Penetration Testing LAB Setup Guide
|
|
|
- Cori Berry
- 8 years ago
- Views:
Transcription
1 Penetration Testing LAB Setup Guide (External Attacker - Intermediate) By: magikh0e - magikh0e@ihtb.org Last Edit: July This guide assumes a few things You have read the basic guide of this lab setup. 2. You like breaking more shit or need to test out some auditing tools. 1
2 Contents Getting Started... 3 Why setup a LAB?... 3 LAB Setup... 4 LAB Setup Creating Virtual Box Instances... 5 Debian LAB Setup Network Setup & Reconfiguration... 6 PfSense... 6 Debian Reconfiguring BackTrack LAB Setup Virtual and Vulnerable Machines Metasploitable 2 Attack of the clones Virtual Lab Layout & Diagrams Virtual Box Layout Virtual Network Diagram Conclusion
3 Getting Started It s simple. Go through the router, over the firewall. There is where you will find grandma s house Good luck! After setting up this LAB environment, you will have the ability to exploit issues from the following categories: 1. You will figure it out Why setup a LAB? If you have made it this far, I am sure you now understand this. If not, go back to the Basic guide =) 3
4 LAB Setup Prerequisites Make sure you have read the basic version of this guide. A lot of the following setup will assume a basic lab has already been created. For the intermediate penetration testing lab setup, you will be using the following. -LAB Setup from the Basic Guide Debian 6: IMPORTANT NOTE In order to follow this guide, you must have already created the basic penetration testing LAB setup. If not, read the basic guide first before continuing: To keep things neat and tidy, create a folder somewhere to place all the above files in. The inside of this folder create a VirtualMachines folder. Here you can store the extracted images, as well as virtual disk you will be creating for BackTrack and PfSense installs. You will obviously need a pretty beefy machine in order to run all of the above machines virtually. At a bare minimal, only the following are required to be running. If you follow the exact guide, you will need at least 4.5GB ram minimum to allocate to all instances. 1. PfSense 2. BackTrack 3. Metasploitable Metasploitable Debian 6 LAB System Requirements 4.5GB of system ram for allocation to Virtual Instances GB hard drive space 17.4 GB without keeping archives and ISO files. 4
5 LAB Setup Creating Virtual Box Instances Debian 6 1. Create a new machine in Virtual Box for Debian 6. Operating System: Debian OS Type: Debian Memory: 512 Startup Disk: GB a. When creating the instance for Debian 6, you will need a minimal of 512mb of ram and a minimal of 12GB hard drive space for the instance. b. Edit the Network Interface of Adapter 1 to match the following settings. While in the configuration, write down the instances MAC Address. Attached to: Internal Network Name: LAN Promiscuous Mode: Allow VMs MAC Address: c. Once the instance has been created, start the instance and then proceed to install Debian 6 to the virtual disk that has just been created. 5
6 LAB Setup Network Setup & Reconfiguration PfSense Resetting Back to Factory Defaults 1. At the PfSense console, Type 4 to proceed with a factory reset. Type y when asked if you wish to proceed with the reset. a. Once the reset is complete and a reboot has been performed, you will be asked to setup VLANs. Type n. b. Once at the Enter the WAN interface prompt type the WLAN1 interface. Type in le0, and then press Enter c. You will now be prompted to specify the LAN interface. Type in le1, and then press Enter. d. To continue press Enter again and then y when prompted to continue. e. PfSense should now be installed. Initial Setup & Configuration 1. Once PfSense has been reset to defaults, you will need to set the IP Address of the LAN interface. a. From the PfSense console select option 2 'Set interface(s) IP address'. b. At the Enter the number of the interface you wish to configure: prompt, type 2 to choose the LAN interface. c. When prompted, use the following IP Address for the LAN interface: d. Use 24 at the LAN IPv4 subnet bit count prompt. e. Type y at the prompt when asked if you would like to enable the DHCP server on LAN. f. When asked to provide the starting address range, use the following starting IP Address: g. You will then be asked to specify the ending IP Address for the DHCP range. Use the following IP Address: h. Type y if asked to enable web configuration. At this point PfSense should be handing out addresses within: range. To confirm, reboot the BackTrack instance and verify that it now has an address within the range specified above. 6
7 Accessing PfSense Interface Now that PfSense has been restored to a default state, and confirmed to be handing out DHCP addresses properly. You can now begin reconfiguring PfSense for the intermediate labs by accessing it via the web interface from the BackTrack machine using Firefox. To access the PfSense web interface, open the following URL in Firefox: The default username is: admin and the default password is: pfsense. Login to the web interface and follow the prompts through the guided wizard to complete installation. Nothing needs to be changed at this point, other than verifying the settings you have specified earlier, set a new password and click on the reload button. NOTE: The Firefox that comes with BackTrack is bundled with noscript, so by default it will block some functionality from the PfSense website. Once you see Congratulations! PfSense is now configured. The configuration has been completed. Click on Click here to continue on to pfsense webconfigurator. this will reload the web interface to get to the main configuration view. Required Packages A few packages are required to be installed for the intermediate LAB setup. If you have already done the optional parts from the beginner guide, you can skip this part. Proxy Server with mod_security - ModSecurity is a web application firewall that can work either embedded or as a reverse proxy. It provides protection from a range of attacks against web applications and allows for HTTP traffic monitoring, logging and real-time analysis. In addition this package allows URL forwarding which can be convenient for hosting multiple websites behind pfsense using 1 IP address. Snort - Snort is an open source network intrusion prevention and detection system (IDS/IPS). Combining the benefits of signature, protocol, and anomaly-based inspection. 1. From the PfSense interface, go to System->Packages. Then Install Proxy Server with mod_security by clicking the + icon next to the listing. 2. Once installed, go back to System->Packages. Then install snort. 7
8 Optional Packages Depending on your purpose for building this LAB, you may also find the following packages useful. Arpwatch - Arpwatch monitors Ethernet/ip address pairings. It also logs certain changes to syslog. Dashboard Widget: Snort - Dashboard widget for Snort. Nmap d0h ntop - ntop is a network probe that shows network usage in a way similar to what top does for processes. System Patches - A package to apply and maintain custom system patches. NOTE: If you are unable to get a list of Available Packages on the PfSense box, check and make sure that the WAN interface on your PfSense instance is receiving an IP address from your local DHCP server. DHCP Setup You can now make use of the MAC Addresses you have taken note off earlier when creating the vulnerable lab machines in the basic guide and intermediate guide. You will need the MAC address from the following instances: Metasploitable2-1, Metasploitable2-2, and Debian 6 Static Reservations 1. Open up the PfSense web interface. Then go to Services->DHCP Server selecting the LAN tab. a. Verify that the range specified is the same range specified you have specified earlier in this guide during the PfSense setup. NOTE: This part seems to have a bug in that the range is usually not what was specified on the console. If you do not fix the range, you will get errors when attempting to create the reservations. If the ranges are not what were specified, correct them and apply the settings before proceeding with the next step. 2. Scroll to the bottom and add a new Static Reservation for the Metasploitable 2-1, Metasploitable2-2 and Debian 6 instances. Metasploitable2-1: MAC Address: IP Address: Hostname: metasploitable2-1 Description: metasploitable2-1 Metasploitable2-2: MAC Address: IP Address: Hostname: Metasploitable2-2 Description: Metasploitable2-2 Debian 6: MAC Address: IP Address: Hostname: Debian 6 Description: Debian 6 3. Once the above reservations have been created, you can now save & apply the settings to PfSense. 8
9 4. Verify the DHCP reservation by restarting each of the vulnerable instances. To simplify the setup, you can edit the /etc/hosts file on the BackTrack machine, adding the following entries: box box debian 9
