Enrolling with PIV and PIV-I Velocity Enrollment Manager
|
|
|
- Joan Hood
- 10 years ago
- Views:
Transcription
1 Enrolling with PIV and PIV-I Velocity Enrollment Manager
2 Overview The Homeland Security Presidential Directive 12 (HSPD-12) called for a common identification standard to be adopted by all Federal Government Agencies. The Person Identity Verification (PIV) credential has been issued to over 8 million Federal employees (almost four million people). The PIV credential is a smart card operating at MHz with a specific data module called End-Point. Certain data is available by a free read, while other personal data requires a personal (secret) PIN (personal identification number) to access (for example the required biometric fingerprint data). PIV card users can utilize their cards in Physical Access Control Systems (PACS) in a number of ways based on the required level of assurance at the specific locations they are permitted to access. At the lowest level of assurance a free read of the Card Holder Unique Identifier (CHUID) data object, and at the highest level of assurance, a multi-factor authentication using Public Key Infrastructure (PKI). The CHIUD contains a Federal Agency Smart Credential (FASC-N), which is used to enroll a user in Velocity, providing a unique credential number for use in the Physical Access Control System (PACS). In a PKI implementation, the FASC-N is used but the certificates on the card (the card certificate in the case of contactless CAK and the Person Certificate in the case of contact PAK ) are used to validate the card and user. For Government contractors, cards are issued with the same card data module, and the same CHUID, however the first three fields of the FASC-N contain only 9 s. These cards are called PIV-I (interoperable). Correct implementation of these cards requires the PACS to utilize the Universal Unique Identification (UUID) number rather that the FASCN. PIV-I cards include the PKI certificates that enable the CAK/PAK schema. Velocity provides the ability to enroll PIV cards on HIRSCH PACS with the appropriate read and MATCH custom settings. The following pages will assist in establishing the devices and Enrollment Manager Settings to enroll the PIV and PIV-I cards into the Velocity system. Page 1
3 To have the PIV read into the Velocity access control system the following setups need to be established. 1. Create the following User Defined Fields in Enrollment Manager. Name Parsing Text Agency Code System Code Credential Credential Series Individual Credential Issue Person Identifier Organizational Category Organization Identifier Person Org Assoc Category Expiration Date Date Locate under Enrollment Manager > Tools > User Defined Fields. Figure 1 - User Defined Fields Page 2
4 2. For PIV the Name field must be Parsed, split between First, Middle and Last Name. Properties Enrollment Manager Tools > Preferences Change the UDF Name Parsing field to the UDF defined. Figure 2 Enrollment Manager Preferences 3. Establish the device for reading the card and install by USB. The driver for the device must be downloaded from the internet as Velocity does not supply the driver. a. SCR3310 b. SCR3311 Figure 3 - CRSCMCEUSB Card Reader Page 3
5 4. The RUU device may also be used to enroll the PIV card. Be sure to have the correct firmware installed on the device using the Cogent software. This will allow for the addressing TCP/IP and will enable the choice for enrollment on the Device Configuration RUU tab. Figure 4 - RUU PIV version 5. If an Enrollment Station is being used, the Special Handling needs to be established under Device Configuration. Enrollment Manager > Tools > Device Configuration > Credential Enrollment Figure 5 - Device Configuration Special Handling Note: The reader used for the enrollment must have the MATCH custom settings as well as the correct firmware for the data to pass correctly into the Enrollment Manager Fields. Page 4
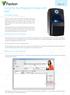
6 6. Select Enrollment Manager Tools > Device Configuration and map the UDF fields to each device used for card reads. Figure 6 UDF Field Mapping for Enrollment Click and Drag to UDF Field. Note: For PIV-I cards, the UDF Field of UUID/GUID is the only field that is necessary to map for credentialing. This field will need to be added to the UDF Fields if both types of cards are being enrolled into Enrollment Manager if previously not added. Enrollment Manager > Tools > User Defined Fields be sure to select Unique Text as the UDF type. 7. Close and reopen Enrollment Manager. There should now be a scan button 8. Select Add Person and select the scan button. Page 5 Figure 7 - Card Reader PIV Figure 8 Users PIN code to unlock data.
7 9. Select the device to read the card if multiple devices are being used. 10. To read all the fields, the card holder will need to enter their PIN to unlock the card. This applies to both PIV and PIV-I card. Once OK is selected, the card will read and the fields will show the data. [Give it a few seconds, and the data will fill in the fields above, and also the output window.]. 11. Click Accept for the data to populate the UDF fields in Enrollment Manager. Figure 10 Scanned Data from PIV/TWIC Card Page 6 Figure 9 Enrolled TWIC from Scan Note the UUID/GUID is all zeros.
8 12. Click Apply to download. You are now ready to issue a credential. Page 7
9 For PIV Credentials bit FASCN 13. Add New Credential Figure 11 - Add New Credential - UDF MATCH Note: The PIV and PIV-I cards may use IDF 2 for use with just the card presented at the reader. If any other IDF is selected, a PIN will be required. This should never be the secret PIN that the user has to unlock the data on the card. The 200-bit FASCN will populate the UDF concatenate window. Select the corresponding UDF fields created and click OK. This will produce the FASCN that will be used for the card read. Page 8
10 To locate the UDF concatenate window, select the UDF button on the Data field. Figure 12 UDF button on Credential General Tab This will supply a 32 digit number in both the Data field and the FASCN field. Figure 13- FASCN Assignment Select the Function Tab and assign the appropriate Door Group for this individual. All Limits o Threat Authority and 2 Person Rule may be assigned Options o Special Needs Access and Passback Executive Override may be assigned Click OK and the PIV credential has been issued. Verification of download may be seen in the Event Viewer. Page 9
11 For PIV-I Credentials The UUID/GUID is the unique text that is used for the credential. Using the contact reader, the card will be read just like the PIV card, with the addition of the UUID. To read all the data the card holder will also need to enter their PIN number. NOTE: The PIV-I card has 9999 instead of a Government Agency Code. Assign a Door Group function and any Limits or Options for this credential. Figure 14 - PIV-I card with PIN Figure Identive 15 The UUID/ Learning GUID Center will have 1900 numbers Carnegie and Building letters. B Santa Ana, California Page 10
