RSA Security Analytics Certified Administrator (CA) Certification Examination Study Guide
|
|
|
- Daniel Baldwin
- 8 years ago
- Views:
Transcription
1 RSA Security Analytics Certified Administrator (CA) Certification Examination Study Guide Introduction The RSA Security Analytics Certified Administrator (CA) examination is based on the critical job functions that an individual would typically be expected to perform with competence when administering the RSA Security Analytics product. An RSA Security Analytics CA is a person who has an IT administrator, IS Analyst, or Security Operations role within an organization. An analysis of the major job functions expected of an RSA Security Analytics CA determined that there are three major areas of job role responsibility: General awareness of the functions and capabilities of the product Configuration and management of the product Monitoring and troubleshooting product operation Candidate Background and Experience An RSA Security Analytics CA candidate should have a minimum of two years of experience in one or more of the following technical areas and understand how these technologies relate to and integrate with the RSA Security Analytics product. Elements of the CA exam touch upon these areas: Previous experience in computer and network operations, information security, system administration, or another related area. Familiarity with most basic system administration tools and processes. Experience in user management, managing reports, and security-related tasks. Experience using the Windows operating system and a web browser. Troubleshooting and problem determination skills. Examination Domains The RSA Security Analytics CA is comprised of three major Domains (subject areas). Each Domain is represented by a series of questions designed to evaluate competence and knowledge of elements relating to that domain. The following table describes the proportion of the examination that relates to each domain: Domain % of Examination 1. General product knowledge features, functions and capabilities 50 % 2. System configurations 35 % 3. Monitoring and Troubleshooting 15 % TOTAL 100 %
2 Domain 1.0: General product knowledge features, functions and capabilities The RSA Security Analytics CA must have a fundamental knowledge of key features and benefits of the RSA Security Analytics product. The RSA Security Analytics CA is expected to be able to identify the functions that highlight the product features and capabilities within a customer s environment and understand how the product can be used to identify security concerns. Content Areas Architecture - Deployment scenarios - Virtual environment - User interface Data collection - Packet capture - Log collection User management - Device users - Roles and Groups Domain 1.0 Sample Items Which of the following is processed last for log traffic within RSA Security Analytics? Network Rules Event Correlation Rules Berkley Packet Filtration Feeds B is the correct choice. Which statement is correct concerning the external storage options for RSA Security Analytics? DAS typically costs twice as much as SAN SAN is typically deployed in environments with very short retention periods DAS typically scales much higher than SAN SAN typically scales much higher than DAS D is the correct choice Which of the following alerting mechanisms is NOT supported by RSA Security Analytics? Syslog SMTP SNMP POP3 D is the correct choice..
3 Domain 2.0: System configurations The RSA Security Analytics CA must have a fundamental knowledge of the key configurations of the RSA Security Analytics product and how to effect system changes to help gather data and provide consolidated metadata for analysis. Content Areas Configurations - Device configuration - Configuring Live - Custom Feeds - Warehouse and Warehouse Connector configuration - Archiver configuration - Configuring Malware Analysis Rules - Rule data flow - Network rules - Application rules - Correlation rules Domain 2.0 Sample Items An RSA Security Analytics Rule is associated with which of the following actions? (choose two) Retaining data for analysis Distributing data among RSA Security Analytics appliances Filtering data for analysis Adding contextual content to network traffic Deleting data that is too old for analysis A and C are the correct choices. RSA Security Analytics can leverage intelligence from the global security community through Live Investigation Alerter Warehouse A is the correct choice. Which of the following components is responsible for indexing metadata in the RSA Security Analytics system? Decoder Concentrator Broker Warehouse B is the correct choice.
4 Domain 3.0:Monitoring and Troubleshooting The RSA Security Analytics CA must have a fundamental knowledge of key monitoring and reporting features in the RSA Security Analytics product, understand what may indicate improper operation, and understand approaches for problem resolution or for seeking further technical assistance. Content Areas Monitoring the environment - Device and system statistics - Concentrator aggregation Performance - Query performance - Tuning the Index - REST API Troubleshooting - Resetting the databases - Viewing logs - Log collection - Crash Reporter Domain 3.0 Sample Items Which of the following is an RSA Security Analytics decoder index file that should never be modified? index-rsa-.xml index-decoder.xml index-default.xml index-system.xml B is the correct choice. When testing rules, reports and charts, which of the following statements is most accurate? a smaller time window is better for testing at least 256 data points are needed for testing regardless of time period larger time windows yield more accurate results the length of time is irrelevant to testing A is the correct choice. The slowest Concentrator device in a system will limit the speed of which of the following? alerts and notifications data warehousing query results log data collection C is the correct choice.
5 Examination Preparation Product Training Although RSA Security Analytics product training is not a strict requirement in preparation for the examination, it is highly recommended. Statistics show that approximately 83% of the candidates who successfully pass the exam on their first attempt have attended RSA training prior to testing. RSA Education Services offers the following courses that relate to the RSA Security Analytics product and material covered on the exam: RSA Security Analytics Administration - The course provides an overview of the RSA Security Analytics product, hands-on configuration of components, managing users, and creating filters and rules. Additionally, the course covers integration with RSA envision and monitoring capabilities. For full and detailed descriptions of RSA Security course offerings, visit: Product Experience Many of the areas addressed by the exam will be familiar to the candidate who has worked with the product through administrative operations. The exam content areas cover a wide range of product functions because an RSA Security Analytics CA may be called upon to assist with deployments, work closely with and educate end users, and maintain the day-to-day operation of the product across a variety of scenarios. Study and Preparation Materials As is common with other industry certification exams, RSA Security Analytics CA examination questions were constructed, reviewed, edited, and refined by groups of subject matter experts. A requirement of each test item is that it be referenced to a definitive source document, publication, product menu selection, etc. Therefore, a finite set of preparation materials can be recommended for study and exam preparation. Although not all of the materials listed below are available in the public domain, the list does constitute a body of knowledge from which examination test items have been drawn. RSA Security Analytics Training Materials (Available only as part of an RSA Security Analytics training course) - RSA Security Analytics Administration Course Student Guide RSA Security Analytics product documentation (Available with the product or through RSA SecurCare Online) RSA Security Analytics Help Menus and Help Screens
