Mailing System: The Intra Mail
|
|
|
- Annis Jenkins
- 10 years ago
- Views:
Transcription
1
2 Mailing System: The Intra Mail Prof. T. Malik Asst. Professor, Telecommunication JSBT School of Engineering & Technology Bangaluru, India Ms. S. P. Harini Research Associate, Network Infrastructure Edith Cowan University, Australia Abstract: INTRAMAILING SYSTEM aims of providing a good communication interface for the organization. It can cut down the time of employees spend on routine communication tasks. Its successful implementation makes easy the job of employees in the organization. The basic problem is that the employees in the organization communicate or makes correspondence only through post, as their units are located in remote areas. This method of communication is very slow in nature and it is not reliable. Therefore the solution for this problem is to develop communication channel that meets the need of the organization. Basically, the computerized solution is for improving the services as well as self-efficiency of the computer. The objective of the system is for meeting the needs of the employees in the organization for communicating with each other within their units. This application provides basic requirements such as Mail management, File transfer and instant messaging. It also has enhanced features like web browsing and utilities. The Intra-mailing System is very user-friendly application. Only certain applications like system monitoring instant messaging, chatting between two users needs a little training. 1
3 1. Introduction The aim of the project was to develop an Intranet Web Based Mailing System connecting to a Linux Server running a Mail Server, Database Server and with Apache as The Web Server. The aim was to implement the necessary functionalities to the users such as receiving and organizing mails through SMTP and PHP MAIL FUNCTION and Sending mails using MERCURY MAIL. All these are provided with the graphical interface so that the users can do their desired work smoothly. Apart from that, the administrator can create and delete user accounts through the server. The system starts with the welcome page prompting the user to establish his authentication. He is allowed to see his mail boxes, read mails and send mails to the other users only after his/her account is verified. 2. Functional Requirements 2.1.Login Page: There should be a login page for the existing user where the username and password are verified and then if he is a valid user, he is allowed for further advancements. 2.2.Inbox: The logged in users should be able to see the lists of new mails as well as the existing ones. 2.3.Compose Mail: User should be able to compose mails and send them to the other users. 2.4.Reply/Forward/Delete: The user should be able to reply to mails, forward mails and also delete mails from his mailboxes. The deleted mails should be moved to the Thrash mailbox. 2.5.Attach Files: The user should be able to attach files to the mails and send them to the desired users. 2.6.Save As Draft: The user should be able to save the incomplete mails in the Draft mailbox and these can be completed later and can be sent to others. 2.7.Record Sent Mails: There should be a provision for keeping a record of the mails that have been sent by the user in a separate mailbox called Sent mailbox. International Journal of Innovative Research and Studies Page 2
4 2.8.Trash mailbox: This mailbox keeps a record of the deleted mails from the other mailboxes such as Inbox, Sent, and Draft. If further mails are deleted from this, the mails should be permanently deleted from the users accounts. 2.9.Chat: An embedded Chatting System will help the user to chat with the online members of Intranet Mail System using Public or Private Chat room Download Mails: Users are allowed to download the mails (in TEXT/CSV/XML formats) for further reference. 3. Simple Mail Transport Protocol (SMTP): RFC Description: Simple Mail Transfer Protocol (SMTP) is the basis of Internet . Its objective is to transfer mail reliably and efficiently. SMTP is the IETF's Standard Number 10, or STD0010. Standard formats are also closely related to the SMTP standard. was the first "killer app" on the ARPANET, and SMTP was the scalable, standardized way to transport that . Its popularity helped drive adoption of TCP/IP and the Internet. SMTP has scaled very well indeed: the basic protocol is still in use 22 years after its standardization and is used by more than 500 million people around the world! 3.2.Location in the Protocol Stack: Rides on top of TCP, although it will run over others, such as X Port Numbers: 25 SMTP 587 Submission ( submission via SMTP on port 587) 3.4.IPv6 client/server availability: Both available. 3.5.Early History: Work on network mail began in 1971 over NCP on ARPANET (pre-ip). RFCs 196, 221, 224, and 278 (all in 1971) dealt with the Mail Box Protocol, a system running over NCP/DTP or NCP/FTP and allowing an ASCII text document to be printed or stored as a file on a remote host. MBP was a subset of FTP saw a flurry of RFC activity to refine electronic mail over the ARPANET. Electronic mail was widely used on the ARPANET by this time. Mail was handled through FTP International Journal of Innovative Research and Studies Page 3
5 commands MAIL and MLFL. RFCs 453, 456, 458, 469, 475, 498, and 510 refined mail protocols and operations. RFC 469 standardized the addressing method. RFC 524 (Mail Protocol, or MP) was an attempt to further define and standardize electronic mail, still making the protocol a part of FTP. It addressed forwarding mail, replying to mail, mail acknowledgement, and author verification. RFC 539 was Dr. Jonathan Postel's first forray into electronic mail. It was a response to RFC 524. RFC 555 was a response to Postel's response. From 1974 to 1980, these RFCs about mail protocols were issued: RFC 630, 644, 720, 751, 754, 763, and 771. Notable among these were: RFC addressing how to authenticate signatures RFC How to transition existing protocols and systems from ARPANET/NCP to Internet/TCP. Modern SMTP protocol begins in 1980 in an RFC by Dr. Jon Postel. RFC 772, Mail Transfer Protocol was an attempt at making a mail protocol that was independent of FTP. It is this RFC that will evolve into the first killer app, SMTP . MTP used port/socket 57, and had 3-digit response codes. It was designed to be independent of the network and transport layers, and work between different operating systems. RFC Comments on the mail transition strategy outlined in RFC 771. RFC 780 (1981) MTP refined (Postel) RFC 784, 785, and 786 (1981) dealt with implementing MTP on a DEC TOPS-20 operating system. RFC 788 (1981) - Postel introduces SMTP, the Simple Mail Transfer Protocol. It will run on port/socket 25 and contains all the basic commands that are used today. RFC 799 (1981) is also very important in its relationship to mail, since it discusses moving to a hierarchical name space (Internet Name Domains) and the implications for and e- mail addressing. RFC 805 (1982) was noted from a big meeting on computer mail. The most important outcome of this meeting was a consensus on using the [email protected] addressing scheme. RFC Multimedia mail meeting notes RFC Summary of a computer mail services meeting in Then came the modern era of SMTP , with the standardization of RFC 821 (SMTP) and RFC 822 (Internet mail format). International Journal of Innovative Research and Studies Page 4
6 4. The SMTP Standard Here were the original commands for the SMTP protocol: Command set from RFC 821: HELO domain MAIL FROM: reverse-path RCPT TO: forword-path DATA RSET SEND FROM: reverse-path SOML FROM: reverse-path SAML FROM: reverse-path VRFY string EXPN string HELP [string] NOOP QUIT TURN A minimum implementation must contain these SMTP "verbs": HELO MAIL RCPT DATA RSET NOOP QUIT After RFC 821 and RFC 822, more than 60 RFCs have been published concerning SMTP, e- mail formats, security, and other core concerns. This does not include POP, IMAP, or PCMAIL! This continuing development has improved the reliability, functionality, performance, and security of . Here is a list of the basic categories of post-rfc 821 e- mail RFCs: Enhancing SMTP (How to add capabilities while maintaining backward compatibility) International Journal of Innovative Research and Studies Page 5
