28 Closest-Point Problems
|
|
|
- Claribel Chambers
- 10 years ago
- Views:
Transcription
1 28 Closest-Point Problems Geometric problems involving points on the plane usually involve implicit or explicit treatment of distances between the points. For example, a very natural problem which arises in many applications is the nearest-neighbor problem: find the point among a set of given points closest to a given new point. This seems to involve checking the distance from the given point to each point in the set, but much better solutions are possible. In this section we'll look at some other distance problems, a prototype algorithm, and a fundamental geometric structure called the Voronoi diagram that can be used effectively for a variety of such problems in the plane. Our approach will be to describe a general method for solving closest point problems through careful consideration of a prototype implementation for a simple problem. Some of the problems that we consider in this chapter are similar to the rangesearching problems of Chapter 26, and the grid and 2D tree methods developed there are suitable for solving the nearest-neighbor and other problems. The fundamental shortcoming of those methods, however, is that they rely on randomness in the point set: they have bad worst-case performance. Our aim in this chapter is to examine another general approach that has guaranteed good performance for many problems, no matter what the input. Some of the methods are too complicated for us to examine a full implementation, and they involve sufficient overhead that the simpler methods may do better when the point set is not large or when it is sufficiently well dispersed. However, the study of methods with good worst-case performance will uncover some fundamental properties of point sets that should be understood even if simpler methods are more suitable in specific situations. The general approach we'll examine provides yet another example of the use of doubly recursive procedures to intertwine processing along the two coordinate directions. The two previous methods we've seen of this type (kd trees and line intersection) have been based on binary search trees; here the method is a "combine and conquer" method based on mergesort. Closest-Pair Problem The closest-pair problem is to find the two points that are closest together among a set of points. This problem is related to the nearest-neighbor problem; though it is not as widely applicable, it will serve us well as a prototype closest-point problem in that it can be solved with an algorithm whose general recursive structure is appropriate for other problems. It would seem necessary to examine the distances between all pairs of points to find the smallest such distance: for N points this would mean a running time proportional to N 2. However, it turns out that we can use sorting to get by with examining only about N logn distances between points in the worst case (far fewer on the average) and get a worst-case running time proportional to N logn (far better on the average). In this section, we'll examine such an algorithm in detail. The algorithm we'll use is based on a straightforward "divide-and-conquer" strategy. The idea is to sort the points on one coordinate, say the x coordinate, then use that ordering to divide the points in half. The closest pair in the whole set is either the closest pair in one of the halves or the closest pair with one member in each half. The interesting case, of course, is when the closest pair crosses the dividing line: the closest pair in each half can obviously be found by using recursive calls, but how can all the pairs on either side of the dividing line be checked efficiently? Since the only information we seek is the closest pair of the point set, we need examine only points within distance min of the dividing line, where min is the smaller of the distances between the closest pairs found in the two halves. By itself, however, this observation isn't enough help in the worst case, since there could be many pairs of points very close to the dividing line; for example, all the points in each half could be lined up right next to the dividing line. To handle such situations, it seems necessary to sort the points on y. Then we can limit the number of distance computations involving each point as follows: proceeding through the points in increasing y order, check if each point is inside the vertical strip containing all points in the plane within min of the dividing line. For each such point, compute the distance between it and any point also in the strip whose y coordinate is less than the y coordinate of the current point, but not more than min less. The fact that the distance between all pairs of points in each half is at least min means that only a few points are likely to be checked.
2 In the small set of points on the left in Figure 28.1, the imaginary vertical dividing line just to the right of F has eight points to the left, eight points to the right. The closest pair on the left half is AC (or AO), the closest pair on the right is JM. If the points are sorted on y, then the closest pair split by the line is found by checking the pairs HI, Cl, FK (the closest pair in the whole point set), and finally EK. For larger point sets, the band that could contain a closest pair spanning the dividing line is narrower, as shown on the right in Figure E j.o.a.g.d.c.f.h.n.k.p.i.b.j.m.l Figure 28.1 Divide-and-conquer approach to find the closest pair. Though this algorithm is stated simply, some care is required to implement it efficiently: for example, it would be too expensive to sort the points on y within our recursive subroutine. We've seen several algorithms with running times described by the recurrence C N = 2C N/2 + N, which implies that C N is proportional to N log N; if we were to do the full sort on y, then the recurrence would become C N = 2C N /2 + N log N, which implies that C N is proportional to N log 2 N (see Chapter 6). To avoid this, we need to avoid the sort of y. The solution to this problem is simple, but subtle. The mergesort method from Chapter 12 is based on dividing the elements to be sorted exactly as the points are divided above. We have two problems to solve and the same general method to solve them, so we may as well solve them simultaneously! Specifically, we'll write one recursive routine that both sorts on y and finds the closest pair. It will do so by splitting the point set in half, then calling itself recursively to sort the two halves on y and find the closest pair in each half, then merging to complete the sort on y and applying the procedure above to complete the closest-pair computation. In this way, we avoid the cost of doing an extra y sort by intermixing the data movement required for the sort with the data movement required for the closest-pair computation. For they sort, the split in half could be done in any way, but for the closest-pair computation, it's required that the points in one half all have smaller x coordinates than the points in the other half. This is easily accomplished by sorting on x before doing the division. In fact, we may as well use the same routine to sort on x! Once this general plan is accepted, the implementation is not difficult to understand. As mentioned above, the implementation will use the recursive sort and merge procedures of Chapter 12. 'fhe first step is to modify the list structures to hold points instead of keys, and to modify merge to check a global variable pass to decide how to do its comparison. If pass=1, we should compare the x coordinates of the two points; if pass=2 we compare the y coordinates of the two points. The implementation of this is straightforward: function merge (a. b: link): link; var c: link; comp: boolean; c:=z; repeat
3 if pass=l then comp: =a.p.x < b.p.x else comp:=a.p.y<b.p.y; if comp then c. next:=a; c:=a; a:=a.next end else c.next:=b; c:=b; b:=b.next end until c=z; merge:=z.next; z.next:=z; The dummy node z which appears at the end of all lists is initialized to contain a "sentinel" point with artificially high x and y coordinates. To compute distances, we use another simple procedure that checks that the distance between the two points given as arguments is less than the global variable min. If so, it resets min to that distance and saves the points in the global variables cpl and cp2: procedure check (p1, p2: point); var dist: real; if (pl.y< >z.p.y) and (p2.y< >z.p.y) then dist:=sqrt((pl.x-p2.x)* (pl.x-p2.x)+(pl.y-p2.y)* (pl.y-p2.y)); if dist<min then min:=dist; cpl:=pl; cp2:=p Thus, the global min always contains the distance between cpl and ep2, the closest pair found so far. The next step is to modify the recursive sort of Chapter 12 also to do the closest-point computation when pass=2, as follows: function sort (c: link; N: integer): link; var a. b: link; i: integer; middle: real; p1, p2, p3, p4: point; if c.next=z then sort:=c else a:=c; for i:= 2 to N div 2 do c:=c.next; b:=c.next; c.next:=z; if pass=2 then middle:=b.p.x; c:=merge (sort(a, N div 2), sort(b.n- (N div 2))); sort:=c; if pass=2 then a:=c; pl:=z.p; p2:=z.p; p3:=z.p; p4:=z.p; repeat if abs (a.p.x - middle) < min then check (a.p, p1); check (a.p, p2); check (a.p,p3); check (a.p, p4); pl:=p2; p2:=p3; p3:=p4; p4:=a.p a: =a.next
