1. Introduction Requesting and setting up a certificate Requesting a certificate Creating a certificate...
|
|
|
- Sara Miller
- 9 years ago
- Views:
Transcription
1 Contents 1. Introduction Requesting and setting up a certificate Requesting a certificate Creating a certificate Installing a certificate Setting up the certificate in Outlook Encryption with Outlook Exporting and importing certificates Exporting a certificate Importing a certificate Installing the ALDI Nord root certificate Downloading and providing certificates Uploading a certificate using the certificate portal Searching for certificates Encrypted communication Version 1.6 page 1 of 42
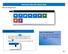
2 1. Introduction This document provides instructions on how to set up encrypted communication with ALDI Nord from the point of view of an external communication partner. If you have questions or queries, please contact your IT administrator. This guide was verified on 02/12/2014. Any changes from the side of the manufacturers can lead to a different behavior as described here. This guideline was developed on the following system: Windows 7 Internet Explorer 8 MS Outlook 2007 On other systems the views and procedures may be different. 2. Requesting and setting up a certificate This section explains how to request and set up a certificate for encrypted communication with ALDI Nord. ALDI Nord currently recommends the Certification Authority (trustcenter) Symantec. This ensures the highest possible compatibility with the encryption mechanisms used by ALDI Nord. As an example, in the following section the product "Digital ID for secure " from Symantec is requested. Please note that the described certificate in this section is issued for a single address and can only be used with this. Access to the address has to be via Outlook and the protocol POP3. The described certificate is valid for one year and entails costs. 2.1 Requesting a certificate Open the website Please choose the topic Products A-Z at Products & Solutions. Encrypted communication Version 1.6 page 2 of 42
3 Please choose Digital IDs for Secure . Now you have to buy the Digital ID by choosing Buy Online. Encrypted communication Version 1.6 page 3 of 42
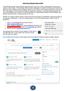
4 Please enter the address you want to use for the encrypted communication here. Please choose the Validity period and click Next. Pleas fill in all required information and click Next. Encrypted communication Version 1.6 page 4 of 42
5 Please agree with the Symantec Digital ID Subscriber Agreement to save your public key on the symantec website. Due to this ALDI can use this key for the encryption. Then please hit Submit. Please read the licence agreement carefully. If you agree, please hit Accept. Encrypted communication Version 1.6 page 5 of 42
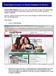
6 In the following half an hour you will get two s. With these s your -address will be confirmed. On the next pages you will find information about how to request a certificate. Depending on your Internet Explorer settings, you might have to follow the steps below to add the Symantec TrustCenter website to your trusted sites. First of all please start the Internet Explorer follow these steps: Choose "Tools", select "Internet Options" Encrypted communication Version 1.6 page 6 of 42
7 At "Internet Options", select the tab "Security" Select the item "Trusted sites" and then click "Sites" Now you can add the website "digitalid.pki.symantec.com" to the zone. Fill in this address and then click Add. To do so, click "Add". Once the website has been added, click "Close" to end the dialogue Encrypted communication Version 1.6 page 7 of 42
8 Once you have closed the Internet Options dialogue, you can continue to process your order. Please note the following before generating the key: Generate the key either with the browser "Mozilla Firefox" or "Internet Explorer". Do not perform any new installations of your system or browser before having received and installed the certificate from Symantec. The private key, which only works with the certificate, will otherwise be lost Creating a certificate You have received two s from Symantec. Please open the first and hit the given link. You will now be forwarded to the following page: Now please open the second from Symantec. There you will find a password which you fill in on this page. Then please login. Encrypted communication Version 1.6 page 8 of 42
9 Click yes After you logged in successfully, you will reach the following page. Please hit Generate. Encrypted communication Version 1.6 page 9 of 42
10 "Please note: The following pages may show some screenshots in german language. As you may receive the same info but in your local language, we suggest you to carefully read the instructions and continue as described." Click OK After generating the certificate must be installed on your computer. To perform this action please hit the button Install certificate. This step may need some minutes. Encrypted communication Version 1.6 page 10 of 42
11 Click yes By hitting the OK-button this step has been finished. You now may logout from the Symantec website. Encrypted communication Version 1.6 page 11 of 42
12 2.3. Installing a certificate This chapter describes how to install the certificate created in the prior steps. You have to do this step to comfortably communicate encrypted with ALDI by using your Outlook. At first, install the Root-CAs of the trustcenter Symatec. For this please open the webpage from Verisgn (a company of Symantec) with the following address: Here you will find the actual rootcertificates. You can download all rootvertificates. In the following it will describe as an example how to download the Symantec Class 1 Public Primary Certification Authority G6. Please right-click on Download Root Now and choose Save As. Encrypted communication Version 1.6 page 12 of 42
13 Save the file with the file-extension.cer. Depending on your Internet browser, you will receive a mask asking you to trust a new certificate authority (CA). Please choose the two options that contain trust to identify websites and trust to identify user or words to that effect and click OK. If you don t get that window please open the.cer -file. You may now get one of the following screens. You have to accept them as described: Click open Click "Allow" Encrypted communication Version 1.6 page 13 of 42
14 After that you must install the certificate: Click "Install Certificate..." Click "Next >" Encrypted communication Version 1.6 page 14 of 42
15 Then select "Place all certificates in the following store" and click "Browse..." Then highlight the entry "Trusted Root Certification Authorities" and click "OK" Finally, click "Finish" Now you may get a security request concerning the installation of a root certificate. Please confirm with Yes : Encrypted communication Version 1.6 page 15 of 42
16 Click "OK" 2.4. Setting up the certificate in Outlook This section explains how to set up your Outlook 2007 to use your certificate as a signature. Start Outlook Select "Tools" in the menu bar in Outlook. Click "Trust Center..." Encrypted communication Version 1.6 page 16 of 42
17 A digital signature in your message allows you to sign your message. The digital signature includes your certificate. Select " Security", match the settings under "Encrypted " and then click "Settings..." For encrypted communication, click "Choose..." Depending on the options previously selected, you may also have to select and store a signature certificate. Now select the requested certificate. Highlight the certificate and then click "OK" Encrypted communication Version 1.6 page 17 of 42
18 You can choose the Security Settings Name yourself. Match the settings and then click "OK" The default settings are now saved. Click "OK". Outlook 2007 is now set up to use your certificate. Encrypted communication Version 1.6 page 18 of 42
19 2.5. Encryption with Outlook This section explains how to correctly create your ALDI communication partner as a contact for encrypted communication. Creating a new contact is also required if for example ALDI Nord customizes the name of an address or if you are asked to do it by an ALDI Nord employee. Furthermore, the buttons required for encryption in Outlook 2007 are explained. Deleting the existing contact: To avoid problems, any contacts of the ALDI Nord communication partner which may already exist must be deleted. Select the category "Contacts" in Outlook. Right-click on the contact and then select "Delete" from the context menu Creating a new contact: To set up encrypted communication correctly, the contact of the ALDI Nord address must be set up as follows. Before you can create the contact using the certificate, there has to be a received signed from your ALDI communication partner. Please upload your public key to the ALDI Nord encryption infrastructure using this address: The ALDI Nord communication partner was therefore able to encrypt the with your public key and attach his/her public key as a signature in the sent to you. Encrypted communication Version 1.6 page 19 of 42
20 Firstly, open the most recent from your ALDI Nord communication partner with a double-click. Right click on the address in the field "From:" and then select "Add to Outlook Contacts" in the context menu A window opens for the new contact. Here you can fill in further information such as phone numbers. Select "Certificates" Encrypted communication Version 1.6 page 20 of 42
21 Check whether a relevant entry has been stored. You can then leave the Contact window by clicking "Save & Close" If you compose s to this contact in the future, always select the recipient from the address book. By previously adjusting the settings and installing the certificate, two buttons have been added to the window for a new message. Encrypted communication Version 1.6 page 21 of 42