6 Examination Details Testing Centers, Locations, and Registration The examination is administered by the Pearson VUE organization an internationally known examination provider. Examination centers are located worldwide. Visit the Pearson VUE web site ( and use the Test Center Locator to find a testing facility convenient to you. You may also use the Pearson VUE site to create a personal login account and register for an exam. The RSA Security Analytics Certified Administrator exam code is CARSASA01. Exam Questions The exam consists of 71 questions to be completed in 90 minutes. The exam consists of multiple-choice, multiple-response, or true/false type questions. The exam is computer-based and closed book you may not utilize any printed material, personal computers, calculators, cell phones, etc. during the test. The minimum passing score is 70%. Test results are calculated automatically at the conclusion of the test and testing center personnel can usually provide you with an authorized copy of your results before you leave the testing center. Exam Costs The fee for taking the exam is US$ Language Availability The RSA Security Analytics Certified Administrator exam is available in English. What to expect at the Testing Center You must present two forms of identification; one of which is a photo ID. You will be required to accept the terms of an RSA Certified Security Professional Certification Non-Disclosure Agreement before beginning the examination. Re-taking the Exam There is no limit on the number of times that you can re-take the certification exam. However, to maintain integrity and confidentiality of the test items, 14 days is the required elapsed time before retaking the test a third time. Please note that you must pay the full exam fee each time that you retake the test. Last Revised March 21, 2014
RSA Archer Certified Administrator (CA) Certification Examination Study Guide
 RSA Archer Certified Administrator (CA) Certification Examination Study Guide Introduction The RSA Archer Certified Administrator (CA) examination is based on the critical job functions that an individual
RSA Archer Certified Administrator (CA) Certification Examination Study Guide Introduction The RSA Archer Certified Administrator (CA) examination is based on the critical job functions that an individual
RSA SecurID Certified Administrator (RSA Authentication Manager 8.0) Certification Examination Study Guide
 RSA SecurID Certified Administrator (RSA Authentication Manager 8.0) Certification Examination Study Guide Introduction The RSA SecurID Certified Administrator (CA) examination is based on the critical
RSA SecurID Certified Administrator (RSA Authentication Manager 8.0) Certification Examination Study Guide Introduction The RSA SecurID Certified Administrator (CA) examination is based on the critical
RSA Security Analytics Security Analytics System Overview
 RSA Security Analytics Security Analytics System Overview Copyright 2010-2015 RSA, the Security Division of EMC. All rights reserved. Trademarks RSA, the RSA Logo and EMC are either registered trademarks
RSA Security Analytics Security Analytics System Overview Copyright 2010-2015 RSA, the Security Division of EMC. All rights reserved. Trademarks RSA, the RSA Logo and EMC are either registered trademarks
10233B: Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010
 Course: 10233B: Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 Description: About this Course This five-day, instructor-led course provides you with the knowledge and skills
Course: 10233B: Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 Description: About this Course This five-day, instructor-led course provides you with the knowledge and skills
Microsoft 10233 - Design and Deploy Messaging Solutions with Microsoft Exchange Server 2010
 1800 ULEARN (853 276) www.ddls.com.au Microsoft 10233 - Design and Deploy Messaging Solutions with Microsoft Exchange Server 2010 Length 5 days Price $4169.00 (inc GST) Overview This five-day, instructor-led
1800 ULEARN (853 276) www.ddls.com.au Microsoft 10233 - Design and Deploy Messaging Solutions with Microsoft Exchange Server 2010 Length 5 days Price $4169.00 (inc GST) Overview This five-day, instructor-led
What s New in Security Analytics 10.4. Be the Hunter.. Not the Hunted
 What s New in Security Analytics 10.4 Be the Hunter.. Not the Hunted Attackers Are Outpacing Detection Attacker Capabilities Time To Discovery Source: VERIZON 2014 DATA BREACH INVESTIGATIONS REPORT 2 TRANSFORM
What s New in Security Analytics 10.4 Be the Hunter.. Not the Hunted Attackers Are Outpacing Detection Attacker Capabilities Time To Discovery Source: VERIZON 2014 DATA BREACH INVESTIGATIONS REPORT 2 TRANSFORM
Salesforce Certified Data Architecture and Management Designer. Study Guide. Summer 16 TRAINING & CERTIFICATION
 Salesforce Certified Data Architecture and Management Designer Study Guide Summer 16 Contents SECTION 1. PURPOSE OF THIS STUDY GUIDE... 2 SECTION 2. ABOUT THE SALESFORCE CERTIFIED DATA ARCHITECTURE AND
Salesforce Certified Data Architecture and Management Designer Study Guide Summer 16 Contents SECTION 1. PURPOSE OF THIS STUDY GUIDE... 2 SECTION 2. ABOUT THE SALESFORCE CERTIFIED DATA ARCHITECTURE AND
Configuring and Managing Microsoft System Center Essentials 2010
 Configuring and Managing Microsoft System Center Essentials 2010 50373: Configuring and Managing Microsoft System Center Essentials 2010 (2 Days) About this Course This two-day instructor-led course provides
Configuring and Managing Microsoft System Center Essentials 2010 50373: Configuring and Managing Microsoft System Center Essentials 2010 (2 Days) About this Course This two-day instructor-led course provides
Adobe Analytics Business Practitioner Adobe Certified Expert Exam Guide. Exam number: 9A0-381
 Adobe Analytics Business Practitioner Adobe Certified Expert Exam Guide Exam number: 9A0-381 Revised 24 June 2015 About Adobe Certified Expert Exams To be an Adobe Certified Expert is to demonstrate expertise
Adobe Analytics Business Practitioner Adobe Certified Expert Exam Guide Exam number: 9A0-381 Revised 24 June 2015 About Adobe Certified Expert Exams To be an Adobe Certified Expert is to demonstrate expertise
Certified Lead System Architect
 White Paper Certified Lead System Architect EXAM BLUEPRINT Copyright 2016 Pegasystems Inc., Cambridge, MA All rights reserved. This document describes products and services of Pegasystems Inc. It may contain
White Paper Certified Lead System Architect EXAM BLUEPRINT Copyright 2016 Pegasystems Inc., Cambridge, MA All rights reserved. This document describes products and services of Pegasystems Inc. It may contain
Course Outline. Managing Enterprise Devices and Apps using System Center Configuration ManagerCourse 20696B: 5 days Instructor Led
 Managing Enterprise Devices and Apps using System Center Configuration ManagerCourse 20696B: 5 days Instructor Led About this Course Get expert instruction and hands-on practice configuring and managing
Managing Enterprise Devices and Apps using System Center Configuration ManagerCourse 20696B: 5 days Instructor Led About this Course Get expert instruction and hands-on practice configuring and managing
Intel Security Certified Product Specialist McAfee Network Security Platform (NSP)
 Intel Security Certified Product Specialist McAfee Network Security Platform (NSP) Why Get Intel Security Certified? As technology and security threats continue to evolve, organizations are looking for
Intel Security Certified Product Specialist McAfee Network Security Platform (NSP) Why Get Intel Security Certified? As technology and security threats continue to evolve, organizations are looking for
MicroStrategy Course Catalog
