RSA Security Analytics Security Analytics System Overview
|
|
|
- Philomena McCarthy
- 8 years ago
- Views:
Transcription
1 RSA Security Analytics Security Analytics System Overview
2 Copyright RSA, the Security Division of EMC. All rights reserved. Trademarks RSA, the RSA Logo and EMC are either registered trademarks or trademarks of EMC Corporation in the United States and/or other countries. All other trademarks used herein are the property of their respective owners. For a list of EMC trademarks, go to License Agreement This software and the associated documentation are proprietary and confidential to EMC, are furnished under license, and may be used and copied only in accordance with the terms of such license and with the inclusion of the copyright notice below. This software and the documentation, and any copies thereof, may not be provided or otherwise made available to any other person. No title to or ownership of the software or documentation or any intellectual property rights thereto is hereby transferred. Any unauthorized use or reproduction of this software and the documentation may be subject to civil and/or criminal liability. This software is subject to change without notice and should not be construed as a commitment by EMC. Third-Party Licenses This product may include software developed by parties other than RSA. The text of the license agreements applicable to third-party software in this product may be viewed in the thirdpartylicenses.pdf file. Note on Encryption Technologies This product may contain encryption technology. Many countries prohibit or restrict the use, import, or export of encryption technologies, and current use, import, and export regulations should be followed when using, importing or exporting this product. Distribution Use, copying, and distribution of any EMC software described in this publication requires an applicable software license. EMC believes the information in this publication is accurate as of its publication date. The information is subject to change without notice. THE INFORMATION IN THIS PUBLICATION IS PROVIDED "AS IS." EMC CORPORATION MAKES NO REPRESENTATIONS OR WARRANTIES OF ANY KIND WITH RESPECT TO THE INFORMATION IN THIS PUBLICATION, AND SPECIFICALLY DISCLAIMS IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. 2
3 Security Analytics System Overview Contents Security Analytics System Overview 4 Glossary 9 3
4 Introduction Security Analytics System Overview Introduction RSA Security Analytics is a distributed and modular system that enables highly flexible deployment architectures that scale with the needs of the organization. Security Analytics allows administrators to collect two types of data from the network infrastructure, packet data and log data. The key aspects of the architecture are: Distributed Data Collection. The packet data is collected using an appliance called Decoder, while the Log Decoder collects log events. The Decoder captures, parses, and reconstructs all network traffic from Layers 2-7, or log and event data from hundreds of devices. The Concentrator indexes metadata extracted from network or log data and makes it available for enterprise-wide querying and real-time analytics while also facilitating reporting and alerting. The Broker aggregates data captured by other devices. Brokers aggregate data from configured Concentrators; Concentrators aggregate data from Decoders. Therefore, a Broker bridges the multiple real-time data stores held in the various Decoder/Concentrator pairs throughout the infrastructure. Real-time Analytics. The Security Analytics Event Stream Analysis (ESA) appliance provides advanced stream analytics such as correlation and complex event processing at high throughputs and low latency. It is capable of processing large volumes of disparate event data from Concentrators. ESA uses an advanced Event Processing Language that allows analysts to express filtering, aggregation, joins, pattern recognition and correlation across multiple disparate event streams. Event Stream Analysis helps to perform powerful incident detection and alerting. RSA Analytics Warehouse. A Hadoop-based distributed computing system, which collects, manages, and enables analytics and reporting on longer-term sets of security data, for example, months or years. The Warehouse can be made up of three or more nodes depending on the organization's analytic, archiving, and resiliency requirements. Analytics Server. The web server for reporting, investigation, administration, and other aspects of the analysts interface. Also enables reporting on data held in the Warehouse. Capacity. Security Analytics has a modular-capacity architecture enabled with direct-attached capacity (DACs) or storage area networks (SANs), that adapts to the organization's short-term investigation and longer-term analytic and data-retention needs. Security Analytics provides large deployment flexibility as it can be architected using as many as multiple dozens of physical appliances or a single physical appliance, based on the particulars of the customer's performance and securityrelated requirements. In addition, the entire Security Analytics system has been optimized to run on virtualized infrastructure. The following image below illustrates the Security Analytics Functional architecture: 4
5 Introduction The System Architecture comprises these major components Decoders, Brokers and Concentrators, Archivers, ESA, Warehouse Connectors, RSA Warehouse. Security Analytics components can be used together as a system or can be used individually. In a security information and event management (SIEM) implementation, the base configuration requires these components: Log Decoder, Concentrator, Broker, Event Stream Analysis (ESA), and the Security Analytics server. In a forensics implementation, the base configuration requires these components: Decoder, Concentrator, Broker, ESA, and Malware Analysis. An optional component is the Incident Management service, which resides on the ESA system and is used to prioritize alerts. The table provides a synopsis of each major component: System component Security Analytics collects two types of data: packet data and log data. Decoder/Log Decoder Packet data, that is, network packets, are collected using the Decoder through the network tap or span port, which is typically determined to be an egress point on an organizations' network. A Log Decoder can collect four different log types - Syslog, ODBC, Windows eventing, and flat files. Windows eventing refers to the Windows 2008 collection methodology and flat files can be obtained via SFTP. 5
6 Introduction System component Both types of Decoders ingest raw transactional data that is enriched, closed out, and aggregated to the warehouse or other Security Analytics components. The process for ingesting and parsing transactional data is a dynamic and open framework. Concentrator/Broker Any data that can be indexed on the Decoder is filtered by the respective Concentrator. Once data is stored in the Concentrator, it is streamed as metadata to the RSA Analytics Warehouse. The Archiver is an appliance that enables long-term log archiving by indexing and compressing log data and sending it to archiving storage. The archiving storage is optimized for long-term data retention, and compliance reporting. Archivers Archiver stores raw logs and log meta from Log Decoders for long termretention, and it uses Direct-Attached Capacity (DAC) for storage. Note: Raw packets and packet meta are not stored in the Archiver. Event Stream Analysis (ESA) This ESA appliance provides event stream analytics such as correlation and complex event processing at high throughputs and low latency. It is capable of processing large volumes of disparate event data from Concentrators. ESA uses advanced Event Processing Language that allows users to express filtering, aggregation, joins, pattern recognition, and correlation across multiple disparate event streams. ESA helps to perform powerful incident detection and alerting. Warehouse Connector allows you to collect meta and events from Decoders and write them in Avro format into a Hadoop-based distributed computing system. Warehouse connectors You can set up Warehouse Connector as a service on existing Log Decoders or Decoders or it can be run as a virtual appliance in your virtual environment. The Warehouse Connector contains the following components: Data Source, Destination, and Data Stream. RSA Analytics Warehouse RSA Analytics Warehouse provides the capacity for longer term data archiving through a Hadoop-based distributed computing system that collects, manages, and enables analytics and reporting on security data. RSA Analytics Warehouse requires a service called Warehouse Connector to collect meta and events from Decoder and Log Decoder and 6
7 Core Versus Downstream Components System component write them in Avro format into a Hadoop-based distributed computing system. Any incoming data at the Log Decoder and Concentrator is ultimately forwarded to the Warehouse. A Warehouse typically consists of two units: Storage nodes and Direct Attached Capacity (DAC). Entire data (not just meta data) is stored in the RSA Analytics Warehouse and is available to Security Analytics when required. Core Versus Downstream Components In Security Analytics, the Core services ingest and parse data, generate meta data, and aggregate generated meta data with the raw data. In the figure below, the Core services are highlighted in blue; they are Decoder, Log Decoder, Concentrator, Broker. Downstream systems use data stored on Core services for analytics, therefore, the operations of downstream services are dependent on Security Analytics Core services. The downstream systems are highlighted in red; they are Archiver, Warehouse, ESA, Malware Analysis, Investigation, and Reporting. Although the Security Analytics Core services can operate and provide a good analytics solution without the downstream systems, the downstream components provide additional analytics. ESA provides real-time correlation across sessions and events as well as between different types of events, such as log and packet data. Investigation provides the ability to drill into data, examine events and files, and reconstruct events in a safe environment. The Malware Analysis service provides real-time, automated inspection for malicious activity in network sessions and associated files. 7
