Getting Started with Trend Micro Certification
|
|
|
- Polly Cox
- 8 years ago
- Views:
Transcription
1 Getting Started with Trend Micro Certification The new Trend Micro Education training and certification program has four tracks that cover a range of audiences. Each product or solution will have one or more of these tracks available: Trend Micro Sales Training and Assessment Trend Micro Technical Sales Training and Assessment Trend Micro Certified Professional Designation Trend Micro Certified Expert Designation
2 The Trend Micro Sales Training and Assessment enables sales consultants to validate that they have the requisite knowledge of Trend Micro products and technology basics necessary to complete sales activities with customers. Qualified candidates should be able to understand the competitive environment, their customers business challenges, and articulate appropriate solutions based on their customers needs and requirements. They should coordinate with technical staff throughout the sales process and utilize proper customer satisfaction techniques. The Trend Micro Technical Sales Training and Assessment enables sales consultants to validate that they have the requisite technical understanding of Trend Micro products, and the ability to explain their functions to customers. Qualified candidates should be able to conduct technical product discussions with customers, translate customer technical requirements into solution recommendations and assist customers with any technical questions. The Trend Micro Certified Professional Designation is intended for consultants who work with Trend Micro product solutions in enterprise environments. Successful candidates demonstrate the knowledge necessary to successfully install, deploy, scale, and manage a product, along with a solid foundation in basic concepts including public/private/hybrid clouds, multi-tenancy, and cloud security. The Trend Micro Certified Expert Designation is intended for consulting architects with extensive experience designing and integrating solutions in enterprise environments. Successful candidates have a deep understanding of the product core components and enterprise architectures, as well as significant troubleshooting skills in both physical and virtual environments. Expert certification is achieved through an in-depth evaluation process, where candidates architect and successfully deploy a production-ready solution. This process ensures that those who achieve Expert status are part of a world-class group of consulting architects.
3 Courses available on the training site: Training Technical Sales Specialization Trend Micro Product Sales Training Training Small Business Security Worry-Free Business Security Hosted Security Certified Professional Certification Certified Expert Complete User Protection (CUP) Solution Overview Control Manager Endpoint Endpoint Application Control OfficeScan Worry-Free Business Security Vulnerability Protection Mail and Collaboration Gateway InterScan Messaging Security PortalProtect Hosted Security ScanMail for Microsoft Exchange Web Gateway InterScan Web Security as a Service InterScan Web Security Virtual Appliance Mobility Mobile Security SafeSync for Enterprise Cloud and Data Center Security Deep Security SecureCloud ServerProtect Custom Defense Deep Discovery Each course has a number of content assets available to students: Video Product datasheets Competition datasheets Training documents How to documents Admin Guide Installation Guide Etc.
4 Users will retain their current certification records in the new Education Portal. In addition, we have defined a mapping between the previous certifications and the new program, and will be automatically giving you credit for the equivalent track in the new program. Trend Micro Certified Sales Representative => Trend Micro Sales Training Trend Micro Certified Sales Specialist => no mapping, this has been eliminated Trend Micro Certified Sales Consultant => Trend Micro Technical Sales Training Trend Micro Certified Security Professional => Trend Micro Technical Sales Training Trend Micro Certified Security Expert => no mapping, this has been eliminated Trend Micro Certified Security Master => Trend Micro Certified Professional Trend Micro Foundation Certification => no mapping, this has been eliminated New Trend Micro Certified Expert We have changed the way certifications expire. They will no longer expire based on a fixed timeframe (1 year, 2 years). The trainings and certifications will continue to be valid until six months after training is available for new product versions. You will have 6 months to complete the new training or certification requirement to keep the status current. If you fail to complete the new training or certification requirement, your status will change to expired.
5 Courses are available online via our Training / Education Portal Please go to and log in with your username and password. After registration you will see following screen please click on Education Portal and you will be re-directed to our WEB-based training tool:
6 Education Portal, please enter Self-Paced and select one of the modules to get started: Within the module, i.e. Complete User Protection you can chose the sales and technical trainings.
overview Enterprise Security Solutions
 Enterprise Security Solutions overview For more than 25 years, Trend Micro has innovated constantly to keep our customers ahead of an ever-evolving IT threat landscape. It s how we got to be the world
Enterprise Security Solutions overview For more than 25 years, Trend Micro has innovated constantly to keep our customers ahead of an ever-evolving IT threat landscape. It s how we got to be the world
OVERVIEW. Enterprise Security Solutions
 Enterprise Security Solutions OVERVIEW For more than 25 years, Trend Micro has innovated constantly to keep our customers ahead of an everevolving IT threat landscape. It s how we got to be the world s
Enterprise Security Solutions OVERVIEW For more than 25 years, Trend Micro has innovated constantly to keep our customers ahead of an everevolving IT threat landscape. It s how we got to be the world s
overview Enterprise Security Solutions
 Enterprise Security Solutions overview For more than 25 years, Trend Micro has innovated constantly to keep our customers ahead of an ever-evolving IT threat landscape. It s how we got to be the world
Enterprise Security Solutions overview For more than 25 years, Trend Micro has innovated constantly to keep our customers ahead of an ever-evolving IT threat landscape. It s how we got to be the world
OVERVIEW. Enterprise Security Solutions
 Enterprise Security Solutions OVERVIEW For more than 25 years, Trend Micro has innovated constantly to keep our customers ahead of an everevolving IT threat landscape. It s how we got to be the world s
Enterprise Security Solutions OVERVIEW For more than 25 years, Trend Micro has innovated constantly to keep our customers ahead of an everevolving IT threat landscape. It s how we got to be the world s
Nessus Cloud User Registration
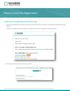 Nessus Cloud User Registration Create Your Tenable Nessus Cloud Account 1. Click on the provided URL to create your account. If the link does not work, please cut and paste the entire URL into your browser.
