EMB. Basics. Goals of this lab: Prerequisites: LXB, NET, DNS
|
|
|
- Derek Mitchell
- 10 years ago
- Views:
Transcription
1 EMB Basics Goals of this lab: Learn how works under the hood Learn about spam filtering and virus scanning Gain experience setting up a full-fledged service Prerequisites: LXB, NET, DNS REVISION: 2.1 [ ] DAVID BYERS
2
3 Table of Contents PREPARATION... 1 Exercise 1: Review and preparation... 1 MAIN LAB... 3 Part 1: Basic mail server... 3 Exercise 2: Mail server installation and basic configuration... 4 Exercise 3: About the mail server... 4 DNS and mail service... 4 Exercise 4: Configure DNS for service... 4 Part 2: End user support... 5 Exercise 5: Implement IMAP server... 5 Expert options... 5 Part 3: Intermediate mail service... 5 User-friendly addresses... 6 Exercise 6: Configuring user-friendly addresses... 6 Spam protection... 6 Exercise 7: Questions about spam filtering... Error! Bookmark not defined. Exercise 8: Implementing spam filtering... 7 Virus filtering (optional)... 8 Exercise 9: Questions about server-based virus scanning... 8 Exercise 10: Implementation of virus scanning... 8 Expert options... 8 IDA/ADIT EMB: BASICS
4 IDA/ADIT EMB: BASICS
5 PREPARATION Do these exercises before proceeding to the main lab. You should be able to complete them using only the on-line Postfix documentation and a computer networks textbook. Exercise 1: Review and preparation Read the documentation for Postfix (or the mail server of your choice) and answer the following questions: 1-1 What processes does the mail server consist of? What does each of the processes do? 1-2 How can your mail server communicate with external programs that process mail (e.g. spam filters or virus scanners)? 1-3 What does a typical SMTP dialog look like? Show how to send a simple using the SMTP protocol. Answers to the questions above. Exercise 2: Spam protection 2-1 What type(s) of spam filtering does Spamassassin provide? 2-2 How does greylisting work? Under what circumstances could greylisting cause problems (e.g. non-acceptance of legitimate , or excessive delays)? 2-3 If users insist on challenge-response spam filtering, how can the third party impact be minimized (ideally nearly eliminated)? 2-4 What is SPF? What is DKIM? How do they prevent spam (and do they actually work)? Answers to all questions above. IDA/ADIT EMB: BASICS 1
6
7 MAIN LAB In this lab you will install and configure a complete mail system, complete from both a network and user point of view. Note that mail should work equally well on the clients as well as the server. A good test of the system is to send from a client to an external address and check that all headers in the are correct. Since you do not have access to a graphic display on the UML instances it is tricky to use graphical clients like Mozilla Thunderbird to read . An alternative that many seem to think works well is to use the text-base client mu t t. If you want to run software that relies on X from your UML instances you could also install necessary packages and login on the client from a lab workstation using ssh. Just make sure that X11 forwarding is enabled. Time taken 2006: 20-30h, average 25h Past problems: This lab has seen the widest variety of problems of any lab in the past, which is reflected in the large variation in time taken. Since the mail system is not only complex in itself, but also interfaces with nearly every other part of the system, there are lots of problem sources, and lots of ways to make mistakes. Therefore, it is vital to work professionally on this lab. That means understanding the software and its interactions with e.g. DNS, the network, the file system and the directory service; understanding the entire configuration and exactly what the role of every configuration statement is; and understanding how incoming and outgoing mail is processed, where files are stored and what is logged. It also means taking small, well-thought-out steps and confirming through testing that each step does exactly what it is supposed to do. You have to slow down if you want to reach the finish line as fast as possible. Part 1: Basic mail server There are lots of different mail servers available. In this course we recommend that beginners use the Postfix mail server. It is a high-quality production mail server that nevertheless is fairly easy to configure. More experienced students may want to try their hand at the classic sendmai l software. It is a bit more difficult to handle than Postfix, but infinitely more flexible. All Debian Gnu/Linux hosts must have a mail server. For hosts that will only forward all mail to another server, Postfix and sendmai l are overkill. Many Debian users like to use e x mh for such hosts, but an even simpler system, such as ssmt p will do the job equally well. You are strongly advised not to install qmai l unless you have previous experience with it. Before starting to install the mail server you must know what your goals are. Read the documentation first and prepare your installation in detail. Postfix documentation is available at and in the Postfix installation itself (man pages and example configuration files). Note that access to port 25 (SMTP) is filtered at the ingress to the university network. This means that you will not be able to send mail to your network from hosts outside the university. You can, however, send mail from your student account. Testing tip: When testing, try to keep the interactions between parts of the system to a minimum. For example, when testing if your server can receive mail, it is a good idea to start with a test case in which IDA/ADIT EMB: BASICS 3
8 you run SMTP manually using e.g. telnet to connect to the server. That way, you won t encounter problems with e.g. the mail user agent or DNS (which isn t completely configured for mail yet). Once you know raw SMTP is working, you should have a test case that involves a mail user agent. Similarly, when testing whether a client can send mail through your server, you should try manual SMTP first, perhaps followed by use of the sendmai l command on the client, and only when that works try using a MUA. Exercise 3: Mail server installation and basic configuration 3-1 Install the mail server of your choice. If you are unsure what to install, use Postfix. Your initial installation should meet the following requirements (minimum): (a) (b) (c) (d) Accept mail from any SMTP server in the world. Be able to send mail to any SMTP server in the world. Not accept mail for any other destinations than your domain. Meet the requirements of RFC 2821, section concerning the postmaster address. 3-2 Configure your clients to always use your mail server for outgoing mail. Client configuration is quite simple: they forward everything, untouched, to the central mail server. Clients must not accept connections from outside computers. Automated test cases that verify that your system meets the requirements. m When you have come this far you should understand how the server works. The following questions test your knowledge of key parts of the mail server. You should not proceed beyond this point before you can answer these questions, or you are likely to run into problems later. Exercise 4: About the mail server 4-1 Answer the following questions about your mail server: (a) (b) (c) (d) (e) (f) DNS and mail service What configuration files does the software use and what are they for? Which command displays the current queue of outgoing mail? Where is incoming stored before being delivered? Where is outgoing queued before delivery? Where does the mail server log messages about delivery? To where (directory and/or file) and in what format does the mail server deliver mail to end users? Answers to the questions above. For service to really work, you will need to configure DNS correctly. When an message is to be delivered, a DNS-aware mail server (which means pretty much every mail server currently running) will search for an MX record for the recipient s domain. MX records indicate hosts that can accept mail for a particular domain (known as Mail exchangers). Each domain may have several MXs, each with a priority. In your case there should be a single MX your mail server. Testing tip: When testing the following exercise, start by testing DNS alone, before you try delivering mail in a way that depends on DNS. That way, if you run in to problems with mail delivery, at least you know that DNS is functioning properly. Exercise 5: Configure DNS for service 5-1 Add the appropriate resource record(s) to your DNS server. No report required. IDA/ADIT EMB: BASICS 4
9 Part 2: End user support Sending mail isn t enough. Users tend to want to read mail as well (strange as that may sound). Today, the preferred way to read mail in a client-server setting is the IMAP protocol. You will implement a basic IMAP server on your system. The recommended IMAP server is Courier. However, Courier requires that your mail server delivers mail to users in so-called maildir format (the default delivery format is usually mbox format). If you are unwilling to reconfigure your mail server to deliver mail in maildir format, consider using uw-imapd as the IMAP server instead. You are advised not to use Cyrus. The Cyrus IMAP server is very capable, but its strengths are in environments with a high volume of mail and a very large number of users. It is not well suited to small installations. When installing the IMAP server, one of the things you need to check is that the IMAP server s idea of where and in what format user mailboxes are matches the mail server s. For example, if the IMAP server expects mail to be delivered in maildir format to a directory in the user s home directory, but the SMTP server delivers to mbox files in /var/mail, you won t be able to read mail using IMAP. Users must be able to read via IMAP from both your server and clients. Testing tip: As with SMTP, you should at least consider having a basic test case in which you run IMAP manually to ensure that you can distinguish failures in the IMAP software from other failures (e.g. networking, DNS or client configuration). You should also test IMAP