Issuance and use of PIV at FAA
|
|
|
- Aldous Hall
- 10 years ago
- Views:
Transcription
1 Issuance and use of PIV at FAA Presented to: Government Smart Card Interagency Advisory Board By: Ed Ebright, Division Manager, ID Media Division Date: May 2011
2 Agenda What we use PIV Card Status FAA HSPD-12 Systems PIV Card Health Check Visitor System Contactless Reader PIV Authoritative Database Forgotten PIV Cards Issues FAA PACS FAA LACS 2
3 What we use PKI Verisign/Symantec. CMS - Intercede IDMS Investigations Tracking System (ITS). FAA developed web based system. In production since Precise Biometrics 250 and 200. AWARE Facial Recognition. Customized for the FAA. 3
4 PIV Card Status As of May 1 st the FAA has issued 68,000 PIV Cards. Total Population 73, % of Federal Employees have their PIV Card. 99% of all Federal and Contractor employees have applied for the PIV Card. 170 Permanent sites issuing PIV Cards. (Accommodates approximately 85% of workforce. Remaining 15% complete while at permanent site and using Mobile Lite concept. (PIV in a Box). 4
5 FAA HSPD-12 Systems PIV Card Health Check The purpose of the PIV Card Health Check is to conduct and share an integrity check on individual PIV Cards. Cardholders can access a website and use a friendly GUI to view the health of their PIV Card. Cardholders may also submit a report to the PIV Helpdesk. 5
6 PIV Card Health Check Helpdesk personnel have real time access to review the same report as the card holder. The system will help in troubleshooting problems such as expired certificates, corrupted cards, and non-card issues such as malfunctioning card reader or login configuration problems. This system is available to other agencies to host and usage. 6
7 PIV Card Health Check 7
8 FAA HSPD-12 Systems Visitor System Web based system which allows FAA employees to sponsor visitors from other agencies. Visitor is notified through and the system automatically walks them through registering their smart card. (PIV and CAC) Data is automatically transferred to the FAA Secure PAD. Facility Manager assigns access to visitor. 8
9 Visitor Administrator Console 9
10 FAA HSPD-12 Systems Contactless Reader Contactless Reader. Windows based system which verifies the contactless has not been broken and provides information read from the contactless portion of PIV Card. Used by all 170 sites. Valuable tool used everyday at every site. To download go to: 10
11 Contactless Reader (Screenshot) 11
12 Additional Systems PIV Authoritative Database (PAD) The PAD is the official FAA repository of all PIV Cards issued. The data from the system is shared with both Physical and Logical Access. When an FAA PIV Card is cancelled or suspended access to FAA Physical and Logical systems is automatically revoked within 15 minutes. 12
13 Additional Systems PIV Authoritative Database (PAD) When other agency PIV Cards are cancelled or suspended access to FAA Physical and Logical system is automatically revoked within 8 hours. This timeframe is configurable. 13
14 14
15 Forgotten PIV Cards Employees will be issued a Temporary PIV Card. When issued, their existing PIV Card will automatically be suspended. Temporary PIV Card can immediately be used for Physical Access and any usage of the PIV Authoritative Certificate. Signing and Encryption certificate are not available on the Temporary PIV Card. Once Temporary PIV Card is returned the employees PIV Card is reinstated. 15
16 Forgotten PIV Cards Temporary PIV Cards are re-usable. 16
17 Issues Readers/Cards Some PIV Cards will work in one reader but not another. They always work in the SmartTerminal ST-1044 by Cherry. Electromagnetically Opaque Sleeve. Cost of the holder and the issues it causes for employees using the PIV Cards. 17
18 Issues Long Names Should be resolved in FIPS Fingerprint Capturing Should be resolved in FIPS with IRIS scanning included. 18
19 FAA PACS The FAA has 1100 facilities. The FAA has 100 sites PIV Compliant. Planning has already begun to PIV enable an additional 500 sites. The remaining 500 sites are under consideration in making PIV Compliant. Average 3-5 employees per site. May not be cost effective These sites are Security Level 1 Facilities. 19
20 FAA PACS We use Pegasus P2000. FAA HQs will begin using PIV Cards in early June. Turnstiles are installed and going through final testing. Handheld devices will be used for entry to garage. MicorFlex CE Codebench software configured with the P
21 FAA LACS Domain Controller Certificates issued from PKI. Network Logon has been completed. Implementation is in process. Office of Security & Hazardous Materials Safety (approximately 470 employees) use PIV Cards exclusively for Network Logon and internal Web Applications. 21
22 22
23 Contacts For more information or to arrange for demonstrations of the FAA systems please contact: Ed Ebright Guy Davidson
24 Questions & Answers
HSPD-12 Implementation Architecture Working Group Concept Overview. Version 1.0 March 17, 2006
 HSPD-12 Implementation Architecture Working Group Concept Overview Version 1.0 March 17, 2006 Table of Contents 1 PIV Lifecycle... 3 2 High Level Component Interaction Diagram... 4 3 PIV Infrastructure
HSPD-12 Implementation Architecture Working Group Concept Overview Version 1.0 March 17, 2006 Table of Contents 1 PIV Lifecycle... 3 2 High Level Component Interaction Diagram... 4 3 PIV Infrastructure
NOAA HSPD-12 PIV-II Implementation October 23, 2007. Who is responsible for implementation of HSPD-12 PIV-II?
 NOAA HSPD-12 PIV-II Implementation What is HSPD-12? Homeland Security Presidential Directive 12 (HSPD-12) is a Presidential requirement signed on August 27, 2004 requiring Federal agencies comply with
NOAA HSPD-12 PIV-II Implementation What is HSPD-12? Homeland Security Presidential Directive 12 (HSPD-12) is a Presidential requirement signed on August 27, 2004 requiring Federal agencies comply with
NEIS HELP DESK FAQS. HSPD-12 Policy/Business Process. General HSPD-12 FAQs can be found online at: http://lincpass.usda.gov/faq.