Nessus Cloud User Registration Create Your Tenable Nessus Cloud Account 1. Click on the provided URL to create your account. If the link does not work, please cut and paste the entire URL into your browser.
Secure Clouds - Secure Services Trend Micro best-in-class solutions enable data center to deliver trusted and secure infrastructures and services
 Secure Clouds - Secure Services Trend Micro best-in-class solutions enable data center to deliver trusted and secure infrastructures and services Udo Schneider Trend Micro Udo_Schneider@trendmicro.de 26.03.2013
Secure Clouds - Secure Services Trend Micro best-in-class solutions enable data center to deliver trusted and secure infrastructures and services Udo Schneider Trend Micro Udo_Schneider@trendmicro.de 26.03.2013
ONLINE LEVEL ONE UMPIRES COURSE PARTICIPANT FACT SHEET
 About the course The Level One Online Umpire s Course has been designed to assist you in achieving the necessary skills and knowledge to be an effective umpire and enjoy your officiating role. The course
About the course The Level One Online Umpire s Course has been designed to assist you in achieving the necessary skills and knowledge to be an effective umpire and enjoy your officiating role. The course
Managing Enterprise Devices and Apps using System Center Configuration Manager
 Course 20696B: Managing Enterprise Devices and Apps using System Center Configuration Manager Course Details Course Outline Module 1: Managing Desktops and Devices in the Enterprise This module explains
Course 20696B: Managing Enterprise Devices and Apps using System Center Configuration Manager Course Details Course Outline Module 1: Managing Desktops and Devices in the Enterprise This module explains
SWGFL Video Conferencing Service Registration of Endpoints. South West Grid for Learning. Version 1.1. Steve Cayley Ian White. Date: February 2004
 SWGFL Video Conferencing Service South West Grid for Learning Version 1.1 Author: Steve Cayley Ian White Date: February 2004 SWGfL Video Conferencing Service Page 1 SWGfL Video Conferencing Service Page
SWGFL Video Conferencing Service South West Grid for Learning Version 1.1 Author: Steve Cayley Ian White Date: February 2004 SWGfL Video Conferencing Service Page 1 SWGfL Video Conferencing Service Page
ATEA eshop. Basic Administration Guide
 Basic Administration Guide Contents Introduction... 3 Audience... 3 Document Location... 3 Special information... 3 1. Login... 4 2. Managing users... 5 3. Increase or decrease licenses... 6 4. Upgrade/Downgrade
Basic Administration Guide Contents Introduction... 3 Audience... 3 Document Location... 3 Special information... 3 1. Login... 4 2. Managing users... 5 3. Increase or decrease licenses... 6 4. Upgrade/Downgrade
Trend Micro Email Encryption Gateway 5
 Trend Micro Email Encryption Gateway 5 Secured by Private Post Quick Installation Guide m Messaging Security Trend Micro Incorporated reserves the right to make changes to this document and to the products
Trend Micro Email Encryption Gateway 5 Secured by Private Post Quick Installation Guide m Messaging Security Trend Micro Incorporated reserves the right to make changes to this document and to the products
Securing Patient Portals
 Securing Patient Portals What you need to know to comply with HIPAA Omnibus and Meaningful Use Brian Selfridge, Partner, Meditology Services, LLC Blake Sutherland, VP Enterprise Business, Trend Micro Brian
Securing Patient Portals What you need to know to comply with HIPAA Omnibus and Meaningful Use Brian Selfridge, Partner, Meditology Services, LLC Blake Sutherland, VP Enterprise Business, Trend Micro Brian
How To Reset A University Password Online On A Computer Or Cell Phone
 Introducing Password Manager Presenter Steve Martin Security Specialist Click here to watch online video 2 Risk & Security Strategy & Governance Security Consulting Security Operations Identity & Access
Introducing Password Manager Presenter Steve Martin Security Specialist Click here to watch online video 2 Risk & Security Strategy & Governance Security Consulting Security Operations Identity & Access
Exam Preparation Guide HP0-Y29: Installing an HP Networking IP Telephony Solution
 HP Certified Professional Program Exam Preparation Guide HP0-Y29: Installing an HP Networking IP Telephony Solution The intent of this guide is to set expectations about the context of the exam and to
HP Certified Professional Program Exam Preparation Guide HP0-Y29: Installing an HP Networking IP Telephony Solution The intent of this guide is to set expectations about the context of the exam and to
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Self- Paced Training Guide:
 Self- Paced Training Guide: You will need to have access to a QuickBooks Online Accountant (QBOA) dashboard before completing the course (if you already have access then you can refer to the link below).
Self- Paced Training Guide: You will need to have access to a QuickBooks Online Accountant (QBOA) dashboard before completing the course (if you already have access then you can refer to the link below).
EACEA. Call for experts. - Instructions for ECAS account creation -
 EACEA Call for experts - Instructions for ECAS account creation - Version 1, August 2013 1 Introduction The European Commission Authentication Service (ECAS) is the system that validates the identity of
EACEA Call for experts - Instructions for ECAS account creation - Version 1, August 2013 1 Introduction The European Commission Authentication Service (ECAS) is the system that validates the identity of
Course Outline. Managing Enterprise Devices and Apps using System Center Configuration ManagerCourse 20696B: 5 days Instructor Led
 Managing Enterprise Devices and Apps using System Center Configuration ManagerCourse 20696B: 5 days Instructor Led About this Course Get expert instruction and hands-on practice configuring and managing
Managing Enterprise Devices and Apps using System Center Configuration ManagerCourse 20696B: 5 days Instructor Led About this Course Get expert instruction and hands-on practice configuring and managing
HP Certified Professional
 Securing HP ProCurve Networks Exam HP0-Y24 Exam Preparation Guide Purpose The intent of this guide is to set expectations about the context of the exam and to help candidates prepare for it. Recommended
Securing HP ProCurve Networks Exam HP0-Y24 Exam Preparation Guide Purpose The intent of this guide is to set expectations about the context of the exam and to help candidates prepare for it. Recommended
For additional information and evaluation copies of Trend Micro products and services, visit our website at www.trendmicro.com.
