Importing and Using your Personal Authentication Certificate with Mozilla SeaMonkey Client (PC)
|
|
|
- Christina Bryan
- 10 years ago
- Views:
Transcription
1 Personal Authentication Certificates Importing and Using your Personal Authentication Certificate with Mozilla SeaMonkey Client (PC) If you originally applied for the certificate on the same computer as your SeaMonkey installation then it should already be installed. You can skip straight to 'Signing and Encrypting'. If your certificate is not already installed on the computer you are using, then please export it from the machine on which it resides using one of the browsers listed on the CPAC main page. You then need to transfer it to this computer ( it to yourself or save the certificate file to USB then copy over). You can then follow the 'import' instructions in this document. Importing your certificate into Mozilla SeaMonkey Signing and Encrypting mails Importing your Certificate into Mozilla SeaMonkey: 1. Open SeaMonkey and then click 'Edit' > 'Preferences'. 2. In the Preferences screen, select 'Privacy & Security' > 'Certificate' and then click the 'Manage Certificates...' button. 3. In the certificate manager interface, make sure the 'Your Certificates' tab is selected and click 'Import'. 1
2 2
3 4. Navigate to the location of the PKCS12 certificate file in which your certificate is stored and enter any necessary passwords. Your certificate will be imported and you will be able to use it to digitally sign and encrypt s. 5. Click OK in the Certificate Manager dialog to return to the Preferences screen. 6. Optional - select Ask me every time under When a server requests my personal certificate. Doing this alerts you to the fact that a server has requested identity confirmation and enables you to select your Comodo Personal Authentication Certificate. 7. Click OK in the Preferences interface to return to SeaMonkey. That's it. You have successfully imported your Comodo Personal Authentication certificate into Mozilla SeaMonkey. Signing and Encrypting Mails Signing an ensures the recipient knows the has come from you and informs them that it has not been modified in transit. Encrypting an ensures that only the recipient can read the content and attachments. Note: In order to encrypt mail, you must first have your recipient s certificate in your certificate store. To obtain their certificate, you need to get your contact to send you a signed . Upon receipt of the signed mail, their certificate will be automatically imported into your certificate store and you will be able to sign/encrypt mail to that person. Assign the certificate Signing and encrypting individual mails Signing and encrypting all mails by default Assign the certificate 1. Open SeaMonkey and select 'Edit' then 'Mail & Newsgroups Account Settings...'. 2. In the 'Mail & Newsgroups Account Settings' screen, select 'Security'. 3
4 3. Click 'Select' beside the text box in the 'Digital Signing' area and select your Comodo Personal Authentication certificate from the list. 4. Click 'OK'. 5. Select the same certificate for Encryption by clicking Yes in the confirmation dialog. 6. Click OK in the Mail & Newsgroups Account Settings interface to finalize your settings. Signing and encrypting individual mails To sign an individual mail: 1. Compose your and attach files as usual. 4
5 2. Click Security and choose Digitally Sign This Message. A pen icon will appear in the status bar, indicating that the message is digitally signed. 3. Click the Send button. To encrypt each mail: 1. Compose your and attach files as usual. 2. Ensure the recipient has a Digital Certificate and you have assigned the Certificate to their entry in your contacts area. 3. Click Security and choose Encrypt This Message. A key icon encrypted. will be displayed in the status bar indicating that the message and the attachments are 4. Click the Send button. Signing and Encrypting all mails by default: 5
6 1. Open SeaMonkey and then click 'Edit' > 'Mail & Newsgroups Account Settings'. 2. In the 'Mail & Newsgroups Account Settings' screen, select 'Security'. 3. Select the appropriate options in the 'Digital Signing' and 'Default Encryption Settings...' areas to sign and/or encrypt your mails by default. 4. As a rule of thumb, many users choose to digitally sign by default but only encrypt when sending a message which requires confidentiality. 5. Click 'OK'. 6
7 About Comodo The Comodo companies are leading global providers of Security, Identity and Trust Assurance services on the Internet. Comodo CA offers a comprehensive array of PKI Digital Certificates and Management Services, Identity and Content Authentication (Two-Factor - Multi-Factor) software, and Network Vulnerability Scanning and PCI compliance solutions. In addition, with over 10,000,000 installations of its threat prevention products, Comodo Security Solutions maintains an extensive suite of endpoint security software and services for businesses and consumers. Continual innovation, a core competence in PKI and a commitment to reversing the growth of Internet-crime distinguish the Comodo companies as vital players in the Internet's ongoing development. Comodo, with offices in the US, UK, China, India, Romania and the Ukraine, secures and authenticates the online transactions and communications for over 200,000 business customers and millions of consumers, providing the intelligent security, authentication and assurance services necessary for trust in on-line transactions. Comodo Security Solutions, Inc. Comodo CA Limited 1255 Broad Street 3rd floor, Office Village Exchange Quay Clifton, New Jersey United States Trafford Road, Salford, Manchester M5 3EQ United Kingdom Tel : Tel : +44 (0) Tel : Fax : +44 (0) [email protected] For additional information on Comodo - visit 7
Importing and Using your Personal Authentication Certificate with Outlook 2010 / 2013
 Personal Authentication Certificates Importing and Using your Personal Authentication Certificate with Outlook 2010 / 2013 If you originally applied for the certificate on the same computer as your Outlook