 MicroStrategy Course Catalog 1 microstrategy.com/education 3 MicroStrategy course matrix 4 MicroStrategy 9 8 MicroStrategy 10 table of contents MicroStrategy course matrix MICROSTRATEGY 9 MICROSTRATEGY
MicroStrategy Course Catalog 1 microstrategy.com/education 3 MicroStrategy course matrix 4 MicroStrategy 9 8 MicroStrategy 10 table of contents MicroStrategy course matrix MICROSTRATEGY 9 MICROSTRATEGY
Salesforce Certified Pardot Consultant Study Guide
 Salesforce Certified Pardot Consultant Study Guide Winter 16 STUDY GUIDE 0 Contents ABOUT THE SALESFORCE CERTIFIED PARDOT CONSULTANT PROGRAM 1 SECTION 1. PURPOSE OF THIS STUDY GUIDE 1 SECTION 2. AUDIENCE
Salesforce Certified Pardot Consultant Study Guide Winter 16 STUDY GUIDE 0 Contents ABOUT THE SALESFORCE CERTIFIED PARDOT CONSULTANT PROGRAM 1 SECTION 1. PURPOSE OF THIS STUDY GUIDE 1 SECTION 2. AUDIENCE
Intel Security Certified Product Specialist
 Intel Security ertified Product Specialist McAfee epolicy Orchestrator (epo) Why Get Intel Security ertified? As technology and security threats continue to evolve, organizations are looking for employees
Intel Security ertified Product Specialist McAfee epolicy Orchestrator (epo) Why Get Intel Security ertified? As technology and security threats continue to evolve, organizations are looking for employees
Salesforce Certified Force.com Developer Study Guide
 Salesforce Certified Force.com Developer Study Guide Summer 15 STUDY GUIDE 0 Contents ABOUT THE SALESFORCE CERTIFIED FORCE.COM DEVELOPER PROGRAM... 1 SECTION 1. PURPOSE OF THIS STUDY GUIDE... 1 SECTION
Salesforce Certified Force.com Developer Study Guide Summer 15 STUDY GUIDE 0 Contents ABOUT THE SALESFORCE CERTIFIED FORCE.COM DEVELOPER PROGRAM... 1 SECTION 1. PURPOSE OF THIS STUDY GUIDE... 1 SECTION
CALNET 3 Category 7 Network Based Management Security. Table of Contents
 State of California IFB STPD 12-001-B CALNET 3 Category 7 Network Based Security Table of Contents 7.2.1.4.a DDoS Detection and Mitigation Features... 1 7.2.2.3 Email Monitoring Service Features... 2 7.2.3.2
State of California IFB STPD 12-001-B CALNET 3 Category 7 Network Based Security Table of Contents 7.2.1.4.a DDoS Detection and Mitigation Features... 1 7.2.2.3 Email Monitoring Service Features... 2 7.2.3.2
Scalability in Log Management
 Whitepaper Scalability in Log Management Research 010-021609-02 ArcSight, Inc. 5 Results Way, Cupertino, CA 95014, USA www.arcsight.com info@arcsight.com Corporate Headquarters: 1-888-415-ARST EMEA Headquarters:
Whitepaper Scalability in Log Management Research 010-021609-02 ArcSight, Inc. 5 Results Way, Cupertino, CA 95014, USA www.arcsight.com info@arcsight.com Corporate Headquarters: 1-888-415-ARST EMEA Headquarters:
Detect & Investigate Threats. OVERVIEW
 Detect & Investigate Threats. OVERVIEW HIGHLIGHTS Introducing RSA Security Analytics, Providing: Security monitoring Incident investigation Compliance reporting Providing Big Data Security Analytics Enterprise-wide
Detect & Investigate Threats. OVERVIEW HIGHLIGHTS Introducing RSA Security Analytics, Providing: Security monitoring Incident investigation Compliance reporting Providing Big Data Security Analytics Enterprise-wide
McAfee Web Gateway Administration Intel Security Education Services Administration Course Training
 McAfee Web Gateway Administration Intel Security Education Services Administration Course Training The McAfee Web Gateway Administration course from Education Services provides an in-depth introduction
McAfee Web Gateway Administration Intel Security Education Services Administration Course Training The McAfee Web Gateway Administration course from Education Services provides an in-depth introduction
Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010
 Course 10233A: Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 OVERVIEW About this Course This five-day, instructor-led course provides you with the knowledge and skills
Course 10233A: Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 OVERVIEW About this Course This five-day, instructor-led course provides you with the knowledge and skills
SP-2002-10231 - Designing a Microsoft SharePoint 2010 Infrastructure
 SP-2002-10231 - Designing a Microsoft SharePoint 2010 Infrastructure Duration: 5 days Course Price: $2,975 Software Assurance Eligible Course Description Course Overview This 5 day ILT training course
SP-2002-10231 - Designing a Microsoft SharePoint 2010 Infrastructure Duration: 5 days Course Price: $2,975 Software Assurance Eligible Course Description Course Overview This 5 day ILT training course
Intel Security Certified Product Specialist Security Information Event Management (SIEM)
 Intel Security Certified Product Specialist Security Information Event Management (SIEM) Why Get Intel Security Certified? As technology and security threats continue to evolve, organizations are looking
Intel Security Certified Product Specialist Security Information Event Management (SIEM) Why Get Intel Security Certified? As technology and security threats continue to evolve, organizations are looking
Whitelist Management
 Whitelist Management Overview The ExchangeDefender Admin Site is a powerful tool that gives you access to all of the benefits ExchangeDefender has to offer, from the safety and convenience of your web
Whitelist Management Overview The ExchangeDefender Admin Site is a powerful tool that gives you access to all of the benefits ExchangeDefender has to offer, from the safety and convenience of your web
Discover & Investigate Advanced Threats. OVERVIEW
 Discover & Investigate Advanced Threats. OVERVIEW HIGHLIGHTS Introducing RSA Security Analytics, Providing: Security monitoring Incident investigation Compliance reporting Providing Big Data Security Analytics
Discover & Investigate Advanced Threats. OVERVIEW HIGHLIGHTS Introducing RSA Security Analytics, Providing: Security monitoring Incident investigation Compliance reporting Providing Big Data Security Analytics
Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 Service Pack 2
 Microsoft Exchange About this Course This five-day, instructor-led course provides you with the knowledge and skills to design and deploy messaging solutions with Server 2010. This course describes how
Microsoft Exchange About this Course This five-day, instructor-led course provides you with the knowledge and skills to design and deploy messaging solutions with Server 2010. This course describes how
McAfee Certified Product Specialist McAfee epolicy Orchestrator
 McAfee Certified Product Specialist McAfee epolicy Orchestrator Exam preparation guide Table of Contents Introduction 3 Becoming McAfee Certified 3 Exam Details 3 Recommended Exam Preparation 4 Exam Objectives
McAfee Certified Product Specialist McAfee epolicy Orchestrator Exam preparation guide Table of Contents Introduction 3 Becoming McAfee Certified 3 Exam Details 3 Recommended Exam Preparation 4 Exam Objectives
Certified System Architect
 White Paper Certified System Architect EXAM BLUEPRINT Copyright 2015 Pegasystems Inc., Cambridge, MA All rights reserved. This document describes products and services of Pegasystems Inc. It may contain
White Paper Certified System Architect EXAM BLUEPRINT Copyright 2015 Pegasystems Inc., Cambridge, MA All rights reserved. This document describes products and services of Pegasystems Inc. It may contain
10965 - IT Service Management with System Center Service Manager
 10965 - IT Service Management with System Center Service Manager Duration: 4 Days Course Price: $2,975 Course Description Course Overview This four day training course will provide students with the key
10965 - IT Service Management with System Center Service Manager Duration: 4 Days Course Price: $2,975 Course Description Course Overview This four day training course will provide students with the key
CA ehealth r6.x Implementation Proven Professional Exam
 CA ehealth r6.x Implementation Proven Professional Exam (CAT-020) Study Guide Version 1.2 - PROPRIETARY AND CONFIDENTIAL INFORMATION 2015 CA. All rights reserved. CA confidential & proprietary information.
