Implementing Secure Solutions for PHI. Ann Geyer Tunitas Group
|
|
|
- Peter Harris
- 10 years ago
- Views:
Transcription
1 Implementing Secure Solutions for PHI Ann Geyer Tunitas Group
2 First Observation Secure infrastructure software deployed to healthcare Early California adopters ( ): SJHS, CHW, Scripps, Sutter, PacifiCare Vendors targeting healthcare market: Tumbleweed, Sigaba, Clearswift, TFS, Omtool, Zix, CertifiedMail Few HCO have broadly utilized their encryption options Encrypted Is still the exception, even for the early adopters Where encryption occurs, it is typically the result user activity
3 What s Holding Secure Back? Administering secure is challenging! Neither of the existing mgmt models works well Secure web application Doesn t make sense to administer external recipients as if they were users of your system Ordinary SMTP mail Secure requires new skill sets for both administrators and users Encryption methods and keys must be negotiated with recipients User can be trusted to get address right But only 1 0f 10 persons found to properly install and use their encryption software ( Why Johnny can t encrypt ~ )
4 Secure Administration Policy Aspects containing PHI sent to an external recipient is a DISCLOSURE subject to HIPAA privacy & security requirements Duty of the enterprise to ensure that the disclosure is properly authorized and documented Disclosures and the method need to be governed by enterprise policy and procedure Also need some ability to monitor and enforce policy Secure management must be sensitive to policy
5 Secure Policy 3 Items relevant to policy Sender identity and role Recipient category, domain, and role Message contents, including the nature of PHI included Policy objectives Should message be sent? Is the disclosure appropriate? Is the recipient s encryption key available? Subsequent actions if message is not sent Verify authorization and purpose User training on privacy or data use policies Key acquisition Report suspected privacy/security incident Subsequent actions, if message is sent Copy to HIM dept or Acctng of Disclosure Log
6 Secure Policy Developing policy is itself challenging is a business tool Secure policy constrains its use Many internal stakeholders Compliance -- respond to privacy and disclosure regs Users -- expectations of personal privacy and convenience IT -- implement and maintain, cost Multi-disciplinary effort Comparable to creating enterprise HIPAA privacy policy, but with a strong technology component Not an administrator or security personnel assignment Requires executive approval and support
7 Secure Administration Workflow Aspects system acquires knowledge of recipients in ad hoc manner Two basic problems User needs to identify & potentially authenticate recipient System needs to acquire or exchange encryption material Argues for a new workflow Procedure to authorize the sending of secure to a particular recipient Procedure to negotiate encryption keys that minimizes sender involvement Procedure to document results Methods to minimize latency Works both ways Consider how your organization will support receiving encrypted
8 Secure Administration Peer Aspect Typical HCO has 40K plus recipients in its directory Even small orgs have too many recipients to manage secure on a case by case basis Recognize and take advantage of solutions that peers have adopted Determine how trust and interoperability issues between mail domains get resolved Recognize physicians and other independent practitioners as having their own solution requirements
9 Peers Translates into a PKI problem S/MIME (PKI) has the greatest promise for secure on an industry scale Solutions are certified and interoperable PKI Bad Rep Poor integration tools User support costs Certificate sources PKI Support from Professional Associations CMA/MEDePass -- California physicians and staff AMA/Verisign Members of AMA physician database AAMT -- US medical transcriptionists Prof assn interested in supporting secure solutions for their members
10 Conclusions Recognize that secure mail solutions require more than technology Acquire enterprise support through multistakeholder policy formation effort Avoid myopia by recognizing that external recipients are your peers in securing messages Capitalize on community solutions such as the multiple association support for PKI and S/MIME Assist security administrators to develop the workflow to support negotiation of encryption parameters Remember that encryption is only part of security Take training requirements serious, surprisingly few administrators have background in security or PKI
11 California Community Trial Motivation Recognize the limitations of SSL for peer communication Strongly motivated to protect the use of as a business tool Develop set of best practices for implementation and policy decisions Validate push certificate distribution model and improved s/mime workflow Support association certificate activities Persuade peers to add s/mime to their solution options
12 California Community Trial Activities -- Implementation Profile use CE, BA, Third Party Department to department (what type of PHI) With infrastructure requiring negotiation (B2B) Without infrastructure requiring direction (B2b) Encryption Options s/mime gateway esmtp StartTLS Push certificates for client/desktop users Association certificates for professional class users Strategies for TP with proprietary approaches Webportals, webmail, required clients
13 California Community Trial Activities Policy Key initiation and exchange When is secure channel required What pre-requisites are required to establish a secure channel Can employees individually establish secure channels with TP What enterprise communication is required Will enterprise accept unencrypted PHI Will enterprise send unencrypted PHI if TP will not establish a secure channel
14 California Community Trial PKI Certificates for Client/Desktop Recipients Any available source of certificates Enterprise knows recipients addresses As long a certificate has known address, it is useful Push Certificates from PK3I Association Certificates California Medical Association providing certificates for physicians and staff American Association for Medical Transcription providing certificates for transcriptionists and clients All certificates will conform to ASTM Healthcare Certificate Policy and its certificate profile
15 California Community Trial New Key Distribution Model Push certificates from PKI Innovations, Inc (PK3I) Enterprise requests certificate from server Server generates the keypair and creates the certificate Send certificate to requestor Sends certificate and keypair to recipient Requestor communicates one-time pin/password to recipient to install keys and certificate in client For Microsoft products, one click install For other products, 2-5 steps depending on how the product has deviated from IETF standards for key storage
16 Typical Workflow
17 Typical Workflow
18 Typical Workflow
19 Improved Workflow
20 Success Factors Maintaining compliance Employees will use for communications Without an encryption alternative, enterprise risks non-compliance Preventing unnecessary costs Implementing a non- alternative will only add costs will not be turned off Registration and user support for trading partner employees is significant Maintaining business independence Adding an security solution to other options