Personal Authentication Certificates Importing and Using your Personal Authentication Certificate with Outlook 2010 / 2013 If you originally applied for the certificate on the same computer as your Outlook
Importing and using your Personal Authentication Certificate with Djigzo for Android
 Personal Authentication Certificates Importing and using your Personal Authentication Certificate with Djigzo for Android Djigzo is a third party mobile application that provides S/MIME services which
Personal Authentication Certificates Importing and using your Personal Authentication Certificate with Djigzo for Android Djigzo is a third party mobile application that provides S/MIME services which
Importing and Using your Personal Authentication Certificate with Mac OS X Mail / Apple Mail
 Personal Authentication Certificates Importing and Using your Personal Authentication Certificate with Mac OS X Mail / Apple Mail If you originally applied for the certificate on the same computer as your
Personal Authentication Certificates Importing and Using your Personal Authentication Certificate with Mac OS X Mail / Apple Mail If you originally applied for the certificate on the same computer as your
Comodo One Software Version 1.8
 rat Comodo One Software Version 1.8 Service Desk End-User Guide Guide Version 1.8.090715 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Introduction to Service Desk Module Comodo Service
rat Comodo One Software Version 1.8 Service Desk End-User Guide Guide Version 1.8.090715 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Introduction to Service Desk Module Comodo Service
rat Comodo One Software Version 1.0 Administrator Guide Guide Version 1.0.071315 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013
 rat Comodo One Software Version 1.0 Administrator Guide Guide Version 1.0.071315 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo One... 3 2 Signing
rat Comodo One Software Version 1.0 Administrator Guide Guide Version 1.0.071315 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo One... 3 2 Signing
Importing your Personal Authentication Certificate to Android Devices
 Personal Authentication Certificates Importing your Personal Authentication Certificate to Android Devices This document explains how you can import your CPAC onto Android devices. Background notes The
Personal Authentication Certificates Importing your Personal Authentication Certificate to Android Devices This document explains how you can import your CPAC onto Android devices. Background notes The
Comodo Mobile Device Manager Software Version 1.0
 Comodo Mobile Device Manager Software Version 1.0 End User Guide Guide Version 1.0.022614 Comodo Security Solutions 1255 Broad Street STE 100 Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo
Comodo Mobile Device Manager Software Version 1.0 End User Guide Guide Version 1.0.022614 Comodo Security Solutions 1255 Broad Street STE 100 Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo
Enterprise Public Key Infrastructure (EPKI) Manager. Version 3.5
 Enterprise Public Key Infrastructure (EPKI) Manager For issuance & management of Enterprise - wide SSL Certificates & Secure Email (S/MIME) Certificates Introduction: Comodo s EPKI Manager is a web-based
Enterprise Public Key Infrastructure (EPKI) Manager For issuance & management of Enterprise - wide SSL Certificates & Secure Email (S/MIME) Certificates Introduction: Comodo s EPKI Manager is a web-based
Comodo Web Application Firewall for Plesk Software Version 2.11
 2 Comodo Web Application Firewall for Plesk Software Version 2.11 Administrator Guide Guide Version 2.11.071315 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Comodo
2 Comodo Web Application Firewall for Plesk Software Version 2.11 Administrator Guide Guide Version 2.11.071315 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Comodo
Comodo MyDLP Software Version 2.0. Endpoint Installation Guide Guide Version 2.0.010215. Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013
 Comodo MyDLP Software Version 2.0 Endpoint Installation Guide Guide Version 2.0.010215 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.About MyDLP... 3 1.1.MyDLP Features...
Comodo MyDLP Software Version 2.0 Endpoint Installation Guide Guide Version 2.0.010215 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.About MyDLP... 3 1.1.MyDLP Features...
Importing and exporting your certificate using Internet Explorer
 Personal Authentication Certificates Importing and exporting your certificate using Internet Explorer This document explains how you can use Internet Explorer to import or export an existing CPAC certificate.
Personal Authentication Certificates Importing and exporting your certificate using Internet Explorer This document explains how you can use Internet Explorer to import or export an existing CPAC certificate.
Comodo Endpoint Security Manager SME Software Version 2.1
 Comodo Endpoint Security Manager SME Software Version 2.1 Quick Start Guide Guide Version 2.1.111114 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Endpoint Security Manager - SME Quick
Comodo Endpoint Security Manager SME Software Version 2.1 Quick Start Guide Guide Version 2.1.111114 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Endpoint Security Manager - SME Quick
Comodo LoginPro Software Version 1.5
 Comodo LoginPro Software Version 1.5 User Guide Guide Version 1.5.030513 Comodo Security Solutions 1255 Broad Street STE 100 Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo LoginPro... 3 1.1.System
Comodo LoginPro Software Version 1.5 User Guide Guide Version 1.5.030513 Comodo Security Solutions 1255 Broad Street STE 100 Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo LoginPro... 3 1.1.System
Domain Control Validation in Comodo Certificate Manager
 Domain Control Validation in Comodo Certificate Manager The purpose of this document is to explain the new domain control validation (DCV) processes for the Comodo Certificate Manager. DCV is an industry
Domain Control Validation in Comodo Certificate Manager The purpose of this document is to explain the new domain control validation (DCV) processes for the Comodo Certificate Manager. DCV is an industry