 General HSPD-12 FAQs can be found online at: http://lincpass.usda.gov/faq.html HSPD-12 Policy/Business Process 1. How long is the entire process for Non-Employees? After enrollment, applicants should receive
General HSPD-12 FAQs can be found online at: http://lincpass.usda.gov/faq.html HSPD-12 Policy/Business Process 1. How long is the entire process for Non-Employees? After enrollment, applicants should receive
Audio: This overview module contains an introduction, five lessons, and a conclusion.
 Homeland Security Presidential Directive 12 (HSPD 12) Overview Audio: Welcome to the Homeland Security Presidential Directive 12 (HSPD 12) overview module, the first in a series of informational modules
Homeland Security Presidential Directive 12 (HSPD 12) Overview Audio: Welcome to the Homeland Security Presidential Directive 12 (HSPD 12) overview module, the first in a series of informational modules
2. Each server or domain controller requires its own server certificate, DoD Root Certificates and enterprise validator installed.
 Purpose and Scope The purpose of this policy is to define the roles and responsibilities on implementing the Homeland Security Presidential Directive 12 (HSPD-12) Logical Access Control (LAC) throughout
Purpose and Scope The purpose of this policy is to define the roles and responsibilities on implementing the Homeland Security Presidential Directive 12 (HSPD-12) Logical Access Control (LAC) throughout
GOALS (2) The goal of this training module is to increase your awareness of HSPD-12 and the corresponding technical standard FIPS 201.
 PERSONAL IDENTITY VERIFICATION (PIV) OVERVIEW INTRODUCTION (1) Welcome to the Homeland Security Presidential Directive 12 (HSPD-12) Personal Identity Verification (PIV) Overview module, designed to familiarize
PERSONAL IDENTITY VERIFICATION (PIV) OVERVIEW INTRODUCTION (1) Welcome to the Homeland Security Presidential Directive 12 (HSPD-12) Personal Identity Verification (PIV) Overview module, designed to familiarize
Justice Management Division
 Justice Management Division Privacy Impact Assessment for the Personal Identity Verification (PIV) Card System Issued by: Stuart Frisch, Senior Component Official for Privacy Reviewed by: Vance E. Hitch,
Justice Management Division Privacy Impact Assessment for the Personal Identity Verification (PIV) Card System Issued by: Stuart Frisch, Senior Component Official for Privacy Reviewed by: Vance E. Hitch,
1. The human guard at the access control entry point determines whether the PIV Card appears to be genuine and has not been altered in any way.
 + Expiration date + Agency card serial number (back of card) + Issuer identification (back of card). The PIV Card may also bear the following optional components: + Agency name and/or department + Department
+ Expiration date + Agency card serial number (back of card) + Issuer identification (back of card). The PIV Card may also bear the following optional components: + Agency name and/or department + Department
The Convergence of IT Security and Physical Access Control
 The Convergence of IT Security and Physical Access Control Using a Single Credential to Secure Access to IT and Physical Resources Executive Summary Organizations are increasingly adopting a model in which
The Convergence of IT Security and Physical Access Control Using a Single Credential to Secure Access to IT and Physical Resources Executive Summary Organizations are increasingly adopting a model in which
What Does it Mean to be PIVish in PACS ICAM PIV in E-PACS Guidance v2.0.2 the short form. December 3, 2012
 Federal CIO Council Information Security and Identity Management Committee IDManagement.gov What Does it Mean to be PIVish in PACS ICAM PIV in E-PACS Guidance v2.0.2 the short form December 3, 2012 HSPD-12
Federal CIO Council Information Security and Identity Management Committee IDManagement.gov What Does it Mean to be PIVish in PACS ICAM PIV in E-PACS Guidance v2.0.2 the short form December 3, 2012 HSPD-12
An Operational Architecture for Federated Identity Management
 An Operational Architecture for Federated Identity Management March 2011 Implementing federated identity management and assurance in operational scenarios Federated Identity Solution The Federated identity
An Operational Architecture for Federated Identity Management March 2011 Implementing federated identity management and assurance in operational scenarios Federated Identity Solution The Federated identity
U.S. Department of Housing and Urban Development
 U.S. Department of Housing and Urban Development PRIVACY IMPACT ASSESSMENT FOR: PERSONAL IDENTITY VERIFICATION (PIV) PROCESS TECHNOLOGY AND DATABASE IN COMPLIANCE WITH HOMELAND SECURITY PRESIDENTIAL DIRECTIVE
U.S. Department of Housing and Urban Development PRIVACY IMPACT ASSESSMENT FOR: PERSONAL IDENTITY VERIFICATION (PIV) PROCESS TECHNOLOGY AND DATABASE IN COMPLIANCE WITH HOMELAND SECURITY PRESIDENTIAL DIRECTIVE
Department of Defense PKI Use Case/Experiences
 UNCLASSIFIED//FOR OFFICIAL USE ONLY Department of Defense PKI Use Case/Experiences PKI IMPLEMENTATION WORKSHOP Debbie Mitchell DoD PKI PMO [email protected] UNCLASSIFIED//FOR OFFICIAL USE ONLY Current
UNCLASSIFIED//FOR OFFICIAL USE ONLY Department of Defense PKI Use Case/Experiences PKI IMPLEMENTATION WORKSHOP Debbie Mitchell DoD PKI PMO [email protected] UNCLASSIFIED//FOR OFFICIAL USE ONLY Current
Smart Cards and Biometrics in Physical Access Control Systems
 Smart Cards and Biometrics in Physical Access Control Systems Robert J. Merkert, Sr. Vice President of Sales Americas Biometric Consortium 2005 Conference September 21, 2005 All Company and/or product
Smart Cards and Biometrics in Physical Access Control Systems Robert J. Merkert, Sr. Vice President of Sales Americas Biometric Consortium 2005 Conference September 21, 2005 All Company and/or product
Office of the Chief Information Officer Department of Energy Identity, Credential, and Access Management (ICAM)
 Department of Energy Identity, Credential, and Access Management (ICAM) Cyber Security Training Conference Tuesday, May 18, 2010 1 Announcement LACS Birds-of-a-Feather Session Logistics Wednesday, May
Department of Energy Identity, Credential, and Access Management (ICAM) Cyber Security Training Conference Tuesday, May 18, 2010 1 Announcement LACS Birds-of-a-Feather Session Logistics Wednesday, May
The Government-wide Implementation of Biometrics for HSPD-12
 The Government-wide Implementation of Biometrics for HSPD-12 David Temoshok Director, Identity Policy and Management GSA Office of Governmentwide Policy September 24, 2008 1 The HSPD-12 Mandate Home Security
The Government-wide Implementation of Biometrics for HSPD-12 David Temoshok Director, Identity Policy and Management GSA Office of Governmentwide Policy September 24, 2008 1 The HSPD-12 Mandate Home Security