4 until a=z end If pass=l, this is exactly the recursive mergesort routine of Chapter 12: it returns a linked list containing the points sorted on their x coordinates (because merge has been modified as described above to compare x coordinates on passl). The magic of this implementation comes whenpass=2. The program not only sorts on y (because merge has been modified as described above to compare y coordinates on pass2) but also completes the closest-point computation, as described in detail below. First, we sort on x; then we sort on y and find the closest pair by invoking sort as follows: G O A D E C H F I K B P N J M L new(z); z.next:=z; z.p.x:=maxint; z.p.y:=maxint; new(h); h.next:=readlist; min:=maxint; pass:=l; h.next:=sort(h.next, N); pass:=2; h.next:=sort(h.next, N); Figure 28.2 Recursive call tree for closest-pair computation After these calls, the closest pair of points is found in the global variables cpl and cp2, which are managed by the check "find the minimum" procedure. The crux of the implementation is the operation of sort when pass=2. Before the recursive calls the points are sorted on x: this ordering is used to divide the points in half and to find the x coordinate of the dividing line. After the recursive calls the points are sorted on y and the distance between every pair of points in each half is known to be greater than min. The ordering on y is used to scan the points near the dividing line; the value of min is used to limit the number of points to be tested. Each point within a distance of min of the dividing line is checked against each of the previous four points found within a distance of min of the dividing line. This check is guaranteed to find any pair of points closer together than min with one member of the pair on either side of the dividing line. (This is an amusing geometric fact which the reader may wish to verify): We know that points that fall on the same side of the dividing line are spaced by at least min, so the number of points falling in any circle of radius min is limited.) Figure 28.2 shows the recursive call tree describing the operation of this algorithm on our small set of points. An internal node in this tree represents a vertical line dividing the points in the left and right subtree. The nodes
5 are numbered in the order in which the vertical lines are tried in the algorithm. This numbering corresponds to a postorder traversal of the tree because the computation involving the dividing line comes aftei- the recursive calls in the program, and is simply another way of looking at the order in which merges are done during a recursive mergesort (see Chapter 12). O G A D G O A D E C H F E C H F O D C F G A E H I K B P I K B P N J
6 M L N M J L K P J L I B N M O D C F K P J L G A E H I B N M Figure 28.3 Closest-pair computation (x coordinate magnified). Thus, first the line between G and 0 is tried and the pair GO is retained as the closest so far. Then the line between A and D is tried, but A and D are too far apart to change min. Then the line between 0 and A is tried and the pairs GD GA and OA all are successively closer pairs. It happens for this example that no closer pairs are found until FK, which is the last pair checked for the last dividing line tried. The careful reader may have noticed that we have not implemented the pure divide-and-conquer algorithm described above-we don't actually compute the closest pair in the two halves, then take the better of the two. Instead, we get the closer of the two closest pairs simply by using a global variable for min during the recursive computation. Each time we find a closer pair, we can consider a narrower vertical strip around the current dividing line, no matter where we are in the recursive computation. Figure 28.3 shows the process in detail. The x -coordinate in these diagrams is magnified to emphasize the x orientation of the process and to point out parallels with mergesort (see Chapter 12). We start by doing a y-sort on the four leftmost points G 0 A D, by sorting G 0, then sorting A D, then merging. After the merge, the y-sort is complete, and we find the closest pair AO spanning the dividing line. Eventually, the points are sorted on their y- coordinate and the closest pair is computed. Property28.1 The closest pair in a set of N points can be found in O(NlogN) steps. Essentially, the computation is done in the time it takes to do two mergesorts (one on the x-coordinate, one on the y-coordinate) plus the cost of looking along the dividing line. This cost is also governed by the recurrence T N = T NI2 +N (see Chapter 6). The general approach we've used here for the closest-pair problem can be used to solve other geometric problems. For example, another question of interest is the all-nearest-neighbors problem: for each point we want to find the point nearest to it. This problem can be solved using a program like the one above with extra processing along the dividing line to find, for each point, whether there is a point on the other side closer than its closest point on its own side. Again, the "free" y sort is helpful for this computation. Voronoi Diagrams The set of all points closer to a given point in a point set than to all other points in the set is an interesting geometric structure cal led the Voronoi po4gon for the point. The union of all the Voronoi polygons for a point set is called its Voronoi diagram. This is the ultimate in closest-point computations: we'll see that most of the problems we face involving distances between points have natural and interesting solutions based on the Voronoi diagram. The diagrams for our sample point sets are shown in Figure The Voronoi polygon for a point is made up of the perpendicular bisectors of the segments linking the point to those points closest to it. Its actual definition is the other way around: the Voronoi polygon is defined to be perimeter of the set of all points in the plane closer to the given point than to any other point in the point set, and each edge on the Voronoi polygon separates a given point from one of the points "closest to" it.
7 The dual of the Voronoi diagram, shown in Figure 28.5, makes this correspon dence explicit: in the dual, a line is drawn between each point and all the points "closest to" it. This is also called the Delaunay triangulation. Put another way, x and y are connected in the Voronoi dual if their Voronoi polygons have an edge in common. Figure 28.4 Voronoi Diagram. Figure 28.5 Delaunay Triangulation. The Voronoi diagram and the Delaunay triangulation have many properties that lead to efficient algorithms for closest-point problems. The property that makes these algorithms efficient is that the number of lines in both the diagram and the dual is proportional to a small constant times N. For example, the line connecting the closest pair of points must be in the dual, so the problem of the previous section can be solved by computing the dual and then simply finding the minimum length line among the lines in the dual. Similarly, the line connecting each point to its nearest neighbor must be in the dual, so the all-nearest-neighbors problem reduces directly to finding the dual. The convex hull of the point set is part of the dual, so computing the Voronoi dual is yet another convex hull algorithm. We'll see yet another example in Chapter 31 of a problem which can be solved efficiently by first finding the Voronoi dual. The defining property of the Voronoi diagram means that it can be used to solve the nearest-neighbor problem: to identify the nearest neighbor in a point set to a given point, we need only find out which Voronoi polygon the point falls in. It is possible to organize the Voronoi polygons in a structure like a 2D tree to allow this search to be done efficiently.
8 The Voronoi diagram can be computed using an algorithm with the same general structure as the closest-point algorithm above. The points are first sorted on their x coordinate. Then that ordering is used to split the points in half, leading to two recursive calls to find the Voronoi diagram of the point set for each half. At the same time, the points are sorted on y; finally, the two Voronoi diagrams for the two halves are merged together. As before, this merging (done with pass=2) can exploit the fact that the points are sorted on x before the recursive calls and that they are sorted on y and that the Voronoi diagrams for the two halves have been built after the recursive calls. However, even with these aids, the merge is quite a complicated task, and presentation of a full implementation would be beyond the scope of this book. The Voronoi diagram is certainly the natural structure for closest-point problems, and understanding the characteristics of a problem in terms of the Voronoi diagram or its dual is certainly a worthwhile exercise. However, for many particular problems, a direct implementation based on the general schema given in this chapter may be suitable. This schema is powerful enough to compute the Voronoi diagram, so it is powerful enough for algorithms based on the Voronoi diagram, and it may admit to simpler, more efficient code, as we saw for the closest-pair problem.