7 Security & Encryption Handling attachments (8-bit, binary, large, multiple types) Format/Headers Internationalization and Encoding FAX/Multimedia DSNs (Delivery Status Notifications) Perhaps the most important changes to Internet were the standardization of MIME, which allowed multiple attached files of different kinds to be sent via SMTP, and SMTP Service Extensions (ESMTP). 5. Internet Mail System Overview: Internet systems can be described in generic terms, which is helpful in understanding basic concepts. The X.400 MHS terminology is frequently used. X.400 was an OSI architecture for electronic messaging. It never caught on the way SMTP did, but the terminology is still useful: Terms defined in the OSI X.400 Message Handling System Model An originator prepares messages with the assistance of his or her User Agent (UA). A UA is an application process that interacts with the Message Transfer System (MTS) to submit messages. The MTS delivers to one or more recipient UAs the messages submitted to it. 14 The MTS is composed of a number of Message Transfer Agents (MTAs). Operating together, the MTAs relay messages and deliver them to the intended recipient UAs, which then make the messages available to the intended recipients. The collection of UAs and MTAs is called the Message Handling System (MHS). The MHS and all of its users are collectively referred to as the Message Handling Environment. 6. Other Common Terms The terms below are more commonly used today when discussing protocols, applications, and models: 6.1.Message User Agent (MUA) A process which acts (usually on behalf of a user) to compose and submit new messages, and process delivered messages. In the split- MUA model, POP or IMAP is used to access delivered messages. International Journal of Innovative Research and Studies Page 6
8 6.2.Message Transfer Agent (MTA) A process which conforms to [SMTP-MTA], which acts as an SMTP server to accept messages from an MSA or another MTA, and either delivers them or acts as an SMTP client to relay them to another MTA. 6.3.Message Submission Agent (MSA) A process which conforms to this specification, which acts as a submission server to accept messages from MUAs, and either delivers them or acts as an SMTP client to relay them to an MTA. 6.4.Mail Delivery Agent (MDA) The MDA is responsible for the actual delivery of messages into a user's mail box. While this may seem like a frivolous task, the important aspect of this component is that the delivery process is separate from the very complex MTA. The main concept that the MDA defines is the structure of the mail store. Modern MDAs usually include the ability to filter mail and in some cases to reformat its contents. 6.5.Mail Access Agent (MAA) The MAA is a new component added to the process about 15 years ago. MAA s are to a certain extent an extension of the MDA. MAA s provide remote access to a user's mail. MAA s speak one or more of a variety of Mail Access Protocols. The two most common Protocols today are POP3 and IMAP4. These protocols have evolved significantly over time. The key functions of an MAA are to authenticate a user and deliver , but some MAA's provide a much more sophisticated set of features for accessing one's MTAs and SMTP MTAs speak SMTP or ESMTP. They are essentially mail routers. An Internet MTA is to mail what a router is to IP datagrams. There are only a handful of ISP-scale MTAs, Sendmail, Postfix, and Qmail being the most common at the moment. MTAs can store mail in queue until the destination is available, and then send it. Thus, they are sometimes called storeandforward relays. 6.7.SMTP and DNS Internet SMTP is highly dependent on DNS. From mail routing to spam-prevention, the DNS system is used extensively. MTAs should have valid DNS A, PTR, and MX records. The MX record is a special record which tells MTAs which SMTP server/mail host to connect to in order to deliver mail to domain X. Multiple MX records can be used for load balancing or redundancy. The lowest number is given the highest priority; SMTP MTAs will International Journal of Innovative Research and Studies Page 7
9 attempt to deliver there first. Below, you can see an example of mail routing from to Detailed explanation follows the picture: Figure 1 User "frito" has drafted an to his friend, [email protected]. He wrote the using Evolution, a popular open source graphical client, or MUA. He had to manually configure the address for his ISP's outgoing SMTP mail relay. He must use this relay; the ISP will not allow outbound SMTP traffic to other mail relays. Once the arrives at his ISP's mail relay, mail.drag.net, it is put in a queue for delivery. This particular MTA is Sendmail, the Internet's old workhorse. In order to forward the mail to the proper destination, the MTA must perform a DNS lookup for free.org's MX records. It receives the following info: ;; ANSWER SECTION: free.org IN MX 10 pluto.free.org. free.org IN MX 20 relay.reliable.com. Mail.drag.net first tries to establish an SMTP connection to the lowest-numbered Mail exchanger, pluto.free.org. However, there is a temporary network outage and it is unable to connect. Next, it will try to connect to the "secondary" Mail exchanger, relay.reliable.com. Relay.reliable.com has been configured to act as a backup store-and-forward mail relay for the free.org domain. Mail.drag.net is able to successfully connect to relay.reliable.com, and sends the message via the SMTP protocol. Relay.reliable.com is running Qmail. Now, on relay.reliable.com, DNS is consulted. Qmail removes itself from the list and tries to deliver to the remaining Mail exchanger, pluto.free.org. It continues trying until the network outage is repaired, then connects via SMTP and delivers the message to pluto. International Journal of Innovative Research and Studies Page 8
10 Once pluto (which is running Postfix) has the message, it will store the mail in user kitt's mailbox file. Kitt will fire up his MUA (Eudora on Mac OS 9), and connect to pluto's MAA, which is a Qpopper POP3 server. The message will be retrieved and then deleted. The mail went through 3 different MTAs in its journey to the recipient. Each one will be listed in the 's header. Note that the clients were running on different Operating Systems, the MTAs were different UNIX/Linux platforms, and the MTAs were all different. It still worked, because it was designed to be platform independent, vendor independent, and non-commercial. 7. Major MTA (SMTP Server) Implementations for Unix/Linux: Sendmail Postfix Exim Qmail Communigate Pro Sendmail and Postfix are the most common MTAs included with modern GNU/Linux distributions, although Debian comes with Exim. 7.1.Security and Authentication: In recent years, most MUAs (mail clients) have the capability to send authenticated and encrypted . This is done via the STARTTLS mechanism on port 25 or 587. Once a TLSsession is started, a username and password can be sent to the server. If the credentials check out O.K., the mail will be accepted for delivery. The number one reason for using SMTP AUTH is to allow remote/mobile/home users to send/transmit/upload from the Internet without requiring that the MTA be an open relay for spammers. STARTTLS is used to encrypt the username and password, so that it cannot be sniffed. Although some people point to TLS as providing encryption of content as well, this is not a good assumption to make. The unencrypted may be forwarded through several other hosts and networks over which you have no control. If you require end-to-end encryption, you should use S/MIME or OpenPGP/GnuPG. Configuring the right TLS/SSL type, ports, and auth types can be a painful chore. Fortunately, many clients can automatically test "what the server supports" to make configuration a little bit easier. At the time of this writing, MUAs such as Mozilla Mail, Evolution, Balsa, Opera M2, Outlook Express, Netscape Mail, KMail, and Sylpheed all supported sending SMTP mail with TLS/SSL and authenticating with username and International Journal of Innovative Research and Studies Page 9
11 password. Many SASL options are available for authentication, but PLAIN and LOGIN are the most common type to use with TLS/SSL. If you are NOT using TLS/SSL, CRAM-MD5 and DIGEST-MD5 will protect your password from packet sniffers. 7.2.Firewall Considerations: SMTP works well through firewalls and NAT/PAT devices such as cheap SOHO router and security devices. Traffic is initiated by SMTP clients to SMTP servers, from random nonprivileged ports to well-known TCP ports. You will probably only need to worry about TCP port 25, although you may have to deal with TCP ports 587 and 465. TCP 587 is the mail submission port, which can be handy for bypassing ISP blocking of port 25 traffic, and 465 is the deprecated SMTPS (SMTP over SSL/TLS) port. Fortunately, most mail client and mail server vendors support the standard STARTTLS method on port 25, and 465 is not required. One item to note is that some firewalls and packet filters actually look at and interfere with SMTP traffic. For example, Cisco's PIX firewall by default only allows RFC-821 minimal commands. Even some Linksys SOHO firewalls will block ESMTP commands like EHLO. If you need/want to use standard ESMTP commands like STARTTLS, 8BITMIME, BINARYMIME, or AUTH, then you will need to configure your firewall to not interfere with SMTP traffic, or select a different type of firewall device that will support ESMTP. 7.3.Client Implementations: All SMTP MTAs can act as clients and servers. Virtually every graphical MUA uses SMTP to transmit/send to an ISP's mail relay/smtp server/mta or an organization's MTA. The user typically has to manually input the mail server name or IP address in account preferences or settings. In many cases, the mail can be submitted to port 25 or 587 (submission), with or without encryption via STARTTLS. The MUA usually retrieves mail via IMAP or POP3. 8. Overview Of The System Here the browser clients have the INTRANET MAIL account. The authentication of the user is verified by PASSWORD AUTHENTICATION SYSTEM which is invoked by INTRA MAIL. PASSWORD AUTHENTICATION sends the required Query to MYSQL DB. MYSQL DB sends back the requested Query results. Then PASSWORD AUTHENTICATION authenticates the user and sends the result back to INTRA MAIL. INTRA MAIL on receiving data initiates the System and brings the TRUE USER to Inbox page. System sends mail to the other user implementing SMTP. All Messages and User details are stored in MYSQL DB. IF International Journal of Innovative Research and Studies Page 10
