NTFS permissions represent a core part of Windows s security system. Using
|
|
|
- David Scott
- 7 years ago
- Views:
Transcription
1 bonus appendix NTFS Permissions NTFS permissions represent a core part of Windows s security system. Using this feature, you can specify exactly which coworkers are allowed to open which files and folders on your machine. In fact, you can also specify how much access each person has. You can dictate, for example, that Gomez and Morticia aren t allowed to open your Fourth-Quarter Projections spreadsheet at all, that Fred and Ginger can open it but not make changes, and that George and Gracie can both open it and make changes. Your colleagues will encounter the permissions you ve set up like this in two different situations: when tapping into your machine from across the network or when sitting down at it and logging in using their own names and passwords. In either case, the NTFS permissions you set up protect your files and folders equally well. Tip: In Chapter 21, of Windows 10: The Missing Manual, you can read about a very similar form of access privileges called sharing permissions. There s a big difference between share permissions and the NTFS permissions described here, though: Share permissions keep people out of your stuff only when they try to access your PC from over the network. Actually, there are other differences, too. NTFS permissions offer more gradations of access. And using NTFS permissions, you can declare individual files not just folders accessible or inaccessible to specific coworkers. Read on for details. bonus appendix: ntfs permissions 1
2 Using NTFS permissions is most decidedly a power-user technique because of the added complexity it introduces. Entire books have been written on the topic of NTFS permissions alone. You ve been warned. Setting Up NTFS Permissions To change the permissions for an NTFS file or folder, you open its Properties dialog box by right-clicking its icon and then choosing Properties from the shortcut menu. Click the Security tab (Figure 1). Figure 1: The Security tab of an NTFS folder s Properties dialog box. If you have any aspirations to be a Windows power user, get used to this dialog box. You re going to see it a lot, because almost every icon on a Windows system files, folders, disks, printers has a Security tab like this one. Step 1: Specify the person The top of the Security tab lists the people and groups that have been granted or denied permissions to the selected file or folder. When you click a name in the list, the Permissions box at the bottom of the dialog box shows you how much access that person or group has. The first step in assigning permissions, then, is to click Edit. You see an editable version of the dialog box shown in Figure windows 10: the missing manual
3 If the person or group isn t listed, then click Edit, then Add to display the Select Users or Groups dialog box, where you can type them in (Figure 2). Tip: Instead of typing in names one at a time, as shown in Figure 16, you can also choose them from a list, which lets you avoid spelling mistakes and having to guess at the variations. To do so, click the Advanced button to display an expanded version of the dialog box, and then click Find Now to search for all the accounts and groups on the computer. Finally, in the resulting list, click the names of the people and groups you want to add (Ctrl-click to select more than one at a time). Click OK to add them to the previous dialog box, and then click OK again to add the selected users and groups to the Security tab. Figure 2: Type the names of the people or groups in the Enter the object names to select box at the bottom, trying not to feel depersonalized by Microsoft s reference to you as an object. If you re adding more than one name, separate them with semicolons. Because remembering exact spellings can be iffy, click Check Names to confirm that these are indeed legitimate account holders. Finally, click OK to insert them into the list on the Security tab. Step 2: Specify the permissions Once you ve added the users and groups you need to the list on the Security tab, you can highlight each one and set permissions for it. You do that by turning on the Allow or Deny checkboxes at the bottom half of the dialog box. The different degrees of freedom break down as follows (they re listed here from least to most control, even though that s not how they re listed in the dialog box): List folder contents, available only for folders, means the selected individuals can see (but not necessarily open) the files and folders inside. That may sound obvious but believe it or not, if you don t turn on this option, the affected people won t even be able to see what s in this folder. The folder will just appear empty. Read lets people examine the contents of the file or folder but not make changes. (They can also examine the permissions settings of these files and folders the ones you re setting up right now.) Read & Execute is a lot like Read, except that it also lets people run any programs they find inside the affected folder. When applied to a folder, furthermore, this permission adds the ability to traverse folders. (Traversing means directly opening inner folders even when you re not allowed to open the outer folder. You might get bonus appendix: ntfs permissions 3
4 to an inner folder by double-clicking a shortcut icon, for example, or by typing the folder s path into the address bar of a window.) Write is like Read, but it adds the freedom to make and save changes to the file. When applied to a folder, this permission means that people can create new files and folders inside it. Modify includes all the abilities of the Write and Read & Execute levels, plus the ability to delete files or folders. Full control confers complete power over the file or folder. The selected person or group can do anything they like with it, including trashing it or its contents, changing its permissions, taking ownership of it (away from you, if they like), and so on. Of course, turning on Allow grants that level of freedom to the specified user or group, and turning it off takes away that freedom. (For details on the Deny checkbox, see the box below.) Note: If you re not careful, it s entirely possible to orphan a file or folder (or even your entire drive) by revoking everyone s permission to it, even your own, making it completely inaccessible by anyone. That s why, before you get too deeply into working with NTFS permissions, you might consider creating an extra user account on your system and granting it full control for all your drives, just in case something goes wrong. Groups and Permissions Once you understand the concept of permissions, and you ve enjoyed a thorough shudder contemplating the complexity of a network administrator s job (six levels of permissions thousands of files thousands of employees = way too many permutations), one other mystery of Windows will fully snap into focus: the purpose of groups. Groups are canned categories, complete with predefined powers over the PC, into which you can put different individuals to save yourself the time of adjusting their permissions and privileges individually. As it turns out, each of the ready-made groups also comes with predefined permissions over the files and folders on your hard drive. Here, for example, is how the system grants permissions to the items in your Windows folder for the Users and Administrators groups: Users Administrators X X Full Control Modify Read & Execute X X List Folder Contents X X Read X X Write X If you belong to the Users group, you have the List Folder Contents permission, which means you can see what s in the Windows folder; the Read permission, which means 4 windows 10: the missing manual
5 you can open up anything you find inside; and the Read & Execute permission, which means you can run programs in that folder (which is essential for Windows itself to run). But people in the Users group aren t allowed to change or delete anything in the Windows folder, or to put anything else inside. Windows is protecting itself against the mischievous and the clueless. Members of the Administrators group have all those abilities and more they also have Modify and Write permissions, which let them add new files and folders to the Windows folder (so that, for example, they can install a new software program on the machine). When Permissions Collide If you ve successfully absorbed all this information about permissions, one thing should be clear: People in the Administrators group ought to be able to change or delete any file in your Windows folder. After all, they have the Modify permission, which ought to give them that power. In fact, they can move or delete anything in any folder in the Windows folder, because the first cardinal rule of NTFS permissions is this: NTFS permissions travel downstream, from outer folders to inner ones. In other words, if you have the Modify and Write permissions to a folder, then you ought to have the same permissions for every file and folder inside it. But in Windows XP, there was something called the Power Users group. It s been turned off in Windows 8, but for the sake of illustration, let s say you re part of it. You d find that you can t, in fact, delete any files or folders in the Windows folder. That s because each of them comes with Modify and Write permissions turned off for Power Users, even though the folder that encloses them has those permissions turned on. Why would Microsoft go to this trouble? Because it wanted to prevent people in this group from inadvertently changing or deleting important Windows files and yet it wanted these people to be able to put new files into the Windows folder, so they could install new programs. This is a perfect example of the second cardinal rule of NTFS permissions: NTFS permissions that have been explicitly applied to a file or folder always override inherited permissions. Here s another example: Suppose your sister, the technical whiz of the household, has given you Read, Write, Modify, Read & Execute, and List Folder Contents permissions to her own Documents folder. Now you can read, change, or delete any file there. But she can still protect an individual document or folder inside her Documents folder the BirthdayPartyPlans.doc file, for example by denying you all permissions to it. You ll be able to open anything else in there, but not that file. bonus appendix: ntfs permissions 5
