ZENworks Patch Management. Doc Hodges Opportunity Response Team Novell, Inc.
|
|
|
- August Cummings
- 10 years ago
- Views:
Transcription
1 ZENworks Patch Management Doc Hodges Opportunity Response Team Novell, Inc.
2 Are you prepared for business continuity threats? Unstable, malfunctioning systems resulting from attacks by viruses, worms and other malicious software Data loss resulting from lack of consistent, timely backups User tinkering resulting in broken workstations Hours of effort per system resulting from manual distribution of software Lost productivity resulting from hours of needless user desktop customization Lack of consistent operating environment preventing rapid system recovery Months of lost effort resulting from manual patch installation 2
3 Threats to Resource Integrity Viruses User errors Human clumsiness Theft Hackers Natural disasters Hard drive failure Power surge/failure Faulty hardware 3
4 A new approach consolidated Resource Management 4
5 Resource Management Stack Remote Mgmt Inventory Personality Data User Profile Patch, Update App Deployment OS Deployment Pre Boot Security Policy ZENworks Resource Management Bare Metal 5
6 Novell ZENworks 6.5 Complete IT resource management for enterprise-wide efficiency ZENworks Desktop Management Linux Management Server Management Data Management 6 Handheld Management
7 ZENworks Linux Management: powerful and secure Linux software management ZENworks Linux Management Provides IT administrators and managers with centralized control over Linux software configurations across their server and workstation infrastructures. 7
8 ZENworks Manages Linux Environments Support for SUSE, Red Hat, Linux updates Cross distribution software package deployment, conflict resolution, update and rollback Secure, scalable deployment Intuitive installation Complete web console Scriptable command-line interface On-demand or scheduled updating Customizable software library 8
9 ZENworks Linux Management The Best RPM Solution Resolves Recursive Dependencies Can graph all requirements for packages to be installed against currently installed packages, and packages available but not installed on the system Organizes Software Allows RPMs to be organized into channels for better management Controls Distribution Allows managed systems to be grouped to control software distribution across entire organization 9
10 ZENworks Linux Management won Best System Management tool 10
11 Virus History CSI/FBI Computer Crime Lab and Security Survey (2003) estimates that 83% of organizations experiencing virus attacks in 2002 suffered an associated loss of $27 million. The LoveLetter virus alone inflicted over 8.75 billion in damages worldwide in a year in which organizations suffered a total of $17.1 billion in virus-related costs. 11
12 Virus Mania In 2003 SQL Slammer Worm, estimated $1.25 billion damages Blaster Worm, estimated $2 billion damages In 2004 Bizten Trojan, Gaobot Worm, Mimmail Worm, Opaserv Worm, Backdoor.Sdbot Trojan, Xombe Trojan Backdoor.Threadsys Trojan, PWSteal Worm, MyDoom Worm, Hostidel Trojan, HLLW.Chemsvy Worm Dumaru Worm, Holar G Worm 49 new virus between Jan 1 Feb 4 th
13 Patches and Pattern Files Currently users combat viruses with virus pattern updates and patches on OS and applications. Security Focus reported in 2003, 223 Vunerabilities, requiring a patch, found in Microsoft products alone. Security Focus reports a total of 35 Vunerabilities in all tracked products in January
14 Applying Patches
15 SneakerNet Patching SneakerNet = running around, manually patching each server and desktop and then verifying the patch (e.g. windows update) Network Fusion says:...many network administrators essentially tracked patch status in their head, fixing holes on the fly. But in the last 2 years, the sheer complexity of networks and number of patches have rendered this approach ineffective. 15
16 SneakerNet - Do The Math Medium-sized network: 10 servers, 1000 desktops Averages patches: 2 per week Installations + Reboots = 404 per day Assume fast 30 minute apply and patch = 202 hours You need to spend 202 hours each day to apply patches! 16
17 Viruses come after the patches [Microsoft has] never had vulnerabilities exploited before the patch was known David Aucsmith (Chief technology officer, Security Business Unit, Microsoft's Corp., BBC News, February 26,
18 The Forensics of a Virus - Blaster July 1 July 16 July 25 Aug 11 Vulnerability reported to us / Patch in progress Bulletin & patch available No exploit Exploit code in public Worm in the world Report Vulnerability in RPC/DDOM reported MS activated highest level emergency response process Bulletin MS delivered to customers (7/16/03) Continued outreach to analysts, press, community, partners, government agencies Exploit X-focus (Chinese group) published exploit tool MS heightened efforts to get information to customers Worm Blaster worm discovered ; variants and other viruses hit simultaneously (i.e. SoBig ) Blaster shows the complex interplay between security researchers, software companies, and hackers 18
19 Architecture overview ZENworks Linux Management SUSE RCE Cache RedHat RCE RCE Server Mandrake Admin Console 19
20 ZENworks Patch Management Overview Full support of appropriate platforms Automated patch acquisition Detailed information about the patch Security fully integrated Robust agent-based architecture Applicable target management and selection Scheduling options Strong reporting Roles-based management Minimum required patch conformance 20
21 ZENworks Patch Management Patch Lifecycle Acquire Patch Research Detect Plan Report Defend Test Monitor Deploy Pilot 21 Rollout
22 Architecture overview ZENworks Patch Management Microsoft Patch Cache Novell PatchLink Patch Server Adobe Admin Console 22
23 Platform support ZENworks Patch Management supports the platforms you need Server runs on Windows 2000 or Windows 2003 Servers Desktop support Windows 98, NT, 2000 and XP Server Support Windows NT, 2000 and 2003 Servers NetWare Patch Support Microsoft, Novell, Adobe 23
24 Automated patch acquision ZENworks Patch Management automates the process Know about the patch Aquire the patch Ensure integrity of the patch Acquire dependant patches 24
25 Patch information ZENworks Patch Management provides extensive patch information Know the vulnerabilities addressed Know the severity of the risk Know if the patch is applicable to you Also Full dependency resolution Superseded patch prevention 25
26 Security every step of the way Acquisition from vendor Microsoft Patch Cache Novell PatchLink Patch Server Adobe Admin Console 26
27 Security every step of the way Delivery to you Microsoft Patch Cache Novell PatchLink Patch Server Adobe Admin Console 27
28 Security every step of the way Distribution Microsoft Patch Cache Novell PatchLink Patch Server Adobe Admin Console 28
29 Agent based architecture Security and flexibility Open NetBIOS ports are big risks! Consistent administrative userid s and passwords are big risks! ZENworks Patch Management agent provides: No NetBIOS ports required to be open Bidirectional initiation of updates Full scheduling engine Support for intermittently connected users 29
30 Target selection Know which devices need updates Manage individually, by group or by policy Policy defines required patches for all devices in your organization Automated compliance 30
