Verification Plus Hygiene 6
|
|
|
- Evelyn Fisher
- 9 years ago
- Views:
Transcription
1 Verification Plus Hygiene 6 WSDL: Product Web Page: Description: Verification with Hygiene combines our state of the art Verification algorithms with Hygiene algorithms to allow our customers to detect and avoid known or potentially dangerous addresses or domains. Note: In this document you will notice that some status codes are labeled as potentially dangerous. This label is a result of the Hygiene component of our processing. Caution should be used when ing to addresses labeled as potentially dangerous. Please see the section below on Hygiene Results for more information. Required License Information: The LicenseInfo parameter in our Web services provides the authentication credentials to allow the user to invoke the web service. If you are currently unregistered with StrikeIron, use your address in the UnregisteredUser field. If you are registered with StrikeIron, use the UserID and Password associated with your StrikeIron account in the UserID and Password fields. Alternatively, you can also use your license key obtained from My StrikeIron with the password blank. LicenseInfo Field: UnregisteredUser Input Address: LicenseInfo Field: RegisteredUser Input UserID: Password: License Subscription Information Output LicenseStatusCode: This field returns a numeric code indicating the StrikeIron license action taken as a result of invoking this operation from the User ID and Password used for input. Valid license codes are, 1, and 2. For example, a valid User ID and Password returns the code with a corresponding LicenseStatus value of Valid license key. LicenseStatus: This field returns the status of the StrikeIron User ID and Password corresponding to the LicenseStatusCode. LicenseActionCode: This field returns a numeric code indicating the StrikeIron license action taken as a result of invoking this operation. GetRemainingHits returns the code 5 with a corresponding LicenseAction value of Get remaining hits. LicenseAction: This field returns the license action taken as a result of invoking this operation from the User ID and Password used corresponding to the LicenseActionCode. RemainingHits: This field returns the number of hits against the StrikeIron license key used when invoking this operation. Amount: This field returns the number of hits used from the StrikeIron User ID provided to invoke this operation. [email protected] [email protected] Password1 Valid license key Decremented hit count 2 Verification with Hygiene Page 1
2 Available Operations: Verify GetReasonCodes GetStatusCodesForMethod GetStatusCodes GetServiceInfo GetRemainingHits Operation: Verify Input Type the address you would like to verify. Required. Timeout: Enter the amount of time, in seconds you would like the service to continue searching for the address. Amount of time must be between 1 and 9 seconds. Required. OptionalSourceId: Optional Id returned with result as SourceIdentifier [email protected] 1 Source1 Operation: Verify Output (ServiceStatus) StatusNbr: This field returns a number referring to the status of this request. (See GetStatusCodes) StatusDescription: This field returns the description of the status number. (See GetStatusCodes) 2 Valid Operation: Verify Output (ServiceResult) Reason: Code: Reason code is associated with a Reason Description and is a subset of a Status Number and Description to further describe the response of the request. Reason: Description: Reason Description will describe the Response of the Request further and is a subset of a Status Number and Description. SourceIdentifier: value input in OptionalSourceId parameter This field returns the address you entered. LocalPart: This field returns the local part of the address. DomainPart: This field returns the domain name. IronStandardCertifiedTimestamp: This field returns the date and the time that the address was checked against real-time data DomainKnowledge Key Value pairs of domain information Key: Value: AddressKnowledge Key Value pairs of address information Key: Value: Hygiene Result: result of the Hygiene routine Net Protect the Domain Protected by a third party Net Protected By Third party protecting the domain 21 Mailbox Confirmed Source1 [email protected] johndoe strikeiron.com T13:23:5.437 Disposable true Cached true Safe US true AppRiver Verification with Hygiene Page 2
3 Operation: GetReasonCodes Input Note: The only input needed for this operation is the LicenseInfo data. This operation displays a list of the Reason Codes for the Verify () method that display in the ReasonCode and ReasonDescription fields. (No input required) Operation: GetReasonCodes Output (ServiceStatus) StatusNbr: This field returns a number referring to the status of this request. (See GetStatusCodes) StatusDescription: This field returns the description of the status number. (See GetStatusCodes) 2 Found Operation: GetReasonCodes Output (ServiceResult) Reason Code Reason Description 21 Mailbox Confirmed 22 User Account Confirmed 23 Mailbox Confirmed but Full 211 Server Will Accept 212 Unable to Verify At This Time 221 Timeout Too Short 222 Server Not Responding 223 Server Deferred 224 Server Throttled 225 Server Actively Rejected 226 Server Connection Lost 31 Symbol 32 Bad Domain in Syntax 33 Bad LocalPart Syntax 34 Domain Not Found 35 Not a Valid Mail Domain 36 Mail Domain is Non-Responsive 37 Mailbox Rejected 311 Trap Domain 41 is Required 42 Timeout must be greater than Verification with Hygiene Page 3
4 Operation: GetStatusCodesForMethod Input *MethodName: Input a method name to obtain a list of the Status Codes for that method that display in the StatusNbr and StatusDescription fields. Input options are: CheckForCellPhone, GetStatusCodesForMethod, GetStatusCodes, GetServiceInfo, and GetRemainingHits. Verify Operation: GetStatusCodesForMethod Output (ServiceStatus) StatusNbr: This field returns a number referring to the status of this request. (See GetStatusCodes) StatusDescription: This field returns the description of the status number. (See GetStatusCodes) 2 Found Operation: GetStatusCodesForMethod Output (ServiceResult) 2 Valid 21 Domain Confirmed 22 Analytics in Progress 25 Valid. Potentially Dangerous. 26 Domain Confirmed. Potentially Dangerous. 27 Analytics in Progress Potentially Dangerous. 3 Not Valid. 31 Not Verified. 4 Invalid Input. 5 Internal Error. Verification with Hygiene Page 4
5 Operation: GetStatusCodes Input Note: The only input needed for this operation is the LicenseInfo data. This operation displays a list of the Status Codes for the Web service that display in the StatusNbr and StatusDescription fields. (No input required) Operation: GetStatusCodes Output (ServiceStatus) StatusNbr: This field returns a number referring to the status of this request. (See GetStatusCodes) StatusDescription: This field returns the description of the status number. (See GetStatusCodes) 2 Found Operation: GetStatusCodes Output (MethodStatusRecord) MethodName: Verify 2 Valid 21 Domain Confirmed 22 Analytics in Progress 25 Valid Potentially Dangerous. 26 Domain Confirmed. Potentially Dangerous. 27 Analytics in Progress Potentially Dangerous. 3 Not Valid. 31 Not Verified. 4 Invalid Input. 5 Internal Error. MethodName: GetReasonCode 2 Found MethodName: GetStatusCodesForMethod 2 Found 3 Not Found 4 Invalid Method Name 5 Internal Error MethodName: GetStatusCodes 2 Found 3 Not Found 5 Internal Error MethodName: GetServiceInfo 2 Found 3 Not Found 5 Internal Error Verification with Hygiene Page 5
