Online Banking Payment Website
|
|
|
- Esther Warner
- 9 years ago
- Views:
Transcription
1 Consultation Paper Online Banking Payment Website In the field of e-commerce, various payment processes have been established. During the last year, the so-called "online transfer has been added. This allows clients to pay the purchase price by means of an online banking transfer involving a so-called online payment service provider. In order to ensure online banking security for the bank s and the client s sake, the present approach sets out a technical payment process solution where the client does not have to disclose to the online service provider their online banking identification data - such as user ID and PIN necessary for initialising the "online transfer"; instead, clients only have to disclose such data directly to their bank. Hereinafter, this model will be labelled "Online Banking Payment Website (OBPW). For several years, the principle of the OBPW portal has been practised successfully by online payment service providers in Europe.
2 - 2-1 Model blueprint This approach is based on an enhancement of the [existing] online banking user interface enabling direct online banking communication between the bank and the client; as a result, authorised online payment service providers will be given special access to the online banking payment interface (OBPW portal) of participating banks so that these online payment service providers can render their services. Basically, the OBPW portal is an online banking website that has been [optimised or, morover,] streamlined for online payment purposes. Any bank participating in online payment services undertakes to offer such a login site or, moreover online banking interface on the internet. As a result, registered online payment service providers may access the OBPW Service of participating banks through a standardised interface which will allow them to submit online payments (cf. fig. Figure 1). Händler 1 Online- Bezahl-. Dienst x ZOB Online - - Bank A Kunde Händler 2 Online- Bezahl- Dienst y ZOB - Bank B Händler 3 Online- Bezahl- Dienst z ZOB - Bank C Sphäre der Bank
3 - 3 - Figure 1: Layer model "Online Banking Payment Website Benefits of this approach: The online banking login data such as client ID and PIN will only be exchanged between the client and the bank in the secure environment [domain]. Third parties will not gain any access to this confidential client data. Online payment service providers will not receive any information on clients account status or their transaction data; instead, they will merely be informed whether the payment order was accepted. Usually, this information will be sufficient for finalising the purchase transaction. Depending on the respective agreement between the online payment service provider and the bank, the bank may include further information in this confirmation (for instance a payment guarantee). Provided they will receive an execution confirmation upon the submission of a payment order, there will be no need for online payment service providers to engineer sophisticated systems for assessing the execution likelihood (scoring / credit rating approaches). Online payment service providers no longer have to analyse any client data. As a result, they can dispense with the data protection measures which they would otherwise have to adopt in such a scenario. Especially for smaller providers, such an approach lowers the barriers to market entry. The user interfaces to the OBPW services are subject to a standard interface specification (cf. chapter 3 Fehler! Verweisquelle konnte nicht gefunden werden.)promulgated by the German Banking Industry Committee (GBIC). This greatly facilitates market access for online payment service providers. They only have to implement one single interface thus receiving access to the OBPW portals of all participating banks in a standardised manner. Clients alertness regarding phishing and Trojan attacks will remain undiminished; this is due to the fact that clients can still be instructed to
4 - 4 - only enter their login data on familiar (URL, certificate) websites belonging to their banks. Due to the fact that the online payment service provider is not directly involved in the client s payment authorisation process, it is only the client and their bank who will have to agree a secure protocol for handling identification data. This also resolves a number of liability issues. The principle of the OBPW portal is separate from the security protocols offered by banks thus allowing the use of both TAN based and also signature based approaches. The certification protocol used by the payment service provider in order to prove compliance with the requirements for processing security relevant data is being simplified (cf. chapter 4 Fehler! Verweisquelle konnte nicht gefunden werden.). The use of standardised interfaces renders the automated processing of websites (screenscraping) redundant. This helps to prevent customer complaints as well as transmission errors which occasionally occurred in the past.
5 - 5-2 Technical model The flowchart below illustrates an OBPW transfer: Figure 2: OBPW transaction flowchart 1. The client purchases something on an e-commerce website. The online merchant forwards the online purchase invoice data to the online payment service provider. Clients enter their name or, moreover, their bank s ID on the website of the payment service provider (step 1). 2. Based on the OBPW directory, the online payment service provider works out which bank is in charge (step 2). 3. The online payment service providers prove their identity to the client s bank using the provider ID issued as part of the GBIC certification process along with any further identification data that may have been agreed; through the client s bank, the online payment service provider accesses the respective OBPW service, transfers the payment order data and obtains the URL of the OBPW portal (step 3).
6 The client will be forwarded by the payment service provider to the OBPW interface of their bank. Based on the familiar features (website layout, address (URL), security certificate) the client will be able to recognise that they are on their bank s OBPW portal, i.e. in the credit institution's [internet] domain (step 4). 5. On the OBPW portal, clients enter their login data and identification data for online banking purposes. Once they have logged on, in order to ascertain that everything is correct, the client will be shown the payment transaction data. During the next step, the client authorises the transaction by entering the authentication data generated by means of the respective security protocol or, respectively, approves it by using their signature card (step 5). 6. Through the OBPW service, the bank sends a payment order acceptance confirmation to the online payment service provider. This message includes the status of the payment order. Provided further message elements have been agreed with the online payment service provider, the message of the bank will contain a confirmation of the payment order execution or a payment guarantee by the bank. The online banking transaction is thus completed (step 6). 7. After leaving the OBPW portal, the client will be redirected to the site of the online payment service provider or of the merchant. If applicable, the online payment service provider will forward the bank s payment message to the online merchant (step 7).