with a real client, such as mutt or thunderbird (and these can be run on any computer on the Internet). Troubleshooting tip: In the past, a few groups have had a lot of problems with this part (most haven t). If you do run in to problems, you need to understand how IMAP works. That way, you can run a manual IMAP session (so you can see if the problems you have are in the client or on the server) and you can snoop the IMAP session (using wi r eshar k or by setting up a relay using socat ask your lab assistant for help) and understand what s going on. Exercise 6: Implement IMAP server 6-1 Install and configure and IMAP server that users on your clients and on the lab workstations can connect to, to read Where and in what format does your IMAP server expect user mailboxes to be? Automated test cases that verify that your system meets the requirements. If you elect to use Courier, then install the fam package first. Otherwise courier may not work correctly. Expert options If you want to try your hand at a more realistic implementation, configure SSL support in the IMAP server. Real sites will have SSL enabled to avoid sending passwords in the clear. If you want to test IMAP over SSL, you should be able to use socat to make the connection (rather than t el net ). If your IMAP server doesn t support SSL natively, then use st unnel as a frontend. Part 3: Intermediate mail service m Your mail service up to this point is technically adequate, but would not meet end-user demands. You still need some basic configuration and some add-on services. The clamav and spamassassin (spamd) processes (spam and virus filtering) use a lot of memory. Your server is configured to have 128Mb of memory by default, but the default configurations of these tools will almost certainly exhaust that. If you start running in to memory problems, stop the spamassassin and clamav processes, then configure the start scripts of spamassassin to start just one child process. If you still run in to problems, you may consider not running spamassassin and clamav as daemon processes, but start them on each incoming mail. IDA/ADIT EMB: BASICS 5
10 User-friendly addresses At this point, all outgoing mail probably has your mail server s fully qualified domain name as the sender domain. This is generally undesirable as you don t want to expose the mail server s name to end users. Furthermore, many organizations like outgoing mail to be stripped of internal user IDs. A common (but seriously flawed) system is to have outgoing mail look like it is sent from firstname.lastname@domain instead of userid@domain, which is what you would get with no special configuration. Transforming addresses like this is an example of address rewriting, a major function of all mail servers. Other examples of address rewriting include appending a domain name to sender addresses that don t have one and converting between different address formats. One thing to keep in mind is that rewriting rules are applied in a specific order, and may be very specific in what they rewrite. When working with address rewriting, make sure you know which order the various rules are applied in, and exactly to what, and how, each rule is applied. You will need to review both the Postfix manual (if you are using Postfix) and the manual pages for the various files involved. Exercise 7: Configuring user-friendly addresses 7-1 Configure your server so that all outgoing mail has your domain name, without any host name, to the right of sign, regardless of which machine the was sent from. No configuration is to be done on the clients; just on the server. 7-2 What are aliases and how are they configured? 7-3 Configure your server to accept mail to firstname.lastname@your-domain. Mail must be delivered to the appropriate user. There are at least three different ways of doing this some of which involve rewriting the address, and some of which that don t. Solutions that don t involve address rewriting are typically easier to work with. 7-4 What are sender canonical maps, and how are they configured? 7-5 Configure your server to rewrite outgoing mail addresses to firstname.lastname format automatically. For this to work, you may need to configure your clients to send all mail without the hostname, with only the hostname, or with something like localhost.localdomain after sign; the documentation on the address rewriting method you use explains why. 7-6 Formulate a policy for firstname.lastname addresses that is suitable for a large organization and that specifies how to handle naming conflicts in a consistent, fair and management-acceptable way. Spam protection Automated test cases that verify that your system meets the requirements. Every server today needs strong spam protection. Spam protection is a fairly hard problem. There are a number of concerns that must be dealt with: False positives False positives are non-spam messages that the system (incorrectly) detects as spam. False positives generally result in customers complaining about lost . False negatives False negatives are spam messages that are not detected as such. False negatives generally result in customers complaining about spam. Processing time Spam filtering can be resource intensive. A large mail system may need several dedicated high-end computers to do nothing but spam filtering. That generally results in complaints from management about costs. 3 rd party impact Spam filtering should never impact a third party (i.e. anyone other than the evil spammer and good-as-gold victim). I ll rant about that a little later. There are a number of different types of spam protection. Some types include content filters, DNSbased blacklists, challenge-response protocols and protocol hacks. IDA/ADIT EMB: BASICS 6
11 Content filters These tools look at the content of each message and use keywords, combinations of keywords, and other features to determine if a message is spam. Content filters can be static or dynamic. Static content filters are like expert systems, with a set of fixed rules that are applied to each message. Dynamic filters learn from example; each individual user must train the filter by indicating messages that are spam and messages that aren t. The filter will automatically learn to distinguish one from the other. Static content filters are fairly effective if the set of rules is updated frequently, and are suitable in installations with multiple users. Dynamic content filters are extremely effective, but each user must train the filter individually, or the number of false positives and false negatives will be too high. Static content filters are resource intensive. DNS-based blacklists DNS-based blacklists use special DNS servers to determine if the sending host is a legitimate sender. Blacklists can also be used to detect if a message has passed through a known open relay or otherwise insecure system (this is a good indication of spam). DNS-based blacklists are fast, but controversial as the policies of the publishers are not always clear and can be somewhat draconian. Challenge-response Challenge-response protocols are extremely effective at preventing spam, but they accomplish this by impacting third parties. Challenge-response systems will reply to messages from unknown senders with a challenge, which the sender must respond to (usually with another or by visiting a web site). Since most spammers use forged sender addresses, and often use valid addresses, challenges to spam messages tend to go to uninvolved third parties. In effect, users of challenge-response spam filters are making other people manually filter their spam for them. Protocol hacks Some newer methods of filtering use protocol hacks to determine if a message is spam or not. For example, SPF (Sender Protected Framework) uses DNS records to indicate valid originating mail servers for a domain (thus making it harder to forge senders in that domain), and Greylisting uses the SMTP protocol to implement what nearly amounts to a challenge-response protocol without the third party impact. Other possibilities also exist, but few are in widespread deployment. Nolisting exploits how DNS lookups for servers are supposed to be done. Exercise 8: Implementing spam filtering 8-1 Configure your mail server so Spamassassin can examine each message before it is delivered. Spam should be marked as such, but not bounced or deleted. Use spamc/spamd. 8-2 Implement greylisting in your mail server. Ensure that local clients are not subjected to greylisting. 8-3 Configure your DNS server to include SPF records for your domain. The only acceptable as a source of from your domain is your server. The SPF record should reflect this. Automated test cases that verify that your system meets the requirements. Testing tip: When testing spam filtering you need a message that will be categorized as spam. Most spam filters will react to the Generic Test for Unsolicited Bulk test string. See for more information. Testing tip: Your tests for greylisting should include manual SMTP sessions. In fact, this is the easiest way to test that greylisting works, once you understand how it is supposed to work. This is also a good time to do some regression testing to ensure that your own clients can still send mail without it being greylisted. If you find that your clients are unable to send mail (or are subject to greylisting) at this point, you probably need to review the configuration changes you made, to ensure that you are aware of all the implications of the changes. Testing tip: Testing SPF requires either a testing service or a mail server that uses SPF records. If you have access to a GMail account, you can view all the headers of mail sent mail to it from your system IDA/ADIT EMB: BASICS 7