 TM TREND MICRO, Incorporated is a pioneer in secure content and threat management. Founded in 1988, provides individuals and organizations of all sizes with award-winning security software, hardware, and
TM TREND MICRO, Incorporated is a pioneer in secure content and threat management. Founded in 1988, provides individuals and organizations of all sizes with award-winning security software, hardware, and
Xopero Backup Build your private cloud backup environment. Getting started
 Xopero Backup Build your private cloud backup environment Getting started 07.05.2015 List of contents Introduction... 2 Get Management Center... 2 Setup Xopero to work... 3 Change the admin password...
Xopero Backup Build your private cloud backup environment Getting started 07.05.2015 List of contents Introduction... 2 Get Management Center... 2 Setup Xopero to work... 3 Change the admin password...
Intelligent, Scalable Web Security
 Solution Overview Citrix and Trend Micro Intelligent, Scalable Web Security Application-Level Control, Load Balancing, High-Traffic Capacity Table of Contents The Challenge... 3 The Solution: Citrix NetScaler
Solution Overview Citrix and Trend Micro Intelligent, Scalable Web Security Application-Level Control, Load Balancing, High-Traffic Capacity Table of Contents The Challenge... 3 The Solution: Citrix NetScaler
http://docs.trendmicro.com/en-us/smb/worry-free-business-security.aspx
 Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
How to Request Access to the Commerce Contract Management System
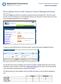 How to Request Access to the Commerce Contract Management System (one-time only) Once you ve logged into SAW, you can add your selected services by clicking on the Click here to add services link. This
How to Request Access to the Commerce Contract Management System (one-time only) Once you ve logged into SAW, you can add your selected services by clicking on the Click here to add services link. This
Managing Enterprise Devices and Apps using System Center Configuration Manager 20696B; 5 Days, Instructor-led
 Managing Enterprise Devices and Apps using System Center Configuration Manager 20696B; 5 Days, Instructor-led Course Description Get expert instruction and hands-on practice configuring and managing clients
Managing Enterprise Devices and Apps using System Center Configuration Manager 20696B; 5 Days, Instructor-led Course Description Get expert instruction and hands-on practice configuring and managing clients
Statement of Work Office 365 Migration. Gateway Unified School District
 May 07, 2013 Statement of Work Office 365 Migration Gateway Unified School District Prepared by: Nicholas Vossburg Prepared for: Scott Sorrells Statement
May 07, 2013 Statement of Work Office 365 Migration Gateway Unified School District Prepared by: Nicholas Vossburg Prepared for: Scott Sorrells Statement
Worry-FreeTM. Business Security Standard and Advanced Editions. Installation and Upgrade Guide. Administrator s Guide
 8 Worry-FreeTM Business Security Standard and Advanced Editions Securing Your Journey to the Cloud Administrator s Guide Installation and Upgrade Guide Trend Micro Incorporated reserves the right to make
8 Worry-FreeTM Business Security Standard and Advanced Editions Securing Your Journey to the Cloud Administrator s Guide Installation and Upgrade Guide Trend Micro Incorporated reserves the right to make
Getting Started with StoreGrid Cloud
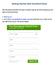 Getting Started with StoreGrid Cloud This document describes the steps to quickly sign up and start backing up your data to StoreGrid Cloud. I. Signing Up 1. Go to http://storegridcloud.vembu.com and select
Getting Started with StoreGrid Cloud This document describes the steps to quickly sign up and start backing up your data to StoreGrid Cloud. I. Signing Up 1. Go to http://storegridcloud.vembu.com and select
INCREASINGLY, ORGANIZATIONS ARE ASKING WHAT CAN T GO TO THE CLOUD, RATHER THAN WHAT CAN. Albin Penič Technical Team Leader Eastern Europe
 INCREASINGLY, ORGANIZATIONS ARE ASKING WHAT CAN T GO TO THE CLOUD, RATHER THAN WHAT CAN Albin Penič Technical Team Leader Eastern Europe Trend Micro 27 years focused on security software Headquartered
INCREASINGLY, ORGANIZATIONS ARE ASKING WHAT CAN T GO TO THE CLOUD, RATHER THAN WHAT CAN Albin Penič Technical Team Leader Eastern Europe Trend Micro 27 years focused on security software Headquartered
CNS-207 - Implementing NetScaler 11.0 For App and Desktop Solutions
 CNS-207 - Implementing NetScaler 11.0 For App and Desktop Solutions Overview The objective of this course is to provide the foundational concepts and teach the skills necessary to implement, configure,
CNS-207 - Implementing NetScaler 11.0 For App and Desktop Solutions Overview The objective of this course is to provide the foundational concepts and teach the skills necessary to implement, configure,
NHS Mail User Guide Guidance on the use of NHSmail for new users AJ O'connell (Sussex HIS) 05/11/2012 V1_4
 NHS Mail User Guide Guidance on the use of NHSmail for new users AJ O'connell (Sussex HIS) 05/11/2012 V1_4 NHS Mail User Guide Information Link: www.nhs.net NHS mail is an Encrypted Email system used by
NHS Mail User Guide Guidance on the use of NHSmail for new users AJ O'connell (Sussex HIS) 05/11/2012 V1_4 NHS Mail User Guide Information Link: www.nhs.net NHS mail is an Encrypted Email system used by
Installation runbook for StorageMadeEasy
 Installation runbook for StorageMadeEasy Test Result: Test Date: Partner Name: StorageMadeEasy Product Name: Product Version: 2.6.1 MOS Version: MOX Version (if applicable): OpenStack version: Product
Installation runbook for StorageMadeEasy Test Result: Test Date: Partner Name: StorageMadeEasy Product Name: Product Version: 2.6.1 MOS Version: MOX Version (if applicable): OpenStack version: Product
Cisco Certification Skills Matrix
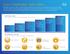 Cisco Certification Skills Matrix Whatever skills you need, IT networking professionals with Cisco Certifications have more to offer. Use this matrix to help evaluate candidates and make the perfect hire.