6 Operation: GetServiceInfo Input Note: The only input needed for this operation is the LicenseInfo data. This operation displays the last time the Web service source data was updated. (No input required) Operation: GetServiceInfo Output (ServiceStatus) StatusNbr: This field returns a status number related to the operation. StatusDescription: This field returns a description of the status number. 2 Found Operation: GetServiceInfo Output (ServiceInfoRecord) InfoKey: (For future development) InfoValue: (For future development) (none) (none) Operation: GetRemainingHits Input Note: The only input needed for this operation is the LicenseInfo data. (No input required) Operation: GetRemainingHits Output (SubscriptionInfo) LicenseStatusCode: This field returns a numeric code indicating the StrikeIron license action taken as a result of invoking this operation from the User ID and Password used for input. Valid license codes are, 1, and 2. For example, a valid User ID and Password returns the code with a corresponding LicenseStatus value of Valid license key. LicenseStatus: This field returns the status of the StrikeIron User ID and Password corresponding to the LicenseStatusCode. LicenseActionCode: This field returns a numeric code indicating the StrikeIron license action taken as a result of invoking this operation. GetRemainingHits returns the code 5 with a corresponding LicenseAction value of Get remaining hits. LicenseAction: This field returns the license action taken as a result of invoking this operation from the User ID and Password used corresponding to the LicenseActionCode. RemainingHits: This field returns the number of hits against the StrikeIron User ID and Password used when invoking this operation. Amount: This field returns the number of hits used from the StrikeIron User ID provided to invoke this operation. Valid license key Decremented hit count 2 GetRemainingHitsResponse: This field only returns subscription information. Verification with Hygiene Page 6
7 What is Analytics is Process? How do I handle this return code? Analytics in Process (AIP) is returned when a definitive Verification result cannot be reached and we believe further processing could determine a definitive result. When you receive this return code the StrikeIron infrastructure is continuing to attempt to resolve your submission. By calling the interface a second time (after a time delay) a definitive result may be available. One common reason for receiving this return code is that the timeout value you have specified is too short for the specified domain. For example, based on domain knowledge we expect gmail.com domains to take several seconds to reply. If you specified a timeout value less than our experience shows is possible, we will return AIP immediately instead of waiting for your call to time out. Another common reason for receiving this return code is that the target domain is a Grey List server. Grey listing is an attempt to discourage spam. Generally this means that a given server will refuse connections from other servers the first time they try to connect. After some time frame (this is server specific and may span a minute or two to twenty minutes or more) if the same server retries the connection it will be allowed. When you receive AIP our process will continue to attempt to resolve the address thus satisfying a grey list server. Verification with Hygiene Page 7
8 What are the Key Value Pairs and their values? The Key Value Pairs returned as part of the verification result allow us to provide more information for certain addresses / domains. These values are NOT an enumerated type and StrikeIron reserves the right to add additional information. Code that is written to process these Key Value Pairs should accommodate this fact. The following Key Value Pairs are currently being returned: Key Type Key Key Value Description DomainKnowledge Disposable True Domain is known to provide disposable addresses Potentially Vulgar True Domain portion of address is potentially vulgar or offensive AddressKnowledge Possible Correction Domain suggestion The domain suggestion could be used to replace the current domain information in this address. Note that all best practices should be observed prior to using the combination of the suggested domain and the local portion of the address as an actual address. Role-Based True The address is commonly associated with a role instead of a specific user Potentially Vulgar True The local part of this address is potentially vulgar or offensive Possible Disposable True Local part of the address follows known patterns of disposable addresses for the specified domain Cached True This result was returned from the StrikeIron result cache. Note that the IronStandardCertifiedTimeSt Verification with Hygiene Page 8
9 What do the various Hygiene Results mean? Safe US - this address is based in the US and is safe. Safe International - this address is based internationally and is safe. Invalid - this address has been determined to be invalid by the hygiene processing. The hygiene process determines an address / domain to be invalid based on information like a domain being parked. The domain may have resources and indicate that s are valid, but s to this domain are unlikely to be received by a real person. Spam Trap - this address / domain has been determined to be a spam trap or honey pot by the hygiene processing. ing these addresses may result in damage to your reputation. Mole - this address / domain shows historical evidence of being associated with submissions to spam tracking services. Former Trap - this address / domain has been previously identified as a spam trap, but at this time would be considered safe if the process did not consider historical evidence. Seed - seed addresses are third party oversight addresses specifically used for monitoring resources, many times for deliverability monitoring. Also included in this category are any litigious addresses, those who seed their address for the sole purpose of litigation. Habitual complainers, those who have an extremely high rate of spam complaints are included in this category as well. Pattern Match - this status uses typical key words, phrases, or patterns that are used for trap purposes. Also included in this category are role based addresses that typically are not delivered to a specific person such as info, support or sales. Unknown - this address / domain did not result in a specific hygiene result. The most common cause of this return value is a timeout during hygiene processing. Verification with Hygiene Page 9
10 What is Net Protect and what do the various codes mean? A Net Protected domain uses a third party service or appliance to filter and detect spam . The rules for determining what is considered as spam by these networks could vary widely. The following codes identify which service or appliance is monitoring a given network: AppRiver Barracuda Google/Postini-McAfeeASAP.com Ironport NAI-McAfee Outblaze Securence Symantec-BrightMail Symantec- MessageLabs SymantecMail Invalument ZeroSpam.ca RBLSMTPD CommTouch CloudMark Government, Military,.edu,.us Red Condor SaaS MaySoft SpamSentinel SaaS WebSense SaaS Trend Micro SaaS Verification with Hygiene Page 1
How To Validate A Phone Number On A Cell Phone On A Network With A Cellphone On A Sim Sims.Com (For A Sims) On A Pc Or Cell Phone (For An Ipad) On An Ipa (For Free
 Global Phone Validation Version 1. WSDL: http://ws.strikeiron.com/strikeiron/globalphonevalidation1?wsdl Product Page: http://www.strikeiron.com/product-list/phone/phone-number-validation/ Description:
Global Phone Validation Version 1. WSDL: http://ws.strikeiron.com/strikeiron/globalphonevalidation1?wsdl Product Page: http://www.strikeiron.com/product-list/phone/phone-number-validation/ Description:
Reverse Phone and Address Lookup Version 1.0.0
 Reverse Phone and Address Lookup Version 1.0.0 WSDL: http://ws.strikeiron.com/reversephoneaddresslookup?wsdl Product Web Page: http://www.strikeiron.com/catalog/productdetail.aspx?pv=1.0.0&pn=reverse+phone+and+address+lookup
