HOME COMPUTER SECURITY AWARENESS
|
|
|
- Abner Kelley
- 8 years ago
- Views:
Transcription
1 HOME COMPUTER SECURITY AWARENESS Sponsoring faculty: Dr Rose Shumba Students: Melissa A Karolewski, Alicia Coon, Sara Raffensperger, Louisa Ehinlaiye Ometere Computer Science Department Indiana University of Pennsylvania Shumba@iup.edu, M.A.Karolewski@iup.edu, A.A.Coon@iup.edu, hjrl@iup.edu, tmtj@iup.edu ABSTRACT Home computer security is often a neglected area of security. In the Fall of 2004, with funding from the ACM CREU (Collaborative Research Experience for Undergraduates in Science and Engineering) program, a project on home computer security was started. The goal of the project was to enhance the public s understanding and acceptance of information security issues through awareness and education. The project consisted of three phases: the identification of currently used practices for computer security, an evaluation of the practices and then a public 1 awareness and education outreach program on the importance and relevance of computer security. Through a questionnaire survey, currently used practices for home security were collected and analyzed. The target population was the IUP student community. During the identification phase, a questionnaire was administered to random IUP classes. From the results of the survey, a list of the best of breed security tools were identified and reviewed. During the last phase, the research was presented to three groups of high school students during the 2005 Natural Science s Science Festival. KEY WORDS Computer Security, Home Computer, Survey Results. 1. Introduction The general public is often isolated from awareness and training opportunities in information security, yet the security of the cyberspace rests on the security of all its components. Although there is a reasonable number of websites with tips on protecting home computers [16, 18], these often have some technical vocabulary or are not known by the public, hence are seldom visited. Many computer owners don t realize the need to pay attention to computer security. No matter how a computer is connected to the Internet, intruders attacks are 1 The public in this case is the IUP community. often successful. Security issues for home users are just as real as security for business users, perhaps more so because home users don't have enough resources to ensure proper security. In the Fall of 2004, with sponsorship from the ACM CREU program, a research project on home computer security was started. The goal of the project was to enhance the public s understanding and acceptance of information security issues through awareness and education. The project consisted of the following three phases: 1. The identification of currently used practices for computer security. 2. An evaluation of practices identified in 1 above, and 3. Public awareness and education on the importance, and practices for home security. This paper is based on phase 1 of the project; the identification of currently used practices for computer security. In order to identify the commonly used practices and tools for computer security, a questionnaire survey research was carried out at IUP in the Fall of This paper describes the methodology, findings from the questionnaire survey research, and the future work on the project. 2. Methodology As stated in the introduction, the project was divided into three phases. The first phase of the project was completed in March A questionnaire survey was administered to the 350 multi-disciplinary IUP students. The aim of the survey was to capture as much data on current practices for computer security. The questionnaire was based on techniques to secure a home computer as given by the CERT Coordination Center [16], and the United States Home computer Emergency Readiness Team [17]. The techniques include good password management, security, use of anti-virus
2 and anti-spyware software, use of firewalls, care in installing programs, use of encryption, backing up of files, care in sharing files, and securing wireless networks. Students from all disciplines participated. Target classes were picked at random. Questionnaires were administered at the start of a targeted class session. The questionnaire had 24 questions which included multiple choice, numeric open end and text open end. A sample of the questionnaire is attached. Participants were given 15 minutes to complete the questionnaire. 2. Analysis of Collected Data The collected data was input analyzed using Excel. The following paragraphs provide an analysis of the data. 78% of the participants understood the difference between anti-virus and anti-spyware programs. MacAfee, with a 47% usage rate, was the most commonly used anti-virus programs, followed by Norton with 34%. The rest of the participants used nothing or other software not listed. Of the participants who used anti-virus programs, 27% claimed updated program(s) on a weekly basis, 14% updated program(s) on a daily basis and 20% updated program(s) on a monthly basis. The rest of the participants (39%) did not know if they updated, didn t know how to update, or never updated. Ad-ware and Spyware-Eliminator are the most popular, with usages rates of 50% and 17% respectively. 12% of the participants used other various programs. 21% of the participants either had no anti-spyware or were unaware if they had any anti-spyware program. Of those who used anti-spyware software, 30% updated programs weekly, 19% updated daily and 51% either never updated or didn t know how to do the update. The most popular firewall was Microsoft (windows) Firewall at 23% usage. The followed by McAfee Personal Firewall at 21%, then ZoneAlarm at 11%. The majority of the participants did not know if they had a firewall or not. Survey data shows that 71% of the participants did not use the same passwords for different logins. 51% did not use unique 2 passwords. 33% of the participants never changed passwords and 40% only changed when necessary. 5% changed passwords 9-12 times/year, 3% changed passwords 5-8 times/year, and 19% changed passwords 1-4 times/year. 74% of the participants remembered passwords without writing them down. 22% used passwords that had something to do with them, i.e. child s name, type of car, an interest, etc. These were easy to remember. The rest of the participants did not remember their passwords, and hence had to write them down. 70% of the participants shared the use of home computer with others. Of the 70%, 44% shared with 1-2 other users, 47% shared with 3-4 other users, and 9% shared with 5-8 other users. Of those who shared computers, 58% restricted access to certain files, the rest did not. 31% used a file-sharing, 12% were unsure, and 57% did not. 58% of the participants had a wireless network in their home. Of those with a wireless network, only 8% had the network secured. 38% of the participants had encryption software. The rest either did not have it or did not know if they had it. Of those with encryption software, only 6% encrypted their files and s. 51% of the participants took time to learn much about programs before installing. Only 32% purchased program, 48% got programs from a national chain, and 20% obtained programs from elsewhere. 45% of participants always scanned attachments. Of the 45%, only 9% always scanned, and 11% scanned sometimes. The rest scanned when they felt like. When attachments came from friends, 5% always scanned, 20% almost always, 20% scan sometimes, and 55% never scanned. 26% of the participants backed up files once a month, only 6% backed up everyday, and 8% backed up monthly. The remaining 60% either didn t know how to back up or never bothered. Patches for the OS was either downloaded manually for those with knowledge about it, and for others the OS automatically updated itself. 2 A unique password is a combination of letters, numbers and/or punctuation marks.