Cisco Certification Skills Matrix Whatever skills you need, IT networking professionals with Cisco Certifications have more to offer. Use this matrix to help evaluate candidates and make the perfect hire.
Endpoint protection for physical and virtual desktops
 datasheet Trend Micro officescan Endpoint protection for physical and virtual desktops In the bring-your-own-device (BYOD) environment, protecting your endpoints against ever-evolving threats has become
datasheet Trend Micro officescan Endpoint protection for physical and virtual desktops In the bring-your-own-device (BYOD) environment, protecting your endpoints against ever-evolving threats has become
TEAL and ECOS Access Instructions for Educators
 TEAL (TEA Login) is the security gateway to TEA web resources. To access your Educator Account, you will need a TEAL profile that is set up with access to your profile in the Educator Certification Online
TEAL (TEA Login) is the security gateway to TEA web resources. To access your Educator Account, you will need a TEAL profile that is set up with access to your profile in the Educator Certification Online
http://www.trendmicro.com/download
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
IRIS Software. Case Study
 IRIS Software Case Study ConsultCRM: IRIS Software ConsultCRM: IRIS Software The Company The Requirement IRIS is the UK s largest private software house with revenues of over 120m and more than 30 years
IRIS Software Case Study ConsultCRM: IRIS Software ConsultCRM: IRIS Software The Company The Requirement IRIS is the UK s largest private software house with revenues of over 120m and more than 30 years
Table of Contents. Table of Contents
 Table of Contents Setup Instructions... 1 Step 1: Download the Required Components... 1 Step 2: Install and Run the Online Backup Module... 3 Step 3: Sign-Up to the Online Backup Service... 4 Step 4: Configure
Table of Contents Setup Instructions... 1 Step 1: Download the Required Components... 1 Step 2: Install and Run the Online Backup Module... 3 Step 3: Sign-Up to the Online Backup Service... 4 Step 4: Configure
Cloud Services. Cloud Control Panel. Admin Guide
 Cloud Services Cloud Control Panel Admin Guide 10/18/2014 CONTENTS Description of Policy Based Encryption... 2 Policy Based Encryption and Email Content Control... 2 Features Summary... 3 Creating an Encryption
Cloud Services Cloud Control Panel Admin Guide 10/18/2014 CONTENTS Description of Policy Based Encryption... 2 Policy Based Encryption and Email Content Control... 2 Features Summary... 3 Creating an Encryption
PLUMgrid UNIVERSITY Advanced Training and Certification for OpenStack Networking
 U N I V E R S I T Y PLUMgrid UNIVERSITY Advanced Training and Certification for Networking PLUMgrid University Advanced Training for Networking has seen rapid growth over the past 5 years. Deployed by
U N I V E R S I T Y PLUMgrid UNIVERSITY Advanced Training and Certification for Networking PLUMgrid University Advanced Training for Networking has seen rapid growth over the past 5 years. Deployed by
Client Server Security3
 Client Server Security3 for Small and Medium Business Getting Started Guide Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
Client Server Security3 for Small and Medium Business Getting Started Guide Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
Intel Security Certified Product Specialist McAfee Network Security Platform (NSP)
 Intel Security Certified Product Specialist McAfee Network Security Platform (NSP) Why Get Intel Security Certified? As technology and security threats continue to evolve, organizations are looking for
Intel Security Certified Product Specialist McAfee Network Security Platform (NSP) Why Get Intel Security Certified? As technology and security threats continue to evolve, organizations are looking for
20696B: Administering System Center Configuration Manager and Intune
 20696B: Administering System Center Configuration Manager and Intune Course Details Course Code: Duration: Notes: 20696B 5 days This course syllabus should be used to determine whether the course is appropriate
20696B: Administering System Center Configuration Manager and Intune Course Details Course Code: Duration: Notes: 20696B 5 days This course syllabus should be used to determine whether the course is appropriate
Sichere bewegliche Arbeitskräfte Trend Micro Safe Mobile Workforce
 Sichere bewegliche Arbeitskräfte Trend Micro Safe Mobile Workforce Richard Javet, Partner Business Manager Gabriel Kälin, Technical Consultant Trend Micro Schweiz, August 2014 8/27/2014 Copyright 2013
Sichere bewegliche Arbeitskräfte Trend Micro Safe Mobile Workforce Richard Javet, Partner Business Manager Gabriel Kälin, Technical Consultant Trend Micro Schweiz, August 2014 8/27/2014 Copyright 2013
Migrating from Legacy to New Business Solutions
 Migrating from Legacy to New Business Solutions Thank you for your loyalty and for choosing the Newest Technology from Bitdefender. As we understand that this is an important step for your business, this
Migrating from Legacy to New Business Solutions Thank you for your loyalty and for choosing the Newest Technology from Bitdefender. As we understand that this is an important step for your business, this
Worry-FreeTM. Business Security Standard and Advanced Editions. System Requirements. Administrator s Guide. Securing Your Journey to the Cloud8
 Worry-FreeTM Business Security Standard and Advanced Editions Securing Your Journey to the Cloud8 Administrator s Guide System Requirements Trend Micro Incorporated reserves the right to make changes to
Worry-FreeTM Business Security Standard and Advanced Editions Securing Your Journey to the Cloud8 Administrator s Guide System Requirements Trend Micro Incorporated reserves the right to make changes to
Cisco Certified Network Associate (CCNA) Cisco Certified Network Associate (CCNA)
 Cisco Certified Network Associate (CCNA) CISCO Certification Path IIHT Nagpur is one of the best IT training Institutes that provides Cisco, Cloud Computing, hardware and networking courses. Address -
Cisco Certified Network Associate (CCNA) CISCO Certification Path IIHT Nagpur is one of the best IT training Institutes that provides Cisco, Cloud Computing, hardware and networking courses. Address -
How To Pass Polycom Cvvv
 INTRODUCTION The Polycom Certified Videoconferencing Engineer (PCVE) examination tests that the successful candidate has the necessary knowledge to perform implementation, configuration and troubleshooting
INTRODUCTION The Polycom Certified Videoconferencing Engineer (PCVE) examination tests that the successful candidate has the necessary knowledge to perform implementation, configuration and troubleshooting
THIRD PARTY USER GUIDE
 THIRD PARTY USER GUIDE Third Party User Guide Page 1 of 12 CONTENTS 1. INTRODUCTION... 3 2. INTENDED AUDIENCE... 3 3. ABOUT SiD... 3 4. HARDWARE & SOFTWARE REQUIREMENTS... 3 6. HOW TO ACCESS SiD VIA INTERNET...