12 and see how it reacts to your SPF records. You can also use the on-line SPF tester at Virus filtering (optional) This section is optional. If you want to try your hand at setting up a more complete service, then proceed, but if you ve had enough of configuration, stop. Your mail server should have good protection against viruses. Since many viruses are delivered by today it has become common practice to implement server-side virus protection, even on Unix type mail systems. Today, there are a great number of both commercial and free alternatives to choose from. Exercise 9: Questions about server-based virus scanning 9-1 What is the most important benefit of server-based virus scanning over client-based virus scanning (where each client scans for viruses in incoming messages)? Answers to the questions above. Regrettably, many implementations of server-based virus filters have a high impact on third parties. For various reasons, server-based virus scanning is often done after the SMTP dialog is completed (scanning is resource intensive, and some antivirus products do not integrate well with mail servers). Many antivirus products are configured by default to send a reply to the originator of the virus-infected . Unfortunately, this reply is hardly ever seen by the real sender (whose host is infected) since practically every virus forges the sender address. Exercise 10: Implementation of virus scanning 10-1 Implement server-based virus scanning on your mail server. Use ClamAV for virus scanning. If a virus is detected, you should not reply to the sender. It is acceptable to either notify the recipient that a virus has been found, or generate an SMTP error message (this assumes that scanning takes place during the SMTP dialog). Automated test cases that verify that your system meets the requirements. Combining virus filtering and spam filtering with amavisd-new Amavisd-new is free software which can be used to connect an server with other programs, and it is quite simple to set up. One problem with amavisd-new is that it prevents spamassassin from rewriting headers, so if you choose to use amavisd-new, you need to think hard about how to make spam filtering really work (and how to demonstrate it). If you are planning to use amavisd-new together with Postfix, LMTP is the preferred solution. Expert options If you want to try your hand at some more advanced SMTP configuration, you could try implementing support for SSL (encrypted connections) either using a dedicated port for SMTP over SSL or by supporting STARTTLS. You can also implement SMTP authentication, so that users can use your mail server to send mail even if they are not on your network, as long as they can authenticate. If you want to test SMTP over SSL (not sure if this can be made to work with STARTTLS) you should be able to use socat to make the connection (rather than t el net ). IDA/ADIT EMB: BASICS 8
13 FEEDBACK FORM EMB Complete this feedback form individually at the end of the lab and hand it to the lab assistant when you finish. Your feedback is essential for improving the labs. Each student should hand in a feedback form. Do not cooperate on completing the form. You do not need to put your name on the feedback form. Your feedback will be evaluated the same way regardless of whether your name is on it or not. Your name is valuable to us in case you have made and comments in the last section that need clarifications or otherwise warrant a follow-up. For each section, please rate the following (range 1 to 5 in all cases). Difficulty: Rate the degree of difficulty (1=too easy, 5=too difficult) Learning: Rate your learning experience (1=learned nothing, 5=learned a lot). Interest: Rate your interest level after completing the part (1=no interest, 5=high interest). Time: How long did the part take to complete (in minutes)? Difficulty Learning Interest Time (minutes) Preparation Part 1: Basic mail server Part 2: End user support Part 3: Intermediate mail service Overall Please answer the following questions: What did you like about this lab? What did you dislike about this lab? Make a suggestion to improve this lab. IDA/ADIT EMB: BASICS
14
15 FEEDBACK FORM EMB Complete this feedback form individually at the end of the lab and hand it to the lab assistant when you finish. Your feedback is essential for improving the labs. Each student should hand in a feedback form. Do not cooperate on completing the form. You do not need to put your name on the feedback form. Your feedback will be evaluated the same way regardless of whether your name is on it or not. Your name is valuable to us in case you have made and comments in the last section that need clarifications or otherwise warrant a follow-up. For each section, please rate the following (range 1 to 5 in all cases). Difficulty: Rate the degree of difficulty (1=too easy, 5=too difficult) Learning: Rate your learning experience (1=learned nothing, 5=learned a lot). Interest: Rate your interest level after completing the part (1=no interest, 5=high interest). Time: How long did the part take to complete (in minutes)? Difficulty Learning Interest Time (minutes) Preparation Part 1: Basic mail server Part 2: End user support Part 3: Intermediate mail service Overall Please answer the following questions: What did you like about this lab? What did you dislike about this lab? Make a suggestion to improve this lab. IDA/ADIT EMB: BASICS
Mail system components. Electronic Mail MRA MUA MSA MAA. David Byers
 Electronic Mail PRINCIPLES DNS ARCHITECTURES SPAM Mail system components () () David Byers MRA [email protected] IDA/ADIT/IISLAB Mail User Agent Reads and writes e-mail Writes e-mail to using (usually)
Electronic Mail PRINCIPLES DNS ARCHITECTURES SPAM Mail system components () () David Byers MRA [email protected] IDA/ADIT/IISLAB Mail User Agent Reads and writes e-mail Writes e-mail to using (usually)
A D M I N I S T R A T O R V 1. 0
 A D M I N I S T R A T O R F A Q V 1. 0 2011 Fastnet SA, St-Sulpice, Switzerland. All rights reserved. Reproduction in whole or in part in any form of this manual without written permission of Fastnet SA
A D M I N I S T R A T O R F A Q V 1. 0 2011 Fastnet SA, St-Sulpice, Switzerland. All rights reserved. Reproduction in whole or in part in any form of this manual without written permission of Fastnet SA
POP3 Connector for Exchange - Configuration
 Eclarsys PopGrabber POP3 Connector for Exchange - Configuration PopGrabber is an excellent replacement for the POP3 connector included in Windows SBS 2000 and 2003. It also works, of course, with Exchange
Eclarsys PopGrabber POP3 Connector for Exchange - Configuration PopGrabber is an excellent replacement for the POP3 connector included in Windows SBS 2000 and 2003. It also works, of course, with Exchange
1 Accessing E-mail accounts on the Axxess Mail Server
 1 Accessing E-mail accounts on the Axxess Mail Server The Axxess Mail Server provides users with access to their e-mail folders through POP3, and IMAP protocols, or OpenWebMail browser interface. The server
1 Accessing E-mail accounts on the Axxess Mail Server The Axxess Mail Server provides users with access to their e-mail folders through POP3, and IMAP protocols, or OpenWebMail browser interface. The server
Mail Avenger. David Mazières New York University
 Mail Avenger David Mazières New York University Early design goals for email Work over weakly connected networks - E.g., early Internet, UUCP, etc. - Move mail closer to recipient whenever you can... -
Mail Avenger David Mazières New York University Early design goals for email Work over weakly connected networks - E.g., early Internet, UUCP, etc. - Move mail closer to recipient whenever you can... -
Exim4U. Email Server Solution For Unix And Linux Systems
 Email Server Solution For Unix And Linux Systems General Overview, Feature Comparison and Screen Shots Exim4U Email Server Solution For Unix And Linux Systems Version 2.x.x October 12, 2012 Copyright 2009
Email Server Solution For Unix And Linux Systems General Overview, Feature Comparison and Screen Shots Exim4U Email Server Solution For Unix And Linux Systems Version 2.x.x October 12, 2012 Copyright 2009
Email Getting Started Guide Unix Platform
 Edition/Issue Email Getting Started Guide Unix Platform One of the most important features of your new Web Hosting account is access to a personalized Email solution that includes individual Email addresses
Edition/Issue Email Getting Started Guide Unix Platform One of the most important features of your new Web Hosting account is access to a personalized Email solution that includes individual Email addresses
IRMACS E-Mail Setup. Your IRMACS e-mail is available internally by the IMAP protocol. The server settings used are:
 IRMACS E-Mail Setup General Information This document covers both the default Apple OSX mail client and the installed Mozilla s Thunderbird mail client. If you are comfortable setting up your own mail
IRMACS E-Mail Setup General Information This document covers both the default Apple OSX mail client and the installed Mozilla s Thunderbird mail client. If you are comfortable setting up your own mail
Ficha técnica de curso Código: IFCAD241
 Curso de: Linux E-mail. Set up, maintain, and secure a small office e- mail server Objetivos: Aprender a instalar, mantener y securizar un correo en un sistema linux. Destinado a: Todo administrador de
Curso de: Linux E-mail. Set up, maintain, and secure a small office e- mail server Objetivos: Aprender a instalar, mantener y securizar un correo en un sistema linux. Destinado a: Todo administrador de
Avira Managed Email Security (AMES) User Guide
 Avira Managed Email Security (AMES) User Guide 1 Product information... 3 1.1 Functionality... 3 1.2 Licensing AMES... 3 2 Getting started with AMES... 4 2.1 Adding a new domain to AMES... 4 2.2 Logging
Avira Managed Email Security (AMES) User Guide 1 Product information... 3 1.1 Functionality... 3 1.2 Licensing AMES... 3 2 Getting started with AMES... 4 2.1 Adding a new domain to AMES... 4 2.2 Logging
Security. Help Documentation
 Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc. Security Antivirus Administration SmarterMail is equipped with
Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc. Security Antivirus Administration SmarterMail is equipped with
Guardian Digital Secure Mail Suite Quick Start Guide
 Guardian Digital Secure Mail Suite Quick Start Guide Copyright c 2004 Guardian Digital, Inc. Contents 1 Introduction 1 2 Contacting Guardian Digital 2 3 Purpose of This Document 3 3.1 Terminology...............................