7 - 7-3 Interface specification As has been mentioned above, the user interfaces to the individual bank s OBPW portals are being standardised by the German Banking Industry Committee (GBIC). Hence, an online payment service provider will only have to implement this interface once. The following XML schema file contains a proposal for the interface specifications of the individual communication steps between the online payment service provider and banks OBPW service presented under Figure 2. The structure of the data listed hereunder will still be fine-tuned with a view to technical and database engineering details. The draft XML schema below will provide an online payment service provider with a complete list of all banks and savings banks that offer an OBPW service. The list contains the requisite access information, e.g. particularly the URL of the OBPW service. 4 Certification requirements Due to the fact that, under the OBPW model, the online payment service provider neither receives nor processes any security relevant data (e.g. banking login data or identification data), the online payment service provider will only have to meet moderate security requirements. However, in order to participate in the OBPW process, online payment service providers will still have to undergo a registration process. This is necessary because it has to be ensured that the online payment service integrates banks OBPW portals correctly and that their own identity authentication is tamper proof. Upon proof of their registration, the online payment service provider will receive a provider ID and a personal ID allowing the online service providers to
8 - 8 - prove their identity towards the OBPW service. Based on this registration, subsequently a participation agreement may be concluded between the online payment service provider and the bank or aggregators on the basis of which additional services, e.g. payment guarantees, may be agreed.
Deltek Touch Time & Expense for GovCon. User Guide for Triumph
 Deltek Touch Time & Expense for GovCon User Guide for Triumph November 25, 2014 While Deltek has attempted to verify that the information in this document is accurate and complete, some typographical or
Deltek Touch Time & Expense for GovCon User Guide for Triumph November 25, 2014 While Deltek has attempted to verify that the information in this document is accurate and complete, some typographical or
Swedbank Payment Portal Implementation Overview
 Swedbank Payment Portal Implementation Overview Product: Hosted Pages Region: Baltics September 2015 Version 1.0 Contents 1. Introduction 1 1.1. Audience 1 1.2. Hosted Page Service Features 1 1.3. Key
Swedbank Payment Portal Implementation Overview Product: Hosted Pages Region: Baltics September 2015 Version 1.0 Contents 1. Introduction 1 1.1. Audience 1 1.2. Hosted Page Service Features 1 1.3. Key
Explanation of MasterCard SecureCode & Verified by Visa
 Explanation of MasterCard SecureCode & Verified by Visa Version: 2.2 Year: 2012 Author: Buckaroo Online Payment Services Online acceptance of MasterCard SecureCode and Verified by Visa Unfortunately, online
Explanation of MasterCard SecureCode & Verified by Visa Version: 2.2 Year: 2012 Author: Buckaroo Online Payment Services Online acceptance of MasterCard SecureCode and Verified by Visa Unfortunately, online
HelpDesk Product sheet
 Product sheet Artologik is the tool for those who are looking for an easy to use but powerful program for support and ticket handling. With Artologik, it is easy to handle entered into the database, anyone
Product sheet Artologik is the tool for those who are looking for an easy to use but powerful program for support and ticket handling. With Artologik, it is easy to handle entered into the database, anyone
Microsoft Exchange Online from BT. Service Description (Shared Platform)
 Microsoft Exchange Online from BT Version 5.1 January 2004 Confidentiality statement All information contained in this document is provided in confidence for the sole purpose of adjudication, and shall
Microsoft Exchange Online from BT Version 5.1 January 2004 Confidentiality statement All information contained in this document is provided in confidence for the sole purpose of adjudication, and shall
Gateway Apps - Security Summary SECURITY SUMMARY
 Gateway Apps - Security Summary SECURITY SUMMARY 27/02/2015 Document Status Title Harmony Security summary Author(s) Yabing Li Version V1.0 Status draft Change Record Date Author Version Change reference
Gateway Apps - Security Summary SECURITY SUMMARY 27/02/2015 Document Status Title Harmony Security summary Author(s) Yabing Li Version V1.0 Status draft Change Record Date Author Version Change reference
Man-in-the-Middle Attacks against the chiptan comfort Online Banking System
 Man-in-the-Middle Attacks against the chiptan comfort Online Banking System RedTeam Pentesting GmbH November 23, 2009 ChipTAN comfort is a new system which is supposed to securely authorise online banking
Man-in-the-Middle Attacks against the chiptan comfort Online Banking System RedTeam Pentesting GmbH November 23, 2009 ChipTAN comfort is a new system which is supposed to securely authorise online banking
HKUST CA. Certification Practice Statement
 HKUST CA Certification Practice Statement IN SUPPORT OF HKUST CA CERTIFICATION SERVICES Version : 2.1 Date : 12 November 2003 Prepared by : Information Technology Services Center Hong Kong University of
HKUST CA Certification Practice Statement IN SUPPORT OF HKUST CA CERTIFICATION SERVICES Version : 2.1 Date : 12 November 2003 Prepared by : Information Technology Services Center Hong Kong University of
FAQs Electronic residence permit
 FAQs Electronic residence permit General 1) When was the electronic residence permit introduced? Since 1 September 2011, foreigners in Germany have been issued with the new electronic residence permit
FAQs Electronic residence permit General 1) When was the electronic residence permit introduced? Since 1 September 2011, foreigners in Germany have been issued with the new electronic residence permit
KAZAKHSTAN STOCK EXCHANGE
 KAZAKHSTAN STOCK EXCHANGE A p p r o v e d by Kazakhstan Stock Exchange Board of Directors decision (minutes No. 15 of November 6, 2002) Effective from November 7, 2002 N O T I C E Rules have been translated
KAZAKHSTAN STOCK EXCHANGE A p p r o v e d by Kazakhstan Stock Exchange Board of Directors decision (minutes No. 15 of November 6, 2002) Effective from November 7, 2002 N O T I C E Rules have been translated
Cryptography and Network Security Chapter 1
 Cryptography and Network Security Chapter 1 Acknowledgments Lecture slides are based on the slides created by Lawrie Brown Chapter 1 Introduction The art of war teaches us to rely not on the likelihood
Cryptography and Network Security Chapter 1 Acknowledgments Lecture slides are based on the slides created by Lawrie Brown Chapter 1 Introduction The art of war teaches us to rely not on the likelihood
E-business. E-business at KSB: Take off with Innovative Solutions.