31 Scheduling options Patch on your schedule Exact time that patches are applied When to check for new patches How many devices to patch at once Server initiated overrides 31
32 Reporting Know the state of your organization Clear, crisp graphical reports indicate status Where are you safe Where are you vulnerable Device success or failure 32
33 33 Home Page
34 Reports Page List of vulnerabilities by Impact 34
35 Reports Page Detail Filter the Vulnerability Report results by All, Detected, and Disabled by selection the desired item from the Filter by drop down menu 35
36 36 Vulnerability Report Detail
37 Patch Status For All Reports 37
38 Patch Status Computer Status for all Computers 38
39 Group Comprehensive Graphical Assessment The Group comprehensive graphical assessment allows the same type of reporting available at the home page to be displayed for a group of computers The data can be filtered by platform, vendor, and impact The perspective can be selected by agent, by patch, or by status 39
40 Patch Status Computer Status for all Computers 40
41 Groups Page By clicking on a group link you can display: Group level assessment report Reports & Inventory for the group Group Membership Mandatory Baseline Deployment History 41
42 Users Page Default Account: PatchLink Default Roles: Administrator Manager Operator Guest 52 Access Control Rights enable you to create custom roles to fit your environment. 42
43 Inventory Page Comprehensive patch detection requires a complete inventory of system information. Inventory information can be filtered by: Operating System Hardware Software Services 43
44 Inventory Page Comprehensive patch detection requires a complete inventory of system information. Inventory information can be filtered by: Operating System Hardware Software Services 44
45 45 Operating Systems View
46 46 Software View
47 47 Hardware View
48 48 Services View
49
Resources Management. Pascal Nuyttens Consultant. Stephan Pauwels Technology Specialist
 Pascal Nuyttens Consultant Stephan Pauwels Technology Specialist What is Required Today? Ensure Security and Compliance Enforce business rules and processes by policy Ensure systems are secure and locked
Pascal Nuyttens Consultant Stephan Pauwels Technology Specialist What is Required Today? Ensure Security and Compliance Enforce business rules and processes by policy Ensure systems are secure and locked
HP ProLiant Essentials Vulnerability and Patch Management Pack Planning Guide
 HP ProLiant Essentials Vulnerability and Patch Management Pack Planning Guide Product overview... 3 Vulnerability scanning components... 3 Vulnerability fix and patch components... 3 Checklist... 4 Pre-installation
HP ProLiant Essentials Vulnerability and Patch Management Pack Planning Guide Product overview... 3 Vulnerability scanning components... 3 Vulnerability fix and patch components... 3 Checklist... 4 Pre-installation
TapeWare THE ONE SOLUTION FOR BACKUP
 TapeWare THE ONE SOLUTION FOR BACKUP The ONE solution for backup When it comes to data protection for the small-to-medium enterprise, Yosemite TapeWare is the only solution you need. With platform support
TapeWare THE ONE SOLUTION FOR BACKUP The ONE solution for backup When it comes to data protection for the small-to-medium enterprise, Yosemite TapeWare is the only solution you need. With platform support
Intelligent Power Protector User manual extension for Microsoft Virtual architectures: Hyper-V 6.0 Manager Hyper-V Server (R1&R2)
 Intelligent Power Protector User manual extension for Microsoft Virtual architectures: Hyper-V 6.0 Manager Hyper-V Server (R1&R2) Hyper-V Manager Hyper-V Server R1, R2 Intelligent Power Protector Main
Intelligent Power Protector User manual extension for Microsoft Virtual architectures: Hyper-V 6.0 Manager Hyper-V Server (R1&R2) Hyper-V Manager Hyper-V Server R1, R2 Intelligent Power Protector Main
Dell UPS Local Node Manager USER'S GUIDE EXTENSION FOR MICROSOFT VIRTUAL ARCHITECTURES Dellups.com
 CHAPTER: Introduction Microsoft virtual architecture: Hyper-V 6.0 Manager Hyper-V Server (R1 & R2) Hyper-V Manager Hyper-V Server R1, Dell UPS Local Node Manager R2 Main Operating System: 2008Enterprise
CHAPTER: Introduction Microsoft virtual architecture: Hyper-V 6.0 Manager Hyper-V Server (R1 & R2) Hyper-V Manager Hyper-V Server R1, Dell UPS Local Node Manager R2 Main Operating System: 2008Enterprise
Patch Management Reference
 Patch Management Reference ZENworks 11 www.novell.com/documentation Legal Notices Novell, Inc. makes no representations or warranties with respect to the contents or use of this documentation, and specifically
Patch Management Reference ZENworks 11 www.novell.com/documentation Legal Notices Novell, Inc. makes no representations or warranties with respect to the contents or use of this documentation, and specifically
IBM Endpoint Manager Version 9.1. Patch Management for Red Hat Enterprise Linux User's Guide
 IBM Endpoint Manager Version 9.1 Patch Management for Red Hat Enterprise Linux User's Guide IBM Endpoint Manager Version 9.1 Patch Management for Red Hat Enterprise Linux User's Guide Note Before using
IBM Endpoint Manager Version 9.1 Patch Management for Red Hat Enterprise Linux User's Guide IBM Endpoint Manager Version 9.1 Patch Management for Red Hat Enterprise Linux User's Guide Note Before using
Red Hat Enterprise Linux and management bundle for HP BladeSystem TM
 HP and Red Hat are announcing a specially priced software bundle for customers deploying Red Hat Linux on HP BladeSystem servers. HP will offer Red Hat Enterprise Linux and management bundle that combines
HP and Red Hat are announcing a specially priced software bundle for customers deploying Red Hat Linux on HP BladeSystem servers. HP will offer Red Hat Enterprise Linux and management bundle that combines
Patch Management Reference
 www.novell.com/documentation Patch Management Reference ZENworks 11 SP3 February 2014 Legal Notices Novell, Inc. makes no representations or warranties with respect to the contents or use of this documentation,
www.novell.com/documentation Patch Management Reference ZENworks 11 SP3 February 2014 Legal Notices Novell, Inc. makes no representations or warranties with respect to the contents or use of this documentation,
Implementing Security Update Management
 Implementing Security Update Management Wayne Harris MCSE Senior Consultant Certified Security Solutions Business Case for Update Management When determining the potential financial impact of poor update
Implementing Security Update Management Wayne Harris MCSE Senior Consultant Certified Security Solutions Business Case for Update Management When determining the potential financial impact of poor update
Patch Management Reference
 www.novell.com/documentation Patch Management Reference ZENworks 11 SP4 November 2015 Legal Notices Novell, Inc. makes no representations or warranties with respect to the contents or use of this documentation,
www.novell.com/documentation Patch Management Reference ZENworks 11 SP4 November 2015 Legal Notices Novell, Inc. makes no representations or warranties with respect to the contents or use of this documentation,
THE COMPLETE VIEWER FOR MS PROJECT. Deployment White Paper
 THE COMPLETE VIEWER FOR MS PROJECT Seavus DOOEL 2010 2 TABLE OF CONTENTS 1 DEPLOYMENT OPTIONS... 3 1.1 SINGLE USER INSTALLATION... 3 1.2 CONCURRENT USER INSTALLATION... 4 1.3 SINGLE COMPANY KEY INSTALLATION...