21 Background Resources
22 HealthKey Sponsored Collaboration Mass HealthData Consortiumn domsec interop trails Demonstrated s/mime based interoperability between vendor s/mime gateway implementations Tumbleweed, TFS, Clearswift (as Baltimore), DICA, Vanguard Ongoing multi-enterprise s/mime gateway project CareGroup, Tufts, Commonwealth of Mass For more info: Joe Miller,
23 Vendor ~ Tumbleweed Early product entrant Significant healthcare installed base S/mime gateway and redirect products Imports any X509 certificate stores in directory Creates proxy certificates for enterprise accounts Full service product line Gateway, malicious content, virus scanning For more information Mike Fiore, [email protected],
24 Vendor ~ TFS Technologies Feature rich gateway product Includes openpgp support in addition to s/mime Includes certificate server for optional certificates for end users Consider use for individual signature at the desktop Free server solution for non-pki based security Supports automated distribution of symmetric key (password) via IVR (voice response), fax, (possibly alternate address) For more info John Casey, [email protected]
25 Vendor ~ Clearswift Inheritor of Content Technologies Sold off by Baltimore in its downsizing Emphasis on policy creation and management Supports distributed policy management Supports multiple message delivery mechanism with optional plugins s/mime gateway; http; technology licensed from sigaba For more information Farren West, [email protected],
26 Vendor ~ OmTool Secure gateway integrated with Exchange / Outlook Supports s/mime Alternate non-pki solutions based on zip / pdf encryption Always acquires receipts / supports security / signature of return mail Provides integration of with fax systems Fax / scan -> secure ; fax -> (internal) Provides security layer for HP Digital Sender Very slick solution, a Tunitas Group favorite For more information, Thad Bouchard, [email protected]
27 California Healthcare PKI Solutions CMA / MEDePass Focus on California physicians & staff High assurance model 2nd year of operation Will help market PKI based solution to your physician community Contact Terry Fotre DO, [email protected], American Association for Medical Transcription Certificates for transcriptionist (certified / non-certified) High assurance model for certified transcriptionist Online registry Go live in 3Q, 2003 Will train subscribers in secure use Contact Ray Smith, [email protected],
28 Technical Resources IETF DomSec spec RFC Domain Security Services using S/MIME Standards basis for use of s/mime gateways NIST guidelines on security RFC.pdf Excellent technical resource Network design discussion SMTP / POP server hardenning Common vulnerabilities and exposures security is not just about encryption!
29 About Tunitas Group Tunitas Group specializes in electronic commerce, communications and data exchange strategies for healthcare organizations. Core Expertise Biometrics and smart cards Directory applications and schema Electronic signature and EDI security solutions mgmt Internet security solutions HIPAA compliance planning Privacy & security policy design PKI planning and design Security assessment project Security risk analysis Internet technologies and protocols Workflow design Clients include Blue Shield of California California DHS California Medical Assn Catholic Healthcare West El Camino Hospital PacifiCare St. Joseph Health System Social Security Administration
Solving the HIPPA email Encryption Problem. Bill Pankey Tunitas Group [email protected]
 Solving the HIPPA email Encryption Problem Bill Pankey Tunitas Group [email protected] Agenda Is there a problem? What are the business requirements? Critical evaluation of solution alternatives Rethinking
Solving the HIPPA email Encryption Problem Bill Pankey Tunitas Group [email protected] Agenda Is there a problem? What are the business requirements? Critical evaluation of solution alternatives Rethinking
White paper. Why Encrypt? Securing email without compromising communications
 White paper Why Encrypt? Securing email without compromising communications Why Encrypt? There s an old saying that a ship is safe in the harbour, but that s not what ships are for. The same can be said
White paper Why Encrypt? Securing email without compromising communications Why Encrypt? There s an old saying that a ship is safe in the harbour, but that s not what ships are for. The same can be said
CoSign for 21CFR Part 11 Compliance
 CoSign for 21CFR Part 11 Compliance 2 Electronic Signatures at Company XYZ Company XYZ operates in a regulated environment and is subject to compliance with numerous US government regulations governed
CoSign for 21CFR Part 11 Compliance 2 Electronic Signatures at Company XYZ Company XYZ operates in a regulated environment and is subject to compliance with numerous US government regulations governed
Receiving Secure Email from Citi For External Customers and Business Partners
 Citi Secure Email Program Receiving Secure Email from Citi For External Customers and Business Partners Protecting the privacy and security of client information is a top priority at Citi. Citi s Secure
Citi Secure Email Program Receiving Secure Email from Citi For External Customers and Business Partners Protecting the privacy and security of client information is a top priority at Citi. Citi s Secure
The GlobalCerts TM SecureMail Gateway TM
 Glob@lCerts PRODUCT OVERVIEW: The GlobalCerts TM SecureMail Gateway TM Automatic encryption and decryption is unique to the SecureMail Gateway. The GlobalCerts SecureMail Gateway is based on a network
Glob@lCerts PRODUCT OVERVIEW: The GlobalCerts TM SecureMail Gateway TM Automatic encryption and decryption is unique to the SecureMail Gateway. The GlobalCerts SecureMail Gateway is based on a network
Direct Secure Messaging: Improving the Secure and Interoperable Exchange of Health Information
 Direct Secure Messaging: Improving the Secure and Interoperable Exchange of Health Information Within the healthcare industry, the exchange of protected health information (PHI) is governed by regulations
Direct Secure Messaging: Improving the Secure and Interoperable Exchange of Health Information Within the healthcare industry, the exchange of protected health information (PHI) is governed by regulations
The basic groups of components are described below. Fig X- 1 shows the relationship between components on a network.
 Elements of Email Email Components There are a number of software components used to produce, send and transfer email. These components can be broken down as clients or servers, although some components
Elements of Email Email Components There are a number of software components used to produce, send and transfer email. These components can be broken down as clients or servers, although some components
GlobalSign Enterprise Solutions
 GlobalSign Enterprise Solutions Secure Email & Key Recovery Using GlobalSign s Auto Enrollment Gateway (AEG) 1 v.1.2 Table of Contents Table of Contents... 2 Introduction... 3 The Benefits of Secure Email...
GlobalSign Enterprise Solutions Secure Email & Key Recovery Using GlobalSign s Auto Enrollment Gateway (AEG) 1 v.1.2 Table of Contents Table of Contents... 2 Introduction... 3 The Benefits of Secure Email...
