Writing for Developers: The New Customers. Amruta Ranade
|
|
|
- Adrian Morgan
- 8 years ago
- Views:
Transcription
1 Writing for Developers: The New Customers Amruta Ranade 1
2 First, let s discuss the difference between User Docs and Developer Docs 2
3 Let s consider an example. Suppose we are writing the user docs for sending an using Gmail: 3
4 User documentation This is what the user documentation would look like: All we have to answer in the user documentation is how the user can send the , and we are done. 4
5 Developer documentation And this is what the Dev docs would need to answer: What is the format of the ? How is the message encapsulated to form the message packet? Description of the headers and metadata How is the message packet converted into a bit stream? How does the Client notify the Server that it wants to send an How does the Client connect to the Server? Which protocol is used? How does the Server look up the recipient's address? How does the Server figure out the recipient s Server?. 5
6 User Docs Dev Docs What is the format of the ? How is the message encapsulated to form the message packet? Description of the headers and metadata One snippet of a User document corresponds to multiple Dev documents.. How is the message packet converted into a bit stream? How does the Client notify the Server that it wants to send an How does the Client connect to the Server? Which protocol is used? How does the Server look up the recipient's address? How does the Server figure out the recipient s Server? 6
7 Why do we need Dev Docs? 7
8 User Docs Dev Docs Resources: One resource to document a feature Resources: More than one resource depending on the technical depth of the feature When: After the feature is designed When: Before the feature is designed Written for: End-users Support Written for: Developers QA Tech Writing Support Sales and Marketing Project Management 8
9 Types of Dev Docs 9
10 API Docs 10
11 What is an API APIs "expose some of a program's internal functions to the outside world in a limited fashion. That makes it possible for applications to share data and take actions on one another's behalf without requiring developers to share all of their software's code. 11
12 Example of an API Doc 12
13 Components of an API Doc Overview: Explain what advantages developers have in using the platform, and in some cases, provide an architectural description of the platform. Getting started: Help the developer get started, in the form of step-bystep tutorials or simpler walkthroughs. Sample code: Provide well-commented code samples that developers can build on. Reference material: Provide detailed information about each class, member, function or XML element. 13
14 Resources Tom Johnson Sarah Maddox API Technical Writing i-technical-writing A Coder s Guide to Writing API Documentation 14
15 Software Architecture Docs 15
16 What is Software Architecture Software architecture is the software s fundamental organization, embodied in its components, their relationships to each other and to the environment, and the principles guiding its design and evolution. 16
17 How do you document a Software Architecture Software architecture is documented in terms of views. To understand views, consider an architect designing a building 17
18 18
19 Understanding Views Just as a building architect might create wiring diagrams, floor plans, and elevations to describe different facets of a building to its different stakeholders (electricians, owners, planning officials), so an IT architect might create physical and security views of an IT system for the stakeholders who have concerns related to these aspects. 19
20 Understanding Views Let s again discuss the example of sending an using Gmail and see the different views that we can use to document the system. 20
21 Context View Start from scratch and build the story of the evolution of the product to the Big Picture 21
22 Context View Basic components 22
23 Context View Building the Big Picture 23
24 Functional and Non-functional View What does the software do? 24
25 Functional View Non-functional View Key functions of the system: Activation Authentication Configuration Send and receive s Send attachments Send s to multiple users Chat Video Chat Group Chat Send on behalf of someone Signature Encryption Folder structure Examples: Performance ( latency and throughput) Scalability (data and traffic volumes) Availability (uptime, downtime, scheduled maintenance, 24x7) Security (authentication, authorisation, data confidentiality) Flexibility Monitoring and management Reliability Accessibility 25
26 Logical View Drill down to the components and connections 26
27 Components Message Composition Headers Metadata Client Component to format the message Component to submit message to server Component to encrypt the message Outgoing Mail Server SMTP Server Incoming Mail Server POP3 Server Protocol HTTP Storage Contact Database Ports 27
28 Process View Workflow for each task 28
29 Process View High-level workflow 29
30 Process View Detailed workflow High-level workflow 30
31 Design View Define the details of each component 31
32 Design View Client Message composition clients usually contain user interfaces to display and edit text. Some applications permit the use of a program-external editor. The clients will perform formatting according to RFC 5322 for headers and body, and MIME for non-textual content and attachments. Headers include the destination fields, To, Cc, and Bcc, and the originator fields From which is the message's author(s), Sender in case there are more authors, and Reply-To in case responses should be addressed to a different mailbox. To better assist the user with destination fields, many clients maintain one or more address books and/or are able to connect to an LDAP directory server. For originator fields, clients may support different identities. Client settings require the user's real name and address for each user's identity, and possibly a list of LDAP servers. 32
33 Interface View How do the components communicate 33
34 Interface View SMTP SMTP stands for Simple Mail Transfer Protocol. The SMTP server handles outgoing mail. The SMTP server listens on well-known port number 25, POP3 listens on port 110 and IMAP uses port 143 Whenever you send a piece of , your client interacts with the SMTP server to handle the sending. The SMTP server on your host may have conversations with other SMTP servers to deliver the . Commands: HELO - introduce yourself EHLO - introduce yourself and request extended mode MAIL FROM: - specify the sender RCPT TO: - specify the recipient DATA - specify the body of the message (To, From and Subject should be the first three lines.) RSET - reset 34