10 Firewall Configuration NAT and Virtual IPs To mimic a real world environment, we will be using network address translation on the firewall into the LAB. The intermediate lab is designed to be from an external attacker s view, unlike the basic guide where the attacker had internal access into the network already. Here you will not find as many entry points changing the playing field and required skill levels. Our simulated WAN network will live on the /24 subnet. You will need to create two 1:1 NATs as well as two Virtual IP Addresses. 1. Go to Firewall->NAT then select the 1:1 tab. Then click on the + icon to add a new NAT entry. 2. Add the following two entries then save & apply the changes. a. External subnet IP: Internal IP: b. External subnet IP: Internal IP: PfSense will not automatically create proxy arps for 1:1 or static NATs. This is where the virtual IPs will come in handy. 1. Go to Firewall->Virtual IPs, add a new virtual IP by clicking the + icon. 2. Add the following two entries then save & apply the changes. a. Type: Proxy ARP IP Address(es): b. Type: Proxy ARP IP Address(es): c. Type: Proxy ARP IP Address(es):
11 Once all the NATs and Virtual IPs have been created, you can now go on to create some firewall rules. To mimic real world examples as close as possible, only a bare minimal amounts of ports will be opened to the outside world. In this guide we will only be allowing: DNS, FTP, HTTP, HTTPS, SSH and SMTP. You can always adapt these rules to allow them to be more restrictive or loose. By default only two rules should currently be define. We will now add some rules by doing the following. 11
12 Adding new firewall rules to PfSense is simple. 1. Go to Firewall->Virtual IPs, add a new rule to the bottom by clicking the + icon. 2. Once in the Firewall: Rules: Edit menu. Create rules to match each of the following. Save and apply the rules once complete. a. Action: Pass Destination: Type: Single host or alias Destination: Destination port range: from: HTTP to: HTTP b. Action: Pass Destination: Type: Single host or alias Destination: Destination port range: from: HTTPS to: HTTPS c. Action: Pass Destination: Type: Single host or alias Destination: Destination port range: from: FTP to: FTP d. Action: Pass Destination: Type: Single host or alias Destination: Destination port range: from: SSH to: SSH e. Action: Pass Protocol: TCP/UDP Destination: Type: Single host or alias Destination: Destination port range: from: DNS to: DNS f. Action: Pass Destination: Type: Single host or alias Destination: Destination port range: from: SMTP to: SMTP 12
13 Once you have installed all the packages you wish to use and configured the appropriate firewall rules. It is off to grandma s house you go. But before you do that, now would be a good time to close down the LAB network from the outside world. 1. From the PfSense console select option 2 'Set interface(s) IP address'. 2. At the Enter the number of the interface you wish to configure prompt, type 1 to choose the WAN interface. 3. Type n when asked Configure WAN interface via DHCP. 4. When prompted, use the following IP Address for the WAN interface: Use 24 at the LAN IPv4 subnet bit count prompt. 6. Type y if asked to enable web configuration. 7. From the VBox Manager interface, Edit the settings of the PfSense instance and change the Network Settings for Adapter 1. a. Change the existing settings to match the following then click OK. Attached to: Internal network Name: WAN 8. From the PfSense console, Type 5 to reboot the instance. 13
14 Debian 6 The Debian 6 instance will be serving as the HTTP load balancer serving request for Metasploitable2-1 and Metasploitable2-2. When installing Debian 6, I used the netinst ISO and performed a standard system install, excluding everything else. If you wish, you can install the graphical environment here. This will give the ability to manage the PfSense firewall from the Debian 6 instance. Once the LAB network has been locked down, only machines living on the /24 network will have access to PfSense configuration interface. To get Debian 6 ready to rock, you will first need to install and configure some new packages. 1. Login to the Debian 6 instance and install haproxy by issuing the following command: apt-get install haproxy 2. Once haproxy has been installed, edit the file: /etc/haproxy/haproxy.cfg, configure this file to match the haproxy.cfg example on page 15. The save and close the file. 3. After editing the file, start up HA Proxy by issuing the following command on the Debian 6 instance. sudo haproxy -f /etc/haproxy/haproxy.conf NOTE: See page 15 for configuration example. HA Proxy should now up and running, though it will not work just yet. You will still need to bring up the two Metasploitable instances before testing this service. 14
15 Penetration Testing LAB - HA Proxy Configuration Example global defaults log local0 log local1 notice maxconn 4096 user haproxy group haproxy daemon log global mode http option httplog option dontlognull retries 3 option redispatch maxconn 2000 contimeout 5000 clitimeout srvtimeout listen PentestLABBalancer :80 mode http cookie PentestLABBalancer balance source option httpclose option forwardfor stats enable stats auth ihtb:ihtb server web_ cookie PentestLABBalancerA check server web_ cookie PentestLABBalancerB check 15
16 Reconfiguring BackTrack The reconfiguration of BackTrack for the intermediate lab does not require many changes. The first being changing BackTracks network settings in VBox Manager. 1. From the VBox Manager interface, Edit the settings of the BackTrack instance and change the Network Settings for Adapter 1. a. Change the existing settings to match the following then click OK. Attached to: Internal network Name: WAN 2. Reboot BackTrack, then log back in. Before running startx issue the following commands in order to get BackTrack talking to the LAB WAN network on /24 ifconfig eth promisc route add default gw NOTE: BackTrack will not keep these settings, so if you reboot they will need to be applied again. 16
17 LAB Setup Virtual and Vulnerable Machines What is a penetration testing LAB without things to exploit? A boring networking lab ;) Metasploitable 2 Attack of the clones In the intermediate lab, we will be using some load balanced web servers, so we will need to add another web server. Seeing the metasploitable 2 instance already has a web server and vulnerable applications installed. We will just clone another Metasploitable 2 instance using the existing one. 1. Using the Metasploitable 2 instance created in the basic version of this guide, you will need to create a clone of the instance in VBox. IMPORTANT NOTE: Be sure to select the re-initialize MAC address option when cloning the instance. a. From the VBox Manager window, Right click on Metasploitable 2 instance, then go to Clone. Take note of the newly created MAC address of the clone, it will be required later. Under the Advanced menu, take note of the MAC address. You will need it later. You should now have two (2) Metasploitable 2 instances. Too simplify things, rename the original Metasploitable 2 to Metasploitable 2-1. Then rename the cloned copy of Metasploitable2-1 to be Metasploitable 2-2. Power on both instances, once they have both finished booting you can then test the HA Proxy setup from earlier. From the BackTrack instance, open the following URL using Firefox If everything went well, you should get 17
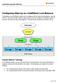
18 Virtual Lab Layout & Diagrams Virtual Box Layout 18
19 19
20 Virtual Network Diagram External Subnet: /24 Internal Subnet: /24 Firewall: Internal: External: BackTrack / Attacker: External: /32 Debian 6: Internal: External: Metasploitable2-1: Internal: External: Metasploitable2-2: Internal: External:
21 Conclusion Once everything has been started, you should now be ready to start testing out your skills in the newly created penetration testing LAB. Keep in mind this LAB has been designed with access from an external attacker s perspective. From the BackTrack machine you can now start exploring the /24 network. Have fun! If you have any questions or issues with the above instructions, please let me know. As this is an initial release, so expect some bugs or un-documented features to come up ;D As always, Hackers do it with all sorts of characters 21
22 Syntax Guide Below is a reference point for syntax and highlighting used throughout this guide. Information Denotes required information. command Reference to a system command, normally not required to be run by the user for the instructions unless stated otherwise. command Reference to a system command to be ran by the user as part of the instructions. Something: something Reference to an option in the GUI application. Action Denotes some action to be performed with the current GUI application. File name Specifies a file name. 22
Penetration Testing LAB Setup Guide
 Penetration Testing LAB Setup Guide (Internal Attacker - Beginner version) By: magikh0e - magikh0e@ihtb.org Last Edit: July 07 2012 This guide assumes a few things... 1. You have installed Backtrack before
Penetration Testing LAB Setup Guide (Internal Attacker - Beginner version) By: magikh0e - magikh0e@ihtb.org Last Edit: July 07 2012 This guide assumes a few things... 1. You have installed Backtrack before
Setting up pfsense as a Stateful Bridging Firewall.