THE COMPLETE VIEWER FOR MS PROJECT Seavus DOOEL 2010 2 TABLE OF CONTENTS 1 DEPLOYMENT OPTIONS... 3 1.1 SINGLE USER INSTALLATION... 3 1.2 CONCURRENT USER INSTALLATION... 4 1.3 SINGLE COMPANY KEY INSTALLATION...
LANDESK SOLUTION BRIEF. Patch Management
 Patch Management Increase the safety, security and efficiency of critical IT systems so IT can spend less time maintaining the computing environment and more time improving it. Develop and maintain patch
Patch Management Increase the safety, security and efficiency of critical IT systems so IT can spend less time maintaining the computing environment and more time improving it. Develop and maintain patch
Red Hat Network Satellite Management and automation of your Red Hat Enterprise Linux environment
 Red Hat Network Satellite Management and automation of your Red Hat Enterprise Linux environment WHAT IS IT? Red Hat Network (RHN) Satellite server is an easy-to-use, advanced systems management platform
Red Hat Network Satellite Management and automation of your Red Hat Enterprise Linux environment WHAT IS IT? Red Hat Network (RHN) Satellite server is an easy-to-use, advanced systems management platform
Streamlining Patch Testing and Deployment
 Streamlining Patch Testing and Deployment Using VMware GSX Server with LANDesk Management Suite to improve patch deployment speed and reliability Executive Summary As corporate IT departments work to keep
Streamlining Patch Testing and Deployment Using VMware GSX Server with LANDesk Management Suite to improve patch deployment speed and reliability Executive Summary As corporate IT departments work to keep
Simplifying Desktop Mgmt With Novell ZENworks
 Simplifying Desktop Mgmt With Novell ZENworks Joe Marton Senior Systems Engineer Collaboration Solution Principal Novell North America [email protected] Ryan Radschlag Network Manager Hartford Joint #1
Simplifying Desktop Mgmt With Novell ZENworks Joe Marton Senior Systems Engineer Collaboration Solution Principal Novell North America [email protected] Ryan Radschlag Network Manager Hartford Joint #1
Solution Recipe: Improve PC Security and Reliability with Intel Virtualization Technology
 Solution Recipe: Improve PC Security and Reliability with Intel Virtualization Technology 30406_VT_Brochure.indd 1 6/20/06 4:01:14 PM Preface Intel has developed a series of unique Solution Recipes designed
Solution Recipe: Improve PC Security and Reliability with Intel Virtualization Technology 30406_VT_Brochure.indd 1 6/20/06 4:01:14 PM Preface Intel has developed a series of unique Solution Recipes designed
IT INFRASTRUCTURE MANAGEMENT SERVICE ADDING POWER TO YOUR NETWORKS
 IT INFRASTRUCTURE MANAGEMENT SERVICE ADDING POWER TO YOUR NETWORKS IT INFRASTRUCTURE MANAGEMENT SERVICES Nortech Remote management IT security Services provide around clock remote Management, real time
IT INFRASTRUCTURE MANAGEMENT SERVICE ADDING POWER TO YOUR NETWORKS IT INFRASTRUCTURE MANAGEMENT SERVICES Nortech Remote management IT security Services provide around clock remote Management, real time
QuickSpecs HP Data Protector Express 4.0 Service Pack 1
 Overview HP Data Protector Express is easy to install, easy to use and easy to manage backup and recovery software designed specifically for smaller organizations. It robustly, yet simply, protects single
Overview HP Data Protector Express is easy to install, easy to use and easy to manage backup and recovery software designed specifically for smaller organizations. It robustly, yet simply, protects single
Patch Management for Red Hat Enterprise Linux. User s Guide
 Patch Management for Red Hat Enterprise Linux User s Guide User s Guide i Note: Before using this information and the product it supports, read the information in Notices. Copyright IBM Corporation 2003,
Patch Management for Red Hat Enterprise Linux User s Guide User s Guide i Note: Before using this information and the product it supports, read the information in Notices. Copyright IBM Corporation 2003,
Red Hat Satellite Management and automation of your Red Hat Enterprise Linux environment
 Red Hat Satellite Management and automation of your Red Hat Enterprise Linux environment WHAT IS IT? Red Hat Satellite server is an easy-to-use, advanced systems management platform for your Linux infrastructure.
Red Hat Satellite Management and automation of your Red Hat Enterprise Linux environment WHAT IS IT? Red Hat Satellite server is an easy-to-use, advanced systems management platform for your Linux infrastructure.
