Native SSL support was implemented in HAProxy 1.5.x, which was released as a stable version in June 2014.
|
|
|
- Neil Watts
- 10 years ago
- Views:
Transcription
1 Introduction HAProxy, which stands for High Availability Proxy, is a popular open source software TCP/HTTP Load Balancer and proxying solution which can be run on Linux, Solaris, and FreeBSD. Its most common use is to improve the performance and reliability of a server environment by distributing the workload across multiple servers (e.g. web, application, database). It is used in many high-profile environments, including: GitHub, Imgur, Instagram, and Twitter. In this tutorial, we will go over how to use HAProxy for SSL termination, for traffic encryption, and for load balancing your web servers. We will also show you how to use HAProxy to redirect HTTP traffic to HTTPS. Native SSL support was implemented in HAProxy 1.5.x, which was released as a stable version in June Prerequisites To complete this tutorial, you must have or obtain the following: At least one web server, with private networking, listening on HTTP (port 80) Root access to an additional VPS on which we will install HAProxy. Instructions to set up root access can be found here (steps 3 and 4): Initial Server Setup with Ubuntu An SSL certificate and private key pair with a "common name" that matches your domain name or IP address If you do not already have an SSL certificate and private key pair, please obtain one before continuing. Here are a few tutorials that contain steps that cover creating SSL certificates:
2 Create an StartSSL Certificate (private.key and ssl.crt) Create a Self-Signed SSL Certificate on Ubuntu (Step 2-- apache.key andapache.crt) Creating a Combined PEM SSL Certificate/Key File To implement SSL termination with HAProxy, we must ensure that your SSL certificate and key pair is in the proper format, PEM. In most cases, you can simply combine your SSL certificate (.crt or.cer file provided by a certificate authority) and its respective private key (.key file, generated by you). Assuming your certificate file is called example.com.crt, and your private key file is called example.com.key, here is an example of how to combine the files: cat example.com.crt example.com.key > example.com.pem sudo cp example.com.pem /etc/ssl/private/ This creates the combined PEM file, called example.com.pem and copies it to/etc/ssl/private. As always, be sure to secure any copies of your private key file, including the PEM file (which contains the private key). In some cases, you may need to copy your CA root certificate and CA intermediate certificates into your PEM file. Our Starting Environment Here is the environment that we are starting with: If your environment differs from the example, like if you are already using SSL on the web server or you have a separate database server, you should be able to adapt this tutorial to work with your environment.
3 If you are unfamiliar with basic load-balancing concepts or terminology, like layer 7 load balancing or backends or ACLs, here is an article that explains the basics: An Introduction to HAProxy and Load Balancing Concepts. Our Goal By the end of this tutorial, we want to have an environment that looks like this: That is, your users will access your website by connecting to your HAProxy server via HTTPS, which will decrypt the SSL session and forward the unencrypted requests to your web servers (i.e. the servers in www-backend) via their private network interfaces on port 80. Your web servers will then send their responses to your HAProxy server, which will encrypt the responses and send them back to the user that made the original request. You can set up your www-backend with as many web servers as you want, as long as they serve identical content. In other words, you can set this up with a single server then scale it out later by adding as many servers as you want. Remember, as your traffic increases, your HAProxy server may become a performance bottleneck if it does not have enough system resources to handle your user traffic.
4 Note: This tutorial does not cover how to ensure that your web/application servers serve the same content because that is often application or web server dependent. Install HAProxy 1.5.x Create a new VPS with private networking. For this tutorial, we will call it haproxy-www, but you may call it whatever you want. In our haproxy-www VPS, add the dedicated PPA to apt-get: sudo add-apt-repository ppa:vbernat/haproxy-1.5 Then update your apt cache: sudo apt-get update Then install HAProxy 1.5 with apt-get with the following command: sudo apt-get install haproxy Now that HAProxy 1.5 is installed, let's configure it! HAProxy Configuration HAProxy's configuration file is located at /etc/haproxy/haproxy.cfg and is divided into two major sections: Global: sets process-wide parameters Proxies: consists of defaults, listen, frontend, and backend sections Again, if you are unfamiliar with HAProxy or basic load-balancing concepts and terminology, please refer to this link: An Introduction to HAProxy and Load Balancing Concepts. HAProxy Configuration: Global All of the HAProxy configuration should be done on your HAProxy VPS, haproxy-www. Open haproxy.cfg in an editor:
5 sudo vi /etc/haproxy/haproxy.cfg You will see that there are two sections already defined: global and defaults. The first thing you will want to do is set maxconn to a reasonable number. This setting affects how many concurrent connections HAProxy will allow, which can affect QoS and prevent your web servers from crashing from trying to serve too many requests. You will need to play around with it to find what works for your environment. Add the following line (with a value you think is reasonable) to the global section of the configuration maxconn 2048 Next, in the defaults section, add the following lines under the line that says mode http: option forwardfor option http-server-close The forwardfor option sets HAProxy to add X-Forwarded-For headers to each request, and the http-server-close option reduces latency between HAProxy and your users by closing connections but maintaining keepalives. HAProxy Configuration: Stats Using HAProxy stats can be useful in determining how HAProxy is handling incoming traffic. If you would like to enable the HAProxy stats page, add the following lines in the defaultssection (substitute user and password with secure values): stats enable stats uri /stats stats realm Haproxy\ Statistics stats auth user:password This will allow you to look at the HAProxy stats page by going to your domain on /stats(e.g. Do not close the config file yet! We will add the proxy configuration next. HAProxy Configuration: Proxies
6 Frontend Configuration The first thing we want to add is a frontend to handle incoming HTTP connections. At the end of the file, let's add a frontend called www-http. Be sure to replace haproxy_www_public_ipwith the public IP of your haproxy-www VPS: frontend www-http bind haproxy_www_public_ip:80 reqadd X-Forwarded-Proto:\ http default_backend www-backend Here is an explanation of what each line in the frontend config snippet above means: frontend www-http: specifies a frontend named "www-http" bind haproxy_www_public_ip:80: replace haproxy_www_public_ip with haproxy-www's public IP address. This tells HAProxy that this frontend will handle the incoming network traffic on this IP address and port 80 (HTTP) reqadd X-Forwarded-Proto:\ http: Adds http header to end of end of the HTTP request default_backend www-backend: this specifies that any traffic that this frontend receives will be forwarded to www-backend, which we will define in a following step Next, we will add a frontend to handle incoming HTTPS connections. At the end of the file, let's add a frontend called www-https. Be sure to replace haproxy_www_public_ip with thepublic IP of your haproxy-www VPS: frontend www-https bind haproxy_www_public_ip:443 ssl crt /etc/ssl/private/example.com.pem reqadd X-Forwarded-Proto:\ https default_backend www-backend frontend www-https: specifies a frontend named "www-https" bind haproxy_www_public_ip:443 ssl crt...: replace haproxy_www_public_ip with haproxy-www's public IP address, and example.com.pem with your SSL certificate and key pair in combined pem format. This tells HAProxy that this frontend will handle the incoming network traffic on this IP address and port 443 (HTTPS).