Comodo MyDLP Software Version 2.0. Installation Guide Guide Version 2.0.010215. Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013
 Comodo MyDLP Software Version 2.0 Installation Guide Guide Version 2.0.010215 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.About MyDLP... 3 1.1.MyDLP Features... 3
Comodo MyDLP Software Version 2.0 Installation Guide Guide Version 2.0.010215 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.About MyDLP... 3 1.1.MyDLP Features... 3
Comodo Mobile Device Manager Software Version 3.0
 Comodo Mobile Device Manager Software Version 3.0 CMDM Cloud Portal Setup Guide Guide Version 3.0.010515 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Comodo Mobile Device Manager - Cloud
Comodo Mobile Device Manager Software Version 3.0 CMDM Cloud Portal Setup Guide Guide Version 3.0.010515 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Comodo Mobile Device Manager - Cloud
PCI Security Compliance
 E N T E R P R I S E Enterprise Security Solutions PCI Security Compliance : What PCI security means for your business The Facts Comodo HackerGuardian TM PCI and the Online Merchant Overview The Payment
E N T E R P R I S E Enterprise Security Solutions PCI Security Compliance : What PCI security means for your business The Facts Comodo HackerGuardian TM PCI and the Online Merchant Overview The Payment
Comodo ONE Software Version 1.8
 rat Comodo ONE Software Version 1.8 RMM - Bulk Enrollment via Active Directory Guide Version 1.8.020216 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 RMM Bulk Enrollment via Active Directory
rat Comodo ONE Software Version 1.8 RMM - Bulk Enrollment via Active Directory Guide Version 1.8.020216 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 RMM Bulk Enrollment via Active Directory
Comodo Mobile Device Manager Software Version 1.0
 Comodo Mobile Device Manager Software Version 1.0 Installation Guide Guide Version 1.0.041114 Comodo Security Solutions 1255 Broad Street STE 100 Clifton, NJ 07013 Table of Contents 1.CMDM Setup... 3 1.1.System
Comodo Mobile Device Manager Software Version 1.0 Installation Guide Guide Version 1.0.041114 Comodo Security Solutions 1255 Broad Street STE 100 Clifton, NJ 07013 Table of Contents 1.CMDM Setup... 3 1.1.System
Web Host Reseller Program
 How To Use Your Account To Implement and Start Selling SSL Through The Web Host Program Version 2.4 Introduction: The Comodo Web Host Reseller Program gives you the unique ability to integrate the Comodo
How To Use Your Account To Implement and Start Selling SSL Through The Web Host Program Version 2.4 Introduction: The Comodo Web Host Reseller Program gives you the unique ability to integrate the Comodo
Comodo Certificate Manager Software Version 4.5
 Comodo Certificate Manager Software Version 4.5 Windows Auto Enrollment Setup Guide Guide Version 4.5.052714 Comodo CA Limited 3rd Floor, 26 Office Village, Exchange Quay, Trafford Road, Salford, Greater
Comodo Certificate Manager Software Version 4.5 Windows Auto Enrollment Setup Guide Guide Version 4.5.052714 Comodo CA Limited 3rd Floor, 26 Office Village, Exchange Quay, Trafford Road, Salford, Greater
Comodo Web Application Firewall Software Version 2.11
 2 Comodo Web Application Firewall Software Version 2.11 Quick Start Guide Guide Version 2.11.071315 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 1.Comodo Web Application Firewall - Quick
2 Comodo Web Application Firewall Software Version 2.11 Quick Start Guide Guide Version 2.11.071315 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 1.Comodo Web Application Firewall - Quick
Comodo Mobile Security for Android Software Version 3.0
 Comodo Mobile Security for Android Software Version 3.0 User Guide Guide Version 3.0.042115 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo Mobile
Comodo Mobile Security for Android Software Version 3.0 User Guide Guide Version 3.0.042115 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo Mobile
Comodo Cloud Drive Software Version 1.0
 2 Comodo Cloud Drive Software Version 1.0 User Guide Guide Version 1.0.101414 Comodo Security Solutions 1255 Broad Street STE 100 Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo Cloud Drive...
2 Comodo Cloud Drive Software Version 1.0 User Guide Guide Version 1.0.101414 Comodo Security Solutions 1255 Broad Street STE 100 Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo Cloud Drive...
Comodo HackerGuardian. PCI Security Compliance The Facts. What PCI security means for your business
 Comodo HackerGuardian PCI Security Compliance The Facts What PCI security means for your business Overview The Payment Card Industry Data Security Standard (PCI DSS) is a set of 12 requirements intended
Comodo HackerGuardian PCI Security Compliance The Facts What PCI security means for your business Overview The Payment Card Industry Data Security Standard (PCI DSS) is a set of 12 requirements intended
Encrypting Your Email Using the free COMODO Secure Email Certificate
 Encrypting Your Email Using the free COMODO Secure Email Certificate These instructions will guide you through the process of getting a free Secure Email Certificate Issued by COMODO. This document will
Encrypting Your Email Using the free COMODO Secure Email Certificate These instructions will guide you through the process of getting a free Secure Email Certificate Issued by COMODO. This document will
HomeConvenience.com. Creating Trust Online CASE STUDY. Comodo Identity and Trust Assurance Suite. Content Verification Certificate.
 TM Creating Trust Online CASE STUDY HomeConvenience.com Comodo Identity and Trust Assurance Suite Content Verification Certificate Hacker Guardian SSL Certification Corner of Trust Logo Who are HomeConvenience?
TM Creating Trust Online CASE STUDY HomeConvenience.com Comodo Identity and Trust Assurance Suite Content Verification Certificate Hacker Guardian SSL Certification Corner of Trust Logo Who are HomeConvenience?
Driving Company Security is Challenging. Centralized Management Makes it Simple.