Guardian Digital Secure Mail Suite Quick Start Guide Copyright c 2004 Guardian Digital, Inc. Contents 1 Introduction 1 2 Contacting Guardian Digital 2 3 Purpose of This Document 3 3.1 Terminology...............................
CipherMail Gateway Quick Setup Guide
 CIPHERMAIL EMAIL ENCRYPTION CipherMail Gateway Quick Setup Guide October 10, 2015, Rev: 9537 Copyright 2015, ciphermail.com. CONTENTS CONTENTS Contents 1 Introduction 4 2 Typical setups 4 2.1 Direct delivery............................
CIPHERMAIL EMAIL ENCRYPTION CipherMail Gateway Quick Setup Guide October 10, 2015, Rev: 9537 Copyright 2015, ciphermail.com. CONTENTS CONTENTS Contents 1 Introduction 4 2 Typical setups 4 2.1 Direct delivery............................
Configuring Your Gateman Email Server
 Configuring Your Gateman Email Server Your Gateman Lifestyle Server includes an Email Server that provides users access to email via an email client and via your web browser using your laptop and mobile
Configuring Your Gateman Email Server Your Gateman Lifestyle Server includes an Email Server that provides users access to email via an email client and via your web browser using your laptop and mobile
Hosted CanIt. Roaring Penguin Software Inc. 26 April 2011
 Hosted CanIt Roaring Penguin Software Inc. 26 April 2011 1 1 Introduction Thank you for selecting Hosted CanIt. This document explains how Hosted CanIt works and how you should configure your network to
Hosted CanIt Roaring Penguin Software Inc. 26 April 2011 1 1 Introduction Thank you for selecting Hosted CanIt. This document explains how Hosted CanIt works and how you should configure your network to
Email Reputation Metrics Troubleshooter. Share it!
 Email Reputation Metrics Troubleshooter page: 1 Email Reputation Metrics Troubleshooter Written By Dale Langley Dale has been working with clients to improve their email deliverability and response rates,
Email Reputation Metrics Troubleshooter page: 1 Email Reputation Metrics Troubleshooter Written By Dale Langley Dale has been working with clients to improve their email deliverability and response rates,
Implementing MDaemon as an Email Security Gateway to Exchange Server
 Implementing MDaemon as an Email Security Gateway to Exchange Server Introduction MDaemon is widely deployed as a very effective antispam/antivirus gateway to Exchange. For optimum performance, we recommend
Implementing MDaemon as an Email Security Gateway to Exchange Server Introduction MDaemon is widely deployed as a very effective antispam/antivirus gateway to Exchange. For optimum performance, we recommend
SMTP Servers. Determine if an email message should be sent to another machine and automatically send it to that machine using SMTP.
 SMTP Servers SMTP: Simple Mail Transfer Protocol (TCP Port 25) The Simple Mail Transfer Protocol (SMTP) is an Internet standard for transferring electronic mail between computers. UNIX systems implement
SMTP Servers SMTP: Simple Mail Transfer Protocol (TCP Port 25) The Simple Mail Transfer Protocol (SMTP) is an Internet standard for transferring electronic mail between computers. UNIX systems implement
English Translation of SecurityGateway for Exchange/SMTP Servers
 Testing: Alt N Technologies SecurityGateway by Sandra Lucifora Administrators spend a considerable amount of their time on the job on eliminating unwanted messages. Viruses, Phishing, and Spoofing pose
Testing: Alt N Technologies SecurityGateway by Sandra Lucifora Administrators spend a considerable amount of their time on the job on eliminating unwanted messages. Viruses, Phishing, and Spoofing pose
Aloaha Mail and Archive
 Aloaha Mail and Archive Aloaha Mail and Archive is an email archiving solution that can archive inbound-, internal and outbound emails directly and transparently into a central mailstore. Additionally
Aloaha Mail and Archive Aloaha Mail and Archive is an email archiving solution that can archive inbound-, internal and outbound emails directly and transparently into a central mailstore. Additionally
Libra Esva. Whitepaper. Glossary. How Email Really Works. Email Security Virtual Appliance. May, 2010. It's So Simple...or Is It?
 Libra Esva Email Security Virtual Appliance Whitepaper May, 2010 How Email Really Works Glossary 1 2 SMTP is a protocol for sending email messages between servers. DNS (Domain Name System) is an internet
Libra Esva Email Security Virtual Appliance Whitepaper May, 2010 How Email Really Works Glossary 1 2 SMTP is a protocol for sending email messages between servers. DNS (Domain Name System) is an internet
Avira AntiVir MailGate 3.2 Release Notes
 Release Notes 1. Features 1.1 Assigning recipient addresses to groups either by using Active Directory or a plain text file 1.1.1 Using a Active Directory server MailGate communicates with Active Directory
Release Notes 1. Features 1.1 Assigning recipient addresses to groups either by using Active Directory or a plain text file 1.1.1 Using a Active Directory server MailGate communicates with Active Directory
Email Gateways Using MDaemon 6.0
 Email Gateways Using MDaemon 6.0 Alt-N Technologies, Ltd 1179 Corporate Drive West, #103 Arlington, TX 76006 Tel: (817) 652-0204 2002 Alt-N Technologies. All rights reserved. Product and company names
Email Gateways Using MDaemon 6.0 Alt-N Technologies, Ltd 1179 Corporate Drive West, #103 Arlington, TX 76006 Tel: (817) 652-0204 2002 Alt-N Technologies. All rights reserved. Product and company names
SPAM FILTER Service Data Sheet
 Content 1 Spam detection problem 1.1 What is spam? 1.2 How is spam detected? 2 Infomail 3 EveryCloud Spam Filter features 3.1 Cloud architecture 3.2 Incoming email traffic protection 3.2.1 Mail traffic
Content 1 Spam detection problem 1.1 What is spam? 1.2 How is spam detected? 2 Infomail 3 EveryCloud Spam Filter features 3.1 Cloud architecture 3.2 Incoming email traffic protection 3.2.1 Mail traffic
How To Ensure Your Email Is Delivered
 Everything You Need to Know About Delivering Email through Your Web Application SECTION 1 The Most Important Fact about Email: Delivery is Never Guaranteed Email is the backbone of the social web, making
Everything You Need to Know About Delivering Email through Your Web Application SECTION 1 The Most Important Fact about Email: Delivery is Never Guaranteed Email is the backbone of the social web, making
Collateral Damage. Consequences of Spam and Virus Filtering for the E-Mail System. Peter Eisentraut 22C3. credativ GmbH.