6 Believe it or not, NTFS permissions get even more complicated, thanks to the third cardinal rule: Permissions accumulate as you burrow downward through subfolders. Now suppose your sister has given you the Read and List Folder Contents permissions to her Documents folder a look but don t touch policy. Thanks to the first cardinal rule, you automatically get the same permissions to every file and folder inside Documents. Suppose one of these inner folders is called Grocery Lists. If she grants you the Modify and Write permissions to the Grocery Lists folder so you can add items to the shopping list, you end up having Read, Modify, and Write permissions for every file in that folder. Those files have accumulated permissions they got the Read permission from Documents, and the Modify and Write permissions from the Grocery Lists folder. Because these layers of inherited permissions can get dizzyingly complex, Microsoft has prepared a little cheat sheet, a dialog box that tells you the bottom line, the net result the effective permissions. To see it, follow these steps: 1. Click the Advanced button on the Security tab. The Advanced Security Settings dialog box appears. Figure 3: The Effective Permissions tab for an NTFS folder. Note that you can t turn these checkboxes on or off; this is a read-only screen that tells you what permissions the selected user or group has for the file or folder. You can t modify the permissions here. You can t tell from this display how these effective permissions have been calculated, either (that is, where the permissions have been inherited from). 6 windows 10: the missing manual
7 2. Click the Effective Access tab; click Select a user. Now you see the same Select User or Group dialog box you saw earlier when you were creating permissions. 3. Click the user or group whose effective permissions you want to see, and then click OK. You return to the Effective Access tab. 4. Click View effective access. You now see checkmarks next to the permissions that are in effect, taking into account folder-permission inheritance and all other factors for the user or group of that particular file or folder (Figure 3). bonus appendix: ntfs permissions 7
Offline Files & Sync Center
 bonus appendix Offline Files & Sync Center The offline files feature is designed for laptop lovers. It lets you carry off files that gerally live on your office network, so you can get some work done while
bonus appendix Offline Files & Sync Center The offline files feature is designed for laptop lovers. It lets you carry off files that gerally live on your office network, so you can get some work done while
9 Administering Shared Folders
 9 Administering Shared Folders Exam Objectives in this Chapter: Manage and troubleshoot access to shared folders. Create and remove shared folders. Why This Chapter Matters Control access to shared folders
9 Administering Shared Folders Exam Objectives in this Chapter: Manage and troubleshoot access to shared folders. Create and remove shared folders. Why This Chapter Matters Control access to shared folders
Copies of QuickBooks aren t cheap, so the people who do your bookkeeping
 appendix d Tracking with the Standalone r Copies of QuickBooks aren t cheap, so the people who do your bookkeeping are probably the only ones who have access to the program. Meanwhile, you may have dozens
appendix d Tracking with the Standalone r Copies of QuickBooks aren t cheap, so the people who do your bookkeeping are probably the only ones who have access to the program. Meanwhile, you may have dozens
Microsoft Outlook Web Access Handbook
 Microsoft Outlook Web Access Handbook Introduction Outlook Web access allows you to use a web browser (Internet Explorer or Firefox) to read your email, send email, and check your online calendar. This
Microsoft Outlook Web Access Handbook Introduction Outlook Web access allows you to use a web browser (Internet Explorer or Firefox) to read your email, send email, and check your online calendar. This
Many home and small office networks exist for no
 C H A P T E R Accessing and Sharing Network Resources Many home and small office networks exist for no other reason than to share a broadband Internet connection. The administrators of those networks attach
C H A P T E R Accessing and Sharing Network Resources Many home and small office networks exist for no other reason than to share a broadband Internet connection. The administrators of those networks attach
Objectives. At the end of this chapter students should be able to:
 NTFS PERMISSIONS AND SECURITY SETTING.1 Introduction to NTFS Permissions.1.1 File Permissions and Folder Permission.2 Assigning NTFS Permissions and Special Permission.2.1 Planning NTFS Permissions.2.2
NTFS PERMISSIONS AND SECURITY SETTING.1 Introduction to NTFS Permissions.1.1 File Permissions and Folder Permission.2 Assigning NTFS Permissions and Special Permission.2.1 Planning NTFS Permissions.2.2
VP-ASP Shopping Cart Quick Start (Free Version) Guide Version 6.50 March 21 2007
 VP-ASP Shopping Cart Quick Start (Free Version) Guide Version 6.50 March 21 2007 Rocksalt International Pty Ltd support@vpasp.com www.vpasp.com Table of Contents 1 INTRODUCTION... 3 2 FEATURES... 4 3 WHAT
VP-ASP Shopping Cart Quick Start (Free Version) Guide Version 6.50 March 21 2007 Rocksalt International Pty Ltd support@vpasp.com www.vpasp.com Table of Contents 1 INTRODUCTION... 3 2 FEATURES... 4 3 WHAT
Windows XP Managing Your Files
 Windows XP Managing Your Files Objective 1: Understand your computer s filing system Your computer's filing system has three basic divisions: files, folders, and drives. 1. File- everything saved on your
Windows XP Managing Your Files Objective 1: Understand your computer s filing system Your computer's filing system has three basic divisions: files, folders, and drives. 1. File- everything saved on your
Getting Started on the Computer With Mouseaerobics! Windows XP
 This handout was modified from materials supplied by the Bill and Melinda Gates Foundation through a grant to the Manchester City Library. Getting Started on the Computer With Mouseaerobics! Windows XP
This handout was modified from materials supplied by the Bill and Melinda Gates Foundation through a grant to the Manchester City Library. Getting Started on the Computer With Mouseaerobics! Windows XP
Networking Lab - Vista Public Network Sharing
 Networking Lab - Vista Public Network Sharing After completing the lab activity, you will be able to: Explain the differences between Windows XP and Windows Vista network sharing. Explain the purpose of
Networking Lab - Vista Public Network Sharing After completing the lab activity, you will be able to: Explain the differences between Windows XP and Windows Vista network sharing. Explain the purpose of
BIGPOND ONLINE STORAGE USER GUIDE Issue 1.1.0-18 August 2005
 BIGPOND ONLINE STORAGE USER GUIDE Issue 1.1.0-18 August 2005 PLEASE NOTE: The contents of this publication, and any associated documentation provided to you, must not be disclosed to any third party without
BIGPOND ONLINE STORAGE USER GUIDE Issue 1.1.0-18 August 2005 PLEASE NOTE: The contents of this publication, and any associated documentation provided to you, must not be disclosed to any third party without
Staying Organized with the Outlook Journal
 CHAPTER Staying Organized with the Outlook Journal In this chapter Using Outlook s Journal 362 Working with the Journal Folder 364 Setting Up Automatic Email Journaling 367 Using Journal s Other Tracking
CHAPTER Staying Organized with the Outlook Journal In this chapter Using Outlook s Journal 362 Working with the Journal Folder 364 Setting Up Automatic Email Journaling 367 Using Journal s Other Tracking
In the same spirit, our QuickBooks 2008 Software Installation Guide has been completely revised as well.
