Figure 2 with a more detailed look at a secure scan chain in Figure 3. In order to use the same key for every test vector, dummy flip-flops (dffs) are inserted and used as test key registers. Each dff is designed similarly to a scan cell except that there is no connection to a combinational block. The number of dffs included in the scan chain depends on the level of security the designer would like to include since the number of dffs determine the size of the test key. When implementing low-cost secure scan for multiple-scan design, the test key is inserted into the scan chain before it is broken into multiple scan chains. This ensures that the key can be randomly distributed throughout the many scan chains without needing to have a constant number of key registers in each chain. All dffs are concurrently checked by the Key Checking Logic (KCL), which is made of a block of combinational logic. The k-input block, where k is the total number of dffs in the scan design (length of the test key), fans into a single FF that is negative edge sensitive to TC. As the CUT switches from test mode to functional mode (TC falls), the FF clocks in the output of the key checking logic. The KCL-FF is then used to inform the remainder of the secure design of the current secure or insecure state of the vector in the scan chain. The third component of the low-cost secure scan solution ensures the random response in the scan chain when the test key fails to be verified by the KCL. The output of the KCL-FF fans out to an array of q 2-input OR gates. The second input of each OR gate comes from a q-bit LFSR that has been randomly seeded using one of a variety of options including, but not limited to, the value already present at reset, a random signal from a FF in the scan chain as shown in Figure 2, or a random signal from the output of a separate random number generator [18]. The former option provides the least amount of overhead, but potentially the least secure, while the latter has the most security, but also the most overhead. By also using an secure signal to the LFSR, also shown in Figure 2, the LFSR seed can continually be changed by an additional random source. Together, the LFSR and OR gate array make up the Random Bit Generator (RBG). The RBG output is used as input to the Random Response Network (RRN) that have also been inserted into the scan chain. The RRN can be made of both AND and OR gates to equalize the random transitions and prevent the random response from being all zeros or all ones. The optimal choice for randomness would be to use XOR gates, but since XORs add more delay, our design choice was to use AND and OR gates. Since the dffs are used to check the test key, dffs must be before any gates of the RRN in the scan chain as shown in Figure 3. If this property is not held, any key information that is trying to pass a gate of the RRN in the scan chain may potentially get altered either preventing the test key from ever being verified or even randomly changing a value to the correct key. Normal mode operation of the CUT is unaffected by the addition of the low-cost secure scan design since the dffs are only used for testing purposes and are not connected to the original design. A. Test Flow Our low-cost secure scan design deviates very little from current scan test flow. Since security of the scan chain is ensured by integrating a test key into the test vectors themselves, no additional pins are necessary to use low-cost secure scan. After a system reset and TC has been enabled for the first time, the secure scan design begins in an insecure state causing any data in the scan chain to be modified as it passes through each RRN gate in the chain. In order to begin the testing process, the secure scan chain must be initialized with the test key in order to set the output of the KCL-FF to 1. Only the test key is required to be in this initialization vector since any other data beyond the first RRN gate most likely will be modified. During this time the KCL will constantly be check the dffs for a correct key. After the initialization vector has been scanned-in,
4 the CUT must be switched to functional mode for one clock in order to allow the KCL-FF to capture the result from the KCL. If the KCL verifies the key stored in the dffs, the KCL-FF is set to 1 and propagates the signal to the RRN, which becomes transparent for the next round of testing allowing the new vector to be scanned-in without alteration. Testing can continue as normal once the initialization process has been finished. However, the chain can return to insecure mode at any time during scan testing if the correct test key is not present in all subsequent test vectors. Should that occur, the RRN will again affect the response in the scan chain and the initialization process must again be performed in order to resume a predictable testing process. IV. LOW-COST SECURE SCAN INSERTION Including low-cost secure scan minimally changes the current scan insertion flow. We were able to implement the LCSS insertion flow using Synopsys Design Compiler [19] and small add-ons functions we developed in C. The add-ons performed tasks like automating the KCL creation depending on the desired number of dffs, creating a desired LFSR size for the RBG, performing RRN randomization and inserting RRN gates. In order to allow smooth RRN insertion, we instantiated temporary placeholder FFs in the scan chain that would later be replaced after the scan chain had been stitched together. The entire process became automated by a single script once the add-on functions were created. We have summarized the lowcost secure scan insertion flow in the following steps. Low-Cost Secure Scan Insertion Flow 1) Define # of dffs (size of key and KCL). 2) Define KCL key (random or user defined). 3) Define # of LFSR bits. 4) Define # of RRN gates (must be # of LFSR bits). 5) Load and Compile KCL and RBG. 6) Load and Compile Targeted Design (TD). 7) Set Current Design to TD. 8) Initialize KCL and RBG in TD. 9) Initialize dffs in TD. Connect CLK of TD to dffs. Connect Q of all dffs to respective KCL port. 1) Initialize RRN placeholder FFs. Connect CLK of TD to all placeholder FFs. Connect D of all placeholder FFs to respective RBG port. 11) Reorder scan chain placing dffs before all RRN placeholder FFs. 12) Perform scan insertion. 13) Replace RRN placeholder FFs with actual RRN gates. 14) Load and Compile new netlist with Low-Cost Secure Scan included in TD V. ANALYSIS AND RESULTS Overall, our low-cost solution has little affect on important overhead aspects of chip design but significantly increases the security of the scan chain and still allows the testability of scan design. A. Overhead When implementing our secure scan solution, we wanted to affect area, test time, and performance as little as possible to maintain a low-cost strategy. Area: The KCL is the only component in our LCSS design that could potentially create a substantial area overhead. The size of the KCL for our designs remains fairly small, but is entirely dependent upon the size of the key and the value of key. The logic to perform the key verification at most will always be (k 1) gates plus the number of inverters. The number of inverters in the KCL are dependent on the value of the key and will never be greater than k. Since k inverters would translate to a key of all zeroes or all ones depending on the KCL implementation, an actual key should have approximately the same number of ones and zeros ( k 2 inverters). So on average, the size of the entire KCL will be 3k 2 1 gates. We implemented our low-cost secure scan and conventional scan on several ISCAS 89 benchmarks [2]. When including LCSS, we used a test key size of 1-bits, a 4-bit LFSR, and 1 RRN gates. The second column of Table I shows the total size of benchmarks before scan insertion, which includes the area of both combinational logic and FFs. Columns three and four list the sizes of the benchmarks after conventional scan and LCSS insertion, respectively. In columns five and six, we have shown the ratio of the overhead created by conventional scan and LCSS. The area overhead of the low-cost secure scan design is fairly significant over the size of the benchmark, but this is also true for conventional scan. If one considers the overhead of our technique over conventional scan, which is shown in column seven, the area overhead is quite minimal. So, as long as scan is going to be used, our technique has very minimal impact on area. Also, as the benchmarks become larger, the overhead becomes less significant since our secure scan size is fixed. We expect that this would hold true even more so for modern designs due to their immense size. The LCSS sizes reported (column four) include dffs that have been added to the ISCAS 89 benchmark scan chains. However, as designs grow larger, usually dummy flip-flops are inserted into scan chains for various purposes [21]. It may be possible to use these dffs as key registers. By using the already present dffs, the impact of low-cost secure scan can be reduced further. The eighth column in Table I shows the overhead if dffs did not have to be added. By considering this, we reduce the overhead of secure scan over conventional scan by more than half as shown by comparing columns seven and nine. Test Time: For modern designs with a very large number of scan cells, including additional test key registers will not affect scan test time by a significant amount. The total LCSS test time (T LCSS ) and test time increase (T inc ) over conventional scan can be summarized by T LCSS = (n comb + 3) nff + k m + n comb + 4 (1) and T inc = (n comb + 3) k m + n ff m, (2)