3 These patches were downloaded weekly, monthly and yearly; even though some did state that they had no idea if patches were downloaded or not. 16% of the participants updated patches with 21% doing it automatically. 3. Conclusion & Future Work From the results of the survey, there is no doubt need to bring home computer security awareness to the public. The researchers organized a number of computer security awareness seminars for the IUP community. The researchers presented their presentation to high school students during the 2005 IUP Natural Science Festival. These seminars stressed the importance of an anti-virus and anti-spyware program on a computer, difference between anti-virus program(s) and anti-spyware program(s) functionalities, importance of updating computer security software, ways of restricting access to personal files, how to secure a wireless network, the need to read learn as much about a program before installation, the necessity of scanning all attachments, regardless of who send the , importance of backing up important files and folders, importance of good password management and the importance of having a firewall on a home computer minguide/securityadminguide-4.html /host_security.htm Garfinkel, S. Spafford, G, Schwartz, A; Practical Unix and Internet Security; O Reilly; Third edition; omputersecurity/ p References: 1. c.htm#ssneeded _97_winter/Topics/quest-design/ works.html myhomepage ness/hack221.shtml technology/tech_paper /host_security-1.html
4 Questionnaire We are carrying out a research on what practices you are using to secure your home computer. Please answer the following question about you home computer. 1. Do you understand the difference between Anti-Virus Programs and Anti-spyware programs? Yes No 2. What Anti-Virus Program do you use? a. McAfee Anti-Virus b. Microsoft (Windows) Anti-Virus c. Norton Anti-Virus d. Linux Anti-Virus e. Mac Anti-Virus f. Other g. Don t know h. Don t have Anti-Virus If you do not use anti-virus software, why don t you? a. I don t use the internet. b. I don t understand anti-virus software. c. Other: 3. How often do you update your Anti-Virus software? a. Daily b. Weekly c. Monthly d. Never e. Don t know f. Don t know how 4. Do you use an Anti-Spyware Program? a. Ad-aware b. Spy Killer c. XoftSpy d. Spyware Eliminator d. None f. Don t know g. Other 5. How often do you run the Anti-spyware? a. Daily b. Weekly c. Monthly d. Never e. Don t know f. Don t know how 6. How often do you update your Anti-spyware program? a. Daily b. Weekly c. Monthly d. Never e. Don t know f. Don t know how 7. What kind of firewall is installed on your computer? a. McAfee Personal Firewall b. Zone Alarm Firewall c. Microsoft (Windows) Firewall d. Norton Firewall from Symantec e. Linux Firewall / Linux Network Firewalls f. Apple Quicktime Firewall g. Don t know h. Don t have Firewall i. Other 8. Do you use the passwords over and over again for different logins? (e.g. Programs, network login, .) Yes No 9. Do you use unique passwords? (i.e. a combination of letters, numbers or punctuation marks) Yes No Sometimes 10. How often do you change your passwords? a. 1-4 times/year b. 5-8 times/year c times/year d. never e. Only when I must
5 11. Do you remember the passwords that you create? a. Yes b. Yes, because they are something that is about me, i.e. child s name, spouse s name, type of car you drive, an interest, etc. c. No, but I have them written down. d. No, I can never remember them. 12 Are you the only user of your home computer? Yes No If No, how many other people use it with you? Have you limited access of certain files and folders to certain users? Yes No Don t know 13. Do you use file sharing networks? Yes No Don t know 14 Do you have an Encryption software on your home computer? Yes No Don t know If yes, what kind is it? 15 How often do you update your Encryption software? a. Never/Don t know/don t have Encryption software b. Every night c. Once a week d. Three or more times in a month e. Every other month 16 Do you encrypt your important files and folders? Yes No 17 Before you buy and install a program to your home computer, do you learn as much about the program as you can? Yes No 18 When you buy a program where do you mainly purchase them from? a. A local store b. A national chain c. Other 19. Do you scan attachments from unknown sources? a. always b. almost always c. sometimes d. almost never e. never f. Don t know 20. Do you scan attachments from known sources? (such as friends and family) a. always b. almost always c. sometimes d. almost never e. never f. Don t know 21. How often do you backup important files on your home computer? a. Once a month b. Every week c. Every day d. Never/don t know 22. How often do you update/download patches for you operating system?
6 a. Weekly b. Monthly c. Yearly d. The OS automatically updates itself e. Never/Don t know 23. Do you have a wireless network in your home? Yes No Don t Know 24. If yes, is it secured? Yes No Don t Know
Netsafe/ AVG New Zealand. NetSafe/ AVG New Zealand. Cyber Security Research. Cyber Security Research. Supplementary Tables. March 2011.
 NetSafe/ AVG New Zealand Contents Page 1. Objectives and Methodology 3 2. Summary and Conclusions 6 3. Main Findings 8 Online security a serious issue 9 Concern about online challenges 11 Most important
NetSafe/ AVG New Zealand Contents Page 1. Objectives and Methodology 3 2. Summary and Conclusions 6 3. Main Findings 8 Online security a serious issue 9 Concern about online challenges 11 Most important
Paul Nguyen. 2014 CSG Interna0onal
 Paul Nguyen 2014 CSG Interna0onal Security is Top- of- Mind Everywhere High- profile breaches: 2K+ breaches expose nearly 1B records in 2013 Increased regulatory pressure State- sponsored hacking around
Paul Nguyen 2014 CSG Interna0onal Security is Top- of- Mind Everywhere High- profile breaches: 2K+ breaches expose nearly 1B records in 2013 Increased regulatory pressure State- sponsored hacking around
Bookmarks for Desktop Self-Defense
 Basic Security Tips Bookmarks for Desktop Self-Defense Get Safe Online http://www.getsafeonline.org/ Get Safe Online will help you protect yourself against Internet threats. The site is sponsored by government
Basic Security Tips Bookmarks for Desktop Self-Defense Get Safe Online http://www.getsafeonline.org/ Get Safe Online will help you protect yourself against Internet threats. The site is sponsored by government
Remote Desktop Part II. AHS Computing
 Remote Desktop Part II AHS Computing Overview How to become connected at home How to be secure when connecting from home Hazards of home computing How to work from home Troubleshooting issues from home
Remote Desktop Part II AHS Computing Overview How to become connected at home How to be secure when connecting from home Hazards of home computing How to work from home Troubleshooting issues from home
Computer Security Basics For UW-Madison Emeritus Faculty and Staff Oakwood Village University Woods September 17, 2014
 Computer Security Basics For UW-Madison Emeritus Faculty and Staff Oakwood Village University Woods September 17, 2014 Presented by Nicholas Davis, CISA, CISSP UW-Madison, Division of Information Technology
Computer Security Basics For UW-Madison Emeritus Faculty and Staff Oakwood Village University Woods September 17, 2014 Presented by Nicholas Davis, CISA, CISSP UW-Madison, Division of Information Technology
Essentials of PC Security: Central Library Tech Center Evansville Vanderburgh Public Library
 Essentials of PC Security: Central Library Tech Center Evansville Vanderburgh Public Library Why should you be concerned? There are over 1 million known computer viruses. An unprotected computer on the
Essentials of PC Security: Central Library Tech Center Evansville Vanderburgh Public Library Why should you be concerned? There are over 1 million known computer viruses. An unprotected computer on the