 Setting up pfsense as a Stateful Bridging Firewall. Contents Contents Setting up pfsense as a Stateful Bridging Firewall.... 1 What king of system these directions will try and help you create.... 1 Selecting
Setting up pfsense as a Stateful Bridging Firewall. Contents Contents Setting up pfsense as a Stateful Bridging Firewall.... 1 What king of system these directions will try and help you create.... 1 Selecting
Configuring HAproxy as a SwiftStack Load Balancer
 Configuring HAproxy as a SwiftStack Load Balancer To illustrate how a SwiftStack cluster can be configured with an external load balancer, such as HAProxy, let s walk through a step-by-step example of
Configuring HAproxy as a SwiftStack Load Balancer To illustrate how a SwiftStack cluster can be configured with an external load balancer, such as HAProxy, let s walk through a step-by-step example of
PFSENSE Load Balance with Fail Over From Version Beta3
 PFSENSE Load Balance with Fail Over From Version Beta3 Following are the Installation instructions of PFSense beginning at first Login to setup Load Balance and Fail over procedures for outbound Internet
PFSENSE Load Balance with Fail Over From Version Beta3 Following are the Installation instructions of PFSense beginning at first Login to setup Load Balance and Fail over procedures for outbound Internet
F-Secure Messaging Security Gateway. Deployment Guide
 F-Secure Messaging Security Gateway Deployment Guide TOC F-Secure Messaging Security Gateway Contents Chapter 1: Deploying F-Secure Messaging Security Gateway...3 1.1 The typical product deployment model...4
F-Secure Messaging Security Gateway Deployment Guide TOC F-Secure Messaging Security Gateway Contents Chapter 1: Deploying F-Secure Messaging Security Gateway...3 1.1 The typical product deployment model...4
ISERink Installation Guide
 ISERink Installation Guide Version 1.1 January 27, 2015 First developed to support cyber defense competitions (CDCs), ISERink is a virtual laboratory environment that allows students an opportunity to
ISERink Installation Guide Version 1.1 January 27, 2015 First developed to support cyber defense competitions (CDCs), ISERink is a virtual laboratory environment that allows students an opportunity to
Building a Penetration Testing Virtual Computer Laboratory
 Building a Penetration Testing Virtual Computer Laboratory User Guide 1 A. Table of Contents Collaborative Virtual Computer Laboratory A. Table of Contents... 2 B. Introduction... 3 C. Configure Host Network
Building a Penetration Testing Virtual Computer Laboratory User Guide 1 A. Table of Contents Collaborative Virtual Computer Laboratory A. Table of Contents... 2 B. Introduction... 3 C. Configure Host Network
Introduction Installation firewall analyzer step by step installation Startup Syslog and SNMP setup on firewall side firewall analyzer startup
 Introduction Installation firewall analyzer step by step installation Startup Syslog and SNMP setup on firewall side firewall analyzer startup Configuration Syslog server add and check Configure SNMP on
Introduction Installation firewall analyzer step by step installation Startup Syslog and SNMP setup on firewall side firewall analyzer startup Configuration Syslog server add and check Configure SNMP on
F-SECURE MESSAGING SECURITY GATEWAY
 F-SECURE MESSAGING SECURITY GATEWAY DEFAULT SETUP GUIDE This guide describes how to set up and configure the F-Secure Messaging Security Gateway appliance in a basic e-mail server environment. AN EXAMPLE
F-SECURE MESSAGING SECURITY GATEWAY DEFAULT SETUP GUIDE This guide describes how to set up and configure the F-Secure Messaging Security Gateway appliance in a basic e-mail server environment. AN EXAMPLE
Virtual Appliance for VMware Server. Getting Started Guide. Revision 2.0.2. Warning and Disclaimer
 Virtual Appliance for VMware Server Getting Started Guide Revision 2.0.2 Warning and Disclaimer This document is designed to provide information about the configuration and installation of the CensorNet
Virtual Appliance for VMware Server Getting Started Guide Revision 2.0.2 Warning and Disclaimer This document is designed to provide information about the configuration and installation of the CensorNet
Lab Objectives & Turn In
 Firewall Lab This lab will apply several theories discussed throughout the networking series. The routing, installing/configuring DHCP, and setting up the services is already done. All that is left for
Firewall Lab This lab will apply several theories discussed throughout the networking series. The routing, installing/configuring DHCP, and setting up the services is already done. All that is left for
Initial Access and Basic IPv4 Internet Configuration
 Initial Access and Basic IPv4 Internet Configuration This quick start guide provides initial and basic Internet (WAN) configuration information for the ProSafe Wireless-N 8-Port Gigabit VPN Firewall FVS318N
Initial Access and Basic IPv4 Internet Configuration This quick start guide provides initial and basic Internet (WAN) configuration information for the ProSafe Wireless-N 8-Port Gigabit VPN Firewall FVS318N
WEBTITAN CLOUD. User Identification Guide BLOCK WEB THREATS BOOST PRODUCTIVITY REDUCE LIABILITIES
 BLOCK WEB THREATS BOOST PRODUCTIVITY REDUCE LIABILITIES WEBTITAN CLOUD User Identification Guide This guide explains how to install and configure the WebTitan Cloud Active Directory components required
BLOCK WEB THREATS BOOST PRODUCTIVITY REDUCE LIABILITIES WEBTITAN CLOUD User Identification Guide This guide explains how to install and configure the WebTitan Cloud Active Directory components required
Configuration Manual English version
 Configuration Manual English version Frama F-Link Configuration Manual (EN) All rights reserved. Frama Group. The right to make changes in this Installation Guide is reserved. Frama Ltd also reserves the
Configuration Manual English version Frama F-Link Configuration Manual (EN) All rights reserved. Frama Group. The right to make changes in this Installation Guide is reserved. Frama Ltd also reserves the
Lab 8.4.2 Configuring Access Policies and DMZ Settings
 Lab 8.4.2 Configuring Access Policies and DMZ Settings Objectives Log in to a multi-function device and view security settings. Set up Internet access policies based on IP address and application. Set
Lab 8.4.2 Configuring Access Policies and DMZ Settings Objectives Log in to a multi-function device and view security settings. Set up Internet access policies based on IP address and application. Set
Intrusion Detection and Prevention: Network and IDS Configuration and Monitoring using Snort
 License Intrusion Detection and Prevention: Network and IDS Configuration and Monitoring using Snort This work by Z. Cliffe Schreuders at Leeds Metropolitan University is licensed under a Creative Commons
License Intrusion Detection and Prevention: Network and IDS Configuration and Monitoring using Snort This work by Z. Cliffe Schreuders at Leeds Metropolitan University is licensed under a Creative Commons
DSL-G604T Install Guides
 Internet connection with NAT...2 Internet connection with No NAT, IP Un-number...6 Port Forwarding...12 Filtering & Firewall Setup...20 Access Control... 21 DMZ Setup... 26 Allow Incoming Ping... 27 How
Internet connection with NAT...2 Internet connection with No NAT, IP Un-number...6 Port Forwarding...12 Filtering & Firewall Setup...20 Access Control... 21 DMZ Setup... 26 Allow Incoming Ping... 27 How
Installation of the On Site Server (OSS)
 Installation of the On Site Server (OSS) rev 1.1 Step #1 - Initial Connection to the OSS Having plugged in power and an ethernet cable in the eth0 interface (see diagram below) you can connect to the unit
Installation of the On Site Server (OSS) rev 1.1 Step #1 - Initial Connection to the OSS Having plugged in power and an ethernet cable in the eth0 interface (see diagram below) you can connect to the unit
Lab 1: Network Devices and Technologies - Capturing Network Traffic
 CompTIA Security+ Lab Series Lab 1: Network Devices and Technologies - Capturing Network Traffic CompTIA Security+ Domain 1 - Network Security Objective 1.1: Explain the security function and purpose of
CompTIA Security+ Lab Series Lab 1: Network Devices and Technologies - Capturing Network Traffic CompTIA Security+ Domain 1 - Network Security Objective 1.1: Explain the security function and purpose of
3.1 RS-232/422/485 Pinout:PORT1-4(RJ-45) RJ-45 RS-232 RS-422 RS-485 PIN1 TXD PIN2 RXD PIN3 GND PIN4 PIN5 T+ 485+ PIN6 T- 485- PIN7 R+ PIN8 R-
 MODEL ATC-2004 TCP/IP TO RS-232/422/485 CONVERTER User s Manual 1.1 Introduction The ATC-2004 is a 4 Port RS232/RS485 to TCP/IP converter integrated with a robust system and network management features
MODEL ATC-2004 TCP/IP TO RS-232/422/485 CONVERTER User s Manual 1.1 Introduction The ATC-2004 is a 4 Port RS232/RS485 to TCP/IP converter integrated with a robust system and network management features
Virtual Managment Appliance Setup Guide
 Virtual Managment Appliance Setup Guide 2 Sophos Installing a Virtual Appliance Installing a Virtual Appliance As an alternative to the hardware-based version of the Sophos Web Appliance, you can deploy
Virtual Managment Appliance Setup Guide 2 Sophos Installing a Virtual Appliance Installing a Virtual Appliance As an alternative to the hardware-based version of the Sophos Web Appliance, you can deploy
Appliance Quick Start Guide. v7.6
 Appliance Quick Start Guide v7.6 rev. 1.0.7 Copyright 2002 2015 Loadbalancer.org, Inc. Table of Contents Loadbalancer.org Terminology... 4 What is a Virtual IP Address?... 5 What is a Floating IP Address?...