7 reqadd X-Forwarded-Proto:\ https: Adds https header to end of end of the HTTPS request default_backend www-backend: this specifies that any traffic that this frontend receives will be forwarded to www-backend, which we will define in a following step Backend Configuration After you are finished configuring the frontends, continue adding your backend by adding the following lines. Be sure to replace the highlighted words with the respective private IP addresses of your web servers: backend www-backend redirect scheme https if!{ ssl_fc } server www-1 www_1_private_ip:80 check server www-2 www_2_private_ip:80 check Here is an explanation of what each line in the backend config snippet above means: backend www-backend: specifies a backend named www-backend redirect scheme https if!{ ssl_fc }: this line redirects HTTP requests to HTTPS, which makes your site HTTPS-only. If you want to allow both HTTP and HTTPS, remove this line server www-1...: specifies a backend server named www-1, the private IP (which you must substitute) and port that it is listening on, 80. The check option makes the load balancer periodically perform a health check on this server server www-2...: similar to the previous line. Add additional lines like this, with appropriate names and IP addresses to add more servers to the load balancer Now save and exit haproxy.cfg. HAProxy is now ready to be started, but let's enable logging first. Enable HAProxy Logging Enabling logging in HAProxy is very simple. First edit the rsyslog.conf file: sudo vi /etc/rsyslog.conf
8 Then find the following two lines, and uncomment them to enable UDP syslog reception. It should look like the following when you are done: $ModLoad imudp $UDPServerRun 514 $UDPServerAddress Now restart rsyslog to enable the new configuration: sudo service rsyslog restart HAProxy logging is is now enabled! The log file will be created at /var/log/haproxy.logonce HAProxy is started. Start HAProxy On haproxy-www, start HAProxy to put your configuration changes into effect: sudo service haproxy restart HAProxy is now performing SSL termination and load balancing your web servers! Your load balanced WordPress is now accessible to your user via the public IP address or domain name of your load balancer, haproxy-www! There are a few things that you will want to check, to make sure everything is set up correctly. Things to Check If you haven't already, update your nameservers to point your domain to your haproxy-www server's public IP address If you want your servers to use only HTTPS, you will want to make sure that your web servers (e.g. www-1, www-2, etc.) are only listening on their private IP addresses on port 80. Otherwise, users will be able to access your web servers via HTTP (unencrypted) on their public IP addresses. Visit haproxy-www via HTTPS and ensure that it works Visit haproxy-www via HTTP and ensure that it redirects to HTTPS (unless you configured it to allow both HTTP and HTTPS) Conclusion
9 Now you have a load balancer solution that handles your SSL connections and can be used to horizontally scale out your server environment. Feel free to combine what you have learned in this guide with other HAProxy guides to improve your environment even further!
ALOHA LOAD BALANCER MANAGING SSL ON THE BACKEND & FRONTEND
 ALOHA LOAD BALANCER MANAGING SSL ON THE BACKEND & FRONTEND APPNOTE #0023 MANAGING SSL ON THE BACKEND & FRONTEND This application note is intended to help you implement SSL management on both the backend
ALOHA LOAD BALANCER MANAGING SSL ON THE BACKEND & FRONTEND APPNOTE #0023 MANAGING SSL ON THE BACKEND & FRONTEND This application note is intended to help you implement SSL management on both the backend
HAProxy. Ryan O'Hara Principal Software Engineer, Red Hat September 17, 2014. 1 HAProxy
 HAProxy Ryan O'Hara Principal Software Engineer, Red Hat September 17, 2014 1 HAProxy HAProxy Overview Capabilities Configuration OpenStack HA Neutron LBaaS Resources Questions 2 HAProxy Overview Load
HAProxy Ryan O'Hara Principal Software Engineer, Red Hat September 17, 2014 1 HAProxy HAProxy Overview Capabilities Configuration OpenStack HA Neutron LBaaS Resources Questions 2 HAProxy Overview Load
FILECLOUD HIGH AVAILABILITY
 FILECLOUD HIGH AVAILABILITY ARCHITECTURE VERSION 1.0 FileCloud HA Architecture... 2 Load Balancers... 3 FileCloud Component: App server node... 3 FileCloud Component: Mongo DB Replica set... 3 Instructions
FILECLOUD HIGH AVAILABILITY ARCHITECTURE VERSION 1.0 FileCloud HA Architecture... 2 Load Balancers... 3 FileCloud Component: App server node... 3 FileCloud Component: Mongo DB Replica set... 3 Instructions
Configuring HAproxy as a SwiftStack Load Balancer
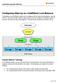 Configuring HAproxy as a SwiftStack Load Balancer To illustrate how a SwiftStack cluster can be configured with an external load balancer, such as HAProxy, let s walk through a step-by-step example of
Configuring HAproxy as a SwiftStack Load Balancer To illustrate how a SwiftStack cluster can be configured with an external load balancer, such as HAProxy, let s walk through a step-by-step example of
Load balancing MySQL with HaProxy. Peter Boros Consultant @ Percona 4/23/13 Santa Clara, CA
 Load balancing MySQL with HaProxy Peter Boros Consultant @ Percona 4/23/13 Santa Clara, CA Agenda What is HaProxy HaProxy configuration Load balancing topologies Checks Load balancing Percona XtraDB Cluster
Load balancing MySQL with HaProxy Peter Boros Consultant @ Percona 4/23/13 Santa Clara, CA Agenda What is HaProxy HaProxy configuration Load balancing topologies Checks Load balancing Percona XtraDB Cluster
How To Analyze Logs On Aloha On A Pcode On A Linux Server On A Microsoft Powerbook (For Acedo) On A Macbook Or Ipad (For An Ubuntu) On An Ubode (For Macrocess
 Application Note Analyze ALOHA s HAProxy logs with halog Document version: v1.1 Last update: 3rd September 2013 Purpose Being able to analyze logs generated by the ALOHA Load-Balancer stored in a third
Application Note Analyze ALOHA s HAProxy logs with halog Document version: v1.1 Last update: 3rd September 2013 Purpose Being able to analyze logs generated by the ALOHA Load-Balancer stored in a third
CS312 Solutions #6. March 13, 2015
 CS312 Solutions #6 March 13, 2015 Solutions 1. (1pt) Define in detail what a load balancer is and what problem it s trying to solve. Give at least two examples of where using a load balancer might be useful,
CS312 Solutions #6 March 13, 2015 Solutions 1. (1pt) Define in detail what a load balancer is and what problem it s trying to solve. Give at least two examples of where using a load balancer might be useful,
How to Make the Client IP Address Available to the Back-end Server
 How to Make the Client IP Address Available to the Back-end Server For Layer 4 - UDP and Layer 4 - TCP services, the actual client IP address is passed to the server in the TCP header. No further configuration
How to Make the Client IP Address Available to the Back-end Server For Layer 4 - UDP and Layer 4 - TCP services, the actual client IP address is passed to the server in the TCP header. No further configuration
HAProxy. Free, Fast High Availability and Load Balancing. Adam Thornton 10 September 2014
 HAProxy Free, Fast High Availability and Load Balancing Adam Thornton 10 September 2014 What? HAProxy is a proxy for Layer 4 (TCP) or Layer 7 (HTTP) traffic GPLv2 http://www.haproxy.org Disclaimer: I don't
HAProxy Free, Fast High Availability and Load Balancing Adam Thornton 10 September 2014 What? HAProxy is a proxy for Layer 4 (TCP) or Layer 7 (HTTP) traffic GPLv2 http://www.haproxy.org Disclaimer: I don't
Migrating the SSL Offloading Configuration of the Alteon Application Switch 2424-SSL to AlteonOS version 27.0.0.0
 Migrating the SSL Offloading Configuration of the Alteon Application Switch 2424-SSL to AlteonOS version 27.0.0.0 Table of Contents 1 Introduction... 1 2 Certificates Repository... 2 3 Common SSL Offloading
Migrating the SSL Offloading Configuration of the Alteon Application Switch 2424-SSL to AlteonOS version 27.0.0.0 Table of Contents 1 Introduction... 1 2 Certificates Repository... 2 3 Common SSL Offloading
vrealize Operations Manager Load Balancing
 vrealize Operations Manager Load Balancing Configuration Guide Version 6.x T E C H N I C A L W H I T E P A P E R D E C E M B E R 2 0 1 5 V E R S I O N 1. 0 Table of Contents Introduction... 4 Load Balancing
vrealize Operations Manager Load Balancing Configuration Guide Version 6.x T E C H N I C A L W H I T E P A P E R D E C E M B E R 2 0 1 5 V E R S I O N 1. 0 Table of Contents Introduction... 4 Load Balancing
Application Note. Active Directory Federation Services deployment guide
 Application Note Active Directory Federation Services deployment guide Document version: v1.1 Last update: 20th January 2014 Purpose ALOHA Load-Balancer deployment guide for Microsoft ADFS and ADFS proxy
Application Note Active Directory Federation Services deployment guide Document version: v1.1 Last update: 20th January 2014 Purpose ALOHA Load-Balancer deployment guide for Microsoft ADFS and ADFS proxy
disect Systems Logging Snort alerts to Syslog and Splunk PRAVEEN DARSHANAM
 disect Systems Logging Snort alerts to Syslog and Splunk PRAVEEN DARSHANAM INTRODUCTION Snort is an open source network Intrusion Detection and Prevention Systems (IDS/IPS) developed by Martin Roesch capable
disect Systems Logging Snort alerts to Syslog and Splunk PRAVEEN DARSHANAM INTRODUCTION Snort is an open source network Intrusion Detection and Prevention Systems (IDS/IPS) developed by Martin Roesch capable
Pertino HA Cluster Deployment: Enabling a Multi- Tier Web Application Using Amazon EC2 and Google CE. A Pertino Deployment Guide
 Pertino HA Cluster Deployment: Enabling a Multi- Tier Web Application Using Amazon EC2 and Google CE A Pertino Deployment Guide 1 Table of Contents Abstract... 2 Introduction... 3 Before you get Started...