Firewall Access Request Form
 SECTION 1 TO BE COMPLETED BY THE APPLICANT By completing the below information the requestor/applicant acknowledges and agrees that he/she has read, understood and will comply with the following: CHECK
SECTION 1 TO BE COMPLETED BY THE APPLICANT By completing the below information the requestor/applicant acknowledges and agrees that he/she has read, understood and will comply with the following: CHECK
Spam, Spyware, Malware and You! Don't give up just yet! Presented by: Mervin Istace Provincial Library Saskatchewan Learning
 Spam, Spyware, Malware and You! Don't give up just yet! Presented by: Mervin Istace Provincial Library Saskatchewan Learning Lee Zelyck Network Administrator Regina Public Library Malware, Spyware, Trojans
Spam, Spyware, Malware and You! Don't give up just yet! Presented by: Mervin Istace Provincial Library Saskatchewan Learning Lee Zelyck Network Administrator Regina Public Library Malware, Spyware, Trojans
Welcome To The L.R.F.H.S. Computer Group Wednesday 27 th November 2013
 Welcome To The L.R.F.H.S. Computer Group Wednesday 27 th November 2013 BACKUP SECURITY AND THE CLOUD BACK UP ALWAYS BACK UP TO AN EXTERNAL DEVICE OR REMOVAL MEDIA- NEVER DIRECTLY ON TO YOUR COMPUTER IF
Welcome To The L.R.F.H.S. Computer Group Wednesday 27 th November 2013 BACKUP SECURITY AND THE CLOUD BACK UP ALWAYS BACK UP TO AN EXTERNAL DEVICE OR REMOVAL MEDIA- NEVER DIRECTLY ON TO YOUR COMPUTER IF
Introduction to Computing @ WSU
 Introduction to Computing @ WSU Table of Contents 1 - Information Technology (IT) Security... 2 Information to Remember... 2 2 - Malware... 2 Information to Remember... 3 3 - Firewalls... 3 Information
Introduction to Computing @ WSU Table of Contents 1 - Information Technology (IT) Security... 2 Information to Remember... 2 2 - Malware... 2 Information to Remember... 3 3 - Firewalls... 3 Information
2011 NATIONAL SMALL BUSINESS STUDY
 2011 NATIONAL SMALL BUSINESS STUDY The National Cyber Security Alliance has conducted a new study with Symantec to analyze cyber security practices, behaviors and perceptions of small businesses throughout
2011 NATIONAL SMALL BUSINESS STUDY The National Cyber Security Alliance has conducted a new study with Symantec to analyze cyber security practices, behaviors and perceptions of small businesses throughout
CYBER-SAFETY BASICS. A computer security tutorial for UC Davis students, faculty and staff
 CYBER-SAFETY BASICS A computer security tutorial for UC Davis students, faculty and staff INTRODUCTION This tutorial provides some basic information and practical suggestions for protecting your personal
CYBER-SAFETY BASICS A computer security tutorial for UC Davis students, faculty and staff INTRODUCTION This tutorial provides some basic information and practical suggestions for protecting your personal
Securing Your Windows Laptop
 Securing Your Windows Laptop Arindam Mandal (arindam.mandal@paladion.net) Paladion Networks (http://www.paladion.net) May 2004 Now-a-days laptops are part of our life. We carry laptops almost everywhere
Securing Your Windows Laptop Arindam Mandal (arindam.mandal@paladion.net) Paladion Networks (http://www.paladion.net) May 2004 Now-a-days laptops are part of our life. We carry laptops almost everywhere
Computer Security Maintenance Information and Self-Check Activities
 Computer Security Maintenance Information and Self-Check Activities Overview Unlike what many people think, computers are not designed to be maintenance free. Just like cars they need routine maintenance.
Computer Security Maintenance Information and Self-Check Activities Overview Unlike what many people think, computers are not designed to be maintenance free. Just like cars they need routine maintenance.
Computer and Information Security End User Questionnaire
 Computer and Information Security End User Questionnaire Human Factors Issues in Computer and Information Security Funded by the National Science Foundation: EIA-0120092 Project http://cis.engr.wisc.edu/
Computer and Information Security End User Questionnaire Human Factors Issues in Computer and Information Security Funded by the National Science Foundation: EIA-0120092 Project http://cis.engr.wisc.edu/
INFORMATION SECURITY BASICS. A computer security tutorial for Holyoke Community College
 INFORMATION SECURITY BASICS A computer security tutorial for Holyoke Community College I NTRODUCTION This tutorial provides some basic information and practical suggestions for protecting your personal
INFORMATION SECURITY BASICS A computer security tutorial for Holyoke Community College I NTRODUCTION This tutorial provides some basic information and practical suggestions for protecting your personal
STRONGER ONLINE SECURITY
 STRONGER ONLINE SECURITY Enhanced online banking without compromise Manage your business banking efficiently and securely Internet banking has given business leaders and treasurers greater control of financial
STRONGER ONLINE SECURITY Enhanced online banking without compromise Manage your business banking efficiently and securely Internet banking has given business leaders and treasurers greater control of financial
Safe Practices for Online Banking
 November 2012 Follow these guidelines to help protect your information while banking online. At First Entertainment Credit Union, our goal is to provide you with the best all around banking experience.
November 2012 Follow these guidelines to help protect your information while banking online. At First Entertainment Credit Union, our goal is to provide you with the best all around banking experience.
Accessing the SUNYIT wireless network for the first time
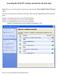 Accessing the SUNYIT wireless network for the first time Right click on your wireless network connection icon and select the View Available Wireless Networks option You may see several networks within
Accessing the SUNYIT wireless network for the first time Right click on your wireless network connection icon and select the View Available Wireless Networks option You may see several networks within
Basic Computer Maintenance
 Basic Computer Maintenance Presented by East Central Regional Library The Institute of, a Federal Agency that fosters innovation, leadership and a lifetime of learning, in conjunction with State Library
Basic Computer Maintenance Presented by East Central Regional Library The Institute of, a Federal Agency that fosters innovation, leadership and a lifetime of learning, in conjunction with State Library
Laura Royer, Extension Faculty, University of Florida/IFAS Osceola County Extension Services
 Consumer Choices: Computer Security Software Prepared by: Dave Palmer, Instructional Media Faculty, University of Florida/IFAS Extension, South Central Extension District Laura Royer, Extension Faculty,
Consumer Choices: Computer Security Software Prepared by: Dave Palmer, Instructional Media Faculty, University of Florida/IFAS Extension, South Central Extension District Laura Royer, Extension Faculty,
Chapter 7A. Functions of Operating Systems. Types of Operating Systems. Operating System Basics
 Chapter 7A Operating System Basics Functions of Operating Provide a user interface Run programs Manage hardware devices Organized file storage 2 Types of Operating Real-time operating system Very fast
Chapter 7A Operating System Basics Functions of Operating Provide a user interface Run programs Manage hardware devices Organized file storage 2 Types of Operating Real-time operating system Very fast
Secondly, if your device is running a Microsoft Windows or Macintosh OS X operating system you will also need to:
 What is Safe Connect and why is it being used? Safe Connect is part of TAMUK's effort to help keep computers on its network as free as possible from viruses, spyware, and operating system security holes.