22 These buttons show you whether the to be sent is to be signed and/or encrypted. Before you can send encrypted s, you must have received a signed from your ALDI Nord communication partner. It is necessary to publish your public key on the trust center s keyserver (cf. section 2.1) or on the site (cf. section 5.3) to let your communication partner send you an encrypted . In the appendix of an sent by your ALDI Nord contact you will receive the signature and the public key of your communication partner. You can recognize an encrypted and signed as follows: This symbol shows that the is encrypted. This symbol shows that the is digitally signed. 3. Exporting and importing certificates Certificates can be exported and imported so that they can be used on another computer. 3.1 Exporting a certificate If you would like to use the certificate requested and installed in section 2 on another computer for the address mentioned above, you have to export the installed certificate from the browser and import it into the browser of the computer to be used in future. This section explains how to do this. First, open the browser on the computer you have used so far (the browser used in section 2.1 to create the key/certificate). Encrypted communication Version 1.6 page 22 of 42
23 At "Tools", click on "Internet Options" At the tab "Content", click on "Certificates" Encrypted communication Version 1.6 page 23 of 42
24 The certificate to be exported (here Rudi Tester) appears under the tab "Personal". Highlight the certificate to be exported and then click on the button "Export..." Click "Next >" Encrypted communication Version 1.6 page 24 of 42
25 Select "Yes, export the private key" and click "Next >" Select "Include all certificates in the certification path if possible" and "Export all extended properties" and click "Next >" Encrypted communication Version 1.6 page 25 of 42
26 Choose a password, confirm it, and click "Next >" Choose a file name and store location the key will be exported to and click "Next >" Encrypted communication Version 1.6 page 26 of 42
27 Check the selected settings and click "Finish" Click "OK" Click "OK" Encrypted communication Version 1.6 page 27 of 42
28 3.2 Importing a certificate You must import the certificate previously exported on the new computer. Firstly, open Internet Explorer (or another browser). Double click on the key (certificate) to be imported. Click "Next >" Encrypted communication Version 1.6 page 28 of 42
29 At "File name", you usually do not have to make any changes. Click "Next >" Type in the password previously chosen for the private key and then click "Next >" Encrypted communication Version 1.6 page 29 of 42
30 The certificate store can be selected automatically. Click "Next >" Check your settings and then click "Finish" A security warning may then appear. Click "OK" to confirm the message. Finally, click "OK" Encrypted communication Version 1.6 page 30 of 42
31 4. Installing the ALDI Nord root certificate With the so-called "Root certificate (CER)" you can check the trust status of the ALDI Nord group user certificates. This means that the system you use can check if the user certificate is really from the ALDI Nord group and if it is still valid. You have three options for receiving the root certificate: 1. You have already received an from an ALDI employee and thus have access to the web messenger: you can download the root certificate there by clicking "Settings". 2. You can download the root certificate from the website " 3. You already have a certificate from one of the trustcenters supported by ALDI Nord and have published your public key on the keyserver. The from an ALDI Nord employee including the root certificate is sent to you directly. Installing the root certificate from the website is not different from installing it from the web messenger. For points 1 and 2, follow the steps below: Open the website in your Internet Explorer. Please note that the website is german: click on the link "Stammzertifikat" under the heading "Stammzertifikat der Unternehmungsgruppe ALDI Nord", as shown below. You will then be asked whether you would like to open or save the file. Click "Open". Encrypted communication Version 1.6 page 31 of 42
32 A security warning may appear. Click "Allow" to continue. The following messages will then appear: Click "Install Certificate " Encrypted communication Version 1.6 page 32 of 42
33 Click "Next >" Click "Next >" Encrypted communication Version 1.6 page 33 of 42
34 Click "Finish" Finally, the following message appears: For option 3, follow the steps below: You already have a certificate from one of the TrustCenters supported by ALDI Nord and have published your public key on the keyserver. Your ALDI Nord communication partner has then sent you an . Open this with a double-click. Encrypted communication Version 1.6 page 34 of 42
35 Click on this symbol The certificate appears, check the data and click "Trust" You can also display the certificate. Encrypted communication Version 1.6 page 35 of 42
36 Before installation a security warning will appear. The thumbprint of the ALDI Nord root certificate is shown here Finally, click "Yes" After installing the root certificate, you can now communicate encrypted with ALDI Nord. Encrypted communication Version 1.6 page 36 of 42
37 5. Alternative procedures for receiving and providing certificates In section 2 setting up for encrypted communication has been described. Here, the following assumptions were made: - A suitable certificate has been purchased and provided at the trust center. - There is an encrypted from an employee of ALDI Nord, which contains the necessary certificates for encryption in the appendix. This section describes two alternative ways to exchange keys using the ALDI certportal Downloading a certificate of a communication partner If the public certificate of an ALDI employee is needed for encrypting , it can be downloaded from the ALDI certportal. Follow this link: Change the language to English. Insert the address of the required contact person as well as the security code at the bottom. Please confirm with Search. Encrypted communication Version 1.6 page 37 of 42
38 Now you can see all existing certificates of this person. Click on the entry to get more information. By using this button, you can download the certificate of your contact person. Sometimes there is more than one certificate shown for an address. Because of that, please check the area Key Usage. Data Encipherment has to be listed for a key to use it for encryption. Encrypted communication Version 1.6 page 38 of 42
39 5.2. Matching a downloaded certificate to an Outlook contact The following describes the way you set up encryption using the certificate you downloaded from This step differs from the steps described in section 2.5 because here no signed from an ALDI Nord employee is needed. The following screenshots are in german language, please use the respective buttons and options as shown and explained in your client software. If you have already created a contact for your communication partner, lease open it and continue with the next step. If you have not, please create one by choosing new or new element and then contact. Please insert your contact information now. The address has to match to the one of the downloaded public certificate. Afterwards please go to certificates. Encrypted communication Version 1.6 page 39 of 42
40 Please enter Import... Please choose the downloaded certificate and hit Open. Encrypted communication Version 1.6 page 40 of 42
41 Please continue now as described in section Uploading own certificates If you already use certificates for encrypting via S/MIME, but these are not uploaded to the keyserver of the trust center, there is the possibility to upload them to the ALDI certportal. Follow this link: Change the language to English. Choose Publish. Encrypted communication Version 1.6 page 41 of 42
42 Move to user certificate and insert your informations. After that, please confirm with transmit. To finish this process, please contact your ALDI communication partner so that he can release your certificate internally for use. Encrypted communication Version 1.6 page 42 of 42
Adding Digital Signature and Encryption in Outlook
 Adding Digital Signature and Encryption in Outlook Using Outlook, the email messages can be signed and encrypted by a digital certificate. To digitally sign a message in Outlook some conditions must be
Adding Digital Signature and Encryption in Outlook Using Outlook, the email messages can be signed and encrypted by a digital certificate. To digitally sign a message in Outlook some conditions must be
Reading an email sent with Voltage SecureMail. Using the Voltage SecureMail Zero Download Messenger (ZDM)
 Reading an email sent with Voltage SecureMail Using the Voltage SecureMail Zero Download Messenger (ZDM) SecureMail is an email protection service developed by Voltage Security, Inc. that provides email
Reading an email sent with Voltage SecureMail Using the Voltage SecureMail Zero Download Messenger (ZDM) SecureMail is an email protection service developed by Voltage Security, Inc. that provides email
Extracting an S/MIME certificate from a digital signature
 Extracting an S/MIME certificate from a digital signature Instructions for Microsoft Outlook 2007 and 2010 Document User_Instruction_Outlook_Certificate_Handling Status Final Date: 03.06.2012 Version:
Extracting an S/MIME certificate from a digital signature Instructions for Microsoft Outlook 2007 and 2010 Document User_Instruction_Outlook_Certificate_Handling Status Final Date: 03.06.2012 Version:
Adobe Digital Signatures in Adobe Acrobat X Pro
 Adobe Digital Signatures in Adobe Acrobat X Pro Setting up a digital signature with Adobe Acrobat X Pro: 1. Open the PDF file you wish to sign digitally. 2. Click on the Tools menu in the upper right corner.