 Consequences of Spam and Virus Filtering for the E-Mail System 22C3 Introduction 12 years of spam... 24 years of SMTP... Things have changed: SMTP is no longer enough. Spam filters, virus filters are part
Consequences of Spam and Virus Filtering for the E-Mail System 22C3 Introduction 12 years of spam... 24 years of SMTP... Things have changed: SMTP is no longer enough. Spam filters, virus filters are part
XGENPLUS SECURITY FEATURES...
 Security Features Table of Contents TABLE OF CONTENTS... 2 1. INTRODUCTION... 3 2. XGENPLUS SECURITY FEATURES... 3 3. SERVER LEVEL FEATURES... 5 4. DOMAIN LEVEL FEATURES... 8 5. USER LEVEL FEATURES...
Security Features Table of Contents TABLE OF CONTENTS... 2 1. INTRODUCTION... 3 2. XGENPLUS SECURITY FEATURES... 3 3. SERVER LEVEL FEATURES... 5 4. DOMAIN LEVEL FEATURES... 8 5. USER LEVEL FEATURES...
Visendo Email Suite a reliable solution for SMBs
 Visendo Email Suite a reliable solution for SMBs Visendo offers a range of Email solutions to assist companies in meeting complex e-mail requirements Visendo Security for Email Servers Multi-engine spam
Visendo Email Suite a reliable solution for SMBs Visendo offers a range of Email solutions to assist companies in meeting complex e-mail requirements Visendo Security for Email Servers Multi-engine spam
AXIGEN Mail Server. Quick Installation and Configuration Guide. Product version: 6.1 Document version: 1.0
 AXIGEN Mail Server Quick Installation and Configuration Guide Product version: 6.1 Document version: 1.0 Last Updated on: May 28, 2008 Chapter 1: Introduction... 3 Welcome... 3 Purpose of this document...
AXIGEN Mail Server Quick Installation and Configuration Guide Product version: 6.1 Document version: 1.0 Last Updated on: May 28, 2008 Chapter 1: Introduction... 3 Welcome... 3 Purpose of this document...
eprism Email Security Appliance 6.0 Release Notes What's New in 6.0
 eprism Email Security Appliance 6.0 Release Notes St. Bernard is pleased to announce the release of version 6.0 of the eprism Email Security Appliance. This release adds several new features while considerably
eprism Email Security Appliance 6.0 Release Notes St. Bernard is pleased to announce the release of version 6.0 of the eprism Email Security Appliance. This release adds several new features while considerably
A Modular Email Architecture Using Open Source Components
 A Modular Email Architecture Using Open Source Components Presented to MVMRUG April 22, 2005 Scott Courtney Sine Nomine Associates Functional Goals SMTP inbound and outbound mail POP3 and IMAP4 mailbox
A Modular Email Architecture Using Open Source Components Presented to MVMRUG April 22, 2005 Scott Courtney Sine Nomine Associates Functional Goals SMTP inbound and outbound mail POP3 and IMAP4 mailbox
How to set up a multifunction device or application to send email using Office 365
 How to set up a multifunction device or application to send email using Office 365 Exchange Online 232 out of 424 rated this helpful Applies to: Exchange Online Topic Last Modified: 2015 10 14 You can
How to set up a multifunction device or application to send email using Office 365 Exchange Online 232 out of 424 rated this helpful Applies to: Exchange Online Topic Last Modified: 2015 10 14 You can
DNS. DNS Fundamentals. Goals of this lab: Prerequisites: LXB, NET
 DNS DNS Fundamentals Goals of this lab: Learn how the domain name system works Learn about tools to test and troubleshoot DNS Learn how to deploy a basic DNS service Prerequisites: LXB, NET REVISION: 2.0
DNS DNS Fundamentals Goals of this lab: Learn how the domain name system works Learn about tools to test and troubleshoot DNS Learn how to deploy a basic DNS service Prerequisites: LXB, NET REVISION: 2.0
Configure a Mail Server
 SECTION 3 Configure a Mail Server In this section of the workbook, you learn how to do the following: Send Mail to root on 3-3 In this exercise, you send an email to user root using the mail command and
SECTION 3 Configure a Mail Server In this section of the workbook, you learn how to do the following: Send Mail to root on 3-3 In this exercise, you send an email to user root using the mail command and
User guide Business Internet e-mail features
 User guide Business Internet e-mail features Page 1 de 1 Table of content Page Introduction 3 1. How do I access my web based e-mail? 3 2. How do I access/alter these enhancements? 3 A. Basic Features
User guide Business Internet e-mail features Page 1 de 1 Table of content Page Introduction 3 1. How do I access my web based e-mail? 3 2. How do I access/alter these enhancements? 3 A. Basic Features
Email Quick-Start Guide
 For TradeMark Media s email system Thank you for choosing TradeMark Media for your email hosting. You ve made a wise choice. TradeMark Media offers comprehensive spam and virus protection, POP3 and WebMail
For TradeMark Media s email system Thank you for choosing TradeMark Media for your email hosting. You ve made a wise choice. TradeMark Media offers comprehensive spam and virus protection, POP3 and WebMail
Domains Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc.
 Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc. Domains All Domains System administrators can use this section
Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc. Domains All Domains System administrators can use this section
Antispam Security Best Practices
 Antispam Security Best Practices First, the bad news. In the war between spammers and legitimate mail users, spammers are winning, and will continue to do so for the foreseeable future. The cost for spammers
Antispam Security Best Practices First, the bad news. In the war between spammers and legitimate mail users, spammers are winning, and will continue to do so for the foreseeable future. The cost for spammers
How To Block Ndr Spam
 How to block NDR spam Spam generates an enormous amount of traffic that is both time-consuming to handle and resource intensive. Apart from that, a large number of organizations have been victims of NDR
How to block NDR spam Spam generates an enormous amount of traffic that is both time-consuming to handle and resource intensive. Apart from that, a large number of organizations have been victims of NDR
Objective This howto demonstrates and explains the different mechanisms for fending off unwanted spam e-mail.
 Collax Spam Filter Howto This howto describes the configuration of the spam filter on a Collax server. Requirements Collax Business Server Collax Groupware Suite Collax Security Gateway Collax Platform
Collax Spam Filter Howto This howto describes the configuration of the spam filter on a Collax server. Requirements Collax Business Server Collax Groupware Suite Collax Security Gateway Collax Platform
Enhanced Spam Defence
 Enhanced Spam Defence An approach to making SMTP connect time blocking a reliable method for e-mail filtering By John Jensen, Topsec Technology Ltd. As the spam problem keeps growing and the associated
Enhanced Spam Defence An approach to making SMTP connect time blocking a reliable method for e-mail filtering By John Jensen, Topsec Technology Ltd. As the spam problem keeps growing and the associated
MailStore Server 5.0 Documentation
 MailStore Server 5.0 Documentation 2010 deepinvent Software GmbH 24. May 2011 Products that are referred to in this document may be either trademarks and/or registered trademarks of the respective owners.
MailStore Server 5.0 Documentation 2010 deepinvent Software GmbH 24. May 2011 Products that are referred to in this document may be either trademarks and/or registered trademarks of the respective owners.