Appliance Quick Start Guide v7.6 rev. 1.0.7 Copyright 2002 2015 Loadbalancer.org, Inc. Table of Contents Loadbalancer.org Terminology... 4 What is a Virtual IP Address?... 5 What is a Floating IP Address?...
Multi-Homing Dual WAN Firewall Router
 Multi-Homing Dual WAN Firewall Router Quick Installation Guide M73-APO09-400 Multi-Homing Dual WAN Firewall Router Overview The Multi-Homing Dual WAN Firewall Router provides three 10/100Mbit Ethernet
Multi-Homing Dual WAN Firewall Router Quick Installation Guide M73-APO09-400 Multi-Homing Dual WAN Firewall Router Overview The Multi-Homing Dual WAN Firewall Router provides three 10/100Mbit Ethernet
Firewall VPN Router. Quick Installation Guide M73-APO09-380
 Firewall VPN Router Quick Installation Guide M73-APO09-380 Firewall VPN Router Overview The Firewall VPN Router provides three 10/100Mbit Ethernet network interface ports which are the Internal/LAN, External/WAN,
Firewall VPN Router Quick Installation Guide M73-APO09-380 Firewall VPN Router Overview The Firewall VPN Router provides three 10/100Mbit Ethernet network interface ports which are the Internal/LAN, External/WAN,
Rally Installation Guide
 Rally Installation Guide Rally On-Premises release 2015.1 rallysupport@rallydev.com www.rallydev.com Version 2015.1 Table of Contents Overview... 3 Server requirements... 3 Browser requirements... 3 Access
Rally Installation Guide Rally On-Premises release 2015.1 rallysupport@rallydev.com www.rallydev.com Version 2015.1 Table of Contents Overview... 3 Server requirements... 3 Browser requirements... 3 Access
Quick Start Guide. Cerberus FTP is distributed in Canada through C&C Software. Visit us today at www.ccsoftware.ca!
 Quick Start Guide Cerberus FTP is distributed in Canada through C&C Software. Visit us today at www.ccsoftware.ca! How to Setup a File Server with Cerberus FTP Server FTP and SSH SFTP are application protocols
Quick Start Guide Cerberus FTP is distributed in Canada through C&C Software. Visit us today at www.ccsoftware.ca! How to Setup a File Server with Cerberus FTP Server FTP and SSH SFTP are application protocols
Virtual Web Appliance Setup Guide
 Virtual Web Appliance Setup Guide 2 Sophos Installing a Virtual Appliance Installing a Virtual Appliance This guide describes the procedures for installing a Virtual Web Appliance. If you are installing
Virtual Web Appliance Setup Guide 2 Sophos Installing a Virtual Appliance Installing a Virtual Appliance This guide describes the procedures for installing a Virtual Web Appliance. If you are installing
STATIC IP SET UP GUIDE VERIZON 7500 WIRELESS ROUTER/MODEM
 STATIC IP SET UP GUIDE VERIZON 7500 WIRELESS ROUTER/MODEM Verizon High Speed Internet for Business Verizon High Speed Internet for Business SETTING UP YOUR NEW STATIC IP CONNECTION AND IP ADDRESS(ES) This
STATIC IP SET UP GUIDE VERIZON 7500 WIRELESS ROUTER/MODEM Verizon High Speed Internet for Business Verizon High Speed Internet for Business SETTING UP YOUR NEW STATIC IP CONNECTION AND IP ADDRESS(ES) This
Field Installation Guide
 Field Installation Guide Orchestrator 1.0 12-Feb-2014 Notice Copyright Copyright 2014 Nutanix, Inc. Nutanix, Inc. 1740 Technology Drive, Suite 150 San Jose, CA 95110 All rights reserved. This product is
Field Installation Guide Orchestrator 1.0 12-Feb-2014 Notice Copyright Copyright 2014 Nutanix, Inc. Nutanix, Inc. 1740 Technology Drive, Suite 150 San Jose, CA 95110 All rights reserved. This product is
User Manual. Onsight Management Suite Version 5.1. Another Innovation by Librestream
 User Manual Onsight Management Suite Version 5.1 Another Innovation by Librestream Doc #: 400075-06 May 2012 Information in this document is subject to change without notice. Reproduction in any manner
User Manual Onsight Management Suite Version 5.1 Another Innovation by Librestream Doc #: 400075-06 May 2012 Information in this document is subject to change without notice. Reproduction in any manner
User s Manual TCP/IP TO RS-232/422/485 CONVERTER. 1.1 Introduction. 1.2 Main features. Dynamic DNS
 MODEL ATC-2000 TCP/IP TO RS-232/422/485 CONVERTER User s Manual 1.1 Introduction The ATC-2000 is a RS232/RS485 to TCP/IP converter integrated with a robust system and network management features designed
MODEL ATC-2000 TCP/IP TO RS-232/422/485 CONVERTER User s Manual 1.1 Introduction The ATC-2000 is a RS232/RS485 to TCP/IP converter integrated with a robust system and network management features designed
DEPLOYMENT GUIDE. This document gives a brief overview of deployment preparation, installation and configuration of a Vectra X-series platform.