Pertino HA Cluster Deployment: Enabling a Multi- Tier Web Application Using Amazon EC2 and Google CE A Pertino Deployment Guide 1 Table of Contents Abstract... 2 Introduction... 3 Before you get Started...
Ciphermail Gateway Separate Front-end and Back-end Configuration Guide
 CIPHERMAIL EMAIL ENCRYPTION Ciphermail Gateway Separate Front-end and Back-end Configuration Guide June 19, 2014, Rev: 8975 Copyright 2010-2014, ciphermail.com. CONTENTS CONTENTS Contents 1 Introduction
CIPHERMAIL EMAIL ENCRYPTION Ciphermail Gateway Separate Front-end and Back-end Configuration Guide June 19, 2014, Rev: 8975 Copyright 2010-2014, ciphermail.com. CONTENTS CONTENTS Contents 1 Introduction
CumuLogic Load Balancer Overview Guide. March 2013. CumuLogic Load Balancer Overview Guide 1
 CumuLogic Load Balancer Overview Guide March 2013 CumuLogic Load Balancer Overview Guide 1 Table of Contents CumuLogic Load Balancer... 3 Architectural Overview of CumuLogic Load Balancer... 4 How to Use
CumuLogic Load Balancer Overview Guide March 2013 CumuLogic Load Balancer Overview Guide 1 Table of Contents CumuLogic Load Balancer... 3 Architectural Overview of CumuLogic Load Balancer... 4 How to Use
Deploying F5 with Microsoft Active Directory Federation Services
 F5 Deployment Guide Deploying F5 with Microsoft Active Directory Federation Services This F5 deployment guide provides detailed information on how to deploy Microsoft Active Directory Federation Services
F5 Deployment Guide Deploying F5 with Microsoft Active Directory Federation Services This F5 deployment guide provides detailed information on how to deploy Microsoft Active Directory Federation Services
Deploying the Barracuda Load Balancer with Microsoft Exchange Server 2010 Version 2.6. Introduction. Table of Contents
 Deploying the Barracuda Load Balancer with Microsoft Exchange Server 2010 Version 2.6 Introduction Organizations use the Barracuda Load Balancer to distribute the load and increase the availability of
Deploying the Barracuda Load Balancer with Microsoft Exchange Server 2010 Version 2.6 Introduction Organizations use the Barracuda Load Balancer to distribute the load and increase the availability of
High Availability Cluster Solutions for Ubuntu14.04 on Power
 High Availability Cluster Solutions for Ubuntu14.04 on Power Author: Iranna D. Ankad ([email protected]) PowerLinux Test Architect Abstract: In this article we focus on how to set up a two-node apache
High Availability Cluster Solutions for Ubuntu14.04 on Power Author: Iranna D. Ankad ([email protected]) PowerLinux Test Architect Abstract: In this article we focus on how to set up a two-node apache
Load-Balancing Introduction (with examples...)
 Load-Balancing Introduction (with examples...) For AFNOG 2015 By Frank Kuse (Rework of slides from Joel Jaeggli and Laban Mwangi) 1 Load-Balancing Introduction (with examples...) For AFNOG 2015 By Frank
Load-Balancing Introduction (with examples...) For AFNOG 2015 By Frank Kuse (Rework of slides from Joel Jaeggli and Laban Mwangi) 1 Load-Balancing Introduction (with examples...) For AFNOG 2015 By Frank
Use Enterprise SSO as the Credential Server for Protected Sites
 Webthority HOW TO Use Enterprise SSO as the Credential Server for Protected Sites This document describes how to integrate Webthority with Enterprise SSO version 8.0.2 or 8.0.3. Webthority can be configured
Webthority HOW TO Use Enterprise SSO as the Credential Server for Protected Sites This document describes how to integrate Webthority with Enterprise SSO version 8.0.2 or 8.0.3. Webthority can be configured
Load Balancing VMware Horizon View. Deployment Guide
 Load Balancing VMware Horizon View Deployment Guide rev. 1.2.6 Copyright 2002 2015 Loadbalancer.org, Inc. 1 Table of Contents About this Guide...4 Loadbalancer.org Appliances Supported...4 Loadbalancer.org
Load Balancing VMware Horizon View Deployment Guide rev. 1.2.6 Copyright 2002 2015 Loadbalancer.org, Inc. 1 Table of Contents About this Guide...4 Loadbalancer.org Appliances Supported...4 Loadbalancer.org
What s Your HTTPS Grade? A Case Study of HTTPS/SSL at Mid Michigan Community College. Brandon Kish @kishba [email protected]
 What s Your HTTPS Grade? A Case Study of HTTPS/SSL at Mid Michigan Community College Brandon Kish @kishba [email protected] About Me Director of Programming Mid Michigan Community College ~4,500 students
What s Your HTTPS Grade? A Case Study of HTTPS/SSL at Mid Michigan Community College Brandon Kish @kishba [email protected] About Me Director of Programming Mid Michigan Community College ~4,500 students
Web Load Balancing on a Budget
 Web Load Balancing on a Budget Pain Hosting 60+ websites Single web server Redundant subsystems (disk, power) SPOF Inconvenient maintenance windows Clients MY TEAM! Scope Simple. Availability. Minimize/mitigate
Web Load Balancing on a Budget Pain Hosting 60+ websites Single web server Redundant subsystems (disk, power) SPOF Inconvenient maintenance windows Clients MY TEAM! Scope Simple. Availability. Minimize/mitigate
Deploying the BIG-IP LTM with. Citrix XenApp. Deployment Guide Version 1.2. What s inside: 2 Prerequisites and configuration notes
 Deployment Guide Version 1.2 Deploying the BIG-IP LTM with What s inside: 2 Prerequisites and configuration notes 3 Configuration Worksheet 4 Using the BIG-IP LTM Application Template for 8 Modifying the
Deployment Guide Version 1.2 Deploying the BIG-IP LTM with What s inside: 2 Prerequisites and configuration notes 3 Configuration Worksheet 4 Using the BIG-IP LTM Application Template for 8 Modifying the
DEPLOYMENT GUIDE Version 1.1. Deploying the BIG-IP LTM v10 with Citrix Presentation Server 4.5
 DEPLOYMENT GUIDE Version 1.1 Deploying the BIG-IP LTM v10 with Citrix Presentation Server 4.5 Table of Contents Table of Contents Deploying the BIG-IP system v10 with Citrix Presentation Server Prerequisites
DEPLOYMENT GUIDE Version 1.1 Deploying the BIG-IP LTM v10 with Citrix Presentation Server 4.5 Table of Contents Table of Contents Deploying the BIG-IP system v10 with Citrix Presentation Server Prerequisites
Load Balancing Microsoft Sharepoint 2010 Load Balancing Microsoft Sharepoint 2013. Deployment Guide