12 the INTRA MAIL is invoked to send mail outside the INTRANET i.e. to INTERNET (World Wide Web) it sends the mail to MERCURY MAIL SERVER. MERCURY MAIL SERVER authenticates the Standardization of mail and Sends it out to the INTERNET and Sends a confirmation message to INTRA MAIL that the MAIL is SEND to the respected user. User can send, save, download and delete mails. INTRA MAIL invokes the CHAT SYSTEM when its ask for. All the chat logs of respective user and according to Public and Private room are stored. INTRA MAIL access those chat logs according to the room and displays at respective CLIENT BROWSER. While Logout INTRA MAIL expires all the Cookies and Connection with the CLIENT BROWSER. 8.1.PHP MAIL: It is one of the most popular PHP based implementation of SMTP (Simple Mail Transfer Protocol). 8.2.MERCURY MAIL: MERCURY MAIL Server provides access to personal mail through the SMTP protocol. It uses a pseudo database format. This provides only users who are totally separate from the local UNIX account database. The mailbox database is stored in parts of the file system that are private to the Mercury Mail. International Journal of Innovative Research and Studies Page 11
13 References: 1. For RFC2821: 2. For PHP: 3. About SMTP: 4. PHP tutorial: http// 5. WIKIPEDIA, WKIBOOKS, WIKISCHOLARS, WKIMEDIA 6. GOOGLE BOOKS 7. PHP THE COMPLETE REFERNCE book. 8. PHP & MYSQL THE COMPLETE REFERENCE book. 9. HTML BLACK BOOK 10. AJAX THE COMPLETE REFERENCE 11. JAVASCRIPT THE COMPLETE REFERENCE International Journal of Innovative Research and Studies Page 12
Linux Network Administration
 Linux Network Administration Sendmail Evolution of Email The birth of electronic mail (email) occurred in the early 1960s The mailbox was a file in a user's home directory that was readable only by that
Linux Network Administration Sendmail Evolution of Email The birth of electronic mail (email) occurred in the early 1960s The mailbox was a file in a user's home directory that was readable only by that
Networking Applications
 Networking Dr. Ayman A. Abdel-Hamid College of Computing and Information Technology Arab Academy for Science & Technology and Maritime Transport Electronic Mail 1 Outline Introduction SMTP MIME Mail Access
Networking Dr. Ayman A. Abdel-Hamid College of Computing and Information Technology Arab Academy for Science & Technology and Maritime Transport Electronic Mail 1 Outline Introduction SMTP MIME Mail Access
Emacs SMTP Library. An Emacs package for sending mail via SMTP. Simon Josefsson, Alex Schroeder
 Emacs SMTP Library An Emacs package for sending mail via SMTP Simon Josefsson, Alex Schroeder Copyright c 2003, 2004 Free Software Foundation, Inc. Permission is granted to copy, distribute and/or modify
Emacs SMTP Library An Emacs package for sending mail via SMTP Simon Josefsson, Alex Schroeder Copyright c 2003, 2004 Free Software Foundation, Inc. Permission is granted to copy, distribute and/or modify
2- Electronic Mail (SMTP), File Transfer (FTP), & Remote Logging (TELNET)
 2- Electronic Mail (SMTP), File Transfer (FTP), & Remote Logging (TELNET) There are three popular applications for exchanging information. Electronic mail exchanges information between people and file
2- Electronic Mail (SMTP), File Transfer (FTP), & Remote Logging (TELNET) There are three popular applications for exchanging information. Electronic mail exchanges information between people and file
2- Electronic Mail (SMTP), File Transfer (FTP), & Remote Logging (TELNET)
 2- Electronic Mail (SMTP), File Transfer (FTP), & Remote Logging (TELNET) There are three popular applications for exchanging information. Electronic mail exchanges information between people and file
2- Electronic Mail (SMTP), File Transfer (FTP), & Remote Logging (TELNET) There are three popular applications for exchanging information. Electronic mail exchanges information between people and file
Table of Contents. Electronic mail. History of email (2) History of email (1) Email history. Basic concepts. Aka e-mail (or email according to Knuth)
 Table of Contents Electronic mail Aka e-mail (or email according to Knuth) Karst Koymans / Jeroen van der Ham Informatics Institute University of Amsterdam Tuesday, September 25, 2011 Email history Basic
Table of Contents Electronic mail Aka e-mail (or email according to Knuth) Karst Koymans / Jeroen van der Ham Informatics Institute University of Amsterdam Tuesday, September 25, 2011 Email history Basic
The basic groups of components are described below. Fig X- 1 shows the relationship between components on a network.
 Elements of Email Email Components There are a number of software components used to produce, send and transfer email. These components can be broken down as clients or servers, although some components
Elements of Email Email Components There are a number of software components used to produce, send and transfer email. These components can be broken down as clients or servers, although some components
Mail agents. Introduction to Internet Mail. Message format (2) Authenticating senders
 Mail agents Introduction to Internet Mail Philip Hazel University of Cambridge MUA = Mail User Agent Interacts directly with the end user Pine, MH, Elm, mutt, mail, Eudora, Marcel, Mailstrom, Mulberry,
Mail agents Introduction to Internet Mail Philip Hazel University of Cambridge MUA = Mail User Agent Interacts directly with the end user Pine, MH, Elm, mutt, mail, Eudora, Marcel, Mailstrom, Mulberry,
CipherMail Gateway Quick Setup Guide
 CIPHERMAIL EMAIL ENCRYPTION CipherMail Gateway Quick Setup Guide October 10, 2015, Rev: 9537 Copyright 2015, ciphermail.com. CONTENTS CONTENTS Contents 1 Introduction 4 2 Typical setups 4 2.1 Direct delivery............................
CIPHERMAIL EMAIL ENCRYPTION CipherMail Gateway Quick Setup Guide October 10, 2015, Rev: 9537 Copyright 2015, ciphermail.com. CONTENTS CONTENTS Contents 1 Introduction 4 2 Typical setups 4 2.1 Direct delivery............................
Internet Technology 2/13/2013
 Internet Technology 03r. Application layer protocols: email Email: Paul Krzyzanowski Rutgers University Spring 2013 1 2 Simple Mail Transfer Protocol () Defined in RFC 2821 (April 2001) Original definition
Internet Technology 03r. Application layer protocols: email Email: Paul Krzyzanowski Rutgers University Spring 2013 1 2 Simple Mail Transfer Protocol () Defined in RFC 2821 (April 2001) Original definition
9236245 Issue 2EN. Nokia and Nokia Connecting People are registered trademarks of Nokia Corporation
 9236245 Issue 2EN Nokia and Nokia Connecting People are registered trademarks of Nokia Corporation Nokia 9300 Configuring connection settings Legal Notice Copyright Nokia 2005. All rights reserved. Reproduction,
9236245 Issue 2EN Nokia and Nokia Connecting People are registered trademarks of Nokia Corporation Nokia 9300 Configuring connection settings Legal Notice Copyright Nokia 2005. All rights reserved. Reproduction,
How To Write An Email On A Linux Computer (No Mail) (No Email) (For Ahem) (Or Ahem, For Ahem). (For An Email) Or Ahem.Org) (Ahem) Or An Email
 Electronic mail Aka email (Knuth) dr. C. P. J. Koymans Informatics Institute Universiteit van Amsterdam November 20, 2007 dr. C. P. J. Koymans (UvA) Electronic mail November 20, 2007 1 / 31 History of
Electronic mail Aka email (Knuth) dr. C. P. J. Koymans Informatics Institute Universiteit van Amsterdam November 20, 2007 dr. C. P. J. Koymans (UvA) Electronic mail November 20, 2007 1 / 31 History of
SMTP Servers. Determine if an email message should be sent to another machine and automatically send it to that machine using SMTP.