Adobe Digital Signatures in Adobe Acrobat X Pro Setting up a digital signature with Adobe Acrobat X Pro: 1. Open the PDF file you wish to sign digitally. 2. Click on the Tools menu in the upper right corner.
Email-Encryption with business partners
 Email-Encryption with business partners Date: 02. November 2006 Document type: User description Version: 1.2 Author: Volker Gebhard, Redaktionsteam WG PKI cio.siemens.com Table of contents: 1. Intention
Email-Encryption with business partners Date: 02. November 2006 Document type: User description Version: 1.2 Author: Volker Gebhard, Redaktionsteam WG PKI cio.siemens.com Table of contents: 1. Intention
eadvantage Certificate Enrollment Procedures
 eadvantage Certificate Enrollment Procedures Purpose: Instructions for members to obtain a digital certificate which is a requirement to conduct financial transactions with the Federal Home Loan Bank of
eadvantage Certificate Enrollment Procedures Purpose: Instructions for members to obtain a digital certificate which is a requirement to conduct financial transactions with the Federal Home Loan Bank of
Virtual Office Remote Installation Guide
 Virtual Office Remote Installation Guide Table of Contents VIRTUAL OFFICE REMOTE INSTALLATION GUIDE... 3 UNIVERSAL PRINTER CONFIGURATION INSTRUCTIONS... 12 CHANGING DEFAULT PRINTERS ON LOCAL SYSTEM...
Virtual Office Remote Installation Guide Table of Contents VIRTUAL OFFICE REMOTE INSTALLATION GUIDE... 3 UNIVERSAL PRINTER CONFIGURATION INSTRUCTIONS... 12 CHANGING DEFAULT PRINTERS ON LOCAL SYSTEM...
for esigntrust Personal Secure Email Enrollment and Generation Guide Operation Guide Microsoft Windows System & Internet Explorer Users
 esigntrust Personal Secure Email Enrollment for and Generation Guide Microsoft Windows System & Internet Explorer Users Operation Guide version. OGXP-SC-EN-1.0.050913 Copyright Macao Post esigntrust Certification
esigntrust Personal Secure Email Enrollment for and Generation Guide Microsoft Windows System & Internet Explorer Users Operation Guide version. OGXP-SC-EN-1.0.050913 Copyright Macao Post esigntrust Certification
Email Account Create for Outlook Express
 Email Account Create for Outlook Express Click Start Menu Choose Outlook Express Click Tools menu from Menu Bar and then click Accounts In Internet Account Wizard, Click Add Button and Click Mail. 1 In
Email Account Create for Outlook Express Click Start Menu Choose Outlook Express Click Tools menu from Menu Bar and then click Accounts In Internet Account Wizard, Click Add Button and Click Mail. 1 In
1. Open the preferences screen by opening the Mail menu and selecting Preferences...
 Using TLS encryption with OS X Mail This guide assumes that you have already created an account in Mail. If you have not, you can use the new account wizard. The new account wizard is in the Accounts window
Using TLS encryption with OS X Mail This guide assumes that you have already created an account in Mail. If you have not, you can use the new account wizard. The new account wizard is in the Accounts window
Using Internet or Windows Explorer to Upload Your Site
 Using Internet or Windows Explorer to Upload Your Site This article briefly describes what an FTP client is and how to use Internet Explorer or Windows Explorer to upload your Web site to your hosting
Using Internet or Windows Explorer to Upload Your Site This article briefly describes what an FTP client is and how to use Internet Explorer or Windows Explorer to upload your Web site to your hosting
PKI Contacts PKI for Fraunhofer Contacts
 Fraunhofer Competence Center PKI PKI Contacts PKI for Fraunhofer Contacts User manual for communication partners of the Fraunhofer-Gesellschaft Author[s]: Uwe Bendisch, Maximilian Gottwald As at: 15.10.2013
Fraunhofer Competence Center PKI PKI Contacts PKI for Fraunhofer Contacts User manual for communication partners of the Fraunhofer-Gesellschaft Author[s]: Uwe Bendisch, Maximilian Gottwald As at: 15.10.2013
Secure e-mail transaction guidelines for external users with Commission personnel.
 Secure e-mail transaction guidelines for external users with Commission personnel. This document describes in general the basic requirements to set up secure (encrypted) e- mail communication between external
Secure e-mail transaction guidelines for external users with Commission personnel. This document describes in general the basic requirements to set up secure (encrypted) e- mail communication between external
Advanced Digital Imaging
 Asset Management System User Interface Cabin River Web Solutions Overview The ADI Asset Management System allows customers and ADI to share digital assets (images and files) in a controlled environment.
Asset Management System User Interface Cabin River Web Solutions Overview The ADI Asset Management System allows customers and ADI to share digital assets (images and files) in a controlled environment.
Exostar LDAP Proxy / SecureEmail Setup Guide. This document provides information on the following topics:
 This document provides information on the following topics: Email Encryption set-up Outlook 2003 Email Encryption set-up Outlook 2007 Email Encryption set-up Outlook 2010 Email Encryption set-up Outlook
This document provides information on the following topics: Email Encryption set-up Outlook 2003 Email Encryption set-up Outlook 2007 Email Encryption set-up Outlook 2010 Email Encryption set-up Outlook
TCS-CA. Outlook Express Configuration [VERSION 1.0] U S E R G U I D E
![TCS-CA. Outlook Express Configuration [VERSION 1.0] U S E R G U I D E TCS-CA. Outlook Express Configuration [VERSION 1.0] U S E R G U I D E](/thumbs/30/14423884.jpg) U S E R G U I D E TCS-CA Outlook Express Configuration [VERSION 1.0] C O N T E N T S 1 DESCRIPTION... 3 2 OUTLOOK EXPRESS AND CERTIFICATES... 4 3 ENABLING SECURITY SETTINGS FOR MAIL ACCOUNT... 5 3.1 Settings
U S E R G U I D E TCS-CA Outlook Express Configuration [VERSION 1.0] C O N T E N T S 1 DESCRIPTION... 3 2 OUTLOOK EXPRESS AND CERTIFICATES... 4 3 ENABLING SECURITY SETTINGS FOR MAIL ACCOUNT... 5 3.1 Settings
User Guide May 2013. Using Certificates in Outlook Express
 User Guide May 2013 Using Certificates in Outlook Express FIGU RES... FIGURES.... T I TL E..............................................................................................................................
User Guide May 2013 Using Certificates in Outlook Express FIGU RES... FIGURES.... T I TL E..............................................................................................................................