THIRD PARTY USER GUIDE Third Party User Guide Page 1 of 12 CONTENTS 1. INTRODUCTION... 3 2. INTENDED AUDIENCE... 3 3. ABOUT SiD... 3 4. HARDWARE & SOFTWARE REQUIREMENTS... 3 6. HOW TO ACCESS SiD VIA INTERNET...
Websense Secure Messaging User Help
 Websense Secure Messaging User Help Welcome to Websense Secure Messaging, a tool that provides a secure portal for the transmission and viewing of sensitive, personal data in email. Use the portal to view
Websense Secure Messaging User Help Welcome to Websense Secure Messaging, a tool that provides a secure portal for the transmission and viewing of sensitive, personal data in email. Use the portal to view
OfficeScan Corporate Edition 6.5
 Press to Advance to Next Slide Copyright 2004 Trend Micro, Inc. OfficeScan Corporate Edition 6.5 Trend Micro Sales Training Module COURSE OBJECTIVES Welcome to Trend Micro s OfficeScan Corporate
Press to Advance to Next Slide Copyright 2004 Trend Micro, Inc. OfficeScan Corporate Edition 6.5 Trend Micro Sales Training Module COURSE OBJECTIVES Welcome to Trend Micro s OfficeScan Corporate
Learn.ITRAUMA.org Purchasing & Managing Licenses for Group Registration
 1. Visit http://learn.itrauma.org. Start by adding the product you wish to purchase in bulk to your cart. 2. On the Cart page, adjust the quantity to the number of licenses you wish to purchase and click
1. Visit http://learn.itrauma.org. Start by adding the product you wish to purchase in bulk to your cart. 2. On the Cart page, adjust the quantity to the number of licenses you wish to purchase and click
Trend Micro Licensing Program
 Press to Advance to Next Slide Copyright 2004 Trend Micro, Inc. Trend Micro Sales Training Module COURSE OBJECTIVES Welcome to the (TMLP) Sales Training Module! Trend Micro s licensing program
Press to Advance to Next Slide Copyright 2004 Trend Micro, Inc. Trend Micro Sales Training Module COURSE OBJECTIVES Welcome to the (TMLP) Sales Training Module! Trend Micro s licensing program
How To Protect A Virtual Desktop From Attack
 Endpoint Security: Become Aware of Virtual Desktop Infrastructures! An Ogren Group Special Report May 2011 Executive Summary Virtual desktops infrastructures, VDI, present IT with the unique opportunity
Endpoint Security: Become Aware of Virtual Desktop Infrastructures! An Ogren Group Special Report May 2011 Executive Summary Virtual desktops infrastructures, VDI, present IT with the unique opportunity
When your users take devices outside the corporate environment, these web security policies and defenses within your network no longer work.
 Deployment Guide Revision C McAfee Web Protection Hybrid Introduction Web Protection provides the licenses and software for you to deploy Web Gateway, SaaS Web Protection, or a hybrid deployment using
Deployment Guide Revision C McAfee Web Protection Hybrid Introduction Web Protection provides the licenses and software for you to deploy Web Gateway, SaaS Web Protection, or a hybrid deployment using
How to configure the TopCloudXL WHMCS plugin (version 2+) Update: 16-09-2015 Version: 2.2
 èè How to configure the TopCloudXL WHMCS plugin (version 2+) Update: 16-09-2015 Version: 2.2 Table of Contents 1. General overview... 3 1.1. Installing the plugin... 3 1.2. Testing the plugin with the
èè How to configure the TopCloudXL WHMCS plugin (version 2+) Update: 16-09-2015 Version: 2.2 Table of Contents 1. General overview... 3 1.1. Installing the plugin... 3 1.2. Testing the plugin with the
Quick Start Guide Migration Planner
 Quick Start Guide Table of Contents...3 10 Start... 3-4 Customer Info...5 Office 365...6 Review Accounts...7 End User...8 DNS...9 Final Review...10 1 Start Customer Info Office 365 Review Accounts Settings
Quick Start Guide Table of Contents...3 10 Start... 3-4 Customer Info...5 Office 365...6 Review Accounts...7 End User...8 DNS...9 Final Review...10 1 Start Customer Info Office 365 Review Accounts Settings
Trend Micro Solutions for PCI DSS Compliance
 s for PCI DSS Compliance A Trend Micro White Paper Addressing PCI DSS Requirements with Trend Micro Enterprise July 2010 I. PCI DSS AND TREND MICRO ENTERPRISE SECURITY Targeted threats, distributed environments,
s for PCI DSS Compliance A Trend Micro White Paper Addressing PCI DSS Requirements with Trend Micro Enterprise July 2010 I. PCI DSS AND TREND MICRO ENTERPRISE SECURITY Targeted threats, distributed environments,
ProvisionPoint Delegate Admin
 ProvisionPoint Delegate Admin Thursday, March 24, 2011 Contents ProvisionPoint Overview... 3 ProvisionPoint Login... 3 Invite New Users... 4 View New User Requests... 5 Quick Approve/Approve New User Requests...