12 .Door Properties - PIV HID iclass reader with 200 bit firmware using a MATCH2 set with Custom Entry Reader Setup Tab Special Handling- 200 bit FASCN Bypass Present PIV card and access granted. Figure 16 - Entry Reader Settings Note: MATCH special settings for the corresponding bit formats 64 bits Custom 24,25,or bits Custom 18, 20 or bits Custom 18,20,21,24,25,26,27,28,and 29[PIV only] 200 bits Custom 27,28,or 29 Note: Along with the MATCH custom settings, the firmware on the reader must also correspond to the bit format. Page 11
13 For PIV-I cards HID iclass with 128 bit firmware and MATCH2 with Custom The PIV-I card uses the FASCN Bypass to allow the UUID to be used Along with the Wiegand HEX Pass-through, the card reads the same at the door The Door Properties is different, using the Enable Wiegand Hex Pass- Through to enable the UUID/GUID to pass through Presented to the reader, the PIV-I card will issue an access grant If the reader has the ability to read both formats, then the cards enrolled will read by presenting the card o If the Agency Code is all 9s the reader will pass through the UUID Velocity Enrollment Manager has all the ability to read both PIV and PIV-I cards. The trick is to make sure all the corresponding devices are established with the correct formats. Enrollment Station o MATCH Custom settings o Reader firmware Device Configuration o User Defined Fields to map the data o Name Parsing is PIV cards are being read Scanning the card o PIN needed for name field Door Properties o Reader settings Page 12
Velocity 3.1 KB640 Release Notes
 Velocity 3.1 KB640 Release Notes Copyright 2013, Identive Group. Released June 1, 2013. Overview The Velocity 3.1 KB640 release supports newer PIV cards which use the updated FIPS201 data layout, allows
Velocity 3.1 KB640 Release Notes Copyright 2013, Identive Group. Released June 1, 2013. Overview The Velocity 3.1 KB640 release supports newer PIV cards which use the updated FIPS201 data layout, allows
Smart Cards and Biometrics in Physical Access Control Systems
 Smart Cards and Biometrics in Physical Access Control Systems Robert J. Merkert, Sr. Vice President of Sales Americas Biometric Consortium 2005 Conference September 21, 2005 All Company and/or product
Smart Cards and Biometrics in Physical Access Control Systems Robert J. Merkert, Sr. Vice President of Sales Americas Biometric Consortium 2005 Conference September 21, 2005 All Company and/or product
Federal Identity, Credentialing, and Access Management. Personal Identity Verification Interoperable (PIV-I) Test Plan. Version 1.1.
 Federal Identity, Credentialing, and Access Management Personal Identity Verification Interoperable (PIV-I) Test Plan Version 1.1.0 Final February 22, 2011 Table of Contents 1 Introduction... 1 1.1 Background...
Federal Identity, Credentialing, and Access Management Personal Identity Verification Interoperable (PIV-I) Test Plan Version 1.1.0 Final February 22, 2011 Table of Contents 1 Introduction... 1 1.1 Background...
What Does it Mean to be PIVish in PACS ICAM PIV in E-PACS Guidance v2.0.2 the short form. December 3, 2012
 Federal CIO Council Information Security and Identity Management Committee IDManagement.gov What Does it Mean to be PIVish in PACS ICAM PIV in E-PACS Guidance v2.0.2 the short form December 3, 2012 HSPD-12
Federal CIO Council Information Security and Identity Management Committee IDManagement.gov What Does it Mean to be PIVish in PACS ICAM PIV in E-PACS Guidance v2.0.2 the short form December 3, 2012 HSPD-12
Required changes to Table 6 2 in FIPS 201
 The PIV Working Group appreciates the opportunity to provide guidance on the initial scope for ICAM Part B. In addressing your request we created three bodies of content: Required changes to Table 6 2
The PIV Working Group appreciates the opportunity to provide guidance on the initial scope for ICAM Part B. In addressing your request we created three bodies of content: Required changes to Table 6 2
Strong Authentication for PIV and PIV-I using PKI and Biometrics
 Strong Authentication for PIV and PIV-I using PKI and Biometrics Adam Shane PSP, Product Manager and Sr. Systems Design Architect AMAG Technology Bob Fontana CSCIP/G, Vice President-Federal Identity Codebench/HID
Strong Authentication for PIV and PIV-I using PKI and Biometrics Adam Shane PSP, Product Manager and Sr. Systems Design Architect AMAG Technology Bob Fontana CSCIP/G, Vice President-Federal Identity Codebench/HID
GSA FIPS 201 Evaluation Program
 GSA FIPS 201 Evaluation Program David Temoshok Director, Federal Identity Policy and Management GSA Office of Governmentwide Policy NIST/DHS/TSA TWIC QPL Workshop April 21, 2010 1 HSPD-12 Government-wide
GSA FIPS 201 Evaluation Program David Temoshok Director, Federal Identity Policy and Management GSA Office of Governmentwide Policy NIST/DHS/TSA TWIC QPL Workshop April 21, 2010 1 HSPD-12 Government-wide
intertrax Suite intertrax exchange intertrax monitor intertrax connect intertrax PIV manager User Guide Version 3 2011
 intertrax Suite intertrax exchange intertrax monitor intertrax connect intertrax PIV manager User Guide Version 3 2011 Copyright 2003-2011 by Salamander Technologies, Inc. Protected by US Patents 5,573,278;
intertrax Suite intertrax exchange intertrax monitor intertrax connect intertrax PIV manager User Guide Version 3 2011 Copyright 2003-2011 by Salamander Technologies, Inc. Protected by US Patents 5,573,278;
solutions Biometrics integration
 Biometrics integration Challenges Demanding access control and identity authentication requirements drive the need for biometrics. Regulations such as Sarbanes-Oxley (SOX), Health Insurance Portability
Biometrics integration Challenges Demanding access control and identity authentication requirements drive the need for biometrics. Regulations such as Sarbanes-Oxley (SOX), Health Insurance Portability
GOALS (2) The goal of this training module is to increase your awareness of HSPD-12 and the corresponding technical standard FIPS 201.
 PERSONAL IDENTITY VERIFICATION (PIV) OVERVIEW INTRODUCTION (1) Welcome to the Homeland Security Presidential Directive 12 (HSPD-12) Personal Identity Verification (PIV) Overview module, designed to familiarize
PERSONAL IDENTITY VERIFICATION (PIV) OVERVIEW INTRODUCTION (1) Welcome to the Homeland Security Presidential Directive 12 (HSPD-12) Personal Identity Verification (PIV) Overview module, designed to familiarize
Practical Challenges in Adopting PIV/PIV-I
 UNCLASSIFIED Practical Challenges in Adopting PIV/PIV-I Hank Morris UNCLASSIFIED 2 UNCLASSIFIED // FOUO Purpose and Agenda Purpose: Explore the policy, process, and mechanisms to securely leverage biometrics
UNCLASSIFIED Practical Challenges in Adopting PIV/PIV-I Hank Morris UNCLASSIFIED 2 UNCLASSIFIED // FOUO Purpose and Agenda Purpose: Explore the policy, process, and mechanisms to securely leverage biometrics
Audio: This overview module contains an introduction, five lessons, and a conclusion.
