Yubico YubiHSM Monitor
|
|
|
- Antony Sims
- 10 years ago
- Views:
Transcription
1 Yubico YubiHSM Monitor Test utility for the YubiHSM Document Version: 1.1 May 24, 2012
2 Introduction Disclaimer Yubico is the leading provider of simple, open online identity protection. The company s flagship product, the YubiKey, uniquely combines driverless USB hardware with open source software. More than a million users in 100 countries rely on YubiKey strong two-factor authentication for securing access to computers, mobile devices, networks and online services. Customers range from individual Internet users to e-governments and Fortune 500 companies. Founded in 2007, Yubico is privately held with offices in California, Sweden and UK. The contents of this document are subject to revision without notice due to continued progress in methodology, design, and manufacturing. Yubico shall have no liability for any error or damages of any kind resulting from the use of this document. The Yubico Software referenced in this document is licensed to you under the terms and conditions accompanying the software or as otherwise agreed between you or the company that you are representing. Trademarks Yubico and YubiKey are trademarks of Yubico Inc. Contact Information Yubico Inc 228 Hamilton Avenue, 3rd Floor Palo Alto, CA USA [email protected] Yubico YubiHSM Monitor 2012 Yubico. All rights reserved. Page 2 of 15
3 Contents Introduction... 2 Disclaimer... 2 Trademarks... 2 Contact Information Document Information Purpose Audience Related documentation Document History Introduction and concepts Sample setup and test Configuring HSM mode Creating keys Exiting the configuration mode Starting the YubiHSM monitor Selecting the YubiHSM port Testing the YubiHSM connection Monitoring roundtrip time and throughput Sample AEAD generation Storing AEAD keys in the persistent storage Using the YubiHSM to generate an AEAD Using the tool to generate an AEAD Using the buffer to create AEADs Using AEADs to verify Yubico OTPs Generation of Yubikey secrets Testing the OTP validation Using the internal OTP database Populating the OTP database during configuration Verifying a Yubico OTP Adding additional database entries Yubico YubiHSM Monitor 2012 Yubico. All rights reserved. Page 3 of 15
4 1 Document Information 1.1 Purpose This document provides a quick reference to the YubiHSM monitor application. The purpose of the monitor application is to provide a simple tool to evaluate YubiHSM concepts and functionality under the Microsoft Windows operating system. 1.2 Audience YubiHSM developers 1.3 Related documentation YubiHSM manual YubiHSM Python framework Yubikey Configuration Utility manual Yubico online forum Document History Date Version Author Activity JE First release ZD Changed document template Yubico YubiHSM Monitor 2012 Yubico. All rights reserved. Page 4 of 15
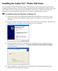
5 2 Introduction and concepts The Yubico YubiHSM test monitor is a simple utility designed to allow quick test and evaluation of YubiHSM HSM mode functionality and concepts. The tool is by no means indented to be used in a production setting. Please refer to the YubiHSM manual for a detailed description of the YubiHSM functionality and concepts. The utility is provided as a single Windows executable. The Windows registry is used to store persistent settings. Here, the command combo box drop down is shown, where all YubiHSM commands are available. The screen is divided into three sections Key handle and nonce Here, key handles and nonces can be entered Execution Here, all YubiHSM commands with associated parameters are entered and returned. Functions for decoding and encoding of AEADs are provided to allow evaluation and test, just like if a second YubiHSM was present. This type of functionality is by nature not a part of a real production setting. Yubikey OTP output Here, output from a Yubikey can be inserted and for automatic parsing and command wrapping. The following sections provide a few examples how to use the tool together with a YubiHSM. For a complete command reference, please refer to the YubiHSM manual. Yubico YubiHSM Monitor 2012 Yubico. All rights reserved. Page 5 of 15
6 3 Sample setup and test Please follow the instructions in section 8 of the YubiHSM manual how to enter configuration mode and get a basic understanding of the configuration process. 3.1 Configuring HSM mode From the terminal, type hsm NO_CFG> hsm Enabled flags 7fffffff = YSM_AEAD_GENERATE,YSM_BUFFER_AEAD_GENERATE,YSM_RANDOM _AEAD_GENERATE,YSM_AEAD_DECRYPT_CMP,YSM_DB_YUBIKEY_AEAD_STORE,YSM_AEAD_YUBIKEY _OTP_DECODE,YSM_DB_YUBIKEY_OTP_VALIDATE,YSM_AES_ECB_BLOCK_ENCRYPT,YSM_AES_ECB_ BLOCK_DECRYPT,YSM_AES_ECB_BLOCK_DECRYPT_CMP,YSM_HMAC_SHA1_GENERATE,YSM_TEMP_KE Y_LOAD a:ysm_aead_generate c:ysm_random_aead_generate e:ysm_db_yubikey_aead_store g:ysm_db_yubikey_otp_validate i:ysm_aes_ecb_block_decrypt k:ysm_hmac_sha1_generate m:flag_debug b:ysm_buffer_aead_generate d:ysm_aead_decrypt_cmp f:ysm_aead_yubikey_otp_decode h:ysm_aes_ecb_block_encrypt j:ysm_aes_ecb_block_decrypt_cmp l:ysm_temp_key_load Toggle bit (space = all, enter = exit) Enter cfg password (g to generate) Enter hsm password (g to generate) Confirm current config being erased (type yes) yes - wait - done HSM> The device is now configured to operate in HSM mode, but we need to load keys in order to proceed. In order to allow debugging, the flag m can be toggled. The key store and the Yubikey database can then be read in clear text. 3.2 Creating keys From the terminal, type keygen 1 2 to create 2 random keys, starting with number 1 HSM> keygen using flags 7fffffff and len ,463b39720b3af66b9835c88be50fd9c7b5b50c63793c2c23112a51ccdf61d5b ,9a4aa df0183e e5c812e48fd4c466b70b fcd5c8a3a1c HSM> The YubiHSM now has basic information to allow the first tests to be conducted. 3.3 Exiting the configuration mode Type exit to exit configuration mode. The YubiHSM LED now switches to a faster flashing to indicate that the YubiHSM has entered HSM mode. Now, close the terminal program to allow the COM port to be opened with the monitor program Yubico YubiHSM Monitor 2012 Yubico. All rights reserved. Page 6 of 15
7 3.4 Starting the YubiHSM monitor The YubiHSM monitor is provided as a self-contained executable file that does not require any additional files. 3.5 Selecting the YubiHSM port In this case, the YubiHSM is present on COM3, which can be verified in the Windows Device Manager. From the Port combo box in the Execution group, select the port where the YubiHSM is connected. The status field shall show Port opened ok. Make sure the terminal program is closed before opening the port, as this otherwise prevents the port from being opened. 3.6 Testing the YubiHSM connection Now, select the YSM_SYSTEM_INFO_QUERY command from the Cmd combo box in the Execution group. Press the Run button and the firmware version and ID string shall appear in the status window. Yubico YubiHSM Monitor 2012 Yubico. All rights reserved. Page 7 of 15
8 3.7 Monitoring roundtrip time and throughput Command execution time and the application-to-device roundtrip time can be measured. In this case, the YSM_ECHO command can be used, which simply echoes back what is being sent. In this example, 8 bytes (Cnt/par field) are sent to the YubiHSM and echoed back 100 times (Cycles field). The average roundtrip time is 337 µs, varying between 207 and 723 µs. For a more precise tracking of the throughput and response times, an external USB hardware analyzer can be used. In this case, an Ellisys USB Explorer 200 analyzer was used to monitor the traffic and verify the turnaround times. As seen, the raw data packet sent out at t = 0 gets its response after 62 Ls, which gives an idea of the YubiHSM processing time. Given the average turnaround time of 337 Ls, the remaining = 275 Ls is a sum of operating system- and USB stack latencies. Yubico YubiHSM Monitor 2012 Yubico. All rights reserved. Page 8 of 15