What is Safe Connect and why is it being used? Safe Connect is part of TAMUK's effort to help keep computers on its network as free as possible from viruses, spyware, and operating system security holes.
Preparing Your Personal Computer to Connect to the VPN
 Preparing Your Personal Computer to Connect to the VPN (Protecting Your Personal Computer Running Windows) Using the VPN to connect your computer to the campus network is the same as bringing your computer
Preparing Your Personal Computer to Connect to the VPN (Protecting Your Personal Computer Running Windows) Using the VPN to connect your computer to the campus network is the same as bringing your computer
Certified Secure Computer User
 Certified Secure Computer User Exam Info Exam Name CSCU (112-12) Exam Credit Towards Certification Certified Secure Computer User (CSCU). Students need to pass the online EC-Council exam to receive the
Certified Secure Computer User Exam Info Exam Name CSCU (112-12) Exam Credit Towards Certification Certified Secure Computer User (CSCU). Students need to pass the online EC-Council exam to receive the
PDQ Guide for the PCI Data Security Standard Self-Assessment Questionnaire C (Version 1.1)
 PDQ has created an Answer Guide for the Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire C to help wash operators complete questionnaires. Part of the Access Customer Management
PDQ has created an Answer Guide for the Payment Card Industry (PCI) Data Security Standard Self-Assessment Questionnaire C to help wash operators complete questionnaires. Part of the Access Customer Management
CYBER-SAFETY. A computer security tutorial for UC Davis students, faculty and staff
 CYBER-SAFETY BASICS A computer security tutorial for UC Davis students, faculty and staff I N T R O D U C T I O N This tutorial provides some basic information and practical suggestions for protecting
CYBER-SAFETY BASICS A computer security tutorial for UC Davis students, faculty and staff I N T R O D U C T I O N This tutorial provides some basic information and practical suggestions for protecting
How to Install Windows 7 software
 Connecting Windows 7 to the network This document outlines the procedure for setting up Windows 7 to use the College and University network. It assumes that the computer is set up and working correctly
Connecting Windows 7 to the network This document outlines the procedure for setting up Windows 7 to use the College and University network. It assumes that the computer is set up and working correctly
How To Understand What A Virus Is And How To Protect Yourself From A Virus
 Viruses, Trojans and Worms Oh My! 2006 Technology Leadership Presentation Series Why is my computer running so slow? What are all of these little windows popping up on my system? Why did my home page change?
Viruses, Trojans and Worms Oh My! 2006 Technology Leadership Presentation Series Why is my computer running so slow? What are all of these little windows popping up on my system? Why did my home page change?
Reliance Bank Fraud Prevention Best Practices
 Reliance Bank Fraud Prevention Best Practices May 2013 User ID and Password Guidelines Create a strong password with at least 8 characters that includes a combination of mixed case letters and numbers.
Reliance Bank Fraud Prevention Best Practices May 2013 User ID and Password Guidelines Create a strong password with at least 8 characters that includes a combination of mixed case letters and numbers.
by New Media Solutions 37 Walnut Street Wellesley, MA 02481 p 781-235-0128 f 781-235-9408 www.avitage.com Avitage IT Infrastructure Security Document
 Avitage IT Infrastructure Security Document The purpose of this document is to detail the IT infrastructure security policies that are in place for the software and services that are hosted by Avitage.
Avitage IT Infrastructure Security Document The purpose of this document is to detail the IT infrastructure security policies that are in place for the software and services that are hosted by Avitage.
General Questions... 1. Requesting Access... 2. Client Support... 3. Downloading Issues... 4. Installation Issues... 4. Connectivity Issues...
 Contents General Questions... 1 Requesting Access... 2 Client Support... 3 Downloading Issues... 4 Installation Issues... 4 Connectivity Issues... 5 Performance Issues... 7 Application Issues... 8 General
Contents General Questions... 1 Requesting Access... 2 Client Support... 3 Downloading Issues... 4 Installation Issues... 4 Connectivity Issues... 5 Performance Issues... 7 Application Issues... 8 General
1. Scope of Service. 1.1 About Boxcryptor Classic
 Manual for Mac OS X Content 1. Scope of Service... 3 1.1 About Boxcryptor Classic... 3 1.2 About this manual... 4 2. Installation... 5 2.1 Installing Boxcryptor Classic... 5 2.2 Licensing Boxcryptor Classic
Manual for Mac OS X Content 1. Scope of Service... 3 1.1 About Boxcryptor Classic... 3 1.2 About this manual... 4 2. Installation... 5 2.1 Installing Boxcryptor Classic... 5 2.2 Licensing Boxcryptor Classic
Optimize your computer for peak performance
 Optimize your computer for peak performance Our personal computers are like fine automobiles they need preventive maintenance to run efficiently and avoid major breakdowns. The following tips can help
Optimize your computer for peak performance Our personal computers are like fine automobiles they need preventive maintenance to run efficiently and avoid major breakdowns. The following tips can help
Information Security. Louis Morgan, CISSP Information Security Officer
 Information Security By Louis Morgan, CISSP Information Security Officer Why Bother with IT Security? Recent estimate - 900 million personal computers worldwide. Computer hackers are out there. How long
Information Security By Louis Morgan, CISSP Information Security Officer Why Bother with IT Security? Recent estimate - 900 million personal computers worldwide. Computer hackers are out there. How long
Online Banking Fraud Prevention Recommendations and Best Practices
 Online Banking Fraud Prevention Recommendations and Best Practices This document provides you with fraud prevention best practices that every employee at Continental National Bank of Miami needs to know
Online Banking Fraud Prevention Recommendations and Best Practices This document provides you with fraud prevention best practices that every employee at Continental National Bank of Miami needs to know
Cyber Security: Software Security and Hard Drive Encryption
 Links in this document have been set for a desktop computer with the resolution set to 1920 x 1080 pixels. Cyber Security: Software Security and Hard Drive Encryption 301-1497, Rev A September 2012 Copyright
Links in this document have been set for a desktop computer with the resolution set to 1920 x 1080 pixels. Cyber Security: Software Security and Hard Drive Encryption 301-1497, Rev A September 2012 Copyright
Welcome to Part 2 of the online course, Spyware and Adware What s in Your Computer?