When you have decided what to include in your signature, you will need to open the signatures and stationery dialogue box:
 Signatures An email signature is a block of information which is added to the bottom of an email to give the recipient information about the sender. It functions in a similar way to using headed paper
Signatures An email signature is a block of information which is added to the bottom of an email to give the recipient information about the sender. It functions in a similar way to using headed paper
SECURE EMAIL USER GUIDE OUTLOOK 2000
 WELLS FARGO AUTHENTICATION SERVICES DATED: MAY 2003 TABLE OF CONTENTS GENERAL INFORMATION... 1 INSTALLING THE WELLS FARGO ROOT CERTIFICATE CHAIN.. 2 INSTALLING THE CERTIFICATES INTO IE... 3 SETTING UP
WELLS FARGO AUTHENTICATION SERVICES DATED: MAY 2003 TABLE OF CONTENTS GENERAL INFORMATION... 1 INSTALLING THE WELLS FARGO ROOT CERTIFICATE CHAIN.. 2 INSTALLING THE CERTIFICATES INTO IE... 3 SETTING UP
APNS Certificate generating and installation
 APNS Certificate generating and installation Quick Guide for generating and installing an Apple APNS Certificate Version: x.x MobiDM Quick Guide for APNS Certificate Page 1 Index 1. APPLE APNS CERTIFICATE...
APNS Certificate generating and installation Quick Guide for generating and installing an Apple APNS Certificate Version: x.x MobiDM Quick Guide for APNS Certificate Page 1 Index 1. APPLE APNS CERTIFICATE...
(CP) Claim Processing Electronic Select Short Cut Key (F12) Type in Menu Id:
 Manual Section 4 Claim Processing (CP) Claim Processing Electronic Select Short Cut Key (F12) Type in Menu Id: CP and enter The # symbol will generate the next Claim ID Process Type: Proof (This will check
Manual Section 4 Claim Processing (CP) Claim Processing Electronic Select Short Cut Key (F12) Type in Menu Id: CP and enter The # symbol will generate the next Claim ID Process Type: Proof (This will check
Secure File Transfer Training Guide. Secure File Transfer Training Guide. Author: Glow Team Page 1 of 15 Ref: GC265_v1.1
 Secure File Transfer Training Guide Internet Explorer Version Ref: GC265_v1.1 Author: Glow Team Page 1 of 15 Ref: GC265_v1.1 Contents Introduction... 3 Prerequisites for this guide... 3 What is Secure
Secure File Transfer Training Guide Internet Explorer Version Ref: GC265_v1.1 Author: Glow Team Page 1 of 15 Ref: GC265_v1.1 Contents Introduction... 3 Prerequisites for this guide... 3 What is Secure
Installing your Digital Certificate & Using on MS Out Look 2007.
 Installing your Digital Certificate & Using on MS Out Look 2007. Note: This technical paper is only to guide you the steps to follow on how to configure and use digital signatures. Therefore Certificate
Installing your Digital Certificate & Using on MS Out Look 2007. Note: This technical paper is only to guide you the steps to follow on how to configure and use digital signatures. Therefore Certificate
gpg4o Manual Version 3.0
 gpg4o Manual Version 3.0 Table of Contents 1 GENERAL... 3 2 SYSTEM REQUIREMENTS... 4 3 INSTALLATION... 5 3.1 Required Software... 5 3.2 Installing GnuPG... 5 3.3 Installing gpg4o... 10 3.4 Setting gpg4o...
gpg4o Manual Version 3.0 Table of Contents 1 GENERAL... 3 2 SYSTEM REQUIREMENTS... 4 3 INSTALLATION... 5 3.1 Required Software... 5 3.2 Installing GnuPG... 5 3.3 Installing gpg4o... 10 3.4 Setting gpg4o...
1. Open Thunderbird. If the Import Wizard window opens, select Don t import anything and click Next and go to step 3.
 Thunderbird The changes that need to be made in the email programs will be the following: Incoming mail server: newmail.one-eleven.net Outgoing mail server (SMTP): newmail.one-eleven.net You will also
Thunderbird The changes that need to be made in the email programs will be the following: Incoming mail server: newmail.one-eleven.net Outgoing mail server (SMTP): newmail.one-eleven.net You will also
1 Login to your CSUF student email account and click on the Settings icon ( ) at the far right.
 Connect to Your Student Email: Microsoft Outlook for PC Before you can access your student email account on your e-mail client, you must first enable POP/IMAP features on your student email account and
Connect to Your Student Email: Microsoft Outlook for PC Before you can access your student email account on your e-mail client, you must first enable POP/IMAP features on your student email account and
SMS for Outlook. Installation, Configuration and Usage Guide
 SMS for Outlook Installation, Configuration and Usage Guide INTRODUCTION Installing TxTStream s SMS for Outlook is easy and will only take a minute or two. We will be using screen shots from a Windows
SMS for Outlook Installation, Configuration and Usage Guide INTRODUCTION Installing TxTStream s SMS for Outlook is easy and will only take a minute or two. We will be using screen shots from a Windows
CCH Axcess Portal Client User Guide
 CCH Axcess Portal Client User Guide Keys Quick reference to the key aspects of a particular function Icon Legend Tip Notes Best practice tips and shortcuts Informational notes about functions Warning Important
CCH Axcess Portal Client User Guide Keys Quick reference to the key aspects of a particular function Icon Legend Tip Notes Best practice tips and shortcuts Informational notes about functions Warning Important
E-mail Encryption. How do I send my e-mail encryption key?
 E-mail Encryption SecurenCrypt e-mail encryption was designed to work as a plug-in with Microsoft Outlook. The following instructions are geared toward users encrypting e-mail with Outlook. However, throughout
E-mail Encryption SecurenCrypt e-mail encryption was designed to work as a plug-in with Microsoft Outlook. The following instructions are geared toward users encrypting e-mail with Outlook. However, throughout
Using TLS Encryption with Microsoft Outlook 2007
 Using TLS Encryption with Microsoft Outlook 2007 This guide is meant to be used with Microsoft Outlook 2007. While the instructions are similar, the menu layouts and options have changed since the previous
Using TLS Encryption with Microsoft Outlook 2007 This guide is meant to be used with Microsoft Outlook 2007. While the instructions are similar, the menu layouts and options have changed since the previous
NICCA User Guide for digitally signing email Using Digital Signature Certificate (DSC) in Outlook Express
 NICCA User Guide for digitally signing email Using Digital Signature Certificate (DSC) in Outlook Express 1. DESCRIPTION This guide explains the procedure for using the NICCA issued digital certificate
NICCA User Guide for digitally signing email Using Digital Signature Certificate (DSC) in Outlook Express 1. DESCRIPTION This guide explains the procedure for using the NICCA issued digital certificate
Registration and Renewal procedure for Dexia Certificate
 Registration and Renewal procedure for Dexia Certificate GTU Environment Dexia Users Associated Dexia Technology Services Page: 1 / 25 Table of contents TABLE OF CONTENTS 2 1 INTRODUCTION 3 2 CONTACT 3
Registration and Renewal procedure for Dexia Certificate GTU Environment Dexia Users Associated Dexia Technology Services Page: 1 / 25 Table of contents TABLE OF CONTENTS 2 1 INTRODUCTION 3 2 CONTACT 3
School Mail System. - Access through Office 365 Exchange Online. User Guide FOR. Education Bureau (EDB)
 School Mail System - Access through Office 365 Exchange Online User Guide FOR Education Bureau (EDB) Version: 1.0 May 2015 The Government of the Hong Kong Special Administrative Region The contents of
School Mail System - Access through Office 365 Exchange Online User Guide FOR Education Bureau (EDB) Version: 1.0 May 2015 The Government of the Hong Kong Special Administrative Region The contents of
Getting a Free Comodo Email Certificate
 Getting a Free Comodo Email Certificate Go here and click on Get It Free Now button. http://www.instantssl.com/ssl certificate products/free email certificate.html It will take you to this form which you
Getting a Free Comodo Email Certificate Go here and click on Get It Free Now button. http://www.instantssl.com/ssl certificate products/free email certificate.html It will take you to this form which you
Sending an Encrypted/Unencrypted Message. Let's Begin: Log In and Set Up Security Questions. Create Additional ProMailSource Accounts:
 Let's Begin: Log In and Set Up Security Questions To start, you can log in from the ProMailSource home page. Sending an Encrypted/Unencrypted Message Every message you send through ProMailSource is automatically
Let's Begin: Log In and Set Up Security Questions To start, you can log in from the ProMailSource home page. Sending an Encrypted/Unencrypted Message Every message you send through ProMailSource is automatically
Jumble for Microsoft Outlook
 Jumble for Microsoft Outlook Jumble is a zero knowledge, end- to- end email encryption solution that integrates with existing email platforms. Jumble integrates at the email client level and removes the
Jumble for Microsoft Outlook Jumble is a zero knowledge, end- to- end email encryption solution that integrates with existing email platforms. Jumble integrates at the email client level and removes the
Using SSH Secure Shell Client for FTP
 Using SSH Secure Shell Client for FTP The SSH Secure Shell for Workstations Windows client application features this secure file transfer protocol that s easy to use. Access the SSH Secure FTP by double-clicking
Using SSH Secure Shell Client for FTP The SSH Secure Shell for Workstations Windows client application features this secure file transfer protocol that s easy to use. Access the SSH Secure FTP by double-clicking
ClicktoFax Service Usage Manual
 ClicktoFax Service Usage Manual 1. Log in to Fax Service 2. Configure your account 3. Send a fax 4. Receive a fax/search for Faxes/View Faxes 5. Logout 6. Additional Support 1. Log into fax service: a.
