Rules for Secure Use of Internet Banka
|
|
|
- Baldric McCarthy
- 3 years ago
- Views:
From this document you will learn the answers to the following questions:
What does GE Money Bank never ask for in an e - mail?
What is a log - in page behaving?
What does GE Money Bank operate?
Transcription
1 Rules for Secure Use of Internet Banka
2 Content TECHNICAL SECURITY FOR YOUR INTERNET BANKA... 3 Encryption... 3 Automatic Logging Off from Internet Banka... 3 Web Application Firewall... 3 Regular Checks on Vulnerability of Internet Banka... 3 PROTECTION OF LOG-IN DETAILS... 3 How to Create a Strong Password and Protect It... 3 Blocking and Unblocking Internet Banka... 3 Process of Changing Mobile Telephone for Mobile Key... 4 Storage of Signature Certificate... 4 Information about Last Log In... 4 How We Designate s, the Website and Applications... 4 Measures Not Provided... 5 How We Contact Our Clients... 5 PERSONAL DATA AND IDENTITY... 5 Prevention and Recovery after Identity Theft. (phishing, telephone phishing, dumpster diving)... 5 How We Protect Client Information and Personal Data... 6 We Can Share Client Information... 6 PROTECT YOUR COMPUTER AND MOBILE DEVICES... 6 Security for Computers and Mobile Devices... 6 Backing Up Data... 6 Security for Wireless Networks... 6 CONTACT US... 6
3 Technical Security for Your Internet Banka Encryption To maintain the confidentiality of your data we encrypt its transmission between your computer and Internet Banka using symmetrical encryption algorithms with a key at least 128 bits long. The transmission of the symmetrical key is encrypted using an asymmetrical key with a length of 2,048 bits. Automatic Logging Off from Internet Banka To increase security there is automatic logging off from Internet Banka after 20 minutes of inactivity. For security reasons and to protect your data and finances, after the end of work in Internet Banka always log off using the Log Off button and then close your internet browser. Web Application Firewall Internet Banka is protected by a web application firewall (WAF). Regular Checks on Vulnerability of Internet Banka To maintain the security of Internet Banka, we test it for the presence of vulnerabilities. Protection of Log-in Details How to Create a Strong Password and Protect It Your password must meet the following criteria: length of 8 to 16 characters at last one character must always be a number at least one character must always be a lower-case letter at least one character must always be an upper-case letter For the creation of the strongest possible password we recommend using the maximum number of characters and including in the password, in addition to the mandatory characters, for example, also non-alphanumerical characters. Pay increased attention to maintaining the confidentiality of your password. Do not disclose your password to other persons, even to family members. If you are worried that you won t remember it, write it down so that only you have access to the records. Store a security envelope with your password in a safe place. Regularly change your password, best of all every month. Promptly change your password in the event of any doubt it is known by an unauthorised person. Do not use simple passwords that contain the names of family members and dates of birth. Such passwords can be easily uncovered and abused. In no settings on your computer should you allow remembering of passwords. Never send your password by , even if somebody asks you for it. For security reasons, GE Money Bank may not request you communicate your password. When inputting your password, always check that you input your password into an application that is operated by GE Money Bank. Blocking and Unblocking Internet Banka The procedure for blocking and unblocking the Internet Banka service differs depending on the type of client. Individuals Not in Business and in Business If you have a request for the blocking or unblocking of access to the Internet Banka service, contact nonstop Customer Service. at GE Money Bank on Or you can contact any branch of GE Money Bank. Legal Entities If you have a request for blocking or unblocking access to the Internet Banka service, contact the branch with which your account is maintained. If you want to block Internet Banka, you can use the GE Money Bank nonstop Customer Service line on If you want to unblock Internet Banka you can use the GE Money Bank Customer Service line on , Mon-Fri 8:00-21:00. and Sat-Sun 8:00-17:00. 3
4 Process of Changing Mobile Telephone for Mobile Key In the event you want to change the number for the sending of a mobile key, it is necessary to visit any GE Money Bank branch.. To increase security, changes are not permitted using Customer Service. Storage of Signature Certificate If you log on to Internet Banka using certificates, do not store the signature certificate on your computer, but outside your computer,. for example on a USB flash disk or other device that you have under your control or that you can store in a safe place. Information about Last Log In In your Internet Banka you will find information about the previous time you logged in and also the five last times you logged in, where you can check whether anybody has logged in to your Internet Banka application. You can find information about the previous time you logged in most quickly at the Internet Banka homepage, where the date and time of last logging in is stated. After clicking on Previous Log-ins you will be redirected to a screen with a list of the last five times you logged in. Here you will find information about the date and time of logging in, the IP address from which the log-in occurred and also information about the type of access to Internet Banka (Standard = logging in to full version of Internet Banka, Mobile = logging in to mobile version of Internet Banka). You can get to the screen with the last five log-ins using the Personal Settings in the Last Log-ins menu. How We Designate s, the Website and Applications Do not respond to s that ask you to input your personal details. GE Money Bank never asks in an for your confidential information, e.g. log-in details for Internet Banka. Check that you are logging in to Internet Banka in the right place: After opening the log-in page for Internet Banka, check in the command line that you can see the address ibs31/controllerservlet. In new browser versions the command line also has a green background. Depending on the type and version of your internet browser, a locked padlock icon should be displayed in the upper or lower part. After clicking on the padlock icon, information about the security certificate is displayed. The Norton Secured logo is displayed in the lower right of the screen. After clicking on the logo, a page opens with information about. the security certificate issued for the domain ibs.internetbanka.cz belonging to GE Money Bank. 4
5 If you suspect that the log-in page is behaving unusually somehow, for example it is requesting the password, mobile key or signature certificate in an unusual place, do not complete the log-in information, contact GE Money Bank Customer Service on and check that you are logging in to Internet Banka on the right page. If you are using Internet Banka with a mobile key, pay attention to the whole text of the text message with the mobile key.. This is because each text message contains, for security reasons, not only the mobile key, but also a description of the transaction. you are authorising. Keep an eye on your money. Regularly check your accounts. If you notice any unusual transactions, promptly contact us. If you suspect a website is fraudulent or you have received a fraudulent , write to us at technickapodpora@ge.com. or call Measures Not Provided At its website, GE Money Bank does not provide and does not offer the option of downloading or links to any software except. GE Money Bank software. An exception is the option of downloading the TeamViewer application file. Non-provided tools therefore. include updates to the operating system, archiving programs, anti-virus programs, anti-malware programs, etc. The software provided includes, for example, the GE Money CZ or bene+ bonuses and discounts applications. How We Contact Our Clients GE Money Bank contacts its clients by telephone or . The telephone number from which a client is contacted can change depending on the department that is contacting the client, or depending on the client s mobile operator. communication is always from addresses ending with the ge.com domain. A client is never asked to provide his security details (for example his password for Internet Banka, PIN for payment card and so on). Personal Data and Identity Prevention and Recovery after Identity Theft (phishing, telephone phishing, dumpster diving) Identity theft is a situation where somebody steals your personal data and uses them without your permission. Identity thieves are inventive; they go through publicly available dumpsters in which documents with personal data can be found. They can work for actual companies and authorities, or pretend that they do. They can also try to convince you by or by telephone to provide your personal data. If they obtain your personal data, they can use it to get money from your bank account, make payments using your credit card, order services or borrow money in your name. The following are signs that somebody has stolen your identity: transactions or payments by card that you did not make, some statements stop coming. Identity theft is a criminal offence. You can make a criminal complaint. 5