9 4 Sample AEAD generation The utility can generate and verify AEADs, which can then be used to test the YubiHSM functionality. Several commands, options and modes are available and two simple examples are shown below. 4.1 Storing AEAD keys in the persistent storage The first step is to store the keys created in the configuration (step 3.2 above) in the monitor s persistent storage. This step is just for the sake of using this test utility as the real keys are already stored in the persistent YubiHSM. Please recall the keys used in step ,463b39720b3af66b9835c88be50fd9c7b5b50c63793c2c23112a51ccdf61d5b ,9a4aa df0183e e5c812e48fd4c466b70b fcd5c8a3a1c Type 1 into the key handle combo box and paste in the first key. The key length field shows 32 as an indication that the key is 32 bytes in length. Then, type in 2 and paste in the other key in the key field in the same way as above. The keys are now stored in the registry and can be conveniently selected using the combo box. Please make sure these keys are just for test purposes as this otherwise could be a security risk. 4.2 Using the YubiHSM to generate an AEAD There are several ways to create AEADs and please refer to the appropriate manual sections for a detailed description of these concepts. The simplest way to create an AEAD is to provide some clear text data and then let the YubiHSM create an AEAD from these bytes. Yubico YubiHSM Monitor 2012 Yubico. All rights reserved. Page 9 of 15
10 In this example, the plain text bytes are entered in the In/PT field. The input length is 8 bytes, shown by the Len field. The AEAD generation requires a nonce, which can either be supplied or be uniquely generated by the YubiHSM. Check the Gen nonce button to use automatic generation. Press the Run button when done. The generated AEAD is displayed in the Out/CT field. The AEAD length is always 8 bytes more than the length of the clear text string, which in this case equals 16 bytes, shown by the Len field. The generated nonce, associated with this AEAD is inserted into the nonce field up in the right corner. The AEAD generated by the YubiHSM can be verified by the utility by pressing the Decode button. If the AEAD is invalid or cannot be verified with the selected key handle or nonce, an error is displayed. For example, change the last 9e to 9f and press Decode. The decoding now fails. 4.3 Using the tool to generate an AEAD The tool can generate an AEAD, which can then be used by AEAD operations in the YubiHSM. Enter in the clear text field and press Encode. Now, the YubiHSM can be used to verify this AEAD. Select the YSM_AEAD_DECRYPT_CMP command and press Run. By changing the plaintext, the AEAD is still valid, but the compare fails: Yubico YubiHSM Monitor 2012 Yubico. All rights reserved. Page 10 of 15
11 However, if the AEAD is changed, another error message is generated Here, the AEAD cannot be decoded as the last byte was changed from e9 to ea 4.4 Using the buffer to create AEADs The Offs field can be used to specify a buffer offset when working with the YubiHSM AEAD data buffer. Enter in the plaintext field and 0 in the Offs field, select the YSM_BUFFER_LOAD command and press Run Enter 4 in the offset field and 3 in the Cnt/par field and, select the YSM_RANDOM_BUFFER_LOAD command and press Run Now, two fixed bytes are inserted in position 0 and 1 of the buffer and three random bytes are generated by the YubiHSM into positions 4, 5 and 6. Bytes 2 and 3 are set to zero when writing to offset zero. Generate an AEAD of the buffer using the YSM_BUFFER_AEAD_GENERATE command: A 15 bytes AEAD is generated, which equals 7 bytes buffer data. Here, the utility automatically decodes the AEAD and the plaintext is shown (which is of course NOT returned by the YubiHSM). The random bytes created in the previous step were obviously 6e b8 6b and as seen, bytes 2 and 3 are zero. Yubico YubiHSM Monitor 2012 Yubico. All rights reserved. Page 11 of 15
12 5 Using AEADs to verify Yubico OTPs One of the main use cases for the YubiHSM is to verify Yubico OTPs, with secrets stored on external media, such as a database on a validation server. This setting typically involves one secure station with a YubiHSM where the secrets are created and the Yubikeys are personalized. The secrets are then converted into AEADs and are then transmitted to the validation server(s) over a potentially unsecure channel. Each validation server then has a YubiHSM to verify received OTPs using these AEADs. Please refer to the YubiHSM manual for a more detailed description of this setting. Validation of Yubico OTPs can also be done using the internal YubiHSM database. This is shown in section Generation of Yubikey secrets The Yubikey secrets consisting of the private identity and the AES key can be packed into a specially formatted AEAD, defined in the yubihsm_if.h file: // 22-bytes Yubikey secrets block typedef struct { uint8_t key[key_size]; uint8_t uid[uid_size]; } YSM_YUBIKEY_SECRETS; // AES key // Unique (secret) ID The resulting AEAD is then = 30 bytes in length. Several options for generation of secrets exist but the following example uses the Yubikey Configuration Tool to configure a single Yubikey with a random private id and key. Make sure the output log file option is set. Yubico YubiHSM Monitor 2012 Yubico. All rights reserved. Page 12 of 15
13 The log file gives the following output: ,52715ba12c82,0a187fd2fbb7ac628c540514c0fd30b1 The format is public-id, private-id, aes-key Concatenate the AES key and private ID into a single string to match the YSM_YUBIKEY_SECRETS format. 0a187fd2fbb7ac628c540514c0fd30b152715ba12c82 Paste this string into the plaintext field and paste the public id into the nonce field. Make sure the Gen nonce button is unchecked. Press Run The resulting 30-byte AEAD is shown in the Out/CT field. 5.2 Testing the OTP validation Now, place the cursor into the Modhex field of the Yubikey OTP output group and press the button The YubiHSM now uses the AEAD supplied in the Out/CT field together with the key handle, nonce and decoded Modhex string to verify the OTP. The result is shown in the Status field and the decoded counter- and timestamp values in the Ctr and Tstp fields. Yubico YubiHSM Monitor 2012 Yubico. All rights reserved. Page 13 of 15
14 6 Using the internal OTP database The YubiHSM internal OTP database has storage for a limited number of secrets. The database can either be populated during configuration from a text file compatible with the Yubico Yubikey provisioning format, via the HSM function YSM_DB_YUBIKEY_AEAD_STORE or a combination of both. Please refer to the YubiHSM manual for a more detailed description of this setting. Validation of Yubico OTPs can also be done using the external AEAD storage. This is shown in section Populating the OTP database during configuration The OTP database can be populated during configuration by uploading a Yubico supplied key file, such as 99950,cccccccbjhhu,fe37a81ab606,46d917606afe4d81830b8822d65a70ca,75467b86adb8, T21:14:16, 99951,cccccccbjhhv,f9fc0cf39012,bf0af3bf814bc8250b4fbb0e806ed8a0,6ba06c87e191, T21:14:16, 99952,cccccccbjhic,8b99376dc0af,ccf6e1e61b93f2cec00dc88cbd1c03bd,905f d, T21:14:16, During the configuration phase, use the terminal program s upload facility together with the dbload command: HSM> dbload - Load id data now. Press ESC to quit inserted ok inserted ok inserted ok Exit back to HSM mode and start the YubiHSM monitor 6.2 Verifying a Yubico OTP Now, select the YSM_DB_YUBIKEY_OTP_VALIDATE command, place the cursor into the Modhex field and insert a Yubikey configured within this range. Press the button In this setting, only the OTP is needed where all other data is taken from the internal database. The result is shown in the Status field and the decoded counter- and timestamp values in the Ctr and Tstp fields. Yubico YubiHSM Monitor 2012 Yubico. All rights reserved. Page 14 of 15