 Homeland Security Presidential Directive 12 (HSPD 12) Overview Audio: Welcome to the Homeland Security Presidential Directive 12 (HSPD 12) overview module, the first in a series of informational modules
Homeland Security Presidential Directive 12 (HSPD 12) Overview Audio: Welcome to the Homeland Security Presidential Directive 12 (HSPD 12) overview module, the first in a series of informational modules
The Convergence of IT Security and Physical Access Control
 The Convergence of IT Security and Physical Access Control Using a Single Credential to Secure Access to IT and Physical Resources Executive Summary Organizations are increasingly adopting a model in which
The Convergence of IT Security and Physical Access Control Using a Single Credential to Secure Access to IT and Physical Resources Executive Summary Organizations are increasingly adopting a model in which
NIST Test Personal Identity Verification (PIV) Cards
 NISTIR 7870 NIST Test Personal Identity Verification (PIV) Cards David A. Cooper http://dx.doi.org/10.6028/nist.ir.7870 NISTIR 7870 NIST Text Personal Identity Verification (PIV) Cards David A. Cooper
NISTIR 7870 NIST Test Personal Identity Verification (PIV) Cards David A. Cooper http://dx.doi.org/10.6028/nist.ir.7870 NISTIR 7870 NIST Text Personal Identity Verification (PIV) Cards David A. Cooper
NOAA HSPD-12 PIV-II Implementation October 23, 2007. Who is responsible for implementation of HSPD-12 PIV-II?
 NOAA HSPD-12 PIV-II Implementation What is HSPD-12? Homeland Security Presidential Directive 12 (HSPD-12) is a Presidential requirement signed on August 27, 2004 requiring Federal agencies comply with
NOAA HSPD-12 PIV-II Implementation What is HSPD-12? Homeland Security Presidential Directive 12 (HSPD-12) is a Presidential requirement signed on August 27, 2004 requiring Federal agencies comply with
NIST s FIPS 201: Personal Identity Verification (PIV) of Federal Employees and Contractors Masaryk University in Brno Faculty of Informatics
 NIST s FIPS 201: Personal Identity Verification (PIV) of Federal Employees and Contractors Masaryk University in Brno Faculty of Informatics Jan Krhovják Outline Introduction and basics of PIV Minimum
NIST s FIPS 201: Personal Identity Verification (PIV) of Federal Employees and Contractors Masaryk University in Brno Faculty of Informatics Jan Krhovják Outline Introduction and basics of PIV Minimum
HSPD-12 Implementation Architecture Working Group Concept Overview. Version 1.0 March 17, 2006
 HSPD-12 Implementation Architecture Working Group Concept Overview Version 1.0 March 17, 2006 Table of Contents 1 PIV Lifecycle... 3 2 High Level Component Interaction Diagram... 4 3 PIV Infrastructure
HSPD-12 Implementation Architecture Working Group Concept Overview Version 1.0 March 17, 2006 Table of Contents 1 PIV Lifecycle... 3 2 High Level Component Interaction Diagram... 4 3 PIV Infrastructure
The Convergence of IT Security and Physical Access Control
 The Convergence of IT Security and Physical Access Control Using a Single Credential to Secure Access to IT and Physical Resources Executive Summary Organizations are increasingly adopting a model in which
The Convergence of IT Security and Physical Access Control Using a Single Credential to Secure Access to IT and Physical Resources Executive Summary Organizations are increasingly adopting a model in which
Government Compliance Document FIPS 201, FIPS 197, FIPS 140-2
 Government Compliance Document FIPS 201, FIPS 197, FIPS 140-2 AMAG Technology has been providing tailored and unified security solutions across a range of government agencies facilities for many years.
Government Compliance Document FIPS 201, FIPS 197, FIPS 140-2 AMAG Technology has been providing tailored and unified security solutions across a range of government agencies facilities for many years.
Glossary (from the Velocity 3.5 SP1 Online Help)
 (from the Velocity 3.5 SP1 Online Help) 2-Person Rule This rule provides a high level of security access control for specialized areas, by requiring two authorized persons to be present to enter or exit
(from the Velocity 3.5 SP1 Online Help) 2-Person Rule This rule provides a high level of security access control for specialized areas, by requiring two authorized persons to be present to enter or exit
Employee Express - PIV Card Registration Instructions
 Employee Express - PIV Card Registration Instructions Steps for Registering your GSA Access/PIV Card 1. Navigate to https://www.employeeexpress.gov/defaultlogin.aspx. 2. Insert your GSA Access Card* into
Employee Express - PIV Card Registration Instructions Steps for Registering your GSA Access/PIV Card 1. Navigate to https://www.employeeexpress.gov/defaultlogin.aspx. 2. Insert your GSA Access Card* into
1. The human guard at the access control entry point determines whether the PIV Card appears to be genuine and has not been altered in any way.
 + Expiration date + Agency card serial number (back of card) + Issuer identification (back of card). The PIV Card may also bear the following optional components: + Agency name and/or department + Department
+ Expiration date + Agency card serial number (back of card) + Issuer identification (back of card). The PIV Card may also bear the following optional components: + Agency name and/or department + Department
Guide for Setting Up Your Multi-Factor Authentication Account and Using Multi-Factor Authentication. Mobile App Activation
 Guide for Setting Up Your Multi-Factor Authentication Account and Using Multi-Factor Authentication Mobile App Activation Before you can activate the mobile app you must download it. You can have up to
Guide for Setting Up Your Multi-Factor Authentication Account and Using Multi-Factor Authentication Mobile App Activation Before you can activate the mobile app you must download it. You can have up to
intertrax MOBILE PIV
 intertrax MOBILE PIV Personnel Identification Verification Software User Guide Version 4 2012 Copyright 2003-2012 by Salamander Technologies, Inc. Protected by US Patents 5,573,278; 5,596,652; 5,793,882;
intertrax MOBILE PIV Personnel Identification Verification Software User Guide Version 4 2012 Copyright 2003-2012 by Salamander Technologies, Inc. Protected by US Patents 5,573,278; 5,596,652; 5,793,882;
Life After PIV. Authentication In Federated Spaces. Presented to. Card Tech/Secure Tech. May 2009. By Lynne Prince Defense Manpower Data Center
 Life After PIV Authentication In Federated Spaces Presented to Card Tech/Secure Tech By Lynne Prince Defense Manpower Data Center Interoperability with HSPD12 Capability PIV provides a secure common credential,
Life After PIV Authentication In Federated Spaces Presented to Card Tech/Secure Tech By Lynne Prince Defense Manpower Data Center Interoperability with HSPD12 Capability PIV provides a secure common credential,
STATEMENT OF WORK. For
 STATEMENT OF WORK For Credentialing and Validation Support for DC Homeland Security & Emergency Management Agency (DC HSEMA) IN SUPPORT OF THE GOVERNMENT OF THE DISTRICT OF COLUMBIA November 15, 2012 1.