PrivaSphere Gateway Certificate Authority (GW CA)
 PrivaSphere Gateway Certificate Authority (GW CA) Send and receive secure emails with your email program through restricting firewalls using SMIME gateway functionalities. PrivaSphere Secure Messaging
PrivaSphere Gateway Certificate Authority (GW CA) Send and receive secure emails with your email program through restricting firewalls using SMIME gateway functionalities. PrivaSphere Secure Messaging
Email Security Solutions
 TECHNOLOGY REPORT Email Security Solutions 1 TECHNOLOGY REPORT SUPPLEMENT EMAIL SECURITY TECHNOLOGY REPORT IF YOUR EMAIL IS SO CRITICAL, CAN YOU BE SURE IT S REALLY REALLY PRIVATE? FIND THE FULL RESULTS
TECHNOLOGY REPORT Email Security Solutions 1 TECHNOLOGY REPORT SUPPLEMENT EMAIL SECURITY TECHNOLOGY REPORT IF YOUR EMAIL IS SO CRITICAL, CAN YOU BE SURE IT S REALLY REALLY PRIVATE? FIND THE FULL RESULTS
Sendmail and PostX: Simplifying HIPAA Email Compliance. Providing healthcare organizations with secure outbound, inbound and internal email
 Sendmail and PostX: Simplifying HIPAA Email Compliance Providing healthcare organizations with secure outbound, inbound and internal email October 5, 2005 About Your Hosts Sendmail Complete email security
Sendmail and PostX: Simplifying HIPAA Email Compliance Providing healthcare organizations with secure outbound, inbound and internal email October 5, 2005 About Your Hosts Sendmail Complete email security
PaperClip Incorporated 3/7/06; Rev 9/18/09. PaperClip Compliant Email Service Whitepaper
 Incorporated 3/7/06; Rev 9/18/09 PaperClip Compliant Email Service Whitepaper Overview The FTC Safeguard Rules require Financial, Insurance and Medical providers to protect their customer s private information
Incorporated 3/7/06; Rev 9/18/09 PaperClip Compliant Email Service Whitepaper Overview The FTC Safeguard Rules require Financial, Insurance and Medical providers to protect their customer s private information
WISHIN Pulse Statement on Privacy, Security and HIPAA Compliance
 WISHIN Pulse Statement on Privacy, Security and HIPAA Compliance SEC-STM-072014 07/2014 Contents Patient Choice... 2 Security Protections... 2 Participation Agreement... 2 Controls... 3 Break the Glass...
WISHIN Pulse Statement on Privacy, Security and HIPAA Compliance SEC-STM-072014 07/2014 Contents Patient Choice... 2 Security Protections... 2 Participation Agreement... 2 Controls... 3 Break the Glass...
Sutter Health. Send It / Secure It / Control It Cloud based data exchange for business. For more information / 1.800.672.7233 info@datamotioncorp.
 Send It / Secure It / Control It Cloud based data exchange for business For more information / 1.800.672.7233 [email protected] CHALLENGE: HIPAA compliance; cost containment SOLUTION: DataMotion
Send It / Secure It / Control It Cloud based data exchange for business For more information / 1.800.672.7233 [email protected] CHALLENGE: HIPAA compliance; cost containment SOLUTION: DataMotion
How To Secure Mail Delivery
 FortiMail Identity Based Encryption A Business Enabler WHITE PAPER FORTINET FortiMail Identity Based Encryption - A Business Enabler PAGE 2 Contents Business Need Secure Mail Delivery... 3 Challenges with
FortiMail Identity Based Encryption A Business Enabler WHITE PAPER FORTINET FortiMail Identity Based Encryption - A Business Enabler PAGE 2 Contents Business Need Secure Mail Delivery... 3 Challenges with
W H I T E PA P E R. Providing Encryption at the Internal Desktop
 W H I T E PA P E R Secure Email Inside the Corporate Network: Providing Encryption at the Internal Desktop Table of Contents Introduction 2 Encryption at the Internal Desktop 2 Current Techniques for Desktop
W H I T E PA P E R Secure Email Inside the Corporate Network: Providing Encryption at the Internal Desktop Table of Contents Introduction 2 Encryption at the Internal Desktop 2 Current Techniques for Desktop
De-Mail. A reliable and secure online communication platform. Armin Wappenschmidt (secunet) More information: www.de-mail.de
 De-Mail A reliable and secure online communication platform Armin Wappenschmidt (secunet) More information: www.de-mail.de 1 Agenda Overview of De-Mail Implementation aspects Current status and outlook
De-Mail A reliable and secure online communication platform Armin Wappenschmidt (secunet) More information: www.de-mail.de 1 Agenda Overview of De-Mail Implementation aspects Current status and outlook
Account Restrictions Agreement [ARA] - Required by LuxSci HIPAA Accounts
![Account Restrictions Agreement [ARA] - Required by LuxSci HIPAA Accounts Account Restrictions Agreement [ARA] - Required by LuxSci HIPAA Accounts](/thumbs/24/3095735.jpg) Medical Privacy Version 2015.04.13 Account Restrictions Agreement [ARA] - Required by LuxSci HIPAA Accounts In order for Lux Scientiae, Incorporated (LuxSci) to ensure the security and privacy of all Electronic
Medical Privacy Version 2015.04.13 Account Restrictions Agreement [ARA] - Required by LuxSci HIPAA Accounts In order for Lux Scientiae, Incorporated (LuxSci) to ensure the security and privacy of all Electronic
IMAP and SMTP Setup in Email Clients
 IMAP and SMTP Setup in Email Clients Configuring an Email Client for IMAP Configuring an Email Client for the SMTP Server Overview Internet Message Access Protocol (IMAP), or a remote connection through
IMAP and SMTP Setup in Email Clients Configuring an Email Client for IMAP Configuring an Email Client for the SMTP Server Overview Internet Message Access Protocol (IMAP), or a remote connection through
EMAIL CONFIGURATION AND SETUP USER GUIDE AND REFERENCE MANUAL
 EMAIL CONFIGURATION AND SETUP USER GUIDE AND REFERENCE MANUAL The following manual will outline the configuration and setup for email access by any staff member. There are multiple ways to configure this
EMAIL CONFIGURATION AND SETUP USER GUIDE AND REFERENCE MANUAL The following manual will outline the configuration and setup for email access by any staff member. There are multiple ways to configure this
Email Encryption Services
 Services ZixCorp provides easy-to-use email encryption services for privacy and regulatory compliance. As the largest email encryption services provider, ZixCorp protects tens of millions of members in
Services ZixCorp provides easy-to-use email encryption services for privacy and regulatory compliance. As the largest email encryption services provider, ZixCorp protects tens of millions of members in
SECURE YOUR DATA EXCHANGE WITH SAFE-T BOX
 SECURE YOUR DATA EXCHANGE SAFE-T BOX WHITE PAPER Safe-T. Smart Security Made Simple. 1 The Costs of Uncontrolled Data Exchange 2 Safe-T Box Secure Data Exchange Platform 2.1 Business Applications and Data
SECURE YOUR DATA EXCHANGE SAFE-T BOX WHITE PAPER Safe-T. Smart Security Made Simple. 1 The Costs of Uncontrolled Data Exchange 2 Safe-T Box Secure Data Exchange Platform 2.1 Business Applications and Data
Pennsylvania Department of Public Welfare. Bureau of Information Systems OBSOLETE. Secure E-Mail User Guide. Version 1.0.