ProvisionPoint Delegate Admin Thursday, March 24, 2011 Contents ProvisionPoint Overview... 3 ProvisionPoint Login... 3 Invite New Users... 4 View New User Requests... 5 Quick Approve/Approve New User Requests...
CLOUD CRUISER FOR WINDOWS AZURE PACK
 CLOUD CRUISER FOR WINDOWS AZURE PACK frequently asked questions 2013 Cloud Cruiser www.cloudcruiser.com OCTOBER 2013 PRODUCT FEATURES What is included with Cloud Cruiser Express? Cloud Cruiser Express
CLOUD CRUISER FOR WINDOWS AZURE PACK frequently asked questions 2013 Cloud Cruiser www.cloudcruiser.com OCTOBER 2013 PRODUCT FEATURES What is included with Cloud Cruiser Express? Cloud Cruiser Express
How to Register for Training
 How to Register for Training We have created a Training Console to help you manage your Tenable training from the Tenable Support Portal. You will be able to enroll in On Demand Training Course(s) or Certification
How to Register for Training We have created a Training Console to help you manage your Tenable training from the Tenable Support Portal. You will be able to enroll in On Demand Training Course(s) or Certification
INTEGRATION GUIDE. DIGIPASS Authentication for Juniper SSL-VPN
 INTEGRATION GUIDE DIGIPASS Authentication for Juniper SSL-VPN Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document is provided 'as is'; VASCO Data
INTEGRATION GUIDE DIGIPASS Authentication for Juniper SSL-VPN Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document is provided 'as is'; VASCO Data
Course MS20696A Managing Enterprise Devices and Apps using System Center Configuration Manager
 3 Riverchase Office Plaza Hoover, Alabama 35244 Phone: 205.989.4944 Fax: 855.317.2187 E-Mail: rwhitney@discoveritt.com Web: www.discoveritt.com Course MS20696A Managing Enterprise Devices and Apps using
3 Riverchase Office Plaza Hoover, Alabama 35244 Phone: 205.989.4944 Fax: 855.317.2187 E-Mail: rwhitney@discoveritt.com Web: www.discoveritt.com Course MS20696A Managing Enterprise Devices and Apps using
Employer Quick User Guideline
 The Hong Kong Institute of Education Employer Quick User Guideline URL: http://edjobplus.ied.edu.hk Step 1: Registration and Login Ed Job Plus 1. Select > Employer panel 2. Register a new account with
The Hong Kong Institute of Education Employer Quick User Guideline URL: http://edjobplus.ied.edu.hk Step 1: Registration and Login Ed Job Plus 1. Select > Employer panel 2. Register a new account with
HP Certified Professional
 HP Certified Professional HP Internet Security & e-commerce Solutions exam #HP1-805 Exam Preparation Guide Purpose of the Exam Preparation Guide Audience The intent of this guide is to set expectations
HP Certified Professional HP Internet Security & e-commerce Solutions exam #HP1-805 Exam Preparation Guide Purpose of the Exam Preparation Guide Audience The intent of this guide is to set expectations
Medical Professional Liability Insurance Claims Online User Manual
 Medical Professional Liability Insurance Claims Online User Manual Missouri Department of Insurance, Financial Institutions and Professional R egistration Contents Summary... 1 Site Address... 1 Account
Medical Professional Liability Insurance Claims Online User Manual Missouri Department of Insurance, Financial Institutions and Professional R egistration Contents Summary... 1 Site Address... 1 Account
!"#$ Stonington Public Schools Parents Guide for InfoSnap Online Enrollment. for Returning. Students. August. Online Enrollment.
 Stonington Public Schools Parents Guide for InfoSnap Online Enrollment for Returning Students August!"#$ Explains how to complete Returning Student Enrollment forms Online through the PowerSchool Parent
Stonington Public Schools Parents Guide for InfoSnap Online Enrollment for Returning Students August!"#$ Explains how to complete Returning Student Enrollment forms Online through the PowerSchool Parent
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme. This
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme. This
NU SSO Account Activation Job Aid NU Employees
 The purpose of this document is to provide National University Single Sign On users with instructions to activate their NU SSO accounts. Contents Employee Activation Self service... 1 Logging in directly...
The purpose of this document is to provide National University Single Sign On users with instructions to activate their NU SSO accounts. Contents Employee Activation Self service... 1 Logging in directly...