 QuickBooks 2008 Software Installation Guide Welcome 3/25/09; Ver. IMD-2.1 This guide is designed to support users installing QuickBooks: Pro or Premier 2008 financial accounting software, especially in
QuickBooks 2008 Software Installation Guide Welcome 3/25/09; Ver. IMD-2.1 This guide is designed to support users installing QuickBooks: Pro or Premier 2008 financial accounting software, especially in
Chapter 28: Expanding Web Studio
 CHAPTER 25 - SAVING WEB SITES TO THE INTERNET Having successfully completed your Web site you are now ready to save (or post, or upload, or ftp) your Web site to the Internet. Web Studio has three ways
CHAPTER 25 - SAVING WEB SITES TO THE INTERNET Having successfully completed your Web site you are now ready to save (or post, or upload, or ftp) your Web site to the Internet. Web Studio has three ways
How to test and debug an ASP.NET application
 Chapter 4 How to test and debug an ASP.NET application 113 4 How to test and debug an ASP.NET application If you ve done much programming, you know that testing and debugging are often the most difficult
Chapter 4 How to test and debug an ASP.NET application 113 4 How to test and debug an ASP.NET application If you ve done much programming, you know that testing and debugging are often the most difficult
Folder Management in Outlook for Macintosh
 Folder Management in Outlook Introduction Learn to create and manage folders in your mailbox on the Exchange server, in Personal Folders saved on your computer s hard disk or to a local network server,
Folder Management in Outlook Introduction Learn to create and manage folders in your mailbox on the Exchange server, in Personal Folders saved on your computer s hard disk or to a local network server,
Why should I back up my certificate? How do I create a backup copy of my certificate?
 Why should I back up my certificate? You should always keep a backup copy of your ACES Business Certificate on a location external to your computer. Since it s stored locally on your computer, in the Windows
Why should I back up my certificate? You should always keep a backup copy of your ACES Business Certificate on a location external to your computer. Since it s stored locally on your computer, in the Windows
16.4.3 Lab: Data Backup and Recovery in Windows XP
 16.4.3 Lab: Data Backup and Recovery in Windows XP Introduction Print and complete this lab. In this lab, you will back up data. You will also perform a recovery of the data. Recommended Equipment The
16.4.3 Lab: Data Backup and Recovery in Windows XP Introduction Print and complete this lab. In this lab, you will back up data. You will also perform a recovery of the data. Recommended Equipment The
What you should know about: Windows 7. What s changed? Why does it matter to me? Do I have to upgrade? Tim Wakeling
 What you should know about: Windows 7 What s changed? Why does it matter to me? Do I have to upgrade? Tim Wakeling Contents What s all the fuss about?...1 Different Editions...2 Features...4 Should you
What you should know about: Windows 7 What s changed? Why does it matter to me? Do I have to upgrade? Tim Wakeling Contents What s all the fuss about?...1 Different Editions...2 Features...4 Should you
Managing documents, files and folders
 Managing documents, files and folders Your computer puts information at your fingertips. Over time, however, you might have so many files that it can be difficult to find the specific file you need. Without
Managing documents, files and folders Your computer puts information at your fingertips. Over time, however, you might have so many files that it can be difficult to find the specific file you need. Without
Mimeo Printer User Guide
 Mimeo Printer User Guide 1.800.GoMimeo mimeo.com Table of Contents Step 1: Download & Install the Mimeo Printer... 2 Step 2: Select Files for Uploading... 4 Step 3: Build Your Document... 8 Frequently
Mimeo Printer User Guide 1.800.GoMimeo mimeo.com Table of Contents Step 1: Download & Install the Mimeo Printer... 2 Step 2: Select Files for Uploading... 4 Step 3: Build Your Document... 8 Frequently
SECTION 5: Finalizing Your Workbook
 SECTION 5: Finalizing Your Workbook In this section you will learn how to: Protect a workbook Protect a sheet Protect Excel files Unlock cells Use the document inspector Use the compatibility checker Mark
SECTION 5: Finalizing Your Workbook In this section you will learn how to: Protect a workbook Protect a sheet Protect Excel files Unlock cells Use the document inspector Use the compatibility checker Mark
REDUCING YOUR MICROSOFT OUTLOOK MAILBOX SIZE
 There are several ways to eliminate having too much email on the Exchange mail server. To reduce your mailbox size it is recommended that you practice the following tasks: Delete items from your Mailbox:
There are several ways to eliminate having too much email on the Exchange mail server. To reduce your mailbox size it is recommended that you practice the following tasks: Delete items from your Mailbox:
Introduction to MS WINDOWS XP
 Introduction to MS WINDOWS XP Mouse Desktop Windows Applications File handling Introduction to MS Windows XP 2 Table of Contents What is Windows XP?... 3 Windows within Windows... 3 The Desktop... 3 The
Introduction to MS WINDOWS XP Mouse Desktop Windows Applications File handling Introduction to MS Windows XP 2 Table of Contents What is Windows XP?... 3 Windows within Windows... 3 The Desktop... 3 The
Workshare imanage Integration File Sharing & DMS Mobility. Getting Started Guide
 Workshare imanage Integration File Sharing & DMS Mobility Getting Started Guide R Work s about to get smarter We have one goal to give you a simpler, faster way to work on documents. We help you work outside
Workshare imanage Integration File Sharing & DMS Mobility Getting Started Guide R Work s about to get smarter We have one goal to give you a simpler, faster way to work on documents. We help you work outside
Outlook Connector. Version 2 User Manual. client-side plugin. Collaborate Using Outlook. Version 2.0.0
 Outlook Connector client-side plugin Collaborate Using Outlook Version 2 User Manual Version 2.0.0 2003-2005 Alt-N Technologies. All rights reserved. MDaemon, WorldClient, and RelayFax are registered trademarks
Outlook Connector client-side plugin Collaborate Using Outlook Version 2 User Manual Version 2.0.0 2003-2005 Alt-N Technologies. All rights reserved. MDaemon, WorldClient, and RelayFax are registered trademarks
Email Retention Information Messages automatically age out of your mailbox
 Email Retention Information Messages automatically age out of your mailbox Everything in your mailbox is subject to deletion after a certain time period (described below) with the exception of your Contacts.