STATEMENT OF WORK For Credentialing and Validation Support for DC Homeland Security & Emergency Management Agency (DC HSEMA) IN SUPPORT OF THE GOVERNMENT OF THE DISTRICT OF COLUMBIA November 15, 2012 1.
Guide for Setting Up Your Multi-Factor Authentication Account and Using Multi-Factor Authentication
 Guide for Setting Up Your Multi-Factor Authentication Account and Using Multi-Factor Authentication This document serves as a How To reference guide for employees to execute the following MFA tasks: 1.
Guide for Setting Up Your Multi-Factor Authentication Account and Using Multi-Factor Authentication This document serves as a How To reference guide for employees to execute the following MFA tasks: 1.
2. Each server or domain controller requires its own server certificate, DoD Root Certificates and enterprise validator installed.
 Purpose and Scope The purpose of this policy is to define the roles and responsibilities on implementing the Homeland Security Presidential Directive 12 (HSPD-12) Logical Access Control (LAC) throughout
Purpose and Scope The purpose of this policy is to define the roles and responsibilities on implementing the Homeland Security Presidential Directive 12 (HSPD-12) Logical Access Control (LAC) throughout
SAGEM MA520 READERS FINGER & SMART CARD ENROLLMENT
 System Galaxy Quick Guide CONFIGURATION AND OPERATION SAGEM MA520 READERS FINGER & SMART CARD ENROLLMENT SG 10.2.0 MAR 2013 Page 2 System Galaxy Biometric Guide for Sagem MA520 & MIFARE Cards Configuring
System Galaxy Quick Guide CONFIGURATION AND OPERATION SAGEM MA520 READERS FINGER & SMART CARD ENROLLMENT SG 10.2.0 MAR 2013 Page 2 System Galaxy Biometric Guide for Sagem MA520 & MIFARE Cards Configuring
US Security Directive FIPS 201
 Security US Security Directive FIPS 201 Compliance Strategies Learn about compliance strategies for governmental agencies in meeting requirements of Homeland Security Presidential Directive 12 (HSPD-12),
Security US Security Directive FIPS 201 Compliance Strategies Learn about compliance strategies for governmental agencies in meeting requirements of Homeland Security Presidential Directive 12 (HSPD-12),
Expiring Certificates on LincPass Cards
 Expiring Certificates on LincPass Cards The MSA HR office has been receiving questions on how to tell when the certificates expire for the LincPass Cards. The best way is to use Method 2 in the following
Expiring Certificates on LincPass Cards The MSA HR office has been receiving questions on how to tell when the certificates expire for the LincPass Cards. The best way is to use Method 2 in the following
Allegion AD-300 Installation Application Note. 1.0 Hardware Requirements. 2.0 Software/Licensing Requirements
 Allegion Schlage AD-300 networked, hardwired locks can be integrated seamlessly with the Doors.NET software when used with the NXT-MSC (Mercury-Powered controllers). You can connect and communicate with
Allegion Schlage AD-300 networked, hardwired locks can be integrated seamlessly with the Doors.NET software when used with the NXT-MSC (Mercury-Powered controllers). You can connect and communicate with
NACCU 2013. Migrating to Contactless: 2013 1
 NACCU 2013 Migrating to Contactless: 2013 1 AGENDA The demise of cards has been predicted for many years. When will this really happen? This presentation by two card industry experts will cover the rise
NACCU 2013 Migrating to Contactless: 2013 1 AGENDA The demise of cards has been predicted for many years. When will this really happen? This presentation by two card industry experts will cover the rise
Implementing Federal Personal Identity Verification for VMware View. By Bryan Salek, Federal Desktop Systems Engineer, VMware
 Implementing Federal Personal Identity Verification for VMware View By Bryan Salek, Federal Desktop Systems Engineer, VMware Technical WHITE PAPER Introduction This guide explains how to implement authentication
Implementing Federal Personal Identity Verification for VMware View By Bryan Salek, Federal Desktop Systems Engineer, VMware Technical WHITE PAPER Introduction This guide explains how to implement authentication
GAO PERSONAL ID VERIFICATION. Agencies Should Set a Higher Priority on Using the Capabilities of Standardized Identification Cards
 GAO United States Government Accountability Office Report to Congressional Requesters September 2011 PERSONAL ID VERIFICATION Agencies Should Set a Higher Priority on Using the Capabilities of Standardized
GAO United States Government Accountability Office Report to Congressional Requesters September 2011 PERSONAL ID VERIFICATION Agencies Should Set a Higher Priority on Using the Capabilities of Standardized
Issuance and use of PIV at FAA
 Issuance and use of PIV at FAA Presented to: Government Smart Card Interagency Advisory Board By: Ed Ebright, Division Manager, ID Media Division Date: May 2011 Agenda What we use PIV Card Status FAA HSPD-12
Issuance and use of PIV at FAA Presented to: Government Smart Card Interagency Advisory Board By: Ed Ebright, Division Manager, ID Media Division Date: May 2011 Agenda What we use PIV Card Status FAA HSPD-12
Jolly Encoder Configuration Guide
 JOLLY TECHNOLOGIES Jolly Encoder Configuration Guide The purpose of this guide is to document the supported hardware, media and configuration process for the Jolly Encoder. Jolly Encoder The Jolly Encoder
JOLLY TECHNOLOGIES Jolly Encoder Configuration Guide The purpose of this guide is to document the supported hardware, media and configuration process for the Jolly Encoder. Jolly Encoder The Jolly Encoder
Using the ievo fingerprint reader with Net2
 Using the ievo fingerprint reader with How does it work? The ievo system stores the encoded fingerprint information within each reader. Once registered on the enrolment reader, the fingerprint data is
Using the ievo fingerprint reader with How does it work? The ievo system stores the encoded fingerprint information within each reader. Once registered on the enrolment reader, the fingerprint data is
U.S. Department of Housing and Urban Development
 U.S. Department of Housing and Urban Development PRIVACY IMPACT ASSESSMENT FOR: PERSONAL IDENTITY VERIFICATION (PIV) PROCESS TECHNOLOGY AND DATABASE IN COMPLIANCE WITH HOMELAND SECURITY PRESIDENTIAL DIRECTIVE
U.S. Department of Housing and Urban Development PRIVACY IMPACT ASSESSMENT FOR: PERSONAL IDENTITY VERIFICATION (PIV) PROCESS TECHNOLOGY AND DATABASE IN COMPLIANCE WITH HOMELAND SECURITY PRESIDENTIAL DIRECTIVE
IDaaS: Managed Credentials for Local & State Emergency Responders