 SMTP Servers SMTP: Simple Mail Transfer Protocol (TCP Port 25) The Simple Mail Transfer Protocol (SMTP) is an Internet standard for transferring electronic mail between computers. UNIX systems implement
SMTP Servers SMTP: Simple Mail Transfer Protocol (TCP Port 25) The Simple Mail Transfer Protocol (SMTP) is an Internet standard for transferring electronic mail between computers. UNIX systems implement
CS43: Computer Networks Email. Kevin Webb Swarthmore College September 24, 2015
 CS43: Computer Networks Email Kevin Webb Swarthmore College September 24, 2015 Three major components: mail (MUA) mail transfer (MTA) simple mail transfer protocol: SMTP User Agent a.k.a. mail reader composing,
CS43: Computer Networks Email Kevin Webb Swarthmore College September 24, 2015 Three major components: mail (MUA) mail transfer (MTA) simple mail transfer protocol: SMTP User Agent a.k.a. mail reader composing,
Email. MIME is the protocol that was devised to allow non-ascii encoded content in an email and attached files to an email.
 Email Basics: Email protocols were developed even before there was an Internet, at a time when no one was anticipating widespread use of digital graphics or even rich text format (fonts, colors, etc.),
Email Basics: Email protocols were developed even before there was an Internet, at a time when no one was anticipating widespread use of digital graphics or even rich text format (fonts, colors, etc.),
CS 356 Lecture 27 Internet Security Protocols. Spring 2013
 CS 356 Lecture 27 Internet Security Protocols Spring 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists
CS 356 Lecture 27 Internet Security Protocols Spring 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists
QMAIL & SMTP: A Secure Application for an Unsecure Protocol. Orr Dunkelman. [email protected]. January 27, 2004 SMTP and QMAIL Slide 1
 QMAIL & SMTP: A Secure Application for an Unsecure Protocol Orr Dunkelman January 27, 2004 SMTP and QMAIL Slide 1 SMTP, MUA and MTA Speak English Whenever we deal with protocols we (=Internet geeks) like
QMAIL & SMTP: A Secure Application for an Unsecure Protocol Orr Dunkelman January 27, 2004 SMTP and QMAIL Slide 1 SMTP, MUA and MTA Speak English Whenever we deal with protocols we (=Internet geeks) like
My FreeScan Vulnerabilities Report
 Page 1 of 6 My FreeScan Vulnerabilities Report Print Help For 66.40.6.179 on Feb 07, 008 Thank you for trying FreeScan. Below you'll find the complete results of your scan, including whether or not the
Page 1 of 6 My FreeScan Vulnerabilities Report Print Help For 66.40.6.179 on Feb 07, 008 Thank you for trying FreeScan. Below you'll find the complete results of your scan, including whether or not the
Email Electronic Mail
 Email Electronic Mail Electronic mail paradigm Most heavily used application on any network Electronic version of paper-based office memo Quick, low-overhead written communication Dates back to time-sharing
Email Electronic Mail Electronic mail paradigm Most heavily used application on any network Electronic version of paper-based office memo Quick, low-overhead written communication Dates back to time-sharing
Protocolo FTP. FTP: Active Mode. FTP: Active Mode. FTP: Active Mode. FTP: the file transfer protocol. Separate control, data connections
 : the file transfer protocol Protocolo at host interface local file system file transfer remote file system utilizes two ports: - a 'data' port (usually port 20...) - a 'command' port (port 21) SISTEMAS
: the file transfer protocol Protocolo at host interface local file system file transfer remote file system utilizes two ports: - a 'data' port (usually port 20...) - a 'command' port (port 21) SISTEMAS
isecuremail User Guide for iphone
 isecuremail User Guide for iphone Page 1 CONTENTS Chapter 1: Welcome... 4 Chapter 2: Getting Started... 5 Compatability... 5 Preliminary Steps... 5 Setting up a POP3 / IMAP4/ Exchange Email Account...
isecuremail User Guide for iphone Page 1 CONTENTS Chapter 1: Welcome... 4 Chapter 2: Getting Started... 5 Compatability... 5 Preliminary Steps... 5 Setting up a POP3 / IMAP4/ Exchange Email Account...
Evolution of the WWW. Communication in the WWW. WWW, HTML, URL and HTTP. HTTP Abstract Message Format. The Client/Server model is used:
 Evolution of the WWW Communication in the WWW World Wide Web (WWW) Access to linked documents, which are distributed over several computers in the History of the WWW Origin 1989 in the nuclear research
Evolution of the WWW Communication in the WWW World Wide Web (WWW) Access to linked documents, which are distributed over several computers in the History of the WWW Origin 1989 in the nuclear research
Sonian Getting Started Guide October 2008
 Sonian Getting Started Guide October 2008 Sonian, Inc. For Authorized Use Only 1 Create your new archiving account 3 Configure your firewall for IMAP collections 4 (Skip this step if you will be using
Sonian Getting Started Guide October 2008 Sonian, Inc. For Authorized Use Only 1 Create your new archiving account 3 Configure your firewall for IMAP collections 4 (Skip this step if you will be using
Mail system components. Electronic Mail MRA MUA MSA MAA. David Byers
 Electronic Mail PRINCIPLES DNS ARCHITECTURES SPAM Mail system components () () David Byers MRA [email protected] IDA/ADIT/IISLAB Mail User Agent Reads and writes e-mail Writes e-mail to using (usually)
Electronic Mail PRINCIPLES DNS ARCHITECTURES SPAM Mail system components () () David Byers MRA [email protected] IDA/ADIT/IISLAB Mail User Agent Reads and writes e-mail Writes e-mail to using (usually)
Fundamentals of the Internet 2009/10. 1. Explain meaning the following networking terminologies:
 Fundamentals of Internet Tutorial Questions (2009) 1. Explain meaning the following networking terminologies: Client/server networking, Coax, twisted pair, protocol, Bit, Byte, Kbps, KBps, MB, KB, MBps,
Fundamentals of Internet Tutorial Questions (2009) 1. Explain meaning the following networking terminologies: Client/server networking, Coax, twisted pair, protocol, Bit, Byte, Kbps, KBps, MB, KB, MBps,
FTP and email. Computer Networks. FTP: the file transfer protocol
 Computer Networks and email Based on Computer Networking, 4 th Edition by Kurose and Ross : the file transfer protocol transfer file to/from remote host client/ model client: side that initiates transfer
Computer Networks and email Based on Computer Networking, 4 th Edition by Kurose and Ross : the file transfer protocol transfer file to/from remote host client/ model client: side that initiates transfer
Simple Mail Transfer Protocol
 Page 1 of 6 Home : Network Programming Simple Mail Transfer Protocol Contents What is SMTP? Basics of SMTP SMTP Commands Relaying of Messages Time Stamps and Return Path in Message Header Mail Exchangers
Page 1 of 6 Home : Network Programming Simple Mail Transfer Protocol Contents What is SMTP? Basics of SMTP SMTP Commands Relaying of Messages Time Stamps and Return Path in Message Header Mail Exchangers
Technical papers How email works
 Technical papers How email works This document has now been archived How email works Contents How email works What is email? What makes up an email? How does email work? The client The server How do email
Technical papers How email works This document has now been archived How email works Contents How email works What is email? What makes up an email? How does email work? The client The server How do email
BlackBerry Enterprise Service 10. Secure Work Space for ios and Android Version: 10.1.1. Security Note
 BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
Email, SNMP, Securing the Web: SSL
 Email, SNMP, Securing the Web: SSL 4 January 2015 Lecture 12 4 Jan 2015 SE 428: Advanced Computer Networks 1 Topics for Today Email (SMTP, POP) Network Management (SNMP) ASN.1 Secure Sockets Layer 4 Jan
Email, SNMP, Securing the Web: SSL 4 January 2015 Lecture 12 4 Jan 2015 SE 428: Advanced Computer Networks 1 Topics for Today Email (SMTP, POP) Network Management (SNMP) ASN.1 Secure Sockets Layer 4 Jan
Implementing MDaemon as an Email Security Gateway to Exchange Server
 Implementing MDaemon as an Email Security Gateway to Exchange Server Introduction MDaemon is widely deployed as a very effective antispam/antivirus gateway to Exchange. For optimum performance, we recommend
Implementing MDaemon as an Email Security Gateway to Exchange Server Introduction MDaemon is widely deployed as a very effective antispam/antivirus gateway to Exchange. For optimum performance, we recommend
Appendix. Web Command Error Codes. Web Command Error Codes
 Appendix Web Command s Error codes marked with * are received in responses from the FTP server, and then returned as the result of FTP command execution. -501 Incorrect parameter type -502 Error getting
Appendix Web Command s Error codes marked with * are received in responses from the FTP server, and then returned as the result of FTP command execution. -501 Incorrect parameter type -502 Error getting
Email. Daniel Zappala. CS 460 Computer Networking Brigham Young University
 Email Daniel Zappala CS 460 Computer Networking Brigham Young University How Email Works 3/25 Major Components user agents POP, IMAP, or HTTP to exchange mail mail transfer agents (MTAs) mailbox to hold
Email Daniel Zappala CS 460 Computer Networking Brigham Young University How Email Works 3/25 Major Components user agents POP, IMAP, or HTTP to exchange mail mail transfer agents (MTAs) mailbox to hold
2014-10-07. Email security
 Email security Simple Mail Transfer Protocol First defined in RFC821 (1982), later updated in RFC 2821 (2001) and most recently in RFC5321 (Oct 2008) Communication involves two hosts SMTP Client SMTP Server
Email security Simple Mail Transfer Protocol First defined in RFC821 (1982), later updated in RFC 2821 (2001) and most recently in RFC5321 (Oct 2008) Communication involves two hosts SMTP Client SMTP Server
Technical Note. ISP Protection against BlackListing. FORTIMAIL Deployment for Outbound Spam Filtering. Rev 2.2
 Technical Note ISP Protection against BlackListing FORTIMAIL Deployment for Outbound Spam Filtering Rev 2.2 April 14, 2009 Table of Contents 1 Objective IP address protection... 3 1.1 Context... 3 1.2
Technical Note ISP Protection against BlackListing FORTIMAIL Deployment for Outbound Spam Filtering Rev 2.2 April 14, 2009 Table of Contents 1 Objective IP address protection... 3 1.1 Context... 3 1.2
IBM i. Networking E-mail. Version 7.2
 IBM i Networking E-mail Version 7.2 IBM i Networking E-mail Version 7.2 Note Before using this information and the product it supports, read the information in Notices on page 53. This document may contain
IBM i Networking E-mail Version 7.2 IBM i Networking E-mail Version 7.2 Note Before using this information and the product it supports, read the information in Notices on page 53. This document may contain
Installation Guide For ChoiceMail Enterprise Edition
 Installation Guide For ChoiceMail Enterprise Edition How to Install ChoiceMail Enterprise On A Server In Front Of Your Company Mail Server August, 2004 Version 2.6x Copyright DigiPortal Software, 2002-2004
Installation Guide For ChoiceMail Enterprise Edition How to Install ChoiceMail Enterprise On A Server In Front Of Your Company Mail Server August, 2004 Version 2.6x Copyright DigiPortal Software, 2002-2004
Electronic mail security. MHS (Message Handling System)
 Electronic mail security Diana Berbecaru < diana.berbecaru @ polito.it> Politecnico di Torino Dip. Automatica e Informatica MHS (Message Handling System) MS MS MUA MUA (Message Transfer ) MS (Message Store)
Electronic mail security Diana Berbecaru < diana.berbecaru @ polito.it> Politecnico di Torino Dip. Automatica e Informatica MHS (Message Handling System) MS MS MUA MUA (Message Transfer ) MS (Message Store)
FTP: the file transfer protocol
 File Transfer: FTP FTP: the file transfer protocol at host FTP interface FTP client local file system file transfer FTP remote file system transfer file to/from remote host client/ model client: side that
File Transfer: FTP FTP: the file transfer protocol at host FTP interface FTP client local file system file transfer FTP remote file system transfer file to/from remote host client/ model client: side that
Network Services. Email SMTP, Internet Message Format. Johann Oberleitner SS 2006
 Network Services Email SMTP, Internet Message Format Johann Oberleitner SS 2006 Agenda Email SMTP Internet Message Format Email Protocols SMTP Send emails POP3/IMAPv4 Read Emails Administrate mailboxes
Network Services Email SMTP, Internet Message Format Johann Oberleitner SS 2006 Agenda Email SMTP Internet Message Format Email Protocols SMTP Send emails POP3/IMAPv4 Read Emails Administrate mailboxes
Computer Networks 1 (Mạng Máy Tính 1) Lectured by: Dr. Phạm Trần Vũ MEng. Nguyễn CaoĐạt
 Computer Networks 1 (Mạng Máy Tính 1) Lectured by: Dr. Phạm Trần Vũ MEng. Nguyễn CaoĐạt 1 Lecture 10: Application Layer 2 Application Layer Where our applications are running Using services provided by
Computer Networks 1 (Mạng Máy Tính 1) Lectured by: Dr. Phạm Trần Vũ MEng. Nguyễn CaoĐạt 1 Lecture 10: Application Layer 2 Application Layer Where our applications are running Using services provided by
9243060 Issue 1 EN. Nokia and Nokia Connecting People are registered trademarks of Nokia Corporation
 9243060 Issue 1 EN Nokia and Nokia Connecting People are registered trademarks of Nokia Corporation Nokia 9300i Configuring connection settings Nokia 9300i Configuring connection settings Legal Notice
9243060 Issue 1 EN Nokia and Nokia Connecting People are registered trademarks of Nokia Corporation Nokia 9300i Configuring connection settings Nokia 9300i Configuring connection settings Legal Notice
Virtual private network. Network security protocols VPN VPN. Instead of a dedicated data link Packets securely sent over a shared network Internet VPN
 Virtual private network Network security protocols COMP347 2006 Len Hamey Instead of a dedicated data link Packets securely sent over a shared network Internet VPN Public internet Security protocol encrypts
Virtual private network Network security protocols COMP347 2006 Len Hamey Instead of a dedicated data link Packets securely sent over a shared network Internet VPN Public internet Security protocol encrypts
Chapter 2 Application Layer. Lecture 5 FTP, Mail. Computer Networking: A Top Down Approach
 Chapter 2 Application Layer Lecture 5 FTP, Mail Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012 Application Layer 2-1 Chapter 2: outline 2.1 principles
Chapter 2 Application Layer Lecture 5 FTP, Mail Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012 Application Layer 2-1 Chapter 2: outline 2.1 principles
Gigabyte Content Management System Console User s Guide. Version: 0.1
 Gigabyte Content Management System Console User s Guide Version: 0.1 Table of Contents Using Your Gigabyte Content Management System Console... 2 Gigabyte Content Management System Key Features and Functions...