 E-business E-business at KSB: Take off with Innovative Solutions. KSB your partner in e-business. For almost 140 years, we have been offering comprehensive service and cost-effective, all-in solutions
E-business E-business at KSB: Take off with Innovative Solutions. KSB your partner in e-business. For almost 140 years, we have been offering comprehensive service and cost-effective, all-in solutions
FedEx Web Services Certification Guide
 FedEx Web Services Certification Guide May 2016 Payment You must remit payment in accordance with the FedEx Service Guide, tariff, service agreement or other terms or instructions provided to you by FedEx
FedEx Web Services Certification Guide May 2016 Payment You must remit payment in accordance with the FedEx Service Guide, tariff, service agreement or other terms or instructions provided to you by FedEx
eservice Portal Overview
 eservice Portal Overview About this Guide Purpose The eservice Portal Overview Guide provides a differences overview of Support Online to eservice Portal migration. The new eservice portal provides the
eservice Portal Overview About this Guide Purpose The eservice Portal Overview Guide provides a differences overview of Support Online to eservice Portal migration. The new eservice portal provides the
Federal law on certification services in the area of the electronic signature
 Law on the electronic signature 94.0 Notice This English translation has no official character. The only authentic texts are the German, French and Italian versions published in the Official Compendium
Law on the electronic signature 94.0 Notice This English translation has no official character. The only authentic texts are the German, French and Italian versions published in the Official Compendium
SMS SERVICE PROVISION
 SMS SERVICE PROVISION Terms and Conditions and Privacy Policy Version 2.01 Aug 2015 Page 1 Contents TERMS & CONDITIONS... 3 Registration... 3 Your Personal Information... 3 Our Obligations to SMS Service
SMS SERVICE PROVISION Terms and Conditions and Privacy Policy Version 2.01 Aug 2015 Page 1 Contents TERMS & CONDITIONS... 3 Registration... 3 Your Personal Information... 3 Our Obligations to SMS Service
Business-to-Business EIPP: Presentment Models, Part 1 By: The Council for Electronic Billing and Payment
 Business-to-Business EIPP: Presentment Models, Part 1 By: The Council for Electronic Billing and Payment Abstract In the short time since the release of the first web browser in 1993, the Internet has
Business-to-Business EIPP: Presentment Models, Part 1 By: The Council for Electronic Billing and Payment Abstract In the short time since the release of the first web browser in 1993, the Internet has
Authorize.net modules for oscommerce Online Merchant.
 Authorize.net Authorize.net modules for oscommerce Online Merchant. Chapters oscommerce Online Merchant v2.3 Copyright Copyright (c) 2014 oscommerce. All rights reserved. Content may be reproduced for
Authorize.net Authorize.net modules for oscommerce Online Merchant. Chapters oscommerce Online Merchant v2.3 Copyright Copyright (c) 2014 oscommerce. All rights reserved. Content may be reproduced for
CONDITIONS FOR ELECTRONIC DATA EXCHANGE VIA ČSOB MULTICASH 24 SERVICE
 This translation of the Conditions for Electronic Data Exchange via ČSOB MultiCash 24 Service from Slovak to English language is for information purposes only and does not represent a binding version.
This translation of the Conditions for Electronic Data Exchange via ČSOB MultiCash 24 Service from Slovak to English language is for information purposes only and does not represent a binding version.
How to Request Access to the Commerce Contract Management System
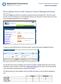 How to Request Access to the Commerce Contract Management System (one-time only) Once you ve logged into SAW, you can add your selected services by clicking on the Click here to add services link. This
How to Request Access to the Commerce Contract Management System (one-time only) Once you ve logged into SAW, you can add your selected services by clicking on the Click here to add services link. This
Instructions for users of the EU Emissions Trading Scheme Union Registry System. Registration and ECAS Account
 Instructions for users of the EU Emissions Trading Scheme Union Registry System Registration and ECAS Account These instructions are addressed to persons who will require access to accounts held on the
Instructions for users of the EU Emissions Trading Scheme Union Registry System Registration and ECAS Account These instructions are addressed to persons who will require access to accounts held on the
OpenHRE Security Architecture. (DRAFT v0.5)
 OpenHRE Security Architecture (DRAFT v0.5) Table of Contents Introduction -----------------------------------------------------------------------------------------------------------------------2 Assumptions----------------------------------------------------------------------------------------------------------------------2
OpenHRE Security Architecture (DRAFT v0.5) Table of Contents Introduction -----------------------------------------------------------------------------------------------------------------------2 Assumptions----------------------------------------------------------------------------------------------------------------------2
Internet Authentication Procedure Guide
 Internet Authentication Procedure Guide Authenticating cardholders successfully V10.0 Released May 2012 Software Version: Internet Authentication Protocol COPYRIGHT NOTICE No part of this publication may
Internet Authentication Procedure Guide Authenticating cardholders successfully V10.0 Released May 2012 Software Version: Internet Authentication Protocol COPYRIGHT NOTICE No part of this publication may
Interoperable Mobile Payment A Requirements-Based Architecture
 Interoperable Mobile Payment A Requirements-Based Architecture Dr. Manfred Männle Encorus Technologies GmbH; product management Payment Platform Summary: Existing payment methods like cash and debit/credit
Interoperable Mobile Payment A Requirements-Based Architecture Dr. Manfred Männle Encorus Technologies GmbH; product management Payment Platform Summary: Existing payment methods like cash and debit/credit