Closest Pair of Points. Kleinberg and Tardos Section 5.4
 Closest Pair of Points Kleinberg and Tardos Section 5.4 Closest Pair of Points Closest pair. Given n points in the plane, find a pair with smallest Euclidean distance between them. Fundamental geometric
Closest Pair of Points Kleinberg and Tardos Section 5.4 Closest Pair of Points Closest pair. Given n points in the plane, find a pair with smallest Euclidean distance between them. Fundamental geometric
EE602 Algorithms GEOMETRIC INTERSECTION CHAPTER 27
 EE602 Algorithms GEOMETRIC INTERSECTION CHAPTER 27 The Problem Given a set of N objects, do any two intersect? Objects could be lines, rectangles, circles, polygons, or other geometric objects Simple to
EE602 Algorithms GEOMETRIC INTERSECTION CHAPTER 27 The Problem Given a set of N objects, do any two intersect? Objects could be lines, rectangles, circles, polygons, or other geometric objects Simple to
5.4 Closest Pair of Points
 5.4 Closest Pair of Points Closest Pair of Points Closest pair. Given n points in the plane, find a pair with smallest Euclidean distance between them. Fundamental geometric primitive. Graphics, computer
5.4 Closest Pair of Points Closest Pair of Points Closest pair. Given n points in the plane, find a pair with smallest Euclidean distance between them. Fundamental geometric primitive. Graphics, computer
Closest Pair Problem
 Closest Pair Problem Given n points in d-dimensions, find two whose mutual distance is smallest. Fundamental problem in many applications as well as a key step in many algorithms. p q A naive algorithm
Closest Pair Problem Given n points in d-dimensions, find two whose mutual distance is smallest. Fundamental problem in many applications as well as a key step in many algorithms. p q A naive algorithm
Computational Geometry. Lecture 1: Introduction and Convex Hulls
 Lecture 1: Introduction and convex hulls 1 Geometry: points, lines,... Plane (two-dimensional), R 2 Space (three-dimensional), R 3 Space (higher-dimensional), R d A point in the plane, 3-dimensional space,
Lecture 1: Introduction and convex hulls 1 Geometry: points, lines,... Plane (two-dimensional), R 2 Space (three-dimensional), R 3 Space (higher-dimensional), R d A point in the plane, 3-dimensional space,
root node level: internal node edge leaf node CS@VT Data Structures & Algorithms 2000-2009 McQuain
 inary Trees 1 A binary tree is either empty, or it consists of a node called the root together with two binary trees called the left subtree and the right subtree of the root, which are disjoint from each
inary Trees 1 A binary tree is either empty, or it consists of a node called the root together with two binary trees called the left subtree and the right subtree of the root, which are disjoint from each
MA 323 Geometric Modelling Course Notes: Day 02 Model Construction Problem
 MA 323 Geometric Modelling Course Notes: Day 02 Model Construction Problem David L. Finn November 30th, 2004 In the next few days, we will introduce some of the basic problems in geometric modelling, and
MA 323 Geometric Modelling Course Notes: Day 02 Model Construction Problem David L. Finn November 30th, 2004 In the next few days, we will introduce some of the basic problems in geometric modelling, and
Shortest Path Algorithms
 Shortest Path Algorithms Jaehyun Park CS 97SI Stanford University June 29, 2015 Outline Cross Product Convex Hull Problem Sweep Line Algorithm Intersecting Half-planes Notes on Binary/Ternary Search Cross
Shortest Path Algorithms Jaehyun Park CS 97SI Stanford University June 29, 2015 Outline Cross Product Convex Hull Problem Sweep Line Algorithm Intersecting Half-planes Notes on Binary/Ternary Search Cross
Scan-Line Fill. Scan-Line Algorithm. Sort by scan line Fill each span vertex order generated by vertex list
 Scan-Line Fill Can also fill by maintaining a data structure of all intersections of polygons with scan lines Sort by scan line Fill each span vertex order generated by vertex list desired order Scan-Line
Scan-Line Fill Can also fill by maintaining a data structure of all intersections of polygons with scan lines Sort by scan line Fill each span vertex order generated by vertex list desired order Scan-Line
CSE 421 Algorithms: Divide and Conquer
 CSE 421 Algorithms: Divide and Conquer Summer 2011 Larry Ruzzo Thanks to Paul Beame, James Lee, Kevin Wayne for some slides hw2 empirical run times e n Plot Time vs n Fit curve to it (e.g., with Excel)
CSE 421 Algorithms: Divide and Conquer Summer 2011 Larry Ruzzo Thanks to Paul Beame, James Lee, Kevin Wayne for some slides hw2 empirical run times e n Plot Time vs n Fit curve to it (e.g., with Excel)
Persistent Data Structures
 6.854 Advanced Algorithms Lecture 2: September 9, 2005 Scribes: Sommer Gentry, Eddie Kohler Lecturer: David Karger Persistent Data Structures 2.1 Introduction and motivation So far, we ve seen only ephemeral
6.854 Advanced Algorithms Lecture 2: September 9, 2005 Scribes: Sommer Gentry, Eddie Kohler Lecturer: David Karger Persistent Data Structures 2.1 Introduction and motivation So far, we ve seen only ephemeral
The Tower of Hanoi. Recursion Solution. Recursive Function. Time Complexity. Recursive Thinking. Why Recursion? n! = n* (n-1)!
 The Tower of Hanoi Recursion Solution recursion recursion recursion Recursive Thinking: ignore everything but the bottom disk. 1 2 Recursive Function Time Complexity Hanoi (n, src, dest, temp): If (n >
The Tower of Hanoi Recursion Solution recursion recursion recursion Recursive Thinking: ignore everything but the bottom disk. 1 2 Recursive Function Time Complexity Hanoi (n, src, dest, temp): If (n >
Data Warehousing und Data Mining
 Data Warehousing und Data Mining Multidimensionale Indexstrukturen Ulf Leser Wissensmanagement in der Bioinformatik Content of this Lecture Multidimensional Indexing Grid-Files Kd-trees Ulf Leser: Data
Data Warehousing und Data Mining Multidimensionale Indexstrukturen Ulf Leser Wissensmanagement in der Bioinformatik Content of this Lecture Multidimensional Indexing Grid-Files Kd-trees Ulf Leser: Data
Analysis of Algorithms I: Binary Search Trees
 Analysis of Algorithms I: Binary Search Trees Xi Chen Columbia University Hash table: A data structure that maintains a subset of keys from a universe set U = {0, 1,..., p 1} and supports all three dictionary
Analysis of Algorithms I: Binary Search Trees Xi Chen Columbia University Hash table: A data structure that maintains a subset of keys from a universe set U = {0, 1,..., p 1} and supports all three dictionary
Sorting revisited. Build the binary search tree: O(n^2) Traverse the binary tree: O(n) Total: O(n^2) + O(n) = O(n^2)
 Sorting revisited How did we use a binary search tree to sort an array of elements? Tree Sort Algorithm Given: An array of elements to sort 1. Build a binary search tree out of the elements 2. Traverse
Sorting revisited How did we use a binary search tree to sort an array of elements? Tree Sort Algorithm Given: An array of elements to sort 1. Build a binary search tree out of the elements 2. Traverse
Using Data-Oblivious Algorithms for Private Cloud Storage Access. Michael T. Goodrich Dept. of Computer Science
 Using Data-Oblivious Algorithms for Private Cloud Storage Access Michael T. Goodrich Dept. of Computer Science Privacy in the Cloud Alice owns a large data set, which she outsources to an honest-but-curious
Using Data-Oblivious Algorithms for Private Cloud Storage Access Michael T. Goodrich Dept. of Computer Science Privacy in the Cloud Alice owns a large data set, which she outsources to an honest-but-curious
Seminar. Path planning using Voronoi diagrams and B-Splines. Stefano Martina [email protected]
 Seminar Path planning using Voronoi diagrams and B-Splines Stefano Martina [email protected] 23 may 2016 This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International
Seminar Path planning using Voronoi diagrams and B-Splines Stefano Martina [email protected] 23 may 2016 This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International
Many algorithms, particularly divide and conquer algorithms, have time complexities which are naturally
 Recurrence Relations Many algorithms, particularly divide and conquer algorithms, have time complexities which are naturally modeled by recurrence relations. A recurrence relation is an equation which
