Sluggish Incident Response: Next-Generation Security Problems and Solutions
|
|
|
- Allan Anderson
- 10 years ago
- Views:
Transcription
1 CUSTOMER NEEDS AND STRATEGIES Sluggish Incident Response: Next-Generation Security Problems and Solutions Christian A. Christiansen Christina Richmond Robert Westervelt IDC OPINION The rush to adopt technologies that detect advanced threats has resulted in an increasing flood of information for consumption by security teams. This increased volume of good information also has an increased level of noise, that is, alerts that do not represent malicious activity. This alert noise presents a challenge to already overburdened incident responders. Organizations must develop and cultivate a security program that reduces the attack surface and has the ability to quickly detect and contain attacks before they move into the next stage of the attack life cycle. The challenging hiring environment for skilled security professionals will no doubt continue to drive interest in external security services to identify threats and aid incident response. No organization has the perfect strategy. Focus should be on solidifying basic security best practices and developing and thoroughly testing incident response (IR) procedures. The strategy should significantly improve the overall security posture and speed up threat containment and remediation of targeted weaknesses. The security program may be supported with the following measures: Review and update incident response procedures. Establish roles and responsibilities and conduct thorough tabletop exercises to validate the procedures and identify any technical limitations in the response processes. Develop a program that identifies and addresses vulnerabilities and configuration issues that are common weak points targeted by criminals. Consider engaging a services provider to assist with an end-to-end breach management program designed for this very task. Consider supporting two-factor authentication for externally accessible resources and assess the state of privileged credentials throughout the environment. Identify critical systems and restrict the environment to run only critical processes and applications. Review log and event management systems and identify tools that help incident responders prioritize alerts and efficiently address threats. Use a platform that integrates log data, threat intelligence data, and incidents into one dashboard for security operation center (SOC) analysts and incident responders to work in tandem, thereby keeping all systems and actions up to date. Hire employees dedicated to incident response and provide training and skills development opportunities. Create a retention program that rewards top performers and establishes a culture that provides a technical career path and potential leadership opportunities for new employees. Additional technology and threat intelligence coupled with support from outside services offerings could help enrich security alerts with context to help responders prioritize investigation and containment efforts. May 2015, IDC #256219
2 IN THIS STUDY This IDC study is the result of discussions with FireEye, its Mandiant incident response organization, and recent interviews with SOC managers and threat analysts about how to better approach incident response management. This study identifies the issues plaguing incident response processes and provides potential solutions to these problems. It also provides an overview of the outside security services that organizations can procure to support their threat response operation. SITUATION OVERVIEW Prioritizing and addressing the growing number of security alerts is at least one of the issues challenging incident responders. It has resulted in an expanding gap between an initial compromise and the time a breach is detected. This is a growing issue as attacks take longer to discover, notification is delayed, forensics investigations are hampered, public opinion declines, and regulators/auditors take harsh actions. Targeted attacks are often multistaged, carefully planned, and are increasingly using sophisticated tools, tactics, and procedures designed to evade common defenses. Most attacks begin with a simple phishing campaign or Web-based attack to gain an initial foothold in an organization. Once a staging ground is established, attackers carefully seek to elevate privileges, often stealing account credentials to appear as legitimate users on the corporate network. These kinds of targeted strikes enable criminal groups and nation-state sponsored attackers to spider out across the whole environment. Their aim is to steal information that is valuable to them which may be credit card numbers, merger and acquisition plans, or technical design specifications. A growing number of established and emerging start-ups are coming to market with so-called advanced threat protection platforms that promise to identify, alert on, and, in some cases, even block suspicious files and behaviors that signal a potential attack in progress. FireEye, which has gained attention with its NX Network Security appliances, has helped fuel much of the attention on previously unidentified malware associated with targeted attack activity. But despite demonstrating success in identifying advanced malware and reducing false positives, details from the long list of recent data breaches, beginning with the security lapse at retail giant Target Corp. during the 2013 holiday season, suggest that incident responders continue to struggle to investigate and contain intrusions before attackers steal information. A recent IDC survey identified many of the challenges that stymie incident response. Organizations indicated that security teams manage multiple consoles for network-based threat management, with some juggling seven or more. The sheer volume of alerts is becoming a significant challenge, with some IT teams getting 10,000 alerts a month or more. With that high number of alerts, false positives may be a significant issue with some organizations, indicating that they have taken steps to minimize false positives and eliminate duplicate alerts. Separating the wheat from the chaff when it comes to identifying alerts that deserve further investigation requires dedicated focus, experienced security analysts, and is typically time consuming IDC #
3 In targeted attacks, there are three issues that cause a customer's IT security analysts to miss critical incidents: Poor visibility and context: Organizations often suffer from the lack of automated tools to measure and assign a risk score to an alert. Often, processes are also not assessed and sharpened to rapidly identify which events indicate the need for more depth. It takes a trained person to identify what needs a deeper look and to contain the issue. Overall, the analyst is blamed when a threat isn't contained, but the real fault lies in the lack of maturity in endpoint forensics, investigation tools, poor integration, and the lack of flight recorder data. Moreover, analysts sometimes lack the technical ability to correlate context across multiple attack environments versus a single failed attempt. An investigation of the most serious infections requires the completion of forensic investigations and being able to clearly communicate the compromise to senior executives and board of directors. IDC believes that by 2018, fully 75% of CSOs/CISOs will report directly to the CEO as interest in information security rises at the board of directors and senior executive level (see IDC FutureScape: Worldwide IT Security Products and Security Services 2015 Predictions Moving Toward Security Integration, IDC #253026, December 2014). Executive leadership may ask what data was potentially being sought; who the adversary is; whether it is a targeted, state-sponsored attack; or a previously identified criminal organization. Those data points are coveted information, but the details are not always absolute. Solutions: Organizations should establish incident response procedures and identify an individual who will lead the IR team. The policy should be regularly tested and updated as needed. Train analysts in identifying alerts that need additional attention. Consider reinforcing internal processes and responders by outsourcing remediation and better equipping them with SaaS analytics and iterative intelligence services that can add the context required to determine the connotation of an alert. Many security service providers now offer end-to-end breach management services that work with enterprise security staff to identify processes, people, and technology critical to an inevitable breach. These services can be purchased either as consulting engagements to develop an incident plan or as both a consulting and a retainer for incident response when (not if) the services will be needed. Limited human resources: The lack of skilled security analysts to support information security activities has been well documented and is a growing problem that has fueled significant growth in security services. IDC estimates the total worldwide professional security services (PSS) market accounted for $18.4 billion in revenue in 2014, and it is expected to reach $23.7 billion in 2019, growing at a 5.2% compound annual growth rate (CAGR) over the period (see Worldwide and U.S. Professional Security Services Forecast: The Perfect Storm, IDC #254562, March 2015). The growing complexity associated with the rapid pace of ongoing initiatives such as cloud, mobile, Big Data and analytics, and social, which collectively make up what IDC calls the 3rd Platform, has driven the need for additional IT security talent, not eliminated it. Staff augmentation can perform end-to-end breach management and provide vulnerability assessments and penetration testing, forensics, and remediation services. Solutions: Specialized vendors with managed services maintain skilled people and have visibility into attacks impacting their entire client base. Managed security service providers (MSSPs) are increasingly offering incident response retainer services, triage assistance, and phone support to address critical alerts. Outsourcing could involve simply adding monitoring services on weekends or holidays or 24 x 7 monitoring to reinforce onsite 2015 IDC #
