Idaho Letter of Intent for 2015 MeF
|
|
|
- Juliet Wright
- 8 years ago
- Views:
Transcription
1 Overview Industry Trusted Customer Requirements Idaho Letter of Intent for 2015 MeF The industry, state and IRS partners recognize that even though fraud filings will still occur, we all must be proactive and take steps to reduce or prevent the fraud. The acceptance of username and passwords as the only source of authentication is no longer a viable solution and must be enhanced through minimum mandatory additional levels of authentication. Minimum requirements are established in cooperation with industry partners, states and the IRS to present a consistent standard for front- end customer identity authentication using recognized national standards from the National Institute of Standards and Technology (NIST) and the IRS Pub The IRS and States working with Industry partners have established the following minimum set of standards and methodology that Industry will use to help deter potential identity theft tax refund fraud activity, which going forward will be based on increasingly stringent and effective national standards and protocols. To preserve innovation and creativity, Industry partners may choose to, and are encouraged to, exceed the minimum standards established and conduct their own independent and unique analysis, based on patterns or trends they observe and identify. These minimum requirements will be reviewed and strengthened by July of each year. Passwords: Through the use of strong passwords and locking out an account after many consecutive failed attempts, the goal is to mitigate password guessing and brute force attacks. For the lockout feature, the working group established a number that industry supports while recognizing that, as stated in the NIST recommendations, locking out an account after only a few failed attempts has a significant impact on legitimate users and are targeting 10 as a reasonable starting point for this first year in lieu of another alternative of increasing the delay after each failed attempt. These standards also meet the IRS Pub 1075 requirements. Out- of- Band Verification: Tax agencies recognize that out- of- band verification is becoming a national standard and recommend that the industry partners implement this protocol. The IRS recently incorporated this standard for its Get Transcript application. Because not all industry partners will implement this verification protocol for this upcoming processing season, the working group also identified a data element to be submitted with each return to identify the ability to verify the customer s address. The tax agencies will also include a question within their annual filing agreements to determine if the industry partner will implement out- of- band verification. Requirements Not Prescriptive: It would not be wise for government to provide very detailed prescriptive requirements and in so doing possibly curtail the ability of the tax software industry to exceed the current critical need for knowing your customer, but the steps outlined are a baseline. The document is formatted to provide clarity to the minimum requirements baseline recognized in current national standards as agreed upon by the working group. Industry will meet the 1
2 requirements set forth in this document based on their particular business models and if an industry partner addresses identity authentication using other features not identified in these minimum requirements, the industry partner will work directly with each tax agency to identify the protocol and gain the agency s approval. The government will not dictate specifically how these standards are met and the vendor ultimately must establish that the e- filing application meets or exceeds the minimum requirements. Initial Target Audience The initial target population of providers is all do- it- yourself taxpayer interfaces into an on- line tax system including (but not limited to): When the data is stored electronically online or When the customer establishes an online account Establishing a trusted customer requirement for this target audience is an important step in building a robust tax filing system that: Follows nationally recognized standards for implementing Knowing Your Customer identity authentication Ensures consistent minimum requirements are established for industry to efficiently support multiple tax agencies Mitigates the potential for account takeovers Reduces the opportunity for fraudulent return filing Establishes a process to verify identity in future interactions including but not limited to password changes Enhances security / protection measures for taxpayer confidential and sensitive information Increases the public confidence and trust in the tax filing system These steps will be accompanied by national and local messaging driving home these principles. Note that these requirements can and will change over time to respond to new technologies and new threats. 2
3 Minimum Requirements for Identity Authentication The following minimum requirements for the target audience will be incorporated in agency e- filing agreements for certification and will be verified by optional post- launch reviews. New Customer Standard I. Username no specific format requirement 1. Include helpful tips such as do not use address, SSN, First and Last Name, etc. II. Password 1. All customers will be provided messaging on the importance of a strong password (at least 8 characters, upper, lower case, digit and special char) as an important step for protecting their identity. 2. Implement a 15 minute interval after lockout feature with no more than 10 unsuccessful login attempts 3. At least 8 characters Including all of the following: o At least 1 uppercase character (A- Z) o At least 1 lowercase character (a- z) o At least 1 digit (0-9) o At least 1 special character (punctuation) III. Three security questions (If the company does not support out-of-band and will be using the security questions as one of the choices in the minimum Returning Customer Standards below) 1. Question and answer provided by the customer or established by industry 2. Do not use questions that have readily available answers 3. Do not use questions that have answers that are shared with others or are available to others IV. Customer is required to enter an address V. Customer is provided an option to enter a cell phone number VI. Address Verification (see Filing Expectations) 1. The preferred method is for industry partners to implement out- of- band verification. a. Out-of -band verification is sending an or text to the customer with a PIN. Through a user interface, the customer enters a PIN which is validated through the software before allowing the customer to continue with the process. 2. If an industry partner does not implement out-of-band for New Customers, the industry partner must make their best effort to verify the address. 3
4 Returning Customer Standard For Processing Year 2016, Industry will: Provide messaging to all returning customers on the importance of a strong password (at least 8 characters, upper, lower case, digit and special char) and given the opportunity to change their password as an important step for protecting their identity; Implement a 15 minute interval after lockout feature with no more than 10 unsuccessful login attempts; Ensure that the customer has previously entered an address; Ensure that the customer has the opportunity to add a cell phone entry. I. Is the IP address or device ID recognized from previous login? If yes, continue to next step. If no, successful completion of one of the following is required before proceeding: 1. Out- of- band verification or 2. Answer randomly selected security question II. Do the security questions on record meet the New Customer standards? (Not applicable if the company is choosing to use alternate authentication methods based on the below options, and such authentication is successful.) If yes, continue to next step If no, 1. Customer must update security questions to meet the New Customer standard III. Is the customer indicating they have a new address? To change an address, customer must successfully complete one of the following: 1. Out- of- band verification to or cell phone with a notification sent to the old address or cell with instructions on what to do if they didn t change their address or IV. Has there been account activity within 90 days? If yes, continue to next step 2. Answer randomly selected security question If no, AND the customer is NOT using a trusted/proven device or IP Address, successful completion of one of the following is required before proceeding: 1. Out- of- band verification or 2. Answer randomly selected security question 4
5 V. In cases of increased system risk based on identified facts and circumstances determined collaboratively by industry, agencies and IRS (needs to be flexible): Customers may be required to successfully complete one of the following before proceeding: 1. Out- of- band verification or 2. Answer randomly selected security question VI. Prior to filing, Industry will complete Address Verification (see Filing Expectations) 1. The preferred method is for industry partners to implement out- of- band verification. a. Out- of- band verification is sending an or text to the customer with a PIN. Through a user interface, the customer enters the PIN, which is validated through the software before allowing the customer to continue with the process. 2. If an industry partner does not implement out- of- band for New Customers, the industry partner must make their best effort to verify the address. Filing Expectations Determine if more than one account is using a Primary and/or Secondary SSN, o If the SSN is used in multiple accounts, at least one of the following actions must apply to all related accounts: Notify account holder(s) that the Primary and/or Secondary SSN is used within another account OR Notify account holder(s) that the Primary and/or Secondary SSN is used within another account AND Implement Additional Authentication measures prior to filing to validate the authenticity of one or more of the related accounts o All account holders have the opportunity to report the situation to the right authorities if they suspect improper use of the SSN. A data element provided by the vendor will be used to indicate the level of verification performed for each filed return. Tax agencies may request acknowledgement of the use of out- of- band within the e- filing agreement (see Agreement Statements) and may use out- of- band capability and the indicators in the process of examining the internal analytics of the return. The following schema data element indicators will be used to report the level of contact verification that occurred during the filing process: Address Verification (Element name _Address_Ind) 0 = Can t send 1 = Bounced 2 = Delivered one- way 3 = Successful out- of- band (text or ) To reduce the occurrences of multiple fraudulent returns, Industry will ensure that, at the point of filing, there are no more than two resident state returns filed with a single federal return. 5