Recurrence Relations Many algorithms, particularly divide and conquer algorithms, have time complexities which are naturally modeled by recurrence relations. A recurrence relation is an equation which
A Note on Maximum Independent Sets in Rectangle Intersection Graphs
 A Note on Maximum Independent Sets in Rectangle Intersection Graphs Timothy M. Chan School of Computer Science University of Waterloo Waterloo, Ontario N2L 3G1, Canada [email protected] September 12,
A Note on Maximum Independent Sets in Rectangle Intersection Graphs Timothy M. Chan School of Computer Science University of Waterloo Waterloo, Ontario N2L 3G1, Canada [email protected] September 12,
Solving Geometric Problems with the Rotating Calipers *
 Solving Geometric Problems with the Rotating Calipers * Godfried Toussaint School of Computer Science McGill University Montreal, Quebec, Canada ABSTRACT Shamos [1] recently showed that the diameter of
Solving Geometric Problems with the Rotating Calipers * Godfried Toussaint School of Computer Science McGill University Montreal, Quebec, Canada ABSTRACT Shamos [1] recently showed that the diameter of
The Essentials of CAGD
 The Essentials of CAGD Chapter 2: Lines and Planes Gerald Farin & Dianne Hansford CRC Press, Taylor & Francis Group, An A K Peters Book www.farinhansford.com/books/essentials-cagd c 2000 Farin & Hansford
The Essentials of CAGD Chapter 2: Lines and Planes Gerald Farin & Dianne Hansford CRC Press, Taylor & Francis Group, An A K Peters Book www.farinhansford.com/books/essentials-cagd c 2000 Farin & Hansford
Geometry Chapter 1. 1.1 Point (pt) 1.1 Coplanar (1.1) 1.1 Space (1.1) 1.2 Line Segment (seg) 1.2 Measure of a Segment
 Geometry Chapter 1 Section Term 1.1 Point (pt) Definition A location. It is drawn as a dot, and named with a capital letter. It has no shape or size. undefined term 1.1 Line A line is made up of points
Geometry Chapter 1 Section Term 1.1 Point (pt) Definition A location. It is drawn as a dot, and named with a capital letter. It has no shape or size. undefined term 1.1 Line A line is made up of points
Example SECTION 13-1. X-AXIS - the horizontal number line. Y-AXIS - the vertical number line ORIGIN - the point where the x-axis and y-axis cross
 CHAPTER 13 SECTION 13-1 Geometry and Algebra The Distance Formula COORDINATE PLANE consists of two perpendicular number lines, dividing the plane into four regions called quadrants X-AXIS - the horizontal
CHAPTER 13 SECTION 13-1 Geometry and Algebra The Distance Formula COORDINATE PLANE consists of two perpendicular number lines, dividing the plane into four regions called quadrants X-AXIS - the horizontal
Vector storage and access; algorithms in GIS. This is lecture 6
 Vector storage and access; algorithms in GIS This is lecture 6 Vector data storage and access Vectors are built from points, line and areas. (x,y) Surface: (x,y,z) Vector data access Access to vector
Vector storage and access; algorithms in GIS This is lecture 6 Vector data storage and access Vectors are built from points, line and areas. (x,y) Surface: (x,y,z) Vector data access Access to vector
Clustering. Data Mining. Abraham Otero. Data Mining. Agenda
 Clustering 1/46 Agenda Introduction Distance K-nearest neighbors Hierarchical clustering Quick reference 2/46 1 Introduction It seems logical that in a new situation we should act in a similar way as in
Clustering 1/46 Agenda Introduction Distance K-nearest neighbors Hierarchical clustering Quick reference 2/46 1 Introduction It seems logical that in a new situation we should act in a similar way as in
IMPROVING PERFORMANCE OF RANDOMIZED SIGNATURE SORT USING HASHING AND BITWISE OPERATORS
 Volume 2, No. 3, March 2011 Journal of Global Research in Computer Science RESEARCH PAPER Available Online at www.jgrcs.info IMPROVING PERFORMANCE OF RANDOMIZED SIGNATURE SORT USING HASHING AND BITWISE
Volume 2, No. 3, March 2011 Journal of Global Research in Computer Science RESEARCH PAPER Available Online at www.jgrcs.info IMPROVING PERFORMANCE OF RANDOMIZED SIGNATURE SORT USING HASHING AND BITWISE
Binary Search Trees CMPSC 122
 Binary Search Trees CMPSC 122 Note: This notes packet has significant overlap with the first set of trees notes I do in CMPSC 360, but goes into much greater depth on turning BSTs into pseudocode than
Binary Search Trees CMPSC 122 Note: This notes packet has significant overlap with the first set of trees notes I do in CMPSC 360, but goes into much greater depth on turning BSTs into pseudocode than
2004 Solutions Ga lois Contest (Grade 10)
 Canadian Mathematics Competition An activity of The Centre for Education in Ma thematics and Computing, University of W aterloo, Wa terloo, Ontario 2004 Solutions Ga lois Contest (Grade 10) 2004 Waterloo
Canadian Mathematics Competition An activity of The Centre for Education in Ma thematics and Computing, University of W aterloo, Wa terloo, Ontario 2004 Solutions Ga lois Contest (Grade 10) 2004 Waterloo
DATA MINING CLUSTER ANALYSIS: BASIC CONCEPTS
 DATA MINING CLUSTER ANALYSIS: BASIC CONCEPTS 1 AND ALGORITHMS Chiara Renso KDD-LAB ISTI- CNR, Pisa, Italy WHAT IS CLUSTER ANALYSIS? Finding groups of objects such that the objects in a group will be similar
DATA MINING CLUSTER ANALYSIS: BASIC CONCEPTS 1 AND ALGORITHMS Chiara Renso KDD-LAB ISTI- CNR, Pisa, Italy WHAT IS CLUSTER ANALYSIS? Finding groups of objects such that the objects in a group will be similar
Converting a Number from Decimal to Binary
 Converting a Number from Decimal to Binary Convert nonnegative integer in decimal format (base 10) into equivalent binary number (base 2) Rightmost bit of x Remainder of x after division by two Recursive
Converting a Number from Decimal to Binary Convert nonnegative integer in decimal format (base 10) into equivalent binary number (base 2) Rightmost bit of x Remainder of x after division by two Recursive
THREE DIMENSIONAL GEOMETRY
 Chapter 8 THREE DIMENSIONAL GEOMETRY 8.1 Introduction In this chapter we present a vector algebra approach to three dimensional geometry. The aim is to present standard properties of lines and planes,
Chapter 8 THREE DIMENSIONAL GEOMETRY 8.1 Introduction In this chapter we present a vector algebra approach to three dimensional geometry. The aim is to present standard properties of lines and planes,
Baltic Way 1995. Västerås (Sweden), November 12, 1995. Problems and solutions
 Baltic Way 995 Västerås (Sweden), November, 995 Problems and solutions. Find all triples (x, y, z) of positive integers satisfying the system of equations { x = (y + z) x 6 = y 6 + z 6 + 3(y + z ). Solution.
Baltic Way 995 Västerås (Sweden), November, 995 Problems and solutions. Find all triples (x, y, z) of positive integers satisfying the system of equations { x = (y + z) x 6 = y 6 + z 6 + 3(y + z ). Solution.
Triangulation by Ear Clipping
 Triangulation by Ear Clipping David Eberly Geometric Tools, LLC http://www.geometrictools.com/ Copyright c 1998-2016. All Rights Reserved. Created: November 18, 2002 Last Modified: August 16, 2015 Contents
Triangulation by Ear Clipping David Eberly Geometric Tools, LLC http://www.geometrictools.com/ Copyright c 1998-2016. All Rights Reserved. Created: November 18, 2002 Last Modified: August 16, 2015 Contents
CSC148 Lecture 8. Algorithm Analysis Binary Search Sorting
 CSC148 Lecture 8 Algorithm Analysis Binary Search Sorting Algorithm Analysis Recall definition of Big Oh: We say a function f(n) is O(g(n)) if there exists positive constants c,b such that f(n)
CSC148 Lecture 8 Algorithm Analysis Binary Search Sorting Algorithm Analysis Recall definition of Big Oh: We say a function f(n) is O(g(n)) if there exists positive constants c,b such that f(n)
http://www.castlelearning.com/review/teacher/assignmentprinting.aspx 5. 2 6. 2 1. 10 3. 70 2. 55 4. 180 7. 2 8. 4
 of 9 1/28/2013 8:32 PM Teacher: Mr. Sime Name: 2 What is the slope of the graph of the equation y = 2x? 5. 2 If the ratio of the measures of corresponding sides of two similar triangles is 4:9, then the
of 9 1/28/2013 8:32 PM Teacher: Mr. Sime Name: 2 What is the slope of the graph of the equation y = 2x? 5. 2 If the ratio of the measures of corresponding sides of two similar triangles is 4:9, then the
Parallel and Perpendicular. We show a small box in one of the angles to show that the lines are perpendicular.