Reverse Phone and Address Lookup Version 1.0.0 WSDL: http://ws.strikeiron.com/reversephoneaddresslookup?wsdl Product Web Page: http://www.strikeiron.com/catalog/productdetail.aspx?pv=1.0.0&pn=reverse+phone+and+address+lookup
SCORECARD EMAIL MARKETING. Find Out How Much You Are Really Getting Out of Your Email Marketing
 EMAIL MARKETING SCORECARD Find Out How Much You Are Really Getting Out of Your Email Marketing This guide is designed to help you self-assess your email sending activities. There are two ways to render
EMAIL MARKETING SCORECARD Find Out How Much You Are Really Getting Out of Your Email Marketing This guide is designed to help you self-assess your email sending activities. There are two ways to render
5 tips to improve your email database. An Experian Data Quality white paper
 5 tips to improve your email database An Experian Data Quality white paper While many marketers spend significant time and effort optimizing content and debating the timing of each campaign, marketers
5 tips to improve your email database An Experian Data Quality white paper While many marketers spend significant time and effort optimizing content and debating the timing of each campaign, marketers
Email Validation. for Improved Deliverability & Marketing Results
 Email Validation for Improved Deliverability & Marketing Results Table of Contents: Overview...Page 2 Mailing to bad emails reduces inbox delivery and sender reputation...page 2 Improving reputation and
Email Validation for Improved Deliverability & Marketing Results Table of Contents: Overview...Page 2 Mailing to bad emails reduces inbox delivery and sender reputation...page 2 Improving reputation and
Configuring CSS Remote Access Methods
 CHAPTER 11 Configuring CSS Remote Access Methods This chapter describes how to configure the Secure Shell Daemon (SSH), Remote Authentication Dial-In User Service (RADIUS), and the Terminal Access Controller
CHAPTER 11 Configuring CSS Remote Access Methods This chapter describes how to configure the Secure Shell Daemon (SSH), Remote Authentication Dial-In User Service (RADIUS), and the Terminal Access Controller
SOPHOS PureMessage Anti Spam Program
 SOPHOS PureMessage Anti Spam Program The following FAQ s should help clarify some questions you might have about Villanova s new anti spam quarantining program. If your question is not answered below,
SOPHOS PureMessage Anti Spam Program The following FAQ s should help clarify some questions you might have about Villanova s new anti spam quarantining program. If your question is not answered below,
Service for checking whether an email is operative or not. Validate email ids in your databases.
 MailStatus API Service for checking whether an email is operative or not. Validate email ids in your databases. Overview Lleida.net MailStatus API allows you to consult the validity of an email address.
MailStatus API Service for checking whether an email is operative or not. Validate email ids in your databases. Overview Lleida.net MailStatus API allows you to consult the validity of an email address.
How to configure your email client
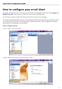 How to configure your email client This guide will teach you how to set up your email client. In this guide we will cover both Outlook and Windows Live mail, which are two of the major email clients used
How to configure your email client This guide will teach you how to set up your email client. In this guide we will cover both Outlook and Windows Live mail, which are two of the major email clients used
How To Ensure Your Email Is Delivered
 Everything You Need to Know About Delivering Email through Your Web Application SECTION 1 The Most Important Fact about Email: Delivery is Never Guaranteed Email is the backbone of the social web, making
Everything You Need to Know About Delivering Email through Your Web Application SECTION 1 The Most Important Fact about Email: Delivery is Never Guaranteed Email is the backbone of the social web, making
More Details About Your Spam Digest & Dashboard
 TABLE OF CONTENTS The Spam Digest What is the Spam Digest? What do I do with the Spam Digest? How do I view a message listed in the Spam Digest list? How do I release a message from the Spam Digest? How
TABLE OF CONTENTS The Spam Digest What is the Spam Digest? What do I do with the Spam Digest? How do I view a message listed in the Spam Digest list? How do I release a message from the Spam Digest? How
Deliverability Best Practices by Tamara Gielen
 Deliverability Best Practices by Tamara Gielen Hello, my name is Tamara Gielen Blogger Community manager Speaker Independent consultant Trainer Based in Belgium 2010 Tamara Gielen BVBA all rights reserved
Deliverability Best Practices by Tamara Gielen Hello, my name is Tamara Gielen Blogger Community manager Speaker Independent consultant Trainer Based in Belgium 2010 Tamara Gielen BVBA all rights reserved
Email Reputation Metrics Troubleshooter. Share it!
 Email Reputation Metrics Troubleshooter page: 1 Email Reputation Metrics Troubleshooter Written By Dale Langley Dale has been working with clients to improve their email deliverability and response rates,
Email Reputation Metrics Troubleshooter page: 1 Email Reputation Metrics Troubleshooter Written By Dale Langley Dale has been working with clients to improve their email deliverability and response rates,
WHITEPAPER. SendGrid Deliverability Guide V2. Everything You Need to Know About Delivering Email through Your Web Application
 WHITEPAPER SendGrid Deliverability Guide V2 Everything You Need to Know About Delivering Email through Your Web Application The Most Important Fact about Email: Delivery is Never Guaranteed Email is the
WHITEPAPER SendGrid Deliverability Guide V2 Everything You Need to Know About Delivering Email through Your Web Application The Most Important Fact about Email: Delivery is Never Guaranteed Email is the
SMTP Status Codes & SMTP Error Codes Reference
 & SMTP Error Codes Reference There comes a time in the life of a Computer Consultant where, one day, he/she will have to deal with email server problems. It is inevitable. Sometimes these problems will
& SMTP Error Codes Reference There comes a time in the life of a Computer Consultant where, one day, he/she will have to deal with email server problems. It is inevitable. Sometimes these problems will
How To Filter Email From A Spam Filter
 Spam Filtering A WORD TO THE WISE WHITE PAPER BY LAURA ATKINS, CO- FOUNDER 2 Introduction Spam filtering is a catch- all term that describes the steps that happen to an email between a sender and a receiver
Spam Filtering A WORD TO THE WISE WHITE PAPER BY LAURA ATKINS, CO- FOUNDER 2 Introduction Spam filtering is a catch- all term that describes the steps that happen to an email between a sender and a receiver
Frequently Asked Questions
 Frequently Asked Questions Table of Contents DNS Settings... 3 MX record... 3 SPF record... 3 Configuring Outbound... 3 Smart host configuration for Exchange 2003... 3 Smart host configuration for Exchange
Frequently Asked Questions Table of Contents DNS Settings... 3 MX record... 3 SPF record... 3 Configuring Outbound... 3 Smart host configuration for Exchange 2003... 3 Smart host configuration for Exchange
PureMessage for Microsoft Exchange Help. Product version: 4.0
 PureMessage for Microsoft Exchange Help Product version: 4.0 Document date: July 2013 Contents 1 About PureMessage for Microsoft Exchange...3 2 Key concepts...4 3 Administration console...7 4 Monitoring...9
PureMessage for Microsoft Exchange Help Product version: 4.0 Document date: July 2013 Contents 1 About PureMessage for Microsoft Exchange...3 2 Key concepts...4 3 Administration console...7 4 Monitoring...9
MCH Channel_e Email Best Practices for Marketers
 MCH Channel_e Email Best Practices for Marketers Best Practices for Marketers Communicating with your prospects and customers through email is a popular channel that provides almost immediate response.