Gigabyte Content Management System Console User s Guide Version: 0.1 Table of Contents Using Your Gigabyte Content Management System Console... 2 Gigabyte Content Management System Key Features and Functions...
Domain Name System (DNS)
 Application Layer Domain Name System Domain Name System (DNS) Problem Want to go to www.google.com, but don t know the IP address Solution DNS queries Name Servers to get correct IP address Essentially
Application Layer Domain Name System Domain Name System (DNS) Problem Want to go to www.google.com, but don t know the IP address Solution DNS queries Name Servers to get correct IP address Essentially
The GlobalCerts TM SecureMail Gateway TM
 Glob@lCerts PRODUCT OVERVIEW: The GlobalCerts TM SecureMail Gateway TM Automatic encryption and decryption is unique to the SecureMail Gateway. The GlobalCerts SecureMail Gateway is based on a network
Glob@lCerts PRODUCT OVERVIEW: The GlobalCerts TM SecureMail Gateway TM Automatic encryption and decryption is unique to the SecureMail Gateway. The GlobalCerts SecureMail Gateway is based on a network
Internet Security [1] VU 184.216. Engin Kirda [email protected]
![Internet Security [1] VU 184.216. Engin Kirda engin@infosys.tuwien.ac.at Internet Security [1] VU 184.216. Engin Kirda engin@infosys.tuwien.ac.at](/thumbs/33/15826620.jpg) Internet Security [1] VU 184.216 Engin Kirda [email protected] Christopher Kruegel [email protected] Administration Challenge 2 deadline is tomorrow 177 correct solutions Challenge 4 will
Internet Security [1] VU 184.216 Engin Kirda [email protected] Christopher Kruegel [email protected] Administration Challenge 2 deadline is tomorrow 177 correct solutions Challenge 4 will
MAPI Connector Overview
 The CommuniGate Pro Server can be used as a "service provider" for Microsoft Windows applications supporting the MAPI (Microsoft Messaging API). To use this service, a special Connector library (CommuniGate
The CommuniGate Pro Server can be used as a "service provider" for Microsoft Windows applications supporting the MAPI (Microsoft Messaging API). To use this service, a special Connector library (CommuniGate
Exchange (UCMAIL) Configuration Procedures
 Exchange (UCMAIL) Configuration Procedures Last Updated: 09/04/2008 by Jon Adams, UCit Email Services Table of Contents New Features for Exchange 2007... 2 Supported Mail Clients... 3 Unsupported or Incompatible
Exchange (UCMAIL) Configuration Procedures Last Updated: 09/04/2008 by Jon Adams, UCit Email Services Table of Contents New Features for Exchange 2007... 2 Supported Mail Clients... 3 Unsupported or Incompatible
Libra Esva. Whitepaper. Glossary. How Email Really Works. Email Security Virtual Appliance. May, 2010. It's So Simple...or Is It?
 Libra Esva Email Security Virtual Appliance Whitepaper May, 2010 How Email Really Works Glossary 1 2 SMTP is a protocol for sending email messages between servers. DNS (Domain Name System) is an internet
Libra Esva Email Security Virtual Appliance Whitepaper May, 2010 How Email Really Works Glossary 1 2 SMTP is a protocol for sending email messages between servers. DNS (Domain Name System) is an internet
List of Common TCP/IP port numbers
 List of Common TCP/IP port numbers For those of you who configure firewalls, routers, port forwarding, and applications connectivity, this regularly updated document lists all standard, common, well known,
List of Common TCP/IP port numbers For those of you who configure firewalls, routers, port forwarding, and applications connectivity, this regularly updated document lists all standard, common, well known,
1 Accessing E-mail accounts on the Axxess Mail Server
 1 Accessing E-mail accounts on the Axxess Mail Server The Axxess Mail Server provides users with access to their e-mail folders through POP3, and IMAP protocols, or OpenWebMail browser interface. The server
1 Accessing E-mail accounts on the Axxess Mail Server The Axxess Mail Server provides users with access to their e-mail folders through POP3, and IMAP protocols, or OpenWebMail browser interface. The server
HOW WILL I KNOW THAT I SHOULD USE THE IAS EMAIL CONTINUITY SERVICE? https://web.ias.edu/updateme/
 WHEN DO I NEED TO ACCESS THE IAS EMAIL CONTINUITY SERVICE? This service is provided to address the following actions during periods where the IAS email servers are offline: 1. If you need to check for
WHEN DO I NEED TO ACCESS THE IAS EMAIL CONTINUITY SERVICE? This service is provided to address the following actions during periods where the IAS email servers are offline: 1. If you need to check for
XGENPLUS SECURITY FEATURES...
 Security Features Table of Contents TABLE OF CONTENTS... 2 1. INTRODUCTION... 3 2. XGENPLUS SECURITY FEATURES... 3 3. SERVER LEVEL FEATURES... 5 4. DOMAIN LEVEL FEATURES... 8 5. USER LEVEL FEATURES...
Security Features Table of Contents TABLE OF CONTENTS... 2 1. INTRODUCTION... 3 2. XGENPLUS SECURITY FEATURES... 3 3. SERVER LEVEL FEATURES... 5 4. DOMAIN LEVEL FEATURES... 8 5. USER LEVEL FEATURES...
Introduction to Computer Networks
 Introduction to Computer Networks Chen Yu Indiana University Basic Building Blocks for Computer Networks Nodes PC, server, special-purpose hardware, sensors Switches Links: Twisted pair, coaxial cable,
Introduction to Computer Networks Chen Yu Indiana University Basic Building Blocks for Computer Networks Nodes PC, server, special-purpose hardware, sensors Switches Links: Twisted pair, coaxial cable,
Understanding SMTP authentication and securing your IBM Lotus Domino 8 server from spam
 Understanding SMTP authentication and securing your IBM Lotus Domino 8 server from spam Shrikant Jamkhandi IBM Software Group Senior Software Engineer Pune, India September 2009 Copyright International
Understanding SMTP authentication and securing your IBM Lotus Domino 8 server from spam Shrikant Jamkhandi IBM Software Group Senior Software Engineer Pune, India September 2009 Copyright International
AXIGEN Mail Server. Quick Installation and Configuration Guide. Product version: 6.1 Document version: 1.0
 AXIGEN Mail Server Quick Installation and Configuration Guide Product version: 6.1 Document version: 1.0 Last Updated on: May 28, 2008 Chapter 1: Introduction... 3 Welcome... 3 Purpose of this document...
AXIGEN Mail Server Quick Installation and Configuration Guide Product version: 6.1 Document version: 1.0 Last Updated on: May 28, 2008 Chapter 1: Introduction... 3 Welcome... 3 Purpose of this document...
