What s Your HTTPS Grade? A Case Study of HTTPS/SSL at Mid Michigan Community College. Brandon [email protected]
|
|
|
- Edgar Harvey
- 10 years ago
- Views:
Transcription
1 What s Your HTTPS Grade? A Case Study of HTTPS/SSL at Mid Michigan Community College Brandon [email protected]
2 About Me Director of Programming Mid Michigan Community College ~4,500 students Former Blackboard Administrator Central Michigan University ~27,000 students Former Moodle Administrator at MMCC I love web [email protected]
3 Why HTTPS? When do you look for the lock?
4 Do you want your sensitive data traveling through a series of tubes in plain sight?
5 Man-In-The-Middle Source:
6 Man-In-The-Middle ISPs (injecting ads, tracking cookies/scripts) Verizon/AT&T Gogo Even certain employers & organizations might do this! (Content filters)
7 Usernames and Passwords 1. People re-use passwords 2. Institutions with LDAP likely have multiple systems prompt for passwords
8 What does this have to do with Moodle? Don t let Moodle be your weak link! Enable HTTPS on your login screen Enable HTTPS everywhere*
9 HTTPS But wait! There s more!
10 NOT ALL HTTPS IS EQUAL!
11 NOT ALL HTTPS IS EQUAL! 1. Deprecated Protocols 2. Weak Ciphers 3. Weak Certificates 4. Bugs in Encryption Libraries
12 1. Protocol: SSL vs. TLS SSL 2.0 SSL 3.0 TLS 1.0 TLS 1.1 TLS 1.2 A cryptographic protocol by any other name would be as secure? Infosec Shakespeare SSL is dead. Long live SSL*! (Transport Layer Security)
13 Cryptography 101 (A)lice is trying to tell (B)ob a secret, but (E)ve is listening in. A communicating with B with E trying to eavesdrop Alice can use the advertised key from Bob to generate gibberish, and only the private key Bob used to generate the public/advertised certificate can unlock/translate the gibberish.
14 2. Weak Ciphers Cipher = algorithm for producing (and understanding) gibberish ay2varjsfumumtvzeh9755gvyckwhg0 Browser and web server have to use the same cipher If a server accepts weak ciphers, attackers will use those to get in
15 Weak Ciphers (continued) Browser ECDHE-ECDSA-AES128-GCM-SHA256 ECDHE-RSA-AES128-GCM-SHA256 DHE-RSA-AES128-GCM-SHA256 ECDHE-ECDSA-CHACHA20-POLY1305-SHA256 ECDHE-RSA-CHACHA20-POLY1305- SHA DHE-RSA-CHACHA20-POLY1305-SHA ECDHE-ECDSA-AES256-SHA256 ECDHE-RSA-AES256-SHA DHE-RSA-AES256-SHA256 ECDHE-ECDSA-AES128-SHA128 ECDHE-RSA-AES128-SHA128 DHE-RSA-AES128-SHA128 RSA-AES128-GCM-SHA RSA-AES256-SHA256 RSA-AES128-SHA RSA-3DES-EDE-SHA168 Server ECDHE-RSA-AES128-GCM-SHA256 ECDHE-RSA-AES128-SHA256 ECDHE-RSA-AES128-SHA AES128-GCM-SHA256 AES128-SHA256 AES128-SHA ECDHE-RSA-AES256-GCM-SHA384 ECDHE-RSA-AES256-SHA384 ECDHE-RSA-AES256-SHA AES256-GCM-SHA384 AES256-SHA256 AES256-SHA ECDHE-RSA-DES-CBC3-SHA DES-CBC3-SHA d=moodle.midmich.edu
16 1+2 = Downgrade attacks Forcing communication with a weak cipher Forcing communication over an older protocol POODLE (October 2014 variant) affected SSL 3 Every vulnerability gets a fun name!
17 3. Weak Certificates The public key, certificate, and private keys we ve talked about are generated with a particular algorithm Google Online Security Blog: The SHA-1 cryptographic hash algorithm has been known to be considerably weaker than it was designed to be since at least years ago. Collision attacks against SHA-1 are too affordable for us to consider it safe for the public web PKI. We can only expect that attacks will get cheaper. Officially deprecated in 2011, but many certificate providers continued to issue certificates with this algorithm. SHA-2/SHA-256 is now preferred. Chrome is especially good about warning users about this now
18 4. Bugs in Encryption Libraries The previous problems were all about the design of the security we use Implementations of SSL/TLS are a whole source of vulnerabilities in their own right! OpenSSL is used in everything from Apache to card entry doors :) Heartbleed OpenSSL vulnerability in April 2014
19 NOT ALL HTTPS IS EQUAL! 1. Deprecated Protocols 2. Weak Ciphers 3. Weak Certificates 4. Bugs in Encryption Libraries
20 What does this mean for my institution? Case Study: Mid Michigan Community College November 2014 March 2015
21 Our Web Sites midmich.edu www. midmich.edu Expires 12/2015 $ Wildcard certificate for lower cost than many separate certificates moodle. midmich.edu Expires 12/2016 $ midweb. midmich.edu Expires 8/2015 $ One expiration date for this one wildcard certificate print. midmich.edu *. midmich.edu Expires 12/2015 $$$
22 Our Web Servers midmich.edu www. midmich.edu Apache moodle. midmich.edu nginx midweb. midmich.edu Tomcat print. midmich.edu IIS
23 Wildcard Cert Realities Different servers expect different formats for certificate and/or private key p12, pfx, p7b, pem, der, oh my! Missing certain chained certificates (I m looking at you Tomcat) causes mobile browsers to fail to connect
24 TL;DR #1 Wikipedia: Too long; didn t read Managing our certificates was a nightmare we tried to limit to once every four years.
25 Qualsys SSL Labs
26
27
28
29 Our Grades midmich.edu www. midmich.edu C/F POODLE, DH, FREAK moodle. midmich.edu B SSL 3 midweb. midmich.edu F POODLE, Bad chain print. midmich.edu No SSL! No SSL!
30 TL;DR #2 Our web servers had inconsistent and insecure configurations. (And we re only as strong as weakest link.)
31 Option 1 Update each web server individually Tomcat: Edit server.xml sslprotocol="tls" sslenabledprotocols= TLSv1.2,TLSv1.1,TLSv1" ciphers="tls_ecdhe_rsa_with_aes_128_cbc_sha256,tl S_ECDHE_RSA_WITH_AES_128_CBC_SHA,TLS_ECDHE_RSA_WI TH_AES_256_CBC_SHA384,TLS_ECDHE_RSA_WITH_AES_256_ CBC_SHA,TLS_ECDHE_RSA_WITH_RC4_128_SHA,TLS_RSA_WI TH_AES_128_CBC_SHA256,TLS_RSA_WITH_AES_128_CBC_SH A,TLS_RSA_WITH_AES_256_CBC_SHA256,TLS_RSA_WITH_AE S_256_CBC_SHA,SSL_RSA_WITH_RC4_128_SHA"
32 Option 1 Update each web server individually Apache: Edit ssl mod s ssl.conf file SSLProtocol all -SSLv2 -SSLv3 SSLHonorCipherOrder on SSLCipherSuite "EECDH+ECDSA+AESGCM \ EECDH+aRSA+AESGCM EECDH+ECDSA+SHA384 \ EECDH+ECDSA+SHA256 EECDH+aRSA+SHA384 \ EECDH+aRSA+SHA256 EECDH+aRSA+RC4 \ EECDH EDH+aRSA RC4!aNULL!eNULL!LOW \!3DES!MD5!EXP!PSK!SRP!DSS"