 This document gives a brief overview of deployment preparation, installation and configuration of a Vectra X-series platform. Traffic Requirements The Vectra X-series platform detects threats and attacks
This document gives a brief overview of deployment preparation, installation and configuration of a Vectra X-series platform. Traffic Requirements The Vectra X-series platform detects threats and attacks
Kaseya Server Instal ation User Guide June 6, 2008
 Kaseya Server Installation User Guide June 6, 2008 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations. Kaseya's
Kaseya Server Installation User Guide June 6, 2008 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations. Kaseya's
Lab 8.4.2 Configuring Access Policies and DMZ Settings
 Lab 8.4.2 Configuring Access Policies and DMZ Settings Objectives Log in to a multi-function device and view security settings. Set up Internet access policies based on IP address and application. Set
Lab 8.4.2 Configuring Access Policies and DMZ Settings Objectives Log in to a multi-function device and view security settings. Set up Internet access policies based on IP address and application. Set
Comodo MyDLP Software Version 2.0. Installation Guide Guide Version 2.0.010215. Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013
 Comodo MyDLP Software Version 2.0 Installation Guide Guide Version 2.0.010215 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.About MyDLP... 3 1.1.MyDLP Features... 3
Comodo MyDLP Software Version 2.0 Installation Guide Guide Version 2.0.010215 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.About MyDLP... 3 1.1.MyDLP Features... 3
Transparent Firewall/Filtering Bridge - pfsense 2.0.2. By William Tarrh
 Transparent Firewall/Filtering Bridge - pfsense 2.0.2 By William Tarrh Version 2 February 6, 2013 1 Transparent Firewall/Filtering Bridge - pfsense 2.0.2 This how to is an updated version of Trendchiller
Transparent Firewall/Filtering Bridge - pfsense 2.0.2 By William Tarrh Version 2 February 6, 2013 1 Transparent Firewall/Filtering Bridge - pfsense 2.0.2 This how to is an updated version of Trendchiller
FI8910W Quick Installation Guide. Indoor MJPEG Pan/Tilt Wireless IP Camera
 Model: FI8910W Quick Installation Guide (For Windows OS) (For MAC OS please go to page 17) Indoor MJPEG Pan/Tilt Wireless IP Camera Black White Package Contents IP Camera FI8910W with IR-Cut.x 1 DC Power
Model: FI8910W Quick Installation Guide (For Windows OS) (For MAC OS please go to page 17) Indoor MJPEG Pan/Tilt Wireless IP Camera Black White Package Contents IP Camera FI8910W with IR-Cut.x 1 DC Power
USER CONFERENCE 2011 SAN FRANCISCO APRIL 26 29. Running MarkLogic in the Cloud DEVELOPER LOUNGE LAB
 USER CONFERENCE 2011 SAN FRANCISCO APRIL 26 29 Running MarkLogic in the Cloud DEVELOPER LOUNGE LAB Table of Contents UNIT 1: Lab description... 3 Pre-requisites:... 3 UNIT 2: Launching an instance on EC2...
USER CONFERENCE 2011 SAN FRANCISCO APRIL 26 29 Running MarkLogic in the Cloud DEVELOPER LOUNGE LAB Table of Contents UNIT 1: Lab description... 3 Pre-requisites:... 3 UNIT 2: Launching an instance on EC2...
How To - Deploy Cyberoam in Gateway Mode
 How To - Deploy Cyberoam in Gateway Mode Cyberoam appliance can be deployed in a network in two modes: Gateway mode. Popularly known as Route mode Bridge mode. Popularly known as Transparent mode Article
How To - Deploy Cyberoam in Gateway Mode Cyberoam appliance can be deployed in a network in two modes: Gateway mode. Popularly known as Route mode Bridge mode. Popularly known as Transparent mode Article
How To Industrial Networking
 How To Industrial Networking Prepared by: Matt Crites Product: Date: April 2014 Any RAM or SN 6xxx series router Legacy firmware 3.14/4.14 or lower Subject: This document provides a step by step procedure
How To Industrial Networking Prepared by: Matt Crites Product: Date: April 2014 Any RAM or SN 6xxx series router Legacy firmware 3.14/4.14 or lower Subject: This document provides a step by step procedure
Multi-Homing Security Gateway
 Multi-Homing Security Gateway MH-5000 Quick Installation Guide 1 Before You Begin It s best to use a computer with an Ethernet adapter for configuring the MH-5000. The default IP address for the MH-5000
Multi-Homing Security Gateway MH-5000 Quick Installation Guide 1 Before You Begin It s best to use a computer with an Ethernet adapter for configuring the MH-5000. The default IP address for the MH-5000
Consolidated Monitoring, Analysis and Automated Remediation For Hybrid IT Infrastructures. Goliath Performance Monitor Installation Guide v11.
 Consolidated Monitoring, Analysis and Automated Remediation For Hybrid IT Infrastructures Goliath Performance Monitor Installation Guide v11.5 (v11.5) Document Date: March 2015 www.goliathtechnologies.com
Consolidated Monitoring, Analysis and Automated Remediation For Hybrid IT Infrastructures Goliath Performance Monitor Installation Guide v11.5 (v11.5) Document Date: March 2015 www.goliathtechnologies.com
MN-700 Base Station Configuration Guide
 MN-700 Base Station Configuration Guide Contents pen the Base Station Management Tool...3 Log ff the Base Station Management Tool...3 Navigate the Base Station Management Tool...4 Current Base Station
MN-700 Base Station Configuration Guide Contents pen the Base Station Management Tool...3 Log ff the Base Station Management Tool...3 Navigate the Base Station Management Tool...4 Current Base Station
IS L06 Protect Servers and Defend Against APTs with Symantec Critical System Protection
 IS L06 Protect Servers and Defend Against APTs with Symantec Critical System Protection Description Lab flow At the end of this lab, you should be able to Discover how to harness the power and capabilities
IS L06 Protect Servers and Defend Against APTs with Symantec Critical System Protection Description Lab flow At the end of this lab, you should be able to Discover how to harness the power and capabilities
Consolidated Monitoring, Analysis and Automated Remediation For Hybrid IT Infrastructures. Goliath Performance Monitor Installation Guide v11.
 Consolidated Monitoring, Analysis and Automated Remediation For Hybrid IT Infrastructures Goliath Performance Monitor Installation Guide v11.6 (v11.6) Document Date: August 2015 www.goliathtechnologies.com
Consolidated Monitoring, Analysis and Automated Remediation For Hybrid IT Infrastructures Goliath Performance Monitor Installation Guide v11.6 (v11.6) Document Date: August 2015 www.goliathtechnologies.com
SonicOS Enhanced 3.8.0.6 Release Notes TZ 180 Series and TZ 190 Series SonicWALL, Inc. Firmware Release: August 28, 2007
 SonicOS Enhanced 3.8.0.6 TZ 180 Series and TZ 190 Series SonicWALL, Inc. Firmware Release: August 28, 2007 CONTENTS PLATFORM COMPATIBILITY SONICWALL RECOMMENDATIONS KNOWN ISSUES RESOLVED KNOWN ISSUES UPGRADING
SonicOS Enhanced 3.8.0.6 TZ 180 Series and TZ 190 Series SonicWALL, Inc. Firmware Release: August 28, 2007 CONTENTS PLATFORM COMPATIBILITY SONICWALL RECOMMENDATIONS KNOWN ISSUES RESOLVED KNOWN ISSUES UPGRADING
Gigabyte Management Console User s Guide (For ASPEED AST 2400 Chipset)
 Gigabyte Management Console User s Guide (For ASPEED AST 2400 Chipset) Version: 1.4 Table of Contents Using Your Gigabyte Management Console... 3 Gigabyte Management Console Key Features and Functions...
Gigabyte Management Console User s Guide (For ASPEED AST 2400 Chipset) Version: 1.4 Table of Contents Using Your Gigabyte Management Console... 3 Gigabyte Management Console Key Features and Functions...