 IDaaS: Managed Credentials for Local & State Emergency Responders NextgenID ID*TRUST Platform NextgenID - Headquarters USA 10226 San Pedro, Suite 100 San Antonio, TX 78216 +1 (210) 530-9991 www.nextgenid.com
IDaaS: Managed Credentials for Local & State Emergency Responders NextgenID ID*TRUST Platform NextgenID - Headquarters USA 10226 San Pedro, Suite 100 San Antonio, TX 78216 +1 (210) 530-9991 www.nextgenid.com
Understanding the differences in PIV, PIV-I, PIV-C August 23, 2010
 Federal CIO Council Information Security and Identity Management Committee Identity, Credential, and Access Management Understanding the differences in PIV, PIV-I, PIV-C August 23, 2010 Tim Baldridge AWG
Federal CIO Council Information Security and Identity Management Committee Identity, Credential, and Access Management Understanding the differences in PIV, PIV-I, PIV-C August 23, 2010 Tim Baldridge AWG
Check Point FDE integration with Digipass Key devices
 INTEGRATION GUIDE Check Point FDE integration with Digipass Key devices 1 VASCO Data Security Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document
INTEGRATION GUIDE Check Point FDE integration with Digipass Key devices 1 VASCO Data Security Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document
I N F O R M A T I O N S E C U R I T Y
 NIST Special Publication 800-73-3 Interfaces for Personal Identity Verification Part 1: End-Point PIV Card Application Namespace, Data Model and Representation Ramaswamy Chandramouli David Cooper James
NIST Special Publication 800-73-3 Interfaces for Personal Identity Verification Part 1: End-Point PIV Card Application Namespace, Data Model and Representation Ramaswamy Chandramouli David Cooper James
User Guide Remote PIV to VDI Using a PIV Card
 User Guide Remote PIV to VDI Using a PIV Card Energy IT Services (IM-64) March 2015 Authors Prepared By Matthew Cummings Senior Systems Engineer IM-64 Version Control Date Version Document Revision Description
User Guide Remote PIV to VDI Using a PIV Card Energy IT Services (IM-64) March 2015 Authors Prepared By Matthew Cummings Senior Systems Engineer IM-64 Version Control Date Version Document Revision Description
S-SupremaConfigurationGuide-DOC 7/23/2014. Suprema Biometrics Configuration Guide ACS OnSite Aparato
 S-SupremaConfigurationGuide-DOC 7/23/2014 Suprema Biometrics Configuration Guide ACS OnSite Aparato Page 2 Suprema Configuration Guide ACS OnSite Aparato Table of Contents 1. SUPREMA BIOSTAR CONFIGURATION...
S-SupremaConfigurationGuide-DOC 7/23/2014 Suprema Biometrics Configuration Guide ACS OnSite Aparato Page 2 Suprema Configuration Guide ACS OnSite Aparato Table of Contents 1. SUPREMA BIOSTAR CONFIGURATION...
The Government-wide Implementation of Biometrics for HSPD-12
 The Government-wide Implementation of Biometrics for HSPD-12 David Temoshok Director, Identity Policy and Management GSA Office of Governmentwide Policy September 24, 2008 1 The HSPD-12 Mandate Home Security
The Government-wide Implementation of Biometrics for HSPD-12 David Temoshok Director, Identity Policy and Management GSA Office of Governmentwide Policy September 24, 2008 1 The HSPD-12 Mandate Home Security
Physical Access Control System (PACS) in a Federal Identity, Credentialing and Access Management (FICAM) Framework
 Physical Access Control System (PACS) in a Federal Identity, Credentialing and Access Management (FICAM) Framework PACS Best Practices using PKI-Authentication A SIA White Paper Security Industry Association
Physical Access Control System (PACS) in a Federal Identity, Credentialing and Access Management (FICAM) Framework PACS Best Practices using PKI-Authentication A SIA White Paper Security Industry Association
Get Smart Card Ready. How to Recover Your Old (Expired) Certificates
 How to Recover Your Old (Expired) Certificates If you want to read signed or encrypted email messages that you sent or received using a nowexpired certificate, you first need to recover that certificate
How to Recover Your Old (Expired) Certificates If you want to read signed or encrypted email messages that you sent or received using a nowexpired certificate, you first need to recover that certificate
VeriSign PKI Client Government Edition v 1.5. VeriSign PKI Client Government. VeriSign PKI Client VeriSign, Inc. Government.
 END USER S GUIDE VeriSign PKI Client Government Edition v 1.5 End User s Guide VeriSign PKI Client Government Version 1.5 Administrator s Guide VeriSign PKI Client VeriSign, Inc. Government Copyright 2010
END USER S GUIDE VeriSign PKI Client Government Edition v 1.5 End User s Guide VeriSign PKI Client Government Version 1.5 Administrator s Guide VeriSign PKI Client VeriSign, Inc. Government Copyright 2010
A Recommendation for the Use of PIV Credentials in Physical Access Control Systems (PACS)
 NIST Special Publication 800-116 A Recommendation for the Use of PIV Credentials in Physical Access Control Systems (PACS) William MacGregor Ketan Mehta David Cooper Karen Scarfone I N F O R M A T I O
NIST Special Publication 800-116 A Recommendation for the Use of PIV Credentials in Physical Access Control Systems (PACS) William MacGregor Ketan Mehta David Cooper Karen Scarfone I N F O R M A T I O
How to Use Your LincPass Credential
 Your LincPass is your USDA personal identity verification (PIV) card. This guide explains how to use your card and PIN to access and protect USDA network and computer resources. What You ll Need to Get
Your LincPass is your USDA personal identity verification (PIV) card. This guide explains how to use your card and PIN to access and protect USDA network and computer resources. What You ll Need to Get
Edge Metrics Data Center User Manual
 Edge Metrics Data Center User Manual Introduction EMDC is an Internet based, Facility Access Control Solution for small to medium size businesses, property management firms, schools, religious facilities,
Edge Metrics Data Center User Manual Introduction EMDC is an Internet based, Facility Access Control Solution for small to medium size businesses, property management firms, schools, religious facilities,
HSPD-12 Homeland Security Presidential Directive #12 Overview
 HSPD-12 Homeland Security Presidential Directive #12 Overview HSPD-12 Stands for Homeland Security Presidential Directive #12. HSPD-12 is the Policy for a Common Identification Standard for Federal Employees
HSPD-12 Homeland Security Presidential Directive #12 Overview HSPD-12 Stands for Homeland Security Presidential Directive #12. HSPD-12 is the Policy for a Common Identification Standard for Federal Employees
Announcing Approval of Federal Information Processing Standard (FIPS) Publication 201-2,