33 Option 1 Update each web server individually IIS: Powershell?
34 Option 2 Load balancer(s) in front of all our web systems nginx was already doing this for our Moodle app servers: See Matt Rice s A Balanced Approach: How to Direct Your Moodle Traffic I had used F5 appliances at another institution HAProxy has had great SSL support in recent years
35 Option 2, Visualized
36 global log /dev/log local0 log /dev/log local1 notice chroot /var/lib/haproxy user haproxy group haproxy daemon # Default SSL material locations ca-base /etc/ssl/certs crt-base /etc/ssl/private # Default ciphers to use on SSL-enabled listening sockets. # For more information, see ciphers(1ssl). ssl-default-bind-ciphers keecdh+arsa+aes:krsa+aes:+aes256:arsa+3des:!rc4-sha:!kedh:!low:!exp:!md5:!anull:!enull ssl-default-bind-options no-sslv3 defaults log global mode http option httplog option log-separate-errors balance roundrobin option dontlognull timeout connect 5000 timeout client timeout server # Separate error logs from access logs errorfile 400 /etc/haproxy/errors/400.http errorfile 403 /etc/haproxy/errors/403.http errorfile 408 /etc/haproxy/errors/408.http errorfile 500 /etc/haproxy/errors/500.http errorfile 502 /etc/haproxy/errors/502.http errorfile 503 /etc/haproxy/errors/503.http errorfile 504 /etc/haproxy/errors/504.http frontend load_balancers ## Binding to both test (192.) and production (67.) IP addresses #HTTP bind :80 bind :80 #HTTPS bind :443 ssl crt /etc/ssl/private/wildcard.midmich.edu.pem bind :443 ssl crt /etc/ssl/private/wildcard.midmich.edu.pem ######################## Sample HAProxy configuration for MMCC ## Moodle ############# acl dest_moodle_prod hdr(host) -i moodle.midmich.edu use_backend moodle_prod_nodes ######################## if dest_moodle_prod backend moodle_prod_nodes option forwardfor option http-server-close http-request set-header X-Forwarded-Port %[dst_port] http-request set-header X-Forwarded-Proto https if { ssl_fc } option httpchk HEAD /admin/tool/heartbeat/index.php HTTP/1.1\r\nUser-Agent:\ HAProxy\r\nHost:\ # Redirect all traffic to HTTPS redirect scheme https if!{ ssl_fc } # Do NOT inject this cookie; however, if it exists, send the user to the appropriate server cookie MAPPSERVER indirect nocache preserve server mapp1 server mapp2 server mapp :80 check inter 2000 cookie mapp :80 check inter 2000 cookie mapp :80 check inter 2000 cookie mapp3 backup
37 global log /dev/log local0 log /dev/log local1 notice chroot /var/lib/haproxy user haproxy group haproxy daemon # Default SSL material locations ca-base /etc/ssl/certs crt-base /etc/ssl/private # Default ciphers to use on SSL-enabled listening sockets. # For more information, see ciphers(1ssl). ssl-default-bind-ciphers keecdh+arsa+aes:krsa+aes:+aes256:arsa+3des:!rc4-sha:!kedh:!low:!exp:!md5:!anull:!enull ssl-default-bind-options no-sslv3 defaults log global mode http option httplog option log-separate-errors balance roundrobin option dontlognull timeout connect 5000 timeout client timeout server # Separate error logs from access logs Configure allowed ciphers and bind ports to certificate errorfile 400 /etc/haproxy/errors/400.http errorfile 403 /etc/haproxy/errors/403.http errorfile 408 /etc/haproxy/errors/408.http errorfile 500 /etc/haproxy/errors/500.http errorfile 502 /etc/haproxy/errors/502.http errorfile 503 /etc/haproxy/errors/503.http errorfile 504 /etc/haproxy/errors/504.http frontend load_balancers ## Binding to both test (192.) and production (67.) IP addresses #HTTP bind :80 bind :80 #HTTPS bind :443 ssl crt /etc/ssl/private/wildcard.midmich.edu.pem bind :443 ssl crt /etc/ssl/private/wildcard.midmich.edu.pem ######################## ## Moodle ############# acl dest_moodle_prod hdr(host) -i moodle.midmich.edu use_backend moodle_prod_nodes ######################## if dest_moodle_prod backend moodle_prod_nodes option forwardfor option http-server-close http-request set-header X-Forwarded-Port %[dst_port] http-request set-header X-Forwarded-Proto https if { ssl_fc } option httpchk HEAD /admin/tool/heartbeat/index.php HTTP/1.1\r\nUser-Agent:\ HAProxy\r\nHost:\ # Redirect all traffic to HTTPS redirect scheme https if!{ ssl_fc } # Do NOT inject this cookie; however, if it exists, send the user to the appropriate server cookie MAPPSERVER indirect nocache preserve server mapp1 server mapp2 server mapp :80 check inter 2000 cookie mapp :80 check inter 2000 cookie mapp :80 check inter 2000 cookie mapp3 backup
38 global log /dev/log local0 log /dev/log local1 notice chroot /var/lib/haproxy user haproxy group haproxy daemon # Default SSL material locations ca-base /etc/ssl/certs crt-base /etc/ssl/private # Default ciphers to use on SSL-enabled listening sockets. # For more information, see ciphers(1ssl). ssl-default-bind-ciphers keecdh+arsa+aes:krsa+aes:+aes256:arsa+3des:!rc4-sha:!kedh:!low:!exp:!md5:!anull:!enull ssl-default-bind-options no-sslv3 defaults log global mode http option httplog option log-separate-errors balance roundrobin option dontlognull timeout connect 5000 timeout client timeout server # Separate error logs from access logs errorfile 400 /etc/haproxy/errors/400.http errorfile 403 /etc/haproxy/errors/403.http errorfile 408 /etc/haproxy/errors/408.http errorfile 500 /etc/haproxy/errors/500.http errorfile 502 /etc/haproxy/errors/502.http errorfile 503 /etc/haproxy/errors/503.http errorfile 504 /etc/haproxy/errors/504.http frontend load_balancers ## Binding to both test (192.) and production (67.) IP addresses #HTTP bind :80 bind :80 #HTTPS bind :443 ssl crt /etc/ssl/private/wildcard.midmich.edu.pem bind :443 ssl crt /etc/ssl/private/wildcard.midmich.edu.pem ######################## ## Moodle ############# acl dest_moodle_prod hdr(host) -i moodle.midmich.edu Connect traffic received on the front end to various backends via ACLs use_backend moodle_prod_nodes ######################## if dest_moodle_prod backend moodle_prod_nodes option forwardfor option http-server-close http-request set-header X-Forwarded-Port %[dst_port] http-request set-header X-Forwarded-Proto https if { ssl_fc } option httpchk HEAD /admin/tool/heartbeat/index.php HTTP/1.1\r\nUser-Agent:\ HAProxy\r\nHost:\ # Redirect all traffic to HTTPS redirect scheme https if!{ ssl_fc } # Do NOT inject this cookie; however, if it exists, send the user to the appropriate server cookie MAPPSERVER indirect nocache preserve server mapp1 server mapp2 server mapp :80 check inter 2000 cookie mapp :80 check inter 2000 cookie mapp :80 check inter 2000 cookie mapp3 backup
39 global log /dev/log local0 log /dev/log local1 notice chroot /var/lib/haproxy user haproxy group haproxy daemon # Default SSL material locations ca-base /etc/ssl/certs crt-base /etc/ssl/private # Default ciphers to use on SSL-enabled listening sockets. # For more information, see ciphers(1ssl). ssl-default-bind-ciphers keecdh+arsa+aes:krsa+aes:+aes256:arsa+3des:!rc4-sha:!kedh:!low:!exp:!md5:!anull:!enull ssl-default-bind-options no-sslv3 defaults log global mode http option httplog option log-separate-errors balance roundrobin option dontlognull timeout connect 5000 timeout client timeout server # Separate error logs from access logs errorfile 400 /etc/haproxy/errors/400.http errorfile 403 /etc/haproxy/errors/403.http errorfile 408 /etc/haproxy/errors/408.http errorfile 500 /etc/haproxy/errors/500.http errorfile 502 /etc/haproxy/errors/502.http errorfile 503 /etc/haproxy/errors/503.http errorfile 504 /etc/haproxy/errors/504.http frontend load_balancers ## Binding to both test (192.) and production (67.) IP addresses #HTTP bind :80 bind :80 #HTTPS bind :443 ssl crt /etc/ssl/private/wildcard.midmich.edu.pem bind :443 ssl crt /etc/ssl/private/wildcard.midmich.edu.pem ######################## ## Moodle ############# acl dest_moodle_prod use_backend moodle_prod_nodes ######################## hdr(host) -i moodle.midmich.edu if dest_moodle_prod backend moodle_prod_nodes option forwardfor option http-server-close http-request set-header X-Forwarded-Port %[dst_port] http-request set-header X-Forwarded-Proto https if { ssl_fc } option httpchk HEAD /admin/tool/heartbeat/index.php HTTP/1.1\r\nUser-Agent:\ HAProxy\r\nHost:\ Inject headers so Moodle servers will know traffic was forwarded # Redirect all traffic to HTTPS redirect scheme https if!{ ssl_fc } # Do NOT inject this cookie; however, if it exists, send the user to the appropriate server cookie MAPPSERVER indirect nocache preserve server mapp1 server mapp2 server mapp :80 check inter 2000 cookie mapp :80 check inter 2000 cookie mapp :80 check inter 2000 cookie mapp3 backup
40 global log /dev/log local0 log /dev/log local1 notice chroot /var/lib/haproxy user haproxy group haproxy daemon # Default SSL material locations ca-base /etc/ssl/certs crt-base /etc/ssl/private # Default ciphers to use on SSL-enabled listening sockets. # For more information, see ciphers(1ssl). ssl-default-bind-ciphers keecdh+arsa+aes:krsa+aes:+aes256:arsa+3des:!rc4-sha:!kedh:!low:!exp:!md5:!anull:!enull ssl-default-bind-options no-sslv3 defaults log global mode http option httplog option log-separate-errors balance roundrobin option dontlognull timeout connect 5000 timeout client timeout server # Separate error logs from access logs errorfile 400 /etc/haproxy/errors/400.http errorfile 403 /etc/haproxy/errors/403.http errorfile 408 /etc/haproxy/errors/408.http errorfile 500 /etc/haproxy/errors/500.http errorfile 502 /etc/haproxy/errors/502.http errorfile 503 /etc/haproxy/errors/503.http errorfile 504 /etc/haproxy/errors/504.http frontend load_balancers ## Binding to both test (192.) and production (67.) IP addresses #HTTP bind :80 bind :80 #HTTPS bind :443 ssl crt /etc/ssl/private/wildcard.midmich.edu.pem bind :443 ssl crt /etc/ssl/private/wildcard.midmich.edu.pem ######################## ## Moodle ############# acl dest_moodle_prod use_backend moodle_prod_nodes ######################## hdr(host) -i moodle.midmich.edu if dest_moodle_prod backend moodle_prod_nodes option forwardfor option http-server-close http-request set-header X-Forwarded-Port %[dst_port] http-request set-header X-Forwarded-Proto https if { ssl_fc } option httpchk HEAD /admin/tool/heartbeat/index.php HTTP/1.1\r\nUser-Agent:\ HAProxy\r\nHost:\ # Redirect all traffic to HTTPS redirect scheme https if!{ ssl_fc } # Do NOT inject this cookie; however, if it exists, send the user to the appropriate server cookie MAPPSERVER indirect nocache preserve server mapp1 server mapp2 server mapp :80 check inter 2000 cookie mapp :80 check inter 2000 cookie mapp :80 check inter 2000 cookie mapp3 backup Define a health check to determine whether servers in the pool are online!