4 personnel. Some service providers also have added dedicated response teams that can be retained when responders need assistance with a serious lapse. Inadequate follow-up to address root causes: The goal of maintaining an incident response team is not only to effectively respond and investigate security incidents. The incident response team increases the awareness about the effectiveness of the information security program and over time can cultivate a culture of security awareness within the entire organization. Remediation plans need short- and long-term strategies based on defense in depth. The security team's investigation and analysis of an attack should be followed up with recommended changes to prevent attacks from leveraging similar weaknesses throughout the organization. A high number of organizations are reviewing configurations monthly and more proactively addressing software vulnerabilities. Another issue that demands attention is the common finding from penetration testing firms that many of the environments they have probed are overly permissive. In overly permissive environments, everything talks to everything, enabling attackers to easily move laterally through networks. Overly permissive networks are easier to set up and less difficult to troubleshoot, but they create attack opportunities. Solutions: A detailed report should follow an incident investigation and contain findings about the root cause of the incident and recommend policy, process, and/or configuration changes to reduce the potential for similar incidents from occurring in the future. To solve this problem, policy is needed to constrain access and segment off critical parts of the network. In addition, turning off rarely used server and application features and components to reduce the attack surface may be beneficial. Consider modern IT management platforms designed to identify weaknesses and privileged account security and management tools to track employee privileges. FUTURE OUTLOOK Advanced threat detection products use a variety of approaches to identify zero-day threats and other advanced malware designed to evade traditional security capabilities. But their success has generated increased alerts, overburdening some organizations with limited IT personnel and budget. Some security vendors are responding by building out their internal professional services capabilities, and organizations are encouraged to contact their security vendor or channel provider for assistance. Wellestablished organizations with incident response services include AT&T, Dell SecureWorks, FireEye- Mandiant, Verizon, and NTT. Some specialized threat analysis and protection (STAP) vendors are having success identifying advanced malware and can also provide the context behind detected threats. A growing number of STAP vendors are adding automated response capabilities designed to quarantine or remove threats. In addition, emerging threat intelligence management platforms can help incident response teams organize and gain more value out of security vendor and other third-party threat intelligence feeds. It could take a period of five years or more before organizations begin to become comfortable with automating response and threat removal activities. Managed security service providers have also added incident response services, with some MSSPs adding dedicated incident response personnel in their security operation centers to provide complete incident response or triage services. IDC expects service offerings to expand over time and is seeing services extending into risk assessments, penetration testing, and other support capabilities IDC #
5 ESSENTIAL GUIDANCE Addressing security basics are a must, but organizations should also address internal processes, identify personnel that need additional training, and support and consider modernizing threat detection and response technology. Further: Consider security vendor products that play an active role in supporting incident response. In addition to forensics tools, network packet recorders, and traditional security products, a growing group of specialized threat analysis and protection vendors combine threat intelligence, data analytics, and increased visibility to identify advanced threats. Evaluate incident response management platforms that track the security incident response process and aid in remediation efforts. Modern platforms claim to integrate with incident response team workflows. Risk-averse organizations that are keeping security in-house require a comprehensive incident response plan and thorough process testing. Consider if automation can decrease the number of generated alerts and potentially reduce the workload of the IR team. Solutions like FireEye as a service can help classify and analyze risks and give subscribers access to historical information and recommendations for securing impacted systems and remediating threats. Make sure incident response plans include measures to handle a malware flood as well as a trickle. If you do produce threat intelligence, focus on quality as a priority over quantity. Where an opportunity for detection presents itself, seize it in the way that offers the greatest longevity for your efforts. Consider emerging threat intelligence management platforms that can aid SOC managers and threat analysts by organizing multiple threat feeds and making the flow of information actionable. Open source threat intelligence frameworks are a good starting point to eliminate the generally manual processes but require custom development. Emerging proprietary solutions can blend feeds, eliminate redundancies, correlate threat indicators, and visualize attack patterns to get a broader picture of adversary objectives. A hybrid approach could take advantage of SaaS platforms that add context to generated alerts. Managed security service providers add visibility and are increasingly offering professional services. MSSPs with professional services capabilities can help assist with risk assessments and provide much-needed support by helping manage determining the scope of an incident. Consider the following types of outside support: Threat intelligence services: Outside threat intelligence services that are tailored to an organization's industry vertical can help bolster the detection of advanced persistent threats (APTs), attacks are unknown, targeted, low and slow, and adaptive. They can also serve to provide additional context behind specific alerts and aid the remediation process to bolster prevention. Look for threat intelligence services that can be customized and provide timely and actionable data. Professional security services (includes consulting and integration): Outside professional services organizations can help configure and manage advanced security detection technologies to ensure that the full value of the technology is being achieved. These services can also include triage assistance with alerts, detailed forensics investigations, and postbreach assessment capabilities. Security consulting firms that specialize in breach, incident response, and forensic analysis can be placed on retainer ahead of time rather than obtaining services at a time of crisis IDC #
6 Consulting security services: Some consultative services specialize in risk assessments, penetration testing, and identifying data governance weaknesses. They may assist with developing and testing an incident response plan or help manage breach notification or disaster recovery procedures. They may also provide security awareness training to help build up a culture of security within the organization over time. LEARN MORE Related Research FireEye Continues Aggressive Expansion Strategy (IDC #lcus , September 2014) Mind the (Security Talent) Gap (IDC #251618, September 2014) Worldwide Threat Intelligence Security Services Forecast: "Iterative Intelligence" Threat Intelligence Comes of Age (IDC #246977, March 2014) Synopsis Bit9 Acquires Black Carbon as the Threat Intelligence Space Continues to Evolve (IDC #lcus , February 2014) This IDC study identifies the issues challenging security incident response activities and explores potential next-generation solutions and strategies to solve them. "High-profile data breaches in recent years have highlighted the need for organizations to find ways to better support overburdened incident responders," says Chris Christiansen, program vice president, Security Products and Services. "Many organizations are increasingly seeking outside assistance. Alerts require increased context and incident response processes need to be better planned, managed, and practiced." 2015 IDC #
7 About IDC International Data Corporation (IDC) is the premier global provider of market intelligence, advisory services, and events for the information technology, telecommunications and consumer technology markets. IDC helps IT professionals, business executives, and the investment community make factbased decisions on technology purchases and business strategy. More than 1,100 IDC analysts provide global, regional, and local expertise on technology and industry opportunities and trends in over 110 countries worldwide. For 50 years, IDC has provided strategic insights to help our clients achieve their key business objectives. IDC is a subsidiary of IDG, the world's leading technology media, research, and events company. Global Headquarters 5 Speen Street Framingham, MA USA idc-insights-community.com Copyright Notice This IDC research document was published as part of an IDC continuous intelligence service, providing written research, analyst interactions, telebriefings, and conferences. Visit to learn more about IDC subscription and consulting services. To view a list of IDC offices worldwide, visit Please contact the IDC Hotline at , ext (or ) or [email protected] for information on applying the price of this document toward the purchase of an IDC service or for information on additional copies or Web rights. Copyright 2015 IDC. Reproduction is forbidden unless authorized. All rights reserved.