Product Brief. DC-Protect. Content based backup and recovery solution. By DATACENTERTECHNOLOGIES
 Product Brief DC-Protect Content based backup and recovery solution By DATACENTERTECHNOLOGIES 2002 DATACENTERTECHNOLOGIES N.V. All rights reserved. This document contains information proprietary and confidential
Product Brief DC-Protect Content based backup and recovery solution By DATACENTERTECHNOLOGIES 2002 DATACENTERTECHNOLOGIES N.V. All rights reserved. This document contains information proprietary and confidential
BladeLogic Software-as-a- Service (SaaS) Solution. Help reduce operating cost, improve security compliance, strengthen cybersecurity posture
 BladeLogic Software-as-a- Service (SaaS) Solution Help reduce operating cost, improve security compliance, strengthen cybersecurity posture February 20, 2014 Contents The Configuration Security Compliance
BladeLogic Software-as-a- Service (SaaS) Solution Help reduce operating cost, improve security compliance, strengthen cybersecurity posture February 20, 2014 Contents The Configuration Security Compliance
Best Practices for Deploying and Managing Linux with Red Hat Network
 Best Practices for Deploying and Managing Linux with Red Hat Network Abstract This technical whitepaper provides a best practices overview for companies deploying and managing their open source environment
Best Practices for Deploying and Managing Linux with Red Hat Network Abstract This technical whitepaper provides a best practices overview for companies deploying and managing their open source environment
Table of Contents. 10.0 Release Notes 2013/04/08. Introduction ... 3. in OS Deployment Manager. in Security Manager ... 7. Known issues ... 9 ...
 Release Notes Release Notes 2013/04/08 Table of Contents Introduction... 3 Deployment Manager... 3 New Features in Deployment Manager... 3 Security Manager... 7 New Features in Security Manager... 7 Known
Release Notes Release Notes 2013/04/08 Table of Contents Introduction... 3 Deployment Manager... 3 New Features in Deployment Manager... 3 Security Manager... 7 New Features in Security Manager... 7 Known
QuickSpecs HP Data Protector Express 4.0 Service Pack 1
 Overview HP Data Protector Express is easy to install, easy to use and easy to manage backup and recovery software designed specifically for smaller organizations. It robustly, yet simply, protects single
Overview HP Data Protector Express is easy to install, easy to use and easy to manage backup and recovery software designed specifically for smaller organizations. It robustly, yet simply, protects single
Kaspersky Endpoint Security 10 for Windows. Deployment guide
 Kaspersky Endpoint Security 10 for Windows Deployment guide Introduction Typical Corporate Network Network servers Internet Gateway Workstations Mail servers Portable media Malware Intrusion Routes Viruses
Kaspersky Endpoint Security 10 for Windows Deployment guide Introduction Typical Corporate Network Network servers Internet Gateway Workstations Mail servers Portable media Malware Intrusion Routes Viruses
Getting Started. Symantec Client Security. About Symantec Client Security. How to get started
 Getting Started Symantec Client Security About Security Security provides scalable, cross-platform firewall, intrusion prevention, and antivirus protection for workstations and antivirus protection for
Getting Started Symantec Client Security About Security Security provides scalable, cross-platform firewall, intrusion prevention, and antivirus protection for workstations and antivirus protection for
Lumension Endpoint Management and Security Suite (LEMSS): Patch and Remediation
 Lumension Endpoint Management and Security Suite (LEMSS): Patch and Remediation Version 7.0 SP1 Evaluation Guide September 2010 Version 2.4 Copyright 2010, Lumension, Inc. Table of Contents Lumension Endpoint
Lumension Endpoint Management and Security Suite (LEMSS): Patch and Remediation Version 7.0 SP1 Evaluation Guide September 2010 Version 2.4 Copyright 2010, Lumension, Inc. Table of Contents Lumension Endpoint
Week Overview. Installing Linux Linux on your Desktop Virtualization Basic Linux system administration
 ULI101 Week 06b Week Overview Installing Linux Linux on your Desktop Virtualization Basic Linux system administration Installing Linux Standalone installation Linux is the only OS on the computer Any existing
ULI101 Week 06b Week Overview Installing Linux Linux on your Desktop Virtualization Basic Linux system administration Installing Linux Standalone installation Linux is the only OS on the computer Any existing
Student Tech Security Training. ITS Security Office
 Student Tech Security Training ITS Security Office ITS Security Office Total Security is an illusion security will always be slightly broken. Find strategies for living with it. Monitor our Network with
Student Tech Security Training ITS Security Office ITS Security Office Total Security is an illusion security will always be slightly broken. Find strategies for living with it. Monitor our Network with
EMC Retrospect 7.5 for Windows. Backup and Recovery Software
 EMC Retrospect 7.5 for Windows Backup and Recovery Software Data Protection for Small and Medium Business EMC Retrospect backup and recovery software delivers automated, reliable data protection for small
EMC Retrospect 7.5 for Windows Backup and Recovery Software Data Protection for Small and Medium Business EMC Retrospect backup and recovery software delivers automated, reliable data protection for small
Enterprise Cybersecurity Best Practices Part Number MAN-00363 Revision 006
 Enterprise Cybersecurity Best Practices Part Number MAN-00363 Revision 006 April 2013 Hologic and the Hologic Logo are trademarks or registered trademarks of Hologic, Inc. Microsoft, Active Directory,