41 global log /dev/log local0 log /dev/log local1 notice chroot /var/lib/haproxy user haproxy group haproxy daemon # Default SSL material locations ca-base /etc/ssl/certs crt-base /etc/ssl/private # Default ciphers to use on SSL-enabled listening sockets. # For more information, see ciphers(1ssl). ssl-default-bind-ciphers keecdh+arsa+aes:krsa+aes:+aes256:arsa+3des:!rc4-sha:!kedh:!low:!exp:!md5:!anull:!enull ssl-default-bind-options no-sslv3 defaults log global mode http option httplog option log-separate-errors balance roundrobin option dontlognull timeout connect 5000 timeout client timeout server # Separate error logs from access logs errorfile 400 /etc/haproxy/errors/400.http errorfile 403 /etc/haproxy/errors/403.http errorfile 408 /etc/haproxy/errors/408.http errorfile 500 /etc/haproxy/errors/500.http errorfile 502 /etc/haproxy/errors/502.http errorfile 503 /etc/haproxy/errors/503.http errorfile 504 /etc/haproxy/errors/504.http frontend load_balancers ## Binding to both test (192.) and production (67.) IP addresses #HTTP bind :80 bind :80 #HTTPS bind :443 ssl crt /etc/ssl/private/wildcard.midmich.edu.pem bind :443 ssl crt /etc/ssl/private/wildcard.midmich.edu.pem ######################## ## Moodle ############# acl dest_moodle_prod use_backend moodle_prod_nodes ######################## hdr(host) -i moodle.midmich.edu if dest_moodle_prod backend moodle_prod_nodes option forwardfor option http-server-close http-request set-header X-Forwarded-Port %[dst_port] http-request set-header X-Forwarded-Proto https if { ssl_fc } option httpchk HEAD /admin/tool/heartbeat/index.php HTTP/1.1\r\nUser-Agent:\ HAProxy\r\nHost:\ # Redirect all traffic to HTTPS redirect scheme https if!{ ssl_fc } We forward all traffic to https at the load balancer level! # Do NOT inject this cookie; however, if it exists, send the user to the appropriate server cookie MAPPSERVER indirect nocache preserve server mapp1 server mapp2 server mapp :80 check inter 2000 cookie mapp :80 check inter 2000 cookie mapp :80 check inter 2000 cookie mapp3 backup
42 global log /dev/log local0 log /dev/log local1 notice chroot /var/lib/haproxy user haproxy group haproxy daemon # Default SSL material locations ca-base /etc/ssl/certs crt-base /etc/ssl/private # Default ciphers to use on SSL-enabled listening sockets. # For more information, see ciphers(1ssl). ssl-default-bind-ciphers keecdh+arsa+aes:krsa+aes:+aes256:arsa+3des:!rc4-sha:!kedh:!low:!exp:!md5:!anull:!enull ssl-default-bind-options no-sslv3 defaults log global mode http option httplog option log-separate-errors balance roundrobin option dontlognull timeout connect 5000 timeout client timeout server # Separate error logs from access logs errorfile 400 /etc/haproxy/errors/400.http errorfile 403 /etc/haproxy/errors/403.http errorfile 408 /etc/haproxy/errors/408.http errorfile 500 /etc/haproxy/errors/500.http errorfile 502 /etc/haproxy/errors/502.http errorfile 503 /etc/haproxy/errors/503.http errorfile 504 /etc/haproxy/errors/504.http frontend load_balancers ## Binding to both test (192.) and production (67.) IP addresses #HTTP bind :80 bind :80 #HTTPS bind :443 ssl crt /etc/ssl/private/wildcard.midmich.edu.pem bind :443 ssl crt /etc/ssl/private/wildcard.midmich.edu.pem ######################## ## Moodle ############# acl dest_moodle_prod use_backend moodle_prod_nodes ######################## hdr(host) -i moodle.midmich.edu if dest_moodle_prod backend moodle_prod_nodes option forwardfor option http-server-close http-request set-header X-Forwarded-Port %[dst_port] http-request set-header X-Forwarded-Proto https if { ssl_fc } option httpchk HEAD /admin/tool/heartbeat/index.php HTTP/1.1\r\nUser-Agent:\ HAProxy\r\nHost:\ # Redirect all traffic to HTTPS redirect scheme https if!{ ssl_fc } List the servers in the pool we keep our worker server as a backup # Do NOT inject this cookie; however, if it exists, send the user to the appropriate server cookie MAPPSERVER indirect nocache preserve server mapp1 server mapp2 server mapp :80 check inter 2000 cookie mapp :80 check inter 2000 cookie mapp :80 check inter 2000 cookie mapp3 backup
43 Advantages TL;DR #2 New vulnerabilities and cipher preferences can be managed for all web systems by tweaking our HAProxy configuration TL;DR #1 We can renew or update our wildcard certificate in one location now we re more likely to revoke and reissue!
44 More Advantages (for MMCC) Two production HAProxy VMs share an IP address When a particular web site goes down, we can put up a standard error page with our help desk info (and possibly a system status page!) Configuring HTTPS for new web systems is much easier copy & paste from sections of the configuration file! We can have test load balancers just change host file on local computer to use our test HAProxy server s configuration We were able to launch a CMS at the same URL and keep the old one running!
45 Making the Case for HTTPS Everywhere
46 FAQs Why encrypt regular content? https.cio.gov/everything Today, there is no such thing as non-sensitive web traffic, and public services should not depend on the benevolence of network operators. Google is giving preference to HTTPS content. Apple emphasizing in ios 9. Doesn t encrypting all requests make them slower? istlsfastyet.com TLS has exactly one performance problem: it is not used widely enough. The Changelog #161: HTTP/2 (formerly SPDY) only supported over TLS by major browsers. Certificates are expensive! letsencrypt.org EFF launching in September 2015
47 Letting go of IE 6
48 Letting go of IE 6 Download IE 6 VM from Modern.IE and see how much of the web has moved on!
49 Embedding Challenges
50 Embedding Challenges
51 Embedding Challenges Step 1: Try changing http https in the URL Step 2: Provide link to original video
52 1. Continue looking for the lock Takeaways 2. Enable HTTPS for all login screens 3. Play around the Qualsys SSL labs tool ssllabs.com/ssltest How are your web sites? How is your bank s site? Other sites you frequent? 4. Start moving to HTTPS everywhere! Holistically consider how you manage your certificates and web server configurations Centralize web services behind appliances or open source load balancers Practice reissuing certificates
ALOHA LOAD BALANCER MANAGING SSL ON THE BACKEND & FRONTEND
 ALOHA LOAD BALANCER MANAGING SSL ON THE BACKEND & FRONTEND APPNOTE #0023 MANAGING SSL ON THE BACKEND & FRONTEND This application note is intended to help you implement SSL management on both the backend
ALOHA LOAD BALANCER MANAGING SSL ON THE BACKEND & FRONTEND APPNOTE #0023 MANAGING SSL ON THE BACKEND & FRONTEND This application note is intended to help you implement SSL management on both the backend
HAProxy. Ryan O'Hara Principal Software Engineer, Red Hat September 17, 2014. 1 HAProxy
 HAProxy Ryan O'Hara Principal Software Engineer, Red Hat September 17, 2014 1 HAProxy HAProxy Overview Capabilities Configuration OpenStack HA Neutron LBaaS Resources Questions 2 HAProxy Overview Load
HAProxy Ryan O'Hara Principal Software Engineer, Red Hat September 17, 2014 1 HAProxy HAProxy Overview Capabilities Configuration OpenStack HA Neutron LBaaS Resources Questions 2 HAProxy Overview Load
Web Load Balancing on a Budget
 Web Load Balancing on a Budget Pain Hosting 60+ websites Single web server Redundant subsystems (disk, power) SPOF Inconvenient maintenance windows Clients MY TEAM! Scope Simple. Availability. Minimize/mitigate
Web Load Balancing on a Budget Pain Hosting 60+ websites Single web server Redundant subsystems (disk, power) SPOF Inconvenient maintenance windows Clients MY TEAM! Scope Simple. Availability. Minimize/mitigate
Is Your SSL Website and Mobile App Really Secure?