CA ehealth r6.x Implementation Proven Professional Exam (CAT-020) Study Guide Version 1.2 - PROPRIETARY AND CONFIDENTIAL INFORMATION 2015 CA. All rights reserved. CA confidential & proprietary information.
Salesforce Certified Pardot Specialist Study Guide
 Salesforce Certified Pardot Specialist Study Guide Summer 15 STUDY GUIDE 0 Contents SECTION 1. PURPOSE OF THIS STUDY GUIDE... 1 SECTION 2. ABOUT THE SALESFORCE CERTIFIED PARDOT SPECIALIST CREDENTIAL...
Salesforce Certified Pardot Specialist Study Guide Summer 15 STUDY GUIDE 0 Contents SECTION 1. PURPOSE OF THIS STUDY GUIDE... 1 SECTION 2. ABOUT THE SALESFORCE CERTIFIED PARDOT SPECIALIST CREDENTIAL...
Check Point Security Administrator R70
 Page 1 of 6 Check Point Security Administrator R70 Check Point Security Administration R70 Length Prerequisites 5 days* (recommended) Basic networking knowledge, knowledge of Windows Server and/or UNIX,
Page 1 of 6 Check Point Security Administrator R70 Check Point Security Administration R70 Length Prerequisites 5 days* (recommended) Basic networking knowledge, knowledge of Windows Server and/or UNIX,
WHITE PAPER SPLUNK SOFTWARE AS A SIEM
 SPLUNK SOFTWARE AS A SIEM Improve your security posture by using Splunk as your SIEM HIGHLIGHTS Splunk software can be used to operate security operations centers (SOC) of any size (large, med, small)
SPLUNK SOFTWARE AS A SIEM Improve your security posture by using Splunk as your SIEM HIGHLIGHTS Splunk software can be used to operate security operations centers (SOC) of any size (large, med, small)
Certified Senior System Architect
 White Paper Certified Senior System Architect EXAM BLUEPRINT Copyright 2015 Pegasystems Inc., Cambridge, MA All rights reserved. This document describes products and services of Pegasystems Inc. It may
White Paper Certified Senior System Architect EXAM BLUEPRINT Copyright 2015 Pegasystems Inc., Cambridge, MA All rights reserved. This document describes products and services of Pegasystems Inc. It may
Security Analytics Topology
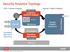 Security Analytics Topology CEP = Stream Analytics Hadoop = Batch Analytics Months to years LOGS PKTS Correlation with Live in Real Time Meta, logs, select payload Decoder Long-term, intensive analysis
Security Analytics Topology CEP = Stream Analytics Hadoop = Batch Analytics Months to years LOGS PKTS Correlation with Live in Real Time Meta, logs, select payload Decoder Long-term, intensive analysis
RSA Archer Training. Governance, Risk and Compliance. Managing enterprise-wide governance, risk and compliance through training and education
 RSA Archer Training Governance, Risk and Compliance Managing enterprise-wide governance, risk and compliance through training and education www.emc.com/rsa-training 1 RSA Archer Training Table of Contents
RSA Archer Training Governance, Risk and Compliance Managing enterprise-wide governance, risk and compliance through training and education www.emc.com/rsa-training 1 RSA Archer Training Table of Contents
Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 Service Pack 2 Course: 10233 Length: 5 Days
 About this Course Designing and Deploying Messaging Solutions with This five-day, instructor-led course provides you with the knowledge and skills to design and deploy messaging solutions with Microsoft
About this Course Designing and Deploying Messaging Solutions with This five-day, instructor-led course provides you with the knowledge and skills to design and deploy messaging solutions with Microsoft
Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 Service Pack 2
 Course 10233B: Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 Service Pack 2 Length: Delivery Method: 5 Days Instructor-led (classroom) About this Course This five-day,
Course 10233B: Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 Service Pack 2 Length: Delivery Method: 5 Days Instructor-led (classroom) About this Course This five-day,
BillQuick Agent 2010 Getting Started Guide
 Time Billing and Project Management Software Built With Your Industry Knowledge BillQuick Agent 2010 Getting Started Guide BQE Software, Inc. 2601 Airport Drive Suite 380 Torrance CA 90505 Support: (310)
Time Billing and Project Management Software Built With Your Industry Knowledge BillQuick Agent 2010 Getting Started Guide BQE Software, Inc. 2601 Airport Drive Suite 380 Torrance CA 90505 Support: (310)
SolarWinds Log & Event Manager
 Corona Technical Services SolarWinds Log & Event Manager Training Project/Implementation Outline James Kluza 14 Table of Contents Overview... 3 Example Project Schedule... 3 Pre-engagement Checklist...
Corona Technical Services SolarWinds Log & Event Manager Training Project/Implementation Outline James Kluza 14 Table of Contents Overview... 3 Example Project Schedule... 3 Pre-engagement Checklist...