INSTALLATION AND CONFIGURATION GUIDE (THIS DOCUMENT RELATES TO MDAEMON v15.5.0 ONWARDS)
 Web: Overview INSTALLATION AND CONFIGURATION GUIDE (THIS DOCUMENT RELATES TO MDAEMON v15.5.0 ONWARDS) This document provides an installation and configuration guide for MDaemon Messaging Server along with
Web: Overview INSTALLATION AND CONFIGURATION GUIDE (THIS DOCUMENT RELATES TO MDAEMON v15.5.0 ONWARDS) This document provides an installation and configuration guide for MDaemon Messaging Server along with
MDaemon configuration recommendations for dealing with spam related issues
 Web: Introduction MDaemon configuration recommendations for dealing with spam related issues Without a doubt, our most common support queries these days fall into one of the following groups:- 1. Why did
Web: Introduction MDaemon configuration recommendations for dealing with spam related issues Without a doubt, our most common support queries these days fall into one of the following groups:- 1. Why did
Analysis of Spam Filter Methods on SMTP Servers Category: Trends in Anti-Spam Development
 Analysis of Spam Filter Methods on SMTP Servers Category: Trends in Anti-Spam Development Author André Tschentscher Address Fachhochschule Erfurt - University of Applied Sciences Applied Computer Science
Analysis of Spam Filter Methods on SMTP Servers Category: Trends in Anti-Spam Development Author André Tschentscher Address Fachhochschule Erfurt - University of Applied Sciences Applied Computer Science
Anti-spam filtering techniques
 Anti-spam filtering techniques Stéphane Bortzmeyer AFNIC (.fr registry) [email protected] ITU, 19 january 2006 1 Anti-spam filtering techniques Background on this work This work started in the french Working
Anti-spam filtering techniques Stéphane Bortzmeyer AFNIC (.fr registry) [email protected] ITU, 19 january 2006 1 Anti-spam filtering techniques Background on this work This work started in the french Working
Internet Security [1] VU 184.216. Engin Kirda [email protected]
![Internet Security [1] VU 184.216. Engin Kirda engin@infosys.tuwien.ac.at Internet Security [1] VU 184.216. Engin Kirda engin@infosys.tuwien.ac.at](/thumbs/33/15826620.jpg) Internet Security [1] VU 184.216 Engin Kirda [email protected] Christopher Kruegel [email protected] Administration Challenge 2 deadline is tomorrow 177 correct solutions Challenge 4 will
Internet Security [1] VU 184.216 Engin Kirda [email protected] Christopher Kruegel [email protected] Administration Challenge 2 deadline is tomorrow 177 correct solutions Challenge 4 will
ECE Mail System Overview. Pablo J. Rebollo ECE Network Operations Center
 ECE Mail System Overview Pablo J. Rebollo ECE Network Operations Center Agenda Overview of ECE mail system How mail system works SPAM!!! ECE mail system statistics and examples Problems References Mail
ECE Mail System Overview Pablo J. Rebollo ECE Network Operations Center Agenda Overview of ECE mail system How mail system works SPAM!!! ECE mail system statistics and examples Problems References Mail
SESA Securing Email with Cisco Email Security Appliance Parts 1 and 2
 Course Overview Securing Email with Cisco Email Security Appliance (SESA) combines Parts 1 and 2 (SESA1, SESA2) into a single three day course. Students learn to use Cisco Email Security Appliances (ESA's)
Course Overview Securing Email with Cisco Email Security Appliance (SESA) combines Parts 1 and 2 (SESA1, SESA2) into a single three day course. Students learn to use Cisco Email Security Appliances (ESA's)
EFFECTIVE SPAM FILTERING WITH MDAEMON
 EFFECTIVE SPAM FILTERING WITH MDAEMON Introduction The following guide provides a recommended method for increasing the overall effectiveness of MDaemon s spam filter to reduce the level of spam received
EFFECTIVE SPAM FILTERING WITH MDAEMON Introduction The following guide provides a recommended method for increasing the overall effectiveness of MDaemon s spam filter to reduce the level of spam received
MailStore Server 7 Documentation
 MailStore Server 7 Documentation 2012 MailStore Software GmbH 11. May 2012 Products that are referred to in this document may be either trademarks and/or registered trademarks of the respective owners.
MailStore Server 7 Documentation 2012 MailStore Software GmbH 11. May 2012 Products that are referred to in this document may be either trademarks and/or registered trademarks of the respective owners.
How to Configure edgebox as an Email Server
 intelligence at the edge of the network www.critical-links.com edgebox V4.5 Introduction: The Email Server panel allows the simple configuration edgebox as an email (Sendmail) server. edgebox uses Smarthost
intelligence at the edge of the network www.critical-links.com edgebox V4.5 Introduction: The Email Server panel allows the simple configuration edgebox as an email (Sendmail) server. edgebox uses Smarthost
Table of Contents. Electronic mail. History of email (2) History of email (1) Email history. Basic concepts. Aka e-mail (or email according to Knuth)
 Table of Contents Electronic mail Aka e-mail (or email according to Knuth) Karst Koymans / Jeroen van der Ham Informatics Institute University of Amsterdam Tuesday, September 25, 2011 Email history Basic
Table of Contents Electronic mail Aka e-mail (or email according to Knuth) Karst Koymans / Jeroen van der Ham Informatics Institute University of Amsterdam Tuesday, September 25, 2011 Email history Basic
Avira Managed Email Security AMES FAQ. www.avira.com
 Avira Managed Email Security AMES FAQ www.avira.com Can AMES be used immediately after an account for our organization has been set up in the MyAccount user portal? Using your account requires a change
Avira Managed Email Security AMES FAQ www.avira.com Can AMES be used immediately after an account for our organization has been set up in the MyAccount user portal? Using your account requires a change
Installing GFI MailEssentials
 Installing GFI MailEssentials Introduction to installing GFI MailEssentials This chapter shows you how to install and configure GFI MailEssentials. GFI MailEssentials can be installed in two ways: Installation
Installing GFI MailEssentials Introduction to installing GFI MailEssentials This chapter shows you how to install and configure GFI MailEssentials. GFI MailEssentials can be installed in two ways: Installation
MDaemon Vs. Microsoft Exchange Server 2013 Standard
 Comparison Guide Vs. The following chart is a side-by-side feature comparison of and. Flex Licensing Maximum Accounts Unlimited Unlimited SMTP, POP3, DomainPOP, and MultiPOP POP3 & SMTP Only SSL / TLS
Comparison Guide Vs. The following chart is a side-by-side feature comparison of and. Flex Licensing Maximum Accounts Unlimited Unlimited SMTP, POP3, DomainPOP, and MultiPOP POP3 & SMTP Only SSL / TLS
Installation Guide. Version 1.5. May 2015 Edition 2002-2015 ICS Learning Group
 Installation Guide Version 1.5 May 2015 Edition 2002-2015 ICS Learning Group 1 Disclaimer ICS Learning Group makes no representations or warranties with respect to the contents or use of this manual, and
Installation Guide Version 1.5 May 2015 Edition 2002-2015 ICS Learning Group 1 Disclaimer ICS Learning Group makes no representations or warranties with respect to the contents or use of this manual, and
Plesk 7.6 For Windows E-mail User Guide
 SWsoft, Inc. Plesk 7.6 For Windows E-mail User Guide (Revision 1.0) (c) 1999-2006 ISBN: N/A SWsoft, Inc. 13755 Sunrise Valley Drive Suite 325 Herndon VA 20171 USA Phone: +1 (703) 815 5670 Fax: +1 (703)
SWsoft, Inc. Plesk 7.6 For Windows E-mail User Guide (Revision 1.0) (c) 1999-2006 ISBN: N/A SWsoft, Inc. 13755 Sunrise Valley Drive Suite 325 Herndon VA 20171 USA Phone: +1 (703) 815 5670 Fax: +1 (703)
How to make the Emails you Send from Outlook 2010 appear to Originate from different Email Addresses
 How to make the Emails you Send from Outlook 2010 appear to Originate from different Email Addresses If you only use a single email address to send out all your business and personal emails then you're
How to make the Emails you Send from Outlook 2010 appear to Originate from different Email Addresses If you only use a single email address to send out all your business and personal emails then you're
Mail Server Administration
 Clemson University CPSC 424: Systems Administration and Security Section 001 Mail Server Administration Authors: Joshua Groppe William Collins Instructor: James M.Martin, Ph.D April 25, 2014 1 Introduction
Clemson University CPSC 424: Systems Administration and Security Section 001 Mail Server Administration Authors: Joshua Groppe William Collins Instructor: James M.Martin, Ph.D April 25, 2014 1 Introduction
How to configure your email client
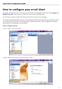 How to configure your email client This guide will teach you how to set up your email client. In this guide we will cover both Outlook and Windows Live mail, which are two of the major email clients used
How to configure your email client This guide will teach you how to set up your email client. In this guide we will cover both Outlook and Windows Live mail, which are two of the major email clients used
Using WinGate 6 Email. Concepts, Features, and Configurations.