6 How We Protect Client Information and Personal Data In the case of mutual exchange of information between GE Money Bank, credit entities, Internet Banka, etc., GE Money Bank ensures that there cannot be unauthorised or random access to information, its alteration, destruction or loss, unauthorised transfers, unauthorised processing, as well as other abuse of information. We Can Share Client Information GE Money Bank, based on consent granted to the processing of personal data, shares personal data and closely works with its affiliate. GE CZ and subsidiaries GE Money Auto, a.s., AgroConsult Bohemia s.r.o., and GE Capital (Czech) Holdings, s.r.o. With GE CZ we share clients personal information, to achieve common goals and therefore protect the rights and lawfully protected interests of GE Money Bank, or other related entities. Recipients can also be other companies working as a part of the Bank Register of Client Information and Non-bank Register of Client Information, or another register that GE Money Bank uses based on the law or regarding the use of which clients are informed in advance (see the BRCI and NRCI Information Memoranda). Recipients can also be other companies providing additional services for GE Money Bank for products and services with which the client expresses its consent or submits a request as a part of negotiations on a contractual relationship with GE Money Bank or in a concluded contractual relationship. Protect Your Computer and Mobile Devices Security for Computers and Mobile Devices Keep your computer and mobile devices secure. Regularly update the operating system on your computer and mobile devices. Use the current version of your internet browser. Install programs that protect your computer and mobile devices, such as anti-virus programs, anti-spyware programs and a firewall, and regularly update them. Use a spam filter, do not open and immediately delete s and attachments that came to you from an unknown sender, because they could contain viruses and unsecure programs. Avoid downloading and installing unknown files from unknown sources to your computer and mobile devices (in particular with the file extension.exe), because they could reduce the security of your computer and mobile devices. If you connect from a place where more than one person has access to your computer, do not leave your computer switched on without supervision. Before you leave your computer, active a password-protected screensaver or use CTRL+ALT+DEL to lock your computer. Backing Up Data In order to maintain the availability of your data, we recommend that you regularly back up important data on data storage devices outside your computer. Suitable storage devices are USB flash discs, external discs and home network storage devices. If you want to maintain the confidentiality of your backed-up data, we recommend encrypted backing-up. By backing up at a cloud storage point you undergo the risk of your backed up personal data leaking and thereby limit the efficiency of your measures to maintain data confidentiality. Security for Wireless Networks Pay increased attention when using public Wi-Fi hotspots. The data transferred can be unencrypted or insufficiently encrypted. Therefore take additional measures such as using https or other encryption if you are accessing s, social networks or sharing sensitive data using a public Wi-Fi hotspot. If you cannot take such measures, consider whether you could delay such activities until you are connected using a secure network. Contact Us Customer Service: Mon Fri 8:00 21:00, Sat Sun 8:00 17:00 To contact Customer Service you can also use a Message. to the Bank in your Internet Banka application, or send. an to internetbanka@ge.com. GE Money Bank, a.s., Vyskočilova 1422/1a, Praha 4-Michle, IČO , zapsáno u MS v Praze, odd. B, vl. 5403, tel.:
General tips for increasing the security of using First Investment Bank's internet banking
 General tips for increasing the security of using First Investment Bank's internet banking Dear Clients, First Investment Bank (Fibank, the Bank) provides you with high level of protection and security
General tips for increasing the security of using First Investment Bank's internet banking Dear Clients, First Investment Bank (Fibank, the Bank) provides you with high level of protection and security
Internet Bank with certificates First steps
 Internet Bank with certificates First steps 2 Content BEFORE YOU START...3 Minimum requirements for your computer...3 Support for service Internet Bank...3 Useful links...3 Security...3 Parameters of certificates...3
Internet Bank with certificates First steps 2 Content BEFORE YOU START...3 Minimum requirements for your computer...3 Support for service Internet Bank...3 Useful links...3 Security...3 Parameters of certificates...3
ONLINE BANKING SECURITY TIPS FOR OUR BUSINESS CLIENTS
 $ ONLINE BANKING SECURITY TIPS FOR OUR BUSINESS CLIENTS Boston Private Bank & Trust Company takes great care to safeguard the security of your Online Banking transactions. In addition to our robust security
$ ONLINE BANKING SECURITY TIPS FOR OUR BUSINESS CLIENTS Boston Private Bank & Trust Company takes great care to safeguard the security of your Online Banking transactions. In addition to our robust security
PREVENTING HIGH-TECH IDENTITY THEFT
 1 PREVENTING HIGH-TECH IDENTITY THEFT Presented by The Monument Group Companies Featured speaker: David Floyd November 19, 2014 2 Introduction Preventing Identity Theft (this session) Monitoring for Theft
1 PREVENTING HIGH-TECH IDENTITY THEFT Presented by The Monument Group Companies Featured speaker: David Floyd November 19, 2014 2 Introduction Preventing Identity Theft (this session) Monitoring for Theft
Advice about online security
 Advice about online security May 2013 Contents Report a suspicious email or website... 3 Security advice... 5 Genuine DWP contacts... 8 Recognising and reporting phishing and bogus emails... 9 How DWP
Advice about online security May 2013 Contents Report a suspicious email or website... 3 Security advice... 5 Genuine DWP contacts... 8 Recognising and reporting phishing and bogus emails... 9 How DWP
Security Tips You are here: Home» Security Tips
 Security Tips You are here: Home» Security Tips Click on a the Security Icon to view detailed information on: Responsibility of the Bank Password Policy Guide Online Security Internet Security Tips Scam
Security Tips You are here: Home» Security Tips Click on a the Security Icon to view detailed information on: Responsibility of the Bank Password Policy Guide Online Security Internet Security Tips Scam
Internet Banking with Certificates
 Internet Banking with Certificates Content Useful Documents... Support... Certificate Parameters... Logging in to Internet Banking for the First Time... Generation of Digital Certificates... Importing
Internet Banking with Certificates Content Useful Documents... Support... Certificate Parameters... Logging in to Internet Banking for the First Time... Generation of Digital Certificates... Importing
Safe Practices for Online Banking
 November 2012 Follow these guidelines to help protect your information while banking online. At First Entertainment Credit Union, our goal is to provide you with the best all around banking experience.