6 Agreement Statements In order to assist with fraud detection and prevention, the Idaho State Tax Commission requests information about the business practices of our vendor partners. 1. Do you use out- of- band verification practices for your customer verification process? a. Out- of- band verification is sending an or text to the customer with a PIN. Through a user interface, the customer enters the PIN, which is validated through the software before allowing the customer to continue with the process. Yes No 2. Do you meet nationally recognized standards for implementing identity authentication by using: a. The standards identified in the Identity Authentication section of this agreement. b. An equivalent standard for identity authentication that meets or exceeds the minimum requirements. Please describe your proposed process for agency review. a. b. Description 3. Do you agree to add consent to disclosure language, such as outlined on page 8, relating to certain characteristics of use of the system, to your user agreement? Yes No (name) (signature) (date) 6
7 In this section, tax services provider is defined as a: Electronic Return Originator (ERO): An ERO originates the electronic submission of a tax return through IRS or state e-file after the taxpayer authorizes the electronic filing of the return. Online Filing Provider: An Online Filing Provider allows taxpayers to self-prepare returns by entering return data directly into commercially available software downloaded from an Internet site and prepared off-line, or through an online Internet site, or loaded from physical media onto a desktop computer or mobile device. Software Developer: An Authorized IRS or state e-file Provider that develops software for the purposes of (a) formatting the electronic portions of returns according to Publication 4164 or state specifications and/or (b) transmitting the electronic portion of returns directly to the IRS or the state. A Software Developer may also sell its software. Transmitter: An Authorized IRS or state e-file Provider that transmits the electronic portion of a return directly to the IRS or the state. An entity that provides a bump up service is also a Transmitter. A bump up service provider increases the transmission rate or line speed of formatted or reformatted information that it is sending to the IRS or the state via a public switched telephone network. A tax services provider may serve its customers in more than one of these roles. A tax services provider may use any tax return information provided by a taxpayer, whether in and for the current year or for prior years, for the purpose of identifying a suspicious or potentially fraudulent return from or related to that taxpayer. For these purposes, tax return information means any and all documents or materials provided by the taxpayer or required by the taxing authority that the tax services provider uses in the course of the return preparation and submission. Tax services providers shall produce analytic compilations of federal and state tax return and submission information that directly relate to the internal management or support of the tax services provider s business, which shall include aggregated data compilations to identify potentially fraudulent behaviors or patterns. The analytic compilation shall employ any tax return information provided by the taxpayer. Tax services providers shall disclose the compilations of tax information to Idaho through IRS secure data transmission on at least a weekly basis and identify by use of federal and state submission IDs any return the preparer believes is potentially fraudulent. In addition, if a tax services provider has a bona fide belief that a particular individual s activity, discovered by data mining a statistical compilation, violated criminal law, the tax services provider shall disclose that individual s tax return information to the state of Idaho. 7
8 During the 2016 filing season, some of the new elements of information (possible fraud indicators) that providers will be collecting and submitting to the tax agency as a part of industry reporting are not in the return itself, but relate to certain characteristics of use of the system. For this reason you may wish to re-visit the language in your taxpayer consent to disclosure. Suggested standard additional text to be included in the taxpayer consent is below. In addition, by using a computer system and software to prepare and transmit my return electronically, I consent to the disclosure to the [state] of all information pertaining to my use of the system and software and to the transmission of my tax return electronically. You may also wish to reference the identity theft language we are adding to our Individual Income Tax instructions booklet for T2015. How Identity Theft May Affect Your Tax Return Identity theft is affecting more people each year. From 2014 to 2015, there was a 64% increase in stolen identities used to file Idaho income tax returns. To help protect you and any refund you may be due, the Tax Commission uses multiple processes to validate your identity and tax return. In some cases, we may contact you for additional information. Also, the software product you use to E-file your taxes may ask for additional information. Our verification processes can take extra time and may delay your refund; however, they re necessary to ensure the safety of your confidential information. 8
9 2015 MeF Individual/Business Test Please only one product per sheet Developer Name: ETIN#: Product Name: NACTP#: Individual or Business Tests: Amended Return (Yes or No): State only ( Yes or No ): Contact Information Primary Contact Name for MeF Individual/Business Tests: Address: Telephone: Fax: Secondary Contact Name for MeF Individual/Business Tests: Address: Telephone: Fax: Please MeFtesting@tax.idaho.gov EFO
10 EFO00284p MeF Individual/Business Tests Please select the Schemas and PDF attachments you will be submitting for testing Schemas 39R 39NR Support Schemas Support Schemas Before June After July 1 ID K-1 PTE-01 Support 41S C 49R R R CG PTE-12 ITC-LIST Individual/Business Attachments PDF Attachment Attachment Name Support 14 41A 49E 49ER 49ESR IC 75IMV 402 NON-Idaho Income Tax Return Miscellaneous Statements Combined Report Spreadsheet ITC Equipment List Form_14_01 Form_41A_01 Form_49E_01 Form_49ER_01 Form_49ESR_01 Form_70_01 Form_75IC_01 Form_75IMV_01 Form_402_01 OtherState_Return_01 Misc_Stmt_01 Comb_Report_01 ITC_Equipment_01 Reimbursement Incentive Credit Reimburse_Credit_01
Covered Areas: Those EVMS departments that have activities with Covered Accounts.
 I. POLICY Eastern Virginia Medical School (EVMS) establishes the following identity theft program ( Program ) to detect, identify, and mitigate identity theft in its Covered Accounts in accordance with
I. POLICY Eastern Virginia Medical School (EVMS) establishes the following identity theft program ( Program ) to detect, identify, and mitigate identity theft in its Covered Accounts in accordance with
Identity Theft Don t Be a Victim How IRS and Tax Professionals Can Prevent Identity Theft and Assist Taxpayers Who Are Victims
 Identity Theft Don t Be a Victim How IRS and Tax Professionals Can Prevent Identity Theft and Assist Taxpayers Who Are Victims Narina Bchtikian Stephen Connor Senior Stakeholder Liaison IRS Small Business/Self-Employed
Identity Theft Don t Be a Victim How IRS and Tax Professionals Can Prevent Identity Theft and Assist Taxpayers Who Are Victims Narina Bchtikian Stephen Connor Senior Stakeholder Liaison IRS Small Business/Self-Employed
IRS & Partners Combat Tax-Related Identity Theft What s New for 2016
 IRS & Partners Combat Tax-Related Identity Theft What s New for 2016 General Scope of Identity Theft Identity theft costs U.S. victims more than all property crimes combined Identity theft remains number
IRS & Partners Combat Tax-Related Identity Theft What s New for 2016 General Scope of Identity Theft Identity theft costs U.S. victims more than all property crimes combined Identity theft remains number
News Release Date: 11/23/15
 News Release Date: 11/23/15 Identity Theft Cross References www.irs.gov IRS Pub 4557, Safeguarding Taxpayer Data IRS Pub 5027, Identity Theft Information for Taxpayers IRS Pub 5199, Tax Preparer Guide
News Release Date: 11/23/15 Identity Theft Cross References www.irs.gov IRS Pub 4557, Safeguarding Taxpayer Data IRS Pub 5027, Identity Theft Information for Taxpayers IRS Pub 5199, Tax Preparer Guide
Disclosing Client Information
 CPE/CE 2 Credit Hours Disclosing Client Information Disclosures, Use, Consent Requirements Interactive Self-Study CPE/CE Course Course Overview Program Content: Publication Date: September 2015. Expiration
CPE/CE 2 Credit Hours Disclosing Client Information Disclosures, Use, Consent Requirements Interactive Self-Study CPE/CE Course Course Overview Program Content: Publication Date: September 2015. Expiration
Here are two informational brochures that disclose ways that we protect your accounts and tips you can use to be safer online.