Email Retention Information Messages automatically age out of your mailbox Everything in your mailbox is subject to deletion after a certain time period (described below) with the exception of your Contacts.
Migrating to Excel 2010 from Excel 2003 - Excel - Microsoft Office 1 of 1
 Migrating to Excel 2010 - Excel - Microsoft Office 1 of 1 In This Guide Microsoft Excel 2010 looks very different, so we created this guide to help you minimize the learning curve. Read on to learn key
Migrating to Excel 2010 - Excel - Microsoft Office 1 of 1 In This Guide Microsoft Excel 2010 looks very different, so we created this guide to help you minimize the learning curve. Read on to learn key
Windows XP Pro: Basics 1
 NORTHWEST MISSOURI STATE UNIVERSITY ONLINE USER S GUIDE 2004 Windows XP Pro: Basics 1 Getting on the Northwest Network Getting on the Northwest network is easy with a university-provided PC, which has
NORTHWEST MISSOURI STATE UNIVERSITY ONLINE USER S GUIDE 2004 Windows XP Pro: Basics 1 Getting on the Northwest Network Getting on the Northwest network is easy with a university-provided PC, which has
Outlook 2010 Desk Reference Guide
 Outlook 2010 Desk Reference Guide Version 1.0 Developed by OR/WA IRM Please remember to print back-to-back. July 12, 2011 Microsoft Outlook 2010 This document has been developed by OR/WA IRM staff to provide
Outlook 2010 Desk Reference Guide Version 1.0 Developed by OR/WA IRM Please remember to print back-to-back. July 12, 2011 Microsoft Outlook 2010 This document has been developed by OR/WA IRM staff to provide
Getting Started with WebSite Tonight
 Getting Started with WebSite Tonight WebSite Tonight Getting Started Guide Version 3.0 (12.2010) Copyright 2010. All rights reserved. Distribution of this work or derivative of this work is prohibited
Getting Started with WebSite Tonight WebSite Tonight Getting Started Guide Version 3.0 (12.2010) Copyright 2010. All rights reserved. Distribution of this work or derivative of this work is prohibited
Hosting Users Guide 2011
 Hosting Users Guide 2011 eofficemgr technology support for small business Celebrating a decade of providing innovative cloud computing services to small business. Table of Contents Overview... 3 Configure
Hosting Users Guide 2011 eofficemgr technology support for small business Celebrating a decade of providing innovative cloud computing services to small business. Table of Contents Overview... 3 Configure
Use Office 365 on your iphone
 Use Office 365 on your iphone Quick Start Guide Check email Set up your iphone to receive your O365 email. Check your calendar wherever you are Always know where you have to be by syncing your calendar
Use Office 365 on your iphone Quick Start Guide Check email Set up your iphone to receive your O365 email. Check your calendar wherever you are Always know where you have to be by syncing your calendar
The primary format type that we use is the one highlighted on top (Microsoft Word 97/200/XP (.doc))
 Open Office Writer is capable of saving documents in many different formats. Click the file menu (upper left corner) and this will open a menu where you can select save as which will open up the box shown
Open Office Writer is capable of saving documents in many different formats. Click the file menu (upper left corner) and this will open a menu where you can select save as which will open up the box shown
ADVANCED OUTLOOK 2003
 ADVANCED OUTLOOK 2003 Table of Contents Page LESSON 1: MANAGING YOUR MAILBOX LIMITS...1 Understanding Mailbox Limits...1 Setting AutoArchive...3 AutoArchiving Your Folders...5 Deleting Items Automatically...7
ADVANCED OUTLOOK 2003 Table of Contents Page LESSON 1: MANAGING YOUR MAILBOX LIMITS...1 Understanding Mailbox Limits...1 Setting AutoArchive...3 AutoArchiving Your Folders...5 Deleting Items Automatically...7
Setting Up Database Security with Access 97
 Setting Up Database Security with Access 97 The most flexible and extensive method of securing a database is called user-level security. This form of security is similar to methods used in most network
Setting Up Database Security with Access 97 The most flexible and extensive method of securing a database is called user-level security. This form of security is similar to methods used in most network
Virtual Office Remote Installation Guide
 Virtual Office Remote Installation Guide Table of Contents VIRTUAL OFFICE REMOTE INSTALLATION GUIDE... 3 UNIVERSAL PRINTER CONFIGURATION INSTRUCTIONS... 12 CHANGING DEFAULT PRINTERS ON LOCAL SYSTEM...
Virtual Office Remote Installation Guide Table of Contents VIRTUAL OFFICE REMOTE INSTALLATION GUIDE... 3 UNIVERSAL PRINTER CONFIGURATION INSTRUCTIONS... 12 CHANGING DEFAULT PRINTERS ON LOCAL SYSTEM...