I D C A N A L Y S T C O N N E C T I O N
 I D C A N A L Y S T C O N N E C T I O N Robert Westervelt Research Manager, Security Products T h e R o l e a nd Value of Continuous Security M o nitoring August 2015 Continuous security monitoring (CSM)
I D C A N A L Y S T C O N N E C T I O N Robert Westervelt Research Manager, Security Products T h e R o l e a nd Value of Continuous Security M o nitoring August 2015 Continuous security monitoring (CSM)
Worldwide Security and Vulnerability Management 2014 2018 Forecast and 2013 Vendor Shares
 Market Analysis Worldwide Security and Vulnerability Management 2014 2018 Forecast and 2013 Vendor Shares Charles J. Kolodgy IN THIS EXCERPT The content for this excerpt was taken directly from IDC Market
Market Analysis Worldwide Security and Vulnerability Management 2014 2018 Forecast and 2013 Vendor Shares Charles J. Kolodgy IN THIS EXCERPT The content for this excerpt was taken directly from IDC Market
SAS Enterprise Decision Management at a Global Financial Services Firm: Enabling More Rapid Implementation of Decision Models into Production
 Buyer Case Study SAS Enterprise Decision Management at a Global Financial Services Firm: Enabling More Rapid Implementation of Decision Models into Production Brian McDonough IDC OPINION The goal of decision
Buyer Case Study SAS Enterprise Decision Management at a Global Financial Services Firm: Enabling More Rapid Implementation of Decision Models into Production Brian McDonough IDC OPINION The goal of decision
Converged and Integrated Datacenter Systems: Creating Operational Efficiencies
 Insight Converged and Integrated Datacenter Systems: Creating Operational Efficiencies Rob Brothers IDC OPINION Enterprise IT has moved away from siloed servers, storage, information, and processes and
Insight Converged and Integrated Datacenter Systems: Creating Operational Efficiencies Rob Brothers IDC OPINION Enterprise IT has moved away from siloed servers, storage, information, and processes and
Worldwide Cloud Systems Management Software 2013 Vendor Shares
 COMPETITIVE ANALYSIS Worldwide Cloud Systems Management Software 2013 Vendor Shares Mary Johnston Turner IDC OPINION In 2013, the worldwide cloud systems management software competitive market showed very
COMPETITIVE ANALYSIS Worldwide Cloud Systems Management Software 2013 Vendor Shares Mary Johnston Turner IDC OPINION In 2013, the worldwide cloud systems management software competitive market showed very
IT as a Service Emerges as a New Management Paradigm in the Software-Defined Datacenter Era
 Customer Needs and Strategies IT as a Service Emerges as a New Management Paradigm in the Software-Defined Datacenter Era Mary Johnston Turner IDC OPINION IT as a service (ITaaS) represents a fundamentally
Customer Needs and Strategies IT as a Service Emerges as a New Management Paradigm in the Software-Defined Datacenter Era Mary Johnston Turner IDC OPINION IT as a service (ITaaS) represents a fundamentally
Worldwide Application Performance Management Software 2013 Vendor Shares
 Competitive Analysis Worldwide Application Performance Management Software 2013 Vendor Shares Melinda-Carol Ballou Rohit Mehra Tim Grieser Mary Johnston Turner IDC OPINION The worldwide application performance
Competitive Analysis Worldwide Application Performance Management Software 2013 Vendor Shares Melinda-Carol Ballou Rohit Mehra Tim Grieser Mary Johnston Turner IDC OPINION The worldwide application performance
Worldwide Security and Vulnerability Management 2009 2013 Forecast and 2008 Vendor Shares
 EXCERPT Worldwide Security and Vulnerability Management 2009 2013 Forecast and 2008 Vendor Shares IN THIS EXCERPT Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015
EXCERPT Worldwide Security and Vulnerability Management 2009 2013 Forecast and 2008 Vendor Shares IN THIS EXCERPT Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com E X C E R P T N i n e S t a r t - U p s a n d I n n o v a t o r s E x t e n d t h e C l o u d S y
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com E X C E R P T N i n e S t a r t - U p s a n d I n n o v a t o r s E x t e n d t h e C l o u d S y
ScienceLogic Offers Unified Infrastructure Monitoring and Analytics for Hybrid IT
 VENDOR PROFILE ScienceLogic Offers Unified Infrastructure Monitoring and Analytics for Hybrid IT Mary Johnston Turner David Immerman IDC OPINION Enterprise datacenter infrastructure environments are becoming
VENDOR PROFILE ScienceLogic Offers Unified Infrastructure Monitoring and Analytics for Hybrid IT Mary Johnston Turner David Immerman IDC OPINION Enterprise datacenter infrastructure environments are becoming
Worldwide Datacenter Automation Software 2013 Vendor Shares
 COMPETITIVE ANALYSIS Worldwide Datacenter Automation Software 2013 Vendor Shares Mary Johnston Turner IDC OPINION In 2013, the worldwide datacenter automation software submarket of the workload scheduling
COMPETITIVE ANALYSIS Worldwide Datacenter Automation Software 2013 Vendor Shares Mary Johnston Turner IDC OPINION In 2013, the worldwide datacenter automation software submarket of the workload scheduling
DevOps and the Cost of Downtime: Fortune 1000 Best Practice Metrics Quantified
 Insight DevOps and the Cost of Downtime: Fortune 1000 Best Practice Metrics Quantified Stephen Elliot IDC OPINION Based on a research survey conducted during October and November of 2014 across multiple
Insight DevOps and the Cost of Downtime: Fortune 1000 Best Practice Metrics Quantified Stephen Elliot IDC OPINION Based on a research survey conducted during October and November of 2014 across multiple
2014 Human Capital Management Survey: HCM Buyer Actions and Plans
 Survey 2014 Human Capital Management Survey: HCM Buyer Actions and Plans Lisa Rowan IDC OPINION This study provides human capital management (HCM) applications buying behavior findings drawn from an IDC
Survey 2014 Human Capital Management Survey: HCM Buyer Actions and Plans Lisa Rowan IDC OPINION This study provides human capital management (HCM) applications buying behavior findings drawn from an IDC
IDC MarketScape: Worldwide Datacenter Infrastructure Management 2015 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Datacenter Infrastructure Management 2015 Vendor Assessment Jennifer Koppy THIS IDC MARKETSCAPE EXCERPT FEATURES EMERSON NETWORK POWER IDC MARKETSCAPE FIGURE