MCH Channel_e Email Best Practices for Marketers Best Practices for Marketers Communicating with your prospects and customers through email is a popular channel that provides almost immediate response.
HOW TO VALIDATE EMAILS THROUGH API USING ADVANCED EMAIL VERIFIER
 HOW TO VALIDATE EMAILS THROUGH API USING ADVANCED EMAIL VERIFIER Introduction Bpsocks.com has partnered with worldwide leader in email marketing and SEO applications vendor; Glocksoft.com to provide an
HOW TO VALIDATE EMAILS THROUGH API USING ADVANCED EMAIL VERIFIER Introduction Bpsocks.com has partnered with worldwide leader in email marketing and SEO applications vendor; Glocksoft.com to provide an
Smart Card Authentication Client. Administrator's Guide
 Smart Card Authentication Client Administrator's Guide April 2013 www.lexmark.com Contents 2 Contents Overview...3 Configuring Smart Card Authentication Client...4 Configuring printer settings for use
Smart Card Authentication Client Administrator's Guide April 2013 www.lexmark.com Contents 2 Contents Overview...3 Configuring Smart Card Authentication Client...4 Configuring printer settings for use
Reputation Monitor User Guide
 August 18, 2015 Return Path, Inc. Table of Contents What is Reputation Monitor... 3 How Reputation Monitor Works... 4 What is a Sender Score... 5 How is a Sender Score Calculated... 5 Reputation Measures
August 18, 2015 Return Path, Inc. Table of Contents What is Reputation Monitor... 3 How Reputation Monitor Works... 4 What is a Sender Score... 5 How is a Sender Score Calculated... 5 Reputation Measures
Webmail Friends & Exceptions Guide
 Webmail Friends & Exceptions Guide Add email addresses to the Exceptions List and the Friends List in your Webmail account to ensure you receive email messages from family, friends, and other important
Webmail Friends & Exceptions Guide Add email addresses to the Exceptions List and the Friends List in your Webmail account to ensure you receive email messages from family, friends, and other important
Improve Email Deliverability: Tactics for Handling Complaints and Boosting Reputation. Sponsored by
 Improve Email Deliverability: Tactics for Handling Complaints and Boosting Reputation Sponsored by Introductions Adam T. Sutton, Senior Reporter MarketingSherpa / MECLABS Primary Research @AdamTSutton
Improve Email Deliverability: Tactics for Handling Complaints and Boosting Reputation Sponsored by Introductions Adam T. Sutton, Senior Reporter MarketingSherpa / MECLABS Primary Research @AdamTSutton
STILETTO 2 Wi-Fi & Hotspot Troubleshooting Guide
 STILETTO 2 Wi-Fi & Hotspot Troubleshooting Guide 1/14 Overview... 3 SIRIUS INTERNET RADIO MODE... 3 1. Q: What is SIRIUS Internet Radio mode?... 3 2. Q: What does the SL2 display when I go into Internet
STILETTO 2 Wi-Fi & Hotspot Troubleshooting Guide 1/14 Overview... 3 SIRIUS INTERNET RADIO MODE... 3 1. Q: What is SIRIUS Internet Radio mode?... 3 2. Q: What does the SL2 display when I go into Internet
Borderware MXtreme. Secure Email Gateway QuickStart Guide. Copyright 2005 CRYPTOCard Corporation All Rights Reserved
 Borderware MXtreme Secure Email Gateway QuickStart Guide Copyright 2005 CRYPTOCard Corporation All Rights Reserved http://www.cryptocard.com Overview MXtreme is a hardened appliance with a highly robust
Borderware MXtreme Secure Email Gateway QuickStart Guide Copyright 2005 CRYPTOCard Corporation All Rights Reserved http://www.cryptocard.com Overview MXtreme is a hardened appliance with a highly robust
Swift Email Verifier API Client MANUAL
 Swift Email Verifier API Java Client- User Manual Swift Email Verifier API Client MANUAL Why use SEV API Client SEV API Client is a simple java tool which is highly optimized to validate and scrub emails
Swift Email Verifier API Java Client- User Manual Swift Email Verifier API Client MANUAL Why use SEV API Client SEV API Client is a simple java tool which is highly optimized to validate and scrub emails
NODE4 SERVICE DESK SYSTEM
 NODE4 SERVICE DESK SYSTEM KNOWLEDGE BASE ARTICLE INTERNAL USE ONLY NODE4 LIMITED 24/04/2015 ADD A POP, IMAP OR OFFICE 365 ACCOUNT TO OUTLOOK USING CUSTOM SETTINGS If you re setting up Outlook for the first
NODE4 SERVICE DESK SYSTEM KNOWLEDGE BASE ARTICLE INTERNAL USE ONLY NODE4 LIMITED 24/04/2015 ADD A POP, IMAP OR OFFICE 365 ACCOUNT TO OUTLOOK USING CUSTOM SETTINGS If you re setting up Outlook for the first
Implementing MDaemon as an Email Security Gateway to Exchange Server
 Implementing MDaemon as an Email Security Gateway to Exchange Server Introduction MDaemon is widely deployed as a very effective antispam/antivirus gateway to Exchange. For optimum performance, we recommend
Implementing MDaemon as an Email Security Gateway to Exchange Server Introduction MDaemon is widely deployed as a very effective antispam/antivirus gateway to Exchange. For optimum performance, we recommend
one Managing your PBX Administrator ACCESSING YOUR PBX ACCOUNT CHECKING ACCOUNT ACTIVITY
 one Managing your PBX Administrator ACCESSING YOUR PBX ACCOUNT Navigate to https://portal.priorityonenet.com/ and log in to the PriorityOne portal account. If you would like your web browser to keep you
one Managing your PBX Administrator ACCESSING YOUR PBX ACCOUNT Navigate to https://portal.priorityonenet.com/ and log in to the PriorityOne portal account. If you would like your web browser to keep you
CommuniGator. Avoiding spam filters
 CommuniGator Avoiding spam filters How to dodge the junk box; deliverability and avoiding spam filters Email marketers often have more to battle with than just creating an email and sending it to their
CommuniGator Avoiding spam filters How to dodge the junk box; deliverability and avoiding spam filters Email marketers often have more to battle with than just creating an email and sending it to their
DST EMAIL. Product FAQs. Thank you for using our products. DST UK www.dstsystems.co.uk
 EFFECTIVE PERSONALISED PRINT AND E-COMMUNICATION SOLUTIONS DESIGNED WITH YOU IN MIND DSTSYSTEMS.CO.UK DST EMAIL Product FAQs version 01 Thank you for using our products. DST UK www.dstsystems.co.uk DST
EFFECTIVE PERSONALISED PRINT AND E-COMMUNICATION SOLUTIONS DESIGNED WITH YOU IN MIND DSTSYSTEMS.CO.UK DST EMAIL Product FAQs version 01 Thank you for using our products. DST UK www.dstsystems.co.uk DST
USING MYWEBSQL FIGURE 1: FIRST AUTHENTICATION LAYER (ENTER YOUR REGULAR SIMMONS USERNAME AND PASSWORD)