If you know exactly how you want your business forms to look and don t mind
 appendix e Advanced Form Customization If you know exactly how you want your business forms to look and don t mind detail work, you can configure QuickBooks forms however you want. With QuickBooks Layout
appendix e Advanced Form Customization If you know exactly how you want your business forms to look and don t mind detail work, you can configure QuickBooks forms however you want. With QuickBooks Layout
AppleShare Client User s Manual
 apple AppleShare Client User s Manual How to use this manual This manual describes how to upgrade your system software and AppleShare Client software and also provides instructions on how to use your AppleShare
apple AppleShare Client User s Manual How to use this manual This manual describes how to upgrade your system software and AppleShare Client software and also provides instructions on how to use your AppleShare
10.3.1.6 Lab - Data Backup and Recovery in Windows XP
 5.0 10.3.1.6 Lab - Data Backup and Recovery in Windows XP Introduction Print and complete this lab. In this lab, you will back up data. You will also perform a recovery of the data. Recommended Equipment
5.0 10.3.1.6 Lab - Data Backup and Recovery in Windows XP Introduction Print and complete this lab. In this lab, you will back up data. You will also perform a recovery of the data. Recommended Equipment
Vodafone PC SMS 2010. (Software version 4.7.1) User Manual
 Vodafone PC SMS 2010 (Software version 4.7.1) User Manual July 19, 2010 Table of contents 1. Introduction...4 1.1 System Requirements... 4 1.2 Reply-to-Inbox... 4 1.3 What s new?... 4 2. Installation...6
Vodafone PC SMS 2010 (Software version 4.7.1) User Manual July 19, 2010 Table of contents 1. Introduction...4 1.1 System Requirements... 4 1.2 Reply-to-Inbox... 4 1.3 What s new?... 4 2. Installation...6
Microsoft Migrating to PowerPoint 2010 from PowerPoint 2003
 In This Guide Microsoft PowerPoint 2010 looks very different, so we created this guide to help you minimize the learning curve. Read on to learn key parts of the new interface, discover free PowerPoint
In This Guide Microsoft PowerPoint 2010 looks very different, so we created this guide to help you minimize the learning curve. Read on to learn key parts of the new interface, discover free PowerPoint
Creating and Managing Shared Folders
 Creating and Managing Shared Folders Microsoft threw all sorts of new services, features, and functions into Windows 2000 Server, but at the heart of it all was still the requirement to be a good file
Creating and Managing Shared Folders Microsoft threw all sorts of new services, features, and functions into Windows 2000 Server, but at the heart of it all was still the requirement to be a good file
Training Manual. Version 6
 Training Manual TABLE OF CONTENTS A. E-MAIL... 4 A.1 INBOX... 8 A.1.1 Create New Message... 8 A.1.1.1 Add Attachments to an E-mail Message... 11 A.1.1.2 Insert Picture into an E-mail Message... 12 A.1.1.3
Training Manual TABLE OF CONTENTS A. E-MAIL... 4 A.1 INBOX... 8 A.1.1 Create New Message... 8 A.1.1.1 Add Attachments to an E-mail Message... 11 A.1.1.2 Insert Picture into an E-mail Message... 12 A.1.1.3
Creating trouble-free numbering in Microsoft Word
 Creating trouble-free numbering in Microsoft Word This note shows you how to create trouble-free chapter, section and paragraph numbering, as well as bulleted and numbered lists that look the way you want
Creating trouble-free numbering in Microsoft Word This note shows you how to create trouble-free chapter, section and paragraph numbering, as well as bulleted and numbered lists that look the way you want
Advanced Excel Charts : Tables : Pivots : Macros
 Advanced Excel Charts : Tables : Pivots : Macros Charts In Excel, charts are a great way to visualize your data. However, it is always good to remember some charts are not meant to display particular types
Advanced Excel Charts : Tables : Pivots : Macros Charts In Excel, charts are a great way to visualize your data. However, it is always good to remember some charts are not meant to display particular types
Outlook Web Access (OWA) 2010 Email Cheat Sheet
 June 9, 2014 Outlook Web Access (OWA) 2010 Email Cheat Sheet Outlook Web Access 2010 allows you to gain access to your messages, calendars, contacts, tasks and public folders from any computer with internet
June 9, 2014 Outlook Web Access (OWA) 2010 Email Cheat Sheet Outlook Web Access 2010 allows you to gain access to your messages, calendars, contacts, tasks and public folders from any computer with internet
Remote Access Using the USDA LincPass
 If you require an accessible version of this course please follow these directions. Press Shift+Control+Y to activate the Adobe Read Out Loud function. Once you have activated the Read Out Loud function
If you require an accessible version of this course please follow these directions. Press Shift+Control+Y to activate the Adobe Read Out Loud function. Once you have activated the Read Out Loud function
Table of Contents. Page 3
 Welcome to Exchange Mail Customer Full Name Your e-mail is now being delivered and stored on the new Exchange server. Your new e-mail address is @rit.edu. This is the e-mail address that you should give
Welcome to Exchange Mail Customer Full Name Your e-mail is now being delivered and stored on the new Exchange server. Your new e-mail address is @rit.edu. This is the e-mail address that you should give
Microsoft Outlook Quick Reference Sheet
 Microsoft Outlook is an incredibly powerful e-mail and personal information management application. Its features and capabilities are extensive. Refer to this handout whenever you require quick reminders
Microsoft Outlook is an incredibly powerful e-mail and personal information management application. Its features and capabilities are extensive. Refer to this handout whenever you require quick reminders
Quick Guide. Passports in Microsoft PowerPoint. Getting Started with PowerPoint. Locating the PowerPoint Folder (PC) Locating PowerPoint (Mac)
 Passports in Microsoft PowerPoint Quick Guide Created Updated PowerPoint is a very versatile tool. It is usually used to create multimedia presentations and printed handouts but it is an almost perfect
Passports in Microsoft PowerPoint Quick Guide Created Updated PowerPoint is a very versatile tool. It is usually used to create multimedia presentations and printed handouts but it is an almost perfect
Getting Started with Dynamic Web Sites
 PHP Tutorial 1 Getting Started with Dynamic Web Sites Setting Up Your Computer To follow this tutorial, you ll need to have PHP, MySQL and a Web server up and running on your computer. This will be your
PHP Tutorial 1 Getting Started with Dynamic Web Sites Setting Up Your Computer To follow this tutorial, you ll need to have PHP, MySQL and a Web server up and running on your computer. This will be your
Appendix K Introduction to Microsoft Visual C++ 6.0
 Appendix K Introduction to Microsoft Visual C++ 6.0 This appendix serves as a quick reference for performing the following operations using the Microsoft Visual C++ integrated development environment (IDE):
Appendix K Introduction to Microsoft Visual C++ 6.0 This appendix serves as a quick reference for performing the following operations using the Microsoft Visual C++ integrated development environment (IDE):
UF Health SharePoint 2010 Introduction to Content Administration
 UF Health SharePoint 2010 Introduction to Content Administration Email: training@health.ufl.edu Web Page: http://training.health.ufl.edu Last Updated 2/7/2014 Introduction to SharePoint 2010 2.0 Hours
UF Health SharePoint 2010 Introduction to Content Administration Email: training@health.ufl.edu Web Page: http://training.health.ufl.edu Last Updated 2/7/2014 Introduction to SharePoint 2010 2.0 Hours
Scan to SMB(PC) Set up Guide
 Scan to SMB(PC) Set up Guide Regarding Trade Names Windows is a registered trademark of Microsoft Corporation in the U.S.A. and/or other countries. Windows XP and Windows Vista are trademarks of Microsoft
Scan to SMB(PC) Set up Guide Regarding Trade Names Windows is a registered trademark of Microsoft Corporation in the U.S.A. and/or other countries. Windows XP and Windows Vista are trademarks of Microsoft
HOW TO BURN A CD/DVD IN WINDOWS XP. Data Projects
 Page 1 HOW TO BURN A CD/DVD IN WINDOWS XP There are two ways to burn files to a CD or DVD using Windows XP: 1. Using Sonic RecordNow! Plus or 2. Using the Windows Explorer CD Burning with Sonic Recordnow!