 Welcome to Part 2 of the online course, Spyware and Adware What s in Your Computer? 1 2 This is the second part of a two-part course on spyware and adware. In this portion of the course we will: Review
Welcome to Part 2 of the online course, Spyware and Adware What s in Your Computer? 1 2 This is the second part of a two-part course on spyware and adware. In this portion of the course we will: Review
Certified Secure Computer User
 Certified Secure Computer User Course Outline Module 01: Foundations of Security Essential Terminologies Computer Security Why Security? Potential Losses Due to Security Attacks Elements of Security The
Certified Secure Computer User Course Outline Module 01: Foundations of Security Essential Terminologies Computer Security Why Security? Potential Losses Due to Security Attacks Elements of Security The
Why you need. McAfee. Multi Acess PARTNER SERVICES
 Why you need McAfee Multi Acess PARTNER SERVICES McAfee Multi Access is an online security app that protects all types of devices. All at once. The simple monthly subscription covers up to five devices
Why you need McAfee Multi Acess PARTNER SERVICES McAfee Multi Access is an online security app that protects all types of devices. All at once. The simple monthly subscription covers up to five devices
BCS IT User Syllabus IT Security for Users Level 2. Version 1.0
 BCS IT User Syllabus IT for Users Level 2 Version 1.0 June 2009 ITS2.1 System Performance ITS2.1.1 Unwanted messages ITS2.1.2 Malicious ITS2.1.1.1 ITS2.1.1.2 ITS2.1.2.1 ITS2.1.2.2 ITS2.1.2.3 ITS2.1.2.4
BCS IT User Syllabus IT for Users Level 2 Version 1.0 June 2009 ITS2.1 System Performance ITS2.1.1 Unwanted messages ITS2.1.2 Malicious ITS2.1.1.1 ITS2.1.1.2 ITS2.1.2.1 ITS2.1.2.2 ITS2.1.2.3 ITS2.1.2.4
Citrix : Remediation - MAC
 Citrix : Remediation - MAC Key Points: 1. 2. 3. 4. 5. 6. 7. Understanding End Point Scan Analysis Supported anti-virus and firewall products Configuring AVAST/SOPHOS and the Mac OS X Firewall Installing
Citrix : Remediation - MAC Key Points: 1. 2. 3. 4. 5. 6. 7. Understanding End Point Scan Analysis Supported anti-virus and firewall products Configuring AVAST/SOPHOS and the Mac OS X Firewall Installing
Galveston College Wireless Network Users Setup Guide Version 1.0
 Galveston College Wireless Network Users Setup Guide Version 1.0 TABLE OF CONTENT 1 DOCUMENT CONTROL RECORD... 3 2 ISSUE AND AMENDMENT RECORD... 3 3 GENERAL... 3 3.1 INTRODUCTION...3 3.2 OBJECTIVE... 3
Galveston College Wireless Network Users Setup Guide Version 1.0 TABLE OF CONTENT 1 DOCUMENT CONTROL RECORD... 3 2 ISSUE AND AMENDMENT RECORD... 3 3 GENERAL... 3 3.1 INTRODUCTION...3 3.2 OBJECTIVE... 3
Manually Add Programs to Your Firewall or Anti-Virus Programs Trusted List. ZoneAlarm
 Manually Add Programs to Your Firewall or Anti-Virus Programs Trusted List ZoneAlarm AVG Open the AVG Anti-Virus plus Firewall. Double-click the Firewall button to configure the Firewall. Add the programs
Manually Add Programs to Your Firewall or Anti-Virus Programs Trusted List ZoneAlarm AVG Open the AVG Anti-Virus plus Firewall. Double-click the Firewall button to configure the Firewall. Add the programs
Version 5 - July 2015 IT Services Page 2
 Version 5 - July 2015 IT Services Page 2 Contents 1. Introduction 4 2. Initial connection 5 3. Network Registration 6 4. Network registration: Scanning your computer (network remediation) 8 5. System check
Version 5 - July 2015 IT Services Page 2 Contents 1. Introduction 4 2. Initial connection 5 3. Network Registration 6 4. Network registration: Scanning your computer (network remediation) 8 5. System check
Survey on the Internet Security Awareness
 Survey on the Internet Security Awareness Implementation date: March 2009 *This survey was conducted as part of Academic Frontier Project for Private Universities funded by MEXT(Ministry of Education,
Survey on the Internet Security Awareness Implementation date: March 2009 *This survey was conducted as part of Academic Frontier Project for Private Universities funded by MEXT(Ministry of Education,
Business Internet Banking / Cash Management Fraud Prevention Best Practices
 Business Internet Banking / Cash Management Fraud Prevention Best Practices This document provides fraud prevention best practices that can be used as a training tool to educate new Users within your organization
Business Internet Banking / Cash Management Fraud Prevention Best Practices This document provides fraud prevention best practices that can be used as a training tool to educate new Users within your organization
Security Practices Essentials. Viruses McAfee Virus Software Critical Windows Updates Network Settings. Spyware Adaware Spybot Windows Defender
 Security Practices Essentials Viruses McAfee Virus Software Critical Windows Updates Network Settings Spyware Adaware Spybot Windows Defender Security Practices Essentials: All computer passwords should
Security Practices Essentials Viruses McAfee Virus Software Critical Windows Updates Network Settings Spyware Adaware Spybot Windows Defender Security Practices Essentials: All computer passwords should
Business ebanking Fraud Prevention Best Practices
 Business ebanking Fraud Prevention Best Practices User ID and Password Guidelines Create a strong password with at least 8 characters that includes a combination of mixed case letters, numbers, and special
Business ebanking Fraud Prevention Best Practices User ID and Password Guidelines Create a strong password with at least 8 characters that includes a combination of mixed case letters, numbers, and special
Security Suites for Mac OS X: For on-demand detection, only four products achieved the 100-percent mark (AV-TEST August 2014).
 18th September 2014 created by Markus Selinger Mac OS X in the Crosshairs 18 Malware Scanners Put to the Test For a long time, Mac OS users believed they were safe, that there was no malware for their
18th September 2014 created by Markus Selinger Mac OS X in the Crosshairs 18 Malware Scanners Put to the Test For a long time, Mac OS users believed they were safe, that there was no malware for their
ELECTRONIC AUTHENTICATION. Understanding the New. Multi-factor authentication and layered security are
 Understanding the New ELECTRONIC AUTHENTICATION Multi-factor authentication and layered security are helping assure safe Internet transactions for credit unions and their members. Assuring Your Online
Understanding the New ELECTRONIC AUTHENTICATION Multi-factor authentication and layered security are helping assure safe Internet transactions for credit unions and their members. Assuring Your Online
Security Maintenance Practices. IT 4823 Information Security Administration. Patches, Fixes, and Revisions. Hardening Operating Systems
 IT 4823 Information Security Administration Securing Operating Systems June 18 Security Maintenance Practices Basic proactive security can prevent many problems Maintenance involves creating a strategy
IT 4823 Information Security Administration Securing Operating Systems June 18 Security Maintenance Practices Basic proactive security can prevent many problems Maintenance involves creating a strategy
Quick Start Guide to Logging in to Online Banking
 Quick Start Guide to Logging in to Online Banking Log In to Internet Banking: Note: The first time you log in you are required to use your Customer ID. Your Customer ID is the primary account holder s
Quick Start Guide to Logging in to Online Banking Log In to Internet Banking: Note: The first time you log in you are required to use your Customer ID. Your Customer ID is the primary account holder s