Enterprise Cybersecurity Best Practices Part Number MAN-00363 Revision 006 April 2013 Hologic and the Hologic Logo are trademarks or registered trademarks of Hologic, Inc. Microsoft, Active Directory,
Patch Management Marvin Christensen /CIAC
 Patch Management Marvin Christensen /CIAC US DOE Cyber Security Group 2004 Training Conference May 26, 2004 Management Track 11:00 am 11:45 pm UCRL-CONF-204220 CIAC 04-099 This work was performed under
Patch Management Marvin Christensen /CIAC US DOE Cyber Security Group 2004 Training Conference May 26, 2004 Management Track 11:00 am 11:45 pm UCRL-CONF-204220 CIAC 04-099 This work was performed under
Computer System Security Updates
 Why patch? If you have already deployed a network architecture, such as the one recommended by Rockwell Automation and Cisco in the Converged Plantwide Ethernet Design and Implementation Guide (http://www.ab.com/networks/architectures.html),
Why patch? If you have already deployed a network architecture, such as the one recommended by Rockwell Automation and Cisco in the Converged Plantwide Ethernet Design and Implementation Guide (http://www.ab.com/networks/architectures.html),
A Comparison of VMware and {Virtual Server}
 A Comparison of VMware and {Virtual Server} Kurt Lamoreaux Consultant, MCSE, VCP Computer Networking and Consulting Services A Funny Thing Happened on the Way to HP World 2004 Call for speakers at the
A Comparison of VMware and {Virtual Server} Kurt Lamoreaux Consultant, MCSE, VCP Computer Networking and Consulting Services A Funny Thing Happened on the Way to HP World 2004 Call for speakers at the
What s New with VMware Virtual Infrastructure
 What s New with VMware Virtual Infrastructure Virtualization: Industry-Standard Way of Computing Early Adoption Mainstreaming Standardization Test & Development Server Consolidation Infrastructure Management
What s New with VMware Virtual Infrastructure Virtualization: Industry-Standard Way of Computing Early Adoption Mainstreaming Standardization Test & Development Server Consolidation Infrastructure Management
ZENworks 11 Support Pack 4 Management Zone Settings Reference. May 2016
 ZENworks 11 Support Pack 4 Management Zone Settings Reference May 2016 Legal Notices For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government
ZENworks 11 Support Pack 4 Management Zone Settings Reference May 2016 Legal Notices For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government
Lumension Endpoint Management and Security Suite Patch and Remediation 7.0 Service Pack 1 Migration Guide
 Lumension Endpoint Management and Security Suite Patch and Remediation 7.0 Service Pack 1 Migration Guide Planning your migration with Service Pack 1 This document provides guidance for customers who plan
Lumension Endpoint Management and Security Suite Patch and Remediation 7.0 Service Pack 1 Migration Guide Planning your migration with Service Pack 1 This document provides guidance for customers who plan
A Better Approach to Backup and Bare-Metal Restore: Disk Imaging Technology
 A Better Approach to Backup and Bare-Metal Restore: Disk Imaging Technology Acronis True Image Enterprise Server for Windows Acronis True Image Server for Windows Acronis True Image Server for Linux Another
A Better Approach to Backup and Bare-Metal Restore: Disk Imaging Technology Acronis True Image Enterprise Server for Windows Acronis True Image Server for Windows Acronis True Image Server for Linux Another
HP Client Automation Standard Fast Track guide
 HP Client Automation Standard Fast Track guide Background Client Automation Version This document is designed to be used as a fast track guide to installing and configuring Hewlett Packard Client Automation
HP Client Automation Standard Fast Track guide Background Client Automation Version This document is designed to be used as a fast track guide to installing and configuring Hewlett Packard Client Automation
Novell ZENworks Patch Management Powered by PatchLink Corporation
 Novell ZENworks Patch Management Powered by PatchLink Corporation V6.0 Administration Guide Novell, Inc. 404 Wyman Street, Suite 500 Waltham, MA 02451 2004 Novell, Inc. All Rights Reserved. http://www.novell.com
Novell ZENworks Patch Management Powered by PatchLink Corporation V6.0 Administration Guide Novell, Inc. 404 Wyman Street, Suite 500 Waltham, MA 02451 2004 Novell, Inc. All Rights Reserved. http://www.novell.com
IBM Tivoli Monitoring for Applications
 Optimize the operation of your critical e-business applications IBM Tivoli Monitoring for Applications Highlights Helps maintain the performance and availability of your application environment including
Optimize the operation of your critical e-business applications IBM Tivoli Monitoring for Applications Highlights Helps maintain the performance and availability of your application environment including
Medical Device Security Health Group Digital Output
 Medical Device Security Health Group Digital Output Security Assessment Report for the Kodak Color Medical Imager 1000 (CMI-1000) Software Version 1.1 Part Number 1G0434 Revision 2.0 June 21, 2005 CMI-1000
Medical Device Security Health Group Digital Output Security Assessment Report for the Kodak Color Medical Imager 1000 (CMI-1000) Software Version 1.1 Part Number 1G0434 Revision 2.0 June 21, 2005 CMI-1000
How To Protect Your Data With Ecm Retrospect
 EMC Retrospect 7.5 for Windows Backup and Recovery Software Data Protection for Small and Medium Business EMC Retrospect backup and recovery software delivers automated, reliable data protection for small
EMC Retrospect 7.5 for Windows Backup and Recovery Software Data Protection for Small and Medium Business EMC Retrospect backup and recovery software delivers automated, reliable data protection for small
System Management. What are my options for deploying System Management on remote computers?