White Paper Secure Reverse Proxy Server and Web Application Firewall
 White Paper Secure Reverse Proxy Server and Web Application Firewall 2 Contents 3 3 4 4 8 Losing control Online accessibility means vulnerability Regain control with a central access point Strategic security
White Paper Secure Reverse Proxy Server and Web Application Firewall 2 Contents 3 3 4 4 8 Losing control Online accessibility means vulnerability Regain control with a central access point Strategic security
Business Bill Pay. Help Guide
 Business Bill Pay Help Guide TABLE OF CONTENTS PAYMENTS...3 1.1 Make Payments...3 1.2 Manage Payees...4 1.3 Manage Payments...5 1.4 Payment History...6 ADMIN TOOLS...7 4.1 Manage Users...7 4.2 Manage Bank
Business Bill Pay Help Guide TABLE OF CONTENTS PAYMENTS...3 1.1 Make Payments...3 1.2 Manage Payees...4 1.3 Manage Payments...5 1.4 Payment History...6 ADMIN TOOLS...7 4.1 Manage Users...7 4.2 Manage Bank
User guide to the EMIR 1 notifications web portal
 User guide to the EMIR 1 notifications web portal Contents 1. INTRODUCTION 2 2. Registering as a user 2 2.1 Super users 3 2.2 Adding additional counterparties 3 2.3 Adding additional users 4 2.4 Adding
User guide to the EMIR 1 notifications web portal Contents 1. INTRODUCTION 2 2. Registering as a user 2 2.1 Super users 3 2.2 Adding additional counterparties 3 2.3 Adding additional users 4 2.4 Adding
Verified Volunteers. A division of SterlingBackcheck. Privacy Policy. Last Updated: November 5, 2014
 1 Verified Volunteers A division of SterlingBackcheck Privacy Policy Last Updated: November 5, 2014 Verified Volunteers, a division of Sterling Backcheck ( Company, we, us, or our ) provide this Privacy
1 Verified Volunteers A division of SterlingBackcheck Privacy Policy Last Updated: November 5, 2014 Verified Volunteers, a division of Sterling Backcheck ( Company, we, us, or our ) provide this Privacy
UPCOMING SCHEME CHANGES
 UPCOMING SCHEME CHANGES MERCHANTS/PARTNERS/ISO COPY Payvision Ref: Payvision-Upcoming Scheme Changes (v1.0)-march 2016 1 Rights of use: COMPLYING WITH ALL APPLICABLE COPYRIGHT LAWS IS THE RESPONSABILITY
UPCOMING SCHEME CHANGES MERCHANTS/PARTNERS/ISO COPY Payvision Ref: Payvision-Upcoming Scheme Changes (v1.0)-march 2016 1 Rights of use: COMPLYING WITH ALL APPLICABLE COPYRIGHT LAWS IS THE RESPONSABILITY
GP webpay - Practical Examples
 GP webpay - Practical Examples Version: 2.0 Global Payments Europe, s.r.o. Created 8.10.2015 Last update 14.12.2015 Author Dimitrij Holovka Manager Approved by Version 2.0 Confidentiality Internal Document
GP webpay - Practical Examples Version: 2.0 Global Payments Europe, s.r.o. Created 8.10.2015 Last update 14.12.2015 Author Dimitrij Holovka Manager Approved by Version 2.0 Confidentiality Internal Document
OAuth: Where are we going?
 OAuth: Where are we going? What is OAuth? OAuth and CSRF Redirection Token Reuse OAuth Grant Types 1 OAuth v1 and v2 "OAuth 2.0 at the hand of a developer with deep understanding of web security will likely
OAuth: Where are we going? What is OAuth? OAuth and CSRF Redirection Token Reuse OAuth Grant Types 1 OAuth v1 and v2 "OAuth 2.0 at the hand of a developer with deep understanding of web security will likely
Terms and Conditions of Mobile mtransfer Service
 Terms and Conditions of Mobile mtransfer Service Art. 1. Definitions The terms and expressions used herein shall have the following meaning: 1. Merchant an entity that offers to the Customer a payment
Terms and Conditions of Mobile mtransfer Service Art. 1. Definitions The terms and expressions used herein shall have the following meaning: 1. Merchant an entity that offers to the Customer a payment
Elavon Payment Gateway Integration Guide 3D Secure
 Elavon Payment Gateway Integration Guide 3D Secure Version: v1.1 Table of Contents 1 About This Guide 3 1.1 Purpose 3 1.2 Audience 3 1.3 Prerequisites 3 1.4 Related Documents 3 2 Introduction 4 3 3D Secure
Elavon Payment Gateway Integration Guide 3D Secure Version: v1.1 Table of Contents 1 About This Guide 3 1.1 Purpose 3 1.2 Audience 3 1.3 Prerequisites 3 1.4 Related Documents 3 2 Introduction 4 3 3D Secure
HDE position on legislative package to regulate payment systems (MIF and PSD II)
 [Transparency Register No.: 31200871765-41] HDE position on legislative package to regulate payment systems (MIF and PSD II) November 2013 I. Einleitung I. Introduction The German Retail Federation HDE
[Transparency Register No.: 31200871765-41] HDE position on legislative package to regulate payment systems (MIF and PSD II) November 2013 I. Einleitung I. Introduction The German Retail Federation HDE
Information System Security
 Information System Security Chapter 1:Introduction Dr. Lo ai Tawalbeh Faculty of Information system and Technology, The Arab Academy for Banking and Financial Sciences. Jordan Chapter 1 Introduction The
Information System Security Chapter 1:Introduction Dr. Lo ai Tawalbeh Faculty of Information system and Technology, The Arab Academy for Banking and Financial Sciences. Jordan Chapter 1 Introduction The
Deutsche Bank db easynet. Secure method of use of the db easynet e-banking system
 Deutsche Bank Secure method of use of the e-banking system Introduction Deutsche Bank pays particular attention to your security. Therefore, the funds entrusted to us by our Customers are protected, using
Deutsche Bank Secure method of use of the e-banking system Introduction Deutsche Bank pays particular attention to your security. Therefore, the funds entrusted to us by our Customers are protected, using
Application Security Testing. Generic Test Strategy
 Application Security Testing Generic Test Strategy Page 2 of 8 Contents 1 Introduction 3 1.1 Purpose: 3 1.2 Application Security Testing: 3 2 Audience 3 3 Test Strategy guidelines 3 3.1 Authentication
Application Security Testing Generic Test Strategy Page 2 of 8 Contents 1 Introduction 3 1.1 Purpose: 3 1.2 Application Security Testing: 3 2 Audience 3 3 Test Strategy guidelines 3 3.1 Authentication
Server based signature service. Overview
 1(11) Server based signature service Overview Based on federated identity Swedish e-identification infrastructure 2(11) Table of contents 1 INTRODUCTION... 3 2 FUNCTIONAL... 4 3 SIGN SUPPORT SERVICE...