 Is Your SSL Website and Mobile App Really Secure? Agenda What is SSL / TLS SSL Vulnerabilities PC/Server Mobile Advice to the Public Hong Kong Computer Emergency Response Team Coordination Centre 香 港 電
Is Your SSL Website and Mobile App Really Secure? Agenda What is SSL / TLS SSL Vulnerabilities PC/Server Mobile Advice to the Public Hong Kong Computer Emergency Response Team Coordination Centre 香 港 電
SSL BEST PRACTICES OVERVIEW
 SSL BEST PRACTICES OVERVIEW THESE PROBLEMS ARE PERVASIVE 77.9% 5.2% 19.2% 42.3% 77.9% of sites are HTTP 5.2% have an incomplete chain 19.2% support weak/insecure cipher suites 42.3% support SSL 3.0 83.1%
SSL BEST PRACTICES OVERVIEW THESE PROBLEMS ARE PERVASIVE 77.9% 5.2% 19.2% 42.3% 77.9% of sites are HTTP 5.2% have an incomplete chain 19.2% support weak/insecure cipher suites 42.3% support SSL 3.0 83.1%
Proto Balance SSL TLS Off-Loading, Load Balancing. User Manual - SSL. http://www.protonet.co.za/
 Proto Balance SSL TLS Off-Loading, Load Balancing http://www.protonet.co.za/ User Manual - SSL Copyright c 2003-2010 Shine The Way 238 CC. All rights reserved. March 13, 2010 Contents 1. Introduction........................................................................
Proto Balance SSL TLS Off-Loading, Load Balancing http://www.protonet.co.za/ User Manual - SSL Copyright c 2003-2010 Shine The Way 238 CC. All rights reserved. March 13, 2010 Contents 1. Introduction........................................................................
CS312 Solutions #6. March 13, 2015
 CS312 Solutions #6 March 13, 2015 Solutions 1. (1pt) Define in detail what a load balancer is and what problem it s trying to solve. Give at least two examples of where using a load balancer might be useful,
CS312 Solutions #6 March 13, 2015 Solutions 1. (1pt) Define in detail what a load balancer is and what problem it s trying to solve. Give at least two examples of where using a load balancer might be useful,
ALOHA Load-Balancer. Microsoft Exchange 2010 deployment guide. Document version: v1.4. ALOHA version concerned: v4.2 and above
 ALOHA Load-Balancer Microsoft Exchange 2010 deployment guide Document version: v1.4 ALOHA version concerned: Microsoft Exchange Server: v4.2 and above 2010 RTM, SP1, SP2, SP3 Last update date: November
ALOHA Load-Balancer Microsoft Exchange 2010 deployment guide Document version: v1.4 ALOHA version concerned: Microsoft Exchange Server: v4.2 and above 2010 RTM, SP1, SP2, SP3 Last update date: November
Native SSL support was implemented in HAProxy 1.5.x, which was released as a stable version in June 2014.
 Introduction HAProxy, which stands for High Availability Proxy, is a popular open source software TCP/HTTP Load Balancer and proxying solution which can be run on Linux, Solaris, and FreeBSD. Its most
Introduction HAProxy, which stands for High Availability Proxy, is a popular open source software TCP/HTTP Load Balancer and proxying solution which can be run on Linux, Solaris, and FreeBSD. Its most
SSL/TLS: The Ugly Truth
 SSL/TLS: The Ugly Truth Examining the flaws in SSL/TLS protocols, and the use of certificate authorities. Adrian Hayter CNS Hut 3 Team [email protected] Contents Introduction to SSL/TLS Cryptography
SSL/TLS: The Ugly Truth Examining the flaws in SSL/TLS protocols, and the use of certificate authorities. Adrian Hayter CNS Hut 3 Team [email protected] Contents Introduction to SSL/TLS Cryptography
EMC VIPR SRM 3.7: GUIDELINES FOR CONFIGURING MULTIPLE FRONTEND SERVERS
 EMC VIPR SRM 3.7: GUIDELINES FOR CONFIGURING MULTIPLE FRONTEND SERVERS ABSTRACT This document describes how to deploy two frontend servers in an EMC ViPR SRM 3.7 installation. The steps presented in this
EMC VIPR SRM 3.7: GUIDELINES FOR CONFIGURING MULTIPLE FRONTEND SERVERS ABSTRACT This document describes how to deploy two frontend servers in an EMC ViPR SRM 3.7 installation. The steps presented in this
Introduction. Purpose. Background. Details
 Introduction Recent media reports confirm that Secure Socket Layer (SSL) 3.0 is obsolete and insecure. This report provides guidance on how to ensure your communications use the more secure Transport Layer
Introduction Recent media reports confirm that Secure Socket Layer (SSL) 3.0 is obsolete and insecure. This report provides guidance on how to ensure your communications use the more secure Transport Layer
Network Security Essentials Chapter 5
 Network Security Essentials Chapter 5 Fourth Edition by William Stallings Lecture slides by Lawrie Brown Chapter 5 Transport-Level Security Use your mentality Wake up to reality From the song, "I've Got
Network Security Essentials Chapter 5 Fourth Edition by William Stallings Lecture slides by Lawrie Brown Chapter 5 Transport-Level Security Use your mentality Wake up to reality From the song, "I've Got
HaProxy możliwości i zastosowania. Marek Oszczapiński m.oszczapiń[email protected]
 HaProxy możliwości i zastosowania Marek Oszczapiński m.oszczapiń[email protected] Agenda Wstęp HaProxy Konfiguracja i zastosowani Podsumowanie Load Balancing Sprzętowe F5, Cisco LD, loadbalancer.org
HaProxy możliwości i zastosowania Marek Oszczapiński m.oszczapiń[email protected] Agenda Wstęp HaProxy Konfiguracja i zastosowani Podsumowanie Load Balancing Sprzętowe F5, Cisco LD, loadbalancer.org
Configuring HAproxy as a SwiftStack Load Balancer
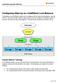 Configuring HAproxy as a SwiftStack Load Balancer To illustrate how a SwiftStack cluster can be configured with an external load balancer, such as HAProxy, let s walk through a step-by-step example of
Configuring HAproxy as a SwiftStack Load Balancer To illustrate how a SwiftStack cluster can be configured with an external load balancer, such as HAProxy, let s walk through a step-by-step example of
Chapter 7 Transport-Level Security
 Cryptography and Network Security Chapter 7 Transport-Level Security Lectured by Nguyễn Đức Thái Outline Web Security Issues Security Socket Layer (SSL) Transport Layer Security (TLS) HTTPS Secure Shell
Cryptography and Network Security Chapter 7 Transport-Level Security Lectured by Nguyễn Đức Thái Outline Web Security Issues Security Socket Layer (SSL) Transport Layer Security (TLS) HTTPS Secure Shell
Snapt Balancer Manual
 Snapt Balancer Manual Version 1.2 pg. 1 Contents Chapter 1: Introduction... 3 Chapter 2: General Usage... 4 Configuration Default Settings... 4 Configuration Performance Tuning... 6 Configuration Snapt
Snapt Balancer Manual Version 1.2 pg. 1 Contents Chapter 1: Introduction... 3 Chapter 2: General Usage... 4 Configuration Default Settings... 4 Configuration Performance Tuning... 6 Configuration Snapt
SSL Server Rating Guide
 SSL Server Rating Guide version 2009j (20 May 2015) Copyright 2009-2015 Qualys SSL Labs (www.ssllabs.com) Abstract The Secure Sockets Layer (SSL) protocol is a standard for encrypted network communication.
SSL Server Rating Guide version 2009j (20 May 2015) Copyright 2009-2015 Qualys SSL Labs (www.ssllabs.com) Abstract The Secure Sockets Layer (SSL) protocol is a standard for encrypted network communication.