 Getting Started, page 1 Managing Assets, page 2 Distributing Software, page 3 Distributing Patches, page 4 Backing Up Assets, page 5 Using Virus Protection, page 6 Security, page 7 Getting Started What
Getting Started, page 1 Managing Assets, page 2 Distributing Software, page 3 Distributing Patches, page 4 Backing Up Assets, page 5 Using Virus Protection, page 6 Security, page 7 Getting Started What
Altiris Patch Management Solution for Linux 7.1 SP2 from Symantec User Guide
 Altiris Patch Management Solution for Linux 7.1 SP2 from Symantec User Guide Altiris Patch Management Solution for Linux 7.1 SP2 from Symantec User Guide The software described in this book is furnished
Altiris Patch Management Solution for Linux 7.1 SP2 from Symantec User Guide Altiris Patch Management Solution for Linux 7.1 SP2 from Symantec User Guide The software described in this book is furnished
Comparison of Firewall, Intrusion Prevention and Antivirus Technologies
 White Paper Comparison of Firewall, Intrusion Prevention and Antivirus Technologies How each protects the network Juan Pablo Pereira Technical Marketing Manager Juniper Networks, Inc. 1194 North Mathilda
White Paper Comparison of Firewall, Intrusion Prevention and Antivirus Technologies How each protects the network Juan Pablo Pereira Technical Marketing Manager Juniper Networks, Inc. 1194 North Mathilda
Introduction to Endpoint Security
 Chapter Introduction to Endpoint Security 1 This chapter provides an overview of Endpoint Security features and concepts. Planning security policies is covered based on enterprise requirements and user
Chapter Introduction to Endpoint Security 1 This chapter provides an overview of Endpoint Security features and concepts. Planning security policies is covered based on enterprise requirements and user
Managing Enterprise Devices and Apps using System Center Configuration Manager
 Course 20696B: Managing Enterprise Devices and Apps using System Center Configuration Manager Course Details Course Outline Module 1: Managing Desktops and Devices in the Enterprise This module explains
Course 20696B: Managing Enterprise Devices and Apps using System Center Configuration Manager Course Details Course Outline Module 1: Managing Desktops and Devices in the Enterprise This module explains
Understand Backup and Recovery Methods
 Understand Backup and Recovery Methods Lesson Overview Understand backup and recovery methods. In this lesson, you will explore: Backup management Backup options Recovery methods Backup Management Windows
Understand Backup and Recovery Methods Lesson Overview Understand backup and recovery methods. In this lesson, you will explore: Backup management Backup options Recovery methods Backup Management Windows
Nessus Agents. October 2015
 Nessus Agents October 2015 Table of Contents Introduction... 3 What Are Nessus Agents?... 3 Scanning... 4 Results... 6 Conclusion... 6 About Tenable Network Security... 6 2 Introduction Today s changing
Nessus Agents October 2015 Table of Contents Introduction... 3 What Are Nessus Agents?... 3 Scanning... 4 Results... 6 Conclusion... 6 About Tenable Network Security... 6 2 Introduction Today s changing
Novell ZENworks Asset Management 7.5
 Novell ZENworks Asset Management 7.5 w w w. n o v e l l. c o m October 2006 INSTALLATION GUIDE Table Of Contents 1. Installation Overview... 1 If you are upgrading... 1 Installation Choices... 1 ZENworks
Novell ZENworks Asset Management 7.5 w w w. n o v e l l. c o m October 2006 INSTALLATION GUIDE Table Of Contents 1. Installation Overview... 1 If you are upgrading... 1 Installation Choices... 1 ZENworks
ALTIRIS Patch Management Solution 6.2 for Windows Help
 ALTIRIS Patch Management Solution 6.2 for Windows Help Notice Altiris Patch Management Solution 6.2 2001-2006 Altiris, Inc. All rights reserved. Document Date: February 13, 2007 Protected by one or more
ALTIRIS Patch Management Solution 6.2 for Windows Help Notice Altiris Patch Management Solution 6.2 2001-2006 Altiris, Inc. All rights reserved. Document Date: February 13, 2007 Protected by one or more
Release Version 4.1 The 2X Software Server Based Computing Guide
 Release Version 4.1 The 2X Software Server Based Computing Guide Information in this document is subject to change without notice. Companies, names, and data used in examples herein are fictitious unless
Release Version 4.1 The 2X Software Server Based Computing Guide Information in this document is subject to change without notice. Companies, names, and data used in examples herein are fictitious unless
Kaseya IT Automation Framework
 Kaseya Kaseya IT Automation Framework An Integrated solution designed for reducing complexity while increasing productivity for IT Professionals and Managed Service Providers. The powerful, web-based automation
Kaseya Kaseya IT Automation Framework An Integrated solution designed for reducing complexity while increasing productivity for IT Professionals and Managed Service Providers. The powerful, web-based automation
Ovation Security Center Data Sheet
 Features Scans for vulnerabilities Discovers assets Deploys security patches transparently Allows only white-listed applications to run in workstations Provides virus protection for Ovation Windows workstations
Features Scans for vulnerabilities Discovers assets Deploys security patches transparently Allows only white-listed applications to run in workstations Provides virus protection for Ovation Windows workstations
Service Level Agreement (SLA) Arcplace Backup Enterprise Service
 (SLA) Arcplace Backup Enterprise Service 1. Introduction This Service Level Agreement ( SLA ) forms an integral part of the Agreement between Arcplace and Customer. This SLA describes the Backup Enterprise
(SLA) Arcplace Backup Enterprise Service 1. Introduction This Service Level Agreement ( SLA ) forms an integral part of the Agreement between Arcplace and Customer. This SLA describes the Backup Enterprise
EXTENSIVE FEATURE DESCRIPTION SECUNIA CORPORATE SOFTWARE INSPECTOR. Non-intrusive, authenticated scanning for OT & IT environments. secunia.
 Non-intrusive, authenticated scanning for OT & IT environments The situation: convenience vs. security Interconnectivity between organizations and corporate networks, the internet and the cloud and thus
Non-intrusive, authenticated scanning for OT & IT environments The situation: convenience vs. security Interconnectivity between organizations and corporate networks, the internet and the cloud and thus
Symantec AntiVirus Installation Guide
 Symantec AntiVirus Installation Guide 10517969 Symantec AntiVirus Installation Guide The software described in this book is furnished under a license agreement and may be used only in accordance with the
Symantec AntiVirus Installation Guide 10517969 Symantec AntiVirus Installation Guide The software described in this book is furnished under a license agreement and may be used only in accordance with the
IBM Endpoint Manager for Core Protection
 IBM Endpoint Manager for Core Protection Device control and endpoint protection designed to guard against malware and loss of sensitive data Highlights Delivers real-time endpoint protection against viruses,
IBM Endpoint Manager for Core Protection Device control and endpoint protection designed to guard against malware and loss of sensitive data Highlights Delivers real-time endpoint protection against viruses,
IQware's Approach to Software and IT security Issues
 IQware's Approach to Software and IT security Issues The Need for Security Security is essential in business intelligence (BI) systems since they have access to critical and proprietary enterprise information.
IQware's Approach to Software and IT security Issues The Need for Security Security is essential in business intelligence (BI) systems since they have access to critical and proprietary enterprise information.