http://docs.trendmicro.com/en-us/enterprise/cloud-app-encryption-foroffice-365.aspx
 Trend Micro Incorporated reserves the right to make changes to this document and to the cloud service described herein without notice. Before installing and using the cloud service, review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the cloud service described herein without notice. Before installing and using the cloud service, review the readme files,
ONLINE LEVEL ONE UMPIRES COURSE CLUB AND ASSOCIATION FACT SHEET
 About the course The Level One Online Umpire s Course has been designed to assist umpires in achieving the necessary skills and knowledge to be an effective umpire and enjoy their officiating role. The
About the course The Level One Online Umpire s Course has been designed to assist umpires in achieving the necessary skills and knowledge to be an effective umpire and enjoy their officiating role. The
Trend ScanMail. for Microsoft Exchange. Quick Start Guide
 Trend ScanMail for Microsoft Exchange Quick Start Guide Trend ScanMail for Microsoft Exchange ScanMail for Exchange This Quick Start Guide provides a step-by-step guide to installing ScanMail for Exchange,
Trend ScanMail for Microsoft Exchange Quick Start Guide Trend ScanMail for Microsoft Exchange ScanMail for Exchange This Quick Start Guide provides a step-by-step guide to installing ScanMail for Exchange,
Virtual Cabinet Document Portal User Guide
 Virtual Cabinet Document Portal User Guide Contents / Introduction Introduction... 2 What to expect when publishing a document... 3 Having difficulty? Troubleshooting guide.... 7 The Virtual Cabinet Document
Virtual Cabinet Document Portal User Guide Contents / Introduction Introduction... 2 What to expect when publishing a document... 3 Having difficulty? Troubleshooting guide.... 7 The Virtual Cabinet Document
ESMO ONLINE EVENT REGISTRATION INSTRUCTION REGISTER YOURSELF
 ESMO ONLINE EVENT REGISTRATION INSTRUCTION REGISTER YOURSELF INDEX Preliminary information Registration requirements... Page 2 Individual registration 1. Account with ESMO... Page 3 2. Login into your
ESMO ONLINE EVENT REGISTRATION INSTRUCTION REGISTER YOURSELF INDEX Preliminary information Registration requirements... Page 2 Individual registration 1. Account with ESMO... Page 3 2. Login into your
ONSITE TRACK EASY Campbell Arnott s Contractor Management Portal Portal User Guide: Employee Registration & Induction Bookings
 ONSITE TRACK EASY Campbell Arnott s Contractor Management Portal Portal User Guide: Employee Registration & Induction Bookings http://campbellsarnottscontractor.com.au 1300 305 072 CONTENTS Overview...
ONSITE TRACK EASY Campbell Arnott s Contractor Management Portal Portal User Guide: Employee Registration & Induction Bookings http://campbellsarnottscontractor.com.au 1300 305 072 CONTENTS Overview...
FortyCloud Installation Guide. Installing FortyCloud Gateways Using AMIs (AWS Billing)
 FortyCloud Installation Guide Installing FortyCloud Gateways Using AMIs (AWS Billing) Date Version Changes 9/29/2015 2.0 2015 FortyCloud Ltd. 15 Berkshire Road Mansfield, MA 02048 USA 1 P a g e Introduction
FortyCloud Installation Guide Installing FortyCloud Gateways Using AMIs (AWS Billing) Date Version Changes 9/29/2015 2.0 2015 FortyCloud Ltd. 15 Berkshire Road Mansfield, MA 02048 USA 1 P a g e Introduction
CXD-202-1 Citrix XenDesktop 5 Administration
 CXD-202-1 Citrix XenDesktop 5 Administration This course provides the foundation necessary for administrators to effectively centralize and manage desktops in the datacenter and deliver them as a service
CXD-202-1 Citrix XenDesktop 5 Administration This course provides the foundation necessary for administrators to effectively centralize and manage desktops in the datacenter and deliver them as a service
Registering at the Securemail site
 Registering at the Securemail site Before using the Secure Mail service for the first time, you must perform a one-time service registration by completing the following steps. 1. When a Secure Mail is
Registering at the Securemail site Before using the Secure Mail service for the first time, you must perform a one-time service registration by completing the following steps. 1. When a Secure Mail is
Mimecast Large File Send
 DATASHEET Mimecast Large File Send For sending large files, lets go back to email Mimecast Large File Send simplifies large file sharing for users by removing the complexity and frustration associated
DATASHEET Mimecast Large File Send For sending large files, lets go back to email Mimecast Large File Send simplifies large file sharing for users by removing the complexity and frustration associated
Planning, Deploying, and Managing an Enterprise Project Management Solution
 Planning, Deploying, and Managing an Enterprise Project Management Solution Course 2732 Five days Instructor-led Introduction The goal of this five-day, instructor-led course is to provide systems engineers
Planning, Deploying, and Managing an Enterprise Project Management Solution Course 2732 Five days Instructor-led Introduction The goal of this five-day, instructor-led course is to provide systems engineers
How to Get Set Up for the 2014 BE-180 and Request an Extension if Needed
 How to Get Set Up for the 2014 BE-180 and Request an Extension if Needed For instructions on how to get set up for the 2014 BE-180 and to request an extension if one is needed, click on one of the links
How to Get Set Up for the 2014 BE-180 and Request an Extension if Needed For instructions on how to get set up for the 2014 BE-180 and to request an extension if one is needed, click on one of the links
Introducing Cisco Voice and Unified Communications Administration Course ICOMM v8.1; 5 Days, Instructor-led
 Introducing Cisco Voice and Unified Communications Administration Course ICOMM v8.1; 5 Days, Instructor-led Course Description Introducing Cisco Voice and Unified Communications Administration (ICOMM)
Introducing Cisco Voice and Unified Communications Administration Course ICOMM v8.1; 5 Days, Instructor-led Course Description Introducing Cisco Voice and Unified Communications Administration (ICOMM)
Microsoft Online Services from Bell. Welcome Kit
 Microsoft Online Services from Bell Welcome Kit Table of Contents Introduction... 3 Installing Microsoft Online Services from Bell... 3 1. Receive first welcome letter... 3 2. Sign Terms and Conditions...
Microsoft Online Services from Bell Welcome Kit Table of Contents Introduction... 3 Installing Microsoft Online Services from Bell... 3 1. Receive first welcome letter... 3 2. Sign Terms and Conditions...
Designing a Windows Server 2008 Applications Infrastructure
 Designing a Windows Server 2008 Applications Infrastructure Course 6437A : Three days; Instructor-Led Introduction This three day course will prepare IT professionals for the role of Enterprise Administrator.
Designing a Windows Server 2008 Applications Infrastructure Course 6437A : Three days; Instructor-Led Introduction This three day course will prepare IT professionals for the role of Enterprise Administrator.