5 TABLE I AREA OVERHEAD OF SCAN AND LOW-COST SECURE SCAN ON ISCAS 89 BENCHMARKS. Benchmark Size of Bench w/ Bench w/ Scan / Bench LCSS / Bench LCSS - Scan LCSS w/o dffs / LCSS w/o dffs - Name Bench Scan LCSS Overhd (%) Overhd (%) Overhd(%) Bench Overhd (%) Scan Overhd (%) s s s s s TABLE II TEST TIME INCREASE (T inc ) OF LCSS WITH 1, 4, AND 8-BIT KEYS ON ISCAS 89 BENCHMARKS. Test Time Increase (%) s35932 s38584 m LCSS k = 1-bit LCSS k = 4-bit LCSS k = 8-bit where n ff is the total number of flip-flops in the design without including dffs, k is the number of test key registers, m is total number of scan chains, and n comb is the number of combinational vectors. Equation 1 accounts for the initialization process, chain test, and all test sequences. Equation 2 is the result of subtracting the total test time of conventional scan from T LCSS. T LCSS could be reduced further if the initialization process and chain test occurred concurrently, but this is dependent upon the location of the dffs. As modern designs continue to have more scan cells and k remains fairly small in comparison, the test time increase will become less significant. We have included potential test time increase (T inc ) percentages in Table II for conventional scan and secure scan using a key size of 1, 4, and 8-bits on two ISCAS 89 benchmarks. We assume the designs use multiple scan chains (m scan chains) and the number of chains are set to a value that will keep each chain length at approximately 1 cells when conventional scan is used. We have also set n comb = 1. The results show that T inc can be negligible for large designs when k is much smaller than n ff. Performance: Performance of a design is not affected by lowcost secure scan any more than it would by conventional scan test. The speed of the design remains only affected by the inclusion of the scan chain itself and not further hindered by the inclusion of dummy flip-flops or RRN gates between the scan cells. Power consumption during normal mode operation is affected very little. However, consumption during test mode only becomes a concern should the designer use a very large key with many RRN gates since this could considerably increase switching activity during scan operation. But as long as the key length and number of RRN gates remain small in comparison to the total number of scan cells, additional power consumption will be minimal. B. Affect on Security and Testability While maintaining a low-cost overhead, our secure scan solution is able to greatly increase the security of the scan chain while still providing the high controllability and observability conventional scan usually provides. Security: If a hacker attempts to perform an attack, any vector scanned-in or any critical data scanned-out will be randomly altered by the RRN throughout the chain. With each additional RRN gate used in a scan chain, the probability of determining the original value drops. If the attacker would like to perform a scan-based sidechannel attack without being hindered by the security measures in place, the hacker must bypass seven security elements: 1) The test key, 2) The location of each test key register in the scan chain (or test vector), 3) The number of RRN gates in each scan chain, 4) The type of RRN gate being used, 5) The random LFSR seed, 6) The LFSR polynomial, and 7) In the case of multiple-scan designs, the hacker must also determine the configuration of the decoder/encoder on the input/output of the scan chain. The last five security elements are very difficult to determine without disassembling the chip and using expensive equipment. Each level of security adds to the complexity of determining the contents of the scan chain. The k-bit key alone provides 2 k potential combinations. Our implementation placed all dffs in the first 2 3 of each scan chain. Choosing k-bits out of the first 2n 3 scan cells in the chain creates an additional level of complexity to the security strategy used in low-cost secure scan, where n is the total scan length including dffs. There are ( ) 2n 3 k possible key location combinations. We placed the RRN gates in the later 1 3 of each scan chain creating a complexity of ( ) n 3 r where r is the total number of RRN gates used in the design. Determining the type of RRN gate doubles the combinations. Also, the LFSR seed and LFSR polynomial each provide 2 q potential combinations. Combining all of these components together result in ( 2n ) ( n ) 2 k+2q (3) k r total combinations. When considering multiple-scan chain decoding/encoding, Equation 3 shows the minimum number of possible combinations. We have summarized the complexity of low-cost secure scan in Table III on two ISCAS 89 benchmarks using various key sizes. For simplicity, we keep the LFSR size fixed at 4-bits (q = 4). Table III shows that as we increase the key and as the number of scan cells increase, the complexity dramatically increases. Scan-Based Observability Attack Prevention: With the lowcost secure scan design in place, if the hacker attempts to run a system in functional mode and immediately takes a snapshot with access to the test control pin, any response on SO will result in randomized data due the lack of a correct test key and the RRN integrated into the chain. A hacker is given a false hope of a successful attack since a response is still scanned-out, but attempting to correlate the responses would fail.
6 TABLE III COMPLEXITY OF LCSS WITH 1, 4, AND 8-BIT KEYS ON ISCAS 89 BENCHMARKS. s35932 Complexity s38584 m LCSS k = 1-bit 2 19`1159 `58 1 r 2 19`958 `479 1 r LCSS k = 4-bit 2 49`1179 `59 4 r 2 49`978 `489 4 r LCSS k = 8-bit 2 89`126 `63 8 r 2 89`14 `52 8 r Scan-Based Controllability/Observability Attack Prevention: If the hacker attempts to scan-in a vector, unless the hacker knows the test key, it will be randomly altered by the RRN essentially creating a new vector unknown to the hacker. When the hacker cycles TC, similar to the scan-based observability attack, the hacker will not be able to easily correlate a particular portion of the response to any critical registers needed to perform an effective attack. This security design is also effective against a fault-injection attack. The hacker may choose a vector at random to potentially force the CUT into a fault condition. However, due to the random stimuli alterations of the integrated RRN, the hacker will have difficulty reproducing the same fault with the same vector. DFT: In a multiple-scan design the test key can be distributed throughout all of the scan chains given that all of the chains are equal in length and the dffs are placed before the RRN gates. Given that there may be hundreds of chains in the design, some chains may have one or two key registers while other chains have none at all. Still, only one KCL is necessary to check the key no matter how many chains are in the design. Placement of the RRN gates only occurs after the scan chain has been divided into multiple chains to prevent the potential of some chains being left unsecured by the RRN. Each of the scan chains can use all q-bits of the LFSR to randomize the data or use a different subset combination. Due to the flexibility of low-cost secure scan, there are a wide variety of customizable arrangements for the dffs and RRN in multiple-scan designs while maintaining a conventional multiple-scan design interface. Enhanced-scan techniques like test compression can still be used without any alterations since no changes are made to the interface of the scan chains. Even launch-off shift (LOS) and launch-off capture (LOC) can be implemented as normal. It may be necessary to add an additional dead cycle between capture and the next initialization cycles for LOS and an additional dead cycle between initialization and launch cycles for LOC, but the end result still successfully captured. Including chips with low-cost secure scan in SoC designs or chips that need in-field testing do not need any special cases since the scan interface has not been changed beyond that of conventional scan design. By this level of abstraction, no additional pins are required by our low-cost secure scan design and map to a JTAG interface in the same fashion as conventional scan. VI. CONCLUSION We have presented a low-overhead secure scan solution that can be used to prevent scan-based side-channel attacks. By integrating the proposed technique into the scan insertion flow, the complexity of determining secret information significantly increases since a hacker must bypass up to seven levels of security until being able to access the scan chain. The hacker also may waste valuable time performing an attack without realizing a security strategy is being used since a random response is still output by the scan chain as opposed to resetting the chip or setting all values to zero/one. This strategy is flexible and can be extended to a variety of security levels depending on the needs and preference of the designer. The goal of adding security as opposed to removing testability allows in-field testing that could later prove invaluable depending on the application. VII. ACKNOWLEDGMENT The authors would like to thank Nisar Ahmed for his many helpful discussions. REFERENCES [1] B. Yang, K. Wu, and R. Karri, Secure Scan: A Design-for-Test Architecture for Crypto Chips, in Proc. of 42nd Annual Conference on Design Automation, June 25, pp [2], Scan Based Side Channel Attack on Dedicated Hardware Implementations of Data Encryption Standard, in Proc. of the IEEE Int. Test Conf. (ITC), 24, pp [3] S. Ravi, A. Raghunathan, and S. Chakradhar, Tamper Resistance Mechanisms for Secure Embedded Systems, in Proc. of the 17th Intl. Conf. on VLSI Design, 24, pp [4] P. Kocher, R. Lee, G. McGraw, A. Raghunathan, and S. Ravi, Security as a New Dimension in Embedded System Design, in Proc. of the 41st Annual Conference on Design Automation, June 24, pp [5] K. Tiri and I. Verbauwhede, A VLSI Design Flow for Secure Side- Channel Attack Resistant ICs, in Proc. of Design, Automation and Test in Europe, Mar. 25, pp [6] J. Lee, M. Tehranipoor, C. Patel, and J. Plusquellic, Securing Scan Design Using Lock & Key Technique, in Intl. Symposium on Defect and Fault Tolerance in VLSI Systems, 25. [7] O. Kömmerling and M. G. Kuhn, Design Principles for Tamper- Resistant Smartcard Processors, in USENIX Workshop on Smartcard Technology, 1999, pp [8] M. Renaudin, F. Bouesse, P. Proust, J. Tual, L. Sourgen, and F. Germain, High Security Smartcards, in Proc of the Design, Automation and Test in Europe Conf., 24. [9] R. Anderson and M. Kuhn, Tamper Resistance a Cautionary Note, in Proc. of the Second USENIX Workshop on Electronic Commerce, 1996, pp [1] K. Hafner, H. C. Ritter, T. M. Schwair, S. Wallstab, M. Deppermann, J. Gessner, S. Koesters, W.-D. Moeller, and G. Sandweg, Design and Test of an Integrated Cryptochip, IEEE Design and Test of Computers, pp. 6 17, Dec [11] R. Zimmermann, A. Curiger, H. Bonnenberg, H. Kaeslin, N. Felber, and W. Fichtner, A 177 Mbit/s VLSI Implementation of the International Data Encryption Algorithm, IEEE Journal of Solid-State Circuits, vol. 29, no. 3, Mar [12] R. Goering, Scan Design Called Portal for Hackers, Oct. 24. [Online]. Available: [13] S. Scheiber, The Best-Laid Boards, Apr. 25. [Online]. Available: [14] D. Hély, M.-L. Flottes, F. Bancel, B. Rouzeyre, N. Bérard, and M. Renovell, Scan Design and Secure Chip, in Proc. of the 1th IEEE Intl. On-Line Testing Symposium, 24. [15] D. Hély, F. Bancel, M.-L. Flottes, and B. Rouzeyre, Test Control for Secure Scan Designs, in Proc. of European Test Symposium, 25. [16] D. Boneh, R. A. Demillo, and R. J. Lipton, On the Importance of Checking Cryptographic Protocols for Faults, Lecture Notes in Computer Science, vol. 1233, pp , [17] E. Biham and A. Shamir, Differential Fault Analysis of Secret Key Cryptosystems, Lecture Notes in Computer Science, vol. 1294, pp , [18] B. Jun and P. Kocher, The Intel Random Number Generator, Cryptography Research, Inc., Tech. Rep., 1999, white Paper Prepared for Intel Corporation. [19] Synopsys DFT Compiler, User Manual for Synopsys Toolset Version 24.6, Synopsys Inc., 24. [2] ISCAS 89 Benchmarks, [Online]. Available: kes/asic/iscas [21] M. L. Bushnell and V. D. Agrawal, Essentials of Electronic Testing. Kluwer Academic Publishers, 2.