Backup Exec Infrastructure Manager 12.5 FAQ
 Backup Exec Infrastructure Manager 12.5 FAQ Contents Overview... 1 Supported Backup Exec Configurations... 4 Backup Exec Infrastructure Manager Installation and Configuration... 6 Backup Exec Upgrades
Backup Exec Infrastructure Manager 12.5 FAQ Contents Overview... 1 Supported Backup Exec Configurations... 4 Backup Exec Infrastructure Manager Installation and Configuration... 6 Backup Exec Upgrades
Computer Viruses: How to Avoid Infection
 Viruses From viruses to worms to Trojan Horses, the catchall term virus describes a threat that's been around almost as long as computers. These rogue programs exist for the simple reason to cause you
Viruses From viruses to worms to Trojan Horses, the catchall term virus describes a threat that's been around almost as long as computers. These rogue programs exist for the simple reason to cause you
Microsoft Software Update Services and Managed Symantec Anti-virus. Michael Satut TSS/Crown IT Support [email protected]
 Microsoft Software Update Services and Managed Symantec Anti-virus Michael Satut TSS/Crown IT Support [email protected] Introduction The recent increase in virus and worm activity has created the
Microsoft Software Update Services and Managed Symantec Anti-virus Michael Satut TSS/Crown IT Support [email protected] Introduction The recent increase in virus and worm activity has created the
Lumension Endpoint Management and Security Suite
 Lumension Endpoint Management and Security Suite Patch and Remediation Module Evaluation Guide July 2012 Version 1.1 Copyright 2009, Lumension L.E.M.S.S:LPR - Table of Contents Introduction... 3 Module
Lumension Endpoint Management and Security Suite Patch and Remediation Module Evaluation Guide July 2012 Version 1.1 Copyright 2009, Lumension L.E.M.S.S:LPR - Table of Contents Introduction... 3 Module
DOBUS And SBL Cloud Services Brochure
 01347 812100 www.softbox.co.uk DOBUS And SBL Cloud Services Brochure [email protected] DOBUS Overview The traditional DOBUS service is a non-internet reliant, resilient, high availability trusted
01347 812100 www.softbox.co.uk DOBUS And SBL Cloud Services Brochure [email protected] DOBUS Overview The traditional DOBUS service is a non-internet reliant, resilient, high availability trusted
McAfee Total Protection Reduce the Complexity of Managing Security
 McAfee Total Protection Reduce the Complexity of Managing Security Computer security has changed dramatically since the first computer virus emerged 25 years ago. It s now far more complex and time-consuming.
McAfee Total Protection Reduce the Complexity of Managing Security Computer security has changed dramatically since the first computer virus emerged 25 years ago. It s now far more complex and time-consuming.
How To Deploy Software Updates Using SCCM 2012 R2
 prajwaldesai.com http://prajwaldesai.com/deploy-software-updates-using-sccm-2012-r2/ How To Deploy Software Updates Using SCCM 2012 R2 Prajwal Desai In this post we will look at the steps on how to deploy
prajwaldesai.com http://prajwaldesai.com/deploy-software-updates-using-sccm-2012-r2/ How To Deploy Software Updates Using SCCM 2012 R2 Prajwal Desai In this post we will look at the steps on how to deploy
Microsoft Technologies
 NETWORK ENGINEERING TRACK Microsoft Technologies QUARTER 1 DESKTOP APPLICATIONS - ESSENTIALS Module 1 - Office Applications This subject enables users to acquire the necessary knowledge and skills to use
NETWORK ENGINEERING TRACK Microsoft Technologies QUARTER 1 DESKTOP APPLICATIONS - ESSENTIALS Module 1 - Office Applications This subject enables users to acquire the necessary knowledge and skills to use
Data Sheet: Endpoint Security Symantec Endpoint Protection The next generation of antivirus technology from Symantec
 The next generation of antivirus technology from Symantec Overview Advanced threat protection combines Symantec AntiVirus with advanced threat prevention to deliver an unmatched defense against malware
The next generation of antivirus technology from Symantec Overview Advanced threat protection combines Symantec AntiVirus with advanced threat prevention to deliver an unmatched defense against malware
Data Sheet: Archiving Altiris Server Management Suite 7.0 from Symantec Essential server management: Discover, provision, manage, and monitor
 Essential server management: Discover, provision, manage, and monitor Overview Complexity with physical and virtual machine proliferation increases the challenges involved in managing servers. Server administrators
Essential server management: Discover, provision, manage, and monitor Overview Complexity with physical and virtual machine proliferation increases the challenges involved in managing servers. Server administrators
Linux Technologies QUARTER 1 DESKTOP APPLICATIONS - ESSENTIALS QUARTER 2 NETWORKING AND OPERATING SYSTEMS ESSENTIALS. Module 1 - Office Applications
 NETWORK ENGINEERING TRACK Linux Technologies QUARTER 1 DESKTOP APPLICATIONS - ESSENTIALS Module 1 - Office Applications This subject enables users to acquire the necessary knowledge and skills to use Office
NETWORK ENGINEERING TRACK Linux Technologies QUARTER 1 DESKTOP APPLICATIONS - ESSENTIALS Module 1 - Office Applications This subject enables users to acquire the necessary knowledge and skills to use Office
Patch Management SoftwareTechnical Specs
 Patch Management SoftwareTechnical Specs 1. Scalable: a. The PMS (Patch Management Software)must be scalable(can grow as network grows). b. The PMSmust be able to support more than 10k nodes from a single
Patch Management SoftwareTechnical Specs 1. Scalable: a. The PMS (Patch Management Software)must be scalable(can grow as network grows). b. The PMSmust be able to support more than 10k nodes from a single
Managing Security Risks in Modern IT Networks
 Managing Security Risks in Modern IT Networks White Paper Table of Contents Executive summary... 3 Introduction: networks under siege... 3 How great is the problem?... 3 Spyware: a growing issue... 3 Feeling
Managing Security Risks in Modern IT Networks White Paper Table of Contents Executive summary... 3 Introduction: networks under siege... 3 How great is the problem?... 3 Spyware: a growing issue... 3 Feeling
Patch management with WinReporter and RemoteExec
 White Paper Patch management with WinReporter and RemoteExec This white paper provides an overview on how to use WinReporter and RemoteExec in conjunction to keep Windows systems updated and immune to