November 2012 Follow these guidelines to help protect your information while banking online. At First Entertainment Credit Union, our goal is to provide you with the best all around banking experience.
Internet Banking with a Mobile Key
 Internet Banking with a Mobile Key Content Useful Documents...3 Support...3 Logging in to Internet Banking for the First Time...3 Activating Internet Banking...4 Transaction Limit...4 Configure Internet
Internet Banking with a Mobile Key Content Useful Documents...3 Support...3 Logging in to Internet Banking for the First Time...3 Activating Internet Banking...4 Transaction Limit...4 Configure Internet
Deutsche Bank db easynet. Secure method of use of the db easynet e-banking system
 Deutsche Bank Secure method of use of the e-banking system Introduction Deutsche Bank pays particular attention to your security. Therefore, the funds entrusted to us by our Customers are protected, using
Deutsche Bank Secure method of use of the e-banking system Introduction Deutsche Bank pays particular attention to your security. Therefore, the funds entrusted to us by our Customers are protected, using
Protecting Yourself from Identity Theft
 Protecting Yourself from Identity Theft Identity theft is everywhere. In fact, according to a 2013 report by Javelin Research, there is one incident of identity fraud every two seconds. While we cannot
Protecting Yourself from Identity Theft Identity theft is everywhere. In fact, according to a 2013 report by Javelin Research, there is one incident of identity fraud every two seconds. While we cannot
Online Security Information. Tips for staying safe online
 Online Security Information ProCredit Bank is committed to protecting the integrity of your transactions and bank account details. ProCredit Bank therefore uses the latest security software and procedures
Online Security Information ProCredit Bank is committed to protecting the integrity of your transactions and bank account details. ProCredit Bank therefore uses the latest security software and procedures
Infocomm Sec rity is incomplete without U Be aware,
 Infocomm Sec rity is incomplete without U Be aware, responsible secure! HACKER Smack that What you can do with these five online security measures... ANTI-VIRUS SCAMS UPDATE FIREWALL PASSWORD [ 2 ] FASTEN
Infocomm Sec rity is incomplete without U Be aware, responsible secure! HACKER Smack that What you can do with these five online security measures... ANTI-VIRUS SCAMS UPDATE FIREWALL PASSWORD [ 2 ] FASTEN
CLEO Remote Access Services CLEO Remote Desktop Access User Guide v1.3
 CLEO ~Remote Access Services Remote Desktop Access User guide CLEO Remote Access Services CLEO Remote Desktop Access User Guide v1.3 August 2007 page 1 of 16 CLEO 2007 CLEO Remote Access Services 3SGD
CLEO ~Remote Access Services Remote Desktop Access User guide CLEO Remote Access Services CLEO Remote Desktop Access User Guide v1.3 August 2007 page 1 of 16 CLEO 2007 CLEO Remote Access Services 3SGD
Secure Your Information and Communication Technology Devices
 You should pay attention to the following items bef the Internet: Secure Your Information and Communication Technology Devices Install proper anti-virus software P.3 Log on as a user and not as an administrator
You should pay attention to the following items bef the Internet: Secure Your Information and Communication Technology Devices Install proper anti-virus software P.3 Log on as a user and not as an administrator
How to Encrypt Files Containing Sensitive Data (using 7zip software or Microsoft password protection) How to Create Strong Passwords
 How to Encrypt Files Containing Sensitive Data (using 7zip software or Microsoft password protection) How to Create Strong Passwords School IT Systems Support Herts for Learning Ltd SROB220, Robertson
How to Encrypt Files Containing Sensitive Data (using 7zip software or Microsoft password protection) How to Create Strong Passwords School IT Systems Support Herts for Learning Ltd SROB220, Robertson
STUDENT S INFORMATION SECURITY GUIDE
 STUDENT S INFORMATION SECURITY GUIDE April 2013 Table of contents Information security is important - also for you...1 Use strong passwords and keep them safe...2 E-mail use...3 Beware of phishing and
STUDENT S INFORMATION SECURITY GUIDE April 2013 Table of contents Information security is important - also for you...1 Use strong passwords and keep them safe...2 E-mail use...3 Beware of phishing and
Barracuda User Guide. Managing your Spam Quarantine
 Managing your Spam Quarantine Barracuda User Guide Step1: Open your internet browser and go to http://myspam.datatechhosting.com this will automatically redirect you to Barracuda s email security service
Managing your Spam Quarantine Barracuda User Guide Step1: Open your internet browser and go to http://myspam.datatechhosting.com this will automatically redirect you to Barracuda s email security service
ONE Mail Direct for Mobile Devices
 ONE Mail Direct for Mobile Devices User Guide Version: 2.0 Document ID: 3292 Document Owner: ONE Mail Product Team Copyright Notice Copyright 2014, ehealth Ontario All rights reserved No part of this document
ONE Mail Direct for Mobile Devices User Guide Version: 2.0 Document ID: 3292 Document Owner: ONE Mail Product Team Copyright Notice Copyright 2014, ehealth Ontario All rights reserved No part of this document
Sound Business Practices for Businesses to Mitigate Corporate Account Takeover
 Sound Business Practices for Businesses to Mitigate Corporate Account Takeover This white paper provides sound business practices for companies to implement to safeguard against Corporate Account Takeover.
Sound Business Practices for Businesses to Mitigate Corporate Account Takeover This white paper provides sound business practices for companies to implement to safeguard against Corporate Account Takeover.
Safe Use of Electronic Services
 Safe Use of Electronic Services Electronic banking is not only quick, cost-effective and convenient but also safe. However, each system is only as safe as its weakest link. The security foundations of
Safe Use of Electronic Services Electronic banking is not only quick, cost-effective and convenient but also safe. However, each system is only as safe as its weakest link. The security foundations of
Online Banking Security Guide Internet-based version
 Online Banking Security Guide Internet-based version Contents Introduction to the Security Guide... 2 Security Guide... 2 Using the internet securely... 2 Security solutions in Online Banking... 3 What
Online Banking Security Guide Internet-based version Contents Introduction to the Security Guide... 2 Security Guide... 2 Using the internet securely... 2 Security solutions in Online Banking... 3 What
Safety& Security Tips
 Safety& Security Tips 1. Security measures adopted by IDBI Bank IDBI Bank has a strong online security policy to ensure our customers have a safe and secure online experience with us. We have 256 bit Secure
Safety& Security Tips 1. Security measures adopted by IDBI Bank IDBI Bank has a strong online security policy to ensure our customers have a safe and secure online experience with us. We have 256 bit Secure
Instructions For Opening UHA Encrypted Email
 Receiving Encrypted Email You have received a secure, encrypted message from UHA. The message will contain the following notice and an attachment named SecureMessageAtt.hml. The attachment is shown circled
Receiving Encrypted Email You have received a secure, encrypted message from UHA. The message will contain the following notice and an attachment named SecureMessageAtt.hml. The attachment is shown circled
National Cyber Security Month 2015: Daily Security Awareness Tips
 National Cyber Security Month 2015: Daily Security Awareness Tips October 1 New Threats Are Constantly Being Developed. Protect Your Home Computer and Personal Devices by Automatically Installing OS Updates.