 This document is scheduled to be published in the Federal Register on 09/05/2013 and available online at http://federalregister.gov/a/2013-21491, and on FDsys.gov Billing Code 3510-13 DEPARTMENT OF COMMERCE
This document is scheduled to be published in the Federal Register on 09/05/2013 and available online at http://federalregister.gov/a/2013-21491, and on FDsys.gov Billing Code 3510-13 DEPARTMENT OF COMMERCE
Physical Access Control with BACnet White Paper
 Physical Access Control with BACnet White Paper Abstract This document outlines the use of existing definitions of as well as extensions to ANSI/ASHRAE 135-2004 BACnet to enable the implementation of and
Physical Access Control with BACnet White Paper Abstract This document outlines the use of existing definitions of as well as extensions to ANSI/ASHRAE 135-2004 BACnet to enable the implementation of and
DIGIPASS KEY series and smart card series for Juniper SSL VPN Authentication
 DIGIPASS KEY series and smart card series for Juniper SSL VPN Authentication Certificate Based 2010 Integration VASCO Data Security. Guideline All rights reserved. Page 1 of 31 Disclaimer Disclaimer of
DIGIPASS KEY series and smart card series for Juniper SSL VPN Authentication Certificate Based 2010 Integration VASCO Data Security. Guideline All rights reserved. Page 1 of 31 Disclaimer Disclaimer of
Tactics, Techniques, & Procedures (TTP) Dual Persona Personal Identity Verification (PIV) Authorization Certificate
 Tactics, Techniques, & Procedures (TTP) Dual Persona Personal Identity Verification (PIV) Authorization Certificate Version 3.0 23 Jan 2012 This document is not to be distributed or changed without express
Tactics, Techniques, & Procedures (TTP) Dual Persona Personal Identity Verification (PIV) Authorization Certificate Version 3.0 23 Jan 2012 This document is not to be distributed or changed without express
Document Digital Signature
 Supplier handbook Software Configuration for Digital Signature and Timestamp to certificate-based signature Document objectives and structure The document aims to support suppliers during the following
Supplier handbook Software Configuration for Digital Signature and Timestamp to certificate-based signature Document objectives and structure The document aims to support suppliers during the following
Guard All Security Symposium. Identity and Access Management
 Guard All Security Symposium Identity and Access Management The Complex Digital World Welcome to the Identiverse Segments / Brands Product Offerings Applications ID Management Solutions Governmental credentialing
Guard All Security Symposium Identity and Access Management The Complex Digital World Welcome to the Identiverse Segments / Brands Product Offerings Applications ID Management Solutions Governmental credentialing
L-1 Fingerprint Reader Solutions. V-Flex 4G
 L- Fingerprint Reader Solutions V-Flex 4G 4G Biometric Performance Redefined with a Flexible and Powerful Device to Secure any Size Premises Advanced Features Large Template Storage Capacity (0,000 in
L- Fingerprint Reader Solutions V-Flex 4G 4G Biometric Performance Redefined with a Flexible and Powerful Device to Secure any Size Premises Advanced Features Large Template Storage Capacity (0,000 in
Electronic Access Control Solutions
 Electronic Access Control Solutions Access Control Access Control Digitus BIOMETRIC ACCESS CONTROL Secure every access point The new db (Digitus Biometric) Biolock Technology paired with our Electromechanical
Electronic Access Control Solutions Access Control Access Control Digitus BIOMETRIC ACCESS CONTROL Secure every access point The new db (Digitus Biometric) Biolock Technology paired with our Electromechanical
Contactless Solutions
 Contactless Solutions Extends Windows Authentication ACCESS secure. Contactless Solutions Add contactless logical access control to your physical access control system w Three-component solution (Prox
Contactless Solutions Extends Windows Authentication ACCESS secure. Contactless Solutions Add contactless logical access control to your physical access control system w Three-component solution (Prox
FOUR PILLARS FOR A SUCCESSFUL PIV ECOSYSTEM
 FOUR PILLARS FOR A SUCCESSFUL PIV ECOSYSTEM Four Pillars that HSPD-12 Programs must consider for a secure, efficient, interoperable PIV enterprise deployment. Continued HSPD-12 Implementation under OMB
FOUR PILLARS FOR A SUCCESSFUL PIV ECOSYSTEM Four Pillars that HSPD-12 Programs must consider for a secure, efficient, interoperable PIV enterprise deployment. Continued HSPD-12 Implementation under OMB
MULTI-FACTOR AUTHENTICATION SET-UP
 MULTI-FACTOR AUTHENTICATION SET-UP DepositPartner Desktop Application TABLE OF CONTENTS Click the link below to go to the section you need: First Time Enrollment Enrolled User Contact information on file
MULTI-FACTOR AUTHENTICATION SET-UP DepositPartner Desktop Application TABLE OF CONTENTS Click the link below to go to the section you need: First Time Enrollment Enrolled User Contact information on file
Comodo Mobile Device Manager Software Version 1.0
 Comodo Mobile Device Manager Software Version 1.0 End User Guide Guide Version 1.0.022614 Comodo Security Solutions 1255 Broad Street STE 100 Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo
Comodo Mobile Device Manager Software Version 1.0 End User Guide Guide Version 1.0.022614 Comodo Security Solutions 1255 Broad Street STE 100 Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo
MAESON MAHERRY. 3 Factor Authentication and what it means to business. Date: 21/10/2013
 MAESON MAHERRY 3 Factor Authentication and what it means to business. Date: 21/10/2013 Concept of identity Identity and Access Management Authoritive Identity Source User Identity Feed and Role Management
MAESON MAHERRY 3 Factor Authentication and what it means to business. Date: 21/10/2013 Concept of identity Identity and Access Management Authoritive Identity Source User Identity Feed and Role Management
PIV Data Model Test Guidelines
 NIST Special Publication 800-85B PIV Data Model Test Guidelines Ramaswamy Chandramouli Ketan Mehta Pius A. Uzamere II David Simon Nabil Ghadiali Andrew P. Founds I N F O R M A T I O N S E C U R I T Y Computer
NIST Special Publication 800-85B PIV Data Model Test Guidelines Ramaswamy Chandramouli Ketan Mehta Pius A. Uzamere II David Simon Nabil Ghadiali Andrew P. Founds I N F O R M A T I O N S E C U R I T Y Computer
ACCESS CONTROL SYSTEM
 ACCESS CONTROL SYSTEM Flexible, Expandable, Economical. The i-pass system comprises of the i-pass controller built with state of the art technology to provide reader access for up to 16 doors and 32 elevator