ExactTarget GENESIS I N TEGRATION GUIDE
 ExactTarget GENESIS I N TEGRATION GUIDE GENESIS INTEGRATION GUIDE II Table of Contents Terms and Conditions of Use... 4 Intended Audience... 4 Account Support... 4 Service and Billing Information... 4
ExactTarget GENESIS I N TEGRATION GUIDE GENESIS INTEGRATION GUIDE II Table of Contents Terms and Conditions of Use... 4 Intended Audience... 4 Account Support... 4 Service and Billing Information... 4
Citrix EdgeSight Administrator s Guide. Citrix EdgeSight for Endpoints 5.3 Citrix EdgeSight for XenApp 5.3
 Citrix EdgeSight Administrator s Guide Citrix EdgeSight for Endpoints 5.3 Citrix EdgeSight for enapp 5.3 Copyright and Trademark Notice Use of the product documented in this guide is subject to your prior
Citrix EdgeSight Administrator s Guide Citrix EdgeSight for Endpoints 5.3 Citrix EdgeSight for enapp 5.3 Copyright and Trademark Notice Use of the product documented in this guide is subject to your prior
The Purview Solution Integration With Splunk
 The Purview Solution Integration With Splunk Integrating Application Management and Business Analytics With Other IT Management Systems A SOLUTION WHITE PAPER WHITE PAPER Introduction Purview Integration
The Purview Solution Integration With Splunk Integrating Application Management and Business Analytics With Other IT Management Systems A SOLUTION WHITE PAPER WHITE PAPER Introduction Purview Integration
Monitoring System Status
 CHAPTER 14 This chapter describes how to monitor the health and activities of the system. It covers these topics: About Logged Information, page 14-121 Event Logging, page 14-122 Monitoring Performance,
CHAPTER 14 This chapter describes how to monitor the health and activities of the system. It covers these topics: About Logged Information, page 14-121 Event Logging, page 14-122 Monitoring Performance,
Planning, Deploying, and Managing an Enterprise Project Management Solution
 Planning, Deploying, and Managing an Enterprise Project Management Solution Course 2732 Five days Instructor-led Introduction The goal of this five-day, instructor-led course is to provide systems engineers
Planning, Deploying, and Managing an Enterprise Project Management Solution Course 2732 Five days Instructor-led Introduction The goal of this five-day, instructor-led course is to provide systems engineers
with Managing RSA the Lifecycle of Key Manager RSA Streamlining Security Operations Data Loss Prevention Solutions RSA Solution Brief
 RSA Solution Brief Streamlining Security Operations with Managing RSA the Lifecycle of Data Loss Prevention and Encryption RSA envision Keys with Solutions RSA Key Manager RSA Solution Brief 1 Who is asking
RSA Solution Brief Streamlining Security Operations with Managing RSA the Lifecycle of Data Loss Prevention and Encryption RSA envision Keys with Solutions RSA Key Manager RSA Solution Brief 1 Who is asking
Overview. ExchangeDefender Admin Web Site
 SPAM Settings Overview The ExchangeDefender Admin Site is a powerful tool that gives you access to all of the benefits ExchangeDefender has to offer, from the safety and convenience of your web browser.
SPAM Settings Overview The ExchangeDefender Admin Site is a powerful tool that gives you access to all of the benefits ExchangeDefender has to offer, from the safety and convenience of your web browser.
Certified Pega Business Architect
 Certified Pega Business Architect PRPC v6.3 White Paper EXAM BLUEPRINT Copyright 2014 Pegasystems Inc., Cambridge, MA All rights reserved. This document describes products and services of Pegasystems Inc.
Certified Pega Business Architect PRPC v6.3 White Paper EXAM BLUEPRINT Copyright 2014 Pegasystems Inc., Cambridge, MA All rights reserved. This document describes products and services of Pegasystems Inc.
XpoLog Center Suite Data Sheet
 XpoLog Center Suite Data Sheet General XpoLog is a data analysis and management platform for Applications IT data. Business applications rely on a dynamic heterogeneous applications infrastructure, such
XpoLog Center Suite Data Sheet General XpoLog is a data analysis and management platform for Applications IT data. Business applications rely on a dynamic heterogeneous applications infrastructure, such
Juniper Secure Analytics Release Notes
 Juniper Secure Analytics Release Notes 2014.5 February 2016 Juniper Networks is pleased to introduce JSA 2014.5. Juniper Secure Analytics (JSA) 2014.5 Release Notes provides new features, known issues
Juniper Secure Analytics Release Notes 2014.5 February 2016 Juniper Networks is pleased to introduce JSA 2014.5. Juniper Secure Analytics (JSA) 2014.5 Release Notes provides new features, known issues
Best Practices for Log File Management (Compliance, Security, Troubleshooting)
 Log Management: Best Practices for Security and Compliance The Essentials Series Best Practices for Log File Management (Compliance, Security, Troubleshooting) sponsored by Introduction to Realtime Publishers
Log Management: Best Practices for Security and Compliance The Essentials Series Best Practices for Log File Management (Compliance, Security, Troubleshooting) sponsored by Introduction to Realtime Publishers
How to select the right Marketing Cloud Edition
 How to select the right Marketing Cloud Edition Email, Mobile & Web Studios ith Salesforce Marketing Cloud, marketers have one platform to manage 1-to-1 customer journeys through the entire customer lifecycle
How to select the right Marketing Cloud Edition Email, Mobile & Web Studios ith Salesforce Marketing Cloud, marketers have one platform to manage 1-to-1 customer journeys through the entire customer lifecycle
Administering a Microsoft SQL Server 2000 Database
 Administering a Microsoft SQL Server 2000 Database Course 2072 - Five days - Instructor-led - Hands-On Introduction This course provides students with the knowledge and skills required to install, configure,
Administering a Microsoft SQL Server 2000 Database Course 2072 - Five days - Instructor-led - Hands-On Introduction This course provides students with the knowledge and skills required to install, configure,
VMware vsphere Data Protection 6.1
 VMware vsphere Data Protection 6.1 Technical Overview Revised August 10, 2015 Contents Introduction... 3 Architecture... 3 Deployment and Configuration... 5 Backup... 6 Application Backup... 6 Backup Data
VMware vsphere Data Protection 6.1 Technical Overview Revised August 10, 2015 Contents Introduction... 3 Architecture... 3 Deployment and Configuration... 5 Backup... 6 Application Backup... 6 Backup Data
Developing Microsoft SharePoint Server 2013 Advanced Solutions MOC 20489
 Developing Microsoft SharePoint Server 2013 Advanced Solutions MOC 20489 Course Outline Module 1: Creating Robust and Efficient Apps for SharePoint In this module, you will review key aspects of the apps
Developing Microsoft SharePoint Server 2013 Advanced Solutions MOC 20489 Course Outline Module 1: Creating Robust and Efficient Apps for SharePoint In this module, you will review key aspects of the apps
AccelOps NOC and SOC Analytics in a Single Pane of Glass Date: March 2016 Author: Tony Palmer, Senior ESG Lab Analyst
 ESG Lab Spotlight AccelOps NOC and SOC Analytics in a Single Pane of Glass Date: March 2016 Author: Tony Palmer, Senior ESG Lab Analyst Abstract: This ESG Lab Spotlight details ESG s hands-on testing of
ESG Lab Spotlight AccelOps NOC and SOC Analytics in a Single Pane of Glass Date: March 2016 Author: Tony Palmer, Senior ESG Lab Analyst Abstract: This ESG Lab Spotlight details ESG s hands-on testing of
11.1. Performance Monitoring
 11.1. Performance Monitoring Windows Reliability and Performance Monitor combines the functionality of the following tools that were previously only available as stand alone: Performance Logs and Alerts