Life After PIV. Authentication In Federated Spaces. Presented to. Card Tech/Secure Tech. May 2009. By Lynne Prince Defense Manpower Data Center
 Life After PIV Authentication In Federated Spaces Presented to Card Tech/Secure Tech By Lynne Prince Defense Manpower Data Center Interoperability with HSPD12 Capability PIV provides a secure common credential,
Life After PIV Authentication In Federated Spaces Presented to Card Tech/Secure Tech By Lynne Prince Defense Manpower Data Center Interoperability with HSPD12 Capability PIV provides a secure common credential,
Strong Authentication for PIV and PIV-I using PKI and Biometrics
 Strong Authentication for PIV and PIV-I using PKI and Biometrics Adam Shane PSP, Product Manager and Sr. Systems Design Architect AMAG Technology Bob Fontana CSCIP/G, Vice President-Federal Identity Codebench/HID
Strong Authentication for PIV and PIV-I using PKI and Biometrics Adam Shane PSP, Product Manager and Sr. Systems Design Architect AMAG Technology Bob Fontana CSCIP/G, Vice President-Federal Identity Codebench/HID
Practical Challenges in Adopting PIV/PIV-I
 UNCLASSIFIED Practical Challenges in Adopting PIV/PIV-I Hank Morris UNCLASSIFIED 2 UNCLASSIFIED // FOUO Purpose and Agenda Purpose: Explore the policy, process, and mechanisms to securely leverage biometrics
UNCLASSIFIED Practical Challenges in Adopting PIV/PIV-I Hank Morris UNCLASSIFIED 2 UNCLASSIFIED // FOUO Purpose and Agenda Purpose: Explore the policy, process, and mechanisms to securely leverage biometrics
For Official Use Only (FOUO)
 The FEMA Mission To support our citizens and first responders to ensure that as a nation we work together to build, sustain, and improve our capability to prepare for, protect against, respond to, and
The FEMA Mission To support our citizens and first responders to ensure that as a nation we work together to build, sustain, and improve our capability to prepare for, protect against, respond to, and
DEPARTMENTAL REGULATION
 U.S. DEPARTMENT OF AGRICULTURE WASHINGTON, D.C. 20250 DEPARTMENTAL REGULATION SUBJECT: Identity, Credential, and Access Management Number: 3640-001 DATE: December 9, 2011 OPI: Office of the Chief Information
U.S. DEPARTMENT OF AGRICULTURE WASHINGTON, D.C. 20250 DEPARTMENTAL REGULATION SUBJECT: Identity, Credential, and Access Management Number: 3640-001 DATE: December 9, 2011 OPI: Office of the Chief Information
RAPIDS Self Service User Guide
 Page 1 RAPIDS Self Service User Guide https://www.dmdc.osd.mil/self_service Page 2 Introduction The RAPIDS Self Service (RSS) application provides sponsors with the capability to generate a DD Form 1172-2
Page 1 RAPIDS Self Service User Guide https://www.dmdc.osd.mil/self_service Page 2 Introduction The RAPIDS Self Service (RSS) application provides sponsors with the capability to generate a DD Form 1172-2
GAO PERSONAL ID VERIFICATION. Agencies Should Set a Higher Priority on Using the Capabilities of Standardized Identification Cards
 GAO United States Government Accountability Office Report to Congressional Requesters September 2011 PERSONAL ID VERIFICATION Agencies Should Set a Higher Priority on Using the Capabilities of Standardized
GAO United States Government Accountability Office Report to Congressional Requesters September 2011 PERSONAL ID VERIFICATION Agencies Should Set a Higher Priority on Using the Capabilities of Standardized
Page 1. Smart Card Applications. Lecture 7: Prof. Sead Muftic Matei Ciobanu Morogan. Lecture 7 : Lecture 7 : Smart Card Applications
 in Open Distributed Processing s 1 in Open Distributed Processing s 2 Prof. Sead Muftic Matei Ciobanu Morogan Lecture 7: 1 2 in Open Distributed Processing s 3 in Open Distributed Processing s Smart s
in Open Distributed Processing s 1 in Open Distributed Processing s 2 Prof. Sead Muftic Matei Ciobanu Morogan Lecture 7: 1 2 in Open Distributed Processing s 3 in Open Distributed Processing s Smart s
Identity, Credential, and Access Management. An information exchange For Information Security and Privacy Advisory Board
 Federal CIO Council Information Security and Identity Management Committee Identity, Credential, and Access Management An information exchange For Information Security and Privacy Advisory Board Deb Gallagher
Federal CIO Council Information Security and Identity Management Committee Identity, Credential, and Access Management An information exchange For Information Security and Privacy Advisory Board Deb Gallagher
U.S. Department of Agriculture HSPD 12 Program. USDA HSPD-12 Implementing PIV cards @ USDA
 U.S. Department of Agriculture HSPD 12 Program USDA HSPD-12 Implementing PIV cards @ USDA April 2009 USDA and the GSA HSPD-12 Shared Solution USDA has been at the forefront of driving a shared solution
U.S. Department of Agriculture HSPD 12 Program USDA HSPD-12 Implementing PIV cards @ USDA April 2009 USDA and the GSA HSPD-12 Shared Solution USDA has been at the forefront of driving a shared solution
Department of Defense INSTRUCTION
 Department of Defense INSTRUCTION NUMBER 1000.13 January 23, 2014 USD(P&R) SUBJECT: Identification (ID) Cards for Members of the Uniformed Services, Their Dependents, and Other Eligible Individuals References:
Department of Defense INSTRUCTION NUMBER 1000.13 January 23, 2014 USD(P&R) SUBJECT: Identification (ID) Cards for Members of the Uniformed Services, Their Dependents, and Other Eligible Individuals References:
NIST s FIPS 201: Personal Identity Verification (PIV) of Federal Employees and Contractors Masaryk University in Brno Faculty of Informatics
 NIST s FIPS 201: Personal Identity Verification (PIV) of Federal Employees and Contractors Masaryk University in Brno Faculty of Informatics Jan Krhovják Outline Introduction and basics of PIV Minimum
NIST s FIPS 201: Personal Identity Verification (PIV) of Federal Employees and Contractors Masaryk University in Brno Faculty of Informatics Jan Krhovják Outline Introduction and basics of PIV Minimum
Enrolling with PIV and PIV-I Velocity Enrollment Manager
 Enrolling with PIV and PIV-I Velocity Enrollment Manager Overview The Homeland Security Presidential Directive 12 (HSPD-12) called for a common identification standard to be adopted by all Federal Government
Enrolling with PIV and PIV-I Velocity Enrollment Manager Overview The Homeland Security Presidential Directive 12 (HSPD-12) called for a common identification standard to be adopted by all Federal Government
Government Compliance Document FIPS 201, FIPS 197, FIPS 140-2
 Government Compliance Document FIPS 201, FIPS 197, FIPS 140-2 AMAG Technology has been providing tailored and unified security solutions across a range of government agencies facilities for many years.