Security in the Age of Nanocomputing. Hacking Devices
 Security in the Age of Nanocomputing Matthew Tan Creti Hacking Devices The ESA estimates its total worldwide losses due to piracy at $3 billion annually [2] One million unlocked iphones could cost Apple
Security in the Age of Nanocomputing Matthew Tan Creti Hacking Devices The ESA estimates its total worldwide losses due to piracy at $3 billion annually [2] One million unlocked iphones could cost Apple
Design Verification & Testing Design for Testability and Scan
 Overview esign for testability (FT) makes it possible to: Assure the detection of all faults in a circuit Reduce the cost and time associated with test development Reduce the execution time of performing
Overview esign for testability (FT) makes it possible to: Assure the detection of all faults in a circuit Reduce the cost and time associated with test development Reduce the execution time of performing
Testing of Digital System-on- Chip (SoC)
 Testing of Digital System-on- Chip (SoC) 1 Outline of the Talk Introduction to system-on-chip (SoC) design Approaches to SoC design SoC test requirements and challenges Core test wrapper P1500 core test
Testing of Digital System-on- Chip (SoC) 1 Outline of the Talk Introduction to system-on-chip (SoC) design Approaches to SoC design SoC test requirements and challenges Core test wrapper P1500 core test
Testing Low Power Designs with Power-Aware Test Manage Manufacturing Test Power Issues with DFTMAX and TetraMAX
 White Paper Testing Low Power Designs with Power-Aware Test Manage Manufacturing Test Power Issues with DFTMAX and TetraMAX April 2010 Cy Hay Product Manager, Synopsys Introduction The most important trend
White Paper Testing Low Power Designs with Power-Aware Test Manage Manufacturing Test Power Issues with DFTMAX and TetraMAX April 2010 Cy Hay Product Manager, Synopsys Introduction The most important trend
Side Channel Analysis and Embedded Systems Impact and Countermeasures
 Side Channel Analysis and Embedded Systems Impact and Countermeasures Job de Haas Agenda Advances in Embedded Systems Security From USB stick to game console Current attacks Cryptographic devices Side
Side Channel Analysis and Embedded Systems Impact and Countermeasures Job de Haas Agenda Advances in Embedded Systems Security From USB stick to game console Current attacks Cryptographic devices Side
Implementation Details
 LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
Introduction to VLSI Testing
 Introduction to VLSI Testing 李 昆 忠 Kuen-Jong Lee Dept. of Electrical Engineering National Cheng-Kung University Tainan, Taiwan, R.O.C. Introduction to VLSI Testing.1 Problems to Think A 32 bit adder A
Introduction to VLSI Testing 李 昆 忠 Kuen-Jong Lee Dept. of Electrical Engineering National Cheng-Kung University Tainan, Taiwan, R.O.C. Introduction to VLSI Testing.1 Problems to Think A 32 bit adder A
VLSI Design Verification and Testing
 VLSI Design Verification and Testing Instructor Chintan Patel (Contact using email: cpatel2@cs.umbc.edu). Text Michael L. Bushnell and Vishwani D. Agrawal, Essentials of Electronic Testing, for Digital,
VLSI Design Verification and Testing Instructor Chintan Patel (Contact using email: cpatel2@cs.umbc.edu). Text Michael L. Bushnell and Vishwani D. Agrawal, Essentials of Electronic Testing, for Digital,
Introduction to Hardware Security and Trust
 Introduction to Hardware Security and Trust Ramesh Karri (rkarri@nyu.edu) Professor of Electrical and Computer Engineering IEEE Computer Society Distinguished visitor (Hardware Security) http://engineering.nyu.edu/people/ramesh-karri
Introduction to Hardware Security and Trust Ramesh Karri (rkarri@nyu.edu) Professor of Electrical and Computer Engineering IEEE Computer Society Distinguished visitor (Hardware Security) http://engineering.nyu.edu/people/ramesh-karri
Power Reduction Techniques in the SoC Clock Network. Clock Power
 Power Reduction Techniques in the SoC Network Low Power Design for SoCs ASIC Tutorial SoC.1 Power Why clock power is important/large» Generally the signal with the highest frequency» Typically drives a
Power Reduction Techniques in the SoC Network Low Power Design for SoCs ASIC Tutorial SoC.1 Power Why clock power is important/large» Generally the signal with the highest frequency» Typically drives a
ESP-CV Custom Design Formal Equivalence Checking Based on Symbolic Simulation
 Datasheet -CV Custom Design Formal Equivalence Checking Based on Symbolic Simulation Overview -CV is an equivalence checker for full custom designs. It enables efficient comparison of a reference design
Datasheet -CV Custom Design Formal Equivalence Checking Based on Symbolic Simulation Overview -CV is an equivalence checker for full custom designs. It enables efficient comparison of a reference design
Introduction to Digital System Design
 Introduction to Digital System Design Chapter 1 1 Outline 1. Why Digital? 2. Device Technologies 3. System Representation 4. Abstraction 5. Development Tasks 6. Development Flow Chapter 1 2 1. Why Digital
Introduction to Digital System Design Chapter 1 1 Outline 1. Why Digital? 2. Device Technologies 3. System Representation 4. Abstraction 5. Development Tasks 6. Development Flow Chapter 1 2 1. Why Digital
TABLE OF CONTENTS. xiii List of Tables. xviii List of Design-for-Test Rules. xix Preface to the First Edition. xxi Preface to the Second Edition
 TABLE OF CONTENTS List of Figures xiii List of Tables xviii List of Design-for-Test Rules xix Preface to the First Edition xxi Preface to the Second Edition xxiii Acknowledgement xxv 1 Boundary-Scan Basics
TABLE OF CONTENTS List of Figures xiii List of Tables xviii List of Design-for-Test Rules xix Preface to the First Edition xxi Preface to the Second Edition xxiii Acknowledgement xxv 1 Boundary-Scan Basics
A Study on Smart Card Security Evaluation Criteria for Side Channel Attacks
 A Study on Smart Card Security Evaluation Criteria for Side Channel Attacks HoonJae Lee 1, ManKi Ahn 2, SeonGan Lim 3, and SangJae Moon 4 1 Dongseo University, Busan, 617-716, Korea hjlee@dongseo.ac.kr
A Study on Smart Card Security Evaluation Criteria for Side Channel Attacks HoonJae Lee 1, ManKi Ahn 2, SeonGan Lim 3, and SangJae Moon 4 1 Dongseo University, Busan, 617-716, Korea hjlee@dongseo.ac.kr
Strengthen RFID Tags Security Using New Data Structure
 International Journal of Control and Automation 51 Strengthen RFID Tags Security Using New Data Structure Yan Liang and Chunming Rong Department of Electrical Engineering and Computer Science, University
International Journal of Control and Automation 51 Strengthen RFID Tags Security Using New Data Structure Yan Liang and Chunming Rong Department of Electrical Engineering and Computer Science, University
Module 3: Floyd, Digital Fundamental
 Module 3: Lecturer : Yongsheng Gao Room : Tech - 3.25 Email : yongsheng.gao@griffith.edu.au Structure : 6 lectures 1 Tutorial Assessment: 1 Laboratory (5%) 1 Test (20%) Textbook : Floyd, Digital Fundamental
Module 3: Lecturer : Yongsheng Gao Room : Tech - 3.25 Email : yongsheng.gao@griffith.edu.au Structure : 6 lectures 1 Tutorial Assessment: 1 Laboratory (5%) 1 Test (20%) Textbook : Floyd, Digital Fundamental
Objective. Testing Principle. Types of Testing. Characterization Test. Verification Testing. VLSI Design Verification and Testing.