 Pennsylvania Department of Public Welfare Bureau of Information Systems Secure E-Mail User Guide Version 1.0 August 30, 2006 Table of Contents Introduction... 3 Purpose... 3 Terms of Use Applicable to
Pennsylvania Department of Public Welfare Bureau of Information Systems Secure E-Mail User Guide Version 1.0 August 30, 2006 Table of Contents Introduction... 3 Purpose... 3 Terms of Use Applicable to
Exchanging Medical Records Online with Direct
 Exchanging Medical Records Online with Direct Scott Rea, VP GOV/EDU Relations & Sr. PKI Architect, DigiCert, Inc. [email protected] www.digicert.com +1 (801) 877-2100 Exchanging Medical Records Online
Exchanging Medical Records Online with Direct Scott Rea, VP GOV/EDU Relations & Sr. PKI Architect, DigiCert, Inc. [email protected] www.digicert.com +1 (801) 877-2100 Exchanging Medical Records Online
Digital certificates and SSL
 Digital certificates and SSL 20 out of 33 rated this helpful Applies to: Exchange Server 2013 Topic Last Modified: 2013-08-26 Secure Sockets Layer (SSL) is a method for securing communications between
Digital certificates and SSL 20 out of 33 rated this helpful Applies to: Exchange Server 2013 Topic Last Modified: 2013-08-26 Secure Sockets Layer (SSL) is a method for securing communications between
Royal Mail Business Integration Gateway Specification
 FSpec401 FSpec401 Royal Mail Customer Solutions Royal Mail Business Integration Gateway Specification - XB60 The FSpec401 document details, for customers, the various methods of connecting to Royal Mail
FSpec401 FSpec401 Royal Mail Customer Solutions Royal Mail Business Integration Gateway Specification - XB60 The FSpec401 document details, for customers, the various methods of connecting to Royal Mail
SSL VPN vs. IPSec VPN
 SSL VPN vs. IPSec VPN White Paper 254 E. Hacienda Avenue Campbell, CA 95008 www.arraynetworks.net (408) 378-6800 1 SSL VPN vs. IPSec VPN Copyright 2002 Array Networks, Inc. SSL VPN vs. IPSec VPN White
SSL VPN vs. IPSec VPN White Paper 254 E. Hacienda Avenue Campbell, CA 95008 www.arraynetworks.net (408) 378-6800 1 SSL VPN vs. IPSec VPN Copyright 2002 Array Networks, Inc. SSL VPN vs. IPSec VPN White
A NATURAL FIT. Microsoft Office 365 TM and Zix TM Email Encryption. By ZixCorp www.zixcorp.com
 Microsoft Office 365 TM and Zix TM Email Encryption A NATURAL FIT By ZixCorp www.zixcorp.com Microsoft Office 365 TM and Zix TM Email Encryption Page 1 INTRODUCTION IT managers and decision makers are
Microsoft Office 365 TM and Zix TM Email Encryption A NATURAL FIT By ZixCorp www.zixcorp.com Microsoft Office 365 TM and Zix TM Email Encryption Page 1 INTRODUCTION IT managers and decision makers are
Emailing from The E2 Shop System EMail address Server Name Server Port, Encryption Protocol, Encryption Type, SMTP User ID SMTP Password
 Emailing from The E2 Shop System With recent releases of E2SS (at least 7.2.7.23), we will be allowing two protocols for EMail delivery. A new protocol for EMail delivery Simple Mail Transfer Protocol
Emailing from The E2 Shop System With recent releases of E2SS (at least 7.2.7.23), we will be allowing two protocols for EMail delivery. A new protocol for EMail delivery Simple Mail Transfer Protocol
MANAGED FILE TRANSFER: 10 STEPS TO HIPAA/HITECH COMPLIANCE
 WHITE PAPER MANAGED FILE TRANSFER: 10 STEPS TO HIPAA/HITECH COMPLIANCE 1. OVERVIEW Do you want to design a file transfer process that is secure? Or one that is compliant? Of course, the answer is both.
WHITE PAPER MANAGED FILE TRANSFER: 10 STEPS TO HIPAA/HITECH COMPLIANCE 1. OVERVIEW Do you want to design a file transfer process that is secure? Or one that is compliant? Of course, the answer is both.