ClicktoFax Service Usage Manual 1. Log in to Fax Service 2. Configure your account 3. Send a fax 4. Receive a fax/search for Faxes/View Faxes 5. Logout 6. Additional Support 1. Log into fax service: a.
ACT State Testing Online Services Tutorial
 ACT State Testing Online Services Tutorial Back-up Test Supervisor Version Released July, 2009 2009 by ACT, Inc., All rights reserved. Back-up Test Supervisor Online Profile Form Introduction The Back-up
ACT State Testing Online Services Tutorial Back-up Test Supervisor Version Released July, 2009 2009 by ACT, Inc., All rights reserved. Back-up Test Supervisor Online Profile Form Introduction The Back-up
Web Conference Manager
 Web Conference Manager Reference Guide Table of Contents 1. Introduction to GTB Web Conferencing... 1 2. System Requirements... 2 3. Web Conferencing Host... 3 Accessing the server... 3 Testing your system...
Web Conference Manager Reference Guide Table of Contents 1. Introduction to GTB Web Conferencing... 1 2. System Requirements... 2 3. Web Conferencing Host... 3 Accessing the server... 3 Testing your system...
How to Add Users 1. 2.
 Administrator Guide Contents How to Add Users... 2 How to Delete a User... 9 How to Create Sub-groups... 12 How to Edit the Email Sent Out to New Users... 14 How to Edit and Add a Logo to Your Group's
Administrator Guide Contents How to Add Users... 2 How to Delete a User... 9 How to Create Sub-groups... 12 How to Edit the Email Sent Out to New Users... 14 How to Edit and Add a Logo to Your Group's
1. Open the Account Settings window by clicking on Account Settings from the Entourage menu.
 Using TLS Encryption with Microsoft Entourage This guide assumes that you have previously configured Entourage to work with your Beloit College email account. If you have not, you can create an account
Using TLS Encryption with Microsoft Entourage This guide assumes that you have previously configured Entourage to work with your Beloit College email account. If you have not, you can create an account
Learn how to create web enabled (browser) forms in InfoPath 2013 and publish them in SharePoint 2013. InfoPath 2013 Web Enabled (Browser) forms
 Learn how to create web enabled (browser) forms in InfoPath 2013 and publish them in SharePoint 2013. InfoPath 2013 Web Enabled (Browser) forms InfoPath 2013 Web Enabled (Browser) forms Creating Web Enabled
Learn how to create web enabled (browser) forms in InfoPath 2013 and publish them in SharePoint 2013. InfoPath 2013 Web Enabled (Browser) forms InfoPath 2013 Web Enabled (Browser) forms Creating Web Enabled
User Guide. Digital Signature
 User Guide Digital Signature ENTRUST ESP 9..2 Document version: 2.2 Publication date: January 2014 This guide is the exclusive property of Notarius Inc. All reproduction, printing or distribution of this
User Guide Digital Signature ENTRUST ESP 9..2 Document version: 2.2 Publication date: January 2014 This guide is the exclusive property of Notarius Inc. All reproduction, printing or distribution of this
Email Update Instructions
 1 Email Update Instructions Contents Email Client Settings The Basics... 3 Outlook 2013... 4 Outlook 2007... 6 Outlook Express... 7 Windows Mail... 8 Thunderbird 3... 9 Apple Mail... 10 2 Email Client
1 Email Update Instructions Contents Email Client Settings The Basics... 3 Outlook 2013... 4 Outlook 2007... 6 Outlook Express... 7 Windows Mail... 8 Thunderbird 3... 9 Apple Mail... 10 2 Email Client
MiraCosta College now offers two ways to access your student virtual desktop.
 MiraCosta College now offers two ways to access your student virtual desktop. We now feature the new VMware Horizon View HTML access option available from https://view.miracosta.edu. MiraCosta recommends
MiraCosta College now offers two ways to access your student virtual desktop. We now feature the new VMware Horizon View HTML access option available from https://view.miracosta.edu. MiraCosta recommends
JCT CONTRACTS DIGITAL SERVICE QUICK REFERENCE USER GUIDE
 JCT CONTRACTS DIGITAL SERVICE QUICK REFERENCE USER GUIDE CONTENTS ACCESSING THE DIGITAL SERVICE ONLINE UPDATES FIND YOUR CONTRACT WORKING ON A CONTRACT Filling out the contract Editing your contract Saving
JCT CONTRACTS DIGITAL SERVICE QUICK REFERENCE USER GUIDE CONTENTS ACCESSING THE DIGITAL SERVICE ONLINE UPDATES FIND YOUR CONTRACT WORKING ON A CONTRACT Filling out the contract Editing your contract Saving
Using Voltage SecureMail
 Using Voltage SecureMail Using Voltage SecureMail Desktop Based on the breakthrough Identity-Based Encryption technology, Voltage SecureMail makes sending a secure email as easy as sending it without encryption.
Using Voltage SecureMail Using Voltage SecureMail Desktop Based on the breakthrough Identity-Based Encryption technology, Voltage SecureMail makes sending a secure email as easy as sending it without encryption.