1(11) Server based signature service Overview Based on federated identity Swedish e-identification infrastructure 2(11) Table of contents 1 INTRODUCTION... 3 2 FUNCTIONAL... 4 3 SIGN SUPPORT SERVICE...
Registrations and Awards Online System User Guidance
 Registrations and Awards Online System User Guidance Awarding Access to HE Learners RAC Generation RACs for Access to HE courses can only be created by the Access to HE Administrator. 1. To download the
Registrations and Awards Online System User Guidance Awarding Access to HE Learners RAC Generation RACs for Access to HE courses can only be created by the Access to HE Administrator. 1. To download the
ELM Manages Identities of 4 Million Government Program Users with. Identity Server
 ELM Manages Identities of 4 Million Government Program Users with Identity Server ELM Implements Single Sign-on With WSO2 Identity Server to Streamline Administration, Improve Productivity, and Reduce
ELM Manages Identities of 4 Million Government Program Users with Identity Server ELM Implements Single Sign-on With WSO2 Identity Server to Streamline Administration, Improve Productivity, and Reduce
WEBKINCSTAR ONLINE SECURITIES TRADING - TERMS AND CONDITIONS OF USE
 WEBKINCSTAR ONLINE SECURITIES TRADING - TERMS AND CONDITIONS OF USE The Hungarian State Treasury (hereinafter: Distributor) provides general information (on its website) and executes securities trading
WEBKINCSTAR ONLINE SECURITIES TRADING - TERMS AND CONDITIONS OF USE The Hungarian State Treasury (hereinafter: Distributor) provides general information (on its website) and executes securities trading
PRIVACY POLICY. I. Introduction. II. Information We Collect
 PRIVACY POLICY school2life, Inc. ( school2life ) Privacy Policy is designed to provide clarity about the information we collect and how we use it to provide a better social gaming experience. By accepting
PRIVACY POLICY school2life, Inc. ( school2life ) Privacy Policy is designed to provide clarity about the information we collect and how we use it to provide a better social gaming experience. By accepting
CHAPTER 4 DEPLOYMENT OF ESGC-PKC IN NON-COMMERCIAL E-COMMERCE APPLICATIONS
 70 CHAPTER 4 DEPLOYMENT OF ESGC-PKC IN NON-COMMERCIAL E-COMMERCE APPLICATIONS 4.1 INTRODUCTION In this research work, a new enhanced SGC-PKC has been proposed for improving the electronic commerce and
70 CHAPTER 4 DEPLOYMENT OF ESGC-PKC IN NON-COMMERCIAL E-COMMERCE APPLICATIONS 4.1 INTRODUCTION In this research work, a new enhanced SGC-PKC has been proposed for improving the electronic commerce and
RSA SecurID Software Token Security Best Practices Guide
 RSA SecurID Software Token Security Best Practices Guide Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com. Trademarks RSA, the RSA
RSA SecurID Software Token Security Best Practices Guide Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com. Trademarks RSA, the RSA
DIGIPASS as a Service. Google Apps Integration
 DIGIPASS as a Service Google Apps Integration April 2011 Table of Contents 1. Introduction 1.1. Audience and Purpose of this Document 1.2. Available Guides 1.3. What is DIGIPASS as a Service? 1.4. About
DIGIPASS as a Service Google Apps Integration April 2011 Table of Contents 1. Introduction 1.1. Audience and Purpose of this Document 1.2. Available Guides 1.3. What is DIGIPASS as a Service? 1.4. About
Cryptography and Network Security
 Cryptography and Network Security Third Edition by William Stallings Lecture slides by Shinu Mathew John http://shinu.info/ Chapter 1 Introduction http://shinu.info/ 2 Background Information Security requirements
Cryptography and Network Security Third Edition by William Stallings Lecture slides by Shinu Mathew John http://shinu.info/ Chapter 1 Introduction http://shinu.info/ 2 Background Information Security requirements
Information Supplement: Requirement 6.6 Code Reviews and Application Firewalls Clarified
 Standard: Data Security Standard (DSS) Requirement: 6.6 Date: February 2008 Information Supplement: Requirement 6.6 Code Reviews and Application Firewalls Clarified Release date: 2008-04-15 General PCI
Standard: Data Security Standard (DSS) Requirement: 6.6 Date: February 2008 Information Supplement: Requirement 6.6 Code Reviews and Application Firewalls Clarified Release date: 2008-04-15 General PCI
PCI-DSS and Application Security Achieving PCI DSS Compliance with Seeker
 PCI-DSS and Application Security Achieving PCI DSS Compliance with Seeker www.quotium.com 1/14 Summary Abstract 3 PCI DSS Statistics 4 PCI DSS Application Security 5 How Seeker Helps You Achieve PCI DSS
PCI-DSS and Application Security Achieving PCI DSS Compliance with Seeker www.quotium.com 1/14 Summary Abstract 3 PCI DSS Statistics 4 PCI DSS Application Security 5 How Seeker Helps You Achieve PCI DSS
White Paper PalmSecure truedentity
 White Paper PalmSecure truedentity Fujitsu PalmSecure truedentity is used for mutual service and user authentication. The user's identity always remains in the possession of the user. A truedentity server
White Paper PalmSecure truedentity Fujitsu PalmSecure truedentity is used for mutual service and user authentication. The user's identity always remains in the possession of the user. A truedentity server
Privacy Policy. If you have questions or complaints regarding our Privacy Policy or practices, please see Contact Us. Introduction
 Privacy Policy This Privacy Policy will be effective from September 1 st, 2014. Please read Pelican Technologies Privacy Policy before using Pelican Technologies services because it will tell you how we
Privacy Policy This Privacy Policy will be effective from September 1 st, 2014. Please read Pelican Technologies Privacy Policy before using Pelican Technologies services because it will tell you how we
SAM Context-Based Authentication Using Juniper SA Integration Guide
 SAM Context-Based Authentication Using Juniper SA Integration Guide Revision A Copyright 2012 SafeNet, Inc. All rights reserved. All attempts have been made to make the information in this document complete
SAM Context-Based Authentication Using Juniper SA Integration Guide Revision A Copyright 2012 SafeNet, Inc. All rights reserved. All attempts have been made to make the information in this document complete
S-Doc User Guide. Instructions on using the Secure Document Online Courier with the CAAT Pension Plan. September 2012
 S-Doc User Guide Instructions on using the Secure Document Online Courier with the CAAT Pension Plan Secure solution provided by Accellion September 2012 S E C U R E C O L L A B O R A T I O N U S E R G
S-Doc User Guide Instructions on using the Secure Document Online Courier with the CAAT Pension Plan Secure solution provided by Accellion September 2012 S E C U R E C O L L A B O R A T I O N U S E R G
Fraud Detection. Configuration Guide for the Fraud Detection Module v.4.2.0. epdq 2014, All rights reserved.