 VLSI Design Verification and Testing Objective VLSI Testing Mohammad Tehranipoor Electrical and Computer Engineering University of Connecticut Need to understand Types of tests performed at different stages
VLSI Design Verification and Testing Objective VLSI Testing Mohammad Tehranipoor Electrical and Computer Engineering University of Connecticut Need to understand Types of tests performed at different stages
Design Verification and Test of Digital VLSI Circuits NPTEL Video Course. Module-VII Lecture-I Introduction to Digital VLSI Testing
 Design Verification and Test of Digital VLSI Circuits NPTEL Video Course Module-VII Lecture-I Introduction to Digital VLSI Testing VLSI Design, Verification and Test Flow Customer's Requirements Specifications
Design Verification and Test of Digital VLSI Circuits NPTEL Video Course Module-VII Lecture-I Introduction to Digital VLSI Testing VLSI Design, Verification and Test Flow Customer's Requirements Specifications
Efficient Interconnect Design with Novel Repeater Insertion for Low Power Applications
 Efficient Interconnect Design with Novel Repeater Insertion for Low Power Applications TRIPTI SHARMA, K. G. SHARMA, B. P. SINGH, NEHA ARORA Electronics & Communication Department MITS Deemed University,
Efficient Interconnect Design with Novel Repeater Insertion for Low Power Applications TRIPTI SHARMA, K. G. SHARMA, B. P. SINGH, NEHA ARORA Electronics & Communication Department MITS Deemed University,
Arbitrary Density Pattern (ADP) Based Reduction of Testing Time in Scan-BIST VLSI Circuits
 Arbitrary Density Pattern (ADP) Based Reduction of Testing Time in Scan-BIST VLSI Circuits G. Naveen Balaji S. Vinoth Vijay Abstract Test power reduction done by Arbitrary Density Patterns (ADP) in which
Arbitrary Density Pattern (ADP) Based Reduction of Testing Time in Scan-BIST VLSI Circuits G. Naveen Balaji S. Vinoth Vijay Abstract Test power reduction done by Arbitrary Density Patterns (ADP) in which
The Boundary Scan Test (BST) technology
 The Boundary Scan Test () technology J. M. Martins Ferreira FEUP / DEEC - Rua Dr. Roberto Frias 42-537 Porto - PORTUGAL Tel. 35 225 8 748 / Fax: 35 225 8 443 (jmf@fe.up.pt / http://www.fe.up.pt/~jmf) Objectives
The Boundary Scan Test () technology J. M. Martins Ferreira FEUP / DEEC - Rua Dr. Roberto Frias 42-537 Porto - PORTUGAL Tel. 35 225 8 748 / Fax: 35 225 8 443 (jmf@fe.up.pt / http://www.fe.up.pt/~jmf) Objectives
Test Resource Partitioning and Reduced Pin-Count Testing Based on Test Data Compression
 Test esource Partitioning and educed Pin-Count Testing Based on Test Data Compression nshuman Chandra and Krishnendu Chakrabarty Department of Electrical and Computer Engineering Duke University, Durham,
Test esource Partitioning and educed Pin-Count Testing Based on Test Data Compression nshuman Chandra and Krishnendu Chakrabarty Department of Electrical and Computer Engineering Duke University, Durham,
Implementation of Full -Parallelism AES Encryption and Decryption
 Implementation of Full -Parallelism AES Encryption and Decryption M.Anto Merline M.E-Commuication Systems, ECE Department K.Ramakrishnan College of Engineering-Samayapuram, Trichy. Abstract-Advanced Encryption
Implementation of Full -Parallelism AES Encryption and Decryption M.Anto Merline M.E-Commuication Systems, ECE Department K.Ramakrishnan College of Engineering-Samayapuram, Trichy. Abstract-Advanced Encryption
What is a System on a Chip?
 What is a System on a Chip? Integration of a complete system, that until recently consisted of multiple ICs, onto a single IC. CPU PCI DSP SRAM ROM MPEG SoC DRAM System Chips Why? Characteristics: Complex
What is a System on a Chip? Integration of a complete system, that until recently consisted of multiple ICs, onto a single IC. CPU PCI DSP SRAM ROM MPEG SoC DRAM System Chips Why? Characteristics: Complex
Lesson 12 Sequential Circuits: Flip-Flops
 Lesson 12 Sequential Circuits: Flip-Flops 1. Overview of a Synchronous Sequential Circuit We saw from last lesson that the level sensitive latches could cause instability in a sequential system. This instability
Lesson 12 Sequential Circuits: Flip-Flops 1. Overview of a Synchronous Sequential Circuit We saw from last lesson that the level sensitive latches could cause instability in a sequential system. This instability
Sequential Logic Design Principles.Latches and Flip-Flops
 Sequential Logic Design Principles.Latches and Flip-Flops Doru Todinca Department of Computers Politehnica University of Timisoara Outline Introduction Bistable Elements Latches and Flip-Flops S-R Latch
Sequential Logic Design Principles.Latches and Flip-Flops Doru Todinca Department of Computers Politehnica University of Timisoara Outline Introduction Bistable Elements Latches and Flip-Flops S-R Latch
Experiment # 9. Clock generator circuits & Counters. Eng. Waleed Y. Mousa
 Experiment # 9 Clock generator circuits & Counters Eng. Waleed Y. Mousa 1. Objectives: 1. Understanding the principles and construction of Clock generator. 2. To be familiar with clock pulse generation
Experiment # 9 Clock generator circuits & Counters Eng. Waleed Y. Mousa 1. Objectives: 1. Understanding the principles and construction of Clock generator. 2. To be familiar with clock pulse generation
The 104 Duke_ACC Machine
 The 104 Duke_ACC Machine The goal of the next two lessons is to design and simulate a simple accumulator-based processor. The specifications for this processor and some of the QuartusII design components
The 104 Duke_ACC Machine The goal of the next two lessons is to design and simulate a simple accumulator-based processor. The specifications for this processor and some of the QuartusII design components
A New Programmable RF System for System-on-Chip Applications
 Vol. 6, o., April, 011 A ew Programmable RF System for System-on-Chip Applications Jee-Youl Ryu 1, Sung-Woo Kim 1, Jung-Hun Lee 1, Seung-Hun Park 1, and Deock-Ho Ha 1 1 Dept. of Information and Communications
Vol. 6, o., April, 011 A ew Programmable RF System for System-on-Chip Applications Jee-Youl Ryu 1, Sung-Woo Kim 1, Jung-Hun Lee 1, Seung-Hun Park 1, and Deock-Ho Ha 1 1 Dept. of Information and Communications
Encounter DFT Architect
 Full-chip, synthesis-based, power-aware test architecture development Cadence Encounter DFT Architect addresses and optimizes multiple design and manufacturing objectives such as timing, area, wiring,
Full-chip, synthesis-based, power-aware test architecture development Cadence Encounter DFT Architect addresses and optimizes multiple design and manufacturing objectives such as timing, area, wiring,
PUF Physical Unclonable Functions
 Physical Unclonable Functions Protecting next-generation Smart Card ICs with SRAM-based s The use of Smart Card ICs has become more widespread, having expanded from historical banking and telecommunication
Physical Unclonable Functions Protecting next-generation Smart Card ICs with SRAM-based s The use of Smart Card ICs has become more widespread, having expanded from historical banking and telecommunication
CHAPTER 11: Flip Flops
 CHAPTER 11: Flip Flops In this chapter, you will be building the part of the circuit that controls the command sequencing. The required circuit must operate the counter and the memory chip. When the teach
CHAPTER 11: Flip Flops In this chapter, you will be building the part of the circuit that controls the command sequencing. The required circuit must operate the counter and the memory chip. When the teach
Mathematical Model Based Total Security System with Qualitative and Quantitative Data of Human
 Int Jr of Mathematics Sciences & Applications Vol3, No1, January-June 2013 Copyright Mind Reader Publications ISSN No: 2230-9888 wwwjournalshubcom Mathematical Model Based Total Security System with Qualitative
Int Jr of Mathematics Sciences & Applications Vol3, No1, January-June 2013 Copyright Mind Reader Publications ISSN No: 2230-9888 wwwjournalshubcom Mathematical Model Based Total Security System with Qualitative
Hardware Implementation of AES Encryption and Decryption System Based on FPGA
 Send Orders for Reprints to reprints@benthamscience.ae The Open Cybernetics & Systemics Journal, 2015, 9, 1373-1377 1373 Open Access Hardware Implementation of AES Encryption and Decryption System Based
Send Orders for Reprints to reprints@benthamscience.ae The Open Cybernetics & Systemics Journal, 2015, 9, 1373-1377 1373 Open Access Hardware Implementation of AES Encryption and Decryption System Based
Chapter 1: Introduction
 Chapter 1 Introduction 1 Chapter 1: Introduction 1.1 Inspiration Cloud Computing Inspired by the cloud computing characteristics like pay per use, rapid elasticity, scalable, on demand self service, secure
Chapter 1 Introduction 1 Chapter 1: Introduction 1.1 Inspiration Cloud Computing Inspired by the cloud computing characteristics like pay per use, rapid elasticity, scalable, on demand self service, secure
Hardware Trojans Detection Methods Julien FRANCQ
 DEFENDING WORLD SECURITY Hardware Trojans Detection Methods Julien FRANCQ 2013, December the 12th Outline c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 2 /
DEFENDING WORLD SECURITY Hardware Trojans Detection Methods Julien FRANCQ 2013, December the 12th Outline c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 2 /
A New Paradigm for Synchronous State Machine Design in Verilog
 A New Paradigm for Synchronous State Machine Design in Verilog Randy Nuss Copyright 1999 Idea Consulting Introduction Synchronous State Machines are one of the most common building blocks in modern digital
A New Paradigm for Synchronous State Machine Design in Verilog Randy Nuss Copyright 1999 Idea Consulting Introduction Synchronous State Machines are one of the most common building blocks in modern digital
PrivyLink Cryptographic Key Server *
 WHITE PAPER PrivyLink Cryptographic Key * Tamper Resistant Protection of Key Information Assets for Preserving and Delivering End-to-End Trust and Values in e-businesses September 2003 E-commerce technology
WHITE PAPER PrivyLink Cryptographic Key * Tamper Resistant Protection of Key Information Assets for Preserving and Delivering End-to-End Trust and Values in e-businesses September 2003 E-commerce technology
A New Multi-site Test for System-on-Chip Using Multi-site Star Test Architecture
 A New Multi-site Test for System-on-Chip Using Multi-site Star Test Architecture Dongkwan Han, Yong Lee, and Sungho Kang As the system-on-chip (SoC) design becomes more complex, the test costs are increasing.