IDC MarketScape IDC MarketScape: Worldwide Datacenter Infrastructure Management 2015 Vendor Assessment Jennifer Koppy THIS IDC MARKETSCAPE EXCERPT FEATURES EMERSON NETWORK POWER IDC MARKETSCAPE FIGURE
"Why Didn't We Do It Sooner?" Deployment of a New BI Solution at The Pain Center of Arizona
 Buyer Case Study "Why Didn't We Do It Sooner?" Deployment of a New BI Solution at The Pain Center of Arizona Dan Vesset IDC OPINION Investment in analytics, business intelligence, and big data technologies
Buyer Case Study "Why Didn't We Do It Sooner?" Deployment of a New BI Solution at The Pain Center of Arizona Dan Vesset IDC OPINION Investment in analytics, business intelligence, and big data technologies
Business Networks: The Next Wave of Innovation
 White Paper Business Networks: The Next Wave of Innovation Sponsored by: Ariba Michael Fauscette November 2014 In This White Paper The business network is forming a new framework for productivity and value
White Paper Business Networks: The Next Wave of Innovation Sponsored by: Ariba Michael Fauscette November 2014 In This White Paper The business network is forming a new framework for productivity and value
Worldwide Workload Management Software 2013 Vendor Shares
 EXCERPT Worldwide Workload Management Software 2013 Vendor Shares Mary Johnston Turner IN THIS EXCERPT The content for this paper is excerpted from the IDC Competitive Analysis Report, Worldwide Workload
EXCERPT Worldwide Workload Management Software 2013 Vendor Shares Mary Johnston Turner IN THIS EXCERPT The content for this paper is excerpted from the IDC Competitive Analysis Report, Worldwide Workload
Advanced Threat Protection with Dell SecureWorks Security Services
 Advanced Threat Protection with Dell SecureWorks Security Services Table of Contents Summary... 2 What are Advanced Threats?... 3 How do advanced threat actors operate?... 3 Addressing the Threat... 5
Advanced Threat Protection with Dell SecureWorks Security Services Table of Contents Summary... 2 What are Advanced Threats?... 3 How do advanced threat actors operate?... 3 Addressing the Threat... 5
Cyber Threat Intelligence Move to an intelligencedriven cybersecurity model
 Cyber Threat Intelligence Move to an intelligencedriven cybersecurity model Stéphane Hurtaud Partner Governance Risk & Compliance Deloitte Laurent De La Vaissière Director Governance Risk & Compliance
Cyber Threat Intelligence Move to an intelligencedriven cybersecurity model Stéphane Hurtaud Partner Governance Risk & Compliance Deloitte Laurent De La Vaissière Director Governance Risk & Compliance
IDC MarketScape: Worldwide Telecom Service Provider 2013 Vendor Assessment
 IDC MARKETSCAPE IDC MarketScape: Worldwide Telecom Service Provider 2013 Vendor Assessment Courtney Munroe Melanie Posey THIS IDC MARKETSCAPE EXCERPT FEATURES: BT GLOBAL SERVICES IDC MARKETSCAPE FIGURE
IDC MARKETSCAPE IDC MarketScape: Worldwide Telecom Service Provider 2013 Vendor Assessment Courtney Munroe Melanie Posey THIS IDC MARKETSCAPE EXCERPT FEATURES: BT GLOBAL SERVICES IDC MARKETSCAPE FIGURE
Journey to 3rd Platform Digital Customer Experience
 Vendor Spotlight Journey to 3rd Platform Digital Customer Experience Sponsored by: Genesys Telecommunications Laboratories Jason Andersson May 2014 COMPETING ON THE 3RD PLATFORM The ICT industry is in
Vendor Spotlight Journey to 3rd Platform Digital Customer Experience Sponsored by: Genesys Telecommunications Laboratories Jason Andersson May 2014 COMPETING ON THE 3RD PLATFORM The ICT industry is in
How To Understand Cloud Economics
 WHITE PAPER Cloud Economics: A Financial Analysis of Information Management IT Delivery Models Sponsored by: Viewpointe LLC Michael Versace October 2013 Randy Perry IDC OPINION Executive Summary Cost optimization
WHITE PAPER Cloud Economics: A Financial Analysis of Information Management IT Delivery Models Sponsored by: Viewpointe LLC Michael Versace October 2013 Randy Perry IDC OPINION Executive Summary Cost optimization
Combating a new generation of cybercriminal with in-depth security monitoring. 1 st Advanced Data Analysis Security Operation Center
 Combating a new generation of cybercriminal with in-depth security monitoring 1 st Advanced Data Analysis Security Operation Center The Challenge Don t leave your systems unmonitored. It takes an average
Combating a new generation of cybercriminal with in-depth security monitoring 1 st Advanced Data Analysis Security Operation Center The Challenge Don t leave your systems unmonitored. It takes an average
Microsoft Office 365: How the Hosted Exchange Server Is Redefining SMB Cloud IT Adoption
 INDUSTRY DEVELOPMENTS AND MODELS Microsoft Office 365: How the Hosted Exchange Server Is Redefining SMB Cloud IT Adoption Christopher Chute IDC OPINION Office 365 is Microsoft's next-generation email and
INDUSTRY DEVELOPMENTS AND MODELS Microsoft Office 365: How the Hosted Exchange Server Is Redefining SMB Cloud IT Adoption Christopher Chute IDC OPINION Office 365 is Microsoft's next-generation email and
IDC MarketScape: Worldwide Service Desk Management Software 2014 Vendor Analysis
 IDC MarketScape IDC MarketScape: Worldwide Service Desk Management Software 2014 Vendor Analysis Robert Young THIS IDC MARKETSCAPE EXCERPT FEATURES: SERVICENOW IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MarketScape IDC MarketScape: Worldwide Service Desk Management Software 2014 Vendor Analysis Robert Young THIS IDC MARKETSCAPE EXCERPT FEATURES: SERVICENOW IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
Worldwide Security and Vulnerability Management Market Shares, 2014: The Need for Improved Incident Response Driving Higher Growth Across the Market
 MARKET SHARE Worldwide Security and Vulnerability Management Market Shares, 2014: The Need for Improved Incident Response Driving Higher Growth Across the Market Robert Ayoub Elizabeth Corr Christian A.
MARKET SHARE Worldwide Security and Vulnerability Management Market Shares, 2014: The Need for Improved Incident Response Driving Higher Growth Across the Market Robert Ayoub Elizabeth Corr Christian A.