 Driving Company Security is Challenging. Centralized Management Makes it Simple. Overview - P3 Security Threats, Downtime and High Costs - P3 Threats to Company Security and Profitability - P4 A Revolutionary
Driving Company Security is Challenging. Centralized Management Makes it Simple. Overview - P3 Security Threats, Downtime and High Costs - P3 Threats to Company Security and Profitability - P4 A Revolutionary
Installing your certificate on your Windows PC
 Installing your certificate on your PC Choose your email software below to learn how to obtain and install a digital certificate. Microsoft Outlook Mail Using Outlook or Mail Step one Visit Comodo for
Installing your certificate on your PC Choose your email software below to learn how to obtain and install a digital certificate. Microsoft Outlook Mail Using Outlook or Mail Step one Visit Comodo for
Comodo Certificate Manager. Centrally Managing Enterprise Security, Trust & Compliance
 Centrally Managing Enterprise Security, Trust & Compliance SSL Certificate Management - PKI With an ever-increasing abundance of web-enabled, collaborative and mobile applications, as well as netaccessible
Centrally Managing Enterprise Security, Trust & Compliance SSL Certificate Management - PKI With an ever-increasing abundance of web-enabled, collaborative and mobile applications, as well as netaccessible
Comodo 2048 bit SSL Certificates. Security for your online business now and long into the future
 Security for your online business now and long into the future Today, online commerce is worth over US $1 trillion and continues to grow at a substantial rate. are an indispensable cornerstone of this
Security for your online business now and long into the future Today, online commerce is worth over US $1 trillion and continues to grow at a substantial rate. are an indispensable cornerstone of this
Comodo Certificate Manager Software Version 4.8
 Comodo Certificate Manager Software Version 4.8 SSL Web Service API Guide Version 4.8.010215 Comodo CA Limited 3rd Floor, 26 Office Village, Exchange Quay, Trafford Road, Salford, Greater Manchester M5
Comodo Certificate Manager Software Version 4.8 SSL Web Service API Guide Version 4.8.010215 Comodo CA Limited 3rd Floor, 26 Office Village, Exchange Quay, Trafford Road, Salford, Greater Manchester M5
Comodo Certificate Manager Software Version 5.0
 Comodo Certificate Manager Software Version 5.0 SSL Web Service API Guide Version 5.0.042015 Comodo CA Limited 3rd Floor, 26 Office Village, Exchange Quay, Trafford Road, Salford, Greater Manchester M5
Comodo Certificate Manager Software Version 5.0 SSL Web Service API Guide Version 5.0.042015 Comodo CA Limited 3rd Floor, 26 Office Village, Exchange Quay, Trafford Road, Salford, Greater Manchester M5
Comodo Certificate Manager. Comodo Enterprise
 Comodo Certificate Manager Comodo Enterprise Challenges Enterprises lose track of the SSL certificates on their websites Expired SSL certificates go unnoticed, which leads to customers seeing browser error
Comodo Certificate Manager Comodo Enterprise Challenges Enterprises lose track of the SSL certificates on their websites Expired SSL certificates go unnoticed, which leads to customers seeing browser error
Comodo SecureEmail Version 2.6
 Comodo SecureEmail Version 2.6 Version 2.6.120710 i 3 rd Comodo CA Limited Floor, 26 Office Village, Exchange Quay, Trafford Road, Salford, Great Manchester M5 3EQ, United Kingdom. Table of Contents 1
Comodo SecureEmail Version 2.6 Version 2.6.120710 i 3 rd Comodo CA Limited Floor, 26 Office Village, Exchange Quay, Trafford Road, Salford, Great Manchester M5 3EQ, United Kingdom. Table of Contents 1
Why strong Validation processes for SSL are essential for the preservation of trust in the Internet economy
 Why strong Validation processes for SSL are essential for the preservation of trust in the Internet economy Weak validation processes undermine the value of SSL as a trust enabling technology Introduction
Why strong Validation processes for SSL are essential for the preservation of trust in the Internet economy Weak validation processes undermine the value of SSL as a trust enabling technology Introduction
SECURE EMAIL USER GUIDE OUTLOOK 2000
 WELLS FARGO AUTHENTICATION SERVICES DATED: MAY 2003 TABLE OF CONTENTS GENERAL INFORMATION... 1 INSTALLING THE WELLS FARGO ROOT CERTIFICATE CHAIN.. 2 INSTALLING THE CERTIFICATES INTO IE... 3 SETTING UP
WELLS FARGO AUTHENTICATION SERVICES DATED: MAY 2003 TABLE OF CONTENTS GENERAL INFORMATION... 1 INSTALLING THE WELLS FARGO ROOT CERTIFICATE CHAIN.. 2 INSTALLING THE CERTIFICATES INTO IE... 3 SETTING UP
Initial Setup of Mozilla Thunderbird with IMAP for Windows 7
 Initial Setup of Mozilla Thunderbird Concept This document describes the procedures for setting up the Mozilla Thunderbird email client to download messages from Google Mail using Internet Message Access
Initial Setup of Mozilla Thunderbird Concept This document describes the procedures for setting up the Mozilla Thunderbird email client to download messages from Google Mail using Internet Message Access
Reading an email sent with Voltage SecureMail. Using the Voltage SecureMail Zero Download Messenger (ZDM)
 Reading an email sent with Voltage SecureMail Using the Voltage SecureMail Zero Download Messenger (ZDM) SecureMail is an email protection service developed by Voltage Security, Inc. that provides email
Reading an email sent with Voltage SecureMail Using the Voltage SecureMail Zero Download Messenger (ZDM) SecureMail is an email protection service developed by Voltage Security, Inc. that provides email
Powerful, customizable protection for web applications and websites running ModSecurity on Apache/Linux based web-servers
 Free ModSecurity Rules from Comodo Powerful, customizable protection for web applications and websites running ModSecurity on Apache/Linux based web-servers This document is for informational purposes
Free ModSecurity Rules from Comodo Powerful, customizable protection for web applications and websites running ModSecurity on Apache/Linux based web-servers This document is for informational purposes
Using Websense Data Endpoint Client Software
 1 Using Websense Data Endpoint Client Software Related topics: Disabling the endpoint client, page 3 Viewing contained files, page 5 Viewing logs, page 6 Updating the endpoint client, page 7 Your organization