Security Protocols/Standards
 Security Protocols/Standards Security Protocols/Standards Security Protocols/Standards How do we actually communicate securely across a hostile network? Provide integrity, confidentiality, authenticity
Security Protocols/Standards Security Protocols/Standards Security Protocols/Standards How do we actually communicate securely across a hostile network? Provide integrity, confidentiality, authenticity
More on SHA-1 deprecation:
 Dear PTC Axeda Customer, This message specifies Axeda and IDM Agent upgrade requirements and timelines for transitioning Axeda Enterprise Server, Global Access Server (GAS), Policy Server, and Questra
Dear PTC Axeda Customer, This message specifies Axeda and IDM Agent upgrade requirements and timelines for transitioning Axeda Enterprise Server, Global Access Server (GAS), Policy Server, and Questra
HTTPS is Fast and Hassle-free with CloudFlare
 HTTPS is Fast and Hassle-free with CloudFlare 1 888 99 FLARE [email protected] www.cloudflare.com In the past, organizations had to choose between performance and security when encrypting their
HTTPS is Fast and Hassle-free with CloudFlare 1 888 99 FLARE [email protected] www.cloudflare.com In the past, organizations had to choose between performance and security when encrypting their
HAProxy. Free, Fast High Availability and Load Balancing. Adam Thornton 10 September 2014
 HAProxy Free, Fast High Availability and Load Balancing Adam Thornton 10 September 2014 What? HAProxy is a proxy for Layer 4 (TCP) or Layer 7 (HTTP) traffic GPLv2 http://www.haproxy.org Disclaimer: I don't
HAProxy Free, Fast High Availability and Load Balancing Adam Thornton 10 September 2014 What? HAProxy is a proxy for Layer 4 (TCP) or Layer 7 (HTTP) traffic GPLv2 http://www.haproxy.org Disclaimer: I don't
Whitepaper : Using Unsniff Network Analyzer to analyze SSL / TLS
 Whitepaper : Using Unsniff Network Analyzer to analyze SSL / TLS A number of applications today use SSL and TLS as a security layer. Unsniff allows authorized users to analyze these applications by decrypting
Whitepaper : Using Unsniff Network Analyzer to analyze SSL / TLS A number of applications today use SSL and TLS as a security layer. Unsniff allows authorized users to analyze these applications by decrypting
Criteria for web application security check. Version 2015.1
 Criteria for web application security check Version 2015.1 i Content Introduction... iii ISC- P- 001 ISC- P- 001.1 ISC- P- 001.2 ISC- P- 001.3 ISC- P- 001.4 ISC- P- 001.5 ISC- P- 001.6 ISC- P- 001.7 ISC-
Criteria for web application security check Version 2015.1 i Content Introduction... iii ISC- P- 001 ISC- P- 001.1 ISC- P- 001.2 ISC- P- 001.3 ISC- P- 001.4 ISC- P- 001.5 ISC- P- 001.6 ISC- P- 001.7 ISC-
SSL: Paved With Good Intentions. Richard Moore [email protected]
 SSL: Paved With Good Intentions Richard Moore [email protected] Why do we need SSL? Privacy Online shopping Online banking Identity Protection Data Integrity Early SSL First public version was SSLv2
SSL: Paved With Good Intentions Richard Moore [email protected] Why do we need SSL? Privacy Online shopping Online banking Identity Protection Data Integrity Early SSL First public version was SSLv2
Security Protocols HTTPS/ DNSSEC TLS. Internet (IPSEC) Network (802.1x) Application (HTTP,DNS) Transport (TCP/UDP) Transport (TCP/UDP) Internet (IP)
 Security Protocols Security Protocols Necessary to communicate securely across untrusted network Provide integrity, confidentiality, authenticity of communications Based on previously discussed cryptographic
Security Protocols Security Protocols Necessary to communicate securely across untrusted network Provide integrity, confidentiality, authenticity of communications Based on previously discussed cryptographic
Secure Web Appliance. SSL Intercept
 Secure Web Appliance SSL Intercept Table of Contents 1. Introduction... 1 1.1. About CYAN Secure Web Appliance... 1 1.2. About SSL Intercept... 1 1.3. About this Manual... 1 1.3.1. Document Conventions...
Secure Web Appliance SSL Intercept Table of Contents 1. Introduction... 1 1.1. About CYAN Secure Web Appliance... 1 1.2. About SSL Intercept... 1 1.3. About this Manual... 1 1.3.1. Document Conventions...
Chapter 17. Transport-Level Security
 Chapter 17 Transport-Level Security Web Security Considerations The World Wide Web is fundamentally a client/server application running over the Internet and TCP/IP intranets The following characteristics
Chapter 17 Transport-Level Security Web Security Considerations The World Wide Web is fundamentally a client/server application running over the Internet and TCP/IP intranets The following characteristics
Payius. Guide to SSL certicates in ecommerce
 Payius Guide to SSL certicates in ecommerce Page 2 Table of Contents 1 About This Guide...3 1.1 Purpose...3 1.2 Audience...3 1.3 Prerequisites...3 1.4 Related Documents...3 2 SSL - The Basics...4 2.1 General...4
Payius Guide to SSL certicates in ecommerce Page 2 Table of Contents 1 About This Guide...3 1.1 Purpose...3 1.2 Audience...3 1.3 Prerequisites...3 1.4 Related Documents...3 2 SSL - The Basics...4 2.1 General...4
Topics in Network Security
 Topics in Network Security Jem Berkes MASc. ECE, University of Waterloo B.Sc. ECE, University of Manitoba www.berkes.ca February, 2009 Ver. 2 In this presentation Wi-Fi security (802.11) Protecting insecure
Topics in Network Security Jem Berkes MASc. ECE, University of Waterloo B.Sc. ECE, University of Manitoba www.berkes.ca February, 2009 Ver. 2 In this presentation Wi-Fi security (802.11) Protecting insecure
SSL Report: ebfl.srpskabanka.rs (91.240.6.48)
 Home Projects Qualys.com Contact You are here: Home > Projects > SSL Server Test > SSL Report: (91.240.6.48) Assessed on: Sun, 03 Jan 2016 15:46:07 UTC HIDDEN Clear cache Scan Another» Summary Overall
Home Projects Qualys.com Contact You are here: Home > Projects > SSL Server Test > SSL Report: (91.240.6.48) Assessed on: Sun, 03 Jan 2016 15:46:07 UTC HIDDEN Clear cache Scan Another» Summary Overall
Application Note. Active Directory Federation Services deployment guide
 Application Note Active Directory Federation Services deployment guide Document version: v1.1 Last update: 20th January 2014 Purpose ALOHA Load-Balancer deployment guide for Microsoft ADFS and ADFS proxy
Application Note Active Directory Federation Services deployment guide Document version: v1.1 Last update: 20th January 2014 Purpose ALOHA Load-Balancer deployment guide for Microsoft ADFS and ADFS proxy
Exchange 2013 deployment guide
 ALOHA Load-Balancer - Application Note Document version: v1.2 Last update: 2nd June 2014 EMEA Headquarters 3, rue du petit robinson ZAC des Metz 78350 Jouy-en-Josas France http://www.haproxy.com/ Purpose
ALOHA Load-Balancer - Application Note Document version: v1.2 Last update: 2nd June 2014 EMEA Headquarters 3, rue du petit robinson ZAC des Metz 78350 Jouy-en-Josas France http://www.haproxy.com/ Purpose
How To Understand And Understand The Security Of A Key Infrastructure
 Security+ Guide to Network Security Fundamentals, Third Edition Chapter 12 Applying Cryptography Objectives Define digital certificates List the various types of digital certificates and how they are used
Security+ Guide to Network Security Fundamentals, Third Edition Chapter 12 Applying Cryptography Objectives Define digital certificates List the various types of digital certificates and how they are used
SSL-TLS VPN 3.0 Certification Report. For: Array Networks, Inc.
 SSL-TLS VPN 3.0 Certification Report For: Array Networks, Inc. Prepared by: ICSA Labs 1000 Bent Creek Blvd., Suite 200 Mechanicsburg, PA 17050 USA http://www.icsalabs.com SSL-TLS VPN 3.0 Certification
SSL-TLS VPN 3.0 Certification Report For: Array Networks, Inc. Prepared by: ICSA Labs 1000 Bent Creek Blvd., Suite 200 Mechanicsburg, PA 17050 USA http://www.icsalabs.com SSL-TLS VPN 3.0 Certification
How to configure SSL proxying in Zorp 3 F5
 How to configure SSL proxying in Zorp 3 F5 June 14, 2013 This tutorial describes how to configure Zorp to proxy SSL traffic Copyright 1996-2013 BalaBit IT Security Ltd. Table of Contents 1. Preface...
How to configure SSL proxying in Zorp 3 F5 June 14, 2013 This tutorial describes how to configure Zorp to proxy SSL traffic Copyright 1996-2013 BalaBit IT Security Ltd. Table of Contents 1. Preface...