Integrating MSS, SEP and NGFW to catch targeted APTs
 #SymVisionEmea #SymVisionEmea Integrating MSS, SEP and NGFW to catch targeted APTs Tom Davison Information Security Practice Manager, UK&I Antonio Forzieri EMEA Solution Lead, Cyber Security 2 Information
#SymVisionEmea #SymVisionEmea Integrating MSS, SEP and NGFW to catch targeted APTs Tom Davison Information Security Practice Manager, UK&I Antonio Forzieri EMEA Solution Lead, Cyber Security 2 Information
IDC MarketScape Excerpt: Worldwide HR BPO 2014 Vendor Assessment
 IDC MarketScape IDC MarketScape Excerpt: Worldwide HR BPO 2014 Vendor Assessment Lisa Rowan THIS IDC MARKETSCAPE EXCERPT FEATURES: ADP IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape HR Business Process
IDC MarketScape IDC MarketScape Excerpt: Worldwide HR BPO 2014 Vendor Assessment Lisa Rowan THIS IDC MARKETSCAPE EXCERPT FEATURES: ADP IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape HR Business Process
Worldwide Problem Management Software Market Shares, 2014: 3rd Platform Technologies and Delivery Models Drive Growth
 MARKET SHARE Worldwide Problem Management Software Market Shares, 2014: 3rd Platform Technologies and Delivery Models Drive Growth Robert Young IDC MARKET SHARE FIGURE FIGURE 1 Worldwide Problem Management
MARKET SHARE Worldwide Problem Management Software Market Shares, 2014: 3rd Platform Technologies and Delivery Models Drive Growth Robert Young IDC MARKET SHARE FIGURE FIGURE 1 Worldwide Problem Management
IDC MarketScape: Worldwide Life Science Sales and Marketing ITO 2015 Vendor Assessment
 IDC MARKETSCAPE IDC MarketScape: Worldwide Life Science Sales and Marketing ITO 2015 Vendor Assessment Eric Newmark THIS IDC MARKETSCAPE EXCERPT FEATURES: IMS HEALTH IDC MARKETSCAPE FIGURE FIGURE 1 IDC
IDC MARKETSCAPE IDC MarketScape: Worldwide Life Science Sales and Marketing ITO 2015 Vendor Assessment Eric Newmark THIS IDC MARKETSCAPE EXCERPT FEATURES: IMS HEALTH IDC MARKETSCAPE FIGURE FIGURE 1 IDC
Continuous Network Monitoring
 Continuous Network Monitoring Eliminate periodic assessment processes that expose security and compliance programs to failure Continuous Network Monitoring Continuous network monitoring and assessment
Continuous Network Monitoring Eliminate periodic assessment processes that expose security and compliance programs to failure Continuous Network Monitoring Continuous network monitoring and assessment
IDC MarketScape: Worldwide Digital Enterprise Strategy Consulting Services 2015 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Digital Enterprise Strategy Consulting Services 2015 Vendor Assessment Cushing Anderson Mette Ahorlu THIS IDC MARKETSCAPE EXCERPT FEATURES PWC IDC MARKETSCAPE
IDC MarketScape IDC MarketScape: Worldwide Digital Enterprise Strategy Consulting Services 2015 Vendor Assessment Cushing Anderson Mette Ahorlu THIS IDC MARKETSCAPE EXCERPT FEATURES PWC IDC MARKETSCAPE
Data Management: Foundational Technologies for Health Insurance Exchange Success
 INDUSTRY BRIEF Data Management: Foundational Technologies for Health Insurance Exchange Success Sponsored by: Informatica Janice W. Young November 2013 IN THIS INDUSTRY BRIEF U.S. health plans have been
INDUSTRY BRIEF Data Management: Foundational Technologies for Health Insurance Exchange Success Sponsored by: Informatica Janice W. Young November 2013 IN THIS INDUSTRY BRIEF U.S. health plans have been
Combating a new generation of cybercriminal with in-depth security monitoring
 Cybersecurity Services Combating a new generation of cybercriminal with in-depth security monitoring 1 st Advanced Data Analysis Security Operation Center The Challenge Don t leave your systems unmonitored.
Cybersecurity Services Combating a new generation of cybercriminal with in-depth security monitoring 1 st Advanced Data Analysis Security Operation Center The Challenge Don t leave your systems unmonitored.
Cirba Targets Software-Defined Infrastructure Control with Workload-Aware Predictive Analytics
 Vendor Profile Cirba Targets Software-Defined Infrastructure Control with Workload-Aware Predictive Analytics Mary Johnston Turner David Immerman IDC OPINION Software-defined infrastructure (SDI) enables
Vendor Profile Cirba Targets Software-Defined Infrastructure Control with Workload-Aware Predictive Analytics Mary Johnston Turner David Immerman IDC OPINION Software-defined infrastructure (SDI) enables
Symantec Global Intelligence Network 2.0 Architecture: Staying Ahead of the Evolving Threat Landscape
 WHITE PAPER: SYMANTEC GLOBAL INTELLIGENCE NETWORK 2.0.... ARCHITECTURE.................................... Symantec Global Intelligence Network 2.0 Architecture: Staying Ahead of the Evolving Threat Who
WHITE PAPER: SYMANTEC GLOBAL INTELLIGENCE NETWORK 2.0.... ARCHITECTURE.................................... Symantec Global Intelligence Network 2.0 Architecture: Staying Ahead of the Evolving Threat Who
IDC MarketScape: Worldwide Business Consulting Strategy for Digital Operations 2015 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Business Consulting Strategy for Digital Operations 2015 Vendor Assessment Michael Versace Cushing Anderson THIS IDC MARKETSCAPE EXCERPT FEATURES KPMG IDC MARKETSCAPE
IDC MarketScape IDC MarketScape: Worldwide Business Consulting Strategy for Digital Operations 2015 Vendor Assessment Michael Versace Cushing Anderson THIS IDC MARKETSCAPE EXCERPT FEATURES KPMG IDC MARKETSCAPE
IDC MarketScape: Worldwide Service Desk Management Software 2014 Vendor Analysis
 IDC MarketScape IDC MarketScape: Worldwide Service Desk Management Software 2014 Vendor Analysis Robert Young THIS IDC MARKETSCAPE EXCERPT FEATURES: CHERWELL SOFTWARE IDC MARKETSCAPE FIGURE FIGURE 1 IDC
IDC MarketScape IDC MarketScape: Worldwide Service Desk Management Software 2014 Vendor Analysis Robert Young THIS IDC MARKETSCAPE EXCERPT FEATURES: CHERWELL SOFTWARE IDC MARKETSCAPE FIGURE FIGURE 1 IDC
Ultimate Software: Successfully Navigating the Transition from On-Premise to Cloud ISV as a Public Company
 Vendor Needs and Strategies Ultimate Software: Successfully Navigating the Transition from On-Premise to Cloud ISV as a Public Company Christine Dover IDC OPINION In 1998, when the company went public,
Vendor Needs and Strategies Ultimate Software: Successfully Navigating the Transition from On-Premise to Cloud ISV as a Public Company Christine Dover IDC OPINION In 1998, when the company went public,
I D C M a r k e t S c a p e : W o r l d w i d e F i n a n c i a l S e r v i c e s C o n s u l t i n g 2 0 1 2 V e n d o r A n a l y s i s
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com C O M P E T I T I V E A N A L Y S I S I D C M a r k e t S c a p e : W o r l d w i d e F i n a n c