 Here are two informational brochures that disclose ways that we protect your accounts and tips you can use to be safer online. FFIEC BUSINESS ACCOUNT GUIDANCE New financial standards will assist credit
Here are two informational brochures that disclose ways that we protect your accounts and tips you can use to be safer online. FFIEC BUSINESS ACCOUNT GUIDANCE New financial standards will assist credit
Modernized e-file Software Developer s Guide
 PUBLICATION 1346N-MeF TAX YEAR 2009 Modernized e-file Software Developer s Guide For Electronic Filers of Individual Income Tax Returns BE SURE TO GET OTHER SOFTWARE DEVELOPER MATERIALS FROM OUR WEB SITE.
PUBLICATION 1346N-MeF TAX YEAR 2009 Modernized e-file Software Developer s Guide For Electronic Filers of Individual Income Tax Returns BE SURE TO GET OTHER SOFTWARE DEVELOPER MATERIALS FROM OUR WEB SITE.
Identity Theft: How the IRS Protects Taxpayers and Helps Victims. Combating Identity Theft and Online Fraud
 Identity Theft: How the IRS Protects Taxpayers and Helps Victims Combating Identity Theft and Online Fraud What is identity theft? Identity theft occurs when someone uses your personal information such
Identity Theft: How the IRS Protects Taxpayers and Helps Victims Combating Identity Theft and Online Fraud What is identity theft? Identity theft occurs when someone uses your personal information such
How the IRS Helps Taxpayers and Assist Victims
 How the IRS Helps Taxpayers and Assist Victims Combating Identity Theft and Online Fraud Phil Oliver and Mark Harrington Privacy, Governmental Liaison and Disclosure May 31, 2013 What is identity theft?
How the IRS Helps Taxpayers and Assist Victims Combating Identity Theft and Online Fraud Phil Oliver and Mark Harrington Privacy, Governmental Liaison and Disclosure May 31, 2013 What is identity theft?
How the IRS Helps Taxpayers and Assists Victims
 How the IRS Helps Taxpayers and Assists Victims Combating Identity Theft and Online Fraud Justin McCarty January, 2014 What is identity theft? Identity theft occurs when someone uses your personal information
How the IRS Helps Taxpayers and Assists Victims Combating Identity Theft and Online Fraud Justin McCarty January, 2014 What is identity theft? Identity theft occurs when someone uses your personal information
SECURING SELF-SERVICE PASSWORD RESET
 SECURING SELF-SERVICE PASSWORD RESET FUNCTIONALITY IN WEB APPLICATIONS David A. Shpritz July, 2010 INTRODUCTION Many web applications requiring user authentication also provide self-service password reset
SECURING SELF-SERVICE PASSWORD RESET FUNCTIONALITY IN WEB APPLICATIONS David A. Shpritz July, 2010 INTRODUCTION Many web applications requiring user authentication also provide self-service password reset
Modernized e-file (MeF) October 2014
 Modernized e-file (MeF) Update October 2014 Agenda Filing Season 2014 A Look Back New for Filing Season 2015 ACA Information Return (AIR) System 2 Filing Season 2014 A Look Back 3 Filing Season 2014 -
Modernized e-file (MeF) Update October 2014 Agenda Filing Season 2014 A Look Back New for Filing Season 2015 ACA Information Return (AIR) System 2 Filing Season 2014 A Look Back 3 Filing Season 2014 -
General tips for increasing the security of using First Investment Bank's internet banking
 General tips for increasing the security of using First Investment Bank's internet banking Dear Clients, First Investment Bank (Fibank, the Bank) provides you with high level of protection and security
General tips for increasing the security of using First Investment Bank's internet banking Dear Clients, First Investment Bank (Fibank, the Bank) provides you with high level of protection and security
FFIEC CONSUMER GUIDANCE
 FFIEC CONSUMER GUIDANCE Important Facts About Your Account Authentication Online Banking & Multi-factor authentication and layered security are helping assure safe Internet transactions for banks and their
FFIEC CONSUMER GUIDANCE Important Facts About Your Account Authentication Online Banking & Multi-factor authentication and layered security are helping assure safe Internet transactions for banks and their
NJ1065 e-file Software Developers Handbook
 New Jersey Division of Revenue and Enterprise Services NJ1065 e-file Software Developers Handbook STATE ELECTRONIC FILING PROGRAM State of New Jersey Division of Revenue and Enterprise Services James J.
New Jersey Division of Revenue and Enterprise Services NJ1065 e-file Software Developers Handbook STATE ELECTRONIC FILING PROGRAM State of New Jersey Division of Revenue and Enterprise Services James J.
H&R Block Digital Tax Preparation, Online, and Mobile Application Privacy Practices and Principles
 Privacy Notice H&R Block Digital Tax Preparation, Online, and Mobile Application Privacy Practices and Principles Protecting your information is important to us. The following guidelines set forth our
Privacy Notice H&R Block Digital Tax Preparation, Online, and Mobile Application Privacy Practices and Principles Protecting your information is important to us. The following guidelines set forth our
Identity Theft and Online Fraud IRS Efforts to Protect Taxpayers. Privacy, Governmental Liaison and Disclosure May 9, 2012
 Identity Theft and Online Fraud IRS Efforts to Protect Taxpayers Privacy, Governmental Liaison and Disclosure May 9, 2012 Today s presentation How identity theft is a threat to the taxpayer What IRS is
Identity Theft and Online Fraud IRS Efforts to Protect Taxpayers Privacy, Governmental Liaison and Disclosure May 9, 2012 Today s presentation How identity theft is a threat to the taxpayer What IRS is
WRITTEN TESTIMONY OF JOHN A
 WRITTEN TESTIMONY OF JOHN A. KOSKINEN COMMISSIONER INTERNAL REVENUE SERVICE BEFORE THE SENATE FINANCE COMMITTEE ON UNAUTHORIZED ATTEMPTS TO ACCESS TAXPAYER DATA JUNE 2, 2015 Chairman Hatch, Ranking Member
WRITTEN TESTIMONY OF JOHN A. KOSKINEN COMMISSIONER INTERNAL REVENUE SERVICE BEFORE THE SENATE FINANCE COMMITTEE ON UNAUTHORIZED ATTEMPTS TO ACCESS TAXPAYER DATA JUNE 2, 2015 Chairman Hatch, Ranking Member
Arkansas Small Business Forum. IRS Identity Theft Prevention Efforts
 Arkansas Small Business Forum IRS Identity Theft Prevention Efforts Contact Information Name: Gregory Metcalf Phone Number: 501-396-5912 Email Address: gregory.o.metcalf@irs.gov A persistent threat to
Arkansas Small Business Forum IRS Identity Theft Prevention Efforts Contact Information Name: Gregory Metcalf Phone Number: 501-396-5912 Email Address: gregory.o.metcalf@irs.gov A persistent threat to
INFORMATION FOR FED/STATE DEVELOPMENT OF MODERNIZED E-FILE FOR BUSINESS INCOME TAX
 Commonwealth of Kentucky Kentucky Department of Revenue INFORMATION FOR FED/STATE DEVELOPMENT OF MODERNIZED E-FILE FOR BUSINESS INCOME TAX KY PUBLICATION 4163 Software Developer s Guide Tax Year 2015 Processing
Commonwealth of Kentucky Kentucky Department of Revenue INFORMATION FOR FED/STATE DEVELOPMENT OF MODERNIZED E-FILE FOR BUSINESS INCOME TAX KY PUBLICATION 4163 Software Developer s Guide Tax Year 2015 Processing
ACCESS TO ACCOUNTS VIA THE INTERNET.