 CONDENSED L E S S O N. Parallel and Perpendicular In this lesson you will learn the meaning of parallel and perpendicular discover how the slopes of parallel and perpendicular lines are related use slopes
CONDENSED L E S S O N. Parallel and Perpendicular In this lesson you will learn the meaning of parallel and perpendicular discover how the slopes of parallel and perpendicular lines are related use slopes
Data Structures and Algorithms Written Examination
 Data Structures and Algorithms Written Examination 22 February 2013 FIRST NAME STUDENT NUMBER LAST NAME SIGNATURE Instructions for students: Write First Name, Last Name, Student Number and Signature where
Data Structures and Algorithms Written Examination 22 February 2013 FIRST NAME STUDENT NUMBER LAST NAME SIGNATURE Instructions for students: Write First Name, Last Name, Student Number and Signature where
Fast Sequential Summation Algorithms Using Augmented Data Structures
 Fast Sequential Summation Algorithms Using Augmented Data Structures Vadim Stadnik [email protected] Abstract This paper provides an introduction to the design of augmented data structures that offer
Fast Sequential Summation Algorithms Using Augmented Data Structures Vadim Stadnik [email protected] Abstract This paper provides an introduction to the design of augmented data structures that offer
CIRCLE COORDINATE GEOMETRY
 CIRCLE COORDINATE GEOMETRY (EXAM QUESTIONS) Question 1 (**) A circle has equation x + y = 2x + 8 Determine the radius and the coordinates of the centre of the circle. r = 3, ( 1,0 ) Question 2 (**) A circle
CIRCLE COORDINATE GEOMETRY (EXAM QUESTIONS) Question 1 (**) A circle has equation x + y = 2x + 8 Determine the radius and the coordinates of the centre of the circle. r = 3, ( 1,0 ) Question 2 (**) A circle
Arrangements And Duality
 Arrangements And Duality 3.1 Introduction 3 Point configurations are tbe most basic structure we study in computational geometry. But what about configurations of more complicated shapes? For example,
Arrangements And Duality 3.1 Introduction 3 Point configurations are tbe most basic structure we study in computational geometry. But what about configurations of more complicated shapes? For example,
Lecture 4 Online and streaming algorithms for clustering
 CSE 291: Geometric algorithms Spring 2013 Lecture 4 Online and streaming algorithms for clustering 4.1 On-line k-clustering To the extent that clustering takes place in the brain, it happens in an on-line
CSE 291: Geometric algorithms Spring 2013 Lecture 4 Online and streaming algorithms for clustering 4.1 On-line k-clustering To the extent that clustering takes place in the brain, it happens in an on-line
Solutions to old Exam 1 problems
 Solutions to old Exam 1 problems Hi students! I am putting this old version of my review for the first midterm review, place and time to be announced. Check for updates on the web site as to which sections
Solutions to old Exam 1 problems Hi students! I am putting this old version of my review for the first midterm review, place and time to be announced. Check for updates on the web site as to which sections
Circle Name: Radius: Diameter: Chord: Secant:
 12.1: Tangent Lines Congruent Circles: circles that have the same radius length Diagram of Examples Center of Circle: Circle Name: Radius: Diameter: Chord: Secant: Tangent to A Circle: a line in the plane
12.1: Tangent Lines Congruent Circles: circles that have the same radius length Diagram of Examples Center of Circle: Circle Name: Radius: Diameter: Chord: Secant: Tangent to A Circle: a line in the plane
Applied Algorithm Design Lecture 5
 Applied Algorithm Design Lecture 5 Pietro Michiardi Eurecom Pietro Michiardi (Eurecom) Applied Algorithm Design Lecture 5 1 / 86 Approximation Algorithms Pietro Michiardi (Eurecom) Applied Algorithm Design
Applied Algorithm Design Lecture 5 Pietro Michiardi Eurecom Pietro Michiardi (Eurecom) Applied Algorithm Design Lecture 5 1 / 86 Approximation Algorithms Pietro Michiardi (Eurecom) Applied Algorithm Design
Questions 1 through 25 are worth 2 points each. Choose one best answer for each.
 Questions 1 through 25 are worth 2 points each. Choose one best answer for each. 1. For the singly linked list implementation of the queue, where are the enqueues and dequeues performed? c a. Enqueue in
Questions 1 through 25 are worth 2 points each. Choose one best answer for each. 1. For the singly linked list implementation of the queue, where are the enqueues and dequeues performed? c a. Enqueue in
A binary search tree is a binary tree with a special property called the BST-property, which is given as follows:
 Chapter 12: Binary Search Trees A binary search tree is a binary tree with a special property called the BST-property, which is given as follows: For all nodes x and y, if y belongs to the left subtree
Chapter 12: Binary Search Trees A binary search tree is a binary tree with a special property called the BST-property, which is given as follows: For all nodes x and y, if y belongs to the left subtree
Number Sense and Operations
 Number Sense and Operations representing as they: 6.N.1 6.N.2 6.N.3 6.N.4 6.N.5 6.N.6 6.N.7 6.N.8 6.N.9 6.N.10 6.N.11 6.N.12 6.N.13. 6.N.14 6.N.15 Demonstrate an understanding of positive integer exponents
Number Sense and Operations representing as they: 6.N.1 6.N.2 6.N.3 6.N.4 6.N.5 6.N.6 6.N.7 6.N.8 6.N.9 6.N.10 6.N.11 6.N.12 6.N.13. 6.N.14 6.N.15 Demonstrate an understanding of positive integer exponents
AP Computer Science AB Syllabus 1
 AP Computer Science AB Syllabus 1 Course Resources Java Software Solutions for AP Computer Science, J. Lewis, W. Loftus, and C. Cocking, First Edition, 2004, Prentice Hall. Video: Sorting Out Sorting,
AP Computer Science AB Syllabus 1 Course Resources Java Software Solutions for AP Computer Science, J. Lewis, W. Loftus, and C. Cocking, First Edition, 2004, Prentice Hall. Video: Sorting Out Sorting,
The GeoMedia Fusion Validate Geometry command provides the GUI for detecting geometric anomalies on a single feature.
 The GeoMedia Fusion Validate Geometry command provides the GUI for detecting geometric anomalies on a single feature. Below is a discussion of the Standard Advanced Validate Geometry types. Empty Geometry
The GeoMedia Fusion Validate Geometry command provides the GUI for detecting geometric anomalies on a single feature. Below is a discussion of the Standard Advanced Validate Geometry types. Empty Geometry
Chapter 11. 11.1 Load Balancing. Approximation Algorithms. Load Balancing. Load Balancing on 2 Machines. Load Balancing: Greedy Scheduling
 Approximation Algorithms Chapter Approximation Algorithms Q. Suppose I need to solve an NP-hard problem. What should I do? A. Theory says you're unlikely to find a poly-time algorithm. Must sacrifice one
Approximation Algorithms Chapter Approximation Algorithms Q. Suppose I need to solve an NP-hard problem. What should I do? A. Theory says you're unlikely to find a poly-time algorithm. Must sacrifice one
Analysis of Algorithms I: Optimal Binary Search Trees
 Analysis of Algorithms I: Optimal Binary Search Trees Xi Chen Columbia University Given a set of n keys K = {k 1,..., k n } in sorted order: k 1 < k 2 < < k n we wish to build an optimal binary search
Analysis of Algorithms I: Optimal Binary Search Trees Xi Chen Columbia University Given a set of n keys K = {k 1,..., k n } in sorted order: k 1 < k 2 < < k n we wish to build an optimal binary search
1) The postfix expression for the infix expression A+B*(C+D)/F+D*E is ABCD+*F/DE*++
 Answer the following 1) The postfix expression for the infix expression A+B*(C+D)/F+D*E is ABCD+*F/DE*++ 2) Which data structure is needed to convert infix notations to postfix notations? Stack 3) The
Answer the following 1) The postfix expression for the infix expression A+B*(C+D)/F+D*E is ABCD+*F/DE*++ 2) Which data structure is needed to convert infix notations to postfix notations? Stack 3) The
Symbol Tables. Introduction
 Symbol Tables Introduction A compiler needs to collect and use information about the names appearing in the source program. This information is entered into a data structure called a symbol table. The
Symbol Tables Introduction A compiler needs to collect and use information about the names appearing in the source program. This information is entered into a data structure called a symbol table. The
Previous Lectures. B-Trees. External storage. Two types of memory. B-trees. Main principles
 B-Trees Algorithms and data structures for external memory as opposed to the main memory B-Trees Previous Lectures Height balanced binary search trees: AVL trees, red-black trees. Multiway search trees:
B-Trees Algorithms and data structures for external memory as opposed to the main memory B-Trees Previous Lectures Height balanced binary search trees: AVL trees, red-black trees. Multiway search trees:
CSE 326, Data Structures. Sample Final Exam. Problem Max Points Score 1 14 (2x7) 2 18 (3x6) 3 4 4 7 5 9 6 16 7 8 8 4 9 8 10 4 Total 92.