Altor Virtual Network Security Analyzer v1.0 Installation Guide
 Altor Virtual Network Security Analyzer v1.0 Installation Guide The Altor Virtual Network Security Analyzer (VNSA) application is deployed as Virtual Appliance running on VMware ESX servers. A single Altor
Altor Virtual Network Security Analyzer v1.0 Installation Guide The Altor Virtual Network Security Analyzer (VNSA) application is deployed as Virtual Appliance running on VMware ESX servers. A single Altor
Using VirtualBox ACHOTL1 Virtual Machines
 Using VirtualBox ACHOTL1 Virtual Machines The steps in the Apache Cassandra Hands-On Training Level One courseware book were written using VMware as the virtualization technology. Therefore, it is recommended
Using VirtualBox ACHOTL1 Virtual Machines The steps in the Apache Cassandra Hands-On Training Level One courseware book were written using VMware as the virtualization technology. Therefore, it is recommended
Load Balancing Microsoft Terminal Services. Deployment Guide
 Load Balancing Microsoft Terminal Services Deployment Guide rev. 1.5.7 Copyright 2002 2016 Loadbalancer.org, Inc. 1 Table of Contents About this Guide... 4 Loadbalancer.org Appliances Supported... 4 Loadbalancer.org
Load Balancing Microsoft Terminal Services Deployment Guide rev. 1.5.7 Copyright 2002 2016 Loadbalancer.org, Inc. 1 Table of Contents About this Guide... 4 Loadbalancer.org Appliances Supported... 4 Loadbalancer.org
Virtual Appliance Setup Guide
 The Virtual Appliance includes the same powerful technology and simple Web based user interface found on the Barracuda Web Application Firewall hardware appliance. It is designed for easy deployment on
The Virtual Appliance includes the same powerful technology and simple Web based user interface found on the Barracuda Web Application Firewall hardware appliance. It is designed for easy deployment on
Chapter 9 Monitoring System Performance
 Chapter 9 Monitoring System Performance This chapter describes the full set of system monitoring features of your ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN. You can be alerted to important
Chapter 9 Monitoring System Performance This chapter describes the full set of system monitoring features of your ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN. You can be alerted to important
Quick Installation Guide
 V48.01 Model: FI8919W Quick Installation Guide Outdoor Pan/Tilt Wireless IP Camera For Windows OS ------- Page 1 For MAC OS ------- Page 15 ShenZhen Foscam Intelligent Technology Co., Ltd Quick Installation
V48.01 Model: FI8919W Quick Installation Guide Outdoor Pan/Tilt Wireless IP Camera For Windows OS ------- Page 1 For MAC OS ------- Page 15 ShenZhen Foscam Intelligent Technology Co., Ltd Quick Installation
SonicWALL PCI 1.1 Implementation Guide
 Compliance SonicWALL PCI 1.1 Implementation Guide A PCI Implementation Guide for SonicWALL SonicOS Standard In conjunction with ControlCase, LLC (PCI Council Approved Auditor) SonicWall SonicOS Standard
Compliance SonicWALL PCI 1.1 Implementation Guide A PCI Implementation Guide for SonicWALL SonicOS Standard In conjunction with ControlCase, LLC (PCI Council Approved Auditor) SonicWall SonicOS Standard
Setting Up Your FTP Server
 Requirements:! A computer dedicated to FTP server only! Linksys router! TCP/IP internet connection Steps: Getting Started Configure Static IP on the FTP Server Computer: Setting Up Your FTP Server 1. This
Requirements:! A computer dedicated to FTP server only! Linksys router! TCP/IP internet connection Steps: Getting Started Configure Static IP on the FTP Server Computer: Setting Up Your FTP Server 1. This
Installation Guide for Pulse on Windows Server 2012
 MadCap Software Installation Guide for Pulse on Windows Server 2012 Pulse Copyright 2014 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software
MadCap Software Installation Guide for Pulse on Windows Server 2012 Pulse Copyright 2014 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software
Web Application Firewall
 Web Application Firewall Getting Started Guide August 3, 2015 Copyright 2014-2015 by Qualys, Inc. All Rights Reserved. Qualys and the Qualys logo are registered trademarks of Qualys, Inc. All other trademarks
Web Application Firewall Getting Started Guide August 3, 2015 Copyright 2014-2015 by Qualys, Inc. All Rights Reserved. Qualys and the Qualys logo are registered trademarks of Qualys, Inc. All other trademarks
Installing, Uninstalling, and Upgrading Service Monitor
 CHAPTER 2 Installing, Uninstalling, and Upgrading Service Monitor This section contains the following topics: Preparing to Install Service Monitor, page 2-1 Installing Cisco Unified Service Monitor, page
CHAPTER 2 Installing, Uninstalling, and Upgrading Service Monitor This section contains the following topics: Preparing to Install Service Monitor, page 2-1 Installing Cisco Unified Service Monitor, page
FortKnox Personal Firewall
 FortKnox Personal Firewall User Manual Document version 1.4 EN ( 15. 9. 2009 ) Copyright (c) 2007-2009 NETGATE Technologies s.r.o. All rights reserved. This product uses compression library zlib Copyright
FortKnox Personal Firewall User Manual Document version 1.4 EN ( 15. 9. 2009 ) Copyright (c) 2007-2009 NETGATE Technologies s.r.o. All rights reserved. This product uses compression library zlib Copyright
Polycom Phones User Guide. 2003-2012 Bicom Systems
 I Table of Contents Part I Introduction 1 Part II Requirements 1 Part III Installation 2 1 Power... Adapter 3 2 Power... over Ethernet (PoE) 3 3 Factory... Settings 3 3 Part IV Registering Phone 1 Manual...
I Table of Contents Part I Introduction 1 Part II Requirements 1 Part III Installation 2 1 Power... Adapter 3 2 Power... over Ethernet (PoE) 3 3 Factory... Settings 3 3 Part IV Registering Phone 1 Manual...
1:1 NAT in ZeroShell. Requirements. Overview. Network Setup
 1:1 NAT in ZeroShell Requirements The version of ZeroShell used for writing this document is Release 1.0.beta11. This document does not describe installing ZeroShell, it is assumed that the user already
1:1 NAT in ZeroShell Requirements The version of ZeroShell used for writing this document is Release 1.0.beta11. This document does not describe installing ZeroShell, it is assumed that the user already
Installing and Configuring vcloud Connector
 Installing and Configuring vcloud Connector vcloud Connector 2.7.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Installing and Configuring vcloud Connector vcloud Connector 2.7.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
READYNAS INSTANT STORAGE. Quick Installation Guide
 READYNAS INSTANT STORAGE Quick Installation Guide Table of Contents Step 1 Connect to FrontView Setup Wizard 3 Installing RAIDar on Windows 3 Installing RAIDar on Mac OS X 3 Installing RAIDar on Linux
READYNAS INSTANT STORAGE Quick Installation Guide Table of Contents Step 1 Connect to FrontView Setup Wizard 3 Installing RAIDar on Windows 3 Installing RAIDar on Mac OS X 3 Installing RAIDar on Linux
SSL VPN. Virtual Appliance Installation Guide. Virtual Private Networks
 SSL VPN Virtual Appliance Installation Guide Virtual Private Networks C ONTENTS Introduction... 2 Installing the Virtual Appliance... 2 Configuring Appliance Operating System Settings... 3 Setting up the
SSL VPN Virtual Appliance Installation Guide Virtual Private Networks C ONTENTS Introduction... 2 Installing the Virtual Appliance... 2 Configuring Appliance Operating System Settings... 3 Setting up the
HP Device Manager 4.6
 Technical white paper HP Device Manager 4.6 Installation and Update Guide Table of contents Overview... 3 HPDM Server preparation... 3 FTP server configuration... 3 Windows Firewall settings... 3 Firewall
Technical white paper HP Device Manager 4.6 Installation and Update Guide Table of contents Overview... 3 HPDM Server preparation... 3 FTP server configuration... 3 Windows Firewall settings... 3 Firewall
ReadyNAS Setup Manual
 ReadyNAS Setup Manual NETGEAR, Inc. 4500 Great America Parkway Santa Clara, CA 95054 USA October 2007 208-10163-01 v1.0 2007 by NETGEAR, Inc. All rights reserved. Trademarks NETGEAR, the NETGEAR logo,
ReadyNAS Setup Manual NETGEAR, Inc. 4500 Great America Parkway Santa Clara, CA 95054 USA October 2007 208-10163-01 v1.0 2007 by NETGEAR, Inc. All rights reserved. Trademarks NETGEAR, the NETGEAR logo,
Note: This case study utilizes Packet Tracer. Please see the Chapter 5 Packet Tracer file located in Supplemental Materials.