 WinGate Feature Guide Using WinGate 6 Email Concepts, Features, and Configurations. Neil Gooden Qbik New Zealand Limited Rev 1.0 December 2004 2 Introduction...3 Basic Email Concepts... 3 Differences in
WinGate Feature Guide Using WinGate 6 Email Concepts, Features, and Configurations. Neil Gooden Qbik New Zealand Limited Rev 1.0 December 2004 2 Introduction...3 Basic Email Concepts... 3 Differences in
Djigzo email encryption. Djigzo white paper
 Djigzo email encryption Djigzo white paper Copyright 2009-2011, djigzo.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in transit or
Djigzo email encryption Djigzo white paper Copyright 2009-2011, djigzo.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in transit or
Instructions Microsoft Outlook Express Page 1
 Instructions Microsoft Outlook Express Page 1 Instructions Microsoft Outlook Express This manual is written for users who already have an e-mail account configured in Outlook Express and will therefore
Instructions Microsoft Outlook Express Page 1 Instructions Microsoft Outlook Express This manual is written for users who already have an e-mail account configured in Outlook Express and will therefore
Spam, Spam and More Spam. Spammers: Cost to send
 Spam, Spam and More Spam cs5480/cs6480 Matthew J. Probst *with some slides/graphics adapted from J.F Kurose and K.W. Ross Spammers: Cost to send Assuming a $10/mo dialup account: 13.4 million messages
Spam, Spam and More Spam cs5480/cs6480 Matthew J. Probst *with some slides/graphics adapted from J.F Kurose and K.W. Ross Spammers: Cost to send Assuming a $10/mo dialup account: 13.4 million messages
Parallels Plesk Control Panel
 Parallels Plesk Control Panel Copyright Notice ISBN: N/A Parallels 660 SW 39 th Street Suite 205 Renton, Washington 98057 USA Phone: +1 (425) 282 6400 Fax: +1 (425) 282 6444 Copyright 1999-2008, Parallels,
Parallels Plesk Control Panel Copyright Notice ISBN: N/A Parallels 660 SW 39 th Street Suite 205 Renton, Washington 98057 USA Phone: +1 (425) 282 6400 Fax: +1 (425) 282 6444 Copyright 1999-2008, Parallels,
If your response to any of the questions above was Yes, then SmarterMail Enterprise Edition may be right for you.
 Professional Edition vs. Enterprise Edition SmarterMail Professional Edition has all of the features required to host a fully-functional mail server. SmarterMail Enterprise Edition offers additional features,
Professional Edition vs. Enterprise Edition SmarterMail Professional Edition has all of the features required to host a fully-functional mail server. SmarterMail Enterprise Edition offers additional features,
Math SMTP Server Configuration
 Math SMTP Server Configuration Šarūnas Burdulis Version 1, August 3, 2005 Contents 1 Requirements for SMTP Service at Math 1 2 Exim 4 1 3 Spam Filtering 2 4 Virus Detection 3 5 Authentication and TLS 4
Math SMTP Server Configuration Šarūnas Burdulis Version 1, August 3, 2005 Contents 1 Requirements for SMTP Service at Math 1 2 Exim 4 1 3 Spam Filtering 2 4 Virus Detection 3 5 Authentication and TLS 4
Cryoserver Archive Lotus Notes Configuration
 Lotus Notes Configuration Version 1.0 December 2007 Forensic & Compliance Systems Ltd +44 (0)800 280 0525 [email protected] www.cryoserver.com Contents INTRODUCTION... 3 SMTP ROUTING TO CRYOSERVER...
Lotus Notes Configuration Version 1.0 December 2007 Forensic & Compliance Systems Ltd +44 (0)800 280 0525 [email protected] www.cryoserver.com Contents INTRODUCTION... 3 SMTP ROUTING TO CRYOSERVER...
Email. Daniel Zappala. CS 460 Computer Networking Brigham Young University
 Email Daniel Zappala CS 460 Computer Networking Brigham Young University How Email Works 3/25 Major Components user agents POP, IMAP, or HTTP to exchange mail mail transfer agents (MTAs) mailbox to hold
Email Daniel Zappala CS 460 Computer Networking Brigham Young University How Email Works 3/25 Major Components user agents POP, IMAP, or HTTP to exchange mail mail transfer agents (MTAs) mailbox to hold
Installing GFI MailEssentials
 Installing GFI MailEssentials Introduction to installing GFI MailEssentials This chapter explains the procedure on how to install and configure GFI MailEssentials. GFI MailEssentials can be installed in
Installing GFI MailEssentials Introduction to installing GFI MailEssentials This chapter explains the procedure on how to install and configure GFI MailEssentials. GFI MailEssentials can be installed in
Release Notes. for Kerio Connect 8.0.0
 Release Notes for Kerio Connect 8.0.0 Date: December 4, 2012 2012 Kerio Technologies. All rights reserved. 1 Important changes in this version New Kerio Connect client The Kerio Connect webmail interface
Release Notes for Kerio Connect 8.0.0 Date: December 4, 2012 2012 Kerio Technologies. All rights reserved. 1 Important changes in this version New Kerio Connect client The Kerio Connect webmail interface
Unifying Information Security. Implementing TLS on the CLEARSWIFT SECURE Email Gateway
 Unifying Information Security Implementing TLS on the CLEARSWIFT SECURE Email Gateway Contents 1 Introduction... 3 2 Understanding TLS... 4 3 Clearswift s Application of TLS... 5 3.1 Opportunistic TLS...
Unifying Information Security Implementing TLS on the CLEARSWIFT SECURE Email Gateway Contents 1 Introduction... 3 2 Understanding TLS... 4 3 Clearswift s Application of TLS... 5 3.1 Opportunistic TLS...
CSE/ISE 311: Systems Administra5on Email Administra5on
 Email Administra5on Don Porter Theme Email systems started with a pre5y simple design Everyone trusted each other, it was nice Then spam came along Lots of complexity and distrust to try to reduce spam
Email Administra5on Don Porter Theme Email systems started with a pre5y simple design Everyone trusted each other, it was nice Then spam came along Lots of complexity and distrust to try to reduce spam
Reliable & Secure Email. Professional, Dependable, Complete Easy to Learn, Use and Grow
 Reliable & Secure Email Professional, Dependable, Complete Easy to Learn, Use and Grow About this Presentation Summarizes primary purposes of email, plus the needs of email providers and users. Introduces
Reliable & Secure Email Professional, Dependable, Complete Easy to Learn, Use and Grow About this Presentation Summarizes primary purposes of email, plus the needs of email providers and users. Introduces
DJIGZO EMAIL ENCRYPTION. Djigzo white paper
 DJIGZO EMAIL ENCRYPTION Djigzo white paper Copyright 2009-2011, djigzo.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in transit or
DJIGZO EMAIL ENCRYPTION Djigzo white paper Copyright 2009-2011, djigzo.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in transit or
Parallels Plesk Panel
 Parallels Plesk Panel Copyright Notice ISBN: N/A Parallels 660 SW 39th Street Suite 205 Renton, Washington 98057 USA Phone: +1 (425) 282 6400 Fax: +1 (425) 282 6444 Copyright 1999-2010, Parallels, Inc.