1. Why is the customer having the penetration test performed against their environment?
 General Questions 1. Why is the customer having the penetration test performed against their environment? Assess vulnerabilities in order to improve security and protect client information. 2. Is the penetration
General Questions 1. Why is the customer having the penetration test performed against their environment? Assess vulnerabilities in order to improve security and protect client information. 2. Is the penetration
Report on Consumer Behaviors and Perceptions of Mobile Security. Presented by NQ Mobile & NCSA January 25, 2012
 Report on Consumer Behaviors and Perceptions of Mobile Security Presented by NQ Mobile & NCSA January 25, 2012 Methodology Online survey of 1,158 consumers. Participants had to own a smartphone. Respondents
Report on Consumer Behaviors and Perceptions of Mobile Security Presented by NQ Mobile & NCSA January 25, 2012 Methodology Online survey of 1,158 consumers. Participants had to own a smartphone. Respondents
Protect Yourself. Who is asking? What information are they asking for? Why do they need it?
 Protect Yourself Your home computer serves many purposes: email, shopping, social networking and more. As you surf the Internet, you should be aware of the various ways to protect yourself. Of primary
Protect Yourself Your home computer serves many purposes: email, shopping, social networking and more. As you surf the Internet, you should be aware of the various ways to protect yourself. Of primary
Created By: 2009 Windows Server Security Best Practices Committee. Revised By: 2014 Windows Server Security Best Practices Committee
 Windows Server Security Best Practices Initial Document Created By: 2009 Windows Server Security Best Practices Committee Document Creation Date: August 21, 2009 Revision Revised By: 2014 Windows Server
Windows Server Security Best Practices Initial Document Created By: 2009 Windows Server Security Best Practices Committee Document Creation Date: August 21, 2009 Revision Revised By: 2014 Windows Server
REMOTELY ACCESS YOUR FILES WITH THE FLAGLER FILECONNECT SYSTEM
 REMOTELY ACCESS YOUR FILES WITH THE FLAGLER FILECONNECT SYSTEM This document explains the various ways to connect to your network files and group share data. In addition, staff and full-time faculty are
REMOTELY ACCESS YOUR FILES WITH THE FLAGLER FILECONNECT SYSTEM This document explains the various ways to connect to your network files and group share data. In addition, staff and full-time faculty are
Parent$Coffee$Presents:$ The$Security$Geek s$guide$to$your$personal$ Security$
 Parent$Coffee$Presents:$ The$Security$Geek s$guide$to$your$personal$ Security$ Look$inside$the$mind$of$a$hacker$ h=ps://www.youtube.com/embed/f7pyhn9ic91$ Introducing$our$speaker$ Understanding$risk$ Measuring$Threats$
Parent$Coffee$Presents:$ The$Security$Geek s$guide$to$your$personal$ Security$ Look$inside$the$mind$of$a$hacker$ h=ps://www.youtube.com/embed/f7pyhn9ic91$ Introducing$our$speaker$ Understanding$risk$ Measuring$Threats$
This article will show you ten ways to keep you computer in in tip-top condition.
 This article will show you ten ways to keep you computer in in tip-top condition. Be careful opening ALL attachments delivered through email This regularly catches out clients of mine. If you receive an
This article will show you ten ways to keep you computer in in tip-top condition. Be careful opening ALL attachments delivered through email This regularly catches out clients of mine. If you receive an
If you are experiencing difficulty joining a session, determine which scenario is applicable to you and follow the recommended guidelines.
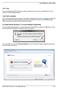 Join Help If you are experiencing difficulty joining a session, determine which scenario is applicable to you and follow the recommended guidelines. I can't join a session. If you're having trouble joining
Join Help If you are experiencing difficulty joining a session, determine which scenario is applicable to you and follow the recommended guidelines. I can't join a session. If you're having trouble joining
Course: Information Security Management in e-governance. Day 1. Session 5: Securing Data and Operating systems
 Course: Information Security Management in e-governance Day 1 Session 5: Securing Data and Operating systems Agenda Introduction to information, data and database systems Information security risks surrounding
Course: Information Security Management in e-governance Day 1 Session 5: Securing Data and Operating systems Agenda Introduction to information, data and database systems Information security risks surrounding
Student Desktop@ Home
 Student Desktop@ Home Full Off Campus Access to your Programs and Files Full Access to the University from Home You can access the University from any computer with an internet connection. This system
Student Desktop@ Home Full Off Campus Access to your Programs and Files Full Access to the University from Home You can access the University from any computer with an internet connection. This system
SMALL BUSINESS PRESENTATION
 STOP.THINK.CONNECT NATIONAL CYBERSECURITY AWARENESS CAMPAIGN SMALL BUSINESS PRESENTATION ABOUT STOP.THINK.CONNECT. In 2009, President Obama issued the Cyberspace Policy Review, which tasked the Department
STOP.THINK.CONNECT NATIONAL CYBERSECURITY AWARENESS CAMPAIGN SMALL BUSINESS PRESENTATION ABOUT STOP.THINK.CONNECT. In 2009, President Obama issued the Cyberspace Policy Review, which tasked the Department
Manual for Android 1.5
 Manual for Android 1.5 1 Table of Content 1. Scope of Service... 3 1.1 About Boxcryptor Classic... 3 1.2 About this manual... 3 2. Installation... 4 3. Basic functionality... 5 3.1. Setting up Boxcryptor
Manual for Android 1.5 1 Table of Content 1. Scope of Service... 3 1.1 About Boxcryptor Classic... 3 1.2 About this manual... 3 2. Installation... 4 3. Basic functionality... 5 3.1. Setting up Boxcryptor
Symantec Norton AntiVirus 9.0.1 for Macintosh Download, Installation, and Basic Use Tutorial
 Symantec Norton AntiVirus 9.0.1 for Macintosh Download, Installation, and Basic Use Tutorial Created by: Melanie Cofield Based on information found at: https://www.utexas.edu/its/bevoware/virus/macxvirus.html
Symantec Norton AntiVirus 9.0.1 for Macintosh Download, Installation, and Basic Use Tutorial Created by: Melanie Cofield Based on information found at: https://www.utexas.edu/its/bevoware/virus/macxvirus.html
7 Steps to Safer Computing
 7 Steps to Safer Computing These are the seven essentials: - Use a firewall. - Keep your software up to date. - Use an up to date antivirus program. - Use an up to date anti-spyware program. - Only download
7 Steps to Safer Computing These are the seven essentials: - Use a firewall. - Keep your software up to date. - Use an up to date antivirus program. - Use an up to date anti-spyware program. - Only download
Assuria can help protectively monitor firewalls for PCI compliance. Assuria can also check the configurations of personal firewalls on host devices
 The Payment Card Industry (PCI) Data Security Standard (DSS) provides an actionable framework for developing a robust payment card data security process. The Payment Application Data Security Standard
The Payment Card Industry (PCI) Data Security Standard (DSS) provides an actionable framework for developing a robust payment card data security process. The Payment Application Data Security Standard
How To Manage A Network Safely
 ICANWK303A Configure and administer a network operating system Release: 1 ICANWK303A Configure and administer a network operating system Modification History Release Release 1 Comments This Unit first
ICANWK303A Configure and administer a network operating system Release: 1 ICANWK303A Configure and administer a network operating system Modification History Release Release 1 Comments This Unit first
Getting Started with Symantec Endpoint Protection
 Getting Started with Symantec Endpoint Protection 20983668 Getting Started with Symantec Endpoint Protection The software described in this book is furnished under a license agreement and may be used only
Getting Started with Symantec Endpoint Protection 20983668 Getting Started with Symantec Endpoint Protection The software described in this book is furnished under a license agreement and may be used only
Boston University Security Awareness. What you need to know to keep information safe and secure
 What you need to know to keep information safe and secure Introduction Welcome to Boston University s Security Awareness training. Depending on your reading speed, this presentation will take approximately
What you need to know to keep information safe and secure Introduction Welcome to Boston University s Security Awareness training. Depending on your reading speed, this presentation will take approximately
References NYS Office of Cyber Security and Critical Infrastructure Coordination Best Practices and Assessment Tools for the Household
 This appendix is a supplement to the Cyber Security: Getting Started Guide, a non-technical reference essential for business managers, office managers, and operations managers. This appendix is one of
This appendix is a supplement to the Cyber Security: Getting Started Guide, a non-technical reference essential for business managers, office managers, and operations managers. This appendix is one of
It is a program or piece of code that is loaded onto your computer without your knowledge and runs against your wishes.