National Cyber Security Month 2015: Daily Security Awareness Tips October 1 New Threats Are Constantly Being Developed. Protect Your Home Computer and Personal Devices by Automatically Installing OS Updates.
Identity Theft Protection
 Identity Theft Protection Email Home EDUCATION on DANGER ZONES Internet Payments Telephone ID theft occurs when someone uses your personal information with out your knowledge to commit fraud. Some terms
Identity Theft Protection Email Home EDUCATION on DANGER ZONES Internet Payments Telephone ID theft occurs when someone uses your personal information with out your knowledge to commit fraud. Some terms
OKPAY guides. Security Guide
 Название раздела OKPAY guides www.okpay.com Security Guide 2012 Contents SECURITY GUIDE Contents Introduction 1. OKPAY Security Overview 2. Security Tips 3. Security Center 3.1. Basic Protection 3.2. Email
Название раздела OKPAY guides www.okpay.com Security Guide 2012 Contents SECURITY GUIDE Contents Introduction 1. OKPAY Security Overview 2. Security Tips 3. Security Center 3.1. Basic Protection 3.2. Email
Email and Security. U3A Radlett Computer Group Meeting 6-Oct-2014 V1.1
 Email and Security U3A Radlett Computer Group Meeting 6-Oct-2014 V1.1 Agenda Introduction Email Security Q&A Introduction Gary Harding email:- U3A@GaryHarding.com Spent more than 40 years working in the
Email and Security U3A Radlett Computer Group Meeting 6-Oct-2014 V1.1 Agenda Introduction Email Security Q&A Introduction Gary Harding email:- U3A@GaryHarding.com Spent more than 40 years working in the
Microsoft and Windows are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries.
 2001 2014 EdgeWave. All rights reserved. The EdgeWave logo is a trademark of EdgeWave Inc. All other trademarks and registered trademarks are hereby acknowledged. Microsoft and Windows are either registered
2001 2014 EdgeWave. All rights reserved. The EdgeWave logo is a trademark of EdgeWave Inc. All other trademarks and registered trademarks are hereby acknowledged. Microsoft and Windows are either registered
ONLINE IDENTITY THEFT KEEP YOURSELF SAFE FROM BESTPRACTICES WHAT DO YOU NEED TO DO IF YOU SUSPECT YOUR WHAT DO YOU NEED TO DO IF YOU SUSPECT YOUR
 ONLINE IDENTITY THEFT KEEP YOURSELF SAFE FROM BESTPRACTICES 01 One must remember that everyone and anyone is a potential target. These cybercriminals and attackers often use different tactics to lure different
ONLINE IDENTITY THEFT KEEP YOURSELF SAFE FROM BESTPRACTICES 01 One must remember that everyone and anyone is a potential target. These cybercriminals and attackers often use different tactics to lure different
Fraud Prevention Tips
 Fraud Prevention Tips The best defense against fraud or identity theft is a proactive approach. Here are a few steps you can take to help protect yourself. Protect your identity Copy the front and back
Fraud Prevention Tips The best defense against fraud or identity theft is a proactive approach. Here are a few steps you can take to help protect yourself. Protect your identity Copy the front and back
INFORMATION SECURITY GUIDE FOR STAFF
 INFORMATION SECURITY GUIDE FOR STAFF December 2013 TABLE OF CONTENTS Why is information security so important for you and the university...1 Use strong passwords and keep them safe...2 E-mail use...2 Beware
INFORMATION SECURITY GUIDE FOR STAFF December 2013 TABLE OF CONTENTS Why is information security so important for you and the university...1 Use strong passwords and keep them safe...2 E-mail use...2 Beware
River Valley Credit Union Online Banking
 River Valley Credit Union Online Banking New user setup guide Members can self enroll for the service by answering a few simple questions. Before beginning the process, please make sure you have this information
River Valley Credit Union Online Banking New user setup guide Members can self enroll for the service by answering a few simple questions. Before beginning the process, please make sure you have this information
Protecting your business from fraud
 Protecting your business from fraud KEY TAKEAWAYS > Understand the most common types of fraud and how to identify them. > What to do if you uncover fraudulent activity or suspect you are a victim of fraud.
Protecting your business from fraud KEY TAKEAWAYS > Understand the most common types of fraud and how to identify them. > What to do if you uncover fraudulent activity or suspect you are a victim of fraud.
NC DPH: Computer Security Basic Awareness Training
 NC DPH: Computer Security Basic Awareness Training Introduction and Training Objective Our roles in the Division of Public Health (DPH) require us to utilize our computer resources in a manner that protects
NC DPH: Computer Security Basic Awareness Training Introduction and Training Objective Our roles in the Division of Public Health (DPH) require us to utilize our computer resources in a manner that protects
10 Quick Tips to Mobile Security
 10 Quick Tips to Mobile Security 10 Quick Tips to Mobile Security contents 03 Introduction 05 Mobile Threats and Consequences 06 Important Mobile Statistics 07 Top 10 Mobile Safety Tips 19 Resources 22
10 Quick Tips to Mobile Security 10 Quick Tips to Mobile Security contents 03 Introduction 05 Mobile Threats and Consequences 06 Important Mobile Statistics 07 Top 10 Mobile Safety Tips 19 Resources 22
Business Identity Fraud Prevention Checklist
 Business Identity Fraud Prevention Checklist 9 Critical Things Every Business Owner Should Do Business identity thieves and fraudsters are clever and determined, and can quickly take advantage of business
Business Identity Fraud Prevention Checklist 9 Critical Things Every Business Owner Should Do Business identity thieves and fraudsters are clever and determined, and can quickly take advantage of business
Learn to protect yourself from Identity Theft. First National Bank can help.