1 Using Websense Data Endpoint Client Software Related topics: Disabling the endpoint client, page 3 Viewing contained files, page 5 Viewing logs, page 6 Updating the endpoint client, page 7 Your organization
Setting up Email in Outlook Express
 Setting up Email in Outlook Express If you have more than one email account but need to use a single computer to access them, then Outlook Express can help. To begin, open Outlook Express by double-clicking
Setting up Email in Outlook Express If you have more than one email account but need to use a single computer to access them, then Outlook Express can help. To begin, open Outlook Express by double-clicking
Internet E-Mail Encryption S/Mime Standard
 Internet E-Mail Encryption S/Mime Standard Disclaimer: Successfully setting up encryption functions in most e-mail clients is usually not a problematic task. However, it should be noted that, when configuring
Internet E-Mail Encryption S/Mime Standard Disclaimer: Successfully setting up encryption functions in most e-mail clients is usually not a problematic task. However, it should be noted that, when configuring
Adding Digital Signature and Encryption in Outlook
 Adding Digital Signature and Encryption in Outlook Using Outlook, the email messages can be signed and encrypted by a digital certificate. To digitally sign a message in Outlook some conditions must be
Adding Digital Signature and Encryption in Outlook Using Outlook, the email messages can be signed and encrypted by a digital certificate. To digitally sign a message in Outlook some conditions must be
Email Account Create for Outlook Express
 Email Account Create for Outlook Express Click Start Menu Choose Outlook Express Click Tools menu from Menu Bar and then click Accounts In Internet Account Wizard, Click Add Button and Click Mail. 1 In
Email Account Create for Outlook Express Click Start Menu Choose Outlook Express Click Tools menu from Menu Bar and then click Accounts In Internet Account Wizard, Click Add Button and Click Mail. 1 In
Creating Trust Online TM. Identity & Trust Assurance in a changing standards environment. *(Extended Validation)
 Creating Trust Online TM Identity & Trust Assurance in a changing standards environment. *(Extended Validation) Introduction Today, online commerce is worth an estimated US $1 trillion and continues to
Creating Trust Online TM Identity & Trust Assurance in a changing standards environment. *(Extended Validation) Introduction Today, online commerce is worth an estimated US $1 trillion and continues to
User Guide Using Certificate in Microsoft Outlook Express
 CERTIFYING AUTHORITY User Guide Using Certificate in Microsoft Outlook Express CONTACT TATA CONSULTANCY SERVICES - [E-SECURITY: PKI SERVICES] 6TH FLOOR, 5-9-62, KHAN LATEEF KHAN ESTATE FATEH MAIDAN ROAD,
CERTIFYING AUTHORITY User Guide Using Certificate in Microsoft Outlook Express CONTACT TATA CONSULTANCY SERVICES - [E-SECURITY: PKI SERVICES] 6TH FLOOR, 5-9-62, KHAN LATEEF KHAN ESTATE FATEH MAIDAN ROAD,
Endpoint Security and the Case For Automated Sandboxing
 WHITE PAPER Endpoint Security and the Case For Automated Sandboxing https://enterprise.comodo.com A World of Constant Threat We live in a world of constant threat. Hackers around the globe work every hour
WHITE PAPER Endpoint Security and the Case For Automated Sandboxing https://enterprise.comodo.com A World of Constant Threat We live in a world of constant threat. Hackers around the globe work every hour
Guide for Securing E-mail With WISeKey CertifyID Personal Digital Certificate (Personal eid)
 The World Internet Security Company Solutions for Security Guide for Securing E-mail With WISeKey CertifyID Personal Digital Certificate (Personal eid) Wherever Security relies on Identity, WISeKey has
The World Internet Security Company Solutions for Security Guide for Securing E-mail With WISeKey CertifyID Personal Digital Certificate (Personal eid) Wherever Security relies on Identity, WISeKey has
Importing your personal certificate(s) to Microsoft Internet Explorer from a Back-up (or export) file
 Importing your personal certificate(s) to Microsoft Internet Explorer from a Back-up (or export) file You may use your Medium Assurance Certificate(s) on any computer that you wish to by importing them
Importing your personal certificate(s) to Microsoft Internet Explorer from a Back-up (or export) file You may use your Medium Assurance Certificate(s) on any computer that you wish to by importing them
Yale Software Library
 Yale Software Library http://www.yale.edu/its/software/ For assistance contact the ITS Help Desk 203-432-9000, [email protected] Two-factor authentication: Installation and configuration instructions for
Yale Software Library http://www.yale.edu/its/software/ For assistance contact the ITS Help Desk 203-432-9000, [email protected] Two-factor authentication: Installation and configuration instructions for
Guide to Obtaining Your Free WISeKey CertifyID Personal Digital Certificate (Personal eid) WISeKey 2010 / Alinghi 2010 Smartcards
 The World Internet Security Company Solutions for Security Guide to Obtaining Your Free WISeKey CertifyID Personal Digital Certificate (Personal eid) WISeKey 2010 / Alinghi 2010 Smartcards Wherever Security
The World Internet Security Company Solutions for Security Guide to Obtaining Your Free WISeKey CertifyID Personal Digital Certificate (Personal eid) WISeKey 2010 / Alinghi 2010 Smartcards Wherever Security
Guide to Obtaining Your Free WISeKey CertifyID Personal Digital Certificate on Aladdin etoken (Personal eid)
 The World Internet Security Company Solutions for Security Guide to Obtaining Your Free WISeKey CertifyID Personal Digital Certificate on Aladdin etoken (Personal eid) Wherever Security relies on Identity,
The World Internet Security Company Solutions for Security Guide to Obtaining Your Free WISeKey CertifyID Personal Digital Certificate on Aladdin etoken (Personal eid) Wherever Security relies on Identity,
Instructions for Microsoft Outlook 2003
 ElkhartNet, Inc. is dedicated to providing our email customers with excellent service and support. In a targeted effort to reduce SPAM and to provide more secure and faster email, we are changing our outgoing
ElkhartNet, Inc. is dedicated to providing our email customers with excellent service and support. In a targeted effort to reduce SPAM and to provide more secure and faster email, we are changing our outgoing
Use the below instructions to configure your wireless settings to connect to the secure wireless network using Microsoft Windows Vista/7.