8 Security Analytics User Interface Security Analytics User Interface At a very high level, Security Analytics performs two functions: Provides a graphical browser-based user interface to administer the Security Analytics architecture, setup configurations and permissions for services. Acquires the data from the Warehouse, Decoders and Concentrators, performs analysis, runs alerts and reports. All Security Analytics modules share a common approach to presenting data and configuration options using a series of dashboards, views, grids, and dialogs. This helps users to navigate in a seamless and easily understandable way. Once familiar with the user interface, users can further improve their productivity by creating custom dashboards for specific purposes. For example, a set of custom dashboards can present information for different regions or different types of threats. Security Analytics Modules Security Analytics organizes administrative, analytical, and reporting tasks into modules representing logical groupings of functions and tasks for services: The dashboard is the entry point for all Security Analytics modules, providing a portal into functions of other modules for user convenience. The Administration module is the user interface for administering and monitoring appliances, devices, and services. When configured, appliances, devices, and services are available to other Security Analytics modules. The Investigation module is the user interface that allows visualization of packets captured by Security Analytics appliances. Malware Analysis is the user interface for automated malware analysis. The Live module is the user interface to access and manage resources available to customers through the Live Content Management System. The Reports and Alerts modules provide the user interface for automated reporting and alerting functions. The Incidents module provides the Incident Management function in Security Analytics. The incident management function is an easy way to track the incident response process and provides the following capabilities: Track the Incident Response in a consistent way. Automate the process of creating actionable security incidents from incoming alerts. Provide business context and investigational tools to help the team discover the root causes. Track the remediation process in an automated way by integrating with a third party help desk system. 8
9 Context Glossary Context This topic defines terminology used in Security Analytics documentation. Click a letter to navigate to a specific term. A B C D E F G H I J K L M N O P R S T V W Z inology Lists The following tables list terminology alphabetically. A Administration module Alerts Anonymised data The Administration module is the user interface for administering and monitoring appliances, devices, and services. When configured, appliances, devices, and services are available to other Security Analytics modules. The Security Analytics Alerts module is the user interface for automated ralerting functions. "Data are anonymised if all identifying elements have been eliminated from a set of personal data. No element may be left in the information which could, by exercising reasonable effort, serve to re-identify the person(s) concerned. Where data have been successfully anonymised, they are no longer personal data." (Source - EU_DP_LAW_HANDBOOK) This term is defined as part of the Security Analytics data privacy solution. anonymization Archiver The Privacy Technology Focus Group defines anonymization as a technology that converts clear text data into a nonhuman readable and irreversible form, including but not limited to one-way hashes and encryption techniques in which the decryption key has been discarded. This term is defined as part of the Security Analytics data privacy solution. The RSA Archiver is an appliance that enables long-term log archiving by indexing and compressing log data and sending it to archiving storage. 9
10 inology Lists B Broker The RSA Broker is an appliance and a service in the Security Analytics network. Brokers aggregate data captured by configured Concentrators, and Concentrators aggregate data from Decoders. Therefore, a Broker bridges the multiple real-time data stores held in the various Decoder/Concentrator pairs throughout the infrastructure. C capacity Security Analytics has a modular-capacity architecture enabled with direct-attached capacity (DACs) or storage area networks (SANs), that adapts to the organization's short-term investigation and longer-term analytic and data-retention needs. Concentrator Core Database Core services The RSA Concentrator is an appliance and service in the Security Analytics network. Concentrators index metadata extracted from network or log data and makes it available for enterprise-wide querying and real-time analytics while also facilitating reporting and alerting. This refers to the combination of the Packet, Meta, Session, and Index data. In Security Analytics, the Core services ingest and parse data, generate meta data, and aggregate generated meta data with the raw data. The Core services are Decoder, Log Decoder, Concentrator, and Broker. D dashboard Decoder downstream system and components drill point The dashboard is the entry point for all Security Analytics modules in the web-based Security Analytics user interface, providing a portal into functions of other modules for user convenience. The RSA Decoder is an appliance and service in the Security Analytics network. In the Security Analytics network}}, packet data is collected using an appliance called Decoder, while the Log Decoder collects log events. The Decoder captures, parses, and reconstructs all network traffic from Layers 2-7, or log and event data from hundreds of devices. As opposed to core components, downstream systems use data stored on Core services for analytics, therefore, the operations of downstream services are dependent on Security Analytics Core services. The downstream systems are Archiver, Warehouse, ESA, Malware Analysis, Investigation, and Reporting. A set of data that an analyst has brought into focus using queries and filters in the Investigation view. In effect, the analyst drills into the captured data to find interesting data that may harbor harmful files or code. 10
11 inology Lists E Event Stream Analysis (ESA) EVP The RSA Event Stream Analysis (ESA) appliance provides advanced stream analytics such as correlation and complex event processing at high throughputs and low latency. It is capable of processing large volumes of disparate event data from Concentrators. ESA uses an advanced Event Processing Language that allows analysts to express filtering, aggregation, joins, pattern recognition and correlation across multiple disparate event streams. Event Stream Analysis helps to perform powerful incident detection and alerting. Events per second is a measure of the processing capacity for an RSA host that is consuming data. F forensics implementation In a forensics implementation, the base Security Analytics configuration requires these components: Decoder, Concentrator, Broker, ESA, and Malware Analysis. An optional component is the Incident Management service, which resides on the ESA system and is used to prioritize alerts. G Global Audit Logging Global Audit Logging provides Security Analytics auditors with consolidated visibility into user activities within Security Analytics in real-time from one centralized location. This visibility includes audit logs gathered from the Security Analytics system and the different services throughout the Security Analytics infrastructure. H hashing host An obfuscation method used to protect sensitive data. A host is the machine on which a service runs. Also referred to as an appliance, a host can be a physical or virtual machine. 11
12 inology Lists I identifiability "An individual is identified in this information; or if an individual, while not identified, is described in this information in a way which makes it possible to find out who the data subject is by conducting further research." (Source - EU_DP_LAW_HANDBOOK) This term is used when discussing the Security Analytics data privacy solution. Incident Management service Incidents module index Investigation module The Incident Management service resides on the ESA system and is used to prioritize alerts. The Incidents module provides the Incident Management function in Security Analytics. The incident management function is an easy way to track the incident response process. The index is a collection of files that provides a way to look up Session IDs using meta values. The Investigation module is the Security Analytics user interface that allows visualization and reconstruction of packets and logs captured by Security Analytics appliances. J jobs system The Security Analytics jobs system lets you begin a long-running task and continue using other parts of Security Analytics while the job is running. Not only can you monitor the progress of the task, but you can also receive notifications when the task has completed and whether the result was success or failure. While you are working in Security Analytics, you can open a quick view of your jobs from the toolbar. K k There are no definitions in this section. L Live module The Live module is the Security Analytics user interface to access and manage resources available to customers through the Live Content Management System. 12