HKUST CA. Certification Practice Statement
 HKUST CA Certification Practice Statement IN SUPPORT OF HKUST CA CERTIFICATION SERVICES Version : 2.1 Date : 12 November 2003 Prepared by : Information Technology Services Center Hong Kong University of
HKUST CA Certification Practice Statement IN SUPPORT OF HKUST CA CERTIFICATION SERVICES Version : 2.1 Date : 12 November 2003 Prepared by : Information Technology Services Center Hong Kong University of
Certification Path Processing in the Tumbleweed Validation Authority Product Line Federal Bridge CA Meeting 10/14/2004
 Certification Path Processing in the Tumbleweed Validation Authority Product Line Federal Bridge CA Meeting 10/14/2004 Stefan Kotes, Engineering Manager Agenda Tumbleweed company overview Certification
Certification Path Processing in the Tumbleweed Validation Authority Product Line Federal Bridge CA Meeting 10/14/2004 Stefan Kotes, Engineering Manager Agenda Tumbleweed company overview Certification
SonicWALL PCI 1.1 Implementation Guide
 Compliance SonicWALL PCI 1.1 Implementation Guide A PCI Implementation Guide for SonicWALL SonicOS Standard In conjunction with ControlCase, LLC (PCI Council Approved Auditor) SonicWall SonicOS Standard
Compliance SonicWALL PCI 1.1 Implementation Guide A PCI Implementation Guide for SonicWALL SonicOS Standard In conjunction with ControlCase, LLC (PCI Council Approved Auditor) SonicWall SonicOS Standard
INTERNET SECURITY: FIREWALLS AND BEYOND. Mehernosh H. Amroli 4-25-2002
 INTERNET SECURITY: FIREWALLS AND BEYOND Mehernosh H. Amroli 4-25-2002 Preview History of Internet Firewall Technology Internet Layer Security Transport Layer Security Application Layer Security Before
INTERNET SECURITY: FIREWALLS AND BEYOND Mehernosh H. Amroli 4-25-2002 Preview History of Internet Firewall Technology Internet Layer Security Transport Layer Security Application Layer Security Before
PineApp TM Mail Encryption Solution TM
 PineApp TM Mail Encryption Solution TM How to keep your outgoing messages fully secured. October 2008 Modern day challenges in E-Mail Security Throughout the years, E-Mail has evolved significantly, emerging
PineApp TM Mail Encryption Solution TM How to keep your outgoing messages fully secured. October 2008 Modern day challenges in E-Mail Security Throughout the years, E-Mail has evolved significantly, emerging
Astaro Mail Archiving Getting Started Guide
 Connect With Confidence Astaro Mail Archiving Getting Started Guide About this Getting Started Guide The Astaro Mail Archiving Service is an archiving platform in the form of a fully hosted service. E-mails
Connect With Confidence Astaro Mail Archiving Getting Started Guide About this Getting Started Guide The Astaro Mail Archiving Service is an archiving platform in the form of a fully hosted service. E-mails
AlphaTrust PRONTO Enterprise Platform Product Overview
 AlphaTrust PRONTO Enterprise Platform Product Overview AlphaTrust PRONTO Enterprise Platform is server-based software that automates the creation of legally enforceable, permanent business records that
AlphaTrust PRONTO Enterprise Platform Product Overview AlphaTrust PRONTO Enterprise Platform is server-based software that automates the creation of legally enforceable, permanent business records that
How to configure your Windows PC post migrating to Microsoft Office 365
 How to configure your Windows PC post migrating to Microsoft Office 365 1 Contents Purpose... 3 Document Support Boundaries... 3 Examples used in this document... 4 Several different Microsoft Office 365
How to configure your Windows PC post migrating to Microsoft Office 365 1 Contents Purpose... 3 Document Support Boundaries... 3 Examples used in this document... 4 Several different Microsoft Office 365
HIPAA Privacy and Information Security Management Briefing
 HIPAA Privacy and Information Security Management Briefing Karen Pagliaro-Meyer Privacy Officer [email protected] (212) 305-7315 Soumitra Sengupta Information Security Officer [email protected] (212)
HIPAA Privacy and Information Security Management Briefing Karen Pagliaro-Meyer Privacy Officer [email protected] (212) 305-7315 Soumitra Sengupta Information Security Officer [email protected] (212)
Secure transmission of Protected Health Information (PHI)
 PHI Email Encryption Instructions for External Entities Page 1 of 5 Secure transmission of Protected Health Information (PHI) To ensure that all communications (email, phone, or fax) containing Protected
PHI Email Encryption Instructions for External Entities Page 1 of 5 Secure transmission of Protected Health Information (PHI) To ensure that all communications (email, phone, or fax) containing Protected
Configuring Outlook to send mail via your Exchange mailbox using an alternative email address
 Configuring Outlook to send mail via your Exchange mailbox using an alternative email address This document is based on Exchange mailboxes and using Outlook 2007. The principles outlined are equally valid
Configuring Outlook to send mail via your Exchange mailbox using an alternative email address This document is based on Exchange mailboxes and using Outlook 2007. The principles outlined are equally valid
An Introduction to Entrust PKI. Last updated: September 14, 2004
 An Introduction to Entrust PKI Last updated: September 14, 2004 2004 Entrust. All rights reserved. Entrust is a registered trademark of Entrust, Inc. in the United States and certain other countries. In
An Introduction to Entrust PKI Last updated: September 14, 2004 2004 Entrust. All rights reserved. Entrust is a registered trademark of Entrust, Inc. in the United States and certain other countries. In
Using etoken for Securing E-mails Using Outlook and Outlook Express
 Using etoken for Securing E-mails Using Outlook and Outlook Express Lesson 15 April 2004 etoken Certification Course Securing Email Using Certificates Unprotected emails can be easily read and/or altered
Using etoken for Securing E-mails Using Outlook and Outlook Express Lesson 15 April 2004 etoken Certification Course Securing Email Using Certificates Unprotected emails can be easily read and/or altered
CHIS, Inc. Privacy General Guidelines
 CHIS, Inc. and HIPAA CHIS, Inc. provides services to healthcare facilities and uses certain protected health information (PHI) in connection with performing these services. Therefore, CHIS, Inc. is classified
CHIS, Inc. and HIPAA CHIS, Inc. provides services to healthcare facilities and uses certain protected health information (PHI) in connection with performing these services. Therefore, CHIS, Inc. is classified
MANAGED FILE TRANSFER: 10 STEPS TO SOX COMPLIANCE
 WHITE PAPER MANAGED FILE TRANSFER: 10 STEPS TO SOX COMPLIANCE 1. OVERVIEW Do you want to design a file transfer process that is secure? Or one that is compliant? Of course, the answer is both. But it s
WHITE PAPER MANAGED FILE TRANSFER: 10 STEPS TO SOX COMPLIANCE 1. OVERVIEW Do you want to design a file transfer process that is secure? Or one that is compliant? Of course, the answer is both. But it s
Microsoft Outlook 2010
 Microsoft Outlook 2010 a. Open Outlook 2010. b. Click File i. Select Info. ii. Within Account Information, click Add Account. c. Within the Setup wizard select Manually configure server settings or additional
Microsoft Outlook 2010 a. Open Outlook 2010. b. Click File i. Select Info. ii. Within Account Information, click Add Account. c. Within the Setup wizard select Manually configure server settings or additional
a) Encryption is enabled on the access point. b) The conference room network is on a separate virtual local area network (VLAN)
 MIS5206 Week 12 Your Name Date 1. Which significant risk is introduced by running the file transfer protocol (FTP) service on a server in a demilitarized zone (DMZ)? a) User from within could send a file
MIS5206 Week 12 Your Name Date 1. Which significant risk is introduced by running the file transfer protocol (FTP) service on a server in a demilitarized zone (DMZ)? a) User from within could send a file
WEB SERVICES SECURITY
 WEB SERVICES SECURITY February 2008 The Government of the Hong Kong Special Administrative Region The contents of this document remain the property of, and may not be reproduced in whole or in part without
WEB SERVICES SECURITY February 2008 The Government of the Hong Kong Special Administrative Region The contents of this document remain the property of, and may not be reproduced in whole or in part without
The following multiple-choice post-course assessment will evaluate your knowledge of the skills and concepts taught in Internet Business Associate.