Configuring Nex-Gen Web Load Balancer
 Configuring Nex-Gen Web Load Balancer Table of Contents Load Balancing Scenarios & Concepts Creating Load Balancer Node using Administration Service Creating Load Balancer Node using NodeCreator Connecting
Configuring Nex-Gen Web Load Balancer Table of Contents Load Balancing Scenarios & Concepts Creating Load Balancer Node using Administration Service Creating Load Balancer Node using NodeCreator Connecting
Security. Contents. S-72.3240 Wireless Personal, Local, Metropolitan, and Wide Area Networks 1
 Contents Security requirements Public key cryptography Key agreement/transport schemes Man-in-the-middle attack vulnerability Encryption. digital signature, hash, certification Complete security solutions
Contents Security requirements Public key cryptography Key agreement/transport schemes Man-in-the-middle attack vulnerability Encryption. digital signature, hash, certification Complete security solutions
SSL EXPLAINED SSL EXPLAINED
 1 Table of Contents Introduction... 3 What is SSL?... 4 How does SSL work?... 7 Google & SSL... 11 SSL/TLS... 13 Web Filtering SSL... 14 About Lightspeed Systems... 26 2 Introduction SSL is a challenge
1 Table of Contents Introduction... 3 What is SSL?... 4 How does SSL work?... 7 Google & SSL... 11 SSL/TLS... 13 Web Filtering SSL... 14 About Lightspeed Systems... 26 2 Introduction SSL is a challenge
Lab Exercise SSL/TLS. Objective. Step 1: Open a Trace. Step 2: Inspect the Trace
 Lab Exercise SSL/TLS Objective To observe SSL/TLS (Secure Sockets Layer / Transport Layer Security) in action. SSL/TLS is used to secure TCP connections, and it is widely used as part of the secure web:
Lab Exercise SSL/TLS Objective To observe SSL/TLS (Secure Sockets Layer / Transport Layer Security) in action. SSL/TLS is used to secure TCP connections, and it is widely used as part of the secure web:
SENSE Security overview 2014
 SENSE Security overview 2014 Abstract... 3 Overview... 4 Installation... 6 Device Control... 7 Enrolment Process... 8 Authentication... 9 Network Protection... 12 Local Storage... 13 Conclusion... 15 2
SENSE Security overview 2014 Abstract... 3 Overview... 4 Installation... 6 Device Control... 7 Enrolment Process... 8 Authentication... 9 Network Protection... 12 Local Storage... 13 Conclusion... 15 2
3.2: Transport Layer: SSL/TLS Secure Socket Layer (SSL) Transport Layer Security (TLS) Protocol
 Chapter 2: Security Techniques Background Chapter 3: Security on Network and Transport Layer Network Layer: IPSec Transport Layer: SSL/TLS Chapter 4: Security on the Application Layer Chapter 5: Security
Chapter 2: Security Techniques Background Chapter 3: Security on Network and Transport Layer Network Layer: IPSec Transport Layer: SSL/TLS Chapter 4: Security on the Application Layer Chapter 5: Security
Transport Layer Security Protocols
 SSL/TLS 1 Transport Layer Security Protocols Secure Socket Layer (SSL) Originally designed to by Netscape to secure HTTP Version 2 is being replaced by version 3 Subsequently became Internet Standard known
SSL/TLS 1 Transport Layer Security Protocols Secure Socket Layer (SSL) Originally designed to by Netscape to secure HTTP Version 2 is being replaced by version 3 Subsequently became Internet Standard known
BlackBerry Enterprise Service 10. Secure Work Space for ios and Android Version: 10.1.1. Security Note
 BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
Reverse Proxy Guide. Version 2.0 April 2016
 Version 2.0 April 2016 Reverse Proxy Guide Copyright 2016 iwebgate. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated
Version 2.0 April 2016 Reverse Proxy Guide Copyright 2016 iwebgate. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated
Secure Socket Layer (SSL) and Transport Layer Security (TLS)
 Secure Socket Layer (SSL) and Transport Layer Security (TLS) Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 [email protected] Audio/Video recordings of this lecture are available
Secure Socket Layer (SSL) and Transport Layer Security (TLS) Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 [email protected] Audio/Video recordings of this lecture are available
SSL and Browsers: The Pillars of Broken Security
 SSL and Browsers: The Pillars of Broken Security Ivan Ristic Wolfgang Kandek Qualys, Inc. Session ID: TECH-403 Session Classification: Intermediate SSL, TLS, And PKI SSL (or TLS, if you prefer) is the
SSL and Browsers: The Pillars of Broken Security Ivan Ristic Wolfgang Kandek Qualys, Inc. Session ID: TECH-403 Session Classification: Intermediate SSL, TLS, And PKI SSL (or TLS, if you prefer) is the
Integrated SSL Scanning
 Software Version 9.0 Copyright Copyright 1996-2008. Finjan Software Inc. and its affiliates and subsidiaries ( Finjan ). All rights reserved. All text and figures included in this publication are the exclusive
Software Version 9.0 Copyright Copyright 1996-2008. Finjan Software Inc. and its affiliates and subsidiaries ( Finjan ). All rights reserved. All text and figures included in this publication are the exclusive
Service Manager and the Heartbleed Vulnerability (CVE-2014-0160)
 Service Manager and the Heartbleed Vulnerability (CVE-2014-0160) Revision 1.0 As of: April 15, 2014 Table of Contents Situation Overview 2 Clarification on the vulnerability applicability 2 Recommended
Service Manager and the Heartbleed Vulnerability (CVE-2014-0160) Revision 1.0 As of: April 15, 2014 Table of Contents Situation Overview 2 Clarification on the vulnerability applicability 2 Recommended
Investment Management System. Connectivity Guide. IMS Connectivity Guide Page 1 of 11
 Investment Management System Connectivity Guide IMS Connectivity Guide Page 1 of 11 1. Introduction This document details the necessary steps and procedures required for organisations to access the Homes
Investment Management System Connectivity Guide IMS Connectivity Guide Page 1 of 11 1. Introduction This document details the necessary steps and procedures required for organisations to access the Homes
Load Balancing Oracle Application Server (Oracle HTTP Server) Quick Reference Guide
 Load Balancing Oracle Application Server (Oracle HTTP Server) Quick Reference Guide v1.1.0 Oracle HTTP Server Ports By default Oracle HTTP Server listens on HTTP port 7777 and HTTPS is disabled. When HTTPS
Load Balancing Oracle Application Server (Oracle HTTP Server) Quick Reference Guide v1.1.0 Oracle HTTP Server Ports By default Oracle HTTP Server listens on HTTP port 7777 and HTTPS is disabled. When HTTPS
DEVELOPING CERTIFICATE-BASED PROJECTS FOR WEB SECURITY CLASSES *
 DEVELOPING CERTIFICATE-BASED PROJECTS FOR WEB SECURITY CLASSES * Shamima Rahman Tuan Anh Nguyen T. Andrew Yang Univ. of Houston Clear Lake 2700 Bay Area Blvd., Houston, TX 77058 [email protected] [email protected]
DEVELOPING CERTIFICATE-BASED PROJECTS FOR WEB SECURITY CLASSES * Shamima Rahman Tuan Anh Nguyen T. Andrew Yang Univ. of Houston Clear Lake 2700 Bay Area Blvd., Houston, TX 77058 [email protected] [email protected]
SSL implementieren aber sicher!
 SSL implementieren aber sicher! Karlsruher Entwicklertag 2014 21.05.2014 Dr. Yun Ding SSL in the news 2011 2012 2013 2014 BEAST CRIME Lucky 13 Compromised CAs RC4 biases BREACH DRBG Backdoor Apple goto
SSL implementieren aber sicher! Karlsruher Entwicklertag 2014 21.05.2014 Dr. Yun Ding SSL in the news 2011 2012 2013 2014 BEAST CRIME Lucky 13 Compromised CAs RC4 biases BREACH DRBG Backdoor Apple goto
Migrating the SSL Offloading Configuration of the Alteon Application Switch 2424-SSL to AlteonOS version 27.0.0.0
 Migrating the SSL Offloading Configuration of the Alteon Application Switch 2424-SSL to AlteonOS version 27.0.0.0 Table of Contents 1 Introduction... 1 2 Certificates Repository... 2 3 Common SSL Offloading
Migrating the SSL Offloading Configuration of the Alteon Application Switch 2424-SSL to AlteonOS version 27.0.0.0 Table of Contents 1 Introduction... 1 2 Certificates Repository... 2 3 Common SSL Offloading
ISY994 Series Network Security Configuration Guide Requires firmware version 3.3.1+ Requires Java 1.7+
 ISY994 Series Network Security Configuration Guide Requires firmware version 3.3.1+ Requires Java 1.7+ Introduction Universal Devices, Inc. takes ISY security extremely seriously. As such, all ISY994 Series
ISY994 Series Network Security Configuration Guide Requires firmware version 3.3.1+ Requires Java 1.7+ Introduction Universal Devices, Inc. takes ISY security extremely seriously. As such, all ISY994 Series
IUCLID 5 Guidance and Support
 IUCLID 5 Guidance and Support Web Service Installation Guide July 2012 v 2.4 July 2012 1/11 Table of Contents 1. Introduction 3 1.1. Important notes 3 1.2. Prerequisites 3 1.3. Installation files 4 2.
IUCLID 5 Guidance and Support Web Service Installation Guide July 2012 v 2.4 July 2012 1/11 Table of Contents 1. Introduction 3 1.1. Important notes 3 1.2. Prerequisites 3 1.3. Installation files 4 2.
Deployment Guide Microsoft IIS 7.0
 Deployment Guide Microsoft IIS 7.0 DG_IIS_022012.1 TABLE OF CONTENTS 1 Introduction... 4 2 Deployment Guide Overview... 4 3 Deployment Guide Prerequisites... 4 4 Accessing the AX Series Load Balancer...
Deployment Guide Microsoft IIS 7.0 DG_IIS_022012.1 TABLE OF CONTENTS 1 Introduction... 4 2 Deployment Guide Overview... 4 3 Deployment Guide Prerequisites... 4 4 Accessing the AX Series Load Balancer...
This chapter describes how to use the Junos Pulse Secure Access Service in a SAML single sign-on deployment. It includes the following sections:
 CHAPTER 1 SAML Single Sign-On This chapter describes how to use the Junos Pulse Secure Access Service in a SAML single sign-on deployment. It includes the following sections: Junos Pulse Secure Access
CHAPTER 1 SAML Single Sign-On This chapter describes how to use the Junos Pulse Secure Access Service in a SAML single sign-on deployment. It includes the following sections: Junos Pulse Secure Access
How to configure SSL proxying in Zorp 6
 How to configure SSL proxying in Zorp 6 April 17, 2015 Abstract This tutorial describes how to configure Zorp to proxy SSL traffic Copyright 1996-2015 BalaBit IT Security Ltd. Table of Contents 1. Preface...
How to configure SSL proxying in Zorp 6 April 17, 2015 Abstract This tutorial describes how to configure Zorp to proxy SSL traffic Copyright 1996-2015 BalaBit IT Security Ltd. Table of Contents 1. Preface...