 Internet Banking Service Agreement Terms and Conditions This Internet Banking Services Agreement Terms and Conditions (Agreement) between you and Glacier Bank govern the use First Security Bank, a Division
Internet Banking Service Agreement Terms and Conditions This Internet Banking Services Agreement Terms and Conditions (Agreement) between you and Glacier Bank govern the use First Security Bank, a Division
MONTSERRAT COLLEGE OF ART WRITTEN INFORMATION SECURITY POLICY (WISP)
 MONTSERRAT COLLEGE OF ART WRITTEN INFORMATION SECURITY POLICY (WISP) 201 CMR 17.00 Standards for the Protection of Personal Information Of Residents of the Commonwealth of Massachusetts Revised April 28,
MONTSERRAT COLLEGE OF ART WRITTEN INFORMATION SECURITY POLICY (WISP) 201 CMR 17.00 Standards for the Protection of Personal Information Of Residents of the Commonwealth of Massachusetts Revised April 28,
CITY OF MARQUETTE, MICHIGAN CITY COMMISSION POLICY
 CITY OF MARQUETTE, MICHIGAN CITY COMMISSION POLICY Policy Number: 2008-02 Date Adopted: October 27, 2008 Department: Administrative SUBJECT: IDENTITY THEFT PREVENTION PROGRAM I. OBJECTIVE: A. To protect
CITY OF MARQUETTE, MICHIGAN CITY COMMISSION POLICY Policy Number: 2008-02 Date Adopted: October 27, 2008 Department: Administrative SUBJECT: IDENTITY THEFT PREVENTION PROGRAM I. OBJECTIVE: A. To protect
Business ebanking - User Sign On & Set Up
 About Sign On Business ebanking has two authentication methods that reduce the risk of online identity theft: secure token authentication and out-of-band authentication. The authentication method companies
About Sign On Business ebanking has two authentication methods that reduce the risk of online identity theft: secure token authentication and out-of-band authentication. The authentication method companies
How IRS Protects Taxpayers and Helps Victims of Identity Theft. Global Identity Summit September 16, 2014
 How IRS Protects Taxpayers and Helps Victims of Identity Theft Global Identity Summit September 16, 2014 Identity theft (IDT) is a serious threat Federal Trade Commission hears from more than 20,000 consumers
How IRS Protects Taxpayers and Helps Victims of Identity Theft Global Identity Summit September 16, 2014 Identity theft (IDT) is a serious threat Federal Trade Commission hears from more than 20,000 consumers
How to complete the Secure Internet Site Declaration (SISD) form
 1 How to complete the Secure Internet Site Declaration (SISD) form The following instructions are designed to assist you in completing the SISD form that forms part of your Merchant application. Once completed,
1 How to complete the Secure Internet Site Declaration (SISD) form The following instructions are designed to assist you in completing the SISD form that forms part of your Merchant application. Once completed,
How to Become an Authorized IRS e-file Provider
 How to Become an Authorized IRS e-file Provider Brian Wozniak IRS Stakeholder Liaison IRS Communications Liaison & Disclosure Office Agenda Explain the e-file mandate Create an e-services account Submit
How to Become an Authorized IRS e-file Provider Brian Wozniak IRS Stakeholder Liaison IRS Communications Liaison & Disclosure Office Agenda Explain the e-file mandate Create an e-services account Submit
What s New Collection Fall 2015
 What s New Collection Fall 2015 Anita Douglas Senior Stakeholder Liaison December 2, 2015 1 What s New Collection Compliance realignment What s Collection look like today Federal Tax Deposit Alerts Early
What s New Collection Fall 2015 Anita Douglas Senior Stakeholder Liaison December 2, 2015 1 What s New Collection Compliance realignment What s Collection look like today Federal Tax Deposit Alerts Early
Tax-Related Identity Theft: IRS Efforts to Assist Victims and Combat IDT Fraud
 Tax-Related Identity Theft: IRS Efforts to Assist Victims and Combat IDT Fraud Glenn Gizzi Senior Stakeholder Liaison Marc Standig Enrolled Agent What is tax-related identity theft? Tax-related identity
Tax-Related Identity Theft: IRS Efforts to Assist Victims and Combat IDT Fraud Glenn Gizzi Senior Stakeholder Liaison Marc Standig Enrolled Agent What is tax-related identity theft? Tax-related identity
Identity Theft and Tax Administration
 PREPARED STATEMENT OF BETH TUCKER IRS DEPUTY COMMISSIONER FOR OPERATIONS SUPPORT BEFORE SUBCOMMITTEE ON FISCAL RESPONSIBILITY AND ECONOMIC GROWTH SENATE FINANCE COMMITTEE ON IDENTITY THEFT MAY 25, 2011
PREPARED STATEMENT OF BETH TUCKER IRS DEPUTY COMMISSIONER FOR OPERATIONS SUPPORT BEFORE SUBCOMMITTEE ON FISCAL RESPONSIBILITY AND ECONOMIC GROWTH SENATE FINANCE COMMITTEE ON IDENTITY THEFT MAY 25, 2011
SAMPLE TEMPLATE. Massachusetts Written Information Security Plan
 SAMPLE TEMPLATE Massachusetts Written Information Security Plan Developed by: Jamy B. Madeja, Esq. Erik Rexford 617-227-8410 jmadeja@buchananassociates.com Each business is required by Massachusetts law
SAMPLE TEMPLATE Massachusetts Written Information Security Plan Developed by: Jamy B. Madeja, Esq. Erik Rexford 617-227-8410 jmadeja@buchananassociates.com Each business is required by Massachusetts law
Your Single Source. for credit, debit and pre-paid services. Fraud Risk and Mitigation
 Your Single Source for credit, debit and pre-paid services Fraud Risk and Mitigation Agenda Types of Fraud Fraud Identification Notifications Next Steps 11/8/2013 2 Types of Fraud Lost and Stolen Cards
Your Single Source for credit, debit and pre-paid services Fraud Risk and Mitigation Agenda Types of Fraud Fraud Identification Notifications Next Steps 11/8/2013 2 Types of Fraud Lost and Stolen Cards
State of Arkansas Department of Finance and Administration Income Tax Administration
 State of Arkansas Department of Finance and Administration Income Tax Administration Publication AR1345 Handbook for Authorized Arkansas e-file Providers Of Individual Income Tax Returns Tax Year 2015
State of Arkansas Department of Finance and Administration Income Tax Administration Publication AR1345 Handbook for Authorized Arkansas e-file Providers Of Individual Income Tax Returns Tax Year 2015
BUSINESS ONLINE BANKING AGREEMENT
 BUSINESS ONLINE BANKING AGREEMENT This Business Online Banking Agreement ("Agreement") establishes the terms and conditions for Business Online Banking Services ( Service(s) ) provided by Mechanics Bank
BUSINESS ONLINE BANKING AGREEMENT This Business Online Banking Agreement ("Agreement") establishes the terms and conditions for Business Online Banking Services ( Service(s) ) provided by Mechanics Bank
Individual Income Tax Software Developer and Transmitter Guide Tax Year 2013
 Individual Income Tax Software Developer and Transmitter Guide Tax Year 2013 1 Illinois Changes - IL-1040 Electronic Filing Program IL-1040 Changes The personal exemption amount for taxpayers and their
Individual Income Tax Software Developer and Transmitter Guide Tax Year 2013 1 Illinois Changes - IL-1040 Electronic Filing Program IL-1040 Changes The personal exemption amount for taxpayers and their
Briefly describe the #1 problem you have encountered with implementing Multi-Factor Authentication.