 Name: Email ID: CSE 326, Data Structures Section: Sample Final Exam Instructions: The exam is closed book, closed notes. Unless otherwise stated, N denotes the number of elements in the data structure
Name: Email ID: CSE 326, Data Structures Section: Sample Final Exam Instructions: The exam is closed book, closed notes. Unless otherwise stated, N denotes the number of elements in the data structure
Selected practice exam solutions (part 5, item 2) (MAT 360)
 Selected practice exam solutions (part 5, item ) (MAT 360) Harder 8,91,9,94(smaller should be replaced by greater )95,103,109,140,160,(178,179,180,181 this is really one problem),188,193,194,195 8. On
Selected practice exam solutions (part 5, item ) (MAT 360) Harder 8,91,9,94(smaller should be replaced by greater )95,103,109,140,160,(178,179,180,181 this is really one problem),188,193,194,195 8. On
Partitioning and Divide and Conquer Strategies
 and Divide and Conquer Strategies Lecture 4 and Strategies Strategies Data partitioning aka domain decomposition Functional decomposition Lecture 4 and Strategies Quiz 4.1 For nuclear reactor simulation,
and Divide and Conquer Strategies Lecture 4 and Strategies Strategies Data partitioning aka domain decomposition Functional decomposition Lecture 4 and Strategies Quiz 4.1 For nuclear reactor simulation,
ARTIFICIAL INTELLIGENCE (CSCU9YE) LECTURE 6: MACHINE LEARNING 2: UNSUPERVISED LEARNING (CLUSTERING)
 ARTIFICIAL INTELLIGENCE (CSCU9YE) LECTURE 6: MACHINE LEARNING 2: UNSUPERVISED LEARNING (CLUSTERING) Gabriela Ochoa http://www.cs.stir.ac.uk/~goc/ OUTLINE Preliminaries Classification and Clustering Applications
ARTIFICIAL INTELLIGENCE (CSCU9YE) LECTURE 6: MACHINE LEARNING 2: UNSUPERVISED LEARNING (CLUSTERING) Gabriela Ochoa http://www.cs.stir.ac.uk/~goc/ OUTLINE Preliminaries Classification and Clustering Applications
CSC2420 Spring 2015: Lecture 3
 CSC2420 Spring 2015: Lecture 3 Allan Borodin January 22, 2015 1 / 1 Announcements and todays agenda Assignment 1 due next Thursday. I may add one or two additional questions today or tomorrow. Todays agenda
CSC2420 Spring 2015: Lecture 3 Allan Borodin January 22, 2015 1 / 1 Announcements and todays agenda Assignment 1 due next Thursday. I may add one or two additional questions today or tomorrow. Todays agenda
Solutions to Homework 6
 Solutions to Homework 6 Debasish Das EECS Department, Northwestern University [email protected] 1 Problem 5.24 We want to find light spanning trees with certain special properties. Given is one example
Solutions to Homework 6 Debasish Das EECS Department, Northwestern University [email protected] 1 Problem 5.24 We want to find light spanning trees with certain special properties. Given is one example
! Solve problem to optimality. ! Solve problem in poly-time. ! Solve arbitrary instances of the problem. !-approximation algorithm.
 Approximation Algorithms Chapter Approximation Algorithms Q Suppose I need to solve an NP-hard problem What should I do? A Theory says you're unlikely to find a poly-time algorithm Must sacrifice one of
Approximation Algorithms Chapter Approximation Algorithms Q Suppose I need to solve an NP-hard problem What should I do? A Theory says you're unlikely to find a poly-time algorithm Must sacrifice one of
Discrete Optimization
 Discrete Optimization [Chen, Batson, Dang: Applied integer Programming] Chapter 3 and 4.1-4.3 by Johan Högdahl and Victoria Svedberg Seminar 2, 2015-03-31 Todays presentation Chapter 3 Transforms using
Discrete Optimization [Chen, Batson, Dang: Applied integer Programming] Chapter 3 and 4.1-4.3 by Johan Högdahl and Victoria Svedberg Seminar 2, 2015-03-31 Todays presentation Chapter 3 Transforms using
Lecture 6 Online and streaming algorithms for clustering
 CSE 291: Unsupervised learning Spring 2008 Lecture 6 Online and streaming algorithms for clustering 6.1 On-line k-clustering To the extent that clustering takes place in the brain, it happens in an on-line
CSE 291: Unsupervised learning Spring 2008 Lecture 6 Online and streaming algorithms for clustering 6.1 On-line k-clustering To the extent that clustering takes place in the brain, it happens in an on-line
Chapter 3. Inversion and Applications to Ptolemy and Euler
 Chapter 3. Inversion and Applications to Ptolemy and Euler 2 Power of a point with respect to a circle Let A be a point and C a circle (Figure 1). If A is outside C and T is a point of contact of a tangent
Chapter 3. Inversion and Applications to Ptolemy and Euler 2 Power of a point with respect to a circle Let A be a point and C a circle (Figure 1). If A is outside C and T is a point of contact of a tangent
Binary Heap Algorithms
 CS Data Structures and Algorithms Lecture Slides Wednesday, April 5, 2009 Glenn G. Chappell Department of Computer Science University of Alaska Fairbanks [email protected] 2005 2009 Glenn G. Chappell
CS Data Structures and Algorithms Lecture Slides Wednesday, April 5, 2009 Glenn G. Chappell Department of Computer Science University of Alaska Fairbanks [email protected] 2005 2009 Glenn G. Chappell
INCIDENCE-BETWEENNESS GEOMETRY
 INCIDENCE-BETWEENNESS GEOMETRY MATH 410, CSUSM. SPRING 2008. PROFESSOR AITKEN This document covers the geometry that can be developed with just the axioms related to incidence and betweenness. The full
INCIDENCE-BETWEENNESS GEOMETRY MATH 410, CSUSM. SPRING 2008. PROFESSOR AITKEN This document covers the geometry that can be developed with just the axioms related to incidence and betweenness. The full
4. How many integers between 2004 and 4002 are perfect squares?
 5 is 0% of what number? What is the value of + 3 4 + 99 00? (alternating signs) 3 A frog is at the bottom of a well 0 feet deep It climbs up 3 feet every day, but slides back feet each night If it started
5 is 0% of what number? What is the value of + 3 4 + 99 00? (alternating signs) 3 A frog is at the bottom of a well 0 feet deep It climbs up 3 feet every day, but slides back feet each night If it started
Approximation of an Open Polygonal Curve with a Minimum Number of Circular Arcs and Biarcs
 Approximation of an Open Polygonal Curve with a Minimum Number of Circular Arcs and Biarcs R. L. Scot Drysdale a Günter Rote b,1 Astrid Sturm b,1 a Department of Computer Science, Dartmouth College b Institut
Approximation of an Open Polygonal Curve with a Minimum Number of Circular Arcs and Biarcs R. L. Scot Drysdale a Günter Rote b,1 Astrid Sturm b,1 a Department of Computer Science, Dartmouth College b Institut
Data Mining Cluster Analysis: Basic Concepts and Algorithms. Clustering Algorithms. Lecture Notes for Chapter 8. Introduction to Data Mining
 Data Mining Cluster Analsis: Basic Concepts and Algorithms Lecture Notes for Chapter 8 Introduction to Data Mining b Tan, Steinbach, Kumar Clustering Algorithms K-means and its variants Hierarchical clustering
Data Mining Cluster Analsis: Basic Concepts and Algorithms Lecture Notes for Chapter 8 Introduction to Data Mining b Tan, Steinbach, Kumar Clustering Algorithms K-means and its variants Hierarchical clustering
Actually Doing It! 6. Prove that the regular unit cube (say 1cm=unit) of sufficiently high dimension can fit inside it the whole city of New York.