A New Multi-site Test for System-on-Chip Using Multi-site Star Test Architecture Dongkwan Han, Yong Lee, and Sungho Kang As the system-on-chip (SoC) design becomes more complex, the test costs are increasing.
THE ADVANTAGES OF COMBINING LOW PIN COUNT TEST WITH SCAN COMPRESSION OF VLSI TESTING
 Zbornik radova 56. Konferencije za ETRAN, Zlatibor, 11-14. juna 2012. Proc. 56th ETRAN Conference, Zlatibor, June 11-14, 2012 THE ADVANTAGES OF COMBINING LOW PIN COUNT TEST WITH SCAN COMPRESSION OF VLSI
Zbornik radova 56. Konferencije za ETRAN, Zlatibor, 11-14. juna 2012. Proc. 56th ETRAN Conference, Zlatibor, June 11-14, 2012 THE ADVANTAGES OF COMBINING LOW PIN COUNT TEST WITH SCAN COMPRESSION OF VLSI
Latches, the D Flip-Flop & Counter Design. ECE 152A Winter 2012
 Latches, the D Flip-Flop & Counter Design ECE 52A Winter 22 Reading Assignment Brown and Vranesic 7 Flip-Flops, Registers, Counters and a Simple Processor 7. Basic Latch 7.2 Gated SR Latch 7.2. Gated SR
Latches, the D Flip-Flop & Counter Design ECE 52A Winter 22 Reading Assignment Brown and Vranesic 7 Flip-Flops, Registers, Counters and a Simple Processor 7. Basic Latch 7.2 Gated SR Latch 7.2. Gated SR
THE semiconductor industry is adopting new fabrication
 896 IEEE TRANSACTIONS ON COMPUTER-AIDED DESIGN OF INTEGRATED CIRCUITS AND SYSTEMS, VOL. 26, NO. 5, MAY 2007 Local At-Speed Scan Enable Generation for Transition Fault Testing Using Low-Cost Testers Nisar
896 IEEE TRANSACTIONS ON COMPUTER-AIDED DESIGN OF INTEGRATED CIRCUITS AND SYSTEMS, VOL. 26, NO. 5, MAY 2007 Local At-Speed Scan Enable Generation for Transition Fault Testing Using Low-Cost Testers Nisar
9/14/2011 14.9.2011 8:38
 Algorithms and Implementation Platforms for Wireless Communications TLT-9706/ TKT-9636 (Seminar Course) BASICS OF FIELD PROGRAMMABLE GATE ARRAYS Waqar Hussain firstname.lastname@tut.fi Department of Computer
Algorithms and Implementation Platforms for Wireless Communications TLT-9706/ TKT-9636 (Seminar Course) BASICS OF FIELD PROGRAMMABLE GATE ARRAYS Waqar Hussain firstname.lastname@tut.fi Department of Computer
Fault Modeling. Why model faults? Some real defects in VLSI and PCB Common fault models Stuck-at faults. Transistor faults Summary
 Fault Modeling Why model faults? Some real defects in VLSI and PCB Common fault models Stuck-at faults Single stuck-at faults Fault equivalence Fault dominance and checkpoint theorem Classes of stuck-at
Fault Modeling Why model faults? Some real defects in VLSI and PCB Common fault models Stuck-at faults Single stuck-at faults Fault equivalence Fault dominance and checkpoint theorem Classes of stuck-at
Digital Systems Design! Lecture 1 - Introduction!!
 ECE 3401! Digital Systems Design! Lecture 1 - Introduction!! Course Basics Classes: Tu/Th 11-12:15, ITE 127 Instructor Mohammad Tehranipoor Office hours: T 1-2pm, or upon appointments @ ITE 441 Email:
ECE 3401! Digital Systems Design! Lecture 1 - Introduction!! Course Basics Classes: Tu/Th 11-12:15, ITE 127 Instructor Mohammad Tehranipoor Office hours: T 1-2pm, or upon appointments @ ITE 441 Email:
Programmable Logic IP Cores in SoC Design: Opportunities and Challenges
 Programmable Logic IP Cores in SoC Design: Opportunities and Challenges Steven J.E. Wilton and Resve Saleh Department of Electrical and Computer Engineering University of British Columbia Vancouver, B.C.,
Programmable Logic IP Cores in SoC Design: Opportunities and Challenges Steven J.E. Wilton and Resve Saleh Department of Electrical and Computer Engineering University of British Columbia Vancouver, B.C.,
Horst Görtz Institute for IT-Security
 Horst Görtz Institute for IT-Security On the Vulnerability of FPGA Bitstream Encryption against Power Analysis Attacks Extracting Keys from Xilinx Virtex-II FPGAs Amir Moradi, Alessandro Barenghi, Timo
Horst Görtz Institute for IT-Security On the Vulnerability of FPGA Bitstream Encryption against Power Analysis Attacks Extracting Keys from Xilinx Virtex-II FPGAs Amir Moradi, Alessandro Barenghi, Timo
Counters and Decoders
 Physics 3330 Experiment #10 Fall 1999 Purpose Counters and Decoders In this experiment, you will design and construct a 4-bit ripple-through decade counter with a decimal read-out display. Such a counter
Physics 3330 Experiment #10 Fall 1999 Purpose Counters and Decoders In this experiment, you will design and construct a 4-bit ripple-through decade counter with a decimal read-out display. Such a counter
JTAG Applications. Product Life-Cycle Support. Software Debug. Integration & Test. Figure 1. Product Life Cycle Support
 JTAG Applications While it is obvious that JTAG based testing can be used in the production phase of a product, new developments and applications of the IEEE-1149.1 standard have enabled the use of JTAG
JTAG Applications While it is obvious that JTAG based testing can be used in the production phase of a product, new developments and applications of the IEEE-1149.1 standard have enabled the use of JTAG
An On-chip Security Monitoring Solution For System Clock For Low Cost Devices
 An On-chip Security Monitoring Solution For System Clock For Low Cost Devices Frank Vater Innovations for High Performance Microelectronics Im Technologiepark 25 15236 Frankfurt (Oder), Germany vater@ihpmicroelectronics.com
An On-chip Security Monitoring Solution For System Clock For Low Cost Devices Frank Vater Innovations for High Performance Microelectronics Im Technologiepark 25 15236 Frankfurt (Oder), Germany vater@ihpmicroelectronics.com
ETEC 2301 Programmable Logic Devices. Chapter 10 Counters. Shawnee State University Department of Industrial and Engineering Technologies
 ETEC 2301 Programmable Logic Devices Chapter 10 Counters Shawnee State University Department of Industrial and Engineering Technologies Copyright 2007 by Janna B. Gallaher Asynchronous Counter Operation
ETEC 2301 Programmable Logic Devices Chapter 10 Counters Shawnee State University Department of Industrial and Engineering Technologies Copyright 2007 by Janna B. Gallaher Asynchronous Counter Operation
FAULT TOLERANCE FOR MULTIPROCESSOR SYSTEMS VIA TIME REDUNDANT TASK SCHEDULING
 FAULT TOLERANCE FOR MULTIPROCESSOR SYSTEMS VIA TIME REDUNDANT TASK SCHEDULING Hussain Al-Asaad and Alireza Sarvi Department of Electrical & Computer Engineering University of California Davis, CA, U.S.A.