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com C O M P E T I T I V E A N A L Y S I S I D C M a r k e t S c a p e : W o r l d w i d e F i n a n c
CyberArk Privileged Threat Analytics. Solution Brief
 CyberArk Privileged Threat Analytics Solution Brief Table of Contents The New Security Battleground: Inside Your Network...3 Privileged Account Security...3 CyberArk Privileged Threat Analytics : Detect
CyberArk Privileged Threat Analytics Solution Brief Table of Contents The New Security Battleground: Inside Your Network...3 Privileged Account Security...3 CyberArk Privileged Threat Analytics : Detect
IDC MarketScape: Worldwide Life Science Sales and Marketing BPO 2015 Vendor Assessment
 IDC MARKETSCAPE IDC MarketScape: Worldwide Life Science Sales and Marketing BPO 2015 Vendor Assessment Eric Newmark THIS IDC MARKETSCAPE EXCERPT FEATURES: IMS HEALTH IDC MARKETSCAPE FIGURE FIGURE 1 IDC
IDC MARKETSCAPE IDC MarketScape: Worldwide Life Science Sales and Marketing BPO 2015 Vendor Assessment Eric Newmark THIS IDC MARKETSCAPE EXCERPT FEATURES: IMS HEALTH IDC MARKETSCAPE FIGURE FIGURE 1 IDC
W H I T E P A P E R A T r u s t e d S e c u r i t y P a r t n e r : A M u s t - H a v e i n T o d a y ' s T h r e a t L a n d s c a p e
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com W H I T E P A P E R A T r u s t e d S e c u r i t y P a r t n e r : A M u s t - H a v e i n T o d
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com W H I T E P A P E R A T r u s t e d S e c u r i t y P a r t n e r : A M u s t - H a v e i n T o d
I D C M a r k e t S c a p e : W o r l d w i d e E n t e r p r i s e M o b i l i t y C o n s u l t i n g 2 0 1 3 V e n d o r S h a r e s
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com E X C E R P T I D C M a r k e t S c a p e : W o r l d w i d e E n t e r p r i s e M o b i l i t y
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com E X C E R P T I D C M a r k e t S c a p e : W o r l d w i d e E n t e r p r i s e M o b i l i t y
Using Converged Infrastructure to Enable Rapid, Cost-Effective Private Cloud Deployments
 Sponsored by: VCE Authors: Richard L. Villars Matthew Marden June 2014 Business Value Highlights Customers using Vblock Systems as a platform for deploying private cloud workloads are realizing significant
Sponsored by: VCE Authors: Richard L. Villars Matthew Marden June 2014 Business Value Highlights Customers using Vblock Systems as a platform for deploying private cloud workloads are realizing significant
W o r l d w i d e a n d U. S. M a n a g e d M o b i l i t y 2 0 1 3 2 0 1 7 F o r e c a s t : U n i t e d S t a t e s L e a d s i n A d o p t i o n
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com M A R K E T A N A L Y S I S W o r l d w i d e a n d U. S. M a n a g e d M o b i l i t y 2 0 1 3 2
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com M A R K E T A N A L Y S I S W o r l d w i d e a n d U. S. M a n a g e d M o b i l i t y 2 0 1 3 2
IDC MarketScape: Worldwide Cloud Professional Services 2016 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Cloud Professional Services 2016 Vendor Assessment Gard Little Chad Huston THIS IDC MARKETSCAPE EXCERPT FEATURES: NTT DATA IDC MARKETSCAPE FIGURE FIGURE 1 IDC
IDC MarketScape IDC MarketScape: Worldwide Cloud Professional Services 2016 Vendor Assessment Gard Little Chad Huston THIS IDC MARKETSCAPE EXCERPT FEATURES: NTT DATA IDC MARKETSCAPE FIGURE FIGURE 1 IDC
DNS Server Security Survey
 EXECUTIVE BRIEF DNS Server Security Survey Sponsored by: EfficientIP Romain Fouchereau June 2014 INTRODUCTION With most organizations having some business linked to and more importantly relying on an online
EXECUTIVE BRIEF DNS Server Security Survey Sponsored by: EfficientIP Romain Fouchereau June 2014 INTRODUCTION With most organizations having some business linked to and more importantly relying on an online
Worldwide Application Performance Management Software 2012 Vendor Shares
 COMPETITIVE ANALYSIS Worldwide Application Performance Management Software 2012 Vendor Shares Mary Johnston Turner Tim Grieser Melinda-Carol Ballou Rohit Mehra IDC OPINION Global Headquarters: 5 Speen
COMPETITIVE ANALYSIS Worldwide Application Performance Management Software 2012 Vendor Shares Mary Johnston Turner Tim Grieser Melinda-Carol Ballou Rohit Mehra IDC OPINION Global Headquarters: 5 Speen
GETTING REAL ABOUT SECURITY MANAGEMENT AND "BIG DATA"
 GETTING REAL ABOUT SECURITY MANAGEMENT AND "BIG DATA" A Roadmap for "Big Data" in Security Analytics ESSENTIALS This paper examines: Escalating complexity of the security management environment, from threats
GETTING REAL ABOUT SECURITY MANAGEMENT AND "BIG DATA" A Roadmap for "Big Data" in Security Analytics ESSENTIALS This paper examines: Escalating complexity of the security management environment, from threats
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com E X C E R P T I D C M a r k e t S c a p e : U. S. B u s i n e s s C o n s u l t i n g S e r v i c
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com E X C E R P T I D C M a r k e t S c a p e : U. S. B u s i n e s s C o n s u l t i n g S e r v i c
Full-Context Forensic Analysis Using the SecureVue Unified Situational Awareness Platform
 Full-Context Forensic Analysis Using the SecureVue Unified Situational Awareness Platform Solution Brief Full-Context Forensic Analysis Using the SecureVue Unified Situational Awareness Platform Finding
Full-Context Forensic Analysis Using the SecureVue Unified Situational Awareness Platform Solution Brief Full-Context Forensic Analysis Using the SecureVue Unified Situational Awareness Platform Finding
Long Term Care Group Deploys Zerto for Data Protection and Recovery for Virtual Environments
 BUYER CASE STUDY Long Term Care Group Deploys Zerto for Data Protection and Recovery for Virtual Environments Iris Feng Eric Sheppard IDC OPINION Today's datacenter is dominated by virtualized workloads
BUYER CASE STUDY Long Term Care Group Deploys Zerto for Data Protection and Recovery for Virtual Environments Iris Feng Eric Sheppard IDC OPINION Today's datacenter is dominated by virtualized workloads
eguide: Designing a Continuous Response Architecture Disrupting the Threat: Identify, Respond, Contain & Recover in Seconds
 Disrupting the Threat: Identify, Respond, Contain & Recover in Seconds Table of Contents Overview 3 The Problem 3 Defining the Threat 3 The Network is Not the Target 4 Incident Response is Ad Hoc 5 Incident
Disrupting the Threat: Identify, Respond, Contain & Recover in Seconds Table of Contents Overview 3 The Problem 3 Defining the Threat 3 The Network is Not the Target 4 Incident Response is Ad Hoc 5 Incident