Page 1 HOW TO BURN A CD/DVD IN WINDOWS XP There are two ways to burn files to a CD or DVD using Windows XP: 1. Using Sonic RecordNow! Plus or 2. Using the Windows Explorer CD Burning with Sonic Recordnow!
Finding and Opening Documents
 In this chapter Learn how to get around in the Open File dialog box. See how to navigate through drives and folders and display the files in other folders. Learn how to search for a file when you can t
In this chapter Learn how to get around in the Open File dialog box. See how to navigate through drives and folders and display the files in other folders. Learn how to search for a file when you can t
Fairfield University Using Xythos for File Sharing
 Fairfield University Using Xythos for File Sharing Version 7.0 Table of Contents I: Manage your Department Folder...2 Your Department Folder... 2 II: Sharing Folders and Files Inside of Fairfield U...3
Fairfield University Using Xythos for File Sharing Version 7.0 Table of Contents I: Manage your Department Folder...2 Your Department Folder... 2 II: Sharing Folders and Files Inside of Fairfield U...3
Google Docs, Sheets, and Slides: Share and collaborate
 Google Docs, Sheets, and Slides: Share and collaborate Once you've created your document, you can share it with others. Collaborators can then edit the same document at the same time you'll always have
Google Docs, Sheets, and Slides: Share and collaborate Once you've created your document, you can share it with others. Collaborators can then edit the same document at the same time you'll always have
HOW TO ORGANIZE PICTURES
 Get started When you upload your pictures to Shutterfly, you can do much more than view them. Our workspace offers tools that let you quickly and easily organize your photos as well. We re going to show
Get started When you upload your pictures to Shutterfly, you can do much more than view them. Our workspace offers tools that let you quickly and easily organize your photos as well. We re going to show
Presentations and PowerPoint
 V-1.1 PART V Presentations and PowerPoint V-1.2 Computer Fundamentals V-1.3 LESSON 1 Creating a Presentation After completing this lesson, you will be able to: Start Microsoft PowerPoint. Explore the PowerPoint
V-1.1 PART V Presentations and PowerPoint V-1.2 Computer Fundamentals V-1.3 LESSON 1 Creating a Presentation After completing this lesson, you will be able to: Start Microsoft PowerPoint. Explore the PowerPoint
OUTLOOK 2010 QUICK GUIDE. Version 1.7
 OUTLOOK 2010 QUICK GUIDE Version 1.7 Table of Contents THE NAVIGATION PANE... 5 Mail... 5 Calendar... 5 Contacts... 5 Tasks... 5 Notes... 5 Folder List... 5 Shortcuts... 5 E-MAIL... 5 Create a new e-mail
OUTLOOK 2010 QUICK GUIDE Version 1.7 Table of Contents THE NAVIGATION PANE... 5 Mail... 5 Calendar... 5 Contacts... 5 Tasks... 5 Notes... 5 Folder List... 5 Shortcuts... 5 E-MAIL... 5 Create a new e-mail
13 Managing Devices. Your computer is an assembly of many components from different manufacturers. LESSON OBJECTIVES
 LESSON 13 Managing Devices OBJECTIVES After completing this lesson, you will be able to: 1. Open System Properties. 2. Use Device Manager. 3. Understand hardware profiles. 4. Set performance options. Estimated
LESSON 13 Managing Devices OBJECTIVES After completing this lesson, you will be able to: 1. Open System Properties. 2. Use Device Manager. 3. Understand hardware profiles. 4. Set performance options. Estimated
Reviewing documents with track changes in Word 2013
 Reviewing documents with track changes in Word 2013 Information Services Reviewing documents with track changes in Word 2013 This note covers how to use Word s reviewing tools to track the changes made
Reviewing documents with track changes in Word 2013 Information Services Reviewing documents with track changes in Word 2013 This note covers how to use Word s reviewing tools to track the changes made
Working with sections in Word
 Working with sections in Word Have you have ever wanted to create a Microsoft Word document with some pages numbered in Roman numerals and the rest in Arabic, or include a landscape page to accommodate
Working with sections in Word Have you have ever wanted to create a Microsoft Word document with some pages numbered in Roman numerals and the rest in Arabic, or include a landscape page to accommodate
Eastern Shore Community College. Employee Information Technology Handbook
 Eastern Shore Community College Employee Information Technology Handbook 6/5/2008 Table of Contents ESCC Network Account Quick Facts...3 Overview... 3 What is my login name and password?... 3 What happens
Eastern Shore Community College Employee Information Technology Handbook 6/5/2008 Table of Contents ESCC Network Account Quick Facts...3 Overview... 3 What is my login name and password?... 3 What happens
User Profile Manager 2.6
 User Profile Manager 2.6 User Guide ForensiT Limited, Innovation Centre Medway, Maidstone Road, Chatham, Kent, ME5 9FD England. Tel: US 1-877-224-1721 (Toll Free) Intl. +44 (0) 845 838 7122 Fax: +44 (0)
User Profile Manager 2.6 User Guide ForensiT Limited, Innovation Centre Medway, Maidstone Road, Chatham, Kent, ME5 9FD England. Tel: US 1-877-224-1721 (Toll Free) Intl. +44 (0) 845 838 7122 Fax: +44 (0)
Google Drive: Access and organize your files
 Google Drive: Access and organize your files Use Google Drive to store and access your files, folders, and Google Docs, Sheets, and Slides anywhere. Change a file on the web, your computer, tablet, or
Google Drive: Access and organize your files Use Google Drive to store and access your files, folders, and Google Docs, Sheets, and Slides anywhere. Change a file on the web, your computer, tablet, or
Building Qualtrics Surveys for EFS & ALC Course Evaluations: Step by Step Instructions
 Building Qualtrics Surveys for EFS & ALC Course Evaluations: Step by Step Instructions Jennifer DeSantis August 28, 2013 A relatively quick guide with detailed explanations of each step. It s recommended
Building Qualtrics Surveys for EFS & ALC Course Evaluations: Step by Step Instructions Jennifer DeSantis August 28, 2013 A relatively quick guide with detailed explanations of each step. It s recommended
SENDING EMAILS & MESSAGES TO GROUPS
 SENDING EMAILS & MESSAGES TO GROUPS Table of Contents What is the Difference between Emails and Selltis Messaging?... 3 Configuring your Email Settings... 4 Sending Emails to Groups Option A: Tasks...