 Polling Question Briefly describe the #1 problem you have encountered with implementing Multi-Factor Authentication. Please type in your response. This poll will close promptly at 1:00 pm CDT Getting the
Polling Question Briefly describe the #1 problem you have encountered with implementing Multi-Factor Authentication. Please type in your response. This poll will close promptly at 1:00 pm CDT Getting the
PRIVACY POLICY (Update 1) FOR ONLINE GIVING FOR THE UNITED METHODIST CHURCH
 A. Overview PRIVACY POLICY (Update 1) FOR ONLINE GIVING FOR THE UNITED METHODIST CHURCH GENERAL COUNCIL ON FINANCE AND ADMINISTRATION OF THE UNITED METHODIST CHURCH, INC., an Illinois corporation 1 Music
A. Overview PRIVACY POLICY (Update 1) FOR ONLINE GIVING FOR THE UNITED METHODIST CHURCH GENERAL COUNCIL ON FINANCE AND ADMINISTRATION OF THE UNITED METHODIST CHURCH, INC., an Illinois corporation 1 Music
Member FAQ. General Information: Security:
 General Information: Security: Why did you change Robins Federal Online Banking? Great question! We listened to an overwhelming response from you, our members that we needed to make these changes. We are
General Information: Security: Why did you change Robins Federal Online Banking? Great question! We listened to an overwhelming response from you, our members that we needed to make these changes. We are
Maryland MeF Test Package for Authorized e-file Providers
 2015 Maryland MeF Test Package for Authorized e-file Providers for Corporation and Pass-Through Entity Income tax returns October 2015 Revenue Administration Division Annapolis, MD 21411-0001 Peter Franchot,
2015 Maryland MeF Test Package for Authorized e-file Providers for Corporation and Pass-Through Entity Income tax returns October 2015 Revenue Administration Division Annapolis, MD 21411-0001 Peter Franchot,
News Release Date: 5/14/14
 News Release Date: 5/14/14 Disclosure and Use of Client Information Allowed Disclosures, Consent Requirements, and the Affordable Care Act IRC 7216 and 6713 Internal Revenue Code section 7216 sets forth
News Release Date: 5/14/14 Disclosure and Use of Client Information Allowed Disclosures, Consent Requirements, and the Affordable Care Act IRC 7216 and 6713 Internal Revenue Code section 7216 sets forth
Individual Income Tax Software Developer and Transmitter Guide Tax Year 2014
 Individual Income Tax Software Developer and Transmitter Guide Tax Year 2014 1 Illinois Changes - IL-1040 Electronic Filing Program IL-1040 Changes A checkbox for Veterans Affairs has been added and the
Individual Income Tax Software Developer and Transmitter Guide Tax Year 2014 1 Illinois Changes - IL-1040 Electronic Filing Program IL-1040 Changes A checkbox for Veterans Affairs has been added and the
PROGRAM TO PREVENT, DETECT & MITIGATE IDENTITY THEFT
 Office of Employee Benefits Administrative Manual PROGRAM TO PREVENT, DETECT & MITIGATE IDENTITY THEFT 150 EFFECTIVE DATE: AUGUST 1, 2009 REVISION DATE: PURPOSE: Ensure that the Office of Employee Benefits
Office of Employee Benefits Administrative Manual PROGRAM TO PREVENT, DETECT & MITIGATE IDENTITY THEFT 150 EFFECTIVE DATE: AUGUST 1, 2009 REVISION DATE: PURPOSE: Ensure that the Office of Employee Benefits
Sound Business Practices for Businesses to Mitigate Corporate Account Takeover
 Sound Business Practices for Businesses to Mitigate Corporate Account Takeover This white paper provides sound business practices for companies to implement to safeguard against Corporate Account Takeover.
Sound Business Practices for Businesses to Mitigate Corporate Account Takeover This white paper provides sound business practices for companies to implement to safeguard against Corporate Account Takeover.
Identity Theft Prevention Policy
 Eastern Kentucky University Policy and Regulation Library 6.#.#P Volume 6, Volume Title: Financial Affairs Chapter #, Chapter Title Section #, Name: Identity Theft Prevention Policy Approval Authority:
Eastern Kentucky University Policy and Regulation Library 6.#.#P Volume 6, Volume Title: Financial Affairs Chapter #, Chapter Title Section #, Name: Identity Theft Prevention Policy Approval Authority:
Colorado Online Tax Returns - How to Avoid Perjury
 Taxpayer Service Division Colorado Department of Revenue September 25, 2014 (Draft) Software Developers Handbook Business Income Tax (Calendar Year 2015) I COLORADO DEPARTMENT OF REVENUE TABLE OF CONTENTS
Taxpayer Service Division Colorado Department of Revenue September 25, 2014 (Draft) Software Developers Handbook Business Income Tax (Calendar Year 2015) I COLORADO DEPARTMENT OF REVENUE TABLE OF CONTENTS
Client Advisory October 2009. Data Security Law MGL Chapter 93H and 201 CMR 17.00
 Client Advisory October 2009 Data Security Law MGL Chapter 93H and 201 CMR 17.00 For a discussion of these and other issues, please visit the update on our website at /law. To receive mailings via email,
Client Advisory October 2009 Data Security Law MGL Chapter 93H and 201 CMR 17.00 For a discussion of these and other issues, please visit the update on our website at /law. To receive mailings via email,
June 2015 Newsletter
 June 2015 Newsletter News From Silver Bridge CPAs TAX TIPS & TRICKS Consider Setting Up an Idaho Medical Savings Account! The state of Idaho has established a tax deduction for contributions made to an
June 2015 Newsletter News From Silver Bridge CPAs TAX TIPS & TRICKS Consider Setting Up an Idaho Medical Savings Account! The state of Idaho has established a tax deduction for contributions made to an
990-EZ, 990, 990-T and 990-PF Information Worksheet 2010
 990-EZ, 990, 990-T and 990-PF Information Worksheet 2010 Part I ' Identifying Information Employer Identification Number..... 20-1931001 Name............................. SPIRIT OF SHARING Doing Business
990-EZ, 990, 990-T and 990-PF Information Worksheet 2010 Part I ' Identifying Information Employer Identification Number..... 20-1931001 Name............................. SPIRIT OF SHARING Doing Business
Tax-Related Identity Theft: IRS Efforts to Assist Victims and Combat IDT Fraud. Brian Wozniak IRS Stakeholder Liaison
 Tax-Related Identity Theft: IRS Efforts to Assist Victims and Combat IDT Fraud Brian Wozniak IRS Stakeholder Liaison November 4, 2015 1 Prevention and Detection In recent years, the IRS has made numerous
Tax-Related Identity Theft: IRS Efforts to Assist Victims and Combat IDT Fraud Brian Wozniak IRS Stakeholder Liaison November 4, 2015 1 Prevention and Detection In recent years, the IRS has made numerous
Section 5 Identify Theft Red Flags and Address Discrepancy Procedures Index
 Index Section 5.1 Purpose.... 2 Section 5.2 Definitions........2 Section 5.3 Validation Information.....2 Section 5.4 Procedures for Opening New Accounts....3 Section 5.5 Procedures for Existing Accounts...
Index Section 5.1 Purpose.... 2 Section 5.2 Definitions........2 Section 5.3 Validation Information.....2 Section 5.4 Procedures for Opening New Accounts....3 Section 5.5 Procedures for Existing Accounts...
2015 SPEC Partner Filing Season Readiness
 Wage & Investment 2015 SPEC Partner Filing Season Readiness Publication 5159 (10-2014) Catalog Number 66732B Department of the Treasury Internal Revenue Service www.irs.gov SPEC Mission Message from Director,
Wage & Investment 2015 SPEC Partner Filing Season Readiness Publication 5159 (10-2014) Catalog Number 66732B Department of the Treasury Internal Revenue Service www.irs.gov SPEC Mission Message from Director,
Red Flag Policy and Procedures for Alexander Orthopaedic Associates
 Red Flag Policy and Procedures for Alexander Orthopaedic Associates The Identify Theft Prevention Program developed by Alexander Medical Group LLC dba Alexander Orthopaedic Associates referred throughout
Red Flag Policy and Procedures for Alexander Orthopaedic Associates The Identify Theft Prevention Program developed by Alexander Medical Group LLC dba Alexander Orthopaedic Associates referred throughout
Authorized. User Agreement
 Authorized User Agreement CareAccord Health Information Exchange (HIE) Table of Contents Authorized User Agreement... 3 CareAccord Health Information Exchange (HIE) Polices and Procedures... 5 SECTION
Authorized User Agreement CareAccord Health Information Exchange (HIE) Table of Contents Authorized User Agreement... 3 CareAccord Health Information Exchange (HIE) Polices and Procedures... 5 SECTION
MOBILE BANKING. Why should I use Mobile Banking?