 Configuration Guide for the Fraud Detection Module v.4.2.0 Table of Contents 1 What is the... Fraud Detection Module? 4 1.1 Benefits 1.2 Access 1.3 Contents... 4... 4... 4 2 Fraud detection... activation
Configuration Guide for the Fraud Detection Module v.4.2.0 Table of Contents 1 What is the... Fraud Detection Module? 4 1.1 Benefits 1.2 Access 1.3 Contents... 4... 4... 4 2 Fraud detection... activation
MERCHANT SERVICE APPLICATION
 MERCHANT SERVICE APPLICATION MERCHANT INFORMATION Merchant Name Merchant Domain Name DBA Name Business Type Merchant Currency Merchant Country Business Registration No Paid Up Capital Registered Business
MERCHANT SERVICE APPLICATION MERCHANT INFORMATION Merchant Name Merchant Domain Name DBA Name Business Type Merchant Currency Merchant Country Business Registration No Paid Up Capital Registered Business
IDENTITY INFORMATION MANAGMENT ARCHITECTURE SUMMARY Architecture and Standards Branch Office of the CIO Province of BC People Collaboration Innovation
 IDENTITY INFORMATION MANAGMENT ARCHITECTURE SUMMARY Architecture and Standards Branch Author: Creation Date: Last Updated: Version: I. Bailey May 28, 2008 March 23, 2009 0.7 Reviewed By Name Organization
IDENTITY INFORMATION MANAGMENT ARCHITECTURE SUMMARY Architecture and Standards Branch Author: Creation Date: Last Updated: Version: I. Bailey May 28, 2008 March 23, 2009 0.7 Reviewed By Name Organization
An Oracle White Paper Dec 2013. Oracle Access Management Security Token Service
 An Oracle White Paper Dec 2013 Oracle Access Management Security Token Service Disclaimer The following is intended to outline our general product direction. It is intended for information purposes only,
An Oracle White Paper Dec 2013 Oracle Access Management Security Token Service Disclaimer The following is intended to outline our general product direction. It is intended for information purposes only,
Mobility Data Marketplace The German approach for the exchange of dynamic traffic data
 Mobility Data Marketplace The German approach for the exchange of dynamic traffic data Lutz Rittershaus Federal Highway Research Institute www.easyway-its.eu History Innovation Program of the German Federal
Mobility Data Marketplace The German approach for the exchange of dynamic traffic data Lutz Rittershaus Federal Highway Research Institute www.easyway-its.eu History Innovation Program of the German Federal
MANAGED FILE TRANSFER: 10 STEPS TO SOX COMPLIANCE
 WHITE PAPER MANAGED FILE TRANSFER: 10 STEPS TO SOX COMPLIANCE 1. OVERVIEW Do you want to design a file transfer process that is secure? Or one that is compliant? Of course, the answer is both. But it s
WHITE PAPER MANAGED FILE TRANSFER: 10 STEPS TO SOX COMPLIANCE 1. OVERVIEW Do you want to design a file transfer process that is secure? Or one that is compliant? Of course, the answer is both. But it s
Access Control Policy. Document Status. Security Classification. Level 4 - PUBLIC. Version 1.0. Approval. Review By June 2012
 Access Control Policy Document Status Security Classification Version 1.0 Level 4 - PUBLIC Status DRAFT Approval Life 3 Years Review By June 2012 Owner Secure Research Database Analyst Retention Change
Access Control Policy Document Status Security Classification Version 1.0 Level 4 - PUBLIC Status DRAFT Approval Life 3 Years Review By June 2012 Owner Secure Research Database Analyst Retention Change
Evaluation of different Open Source Identity management Systems
 Evaluation of different Open Source Identity management Systems Ghasan Bhatti, Syed Yasir Imtiaz Linkoping s universitetet, Sweden [ghabh683, syeim642]@student.liu.se 1. Abstract Identity management systems
Evaluation of different Open Source Identity management Systems Ghasan Bhatti, Syed Yasir Imtiaz Linkoping s universitetet, Sweden [ghabh683, syeim642]@student.liu.se 1. Abstract Identity management systems
The Johns Hopkins Technology Ventures Inventor Portal How to Submit an Invention Disclosure Table of Contents
 The Johns Hopkins Technology Ventures Inventor Portal How to Submit an Invention Disclosure Table of Contents 1. Requesting an Account Page 2. 2. Logging In to the Inventor Portal Page 4. 3. Administrative
The Johns Hopkins Technology Ventures Inventor Portal How to Submit an Invention Disclosure Table of Contents 1. Requesting an Account Page 2. 2. Logging In to the Inventor Portal Page 4. 3. Administrative
Technical Guideline TR-03107-1 Electronic Identities and Trust Services in E-Government
 Technical Guideline TR-03107-1 Electronic Identities and Trust Services in E-Government Part 1: Assurance levels and mechanisms Version 1.0 This translation is informative only. The normative version is
Technical Guideline TR-03107-1 Electronic Identities and Trust Services in E-Government Part 1: Assurance levels and mechanisms Version 1.0 This translation is informative only. The normative version is
IBM Unica emessage Version 8 Release 6 February 13, 2015. User's Guide
 IBM Unica emessage Version 8 Release 6 February 13, 2015 User's Guide Note Before using this information and the product it supports, read the information in Notices on page 403. This edition applies to
IBM Unica emessage Version 8 Release 6 February 13, 2015 User's Guide Note Before using this information and the product it supports, read the information in Notices on page 403. This edition applies to
How To Protect A Web Application From Attack From A Trusted Environment
 Standard: Version: Date: Requirement: Author: PCI Data Security Standard (PCI DSS) 1.2 October 2008 6.6 PCI Security Standards Council Information Supplement: Application Reviews and Web Application Firewalls
Standard: Version: Date: Requirement: Author: PCI Data Security Standard (PCI DSS) 1.2 October 2008 6.6 PCI Security Standards Council Information Supplement: Application Reviews and Web Application Firewalls
"You" and "your" mean the account holder(s) and anyone else with authority to deposit, withdraw, or exercise control over the funds in the account.