15 As the counters are checked and maintained in this mode, replay detection is provided as well: By sending the same OTP again, the YubiHSM detects the replay and reports YSM_OTP_REPLAY. 6.3 Adding additional database entries In HSM mode, additional database entries can be added using the YSM_DB_YUBIKEY_AEAD_STORE command. AEADs are created as described in section 5.1. Switching back to configuration mode and returning to the terminal allows us to verify that the newly inserted record exists HSM> dblist 00000,cccccccbjhhu,00001/ ,cccccccbjhhv,00000/ ,cccccccbjhic,00000/ ,cbcdcecfcgch,00001/004 Entries invalid free As seen here, a few OTPs have been generated here so the counters for the newly added record cbcdcecfcgch is now 2/1. Yubico YubiHSM Monitor 2012 Yubico. All rights reserved. Page 15 of 15
Configuring a YubiKey for the YubiCloud
 Configuring a YubiKey for the YubiCloud With the YubiKey Cross-Platform Personalization Tool April 9, 2013 Configuring a YubiKey for the YubiCloud 2012 Yubico. All rights reserved. Page 1 of 8 Introduction
Configuring a YubiKey for the YubiCloud With the YubiKey Cross-Platform Personalization Tool April 9, 2013 Configuring a YubiKey for the YubiCloud 2012 Yubico. All rights reserved. Page 1 of 8 Introduction
VIP YubiKey Unlock Guide
 VIP YubiKey Unlock Guide Unlocking the VIP YubiKey for YubiCloud OTP February 22, 2013 VIP YubiKey Unlock Guide 2012 Yubico. All rights reserved. Page 1 of 9 Introduction Yubico is the leading provider
VIP YubiKey Unlock Guide Unlocking the VIP YubiKey for YubiCloud OTP February 22, 2013 VIP YubiKey Unlock Guide 2012 Yubico. All rights reserved. Page 1 of 9 Introduction Yubico is the leading provider
NetMotion + YubiRADIUS Quick Start Guide
 NetMotion + YubiRADIUS Quick Start Guide March 22, 2013 NetMotion + YubiRADIUS Quick Start Guide 2012 Yubico. All rights reserved. Page 1 of 7 Introduction Disclaimer Yubico is the leading provider of
NetMotion + YubiRADIUS Quick Start Guide March 22, 2013 NetMotion + YubiRADIUS Quick Start Guide 2012 Yubico. All rights reserved. Page 1 of 7 Introduction Disclaimer Yubico is the leading provider of
YubiKey & OATH- TOTP Verification
 YubiKey & OATH- TOTP Verification February 7, 2014 YubiKey & OATH-TOTP Verification 2014 Yubico. All rights reserved. Page 1 of 11 Introduction Disclaimer Yubico is the leading provider of simple, open
YubiKey & OATH- TOTP Verification February 7, 2014 YubiKey & OATH-TOTP Verification 2014 Yubico. All rights reserved. Page 1 of 11 Introduction Disclaimer Yubico is the leading provider of simple, open
YubiCloud OTP Validation Service. Version 1.2
 YubiCloud OTP Validation Service Version 1.2 5/12/2015 Introduction Disclaimer Yubico is the leading provider of simple, open online identity protection. The company s flagship product, the YubiKey, uniquely
YubiCloud OTP Validation Service Version 1.2 5/12/2015 Introduction Disclaimer Yubico is the leading provider of simple, open online identity protection. The company s flagship product, the YubiKey, uniquely
YubiCloud Validation Service. Version 1.1
 YubiCloud Service Version 1.1 5/29/2012 Introduction Disclaimer Yubico is the leading provider of simple, open online identity protection. The company s flagship product, the YubiKey, uniquely combines
YubiCloud Service Version 1.1 5/29/2012 Introduction Disclaimer Yubico is the leading provider of simple, open online identity protection. The company s flagship product, the YubiKey, uniquely combines
September 25, 2015. Programming YubiKeys for Okta Adaptive Multi-Factor Authentication
 Programming YubiKeys for Okta Adaptive Multi-Factor Authentication September 25, 2015 Programming YubiKeys for Okta Adaptive Multi-Factor Authentication Page 1 of 14 Copyright 2015 Yubico Inc. All rights
Programming YubiKeys for Okta Adaptive Multi-Factor Authentication September 25, 2015 Programming YubiKeys for Okta Adaptive Multi-Factor Authentication Page 1 of 14 Copyright 2015 Yubico Inc. All rights
YubiKey Authentication Module Design Guideline
 YubiKey Authentication Module Design Guideline Yubico Application Note Version 1.0 May 7, 2012 Introduction Disclaimer Yubico is the leading provider of simple, open online identity protection. The company
YubiKey Authentication Module Design Guideline Yubico Application Note Version 1.0 May 7, 2012 Introduction Disclaimer Yubico is the leading provider of simple, open online identity protection. The company
YubiRADIUS Deployment Guide for corporate remote access. How to Guide
 YubiRADIUS Deployment Guide for corporate remote access How to Guide May 15, 2012 Introduction Disclaimer Yubico is the leading provider of simple, open online identity protection. The company s flagship
YubiRADIUS Deployment Guide for corporate remote access How to Guide May 15, 2012 Introduction Disclaimer Yubico is the leading provider of simple, open online identity protection. The company s flagship
NEO Manager Quick Start Guide
 NEO Manager Quick Start Guide For the YubiKey NEO and NEO-n Version 1.1 November 19, 2014 NEO Manager Quick Start Guide 2014 Yubico. All rights reserved. Page 1 of 6 About Yubico Disclaimer As the inventors
NEO Manager Quick Start Guide For the YubiKey NEO and NEO-n Version 1.1 November 19, 2014 NEO Manager Quick Start Guide 2014 Yubico. All rights reserved. Page 1 of 6 About Yubico Disclaimer As the inventors
YubiKey OSX Login. yubico. Via Yubico-PAM Challenge-Response. Version 1.6. October 24, 2015
 YubiKey OSX Login Via Yubico-PAM Challenge-Response Version 1.6 October 24, 2015 YubiKey OSX Login 2015 Yubico. All rights reserved. Page 1 of 18 About Yubico Disclaimer As the inventors of the YubiKey,
YubiKey OSX Login Via Yubico-PAM Challenge-Response Version 1.6 October 24, 2015 YubiKey OSX Login 2015 Yubico. All rights reserved. Page 1 of 18 About Yubico Disclaimer As the inventors of the YubiKey,
Replacing legacy twofactor. with YubiRADIUS for corporate remote access. How to Guide
 Replacing legacy twofactor authentication with YubiRADIUS for corporate remote access How to Guide May 15, 2012 Introduction Disclaimer Yubico is the leading provider of simple, open online identity protection.
Replacing legacy twofactor authentication with YubiRADIUS for corporate remote access How to Guide May 15, 2012 Introduction Disclaimer Yubico is the leading provider of simple, open online identity protection.
Yubico PIV Management Tools
 Yubico PIV Management Tools Active Directory Smart Card Logon using the YubiKey NEO or NEO-n Document Version 1.0 April 15, 2015 Yubico PIV Management Tools 2015 Yubico. All rights reserved. Page 1 of
Yubico PIV Management Tools Active Directory Smart Card Logon using the YubiKey NEO or NEO-n Document Version 1.0 April 15, 2015 Yubico PIV Management Tools 2015 Yubico. All rights reserved. Page 1 of
YubiKey Integration for Full Disk Encryption
 YubiKey Integration for Full Disk Encryption Pre-Boot Authentication Version 1.2 May 7, 2012 Introduction Disclaimer yubico Yubico is the leading provider of simple, open online identity protection. The
YubiKey Integration for Full Disk Encryption Pre-Boot Authentication Version 1.2 May 7, 2012 Introduction Disclaimer yubico Yubico is the leading provider of simple, open online identity protection. The
YubiKey Security Evaluation
 YubiKey Security Evaluation Discussion of security properties and best practices Version: 2.0.1 July 23, 2012 Introduction Disclaimer Yubico is the leading provider of simple, open online identity protection.
YubiKey Security Evaluation Discussion of security properties and best practices Version: 2.0.1 July 23, 2012 Introduction Disclaimer Yubico is the leading provider of simple, open online identity protection.