 MOBILE BANKING What is Mobile Banking? With Mobile Banking, you can access your account, conduct transfers, and pay and manage bills from any mobile device that has web browsing capabilities and a data
MOBILE BANKING What is Mobile Banking? With Mobile Banking, you can access your account, conduct transfers, and pay and manage bills from any mobile device that has web browsing capabilities and a data
Identity Theft Prevention Program. Approved by the Arizona Board of Regents on May 1, 2009
 Identity Theft Prevention Program Approved by the Arizona Board of Regents on May 1, 2009 I. Purpose & Scope This Program was developed pursuant to the Federal Trade Commission s ( FTC ) Red Flag Rules
Identity Theft Prevention Program Approved by the Arizona Board of Regents on May 1, 2009 I. Purpose & Scope This Program was developed pursuant to the Federal Trade Commission s ( FTC ) Red Flag Rules
Federal and State Government Identity Theft and Protection Initiatives
 Federal and State Government Identity Theft and Protection Initiatives Jill Runow May 1, 2012 Identity theft: It is not a new problem 2 The most misused SSN of all time Happened more than 70 years ago
Federal and State Government Identity Theft and Protection Initiatives Jill Runow May 1, 2012 Identity theft: It is not a new problem 2 The most misused SSN of all time Happened more than 70 years ago
Infrastructure Our Tax Securing Presented by:
 Securing Our Tax Infrastructure Security and Fraud in the efile Age FTA Technology Conference August 15, 2011 Presented by: Clinton Mugge Joan Barr 8/15/11 1 [ Agenda ] 1 2 3 4 Security Threats Impact
Securing Our Tax Infrastructure Security and Fraud in the efile Age FTA Technology Conference August 15, 2011 Presented by: Clinton Mugge Joan Barr 8/15/11 1 [ Agenda ] 1 2 3 4 Security Threats Impact
Transcript Tax Fraud & Identity Theft - Protecting your clients and yourself Webinar
 Slide 1 Good morning and welcome to today s webinar. I am Larry Womac and I will be your presenter. With me are our subject matter experts Joseph Adversalo and Nepoh Lappia. Slide 2 Today s webinar is
Slide 1 Good morning and welcome to today s webinar. I am Larry Womac and I will be your presenter. With me are our subject matter experts Joseph Adversalo and Nepoh Lappia. Slide 2 Today s webinar is
BBVA Wallet Application Privacy Policy
 BBVA Wallet Application Privacy Policy Effective date: September 14, 2015 This Privacy Policy describes our practices related to the use, storage and disclosure of information we collect from or about
BBVA Wallet Application Privacy Policy Effective date: September 14, 2015 This Privacy Policy describes our practices related to the use, storage and disclosure of information we collect from or about
Guideline on Access Control
 CMSGu2011-08 Mauritian Computer Emergency Response Team CERT-MU SECURITY GUIDELINE 2011-02 Enhancing Cyber Security in Mauritius Guideline on Access Control National Computer Board Mauritius Version 1.0
CMSGu2011-08 Mauritian Computer Emergency Response Team CERT-MU SECURITY GUIDELINE 2011-02 Enhancing Cyber Security in Mauritius Guideline on Access Control National Computer Board Mauritius Version 1.0
DailyMailz may collect and process the following personal information about you:
 Privacy Policy DailyMailz is committed to preserving the privacy of all visitors to its website www.dailymailz.nl ("Website"). This privacy policy along with DailyMailz s terms and conditions of use and
Privacy Policy DailyMailz is committed to preserving the privacy of all visitors to its website www.dailymailz.nl ("Website"). This privacy policy along with DailyMailz s terms and conditions of use and
FINAL May 2005. Guideline on Security Systems for Safeguarding Customer Information
 FINAL May 2005 Guideline on Security Systems for Safeguarding Customer Information Table of Contents 1 Introduction 1 1.1 Purpose of Guideline 1 2 Definitions 2 3 Internal Controls and Procedures 2 3.1
FINAL May 2005 Guideline on Security Systems for Safeguarding Customer Information Table of Contents 1 Introduction 1 1.1 Purpose of Guideline 1 2 Definitions 2 3 Internal Controls and Procedures 2 3.1
Identity Theft Prevention Program
 Smyth County Policy Identity Theft Prevention Program Purpose The purpose of the program is to establish an Identity Theft Prevention Program designed to detect, prevent and mitigate identity theft in
Smyth County Policy Identity Theft Prevention Program Purpose The purpose of the program is to establish an Identity Theft Prevention Program designed to detect, prevent and mitigate identity theft in
The World of Identity Theft from the IRS s Point of View
 1 The World of Identity Theft from the IRS s Point of View Becky Chiaramida, Director IRS Office of Privacy, Governmental Liaison and Disclosure October 2, 2012 Identity theft: It is not a new problem
1 The World of Identity Theft from the IRS s Point of View Becky Chiaramida, Director IRS Office of Privacy, Governmental Liaison and Disclosure October 2, 2012 Identity theft: It is not a new problem
Oklahoma Tax Commission
 Oklahoma Tax Commission Electronic Filer Handbook Individual Income Tax Tax Year 2015 August 25, 2015 Table of Contents Contents Table of Contents... 1 Introduction... 2 Publications... 3 Internal Revenue
Oklahoma Tax Commission Electronic Filer Handbook Individual Income Tax Tax Year 2015 August 25, 2015 Table of Contents Contents Table of Contents... 1 Introduction... 2 Publications... 3 Internal Revenue
2014 Handbook for Authorized e-file Providers FTB Pub. 1345
 2014 Handbook for Authorized e-file Providers FTB Pub. 1345 State of California Franchise Tax Board ftb.ca.gov Table of Contents Table of Contents... 2 Section 1 Introduction... 3 1.1 Welcome... 3 1.2
2014 Handbook for Authorized e-file Providers FTB Pub. 1345 State of California Franchise Tax Board ftb.ca.gov Table of Contents Table of Contents... 2 Section 1 Introduction... 3 1.1 Welcome... 3 1.2
BANKOH BUSINESS CONNECTIONS WIRE TRANSFER GUIDE
 BANKOH BUSINESS CONNECTIONS WIRE TRANSFER GUIDE Revision 2/2013 1 of 35 Contents GENERAL INFORMATION... 3 Wire Transfers... 3 Types of Wires... 3 Wire Templates... 3 Bankoh Business Connections Wire Cut-off
BANKOH BUSINESS CONNECTIONS WIRE TRANSFER GUIDE Revision 2/2013 1 of 35 Contents GENERAL INFORMATION... 3 Wire Transfers... 3 Types of Wires... 3 Wire Templates... 3 Bankoh Business Connections Wire Cut-off
Identity Theft Prevention Program
 The University of North Carolina at Chapel Hill Identity Theft Prevention Program The Board of Trustees of The University of North Carolina at Chapel Hill (the University ) adopts this Identity Theft Prevention
The University of North Carolina at Chapel Hill Identity Theft Prevention Program The Board of Trustees of The University of North Carolina at Chapel Hill (the University ) adopts this Identity Theft Prevention
Helping the Identity Theft Victim
 Helping the Identity Theft Victim Seminar Objectives Increase awareness of how to help IDT victims Improve understanding of Taxpayer Protection Program, Identity Protection Specialized Unit, and Identity