13 inology Lists Log Decoder A Log Decoder is a type of Decoder that collects logs rather than packets. It can collect four different log types - Syslog, ODBC, Windows eventing, and flat files. M Malware Analysis Message Digest meta meta DB Meta ID meta items meta key meta value metered licensing Malware Analysis is an appliance and a colocated service in Security Analytics. The service is used for automated malware analysis and is accessible through the Investigation module. Uses a one-way hash function to turn an arbitrary number of bytes into a fixed-length byte sequence. This is used as part of a data privacy solution. Meta is shorthand for "meta items" or metadata. In Security Analytics it is used in various combinations. The meta database contains items of information that are extracted by a Decoder or Log Decoder from the raw data stream. Parsers, rules, or feeds can generate meta items. A number used to uniquely identify a meta item in the meta database. A Decoder ingests and parses raw data, creating meta items (metadata) in the process. A name used to classify the type of each meta item. Common meta keys include ip.src, time, or service. Each meta item contains a value. The value is what each parser, feed, or rule generates. Metered licensing is a Security Analytics licensing method based on a throughput per day of logs (SIEM) or network packets (Network Monitoring and Network Malware), combined with the separate purchase of the hardware needed to deploy the system and meet customers' retention requirements. N NextGen A term that was formerly used to describe the RSA Broker, Concentrator, Decoder, and Log Decoder. These are now known as Security Analytics Core appliances and services. 13
14 inology Lists O out-of-the-box trial licensing Out-of- Compliance banners Security Analytics 10.5 ships with a default Trial out-of-the-box license that enables customers to use the product with full functionality for 90 days. The 90-day time period begins when the Security Analytics user interface is configured and used for the first time. A red banner is displayed during log on if your license is expired or you have exceeded your allotted usage. You may also see a red banner if your license has internal errors. A red banner cannot be dismissed. A yellow banner is displayed during system log on if your license is approaching expiration or you are nearing your allotted usage. You can dismiss the yellow banner by clicking the Dismiss button. P Packet ID packet DB A number used to uniquely identify a packet or log in a packet database. The packet database contains the raw, captured data. On a Decoder, the packet database contains packets as captured from the network. Log Decoders use the packet database to store raw logs. The raw data stored in the packet database is accessible by a Packet ID, however, this ID is typically never visible to the end user. personal data "Under EU law, personal data are defined as information relating to an identified or identifiable natural person, that is, information about a person whose identity is either manifestly clear or can at least be established by obtaining additional information." (Source - EU_DP_LAW_HANDBOOK) R RSA Analytics Warehouse Reports module roles A Hadoop-based distributed computing system, which collects, manages, and enables analytics and reporting on longer-term sets of security data, for example, months or years. The Warehouse can be made up of three or more nodes depending on the organization's analytic, archiving, and resiliency requirements. It requires a service called Warehouse Connector to collect meta and events from Decoder and Log Decoder and write them in Avro format into a Hadoop-based distributed computing system. The Reports module is the Security Analytics user interface for automated reporting functions. In Security Analytics, roles determine what users can do. A role has permissions assigned to it and you must assign a role to each user. The user then has permission to do what the role allows. 14
15 inology Lists S Security Analytics Core (formerly NextGen) Security Analytics Server sensitive data The following products are part of the Security Analytics Core suite: Decoder, Log Decoder, Concentrator, Broker, Archiver, Workbench. The web server for reporting, investigation, administration, and other aspects of the analysts interface. Also enables reporting on data held in the Warehouse. Regulatory mandates in some locations, for example the European Union (EU), require that information systems provide a means of protecting data when operating on sensitive data. Any data that could directly or indirectly depict "Who did what when?" may be considered personally identifiable or sensitive data. service service-based licensing session Session ID Session DB A service runs on a host and performs a unique function, such as collecting logs or archiving data. Security Analytics services include Archiver, Broker, Concentrator, Decoder, Event Stream Analysis, Incident Management, IPDB Extractor, Log Collector, Log Decoder, Malware Analysis, Reporting Engine, Warehouse Connector, and Workbench. This is a per-service permanent Security Analytics license that has no expiration date. Support for servicebased licensing is applicable for all appliances that require a license. On a packet Decoder, a session represents a single, logical, network stream. For example, a TCP/IP connection is one session. On a Log Decoder, each log event is one session. Each session contains references to all the Packet IDs and Meta IDs that refer to the session. A number used to uniquely identify a session in the Session DB. The session database contains information that ties the packet and meta items together into sessions. SIEM implementation subscription licensing In a security information and event management (SIEM) implementation, the base Security Analytics configuration requires these components: Log Decoder, Concentrator, Broker, Event Stream Analysis (ESA), and the Security Analytics server. Subscription licenses for Security Analytics are offered for a specific time period that ranges from 12 to 36 months. Once licensed, subscription licenses are non-cancellable and non-downgradeable. T Transient data In Security Analytics, transient data is not stored on disk. When a meta key is marked as transient in the custom index file or the Services Config view where parsers for the service are configured, the Decoder, Log Decoder does not save the meta key to disk, but holds it in memory where it can be analyzed until overwritten. 15
16 inology Lists U u There are no definitions in this section. V virtual appliance A virtual instance of a Security Analytics appliance. W Warehouse Connector Windows eventing Warehouse Connector allows collects meta and events from Decoders and write them in Avro format into a Hadoop-based distributed computing system. You can set up Warehouse Connector as a service on existing Log Decoders or Decoders or it can be run as a virtual appliance in your virtual environment. Windows eventing pertains to Log Decoders, and refers to the Windows 2008 collection methodology and flat files can be obtained via SFTP. Z z There are no definitions in this section. 16
Detect & Investigate Threats. OVERVIEW
 Detect & Investigate Threats. OVERVIEW HIGHLIGHTS Introducing RSA Security Analytics, Providing: Security monitoring Incident investigation Compliance reporting Providing Big Data Security Analytics Enterprise-wide
Detect & Investigate Threats. OVERVIEW HIGHLIGHTS Introducing RSA Security Analytics, Providing: Security monitoring Incident investigation Compliance reporting Providing Big Data Security Analytics Enterprise-wide
Discover & Investigate Advanced Threats. OVERVIEW
 Discover & Investigate Advanced Threats. OVERVIEW HIGHLIGHTS Introducing RSA Security Analytics, Providing: Security monitoring Incident investigation Compliance reporting Providing Big Data Security Analytics
Discover & Investigate Advanced Threats. OVERVIEW HIGHLIGHTS Introducing RSA Security Analytics, Providing: Security monitoring Incident investigation Compliance reporting Providing Big Data Security Analytics
RSA Security Analytics Netflow Collection Configuration Guide
 RSA Security Analytics Netflow Collection Configuration Guide Copyright 2010-2015 RSA, the Security Division of EMC. All rights reserved. Trademarks RSA, the RSA Logo and EMC are either registered trademarks
RSA Security Analytics Netflow Collection Configuration Guide Copyright 2010-2015 RSA, the Security Division of EMC. All rights reserved. Trademarks RSA, the RSA Logo and EMC are either registered trademarks
RSA Security Analytics Netflow Collection Configuration Guide
 RSA Security Analytics Netflow Collection Configuration Guide Copyright 2010-2015 RSA, the Security Division of EMC. All rights reserved. Trademarks RSA, the RSA Logo and EMC are either registered trademarks
RSA Security Analytics Netflow Collection Configuration Guide Copyright 2010-2015 RSA, the Security Division of EMC. All rights reserved. Trademarks RSA, the RSA Logo and EMC are either registered trademarks
RSA Security Analytics Virtual Appliance Setup Guide
 RSA Security Analytics Virtual Appliance Setup Guide Copyright 2010-2015 RSA, the Security Division of EMC. All rights reserved. Trademarks RSA, the RSA Logo and EMC are either registered trademarks or
RSA Security Analytics Virtual Appliance Setup Guide Copyright 2010-2015 RSA, the Security Division of EMC. All rights reserved. Trademarks RSA, the RSA Logo and EMC are either registered trademarks or
CHANGING THE SECURITY MONITORING STATUS QUO Solving SIEM problems with RSA Security Analytics
 CHANGING THE SECURITY MONITORING STATUS QUO Solving SIEM problems with RSA Security Analytics TRADITIONAL SIEMS ARE SHOWING THEIR AGE Security Information and Event Management (SIEM) tools have been a
CHANGING THE SECURITY MONITORING STATUS QUO Solving SIEM problems with RSA Security Analytics TRADITIONAL SIEMS ARE SHOWING THEIR AGE Security Information and Event Management (SIEM) tools have been a
RSA Security Analytics. S4 Broker Setup Guide
 RSA Security Analytics S4 Broker Setup Guide Copyright 2010-2013 RSA, the Security Division of EMC. All rights reserved. Trademarks RSA, the RSA Logo and EMC are either registered trademarks or trademarks
RSA Security Analytics S4 Broker Setup Guide Copyright 2010-2013 RSA, the Security Division of EMC. All rights reserved. Trademarks RSA, the RSA Logo and EMC are either registered trademarks or trademarks