 USING MYWEBSQL MyWebSQL is a database web administration tool that will be used during LIS 458 & CS 333. This document will provide the basic steps for you to become familiar with the application. 1. To
USING MYWEBSQL MyWebSQL is a database web administration tool that will be used during LIS 458 & CS 333. This document will provide the basic steps for you to become familiar with the application. 1. To
A White Paper. VerticalResponse, Email Delivery and You A Handy Guide. VerticalResponse,Inc. 501 2nd Street, Suite 700 San Francisco, CA 94107
 A White Paper VerticalResponse, Email Delivery and You Delivering email seems pretty straightforward, right? You upload a mailing list, create an email, hit send, and then mighty wizards transport that
A White Paper VerticalResponse, Email Delivery and You Delivering email seems pretty straightforward, right? You upload a mailing list, create an email, hit send, and then mighty wizards transport that
Smart Card Authentication. Administrator's Guide
 Smart Card Authentication Administrator's Guide October 2012 www.lexmark.com Contents 2 Contents Overview...4 Configuring the applications...5 Configuring printer settings for use with the applications...5
Smart Card Authentication Administrator's Guide October 2012 www.lexmark.com Contents 2 Contents Overview...4 Configuring the applications...5 Configuring printer settings for use with the applications...5
Frequently Asked Questions for New Electric Mail Administrators 1 Domain Setup/Administration
 Frequently Asked Questions for New Electric Mail Administrators 1 Domain Setup/Administration 1.1 How do I access the records of the domain(s) that I administer? To access the domains you administer, you
Frequently Asked Questions for New Electric Mail Administrators 1 Domain Setup/Administration 1.1 How do I access the records of the domain(s) that I administer? To access the domains you administer, you
Email: [email protected] Toll Free: 1-866-716-2040 International: 1-646-506-9354
 1. Check your Welcome e-mail for login credentials for the control panel. 2. Using the login details in the welcome e-mail; login at https://cp.hostallapps.com Adding Domain: 1. On the Home Page of the
1. Check your Welcome e-mail for login credentials for the control panel. 2. Using the login details in the welcome e-mail; login at https://cp.hostallapps.com Adding Domain: 1. On the Home Page of the
Contact for all enquiries Phone: +61 2 8006 9730. Email: [email protected]. Page 2. RecordPoint Release Notes V3.8 for SharePoint 2013
 Release Notes V3.8 Notice This document contains confidential and trade secret information of RecordPoint Software ( RPS ). RecordPoint Software has prepared this document for use solely with RecordPoint.
Release Notes V3.8 Notice This document contains confidential and trade secret information of RecordPoint Software ( RPS ). RecordPoint Software has prepared this document for use solely with RecordPoint.
PureMessage for Microsoft Exchange Help. Product version: 3.1
 PureMessage for Microsoft Exchange Help Product version: 3.1 Document date: June 2015 Contents 1 About PureMessage for Microsoft Exchange...4 2 Key concepts...5 2.1 Key concepts overview...5 2.2 Inbound,
PureMessage for Microsoft Exchange Help Product version: 3.1 Document date: June 2015 Contents 1 About PureMessage for Microsoft Exchange...4 2 Key concepts...5 2.1 Key concepts overview...5 2.2 Inbound,
Collax Mail Server. Howto. This howto describes the setup of a Collax server as mail server.
 Collax Mail Server Howto This howto describes the setup of a Collax server as mail server. Requirements Collax Business Server Collax Groupware Suite Collax Platform Server including Collax Communication
Collax Mail Server Howto This howto describes the setup of a Collax server as mail server. Requirements Collax Business Server Collax Groupware Suite Collax Platform Server including Collax Communication
How to Engage Your Contacts Using Email Marketing
 How to Engage Your Contacts Using Email Marketing We will be starting at 2:00 pm EST. Use the Question Pane in GoToWebinar to Ask Questions! CHAT WITH US: 1 Using the question pane shown above 2 Use the
How to Engage Your Contacts Using Email Marketing We will be starting at 2:00 pm EST. Use the Question Pane in GoToWebinar to Ask Questions! CHAT WITH US: 1 Using the question pane shown above 2 Use the
e-filing Secure Web Service User Manual
 e-filing Secure Web Service User Manual Page1 CONTENTS 1 BULK ITR... 6 2 BULK PAN VERIFICATION... 9 3 GET ITR-V BY TOKEN NUMBER... 13 4 GET ITR-V BY ACKNOWLEDGMENT NUMBER... 16 5 GET RETURN STATUS... 19
e-filing Secure Web Service User Manual Page1 CONTENTS 1 BULK ITR... 6 2 BULK PAN VERIFICATION... 9 3 GET ITR-V BY TOKEN NUMBER... 13 4 GET ITR-V BY ACKNOWLEDGMENT NUMBER... 16 5 GET RETURN STATUS... 19
Cisco EXAM - 300-207. Implementing Cisco Threat Control Solutions (SITCS) Buy Full Product. http://www.examskey.com/300-207.html
 Cisco EXAM - 300-207 Implementing Cisco Threat Control Solutions (SITCS) Buy Full Product http://www.examskey.com/300-207.html Examskey Cisco 300-207 exam demo product is here for you to test the quality
Cisco EXAM - 300-207 Implementing Cisco Threat Control Solutions (SITCS) Buy Full Product http://www.examskey.com/300-207.html Examskey Cisco 300-207 exam demo product is here for you to test the quality
INUVIKA OVD SUPPORT SUPPORT SYSTEM GUIDE. Mathieu Schires Version 1.1 Published 28/04/2015
 INUVIKA OVD SUPPORT SUPPORT SYSTEM GUIDE Mathieu Schires Version 1.1 Published 28/04/2015 This document describes how to use the Inuvika Support System for reporting support incidents related to Inuvika
INUVIKA OVD SUPPORT SUPPORT SYSTEM GUIDE Mathieu Schires Version 1.1 Published 28/04/2015 This document describes how to use the Inuvika Support System for reporting support incidents related to Inuvika
Knowledge Guide: Deliverability. Your Reputation Holds the Key to Deliverability. virtualroi May 2009. by: Return Path
 Knowledge Guide: Deliverability Your Reputation Holds the Key to Deliverability virtualroi May 2009 by: Return Path Your Reputation Holds the Key to Deliverability Twenty percent of legitimate email never
Knowledge Guide: Deliverability Your Reputation Holds the Key to Deliverability virtualroi May 2009 by: Return Path Your Reputation Holds the Key to Deliverability Twenty percent of legitimate email never
Email Deliverability. Best Practices for Getting to the Inbox
 Email Deliverability Best Practices for Getting to the Inbox About Real Magnet Real Magnet develops digital marketing technologies with a focus on Email and Marketing Automation. Its full-featured platform