Government Compliance Document FIPS 201, FIPS 197, FIPS 140-2 AMAG Technology has been providing tailored and unified security solutions across a range of government agencies facilities for many years.
PIV Scheduler Tool. Screen Shots from May 1, 2013 9:00am Eastern
 PIV Scheduler Tool Screen Shots from May 1, 2013 9:00am Eastern PIV Scheduler Tool This slide deck was created to provide a heads up and quick overview of the PIV Scheduler Tool to the Education Staff
PIV Scheduler Tool Screen Shots from May 1, 2013 9:00am Eastern PIV Scheduler Tool This slide deck was created to provide a heads up and quick overview of the PIV Scheduler Tool to the Education Staff
intertrax MOBILE PIV
 intertrax MOBILE PIV Personnel Identification Verification Software User Guide Version 4 2012 Copyright 2003-2012 by Salamander Technologies, Inc. Protected by US Patents 5,573,278; 5,596,652; 5,793,882;
intertrax MOBILE PIV Personnel Identification Verification Software User Guide Version 4 2012 Copyright 2003-2012 by Salamander Technologies, Inc. Protected by US Patents 5,573,278; 5,596,652; 5,793,882;
Personal Identity Verification
 for the Personal Identity Verification Contact Point Cynthia Sjoberg Program Manager, HSPD 12 Training and Operations Security Division Office of Security Department of Homeland Security (202) 447 5010
for the Personal Identity Verification Contact Point Cynthia Sjoberg Program Manager, HSPD 12 Training and Operations Security Division Office of Security Department of Homeland Security (202) 447 5010
intertrax Suite intertrax exchange intertrax monitor intertrax connect intertrax PIV manager User Guide Version 3 2011
 intertrax Suite intertrax exchange intertrax monitor intertrax connect intertrax PIV manager User Guide Version 3 2011 Copyright 2003-2011 by Salamander Technologies, Inc. Protected by US Patents 5,573,278;
intertrax Suite intertrax exchange intertrax monitor intertrax connect intertrax PIV manager User Guide Version 3 2011 Copyright 2003-2011 by Salamander Technologies, Inc. Protected by US Patents 5,573,278;
How to Use Your LincPass Credential
 Your LincPass is your USDA personal identity verification (PIV) card. This guide explains how to use your card and PIN to access and protect USDA network and computer resources. What You ll Need to Get
Your LincPass is your USDA personal identity verification (PIV) card. This guide explains how to use your card and PIN to access and protect USDA network and computer resources. What You ll Need to Get
Executive Summary P 1. ActivIdentity
 WHITE PAPER WP Converging Access of IT and Building Resources P 1 Executive Summary To get business done, users must have quick, simple access to the resources they need, when they need them, whether they
WHITE PAPER WP Converging Access of IT and Building Resources P 1 Executive Summary To get business done, users must have quick, simple access to the resources they need, when they need them, whether they
Personal Identity Verification (PIV) of Federal Employees and Contractors
 FIPS PUB 201-1 Change Notice 1 FEDERAL INFORMATION PROCESSING STANDARDS PUBLICATION Personal Identity Verification (PIV) of Federal Employees and Contractors Computer Security Division Information Technology
FIPS PUB 201-1 Change Notice 1 FEDERAL INFORMATION PROCESSING STANDARDS PUBLICATION Personal Identity Verification (PIV) of Federal Employees and Contractors Computer Security Division Information Technology
Status: Final. Form Date: 30-SEP-13. Question 1: OPDIV Question 1 Answer: OS
 Status: Final Form Date: 30-SEP-13 Question 1: OPDIV Question 1 Answer: OS Question 2: PIA Unique Identifier (UID): Question 2 Answer: P-2277902-798208 Question 2A: Name: Question 2A Answer: Identity and
Status: Final Form Date: 30-SEP-13 Question 1: OPDIV Question 1 Answer: OS Question 2: PIA Unique Identifier (UID): Question 2 Answer: P-2277902-798208 Question 2A: Name: Question 2A Answer: Identity and
GSA FIPS 201 Evaluation Program
 GSA FIPS 201 Evaluation Program David Temoshok Director, Federal Identity Policy and Management GSA Office of Governmentwide Policy NIST/DHS/TSA TWIC QPL Workshop April 21, 2010 1 HSPD-12 Government-wide
GSA FIPS 201 Evaluation Program David Temoshok Director, Federal Identity Policy and Management GSA Office of Governmentwide Policy NIST/DHS/TSA TWIC QPL Workshop April 21, 2010 1 HSPD-12 Government-wide
The Convergence of IT Security and Physical Access Control
 The Convergence of IT Security and Physical Access Control Using a Single Credential to Secure Access to IT and Physical Resources Executive Summary Organizations are increasingly adopting a model in which
The Convergence of IT Security and Physical Access Control Using a Single Credential to Secure Access to IT and Physical Resources Executive Summary Organizations are increasingly adopting a model in which
Understanding the differences in PIV, PIV-I, PIV-C August 23, 2010
 Federal CIO Council Information Security and Identity Management Committee Identity, Credential, and Access Management Understanding the differences in PIV, PIV-I, PIV-C August 23, 2010 Tim Baldridge AWG
Federal CIO Council Information Security and Identity Management Committee Identity, Credential, and Access Management Understanding the differences in PIV, PIV-I, PIV-C August 23, 2010 Tim Baldridge AWG
IDaaS: Managed Credentials for Local & State Emergency Responders