FAULT TOLERANCE FOR MULTIPROCESSOR SYSTEMS VIA TIME REDUNDANT TASK SCHEDULING Hussain Al-Asaad and Alireza Sarvi Department of Electrical & Computer Engineering University of California Davis, CA, U.S.A.
Data Deduplication Scheme for Cloud Storage
 26 Data Deduplication Scheme for Cloud Storage 1 Iuon-Chang Lin and 2 Po-Ching Chien Abstract Nowadays, the utilization of storage capacity becomes an important issue in cloud storage. In this paper, we
26 Data Deduplication Scheme for Cloud Storage 1 Iuon-Chang Lin and 2 Po-Ching Chien Abstract Nowadays, the utilization of storage capacity becomes an important issue in cloud storage. In this paper, we
Research Article. ISSN 2347-9523 (Print) *Corresponding author Shi-hai Zhu Email:
 Scholars Journal of Engineering and Technology (SJET) Sch. J. Eng. Tech., 2014; 2(3A):352-357 Scholars Academic and Scientific Publisher (An International Publisher for Academic and Scientific Resources)
Scholars Journal of Engineering and Technology (SJET) Sch. J. Eng. Tech., 2014; 2(3A):352-357 Scholars Academic and Scientific Publisher (An International Publisher for Academic and Scientific Resources)
150127-Microprocessor & Assembly Language
 Chapter 3 Z80 Microprocessor Architecture The Z 80 is one of the most talented 8 bit microprocessors, and many microprocessor-based systems are designed around the Z80. The Z80 microprocessor needs an
Chapter 3 Z80 Microprocessor Architecture The Z 80 is one of the most talented 8 bit microprocessors, and many microprocessor-based systems are designed around the Z80. The Z80 microprocessor needs an
The Reduced Address Space (RAS) for Application Memory Authentication
 The Reduced Address Space (RAS) for Application Memory Authentication David Champagne, Reouven Elbaz and Ruby B. Lee Princeton University, USA Introduction Background: TPM, XOM, AEGIS, SP, SecureBlue want
The Reduced Address Space (RAS) for Application Memory Authentication David Champagne, Reouven Elbaz and Ruby B. Lee Princeton University, USA Introduction Background: TPM, XOM, AEGIS, SP, SecureBlue want
Lecture 5: Gate Logic Logic Optimization
 Lecture 5: Gate Logic Logic Optimization MAH, AEN EE271 Lecture 5 1 Overview Reading McCluskey, Logic Design Principles- or any text in boolean algebra Introduction We could design at the level of irsim
Lecture 5: Gate Logic Logic Optimization MAH, AEN EE271 Lecture 5 1 Overview Reading McCluskey, Logic Design Principles- or any text in boolean algebra Introduction We could design at the level of irsim
Microsemi Security Center of Excellence
 Microsemi Security Center of Excellence Sales and FAE Training August 24, 2015 1 Outline What is the Security Center of Excellence (SCoE)? Overview of Microsemi s Security capabilities and expertise Threat
Microsemi Security Center of Excellence Sales and FAE Training August 24, 2015 1 Outline What is the Security Center of Excellence (SCoE)? Overview of Microsemi s Security capabilities and expertise Threat
Network Security Technology Network Management
 COMPUTER NETWORKS Network Security Technology Network Management Source Encryption E(K,P) Decryption D(K,C) Destination The author of these slides is Dr. Mark Pullen of George Mason University. Permission
COMPUTER NETWORKS Network Security Technology Network Management Source Encryption E(K,P) Decryption D(K,C) Destination The author of these slides is Dr. Mark Pullen of George Mason University. Permission
AN IMPROVED DESIGN OF REVERSIBLE BINARY TO BINARY CODED DECIMAL CONVERTER FOR BINARY CODED DECIMAL MULTIPLICATION
 American Journal of Applied Sciences 11 (1): 69-73, 2014 ISSN: 1546-9239 2014 Science Publication doi:10.3844/ajassp.2014.69.73 Published Online 11 (1) 2014 (http://www.thescipub.com/ajas.toc) AN IMPROVED
American Journal of Applied Sciences 11 (1): 69-73, 2014 ISSN: 1546-9239 2014 Science Publication doi:10.3844/ajassp.2014.69.73 Published Online 11 (1) 2014 (http://www.thescipub.com/ajas.toc) AN IMPROVED
Lecture 8: Synchronous Digital Systems
 Lecture 8: Synchronous Digital Systems The distinguishing feature of a synchronous digital system is that the circuit only changes in response to a system clock. For example, consider the edge triggered
Lecture 8: Synchronous Digital Systems The distinguishing feature of a synchronous digital system is that the circuit only changes in response to a system clock. For example, consider the edge triggered
An Effective Deterministic BIST Scheme for Shifter/Accumulator Pairs in Datapaths
 An Effective Deterministic BIST Scheme for Shifter/Accumulator Pairs in Datapaths N. KRANITIS M. PSARAKIS D. GIZOPOULOS 2 A. PASCHALIS 3 Y. ZORIAN 4 Institute of Informatics & Telecommunications, NCSR
An Effective Deterministic BIST Scheme for Shifter/Accumulator Pairs in Datapaths N. KRANITIS M. PSARAKIS D. GIZOPOULOS 2 A. PASCHALIS 3 Y. ZORIAN 4 Institute of Informatics & Telecommunications, NCSR
Implementation of Modified Booth Algorithm (Radix 4) and its Comparison with Booth Algorithm (Radix-2)
 Advance in Electronic and Electric Engineering. ISSN 2231-1297, Volume 3, Number 6 (2013), pp. 683-690 Research India Publications http://www.ripublication.com/aeee.htm Implementation of Modified Booth
Advance in Electronic and Electric Engineering. ISSN 2231-1297, Volume 3, Number 6 (2013), pp. 683-690 Research India Publications http://www.ripublication.com/aeee.htm Implementation of Modified Booth
ON SUITABILITY OF FPGA BASED EVOLVABLE HARDWARE SYSTEMS TO INTEGRATE RECONFIGURABLE CIRCUITS WITH HOST PROCESSING UNIT
 216 ON SUITABILITY OF FPGA BASED EVOLVABLE HARDWARE SYSTEMS TO INTEGRATE RECONFIGURABLE CIRCUITS WITH HOST PROCESSING UNIT *P.Nirmalkumar, **J.Raja Paul Perinbam, @S.Ravi and #B.Rajan *Research Scholar,
216 ON SUITABILITY OF FPGA BASED EVOLVABLE HARDWARE SYSTEMS TO INTEGRATE RECONFIGURABLE CIRCUITS WITH HOST PROCESSING UNIT *P.Nirmalkumar, **J.Raja Paul Perinbam, @S.Ravi and #B.Rajan *Research Scholar,
ADVANCED IC REVERSE ENGINEERING TECHNIQUES: IN DEPTH ANALYSIS OF A MODERN SMART CARD. Olivier THOMAS Blackhat USA 2015
 ADVANCED IC REVERSE ENGINEERING TECHNIQUES: IN DEPTH ANALYSIS OF A MODERN SMART CARD Olivier THOMAS Blackhat USA 2015 About Texplained Texplained [Technology Explained] refers
ADVANCED IC REVERSE ENGINEERING TECHNIQUES: IN DEPTH ANALYSIS OF A MODERN SMART CARD Olivier THOMAS Blackhat USA 2015 About Texplained Texplained [Technology Explained] refers
Design and Analysis of Parallel AES Encryption and Decryption Algorithm for Multi Processor Arrays
 IOSR Journal of VLSI and Signal Processing (IOSR-JVSP) Volume 5, Issue, Ver. III (Jan - Feb. 205), PP 0- e-issn: 239 4200, p-issn No. : 239 497 www.iosrjournals.org Design and Analysis of Parallel AES
IOSR Journal of VLSI and Signal Processing (IOSR-JVSP) Volume 5, Issue, Ver. III (Jan - Feb. 205), PP 0- e-issn: 239 4200, p-issn No. : 239 497 www.iosrjournals.org Design and Analysis of Parallel AES
Victor Shoup Avi Rubin. fshoup,rubing@bellcore.com. Abstract
 Session Key Distribution Using Smart Cards Victor Shoup Avi Rubin Bellcore, 445 South St., Morristown, NJ 07960 fshoup,rubing@bellcore.com Abstract In this paper, we investigate a method by which smart
Session Key Distribution Using Smart Cards Victor Shoup Avi Rubin Bellcore, 445 South St., Morristown, NJ 07960 fshoup,rubing@bellcore.com Abstract In this paper, we investigate a method by which smart
Hardware Security Modules for Protecting Embedded Systems
 Hardware Security Modules for Protecting Embedded Systems Marko Wolf, ESCRYPT GmbH Embedded Security, Munich, Germany André Weimerskirch, ESCRYPT Inc. Embedded Security, Ann Arbor, USA 1 Introduction &