 Learn to protect yourself from Identity Theft. First National Bank can help. Your identity is one of the most valuable things you own. It s important to keep your identity from being stolen by someone
Learn to protect yourself from Identity Theft. First National Bank can help. Your identity is one of the most valuable things you own. It s important to keep your identity from being stolen by someone
INTERNET SAFETY: VIRUS: a computer program that can copy itself and infect your computer. CAPTCHAS: type the letters to set up an online account
 INTERNET SAFETY: VIRUS: a computer program that can copy itself and infect your computer Malware: Harmful software programs designed to damage your computer without you knowing. Spyware: Undetected programs
INTERNET SAFETY: VIRUS: a computer program that can copy itself and infect your computer Malware: Harmful software programs designed to damage your computer without you knowing. Spyware: Undetected programs
Quarantined Messages 5 What are quarantined messages? 5 What username and password do I use to access my quarantined messages? 5
 Contents Paul Bunyan Net Email Filter 1 What is the Paul Bunyan Net Email Filter? 1 How do I get to the Email Filter? 1 How do I release a message from the Email Filter? 1 How do I delete messages listed
Contents Paul Bunyan Net Email Filter 1 What is the Paul Bunyan Net Email Filter? 1 How do I get to the Email Filter? 1 How do I release a message from the Email Filter? 1 How do I delete messages listed
Keeping your online health and social care records safe and secure
 Keeping your online health and social care records safe and secure Keeping your online health and social care records safe and secure By 2015, everyone in England will have access to their GP medical records
Keeping your online health and social care records safe and secure Keeping your online health and social care records safe and secure By 2015, everyone in England will have access to their GP medical records
AVOIDING ONLINE THREATS CYBER SECURITY MYTHS, FACTS, TIPS. ftrsecure.com
 AVOIDING ONLINE THREATS CYBER SECURITY MYTHS, FACTS, TIPS ftrsecure.com Can You Separate Myths From Facts? Many Internet myths still persist that could leave you vulnerable to internet crimes. Check out
AVOIDING ONLINE THREATS CYBER SECURITY MYTHS, FACTS, TIPS ftrsecure.com Can You Separate Myths From Facts? Many Internet myths still persist that could leave you vulnerable to internet crimes. Check out
GadgetTrak Mobile Security Android & BlackBerry Installation & Operation Manual
 GadgetTrak Mobile Security Android & BlackBerry Installation & Operation Manual Overview GadgetTrak Mobile Security is an advanced software application designed to assist in the recovery of your mobile
GadgetTrak Mobile Security Android & BlackBerry Installation & Operation Manual Overview GadgetTrak Mobile Security is an advanced software application designed to assist in the recovery of your mobile
Information Security It s Everyone s Responsibility
 Information Security It s Everyone s Responsibility Developed By The University of Texas at Dallas (ISO) Purpose of Training As an employee, you are often the first line of defense protecting valuable
Information Security It s Everyone s Responsibility Developed By The University of Texas at Dallas (ISO) Purpose of Training As an employee, you are often the first line of defense protecting valuable
Secure Email FAQs for External Stakeholders
 Secure Email FAQs for External Stakeholders Ver: 07 November 2012 What is secure email and why am I getting encrypted emails from the IPCC? Why do I have to register to open a Registered Envelope? What
Secure Email FAQs for External Stakeholders Ver: 07 November 2012 What is secure email and why am I getting encrypted emails from the IPCC? Why do I have to register to open a Registered Envelope? What
Security Guide. for electronic transactions. UniBank is a division of Teachers Mutual Bank Limited
 Security Guide for electronic transactions UniBank is a division of Teachers Mutual Bank Limited Teachers Mutual Bank Limited ABN 30 087 650 459 AFSL/Australian Credit Licence 238981 Who We Are UniBank
Security Guide for electronic transactions UniBank is a division of Teachers Mutual Bank Limited Teachers Mutual Bank Limited ABN 30 087 650 459 AFSL/Australian Credit Licence 238981 Who We Are UniBank
SECURITY RECOMMENDATIONS INTERNET BANKING TRANSACTIONAL
 SECURITY RECOMMENDATIONS INTERNET BANKING TRANSACTIONAL This page should provide customers with all the information they need concerning the security of a transactional Internet banking site and, in particular,
SECURITY RECOMMENDATIONS INTERNET BANKING TRANSACTIONAL This page should provide customers with all the information they need concerning the security of a transactional Internet banking site and, in particular,
When visiting online banking's sign-on page, your browser establishes a secure session with our server.
 The privacy of communications between you (your browser) and our servers is ensured via encryption. Encryption scrambles messages exchanged between your browser and our online banking server. How Encryption
The privacy of communications between you (your browser) and our servers is ensured via encryption. Encryption scrambles messages exchanged between your browser and our online banking server. How Encryption
A. I do not have my own personal certificate I am a new client or want to download a new certificate
 This user guide will help you to create your personal certificate in file/browser or smart card certificate. If you already own a personal certificate in file that you have saved on your computer, you
This user guide will help you to create your personal certificate in file/browser or smart card certificate. If you already own a personal certificate in file that you have saved on your computer, you
eprism Email Security Suite
 FAQ V8.3 eprism Email Security Suite 800-782-3762 www.edgewave.com 2001 2012 EdgeWave. All rights reserved. The EdgeWave logo is a trademark of EdgeWave Inc. All other trademarks and registered trademarks
FAQ V8.3 eprism Email Security Suite 800-782-3762 www.edgewave.com 2001 2012 EdgeWave. All rights reserved. The EdgeWave logo is a trademark of EdgeWave Inc. All other trademarks and registered trademarks
Armstrong State University Fall Staff Assembly. Chief Wayne Willcox, MSCJ, CLEE
 Armstrong State University Fall Staff Assembly Chief Wayne Willcox, MSCJ, CLEE Identity Theft: When someone uses your personal information without your permission to commit fraud or other crime Name Social
Armstrong State University Fall Staff Assembly Chief Wayne Willcox, MSCJ, CLEE Identity Theft: When someone uses your personal information without your permission to commit fraud or other crime Name Social
Guide to credit card security
 Contents Click on a title below to jump straight to that section. What is credit card fraud? Types of credit card fraud Current scams Keeping your card and card details safe Banking and shopping securely
Contents Click on a title below to jump straight to that section. What is credit card fraud? Types of credit card fraud Current scams Keeping your card and card details safe Banking and shopping securely
Helping you to protect yourself against fraud and financial crime
 Helping you to protect yourself against fraud and financial crime first direct takes fraud & other financial crimes very seriously. Even though we have market-leading fraud detection systems, we want you
Helping you to protect yourself against fraud and financial crime first direct takes fraud & other financial crimes very seriously. Even though we have market-leading fraud detection systems, we want you
BCS IT User Syllabus IT Security for Users Level 2. Version 1.0
 BCS IT User Syllabus IT for Users Level 2 Version 1.0 June 2009 ITS2.1 System Performance ITS2.1.1 Unwanted messages ITS2.1.2 Malicious ITS2.1.1.1 ITS2.1.1.2 ITS2.1.2.1 ITS2.1.2.2 ITS2.1.2.3 ITS2.1.2.4
BCS IT User Syllabus IT for Users Level 2 Version 1.0 June 2009 ITS2.1 System Performance ITS2.1.1 Unwanted messages ITS2.1.2 Malicious ITS2.1.1.1 ITS2.1.1.2 ITS2.1.2.1 ITS2.1.2.2 ITS2.1.2.3 ITS2.1.2.4
PORTLANDDIOCESE.ORG Email - How to Connect Table of Contents
 1 PORTLANDDIOCESE.ORG Email - How to Connect Table of Contents Email Access via a Web Browser... 2 Email Client Setup... 3 Outlook 2013 for Windows... 3 Outlook for Mac 2011... 4 Mac OS X 10.6+... 4 iphone
1 PORTLANDDIOCESE.ORG Email - How to Connect Table of Contents Email Access via a Web Browser... 2 Email Client Setup... 3 Outlook 2013 for Windows... 3 Outlook for Mac 2011... 4 Mac OS X 10.6+... 4 iphone
BlackBerry Internet Service. Version: 4.5.1. User Guide
 BlackBerry Internet Service Version: 4.5.1 User Guide Published: 2014-05-22 SWD-20140522173857703 Contents 1 Getting started...7 About the messaging service plans for the BlackBerry Internet Service...7
BlackBerry Internet Service Version: 4.5.1 User Guide Published: 2014-05-22 SWD-20140522173857703 Contents 1 Getting started...7 About the messaging service plans for the BlackBerry Internet Service...7
Wakefield Council Secure email and file transfer User guide for customers, partners and agencies
 Wakefield Council Secure email and file transfer User guide for customers, partners and agencies The nature of the work the council carries out means that we often deal with information that is sensitive
Wakefield Council Secure email and file transfer User guide for customers, partners and agencies The nature of the work the council carries out means that we often deal with information that is sensitive
Using the Web email service
 Using the Web email service This booklet describes the web based email service used by Sandwell schools. The web based email service was introduced in January 2005 to replace an earlier webmail system.