White Paper Patch management with WinReporter and RemoteExec This white paper provides an overview on how to use WinReporter and RemoteExec in conjunction to keep Windows systems updated and immune to
LT Auditor+ for Windows
 LT Auditor+ for Windows Quick Start Guide Documentation issue: 5.3 Copyright Blue Lance Inc. Distributed by: LT Auditor+ for Windows: Overview LT Auditor+ is a security software application that provides
LT Auditor+ for Windows Quick Start Guide Documentation issue: 5.3 Copyright Blue Lance Inc. Distributed by: LT Auditor+ for Windows: Overview LT Auditor+ is a security software application that provides
How to Make Microsoft Security Patch Testing More Efficient
 How to Make Microsoft Security Patch Testing More Efficient Published Sept 2005 Abstract Despite the perils of deploying a Microsoft security patch to an enterprise s operating environment without first
How to Make Microsoft Security Patch Testing More Efficient Published Sept 2005 Abstract Despite the perils of deploying a Microsoft security patch to an enterprise s operating environment without first
BACKUP STANDARD YOSEMITE THE NEW NAME FOR DATA PROTECTION. backup simplified TM
 BACKUP STANDARD THE NEW NAME FOR DATA PROTECTION YOSEMITE backup simplified TM The SMALL BUSINESS solution for backup When it comes to data protection for the single server to small business, Yosemite
BACKUP STANDARD THE NEW NAME FOR DATA PROTECTION YOSEMITE backup simplified TM The SMALL BUSINESS solution for backup When it comes to data protection for the single server to small business, Yosemite
HEAT DSM 2015.2 Release Overview. Andreas Fuchs Product Management November 16th, 2015
 HEAT DSM 2015.2 Release Overview Andreas Fuchs Product Management November 16th, 2015 HEAT DSM 2015.2 Highlights HEAT Discovery Integration Patch Management Enhancements HEAT PatchLink Integration HEAT
HEAT DSM 2015.2 Release Overview Andreas Fuchs Product Management November 16th, 2015 HEAT DSM 2015.2 Highlights HEAT Discovery Integration Patch Management Enhancements HEAT PatchLink Integration HEAT
EMC Retrospect 7.5 for Windows. Backup and Recovery Software
 EMC Retrospect 7.5 for Windows Backup and Recovery Software Data Protection for Small and Medium Business EMC Retrospect backup and recovery software delivers automated, reliable data protection for small
EMC Retrospect 7.5 for Windows Backup and Recovery Software Data Protection for Small and Medium Business EMC Retrospect backup and recovery software delivers automated, reliable data protection for small
IBM Endpoint Manager Version 9.2. Patch Management for SUSE Linux Enterprise User's Guide
 IBM Endpoint Manager Version 9.2 Patch Management for SUSE Linux Enterprise User's Guide IBM Endpoint Manager Version 9.2 Patch Management for SUSE Linux Enterprise User's Guide Note Before using this
IBM Endpoint Manager Version 9.2 Patch Management for SUSE Linux Enterprise User's Guide IBM Endpoint Manager Version 9.2 Patch Management for SUSE Linux Enterprise User's Guide Note Before using this
Eaton NetWatch v5.0 NetWatch on Microsoft Hyper-V server 2008 Installation and configuration guide
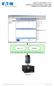 Eaton NetWatch v5.0 NetWatch on Microsoft Hyper-V server 2008 Installation and configuration guide Hyper-V 6.0 NetWatch Main operating system: 2008 Enterprise x64 (hosting Hyper-V) Eaton UPS Eaton NetWatch
Eaton NetWatch v5.0 NetWatch on Microsoft Hyper-V server 2008 Installation and configuration guide Hyper-V 6.0 NetWatch Main operating system: 2008 Enterprise x64 (hosting Hyper-V) Eaton UPS Eaton NetWatch
Closing the Vulnerability Gap of Third- Party Patching
 SOLUTION BRIEF: THIRD-PARTY PATCH MANAGEMENT........................................ Closing the Vulnerability Gap of Third- Party Patching Who should read this paper IT Managers who are trying to manage
SOLUTION BRIEF: THIRD-PARTY PATCH MANAGEMENT........................................ Closing the Vulnerability Gap of Third- Party Patching Who should read this paper IT Managers who are trying to manage
IBM Tivoli Endpoint Manager for Security and Compliance
 IBM Endpoint Manager for Security and Compliance A single solution for managing endpoint security across the organization Highlights Provide up-to-date visibility and control from a single management console
IBM Endpoint Manager for Security and Compliance A single solution for managing endpoint security across the organization Highlights Provide up-to-date visibility and control from a single management console
Data Sheet: Server Management Altiris Server Management Suite 7.0 Essential server management: Discover, provision, manage, and monitor
 Essential server management: Discover, provision, manage, and monitor Overview Complexity with physical and virtual machine proliferation increases the challenges involved in managing servers. Server administrators
Essential server management: Discover, provision, manage, and monitor Overview Complexity with physical and virtual machine proliferation increases the challenges involved in managing servers. Server administrators
Release Version 3 The 2X Software Server Based Computing Guide
 Release Version 3 The 2X Software Server Based Computing Guide Information in this document is subject to change without notice. Companies, names, and data used in examples herein are fictitious unless
Release Version 3 The 2X Software Server Based Computing Guide Information in this document is subject to change without notice. Companies, names, and data used in examples herein are fictitious unless
PARALLELS SERVER 4 BARE METAL README
 PARALLELS SERVER 4 BARE METAL README This document provides the first-priority information on Parallels Server 4 Bare Metal and supplements the included documentation. TABLE OF CONTENTS 1 About Parallels
PARALLELS SERVER 4 BARE METAL README This document provides the first-priority information on Parallels Server 4 Bare Metal and supplements the included documentation. TABLE OF CONTENTS 1 About Parallels
TIME TO LIVE ON THE NETWORK
 TIME TO LIVE ON THE NETWORK Executive Summary This experiment tests to see how well commonly used computer platforms withstand Internet attacks in the wild. The experiment quantifies the amount of time
TIME TO LIVE ON THE NETWORK Executive Summary This experiment tests to see how well commonly used computer platforms withstand Internet attacks in the wild. The experiment quantifies the amount of time