 IDaaS: Managed Credentials for Local & State Emergency Responders NextgenID ID*TRUST Platform NextgenID - Headquarters USA 10226 San Pedro, Suite 100 San Antonio, TX 78216 +1 (210) 530-9991 www.nextgenid.com
IDaaS: Managed Credentials for Local & State Emergency Responders NextgenID ID*TRUST Platform NextgenID - Headquarters USA 10226 San Pedro, Suite 100 San Antonio, TX 78216 +1 (210) 530-9991 www.nextgenid.com
Moving to Multi-factor Authentication. Kevin Unthank
 Moving to Multi-factor Authentication Kevin Unthank What is Authentication 3 steps of Access Control Identification: The entity makes claim to a particular Identity Authentication: The entity proves that
Moving to Multi-factor Authentication Kevin Unthank What is Authentication 3 steps of Access Control Identification: The entity makes claim to a particular Identity Authentication: The entity proves that
Announcing Approval of Federal Information Processing Standard (FIPS) Publication 201-2,
 This document is scheduled to be published in the Federal Register on 09/05/2013 and available online at http://federalregister.gov/a/2013-21491, and on FDsys.gov Billing Code 3510-13 DEPARTMENT OF COMMERCE
This document is scheduled to be published in the Federal Register on 09/05/2013 and available online at http://federalregister.gov/a/2013-21491, and on FDsys.gov Billing Code 3510-13 DEPARTMENT OF COMMERCE
Frequently Asked Questions
 Frequently Asked Questions Naval VAMOSC Public Key Infrastructure/ Common Access Card (PKI/CAC) Registration and Log in Please Note: A PKI-enabled browser is required for certificate registration and to
Frequently Asked Questions Naval VAMOSC Public Key Infrastructure/ Common Access Card (PKI/CAC) Registration and Log in Please Note: A PKI-enabled browser is required for certificate registration and to
solutions Biometrics integration
 Biometrics integration Challenges Demanding access control and identity authentication requirements drive the need for biometrics. Regulations such as Sarbanes-Oxley (SOX), Health Insurance Portability
Biometrics integration Challenges Demanding access control and identity authentication requirements drive the need for biometrics. Regulations such as Sarbanes-Oxley (SOX), Health Insurance Portability
SPOT FAQ S Frequently Asked Questions
 Signing up for SPOT Training 1. How can I sign up for training? 2. I am having trouble accessing the training site, what do I do? Our training department can help you. Please contact them via email at:
Signing up for SPOT Training 1. How can I sign up for training? 2. I am having trouble accessing the training site, what do I do? Our training department can help you. Please contact them via email at:
NASA PIV smartcards at Headquarters Frequently Asked Questions (FAQ s)
 Frequently Asked Questions (FAQ s) November, 2013 This list of FAQs is a subset of a larger list derived by the Agency. This list is tailored to meet the needs of users at Headquarters. If you do not find
Frequently Asked Questions (FAQ s) November, 2013 This list of FAQs is a subset of a larger list derived by the Agency. This list is tailored to meet the needs of users at Headquarters. If you do not find
Achieving Universal Secure Identity Verification with Convenience and Personal Privacy A PRIVARIS BUSINESS WHITE PAPER
 with Convenience and Personal Privacy version 0.2 Aug.18, 2007 WHITE PAPER CONTENT Introduction... 3 Identity verification and multi-factor authentication..... 4 Market adoption... 4 Making biometrics
with Convenience and Personal Privacy version 0.2 Aug.18, 2007 WHITE PAPER CONTENT Introduction... 3 Identity verification and multi-factor authentication..... 4 Market adoption... 4 Making biometrics
HSPD-12 Homeland Security Presidential Directive #12 Overview
 HSPD-12 Homeland Security Presidential Directive #12 Overview HSPD-12 Stands for Homeland Security Presidential Directive #12. HSPD-12 is the Policy for a Common Identification Standard for Federal Employees
HSPD-12 Homeland Security Presidential Directive #12 Overview HSPD-12 Stands for Homeland Security Presidential Directive #12. HSPD-12 is the Policy for a Common Identification Standard for Federal Employees
WHITE PAPER Usher Mobile Identity Platform
 WHITE PAPER Usher Mobile Identity Platform Security Architecture For more information, visit Usher.com [email protected] Toll Free (US ONLY): 1 888.656.4464 Direct Dial: 703.848.8710 Table of contents Introduction
WHITE PAPER Usher Mobile Identity Platform Security Architecture For more information, visit Usher.com [email protected] Toll Free (US ONLY): 1 888.656.4464 Direct Dial: 703.848.8710 Table of contents Introduction
Expiring Certificates on LincPass Cards
 Expiring Certificates on LincPass Cards The MSA HR office has been receiving questions on how to tell when the certificates expire for the LincPass Cards. The best way is to use Method 2 in the following
Expiring Certificates on LincPass Cards The MSA HR office has been receiving questions on how to tell when the certificates expire for the LincPass Cards. The best way is to use Method 2 in the following
Using FICAM as a model for TSCP Best Prac:ces in Physical Iden:ty and Access Management. TSCP Symposium November 2013
 Using FICAM as a model for TSCP Best Prac:ces in Physical Iden:ty and Access Management TSCP Symposium November 2013 Quantum Secure s Focus on FICAM and Related Standards Complete Suite of Physical Iden:ty