Using the Web email service This booklet describes the web based email service used by Sandwell schools. The web based email service was introduced in January 2005 to replace an earlier webmail system.
E-MAIL FILTERING FAQ
 V8.3 E-MAIL FILTERING FAQ COLTON.COM Why? Why are we switching from Postini? The Postini product and service was acquired by Google in 2007. In 2011 Google announced it would discontinue Postini. Replacement:
V8.3 E-MAIL FILTERING FAQ COLTON.COM Why? Why are we switching from Postini? The Postini product and service was acquired by Google in 2007. In 2011 Google announced it would discontinue Postini. Replacement:
STRONGER ONLINE SECURITY
 STRONGER ONLINE SECURITY Enhanced online banking without compromise Manage your business banking efficiently and securely Internet banking has given business leaders and treasurers greater control of financial
STRONGER ONLINE SECURITY Enhanced online banking without compromise Manage your business banking efficiently and securely Internet banking has given business leaders and treasurers greater control of financial
BlackBerry Internet Service Using the Browser on Your BlackBerry Smartphone Version: 2.8
 BlackBerry Internet Service Using the Browser on Your BlackBerry Smartphone Version: 2.8 User Guide SWDT653811-793266-0827104650-001 Contents Getting started... 3 About messaging service plans for BlackBerry
BlackBerry Internet Service Using the Browser on Your BlackBerry Smartphone Version: 2.8 User Guide SWDT653811-793266-0827104650-001 Contents Getting started... 3 About messaging service plans for BlackBerry
Tips for Banking Online Safely
 If proper attention is given to safety and security, banking and monetary activities can be completed online in a convenient and effective fashion. This guide helps to establish procedures for remaining
If proper attention is given to safety and security, banking and monetary activities can be completed online in a convenient and effective fashion. This guide helps to establish procedures for remaining
CONDITIONS FOR ELECTRONIC DATA EXCHANGE VIA ČSOB MULTICASH 24 SERVICE
 This translation of the Conditions for Electronic Data Exchange via ČSOB MultiCash 24 Service from Slovak to English language is for information purposes only and does not represent a binding version.
This translation of the Conditions for Electronic Data Exchange via ČSOB MultiCash 24 Service from Slovak to English language is for information purposes only and does not represent a binding version.
PROTECT YOUR COMPUTER AND YOUR PRIVACY!
 PROTECT YOUR COMPUTER AND YOUR PRIVACY! Fraud comes in many shapes simple: the loss of both money protecting your computer and Take action and get peace of and sizes, but the outcome is and time. That
PROTECT YOUR COMPUTER AND YOUR PRIVACY! Fraud comes in many shapes simple: the loss of both money protecting your computer and Take action and get peace of and sizes, but the outcome is and time. That
SUBJECT: Effective Date Policy Number Security of Mobile Computing, Data Storage, and Communication Devices
 SUBJECT: Effective Date Policy Number Security of Mobile Computing, Data Storage, and Communication Devices 8-27-2015 4-007.1 Supersedes 4-007 Page Of 1 5 Responsible Authority Vice Provost for Information
SUBJECT: Effective Date Policy Number Security of Mobile Computing, Data Storage, and Communication Devices 8-27-2015 4-007.1 Supersedes 4-007 Page Of 1 5 Responsible Authority Vice Provost for Information
ITSC Training Courses Student IT Competence Programme SIIS1 Information Security
 ITSC Training Courses Student IT Competence Programme SI1 2012 2013 Prof. Chan Yuen Yan, Rosanna Department of Engineering The Chinese University of Hong Kong SI1-1 Course Outline What you should know
ITSC Training Courses Student IT Competence Programme SI1 2012 2013 Prof. Chan Yuen Yan, Rosanna Department of Engineering The Chinese University of Hong Kong SI1-1 Course Outline What you should know
Portal Administration. Administrator Guide
 Portal Administration Administrator Guide Portal Administration Guide Documentation version: 1.0 Legal Notice Legal Notice Copyright 2013 Symantec Corporation. All rights reserved. Symantec, the Symantec
Portal Administration Administrator Guide Portal Administration Guide Documentation version: 1.0 Legal Notice Legal Notice Copyright 2013 Symantec Corporation. All rights reserved. Symantec, the Symantec
Protect yourself online
 Protect yourself online Advice from Nottinghamshire Police s Pre Crime Unit Get daily updates: www.nottinghamshire.police.uk www.twitter.com/nottspolice www.facebook.com/nottspolice www.youtube.com/nottinghampolice
Protect yourself online Advice from Nottinghamshire Police s Pre Crime Unit Get daily updates: www.nottinghamshire.police.uk www.twitter.com/nottspolice www.facebook.com/nottspolice www.youtube.com/nottinghampolice
Royal Mail Group. getting started. with Symantec Endpoint Encryption. A user guide from Royal Mail Technology
 getting started with Symantec Endpoint Encryption A user guide from Royal Mail Technology For further help, contact the IT Helpdesk on 5415 2555 (01246 282555) March 2010 Contents 1 Introduction to Symantec
getting started with Symantec Endpoint Encryption A user guide from Royal Mail Technology For further help, contact the IT Helpdesk on 5415 2555 (01246 282555) March 2010 Contents 1 Introduction to Symantec
eprism Email Security Suite
 FAQ V8.3 eprism Email Security Suite 800-782-3762 www.edgewave.com 2001 2012 EdgeWave. All rights reserved. The EdgeWave logo is a trademark of EdgeWave Inc. All other trademarks and registered trademarks
FAQ V8.3 eprism Email Security Suite 800-782-3762 www.edgewave.com 2001 2012 EdgeWave. All rights reserved. The EdgeWave logo is a trademark of EdgeWave Inc. All other trademarks and registered trademarks
suntrust.com 800.SUNTRUST
 suntrust.com 800.SUNTRUST SunTrust Bank is an Equal Housing Lender. Member FDIC. 2010 SunTrust Banks, Inc., SunTrust, Live Solid. Bank Solid., SunTrust Rewards, and Signature Advantage Checking, are federally
suntrust.com 800.SUNTRUST SunTrust Bank is an Equal Housing Lender. Member FDIC. 2010 SunTrust Banks, Inc., SunTrust, Live Solid. Bank Solid., SunTrust Rewards, and Signature Advantage Checking, are federally
On-Site Computer Solutions values these technologies as part of an overall security plan:
 Network Security Best Practices On-Site Computer Solutions Brian McMurtry Version 1.2 Revised June 23, 2008 In a business world where data privacy, integrity, and security are paramount, the small and
Network Security Best Practices On-Site Computer Solutions Brian McMurtry Version 1.2 Revised June 23, 2008 In a business world where data privacy, integrity, and security are paramount, the small and
This document provides a brief, end-user overview of the Cisco Registered Envelop Service which has been implemented by Sterne Agee.