 Virus What is a virus? It is a program or piece of code that is loaded onto your computer without your knowledge and runs against your wishes. It can also be defined as a set of codes written to cause
Virus What is a virus? It is a program or piece of code that is loaded onto your computer without your knowledge and runs against your wishes. It can also be defined as a set of codes written to cause
Personal Firewall Usability-A Survey
 Personal Firewall Usability-A Survey Jiao Dapeng Helsinki University of Technology Jiao.Dapeng@hut.fi Abstract In this paper, we focus on the usability challenges presented by personal firewalls. Nowadays,
Personal Firewall Usability-A Survey Jiao Dapeng Helsinki University of Technology Jiao.Dapeng@hut.fi Abstract In this paper, we focus on the usability challenges presented by personal firewalls. Nowadays,
A Windows Desktop Security Primer
 A Windows Desktop Security Primer ITSS Technical Briefing Jay Stamps, ITSS, jstamps@stanford.edu, 723-0018 Turing Auditorium, May 20, 2005 Topics for the Afternoon Windows XP Professional Security Setting
A Windows Desktop Security Primer ITSS Technical Briefing Jay Stamps, ITSS, jstamps@stanford.edu, 723-0018 Turing Auditorium, May 20, 2005 Topics for the Afternoon Windows XP Professional Security Setting
Cyber Security Beginners Guide to Firewalls A Non-Technical Guide
 Cyber Security Beginners Guide to Firewalls A Non-Technical Guide Essential for Business Managers Office Managers Operations Managers Multi-State Information Sharing and Analysis Center (MS-ISAC) U.S.
Cyber Security Beginners Guide to Firewalls A Non-Technical Guide Essential for Business Managers Office Managers Operations Managers Multi-State Information Sharing and Analysis Center (MS-ISAC) U.S.
Result of the Attitude Survey on Information Security
 Presentation Result of the Attitude Survey on Information Security Conducted toward the companies Operating in Thailand February, 2009 Center of the International Cooperation for Computerization of Japan
Presentation Result of the Attitude Survey on Information Security Conducted toward the companies Operating in Thailand February, 2009 Center of the International Cooperation for Computerization of Japan
Countermeasures against Spyware
 (2) Countermeasures against Spyware Are you sure your computer is not infected with Spyware? Information-technology Promotion Agency IT Security Center http://www.ipa.go.jp/security/ 1. What is a Spyware?
(2) Countermeasures against Spyware Are you sure your computer is not infected with Spyware? Information-technology Promotion Agency IT Security Center http://www.ipa.go.jp/security/ 1. What is a Spyware?
Contact details For contacting ENISA or for general enquiries on information security awareness matters, please use the following details:
 Malicious software About ENISA The European Network and Information Security Agency (ENISA) is an EU agency created to advance the functioning of the internal market. ENISA is a centre of excellence for
Malicious software About ENISA The European Network and Information Security Agency (ENISA) is an EU agency created to advance the functioning of the internal market. ENISA is a centre of excellence for
Before you begin 2 Initial laptop setup 2 Configure Microsoft update 3 Install University of Kent programs 3
 Advanced IT user guide Staff laptop setup For staff laptops owned by the University Contents Before you begin 2 Initial laptop setup 2 Configure Microsoft update 3 Install University of Kent programs 3
Advanced IT user guide Staff laptop setup For staff laptops owned by the University Contents Before you begin 2 Initial laptop setup 2 Configure Microsoft update 3 Install University of Kent programs 3
Ordering Offsite Backups
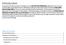 Introduction The purpose of this Startup Guide is to familiarize you with Own Web Now's Offsite Backup offering and show you how to purchase, deploy and manage the service. Offsite Backup offering is an
Introduction The purpose of this Startup Guide is to familiarize you with Own Web Now's Offsite Backup offering and show you how to purchase, deploy and manage the service. Offsite Backup offering is an
Protection for Mac and Linux computers: genuine need or nice to have?
 Protection for Mac and Linux computers: genuine need or nice to have? The current risk to computers running non-windows platforms is small but growing. As Mac and Linux computers become more prevalent
Protection for Mac and Linux computers: genuine need or nice to have? The current risk to computers running non-windows platforms is small but growing. As Mac and Linux computers become more prevalent
Computer Security. Uses Zip disks that hold up to 750 MB of data. Must buy and hook up the drive.