LOG AND EVENT MANAGEMENT FOR SECURITY AND COMPLIANCE
 PRODUCT BRIEF LOG AND EVENT MANAGEMENT FOR SECURITY AND COMPLIANCE The Tripwire VIA platform delivers system state intelligence, a continuous approach to security that provides leading indicators of breach
PRODUCT BRIEF LOG AND EVENT MANAGEMENT FOR SECURITY AND COMPLIANCE The Tripwire VIA platform delivers system state intelligence, a continuous approach to security that provides leading indicators of breach
LOG MANAGEMENT AND SIEM FOR SECURITY AND COMPLIANCE
 PRODUCT BRIEF LOG MANAGEMENT AND SIEM FOR SECURITY AND COMPLIANCE As part of the Tripwire VIA platform, Tripwire Log Center offers out-of-the-box integration with Tripwire Enterprise to offer visibility
PRODUCT BRIEF LOG MANAGEMENT AND SIEM FOR SECURITY AND COMPLIANCE As part of the Tripwire VIA platform, Tripwire Log Center offers out-of-the-box integration with Tripwire Enterprise to offer visibility
LOG INTELLIGENCE FOR SECURITY AND COMPLIANCE
 PRODUCT BRIEF uugiven today s environment of sophisticated security threats, big data security intelligence solutions and regulatory compliance demands, the need for a log intelligence solution has become
PRODUCT BRIEF uugiven today s environment of sophisticated security threats, big data security intelligence solutions and regulatory compliance demands, the need for a log intelligence solution has become
RSA SecurID Software Token Security Best Practices Guide
 RSA SecurID Software Token Security Best Practices Guide Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com. Trademarks RSA, the RSA
RSA SecurID Software Token Security Best Practices Guide Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com. Trademarks RSA, the RSA
RSA SecurID Software Token 1.0 for Android Administrator s Guide
 RSA SecurID Software Token 1.0 for Android Administrator s Guide Contact Information See the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com Trademarks RSA,
RSA SecurID Software Token 1.0 for Android Administrator s Guide Contact Information See the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com Trademarks RSA,
How To Secure An Rsa Authentication Agent
 RSA Authentication Agents Security Best Practices Guide Version 3 Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com. Trademarks RSA,
RSA Authentication Agents Security Best Practices Guide Version 3 Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com. Trademarks RSA,
AlienVault Unified Security Management (USM) 4.x-5.x. Deployment Planning Guide
 AlienVault Unified Security Management (USM) 4.x-5.x Deployment Planning Guide USM 4.x-5.x Deployment Planning Guide, rev. 1 Copyright AlienVault, Inc. All rights reserved. The AlienVault Logo, AlienVault,
AlienVault Unified Security Management (USM) 4.x-5.x Deployment Planning Guide USM 4.x-5.x Deployment Planning Guide, rev. 1 Copyright AlienVault, Inc. All rights reserved. The AlienVault Logo, AlienVault,
Cautela Labs Cloud Agile. Secured. Threat Management Security Solutions at Work
 Cautela Labs Cloud Agile. Secured. Threat Management Security Solutions at Work Security concerns and dangers come both from internal means as well as external. In order to enhance your security posture
Cautela Labs Cloud Agile. Secured. Threat Management Security Solutions at Work Security concerns and dangers come both from internal means as well as external. In order to enhance your security posture
Cyber Security. BDS PhantomWorks. Boeing Energy. Copyright 2011 Boeing. All rights reserved.
 Cyber Security Automation of energy systems provides attack surfaces that previously did not exist Cyber attacks have matured from teenage hackers to organized crime to nation states Centralized control
Cyber Security Automation of energy systems provides attack surfaces that previously did not exist Cyber attacks have matured from teenage hackers to organized crime to nation states Centralized control
IBM InfoSphere Guardium Data Activity Monitor for Hadoop-based systems
 IBM InfoSphere Guardium Data Activity Monitor for Hadoop-based systems Proactively address regulatory compliance requirements and protect sensitive data in real time Highlights Monitor and audit data activity
IBM InfoSphere Guardium Data Activity Monitor for Hadoop-based systems Proactively address regulatory compliance requirements and protect sensitive data in real time Highlights Monitor and audit data activity
What s New in Security Analytics 10.4. Be the Hunter.. Not the Hunted
 What s New in Security Analytics 10.4 Be the Hunter.. Not the Hunted Attackers Are Outpacing Detection Attacker Capabilities Time To Discovery Source: VERIZON 2014 DATA BREACH INVESTIGATIONS REPORT 2 TRANSFORM
What s New in Security Analytics 10.4 Be the Hunter.. Not the Hunted Attackers Are Outpacing Detection Attacker Capabilities Time To Discovery Source: VERIZON 2014 DATA BREACH INVESTIGATIONS REPORT 2 TRANSFORM
RSA SecurID Software Token 1.3 for iphone and ipad Administrator s Guide
 RSA SecurID Software Token 1.3 for iphone and ipad Administrator s Guide Contact Information See the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com Trademarks
RSA SecurID Software Token 1.3 for iphone and ipad Administrator s Guide Contact Information See the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com Trademarks
with Managing RSA the Lifecycle of Key Manager RSA Streamlining Security Operations Data Loss Prevention Solutions RSA Solution Brief
 RSA Solution Brief Streamlining Security Operations with Managing RSA the Lifecycle of Data Loss Prevention and Encryption RSA envision Keys with Solutions RSA Key Manager RSA Solution Brief 1 Who is asking
RSA Solution Brief Streamlining Security Operations with Managing RSA the Lifecycle of Data Loss Prevention and Encryption RSA envision Keys with Solutions RSA Key Manager RSA Solution Brief 1 Who is asking
Unified Security, ATP and more
 SYMANTEC Unified Security, ATP and more TAKE THE NEXT STEP Martin Werner PreSales Consultant, Symantec Switzerland AG MEET SWISS INFOSEC! 27.01.2016 Unified Security 2 Symantec Enterprise Security Users
SYMANTEC Unified Security, ATP and more TAKE THE NEXT STEP Martin Werner PreSales Consultant, Symantec Switzerland AG MEET SWISS INFOSEC! 27.01.2016 Unified Security 2 Symantec Enterprise Security Users
IBM Security. 2013 IBM Corporation. 2013 IBM Corporation
 IBM Security Security Intelligence What is Security Intelligence? Security Intelligence --noun 1.the real-time collection, normalization and analytics of the data generated by users, applications and infrastructure
IBM Security Security Intelligence What is Security Intelligence? Security Intelligence --noun 1.the real-time collection, normalization and analytics of the data generated by users, applications and infrastructure
NETWRIX EVENT LOG MANAGER
 NETWRIX EVENT LOG MANAGER QUICK-START GUIDE FOR THE ENTERPRISE EDITION Product Version: 4.0 July/2012. Legal Notice The information in this publication is furnished for information use only, and does not
NETWRIX EVENT LOG MANAGER QUICK-START GUIDE FOR THE ENTERPRISE EDITION Product Version: 4.0 July/2012. Legal Notice The information in this publication is furnished for information use only, and does not
RSA Authentication Manager 8.1 Help Desk Administrator s Guide
 RSA Authentication Manager 8.1 Help Desk Administrator s Guide Contact Information Go to the RSA corporate website for regional Customer Support telephone and fax numbers: www.emc.com/domains/rsa/index.htm
RSA Authentication Manager 8.1 Help Desk Administrator s Guide Contact Information Go to the RSA corporate website for regional Customer Support telephone and fax numbers: www.emc.com/domains/rsa/index.htm
Best Practices for Log File Management (Compliance, Security, Troubleshooting)
 Log Management: Best Practices for Security and Compliance The Essentials Series Best Practices for Log File Management (Compliance, Security, Troubleshooting) sponsored by Introduction to Realtime Publishers
Log Management: Best Practices for Security and Compliance The Essentials Series Best Practices for Log File Management (Compliance, Security, Troubleshooting) sponsored by Introduction to Realtime Publishers
Case Study: University of Dayton and Novell Identity & Security Solutions Rick Wagner
 Case Study: University of Dayton and Novell Identity & Security Solutions Rick Wagner Senior Product Manager, Security Management rwagner@novell.com University of Dayton Recognized by US News and World
Case Study: University of Dayton and Novell Identity & Security Solutions Rick Wagner Senior Product Manager, Security Management rwagner@novell.com University of Dayton Recognized by US News and World
RSA Authentication Manager 7.1 Basic Exercises
 RSA Authentication Manager 7.1 Basic Exercises Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com Trademarks RSA and the RSA logo
RSA Authentication Manager 7.1 Basic Exercises Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com Trademarks RSA and the RSA logo
RSA Security Analytics Certified Administrator (CA) Certification Examination Study Guide
 RSA Security Analytics Certified Administrator (CA) Certification Examination Study Guide Introduction The RSA Security Analytics Certified Administrator (CA) examination is based on the critical job functions
RSA Security Analytics Certified Administrator (CA) Certification Examination Study Guide Introduction The RSA Security Analytics Certified Administrator (CA) examination is based on the critical job functions
RSA Authentication Manager 7.1 to 8.1 Migration Guide: Upgrading RSA SecurID Appliance 3.0 On Existing Hardware
 RSA Authentication Manager 7.1 to 8.1 Migration Guide: Upgrading RSA SecurID Appliance 3.0 On Existing Hardware Contact Information Go to the RSA corporate website for regional Customer Support telephone
RSA Authentication Manager 7.1 to 8.1 Migration Guide: Upgrading RSA SecurID Appliance 3.0 On Existing Hardware Contact Information Go to the RSA corporate website for regional Customer Support telephone
LogInspect 5 Product Features Robust. Dynamic. Unparalleled.