11.1. Performance Monitoring Windows Reliability and Performance Monitor combines the functionality of the following tools that were previously only available as stand alone: Performance Logs and Alerts
MCITP: Sharepoint Administrator Boot Camp (10174, 10231) H6C10S
 HP Education Services course data sheet MCITP: Sharepoint Administrator Boot Camp (10174, 10231) H6C10S Course Overview Prepare for the MCTS and MCITP SharePoint 2010 certifications. Gain the cloud-related
HP Education Services course data sheet MCITP: Sharepoint Administrator Boot Camp (10174, 10231) H6C10S Course Overview Prepare for the MCTS and MCITP SharePoint 2010 certifications. Gain the cloud-related
Salesforce Certified Marketing Cloud Email Specialist Study Guide
 Salesforce Certified Marketing Cloud Email Specialist Study Guide Winter 16 STUDY GUIDE 0 Contents SECTION 1. PURPOSE OF THIS STUDY GUIDE... 1 SECTION 2. ABOUT THE SALESFORCE CERTIFIED MARKETING CLOUD
Salesforce Certified Marketing Cloud Email Specialist Study Guide Winter 16 STUDY GUIDE 0 Contents SECTION 1. PURPOSE OF THIS STUDY GUIDE... 1 SECTION 2. ABOUT THE SALESFORCE CERTIFIED MARKETING CLOUD
Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 Service Pack 2
 Designing and Deploying Messaging Solutions with Microsoft Exchange Service Pack 2 Course Details Course Code: Duration: Notes: 10233B 5 days This course syllabus should be used to determine whether the
Designing and Deploying Messaging Solutions with Microsoft Exchange Service Pack 2 Course Details Course Code: Duration: Notes: 10233B 5 days This course syllabus should be used to determine whether the
Log Analysis: Overall Issues p. 1 Introduction p. 2 IT Budgets and Results: Leveraging OSS Solutions at Little Cost p. 2 Reporting Security
 Foreword p. xvii Log Analysis: Overall Issues p. 1 Introduction p. 2 IT Budgets and Results: Leveraging OSS Solutions at Little Cost p. 2 Reporting Security Information to Management p. 5 Example of an
Foreword p. xvii Log Analysis: Overall Issues p. 1 Introduction p. 2 IT Budgets and Results: Leveraging OSS Solutions at Little Cost p. 2 Reporting Security Information to Management p. 5 Example of an
McAfee Security Information Event Management (SIEM) Administration Course 101
 McAfee Security Information Event Management (SIEM) Administration Course 101 Intel Security Education Services Administration Course The McAfee SIEM Administration course from McAfee Education Services
McAfee Security Information Event Management (SIEM) Administration Course 101 Intel Security Education Services Administration Course The McAfee SIEM Administration course from McAfee Education Services
Microsoft 20345-2 Designing and Deploying Microsoft Exchange Server 2016
 1800 ULEARN (853 276) www.ddls.com.au Microsoft 20345-2 Designing and Deploying Microsoft Exchange Server 2016 Length 5 days Price $4169.00 (inc GST) Version A Overview This course provides experienced
1800 ULEARN (853 276) www.ddls.com.au Microsoft 20345-2 Designing and Deploying Microsoft Exchange Server 2016 Length 5 days Price $4169.00 (inc GST) Version A Overview This course provides experienced
Server Monitoring: Centralize and Win
 Server Monitoring: Centralize and Win Table of Contents Introduction 2 Event & Performance Management 2 Troubleshooting 3 Health Reporting & Notification 3 Security Posture & Compliance Fulfillment 4 TNT
Server Monitoring: Centralize and Win Table of Contents Introduction 2 Event & Performance Management 2 Troubleshooting 3 Health Reporting & Notification 3 Security Posture & Compliance Fulfillment 4 TNT
Application Monitoring and UEM 5.6 Professional Certification
 Application Monitoring and UEM 5.6 Professional Certification Exam Blueprint Contributors Ted Feyler, dynatrace Architect, CSO Services Portfolio Manager Rob Vollum, dynatrace Architect, Director dynatrace
Application Monitoring and UEM 5.6 Professional Certification Exam Blueprint Contributors Ted Feyler, dynatrace Architect, CSO Services Portfolio Manager Rob Vollum, dynatrace Architect, Director dynatrace
Official Cert Guide. CCNP Security IPS 642-627. Odunayo Adesina, CCIE No. 26695 Keith Barker, CCIE No. 6783. Cisco Press.
 CCNP Security IPS 642-627 Official Cert Guide David Burns Odunayo Adesina, CCIE No. 26695 Keith Barker, CCIE No. 6783 Cisco Press 800 East 96th Street Indianapolis, IN 46240 Contents Introduction xxviii
CCNP Security IPS 642-627 Official Cert Guide David Burns Odunayo Adesina, CCIE No. 26695 Keith Barker, CCIE No. 6783 Cisco Press 800 East 96th Street Indianapolis, IN 46240 Contents Introduction xxviii
Course 10233:Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 Service Pack 2
 Course 10233:Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 Service Pack 2 Type:Course Audience(s):IT Professionals Technology:Microsoft Exchange Level:200 This Revision:B
Course 10233:Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 Service Pack 2 Type:Course Audience(s):IT Professionals Technology:Microsoft Exchange Level:200 This Revision:B
EXPERT STRATEGIES FOR LOG COLLECTION, ROOT CAUSE ANALYSIS, AND COMPLIANCE
 EXPERT STRATEGIES FOR LOG COLLECTION, ROOT CAUSE ANALYSIS, AND COMPLIANCE A reliable, high-performance network is critical to your IT infrastructure and organization. Equally important to network performance
EXPERT STRATEGIES FOR LOG COLLECTION, ROOT CAUSE ANALYSIS, AND COMPLIANCE A reliable, high-performance network is critical to your IT infrastructure and organization. Equally important to network performance
Medicare Sales Training and Certification User Manual v2
 Medicare Sales Training and Certification User Manual v2 1 Copyright 2007, Gorman Health Group, LLC Medicare Sales Training and Certification Modules Gorman Health Group Medicare Sales Training and Certification
Medicare Sales Training and Certification User Manual v2 1 Copyright 2007, Gorman Health Group, LLC Medicare Sales Training and Certification Modules Gorman Health Group Medicare Sales Training and Certification
Oracle Education @ USF
 Oracle Education @ USF Oracle Education @ USF helps increase your employability and also trains and prepares you for the competitive job market at a much lower cost compared to Oracle University. Oracle
Oracle Education @ USF Oracle Education @ USF helps increase your employability and also trains and prepares you for the competitive job market at a much lower cost compared to Oracle University. Oracle
Deltek Touch Time & Expense for GovCon. User Guide for Triumph
 Deltek Touch Time & Expense for GovCon User Guide for Triumph November 25, 2014 While Deltek has attempted to verify that the information in this document is accurate and complete, some typographical or
Deltek Touch Time & Expense for GovCon User Guide for Triumph November 25, 2014 While Deltek has attempted to verify that the information in this document is accurate and complete, some typographical or
LOG AND EVENT MANAGEMENT FOR SECURITY AND COMPLIANCE
 PRODUCT BRIEF LOG AND EVENT MANAGEMENT FOR SECURITY AND COMPLIANCE The Tripwire VIA platform delivers system state intelligence, a continuous approach to security that provides leading indicators of breach
PRODUCT BRIEF LOG AND EVENT MANAGEMENT FOR SECURITY AND COMPLIANCE The Tripwire VIA platform delivers system state intelligence, a continuous approach to security that provides leading indicators of breach
IBM Security QRadar SIEM & Fortinet FortiGate / FortiAnalyzer
 IBM Security QRadar SIEM & Fortinet / FortiAnalyzer Introducing new functionality for IBM QRadar Security Intelligence Platform: integration with Fortinet s firewalls and logs forwarded by FortiAnalyzer.