Policy Based Encryption Gateway. Administration Guide
 Policy Based Encryption Gateway Administration Guide Document Revision Date: Sept. 11, 2012 Policy Based Encryption Gateway Admin Guide i Contents Description of Policy Based Encryption... 1 Policy Based
Policy Based Encryption Gateway Administration Guide Document Revision Date: Sept. 11, 2012 Policy Based Encryption Gateway Admin Guide i Contents Description of Policy Based Encryption... 1 Policy Based
Administering Windows Server 2012
 www.etidaho.com (208) 327-0768 Course 20411D: Administering Windows Server 2012 5 Days About this Course Get hands on instruction and practice administering Windows Server 2012, including Windows Server
www.etidaho.com (208) 327-0768 Course 20411D: Administering Windows Server 2012 5 Days About this Course Get hands on instruction and practice administering Windows Server 2012, including Windows Server
Kittys School Management System
 Management Module: Login Module: In this module site admin can be able to login by using their unique username and password. Add Section and Standard: Subject: Syllabus: Inbox: i. Admin can add the Standard
Management Module: Login Module: In this module site admin can be able to login by using their unique username and password. Add Section and Standard: Subject: Syllabus: Inbox: i. Admin can add the Standard
Experience IT. Let us describe the new experience.
 SysAid IT 8.5 1 Experience IT SysAid 8.5 enriches and improves the overall ITSM (IT Service Management) experience, focusing on: End-User Satisfaction Let us describe the new experience. 2 End-User Portal
SysAid IT 8.5 1 Experience IT SysAid 8.5 enriches and improves the overall ITSM (IT Service Management) experience, focusing on: End-User Satisfaction Let us describe the new experience. 2 End-User Portal
The web-based training (WBT) is a detailed training resource on Access Online functions. The WBT includes:
 The web-based training (WBT) is a detailed training resource on Access Online functions. The WBT includes: Interactive lessons Detailed user guides Quick references Recorded instructor-led classes Interactive
The web-based training (WBT) is a detailed training resource on Access Online functions. The WBT includes: Interactive lessons Detailed user guides Quick references Recorded instructor-led classes Interactive
Integrating Trend Micro OfficeScan 10 EventTracker v7.x
 Integrating Trend Micro OfficeScan 10 EventTracker v7.x Publication Date: August 26, 2015 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Abstract This guide will help you in
Integrating Trend Micro OfficeScan 10 EventTracker v7.x Publication Date: August 26, 2015 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Abstract This guide will help you in
IBM Systems Middleware Business Partner Sponsored Education Program - Self Paced Virtual Classes Overview & FAQs November, 2015 -- Version 7
 IBM Systems Middleware Business Partner Sponsored Education Program - Self Paced Virtual Classes Overview & FAQs November, 2015 -- Version 7 November 2015 Version 7 Contents Self Paced Virtual Course (SPVC)
IBM Systems Middleware Business Partner Sponsored Education Program - Self Paced Virtual Classes Overview & FAQs November, 2015 -- Version 7 November 2015 Version 7 Contents Self Paced Virtual Course (SPVC)
How to survive in a world of Virtualization and Cloud Computing, where you even can t trust your own environment anymore. Raimund Genes, CTO
 How to survive in a world of Virtualization and Cloud Computing, where you even can t trust your own environment anymore. Raimund Genes, CTO Data everywhere but protection? Unprotected Data Needing Protection
How to survive in a world of Virtualization and Cloud Computing, where you even can t trust your own environment anymore. Raimund Genes, CTO Data everywhere but protection? Unprotected Data Needing Protection
JANUARY 2015 EDUCATION PROGRAM GUIDE PARTNER PARTN ADVANTAGE
 JANUARY 2015 PARTN ADVANT EDUCATION PROGRAM GUIDE R S Table of Contents Introduction Sales Tracks Accreditation CommVault Sales Professional Accreditation...4 Knowledge Transfer Simpana Sales Enablement
JANUARY 2015 PARTN ADVANT EDUCATION PROGRAM GUIDE R S Table of Contents Introduction Sales Tracks Accreditation CommVault Sales Professional Accreditation...4 Knowledge Transfer Simpana Sales Enablement
Setup Corporate (Microsoft Exchange) Email. This tutorial will walk you through the steps of setting up your corporate email account.
 Setup Corporate (Microsoft Exchange) Email This tutorial will walk you through the steps of setting up your corporate email account. Microsoft Exchange Email Support Exchange Server Information You will
Setup Corporate (Microsoft Exchange) Email This tutorial will walk you through the steps of setting up your corporate email account. Microsoft Exchange Email Support Exchange Server Information You will
Support and Service Management Service Description
 Support and Service Management Service Description Business Productivity Online Suite - Standard Microsoft Exchange Online Standard Microsoft SharePoint Online Standard Microsoft Office Communications
Support and Service Management Service Description Business Productivity Online Suite - Standard Microsoft Exchange Online Standard Microsoft SharePoint Online Standard Microsoft Office Communications
Sophos Certified Architect Course overview
 Sophos Certified Architect Course overview UTM This course provides an in-depth study of UTM, designed for experienced technical professionals who will be planning, installing, configuring and supporting
Sophos Certified Architect Course overview UTM This course provides an in-depth study of UTM, designed for experienced technical professionals who will be planning, installing, configuring and supporting
Infor CRM Education on Infor Campus
 Infor CRM Education on Infor Campus Infor CRM courses are located on Infor Campus here! Instructions to locate and register for Infor CRM videos, non-certification, and certification courses are included
Infor CRM Education on Infor Campus Infor CRM courses are located on Infor Campus here! Instructions to locate and register for Infor CRM videos, non-certification, and certification courses are included
http://docs.trendmicro.com
 Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