 Load Balancing Microsoft Sharepoint 2010 Load Balancing Microsoft Sharepoint 2013 Deployment Guide rev. 1.4.2 Copyright 2015 Loadbalancer.org, Inc. 1 Table of Contents About this Guide... 3 Appliances
Load Balancing Microsoft Sharepoint 2010 Load Balancing Microsoft Sharepoint 2013 Deployment Guide rev. 1.4.2 Copyright 2015 Loadbalancer.org, Inc. 1 Table of Contents About this Guide... 3 Appliances
Security IIS Service Lesson 6
 Security IIS Service Lesson 6 Skills Matrix Technology Skill Objective Domain Objective # Configuring Certificates Configure SSL security 3.6 Assigning Standard and Special NTFS Permissions Enabling and
Security IIS Service Lesson 6 Skills Matrix Technology Skill Objective Domain Objective # Configuring Certificates Configure SSL security 3.6 Assigning Standard and Special NTFS Permissions Enabling and
Penetration Testing LAB Setup Guide
 Penetration Testing LAB Setup Guide (External Attacker - Intermediate) By: magikh0e - [email protected] Last Edit: July 06 2012 This guide assumes a few things... 1. You have read the basic guide of this
Penetration Testing LAB Setup Guide (External Attacker - Intermediate) By: magikh0e - [email protected] Last Edit: July 06 2012 This guide assumes a few things... 1. You have read the basic guide of this
HaProxy możliwości i zastosowania. Marek Oszczapiński m.oszczapiń[email protected]
 HaProxy możliwości i zastosowania Marek Oszczapiński m.oszczapiń[email protected] Agenda Wstęp HaProxy Konfiguracja i zastosowani Podsumowanie Load Balancing Sprzętowe F5, Cisco LD, loadbalancer.org
HaProxy możliwości i zastosowania Marek Oszczapiński m.oszczapiń[email protected] Agenda Wstęp HaProxy Konfiguracja i zastosowani Podsumowanie Load Balancing Sprzętowe F5, Cisco LD, loadbalancer.org
Load balancing Microsoft IAG
 Load balancing Microsoft IAG Using ZXTM with Microsoft IAG (Intelligent Application Gateway) Server Zeus Technology Limited Zeus Technology UK: +44 (0)1223 525000 The Jeffreys Building 1955 Landings Drive
Load balancing Microsoft IAG Using ZXTM with Microsoft IAG (Intelligent Application Gateway) Server Zeus Technology Limited Zeus Technology UK: +44 (0)1223 525000 The Jeffreys Building 1955 Landings Drive
Introduction to Mobile Access Gateway Installation
 Introduction to Mobile Access Gateway Installation This document describes the installation process for the Mobile Access Gateway (MAG), which is an enterprise integration component that provides a secure
Introduction to Mobile Access Gateway Installation This document describes the installation process for the Mobile Access Gateway (MAG), which is an enterprise integration component that provides a secure
Snapt Balancer Manual
 Snapt Balancer Manual Version 1.2 pg. 1 Contents Chapter 1: Introduction... 3 Chapter 2: General Usage... 4 Configuration Default Settings... 4 Configuration Performance Tuning... 6 Configuration Snapt
Snapt Balancer Manual Version 1.2 pg. 1 Contents Chapter 1: Introduction... 3 Chapter 2: General Usage... 4 Configuration Default Settings... 4 Configuration Performance Tuning... 6 Configuration Snapt
Load Balancing Microsoft AD FS. Deployment Guide
 Load Balancing Microsoft AD FS Deployment Guide rev. 1.1.1 Copyright 2002 2015 Loadbalancer.org, Inc. Table of Contents About this Guide...4 Loadbalancer.org Appliances Supported...4 Loadbalancer.org Software
Load Balancing Microsoft AD FS Deployment Guide rev. 1.1.1 Copyright 2002 2015 Loadbalancer.org, Inc. Table of Contents About this Guide...4 Loadbalancer.org Appliances Supported...4 Loadbalancer.org Software
Deployment Guide Oracle Siebel CRM
 Deployment Guide Oracle Siebel CRM DG_ OrSCRM_032013.1 TABLE OF CONTENTS 1 Introduction...4 2 Deployment Topology...4 2.1 Deployment Prerequisites...6 2.2 Siebel CRM Server Roles...7 3 Accessing the AX
Deployment Guide Oracle Siebel CRM DG_ OrSCRM_032013.1 TABLE OF CONTENTS 1 Introduction...4 2 Deployment Topology...4 2.1 Deployment Prerequisites...6 2.2 Siebel CRM Server Roles...7 3 Accessing the AX
EMC VIPR SRM 3.7: GUIDELINES FOR CONFIGURING MULTIPLE FRONTEND SERVERS
 EMC VIPR SRM 3.7: GUIDELINES FOR CONFIGURING MULTIPLE FRONTEND SERVERS ABSTRACT This document describes how to deploy two frontend servers in an EMC ViPR SRM 3.7 installation. The steps presented in this
EMC VIPR SRM 3.7: GUIDELINES FOR CONFIGURING MULTIPLE FRONTEND SERVERS ABSTRACT This document describes how to deploy two frontend servers in an EMC ViPR SRM 3.7 installation. The steps presented in this
ADOBE CONNECT ENTERPRISE SERVER 6
 Chapter 1: ADOBE CONNECT ENTERPRISE SERVER 6 SSL CONFIGURATION GUIDE Copyright 2006 Adobe Systems Incorporated. All rights reserved. Adobe Connect Enterprise Server 6, for Windows If this guide is distributed
Chapter 1: ADOBE CONNECT ENTERPRISE SERVER 6 SSL CONFIGURATION GUIDE Copyright 2006 Adobe Systems Incorporated. All rights reserved. Adobe Connect Enterprise Server 6, for Windows If this guide is distributed
White Paper. Installation and Configuration of Fabasoft Folio IMAP Service. Fabasoft Folio 2015 Update Rollup 3
 White Paper Fabasoft Folio 2015 Update Rollup 3 Copyright Fabasoft R&D GmbH, Linz, Austria, 2016. All rights reserved. All hardware and software names used are registered trade names and/or registered
White Paper Fabasoft Folio 2015 Update Rollup 3 Copyright Fabasoft R&D GmbH, Linz, Austria, 2016. All rights reserved. All hardware and software names used are registered trade names and/or registered
App Orchestration 2.5
 Configuring NetScaler 10.5 Load Balancing with StoreFront 2.5.2 and NetScaler Gateway for Prepared by: James Richards Last Updated: August 20, 2014 Contents Introduction... 3 Configure the NetScaler load
Configuring NetScaler 10.5 Load Balancing with StoreFront 2.5.2 and NetScaler Gateway for Prepared by: James Richards Last Updated: August 20, 2014 Contents Introduction... 3 Configure the NetScaler load
Load Balancing Trend Micro InterScan Web Gateway
 Load Balancing Trend Micro InterScan Web Gateway Deployment Guide rev. 1.1.7 Copyright 2002 2015 Loadbalancer.org, Inc. 1 Table of Contents About this Guide... 3 Loadbalancer.org Appliances Supported...