 Course Assessment Answers-1 Course Assessment The following multiple-choice post-course assessment will evaluate your knowledge of the skills and concepts taught in Internet Business Associate. 1. A person
Course Assessment Answers-1 Course Assessment The following multiple-choice post-course assessment will evaluate your knowledge of the skills and concepts taught in Internet Business Associate. 1. A person
Email Encryption Services
 Services ZixCorp provides easy-to-use email encryption services for privacy and regulatory compliance. As the largest email encryption services provider, ZixCorp protects tens of millions of members in
Services ZixCorp provides easy-to-use email encryption services for privacy and regulatory compliance. As the largest email encryption services provider, ZixCorp protects tens of millions of members in
CHARTER BUSINESS custom hosting faqs 2010 INTERNET. Q. How do I access my email? Q. How do I change or reset a password for an email account?
 Contents Page Q. How do I access my email? Q. How do I change or reset a password for an email account? Q. How do I forward or redirect my messages to a different email address? Q. How do I set up an auto-reply
Contents Page Q. How do I access my email? Q. How do I change or reset a password for an email account? Q. How do I forward or redirect my messages to a different email address? Q. How do I set up an auto-reply
Implementing Transparent Security for Desktop Encryption Users
 Implementing Transparent Security for Desktop Encryption Users Solutions to automate email encryption with external parties Get this White Paper Entrust Inc. All All Rights Reserved. 1 1 Contents Introduction...
Implementing Transparent Security for Desktop Encryption Users Solutions to automate email encryption with external parties Get this White Paper Entrust Inc. All All Rights Reserved. 1 1 Contents Introduction...
Internet Banking Internal Control Questionnaire
 Internet Banking Internal Control Questionnaire Completed by: Date Completed: 1. Has the institution developed and implemented a sound system of internal controls over Internet banking technology and systems?
Internet Banking Internal Control Questionnaire Completed by: Date Completed: 1. Has the institution developed and implemented a sound system of internal controls over Internet banking technology and systems?
Processo Civile Telematico (On-line Civil Trial)
 Processo Civile Telematico (On-line Civil Trial) By Giulio Borsari Italian Ministry of Justice IT Department via Crescenzio 7/c Rome Phone +39 051 4200210 (alt. +39 06 68620209) Fax +39 051 4200200 [email protected]
Processo Civile Telematico (On-line Civil Trial) By Giulio Borsari Italian Ministry of Justice IT Department via Crescenzio 7/c Rome Phone +39 051 4200210 (alt. +39 06 68620209) Fax +39 051 4200200 [email protected]
Configuration Manual for Lime Domains
 Email Accounts Configuration Manual for Lime Domains Table of Contents Introduction:... 2 To configure your Outlook Express client:... 3 To configure your Microsoft Outlook client:... 12 To configure your
Email Accounts Configuration Manual for Lime Domains Table of Contents Introduction:... 2 To configure your Outlook Express client:... 3 To configure your Microsoft Outlook client:... 12 To configure your
How to Pop Email to Outlook
 Webmail Access How to Pop Email to Outlook You can access your email account through the following URL: http://webmail.usalocalbiz.com. The login is your full email address and your account password. We
Webmail Access How to Pop Email to Outlook You can access your email account through the following URL: http://webmail.usalocalbiz.com. The login is your full email address and your account password. We
WHITEPAPER. SECUREAUTH 2-FACTOR AS A SERVICE 2FaaS
 WHITEPAPER SECUREAUTH 2-FACTOR AS A SERVICE 2FaaS EXECUTIVE OVERVIEW 2-Factor as a Service (2FaaS) is a 100% cloud-hosted authentication solution that offers flexible security without compromising user
WHITEPAPER SECUREAUTH 2-FACTOR AS A SERVICE 2FaaS EXECUTIVE OVERVIEW 2-Factor as a Service (2FaaS) is a 100% cloud-hosted authentication solution that offers flexible security without compromising user
SecurEnvoy Security Server. SecurMail Solutions Guide
 SecurEnvoy Security Server SecurMail Solutions Guide SecurMail Solutions Guide 2009 SecurEnvoy Printed: 2009 in United Kingdom Publisher SecurEnvoy Publishing Managing Editor SecurEnvoy Training Dept Technical
SecurEnvoy Security Server SecurMail Solutions Guide SecurMail Solutions Guide 2009 SecurEnvoy Printed: 2009 in United Kingdom Publisher SecurEnvoy Publishing Managing Editor SecurEnvoy Training Dept Technical
TELSTRA BUSINESS MAIL QUICK REFERENCE GUIDE
 1.1 Introduction 01 1.2 The Checklist 02 1.3 Business Mail Requirements 03 1.4 Downloading & Installing Outlook 2003 04 BEFORE YOU START 1.1 INTRODUCTION 1.1.1 Who this Guide is For 1.1.2 What s in this
1.1 Introduction 01 1.2 The Checklist 02 1.3 Business Mail Requirements 03 1.4 Downloading & Installing Outlook 2003 04 BEFORE YOU START 1.1 INTRODUCTION 1.1.1 Who this Guide is For 1.1.2 What s in this
Set up Outlook for your new student e mail with IMAP/POP3 settings
 Set up Outlook for your new student e mail with IMAP/POP3 settings 1. Open Outlook. The Account Settings dialog box will open the first time you open Outlook. If the Account Settings dialog box doesn't
Set up Outlook for your new student e mail with IMAP/POP3 settings 1. Open Outlook. The Account Settings dialog box will open the first time you open Outlook. If the Account Settings dialog box doesn't
Medical Privacy Version 2015.12.10 - Standard. Business Associate Agreement. 1. Definitions
 Medical Privacy Version 2015.12.10 - Standard Business Associate Agreement This Business Associate Agreement (the Agreement ) shall apply to the extent that the Lux Scientiae HIPAA Customer signee is a