 Use the below instructions to configure your wireless settings to connect to the secure wireless network using Microsoft Windows Vista/7. 1. Click the Windows Start button, then Control Panel How-To-WCC-Secure-Windows-7-11/4/2010-4:09
Use the below instructions to configure your wireless settings to connect to the secure wireless network using Microsoft Windows Vista/7. 1. Click the Windows Start button, then Control Panel How-To-WCC-Secure-Windows-7-11/4/2010-4:09
Using Entrust certificates with Microsoft Office and Windows
 Entrust Managed Services PKI Using Entrust certificates with Microsoft Office and Windows Document issue: 1.0 Date of issue: May 2009 Copyright 2009 Entrust. All rights reserved. Entrust is a trademark
Entrust Managed Services PKI Using Entrust certificates with Microsoft Office and Windows Document issue: 1.0 Date of issue: May 2009 Copyright 2009 Entrust. All rights reserved. Entrust is a trademark
Hyperoo 2.0 A (Very) Quick Start
 Hyperoo 2.0 A (Very) Quick Start Download and install the Hyperoo 2.0 beta Hyperoo 2.0 is a client/server based application and as such requires that you install both the Hyperoo Client and Hyperoo Server
Hyperoo 2.0 A (Very) Quick Start Download and install the Hyperoo 2.0 beta Hyperoo 2.0 is a client/server based application and as such requires that you install both the Hyperoo Client and Hyperoo Server
Here are the steps to configure Outlook Express for use with Salmar's Zimbra server. Select "Tools" and then "Accounts from the pull down menu.
 Salmar Consulting Inc. Setting up Outlook Express to use Zimbra Marcel Gagné, February 2010 Here are the steps to configure Outlook Express for use with Salmar's Zimbra server. Open Outlook Express. Select
Salmar Consulting Inc. Setting up Outlook Express to use Zimbra Marcel Gagné, February 2010 Here are the steps to configure Outlook Express for use with Salmar's Zimbra server. Open Outlook Express. Select
How to Setup your E-mail Account -Apple Mail for Mac OS X 1- Open Mail
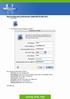 How to Setup your E-mail Account -Apple Mail for Mac OS X 1- Open Mail 2- The welcome screen will appear as follow: Fill in the above information as follow Full Name: type your display name E-Mail address:
How to Setup your E-mail Account -Apple Mail for Mac OS X 1- Open Mail 2- The welcome screen will appear as follow: Fill in the above information as follow Full Name: type your display name E-Mail address:
IMPORTING AND EXPORTING CERTIFICATES IN IE AND FIREFOX FOR BPIA AND PRACS
 IMPORTING AND EXPORTING CERTIFICATES IN IE AND FIREFOX FOR BPIA AND PRACS Exporting a certificate is useful for keeping a backup copy of your certificate or for importing it to another browser (either
IMPORTING AND EXPORTING CERTIFICATES IN IE AND FIREFOX FOR BPIA AND PRACS Exporting a certificate is useful for keeping a backup copy of your certificate or for importing it to another browser (either
CHARTER BUSINESS custom hosting faqs 2010 INTERNET. Q. How do I access my email? Q. How do I change or reset a password for an email account?
 Contents Page Q. How do I access my email? Q. How do I change or reset a password for an email account? Q. How do I forward or redirect my messages to a different email address? Q. How do I set up an auto-reply
Contents Page Q. How do I access my email? Q. How do I change or reset a password for an email account? Q. How do I forward or redirect my messages to a different email address? Q. How do I set up an auto-reply
Comodo Certificate Manager Version 5.4
 Comodo Certificate Manager Version 5.4 Comodo Certificate Authority Proxy Server Architectural Overview Guide Version 5.4.031816 Comodo CA Limited 3rd Floor, 26 Office Village, Exchange Quay, Trafford
Comodo Certificate Manager Version 5.4 Comodo Certificate Authority Proxy Server Architectural Overview Guide Version 5.4.031816 Comodo CA Limited 3rd Floor, 26 Office Village, Exchange Quay, Trafford
Overview. Comodo Certificate Manager
 Overview Comodo Certificate Manager SSL CERTIFICATE MANAGEMENT Streamlined Tracking and Management of Enterprise Certificate Lifecycles, Security and Compliance Loss of control over SSL certificate inventory
Overview Comodo Certificate Manager SSL CERTIFICATE MANAGEMENT Streamlined Tracking and Management of Enterprise Certificate Lifecycles, Security and Compliance Loss of control over SSL certificate inventory
Prerequisite. Getting Started. Email Signing and Encryption using Microsoft outlook 2007
 Email Signing and Encryption using Microsoft outlook 2007 Prerequisite a. The user s email account has been added and correctly configured into Microsoft outlook. b. The user has an authentication certificate.
Email Signing and Encryption using Microsoft outlook 2007 Prerequisite a. The user s email account has been added and correctly configured into Microsoft outlook. b. The user has an authentication certificate.