Hardware Security Modules for Protecting Embedded Systems Marko Wolf, ESCRYPT GmbH Embedded Security, Munich, Germany André Weimerskirch, ESCRYPT Inc. Embedded Security, Ann Arbor, USA 1 Introduction &
SECURE IMPLEMENTATIONS OF CONTENT PROTECTION (DRM) SCHEMES ON CONSUMER ELECTRONIC DEVICES
 SECURE IMPLEMENTATIONS OF CONTENT PROTECTION (DRM) SCHEMES ON CONSUMER ELECTRONIC DEVICES Contents Introduction... 3 DRM Threat Model... 3 DRM Flow... 4 DRM Assets... 5 Threat Model... 5 Protection of
SECURE IMPLEMENTATIONS OF CONTENT PROTECTION (DRM) SCHEMES ON CONSUMER ELECTRONIC DEVICES Contents Introduction... 3 DRM Threat Model... 3 DRM Flow... 4 DRM Assets... 5 Threat Model... 5 Protection of
Introduction to CMOS VLSI Design (E158) Lecture 8: Clocking of VLSI Systems
 Harris Introduction to CMOS VLSI Design (E158) Lecture 8: Clocking of VLSI Systems David Harris Harvey Mudd College David_Harris@hmc.edu Based on EE271 developed by Mark Horowitz, Stanford University MAH
Harris Introduction to CMOS VLSI Design (E158) Lecture 8: Clocking of VLSI Systems David Harris Harvey Mudd College David_Harris@hmc.edu Based on EE271 developed by Mark Horowitz, Stanford University MAH
Joint Interpretation Library
 for smart cards and similar devices Document purpose: provide requirements to developers and guidance to evaluators to fulfill the Security Architecture requirements of CC V3 ADV_ARC family. Version 2.0
for smart cards and similar devices Document purpose: provide requirements to developers and guidance to evaluators to fulfill the Security Architecture requirements of CC V3 ADV_ARC family. Version 2.0
Lecture 9 - Message Authentication Codes
 Lecture 9 - Message Authentication Codes Boaz Barak March 1, 2010 Reading: Boneh-Shoup chapter 6, Sections 9.1 9.3. Data integrity Until now we ve only been interested in protecting secrecy of data. However,
Lecture 9 - Message Authentication Codes Boaz Barak March 1, 2010 Reading: Boneh-Shoup chapter 6, Sections 9.1 9.3. Data integrity Until now we ve only been interested in protecting secrecy of data. However,
DIGITAL ELECTRONICS. Counters. By: Electrical Engineering Department
 Counters By: Electrical Engineering Department 1 Counters Upon completion of the chapter, students should be able to:.1 Understand the basic concepts of asynchronous counter and synchronous counters, and
Counters By: Electrical Engineering Department 1 Counters Upon completion of the chapter, students should be able to:.1 Understand the basic concepts of asynchronous counter and synchronous counters, and
Switch Fabric Implementation Using Shared Memory
 Order this document by /D Switch Fabric Implementation Using Shared Memory Prepared by: Lakshmi Mandyam and B. Kinney INTRODUCTION Whether it be for the World Wide Web or for an intra office network, today
Order this document by /D Switch Fabric Implementation Using Shared Memory Prepared by: Lakshmi Mandyam and B. Kinney INTRODUCTION Whether it be for the World Wide Web or for an intra office network, today
NTE2053 Integrated Circuit 8 Bit MPU Compatible A/D Converter
 NTE2053 Integrated Circuit 8 Bit MPU Compatible A/D Converter Description: The NTE2053 is a CMOS 8 bit successive approximation Analog to Digital converter in a 20 Lead DIP type package which uses a differential
NTE2053 Integrated Circuit 8 Bit MPU Compatible A/D Converter Description: The NTE2053 is a CMOS 8 bit successive approximation Analog to Digital converter in a 20 Lead DIP type package which uses a differential
A STUDY OF INSTRUMENT REUSE AND RETARGETING IN P1687
 A STUDY OF INSTRUMENT REUSE AND RETARGETING IN P1687 Farrokh Ghani Zadegan, Urban Ingelsson, Erik Larsson Linköping University Gunnar Carlsson Ericsson ABSTRACT Modern chips may contain a large number
A STUDY OF INSTRUMENT REUSE AND RETARGETING IN P1687 Farrokh Ghani Zadegan, Urban Ingelsson, Erik Larsson Linköping University Gunnar Carlsson Ericsson ABSTRACT Modern chips may contain a large number
Modeling Latches and Flip-flops
 Lab Workbook Introduction Sequential circuits are digital circuits in which the output depends not only on the present input (like combinatorial circuits), but also on the past sequence of inputs. In effect,
Lab Workbook Introduction Sequential circuits are digital circuits in which the output depends not only on the present input (like combinatorial circuits), but also on the past sequence of inputs. In effect,
A comprehensive survey on various ETC techniques for secure Data transmission
 A comprehensive survey on various ETC techniques for secure Data transmission Shaikh Nasreen 1, Prof. Suchita Wankhade 2 1, 2 Department of Computer Engineering 1, 2 Trinity College of Engineering and
A comprehensive survey on various ETC techniques for secure Data transmission Shaikh Nasreen 1, Prof. Suchita Wankhade 2 1, 2 Department of Computer Engineering 1, 2 Trinity College of Engineering and
Decimal Number (base 10) Binary Number (base 2)
 LECTURE 5. BINARY COUNTER Before starting with counters there is some vital information that needs to be understood. The most important is the fact that since the outputs of a digital chip can only be
LECTURE 5. BINARY COUNTER Before starting with counters there is some vital information that needs to be understood. The most important is the fact that since the outputs of a digital chip can only be
Testing & Verification of Digital Circuits ECE/CS 5745/6745. Hardware Verification using Symbolic Computation
 Testing & Verification of Digital Circuits ECE/CS 5745/6745 Hardware Verification using Symbolic Computation Instructor: Priyank Kalla (kalla@ece.utah.edu) 3 Credits Mon, Wed, 1:25-2:45pm, WEB L105 Office
Testing & Verification of Digital Circuits ECE/CS 5745/6745 Hardware Verification using Symbolic Computation Instructor: Priyank Kalla (kalla@ece.utah.edu) 3 Credits Mon, Wed, 1:25-2:45pm, WEB L105 Office
Split Based Encryption in Secure File Transfer
 Split Based Encryption in Secure File Transfer Parul Rathor, Rohit Sehgal Assistant Professor, Dept. of CSE, IET, Nagpur University, India Assistant Professor, Dept. of CSE, IET, Alwar, Rajasthan Technical
Split Based Encryption in Secure File Transfer Parul Rathor, Rohit Sehgal Assistant Professor, Dept. of CSE, IET, Nagpur University, India Assistant Professor, Dept. of CSE, IET, Alwar, Rajasthan Technical
Application of Automatic Variable Password Technique in Das s Remote System Authentication Scheme Using Smart Card
 Application of Automatic Variable Password Technique in Das s Remote System Authentication Scheme Using Smart Card C. Koner, Member, IACSIT, C. T. Bhunia, Sr. Member, IEEE and U. Maulik, Sr. Member, IEEE
Application of Automatic Variable Password Technique in Das s Remote System Authentication Scheme Using Smart Card C. Koner, Member, IACSIT, C. T. Bhunia, Sr. Member, IEEE and U. Maulik, Sr. Member, IEEE
CMOS Binary Full Adder
 CMOS Binary Full Adder A Survey of Possible Implementations Group : Eren Turgay Aaron Daniels Michael Bacelieri William Berry - - Table of Contents Key Terminology...- - Introduction...- 3 - Design Architectures...-
CMOS Binary Full Adder A Survey of Possible Implementations Group : Eren Turgay Aaron Daniels Michael Bacelieri William Berry - - Table of Contents Key Terminology...- - Introduction...- 3 - Design Architectures...-
Outline Intrusion Detection CS 239 Security for Networks and System Software June 3, 2002
 Outline Intrusion Detection CS 239 Security for Networks and System Software June 3, 2002 Introduction Characteristics of intrusion detection systems Some sample intrusion detection systems Page 1 Page
Outline Intrusion Detection CS 239 Security for Networks and System Software June 3, 2002 Introduction Characteristics of intrusion detection systems Some sample intrusion detection systems Page 1 Page