ACCESS CONTROL SYSTEM Flexible, Expandable, Economical. The i-pass system comprises of the i-pass controller built with state of the art technology to provide reader access for up to 16 doors and 32 elevator
Basic Mercury Powered NXT Configuration in Doors.NET TM Application Note. 1.0 Adding an NXT-MSC Controller to the NXT Gateway
 Doors.NET installation and controller configuration is a three step process. Each of these steps has its own document, with controller configuration broken into separate documents per hardware type. software
Doors.NET installation and controller configuration is a three step process. Each of these steps has its own document, with controller configuration broken into separate documents per hardware type. software
Token User Guide. Version 1.0/ July 2013
 Token User Guide Version 1.0/ July 2013 Index Overview... 3 Usage requirements... 4 KIT contents... 5 Smart Card installation... 6 Reader driver installation... 7 In the case of Windows XP... 7 In the
Token User Guide Version 1.0/ July 2013 Index Overview... 3 Usage requirements... 4 KIT contents... 5 Smart Card installation... 6 Reader driver installation... 7 In the case of Windows XP... 7 In the
PrivateServer HSM Integration with Microsoft IIS
 PrivateServer HSM Integration with Microsoft IIS January 2014 Document Version 1.1 Notice The information provided in this document is the sole property of Algorithmic Research Ltd. No part of this document
PrivateServer HSM Integration with Microsoft IIS January 2014 Document Version 1.1 Notice The information provided in this document is the sole property of Algorithmic Research Ltd. No part of this document
Moving to Multi-factor Authentication. Kevin Unthank
 Moving to Multi-factor Authentication Kevin Unthank What is Authentication 3 steps of Access Control Identification: The entity makes claim to a particular Identity Authentication: The entity proves that
Moving to Multi-factor Authentication Kevin Unthank What is Authentication 3 steps of Access Control Identification: The entity makes claim to a particular Identity Authentication: The entity proves that
Velocity Web Services Client 1.0 Installation Guide and Release Notes
 Velocity Web Services Client 1.0 Installation Guide and Release Notes Copyright 2014-2015, Identiv. Last updated June 24, 2015. Overview This document provides the only information about version 1.0 of
Velocity Web Services Client 1.0 Installation Guide and Release Notes Copyright 2014-2015, Identiv. Last updated June 24, 2015. Overview This document provides the only information about version 1.0 of
Secure Held Print Jobs. Administrator's Guide
 Secure Held Print Jobs Administrator's Guide September 2013 www.lexmark.com Contents 2 Contents Overview...3 Configuring Secure Held Print Jobs...4 Configuring and securing the application...4 Using Secure
Secure Held Print Jobs Administrator's Guide September 2013 www.lexmark.com Contents 2 Contents Overview...3 Configuring Secure Held Print Jobs...4 Configuring and securing the application...4 Using Secure
BIOMETRIC SOLUTIONS 2013 ISSUE
 BIOMETRIC SOLUTIONS 2013 ISSUE Southern Supplies Limited (SSL) was established on January 14th 1982 with one aim in mind : "To be the preferred supplier to the industries we service." Over time, our expertise
BIOMETRIC SOLUTIONS 2013 ISSUE Southern Supplies Limited (SSL) was established on January 14th 1982 with one aim in mind : "To be the preferred supplier to the industries we service." Over time, our expertise
No additional requirements to use the PIV I card for physical facility access have been identified.
 1. The RFI request document regarding Driver Authentication states that "any one or more of the following methods" will be required: Personal Identification Number (PIN) Non Federal Personal Identity Verification
1. The RFI request document regarding Driver Authentication states that "any one or more of the following methods" will be required: Personal Identification Number (PIN) Non Federal Personal Identity Verification
How to setup a network printer using HP Universal Printer Driver
 How to setup a network printer using HP Universal Printer Driver This patch is only usable on HP T5730 Thin Client and up. The Printer also has to be networked and be PCL6 driver compatible in order to
How to setup a network printer using HP Universal Printer Driver This patch is only usable on HP T5730 Thin Client and up. The Printer also has to be networked and be PCL6 driver compatible in order to
Technical Implementation Guidance: Smart Card Enabled Physical Access Control Systems Version 2.3
 Technical Implementation Guidance: Smart Card Enabled Physical Access Control Systems Version 2.3 Approved by: Government Smart Card Interagency Advisory Board Prepared by: Physical Access Interagency
Technical Implementation Guidance: Smart Card Enabled Physical Access Control Systems Version 2.3 Approved by: Government Smart Card Interagency Advisory Board Prepared by: Physical Access Interagency
Justice Management Division
 Justice Management Division Privacy Impact Assessment for the Personal Identity Verification (PIV) Card System Issued by: Stuart Frisch, Senior Component Official for Privacy Reviewed by: Vance E. Hitch,
Justice Management Division Privacy Impact Assessment for the Personal Identity Verification (PIV) Card System Issued by: Stuart Frisch, Senior Component Official for Privacy Reviewed by: Vance E. Hitch,
Comodo Web Application Firewall for Plesk Software Version 2.11
 2 Comodo Web Application Firewall for Plesk Software Version 2.11 Administrator Guide Guide Version 2.11.071315 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Comodo
2 Comodo Web Application Firewall for Plesk Software Version 2.11 Administrator Guide Guide Version 2.11.071315 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Comodo
Emergency Response Official Credentials A Smart Card Alliance White Paper. Salvatore D Agostino CEO, IDmachines LLC sal@idmachines.
 Emergency Response Official Credentials A Smart Card Alliance White Paper Salvatore D Agostino CEO, IDmachines LLC [email protected] Smart Card Alliance Broad collection of professionals working with
Emergency Response Official Credentials A Smart Card Alliance White Paper Salvatore D Agostino CEO, IDmachines LLC [email protected] Smart Card Alliance Broad collection of professionals working with
Digitus Biometrics. 2015 Product Catalogue. Request a quote or design assistance by emailing [email protected] or calling 912.231.8175.