Using etoken for SSL Web Authentication. SSL V3.0 Overview
 Using etoken for SSL Web Authentication Lesson 12 April 2004 etoken Certification Course SSL V3.0 Overview Secure Sockets Layer protocol, version 3.0 Provides communication privacy over the internet. Prevents
Using etoken for SSL Web Authentication Lesson 12 April 2004 etoken Certification Course SSL V3.0 Overview Secure Sockets Layer protocol, version 3.0 Provides communication privacy over the internet. Prevents
etoken Enterprise For: SSL SSL with etoken
 etoken Enterprise For: SSL SSL with etoken System Requirements Windows 2000 Internet Explorer 5.0 and above Netscape 4.6 and above etoken R2 or Pro key Install etoken RTE Certificates from: (click on the
etoken Enterprise For: SSL SSL with etoken System Requirements Windows 2000 Internet Explorer 5.0 and above Netscape 4.6 and above etoken R2 or Pro key Install etoken RTE Certificates from: (click on the
Getting a Free Comodo Email Certificate
 Getting a Free Comodo Email Certificate Go here and click on Get It Free Now button. http://www.instantssl.com/ssl certificate products/free email certificate.html It will take you to this form which you
Getting a Free Comodo Email Certificate Go here and click on Get It Free Now button. http://www.instantssl.com/ssl certificate products/free email certificate.html It will take you to this form which you
Outlook Express. Make Changes in Red: Open up Outlook Express. From the Menu Bar. Tools to Accounts - Click on Mail Tab.
 Outlook Express Open up Outlook Express From the Menu Bar Tools to Accounts - Click on Mail Tab Click on mail.nefcom.net (default) Click on Properties button Click on the General tab User Information E-mail
Outlook Express Open up Outlook Express From the Menu Bar Tools to Accounts - Click on Mail Tab Click on mail.nefcom.net (default) Click on Properties button Click on the General tab User Information E-mail
Prerequisite. Getting Started. Email Signing and Encryption using Microsoft outlook 2010
 Email Signing and Encryption using Microsoft outlook 2010 Prerequisite a. The user s email account has been added and correctly configured into Microsoft outlook. b. The user has an authentication certificate.
Email Signing and Encryption using Microsoft outlook 2010 Prerequisite a. The user s email account has been added and correctly configured into Microsoft outlook. b. The user has an authentication certificate.
6. Is it mandatory to have the digital certificate issued from NICCA?...3. 7. Is it mandatory for the sender and receiver to have a NIC email id?...
 FAQ FOR S/MIME 1. What is S/MIME?...2 2. What is digital certificate?...2 3. What is an encrypted email?...2 4. Is it mandatory to use this service?...2 5. What I need to do to start using S/MIME service?...2
FAQ FOR S/MIME 1. What is S/MIME?...2 2. What is digital certificate?...2 3. What is an encrypted email?...2 4. Is it mandatory to use this service?...2 5. What I need to do to start using S/MIME service?...2
Internet Explorer Settings for use with Privia
 Internet Explorer Settings for use with Privia The following document is intended for users who are running Privia and Internet Explorer who either cannot install the Privia client or the client is not
Internet Explorer Settings for use with Privia The following document is intended for users who are running Privia and Internet Explorer who either cannot install the Privia client or the client is not
Installing your certificate on your Mac
 Installing your certificate on your Mac Choose your email software from the options below. Apple Mail Using Apple Mail Apple Mail 1 of 2 Step one Visit Comodo for your free secure email certificate by
Installing your certificate on your Mac Choose your email software from the options below. Apple Mail Using Apple Mail Apple Mail 1 of 2 Step one Visit Comodo for your free secure email certificate by
DPMS2 McAfee Endpoint Encryption New Installation
 DPMS2 McAfee Endpoint Encryption New Installation Contents DPMS2 McAfee Endpoint Encryption New Installation... 1 1. Registering for the Application... 2 2. Downloading the Application... 6 3. Important
DPMS2 McAfee Endpoint Encryption New Installation Contents DPMS2 McAfee Endpoint Encryption New Installation... 1 1. Registering for the Application... 2 2. Downloading the Application... 6 3. Important
Schools Remote Access Server
 Schools Remote Access Server This system is for school use only. Not for personal or private file use. Please observe all of the school district IT rules. 6076 State Farm Rd., Guilderland, NY 12084 Phone:
Schools Remote Access Server This system is for school use only. Not for personal or private file use. Please observe all of the school district IT rules. 6076 State Farm Rd., Guilderland, NY 12084 Phone:
Using etoken for Securing E-mails Using Outlook and Outlook Express
 Using etoken for Securing E-mails Using Outlook and Outlook Express Lesson 15 April 2004 etoken Certification Course Securing Email Using Certificates Unprotected emails can be easily read and/or altered
Using etoken for Securing E-mails Using Outlook and Outlook Express Lesson 15 April 2004 etoken Certification Course Securing Email Using Certificates Unprotected emails can be easily read and/or altered
Configuring an Email Client to Connect to CASS Mail Servers
 Configuring an Email Client to Connect to CASS Mail Servers Table of Contents Introduction... 2 Webmail... 2 Settings... 2 Forwarding... 2 Email Client Configuration... 3 Outlook 2003... 3 Outlook 2007...
Configuring an Email Client to Connect to CASS Mail Servers Table of Contents Introduction... 2 Webmail... 2 Settings... 2 Forwarding... 2 Email Client Configuration... 3 Outlook 2003... 3 Outlook 2007...