Load Balancing Trend Micro InterScan Web Gateway Deployment Guide rev. 1.1.7 Copyright 2002 2015 Loadbalancer.org, Inc. 1 Table of Contents About this Guide... 3 Loadbalancer.org Appliances Supported...
Introduction to the EIS Guide
 Introduction to the EIS Guide The AirWatch Enterprise Integration Service (EIS) provides organizations the ability to securely integrate with back-end enterprise systems from either the AirWatch SaaS environment
Introduction to the EIS Guide The AirWatch Enterprise Integration Service (EIS) provides organizations the ability to securely integrate with back-end enterprise systems from either the AirWatch SaaS environment
SSL Inspection Step-by-Step Guide. June 6, 2016
 SSL Inspection Step-by-Step Guide June 6, 2016 Key Drivers for Inspecting Outbound SSL Traffic Eliminate blind spots of SSL encrypted communication to/from the enterprise Maintaining information s communication
SSL Inspection Step-by-Step Guide June 6, 2016 Key Drivers for Inspecting Outbound SSL Traffic Eliminate blind spots of SSL encrypted communication to/from the enterprise Maintaining information s communication
Prerequisites. Creating Profiles
 Prerequisites Make sure you have the following prerequisites completed: Determine what the FQDN will be and what virtual IP Address will be used. Add the FQDN and virtual IP into your company's DNS. Create
Prerequisites Make sure you have the following prerequisites completed: Determine what the FQDN will be and what virtual IP Address will be used. Add the FQDN and virtual IP into your company's DNS. Create
Step One: Installing Rsnapshot and Configuring SSH Keys
 Source: https://www.digitalocean.com/community/articles/how-to-installrsnapshot-on-ubuntu-12-04 What the Red Means The lines that the user needs to enter or customize will be in red in this tutorial! The
Source: https://www.digitalocean.com/community/articles/how-to-installrsnapshot-on-ubuntu-12-04 What the Red Means The lines that the user needs to enter or customize will be in red in this tutorial! The
CHAPTER 7 SSL CONFIGURATION AND TESTING
 CHAPTER 7 SSL CONFIGURATION AND TESTING 7.1 Configuration and Testing of SSL Nowadays, it s very big challenge to handle the enterprise applications as they are much complex and it is a very sensitive
CHAPTER 7 SSL CONFIGURATION AND TESTING 7.1 Configuration and Testing of SSL Nowadays, it s very big challenge to handle the enterprise applications as they are much complex and it is a very sensitive
How to Configure Captive Portal
 How to Configure Captive Portal Captive portal is one of the user identification methods available on the Palo Alto Networks firewall. Unknown users sending HTTP or HTTPS 1 traffic will be authenticated,
How to Configure Captive Portal Captive portal is one of the user identification methods available on the Palo Alto Networks firewall. Unknown users sending HTTP or HTTPS 1 traffic will be authenticated,
Microsoft Internet Information Services (IIS) Deployment Guide
 Microsoft Internet Information Services (IIS) Deployment Guide v1.2.9 Copyright 2013 Loadbalancer.org, Inc. 1 Table of Contents About this Guide... 4 Appliances Supported... 4 Microsoft IIS Software Versions
Microsoft Internet Information Services (IIS) Deployment Guide v1.2.9 Copyright 2013 Loadbalancer.org, Inc. 1 Table of Contents About this Guide... 4 Appliances Supported... 4 Microsoft IIS Software Versions
CYAN Secure Web Microsoft ISA Server Deployment Guide
 February 2010 Applies to: CYAN Secure Web 1.7.18 and above Table of Contents 1 Introduction...2 2 Prerequisites...3 3 Deployment scenarios...4 3.1 Variant 1: CYAN Secure Web is downstream proxy...4 3.2
February 2010 Applies to: CYAN Secure Web 1.7.18 and above Table of Contents 1 Introduction...2 2 Prerequisites...3 3 Deployment scenarios...4 3.1 Variant 1: CYAN Secure Web is downstream proxy...4 3.2
MassTransit 6.0 Enterprise Web Configuration for Macintosh OS 10.5 Server
 MassTransit 6.0 Enterprise Web Configuration for Macintosh OS 10.5 Server November 6, 2008 Group Logic, Inc. 1100 North Glebe Road, Suite 800 Arlington, VA 22201 Phone: 703-528-1555 Fax: 703-528-3296 E-mail:
MassTransit 6.0 Enterprise Web Configuration for Macintosh OS 10.5 Server November 6, 2008 Group Logic, Inc. 1100 North Glebe Road, Suite 800 Arlington, VA 22201 Phone: 703-528-1555 Fax: 703-528-3296 E-mail:
CLEARSWIFT SECURE Web Gateway HTTPS/SSL decryption
 CLEARSWIFT SECURE Web Gateway HTTPS/SSL decryption Introduction This Technical FAQ explains the functionality of the optional HTTPS/SSL scanning and inspection module available for the Web Gateway and
CLEARSWIFT SECURE Web Gateway HTTPS/SSL decryption Introduction This Technical FAQ explains the functionality of the optional HTTPS/SSL scanning and inspection module available for the Web Gateway and
Deployment Guide May-2015 rev. a. APV Oracle PeopleSoft Enterprise 9 Deployment Guide
 Deployment Guide May-2015 rev. a APV Oracle PeopleSoft Enterprise 9 Deployment Guide 1 Introduction... 3 2 Prerequisites and Assumptions... 4 2.1 Oracle PeopleSoft Enterprise... 4 2.2 Array Networks APV
Deployment Guide May-2015 rev. a APV Oracle PeopleSoft Enterprise 9 Deployment Guide 1 Introduction... 3 2 Prerequisites and Assumptions... 4 2.1 Oracle PeopleSoft Enterprise... 4 2.2 Array Networks APV
Enable SSL in Go2Group SOAP Server
 Enable SSL in Go2Group SOAP Server To enable SSL in Go2Group SOAP service, there are 7 major points you have to follow: I. Install JDK 1.5 or above. (Step 1) II. Use keytool utility to generate RSA key
Enable SSL in Go2Group SOAP Server To enable SSL in Go2Group SOAP service, there are 7 major points you have to follow: I. Install JDK 1.5 or above. (Step 1) II. Use keytool utility to generate RSA key
Install an SSL Certificate onto SilverStream. Sender Recipient Attached FIles Pages Date. Development Internal/External None 5 6/16/08
 Technical Note Sender Recipient Attached FIles Pages Date Development Internal/External None 5 6/16/08 This technical note explains how to generate a Certificate Signing Request (CSR) and install an SSL
Technical Note Sender Recipient Attached FIles Pages Date Development Internal/External None 5 6/16/08 This technical note explains how to generate a Certificate Signing Request (CSR) and install an SSL
Reverse Proxy with SSL - ProxySG Technical Brief
 SGOS 5 Series Reverse Proxy with SSL - ProxySG Technical Brief What is Reverse Proxy with SSL? The Blue Coat ProxySG includes the functionality for a robust and flexible reverse proxy solution. In addition
SGOS 5 Series Reverse Proxy with SSL - ProxySG Technical Brief What is Reverse Proxy with SSL? The Blue Coat ProxySG includes the functionality for a robust and flexible reverse proxy solution. In addition
Deploying the BIG-IP System with Oracle E-Business Suite 11i
 Deploying the BIG-IP System with Oracle E-Business Suite 11i Introducing the BIG-IP and Oracle 11i configuration Configuring the BIG-IP system for deployment with Oracle 11i Configuring the BIG-IP system
Deploying the BIG-IP System with Oracle E-Business Suite 11i Introducing the BIG-IP and Oracle 11i configuration Configuring the BIG-IP system for deployment with Oracle 11i Configuring the BIG-IP system
CYAN SECURE WEB HOWTO. NTLM Authentication
 CYAN SECURE WEB HOWTO June 2008 Applies to: CYAN Secure Web 1.4 and above NTLM helps to transparently synchronize user names and passwords of an Active Directory Domain and use them for authentication.