Email Deliverability Best Practices for Getting to the Inbox About Real Magnet Real Magnet develops digital marketing technologies with a focus on Email and Marketing Automation. Its full-featured platform
DMA s E-Mail Authentication Requirement: FAQs and Best Practices
 DMA s E-Mail Authentication Requirement: FAQs and Best Practices DMA s Board of Directors approved a new guideline for ethical marketing practices in October 2005, with the new member requirement going
DMA s E-Mail Authentication Requirement: FAQs and Best Practices DMA s Board of Directors approved a new guideline for ethical marketing practices in October 2005, with the new member requirement going
SYNAQ Securemail Technical Requirements and System Limits
 SYNAQ Securemail Technical Requirements and System Limits OVERVIEW OUR COMMITMENT TO SECURITY AND STABLE SERVICE DELIVERY While the SYNAQ Acceptable Usage Policy ( AUP, viewable here), service definitions,
SYNAQ Securemail Technical Requirements and System Limits OVERVIEW OUR COMMITMENT TO SECURITY AND STABLE SERVICE DELIVERY While the SYNAQ Acceptable Usage Policy ( AUP, viewable here), service definitions,
Avaya Modular Messaging Microsoft Outlook Client Release 5.2
 Avaya Modular Messaging Microsoft Outlook Client Release 5.2 Important: Instructions in this guide are applicable only if your message store is the Avaya Message Storage Server (MSS) or Microsoft Exchange
Avaya Modular Messaging Microsoft Outlook Client Release 5.2 Important: Instructions in this guide are applicable only if your message store is the Avaya Message Storage Server (MSS) or Microsoft Exchange
eprism Email Security Appliance 6.0 Intercept Anti-Spam Quick Start Guide
 eprism Email Security Appliance 6.0 Intercept Anti-Spam Quick Start Guide This guide is designed to help the administrator configure the eprism Intercept Anti-Spam engine to provide a strong spam protection
eprism Email Security Appliance 6.0 Intercept Anti-Spam Quick Start Guide This guide is designed to help the administrator configure the eprism Intercept Anti-Spam engine to provide a strong spam protection
Cybersecurity Health Check At A Glance
 This cybersecurity health check provides a quick view of compliance gaps and is not intended to replace a professional HIPAA Security Risk Analysis. Failing to have more than five security measures not
This cybersecurity health check provides a quick view of compliance gaps and is not intended to replace a professional HIPAA Security Risk Analysis. Failing to have more than five security measures not
Fast, flexible & efficient email delivery software
 by Fast, flexible & efficient email delivery software Built on top of industry-standard AMQP message broker. Send millions of emails per hour. Why MailerQ? No Cloud Fast Flexible Many email solutions require
by Fast, flexible & efficient email delivery software Built on top of industry-standard AMQP message broker. Send millions of emails per hour. Why MailerQ? No Cloud Fast Flexible Many email solutions require
SMTPSWITCH MAILER V6 FEATURES
 SMTPSWITCH MAILER V6 FEATURES 22 Powerful Features Packed in a Single Email Marketing/Bulk Mailing Program! Easy and Advanced WYSIWYG/HTML Editing SMTPSwitch Mailer has a powerful built-in WYSIWYG editor
SMTPSWITCH MAILER V6 FEATURES 22 Powerful Features Packed in a Single Email Marketing/Bulk Mailing Program! Easy and Advanced WYSIWYG/HTML Editing SMTPSwitch Mailer has a powerful built-in WYSIWYG editor
Chapter 1: What are SPAM traps?... 2. The logic behind SPAM traps... 2. Definitions of the types of SPAM traps... 3
 Table of Contents Chapter 1: What are SPAM traps?... 2 The logic behind SPAM traps... 2 Definitions of the types of SPAM traps... 3 Chapter 2: How do SPAM traps end up in your database?... 5 The risk SPAM
Table of Contents Chapter 1: What are SPAM traps?... 2 The logic behind SPAM traps... 2 Definitions of the types of SPAM traps... 3 Chapter 2: How do SPAM traps end up in your database?... 5 The risk SPAM
Quick Start for Network Agent. 5-Step Quick Start. What is Network Agent?
 What is Network Agent? Websense Network Agent software monitors all internet traffic on the machines that you assign to it. Network Agent filters HTTP traffic and more than 70 other popular internet protocols,
What is Network Agent? Websense Network Agent software monitors all internet traffic on the machines that you assign to it. Network Agent filters HTTP traffic and more than 70 other popular internet protocols,
Cannot send Autosupport e-mail, error message: Unknown User
 Cannot send Autosupport e-mail, error message: Unknown User Symptoms Unable to send Autosupport e-mails and the following error message is reported: asup.smtp.fail http://now.netapp.com/eservice/ems?emsaction=details&eventid=200573&software=ontap&em
Cannot send Autosupport e-mail, error message: Unknown User Symptoms Unable to send Autosupport e-mails and the following error message is reported: asup.smtp.fail http://now.netapp.com/eservice/ems?emsaction=details&eventid=200573&software=ontap&em
Appendix. Web Command Error Codes. Web Command Error Codes
 Appendix Web Command s Error codes marked with * are received in responses from the FTP server, and then returned as the result of FTP command execution. -501 Incorrect parameter type -502 Error getting
Appendix Web Command s Error codes marked with * are received in responses from the FTP server, and then returned as the result of FTP command execution. -501 Incorrect parameter type -502 Error getting
Email Encryption Procedures
 Email Encryption Procedures Contents: I. Compose an Encrypted Message II. What Your Recipients Will Receive a. Registering a NewAccount b. Logging into a Created Account c. Reading and Replying III. Reading
Email Encryption Procedures Contents: I. Compose an Encrypted Message II. What Your Recipients Will Receive a. Registering a NewAccount b. Logging into a Created Account c. Reading and Replying III. Reading
Using Barracuda Spam Firewall
 Using Barracuda Spam Firewall Creating your Barracuda account Your Barracuda account has been created for you if you are a current Hartwick College student, staff or faculty member. Setting Your Password.
Using Barracuda Spam Firewall Creating your Barracuda account Your Barracuda account has been created for you if you are a current Hartwick College student, staff or faculty member. Setting Your Password.