 LogInspect 5 Product Features Robust. Dynamic. Unparalleled. Enjoy ultra fast search capabilities in simple and complex modes optimized for Big Data Easily filter and display relevant topics, eg: Top 10
LogInspect 5 Product Features Robust. Dynamic. Unparalleled. Enjoy ultra fast search capabilities in simple and complex modes optimized for Big Data Easily filter and display relevant topics, eg: Top 10
Netwrix Auditor. Administrator's Guide. Version: 7.1 10/30/2015
 Netwrix Auditor Administrator's Guide Version: 7.1 10/30/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from Netwrix Corporation
Netwrix Auditor Administrator's Guide Version: 7.1 10/30/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from Netwrix Corporation
LogPoint 5.1 Product Features Robust. Dynamic. Unparalleled.
 LogPoint 5.1 Product Features Robust. Dynamic. Unparalleled. LOGPOINT Enjoy ultra fast search capabilities in simple and complex modes optimized for Big Data Easily filter and display relevant topics,
LogPoint 5.1 Product Features Robust. Dynamic. Unparalleled. LOGPOINT Enjoy ultra fast search capabilities in simple and complex modes optimized for Big Data Easily filter and display relevant topics,
IBM QRadar Security Intelligence Platform appliances
 IBM QRadar Security Intelligence Platform Comprehensive, state-of-the-art solutions providing next-generation security intelligence Highlights Get integrated log management, security information and event
IBM QRadar Security Intelligence Platform Comprehensive, state-of-the-art solutions providing next-generation security intelligence Highlights Get integrated log management, security information and event
Secret Server Splunk Integration Guide
 Secret Server Splunk Integration Guide Table of Contents Meeting Information Security Compliance Mandates: Secret Server and Splunk SIEM Integration and Configuration... 1 The Secret Server Approach to
Secret Server Splunk Integration Guide Table of Contents Meeting Information Security Compliance Mandates: Secret Server and Splunk SIEM Integration and Configuration... 1 The Secret Server Approach to
Tech Brief. Choosing the Right Log Management Product. By Michael Pastore
 Choosing the Right Log Management Product By Michael Pastore Tech Brief an Log management is IT s version of the good old fashioned detective work that authorities credit for solving a lot of crimes. It
Choosing the Right Log Management Product By Michael Pastore Tech Brief an Log management is IT s version of the good old fashioned detective work that authorities credit for solving a lot of crimes. It
Clavister InSight TM. Protecting Values
 Clavister InSight TM Clavister SSP Security Services Platform firewall VPN termination intrusion prevention anti-virus anti-spam content filtering traffic shaping authentication Protecting Values & Enterprise-wide
Clavister InSight TM Clavister SSP Security Services Platform firewall VPN termination intrusion prevention anti-virus anti-spam content filtering traffic shaping authentication Protecting Values & Enterprise-wide
IBM QRadar Security Intelligence April 2013
 IBM QRadar Security Intelligence April 2013 1 2012 IBM Corporation Today s Challenges 2 Organizations Need an Intelligent View into Their Security Posture 3 What is Security Intelligence? Security Intelligence
IBM QRadar Security Intelligence April 2013 1 2012 IBM Corporation Today s Challenges 2 Organizations Need an Intelligent View into Their Security Posture 3 What is Security Intelligence? Security Intelligence
RSA Security Analytics
 RSA Security Analytics Event Source Log Configuration Guide RSA Authentication Manager and User Credential Manager Last Modified: Friday, March 13, 2015 Event Source Product Information: Vendor: RSA, The
RSA Security Analytics Event Source Log Configuration Guide RSA Authentication Manager and User Credential Manager Last Modified: Friday, March 13, 2015 Event Source Product Information: Vendor: RSA, The
IBM SECURITY QRADAR INCIDENT FORENSICS
 IBM SECURITY QRADAR INCIDENT FORENSICS DELIVERING CLARITY TO CYBER SECURITY INVESTIGATIONS Gyenese Péter Channel Sales Leader, CEE IBM Security Systems 12014 IBM Corporation Harsh realities for many enterprise
IBM SECURITY QRADAR INCIDENT FORENSICS DELIVERING CLARITY TO CYBER SECURITY INVESTIGATIONS Gyenese Péter Channel Sales Leader, CEE IBM Security Systems 12014 IBM Corporation Harsh realities for many enterprise
Scalability in Log Management
 Whitepaper Scalability in Log Management Research 010-021609-02 ArcSight, Inc. 5 Results Way, Cupertino, CA 95014, USA www.arcsight.com info@arcsight.com Corporate Headquarters: 1-888-415-ARST EMEA Headquarters:
Whitepaper Scalability in Log Management Research 010-021609-02 ArcSight, Inc. 5 Results Way, Cupertino, CA 95014, USA www.arcsight.com info@arcsight.com Corporate Headquarters: 1-888-415-ARST EMEA Headquarters:
Symantec Security Information Manager 4.8 Release Notes
 Symantec Security Information Manager 4.8 Release Notes Symantec Security Information Manager 4.8 Release Notes The software described in this book is furnished under a license agreement and may be used
Symantec Security Information Manager 4.8 Release Notes Symantec Security Information Manager 4.8 Release Notes The software described in this book is furnished under a license agreement and may be used
Netwrix Auditor for Windows Server
 Netwrix Auditor for Windows Server Quick-Start Guide Version: 7.0 7/7/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from
Netwrix Auditor for Windows Server Quick-Start Guide Version: 7.0 7/7/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from
Configuring Celerra for Security Information Management with Network Intelligence s envision
 Configuring Celerra for Security Information Management with Best Practices Planning Abstract appliance is used to monitor log information from any device on the network to determine how that device is
Configuring Celerra for Security Information Management with Best Practices Planning Abstract appliance is used to monitor log information from any device on the network to determine how that device is
RSA Authentication Manager 8.1 Help Desk Administrator s Guide. Revision 1
 RSA Authentication Manager 8.1 Help Desk Administrator s Guide Revision 1 Contact Information Go to the RSA corporate website for regional Customer Support telephone and fax numbers: www.emc.com/domains/rsa/index.htm
RSA Authentication Manager 8.1 Help Desk Administrator s Guide Revision 1 Contact Information Go to the RSA corporate website for regional Customer Support telephone and fax numbers: www.emc.com/domains/rsa/index.htm
IMPLEMENTING A SECURITY ANALYTICS ARCHITECTURE
 IMPLEMENTING A SECURITY ANALYTICS ARCHITECTURE Solution Brief SUMMARY New security threats demand a new approach to security management. Security teams need a security analytics architecture that can handle
IMPLEMENTING A SECURITY ANALYTICS ARCHITECTURE Solution Brief SUMMARY New security threats demand a new approach to security management. Security teams need a security analytics architecture that can handle
Security Information/Event Management Security Development Life Cycle Version 5
 Security Information/Event Management Security Development Life Cycle Version 5 If your enterprise is like most, you are collecting logs from most every device with security relevance. The flood of events
Security Information/Event Management Security Development Life Cycle Version 5 If your enterprise is like most, you are collecting logs from most every device with security relevance. The flood of events
An Oracle White Paper May 2013. Oracle Audit Vault and Database Firewall 12.1 Sizing Best Practices
 An Oracle White Paper May 2013 Oracle Audit Vault and Database Firewall 12.1 Sizing Best Practices Introduction... 1 Component Overview... 2 Sizing Hardware Requirements... 3 Audit Vault Server Sizing...