Rohos Logon Key for Windows Remote Desktop logon with YubiKey token
 Rohos Logon Key for Windows Remote Desktop logon with YubiKey token Step-by-Step Integration Guide. Tesline-Service S.R.L. 10 Calea Iesilor str., Chisinau, MD-2069, Moldova. Tel: +373-22-740-242 www.rohos.com
Rohos Logon Key for Windows Remote Desktop logon with YubiKey token Step-by-Step Integration Guide. Tesline-Service S.R.L. 10 Calea Iesilor str., Chisinau, MD-2069, Moldova. Tel: +373-22-740-242 www.rohos.com
YubiRADIUS Virtual Appliance. Configuration and Administration Guide Software version: 3.6.0 Document version: 1.0
 YubiRADIUS Virtual Appliance Configuration and Administration Guide Software version: 3.6.0 Document version: 1.0 December 14, 2012 Introduction Disclaimer Yubico is the leading provider of simple, open
YubiRADIUS Virtual Appliance Configuration and Administration Guide Software version: 3.6.0 Document version: 1.0 December 14, 2012 Introduction Disclaimer Yubico is the leading provider of simple, open
Decryption. Palo Alto Networks. PAN-OS Administrator s Guide Version 6.0. Copyright 2007-2015 Palo Alto Networks
 Decryption Palo Alto Networks PAN-OS Administrator s Guide Version 6.0 Contact Information Corporate Headquarters: Palo Alto Networks 4401 Great America Parkway Santa Clara, CA 95054 www.paloaltonetworks.com/company/contact-us
Decryption Palo Alto Networks PAN-OS Administrator s Guide Version 6.0 Contact Information Corporate Headquarters: Palo Alto Networks 4401 Great America Parkway Santa Clara, CA 95054 www.paloaltonetworks.com/company/contact-us
StarWind iscsi SAN Software: Challenge-Handshake Authentication Protocol (CHAP) for Authentication of Users
 StarWind iscsi SAN Software: Challenge-Handshake Authentication Protocol (CHAP) for Authentication of Users www.starwindsoftware.com Copyright 2008-2011. All rights reserved. COPYRIGHT Copyright 2008-2011.
StarWind iscsi SAN Software: Challenge-Handshake Authentication Protocol (CHAP) for Authentication of Users www.starwindsoftware.com Copyright 2008-2011. All rights reserved. COPYRIGHT Copyright 2008-2011.
SUDT AccessPort TM Advanced Terminal / Monitor / Debugger Version 1.37 User Manual
 SUDT AccessPort TM Advanced Terminal / Monitor / Debugger Version 1.37 User Manual Version 1.0 - January 20, 2015 CHANGE HISTORY Version Date Description of Changes 1.0 January 20, 2015 Initial Publication
SUDT AccessPort TM Advanced Terminal / Monitor / Debugger Version 1.37 User Manual Version 1.0 - January 20, 2015 CHANGE HISTORY Version Date Description of Changes 1.0 January 20, 2015 Initial Publication
NETWRIX EVENT LOG MANAGER
 NETWRIX EVENT LOG MANAGER ADMINISTRATOR S GUIDE Product Version: 4.0 July/2012. Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment
NETWRIX EVENT LOG MANAGER ADMINISTRATOR S GUIDE Product Version: 4.0 July/2012. Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment
How to Time Stamp PDF and Microsoft Office 2010/2013 Documents with the Time Stamp Server
 How to Time Stamp PDF and Microsoft Office 2010/2013 Documents with the Time Stamp Server Introduction Time stamping is an important mechanism for the long-term preservation of digital signatures, time
How to Time Stamp PDF and Microsoft Office 2010/2013 Documents with the Time Stamp Server Introduction Time stamping is an important mechanism for the long-term preservation of digital signatures, time
YubiKey PIV Deployment Guide
 YubiKey PIV Deployment Guide Best Practices and Basic Setup YubiKey 4, YubiKey 4 Nano, YubiKey NEO, YubiKey NEO-n YubiKey PIV Deployment Guide 2016 Yubico. All rights reserved. Page 1 of 27 Copyright 2016
YubiKey PIV Deployment Guide Best Practices and Basic Setup YubiKey 4, YubiKey 4 Nano, YubiKey NEO, YubiKey NEO-n YubiKey PIV Deployment Guide 2016 Yubico. All rights reserved. Page 1 of 27 Copyright 2016
WA Manager Alarming System Management Software Windows 98, NT, XP, 2000 User Guide
 WA Manager Alarming System Management Software Windows 98, NT, XP, 2000 User Guide Version 2.1, 4/2010 Disclaimer While every effort has been made to ensure that the information in this guide is accurate
WA Manager Alarming System Management Software Windows 98, NT, XP, 2000 User Guide Version 2.1, 4/2010 Disclaimer While every effort has been made to ensure that the information in this guide is accurate
BLUETOOTH SERIAL PORT PROFILE. iwrap APPLICATION NOTE
 BLUETOOTH SERIAL PORT PROFILE iwrap APPLICATION NOTE Thursday, 19 April 2012 Version 1.2 Copyright 2000-2012 Bluegiga Technologies All rights reserved. Bluegiga Technologies assumes no responsibility for
BLUETOOTH SERIAL PORT PROFILE iwrap APPLICATION NOTE Thursday, 19 April 2012 Version 1.2 Copyright 2000-2012 Bluegiga Technologies All rights reserved. Bluegiga Technologies assumes no responsibility for
Getting Started with IntelleView POS Administrator Software
 Getting Started with IntelleView POS Administrator Software Administrator s Guide for Software Version 1.2 About this Guide This administrator s guide explains how to start using your IntelleView POS (IntelleView)
Getting Started with IntelleView POS Administrator Software Administrator s Guide for Software Version 1.2 About this Guide This administrator s guide explains how to start using your IntelleView POS (IntelleView)
Step-by-step installation guide for monitoring untrusted servers using Operations Manager ( Part 3 of 3)
 Step-by-step installation guide for monitoring untrusted servers using Operations Manager ( Part 3 of 3) Manual installation of agents and importing the SCOM certificate to the servers to be monitored:
Step-by-step installation guide for monitoring untrusted servers using Operations Manager ( Part 3 of 3) Manual installation of agents and importing the SCOM certificate to the servers to be monitored:
Device LinkUP + Desktop LP Guide RDP
 Device LinkUP + Desktop LP Guide RDP Version 2.1 January 2016 Copyright 2015 iwebgate. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval
Device LinkUP + Desktop LP Guide RDP Version 2.1 January 2016 Copyright 2015 iwebgate. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval
WildFire Cloud File Analysis
 WildFire 6.1 Administrator s Guide WildFire Cloud File Analysis Palo Alto Networks WildFire Administrator s Guide Version 6.1 Contact Information Corporate Headquarters: Palo Alto Networks 4401 Great America
WildFire 6.1 Administrator s Guide WildFire Cloud File Analysis Palo Alto Networks WildFire Administrator s Guide Version 6.1 Contact Information Corporate Headquarters: Palo Alto Networks 4401 Great America
NETWRIX EVENT LOG MANAGER
 NETWRIX EVENT LOG MANAGER QUICK-START GUIDE FOR THE ENTERPRISE EDITION Product Version: 4.0 July/2012. Legal Notice The information in this publication is furnished for information use only, and does not
NETWRIX EVENT LOG MANAGER QUICK-START GUIDE FOR THE ENTERPRISE EDITION Product Version: 4.0 July/2012. Legal Notice The information in this publication is furnished for information use only, and does not
Iridium Extreme TM Satellite Phone. Data Services Manual
 Iridium Extreme TM Satellite Phone Data Services Manual Table of Contents 1 OVERVIEW... 1 2 HOW IT WORKS... 1 3 BEFORE INSTALLING... 2 4 USB DRIVER INSTALLATION... 3 5 MODEM INSTALLATION AND CONFIGURATION...