Worldwide Specialized Threat Analysis and Protection Market Shares, 2014: Rapidly Evolving Security Defenses
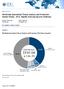 Market Share Worldwide Specialized Threat Analysis and Protection Market Shares, 2014: Rapidly Evolving Security Defenses Robert Westervelt Rob Ayoub Pete Lindstrom Elizabeth Corr IDC MARKET SHARE FIGURE
Market Share Worldwide Specialized Threat Analysis and Protection Market Shares, 2014: Rapidly Evolving Security Defenses Robert Westervelt Rob Ayoub Pete Lindstrom Elizabeth Corr IDC MARKET SHARE FIGURE
Content Analyst's Cerebrant Combines SaaS Discovery, Machine Learning, and Content to Perform Next-Generation Research
 INSIGHT Content Analyst's Cerebrant Combines SaaS Discovery, Machine Learning, and Content to Perform Next-Generation Research David Schubmehl IDC OPINION Organizations are looking for better ways to perform
INSIGHT Content Analyst's Cerebrant Combines SaaS Discovery, Machine Learning, and Content to Perform Next-Generation Research David Schubmehl IDC OPINION Organizations are looking for better ways to perform
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com C O M P E T I T I V E A N A L Y S I S W o r l d w i d e C l o u d S y s t e m s M a n a g e m e n
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com C O M P E T I T I V E A N A L Y S I S W o r l d w i d e C l o u d S y s t e m s M a n a g e m e n
I N D U S T R Y D E V E L O P M E N T S A N D M O D E L S. I D C M a t u r i t y M o d e l : P r i n t a n d D o c u m e n t M a n a g e m e n t
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com E X C E R P T I N D U S T R Y D E V E L O P M E N T S A N D M O D E L S I D C M a t u r i t y M o
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com E X C E R P T I N D U S T R Y D E V E L O P M E N T S A N D M O D E L S I D C M a t u r i t y M o
2012 North American Managed Security Service Providers Growth Leadership Award
 2011 South African Data Centre Green Excellence Award in Technology Innovation Cybernest 2012 2012 North American Managed Security Service Providers Growth Leadership Award 2011 Frost & Sullivan 1 We Accelerate
2011 South African Data Centre Green Excellence Award in Technology Innovation Cybernest 2012 2012 North American Managed Security Service Providers Growth Leadership Award 2011 Frost & Sullivan 1 We Accelerate
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com E XCERPT M A R K E T A N A L Y S I S W o r l d w i d e S e c u r i t y a n d V u l n e r a b i l i
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com E XCERPT M A R K E T A N A L Y S I S W o r l d w i d e S e c u r i t y a n d V u l n e r a b i l i
The SIEM Evaluator s Guide
 Using SIEM for Compliance, Threat Management, & Incident Response Security information and event management (SIEM) tools are designed to collect, store, analyze, and report on log data for threat detection,
Using SIEM for Compliance, Threat Management, & Incident Response Security information and event management (SIEM) tools are designed to collect, store, analyze, and report on log data for threat detection,
Session 9: Changing Paradigms and Challenges Tools for Space Systems Cyber Situational Awareness
 Session 9: Changing Paradigms and Challenges Tools for Space Systems Cyber Situational Awareness Wayne A. Wheeler The Aerospace Corporation GSAW 2015, Los Angeles, CA, March 2015 Agenda Emerging cyber
Session 9: Changing Paradigms and Challenges Tools for Space Systems Cyber Situational Awareness Wayne A. Wheeler The Aerospace Corporation GSAW 2015, Los Angeles, CA, March 2015 Agenda Emerging cyber
Hybrid Cloud Drives Need for Software-Defined WANs in Enterprise
 Insight Hybrid Cloud Drives Need for Software-Defined WANs in Enterprise Brad Casemore Rohit Mehra Nav Chander IDC OPINION The wide area network (WAN) will be critical to the success of enterprise hybrid
Insight Hybrid Cloud Drives Need for Software-Defined WANs in Enterprise Brad Casemore Rohit Mehra Nav Chander IDC OPINION The wide area network (WAN) will be critical to the success of enterprise hybrid
A Case for Managed Security
 A Case for Managed Security By Christopher Harper Managing Director, Security Superior Managed IT & Security Services 1. INTRODUCTION Most firms believe security breaches happen because of one key malfunction
A Case for Managed Security By Christopher Harper Managing Director, Security Superior Managed IT & Security Services 1. INTRODUCTION Most firms believe security breaches happen because of one key malfunction
Attack Intelligence: Why It Matters
 Attack Intelligence: Why It Matters WHITE PAPER Core Security +1 617.399-6980 [email protected] www.coresecurity.com A Proactive Strategy Attacks against your organization are more prevalent than ever,
Attack Intelligence: Why It Matters WHITE PAPER Core Security +1 617.399-6980 [email protected] www.coresecurity.com A Proactive Strategy Attacks against your organization are more prevalent than ever,
IDC MarketScape: Worldwide Hydrocarbon Accounting Software 2013 Vendor Assessment
 IDC MARKETSCAPE IDC MarketScape: Worldwide Hydrocarbon Accounting Software 2013 Vendor Assessment Jill Feblowitz THIS IDC MARKETSCAPE EXCERPT FEATURES: TIETO IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MARKETSCAPE IDC MarketScape: Worldwide Hydrocarbon Accounting Software 2013 Vendor Assessment Jill Feblowitz THIS IDC MARKETSCAPE EXCERPT FEATURES: TIETO IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
The State of Mobility in the Enterprise in 2014: An IDC Survey of Devices, Platforms, Decisions, and Deployments
 Survey The State of Mobility in the Enterprise in 2014: An IDC Survey of Devices, Platforms, Decisions, and Deployments Ben Hoffman IDC OPINION IDC recently fielded results for its Enterprise Mobile Device
Survey The State of Mobility in the Enterprise in 2014: An IDC Survey of Devices, Platforms, Decisions, and Deployments Ben Hoffman IDC OPINION IDC recently fielded results for its Enterprise Mobile Device
Unified Security, ATP and more
 SYMANTEC Unified Security, ATP and more TAKE THE NEXT STEP Martin Werner PreSales Consultant, Symantec Switzerland AG MEET SWISS INFOSEC! 27.01.2016 Unified Security 2 Symantec Enterprise Security Users
SYMANTEC Unified Security, ATP and more TAKE THE NEXT STEP Martin Werner PreSales Consultant, Symantec Switzerland AG MEET SWISS INFOSEC! 27.01.2016 Unified Security 2 Symantec Enterprise Security Users
IDC MarketScape: Worldwide Oracle Implementation Services Ecosystem 2014 Vendor Assessment
 IDC MARKETSCAPE IDC MarketScape: Worldwide Oracle Implementation Services Ecosystem 2014 Vendor Assessment Ali Zaidi Gard Little Chad Huston THIS IDC MARKETSCAPE EXCERPT FEATURES: ACCENTURE IDC MARKETSCAPE