Medical Privacy Version 2015.12.10 - Standard Business Associate Agreement This Business Associate Agreement (the Agreement ) shall apply to the extent that the Lux Scientiae HIPAA Customer signee is a
Vendor Questionnaire
 Instructions: This questionnaire was developed to assess the vendor s information security practices and standards. Please complete this form as completely as possible, answering yes or no, and explaining
Instructions: This questionnaire was developed to assess the vendor s information security practices and standards. Please complete this form as completely as possible, answering yes or no, and explaining
Set Up E-mail Setup with Microsoft Outlook 2007 using POP3
 Page 1 of 14 Help Center Set Up E-mail Setup with Microsoft Outlook 2007 using POP3 Learn how to configure Outlook 2007 for use with your 1&1 e-mail account using POP3. Before you begin, you will need
Page 1 of 14 Help Center Set Up E-mail Setup with Microsoft Outlook 2007 using POP3 Learn how to configure Outlook 2007 for use with your 1&1 e-mail account using POP3. Before you begin, you will need
Internet File Management & HIPAA A Practical Approach towards Responding to the Privacy Regulation of the Act
 White Paper Internet File Management & HIPAA A Practical Approach towards Responding to the Privacy Regulation of the Act The recent activation of the privacy requirement of the Health Insurance Portability
White Paper Internet File Management & HIPAA A Practical Approach towards Responding to the Privacy Regulation of the Act The recent activation of the privacy requirement of the Health Insurance Portability
How to Request Access to the Commerce Contract Management System
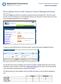 How to Request Access to the Commerce Contract Management System (one-time only) Once you ve logged into SAW, you can add your selected services by clicking on the Click here to add services link. This
How to Request Access to the Commerce Contract Management System (one-time only) Once you ve logged into SAW, you can add your selected services by clicking on the Click here to add services link. This
Electronic Prescribing of Controlled Substances Technical Framework Panel. Mark Gingrich, RxHub LLC July 11, 2006
 Electronic Prescribing of Controlled Substances Technical Framework Panel Mark Gingrich, RxHub LLC July 11, 2006 RxHub Overview Founded 2001 as nationwide, universal electronic information exchange Encompass
Electronic Prescribing of Controlled Substances Technical Framework Panel Mark Gingrich, RxHub LLC July 11, 2006 RxHub Overview Founded 2001 as nationwide, universal electronic information exchange Encompass
April 2005. PGP White Paper. PGP Universal 2.0 Technical Overview
 April 2005 PGP White Paper PGP Universal 2.0 Technical Overview 1 Table of Contents EXECUTIVE SUMMARY... 2 INTRODUCTION... 3 THE PGP ECOSYSTEM... 4 WHAT IS THE PGP ECOSYSTEM?... 4 PGP Global Directory...
April 2005 PGP White Paper PGP Universal 2.0 Technical Overview 1 Table of Contents EXECUTIVE SUMMARY... 2 INTRODUCTION... 3 THE PGP ECOSYSTEM... 4 WHAT IS THE PGP ECOSYSTEM?... 4 PGP Global Directory...
The DoD Public Key Infrastructure And Public Key-Enabling Frequently Asked Questions
 The DoD Public Key Infrastructure And Public Key-Enabling Frequently Asked Questions May 3, 2004 TABLE OF CONTENTS GENERAL PKI QUESTIONS... 1 1. What is PKI?...1 2. What functionality is provided by a
The DoD Public Key Infrastructure And Public Key-Enabling Frequently Asked Questions May 3, 2004 TABLE OF CONTENTS GENERAL PKI QUESTIONS... 1 1. What is PKI?...1 2. What functionality is provided by a
New Single Sign-on Options for IBM Lotus Notes & Domino. 2012 IBM Corporation
 New Single Sign-on Options for IBM Lotus Notes & Domino 2012 IBM Corporation IBM s statements regarding its plans, directions, and intent are subject to change or withdrawal without notice at IBM s sole
New Single Sign-on Options for IBM Lotus Notes & Domino 2012 IBM Corporation IBM s statements regarding its plans, directions, and intent are subject to change or withdrawal without notice at IBM s sole
Tumbleweed MailGate Secure Messenger
 EMAIL SECURITY SOLUTIONS TECHNOLOGY REPORT Tumbleweed MailGate Secure Messenger JANUARY 2007 www.westcoastlabs.org 2 EMAIL SECURITY SOLUTIONS TECHNOLOGY REPORT CONTENTS MailGate Secure Messenger Tumbleweed
EMAIL SECURITY SOLUTIONS TECHNOLOGY REPORT Tumbleweed MailGate Secure Messenger JANUARY 2007 www.westcoastlabs.org 2 EMAIL SECURITY SOLUTIONS TECHNOLOGY REPORT CONTENTS MailGate Secure Messenger Tumbleweed
DMZ Gateways: Secret Weapons for Data Security
 A L I N O M A S O F T W A R E W H I T E P A P E R DMZ Gateways: Secret Weapons for Data Security A L I N O M A S O F T W A R E W H I T E P A P E R DMZ Gateways: Secret Weapons for Data Security EXECUTIVE
A L I N O M A S O F T W A R E W H I T E P A P E R DMZ Gateways: Secret Weapons for Data Security A L I N O M A S O F T W A R E W H I T E P A P E R DMZ Gateways: Secret Weapons for Data Security EXECUTIVE
Bridging People and Process. Bridging People and Process. Bridging People and Process. Bridging People and Process
 USER MANUAL DATAMOTION SECUREMAIL SERVER Bridging People and Process APPLICATION VERSION 1.1 Bridging People and Process Bridging People and Process Bridging People and Process Published By: DataMotion,
USER MANUAL DATAMOTION SECUREMAIL SERVER Bridging People and Process APPLICATION VERSION 1.1 Bridging People and Process Bridging People and Process Bridging People and Process Published By: DataMotion,
Building A Secure Microsoft Exchange Continuity Appliance
 Building A Secure Microsoft Exchange Continuity Appliance Teneros, Inc. 215 Castro Street, 3rd Floor Mountain View, California 94041-1203 USA p 650.641.7400 f 650.641.7401 ON AVAILABLE ACCESSIBLE Building