20.12. smtplib SMTP protocol client
 20.12. smtplib SMTP protocol client The smtplib module defines an SMTP client session object that can be used to send mail to any Internet machine with an SMTP or ESMTP listener daemon. For details of
20.12. smtplib SMTP protocol client The smtplib module defines an SMTP client session object that can be used to send mail to any Internet machine with an SMTP or ESMTP listener daemon. For details of
Mail Programs. Manual
 Manual April 2015, Copyright Webland AG 2015 Table of Contents Introduction Basics Server Information SSL POP3 IMAP Instructions Windows Outlook 2000 Outlook 2002/2003/XP Outlook 2007 Outlook 2010 Outlook
Manual April 2015, Copyright Webland AG 2015 Table of Contents Introduction Basics Server Information SSL POP3 IMAP Instructions Windows Outlook 2000 Outlook 2002/2003/XP Outlook 2007 Outlook 2010 Outlook
A D M I N I S T R A T O R V 1. 0
 A D M I N I S T R A T O R F A Q V 1. 0 2011 Fastnet SA, St-Sulpice, Switzerland. All rights reserved. Reproduction in whole or in part in any form of this manual without written permission of Fastnet SA
A D M I N I S T R A T O R F A Q V 1. 0 2011 Fastnet SA, St-Sulpice, Switzerland. All rights reserved. Reproduction in whole or in part in any form of this manual without written permission of Fastnet SA
Articles Fighting SPAM in Lotus Domino
 Page 1 of 5 Articles Fighting SPAM in Lotus Domino For many e-mail administrators these days, the number one complaint from the users and managers is unsolicited emails flooding the system, commonly called
Page 1 of 5 Articles Fighting SPAM in Lotus Domino For many e-mail administrators these days, the number one complaint from the users and managers is unsolicited emails flooding the system, commonly called
1 Introduction: Network Applications
 1 Introduction: Network Applications Some Network Apps E-mail Web Instant messaging Remote login P2P file sharing Multi-user network games Streaming stored video clips Internet telephone Real-time video
1 Introduction: Network Applications Some Network Apps E-mail Web Instant messaging Remote login P2P file sharing Multi-user network games Streaming stored video clips Internet telephone Real-time video
Internet Technologies Internet Protocols and Services
 QAFQAZ UNIVERSITY Computer Engineering Department Internet Technologies Internet Protocols and Services Dr. Abzetdin ADAMOV Chair of Computer Engineering Department [email protected] http://ce.qu.edu.az/~aadamov
QAFQAZ UNIVERSITY Computer Engineering Department Internet Technologies Internet Protocols and Services Dr. Abzetdin ADAMOV Chair of Computer Engineering Department [email protected] http://ce.qu.edu.az/~aadamov
Remote login (Telnet):
 SFWR 4C03: Computer Networks and Computer Security Feb 23-26 2004 Lecturer: Kartik Krishnan Lectures 19-21 Remote login (Telnet): Telnet permits a user to connect to an account on a remote machine. A client
SFWR 4C03: Computer Networks and Computer Security Feb 23-26 2004 Lecturer: Kartik Krishnan Lectures 19-21 Remote login (Telnet): Telnet permits a user to connect to an account on a remote machine. A client
Initial Setup of Mozilla Thunderbird with IMAP for OS X Lion
 Initial Setup of Mozilla Thunderbird Concept This document describes the procedures for setting up the Mozilla Thunderbird email client to download messages from Google Mail using Internet Message Access
Initial Setup of Mozilla Thunderbird Concept This document describes the procedures for setting up the Mozilla Thunderbird email client to download messages from Google Mail using Internet Message Access
Webmail Using the Hush Encryption Engine
 Webmail Using the Hush Encryption Engine Introduction...2 Terms in this Document...2 Requirements...3 Architecture...3 Authentication...4 The Role of the Session...4 Steps...5 Private Key Retrieval...5
Webmail Using the Hush Encryption Engine Introduction...2 Terms in this Document...2 Requirements...3 Architecture...3 Authentication...4 The Role of the Session...4 Steps...5 Private Key Retrieval...5
Standard Guide. Standard Guide. Standard Guide
 Table of Contents 1. Introduction 1 1.1. Introduction 1 1.2. Prerequisites 1.3. How Internet Email Works 2. 3. 2 Overview 3 2.1. Overview 3 2.2. Structure of MailEnable 3-4 2.3. Administration 4-5 2.4.
Table of Contents 1. Introduction 1 1.1. Introduction 1 1.2. Prerequisites 1.3. How Internet Email Works 2. 3. 2 Overview 3 2.1. Overview 3 2.2. Structure of MailEnable 3-4 2.3. Administration 4-5 2.4.
Lecture (02) Networking Model (TCP/IP) Networking Standard (OSI) (I)
 Lecture (02) Networking Model (TCP/IP) Networking Standard (OSI) (I) By: Dr. Ahmed ElShafee ١ Dr. Ahmed ElShafee, ACU : Fall 2015, Networks II Agenda Introduction to networking architecture Historical
Lecture (02) Networking Model (TCP/IP) Networking Standard (OSI) (I) By: Dr. Ahmed ElShafee ١ Dr. Ahmed ElShafee, ACU : Fall 2015, Networks II Agenda Introduction to networking architecture Historical
Filtering Mail with Milter. David F. Skoll Roaring Penguin Software Inc.
 Filtering Mail with Milter David F. Skoll Roaring Penguin Software Inc. Why filter mail? Overview Different filtering approaches Delivery agent (e.g. Procmail) Central filtering (Milter) Milter Architecture
Filtering Mail with Milter David F. Skoll Roaring Penguin Software Inc. Why filter mail? Overview Different filtering approaches Delivery agent (e.g. Procmail) Central filtering (Milter) Milter Architecture
Evolution of the WWW. Communication in the WWW. WWW, HTML, URL and HTTP. HTTP - Message Format. The Client/Server model is used:
 Evolution of the WWW Communication in the WWW World Wide Web (WWW) Access to linked documents, which are distributed over several computers in the History of the WWW Origin 1989 in the nuclear research
Evolution of the WWW Communication in the WWW World Wide Web (WWW) Access to linked documents, which are distributed over several computers in the History of the WWW Origin 1989 in the nuclear research
How to Setup your E-mail Account -Apple Mail for Mac OS X 1- Open Mail
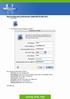 How to Setup your E-mail Account -Apple Mail for Mac OS X 1- Open Mail 2- The welcome screen will appear as follow: Fill in the above information as follow Full Name: type your display name E-Mail address:
How to Setup your E-mail Account -Apple Mail for Mac OS X 1- Open Mail 2- The welcome screen will appear as follow: Fill in the above information as follow Full Name: type your display name E-Mail address:
Peer-to-Peer Support for Distributed Mail Transfer Mechanism. Abstract
 Peer-to-Peer Support for Distributed Mail Transfer Mechanism Kai-Hsiang Yang, Jenq-Haur Wang, Chi-Chien Pan, and Tzao-Lin Lee Department of Computer Science and Information Engineering, National Taiwan
Peer-to-Peer Support for Distributed Mail Transfer Mechanism Kai-Hsiang Yang, Jenq-Haur Wang, Chi-Chien Pan, and Tzao-Lin Lee Department of Computer Science and Information Engineering, National Taiwan
DATA COMMUNICATOIN NETWORKING
 DATA COMMUNICATOIN NETWORKING Instructor: Ouldooz Baghban Karimi Course Book: Computer Networking, A Top-Down Approach By: Kurose, Ross Introduction Course Overview Basics of Computer Networks Internet
DATA COMMUNICATOIN NETWORKING Instructor: Ouldooz Baghban Karimi Course Book: Computer Networking, A Top-Down Approach By: Kurose, Ross Introduction Course Overview Basics of Computer Networks Internet
The following multiple-choice post-course assessment will evaluate your knowledge of the skills and concepts taught in Internet Business Associate.