Iridium Extreme TM Satellite Phone Data Services Manual Table of Contents 1 OVERVIEW... 1 2 HOW IT WORKS... 1 3 BEFORE INSTALLING... 2 4 USB DRIVER INSTALLATION... 3 5 MODEM INSTALLATION AND CONFIGURATION...
Windows BitLocker Drive Encryption Step-by-Step Guide
 Windows BitLocker Drive Encryption Step-by-Step Guide Microsoft Corporation Published: September 2006 Abstract Microsoft Windows BitLocker Drive Encryption is a new hardware-enhanced feature in the Microsoft
Windows BitLocker Drive Encryption Step-by-Step Guide Microsoft Corporation Published: September 2006 Abstract Microsoft Windows BitLocker Drive Encryption is a new hardware-enhanced feature in the Microsoft
C-GEP 100 Monitoring application user manual
 C-GEP 100 Monitoring application user manual 1 Introduction: C-GEP is a very versatile platform for network monitoring applications. The ever growing need for network bandwith like HD video streaming and
C-GEP 100 Monitoring application user manual 1 Introduction: C-GEP is a very versatile platform for network monitoring applications. The ever growing need for network bandwith like HD video streaming and
Comdial Network Management System User Instructions
 Comdial Network Management System User Instructions GCA40 237.01 8/00 printed in U.S.A. Microsoft and Windows 95 are registered trademarks of Microsoft Corporation, Redmond WA. pcanywhere is a registered
Comdial Network Management System User Instructions GCA40 237.01 8/00 printed in U.S.A. Microsoft and Windows 95 are registered trademarks of Microsoft Corporation, Redmond WA. pcanywhere is a registered
ScanShell.Net Install Guide
 ScanShell.Net Install Guide Please install the software first - DO NOT PLUG IN THE SCANNER The scanner has been carefully packaged to avoid damage during transportation. Before operating the scanner, please
ScanShell.Net Install Guide Please install the software first - DO NOT PLUG IN THE SCANNER The scanner has been carefully packaged to avoid damage during transportation. Before operating the scanner, please
BUFFALO LS421DE NAS. 1) Go to Buffalo web-site, buffalotech.com, download the following: - firmware update, comes with LSupdater program - unzip file
 BUFFALO LS421DE NAS OUR NAS HARDWARE CONFIGURATIONS NAS1: - 2 Crucial M500 960GB SATA III 2.5 SSD (new) - 2 Icy Dock EZConvert Pro MB982SP-1S 2.5 SSD to 3.5 SATA Adapter Case RAID0 - DLNA Media Server
BUFFALO LS421DE NAS OUR NAS HARDWARE CONFIGURATIONS NAS1: - 2 Crucial M500 960GB SATA III 2.5 SSD (new) - 2 Icy Dock EZConvert Pro MB982SP-1S 2.5 SSD to 3.5 SATA Adapter Case RAID0 - DLNA Media Server
TX3 Series TELEPHONE ACCESS SYSTEMS. Configurator Quick Start. Version 2.2 Mircom Copyright 2014 LT-973
 TX3 Series TELEPHONE ACCESS SYSTEMS Configurator Quick Start Version 2.2 Mircom Copyright 2014 LT-973 Copyright 2014 Mircom Inc. All rights reserved. Mircom Configurator Software Guide v.2.2 for Windows
TX3 Series TELEPHONE ACCESS SYSTEMS Configurator Quick Start Version 2.2 Mircom Copyright 2014 LT-973 Copyright 2014 Mircom Inc. All rights reserved. Mircom Configurator Software Guide v.2.2 for Windows
Integrated Virtual Debugger for Visual Studio Developer s Guide VMware Workstation 8.0
 Integrated Virtual Debugger for Visual Studio Developer s Guide VMware Workstation 8.0 This document supports the version of each product listed and supports all subsequent versions until the document
Integrated Virtual Debugger for Visual Studio Developer s Guide VMware Workstation 8.0 This document supports the version of each product listed and supports all subsequent versions until the document
WAVES. MultiRack SETUP GUIDE V9.80
 WAVES MultiRack SETUP GUIDE V9.80 1 Table of Contents 1. Overview... 3 2. Basic Requirements... 3 3. Software... 4 4. Required Waves Licenses... 4 5. Installing MultiRack... 5 6. MultiRack Native... 6
WAVES MultiRack SETUP GUIDE V9.80 1 Table of Contents 1. Overview... 3 2. Basic Requirements... 3 3. Software... 4 4. Required Waves Licenses... 4 5. Installing MultiRack... 5 6. MultiRack Native... 6
Config software for D2 systems USER S MANUAL
 DT-CONFIG SOFTWARE Config software for D2 systems USER S MANUAL CONTENTS 1. Introductions ------------------------------------------------------------------- 3 2. System Requirement and Connection ----------------------------------------
DT-CONFIG SOFTWARE Config software for D2 systems USER S MANUAL CONTENTS 1. Introductions ------------------------------------------------------------------- 3 2. System Requirement and Connection ----------------------------------------
OCS Training Workshop LAB14. Email Setup
 OCS Training Workshop LAB14 Email Setup Introduction The objective of this lab is to provide the skills to develop and trouble shoot email messaging. Overview Electronic mail (email) is a method of exchanging
OCS Training Workshop LAB14 Email Setup Introduction The objective of this lab is to provide the skills to develop and trouble shoot email messaging. Overview Electronic mail (email) is a method of exchanging
Sharp Remote Device Manager (SRDM) Server Software Setup Guide
 Sharp Remote Device Manager (SRDM) Server Software Setup Guide This Guide explains how to install the software which is required in order to use Sharp Remote Device Manager (SRDM). SRDM is a web-based
Sharp Remote Device Manager (SRDM) Server Software Setup Guide This Guide explains how to install the software which is required in order to use Sharp Remote Device Manager (SRDM). SRDM is a web-based
Yubico Authenticator User's Guide
 Yubico Authenticator User's Guide YubiKeys with desktop computers and NFCenabled Android smartphones Yubico Authenticator User's Guide 2016 Yubico. All rights reserved. Page 1 of 23 Copyright 2016 Yubico
Yubico Authenticator User's Guide YubiKeys with desktop computers and NFCenabled Android smartphones Yubico Authenticator User's Guide 2016 Yubico. All rights reserved. Page 1 of 23 Copyright 2016 Yubico
IntelliTouch Remote Control & Monitor for Service Professionals. User s Guide. ScreenLogic Wireless Connection Kit Installation Guide
 IntelliTouch Remote Control & Monitor for Service Professionals User s Guide P/N 520840 - Rev A ScreenLogic Wireless Connection Kit Installation Guide ScreenLogic Wireless Connection Kit Installation Guide
IntelliTouch Remote Control & Monitor for Service Professionals User s Guide P/N 520840 - Rev A ScreenLogic Wireless Connection Kit Installation Guide ScreenLogic Wireless Connection Kit Installation Guide
DLP USB Scroll Control. Configuration Guide for QBox
 DLP USB Scroll Control Configuration Guide for QBox Copyright information 2003-2014 Autocue Group Ltd. All rights reserved. All information about Autocue software, hardware and accessories including company
DLP USB Scroll Control Configuration Guide for QBox Copyright information 2003-2014 Autocue Group Ltd. All rights reserved. All information about Autocue software, hardware and accessories including company
System Administration Training Guide. S100 Installation and Site Management
 System Administration Training Guide S100 Installation and Site Management Table of contents System Requirements for Acumatica ERP 4.2... 5 Learning Objects:... 5 Web Browser... 5 Server Software... 5
System Administration Training Guide S100 Installation and Site Management Table of contents System Requirements for Acumatica ERP 4.2... 5 Learning Objects:... 5 Web Browser... 5 Server Software... 5
WildFire Cloud File Analysis
 WildFire Cloud File Analysis The following topics describe the different methods for sending files to the WildFire Cloud for analysis. Forward Files to the WildFire Cloud Verify Firewall File Forwarding