 Basic Computer Security Practices Make backups of important files. Apply patches to the operating system. Use anti-virus software, update definitions very frequently, and run a full virus scan at least
Basic Computer Security Practices Make backups of important files. Apply patches to the operating system. Use anti-virus software, update definitions very frequently, and run a full virus scan at least
Remote VPN: Remote access for personal devices
 Remote VPN: Remote access for personal devices Documentation Team. March 2013. About Remote VPN Remote VPN 1 provides staff and students with secure, authenticated remote access to personal and shared
Remote VPN: Remote access for personal devices Documentation Team. March 2013. About Remote VPN Remote VPN 1 provides staff and students with secure, authenticated remote access to personal and shared
How to Deal with Spyware A CyberAngels Quick Tutorial
 How to Deal with Spyware A CyberAngels Quick Tutorial Adapted from the US Computer Emergency Readiness Team Spyware and Adware After completing this tutorial, you will be able to: Identify the main risks
How to Deal with Spyware A CyberAngels Quick Tutorial Adapted from the US Computer Emergency Readiness Team Spyware and Adware After completing this tutorial, you will be able to: Identify the main risks
1. Please login to the Own Web Now Support Portal (https://support.ownwebnow.com) with your email address and a password.
 Offsite Backups Introduction The purpose of this Startup Guide is to familiarize you with Own Web Now's Offsite Backup offering and show you how to purchase, deploy and manage the service. Offsite Backup
Offsite Backups Introduction The purpose of this Startup Guide is to familiarize you with Own Web Now's Offsite Backup offering and show you how to purchase, deploy and manage the service. Offsite Backup
Cyber Security: Beginners Guide to Firewalls
 Cyber Security: Beginners Guide to Firewalls A Non-Technical Guide Essential for Business Managers Office Managers Operations Managers This appendix is a supplement to the Cyber Security: Getting Started
Cyber Security: Beginners Guide to Firewalls A Non-Technical Guide Essential for Business Managers Office Managers Operations Managers This appendix is a supplement to the Cyber Security: Getting Started
National Cybersecurity Awareness Campaign
 National Cybersecurity Awareness Campaign About Stop.Think.Connect. In 2009, President Obama issued the Cyberspace Policy Review, which tasked the Department of Homeland Security with creating an ongoing
National Cybersecurity Awareness Campaign About Stop.Think.Connect. In 2009, President Obama issued the Cyberspace Policy Review, which tasked the Department of Homeland Security with creating an ongoing
Client Security Risk Assessment Questionnaire
 Select the appropriate answer from the drop down in the column, and provide a brief description in the section. 1 Do you have a member of your organization with dedicated information security duties? 2
Select the appropriate answer from the drop down in the column, and provide a brief description in the section. 1 Do you have a member of your organization with dedicated information security duties? 2
EasyBiz. Business Software Solutions for South African Businesses NETWORK SETUP IN QUICKBOOKS ACCOUNTING MADE EASY
 EasyBiz OFFICIAL INTUIT-AUTHORISED SOLUTION PROVIDER ACCOUNTING MADE EASY Business Software Solutions for South African Businesses NETWORK SETUP IN QUICKBOOKS Network Setup for QuickBooks 2013 QuickBooks
EasyBiz OFFICIAL INTUIT-AUTHORISED SOLUTION PROVIDER ACCOUNTING MADE EASY Business Software Solutions for South African Businesses NETWORK SETUP IN QUICKBOOKS Network Setup for QuickBooks 2013 QuickBooks
Why is a strong password important?
 Internet Security Why is a strong password important? Identity theft motives: To gain access to resources For the challenge/fun Personal reasons Theft methods Brute forcing and other script hacking methods
Internet Security Why is a strong password important? Identity theft motives: To gain access to resources For the challenge/fun Personal reasons Theft methods Brute forcing and other script hacking methods
Encrypting Personal Health Information on Mobile Devices
 Ann Cavoukian, Ph.D. Information and Privacy Commissioner/Ontario Number 12 May 2007 Encrypting Personal Health Information on Mobile Devices Section 12 (1) of the Personal Health Information Protection
Ann Cavoukian, Ph.D. Information and Privacy Commissioner/Ontario Number 12 May 2007 Encrypting Personal Health Information on Mobile Devices Section 12 (1) of the Personal Health Information Protection
AllianceIT Managed Services
 AllianceIT Managed Services confidence predictability productivity focus Uncertainty is a business killer. To be successful, companies have to know that their critical IT systems will be available on demand
AllianceIT Managed Services confidence predictability productivity focus Uncertainty is a business killer. To be successful, companies have to know that their critical IT systems will be available on demand
PC Security & Housekeeping March 2015
 PC Security & Housekeeping March 2015 Anti-malware programs Always keep your firewall, anti-virus, and anti-spyware products up to date! There are many good commercial products available, such as: o Norton
PC Security & Housekeeping March 2015 Anti-malware programs Always keep your firewall, anti-virus, and anti-spyware products up to date! There are many good commercial products available, such as: o Norton
Survey of Spyware Tools and Counter Measures
 Survey of Spyware Tools and Counter Measures Dr. Robert W. Baldwin Plus Five Consulting, Inc. Kevin W. Kingdon Intellitrove, Inc. Outline Spyware Demonstration Spyware: Architecture & Features Ethics Counter
Survey of Spyware Tools and Counter Measures Dr. Robert W. Baldwin Plus Five Consulting, Inc. Kevin W. Kingdon Intellitrove, Inc. Outline Spyware Demonstration Spyware: Architecture & Features Ethics Counter
What are the common online dangers?
 ONLINE SECURITY GUIDELINES Internet Banking is convenient and times saving. You can do remittances, place online deposit and other transactions through online banking with the convenience and privacy of
ONLINE SECURITY GUIDELINES Internet Banking is convenient and times saving. You can do remittances, place online deposit and other transactions through online banking with the convenience and privacy of
SmartFiler Backup Appliance User Guide 2.0
 SmartFiler Backup Appliance User Guide 2.0 SmartFiler Backup Appliance User Guide 1 Table of Contents Overview... 5 Solution Overview... 5 SmartFiler Backup Appliance Overview... 5 Getting Started... 7
SmartFiler Backup Appliance User Guide 2.0 SmartFiler Backup Appliance User Guide 1 Table of Contents Overview... 5 Solution Overview... 5 SmartFiler Backup Appliance Overview... 5 Getting Started... 7
Norton Small Business. Getting Started Guide
 Norton Small Business Getting Started Guide The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Copyright 2015
Norton Small Business Getting Started Guide The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Copyright 2015
Firewall Test. Firewall protection in public networks. Commissioned by CHIP. Language: English. Last Revision: 11 th April 2014
 Firewall Test Firewall protection in public networks Commissioned by CHIP Language: English Last Revision: 11 th April 2014 www.av-comparatives.org Commissioned by - 1 - Contents Firewall protection in
Firewall Test Firewall protection in public networks Commissioned by CHIP Language: English Last Revision: 11 th April 2014 www.av-comparatives.org Commissioned by - 1 - Contents Firewall protection in
Internet Security for Windows XP and Vista
 Welcome Windows XP and Vista Users Welcome to Alliance Internet. You have joined one of the fastest growing Internet providers in the area. This information will help you understand how your Internet works.
Welcome Windows XP and Vista Users Welcome to Alliance Internet. You have joined one of the fastest growing Internet providers in the area. This information will help you understand how your Internet works.