 1: 1. Compute a random 4-dimensional polytope P as the convex hull of 10 random points using rand sphere(4,10). Run VISUAL to see a Schlegel diagram. How many 3-dimensional polytopes do you see? How many
1: 1. Compute a random 4-dimensional polytope P as the convex hull of 10 random points using rand sphere(4,10). Run VISUAL to see a Schlegel diagram. How many 3-dimensional polytopes do you see? How many
Algorithms. Algorithms GEOMETRIC APPLICATIONS OF BSTS. 1d range search line segment intersection kd trees interval search trees rectangle intersection
 Algorithms ROBERT SEDGEWICK KEVIN WAYNE GEOMETRIC APPLICATIONS OF BSTS Algorithms F O U R T H E D I T I O N ROBERT SEDGEWICK KEVIN WAYNE 1d range search line segment intersection kd trees interval search
Algorithms ROBERT SEDGEWICK KEVIN WAYNE GEOMETRIC APPLICATIONS OF BSTS Algorithms F O U R T H E D I T I O N ROBERT SEDGEWICK KEVIN WAYNE 1d range search line segment intersection kd trees interval search
KDDCS: A Load-Balanced In-Network Data-Centric Storage Scheme for Sensor Networks
 KDDCS: A Load-Balanced In-Network Data-Centric Storage Scheme for Sensor Networks Mohamed Aly Kirk Pruhs Panos K. Chrysanthis Department of Computer Science University of Pittsburgh Pittsburgh, PA 1526,
KDDCS: A Load-Balanced In-Network Data-Centric Storage Scheme for Sensor Networks Mohamed Aly Kirk Pruhs Panos K. Chrysanthis Department of Computer Science University of Pittsburgh Pittsburgh, PA 1526,
! Solve problem to optimality. ! Solve problem in poly-time. ! Solve arbitrary instances of the problem. #-approximation algorithm.
 Approximation Algorithms 11 Approximation Algorithms Q Suppose I need to solve an NP-hard problem What should I do? A Theory says you're unlikely to find a poly-time algorithm Must sacrifice one of three
Approximation Algorithms 11 Approximation Algorithms Q Suppose I need to solve an NP-hard problem What should I do? A Theory says you're unlikely to find a poly-time algorithm Must sacrifice one of three
Investigating Area Under a Curve
 Mathematics Investigating Area Under a Curve About this Lesson This lesson is an introduction to areas bounded by functions and the x-axis on a given interval. Since the functions in the beginning of the
Mathematics Investigating Area Under a Curve About this Lesson This lesson is an introduction to areas bounded by functions and the x-axis on a given interval. Since the functions in the beginning of the
Strictly Localized Construction of Planar Bounded-Degree Spanners of Unit Disk Graphs
 Strictly Localized Construction of Planar Bounded-Degree Spanners of Unit Disk Graphs Iyad A. Kanj Ljubomir Perković Ge Xia Abstract We describe a new distributed and strictly-localized approach for constructing
Strictly Localized Construction of Planar Bounded-Degree Spanners of Unit Disk Graphs Iyad A. Kanj Ljubomir Perković Ge Xia Abstract We describe a new distributed and strictly-localized approach for constructing
Efficient Data Structures for Decision Diagrams
 Artificial Intelligence Laboratory Efficient Data Structures for Decision Diagrams Master Thesis Nacereddine Ouaret Professor: Supervisors: Boi Faltings Thomas Léauté Radoslaw Szymanek Contents Introduction...
Artificial Intelligence Laboratory Efficient Data Structures for Decision Diagrams Master Thesis Nacereddine Ouaret Professor: Supervisors: Boi Faltings Thomas Léauté Radoslaw Szymanek Contents Introduction...
Data Mining Cluster Analysis: Advanced Concepts and Algorithms. Lecture Notes for Chapter 9. Introduction to Data Mining
 Data Mining Cluster Analysis: Advanced Concepts and Algorithms Lecture Notes for Chapter 9 Introduction to Data Mining by Tan, Steinbach, Kumar Tan,Steinbach, Kumar Introduction to Data Mining 4/18/2004
Data Mining Cluster Analysis: Advanced Concepts and Algorithms Lecture Notes for Chapter 9 Introduction to Data Mining by Tan, Steinbach, Kumar Tan,Steinbach, Kumar Introduction to Data Mining 4/18/2004
MATHEMATICAL ENGINEERING TECHNICAL REPORTS. The Best-fit Heuristic for the Rectangular Strip Packing Problem: An Efficient Implementation
 MATHEMATICAL ENGINEERING TECHNICAL REPORTS The Best-fit Heuristic for the Rectangular Strip Packing Problem: An Efficient Implementation Shinji IMAHORI, Mutsunori YAGIURA METR 2007 53 September 2007 DEPARTMENT
MATHEMATICAL ENGINEERING TECHNICAL REPORTS The Best-fit Heuristic for the Rectangular Strip Packing Problem: An Efficient Implementation Shinji IMAHORI, Mutsunori YAGIURA METR 2007 53 September 2007 DEPARTMENT
Carnegie Mellon University. Extract from Andrew Moore's PhD Thesis: Ecient Memory-based Learning for Robot Control
 An intoductory tutorial on kd-trees Andrew W. Moore Carnegie Mellon University [email protected] Extract from Andrew Moore's PhD Thesis: Ecient Memory-based Learning for Robot Control PhD. Thesis Technical
An intoductory tutorial on kd-trees Andrew W. Moore Carnegie Mellon University [email protected] Extract from Andrew Moore's PhD Thesis: Ecient Memory-based Learning for Robot Control PhD. Thesis Technical
Section 8.8. 1. The given line has equations. x = 3 + t(13 3) = 3 + 10t, y = 2 + t(3 + 2) = 2 + 5t, z = 7 + t( 8 7) = 7 15t.
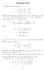 . The given line has equations Section 8.8 x + t( ) + 0t, y + t( + ) + t, z 7 + t( 8 7) 7 t. The line meets the plane y 0 in the point (x, 0, z), where 0 + t, or t /. The corresponding values for x and
. The given line has equations Section 8.8 x + t( ) + 0t, y + t( + ) + t, z 7 + t( 8 7) 7 t. The line meets the plane y 0 in the point (x, 0, z), where 0 + t, or t /. The corresponding values for x and
You must have: Ruler graduated in centimetres and millimetres, protractor, compasses, pen, HB pencil, eraser, calculator. Tracing paper may be used.
 Write your name here Surname Other names Edexcel IGCSE Mathematics B Paper 1 Centre Number Candidate Number Monday 6 June 2011 Afternoon Time: 1 hour 30 minutes Paper Reference 4MB0/01 You must have: Ruler
Write your name here Surname Other names Edexcel IGCSE Mathematics B Paper 1 Centre Number Candidate Number Monday 6 June 2011 Afternoon Time: 1 hour 30 minutes Paper Reference 4MB0/01 You must have: Ruler
Curriculum Map by Block Geometry Mapping for Math Block Testing 2007-2008. August 20 to August 24 Review concepts from previous grades.
 Curriculum Map by Geometry Mapping for Math Testing 2007-2008 Pre- s 1 August 20 to August 24 Review concepts from previous grades. August 27 to September 28 (Assessment to be completed by September 28)
Curriculum Map by Geometry Mapping for Math Testing 2007-2008 Pre- s 1 August 20 to August 24 Review concepts from previous grades. August 27 to September 28 (Assessment to be completed by September 28)
DEFINITIONS. Perpendicular Two lines are called perpendicular if they form a right angle.