IBM Security QRadar SIEM & Fortinet / FortiAnalyzer Introducing new functionality for IBM QRadar Security Intelligence Platform: integration with Fortinet s firewalls and logs forwarded by FortiAnalyzer.
CNS-205 Citrix NetScaler 10 Essentials and Networking
 CNS-205 Citrix NetScaler 10 Essentials and Networking The objective of the Citrix NetScaler 10 Essentials and Networking course is to provide the foundational concepts and advanced skills necessary to
CNS-205 Citrix NetScaler 10 Essentials and Networking The objective of the Citrix NetScaler 10 Essentials and Networking course is to provide the foundational concepts and advanced skills necessary to
CNS-301-3I ~ Citrix NetScaler 11 Advanced Implementation
 CNS-301-3I ~ Citrix NetScaler 11 Advanced Implementation11 vanced Implementation Overview Designed for students with previous NetScaler experience, this course is best suited for individuals who will be
CNS-301-3I ~ Citrix NetScaler 11 Advanced Implementation11 vanced Implementation Overview Designed for students with previous NetScaler experience, this course is best suited for individuals who will be
Performing Advanced Incident Response Interactive Exercise
 Performing Advanced Incident Response Interactive Exercise Post-Conference Summary Merlin Namuth Robert Huber SCENARIO 1 - PHISHING EMAILS... 3... 3 Mitigations... 3 SCENARIO 2 - IDS ALERT FOR PSEXEC...
Performing Advanced Incident Response Interactive Exercise Post-Conference Summary Merlin Namuth Robert Huber SCENARIO 1 - PHISHING EMAILS... 3... 3 Mitigations... 3 SCENARIO 2 - IDS ALERT FOR PSEXEC...
Healthcare Financial Management Association. HFMA Certification Program & Policies Handbook
 Healthcare Financial Management Association HFMA Certification Program & Policies Handbook Contents I. HFMA Certification Program: Purpose & Governance Pages 4 6 II. HFMA Certification Examinations Pages
Healthcare Financial Management Association HFMA Certification Program & Policies Handbook Contents I. HFMA Certification Program: Purpose & Governance Pages 4 6 II. HFMA Certification Examinations Pages
Microsoft Project Server 2010 Technical Boot Camp
 Microsoft Project Server 2010 Technical Boot Camp Course M50558 5 Day(s) 30:00 Hours Introduction Course retirement date: November 30, 2012 For a complete list of courseware retirements, see: www.microsoft.com/learning/en/us/training/retired
Microsoft Project Server 2010 Technical Boot Camp Course M50558 5 Day(s) 30:00 Hours Introduction Course retirement date: November 30, 2012 For a complete list of courseware retirements, see: www.microsoft.com/learning/en/us/training/retired
CA PPM 14.x Business Analyst Certification Exam
 CA PPM 14.x Business Analyst Certification Exam (CAT-242) Study Guide Version 1.0 - PROPRIETARY AND CONFIDENTIAL INFORMATION 2015 CA. All rights reserved. CA confidential & proprietary information. For
CA PPM 14.x Business Analyst Certification Exam (CAT-242) Study Guide Version 1.0 - PROPRIETARY AND CONFIDENTIAL INFORMATION 2015 CA. All rights reserved. CA confidential & proprietary information. For
Tech Brief. Choosing the Right Log Management Product. By Michael Pastore
 Choosing the Right Log Management Product By Michael Pastore Tech Brief an Log management is IT s version of the good old fashioned detective work that authorities credit for solving a lot of crimes. It
Choosing the Right Log Management Product By Michael Pastore Tech Brief an Log management is IT s version of the good old fashioned detective work that authorities credit for solving a lot of crimes. It
MCITP: Enterprise Messaging Administrator 2010 Boot Camp
 MCITP: Enterprise Messaging Administrator 2010 Boot Camp Validate your Exchange Server skills with the MCITP: Enterprise Messaging Administrator certification. In an intensive and immersive hands-on learning
MCITP: Enterprise Messaging Administrator 2010 Boot Camp Validate your Exchange Server skills with the MCITP: Enterprise Messaging Administrator certification. In an intensive and immersive hands-on learning
Security Administration R77
 Security Administration R77 Validate your skills on the GAiA operating system Check Point Security Administration R77 provides an understanding of the basic concepts and skills necessary to configure Check
Security Administration R77 Validate your skills on the GAiA operating system Check Point Security Administration R77 provides an understanding of the basic concepts and skills necessary to configure Check
Office SharePoint Server 2007
 Top 10 Benefits of WSS 3.0 Office SharePoint Server 2007 1. Improve team productivity with easy-to-use collaborative tools Connect people with the information and resources they need. Users can create
Top 10 Benefits of WSS 3.0 Office SharePoint Server 2007 1. Improve team productivity with easy-to-use collaborative tools Connect people with the information and resources they need. Users can create
Alex Wong Senior Manager - Product Management Bruce Ong Director - Product Management
 Alex Wong Senior Manager - Product Management Bruce Ong Director - Product Management 1 Product Roadmap Disclaimer Any forward-looking indication of plans for products is preliminary and all future release
Alex Wong Senior Manager - Product Management Bruce Ong Director - Product Management 1 Product Roadmap Disclaimer Any forward-looking indication of plans for products is preliminary and all future release
Consolidating HFC Device and Network Management and Monitoring under SCTE HMS SNMP
 Consolidating HFC Device and Network Management and Monitoring under SCTE HMS SNMP NuDesign OEM Product Family The SCTE HMS subcommitte has devised an extensive set of standards for outside and inside
Consolidating HFC Device and Network Management and Monitoring under SCTE HMS SNMP NuDesign OEM Product Family The SCTE HMS subcommitte has devised an extensive set of standards for outside and inside
Administering System Center 2012 Configuration Manager
 Administering System Center 2012 Configuration Manager MOC 10747 Duración: 25 horas Introducción This course describes how to configure and manage a System Center 2012 R2 Configuration Manager site and
Administering System Center 2012 Configuration Manager MOC 10747 Duración: 25 horas Introducción This course describes how to configure and manage a System Center 2012 R2 Configuration Manager site and
See Criminal Internet Communication as it Happens.