 Email Encryption User Guide Sterne Agee is committed to the security of your information. We have implemented Cisco Email Encryption to secure email communication so that only you can open it.* Questions?
Email Encryption User Guide Sterne Agee is committed to the security of your information. We have implemented Cisco Email Encryption to secure email communication so that only you can open it.* Questions?
Data Access Request Service
 Data Access Request Service Guidance Notes on Security Version: 4.0 Date: 01/04/2015 1 Copyright 2014, Health and Social Care Information Centre. Introduction This security guidance is for organisations
Data Access Request Service Guidance Notes on Security Version: 4.0 Date: 01/04/2015 1 Copyright 2014, Health and Social Care Information Centre. Introduction This security guidance is for organisations
Computer Security at Columbia College. Barak Zahavy April 2010
 Computer Security at Columbia College Barak Zahavy April 2010 Outline 2 Computer Security: What and Why Identity Theft Costs Prevention Further considerations Approach Broad range of awareness Cover a
Computer Security at Columbia College Barak Zahavy April 2010 Outline 2 Computer Security: What and Why Identity Theft Costs Prevention Further considerations Approach Broad range of awareness Cover a
Remote Deposit Quick Start Guide
 Treasury Management Fraud Prevention How to Protect Your Business Remote Deposit Quick Start Guide What s Inside We re committed to the safety of your company s financial information. We want to make you
Treasury Management Fraud Prevention How to Protect Your Business Remote Deposit Quick Start Guide What s Inside We re committed to the safety of your company s financial information. We want to make you
Logging into LTC Instant Access the First Time
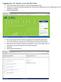 Logging into LTC Instant Access the First Time Access the Instant Access website at: https://mycampus.gotoltc.edu Enter your LTC network username and password. These are the credentials you use to initially
Logging into LTC Instant Access the First Time Access the Instant Access website at: https://mycampus.gotoltc.edu Enter your LTC network username and password. These are the credentials you use to initially
Top tips for improved network security
 Top tips for improved network security Network security is beleaguered by malware, spam and security breaches. Some criminal, some malicious, some just annoying but all impeding the smooth running of a
Top tips for improved network security Network security is beleaguered by malware, spam and security breaches. Some criminal, some malicious, some just annoying but all impeding the smooth running of a
How to Install Windows 7 software
 Connecting Windows 7 to the network This document outlines the procedure for setting up Windows 7 to use the College and University network. It assumes that the computer is set up and working correctly
Connecting Windows 7 to the network This document outlines the procedure for setting up Windows 7 to use the College and University network. It assumes that the computer is set up and working correctly
Computer Security Self-Test: Questions & Scenarios
 Computer Security Self-Test: Questions & Scenarios Rev. Sept 2015 Scenario #1: Your supervisor is very busy and asks you to log into the HR Server using her user-id and password to retrieve some reports.
Computer Security Self-Test: Questions & Scenarios Rev. Sept 2015 Scenario #1: Your supervisor is very busy and asks you to log into the HR Server using her user-id and password to retrieve some reports.
Identity Theft, Fraud & You. Prepare. Protect. Prevent.
 Prepare. Protect. Prevent. Identity Theft, Fraud & You Fraud and identity theft incidents claimed fewer victims in 2010 than in previous years. But don t get too comfortable. Average out-of-pocket consumer
Prepare. Protect. Prevent. Identity Theft, Fraud & You Fraud and identity theft incidents claimed fewer victims in 2010 than in previous years. But don t get too comfortable. Average out-of-pocket consumer
account multiple solutions
 Quick Start Guide 1 Our easy to use guide will get you up and running in no time! The guide will assist you with: Generating your Sage Pay login Navigation Creating contacts Creating system users Setting
Quick Start Guide 1 Our easy to use guide will get you up and running in no time! The guide will assist you with: Generating your Sage Pay login Navigation Creating contacts Creating system users Setting
USER S MANUAL Cloud Email Firewall 4.3.2.4 1. Cloud Email & Web Security
 USER S MANUAL Cloud Email Firewall 4.3.2.4 1 Contents 1. INTRODUCTION TO CLOUD EMAIL FIREWALL... 4 1.1. WHAT IS CLOUD EMAIL FIREWALL?... 4 1.1.1. What makes Cloud Email Firewall different?... 4 1.1.2.
USER S MANUAL Cloud Email Firewall 4.3.2.4 1 Contents 1. INTRODUCTION TO CLOUD EMAIL FIREWALL... 4 1.1. WHAT IS CLOUD EMAIL FIREWALL?... 4 1.1.1. What makes Cloud Email Firewall different?... 4 1.1.2.
Intercepting your mail. They can complete change of address forms and receive mail that s intended for you.