WildFire Cloud File Analysis The following topics describe the different methods for sending files to the WildFire Cloud for analysis. Forward Files to the WildFire Cloud Verify Firewall File Forwarding
NetWrix Privileged Account Manager Version 4.0 Quick Start Guide
 NetWrix Privileged Account Manager Version 4.0 Quick Start Guide Table of Contents Table of Contents... 2 1. Introduction... 3 1.1. What is NetWrix Privileged Account Manager?... 3 1.2. Licensing... 3
NetWrix Privileged Account Manager Version 4.0 Quick Start Guide Table of Contents Table of Contents... 2 1. Introduction... 3 1.1. What is NetWrix Privileged Account Manager?... 3 1.2. Licensing... 3
GreenRADIUS Virtual Appliance
 GreenRADIUS Virtual Appliance Configuration and Administration Guide Software version: 1.0 Document version: 1.1 September 1, 2014 Introduction Disclaimer Green Rocket Security is aprovider of online and
GreenRADIUS Virtual Appliance Configuration and Administration Guide Software version: 1.0 Document version: 1.1 September 1, 2014 Introduction Disclaimer Green Rocket Security is aprovider of online and
Digipass Plug-In for IAS. IAS Plug-In IAS. Microsoft's Internet Authentication Service. Installation Guide
 Digipass Plug-In for IAS IAS Plug-In IAS Microsoft's Internet Authentication Service Installation Guide Disclaimer of Warranties and Limitations of Liabilities Disclaimer of Warranties and Limitations
Digipass Plug-In for IAS IAS Plug-In IAS Microsoft's Internet Authentication Service Installation Guide Disclaimer of Warranties and Limitations of Liabilities Disclaimer of Warranties and Limitations
MITEL SIP CoE. Technical. Configuration Notes. Configure Ascom i62 phones for use with MiVoice Office. SIP CoE 14-4940-00310
 MITEL SIP CoE Technical Configuration Notes Configure Ascom i62 phones for use with MiVoice Office SIP CoE 14-4940-00310 NOTICE The information contained in this document is believed to be accurate in
MITEL SIP CoE Technical Configuration Notes Configure Ascom i62 phones for use with MiVoice Office SIP CoE 14-4940-00310 NOTICE The information contained in this document is believed to be accurate in
ACTi NVR Config Converter User s Manual. Version 1.0.0.17 2012/06/07
 ACTi NVR Config Converter User s Manual Version 1.0.0.17 2012/06/07 Legal Notice Disclaimer The information contained in this document is intended for general information purposes. ACTi Corporation shall
ACTi NVR Config Converter User s Manual Version 1.0.0.17 2012/06/07 Legal Notice Disclaimer The information contained in this document is intended for general information purposes. ACTi Corporation shall
Step by Step Guide to implement SMS authentication to F5 Big-IP APM (Access Policy Manager)
 Installation guide for securing the authentication to your F5 Big-IP APM solution with Nordic Edge One Time Password Server, delivering strong authetication via SMS to your mobile phone. 1 Summary This
Installation guide for securing the authentication to your F5 Big-IP APM solution with Nordic Edge One Time Password Server, delivering strong authetication via SMS to your mobile phone. 1 Summary This
AN017. CAN Bus Monitor for Kvaser. Introduction. CAN Monitor
 AN017 CAN Bus Monitor for Kvaser Introduction CAN card manufactures provide a wide range of tools for performing CAN analysis. The CAN Monitor is the simplest form of software tool, usually packaged free
AN017 CAN Bus Monitor for Kvaser Introduction CAN card manufactures provide a wide range of tools for performing CAN analysis. The CAN Monitor is the simplest form of software tool, usually packaged free
Smart Business Architecture for Midsize Networks Network Management Deployment Guide
 Smart Business Architecture for Midsize Networks Network Management Deployment Guide Introduction: Smart Business Architecture for Mid-sized Networks, Network Management Deployment Guide With the Smart
Smart Business Architecture for Midsize Networks Network Management Deployment Guide Introduction: Smart Business Architecture for Mid-sized Networks, Network Management Deployment Guide With the Smart
Nokia and Nokia Connecting People are registered trademarks of Nokia Corporation
 Nokia and Nokia Connecting People are registered trademarks of Nokia Corporation Nokia E70 Configuring connection settings Nokia E70 Configuring connection settings Legal Notice Copyright Nokia 2006. All
Nokia and Nokia Connecting People are registered trademarks of Nokia Corporation Nokia E70 Configuring connection settings Nokia E70 Configuring connection settings Legal Notice Copyright Nokia 2006. All
Installation Guide for LynxClient
 Installation Guide for LynxClient Technical Support: 972-231-6874 Ext. 140 8am to 5pm CST Email: [email protected] PC Keyboard Duress Button LynxKey & LynxKeyPro USB Duress Button LynxUSB Notification Popup
Installation Guide for LynxClient Technical Support: 972-231-6874 Ext. 140 8am to 5pm CST Email: [email protected] PC Keyboard Duress Button LynxKey & LynxKeyPro USB Duress Button LynxUSB Notification Popup
VMware Horizon FLEX User Guide
 Horizon FLEX 1.1 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this
Horizon FLEX 1.1 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this
Implementation Guide for protecting
 Implementation Guide for protecting Remote Web Workplace (RWW) Outlook Web Access (OWA) 2003 SharePoint 2003 IIS Web Sites with BlackShield ID Copyright 2010 CRYPTOCard Inc. http:// www.cryptocard.com
Implementation Guide for protecting Remote Web Workplace (RWW) Outlook Web Access (OWA) 2003 SharePoint 2003 IIS Web Sites with BlackShield ID Copyright 2010 CRYPTOCard Inc. http:// www.cryptocard.com
UG103.5 EMBER APPLICATION DEVELOPMENT FUNDAMENTALS: SECURITY
 EMBER APPLICATION DEVELOPMENT FUNDAMENTALS: SECURITY This document introduces some basic security concepts, including network layer security, trust centers, and application support layer security features.
EMBER APPLICATION DEVELOPMENT FUNDAMENTALS: SECURITY This document introduces some basic security concepts, including network layer security, trust centers, and application support layer security features.
HOTPin Integration Guide: DirectAccess
 1 HOTPin Integration Guide: DirectAccess Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document is provided 'as is'; Celestix assumes no responsibility
1 HOTPin Integration Guide: DirectAccess Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document is provided 'as is'; Celestix assumes no responsibility
OfficeServ Link. User Guide. Version 2.1 June 2005
 OfficeServ Link User Guide Version 2.1 June 2005 OfficeServ Link Version 2.1 User Guide This manual should be read before the installation and operation of the OfficeServ Link Software. COPYRIGHT This
OfficeServ Link User Guide Version 2.1 June 2005 OfficeServ Link Version 2.1 User Guide This manual should be read before the installation and operation of the OfficeServ Link Software. COPYRIGHT This
BlackBerry Enterprise Service 10. Secure Work Space for ios and Android Version: 10.1.1. Security Note
 BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
MANUFACTURER RamSoft Incorporated 243 College St, Suite 100 Toronto, ON M5T 1R5 CANADA
 All Information provided in this document and in the accompanying software is subject to change without notice and does not represent a commitment on the part of RamSoft. RamSoft assumes no responsibility
All Information provided in this document and in the accompanying software is subject to change without notice and does not represent a commitment on the part of RamSoft. RamSoft assumes no responsibility
WinSALTS. The 32-bit version of the WinSALTS Program. WinSALTS Training Handout Modified for ROM II EDI Users 10 March 10, 2005 Version 5.