 Note: This case study utilizes Packet Tracer. Please see the Chapter 5 Packet Tracer file located in Supplemental Materials. CHAPTER 5 OBJECTIVES Configure a router with an initial configuration. Use the
Note: This case study utilizes Packet Tracer. Please see the Chapter 5 Packet Tracer file located in Supplemental Materials. CHAPTER 5 OBJECTIVES Configure a router with an initial configuration. Use the
Installation Guide for Pulse on Windows Server 2008R2
 MadCap Software Installation Guide for Pulse on Windows Server 2008R2 Pulse Copyright 2014 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software
MadCap Software Installation Guide for Pulse on Windows Server 2008R2 Pulse Copyright 2014 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software
Installing and Using the vnios Trial
 Installing and Using the vnios Trial The vnios Trial is a software package designed for efficient evaluation of the Infoblox vnios appliance platform. Providing the complete suite of DNS, DHCP and IPAM
Installing and Using the vnios Trial The vnios Trial is a software package designed for efficient evaluation of the Infoblox vnios appliance platform. Providing the complete suite of DNS, DHCP and IPAM
AP6511 First Time Configuration Procedure
 AP6511 First Time Configuration Procedure Recommended Minimum Configuration Steps From the factory, all of the 6511 AP s should be configured with a shadow IP that starts with 169.254.xxx.xxx with the
AP6511 First Time Configuration Procedure Recommended Minimum Configuration Steps From the factory, all of the 6511 AP s should be configured with a shadow IP that starts with 169.254.xxx.xxx with the
6.0. Getting Started Guide
 6.0 Getting Started Guide Netmon Getting Started Guide 2 Contents Contents... 2 Appliance Installation... 3 IP Address Assignment (Optional)... 3 Logging In For the First Time... 5 Initial Setup... 6 License
6.0 Getting Started Guide Netmon Getting Started Guide 2 Contents Contents... 2 Appliance Installation... 3 IP Address Assignment (Optional)... 3 Logging In For the First Time... 5 Initial Setup... 6 License
Backup & Disaster Recovery Appliance User Guide
 Built on the Intel Hybrid Cloud Platform Backup & Disaster Recovery Appliance User Guide Order Number: G68664-001 Rev 1.0 June 22, 2012 Contents Registering the BDR Appliance... 4 Step 1: Register the
Built on the Intel Hybrid Cloud Platform Backup & Disaster Recovery Appliance User Guide Order Number: G68664-001 Rev 1.0 June 22, 2012 Contents Registering the BDR Appliance... 4 Step 1: Register the
Wanos on Hyper-V Comprehensive guide for a complete lab
 Wanos on Hyper-V Comprehensive guide for a complete lab This document will guide the user in setting up a Wanos appliance using Hyper-V on a Microsoft Windows Server 2012 R2. Four Virtual Machines will
Wanos on Hyper-V Comprehensive guide for a complete lab This document will guide the user in setting up a Wanos appliance using Hyper-V on a Microsoft Windows Server 2012 R2. Four Virtual Machines will
VMware vcenter Log Insight Getting Started Guide
 VMware vcenter Log Insight Getting Started Guide vcenter Log Insight 1.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
VMware vcenter Log Insight Getting Started Guide vcenter Log Insight 1.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
NEFSIS DEDICATED SERVER
 NEFSIS TRAINING SERIES Nefsis Dedicated Server version 5.2.0.XXX (DRAFT Document) Requirements and Implementation Guide (Rev5-113009) REQUIREMENTS AND INSTALLATION OF THE NEFSIS DEDICATED SERVER Nefsis
NEFSIS TRAINING SERIES Nefsis Dedicated Server version 5.2.0.XXX (DRAFT Document) Requirements and Implementation Guide (Rev5-113009) REQUIREMENTS AND INSTALLATION OF THE NEFSIS DEDICATED SERVER Nefsis
ADTRAN 3120 / 3130 Internet Configuration Guide
 AdTran Internet Configuration Guide v1.15 ADTRAN 3120 / 3130 Internet Configuration Guide 169 Saxony Road, Suite 212 Encinitas, CA 92024 Phone & Fax: (800) 477-1477 Table of Contents Introduction... 1
AdTran Internet Configuration Guide v1.15 ADTRAN 3120 / 3130 Internet Configuration Guide 169 Saxony Road, Suite 212 Encinitas, CA 92024 Phone & Fax: (800) 477-1477 Table of Contents Introduction... 1
First Installation Guide
 Getting started with gateprotect First Installation Guide Installation and First Configuration of Next Generation UTM and Firewall Appliances May 2013 Thank you for choosing a gateprotect Next Generation
Getting started with gateprotect First Installation Guide Installation and First Configuration of Next Generation UTM and Firewall Appliances May 2013 Thank you for choosing a gateprotect Next Generation
Service Managed Gateway TM. How to Configure a Firewall
 Service Managed Gateway TM Issue 1.3 Date 10 March 2006 Table of contents 1 Introduction... 3 1.1 What is a firewall?... 3 1.2 The benefits of using a firewall... 3 2 How to configure firewall settings
Service Managed Gateway TM Issue 1.3 Date 10 March 2006 Table of contents 1 Introduction... 3 1.1 What is a firewall?... 3 1.2 The benefits of using a firewall... 3 2 How to configure firewall settings
Barracuda Link Balancer Administrator s Guide
 Barracuda Link Balancer Administrator s Guide Version 1.0 Barracuda Networks Inc. 3175 S. Winchester Blvd. Campbell, CA 95008 http://www.barracuda.com Copyright Notice Copyright 2008, Barracuda Networks
Barracuda Link Balancer Administrator s Guide Version 1.0 Barracuda Networks Inc. 3175 S. Winchester Blvd. Campbell, CA 95008 http://www.barracuda.com Copyright Notice Copyright 2008, Barracuda Networks
Configuring Security for FTP Traffic
 2 Configuring Security for FTP Traffic Securing FTP traffic Creating a security profile for FTP traffic Configuring a local traffic FTP profile Assigning an FTP security profile to a local traffic FTP
2 Configuring Security for FTP Traffic Securing FTP traffic Creating a security profile for FTP traffic Configuring a local traffic FTP profile Assigning an FTP security profile to a local traffic FTP
Team Foundation Server 2013 Installation Guide
 Team Foundation Server 2013 Installation Guide Page 1 of 164 Team Foundation Server 2013 Installation Guide Benjamin Day benday@benday.com v1.1.0 May 28, 2014 Team Foundation Server 2013 Installation Guide
Team Foundation Server 2013 Installation Guide Page 1 of 164 Team Foundation Server 2013 Installation Guide Benjamin Day benday@benday.com v1.1.0 May 28, 2014 Team Foundation Server 2013 Installation Guide
VMware vcenter Log Insight Getting Started Guide
 VMware vcenter Log Insight Getting Started Guide vcenter Log Insight 2.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
VMware vcenter Log Insight Getting Started Guide vcenter Log Insight 2.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
Sentral servers provide a wide range of services to school networks.