 FIRST BANK KANSAS Information about Electronic Fund Transfers The Electronic Fund Transfer Act and Regulation E require banks to provide certain information to customers regarding electronic fund transfer
FIRST BANK KANSAS Information about Electronic Fund Transfers The Electronic Fund Transfer Act and Regulation E require banks to provide certain information to customers regarding electronic fund transfer
General Contractual Terms and Conditions of KRÁLOVOPOLSKÁ SLÉVÁRNA, s.r.o.
 General Contractual Terms and Conditions of KRÁLOVOPOLSKÁ SLÉVÁRNA, s.r.o. 1. General provisions 1.1. These terms and conditions (TC) govern the sale of products and services (hereinafter as goods ) of
General Contractual Terms and Conditions of KRÁLOVOPOLSKÁ SLÉVÁRNA, s.r.o. 1. General provisions 1.1. These terms and conditions (TC) govern the sale of products and services (hereinafter as goods ) of
Swivel Multi-factor Authentication
 Swivel Multi-factor Authentication White Paper Abstract Swivel is a flexible authentication solution that offers a wide range of authentication models. The use of the Swivel patented one-time code extraction
Swivel Multi-factor Authentication White Paper Abstract Swivel is a flexible authentication solution that offers a wide range of authentication models. The use of the Swivel patented one-time code extraction
The Gestamp Supplier Risk Management (SRM) system. Supplier Frequently Asked Questions (FAQ)
 The Gestamp Supplier Risk Management (SRM) system Supplier Frequently Asked Questions (FAQ) April 2016 2013 Contents Overview... 4 Why has Gestamp partnered with Achilles?... 4 The importance of complying
The Gestamp Supplier Risk Management (SRM) system Supplier Frequently Asked Questions (FAQ) April 2016 2013 Contents Overview... 4 Why has Gestamp partnered with Achilles?... 4 The importance of complying
Pre requisites for Digital Signature
 Pre requisites for Digital Signature Know about Digital Signature Certificate You should have a legally valid Class III digital certificate as per Indian IT Act from the licensed Certifying Authorities
Pre requisites for Digital Signature Know about Digital Signature Certificate You should have a legally valid Class III digital certificate as per Indian IT Act from the licensed Certifying Authorities
Amendments Guide for FP7 Grant Agreements
 Amendments Guide for FP7 Grant Agreements Version 10/09/2013 Disclaimer This guide is aimed at assisting beneficiaries. It is provided for information purposes only and its contents are not intended to
Amendments Guide for FP7 Grant Agreements Version 10/09/2013 Disclaimer This guide is aimed at assisting beneficiaries. It is provided for information purposes only and its contents are not intended to
Research and Implementation of Single Sign-On Mechanism for ASP Pattern *
 Research and Implementation of Single Sign-On Mechanism for ASP Pattern * Bo Li, Sheng Ge, Tian-yu Wo, and Dian-fu Ma Computer Institute, BeiHang University, PO Box 9-32 Beijing 100083 Abstract Software
Research and Implementation of Single Sign-On Mechanism for ASP Pattern * Bo Li, Sheng Ge, Tian-yu Wo, and Dian-fu Ma Computer Institute, BeiHang University, PO Box 9-32 Beijing 100083 Abstract Software
LAW ON PAYMENT SERVICES
 LAW ON PAYMENT SERVICES Part I INTRODUCTORY PROVISIONS Subject matter Article 1 This Law regulates the conditions and manner of providing payment services, electronic money, payment systems and supervision
LAW ON PAYMENT SERVICES Part I INTRODUCTORY PROVISIONS Subject matter Article 1 This Law regulates the conditions and manner of providing payment services, electronic money, payment systems and supervision
D.I.M. allows different authentication procedures, from simple e-mail confirmation to electronic ID.
 Seite 1 von 11 Distributed Identity Management The intention of Distributed Identity Management is the advancement of the electronic communication infrastructure in justice with the goal of defining open,
Seite 1 von 11 Distributed Identity Management The intention of Distributed Identity Management is the advancement of the electronic communication infrastructure in justice with the goal of defining open,
Ecommerce Setup Wizard Site Setup Wizards
 Ecommerce Setup Wizard Site Setup Wizards ecommerce Setup Wizard Before you begin this wizard you must first set up your ecommerce gateway This wizard will require information that is provided to you by
Ecommerce Setup Wizard Site Setup Wizards ecommerce Setup Wizard Before you begin this wizard you must first set up your ecommerce gateway This wizard will require information that is provided to you by
ONE SINGLE ADDRESS FOR ALL YOUR ONLINE PROCEDURES. as part of your professional activity. Business Portal
 ONE SINGLE ADDRESS FOR ALL YOUR ONLINE PROCEDURES as part of your professional activity Business Portal WHY CHOOSE MYGUICHET? MyGuichet is a secure interactive platform available on guichet.lu. It allows
ONE SINGLE ADDRESS FOR ALL YOUR ONLINE PROCEDURES as part of your professional activity Business Portal WHY CHOOSE MYGUICHET? MyGuichet is a secure interactive platform available on guichet.lu. It allows
Doxis4 InvoiceMaster Read SLX
 Automated invoice scanning and validation Doxis4 InvoiceMaster Read SLX Executive summary Doxis4 InvoiceMaster Read SLX is the complete standard solution for the automated processing of incoming invoices.