Development of Low Cost Private Office Access Control System(OACS)
 Development of Low Cost Private Office Access Control System(OACS) Sadeque Reza Khan Prime University, Department of Electrical and Electronic Engineering, Dhaka-1216, Bangladesh sadeque_008@yahoo.com
Development of Low Cost Private Office Access Control System(OACS) Sadeque Reza Khan Prime University, Department of Electrical and Electronic Engineering, Dhaka-1216, Bangladesh sadeque_008@yahoo.com
Solutions for Increasing the Number of PC Parallel Port Control and Selecting Lines
 Solutions for Increasing the Number of PC Parallel Port Control and Selecting Lines Mircea Popa Abstract: The paper approaches the problem of control and selecting possibilities offered by the PC parallel
Solutions for Increasing the Number of PC Parallel Port Control and Selecting Lines Mircea Popa Abstract: The paper approaches the problem of control and selecting possibilities offered by the PC parallel
GETTING STARTED WITH PROGRAMMABLE LOGIC DEVICES, THE 16V8 AND 20V8
 GETTING STARTED WITH PROGRAMMABLE LOGIC DEVICES, THE 16V8 AND 20V8 Robert G. Brown All Rights Reserved August 25, 2000 Alta Engineering 58 Cedar Lane New Hartford, CT 06057-2905 (860) 489-8003 www.alta-engineering.com
GETTING STARTED WITH PROGRAMMABLE LOGIC DEVICES, THE 16V8 AND 20V8 Robert G. Brown All Rights Reserved August 25, 2000 Alta Engineering 58 Cedar Lane New Hartford, CT 06057-2905 (860) 489-8003 www.alta-engineering.com
FPGA BASED HARDWARE KEY FOR TEMPORAL ENCRYPTION
 FPGA BASED HARDWARE KEY FOR TEMPORAL ENCRYPTION Abstract In this paper, a novel encryption scheme with time based key technique on an FPGA is presented. Time based key technique ensures right key to be
FPGA BASED HARDWARE KEY FOR TEMPORAL ENCRYPTION Abstract In this paper, a novel encryption scheme with time based key technique on an FPGA is presented. Time based key technique ensures right key to be
Intrusion Detection and Cyber Security Monitoring of SCADA and DCS Networks
 Intrusion Detection and Cyber Security Monitoring of SCADA and DCS Networks Dale Peterson Director, Network Security Practice Digital Bond, Inc. 1580 Sawgrass Corporate Parkway, Suite 130 Sunrise, FL 33323
Intrusion Detection and Cyber Security Monitoring of SCADA and DCS Networks Dale Peterson Director, Network Security Practice Digital Bond, Inc. 1580 Sawgrass Corporate Parkway, Suite 130 Sunrise, FL 33323
Lecture 7: Clocking of VLSI Systems
 Lecture 7: Clocking of VLSI Systems MAH, AEN EE271 Lecture 7 1 Overview Reading Wolf 5.3 Two-Phase Clocking (good description) W&E 5.5.1, 5.5.2, 5.5.3, 5.5.4, 5.5.9, 5.5.10 - Clocking Note: The analysis
Lecture 7: Clocking of VLSI Systems MAH, AEN EE271 Lecture 7 1 Overview Reading Wolf 5.3 Two-Phase Clocking (good description) W&E 5.5.1, 5.5.2, 5.5.3, 5.5.4, 5.5.9, 5.5.10 - Clocking Note: The analysis
DIGITAL TECHNICS II. Dr. Bálint Pődör. Óbuda University, Microelectronics and Technology Institute. 2nd (Spring) term 2012/2013
 DIGITAL TECHNICS II Dr. Bálint Pődör Óbuda University, Microelectronics and Technology Institute 4. LECTURE: COUNTERS AND RELATED 2nd (Spring) term 2012/2013 1 4. LECTURE: COUNTERS AND RELATED 1. Counters,
DIGITAL TECHNICS II Dr. Bálint Pődör Óbuda University, Microelectronics and Technology Institute 4. LECTURE: COUNTERS AND RELATED 2nd (Spring) term 2012/2013 1 4. LECTURE: COUNTERS AND RELATED 1. Counters,
Asynchronous IC Interconnect Network Design and Implementation Using a Standard ASIC Flow
 Asynchronous IC Interconnect Network Design and Implementation Using a Standard ASIC Flow Bradley R. Quinton Dept. of Electrical and Computer Engineering University of British Columbia bradq@ece.ubc.ca
Asynchronous IC Interconnect Network Design and Implementation Using a Standard ASIC Flow Bradley R. Quinton Dept. of Electrical and Computer Engineering University of British Columbia bradq@ece.ubc.ca
Hardware Implementation of Improved Adaptive NoC Router with Flit Flow History based Load Balancing Selection Strategy
 Hardware Implementation of Improved Adaptive NoC Rer with Flit Flow History based Load Balancing Selection Strategy Parag Parandkar 1, Sumant Katiyal 2, Geetesh Kwatra 3 1,3 Research Scholar, School of
Hardware Implementation of Improved Adaptive NoC Rer with Flit Flow History based Load Balancing Selection Strategy Parag Parandkar 1, Sumant Katiyal 2, Geetesh Kwatra 3 1,3 Research Scholar, School of
ASYNCHRONOUS COUNTERS
 LB no.. SYNCHONOUS COUNTES. Introduction Counters are sequential logic circuits that counts the pulses applied at their clock input. They usually have 4 bits, delivering at the outputs the corresponding
LB no.. SYNCHONOUS COUNTES. Introduction Counters are sequential logic circuits that counts the pulses applied at their clock input. They usually have 4 bits, delivering at the outputs the corresponding
COMBINATIONAL and SEQUENTIAL LOGIC CIRCUITS Hardware implementation and software design
 PH-315 COMINATIONAL and SEUENTIAL LOGIC CIRCUITS Hardware implementation and software design A La Rosa I PURPOSE: To familiarize with combinational and sequential logic circuits Combinational circuits
PH-315 COMINATIONAL and SEUENTIAL LOGIC CIRCUITS Hardware implementation and software design A La Rosa I PURPOSE: To familiarize with combinational and sequential logic circuits Combinational circuits
CryptoFirewall Technology Introduction
 CryptoFirewall Technology Introduction Cryptography Research, Inc. www.cryptography.com 575 Market St., 21 st Floor, San Francisco, CA 94105 1998-2007 Cryptography Research, Inc. Protected under issued
CryptoFirewall Technology Introduction Cryptography Research, Inc. www.cryptography.com 575 Market St., 21 st Floor, San Francisco, CA 94105 1998-2007 Cryptography Research, Inc. Protected under issued
MF1 IC S50. 1. General description. Functional specification. 1.1 Contactless Energy and Data Transfer. 1.2 Anticollision. Energy
 Rev. 5.2 15 January 2007 Product data sheet 001052 PUBLIC 1. General description NXP has developed the Mifare to be used in contactess smart cards according to ISO/IEC 14443A. The communication layer (
Rev. 5.2 15 January 2007 Product data sheet 001052 PUBLIC 1. General description NXP has developed the Mifare to be used in contactess smart cards according to ISO/IEC 14443A. The communication layer (
ISSCC 2003 / SESSION 13 / 40Gb/s COMMUNICATION ICS / PAPER 13.7
 ISSCC 2003 / SESSION 13 / 40Gb/s COMMUNICATION ICS / PAPER 13.7 13.7 A 40Gb/s Clock and Data Recovery Circuit in 0.18µm CMOS Technology Jri Lee, Behzad Razavi University of California, Los Angeles, CA
ISSCC 2003 / SESSION 13 / 40Gb/s COMMUNICATION ICS / PAPER 13.7 13.7 A 40Gb/s Clock and Data Recovery Circuit in 0.18µm CMOS Technology Jri Lee, Behzad Razavi University of California, Los Angeles, CA
Chapter 13: Verification
 Chapter 13: Verification Prof. Ming-Bo Lin Department of Electronic Engineering National Taiwan University of Science and Technology Digital System Designs and Practices Using Verilog HDL and FPGAs @ 2008-2010,
Chapter 13: Verification Prof. Ming-Bo Lin Department of Electronic Engineering National Taiwan University of Science and Technology Digital System Designs and Practices Using Verilog HDL and FPGAs @ 2008-2010,
Pertinent Side Channel Attacks on Elliptic Curve Cryptographic Systems
 Pertinent Side Channel Attacks on Elliptic Curve Cryptographic Systems Stanford University CS259c/MATH250: Elliptic Curves in Cryptography December 15, 2011 1 Introduction Elliptic curve cryptosystems
Pertinent Side Channel Attacks on Elliptic Curve Cryptographic Systems Stanford University CS259c/MATH250: Elliptic Curves in Cryptography December 15, 2011 1 Introduction Elliptic curve cryptosystems