An Oracle White Paper May 2013 Oracle Audit Vault and Database Firewall 12.1 Sizing Best Practices Introduction... 1 Component Overview... 2 Sizing Hardware Requirements... 3 Audit Vault Server Sizing...
THE 2014 THREAT DETECTION CHECKLIST. Six ways to tell a criminal from a customer.
 THE 2014 THREAT DETECTION CHECKLIST Six ways to tell a criminal from a customer. Telling criminals from customers online isn t getting any easier. Attackers target the entire online user lifecycle from
THE 2014 THREAT DETECTION CHECKLIST Six ways to tell a criminal from a customer. Telling criminals from customers online isn t getting any easier. Attackers target the entire online user lifecycle from
Netwrix Auditor for Active Directory
 Netwrix Auditor for Active Directory Quick-Start Guide Version: 7.1 10/26/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment
Netwrix Auditor for Active Directory Quick-Start Guide Version: 7.1 10/26/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment
Netwrix Auditor for SQL Server
 Netwrix Auditor for SQL Server Quick-Start Guide Version: 7.1 10/26/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from
Netwrix Auditor for SQL Server Quick-Start Guide Version: 7.1 10/26/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from
QRadar Security Intelligence Platform Appliances
 DATASHEET Total Security Intelligence An IBM Company QRadar Security Intelligence Platform Appliances QRadar Security Intelligence Platform appliances combine typically disparate network and security management
DATASHEET Total Security Intelligence An IBM Company QRadar Security Intelligence Platform Appliances QRadar Security Intelligence Platform appliances combine typically disparate network and security management
IBM Software Top tips for securing big data environments
 IBM Software Top tips for securing big data environments Why big data doesn t have to mean big security challenges 2 Top Comprehensive tips for securing data big protection data environments for physical,
IBM Software Top tips for securing big data environments Why big data doesn t have to mean big security challenges 2 Top Comprehensive tips for securing data big protection data environments for physical,
RSA envision. Platform. Real-time Actionable Security Information, Streamlined Incident Handling, Effective Security Measures. RSA Solution Brief
 RSA Solution Brief RSA envision Platform Real-time Actionable Information, Streamlined Incident Handling, Effective Measures RSA Solution Brief The job of Operations, whether a large organization with
RSA Solution Brief RSA envision Platform Real-time Actionable Information, Streamlined Incident Handling, Effective Measures RSA Solution Brief The job of Operations, whether a large organization with
IBM Software Information Management Creating an Integrated, Optimized, and Secure Enterprise Data Platform:
 Creating an Integrated, Optimized, and Secure Enterprise Data Platform: IBM PureData System for Transactions with SafeNet s ProtectDB and DataSecure Table of contents 1. Data, Data, Everywhere... 3 2.
Creating an Integrated, Optimized, and Secure Enterprise Data Platform: IBM PureData System for Transactions with SafeNet s ProtectDB and DataSecure Table of contents 1. Data, Data, Everywhere... 3 2.
Consolidated Monitoring, Analysis, and Automated Remediation For Hybrid IT Infrastructures
 Consolidated Monitoring, Analysis, and Automated Remediation For Hybrid IT Infrastructures Goliath Performance Monitor Quick Start Configuration Guide v11.5 (v11.5) Document Date: April 2015 www.goliathtechnologies.com
Consolidated Monitoring, Analysis, and Automated Remediation For Hybrid IT Infrastructures Goliath Performance Monitor Quick Start Configuration Guide v11.5 (v11.5) Document Date: April 2015 www.goliathtechnologies.com
The Purview Solution Integration With Splunk
 The Purview Solution Integration With Splunk Integrating Application Management and Business Analytics With Other IT Management Systems A SOLUTION WHITE PAPER WHITE PAPER Introduction Purview Integration
The Purview Solution Integration With Splunk Integrating Application Management and Business Analytics With Other IT Management Systems A SOLUTION WHITE PAPER WHITE PAPER Introduction Purview Integration
Security Analytics Topology
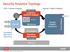 Security Analytics Topology CEP = Stream Analytics Hadoop = Batch Analytics Months to years LOGS PKTS Correlation with Live in Real Time Meta, logs, select payload Decoder Long-term, intensive analysis
Security Analytics Topology CEP = Stream Analytics Hadoop = Batch Analytics Months to years LOGS PKTS Correlation with Live in Real Time Meta, logs, select payload Decoder Long-term, intensive analysis
RSA Authentication Manager 7.1 Security Best Practices Guide. Version 2
 RSA Authentication Manager 7.1 Security Best Practices Guide Version 2 Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com. Trademarks
RSA Authentication Manager 7.1 Security Best Practices Guide Version 2 Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com. Trademarks
EMC Documentum Interactive Delivery Services Accelerated Overview
 White Paper EMC Documentum Interactive Delivery Services Accelerated A Detailed Review Abstract This white paper presents an overview of EMC Documentum Interactive Delivery Services Accelerated (IDSx).
White Paper EMC Documentum Interactive Delivery Services Accelerated A Detailed Review Abstract This white paper presents an overview of EMC Documentum Interactive Delivery Services Accelerated (IDSx).
RSA Security Analytics
 RSA Security Analytics Event Source Log Configuration Guide VMware NSX Last Modified: Friday, March 13, 2015 Event Source Product Information: Vendor: VMware Event Source: VMware NSX Version: 6.1.2 RSA
RSA Security Analytics Event Source Log Configuration Guide VMware NSX Last Modified: Friday, March 13, 2015 Event Source Product Information: Vendor: VMware Event Source: VMware NSX Version: 6.1.2 RSA
An Oracle White Paper June 2011. Oracle Database Firewall 5.0 Sizing Best Practices
 An Oracle White Paper June 2011 Oracle Database Firewall 5.0 Sizing Best Practices Introduction... 1 Component Overview... 1 Database Firewall Deployment Modes... 2 Sizing Hardware Requirements... 2 Database
An Oracle White Paper June 2011 Oracle Database Firewall 5.0 Sizing Best Practices Introduction... 1 Component Overview... 1 Database Firewall Deployment Modes... 2 Sizing Hardware Requirements... 2 Database
RSA Security Analytics
 RSA Security Analytics Event Source Log Configuration Guide Sourcefire Defense Center Last Modified: Thursday, July 30, 2015 Event Source Product Information: Vendor: Sourcefire Event Source: Defense Center
RSA Security Analytics Event Source Log Configuration Guide Sourcefire Defense Center Last Modified: Thursday, July 30, 2015 Event Source Product Information: Vendor: Sourcefire Event Source: Defense Center
NitroView. Content Aware SIEM TM. Unified Security and Compliance Unmatched Speed and Scale. Application Data Monitoring. Database Monitoring
 NitroView Unified Security and Compliance Unmatched Speed and Scale Application Data Monitoring Database Monitoring Log Management Content Aware SIEM TM IPS Today s security challenges demand a new approach
NitroView Unified Security and Compliance Unmatched Speed and Scale Application Data Monitoring Database Monitoring Log Management Content Aware SIEM TM IPS Today s security challenges demand a new approach
Monitor Mobile Devices via ActiveSync Using EventTracker
 Monitor Mobile Devices via ActiveSync Using EventTracker White Paper Publication Date: March 1, 2013 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com About This Guide Exchange
Monitor Mobile Devices via ActiveSync Using EventTracker White Paper Publication Date: March 1, 2013 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com About This Guide Exchange
Breach Found. Did It Hurt?