PaperClip. em4 Cloud Client. Setup Guide
 PaperClip em4 Cloud Client Setup Guide Copyright Information Copyright 2014, PaperClip Inc. - The PaperClip32 product name and PaperClip Logo are registered trademarks of PaperClip Inc. All brand and product
PaperClip em4 Cloud Client Setup Guide Copyright Information Copyright 2014, PaperClip Inc. - The PaperClip32 product name and PaperClip Logo are registered trademarks of PaperClip Inc. All brand and product
Encrypting Your Email Using the free COMODO Secure Email Certificate
 Encrypting Your Email Using the free COMODO Secure Email Certificate These instructions will guide you through the process of getting a free Secure Email Certificate Issued by COMODO. This document will
Encrypting Your Email Using the free COMODO Secure Email Certificate These instructions will guide you through the process of getting a free Secure Email Certificate Issued by COMODO. This document will
Outlook Web App User Guide
 Outlook Web App Table of Contents QUICK REFERENCE... 2 OUTLOOK WEB APP URL... 2 Imagine! Help Desk...... 2 OUTLOOK WEB APP MAIN WINDOW... 2 KEY NEW FEATURES... 3 GETTING STARTED WITH OUTLOOK... 4 LOGGING
Outlook Web App Table of Contents QUICK REFERENCE... 2 OUTLOOK WEB APP URL... 2 Imagine! Help Desk...... 2 OUTLOOK WEB APP MAIN WINDOW... 2 KEY NEW FEATURES... 3 GETTING STARTED WITH OUTLOOK... 4 LOGGING
User Guide Using Certificate in Microsoft Outlook Express
 CERTIFYING AUTHORITY User Guide Using Certificate in Microsoft Outlook Express CONTACT TATA CONSULTANCY SERVICES - [E-SECURITY: PKI SERVICES] 6TH FLOOR, 5-9-62, KHAN LATEEF KHAN ESTATE FATEH MAIDAN ROAD,
CERTIFYING AUTHORITY User Guide Using Certificate in Microsoft Outlook Express CONTACT TATA CONSULTANCY SERVICES - [E-SECURITY: PKI SERVICES] 6TH FLOOR, 5-9-62, KHAN LATEEF KHAN ESTATE FATEH MAIDAN ROAD,
DigitalPersona Privacy Manager Pro
 DigitalPersona Privacy Manager Pro DigitalPersona Privacy Manager Pro is a centrally-managed secure communication solution for businesses. It allows sensitive documents and communications to remain private,
DigitalPersona Privacy Manager Pro DigitalPersona Privacy Manager Pro is a centrally-managed secure communication solution for businesses. It allows sensitive documents and communications to remain private,
Zarafa S/MIME Webaccess Plugin User Manual. Client side configuration and usage.
 Zarafa S/MIME Webaccess Plugin User Manual Client side configuration and usage. Zarafa S/MIME Webaccess plugin provides S/MIME functionality, for receiving and sending encrypted and / or sign messages
Zarafa S/MIME Webaccess Plugin User Manual Client side configuration and usage. Zarafa S/MIME Webaccess plugin provides S/MIME functionality, for receiving and sending encrypted and / or sign messages
GroupWise Web Access 8.0
 GroupWise Web Access 8.0 How to check your email via the Internet For More Information, please contact: Administrative Office of the Courts Technology Help Desk (615) 532 9503 or (800) 448-7980 Table of
GroupWise Web Access 8.0 How to check your email via the Internet For More Information, please contact: Administrative Office of the Courts Technology Help Desk (615) 532 9503 or (800) 448-7980 Table of
RoboMail Mass Mail Software
 RoboMail Mass Mail Software RoboMail is a comprehensive mass mail software, which has a built-in e-mail server to send out e-mail without using ISP's server. You can prepare personalized e-mail easily.
RoboMail Mass Mail Software RoboMail is a comprehensive mass mail software, which has a built-in e-mail server to send out e-mail without using ISP's server. You can prepare personalized e-mail easily.
OUTLOOK WEB APP (OWA): MAIL
 Office 365 Navigation Pane: Navigating in Office 365 Click the App Launcher and then choose the application (i.e. Outlook, Calendar, People, etc.). To modify your personal account settings, click the Logon
Office 365 Navigation Pane: Navigating in Office 365 Click the App Launcher and then choose the application (i.e. Outlook, Calendar, People, etc.). To modify your personal account settings, click the Logon
Migrating Groupwise Data
 Migrating Groupwise Data Requirements: Windows Computer on CCSF admin network Outlook 2010 Groupwise 8 windows client Network access Office 365 login and password Groupwise login and password USB Flash
Migrating Groupwise Data Requirements: Windows Computer on CCSF admin network Outlook 2010 Groupwise 8 windows client Network access Office 365 login and password Groupwise login and password USB Flash
Simple Guide to Digital Signatures
 Simple Guide to Digital Signatures Rohas Nagpal Asian School of Cyber Laws About the author Rohas Nagpal is the founder President of Asian School of Cyber Laws. He advises Governments and corporates around
Simple Guide to Digital Signatures Rohas Nagpal Asian School of Cyber Laws About the author Rohas Nagpal is the founder President of Asian School of Cyber Laws. He advises Governments and corporates around
Upgrade of Business Systems Data Warehouse Reporting
 Upgrade of Business Systems Data Warehouse Reporting The Business Systems Data Warehouse Reporting System was upgraded to a new version of Business Objects the weekend of December 12 th. The current system
Upgrade of Business Systems Data Warehouse Reporting The Business Systems Data Warehouse Reporting System was upgraded to a new version of Business Objects the weekend of December 12 th. The current system
Open a PDF document using Adobe Reader, then click on the Tools menu on the upper left hand corner.
 This document illustrates how to digitally sign PDF documents using Acrobat Reader 11. The illustrations assume that the user already has a digital certificate. You will need the latest version of Adobe
This document illustrates how to digitally sign PDF documents using Acrobat Reader 11. The illustrations assume that the user already has a digital certificate. You will need the latest version of Adobe
Setting Up Your FTP Server
 Requirements:! A computer dedicated to FTP server only! Linksys router! TCP/IP internet connection Steps: Getting Started Configure Static IP on the FTP Server Computer: Setting Up Your FTP Server 1. This
Requirements:! A computer dedicated to FTP server only! Linksys router! TCP/IP internet connection Steps: Getting Started Configure Static IP on the FTP Server Computer: Setting Up Your FTP Server 1. This
Installation Guide. Research Computing Team V1.9 RESTRICTED
 Installation Guide Research Computing Team V1.9 RESTRICTED Document History This document relates to the BEAR DataShare service which is based on the product Power Folder, version 10.3.232 ( some screenshots
Installation Guide Research Computing Team V1.9 RESTRICTED Document History This document relates to the BEAR DataShare service which is based on the product Power Folder, version 10.3.232 ( some screenshots
ADFS Integration Guidelines
 ADFS Integration Guidelines Version 1.6 updated March 13 th 2014 Table of contents About This Guide 3 Requirements 3 Part 1 Configure Marcombox in the ADFS Environment 4 Part 2 Add Relying Party in ADFS
ADFS Integration Guidelines Version 1.6 updated March 13 th 2014 Table of contents About This Guide 3 Requirements 3 Part 1 Configure Marcombox in the ADFS Environment 4 Part 2 Add Relying Party in ADFS
HOW TO PURCHASE AND INSTALL YOUR VERISIGN DIGITAL SIGNATURE
 HOW TO PURCHASE AND INSTALL YOUR VERISIGN DIGITAL SIGNATURE (Instructions prepared compliments of PDF-It!) Morgan Babin-Reporting Solutions pdf-it Home How to obtain a Verisign Digital Signature 2 Check
HOW TO PURCHASE AND INSTALL YOUR VERISIGN DIGITAL SIGNATURE (Instructions prepared compliments of PDF-It!) Morgan Babin-Reporting Solutions pdf-it Home How to obtain a Verisign Digital Signature 2 Check
Using the jmrdesign Service Desk
 The jmrdesign Service Desk provides supported client users with a more comprehensive resource and easier to use interface. The jmrdesign Service Desk is designed to increase the efficiency and reduce the
The jmrdesign Service Desk provides supported client users with a more comprehensive resource and easier to use interface. The jmrdesign Service Desk is designed to increase the efficiency and reduce the
Email Update Instructions
 Email Update Instructions Table of Contents Email Client Settings The Basics... 2 Outlook 2013... 2 Outlook 2007... 4 Outlook Express... 6 Windows Mail... 7 Thunderbird 3... 9 Apple Mail... 11 1 Email
Email Update Instructions Table of Contents Email Client Settings The Basics... 2 Outlook 2013... 2 Outlook 2007... 4 Outlook Express... 6 Windows Mail... 7 Thunderbird 3... 9 Apple Mail... 11 1 Email
1. Open the preferences screen by opening the Mail menu and selecting Preferences...
 Using TLS encryption with OS X Mail This guide assumes that you have already created an account in Mail. If you have not, you can use the new account wizard. The new account wizard is in the Accounts window
Using TLS encryption with OS X Mail This guide assumes that you have already created an account in Mail. If you have not, you can use the new account wizard. The new account wizard is in the Accounts window
Using Your New Webmail
 1 Using Your New Webmail Contents Compose a New Message... 3 Add an Attachment... 5 Insert a Hyperlink... 6 Forward an Email... 7 Search Email... 8 Download Email from an existing POP3 Account... 9 Move
1 Using Your New Webmail Contents Compose a New Message... 3 Add an Attachment... 5 Insert a Hyperlink... 6 Forward an Email... 7 Search Email... 8 Download Email from an existing POP3 Account... 9 Move
Carillon eshop User s Guide
 Carillon eshop User s Guide Prepared by: Carillon Information Security, Inc. Version: 3.0 Updated on: 2015-01-29 Status: PUBLIC Contents Carillon eshop User Guide 1 Introduction... 4 1.1 Prerequisites...