CYAN SECURE WEB HOWTO June 2008 Applies to: CYAN Secure Web 1.4 and above NTLM helps to transparently synchronize user names and passwords of an Active Directory Domain and use them for authentication.
DEPLOYMENT GUIDE Version 1.0. Deploying the BIG-IP LTM with the Zimbra Open Source Email and Collaboration Suite
 DEPLOYMENT GUIDE Version 1.0 Deploying the BIG-IP LTM with the Zimbra Open Source Email and Collaboration Suite Table of Contents Table of Contents Deploying the BIG-IP LTM with the Zimbra Open Source
DEPLOYMENT GUIDE Version 1.0 Deploying the BIG-IP LTM with the Zimbra Open Source Email and Collaboration Suite Table of Contents Table of Contents Deploying the BIG-IP LTM with the Zimbra Open Source
DEPLOYMENT GUIDE Version 1.2. Deploying F5 with Microsoft Exchange Server 2007
 DEPLOYMENT GUIDE Version 1.2 Deploying F5 with Microsoft Exchange Server 2007 Table of Contents Table of Contents Deploying F5 devices with Microsoft Exchange Server 2007 Client Access Servers Prerequisites
DEPLOYMENT GUIDE Version 1.2 Deploying F5 with Microsoft Exchange Server 2007 Table of Contents Table of Contents Deploying F5 devices with Microsoft Exchange Server 2007 Client Access Servers Prerequisites
Load Balancing VMware Horizon View. Deployment Guide
 Load Balancing VMware Horizon View Deployment Guide v1.1.0 Copyright 2014 Loadbalancer.org, Inc. 1 Table of Contents About this Guide... 4 Appliances Supported... 4 VMware Horizon View Versions Supported...4
Load Balancing VMware Horizon View Deployment Guide v1.1.0 Copyright 2014 Loadbalancer.org, Inc. 1 Table of Contents About this Guide... 4 Appliances Supported... 4 VMware Horizon View Versions Supported...4
Load Balancing Microsoft Terminal Services. Deployment Guide
 Load Balancing Microsoft Terminal Services Deployment Guide rev. 1.5.7 Copyright 2002 2016 Loadbalancer.org, Inc. 1 Table of Contents About this Guide... 4 Loadbalancer.org Appliances Supported... 4 Loadbalancer.org
Load Balancing Microsoft Terminal Services Deployment Guide rev. 1.5.7 Copyright 2002 2016 Loadbalancer.org, Inc. 1 Table of Contents About this Guide... 4 Loadbalancer.org Appliances Supported... 4 Loadbalancer.org
Load Balancing McAfee Web Gateway. Deployment Guide
 Load Balancing McAfee Web Gateway Deployment Guide rev. 1.1.4 Copyright 2015 Loadbalancer.org, Inc. 1 Table of Contents About this Guide... 3 Loadbalancer.org Appliances Supported...3 Loadbalancer.org
Load Balancing McAfee Web Gateway Deployment Guide rev. 1.1.4 Copyright 2015 Loadbalancer.org, Inc. 1 Table of Contents About this Guide... 3 Loadbalancer.org Appliances Supported...3 Loadbalancer.org
Installing Dspace 1.8 on Ubuntu 12.04
 Installing Dspace 1.8 on Ubuntu 12.04 This is an abridged version of the dspace 1.8 installation guide, specifically targeted at getting a basic server running from scratch using Ubuntu. More information
Installing Dspace 1.8 on Ubuntu 12.04 This is an abridged version of the dspace 1.8 installation guide, specifically targeted at getting a basic server running from scratch using Ubuntu. More information
Rapid Access Cloud: Se1ng up a Proxy Host
 Rapid Access Cloud: Se1ng up a Proxy Host Rapid Access Cloud: Se1ng up a Proxy Host Prerequisites Set up security groups The Proxy Security Group The Internal Security Group Launch your internal instances
Rapid Access Cloud: Se1ng up a Proxy Host Rapid Access Cloud: Se1ng up a Proxy Host Prerequisites Set up security groups The Proxy Security Group The Internal Security Group Launch your internal instances
Generating and Installing SSL Certificates on the Cisco ISA500
 Application Note Generating and Installing SSL Certificates on the Cisco ISA500 This application note describes how to generate and install SSL certificates on the Cisco ISA500 security appliance. It includes
Application Note Generating and Installing SSL Certificates on the Cisco ISA500 This application note describes how to generate and install SSL certificates on the Cisco ISA500 security appliance. It includes
Unifying Information Security. Implementing TLS on the CLEARSWIFT SECURE Email Gateway
 Unifying Information Security Implementing TLS on the CLEARSWIFT SECURE Email Gateway Contents 1 Introduction... 3 2 Understanding TLS... 4 3 Clearswift s Application of TLS... 5 3.1 Opportunistic TLS...
Unifying Information Security Implementing TLS on the CLEARSWIFT SECURE Email Gateway Contents 1 Introduction... 3 2 Understanding TLS... 4 3 Clearswift s Application of TLS... 5 3.1 Opportunistic TLS...
Collax Web Security. Howto. This howto describes the setup of a Web proxy server as Web content filter.
 Collax Web Security Howto This howto describes the setup of a Web proxy server as Web content filter. Requirements Collax Business Server Collax Security Gateway Collax Platform Server including Collax
Collax Web Security Howto This howto describes the setup of a Web proxy server as Web content filter. Requirements Collax Business Server Collax Security Gateway Collax Platform Server including Collax
App Orchestration 2.5
 App Orchestration 2.5 Configuring SSL for App Orchestration 2.5 Prepared by: Andy Zhu Last Updated: July 25, 2014 Contents Introduction... 3 Configure SSL on the App Orchestration configuration server...
App Orchestration 2.5 Configuring SSL for App Orchestration 2.5 Prepared by: Andy Zhu Last Updated: July 25, 2014 Contents Introduction... 3 Configure SSL on the App Orchestration configuration server...