Helping the Identity Theft Victim Seminar Objectives Increase awareness of how to help IDT victims Improve understanding of Taxpayer Protection Program, Identity Protection Specialized Unit, and Identity
Replicated Website & Back-Office Privacy Policy
 Replicated Website & Back-Office Privacy Policy EFFECTIVE DECEMBER 1, 2015 WEALTH GENERATORS LLC 12 SOUTH 400 WEST SALT LAKE CITY UT 84101 801.939.3580 WWW.WEALTHGENERATORS.COM Wealth Generators LLC Replicated
Replicated Website & Back-Office Privacy Policy EFFECTIVE DECEMBER 1, 2015 WEALTH GENERATORS LLC 12 SOUTH 400 WEST SALT LAKE CITY UT 84101 801.939.3580 WWW.WEALTHGENERATORS.COM Wealth Generators LLC Replicated
ONLINE BANKING SECURITY TIPS FOR OUR BUSINESS CLIENTS
 $ ONLINE BANKING SECURITY TIPS FOR OUR BUSINESS CLIENTS Boston Private Bank & Trust Company takes great care to safeguard the security of your Online Banking transactions. In addition to our robust security
$ ONLINE BANKING SECURITY TIPS FOR OUR BUSINESS CLIENTS Boston Private Bank & Trust Company takes great care to safeguard the security of your Online Banking transactions. In addition to our robust security
MOBILE DEPOSIT AGREEMENT AND DISCLOSURE ONLINE BANKING AGREEMENT ADDENDUM
 MOBILE DEPOSIT AGREEMENT AND DISCLOSURE ONLINE BANKING AGREEMENT ADDENDUM This Addendum ( Addendum ) to the Citizens State Bank of Paola Online Banking Agreement between you and Citizens State Bank of
MOBILE DEPOSIT AGREEMENT AND DISCLOSURE ONLINE BANKING AGREEMENT ADDENDUM This Addendum ( Addendum ) to the Citizens State Bank of Paola Online Banking Agreement between you and Citizens State Bank of
Information Technology Security Policies
 Information Technology Security Policies Randolph College 2500 Rivermont Ave. Lynchburg, VA 24503 434-947- 8700 Revised 01/10 Page 1 Introduction Computer information systems and networks are an integral
Information Technology Security Policies Randolph College 2500 Rivermont Ave. Lynchburg, VA 24503 434-947- 8700 Revised 01/10 Page 1 Introduction Computer information systems and networks are an integral
BUSINESS ASSOCIATE AGREEMENT HIPAA Protected Health Information
 BUSINESS ASSOCIATE AGREEMENT HIPAA Protected Health Information I. PREAMBLE ( Covered Entity ) and ( Business Associate ) (jointly the Parties ) wish to enter into an Agreement to comply with the requirements
BUSINESS ASSOCIATE AGREEMENT HIPAA Protected Health Information I. PREAMBLE ( Covered Entity ) and ( Business Associate ) (jointly the Parties ) wish to enter into an Agreement to comply with the requirements
North American Electric Reliability Corporation: Critical Infrastructure Protection, Version 5 (NERC-CIP V5)
 Whitepaper North American Electric Reliability Corporation: Critical Infrastructure Protection, Version 5 (NERC-CIP V5) NERC-CIP Overview The North American Electric Reliability Corporation (NERC) is a
Whitepaper North American Electric Reliability Corporation: Critical Infrastructure Protection, Version 5 (NERC-CIP V5) NERC-CIP Overview The North American Electric Reliability Corporation (NERC) is a
BUSINESS CHICKS, INC. Privacy Policy
 BUSINESS CHICKS, INC. Privacy Policy Welcome to businesschicks.com, the online and mobile service of Business Chicks, Inc. ( Company, we, or us ). Our Privacy Policy explains how we collect, use, disclose,
BUSINESS CHICKS, INC. Privacy Policy Welcome to businesschicks.com, the online and mobile service of Business Chicks, Inc. ( Company, we, or us ). Our Privacy Policy explains how we collect, use, disclose,
IRS Tax Return Transcript Request Process
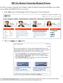 IRS Tax Return Transcript Request Process Tax filers can request a transcript, free of charge, of their Tax Return Transcript from the IRS in one of three ways available on the IRS Web site at www.irs.gov.
IRS Tax Return Transcript Request Process Tax filers can request a transcript, free of charge, of their Tax Return Transcript from the IRS in one of three ways available on the IRS Web site at www.irs.gov.
COUNCIL POLICY NO. C-13
 COUNCIL POLICY NO. C-13 TITLE: POLICY: Identity Theft Prevention Program See attachment. REFERENCE: Salem City Council Finance Committee Report dated November 7, 2011, Agenda Item No. 3 (a) Supplants Administrative
COUNCIL POLICY NO. C-13 TITLE: POLICY: Identity Theft Prevention Program See attachment. REFERENCE: Salem City Council Finance Committee Report dated November 7, 2011, Agenda Item No. 3 (a) Supplants Administrative
HIPAA Security. 2 Security Standards: Administrative Safeguards. Security Topics
 HIPAA Security SERIES Security Topics 1. Security 101 for Covered Entities 5. 2. Security Standards - Organizational, Security Policies Standards & Procedures, - Administrative and Documentation Safeguards
HIPAA Security SERIES Security Topics 1. Security 101 for Covered Entities 5. 2. Security Standards - Organizational, Security Policies Standards & Procedures, - Administrative and Documentation Safeguards
Staying Safe after the Anthem Breach. Dartmouth College 3/25/15 ITS Security Team
 Staying Safe after the Anthem Breach Dartmouth College 3/25/15 ITS Security Team Anthem Breach Reported on Feb 4, 2015 80 million records exposed Current and former members since 2004 Data exposed: o Names
Staying Safe after the Anthem Breach Dartmouth College 3/25/15 ITS Security Team Anthem Breach Reported on Feb 4, 2015 80 million records exposed Current and former members since 2004 Data exposed: o Names
FREQUENTLY ASKED QUESTIONS
 FREQUENTLY ASKED QUESTIONS 1. What is the YES BANK MasterCard SecureCode? The MasterCard SecureCode is a service offered by YES BANK in partnership with MasterCard. This authentication is basically a password
FREQUENTLY ASKED QUESTIONS 1. What is the YES BANK MasterCard SecureCode? The MasterCard SecureCode is a service offered by YES BANK in partnership with MasterCard. This authentication is basically a password
MONROE COUNTY WATER AUTHORITY IDENTITY THEFT PREVENTION POLICY REVISED MARCH 2014
 MONROE COUNTY WATER AUTHORITY IDENTITY THEFT PREVENTION POLICY REVISED MARCH 2014 Section 41.90 of Title 12 of the Code of Federal Regulations (the Regulations ) requires every utility that offers or maintains
MONROE COUNTY WATER AUTHORITY IDENTITY THEFT PREVENTION POLICY REVISED MARCH 2014 Section 41.90 of Title 12 of the Code of Federal Regulations (the Regulations ) requires every utility that offers or maintains
FFIEC BUSINESS ACCOUNT GUIDANCE
 FFIEC BUSINESS ACCOUNT GUIDANCE New financial standards will assist credit unions and business account holders to make online banking safer and more secure from account hijacking and unauthorized funds
FFIEC BUSINESS ACCOUNT GUIDANCE New financial standards will assist credit unions and business account holders to make online banking safer and more secure from account hijacking and unauthorized funds
IDENTITY THEFT PREVENTION PROGRAM
 IDENTITY THEFT PREVENTION PROGRAM Implemented October 2009 Page 1 Table of Contents Background... 3 Purpose... 3 Definitions... 3 Pretext Calling... 4 Receiving Telephone Calls... 5 Change of Address...
IDENTITY THEFT PREVENTION PROGRAM Implemented October 2009 Page 1 Table of Contents Background... 3 Purpose... 3 Definitions... 3 Pretext Calling... 4 Receiving Telephone Calls... 5 Change of Address...