 Digitus Biometrics 2015 Product Catalogue Request a quote or design assistance by emailing [email protected] or calling 912.231.8175. Table of Contents Access Control Solutions db ServerRack
Digitus Biometrics 2015 Product Catalogue Request a quote or design assistance by emailing [email protected] or calling 912.231.8175. Table of Contents Access Control Solutions db ServerRack
SYMMETRY PRODUCT OVERVIEW
 ACCESS CONTROL The Symmetry Security Management Systems provides powerful integrated solutions for organizations requiring Access Control and Integrated Security. Solutions are available for organizations
ACCESS CONTROL The Symmetry Security Management Systems provides powerful integrated solutions for organizations requiring Access Control and Integrated Security. Solutions are available for organizations
Architecture for Issuing DoD Mobile Derived Credentials. David A. Sowers. Master of Science In Computer Engineering
 Architecture for Issuing DoD Mobile Derived Credentials David A. Sowers Thesis submitted to the faculty of the Virginia Polytechnic Institute and State University in partial fulfillment of the requirements
Architecture for Issuing DoD Mobile Derived Credentials David A. Sowers Thesis submitted to the faculty of the Virginia Polytechnic Institute and State University in partial fulfillment of the requirements
Computer prepare to work with the eid card using Internet Explorer
 Computer prepare to work with the eid card using Internet Explorer Content 1. Card Reader drivers installation 2. Computer prepare to work with eid card 3. Basic certificates installation using Internet
Computer prepare to work with the eid card using Internet Explorer Content 1. Card Reader drivers installation 2. Computer prepare to work with eid card 3. Basic certificates installation using Internet
Fingerprint Identity User Manual for the Griaule Biometric Framework 040-0103-01 Rev 1.00
 Fingerprint Identity User Manual for the Griaule Biometric Framework 040-0103-01 Rev 1.00 www.griaulebiometrics.com Brazil Phone: 55-19-3289-2108 USA Phone: (408) 490 3438 Fingerprint Identity Index Getting
Fingerprint Identity User Manual for the Griaule Biometric Framework 040-0103-01 Rev 1.00 www.griaulebiometrics.com Brazil Phone: 55-19-3289-2108 USA Phone: (408) 490 3438 Fingerprint Identity Index Getting
User Guide Remote Access to VDI/Workplace Using PIV
 User Guide Remote Access to VDI/Workplace Using PIV Innovation & Engineering Office (IM-64) May 2015 Table of Contents 1 Overview... 3 1.1 Web Browsers... 3 1.2 Operating Systems... 3 2 Types of Smart
User Guide Remote Access to VDI/Workplace Using PIV Innovation & Engineering Office (IM-64) May 2015 Table of Contents 1 Overview... 3 1.1 Web Browsers... 3 1.2 Operating Systems... 3 2 Types of Smart
Application Note. Example of user log on Magelis HMI with XB5S5B2L2 biometric switch. Advanced Technical Support - Brazil. Version: 1.
 Application Note Example of user log on Magelis HMI with XB5S5B2L2 biometric switch. Version: 1.0 Advanced Technical Support - Brazil Technical Specifications Hardware: Firmware: HMIGTO4310 XB5S5B2L2 Software:
Application Note Example of user log on Magelis HMI with XB5S5B2L2 biometric switch. Version: 1.0 Advanced Technical Support - Brazil Technical Specifications Hardware: Firmware: HMIGTO4310 XB5S5B2L2 Software:
SYMMETRY. DATASHEET ACCESS CONTROL Product Overview
 DATASHEET ACCESS CONTROL Product Overview SYMMETRY The AMAG Technology range of Security Management Systems provides powerful integrated solutions for organizations requiring Access Control and Integrated
DATASHEET ACCESS CONTROL Product Overview SYMMETRY The AMAG Technology range of Security Management Systems provides powerful integrated solutions for organizations requiring Access Control and Integrated
Comodo One Software Version 1.8
 rat Comodo One Software Version 1.8 Service Desk End-User Guide Guide Version 1.8.090715 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Introduction to Service Desk Module Comodo Service
rat Comodo One Software Version 1.8 Service Desk End-User Guide Guide Version 1.8.090715 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Introduction to Service Desk Module Comodo Service
Achieving Universal Secure Identity Verification with Convenience and Personal Privacy A PRIVARIS BUSINESS WHITE PAPER
 with Convenience and Personal Privacy version 0.2 Aug.18, 2007 WHITE PAPER CONTENT Introduction... 3 Identity verification and multi-factor authentication..... 4 Market adoption... 4 Making biometrics
with Convenience and Personal Privacy version 0.2 Aug.18, 2007 WHITE PAPER CONTENT Introduction... 3 Identity verification and multi-factor authentication..... 4 Market adoption... 4 Making biometrics
Administration Guide ActivClient for Windows 6.2
 Administration Guide ActivClient for Windows 6.2 ActivClient for Windows Administration Guide P 2 Table of Contents Chapter 1: Introduction....................................................................12
Administration Guide ActivClient for Windows 6.2 ActivClient for Windows Administration Guide P 2 Table of Contents Chapter 1: Introduction....................................................................12
10713 N FM 620 Suite 201 Austin, TX 78726. 2FA ONE version 4.0 Server Installation and Setup Guide 2014 2FA, Inc.
 10713 N FM 620 Suite 201 Austin, TX 78726 2FA ONE version 4.0 Server Installation and Setup Guide 2014 2FA, Inc. Copyright 2014 2FA, Inc. All Rights Reserved HID is a registered trademark of HID Global.
10713 N FM 620 Suite 201 Austin, TX 78726 2FA ONE version 4.0 Server Installation and Setup Guide 2014 2FA, Inc. Copyright 2014 2FA, Inc. All Rights Reserved HID is a registered trademark of HID Global.
Derived credentials. NIST SP 800-63-1 ( 5.3.5) provides for long term derived credentials
 Daon your trusted Identity Partner Derived Credentials A Use Case Cathy Tilton Daon 1 February 2012 Derived credentials NIST SP 800-63-1 ( 5.3.5) provides for long term derived credentials Derived credential
Daon your trusted Identity Partner Derived Credentials A Use Case Cathy Tilton Daon 1 February 2012 Derived credentials NIST SP 800-63-1 ( 5.3.5) provides for long term derived credentials Derived credential
support HP MFP Scan Setup Wizard 1.1
 support HP MFP Scan Setup Wizard 1.1 Security Level: Customer Verbal Use Date Written/Updated: October 11, 2007 Document Summary a The Scan Setup Wizard is a Windows utility that end users can download
support HP MFP Scan Setup Wizard 1.1 Security Level: Customer Verbal Use Date Written/Updated: October 11, 2007 Document Summary a The Scan Setup Wizard is a Windows utility that end users can download
Aperio Online. Aperio. Online Programming Application Manual. Aperio Online Quick Installation Guide, Document No: ST-001322-A, Date: 8 juli 2013
 Aperio TM Online Programming Application Manual Document No: ST-001321-A, Issue date: 8 July 2013 1 Aperio Online Quick Installation Guide, Document No: ST-001322-A, Date: 8 juli 2013 Table of Contents
Aperio TM Online Programming Application Manual Document No: ST-001321-A, Issue date: 8 July 2013 1 Aperio Online Quick Installation Guide, Document No: ST-001322-A, Date: 8 juli 2013 Table of Contents