Configuring Mozilla Thunderbird to Access Your SAS Email Account
 Configuring Mozilla Thunderbird to Access Your SAS Email Account 1. When you launch Thunderbird for the first time, the Import Wizard will appear: If Thunderbird detects that another email program was
Configuring Mozilla Thunderbird to Access Your SAS Email Account 1. When you launch Thunderbird for the first time, the Import Wizard will appear: If Thunderbird detects that another email program was
Microsoft Exchange Hosted Archive (MEHA)
 Microsoft Exchange Hosted Archive (MEHA) All the Features of NYSeMAIL Archiving including Using for Business Continuity Using MEHA Using MEHA The Microsoft Exchange Hosted Archive (MEHA) can be accessed
Microsoft Exchange Hosted Archive (MEHA) All the Features of NYSeMAIL Archiving including Using for Business Continuity Using MEHA Using MEHA The Microsoft Exchange Hosted Archive (MEHA) can be accessed
YSU Secure Wireless Connect Guide Windows XP Home/Professional/Media Center/Tablet PC Edition
 YSU Secure Wireless Connect Guide Windows XP Home/Professional/Media Center/Tablet PC Edition Required Items: Windows XP Home, Professional, Media Center, or Tablet PC Edition Any 802.11b, g, b/g, or a/b/g
YSU Secure Wireless Connect Guide Windows XP Home/Professional/Media Center/Tablet PC Edition Required Items: Windows XP Home, Professional, Media Center, or Tablet PC Edition Any 802.11b, g, b/g, or a/b/g
Client Authenticated SSL Server Setup Guide for Microsoft Windows IIS
 Page 1 of 20 PROTECTID Client Authenticated SSL Server Setup Guide for Microsoft Windows IIS Document: MK UM 01180405 01 ProtectIDclientAuthSSLsetupIIS.doc Page 2 of 20 Copyright 2005 Sentry Project Management
Page 1 of 20 PROTECTID Client Authenticated SSL Server Setup Guide for Microsoft Windows IIS Document: MK UM 01180405 01 ProtectIDclientAuthSSLsetupIIS.doc Page 2 of 20 Copyright 2005 Sentry Project Management
Outlook 2002. 1. Start Outlook, and click on mserver.wlu.ca. 2. From the Tools menu, choose Options
 Mserver to Ipmail Conversion Instructions The new email server called ipmail is configured to allow only encrypted email sessions. Members of the Laurier community who are currently using unencrypted email
Mserver to Ipmail Conversion Instructions The new email server called ipmail is configured to allow only encrypted email sessions. Members of the Laurier community who are currently using unencrypted email
TERAcloud w w w. t e r a c l o u d. u k
 Accessing your account Once you have received the confirmation email, there will be a link to your personal area where you can download the backup application. In the example here we are using the support
Accessing your account Once you have received the confirmation email, there will be a link to your personal area where you can download the backup application. In the example here we are using the support
I. Configuring Digital signature certificate in Microsoft Outlook 2003:
 I. Configuring Digital signature certificate in Microsoft Outlook 2003: In order to configure Outlook 2003 to use the new message security settings please follow these steps: 1. Open Outlook. 2. Go to
I. Configuring Digital signature certificate in Microsoft Outlook 2003: In order to configure Outlook 2003 to use the new message security settings please follow these steps: 1. Open Outlook. 2. Go to
Remedy ITSM Service Request Management Quick Start Guide
 Remedy ITSM Service Request Management Quick Start Guide Table of Contents 1.0 Getting Started With Remedy s Service Request Management. 3 2.0 Submitting a Service Request.7 3.0 Updating a Service Request
Remedy ITSM Service Request Management Quick Start Guide Table of Contents 1.0 Getting Started With Remedy s Service Request Management. 3 2.0 Submitting a Service Request.7 3.0 Updating a Service Request
TriCore Secure Web Email Gateway User Guide 1
 TriCore Secure Web Email Gateway User Guide This document provides information about TriCore Secure Web Email Gateway. This document is for users who are authorized to send and receive encrypted email
TriCore Secure Web Email Gateway User Guide This document provides information about TriCore Secure Web Email Gateway. This document is for users who are authorized to send and receive encrypted email
Email client configuration guide. Business Email
 Email client configuration guide Business Email August 2013 Contents 1. Mac Email Clients 1.1 Downloading Microsoft Outlook (Professional Plan Users) 1.2 Configuring Microsoft Outlook (Full Exchange Server
Email client configuration guide Business Email August 2013 Contents 1. Mac Email Clients 1.1 Downloading Microsoft Outlook (Professional Plan Users) 1.2 Configuring Microsoft Outlook (Full Exchange Server
Setup Instructions for Internet Access & Email Authentication
 Setup Instructions for Internet Access & Email Authentication User Manual Version: 1.2 Your Domain Wctel.net Examples: mail.wctel.net Smtp.wctel.net 1 EMAIL AUTHENTICATION... 3 What is Authentication?...
Setup Instructions for Internet Access & Email Authentication User Manual Version: 1.2 Your Domain Wctel.net Examples: mail.wctel.net Smtp.wctel.net 1 EMAIL AUTHENTICATION... 3 What is Authentication?...
How To Send An Encrypted Email In Outlook 2000 (For A Password Protected Email) On A Pc Or Macintosh (For An Ipo) On Pc Or Ipo (For Pc Or For A Password Safemail) On An Iphone Or
 Outlook 2000 1. Open Outlook 2000 and select the Tools > Options > Security. 2. Click Change Settings. 3. Under the Certificates and Algorithms, there are two Choose buttons. The first allows you to select
Outlook 2000 1. Open Outlook 2000 and select the Tools > Options > Security. 2. Click Change Settings. 3. Under the Certificates and Algorithms, there are two Choose buttons. The first allows you to select