SENDING EMAILS & MESSAGES TO GROUPS Table of Contents What is the Difference between Emails and Selltis Messaging?... 3 Configuring your Email Settings... 4 Sending Emails to Groups Option A: Tasks...
An Overview of Outlook
 An Overview of Outlook Alabama Association of REALTORS STATE OF ALASKA 2012 SUMMER CONFERENCE - IT S A FAMILY AFFAIR http://www.state.ak.us/local/akpages/admin/info/msea/ Perdido Beach Resort - Orange
An Overview of Outlook Alabama Association of REALTORS STATE OF ALASKA 2012 SUMMER CONFERENCE - IT S A FAMILY AFFAIR http://www.state.ak.us/local/akpages/admin/info/msea/ Perdido Beach Resort - Orange
Enabling Backups for Windows and MAC OS X
 Enabling Backups for Windows and MAC OS X TM Trademarks and Copyrights Copyright Storix, Inc. 1999-2005 Storix is a registered trademark of Storix, Inc. SBAdmin is a trademark of Storix, Inc in the USA
Enabling Backups for Windows and MAC OS X TM Trademarks and Copyrights Copyright Storix, Inc. 1999-2005 Storix is a registered trademark of Storix, Inc. SBAdmin is a trademark of Storix, Inc in the USA
Outlook 2010 Email Computer Training Solutions Student Guide Version Revision Date Course Length
 Outlook 2010 Email Computer Training Solutions Version 0.3 Revision Date Course Length 2013-Mar-05 3.5 hours Table of Contents Quick Reference... 3 Outlook 2010 Main Window... 3 Icons in the Guide...
Outlook 2010 Email Computer Training Solutions Version 0.3 Revision Date Course Length 2013-Mar-05 3.5 hours Table of Contents Quick Reference... 3 Outlook 2010 Main Window... 3 Icons in the Guide...
Podcasting with Audacity
 Podcasting with Audacity Table of Contents Introduction... 1 Why Podcast?... 2 Audacity Set-Up... 2 Installation... 2 Configuration... 2 Audacity Intro... 3 Adding tracks... 4 Prepare to Start Recording...
Podcasting with Audacity Table of Contents Introduction... 1 Why Podcast?... 2 Audacity Set-Up... 2 Installation... 2 Configuration... 2 Audacity Intro... 3 Adding tracks... 4 Prepare to Start Recording...
Authorware Install Directions for IE in Windows Vista, Windows 7, and Windows 8
 Authorware Install Directions for IE in Windows Vista, Windows 7, and Windows 8 1. Read entire document before continuing. 2. Close all browser windows. There should be no websites open. If you are using
Authorware Install Directions for IE in Windows Vista, Windows 7, and Windows 8 1. Read entire document before continuing. 2. Close all browser windows. There should be no websites open. If you are using
IT Quick Reference Guides Using Windows 7
 IT Quick Reference Guides Using Windows 7 Windows Guides This sheet covers many of the basic commands for using the Windows 7 operating system. WELCOME TO WINDOWS 7 After you log into your machine, the
IT Quick Reference Guides Using Windows 7 Windows Guides This sheet covers many of the basic commands for using the Windows 7 operating system. WELCOME TO WINDOWS 7 After you log into your machine, the
Using Zimbra Briefcase
 Using Zimbra Briefcase The Zimbra Collaboration Suite has a built-in utility for storing and sharing files called Briefcase. Putting files into your Briefcase makes them available to you and others that
Using Zimbra Briefcase The Zimbra Collaboration Suite has a built-in utility for storing and sharing files called Briefcase. Putting files into your Briefcase makes them available to you and others that
Content Author's Reference and Cookbook
 Sitecore CMS 6.5 Content Author's Reference and Cookbook Rev. 110621 Sitecore CMS 6.5 Content Author's Reference and Cookbook A Conceptual Overview and Practical Guide to Using Sitecore Table of Contents
Sitecore CMS 6.5 Content Author's Reference and Cookbook Rev. 110621 Sitecore CMS 6.5 Content Author's Reference and Cookbook A Conceptual Overview and Practical Guide to Using Sitecore Table of Contents
Dynamics CRM for Outlook Basics
 Dynamics CRM for Outlook Basics Microsoft Dynamics CRM April, 2015 Contents Welcome to the CRM for Outlook Basics guide... 1 Meet CRM for Outlook.... 2 A new, but comfortably familiar face................................................................
Dynamics CRM for Outlook Basics Microsoft Dynamics CRM April, 2015 Contents Welcome to the CRM for Outlook Basics guide... 1 Meet CRM for Outlook.... 2 A new, but comfortably familiar face................................................................
How to Connect to Remote Desktop & How to Use Cisco AnyConnect Secure Mobility Client Secure VPN Connection
 How to Connect to Remote Desktop & How to Use Cisco AnyConnect Secure Mobility Client Secure VPN Connection Revised 09/2014 These instructions presume that you already have the Cisco AnyConnect Secure
How to Connect to Remote Desktop & How to Use Cisco AnyConnect Secure Mobility Client Secure VPN Connection Revised 09/2014 These instructions presume that you already have the Cisco AnyConnect Secure
TLMC WORKSHOP: THESIS FORMATTING IN WORD 2010
 Table of Contents Introduction... 2 Getting Help... 2 Tips... 2 Working with Styles... 3 Applying a Style... 3 Choosing Which Styles to Use... 3 Modifying a Style... 4 Creating A New Style... 4 Setting
Table of Contents Introduction... 2 Getting Help... 2 Tips... 2 Working with Styles... 3 Applying a Style... 3 Choosing Which Styles to Use... 3 Modifying a Style... 4 Creating A New Style... 4 Setting
Upgrading from Windows XP to Windows 7
 Upgrading your PC from Windows XP to Windows 7 requires a custom installation which doesn't preserve your programs, files, or settings. It s sometimes called a clean installation for that reason. A custom
Upgrading your PC from Windows XP to Windows 7 requires a custom installation which doesn't preserve your programs, files, or settings. It s sometimes called a clean installation for that reason. A custom
Using Excel for Business Analysis: A Guide to Financial Modelling Fundamentals
 Excel 2003 Instructions Using Excel for Business Analysis: A Guide to Financial Modelling Fundamentals contains extensive instructions for using Excel 2010 and Excel for Mac 2011. There are a few instances
Excel 2003 Instructions Using Excel for Business Analysis: A Guide to Financial Modelling Fundamentals contains extensive instructions for using Excel 2010 and Excel for Mac 2011. There are a few instances
TAMUS Terminal Server Setup BPP SQL/Alva
 We have a new method of connecting to the databases that does not involve using the Texas A&M campus VPN. The new way of gaining access is via Remote Desktop software to a terminal server running here
We have a new method of connecting to the databases that does not involve using the Texas A&M campus VPN. The new way of gaining access is via Remote Desktop software to a terminal server running here
Online Sharing User Manual
 Online Sharing User Manual June 13, 2007 If discrepancies between this document and Online Sharing are discovered, please contact backupfeedback@verizon.net. Copyrights and Proprietary Notices The information
Online Sharing User Manual June 13, 2007 If discrepancies between this document and Online Sharing are discovered, please contact backupfeedback@verizon.net. Copyrights and Proprietary Notices The information
GETTING STARTED TABLE OF CONTENTS
 Windows 7 Tutorial GETTING STARTED An operating system, sometimes called an OS, is the main program the computer uses to function properly. Operating systems act as a link between you, the user, and the
Windows 7 Tutorial GETTING STARTED An operating system, sometimes called an OS, is the main program the computer uses to function properly. Operating systems act as a link between you, the user, and the
Security Guidelines for MapInfo Discovery 1.1
 Security Guidelines for MapInfo Discovery 1.1 This paper provides guidelines and detailed instructions for improving the security of your Mapinfo Discovery deployment. In this document: Overview.........................................