 Course Assessment Answers-1 Course Assessment The following multiple-choice post-course assessment will evaluate your knowledge of the skills and concepts taught in Internet Business Associate. 1. A person
Course Assessment Answers-1 Course Assessment The following multiple-choice post-course assessment will evaluate your knowledge of the skills and concepts taught in Internet Business Associate. 1. A person
SECURE FTP CONFIGURATION SETUP GUIDE
 SECURE FTP CONFIGURATION SETUP GUIDE CONTENTS Overview... 3 Secure FTP (FTP over SSL/TLS)... 3 Connectivity... 3 Settings... 4 FTP file cleanup information... 5 Troubleshooting... 5 Tested FTP clients
SECURE FTP CONFIGURATION SETUP GUIDE CONTENTS Overview... 3 Secure FTP (FTP over SSL/TLS)... 3 Connectivity... 3 Settings... 4 FTP file cleanup information... 5 Troubleshooting... 5 Tested FTP clients
Defining your local domains
 To fully configure the Virtual SMTP server you must first define your local domains and specify the IP address where messages will be delivered. Then you need to test for successful mail deliverability
To fully configure the Virtual SMTP server you must first define your local domains and specify the IP address where messages will be delivered. Then you need to test for successful mail deliverability
Exim4U. Email Server Solution For Unix And Linux Systems
 Email Server Solution For Unix And Linux Systems General Overview, Feature Comparison and Screen Shots Exim4U Email Server Solution For Unix And Linux Systems Version 2.x.x October 12, 2012 Copyright 2009
Email Server Solution For Unix And Linux Systems General Overview, Feature Comparison and Screen Shots Exim4U Email Server Solution For Unix And Linux Systems Version 2.x.x October 12, 2012 Copyright 2009
Lecture 23: Firewalls
 Lecture 23: Firewalls Introduce several types of firewalls Discuss their advantages and disadvantages Compare their performances Demonstrate their applications C. Ding -- COMP581 -- L23 What is a Digital
Lecture 23: Firewalls Introduce several types of firewalls Discuss their advantages and disadvantages Compare their performances Demonstrate their applications C. Ding -- COMP581 -- L23 What is a Digital
Unifying Information Security. Implementing TLS on the CLEARSWIFT SECURE Email Gateway
 Unifying Information Security Implementing TLS on the CLEARSWIFT SECURE Email Gateway Contents 1 Introduction... 3 2 Understanding TLS... 4 3 Clearswift s Application of TLS... 5 3.1 Opportunistic TLS...
Unifying Information Security Implementing TLS on the CLEARSWIFT SECURE Email Gateway Contents 1 Introduction... 3 2 Understanding TLS... 4 3 Clearswift s Application of TLS... 5 3.1 Opportunistic TLS...
Linux MDS Firewall Supplement
 Linux MDS Firewall Supplement Table of Contents Introduction... 1 Two Options for Building a Firewall... 2 Overview of the iptables Command-Line Utility... 2 Overview of the set_fwlevel Command... 2 File
Linux MDS Firewall Supplement Table of Contents Introduction... 1 Two Options for Building a Firewall... 2 Overview of the iptables Command-Line Utility... 2 Overview of the set_fwlevel Command... 2 File
SPAMfighter SMTP Anti Spam Server
 SPAMfighter SMTP Anti Spam Server Users Manual Copyright SPAMfighter ApS 2005 Revised 4/27/2006 1 Table of Contents 2 Terminology...3 3 Technology...4 3.1 Tunneling and Interception...4 3.2 Content Classification...5
SPAMfighter SMTP Anti Spam Server Users Manual Copyright SPAMfighter ApS 2005 Revised 4/27/2006 1 Table of Contents 2 Terminology...3 3 Technology...4 3.1 Tunneling and Interception...4 3.2 Content Classification...5
Using email over FleetBroadband
 Using email over FleetBroadband Version 01 20 October 2007 inmarsat.com/fleetbroadband Whilst the information has been prepared by Inmarsat in good faith, and all reasonable efforts have been made to ensure
Using email over FleetBroadband Version 01 20 October 2007 inmarsat.com/fleetbroadband Whilst the information has been prepared by Inmarsat in good faith, and all reasonable efforts have been made to ensure
WEBROOT EMAIL ARCHIVING SERVICE. Getting Started Guide North America. The best security in an unsecured world. TM
 WEBROOT EMAIL ARCHIVING SERVICE Getting Started Guide North America Webroot Software, Inc. World Headquarters 2560 55th Street Boulder CO 80301 USA www.webroot.com 800.870.8102 Table of Contents Create
WEBROOT EMAIL ARCHIVING SERVICE Getting Started Guide North America Webroot Software, Inc. World Headquarters 2560 55th Street Boulder CO 80301 USA www.webroot.com 800.870.8102 Table of Contents Create
Glossary of Technical Terms Related to IPv6
 AAAA Record An AAAA record stores a 128-bit Internet Protocol version 6 (IPv6) address, which does not fit the standard A record format. For example, 2007:0db6:85a3:0000:0000:6a2e:0371:7234 is a valid
AAAA Record An AAAA record stores a 128-bit Internet Protocol version 6 (IPv6) address, which does not fit the standard A record format. For example, 2007:0db6:85a3:0000:0000:6a2e:0371:7234 is a valid
SMTP Best Practices, Configurations and Troubleshooting on Lotus Domino.
 SMTP Best Practices, Configurations and Troubleshooting on Lotus Domino. 9 th th June 2011 Chandra Shekhar Anumandla - Lotus Technical Support Engineer Presenter Seema Janjirkar Lotus Technical Advisor
SMTP Best Practices, Configurations and Troubleshooting on Lotus Domino. 9 th th June 2011 Chandra Shekhar Anumandla - Lotus Technical Support Engineer Presenter Seema Janjirkar Lotus Technical Advisor
MailEnable Scalability White Paper Version 1.2
 MailEnable Scalability White Paper Version 1.2 Table of Contents 1 Overview...2 2 Core architecture...3 2.1 Configuration repository...3 2.2 Storage repository...3 2.3 Connectors...3 2.3.1 SMTP Connector...3
MailEnable Scalability White Paper Version 1.2 Table of Contents 1 Overview...2 2 Core architecture...3 2.1 Configuration repository...3 2.2 Storage repository...3 2.3 Connectors...3 2.3.1 SMTP Connector...3
CSE/ISE 311: Systems Administra5on Email Administra5on
 Email Administra5on Don Porter Theme Email systems started with a pre5y simple design Everyone trusted each other, it was nice Then spam came along Lots of complexity and distrust to try to reduce spam
Email Administra5on Don Porter Theme Email systems started with a pre5y simple design Everyone trusted each other, it was nice Then spam came along Lots of complexity and distrust to try to reduce spam
Sending an Encrypted/Unencrypted Message. Let's Begin: Log In and Set Up Security Questions. Create Additional ProMailSource Accounts:
 Let's Begin: Log In and Set Up Security Questions To start, you can log in from the ProMailSource home page. Sending an Encrypted/Unencrypted Message Every message you send through ProMailSource is automatically
Let's Begin: Log In and Set Up Security Questions To start, you can log in from the ProMailSource home page. Sending an Encrypted/Unencrypted Message Every message you send through ProMailSource is automatically
Domains Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc.
 Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc. Domains All Domains System administrators can use this section
Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc. Domains All Domains System administrators can use this section
Mail Server Administration
 Clemson University CPSC 424: Systems Administration and Security Section 001 Mail Server Administration Authors: Joshua Groppe William Collins Instructor: James M.Martin, Ph.D April 25, 2014 1 Introduction
Clemson University CPSC 424: Systems Administration and Security Section 001 Mail Server Administration Authors: Joshua Groppe William Collins Instructor: James M.Martin, Ph.D April 25, 2014 1 Introduction
Email: [email protected] Toll Free: 1-866-716-2040 International: 1-646-506-9354
 1. Check your Welcome e-mail for login credentials for the control panel. 2. Using the login details in the welcome e-mail; login at https://cp.hostallapps.com Adding Domain: 1. On the Home Page of the
1. Check your Welcome e-mail for login credentials for the control panel. 2. Using the login details in the welcome e-mail; login at https://cp.hostallapps.com Adding Domain: 1. On the Home Page of the
Ciphermail for BlackBerry Quick Start Guide
 CIPHERMAIL EMAIL ENCRYPTION Ciphermail for BlackBerry Quick Start Guide June 19, 2014, Rev: 8975 Copyright 2010-2014, ciphermail.com. Introduction This guide will explain how to setup and configure a Ciphermail
CIPHERMAIL EMAIL ENCRYPTION Ciphermail for BlackBerry Quick Start Guide June 19, 2014, Rev: 8975 Copyright 2010-2014, ciphermail.com. Introduction This guide will explain how to setup and configure a Ciphermail