Parallels Plesk Panel Copyright Notice ISBN: N/A Parallels 660 SW 39th Street Suite 205 Renton, Washington 98057 USA Phone: +1 (425) 282 6400 Fax: +1 (425) 282 6444 Copyright 1999-2010, Parallels, Inc.
Plesk for Windows Copyright Notice
 2 Plesk for Windows Copyright Notice ISBN: N/A SWsoft. 13755 Sunrise Valley Drive Suite 325 Herndon VA 20171 USA Phone: +1 (703) 815 5670 Fax: +1 (703) 815 5675 Copyright 1999-2007, SWsoft Holdings, Ltd.
2 Plesk for Windows Copyright Notice ISBN: N/A SWsoft. 13755 Sunrise Valley Drive Suite 325 Herndon VA 20171 USA Phone: +1 (703) 815 5670 Fax: +1 (703) 815 5675 Copyright 1999-2007, SWsoft Holdings, Ltd.
NeoMail Guide. Neotel (Pty) Ltd
 NeoMail Guide Neotel (Pty) Ltd NeoMail Connect Guide... 1 1. POP and IMAP Client access... 3 2. Outlook Web Access... 4 3. Outlook (IMAP and POP)... 6 4. Outlook 2007... 16 5. Outlook Express... 24 1.
NeoMail Guide Neotel (Pty) Ltd NeoMail Connect Guide... 1 1. POP and IMAP Client access... 3 2. Outlook Web Access... 4 3. Outlook (IMAP and POP)... 6 4. Outlook 2007... 16 5. Outlook Express... 24 1.
SME- Mail to SMS & MMS Gateway with NowSMS Quick Start Guide
 SME- Mail to SMS & MMS Gateway with NowSMS Quick Start Guide One of the typical usage cases for NowSMS is as an E-Mail to SMS & MMS Gateway. E-Mail users can send an SMS or MMS message by sending an e-mail
SME- Mail to SMS & MMS Gateway with NowSMS Quick Start Guide One of the typical usage cases for NowSMS is as an E-Mail to SMS & MMS Gateway. E-Mail users can send an SMS or MMS message by sending an e-mail
Avira Managed Email Security (AMES) User Guide
 Avira Managed Email Security (AMES) User Guide Table of Contents Table of Contents 1. Product information... 4 1.1 Functionality................................................................4 1.2 Licensing
Avira Managed Email Security (AMES) User Guide Table of Contents Table of Contents 1. Product information... 4 1.1 Functionality................................................................4 1.2 Licensing
Written by: Johan Strand, Reviewed by: Chafic Nassif, Date: 2006-04-26. Getting an ipath server running on Linux
 Getting an ipath server running on Linux Table of Contents Table of Contents... 2 1.0. Introduction... 3 2.0. Overview... 3 3.0. Installing Linux... 3 4.0. Installing software that ipath requires... 3
Getting an ipath server running on Linux Table of Contents Table of Contents... 2 1.0. Introduction... 3 2.0. Overview... 3 3.0. Installing Linux... 3 4.0. Installing software that ipath requires... 3
Advanced Settings. Help Documentation
 Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc. Advanced Settings Abuse Detection SmarterMail has several methods
Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc. Advanced Settings Abuse Detection SmarterMail has several methods
Talk Internet User Guides Controlgate Administrative User Guide
 Talk Internet User Guides Controlgate Administrative User Guide Contents Contents (This Page) 2 Accessing the Controlgate Interface 3 Adding a new domain 4 Setup Website Hosting 5 Setup FTP Users 6 Setup
Talk Internet User Guides Controlgate Administrative User Guide Contents Contents (This Page) 2 Accessing the Controlgate Interface 3 Adding a new domain 4 Setup Website Hosting 5 Setup FTP Users 6 Setup
Setting Up Sharp MX-Color Imagers To Scan To Email
 Setting Up Sharp MX-Color Imagers To Scan To Email MX-2300, MX-2600, MX-2700, MX-3100, MX-3501, MX-4501, MX-5500, MX-6200, MX-6201, MX-7000, MX-7001, MX-M850, MX-M950, MX-M1100 Step 1. Click Start > Run
Setting Up Sharp MX-Color Imagers To Scan To Email MX-2300, MX-2600, MX-2700, MX-3100, MX-3501, MX-4501, MX-5500, MX-6200, MX-6201, MX-7000, MX-7001, MX-M850, MX-M950, MX-M1100 Step 1. Click Start > Run
Do you need to... Do you need to...
 TM Guards your Email. Kills Spam and Viruses. Do you need to... Do you need to... Scan your e-mail traffic for Viruses? Scan your e-mail traffic for Viruses? Reduce time wasted dealing with Spam? Reduce
TM Guards your Email. Kills Spam and Viruses. Do you need to... Do you need to... Scan your e-mail traffic for Viruses? Scan your e-mail traffic for Viruses? Reduce time wasted dealing with Spam? Reduce
Parallels Plesk Automation
 Parallels Plesk Automation Copyright Notice Parallels IP Holdings GmbH Vordergasse 59 CH-Schaffhausen Switzerland Phone: +41 526320 411 Fax: +41 52672 2010 Global Headquarters 500 SW 39 th Street, Suite
Parallels Plesk Automation Copyright Notice Parallels IP Holdings GmbH Vordergasse 59 CH-Schaffhausen Switzerland Phone: +41 526320 411 Fax: +41 52672 2010 Global Headquarters 500 SW 39 th Street, Suite
How To Create A Mailbox In Windows Mail On A Pc Or Mac Or Ipad (For A Mac)
 Advanced Mailbox Email Software Setup Guide Advanced Mailbox Setup Guide Setting up an Advanced mailbox only takes a few minutes. You can set up any email software to send and receive email from your mailbox.
Advanced Mailbox Email Software Setup Guide Advanced Mailbox Setup Guide Setting up an Advanced mailbox only takes a few minutes. You can set up any email software to send and receive email from your mailbox.
Emailing from The E2 Shop System EMail address Server Name Server Port, Encryption Protocol, Encryption Type, SMTP User ID SMTP Password
 Emailing from The E2 Shop System With recent releases of E2SS (at least 7.2.7.23), we will be allowing two protocols for EMail delivery. A new protocol for EMail delivery Simple Mail Transfer Protocol
Emailing from The E2 Shop System With recent releases of E2SS (at least 7.2.7.23), we will be allowing two protocols for EMail delivery. A new protocol for EMail delivery Simple Mail Transfer Protocol
Intercept Anti-Spam Quick Start Guide
 Intercept Anti-Spam Quick Start Guide Software Version: 6.5.2 Date: 5/24/07 PREFACE...3 PRODUCT DOCUMENTATION...3 CONVENTIONS...3 CONTACTING TECHNICAL SUPPORT...4 COPYRIGHT INFORMATION...4 OVERVIEW...5
Intercept Anti-Spam Quick Start Guide Software Version: 6.5.2 Date: 5/24/07 PREFACE...3 PRODUCT DOCUMENTATION...3 CONVENTIONS...3 CONTACTING TECHNICAL SUPPORT...4 COPYRIGHT INFORMATION...4 OVERVIEW...5
Spam Testing Methodology Opus One, Inc. March, 2007
 Spam Testing Methodology Opus One, Inc. March, 2007 This document describes Opus One s testing methodology for anti-spam products. This methodology has been used, largely unchanged, for four tests published
Spam Testing Methodology Opus One, Inc. March, 2007 This document describes Opus One s testing methodology for anti-spam products. This methodology has been used, largely unchanged, for four tests published
VPOP3 Your email post office Getting Started Guide
 VPOP3 Your email post office Getting Started Guide VPOP3 Getting Started Guide, version 2.1 1 Copyright Statement This manual is proprietary information of Paul Smith Computer Services and is not to be
VPOP3 Your email post office Getting Started Guide VPOP3 Getting Started Guide, version 2.1 1 Copyright Statement This manual is proprietary information of Paul Smith Computer Services and is not to be