RSA Security Analytics
 RSA Security Analytics Event Source Log Configuration Guide Microsoft Windows using Eventing Collection Last Modified: Thursday, July 30, 2015 Event Source Product Information: Vendor: Microsoft Event
RSA Security Analytics Event Source Log Configuration Guide Microsoft Windows using Eventing Collection Last Modified: Thursday, July 30, 2015 Event Source Product Information: Vendor: Microsoft Event
ClusterLoad ESX Virtual Appliance quick start guide v6.3
 ClusterLoad ESX Virtual Appliance quick start guide v6.3 ClusterLoad terminology...2 What are your objectives?...3 What is the difference between a one-arm and a two-arm configuration?...3 What are the
ClusterLoad ESX Virtual Appliance quick start guide v6.3 ClusterLoad terminology...2 What are your objectives?...3 What is the difference between a one-arm and a two-arm configuration?...3 What are the
Load Balancing Oracle Application Server (Oracle HTTP Server) Quick Reference Guide
 Load Balancing Oracle Application Server (Oracle HTTP Server) Quick Reference Guide v1.1.0 Oracle HTTP Server Ports By default Oracle HTTP Server listens on HTTP port 7777 and HTTPS is disabled. When HTTPS
Load Balancing Oracle Application Server (Oracle HTTP Server) Quick Reference Guide v1.1.0 Oracle HTTP Server Ports By default Oracle HTTP Server listens on HTTP port 7777 and HTTPS is disabled. When HTTPS
Managing the SSL Certificate for the ESRS HTTPS Listener Service Technical Notes P/N 300-011-843 REV A01 January 14, 2011
 Managing the SSL Certificate for the ESRS HTTPS Listener Service Technical Notes P/N 300-011-843 REV A01 January 14, 2011 This document contains information on these topics: Introduction... 2 Terminology...
Managing the SSL Certificate for the ESRS HTTPS Listener Service Technical Notes P/N 300-011-843 REV A01 January 14, 2011 This document contains information on these topics: Introduction... 2 Terminology...
Pexip Infinity Reverse Proxy Deployment Guide
 Pexip Infinity Reverse Proxy Deployment Guide Introduction About the Pexip App and reverse proxies The Pexip App for mobile devices such as ios phones and tablets enables conference participants to extend
Pexip Infinity Reverse Proxy Deployment Guide Introduction About the Pexip App and reverse proxies The Pexip App for mobile devices such as ios phones and tablets enables conference participants to extend
Enable SSL for Apollo 2015
 Enable SSL for Apollo 2015 [1] Obtain proper SSL certificate *.pfx (contains both certificate and private keys) For example, the pfx file contains both certificate and private keys, also the ascii file
Enable SSL for Apollo 2015 [1] Obtain proper SSL certificate *.pfx (contains both certificate and private keys) For example, the pfx file contains both certificate and private keys, also the ascii file
Deploying the BIG-IP System with Microsoft IIS
 Deploying the BIG-IP System with Welcome to the F5 deployment guide for Microsoft Internet Information Services (IIS). This document contains guidance on configuring the BIG-IP system version 11.4 and
Deploying the BIG-IP System with Welcome to the F5 deployment guide for Microsoft Internet Information Services (IIS). This document contains guidance on configuring the BIG-IP system version 11.4 and
Volume SYSLOG JUNCTION. User s Guide. User s Guide
 Volume 1 SYSLOG JUNCTION User s Guide User s Guide SYSLOG JUNCTION USER S GUIDE Introduction I n simple terms, Syslog junction is a log viewer with graphing capabilities. It can receive syslog messages
Volume 1 SYSLOG JUNCTION User s Guide User s Guide SYSLOG JUNCTION USER S GUIDE Introduction I n simple terms, Syslog junction is a log viewer with graphing capabilities. It can receive syslog messages
Reverse Proxy Guide. Version 2.0 April 2016
 Version 2.0 April 2016 Reverse Proxy Guide Copyright 2016 iwebgate. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated
Version 2.0 April 2016 Reverse Proxy Guide Copyright 2016 iwebgate. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated
Deploying F5 for Microsoft Office Web Apps Server 2013
 Deploying F5 for Microsoft Office Web Apps Server 2013 Welcome to the F5 - Microsoft Office Web Apps Server deployment guide. This document contains guidance on configuring the BIG-IP Local Traffic Manager
Deploying F5 for Microsoft Office Web Apps Server 2013 Welcome to the F5 - Microsoft Office Web Apps Server deployment guide. This document contains guidance on configuring the BIG-IP Local Traffic Manager
Installing and Configuring vcenter Multi-Hypervisor Manager
 Installing and Configuring vcenter Multi-Hypervisor Manager vcenter Server 5.1 vcenter Multi-Hypervisor Manager 1.1 This document supports the version of each product listed and supports all subsequent
Installing and Configuring vcenter Multi-Hypervisor Manager vcenter Server 5.1 vcenter Multi-Hypervisor Manager 1.1 This document supports the version of each product listed and supports all subsequent
How to configure HTTPS proxying in Zorp 6
 How to configure HTTPS proxying in Zorp 6 April 17, 2015 Abstract This tutorial describes how to configure Zorp to proxy HTTPS traffic Copyright 1996-2015 BalaBit IT Security Ltd. Table of Contents 1.
How to configure HTTPS proxying in Zorp 6 April 17, 2015 Abstract This tutorial describes how to configure Zorp to proxy HTTPS traffic Copyright 1996-2015 BalaBit IT Security Ltd. Table of Contents 1.
Configuring Security Features of Session Recording
 Configuring Security Features of Session Recording Summary This article provides information about the security features of Citrix Session Recording and outlines the process of configuring Session Recording
Configuring Security Features of Session Recording Summary This article provides information about the security features of Citrix Session Recording and outlines the process of configuring Session Recording
DEPLOYMENT GUIDE Version 1.2. Deploying the BIG-IP system v10 with Microsoft Exchange Outlook Web Access 2007
 DEPLOYMENT GUIDE Version 1.2 Deploying the BIG-IP system v10 with Microsoft Exchange Outlook Web Access 2007 Table of Contents Table of Contents Deploying the BIG-IP system v10 with Microsoft Outlook Web
DEPLOYMENT GUIDE Version 1.2 Deploying the BIG-IP system v10 with Microsoft Exchange Outlook Web Access 2007 Table of Contents Table of Contents Deploying the BIG-IP system v10 with Microsoft Outlook Web
1. If there is a temporary SSL certificate in your /ServerRoot/ssl/certs/ directory, move or delete it. 2. Run the following command:
 C2Net Stronghold Cisco Adaptive Security Appliance (ASA) 5500 Cobalt RaQ4/XTR F5 BIG IP (version 9) F5 BIG IP (pre-version 9) F5 FirePass VPS HSphere Web Server IBM HTTP Server Java-based web server (generic)
C2Net Stronghold Cisco Adaptive Security Appliance (ASA) 5500 Cobalt RaQ4/XTR F5 BIG IP (version 9) F5 BIG IP (pre-version 9) F5 FirePass VPS HSphere Web Server IBM HTTP Server Java-based web server (generic)
Microsoft Exchange Server
 Deployment Guide Document Version: 4.9.2 Deploying the BIG-IP System v10 with Microsoft Welcome to the F5 and Microsoft Exchange 2010 deployment guide. This document contains guidance on configuring the
Deployment Guide Document Version: 4.9.2 Deploying the BIG-IP System v10 with Microsoft Welcome to the F5 and Microsoft Exchange 2010 deployment guide. This document contains guidance on configuring the
Microsoft Lync Server Overview
 Organizations can use the to enhance the scalability and availability of their Microsoft Lync Server 2010 deployments (formerly known as Microsoft Office Communications Server). Barracuda Networks has
Organizations can use the to enhance the scalability and availability of their Microsoft Lync Server 2010 deployments (formerly known as Microsoft Office Communications Server). Barracuda Networks has
Create a virtual machine at your assigned virtual server. Use the following specs
 CIS Networking Installing Ubuntu Server on Windows hyper-v Much of this information was stolen from http://www.isummation.com/blog/installing-ubuntu-server-1104-64bit-on-hyper-v/ Create a virtual machine
CIS Networking Installing Ubuntu Server on Windows hyper-v Much of this information was stolen from http://www.isummation.com/blog/installing-ubuntu-server-1104-64bit-on-hyper-v/ Create a virtual machine
GRAVITYZONE HERE. Deployment Guide VLE Environment
 GRAVITYZONE HERE Deployment Guide VLE Environment LEGAL NOTICE All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means, electronic or mechanical, including
GRAVITYZONE HERE Deployment Guide VLE Environment LEGAL NOTICE All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means, electronic or mechanical, including
Deploying the Barracuda Load Balancer with Office Communications Server 2007 R2. Office Communications Server Overview.