 WinSALTS The 32-bit version of the WinSALTS Program WinSALTS Training Handout Modified for ROM II EDI Users 10 March 10, 2005 Version 5.04 SALTS CENTRAL NAVSISA (N00367) 5450 Carlisle Pike P.O. Box 2010
WinSALTS The 32-bit version of the WinSALTS Program WinSALTS Training Handout Modified for ROM II EDI Users 10 March 10, 2005 Version 5.04 SALTS CENTRAL NAVSISA (N00367) 5450 Carlisle Pike P.O. Box 2010
µtasker Document FTP Client
 Embedding it better... µtasker Document FTP Client utaskerftp_client.doc/1.01 Copyright 2012 M.J.Butcher Consulting Table of Contents 1. Introduction...3 2. FTP Log-In...4 3. FTP Operation Modes...4 4.
Embedding it better... µtasker Document FTP Client utaskerftp_client.doc/1.01 Copyright 2012 M.J.Butcher Consulting Table of Contents 1. Introduction...3 2. FTP Log-In...4 3. FTP Operation Modes...4 4.
Strong Authentication for Cisco ASA 5500 Series
 Strong Authentication for Cisco ASA 5500 Series with Powerful Authentication Management for Service Providers and Enterprises Authentication Service Delivery Made EASY Copyright Copyright 2011. CRYPTOCard
Strong Authentication for Cisco ASA 5500 Series with Powerful Authentication Management for Service Providers and Enterprises Authentication Service Delivery Made EASY Copyright Copyright 2011. CRYPTOCard
DB Administration COMOS. Platform DB Administration. Trademarks 1. Prerequisites. MS SQL Server 2005/2008 3. Oracle. Operating Manual 09/2011
 Trademarks 1 Prerequisites 2 COMOS Platform MS SQL Server 2005/2008 3 Oracle 4 Operating Manual 09/2011 A5E03638301-01 Legal information Legal information Warning notice system This manual contains notices
Trademarks 1 Prerequisites 2 COMOS Platform MS SQL Server 2005/2008 3 Oracle 4 Operating Manual 09/2011 A5E03638301-01 Legal information Legal information Warning notice system This manual contains notices
Wireless N 150 USB Adapter with 10dBi High Gain Antenna. Model # AWLL5055 User s Manual. Rev. 1.0
 Wireless N 150 USB Adapter with 10dBi High Gain Antenna Model # AWLL5055 User s Manual Rev. 1.0 Table of Contents 1. Introduction...2 1.1 Package Contents...2 1.2 Features...2 2. Install Wireless USB Adapter...3
Wireless N 150 USB Adapter with 10dBi High Gain Antenna Model # AWLL5055 User s Manual Rev. 1.0 Table of Contents 1. Introduction...2 1.1 Package Contents...2 1.2 Features...2 2. Install Wireless USB Adapter...3
How To Test The Bandwidth Meter For Hyperv On Windows V2.4.2.2 (Windows) On A Hyperv Server (Windows V2) On An Uniden V2 (Amd64) Or V2A (Windows 2
 BANDWIDTH METER FOR HYPER-V NEW FEATURES OF 2.0 The Bandwidth Meter is an active application now, not just a passive observer. It can send email notifications if some bandwidth threshold reached, run scripts
BANDWIDTH METER FOR HYPER-V NEW FEATURES OF 2.0 The Bandwidth Meter is an active application now, not just a passive observer. It can send email notifications if some bandwidth threshold reached, run scripts
The YubiKey Manual. Usage, configuration and introduction of basic concepts
 Usage, configuration and introduction of basic concepts Version: 3.3 Date: 17 th September, 2014 Disclaimer The contents of this document are subject to revision without notice due to continued progress
Usage, configuration and introduction of basic concepts Version: 3.3 Date: 17 th September, 2014 Disclaimer The contents of this document are subject to revision without notice due to continued progress
Table of Contents. Cisco Wi Fi Protected Access 2 (WPA 2) Configuration Example
 Table of Contents Wi Fi Protected Access 2 (WPA 2) Configuration Example...1 Document ID: 67134...1 Introduction...1 Prerequisites...1 Requirements...1 Components Used...2 Conventions...2 Background Information...2
Table of Contents Wi Fi Protected Access 2 (WPA 2) Configuration Example...1 Document ID: 67134...1 Introduction...1 Prerequisites...1 Requirements...1 Components Used...2 Conventions...2 Background Information...2
Installing and Configuring vcenter Support Assistant
 Installing and Configuring vcenter Support Assistant vcenter Support Assistant 5.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced
Installing and Configuring vcenter Support Assistant vcenter Support Assistant 5.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced
User Manual. Thermo Scientific Orion
 User Manual Thermo Scientific Orion Orion Star Com Software Program 68X637901 Revision A April 2013 Contents Chapter 1... 4 Introduction... 4 Star Com Functions... 5 Chapter 2... 6 Software Installation
User Manual Thermo Scientific Orion Orion Star Com Software Program 68X637901 Revision A April 2013 Contents Chapter 1... 4 Introduction... 4 Star Com Functions... 5 Chapter 2... 6 Software Installation
MT-350 SMS. Operation Manual. PORTech Communications Inc.
 MT-350 SMS Operation Manual PORTech Communications Inc. Index 1.Hardware Setup...1 2.Software Setup...1 3.Operation Guide...2 4.How to send out a short message...3 5.Report File...6 6.Q & A...6 MT-350
MT-350 SMS Operation Manual PORTech Communications Inc. Index 1.Hardware Setup...1 2.Software Setup...1 3.Operation Guide...2 4.How to send out a short message...3 5.Report File...6 6.Q & A...6 MT-350
VMware Horizon FLEX User Guide
 Horizon FLEX 1.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this
Horizon FLEX 1.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this
Microsoft Networks. SMB File Sharing Protocol Extensions. Document Version 3.4
 Microsoft Networks SMB File Sharing Protocol Extensions Document Version 3.4 February 7, 2010 1. Introduction...2 2. Negotiate Protocol...2 3. Session Setup and X...3 4. Tree Connect and X SMB...4 5. Locking
Microsoft Networks SMB File Sharing Protocol Extensions Document Version 3.4 February 7, 2010 1. Introduction...2 2. Negotiate Protocol...2 3. Session Setup and X...3 4. Tree Connect and X SMB...4 5. Locking
Diamond II v2.3 Service Pack 4 Installation Manual
 Diamond II v2.3 Service Pack 4 Installation Manual P/N 460987001B ISS 26APR11 Copyright Disclaimer Trademarks and patents Intended use Software license agreement FCC compliance Certification and compliance
Diamond II v2.3 Service Pack 4 Installation Manual P/N 460987001B ISS 26APR11 Copyright Disclaimer Trademarks and patents Intended use Software license agreement FCC compliance Certification and compliance
Active Directory Integration with Blue Coat
 The Web Security Authority. TM Active Directory Integration with Blue Coat NOTE: This techbrief is applicable when using NTLM under Windows 2000 Server. Introduction Windows 2000 server utilizes Active
The Web Security Authority. TM Active Directory Integration with Blue Coat NOTE: This techbrief is applicable when using NTLM under Windows 2000 Server. Introduction Windows 2000 server utilizes Active
Installing the Gerber P2C Plotter USB Driver
 Installing the Gerber P2C Plotter USB Driver 1 You can install a Gerber P2C plotter using a USB connection and communicate with it using compatible design software. The following procedures describe installing
Installing the Gerber P2C Plotter USB Driver 1 You can install a Gerber P2C plotter using a USB connection and communicate with it using compatible design software. The following procedures describe installing
How to configure MAC authentication on a ProCurve switch
 An HP ProCurve Networking Application Note How to configure MAC authentication on a ProCurve switch Contents 1. Introduction... 3 2. Prerequisites... 3 3. Network diagram... 3 4. Configuring the ProCurve
An HP ProCurve Networking Application Note How to configure MAC authentication on a ProCurve switch Contents 1. Introduction... 3 2. Prerequisites... 3 3. Network diagram... 3 4. Configuring the ProCurve
Installing CaseMap Server User Guide
 Installing CaseMap Server User Guide CaseMap Server, Version 1.8 System Requirements Installing CaseMap Server Installing the CaseMap Admin Console Installing the CaseMap SQL Import Utility Testing Installation
Installing CaseMap Server User Guide CaseMap Server, Version 1.8 System Requirements Installing CaseMap Server Installing the CaseMap Admin Console Installing the CaseMap SQL Import Utility Testing Installation
StorageCraft ShadowStream User Guide StorageCraft Copyright Declaration
 StorageCraft Copyright Declaration StorageCraft ImageManager, StorageCraft ShadowProtect, StorageCraft Cloud, and StorageCraft Cloud Services, together with any associated logos, are trademarks of StorageCraft
StorageCraft Copyright Declaration StorageCraft ImageManager, StorageCraft ShadowProtect, StorageCraft Cloud, and StorageCraft Cloud Services, together with any associated logos, are trademarks of StorageCraft
How To Connect To A Ppanasonic Pbx On A Pc Or Mac Or Ipa (For A Pc) With A Usb Or Ipo (For Mac) With Pbq (For Pc) On A Usb (For Pb
 R KX-Series PBX TAPI Service Provider Installation Manual Revision: 4.0.0.1 October 2011 Introduction About TSP Panasonic TAPI Service Provider for TDA/TDE/NCP/NS Series PBX (Panasonic TSP) is a driver
R KX-Series PBX TAPI Service Provider Installation Manual Revision: 4.0.0.1 October 2011 Introduction About TSP Panasonic TAPI Service Provider for TDA/TDE/NCP/NS Series PBX (Panasonic TSP) is a driver
Kvaser BlackBird Getting Started Guide
 Kvaser BlackBird Getting Started Guide Copyright 2007-2011 Kvaser AB, Mölndal, Sweden http://www.kvaser.com Last updated Wednesday, 18 September 2013 We believe that the information contained herein was
Kvaser BlackBird Getting Started Guide Copyright 2007-2011 Kvaser AB, Mölndal, Sweden http://www.kvaser.com Last updated Wednesday, 18 September 2013 We believe that the information contained herein was
APPLICATION NOTE. Secure Personalization with Transport Key Authentication. ATSHA204A, ATECC108A, and ATECC508A. Introduction.