 DEFINITIONS Degree A degree is the 1 th part of a straight angle. 180 Right Angle A 90 angle is called a right angle. Perpendicular Two lines are called perpendicular if they form a right angle. Congruent
DEFINITIONS Degree A degree is the 1 th part of a straight angle. 180 Right Angle A 90 angle is called a right angle. Perpendicular Two lines are called perpendicular if they form a right angle. Congruent
WORK SCHEDULE: MATHEMATICS 2007
 , K WORK SCHEDULE: MATHEMATICS 00 GRADE MODULE TERM... LO NUMBERS, OPERATIONS AND RELATIONSHIPS able to recognise, represent numbers and their relationships, and to count, estimate, calculate and check
, K WORK SCHEDULE: MATHEMATICS 00 GRADE MODULE TERM... LO NUMBERS, OPERATIONS AND RELATIONSHIPS able to recognise, represent numbers and their relationships, and to count, estimate, calculate and check
Home Page. Data Structures. Title Page. Page 1 of 24. Go Back. Full Screen. Close. Quit
 Data Structures Page 1 of 24 A.1. Arrays (Vectors) n-element vector start address + ielementsize 0 +1 +2 +3 +4... +n-1 start address continuous memory block static, if size is known at compile time dynamic,
Data Structures Page 1 of 24 A.1. Arrays (Vectors) n-element vector start address + ielementsize 0 +1 +2 +3 +4... +n-1 start address continuous memory block static, if size is known at compile time dynamic,
BALTIC OLYMPIAD IN INFORMATICS Stockholm, April 18-22, 2009 Page 1 of?? ENG rectangle. Rectangle
 Page 1 of?? ENG rectangle Rectangle Spoiler Solution of SQUARE For start, let s solve a similar looking easier task: find the area of the largest square. All we have to do is pick two points A and B and
Page 1 of?? ENG rectangle Rectangle Spoiler Solution of SQUARE For start, let s solve a similar looking easier task: find the area of the largest square. All we have to do is pick two points A and B and
G.H. Raisoni College of Engineering, Nagpur. Department of Information Technology
 Practical List 1) WAP to implement line generation using DDA algorithm 2) WAP to implement line using Bresenham s line generation algorithm. 3) WAP to generate circle using circle generation algorithm
Practical List 1) WAP to implement line generation using DDA algorithm 2) WAP to implement line using Bresenham s line generation algorithm. 3) WAP to generate circle using circle generation algorithm
A binary search tree or BST is a binary tree that is either empty or in which the data element of each node has a key, and:
 Binary Search Trees 1 The general binary tree shown in the previous chapter is not terribly useful in practice. The chief use of binary trees is for providing rapid access to data (indexing, if you will)
Binary Search Trees 1 The general binary tree shown in the previous chapter is not terribly useful in practice. The chief use of binary trees is for providing rapid access to data (indexing, if you will)
A fast and robust algorithm to count topologically persistent holes in noisy clouds
 A fast and robust algorithm to count topologically persistent holes in noisy clouds Vitaliy Kurlin Durham University Department of Mathematical Sciences, Durham, DH1 3LE, United Kingdom [email protected],
A fast and robust algorithm to count topologically persistent holes in noisy clouds Vitaliy Kurlin Durham University Department of Mathematical Sciences, Durham, DH1 3LE, United Kingdom [email protected],
Grade 7 & 8 Math Circles Circles, Circles, Circles March 19/20, 2013
 Faculty of Mathematics Waterloo, Ontario N2L 3G Introduction Grade 7 & 8 Math Circles Circles, Circles, Circles March 9/20, 203 The circle is a very important shape. In fact of all shapes, the circle is
Faculty of Mathematics Waterloo, Ontario N2L 3G Introduction Grade 7 & 8 Math Circles Circles, Circles, Circles March 9/20, 203 The circle is a very important shape. In fact of all shapes, the circle is
Approximation Algorithms
 Approximation Algorithms or: How I Learned to Stop Worrying and Deal with NP-Completeness Ong Jit Sheng, Jonathan (A0073924B) March, 2012 Overview Key Results (I) General techniques: Greedy algorithms
Approximation Algorithms or: How I Learned to Stop Worrying and Deal with NP-Completeness Ong Jit Sheng, Jonathan (A0073924B) March, 2012 Overview Key Results (I) General techniques: Greedy algorithms
Binary Search Trees. A Generic Tree. Binary Trees. Nodes in a binary search tree ( B-S-T) are of the form. P parent. Key. Satellite data L R
 Binary Search Trees A Generic Tree Nodes in a binary search tree ( B-S-T) are of the form P parent Key A Satellite data L R B C D E F G H I J The B-S-T has a root node which is the only node whose parent
Binary Search Trees A Generic Tree Nodes in a binary search tree ( B-S-T) are of the form P parent Key A Satellite data L R B C D E F G H I J The B-S-T has a root node which is the only node whose parent
HW4: Merge Sort. 1 Assignment Goal. 2 Description of the Merging Problem. Course: ENEE759K/CMSC751 Title:
 HW4: Merge Sort Course: ENEE759K/CMSC751 Title: Merge Sort Date Assigned: March 24th, 2009 Date Due: April 10th, 2009 11:59pm Contact: Fuat Keceli keceli (at) umd (dot) edu 1 Assignment Goal The final
HW4: Merge Sort Course: ENEE759K/CMSC751 Title: Merge Sort Date Assigned: March 24th, 2009 Date Due: April 10th, 2009 11:59pm Contact: Fuat Keceli keceli (at) umd (dot) edu 1 Assignment Goal The final
System Interconnect Architectures. Goals and Analysis. Network Properties and Routing. Terminology - 2. Terminology - 1
 System Interconnect Architectures CSCI 8150 Advanced Computer Architecture Hwang, Chapter 2 Program and Network Properties 2.4 System Interconnect Architectures Direct networks for static connections Indirect
System Interconnect Architectures CSCI 8150 Advanced Computer Architecture Hwang, Chapter 2 Program and Network Properties 2.4 System Interconnect Architectures Direct networks for static connections Indirect
NEW MEXICO Grade 6 MATHEMATICS STANDARDS
 PROCESS STANDARDS To help New Mexico students achieve the Content Standards enumerated below, teachers are encouraged to base instruction on the following Process Standards: Problem Solving Build new mathematical
PROCESS STANDARDS To help New Mexico students achieve the Content Standards enumerated below, teachers are encouraged to base instruction on the following Process Standards: Problem Solving Build new mathematical
Shortest Inspection-Path. Queries in Simple Polygons
 Shortest Inspection-Path Queries in Simple Polygons Christian Knauer, Günter Rote B 05-05 April 2005 Shortest Inspection-Path Queries in Simple Polygons Christian Knauer, Günter Rote Institut für Informatik,
Shortest Inspection-Path Queries in Simple Polygons Christian Knauer, Günter Rote B 05-05 April 2005 Shortest Inspection-Path Queries in Simple Polygons Christian Knauer, Günter Rote Institut für Informatik,
Exam study sheet for CS2711. List of topics
 Exam study sheet for CS2711 Here is the list of topics you need to know for the final exam. For each data structure listed below, make sure you can do the following: 1. Give an example of this data structure
Exam study sheet for CS2711 Here is the list of topics you need to know for the final exam. For each data structure listed below, make sure you can do the following: 1. Give an example of this data structure
Outline BST Operations Worst case Average case Balancing AVL Red-black B-trees. Binary Search Trees. Lecturer: Georgy Gimel farb
 Binary Search Trees Lecturer: Georgy Gimel farb COMPSCI 220 Algorithms and Data Structures 1 / 27 1 Properties of Binary Search Trees 2 Basic BST operations The worst-case time complexity of BST operations
Binary Search Trees Lecturer: Georgy Gimel farb COMPSCI 220 Algorithms and Data Structures 1 / 27 1 Properties of Binary Search Trees 2 Basic BST operations The worst-case time complexity of BST operations