 Wazza s QuickStart Publishing iweb Sites to a Sentral Server Background Mac OS X, Sentral, iweb 09 Sentral servers provide a wide range of services to school networks. A Sentral server provides a publishing
Wazza s QuickStart Publishing iweb Sites to a Sentral Server Background Mac OS X, Sentral, iweb 09 Sentral servers provide a wide range of services to school networks. A Sentral server provides a publishing
DDNS Management System User Manual V1.0
 DDNS Management System User Manual V1.0 1 03/01/2012 Table of Contents 1. Introduction.3 2. Network Configuration 3 2.1. Configuring DDNS locally through DVR Menu..3 2.2. Configuring DDNS through Internet
DDNS Management System User Manual V1.0 1 03/01/2012 Table of Contents 1. Introduction.3 2. Network Configuration 3 2.1. Configuring DDNS locally through DVR Menu..3 2.2. Configuring DDNS through Internet
Quick Installation Guide DAP-1360. Wireless N 300 Access Point & Router
 DAP-1360 Wireless N 300 Access Point & Router BEFORE YOU BEGIN Delivery Package Access point DAP-1360 Power adapter DC 12V Ethernet cable (CAT 5E) (brochure). If any of the items are missing, please contact
DAP-1360 Wireless N 300 Access Point & Router BEFORE YOU BEGIN Delivery Package Access point DAP-1360 Power adapter DC 12V Ethernet cable (CAT 5E) (brochure). If any of the items are missing, please contact
Guide to the LBaaS plugin ver. 1.0.2 for Fuel
 Guide to the LBaaS plugin ver. 1.0.2 for Fuel Load Balancing plugin for Fuel LBaaS (Load Balancing as a Service) is currently an advanced service of Neutron that provides load balancing for Neutron multi
Guide to the LBaaS plugin ver. 1.0.2 for Fuel Load Balancing plugin for Fuel LBaaS (Load Balancing as a Service) is currently an advanced service of Neutron that provides load balancing for Neutron multi
Innominate mguard Version 6
 Innominate mguard Version 6 Configuration Examples mguard smart mguard PCI mguard blade mguard industrial RS EAGLE mguard mguard delta Innominate Security Technologies AG Albert-Einstein-Str. 14 12489
Innominate mguard Version 6 Configuration Examples mguard smart mguard PCI mguard blade mguard industrial RS EAGLE mguard mguard delta Innominate Security Technologies AG Albert-Einstein-Str. 14 12489
How to convert a wireless router to be a wireless. access point
 How to convert a wireless router to be a wireless access point Thanks for purchasing Edimax Wireless Router. This instruction can be applied if you want to keep your wired router and you need Edimax Wireless
How to convert a wireless router to be a wireless access point Thanks for purchasing Edimax Wireless Router. This instruction can be applied if you want to keep your wired router and you need Edimax Wireless
WatchGuard Dimension v1.1 Update 1 Release Notes
 WatchGuard Dimension v1.1 Update 1 Release Notes Build Number 442674 Revision Date March 25, 2014 WatchGuard Dimension is the next-generation cloud-ready visibility solution for our Unified Threat Management
WatchGuard Dimension v1.1 Update 1 Release Notes Build Number 442674 Revision Date March 25, 2014 WatchGuard Dimension is the next-generation cloud-ready visibility solution for our Unified Threat Management
Deploying Windows Streaming Media Servers NLB Cluster and metasan
 Deploying Windows Streaming Media Servers NLB Cluster and metasan Introduction...................................................... 2 Objectives.......................................................
Deploying Windows Streaming Media Servers NLB Cluster and metasan Introduction...................................................... 2 Objectives.......................................................
Steps for Basic Configuration
 1. This guide describes how to use the Unified Threat Management appliance (UTM) Basic Setup Wizard to configure the UTM for connection to your network. It also describes how to register the UTM with NETGEAR.
1. This guide describes how to use the Unified Threat Management appliance (UTM) Basic Setup Wizard to configure the UTM for connection to your network. It also describes how to register the UTM with NETGEAR.
Load Balancing Router. User s Guide
 Load Balancing Router User s Guide TABLE OF CONTENTS 1: INTRODUCTION... 1 Internet Features... 1 Other Features... 3 Package Contents... 4 Physical Details... 4 2: BASIC SETUP... 8 Overview... 8 Procedure...
Load Balancing Router User s Guide TABLE OF CONTENTS 1: INTRODUCTION... 1 Internet Features... 1 Other Features... 3 Package Contents... 4 Physical Details... 4 2: BASIC SETUP... 8 Overview... 8 Procedure...
Yealink Phones User Guide. 2003-2012 Bicom Systems
 I Table of Contents Part I Introduction 1 Part II Requirements 1 Part III Installation 2 1 Power... Adapter 3 2 Power... over Ethernet (PoE) 3 3 IP Address... 3 4 Factory... Settings 3 4 Part IV Registering
I Table of Contents Part I Introduction 1 Part II Requirements 1 Part III Installation 2 1 Power... Adapter 3 2 Power... over Ethernet (PoE) 3 3 IP Address... 3 4 Factory... Settings 3 4 Part IV Registering
Document No. FO1001 Issue Date: Draft: Work Group: FibreOP Technical Team October 1, 2013 Final:
 Document No. FO1001 Issue Date: Draft: Work Group: FibreOP Technical Team October 1, 2013 Final: Title: Single Static IP Basic Set-up Version 1.1 Summary: Use the following method to perform the basic
Document No. FO1001 Issue Date: Draft: Work Group: FibreOP Technical Team October 1, 2013 Final: Title: Single Static IP Basic Set-up Version 1.1 Summary: Use the following method to perform the basic
Configuring MassTransit Server to listen on ports less than 1024 using WaterRoof on Macintosh Workstations
 Configuring MassTransit Server to listen on ports less than 1024 using WaterRoof on Macintosh Workstations Summary This article explains how to configure MassTransit to listen on ports less than 1024 without
Configuring MassTransit Server to listen on ports less than 1024 using WaterRoof on Macintosh Workstations Summary This article explains how to configure MassTransit to listen on ports less than 1024 without
Load Balancing McAfee Web Gateway. Deployment Guide
 Load Balancing McAfee Web Gateway Deployment Guide rev. 1.1.4 Copyright 2015 Loadbalancer.org, Inc. 1 Table of Contents About this Guide... 3 Loadbalancer.org Appliances Supported...3 Loadbalancer.org
Load Balancing McAfee Web Gateway Deployment Guide rev. 1.1.4 Copyright 2015 Loadbalancer.org, Inc. 1 Table of Contents About this Guide... 3 Loadbalancer.org Appliances Supported...3 Loadbalancer.org
Volume SYSLOG JUNCTION. User s Guide. User s Guide
 Volume 1 SYSLOG JUNCTION User s Guide User s Guide SYSLOG JUNCTION USER S GUIDE Introduction I n simple terms, Syslog junction is a log viewer with graphing capabilities. It can receive syslog messages
Volume 1 SYSLOG JUNCTION User s Guide User s Guide SYSLOG JUNCTION USER S GUIDE Introduction I n simple terms, Syslog junction is a log viewer with graphing capabilities. It can receive syslog messages
Configure thin client settings locally
 This chapter contains information to help you set up your thin client hardware, look and feel, and system settings using the Control Center. Tip While it is not recommended to use dialog boxes for configuring
This chapter contains information to help you set up your thin client hardware, look and feel, and system settings using the Control Center. Tip While it is not recommended to use dialog boxes for configuring
Step-by-Step Setup Guide Wireless File Transmitter FTP Mode
 EOS Step-by-Step Setup Guide Wireless File Transmitter FTP Mode Infrastructure & Ad Hoc Networks Mac OS X 10.5-10.6 2012 Canon U.S.A., Inc. All Rights Reserved. Reproduction in whole or in part without
EOS Step-by-Step Setup Guide Wireless File Transmitter FTP Mode Infrastructure & Ad Hoc Networks Mac OS X 10.5-10.6 2012 Canon U.S.A., Inc. All Rights Reserved. Reproduction in whole or in part without
HOMEROOM SERVER INSTALLATION & NETWORK CONFIGURATION GUIDE
 HOMEROOM SERVER INSTALLATION & NETWORK CONFIGURATION GUIDE Level 1, 61 Davey St Hobart, TAS 7000 T (03) 6165 1555 www.getbusi.com Table of Contents ABOUT THIS MANUAL! 1 SYSTEM REQUIREMENTS! 2 Hardware
HOMEROOM SERVER INSTALLATION & NETWORK CONFIGURATION GUIDE Level 1, 61 Davey St Hobart, TAS 7000 T (03) 6165 1555 www.getbusi.com Table of Contents ABOUT THIS MANUAL! 1 SYSTEM REQUIREMENTS! 2 Hardware