Carillon eshop User s Guide Prepared by: Carillon Information Security, Inc. Version: 3.0 Updated on: 2015-01-29 Status: PUBLIC Contents Carillon eshop User Guide 1 Introduction... 4 1.1 Prerequisites...
Frequently Asked Questions
 Frequently Asked Questions Development & Maintenance of Web Based Portal and MIS for Monitoring & Evaluation of Vocational Training Improvement Project Version 1.0 Help Desk: [email protected] 0120
Frequently Asked Questions Development & Maintenance of Web Based Portal and MIS for Monitoring & Evaluation of Vocational Training Improvement Project Version 1.0 Help Desk: [email protected] 0120
Initial Setup of Microsoft Outlook with Google Apps Sync for Windows 7. Initial Setup of Microsoft Outlook with Google Apps Sync for Windows 7
 Microsoft Outlook with Initial Setup of Concept This document describes the procedures for setting up the Microsoft Outlook email client to download messages from Google Mail using Internet Message Access
Microsoft Outlook with Initial Setup of Concept This document describes the procedures for setting up the Microsoft Outlook email client to download messages from Google Mail using Internet Message Access
Installing your certificate on your Windows PC
 Installing your certificate on your PC Choose your email software below to learn how to obtain and install a digital certificate. Microsoft Outlook Mail Using Outlook or Mail Step one Visit Comodo for
Installing your certificate on your PC Choose your email software below to learn how to obtain and install a digital certificate. Microsoft Outlook Mail Using Outlook or Mail Step one Visit Comodo for
Masergy Fax Solutions Virtual Fax and Fax Line User Guide
 Masergy Fax Solutions Virtual Fax and Fax Line User Guide Version 1 July 30, 2015 Table of Contents Getting Started 3 Installation 3 Print to Fax..9 Web to Fax.13 Receiving Fax..17 Page 2 of 17 Getting
Masergy Fax Solutions Virtual Fax and Fax Line User Guide Version 1 July 30, 2015 Table of Contents Getting Started 3 Installation 3 Print to Fax..9 Web to Fax.13 Receiving Fax..17 Page 2 of 17 Getting
Exchange 2010 PKI Configuration Guide
 Exchange 2010 PKI Configuration Guide Overview 1. Summary 2. Environment 3. Configuration a) Active Directory Configuration b) CA Configuration c) Exchange Server IIS Configuration d) Exchange Configuration
Exchange 2010 PKI Configuration Guide Overview 1. Summary 2. Environment 3. Configuration a) Active Directory Configuration b) CA Configuration c) Exchange Server IIS Configuration d) Exchange Configuration
E-mail encryption with business partners
 (Guideline for ) Date: 2013-07-15 Document type: user description Version: 3.2 : Editorial team PKI cio.siemens.com Table of contents 1. Intention of the document:... 3 2. Prerequisites on business partner
(Guideline for ) Date: 2013-07-15 Document type: user description Version: 3.2 : Editorial team PKI cio.siemens.com Table of contents 1. Intention of the document:... 3 2. Prerequisites on business partner
Schools Remote Access Server
 Schools Remote Access Server This system is for school use only. Not for personal or private file use. Please observe all of the school district IT rules. 6076 State Farm Rd., Guilderland, NY 12084 Phone:
Schools Remote Access Server This system is for school use only. Not for personal or private file use. Please observe all of the school district IT rules. 6076 State Farm Rd., Guilderland, NY 12084 Phone:
Using Entrust certificates with Microsoft Office and Windows
 Entrust Managed Services PKI Using Entrust certificates with Microsoft Office and Windows Document issue: 1.0 Date of issue: May 2009 Copyright 2009 Entrust. All rights reserved. Entrust is a trademark
Entrust Managed Services PKI Using Entrust certificates with Microsoft Office and Windows Document issue: 1.0 Date of issue: May 2009 Copyright 2009 Entrust. All rights reserved. Entrust is a trademark
Getting Started. Install the Omni Mobile Client
 Getting Started This Quick Start Guide is for Windows Mobile Smart Phones (no touch-screen support) devices. There is a separate Quick Start Guide for Pocket PC and Windows Mobile touch-screen PDA and
Getting Started This Quick Start Guide is for Windows Mobile Smart Phones (no touch-screen support) devices. There is a separate Quick Start Guide for Pocket PC and Windows Mobile touch-screen PDA and
Internet E-Mail Encryption S/Mime Standard
 Internet E-Mail Encryption S/Mime Standard Disclaimer: Successfully setting up encryption functions in most e-mail clients is usually not a problematic task. However, it should be noted that, when configuring
Internet E-Mail Encryption S/Mime Standard Disclaimer: Successfully setting up encryption functions in most e-mail clients is usually not a problematic task. However, it should be noted that, when configuring
User Guide Trust Safety Accounting Upload PC Law and SFTP Software Release: Final Date
 User Guide Trust Safety Accounting Upload PC Law and SFTP Software Release: Final Date: July 22, 2015 TABLE OF CONTENTS Page TRUST SAFETY ACCOUNTING UPLOAD USER GUIDE... 2 BACKGROUND... 2 HOW TO USE THE
User Guide Trust Safety Accounting Upload PC Law and SFTP Software Release: Final Date: July 22, 2015 TABLE OF CONTENTS Page TRUST SAFETY ACCOUNTING UPLOAD USER GUIDE... 2 BACKGROUND... 2 HOW TO USE THE
Email Instructions. Outlook (Windows) Mail (Mac) Webmail Windows Live Mail iphone 4, 4S, 5, 5c, 5s Samsung Galaxy S4 BlackBerry
 Email Instructions Outlook (Windows) Mail (Mac) Webmail Windows Live Mail iphone 4, 4S, 5, 5c, 5s Samsung Galaxy S4 BlackBerry ii Table of Contents Table of Contents 1 Mail Account Settings 1 Account Set
Email Instructions Outlook (Windows) Mail (Mac) Webmail Windows Live Mail iphone 4, 4S, 5, 5c, 5s Samsung Galaxy S4 BlackBerry ii Table of Contents Table of Contents 1 Mail Account Settings 1 Account Set
BUSINESS CLASS POP3 E-MAIL END USER GUIDE TIME WARNER CABLE BUSINESS SERVICES VERSION 1.0, RELEASE 1.2
 BUSINESS CLASS POP3 E-MAIL END USER GUIDE TIME WARNER CABLE BUSINESS SERVICES VERSION 1.0, RELEASE 1.2 Table of Contents MANAGING E-MAIL ACCOUNTS... 3 GENERIC CONFIGURATION INSTRUCTIONS... 3 POP mail...