Automated invoice scanning and validation Doxis4 InvoiceMaster Read SLX Executive summary Doxis4 InvoiceMaster Read SLX is the complete standard solution for the automated processing of incoming invoices.
1. Definitions The following definitions are, both in the singular and in the plural, used in these terms and conditions payment methods Buckaroo:
 Conditions Paymenttypes Buckaroo version 7.4 01-12-2014 Page 1 of 7 Specific Terms and Conditions per Payment Method This document contains the terms and conditions that Buckaroo and Payment Service Owners
Conditions Paymenttypes Buckaroo version 7.4 01-12-2014 Page 1 of 7 Specific Terms and Conditions per Payment Method This document contains the terms and conditions that Buckaroo and Payment Service Owners
MOBILKINCSTAR ONLINE SECURITIES TRADING TERMS AND CONDITIONS OF USE
 MOBILKINCSTAR ONLINE SECURITIES TRADING TERMS AND CONDITIONS OF USE The Hungarian State Treasury (hereinafter: Distributor) provides general information, executes securities trading and investment transactions
MOBILKINCSTAR ONLINE SECURITIES TRADING TERMS AND CONDITIONS OF USE The Hungarian State Treasury (hereinafter: Distributor) provides general information, executes securities trading and investment transactions
HSBCnet User Guide Dubai Trade Portal
 HSBCnet User Guide Dubai Trade Portal February 2011 Issued by HSBC Bank plc HSBC Bank plc 2011. All rights reserved. Features and functionality may vary by country. Please confirm availability with your
HSBCnet User Guide Dubai Trade Portal February 2011 Issued by HSBC Bank plc HSBC Bank plc 2011. All rights reserved. Features and functionality may vary by country. Please confirm availability with your
Order Notifications - reporting a payment status
 Corporate Gateway Order Notifications - reporting a payment status V5.0 May 2014 Use this guide to: Understand order notifications. Learn how to use the Order Notification Service. New to Order Notifications?
Corporate Gateway Order Notifications - reporting a payment status V5.0 May 2014 Use this guide to: Understand order notifications. Learn how to use the Order Notification Service. New to Order Notifications?
How To Build A Connector On A Website (For A Nonprogrammer)
 Index Data's MasterKey Connect Product Description MasterKey Connect is an innovative technology that makes it easy to automate access to services on the web. It allows nonprogrammers to create 'connectors'
Index Data's MasterKey Connect Product Description MasterKey Connect is an innovative technology that makes it easy to automate access to services on the web. It allows nonprogrammers to create 'connectors'
E-mail Policy Of Government of India
 E-mail Policy Of Government of India October 2014 Version 1.0 Department of Electronics and Information Technology Ministry of Communications and Information Technology Government of India New Delhi -
E-mail Policy Of Government of India October 2014 Version 1.0 Department of Electronics and Information Technology Ministry of Communications and Information Technology Government of India New Delhi -
OpenID connect @ Deutsche telekom. Dr. Torsten Lodderstedt, Deutsche Telekom AG
 OpenID connect @ Deutsche telekom Dr. Torsten Lodderstedt, Deutsche Telekom AG service ecosystem and Telekom Login Dr. Torsten Lodderstedt / OpenID Workshop @ IIW #18 2014-05-05 2 Open Standards: Our History
OpenID connect @ Deutsche telekom Dr. Torsten Lodderstedt, Deutsche Telekom AG service ecosystem and Telekom Login Dr. Torsten Lodderstedt / OpenID Workshop @ IIW #18 2014-05-05 2 Open Standards: Our History
WHITE PAPER. How to simplify and control the cardholder security environment
 WHITE PAPER How to simplify and control the cardholder security environment Document Version V1-0 Document Set: QCC Information Security Prepared By Nick Prescot - QCC Information Security Ltd Sponsored
WHITE PAPER How to simplify and control the cardholder security environment Document Version V1-0 Document Set: QCC Information Security Prepared By Nick Prescot - QCC Information Security Ltd Sponsored
eway AU Hosted Payment Page
 Web Active Corporation eway AU Hosted Payment Page Full Analysis and Data Type Field Specifications Contents Introduction... 3 Customisation... 4 Processing Fraud Protected Transactions... 5 Appendix A
Web Active Corporation eway AU Hosted Payment Page Full Analysis and Data Type Field Specifications Contents Introduction... 3 Customisation... 4 Processing Fraud Protected Transactions... 5 Appendix A
IndusGuard Web Application Firewall Test Drive User Registration
 IndusGuard Web Application Firewall Test Drive User Registration Document Version 1.0 24/06/2015 Confidentiality INDUSFACE HAS PREPARED THIS DOCUMENT FOR INTERNAL PURPOSE. NEITHER THIS DOCUMENT NOR ITS
IndusGuard Web Application Firewall Test Drive User Registration Document Version 1.0 24/06/2015 Confidentiality INDUSFACE HAS PREPARED THIS DOCUMENT FOR INTERNAL PURPOSE. NEITHER THIS DOCUMENT NOR ITS
SSL VPN Technology White Paper
 SSL VPN Technology White Paper Keywords: SSL VPN, HTTPS, Web access, TCP access, IP access Abstract: SSL VPN is an emerging VPN technology based on HTTPS. This document describes its implementation and
SSL VPN Technology White Paper Keywords: SSL VPN, HTTPS, Web access, TCP access, IP access Abstract: SSL VPN is an emerging VPN technology based on HTTPS. This document describes its implementation and