CumuLogic Load Balancer Overview Guide. March 2013. CumuLogic Load Balancer Overview Guide 1
 CumuLogic Load Balancer Overview Guide March 2013 CumuLogic Load Balancer Overview Guide 1 Table of Contents CumuLogic Load Balancer... 3 Architectural Overview of CumuLogic Load Balancer... 4 How to Use
CumuLogic Load Balancer Overview Guide March 2013 CumuLogic Load Balancer Overview Guide 1 Table of Contents CumuLogic Load Balancer... 3 Architectural Overview of CumuLogic Load Balancer... 4 How to Use
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de
 Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Microsoft Forefront TMG How to use SQL Server 2008 Express Reporting Services Abstract In this
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Microsoft Forefront TMG How to use SQL Server 2008 Express Reporting Services Abstract In this
How to Configure Captive Portal
 How to Configure Captive Portal Captive portal is one of the user identification methods available on the Palo Alto Networks firewall. Unknown users sending HTTP or HTTPS 1 traffic will be authenticated,
How to Configure Captive Portal Captive portal is one of the user identification methods available on the Palo Alto Networks firewall. Unknown users sending HTTP or HTTPS 1 traffic will be authenticated,
Integrating the F5 BigIP with Blackboard
 Integrating the F5 BigIP with Blackboard Nick McClure [email protected] Lead Systems Programmer University of Kentucky Created August 1, 2006 Last Updated June 17, 2008 Integrating the F5 BigIP with Blackboard
Integrating the F5 BigIP with Blackboard Nick McClure [email protected] Lead Systems Programmer University of Kentucky Created August 1, 2006 Last Updated June 17, 2008 Integrating the F5 BigIP with Blackboard
Fast, Scalable And Secure Web Hosting For Entrepreneurs
 Fast, Scalable And Secure Web Hosting For Entrepreneurs Learn to set up your server and website Wim Bervoets This book is for sale at http://leanpub.com/fastscalableandsecurewebhostingforentrepreneurs
Fast, Scalable And Secure Web Hosting For Entrepreneurs Learn to set up your server and website Wim Bervoets This book is for sale at http://leanpub.com/fastscalableandsecurewebhostingforentrepreneurs
Real-Time Communication Security: SSL/TLS. Guevara Noubir [email protected] CSU610
 Real-Time Communication Security: SSL/TLS Guevara Noubir [email protected] CSU610 1 Some Issues with Real-time Communication Session key establishment Perfect Forward Secrecy Diffie-Hellman based PFS
Real-Time Communication Security: SSL/TLS Guevara Noubir [email protected] CSU610 1 Some Issues with Real-time Communication Session key establishment Perfect Forward Secrecy Diffie-Hellman based PFS
ATS Test Documentation
 ATS Test Documentation Release 0.1 Feifei Cai March 31, 2015 Contents 1 HTTP 3 1.1 Keep-alive................................................ 3 1.2 Connection Timeouts...........................................
ATS Test Documentation Release 0.1 Feifei Cai March 31, 2015 Contents 1 HTTP 3 1.1 Keep-alive................................................ 3 1.2 Connection Timeouts...........................................
Using etoken for SSL Web Authentication. SSL V3.0 Overview
 Using etoken for SSL Web Authentication Lesson 12 April 2004 etoken Certification Course SSL V3.0 Overview Secure Sockets Layer protocol, version 3.0 Provides communication privacy over the internet. Prevents
Using etoken for SSL Web Authentication Lesson 12 April 2004 etoken Certification Course SSL V3.0 Overview Secure Sockets Layer protocol, version 3.0 Provides communication privacy over the internet. Prevents
Setting Up SSL From Client to Web Server and Plugin to WAS
 IBM Software Group Setting Up SSL From Client to Web Server and Plugin to WAS Harold Fanning ([email protected]) WebSphere L2 Support 12 December 2012 Agenda Secure Socket Layer (SSL) from a Client to
IBM Software Group Setting Up SSL From Client to Web Server and Plugin to WAS Harold Fanning ([email protected]) WebSphere L2 Support 12 December 2012 Agenda Secure Socket Layer (SSL) from a Client to
Internet Banking System Web Application Penetration Test Report
 Internet Banking System Web Application Penetration Test Report Kiev - 2014 1. Executive Summary This report represents the results of the Bank (hereinafter the Client) Internet Banking Web Application
Internet Banking System Web Application Penetration Test Report Kiev - 2014 1. Executive Summary This report represents the results of the Bank (hereinafter the Client) Internet Banking Web Application
Digital Certificates (Public Key Infrastructure) Reshma Afshar Indiana State University
 Digital Certificates (Public Key Infrastructure) Reshma Afshar Indiana State University October 2015 1 List of Figures Contents 1 Introduction 1 2 History 2 3 Public Key Infrastructure (PKI) 3 3.1 Certificate
Digital Certificates (Public Key Infrastructure) Reshma Afshar Indiana State University October 2015 1 List of Figures Contents 1 Introduction 1 2 History 2 3 Public Key Infrastructure (PKI) 3 3.1 Certificate
Architecture and Data Flow Overview. BlackBerry Enterprise Service 10 721-08877-123 Version: 10.2. Quick Reference
 Architecture and Data Flow Overview BlackBerry Enterprise Service 10 721-08877-123 Version: Quick Reference Published: 2013-11-28 SWD-20131128130321045 Contents Key components of BlackBerry Enterprise
Architecture and Data Flow Overview BlackBerry Enterprise Service 10 721-08877-123 Version: Quick Reference Published: 2013-11-28 SWD-20131128130321045 Contents Key components of BlackBerry Enterprise
Best Practice Guide (SSL Implementation) for Mobile App Development 最 佳 行 事 指 引. Jointly published by. Publication version 1.
 Best Practice Guide (SSL Implementation) for Mobile App Development 流 動 應 用 程 式 (SSL 實 施 ) 最 佳 行 事 指 引 香 港 電 腦 事 故 協 調 中 心 ] Jointly published by [ 專 業 資 訊 保 安 協 會 ] Hong Kong Computer Emergency Response
Best Practice Guide (SSL Implementation) for Mobile App Development 流 動 應 用 程 式 (SSL 實 施 ) 最 佳 行 事 指 引 香 港 電 腦 事 故 協 調 中 心 ] Jointly published by [ 專 業 資 訊 保 安 協 會 ] Hong Kong Computer Emergency Response
Application Note. Lync 2010 deployment guide. Document version: v1.2 Last update: 12th December 2013 Lync server: 2010 ALOHA version: 5.
 Application Note Document version: v1.2 Last update: 12th December 2013 Lync server: 2010 ALOHA version: 5.5 and above Contents 1 Introduction 4 1.1 About Exceliance.....................................
Application Note Document version: v1.2 Last update: 12th December 2013 Lync server: 2010 ALOHA version: 5.5 and above Contents 1 Introduction 4 1.1 About Exceliance.....................................
Kentico CMS security facts
 Kentico CMS security facts ELSE 1 www.kentico.com Preface The document provides the reader an overview of how security is handled by Kentico CMS. It does not give a full list of all possibilities in the
Kentico CMS security facts ELSE 1 www.kentico.com Preface The document provides the reader an overview of how security is handled by Kentico CMS. It does not give a full list of all possibilities in the
Vulnerabilità dei protocolli SSL/TLS
 Università degli Studi di Milano Facoltà di Scienze Matematiche, Fisiche e Naturali Dipartimento di Informatica e Comunicazione Vulnerabilità dei protocolli SSL/TLS Andrea Visconti Overview Introduction
Università degli Studi di Milano Facoltà di Scienze Matematiche, Fisiche e Naturali Dipartimento di Informatica e Comunicazione Vulnerabilità dei protocolli SSL/TLS Andrea Visconti Overview Introduction
Enabling SSL and Client Certificates on the SAP J2EE Engine
 Enabling SSL and Client Certificates on the SAP J2EE Engine Angel Dichev RIG, SAP Labs SAP AG 1 Learning Objectives As a result of this session, you will be able to: Understand the different SAP J2EE Engine
Enabling SSL and Client Certificates on the SAP J2EE Engine Angel Dichev RIG, SAP Labs SAP AG 1 Learning Objectives As a result of this session, you will be able to: Understand the different SAP J2EE Engine
Sichere Software- Entwicklung für Java Entwickler
 Sichere Software- Entwicklung für Java Entwickler Dominik Schadow Senior Consultant Trivadis GmbH 05/09/2012 BASEL BERN LAUSANNE ZÜRICH DÜSSELDORF FRANKFURT A.M. FREIBURG I.BR. HAMBURG MÜNCHEN STUTTGART
Sichere Software- Entwicklung für Java Entwickler Dominik Schadow Senior Consultant Trivadis GmbH 05/09/2012 BASEL BERN LAUSANNE ZÜRICH DÜSSELDORF FRANKFURT A.M. FREIBURG I.BR. HAMBURG MÜNCHEN STUTTGART
Table of Contents. Open-Xchange Authentication & Session Handling. 1.Introduction...3
 Open-Xchange Authentication & Session Handling Table of Contents 1.Introduction...3 2.System overview/implementation...4 2.1.Overview... 4 2.1.1.Access to IMAP back end services...4 2.1.2.Basic Implementation
Open-Xchange Authentication & Session Handling Table of Contents 1.Introduction...3 2.System overview/implementation...4 2.1.Overview... 4 2.1.1.Access to IMAP back end services...4 2.1.2.Basic Implementation
Penetration Testing LAB Setup Guide
 Penetration Testing LAB Setup Guide (External Attacker - Intermediate) By: magikh0e - [email protected] Last Edit: July 06 2012 This guide assumes a few things... 1. You have read the basic guide of this
Penetration Testing LAB Setup Guide (External Attacker - Intermediate) By: magikh0e - [email protected] Last Edit: July 06 2012 This guide assumes a few things... 1. You have read the basic guide of this
How to break in. Tecniche avanzate di pen testing in ambito Web Application, Internal Network and Social Engineering
 How to break in Tecniche avanzate di pen testing in ambito Web Application, Internal Network and Social Engineering Time Agenda Agenda Item 9:30 10:00 Introduction 10:00 10:45 Web Application Penetration
How to break in Tecniche avanzate di pen testing in ambito Web Application, Internal Network and Social Engineering Time Agenda Agenda Item 9:30 10:00 Introduction 10:00 10:45 Web Application Penetration
SSL... 2 2.1. 3 2.2. 2.2.1. 2.2.2. SSL VPN
 1. Introduction... 2 2. Remote Access via SSL... 2 2.1. Configuration of the Astaro Security Gateway... 3 2.2. Configuration of the Remote Client...10 2.2.1. Astaro User Portal: Getting Software and Certificates...10
1. Introduction... 2 2. Remote Access via SSL... 2 2.1. Configuration of the Astaro Security Gateway... 3 2.2. Configuration of the Remote Client...10 2.2.1. Astaro User Portal: Getting Software and Certificates...10
You re FREE Guide SSL. (Secure Sockets Layer) webvisions www.webvisions.com +65 6868 1168 [email protected]
 SSL You re FREE Guide to (Secure Sockets Layer) What is a Digital Certificate? SSL Certificates, also known as public key certificates or Digital Certificates, are essential to secure Internet browsing.