IDC MARKETSCAPE IDC MarketScape: Worldwide Oracle Implementation Services Ecosystem 2014 Vendor Assessment Ali Zaidi Gard Little Chad Huston THIS IDC MARKETSCAPE EXCERPT FEATURES: ACCENTURE IDC MARKETSCAPE
Allstate Getting Much More from Its IT Services with ServiceNow Cloud-Based IT Service Management Solution
 IDC ExpertROI SPOTLIGHT Allstate Getting Much More from Its IT Services with ServiceNow Cloud-Based IT Service Management Solution Sponsored by: ServiceNow Matthew Marden March 2015 Overview The Allstate
IDC ExpertROI SPOTLIGHT Allstate Getting Much More from Its IT Services with ServiceNow Cloud-Based IT Service Management Solution Sponsored by: ServiceNow Matthew Marden March 2015 Overview The Allstate
Incorporating Mobility into a Customer Experience Strategy
 INSIGHT Incorporating Mobility into a Customer Experience Strategy Michael Fauscette IDC OPINION IDC believes that mobility must be a part of any customer experience (CX) strategy. Consistent engagement
INSIGHT Incorporating Mobility into a Customer Experience Strategy Michael Fauscette IDC OPINION IDC believes that mobility must be a part of any customer experience (CX) strategy. Consistent engagement
WHITE PAPER Cloud-Based, Automated Breach Detection. The Seculert Platform
 WHITE PAPER Cloud-Based, Automated Breach Detection The Seculert Platform Table of Contents Introduction 3 Automatic Traffic Log Analysis 4 Elastic Sandbox 5 Botnet Interception 7 Speed and Precision 9
WHITE PAPER Cloud-Based, Automated Breach Detection The Seculert Platform Table of Contents Introduction 3 Automatic Traffic Log Analysis 4 Elastic Sandbox 5 Botnet Interception 7 Speed and Precision 9
IDC MarketScape: Worldwide Supply Chain Management Business Consulting Services 2014 Vendor Assessment
 IDC MARKETSCAPE IDC MarketScape: Worldwide Supply Chain Management Business Consulting Services 2014 Vendor Assessment Cushing Anderson Simon Ellis THIS IDC MARKETSCAPE EXCERPT FEATURES EY IDC MARKETSCAPE
IDC MARKETSCAPE IDC MarketScape: Worldwide Supply Chain Management Business Consulting Services 2014 Vendor Assessment Cushing Anderson Simon Ellis THIS IDC MARKETSCAPE EXCERPT FEATURES EY IDC MARKETSCAPE
The Benefits of an Integrated Approach to Security in the Cloud
 The Benefits of an Integrated Approach to Security in the Cloud Judith Hurwitz President and CEO Marcia Kaufman COO and Principal Analyst Daniel Kirsch Senior Analyst Sponsored by IBM Introduction The
The Benefits of an Integrated Approach to Security in the Cloud Judith Hurwitz President and CEO Marcia Kaufman COO and Principal Analyst Daniel Kirsch Senior Analyst Sponsored by IBM Introduction The
Impact of Juniper Training and Certification on Network Management Activities
 WHITE PAPER Impact of Juniper Training and Certification on Network Management Activities Sponsored by: Juniper Networks Cushing Anderson January 2014 IDC OPINION IDC believes sufficient training and appropriate
WHITE PAPER Impact of Juniper Training and Certification on Network Management Activities Sponsored by: Juniper Networks Cushing Anderson January 2014 IDC OPINION IDC believes sufficient training and appropriate
How Collaboration Can Help Achieve Your Business Goals: A European Perspective
 ANALYST CONNECTION How Collaboration Can Help Achieve Your Business Goals: A European Perspective Commissioned by: Verizon and Cisco Jason Andersson July 2015 Marta Muñoz Méndez-Villamil THE POWER OF COLLABORATION
ANALYST CONNECTION How Collaboration Can Help Achieve Your Business Goals: A European Perspective Commissioned by: Verizon and Cisco Jason Andersson July 2015 Marta Muñoz Méndez-Villamil THE POWER OF COLLABORATION
Advanced Threats: The New World Order
 Advanced Threats: The New World Order Gary Lau Technology Consulting Manager Greater China [email protected] 1 Agenda Change of Threat Landscape and Business Impact Case Sharing Korean Incidents EMC CIRC
Advanced Threats: The New World Order Gary Lau Technology Consulting Manager Greater China [email protected] 1 Agenda Change of Threat Landscape and Business Impact Case Sharing Korean Incidents EMC CIRC
Worldwide DDI Market Update
 Update Worldwide DDI Market Update Nolan Greene Petr Jirovsky IN THIS UPDATE This IDC update reviews the revenue and shipments of the worldwide DDI (DNS, DHCP, and IP address management [IPAM]) solutions
Update Worldwide DDI Market Update Nolan Greene Petr Jirovsky IN THIS UPDATE This IDC update reviews the revenue and shipments of the worldwide DDI (DNS, DHCP, and IP address management [IPAM]) solutions
Windows Server 2003 Migration: Take a Fresh Look at Your IT Infrastructure
 EXECUTIVE BRIEF Windows Server 2003 Migration: Take a Fresh Look at Your IT Infrastructure Sponsored by: Symantec Carla Arend December 2014 Andrew Buss IDC Opinion Microsoft will be ending Extended Support
EXECUTIVE BRIEF Windows Server 2003 Migration: Take a Fresh Look at Your IT Infrastructure Sponsored by: Symantec Carla Arend December 2014 Andrew Buss IDC Opinion Microsoft will be ending Extended Support
Cloud-Managed WiFi Set to Grow to $2.5 Billion by 2018
 Insight Cloud-Managed WiFi Set to Grow to $2.5 Billion by 2018 Nolan Greene Curtis Price Rohit Mehra IDC OPINION The worldwide enterprise wireless (WLAN) market for cloud-managed WiFi reached $334.0 million
Insight Cloud-Managed WiFi Set to Grow to $2.5 Billion by 2018 Nolan Greene Curtis Price Rohit Mehra IDC OPINION The worldwide enterprise wireless (WLAN) market for cloud-managed WiFi reached $334.0 million
Accenture Intelligent Security for the Digital Enterprise. Archer s important role in solving today's pressing security challenges
 Accenture Intelligent Security for the Digital Enterprise Archer s important role in solving today's pressing security challenges The opportunity to improve cyber security has never been greater 229 2,287
Accenture Intelligent Security for the Digital Enterprise Archer s important role in solving today's pressing security challenges The opportunity to improve cyber security has never been greater 229 2,287
Worldwide Advanced and Predictive Analytics Software Market Shares, 2014: The Rise of the Long Tail
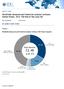 MARKET SHARE Worldwide Advanced and Predictive Analytics Software Market Shares, 2014: The Rise of the Long Tail Alys Woodward Dan Vesset IDC MARKET SHARE FIGURE FIGURE 1 Worldwide Advanced and Predictive
MARKET SHARE Worldwide Advanced and Predictive Analytics Software Market Shares, 2014: The Rise of the Long Tail Alys Woodward Dan Vesset IDC MARKET SHARE FIGURE FIGURE 1 Worldwide Advanced and Predictive