 APPLICATION NOTE Secure Personalization with Transport Key Authentication ATSHA204A, ATECC108A, and ATECC508A Introduction The Atmel CryptoAuthentication ATSHA204A, ATECC108A, and ATECC508A devices (crypto
APPLICATION NOTE Secure Personalization with Transport Key Authentication ATSHA204A, ATECC108A, and ATECC508A Introduction The Atmel CryptoAuthentication ATSHA204A, ATECC108A, and ATECC508A devices (crypto
Integrating idrac 7 with Microsoft Active Directory
 Integrating idrac 7 with Microsoft Active Directory Whitepaper Author: Jim Slaughter This document is for informational purposes only and may contain typographical errors and technical inaccuracies. The
Integrating idrac 7 with Microsoft Active Directory Whitepaper Author: Jim Slaughter This document is for informational purposes only and may contain typographical errors and technical inaccuracies. The
Allworx OfficeSafe Operations Guide Release 6.0
 Allworx OfficeSafe Operations Guide Release 6.0 No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopy,
Allworx OfficeSafe Operations Guide Release 6.0 No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopy,
Strong Authentication for Microsoft SharePoint
 Strong Authentication for Microsoft SharePoint with Powerful Authentication Management for Service Providers and Enterprises Authentication Service Delivery Made EASY Copyright Copyright 2011. CRYPTOCard
Strong Authentication for Microsoft SharePoint with Powerful Authentication Management for Service Providers and Enterprises Authentication Service Delivery Made EASY Copyright Copyright 2011. CRYPTOCard
vcenter Support Assistant User's Guide
 vcenter Support Assistant 5.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions
vcenter Support Assistant 5.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions
Netflow Collection with AlienVault Alienvault 2013
 Netflow Collection with AlienVault Alienvault 2013 CONFIGURE Configuring NetFlow Capture of TCP/IP Traffic from an AlienVault Sensor or Remote Hardware Level: Beginner to Intermediate Netflow Collection
Netflow Collection with AlienVault Alienvault 2013 CONFIGURE Configuring NetFlow Capture of TCP/IP Traffic from an AlienVault Sensor or Remote Hardware Level: Beginner to Intermediate Netflow Collection
SPHOL326: Designing a SharePoint 2013 Site. Hands-On Lab. Lab Manual
 2013 SPHOL326: Designing a SharePoint 2013 Site Hands-On Lab Lab Manual This document is provided as-is. Information and views expressed in this document, including URL and other Internet Web site references,
2013 SPHOL326: Designing a SharePoint 2013 Site Hands-On Lab Lab Manual This document is provided as-is. Information and views expressed in this document, including URL and other Internet Web site references,
ebus Player Quick Start Guide
 ebus Player Quick Start Guide This guide provides you with the information you need to efficiently set up and start using the ebus Player software application to control your GigE Vision or USB3 Vision
ebus Player Quick Start Guide This guide provides you with the information you need to efficiently set up and start using the ebus Player software application to control your GigE Vision or USB3 Vision
Bidirectional wireless communication using EmbedRF
 Bidirectional wireless communication using EmbedRF 1. Tools you will need for this application note... 2 2. Introduction... 3 3. Connect EmbedRF Board to USB Interface Board... 3 4. Install and Run EmbedRF
Bidirectional wireless communication using EmbedRF 1. Tools you will need for this application note... 2 2. Introduction... 3 3. Connect EmbedRF Board to USB Interface Board... 3 4. Install and Run EmbedRF
www.rohos.com Two-factor authentication Free portable encryption for USB drive Hardware disk encryption Face recognition logon
 Two-factor authentication Free portable encryption for USB drive Hardware disk encryption Face recognition logon Secure Windows and Mac login by USB key www.rohos.com Rohos Logon Key Secure two-factor
Two-factor authentication Free portable encryption for USB drive Hardware disk encryption Face recognition logon Secure Windows and Mac login by USB key www.rohos.com Rohos Logon Key Secure two-factor
Sample Configuration: Cisco UCS, LDAP and Active Directory
 First Published: March 24, 2011 Last Modified: March 27, 2014 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS
First Published: March 24, 2011 Last Modified: March 27, 2014 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS
Perceptive Intelligent Capture Solution Configration Manager
 Perceptive Intelligent Capture Solution Configration Manager Installation and Setup Guide Version: 1.0.x Written by: Product Knowledge, R&D Date: February 2016 2015 Lexmark International Technology, S.A.
Perceptive Intelligent Capture Solution Configration Manager Installation and Setup Guide Version: 1.0.x Written by: Product Knowledge, R&D Date: February 2016 2015 Lexmark International Technology, S.A.
Network Projector Operation Guide
 Network Projector Operation Guide Table of contents Preparation...3 Connecting the projector with your computer...3 Wired connection... 3 Wireless connection (for selective models)... 4 QPresenter...7
Network Projector Operation Guide Table of contents Preparation...3 Connecting the projector with your computer...3 Wired connection... 3 Wireless connection (for selective models)... 4 QPresenter...7
QUICK START GUIDE MONDOPAD/WIN7 009-1488-01
 QUICK START GUIDE MONDOPAD/WIN7 009-1488-01 CONTENTS Hardware Setup...3 Windows Setup and Registration Process...3 Microsoft Windows Setup...3 Mondopad Software Registration...4 Microsoft Office Activation...4
QUICK START GUIDE MONDOPAD/WIN7 009-1488-01 CONTENTS Hardware Setup...3 Windows Setup and Registration Process...3 Microsoft Windows Setup...3 Mondopad Software Registration...4 Microsoft Office Activation...4