SSL You re FREE Guide to (Secure Sockets Layer) What is a Digital Certificate? SSL Certificates, also known as public key certificates or Digital Certificates, are essential to secure Internet browsing.
Sophos UTM. Remote Access via SSL. Configuring UTM and Client
 Sophos UTM Remote Access via SSL Configuring UTM and Client Product version: 9.000 Document date: Friday, January 11, 2013 The specifications and information in this document are subject to change without
Sophos UTM Remote Access via SSL Configuring UTM and Client Product version: 9.000 Document date: Friday, January 11, 2013 The specifications and information in this document are subject to change without
Apache Tomcat. Load-balancing and Clustering. Mark Thomas, 20 November 2014. 2014 Pivotal Software, Inc. All rights reserved.
 2 Apache Tomcat Load-balancing and Clustering Mark Thomas, 20 November 2014 Introduction Apache Tomcat committer since December 2003 [email protected] Tomcat 8 release manager Member of the Servlet, WebSocket
2 Apache Tomcat Load-balancing and Clustering Mark Thomas, 20 November 2014 Introduction Apache Tomcat committer since December 2003 [email protected] Tomcat 8 release manager Member of the Servlet, WebSocket
AX Series with Microsoft Exchange Server 2010
 Deployment Guide AX Series with Microsoft Exchange Server 2010 v.1.1 DEPLOYMENT GUIDE AX Series with Microsoft Exchange Server 2010 Table of Contents 1. Introduction... 4 1.1 Prerequisites and Assumptions...4
Deployment Guide AX Series with Microsoft Exchange Server 2010 v.1.1 DEPLOYMENT GUIDE AX Series with Microsoft Exchange Server 2010 Table of Contents 1. Introduction... 4 1.1 Prerequisites and Assumptions...4
Astaro Security Gateway V8. Remote Access via SSL Configuring ASG and Client
 Astaro Security Gateway V8 Remote Access via SSL Configuring ASG and Client 1. Introduction This guide contains complementary information on the Administration Guide and the Online Help. If you are not
Astaro Security Gateway V8 Remote Access via SSL Configuring ASG and Client 1. Introduction This guide contains complementary information on the Administration Guide and the Online Help. If you are not
Security Engineering Part III Network Security. Security Protocols (I): SSL/TLS
 Security Engineering Part III Network Security Security Protocols (I): SSL/TLS Juan E. Tapiador [email protected] Department of Computer Science, UC3M Security Engineering 4th year BSc in Computer Science,
Security Engineering Part III Network Security Security Protocols (I): SSL/TLS Juan E. Tapiador [email protected] Department of Computer Science, UC3M Security Engineering 4th year BSc in Computer Science,
3. Broken Account and Session Management. 4. Cross-Site Scripting (XSS) Flaws. Web browsers execute code sent from websites. Account Management
 What is an? s Ten Most Critical Web Application Security Vulnerabilities Anthony LAI, CISSP, CISA Chapter Leader (Hong Kong) [email protected] Open Web Application Security Project http://www.owasp.org
What is an? s Ten Most Critical Web Application Security Vulnerabilities Anthony LAI, CISSP, CISA Chapter Leader (Hong Kong) [email protected] Open Web Application Security Project http://www.owasp.org
AAF boost. AAF boost 2014 report for AAF EXAMPLE ORGANISATION
 2014 AAF boost 2014 report for AAF EXAMPLE ORGANISATION This report focuses on the following 4 key areas to help boost your connection to the federation: Assurance; Awareness of federation tools; Your
2014 AAF boost 2014 report for AAF EXAMPLE ORGANISATION This report focuses on the following 4 key areas to help boost your connection to the federation: Assurance; Awareness of federation tools; Your
present the complete guide to ssl and seo
 present the complete guide to ssl and seo The Complete Guide to Setting up SSL and SEO Google recently announced that HTTPS is now being used as a ranking signal in its search engine algorithm. Websites
present the complete guide to ssl and seo The Complete Guide to Setting up SSL and SEO Google recently announced that HTTPS is now being used as a ranking signal in its search engine algorithm. Websites
A Study of What Really Breaks SSL HITB Amsterdam 2011
 A Study of What Really Breaks SSL HITB Amsterdam 2011 v1.0 Ivan Ristic Michael Small 20 May 2011 Agenda 1. State of SSL 2. Quick intro to SSL Labs 3. SSL Configuration Surveys 4. Survey of Actual SSL Usage
A Study of What Really Breaks SSL HITB Amsterdam 2011 v1.0 Ivan Ristic Michael Small 20 May 2011 Agenda 1. State of SSL 2. Quick intro to SSL Labs 3. SSL Configuration Surveys 4. Survey of Actual SSL Usage
Web Application Security Assessment and Vulnerability Mitigation Tests
 White paper BMC Remedy Action Request System 7.6.04 Web Application Security Assessment and Vulnerability Mitigation Tests January 2011 www.bmc.com Contacting BMC Software You can access the BMC Software
White paper BMC Remedy Action Request System 7.6.04 Web Application Security Assessment and Vulnerability Mitigation Tests January 2011 www.bmc.com Contacting BMC Software You can access the BMC Software
IIS Reverse Proxy Implementation
 IIS Reverse Proxy Implementation for OXI/OEDS Servers V E R S I O N : 1. 1 M A Y 2 9, 2 0 1 5 Table of Contents Intended Audience 3 About this Document 3 Advisories and Known Issues 3 Additional Considerations
IIS Reverse Proxy Implementation for OXI/OEDS Servers V E R S I O N : 1. 1 M A Y 2 9, 2 0 1 5 Table of Contents Intended Audience 3 About this Document 3 Advisories and Known Issues 3 Additional Considerations
DOSarrest Security Services (DSS) Version 4.0
 DOSarrest Security Services (DSS) Version 4.0 DOSarrest DSS User Guide The DSS is the main customer portal where customers can view and manipulate traffic statistics from a wide variety of variables that
DOSarrest Security Services (DSS) Version 4.0 DOSarrest DSS User Guide The DSS is the main customer portal where customers can view and manipulate traffic statistics from a wide variety of variables that
Lab Exercise SSL/TLS. Objective. Requirements. Step 1: Capture a Trace
 Lab Exercise SSL/TLS Objective To observe SSL/TLS (Secure Sockets Layer / Transport Layer Security) in action. SSL/TLS is used to secure TCP connections, and it is widely used as part of the secure web:
Lab Exercise SSL/TLS Objective To observe SSL/TLS (Secure Sockets Layer / Transport Layer Security) in action. SSL/TLS is used to secure TCP connections, and it is widely used as part of the secure web:
Table of Contents. Chapter 1: Installing Endpoint Application Control. Chapter 2: Getting Support. Index
 Table of Contents Chapter 1: Installing Endpoint Application Control System Requirements... 1-2 Installation Flow... 1-2 Required Components... 1-3 Welcome... 1-4 License Agreement... 1-5 Proxy Server...
Table of Contents Chapter 1: Installing Endpoint Application Control System Requirements... 1-2 Installation Flow... 1-2 Required Components... 1-3 Welcome... 1-4 License Agreement... 1-5 Proxy Server...