API Guide v 1.6 14/11/2013
 1 About netcore netcore is a leader in digital communications space. The mission of the company is to help clients communicate effectively for marketing and business needs. We help organizations in the
1 About netcore netcore is a leader in digital communications space. The mission of the company is to help clients communicate effectively for marketing and business needs. We help organizations in the
Dell OpenManage Mobile Version 1.4 User s Guide (Android)
 Dell OpenManage Mobile Version 1.4 User s Guide (Android) Notes, cautions, and warnings NOTE: A NOTE indicates important information that helps you make better use of your computer. CAUTION: A CAUTION
Dell OpenManage Mobile Version 1.4 User s Guide (Android) Notes, cautions, and warnings NOTE: A NOTE indicates important information that helps you make better use of your computer. CAUTION: A CAUTION
How To Use The Rss Feeder On Firstclass (First Class) And First Class (Firstclass) For Free
 RSS Feeder - Administrator Guide for OpenText Social Workplace and FirstClass Werner de Jong, Senior Solutions Architect 8 July 2011 Abstract This document is an administrator s guide to the installation
RSS Feeder - Administrator Guide for OpenText Social Workplace and FirstClass Werner de Jong, Senior Solutions Architect 8 July 2011 Abstract This document is an administrator s guide to the installation
Dell KACE K1000 Management Appliance. Service Desk Administrator Guide. Release 5.3. Revision Date: May 13, 2011
 Dell KACE K1000 Management Appliance Service Desk Administrator Guide Release 5.3 Revision Date: May 13, 2011 2004-2011 Dell, Inc. All rights reserved. Information concerning third-party copyrights and
Dell KACE K1000 Management Appliance Service Desk Administrator Guide Release 5.3 Revision Date: May 13, 2011 2004-2011 Dell, Inc. All rights reserved. Information concerning third-party copyrights and
User Documentation. Administrator Manual. www.proposalsoftware.com
 User Documentation Administrator Manual Proposal Software 1140 US Highway 287, Suite 400-102 Broomfield, CO 80020 USA Tel: 203.604.6597 www.proposalsoftware.com Table of Contents Open the WebPro Viewer...
User Documentation Administrator Manual Proposal Software 1140 US Highway 287, Suite 400-102 Broomfield, CO 80020 USA Tel: 203.604.6597 www.proposalsoftware.com Table of Contents Open the WebPro Viewer...
Comprehensive Email Filtering: Barracuda Spam Firewall Safeguards Legitimate Email
 : Barracuda Firewall Safeguards Legitimate Email Email has undoubtedly become a valued communications tool among organizations worldwide. With frequent virus attacks and the alarming influx of spam, email
: Barracuda Firewall Safeguards Legitimate Email Email has undoubtedly become a valued communications tool among organizations worldwide. With frequent virus attacks and the alarming influx of spam, email
B a r r a c u d a M e s s a g e A r c h i v e r O u t l o o k A d d - I n U s e r G u i d e. V e r si on 3. 1
 B a r r a c u d a M e s s a g e A r c h i v e r O u t l o o k A d d - I n U s e r G u i d e V e r si on 3. 1 Barracuda Networks, Inc. 3175 S. Winchester Blvd Campbell, CA 95008 http://www.barracuda.com
B a r r a c u d a M e s s a g e A r c h i v e r O u t l o o k A d d - I n U s e r G u i d e V e r si on 3. 1 Barracuda Networks, Inc. 3175 S. Winchester Blvd Campbell, CA 95008 http://www.barracuda.com
eservice Portal Overview
 eservice Portal Overview About this Guide Purpose The eservice Portal Overview Guide provides a differences overview of Support Online to eservice Portal migration. The new eservice portal provides the
eservice Portal Overview About this Guide Purpose The eservice Portal Overview Guide provides a differences overview of Support Online to eservice Portal migration. The new eservice portal provides the
Managing Your Emails Lists: Bounces, Holds, Unsubscribes
 This document covers what you need to know keep your email list healthy with low rates of bounced emails and unsubscribes. You should be able to use this documentation to assist you in understanding mailing
This document covers what you need to know keep your email list healthy with low rates of bounced emails and unsubscribes. You should be able to use this documentation to assist you in understanding mailing
Guardian Digital Secure Mail Suite Quick Start Guide
 Guardian Digital Secure Mail Suite Quick Start Guide Copyright c 2004 Guardian Digital, Inc. Contents 1 Introduction 1 2 Contacting Guardian Digital 2 3 Purpose of This Document 3 3.1 Terminology...............................
Guardian Digital Secure Mail Suite Quick Start Guide Copyright c 2004 Guardian Digital, Inc. Contents 1 Introduction 1 2 Contacting Guardian Digital 2 3 Purpose of This Document 3 3.1 Terminology...............................
Service Launch Guide (US Customer) SEG Filtering
 Secure Network Gateway / Secure E-Mail Gateway (SEG) Service Service Launch Guide Service Launch Guide (US Customer) SEG Filtering Overview The following information will guide you through the steps required
Secure Network Gateway / Secure E-Mail Gateway (SEG) Service Service Launch Guide Service Launch Guide (US Customer) SEG Filtering Overview The following information will guide you through the steps required
The IVE also supports using the following additional features with CA certificates:
 1 A CA certificate allows you to control access to realms, roles, and resource policies based on certificates or certificate attributes. For example, you may specify that users must present a valid client-side
1 A CA certificate allows you to control access to realms, roles, and resource policies based on certificates or certificate attributes. For example, you may specify that users must present a valid client-side
ExchangeDefender. Understanding the tool that can save and secure your business
 ExchangeDefender Understanding the tool that can save and secure your business OVERVIEW The purpose of this Startup Guide is to familiarize you with ExchangeDefender's Exchange and SharePoint Hosting.
ExchangeDefender Understanding the tool that can save and secure your business OVERVIEW The purpose of this Startup Guide is to familiarize you with ExchangeDefender's Exchange and SharePoint Hosting.
Email Quick-Start Guide
 For TradeMark Media s email system Thank you for choosing TradeMark Media for your email hosting. You ve made a wise choice. TradeMark Media offers comprehensive spam and virus protection, POP3 and WebMail
For TradeMark Media s email system Thank you for choosing TradeMark Media for your email hosting. You ve made a wise choice. TradeMark Media offers comprehensive spam and virus protection, POP3 and WebMail
Reporting - Bounce rates
 Reporting - Bounce rates An email that doesn't get delivered, is referred to as bounced. The bounce rate refers to the percentage of email addresses in your contact list that didn t receive your message
Reporting - Bounce rates An email that doesn't get delivered, is referred to as bounced. The bounce rate refers to the percentage of email addresses in your contact list that didn t receive your message
DOSarrest Security Services (DSS) Version 4.0
 DOSarrest Security Services (DSS) Version 4.0 DOSarrest DSS User Guide The DSS is the main customer portal where customers can view and manipulate traffic statistics from a wide variety of variables that
DOSarrest Security Services (DSS) Version 4.0 DOSarrest DSS User Guide The DSS is the main customer portal where customers can view and manipulate traffic statistics from a wide variety of variables that
IDAM Most frequently encountered messages / known issues document
 IDAM Most frequently encountered messages / known issues document Amendment History Version Date Comment By 0.1 20-Dec-2012 Initial version Madhusudan Kappaganthula SharePoint location https://wss2.bp.com/dct/functions/teams/diessl/idam/operational%20processes/forms/allitems.aspx?