Security Guidelines for MapInfo Discovery 1.1 This paper provides guidelines and detailed instructions for improving the security of your Mapinfo Discovery deployment. In this document: Overview.........................................
This document is provided "as-is". Information and views expressed in this document, including URLs and other Internet Web site references, may
 This document is provided "as-is". Information and views expressed in this document, including URLs and other Internet Web site references, may change without notice. Some examples depicted herein are
This document is provided "as-is". Information and views expressed in this document, including URLs and other Internet Web site references, may change without notice. Some examples depicted herein are
Microsoft Word 2010 Training
 Microsoft Word 2010 Training Microsoft Word 102 Instructor: Debbie Minnerly Course goals Learn how to work with paragraphs. Set tabs and work with tables. Learn about styles Use the spelling and grammar
Microsoft Word 2010 Training Microsoft Word 102 Instructor: Debbie Minnerly Course goals Learn how to work with paragraphs. Set tabs and work with tables. Learn about styles Use the spelling and grammar
How to create PDF maps, pdf layer maps and pdf maps with attributes using ArcGIS. Lynne W Fielding, GISP Town of Westwood
 How to create PDF maps, pdf layer maps and pdf maps with attributes using ArcGIS Lynne W Fielding, GISP Town of Westwood PDF maps are a very handy way to share your information with the public as well
How to create PDF maps, pdf layer maps and pdf maps with attributes using ArcGIS Lynne W Fielding, GISP Town of Westwood PDF maps are a very handy way to share your information with the public as well
FirstClass FAQ's An item is missing from my FirstClass desktop
 FirstClass FAQ's An item is missing from my FirstClass desktop Deleted item: If you put a item on your desktop, you can delete it. To determine what kind of item (conference-original, conference-alias,
FirstClass FAQ's An item is missing from my FirstClass desktop Deleted item: If you put a item on your desktop, you can delete it. To determine what kind of item (conference-original, conference-alias,
Sendspace Wizard Desktop Tool Step-By-Step Guide
 Sendspace Wizard Desktop Tool Step-By-Step Guide Copyright 2007 by sendspace.com This publication is designed to provide accurate and authoritative information for users of sendspace, the easy big file
Sendspace Wizard Desktop Tool Step-By-Step Guide Copyright 2007 by sendspace.com This publication is designed to provide accurate and authoritative information for users of sendspace, the easy big file
Archiving in Microsoft Outlook. This document looks at archiving and saving space in the Microsoft Outlook email program. INFORMATION SYSTEMS SERVICES
 INFORMATION SYSTEMS SERVICES Archiving in Microsoft Outlook This document looks at archiving and saving space in the Microsoft Outlook email program. AUTHOR: ISS DATE: December 2005 EDITION: 2.0 TUT 104
INFORMATION SYSTEMS SERVICES Archiving in Microsoft Outlook This document looks at archiving and saving space in the Microsoft Outlook email program. AUTHOR: ISS DATE: December 2005 EDITION: 2.0 TUT 104
Xythos on Demand Quick Start Guide For Xythos Drive
 Xythos on Demand Quick Start Guide For Xythos Drive What is Xythos on Demand? Xythos on Demand is not your ordinary online storage or file sharing web site. Instead, it is an enterprise-class document
Xythos on Demand Quick Start Guide For Xythos Drive What is Xythos on Demand? Xythos on Demand is not your ordinary online storage or file sharing web site. Instead, it is an enterprise-class document
Backing Up and Deleting Files
 CHAPTER 5 Backing Up and Deleting Files Video files can be copied from the hard disk to external storage media, such as CD-R, DVD, MO, or ZIP drives. Video files saved on the hard disk can be easily deleted
CHAPTER 5 Backing Up and Deleting Files Video files can be copied from the hard disk to external storage media, such as CD-R, DVD, MO, or ZIP drives. Video files saved on the hard disk can be easily deleted
Upgrading from Windows XP to Windows 7
 We highly recommend that you print this tutorial. Your PC will restart during the Windows 7 installation process, so having a printed copy will help you follow the steps if you're unable to return to this
We highly recommend that you print this tutorial. Your PC will restart during the Windows 7 installation process, so having a printed copy will help you follow the steps if you're unable to return to this
Statgraphics Getting started
 Statgraphics Getting started The aim of this exercise is to introduce you to some of the basic features of the Statgraphics software. Starting Statgraphics 1. Log in to your PC, using the usual procedure
Statgraphics Getting started The aim of this exercise is to introduce you to some of the basic features of the Statgraphics software. Starting Statgraphics 1. Log in to your PC, using the usual procedure
QuickBooks 2010 Installation Guide
 QuickBooks 2010 Installation Guide This article provides instructions for installing QuickBooks 2010 on a single computer and in a network environment. QuickBooks Elements Several elements are involved
QuickBooks 2010 Installation Guide This article provides instructions for installing QuickBooks 2010 on a single computer and in a network environment. QuickBooks Elements Several elements are involved
OUTLOOK WEB APP (OWA): MAIL
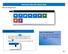 Office 365 Navigation Pane: Navigating in Office 365 Click the App Launcher and then choose the application (i.e. Outlook, Calendar, People, etc.). To modify your personal account settings, click the Logon
Office 365 Navigation Pane: Navigating in Office 365 Click the App Launcher and then choose the application (i.e. Outlook, Calendar, People, etc.). To modify your personal account settings, click the Logon