Using FICAM as a model for TSCP Best Prac:ces in Physical Iden:ty and Access Management TSCP Symposium November 2013 Quantum Secure s Focus on FICAM and Related Standards Complete Suite of Physical Iden:ty
US Security Directive FIPS 201
 Security US Security Directive FIPS 201 Compliance Strategies Learn about compliance strategies for governmental agencies in meeting requirements of Homeland Security Presidential Directive 12 (HSPD-12),
Security US Security Directive FIPS 201 Compliance Strategies Learn about compliance strategies for governmental agencies in meeting requirements of Homeland Security Presidential Directive 12 (HSPD-12),
NIST Test Personal Identity Verification (PIV) Cards
 NISTIR 7870 NIST Test Personal Identity Verification (PIV) Cards David A. Cooper http://dx.doi.org/10.6028/nist.ir.7870 NISTIR 7870 NIST Text Personal Identity Verification (PIV) Cards David A. Cooper
NISTIR 7870 NIST Test Personal Identity Verification (PIV) Cards David A. Cooper http://dx.doi.org/10.6028/nist.ir.7870 NISTIR 7870 NIST Text Personal Identity Verification (PIV) Cards David A. Cooper
Use of Common Access Cards (CACs) from Home on Windows 7 without Middleware
 Use of Common Access Cards (CACs) from Home on Windows 7 without Middleware Problem: Microsoft Windows 7 includes a native capability to read and use the newest CACbased PKI certificates without installing
Use of Common Access Cards (CACs) from Home on Windows 7 without Middleware Problem: Microsoft Windows 7 includes a native capability to read and use the newest CACbased PKI certificates without installing
Small Business Administration Privacy Impact Assessment
 Small Business Administration Privacy Impact Assessment Name of Project: Personal Identity Verification (PIV)/ Homeland Security Presidential Directive 12 (HSPD-12) (Note: This PIA is intended to cover
Small Business Administration Privacy Impact Assessment Name of Project: Personal Identity Verification (PIV)/ Homeland Security Presidential Directive 12 (HSPD-12) (Note: This PIA is intended to cover
Get Smart Card Ready. How to Recover Your Old (Expired) Certificates
 How to Recover Your Old (Expired) Certificates If you want to read signed or encrypted email messages that you sent or received using a nowexpired certificate, you first need to recover that certificate
How to Recover Your Old (Expired) Certificates If you want to read signed or encrypted email messages that you sent or received using a nowexpired certificate, you first need to recover that certificate
DEPARTMENT OF DEFENSE GUIDEBOOK FOR CAC-ELIGIBLE CONTRACTORS FOR UNCLASSIFIED NETWORK ACCESS
 DEPARTMENT OF DEFENSE GUIDEBOOK FOR CAC-ELIGIBLE CONTRACTORS FOR UNCLASSIFIED NETWORK ACCESS 21 NOVEMBER 2014 Contents SCOPE CHAPTER 1 INTRODUCTION... 4 1.1 PURPOSE AND BACKGROUND... 4 1.2 POLICY AND REGULATIONS...
DEPARTMENT OF DEFENSE GUIDEBOOK FOR CAC-ELIGIBLE CONTRACTORS FOR UNCLASSIFIED NETWORK ACCESS 21 NOVEMBER 2014 Contents SCOPE CHAPTER 1 INTRODUCTION... 4 1.1 PURPOSE AND BACKGROUND... 4 1.2 POLICY AND REGULATIONS...
Product Testing Programs
 Catalog of USG Product Programs Version 1.0 November 15, 2010 NSTC Subcommittee on s and Identity Management 1. Introduction This Catalog of USG Product Programs (Catalog) supplements the Registry of USG,
Catalog of USG Product Programs Version 1.0 November 15, 2010 NSTC Subcommittee on s and Identity Management 1. Introduction This Catalog of USG Product Programs (Catalog) supplements the Registry of USG,
DUKE ENERGY CENTER BUILDING CARD ACCESS SYSTEM POLICY
 DUKE ENERGY CENTER BUILDING CARD ACCESS SYSTEM POLICY January 19, 2010 I. CARD ACCESS SYSTEM The Childress Klein Charlotte Uptown base building card access system consists of GE Access Card Readers, GE
DUKE ENERGY CENTER BUILDING CARD ACCESS SYSTEM POLICY January 19, 2010 I. CARD ACCESS SYSTEM The Childress Klein Charlotte Uptown base building card access system consists of GE Access Card Readers, GE
Frequently Asked Questions (FAQs) SIPRNet Hardware Token
 Air Force Public Key Infrastructure System Program Office (ESC/HNCDP) Phone: 210-925-2562 / DSN: 945-2562 Web: https://afpki.lackland.af.mil Frequently Asked Questions (FAQs) SIPRNet Hardware Token Updated:
Air Force Public Key Infrastructure System Program Office (ESC/HNCDP) Phone: 210-925-2562 / DSN: 945-2562 Web: https://afpki.lackland.af.mil Frequently Asked Questions (FAQs) SIPRNet Hardware Token Updated:
Information Technology Policy
 Information Technology Policy Identity Protection and Access Management (IPAM) Architectural Standard Identity Management Services ITP Number ITP-SEC013 Category Recommended Policy Contact [email protected]
Information Technology Policy Identity Protection and Access Management (IPAM) Architectural Standard Identity Management Services ITP Number ITP-SEC013 Category Recommended Policy Contact [email protected]
Derived credentials. NIST SP 800-63-1 ( 5.3.5) provides for long term derived credentials
 Daon your trusted Identity Partner Derived Credentials A Use Case Cathy Tilton Daon 1 February 2012 Derived credentials NIST SP 800-63-1 ( 5.3.5) provides for long term derived credentials Derived credential
Daon your trusted Identity Partner Derived Credentials A Use Case Cathy Tilton Daon 1 February 2012 Derived credentials NIST SP 800-63-1 ( 5.3.5) provides for long term derived credentials Derived credential
No additional requirements to use the PIV I card for physical facility access have been identified.