IDAM Most frequently encountered messages / known issues document Amendment History Version Date Comment By 0.1 20-Dec-2012 Initial version Madhusudan Kappaganthula SharePoint location https://wss2.bp.com/dct/functions/teams/diessl/idam/operational%20processes/forms/allitems.aspx?
Instructions How to use and send the PIT (Physician in Training) Permit Application Spreadsheet
 Instructions How to use and send the PIT (Physician in Training) Permit Application Spreadsheet 1. Download and save the TMB PIT Permit Application Submission Spreadsheet. a. Double click on the attachment
Instructions How to use and send the PIT (Physician in Training) Permit Application Spreadsheet 1. Download and save the TMB PIT Permit Application Submission Spreadsheet. a. Double click on the attachment
SIP Messages. 180 Ringing The UA receiving the INVITE is trying to alert the user. This response MAY be used to initiate local ringback.
 SIP Messages 100 Trying This response indicates that the request has been received by the next-hop server and that some unspecified action is being taken on behalf of this call (for example, a database
SIP Messages 100 Trying This response indicates that the request has been received by the next-hop server and that some unspecified action is being taken on behalf of this call (for example, a database
Using Email Security to Protect Against Phishing, Spam, and Targeted Attacks: Combining Features for Higher Education
 White Paper Using Email Security to Protect Against Phishing, Spam, and Targeted Attacks: Combining Features for Higher Education Online criminals are constantly looking for new ways to reach their targets
White Paper Using Email Security to Protect Against Phishing, Spam, and Targeted Attacks: Combining Features for Higher Education Online criminals are constantly looking for new ways to reach their targets
Troubleshooting IMAP Clients and ViewMail for Outlook in Cisco Unity Connection 8.x
 CHAPTER 17 Troubleshooting IMAP Clients and ViewMail for Outlook in Cisco Unity Connection 8.x See the following sections for problems that can occur in IMAP clients and in Cisco Unity Connection ViewMail
CHAPTER 17 Troubleshooting IMAP Clients and ViewMail for Outlook in Cisco Unity Connection 8.x See the following sections for problems that can occur in IMAP clients and in Cisco Unity Connection ViewMail
Guideline for E-mail Services
 Guideline for E-mail Services Under the Policy on Information Technology, the Vice-President and Provost is authorized to establish guidelines for information technology services at the University of Toronto.
Guideline for E-mail Services Under the Policy on Information Technology, the Vice-President and Provost is authorized to establish guidelines for information technology services at the University of Toronto.
Chapter 6 Updating Software Images and Configuration Files
 Chapter 6 Updating Software Images and Configuration Files This chapter describes how to copy and save configuration files and software image files. Downloading and Uploading a Software Image on a TFTP
Chapter 6 Updating Software Images and Configuration Files This chapter describes how to copy and save configuration files and software image files. Downloading and Uploading a Software Image on a TFTP
MAC OS X 10.5 Mail Setup
 MAC OS X 10.5 Mail Setup Automatically Configuring Mail Manually Configuring Mail Changing Mail Settings Automatically Configuring Mail Mail in Mac OS X 10.5 includes the automatically set up account option.
MAC OS X 10.5 Mail Setup Automatically Configuring Mail Manually Configuring Mail Changing Mail Settings Automatically Configuring Mail Mail in Mac OS X 10.5 includes the automatically set up account option.
Managing Users and Identity Stores
 CHAPTER 8 Overview ACS manages your network devices and other ACS clients by using the ACS network resource repositories and identity stores. When a host connects to the network through ACS requesting
CHAPTER 8 Overview ACS manages your network devices and other ACS clients by using the ACS network resource repositories and identity stores. When a host connects to the network through ACS requesting
Absolute Software Topup Tax (Year 2 onwards)
 Absolute Software Topup Tax (Year 2 onwards) Getting Started After having renewed the package online or with the Sales team you would have had a receipted invoice and a set of registration codes emailed
Absolute Software Topup Tax (Year 2 onwards) Getting Started After having renewed the package online or with the Sales team you would have had a receipted invoice and a set of registration codes emailed
OBiTALK Portal Device Management
 OBiTALK Portal Device Management By using the OBiTALK portal, you can easily manage features, control device access privileges and add up to two (2) BYOD (Bring Your Own Device) SIP or Google Voice service
OBiTALK Portal Device Management By using the OBiTALK portal, you can easily manage features, control device access privileges and add up to two (2) BYOD (Bring Your Own Device) SIP or Google Voice service
Cloud Services ADM. Agent Deployment Guide
 Cloud Services ADM Agent Deployment Guide 10/15/2014 CONTENTS System Requirements... 1 Hardware Requirements... 1 Installation... 2 SQL Connection... 4 AD Mgmt Agent... 5 MMC... 7 Service... 8 License
Cloud Services ADM Agent Deployment Guide 10/15/2014 CONTENTS System Requirements... 1 Hardware Requirements... 1 Installation... 2 SQL Connection... 4 AD Mgmt Agent... 5 MMC... 7 Service... 8 License
Contents CHAPTER 1 IMail Utilities
 Contents CHAPTER 1 IMail Utilities CHAPTER 2 Collaboration Duplicate Entry Remover... 2 CHAPTER 3 Disk Space Usage Reporter... 3 CHAPTER 4 Forward Finder... 4 CHAPTER 5 IMAP Copy Utility... 5 About IMAP
Contents CHAPTER 1 IMail Utilities CHAPTER 2 Collaboration Duplicate Entry Remover... 2 CHAPTER 3 Disk Space Usage Reporter... 3 CHAPTER 4 Forward Finder... 4 CHAPTER 5 IMAP Copy Utility... 5 About IMAP
Eiteasy s Enterprise Email Filter
 Eiteasy s Enterprise Email Filter Eiteasy s Enterprise Email Filter acts as a shield for companies, small and large, who are being inundated with Spam, viruses and other malevolent outside threats. Spammer
Eiteasy s Enterprise Email Filter Eiteasy s Enterprise Email Filter acts as a shield for companies, small and large, who are being inundated with Spam, viruses and other malevolent outside threats. Spammer
Dell KACE K1000 System Management Appliance Version 5.4. Service Desk Administrator Guide
 Dell KACE K1000 System Management Appliance Version 5.4 Service Desk Administrator Guide October 2012 2004-2012 Dell Inc. All rights reserved. Reproduction of these materials in any manner whatsoever without
Dell KACE K1000 System Management Appliance Version 5.4 Service Desk Administrator Guide October 2012 2004-2012 Dell Inc. All rights reserved. Reproduction of these materials in any manner whatsoever without