 At SunTrust, we re committed to protecting your accounts and identity. That s why we ve created this Identity Theft Guide. This guide provides information about online fraud and identity theft, as well
At SunTrust, we re committed to protecting your accounts and identity. That s why we ve created this Identity Theft Guide. This guide provides information about online fraud and identity theft, as well
Online Security Awareness - UAE Exchange - Foreign Exchange Send Money UAE Exchange
 The responsibility of safeguarding your personal information starts with you. Your information is critical and it must be protected from unauthorised disclosure, modification or destruction. Here we are
The responsibility of safeguarding your personal information starts with you. Your information is critical and it must be protected from unauthorised disclosure, modification or destruction. Here we are
Frequently Asked Questions (FAQ)
 Your personal information and account security is important to us. This product employs a Secure Sign On process that includes layers of protection at time of product log in to mitigate risk, and thwart
Your personal information and account security is important to us. This product employs a Secure Sign On process that includes layers of protection at time of product log in to mitigate risk, and thwart
Online Banking Fraud Prevention Recommendations and Best Practices
 Online Banking Fraud Prevention Recommendations and Best Practices This document provides you with fraud prevention best practices that every employee at Continental National Bank of Miami needs to know
Online Banking Fraud Prevention Recommendations and Best Practices This document provides you with fraud prevention best practices that every employee at Continental National Bank of Miami needs to know
I dentity theft occurs
 1.3.1.F1 Identity Family Economics and Financial Education W h at i s I d e n t i t y T h e f t? I dentity theft occurs when someone wrongfully acquires and uses a consumer s personal identification, credit,
1.3.1.F1 Identity Family Economics and Financial Education W h at i s I d e n t i t y T h e f t? I dentity theft occurs when someone wrongfully acquires and uses a consumer s personal identification, credit,
PROTECT YOUR FINANCIAL TRANSACTIONS
 PROTECT YOUR FINANCIAL TRANSACTIONS Caisses populaires acadiennes www.acadie.com/en It s a wealth of ways to strengthen the security of your financial transactions. By implementing simple measures to mitigate
PROTECT YOUR FINANCIAL TRANSACTIONS Caisses populaires acadiennes www.acadie.com/en It s a wealth of ways to strengthen the security of your financial transactions. By implementing simple measures to mitigate
PORTLANDDIOCESE.ORG Email - How to Connect Table of Contents
 1 PORTLANDDIOCESE.ORG Email - How to Connect Table of Contents Email Access via a Web Browser... 2 Email Client Setup... 3 Outlook 2007, 2010 & 2013 for Windows... 3 Outlook for Mac 2011... 5 Mac OS X
1 PORTLANDDIOCESE.ORG Email - How to Connect Table of Contents Email Access via a Web Browser... 2 Email Client Setup... 3 Outlook 2007, 2010 & 2013 for Windows... 3 Outlook for Mac 2011... 5 Mac OS X
Management and Storage of Sensitive Information UH Information Security Team (InfoSec)
 Management and Storage of Sensitive Information UH Information Security Team (InfoSec) Who Are We? UH Information Security Team Jodi Ito - Information Security Officer Deanna Pasternak & Taylor Summers
Management and Storage of Sensitive Information UH Information Security Team (InfoSec) Who Are We? UH Information Security Team Jodi Ito - Information Security Officer Deanna Pasternak & Taylor Summers
How to stay safe online
 How to stay safe online Everyone knows about computer viruses...or at least they think they do. Nearly 30 years ago, the first computer virus was written and since then, millions of viruses and other malware
How to stay safe online Everyone knows about computer viruses...or at least they think they do. Nearly 30 years ago, the first computer virus was written and since then, millions of viruses and other malware
Best Practices Guide to Electronic Banking
 Best Practices Guide to Electronic Banking City Bank & Trust Company offers a variety of services to our customers. As these services have evolved over time, a much higher percentage of customers have
Best Practices Guide to Electronic Banking City Bank & Trust Company offers a variety of services to our customers. As these services have evolved over time, a much higher percentage of customers have
A practical guide to IT security
 Data protection A practical guide to IT security Ideal for the small business The Data Protection Act states that appropriate technical and organisational measures shall be taken against unauthorised or
Data protection A practical guide to IT security Ideal for the small business The Data Protection Act states that appropriate technical and organisational measures shall be taken against unauthorised or
Secure and Safe Computing Primer Examples of Desktop and Laptop standards and guidelines
 Secure and Safe Computing Primer Examples of Desktop and Laptop standards and guidelines 1. Implement anti-virus software An anti-virus program is necessary to protect your computer from malicious programs,
Secure and Safe Computing Primer Examples of Desktop and Laptop standards and guidelines 1. Implement anti-virus software An anti-virus program is necessary to protect your computer from malicious programs,
How To Protect Yourself Online
 NetBank security guide Commonwealth Bank Personal 1 Contents Page 4 5 5 5 7 7 9 9 9 11 12 12 13 13 13 14 14 14 16 16 16 17 18 18 19 19 20 21 Section Peace of mind with NetBank What are the common online
NetBank security guide Commonwealth Bank Personal 1 Contents Page 4 5 5 5 7 7 9 9 9 11 12 12 13 13 13 14 14 14 16 16 16 17 18 18 19 19 20 21 Section Peace of mind with NetBank What are the common online
Policy Document. Communications and Operation Management Policy
 Policy Document Communications and Operation Management Policy [23/08/2011] Page 1 of 11 Document Control Organisation Redditch Borough Council Title Communications and Operation Management Policy Author
Policy Document Communications and Operation Management Policy [23/08/2011] Page 1 of 11 Document Control Organisation Redditch Borough Council Title Communications and Operation Management Policy Author
High Speed Internet - User Guide. Welcome to. your world.
 High Speed Internet - User Guide Welcome to your world. 1 Welcome to your world :) Thank you for choosing Cogeco High Speed Internet. Welcome to your new High Speed Internet service. When it comes to a
High Speed Internet - User Guide Welcome to your world. 1 Welcome to your world :) Thank you for choosing Cogeco High Speed Internet. Welcome to your new High Speed Internet service. When it comes to a
Section 12 MUST BE COMPLETED BY: 4/22
 Test Out Online Lesson 12 Schedule Section 12 MUST BE COMPLETED BY: 4/22 Section 12.1: Best Practices This section discusses the following security best practices: Implement the Principle of Least Privilege
Test Out Online Lesson 12 Schedule Section 12 MUST BE COMPLETED BY: 4/22 Section 12.1: Best Practices This section discusses the following security best practices: Implement the Principle of Least Privilege
Level 3 Cambridge Technical in IT 05839/ 05840/ 05841/ 05842 Unit 3 Cyber security. Date Morning/Afternoon Time Allowed: 1 hour
 SAMPLE ASSESSMENT MATERIAL Level 3 Cambridge Technical in IT 05839/ 05840/ 05841/ 05842 Unit 3 Cyber security Date Morning/Afternoon Time Allowed: 1 hour You must have: The Insert (clean copy case study)
SAMPLE ASSESSMENT MATERIAL Level 3 Cambridge Technical in IT 05839/ 05840/ 05841/ 05842 Unit 3 Cyber security Date Morning/Afternoon Time Allowed: 1 hour You must have: The Insert (clean copy case study)