BUSINESS CLASS POP3 E-MAIL END USER GUIDE TIME WARNER CABLE BUSINESS SERVICES VERSION 1.0, RELEASE 1.2 Table of Contents MANAGING E-MAIL ACCOUNTS... 3 GENERIC CONFIGURATION INSTRUCTIONS... 3 POP mail...
Personal Online Banking:
 Personal Online Banking: If you access your account information through CNB Online Banking, our personal banking site, you will be able to import your account transactions directly into Quicken/QuickBooks.
Personal Online Banking: If you access your account information through CNB Online Banking, our personal banking site, you will be able to import your account transactions directly into Quicken/QuickBooks.
Google Docs A Tutorial
 Google Docs A Tutorial What is it? Google Docs is a free online program that allows users to create documents, spreadsheets and presentations online and share them with others for collaboration. This allows
Google Docs A Tutorial What is it? Google Docs is a free online program that allows users to create documents, spreadsheets and presentations online and share them with others for collaboration. This allows
To add files to your email, first create the email. When you have opened a new email:
 Email attachments You can send files, folders and other items within an email along with the mail message itself. Items which have been added to emails are called attachments. Adding an attachment to an
Email attachments You can send files, folders and other items within an email along with the mail message itself. Items which have been added to emails are called attachments. Adding an attachment to an
ECA IIS Instructions. January 2005
 ECA IIS Instructions January 2005 THIS PAGE INTENTIONALLY BLANK ECA IIS Instructions ii July 22, 2005 Table of Contents 1. Install Certificate in IIS 5.0... 1 2. Obtain and Install the ECA Root Certificate
ECA IIS Instructions January 2005 THIS PAGE INTENTIONALLY BLANK ECA IIS Instructions ii July 22, 2005 Table of Contents 1. Install Certificate in IIS 5.0... 1 2. Obtain and Install the ECA Root Certificate
All existing accounts will be listed. 2. Click Add and select Mail to add a new E-mail account (see Figure 2). Figure 1. Figure 2
 Microsoft Outlook Express 5.x, 6.0 This section describes how to configure Outlook Express to access POP E-mail. 1. Click Tools and select Accounts from the pull-down menu (see Figure 1). Figure 1 All
Microsoft Outlook Express 5.x, 6.0 This section describes how to configure Outlook Express to access POP E-mail. 1. Click Tools and select Accounts from the pull-down menu (see Figure 1). Figure 1 All
BillQuick Installation Guide for Microsoft SQL Server 2005 Express Edition
 Time Billing and Project Management Software Built With Your Industry Knowledge BillQuick Installation Guide for Microsoft SQL Server 2005 Express Edition BQE Software, Inc. 2601 Airport Drive Suite 380
Time Billing and Project Management Software Built With Your Industry Knowledge BillQuick Installation Guide for Microsoft SQL Server 2005 Express Edition BQE Software, Inc. 2601 Airport Drive Suite 380
AKO Email Shutdown Quick Reference Guide
 AKO Email Shutdown Quick Reference Guide NETWORK ENTERPRISE CENTER This guide explains how the Army is shutting down AKO Email and outlines steps you must take to ensure a smooth transition to full DoD
AKO Email Shutdown Quick Reference Guide NETWORK ENTERPRISE CENTER This guide explains how the Army is shutting down AKO Email and outlines steps you must take to ensure a smooth transition to full DoD
About DropSend. Sending Files with DropSend
 About DropSend DropSend is a service that allows businesses and individuals to send large files, store files online and collaborate in a quick and easy way. DropSend Business Plan will help your company
About DropSend DropSend is a service that allows businesses and individuals to send large files, store files online and collaborate in a quick and easy way. DropSend Business Plan will help your company
Outlook Express. Make Changes in Red: Open up Outlook Express. From the Menu Bar. Tools to Accounts - Click on. User Information
 Outlook Express Open up Outlook Express From the Menu Bar Tools to Accounts - Click on Mail Tab Click on mail.btconline.net mail (default) Click on Properties button Click on the General tab User Information
Outlook Express Open up Outlook Express From the Menu Bar Tools to Accounts - Click on Mail Tab Click on mail.btconline.net mail (default) Click on Properties button Click on the General tab User Information
TSM for Windows Installation Instructions: Download the latest TSM Client Using the following link:
 TSM for Windows Installation Instructions: Download the latest TSM Client Using the following link: ftp://ftp.software.ibm.com/storage/tivoli-storagemanagement/maintenance/client/v6r2/windows/x32/v623/
TSM for Windows Installation Instructions: Download the latest TSM Client Using the following link: ftp://ftp.software.ibm.com/storage/tivoli-storagemanagement/maintenance/client/v6r2/windows/x32/v623/
How to Order and Install Odette Certificates. Odette CA Help File and User Manual
 How to Order and Install Odette Certificates Odette CA Help File and User Manual 1 Release date 24.02.2014 Contents Preparation for Ordering an Odette Certificate... 3 Step 1: Prepare the information you
How to Order and Install Odette Certificates Odette CA Help File and User Manual 1 Release date 24.02.2014 Contents Preparation for Ordering an Odette Certificate... 3 Step 1: Prepare the information you
Recommended Browser Setting for MySBU Portal
 The MySBU portal is built using Microsoft s SharePoint technology framework, therefore, for the best viewing experience, Southwest Baptist University recommends the use of Microsoft s Internet Explorer,
The MySBU portal is built using Microsoft s SharePoint technology framework, therefore, for the best viewing experience, Southwest Baptist University recommends the use of Microsoft s Internet Explorer,
Cox Managed CPE Services. RADIUS Authentication for AnyConnect VPN Version 1.3 [Draft]
![Cox Managed CPE Services. RADIUS Authentication for AnyConnect VPN Version 1.3 [Draft] Cox Managed CPE Services. RADIUS Authentication for AnyConnect VPN Version 1.3 [Draft]](/thumbs/39/18543129.jpg) Cox Managed CPE Services RADIUS Authentication for AnyConnect VPN Version 1.3 [Draft] September, 2015 2015 by Cox Communications. All rights reserved. No part of this document may be reproduced or transmitted
Cox Managed CPE Services RADIUS Authentication for AnyConnect VPN Version 1.3 [Draft] September, 2015 2015 by Cox Communications. All rights reserved. No part of this document may be reproduced or transmitted
Remote Desktop Services
 Remote Desktop Services AMERICAN INSTITUTES FOR RESEARCH AIR REMOTE DESKTOP SERVICES (RDS) GUIDE Overview Welcome to AIR Remote Desktop Services! AIR Remote Desktop Services can be accessed from a Windows
Remote Desktop Services AMERICAN INSTITUTES FOR RESEARCH AIR REMOTE DESKTOP SERVICES (RDS) GUIDE Overview Welcome to AIR Remote Desktop Services! AIR Remote Desktop Services can be accessed from a Windows
Windows and MAC User Handbook Remote and Secure Connection Version 1.01 09/19/2013. User Handbook
 Windows and MAC User Handbook How to Connect Your PC or MAC Remotely and Securely to Your U.S. Department of Commerce Account Developed for You by the Office of IT Services (OITS)/IT Service Desk *** For
Windows and MAC User Handbook How to Connect Your PC or MAC Remotely and Securely to Your U.S. Department of Commerce Account Developed for You by the Office of IT Services (OITS)/IT Service Desk *** For
Encrypting Files Using AxCrypt
 Encrypting Files Using AxCrypt Documents, spreadsheets, databases, and other files that contain personal information or other sensitive information MUST BE encrypted when being transmitted to someone else
Encrypting Files Using AxCrypt Documents, spreadsheets, databases, and other files that contain personal information or other sensitive information MUST BE encrypted when being transmitted to someone else