 1. The RFI request document regarding Driver Authentication states that "any one or more of the following methods" will be required: Personal Identification Number (PIN) Non Federal Personal Identity Verification
1. The RFI request document regarding Driver Authentication states that "any one or more of the following methods" will be required: Personal Identification Number (PIN) Non Federal Personal Identity Verification
Help Desk Self Service Quick Start Guide
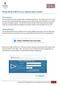 Help Desk Self Service Quick Start Guide Introduction Faculty and Staff can submit support tickets via Help Desk Self- Service. This will give users more control over how they submit helpdesk tickets and
Help Desk Self Service Quick Start Guide Introduction Faculty and Staff can submit support tickets via Help Desk Self- Service. This will give users more control over how they submit helpdesk tickets and
Federal Identity Management Handbook
 September 2005 PUBLIC DRAFT Acknowledgements The Office of Management and Budget and the Federal Identity Credentialing Committee would like to acknowledge the significant contributions of the National
September 2005 PUBLIC DRAFT Acknowledgements The Office of Management and Budget and the Federal Identity Credentialing Committee would like to acknowledge the significant contributions of the National
U.S. Department of Energy Washington, D.C.
 U.S. Department of Energy Washington, D.C. ORDER DOE O 206.2 Approved: SUBJECT: IDENTITY, CREDENTIAL, AND ACCESS MANAGEMENT (ICAM) 1. PURPOSE. To establish requirements and responsibilities for DOE s identity,
U.S. Department of Energy Washington, D.C. ORDER DOE O 206.2 Approved: SUBJECT: IDENTITY, CREDENTIAL, AND ACCESS MANAGEMENT (ICAM) 1. PURPOSE. To establish requirements and responsibilities for DOE s identity,
Emergency Response Official Credentials A Smart Card Alliance White Paper. Salvatore D Agostino CEO, IDmachines LLC sal@idmachines.
 Emergency Response Official Credentials A Smart Card Alliance White Paper Salvatore D Agostino CEO, IDmachines LLC [email protected] Smart Card Alliance Broad collection of professionals working with
Emergency Response Official Credentials A Smart Card Alliance White Paper Salvatore D Agostino CEO, IDmachines LLC [email protected] Smart Card Alliance Broad collection of professionals working with
MAESON MAHERRY. 3 Factor Authentication and what it means to business. Date: 21/10/2013
 MAESON MAHERRY 3 Factor Authentication and what it means to business. Date: 21/10/2013 Concept of identity Identity and Access Management Authoritive Identity Source User Identity Feed and Role Management
MAESON MAHERRY 3 Factor Authentication and what it means to business. Date: 21/10/2013 Concept of identity Identity and Access Management Authoritive Identity Source User Identity Feed and Role Management
esign Online Digital Signature Service
 esign Online Digital Signature Service Government of India Ministry of Communications and Information Technology Department of Electronics and Information Technology Controller of Certifying Authorities
esign Online Digital Signature Service Government of India Ministry of Communications and Information Technology Department of Electronics and Information Technology Controller of Certifying Authorities
2. APPLICABILITY AND SCOPE
 Department of Defense DIRECTIVE NUMBER 1000.25 July 19, 2004 Certified Current as of April 23, 2007 USD(P&R) SUBJECT: DoD Personnel Identity Protection (PIP) Program References: (a) DoD Directive 1000.22,
Department of Defense DIRECTIVE NUMBER 1000.25 July 19, 2004 Certified Current as of April 23, 2007 USD(P&R) SUBJECT: DoD Personnel Identity Protection (PIP) Program References: (a) DoD Directive 1000.22,
TELSTRA RSS CA Subscriber Agreement (SA)
 TELSTRA RSS CA Subscriber Agreement (SA) Last Revision Date: December 16, 2009 Version: Published By: Telstra Corporation Ltd Copyright 2009 by Telstra Corporation All rights reserved. No part of this
TELSTRA RSS CA Subscriber Agreement (SA) Last Revision Date: December 16, 2009 Version: Published By: Telstra Corporation Ltd Copyright 2009 by Telstra Corporation All rights reserved. No part of this
U.S. DEPARTMENT OF COMMERCE UNITED STATES PATENT AND TRADEMARK OFFICE. Privacy Impact Assessment
 U.S. DEPARTMENT OF COMMERCE UNITED STATES PATENT AND TRADEMARK OFFICE Privacy Impact Assessment Personal Identity Verification System Card Management System (HSPD12-PIVS/CMS) PTOI-007-00 September 18,
U.S. DEPARTMENT OF COMMERCE UNITED STATES PATENT AND TRADEMARK OFFICE Privacy Impact Assessment Personal Identity Verification System Card Management System (HSPD12-PIVS/CMS) PTOI-007-00 September 18,
The Benefits of an Industry Standard Platform for Enterprise Sign-On
 white paper The Benefits of an Industry Standard Platform for Enterprise Sign-On The need for scalable solutions to the growing concerns about enterprise security and regulatory compliance can be addressed
white paper The Benefits of an Industry Standard Platform for Enterprise Sign-On The need for scalable solutions to the growing concerns about enterprise security and regulatory compliance can be addressed
HOMELAND SECURITY PRESIDENTIAL DIRECTIVE 12 (HSPD-12) PROGRAM
 Department of Veterans Affairs Washington, DC 20420 VA HANDBOOK 0735 Transmittal Sheet Version 5.5 HOMELAND SECURITY PRESIDENTIAL DIRECTIVE 12 (HSPD-12) PROGRAM 1. REASON FOR ISSUE: This handbook defines
Department of Veterans Affairs Washington, DC 20420 VA HANDBOOK 0735 Transmittal Sheet Version 5.5 HOMELAND SECURITY PRESIDENTIAL DIRECTIVE 12 (HSPD-12) PROGRAM 1. REASON FOR ISSUE: This handbook defines
SENDING AND RECEIVING PROTECTED INFORMATION VIA ELECTRONIC MAIL. Naval Medical Center Portsmouth IMD Training Division
 SENDING AND RECEIVING PROTECTED INFORMATION VIA ELECTRONIC MAIL Naval Medical Center Portsmouth IMD Training Division INTRODUCTION The following slides will help you set up your computer and Microsoft
SENDING AND RECEIVING PROTECTED INFORMATION VIA ELECTRONIC MAIL Naval Medical Center Portsmouth IMD Training Division INTRODUCTION The following slides will help you set up your computer and Microsoft
Identity - Privacy - Security