CCH esign. Quick Start Guide
 CCH esign Quick Start Guide December 2015 2015 CCH Incorporated and its affiliates and licensors. All rights reserved. Material in this publication may not be reproduced or transmitted, in any form or
CCH esign Quick Start Guide December 2015 2015 CCH Incorporated and its affiliates and licensors. All rights reserved. Material in this publication may not be reproduced or transmitted, in any form or
DELAWARE DIVISION OF REVENUE 2014-2015 DELAWARE BUSINESS MEF E-FILE HANDBOOK. for Software Developers, Transmitters and EROs who file: October 2015
 DELAWARE DIVISION OF REVENUE 2014-2015 DELAWARE BUSINESS MEF E-FILE HANDBOOK for Software Developers, Transmitters and EROs who file: Delaware corporation and pass-through entity tax returns via the Federal/state
DELAWARE DIVISION OF REVENUE 2014-2015 DELAWARE BUSINESS MEF E-FILE HANDBOOK for Software Developers, Transmitters and EROs who file: Delaware corporation and pass-through entity tax returns via the Federal/state
Standard: Information Security Incident Management
 Standard: Information Security Incident Management Page 1 Executive Summary California State University Information Security Policy 8075.00 states security incidents involving loss, damage or misuse of
Standard: Information Security Incident Management Page 1 Executive Summary California State University Information Security Policy 8075.00 states security incidents involving loss, damage or misuse of
CASHMERE VALLEY BANK ELECTRONIC BANKING AGREEMENT AND DISCLOSURE STATEMENT
 CASHMERE VALLEY BANK ELECTRONIC BANKING AGREEMENT AND DISCLOSURE STATEMENT In this Electronic Banking Agreement and Disclosure, Agreement, "you", "your", and "yours" refers to each person that will be
CASHMERE VALLEY BANK ELECTRONIC BANKING AGREEMENT AND DISCLOSURE STATEMENT In this Electronic Banking Agreement and Disclosure, Agreement, "you", "your", and "yours" refers to each person that will be
Online Banking Agreement
 Online Banking Agreement The Online Banking Agreement (Agreement) states the terms and conditions for OneWest Bank's Online Banking services. In this Agreement, "you", "your", and "yours" refer to the
Online Banking Agreement The Online Banking Agreement (Agreement) states the terms and conditions for OneWest Bank's Online Banking services. In this Agreement, "you", "your", and "yours" refer to the
Electronic Fraud Awareness Advisory
 Electronic Fraud Awareness Advisory Indiana Bankers Association Fraud Awareness Task Force February, 2012 Electronic Fraud Awareness Advisory Purpose/Summary The Indiana Bankers Association (IBA) was involved
Electronic Fraud Awareness Advisory Indiana Bankers Association Fraud Awareness Task Force February, 2012 Electronic Fraud Awareness Advisory Purpose/Summary The Indiana Bankers Association (IBA) was involved
University Identity Theft and Detection Program (NEW) All Campuses and All Service Providers Subject to the Red Flags Rule
 NUMBER: BUSF 4.12 SECTION: SUBJECT: Finance and Planning University Identity Theft and Detection Program (NEW) DATE: March 3, 2011 Policy for: Procedure for: Authorized by: Issued by: All Campuses and
NUMBER: BUSF 4.12 SECTION: SUBJECT: Finance and Planning University Identity Theft and Detection Program (NEW) DATE: March 3, 2011 Policy for: Procedure for: Authorized by: Issued by: All Campuses and
FFIEC Supplemental Guidance to Authentication in an Internet Banking Environment. Robert Farmer Senior Technology Compliance Manager
 FFIEC Supplemental Guidance to Authentication in an Robert Farmer Senior Technology Compliance Manager 1 888 250 4400 Effective Date The FFIEC Supplement to Authentication in an was issued on June 28,
FFIEC Supplemental Guidance to Authentication in an Robert Farmer Senior Technology Compliance Manager 1 888 250 4400 Effective Date The FFIEC Supplement to Authentication in an was issued on June 28,
Maryland MeF Handbook for Authorized e-file Providers
 2014 Maryland MeF Handbook for Authorized e-file Providers for Corporation and Pass-Through Entity Income Tax Returns October 2014 Revenue Administration Division Annapolis, MD 21411 Peter Franchot, Comptroller
2014 Maryland MeF Handbook for Authorized e-file Providers for Corporation and Pass-Through Entity Income Tax Returns October 2014 Revenue Administration Division Annapolis, MD 21411 Peter Franchot, Comptroller
TaxSlayer Frequently Asked Questions (FAQs)
 TaxSlayer Frequently Asked Questions (FAQs) Background: The VITA/TCE software contract has been awarded to TaxSlayer, LLC. TaxSlayer will be the new software provider for the VITA/TCE Programs beginning
TaxSlayer Frequently Asked Questions (FAQs) Background: The VITA/TCE software contract has been awarded to TaxSlayer, LLC. TaxSlayer will be the new software provider for the VITA/TCE Programs beginning
EBank Debit Card Terms and Conditions
 c/o Sinclair & Schanzen Road, Windhoek, Namibia P O Box 97438, Windhoek, Namibia T +264 61 297 1000, F +264 61 297 1800 E info@ebank.na, www.ebank.na EBank Debit Card Terms and Conditions Debit Card Terms
c/o Sinclair & Schanzen Road, Windhoek, Namibia P O Box 97438, Windhoek, Namibia T +264 61 297 1000, F +264 61 297 1800 E info@ebank.na, www.ebank.na EBank Debit Card Terms and Conditions Debit Card Terms
NATIONAL CREDIT UNION ADMINISTRATION CREDIT UNION ONLINE: CREDIT UNION PROFILE AND 5300 CALL REPORT
 NATIONAL CREDIT UNION ADMINISTRATION CREDIT UNION ONLINE: CREDIT UNION PROFILE AND 5300 CALL REPORT INSTRUCTION GUIDE For Natural Person Credit Unions NCUA 10200 (REV 4) Table of Contents A. Introduction...
NATIONAL CREDIT UNION ADMINISTRATION CREDIT UNION ONLINE: CREDIT UNION PROFILE AND 5300 CALL REPORT INSTRUCTION GUIDE For Natural Person Credit Unions NCUA 10200 (REV 4) Table of Contents A. Introduction...
Franchise Data Compromise Trends and Cardholder. December, 2010
 Franchise Data Compromise Trends and Cardholder Security Best Practices December, 2010 Franchise Data Security Agenda Cardholder Data Compromise Overview Breach Commonalities Hacking Techniques Franchisee
Franchise Data Compromise Trends and Cardholder Security Best Practices December, 2010 Franchise Data Security Agenda Cardholder Data Compromise Overview Breach Commonalities Hacking Techniques Franchisee
Red Flag Rules: A Step by Step Guide to Developing a Prevention & Training Program
 Red Flag Rules: A Step by Step Guide to Developing a Prevention & Training Program A Case Study of Sam Houston State University s Red Flag Program Dr. Kristy L. Vienne Objective Participants will: Understand
Red Flag Rules: A Step by Step Guide to Developing a Prevention & Training Program A Case Study of Sam Houston State University s Red Flag Program Dr. Kristy L. Vienne Objective Participants will: Understand
B. Credit - Deferral of payment of a debt incurred for the purchase of goods services, including educational services.
 Date Revised: Page 1 of 16 5-21 Identity Theft Prevention Program I. BACKGROUND As a result of the increasing instances of identity theft, the United States Congress passed the Fair and Accurate Credit
Date Revised: Page 1 of 16 5-21 Identity Theft Prevention Program I. BACKGROUND As a result of the increasing instances of identity theft, the United States Congress passed the Fair and Accurate Credit
Nebraska Handbook for
 Publication 1345N-MeF Nebraska Handbook for Electronic Filers of Individual Income Tax Returns Tax Year 2015 Additional information can be found on the Department's website. 8-540-2015 Table of Contents
Publication 1345N-MeF Nebraska Handbook for Electronic Filers of Individual Income Tax Returns Tax Year 2015 Additional information can be found on the Department's website. 8-540-2015 Table of Contents