Building A Secure Microsoft Exchange Continuity Appliance Teneros, Inc. 215 Castro Street, 3rd Floor Mountain View, California 94041-1203 USA p 650.641.7400 f 650.641.7401 ON AVAILABLE ACCESSIBLE Building
Policies and Procedures for Electronic Protected Health Information (ephi) and Personally Identifiable Information (PII)
 Policies and Procedures for Electronic Protected Health Information (ephi) and Personally Identifiable Information (PII) Effective Date: April 10, 2012 Prepared by: Joe Raschke (IT) Table of Contents Purpose
Policies and Procedures for Electronic Protected Health Information (ephi) and Personally Identifiable Information (PII) Effective Date: April 10, 2012 Prepared by: Joe Raschke (IT) Table of Contents Purpose
HTTP connections can use transport-layer security (SSL or its successor, TLS) to provide data integrity
 Improving File Sharing Security: A Standards Based Approach A Xythos Software White Paper January 2, 2003 Abstract Increasing threats to enterprise networks coupled with an ever-growing dependence upon
Improving File Sharing Security: A Standards Based Approach A Xythos Software White Paper January 2, 2003 Abstract Increasing threats to enterprise networks coupled with an ever-growing dependence upon
Enterprise Cybersecurity Best Practices Part Number MAN-00363 Revision 006
 Enterprise Cybersecurity Best Practices Part Number MAN-00363 Revision 006 April 2013 Hologic and the Hologic Logo are trademarks or registered trademarks of Hologic, Inc. Microsoft, Active Directory,
Enterprise Cybersecurity Best Practices Part Number MAN-00363 Revision 006 April 2013 Hologic and the Hologic Logo are trademarks or registered trademarks of Hologic, Inc. Microsoft, Active Directory,
Healthcare Compliance Solutions
 Privacy Compliance Healthcare Compliance Solutions Trust and privacy are essential for building meaningful human relationships. Let Protected Trust be your Safe Harbor The U.S. Department of Health and
Privacy Compliance Healthcare Compliance Solutions Trust and privacy are essential for building meaningful human relationships. Let Protected Trust be your Safe Harbor The U.S. Department of Health and
Certification Practice Statement
 FernUniversität in Hagen: Certification Authority (CA) Certification Practice Statement VERSION 1.1 Ralph Knoche 18.12.2009 Contents 1. Introduction... 4 1.1. Overview... 4 1.2. Scope of the Certification
FernUniversität in Hagen: Certification Authority (CA) Certification Practice Statement VERSION 1.1 Ralph Knoche 18.12.2009 Contents 1. Introduction... 4 1.1. Overview... 4 1.2. Scope of the Certification
WHITE PAPER. Managed File Transfer: When Data Loss Prevention Is Not Enough Moving Beyond Stopping Leaks and Protecting Email
 WHITE PAPER Managed File Transfer: When Data Loss Prevention Is Not Enough Moving Beyond Stopping Leaks and Protecting Email EXECUTIVE SUMMARY Data Loss Prevention (DLP) monitoring products have greatly
WHITE PAPER Managed File Transfer: When Data Loss Prevention Is Not Enough Moving Beyond Stopping Leaks and Protecting Email EXECUTIVE SUMMARY Data Loss Prevention (DLP) monitoring products have greatly
Transglobal Secure Collaboration Program Secure E-mail v.1 Gateway Design Principles
 Transglobal Secure Collaboration Program Secure E-mail v.1 Gateway Design Principles Prepared by: CP Secure E-mail v.1 Project Team Version: 2.0.2 Date: 16 July 2012 Page i Copyright 2012 Transglobal Secure
Transglobal Secure Collaboration Program Secure E-mail v.1 Gateway Design Principles Prepared by: CP Secure E-mail v.1 Project Team Version: 2.0.2 Date: 16 July 2012 Page i Copyright 2012 Transglobal Secure
Optus EmailSMS for MS Outlook and Lotus Notes
 Optus EmailSMS for MS Outlook and Lotus Notes Service Description, August 2005. OVERVIEW This document provides an overview of the Optus EmailSMS service delivered jointly by Optus and redcoal. It highlights
Optus EmailSMS for MS Outlook and Lotus Notes Service Description, August 2005. OVERVIEW This document provides an overview of the Optus EmailSMS service delivered jointly by Optus and redcoal. It highlights
Microsoft Exchange Server 2007, Upgrade from Exchange 2000/2003 (3938. 3938/5049/5050) Course KC3065 5 Days OVERVIEW COURSE OBJECTIVES AUDIENCE
 Microsoft Exchange, Upgrade from Exchange 2000/2003 COURSE OVERVIEW This instructor-led course offers Microsoft Exchange Server administrators with the skills they need to manage a Microsoft Exchange infrastructure.
Microsoft Exchange, Upgrade from Exchange 2000/2003 COURSE OVERVIEW This instructor-led course offers Microsoft Exchange Server administrators with the skills they need to manage a Microsoft Exchange infrastructure.
CIPHERMAIL EMAIL ENCRYPTION. CipherMail white paper
 CIPHERMAIL EMAIL ENCRYPTION CipherMail white paper Copyright 2009-2014, ciphermail.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in
CIPHERMAIL EMAIL ENCRYPTION CipherMail white paper Copyright 2009-2014, ciphermail.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in
Email Setup Guide. network support pc repairs web design graphic design Internet services spam filtering hosting sales programming
 Email Setup Guide 1. Entourage 2008 Page 2 2. ios / iphone Page 5 3. Outlook 2013 Page 10 4. Outlook 2007 Page 17 5. Windows Live Mail a. New Account Setup Page 21 b. Change Existing Account Page 25 Entourage
Email Setup Guide 1. Entourage 2008 Page 2 2. ios / iphone Page 5 3. Outlook 2013 Page 10 4. Outlook 2007 Page 17 5. Windows Live Mail a. New Account Setup Page 21 b. Change Existing Account Page 25 Entourage
Ciphire Mail. Abstract
 Ciphire Mail Technical Introduction Abstract Ciphire Mail is cryptographic software providing email encryption and digital signatures. The Ciphire Mail client resides on the user's computer between the
Ciphire Mail Technical Introduction Abstract Ciphire Mail is cryptographic software providing email encryption and digital signatures. The Ciphire Mail client resides on the user's computer between the