 Identity - Privacy - Security Systems Security Engineering and Privacy Privacy and Security Workshop 3 Nov 2006 Toronto Recent Digital FIPS Border 201 Motivation Identity Security for Security Privacy
Identity - Privacy - Security Systems Security Engineering and Privacy Privacy and Security Workshop 3 Nov 2006 Toronto Recent Digital FIPS Border 201 Motivation Identity Security for Security Privacy
Required changes to Table 6 2 in FIPS 201
 The PIV Working Group appreciates the opportunity to provide guidance on the initial scope for ICAM Part B. In addressing your request we created three bodies of content: Required changes to Table 6 2
The PIV Working Group appreciates the opportunity to provide guidance on the initial scope for ICAM Part B. In addressing your request we created three bodies of content: Required changes to Table 6 2
IT Operations User Access Management Policies
 1. Approval and Authorisation Completion of the following signature blocks signifies the review and approval of this Process (signed copy held in safe) Name Job Title Signature Date Authored by:-
1. Approval and Authorisation Completion of the following signature blocks signifies the review and approval of this Process (signed copy held in safe) Name Job Title Signature Date Authored by:-
Department of Veterans Affairs VA DIRECTIVE 6510 VA IDENTITY AND ACCESS MANAGEMENT
 Department of Veterans Affairs VA DIRECTIVE 6510 Washington, DC 20420 Transmittal Sheet VA IDENTITY AND ACCESS MANAGEMENT 1. REASON FOR ISSUE: This Directive defines the policy and responsibilities to
Department of Veterans Affairs VA DIRECTIVE 6510 Washington, DC 20420 Transmittal Sheet VA IDENTITY AND ACCESS MANAGEMENT 1. REASON FOR ISSUE: This Directive defines the policy and responsibilities to
Multi-Factor Authentication Protecting Applications and Critical Data against Unauthorized Access
 Multi-Factor Authentication Protecting Applications and Critical Data against Unauthorized Access CONTENTS What is Authentication? Implementing Multi-Factor Authentication Token and Smart Card Technologies
Multi-Factor Authentication Protecting Applications and Critical Data against Unauthorized Access CONTENTS What is Authentication? Implementing Multi-Factor Authentication Token and Smart Card Technologies
FOUR PILLARS FOR A SUCCESSFUL PIV ECOSYSTEM
 FOUR PILLARS FOR A SUCCESSFUL PIV ECOSYSTEM Four Pillars that HSPD-12 Programs must consider for a secure, efficient, interoperable PIV enterprise deployment. Continued HSPD-12 Implementation under OMB
FOUR PILLARS FOR A SUCCESSFUL PIV ECOSYSTEM Four Pillars that HSPD-12 Programs must consider for a secure, efficient, interoperable PIV enterprise deployment. Continued HSPD-12 Implementation under OMB
Strong Authentication for Healthcare
 Strong Authentication for Healthcare Entrust Solutions for Centers for Medicare & Medicaid Services Authentication Compliance Entrust Inc. All All Rights Reserved. 1 1 Entrust is a registered trademark
Strong Authentication for Healthcare Entrust Solutions for Centers for Medicare & Medicaid Services Authentication Compliance Entrust Inc. All All Rights Reserved. 1 1 Entrust is a registered trademark
Strong Identity Authentication for First Responders
 Strong Identity Authentication for First Responders Entrust Solutions for Compliance to U.S. Department of Homeland Security First Responder Authentication Credential (FRAC) Standards Entrust Inc. All
Strong Identity Authentication for First Responders Entrust Solutions for Compliance to U.S. Department of Homeland Security First Responder Authentication Credential (FRAC) Standards Entrust Inc. All
AIE Frequently Asked Questions
 AIE Frequently Asked Questions Q: What is AIE? A: AIE stands for Automated Installation Entry (AIE) The AIE system is designed to leverage technology to increase security for Soldiers, Family Members,
AIE Frequently Asked Questions Q: What is AIE? A: AIE stands for Automated Installation Entry (AIE) The AIE system is designed to leverage technology to increase security for Soldiers, Family Members,
The following questions and responses have been amended from those previously answered on Clarification No. 1, dated August 19, 2014:
 DALLAS/FORT WORTH INTERNATIONAL AIRPORT September 5, 2014 CLARIFICATIONS Re: - Access Control Management System, Deadline for Proposal Submittal: September 22, 2014 at 11:00 a.m. (Central Time) The following
DALLAS/FORT WORTH INTERNATIONAL AIRPORT September 5, 2014 CLARIFICATIONS Re: - Access Control Management System, Deadline for Proposal Submittal: September 22, 2014 at 11:00 a.m. (Central Time) The following
NSF AuthentX Identity Management System (IDMS) Privacy Impact Assessment. Version: 1.1 Date: 12/04/2006. National Science Foundation
 This document has been archived and replaced by piaauthentx1207..0 National Science Foundation NSF AuthentX Identity Management System (IDMS) Privacy Impact Assessment Version: 1.1 Date: 12/04/2006 Table
This document has been archived and replaced by piaauthentx1207..0 National Science Foundation NSF AuthentX Identity Management System (IDMS) Privacy Impact Assessment Version: 1.1 Date: 12/04/2006 Table
The Implementation of Homeland Security Presidential Directive 12
 The Implementation of Homeland Security Presidential Directive 12 David Temoshok Director, Identity Policy and Management GSA Office of Governmentwide Policy Information Security and Privacy Advisory Board
The Implementation of Homeland Security Presidential Directive 12 David Temoshok Director, Identity Policy and Management GSA Office of Governmentwide Policy Information Security and Privacy Advisory Board
MyKey is the digital signature software governed by Malaysia s Digital Signature Act 1997 & is accepted by the courts of law in Malaysia.
 About Digital Signature using MyKey Purpose MyKey is the digital signature software governed by Malaysia s Digital Signature Act 1997 & is accepted by the courts of law in Malaysia. A document digitally
About Digital Signature using MyKey Purpose MyKey is the digital signature software governed by Malaysia s Digital Signature Act 1997 & is accepted by the courts of law in Malaysia. A document digitally