 A PRODUCT OF See Criminal Internet Communication as it Happens. In Real Time or Recreated. From the Field or From Your Desk. That s Intelligence. That s Intellego. 2 / Visual Reconstruction & Analysis
A PRODUCT OF See Criminal Internet Communication as it Happens. In Real Time or Recreated. From the Field or From Your Desk. That s Intelligence. That s Intellego. 2 / Visual Reconstruction & Analysis
Course Outline: Course 20489B: Developing Microsoft SharePoint Server 2013 Advanced Solutions
 Course Outline: Course 20489B: Developing Microsoft SharePoint Server 2013 Advanced Learning Method: Instructor-led Classroom Learning Duration: 5.00 Day(s)/ 40 hrs Overview: This course provides SharePoint
Course Outline: Course 20489B: Developing Microsoft SharePoint Server 2013 Advanced Learning Method: Instructor-led Classroom Learning Duration: 5.00 Day(s)/ 40 hrs Overview: This course provides SharePoint
Administering a Microsoft SQL Server 2000 Database
 Aug/12/2002 Page 1 of 5 Administering a Microsoft SQL Server 2000 Database Catalog No: RS-MOC2072 MOC Course Number: 2072 5 days Tuition: $2,070 Introduction This course provides students with the knowledge
Aug/12/2002 Page 1 of 5 Administering a Microsoft SQL Server 2000 Database Catalog No: RS-MOC2072 MOC Course Number: 2072 5 days Tuition: $2,070 Introduction This course provides students with the knowledge
MATRIXX Professional Services
 MATRIXX PROFESSIONAL SERVICES PARTNER CERTIFICATION MATRIXX Professional Services Professional Certification Version 2.1 TABLE OF CONTENTS 1 Professional Certification Overview 1 1.1 Motivation 1 1.2 Approach
MATRIXX PROFESSIONAL SERVICES PARTNER CERTIFICATION MATRIXX Professional Services Professional Certification Version 2.1 TABLE OF CONTENTS 1 Professional Certification Overview 1 1.1 Motivation 1 1.2 Approach
NitroView. Content Aware SIEM TM. Unified Security and Compliance Unmatched Speed and Scale. Application Data Monitoring. Database Monitoring
 NitroView Unified Security and Compliance Unmatched Speed and Scale Application Data Monitoring Database Monitoring Log Management Content Aware SIEM TM IPS Today s security challenges demand a new approach
NitroView Unified Security and Compliance Unmatched Speed and Scale Application Data Monitoring Database Monitoring Log Management Content Aware SIEM TM IPS Today s security challenges demand a new approach
DE-20489B Developing Microsoft SharePoint Server 2013 Advanced Solutions
 DE-20489B Developing Microsoft SharePoint Server 2013 Advanced Solutions Summary Duration Vendor Audience 5 Days Microsoft Developer Published Level Technology 21 November 2013 300 Microsoft SharePoint
DE-20489B Developing Microsoft SharePoint Server 2013 Advanced Solutions Summary Duration Vendor Audience 5 Days Microsoft Developer Published Level Technology 21 November 2013 300 Microsoft SharePoint
Web Analytics Understand your web visitors without web logs or page tags and keep all your data inside your firewall.
 Web Analytics Understand your web visitors without web logs or page tags and keep all your data inside your firewall. 5401 Butler Street, Suite 200 Pittsburgh, PA 15201 +1 (412) 408 3167 www.metronomelabs.com
Web Analytics Understand your web visitors without web logs or page tags and keep all your data inside your firewall. 5401 Butler Street, Suite 200 Pittsburgh, PA 15201 +1 (412) 408 3167 www.metronomelabs.com
Certified Senior System Architect
 Certified Senior System Architect PRPC v7.1 White Paper EXAM BLUEPRINT Copyright 2014 Pegasystems Inc., Cambridge, MA All rights reserved. This document describes products and services of Pegasystems Inc.
Certified Senior System Architect PRPC v7.1 White Paper EXAM BLUEPRINT Copyright 2014 Pegasystems Inc., Cambridge, MA All rights reserved. This document describes products and services of Pegasystems Inc.
Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010
 CÔNG TY CỔ PHẦN TRƯỜNG CNTT TÂN ĐỨC TAN DUC INFORMATION TECHNOLOGY SCHOOL JSC LEARN MORE WITH LESS! Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 Course 10233A: Five days;
CÔNG TY CỔ PHẦN TRƯỜNG CNTT TÂN ĐỨC TAN DUC INFORMATION TECHNOLOGY SCHOOL JSC LEARN MORE WITH LESS! Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 Course 10233A: Five days;
FortiMail Email Filtering. Course 221 - for FortiMail v4.0. Course Overview
 FortiMail Email Filtering Course 221 - for FortiMail v4.0 Course Overview FortiMail Email Filtering is a 3-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed
FortiMail Email Filtering Course 221 - for FortiMail v4.0 Course Overview FortiMail Email Filtering is a 3-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed
525 South 29 th Street. Harrisburg, PA 17104. Learning Management System User s Guide
 525 South 29 th Street Harrisburg, PA 17104 Learning Management System User s Guide July 2015 1 Table of Contents User Accounts Overview 3 Changing your Email address 3 Changing your Password 3 Changing
525 South 29 th Street Harrisburg, PA 17104 Learning Management System User s Guide July 2015 1 Table of Contents User Accounts Overview 3 Changing your Email address 3 Changing your Password 3 Changing
STARTER KIT. Infoblox DNS Firewall for FireEye
 STARTER KIT Introduction Infoblox DNS Firewall integration with FireEye Malware Protection System delivers a unique and powerful defense against Advanced Persistent Threats (APT) for business networks.
STARTER KIT Introduction Infoblox DNS Firewall integration with FireEye Malware Protection System delivers a unique and powerful defense against Advanced Persistent Threats (APT) for business networks.
Using Microsoft Operations Manager To Monitor And Maintain Your Farm. Michael Noel. michael@cco.com
 Using Microsoft Operations Manager To Monitor And Maintain Your Farm Michael Noel michael@cco.com About the Presenter and Convergent Computing Author of SAMS Publishing titles SharePoint 2007 Unleashed,
Using Microsoft Operations Manager To Monitor And Maintain Your Farm Michael Noel michael@cco.com About the Presenter and Convergent Computing Author of SAMS Publishing titles SharePoint 2007 Unleashed,