 Deploying the Barracuda Load Balancer with Office Communications Server 2007 R2 Organizations can use the Barracuda Load Balancer to enhance the scalability and availability of their Microsoft Office Communications
Deploying the Barracuda Load Balancer with Office Communications Server 2007 R2 Organizations can use the Barracuda Load Balancer to enhance the scalability and availability of their Microsoft Office Communications
SolarWinds Technical Reference
 SolarWinds Technical Reference Using SSL Certificates in Web Help Desk Introduction... 1 How WHD Uses SSL... 1 Setting WHD to use HTTPS... 1 Enabling HTTPS and Initializing the Java Keystore... 1 Keys
SolarWinds Technical Reference Using SSL Certificates in Web Help Desk Introduction... 1 How WHD Uses SSL... 1 Setting WHD to use HTTPS... 1 Enabling HTTPS and Initializing the Java Keystore... 1 Keys
Deployment Guide Microsoft IIS 7.0
 Deployment Guide Microsoft IIS 7.0 DG_IIS_022012.1 TABLE OF CONTENTS 1 Introduction... 4 2 Deployment Guide Overview... 4 3 Deployment Guide Prerequisites... 4 4 Accessing the AX Series Load Balancer...
Deployment Guide Microsoft IIS 7.0 DG_IIS_022012.1 TABLE OF CONTENTS 1 Introduction... 4 2 Deployment Guide Overview... 4 3 Deployment Guide Prerequisites... 4 4 Accessing the AX Series Load Balancer...
AlienVault Unified Security Management (USM) 4.x-5.x. Deploying HIDS Agents to Linux Hosts
 AlienVault Unified Security Management (USM) 4.x-5.x Deploying HIDS Agents to Linux Hosts USM 4.x-5.x Deploying HIDS Agents to Linux Hosts, rev. 2 Copyright 2015 AlienVault, Inc. All rights reserved. AlienVault,
AlienVault Unified Security Management (USM) 4.x-5.x Deploying HIDS Agents to Linux Hosts USM 4.x-5.x Deploying HIDS Agents to Linux Hosts, rev. 2 Copyright 2015 AlienVault, Inc. All rights reserved. AlienVault,
Setup Corporate (Microsoft Exchange) Email. This tutorial will walk you through the steps of setting up your corporate email account.
 Setup Corporate (Microsoft Exchange) Email This tutorial will walk you through the steps of setting up your corporate email account. Microsoft Exchange Email Support Exchange Server Information You will
Setup Corporate (Microsoft Exchange) Email This tutorial will walk you through the steps of setting up your corporate email account. Microsoft Exchange Email Support Exchange Server Information You will
Deploying the BIG-IP LTM and APM with Citrix XenApp or XenDesktop
 Deployment Guide Deploying the BIG-IP LTM and APM with Citrix XenApp or XenDesktop Welcome to the F5 deployment guide for Citrix VDI applications, including XenApp and XenDesktop with the BIG-IP v11.2
Deployment Guide Deploying the BIG-IP LTM and APM with Citrix XenApp or XenDesktop Welcome to the F5 deployment guide for Citrix VDI applications, including XenApp and XenDesktop with the BIG-IP v11.2
BASICS OF SCALING: LOAD BALANCERS
 BASICS OF SCALING: LOAD BALANCERS Lately, I ve been doing a lot of work on systems that require a high degree of scalability to handle large traffic spikes. This has led to a lot of questions from friends
BASICS OF SCALING: LOAD BALANCERS Lately, I ve been doing a lot of work on systems that require a high degree of scalability to handle large traffic spikes. This has led to a lot of questions from friends
SSL Tunnels. Introduction
 SSL Tunnels Introduction As you probably know, SSL protects data communications by encrypting all data exchanged between a client and a server using cryptographic algorithms. This makes it very difficult,
SSL Tunnels Introduction As you probably know, SSL protects data communications by encrypting all data exchanged between a client and a server using cryptographic algorithms. This makes it very difficult,
SECURE Web Gateway. HTTPS/SSL Technical FAQ. Version 1.1. Date 04/10/12
 SECURE Web Gateway HTTPS/SSL Technical FAQ Version 1.1 Date 04/10/12 Introduction This Technical FAQ explains the operation of the HTTPS/SSL scanning and how it is deployed. How does the SECURE Web Gateway
SECURE Web Gateway HTTPS/SSL Technical FAQ Version 1.1 Date 04/10/12 Introduction This Technical FAQ explains the operation of the HTTPS/SSL scanning and how it is deployed. How does the SECURE Web Gateway
Appliance Quick Start Guide. v7.6
 Appliance Quick Start Guide v7.6 rev. 1.0.7 Copyright 2002 2015 Loadbalancer.org, Inc. Table of Contents Loadbalancer.org Terminology... 4 What is a Virtual IP Address?... 5 What is a Floating IP Address?...
Appliance Quick Start Guide v7.6 rev. 1.0.7 Copyright 2002 2015 Loadbalancer.org, Inc. Table of Contents Loadbalancer.org Terminology... 4 What is a Virtual IP Address?... 5 What is a Floating IP Address?...
Setting Up SSL on IIS6 for MEGA Advisor
 Setting Up SSL on IIS6 for MEGA Advisor Revised: July 5, 2012 Created: February 1, 2008 Author: Melinda BODROGI CONTENTS Contents... 2 Principle... 3 Requirements... 4 Install the certification authority
Setting Up SSL on IIS6 for MEGA Advisor Revised: July 5, 2012 Created: February 1, 2008 Author: Melinda BODROGI CONTENTS Contents... 2 Principle... 3 Requirements... 4 Install the certification authority
Ulteo Open Virtual Desktop Installation
 Ulteo Open Virtual Desktop Installation Copyright 2008 Ulteo SAS - CONTENTS CONTENTS Contents 1 Prerequisites 2 1.1 Installation of MySQL....................................... 2 2 Session Manager (sm.ulteo.com)
Ulteo Open Virtual Desktop Installation Copyright 2008 Ulteo SAS - CONTENTS CONTENTS Contents 1 Prerequisites 2 1.1 Installation of MySQL....................................... 2 2 Session Manager (sm.ulteo.com)
Host your websites. The process to host a single website is different from having multiple sites.
 The following guide will help you to setup the hosts, in case you want to run multiple websites on your VPS. This is similar to setting up a shared server that hosts multiple websites, using a single shared
The following guide will help you to setup the hosts, in case you want to run multiple websites on your VPS. This is similar to setting up a shared server that hosts multiple websites, using a single shared
Installation Procedure SSL Certificates in IIS 7
 Installation Procedure SSL Certificates in IIS 7 This document will explain the creation and installation procedures for enabling an IIS website to use Secure Socket Layer (SSL). Check IIS for existing
Installation Procedure SSL Certificates in IIS 7 This document will explain the creation and installation procedures for enabling an IIS website to use Secure Socket Layer (SSL). Check IIS for existing