 ANALYST BRIEF Breach Found. Did It Hurt? INCIDENT RESPONSE PART 2: A PROCESS FOR ASSESSING LOSS Authors Christopher Morales, Jason Pappalexis Overview Malware infections impact every organization. Many
ANALYST BRIEF Breach Found. Did It Hurt? INCIDENT RESPONSE PART 2: A PROCESS FOR ASSESSING LOSS Authors Christopher Morales, Jason Pappalexis Overview Malware infections impact every organization. Many
IBM Security QRadar Risk Manager
 IBM Security QRadar Risk Manager Proactively manage vulnerabilities and network device configuration to reduce risk, improve compliance Highlights Collect network security device configuration data to
IBM Security QRadar Risk Manager Proactively manage vulnerabilities and network device configuration to reduce risk, improve compliance Highlights Collect network security device configuration data to
IBM Security Intelligence Strategy
 IBM Security Intelligence Strategy Delivering Insight with Agility October 17, 2014 Victor Margina Security Solutions Accent Electronic 12013 IBM Corporation We are in an era of continuous breaches Operational
IBM Security Intelligence Strategy Delivering Insight with Agility October 17, 2014 Victor Margina Security Solutions Accent Electronic 12013 IBM Corporation We are in an era of continuous breaches Operational
CA Oblicore Guarantee for Managed Service Providers
 PRODUCT SHEET CA Oblicore Guarantee for Managed Service Providers CA Oblicore Guarantee for Managed Service Providers Value proposition CA Oblicore Guarantee is designed to automate, activate and accelerate
PRODUCT SHEET CA Oblicore Guarantee for Managed Service Providers CA Oblicore Guarantee for Managed Service Providers Value proposition CA Oblicore Guarantee is designed to automate, activate and accelerate
RSA Authentication Agent 7.2 for Microsoft Windows Installation and Administration Guide
 RSA Authentication Agent 7.2 for Microsoft Windows Installation and Administration Guide Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com
RSA Authentication Agent 7.2 for Microsoft Windows Installation and Administration Guide Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com
Securing your IT infrastructure with SOC/NOC collaboration
 Technical white paper Securing your IT infrastructure with SOC/NOC collaboration Universal log management for IT operations Table of contents Executive summary 2 IT operations: Handle IT incidents and
Technical white paper Securing your IT infrastructure with SOC/NOC collaboration Universal log management for IT operations Table of contents Executive summary 2 IT operations: Handle IT incidents and
GETTING REAL ABOUT SECURITY MANAGEMENT AND "BIG DATA"
 GETTING REAL ABOUT SECURITY MANAGEMENT AND "BIG DATA" A Roadmap for "Big Data" in Security Analytics ESSENTIALS This paper examines: Escalating complexity of the security management environment, from threats
GETTING REAL ABOUT SECURITY MANAGEMENT AND "BIG DATA" A Roadmap for "Big Data" in Security Analytics ESSENTIALS This paper examines: Escalating complexity of the security management environment, from threats
BlackShield ID Agent for Remote Web Workplace
 Agent for Remote Web Workplace 2010 CRYPTOCard Corp. All rights reserved. http:// www.cryptocard.com Copyright Copyright 2010, CRYPTOCard All Rights Reserved. No part of this publication may be reproduced,
Agent for Remote Web Workplace 2010 CRYPTOCard Corp. All rights reserved. http:// www.cryptocard.com Copyright Copyright 2010, CRYPTOCard All Rights Reserved. No part of this publication may be reproduced,
McAfee Security Information Event Management (SIEM) Administration Course 101
 McAfee Security Information Event Management (SIEM) Administration Course 101 Intel Security Education Services Administration Course The McAfee SIEM Administration course from McAfee Education Services
McAfee Security Information Event Management (SIEM) Administration Course 101 Intel Security Education Services Administration Course The McAfee SIEM Administration course from McAfee Education Services
WHITE PAPER SPLUNK SOFTWARE AS A SIEM
 SPLUNK SOFTWARE AS A SIEM Improve your security posture by using Splunk as your SIEM HIGHLIGHTS Splunk software can be used to operate security operations centers (SOC) of any size (large, med, small)
SPLUNK SOFTWARE AS A SIEM Improve your security posture by using Splunk as your SIEM HIGHLIGHTS Splunk software can be used to operate security operations centers (SOC) of any size (large, med, small)
RAVEN, Network Security and Health for the Enterprise
 RAVEN, Network Security and Health for the Enterprise The Promia RAVEN is a hardened Security Information and Event Management (SIEM) solution further providing network health, and interactive visualizations
RAVEN, Network Security and Health for the Enterprise The Promia RAVEN is a hardened Security Information and Event Management (SIEM) solution further providing network health, and interactive visualizations
Niara Security Intelligence. Overview. Threat Discovery and Incident Investigation Reimagined
 Niara Security Intelligence Threat Discovery and Incident Investigation Reimagined Niara enables Compromised user discovery Malicious insider discovery Threat hunting Incident investigation Overview In
Niara Security Intelligence Threat Discovery and Incident Investigation Reimagined Niara enables Compromised user discovery Malicious insider discovery Threat hunting Incident investigation Overview In
EMC ViPR Controller. Version 2.4. User Interface Virtual Data Center Configuration Guide 302-002-416 REV 01 DRAFT
 EMC ViPR Controller Version 2.4 User Interface Virtual Data Center Configuration Guide 302-002-416 REV 01 DRAFT Copyright 2014-2015 EMC Corporation. All rights reserved. Published in USA. Published November,
EMC ViPR Controller Version 2.4 User Interface Virtual Data Center Configuration Guide 302-002-416 REV 01 DRAFT Copyright 2014-2015 EMC Corporation. All rights reserved. Published in USA. Published November,
Find the needle in the security haystack
 Find the needle in the security haystack Gunnar Kristian Kopperud Principal Presales Consultant Security & Endpoint Management Technology Day Oslo 1 Find the needle in the security haystack Manually deep
Find the needle in the security haystack Gunnar Kristian Kopperud Principal Presales Consultant Security & Endpoint Management Technology Day Oslo 1 Find the needle in the security haystack Manually deep
QRadar Security Management Appliances
 QRadar Security Management Appliances Q1 Labs QRadar network security management appliances and related software provide enterprises with an integrated framework that combines typically disparate network
QRadar Security Management Appliances Q1 Labs QRadar network security management appliances and related software provide enterprises with an integrated framework that combines typically disparate network
IBM TSM DISASTER RECOVERY BEST PRACTICES WITH EMC DATA DOMAIN DEDUPLICATION STORAGE
 White Paper IBM TSM DISASTER RECOVERY BEST PRACTICES WITH EMC DATA DOMAIN DEDUPLICATION STORAGE Abstract This white paper focuses on recovery of an IBM Tivoli Storage Manager (TSM) server and explores
White Paper IBM TSM DISASTER RECOVERY BEST PRACTICES WITH EMC DATA DOMAIN DEDUPLICATION STORAGE Abstract This white paper focuses on recovery of an IBM Tivoli Storage Manager (TSM) server and explores
Enforcive / Enterprise Security
 TM Enforcive / Enterprise Security End to End Security and Compliance Management for the IBM i Enterprise Enforcive / Enterprise Security is the single most comprehensive and easy to use security and compliance
TM Enforcive / Enterprise Security End to End Security and Compliance Management for the IBM i Enterprise Enforcive / Enterprise Security is the single most comprehensive and easy to use security and compliance
Niara Security Analytics. Overview. Automatically detect attacks on the inside using machine learning
 Niara Security Analytics Automatically detect attacks on the inside using machine learning Automatically detect attacks on the inside Supercharge analysts capabilities Enhance existing security investments
Niara Security Analytics Automatically detect attacks on the inside using machine learning Automatically detect attacks on the inside Supercharge analysts capabilities Enhance existing security investments
NETWRIX EVENT LOG MANAGER
 NETWRIX EVENT LOG MANAGER ADMINISTRATOR S GUIDE Product Version: 4.0 July/2012. Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment
NETWRIX EVENT LOG MANAGER ADMINISTRATOR S GUIDE Product Version: 4.0 July/2012. Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment
場 次 :C-3 公 司 名 稱 :RSA, The Security Division of EMC 主 題 : 如 何 應 用 網 路 封 包 分 析 對 付 資 安 威 脅 主 講 人 :Jerry.Huang@rsa.com Sr. Technology Consultant GCR
 場 次 :C-3 公 司 名 稱 :RSA, The Security Division of EMC 主 題 : 如 何 應 用 網 路 封 包 分 析 對 付 資 安 威 脅 主 講 人 :Jerry.Huang@rsa.com Sr. Technology Consultant GCR Minimum Requirements of Security Management and Compliance
場 次 :C-3 公 司 名 稱 :RSA, The Security Division of EMC 主 題 : 如 何 應 用 網 路 封 包 分 析 對 付 資 安 威 脅 主 講 人 :Jerry.Huang@rsa.com Sr. Technology Consultant GCR Minimum Requirements of Security Management and Compliance
IBM Software InfoSphere Guardium. Planning a data security and auditing deployment for Hadoop
 Planning a data security and auditing deployment for Hadoop 2 1 2 3 4 5 6 Introduction Architecture Plan Implement Operationalize Conclusion Key requirements for detecting data breaches and addressing
Planning a data security and auditing deployment for Hadoop 2 1 2 3 4 5 6 Introduction Architecture Plan Implement Operationalize Conclusion Key requirements for detecting data breaches and addressing
Cyber Security Services: Data Loss Prevention Monitoring Overview
 WHITE PAPER: DLP MONITORING OVERVIEW........................................ Cyber Security Services: Data Loss Prevention Monitoring Overview Who should read this paper Customers who are interested in
WHITE PAPER: DLP MONITORING OVERVIEW........................................ Cyber Security Services: Data Loss Prevention Monitoring Overview Who should read this paper Customers who are interested in
Boosting enterprise security with integrated log management
 IBM Software Thought Leadership White Paper May 2013 Boosting enterprise security with integrated log management Reduce security risks and improve compliance across diverse IT environments 2 Boosting enterprise
IBM Software Thought Leadership White Paper May 2013 Boosting enterprise security with integrated log management Reduce security risks and improve compliance across diverse IT environments 2 Boosting enterprise
Extreme Networks: A SOLUTION WHITE PAPER
 Extreme Networks: The Purview Solution Integration with SIEM Integrating Application Management and Business Analytics into other IT management systems A SOLUTION WHITE PAPER WHITE PAPER Introduction Purview
Extreme Networks: The Purview Solution Integration with SIEM Integrating Application Management and Business Analytics into other IT management systems A SOLUTION WHITE PAPER WHITE PAPER Introduction Purview
User Guidance. CimTrak Integrity & Compliance Suite 2.0.6.19
 CimTrak Integrity & Compliance Suite 2.0.6.19 Master Repository Management Console File System Agent Network Device Agent Command Line Utility Ping Utility Proxy Utility FTP Repository Interface User Guidance
CimTrak Integrity & Compliance Suite 2.0.6.19 Master Repository Management Console File System Agent Network Device Agent Command Line Utility Ping Utility Proxy Utility FTP Repository Interface User Guidance
Take the Red Pill: Becoming One with Your Computing Environment using Security Intelligence
 Take the Red Pill: Becoming One with Your Computing Environment using Security Intelligence Chris Poulin Security Strategist, IBM Reboot Privacy & Security Conference 2013 1 2012 IBM Corporation Securing
Take the Red Pill: Becoming One with Your Computing Environment using Security Intelligence Chris Poulin Security Strategist, IBM Reboot Privacy & Security Conference 2013 1 2012 IBM Corporation Securing
Rational Reporting. Module 3: IBM Rational Insight and IBM Cognos Data Manager
 Rational Reporting Module 3: IBM Rational Insight and IBM Cognos Data Manager 1 Copyright IBM Corporation 2012 What s next? Module 1: RRDI and IBM Rational Insight Introduction Module 2: IBM Rational Insight
Rational Reporting Module 3: IBM Rational Insight and IBM Cognos Data Manager 1 Copyright IBM Corporation 2012 What s next? Module 1: RRDI and IBM Rational Insight Introduction Module 2: IBM Rational Insight
My AutoSupport. User Guide. October 2013
 System User Guide My AutoSupport October 2013 NetApp AutoSupport is an integrated, efficient monitoring and reporting technology that checks the health of your AutoSupport enabled NetApp systems on a continual
System User Guide My AutoSupport October 2013 NetApp AutoSupport is an integrated, efficient monitoring and reporting technology that checks the health of your AutoSupport enabled NetApp systems on a continual
LANDesk Data Analytics
 LANDesk White Paper LANDesk Data Analytics An innovative, comprehensive approach to managing software and hardware assets Visit www.landesk.com for more information. To the maximum extent permitted under
LANDesk White Paper LANDesk Data Analytics An innovative, comprehensive approach to managing software and hardware assets Visit www.landesk.com for more information. To the maximum extent permitted under
LANDesk Service Desk Certified in All 15 ITIL. v3 Suitability Requirements. LANDesk demonstrates capabilities for all PinkVERIFY 3.
 LANDesk Service Desk LANDesk Service Desk Certified in All 15 ITIL v3 Suitability Requirements PinkVERIFY is an objective software tool assessment service that validates toolsets that meet a set of functional
LANDesk Service Desk LANDesk Service Desk Certified in All 15 ITIL v3 Suitability Requirements PinkVERIFY is an objective software tool assessment service that validates toolsets that meet a set of functional
Symantec Security Information Manager 4.5 Administrator's Guide
 Symantec Security Information Manager 4.5 Administrator's Guide Symantec Security Information Manager 4.5 Administrator's Guide The software described in this book is furnished under a license agreement
Symantec Security Information Manager 4.5 Administrator's Guide Symantec Security Information Manager 4.5 Administrator's Guide The software described in this book is furnished under a license agreement
Extreme Networks Security Analytics G2 Risk Manager
 DATA SHEET Extreme Networks Security Analytics G2 Risk Manager Proactively manage vulnerabilities and network device configuration to reduce risk, improve compliance HIGHLIGHTS Visualize current and potential
DATA SHEET Extreme Networks Security Analytics G2 Risk Manager Proactively manage vulnerabilities and network device configuration to reduce risk, improve compliance HIGHLIGHTS Visualize current and potential
Advanced Visibility. Moving Beyond a Log Centric View. Matthew Gardiner, RSA & Richard Nichols, RSA
 Advanced Visibility Moving Beyond a Log Centric View Matthew Gardiner, RSA & Richard Nichols, RSA 1 Security is getting measurability worse Percent of breaches where time to compromise (red)/time to Discovery
Advanced Visibility Moving Beyond a Log Centric View Matthew Gardiner, RSA & Richard Nichols, RSA 1 Security is getting measurability worse Percent of breaches where time to compromise (red)/time to Discovery
Enabling Security Operations with RSA envision. August, 2009
 Enabling Security Operations with RSA envision August, 2009 Agenda What is security operations? How does RSA envision help with security operations? How does RSA envision fit with other EMC products? If
Enabling Security Operations with RSA envision August, 2009 Agenda What is security operations? How does RSA envision help with security operations? How does RSA envision fit with other EMC products? If
Paper 064-2014. Robert Bonham, Gregory A. Smith, SAS Institute Inc., Cary NC
 Paper 064-2014 Log entries, Events, Performance Measures, and SLAs: Understanding and Managing your SAS Deployment by Leveraging the SAS Environment Manager Data Mart ABSTRACT Robert Bonham, Gregory A.
Paper 064-2014 Log entries, Events, Performance Measures, and SLAs: Understanding and Managing your SAS Deployment by Leveraging the SAS Environment Manager Data Mart ABSTRACT Robert Bonham, Gregory A.
The SIEM Evaluator s Guide
 Using SIEM for Compliance, Threat Management, & Incident Response Security information and event management (SIEM) tools are designed to collect, store, analyze, and report on log data for threat detection,
Using SIEM for Compliance, Threat Management, & Incident Response Security information and event management (SIEM) tools are designed to collect, store, analyze, and report on log data for threat detection,