35 Interface View POP3 In the simplest implementations of POP3, the server really does maintain a collection of text files -- one for each account. When a message arrives, the POP3 server simply appends it to the bottom of the recipient's file. When you check your , your client connects to the POP3 server using port 110. The POP3 server requires an account name and a password. Once you've logged in, the POP3 server opens your text file and allows you to access it. Commands: PASS - enter your password QUIT - quit the POP3 server LIST - list the messages and their size RETR - retrieve a message, pass it a message number DELE - delete a message, pass it a message number TOP - show the top x lines of a message, pass it a message number and the number of lines 35
36 Technology Selection Why did you choose X? 36
37 POP3 IMAP Workflow: Connect to server Retrieve all mail Store locally as new mail Delete mail from server Disconnect Advantages: Mail stored locally, always accessible, even without internet connection Internet connection needed only for sending and receiving mail Saves server storage space Option to leave copy of mail on server Consolidate multiple accounts and servers into one inbox Choose POP if You want to access your mail from only one single device You need constant access to your , regardless of internet availability Your server storage space is limited Workflow: Connect to server Fetch user requested content and cache it locally, Process user edits Disconnect Advantages: Mail stored on remote server, i.e. accessible from multiple different locations Internet connection needed to access mail Faster overview as only headers are downloaded until content is explicitly requested Mail is automatically backed up if server is managed properly Saves local storage space Option to store mail locally Choose IMAP if You want to access your from multiple different devices You have a reliable and constant internet connection You want to receive a quick overview of new s or s on the server Your local storage space is limited 37
38 Other Views Data View Implementation View Deployment View Operational View Infrastructure View You don t have to document all the views. Pick and choose the views that are applicable to you, depending on the audience. For instance, the Deployment team will be interested in the Deployment and Infrastructure views, while the Database Admin will be interested in the Data View. 38
39 Design Docs 39
40 Design Docs Software Architecture docs are system-level docs. They are the base of Dev docs. Design docs are feature specific. They assume the knowledge covered in the software architecture docs and build on it. They are incremental additions to the architecture docs. Design docs usually accompany an architecture diagram with pointers to detailed feature specifications of smaller pieces of the design. 40
41 Design Docs What should a Design Doc include: Overview/Concept/Problem statement Context diagram and background information Possible solutions Analysis of possible solutions Solution chosen and rationale Areas impacted by chosen solution Workflow Code implementation Scenarios not addressed References 41
42 Design Doc Example Requirement: User should be able to send and receive s using Gmail. Background and prerequisites: Before understanding how Gmail sends and receives , we need to understand: Architecture of Gmail How is an composed How SMTP works How POP3 works 42
43 Design Doc Example Solution: 1. User composes an on the client. 2. Client connects to the server. 3. Server looks up the contact database and locates the recipient server. 4. Server transfers the to the recipient server using the SMTP protocol. 5. Recipient server sends a notification to the recipient client that an has been received. 6. Recipient client connects to the recipient server. 7. is transferred to the recipient client using the POP3 protocol. 8. Recipient client downloads the and displays it to the user. 43
44 Design Doc Example Solution: 44
45 Design Doc Example Code implementation <Written by Developers> Areas of impact Client Details Server Details Scenarios not addressed Sending s to multiple users has not been addressed in this solution. 45
46 Process 46
47 Software Architecture Docs Refer to User docs, sales and support, marketing docs Browse code Daily TOI sessions with Developers 47
48 Design Docs Sprint planning Team discussion meeting Engineering requirements meeting Design Review meeting Code review QA TOI/Demo Sales and Support TOI Add links to user docs and sales and support, and marketing docs. 48
49 FAQs These docs are very technical. Shouldn t the Developers be writing these? If developers want to say: Miss Piggy wants to go to lunch, so she starts a new and types Kermit's address in the "To:" box. They end up writing: Assume a function AddressOf(x) which is defined as the mapping from a user x, to the RFC-822 compliant address of that user, an ANSI string. Let us assume user A and user B, where A wants to send an to user B. So user A initiates a new message using any (but not all) of the techniques defined elsewhere, and types AddressOf(B) in the To: editbox. 49
50 FAQs What are the challenges? Very technical Input to output ratio is skewed Need to use all skills of tech writing What are the rewards? Real-time user feedback Sound technical knowledge develop your own process to ramp up faster Niche field 50
51 FAQs What are the skills of user documentation that can be applicable for developer documentation? Technical + Writing Analytical thinking Videos, Concept topics, Information Architecture Most important: Interviewing the SMEs 51
52 @AmrutaRanade 52
Chapter 2 Application Layer. Lecture 5 FTP, Mail. Computer Networking: A Top Down Approach
 Chapter 2 Application Layer Lecture 5 FTP, Mail Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012 Application Layer 2-1 Chapter 2: outline 2.1 principles
Chapter 2 Application Layer Lecture 5 FTP, Mail Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012 Application Layer 2-1 Chapter 2: outline 2.1 principles
CS43: Computer Networks Email. Kevin Webb Swarthmore College September 24, 2015
 CS43: Computer Networks Email Kevin Webb Swarthmore College September 24, 2015 Three major components: mail (MUA) mail transfer (MTA) simple mail transfer protocol: SMTP User Agent a.k.a. mail reader composing,
CS43: Computer Networks Email Kevin Webb Swarthmore College September 24, 2015 Three major components: mail (MUA) mail transfer (MTA) simple mail transfer protocol: SMTP User Agent a.k.a. mail reader composing,
FTP and email. Computer Networks. FTP: the file transfer protocol
 Computer Networks and email Based on Computer Networking, 4 th Edition by Kurose and Ross : the file transfer protocol transfer file to/from remote host client/ model client: side that initiates transfer
Computer Networks and email Based on Computer Networking, 4 th Edition by Kurose and Ross : the file transfer protocol transfer file to/from remote host client/ model client: side that initiates transfer
Networking Applications
 Networking Dr. Ayman A. Abdel-Hamid College of Computing and Information Technology Arab Academy for Science & Technology and Maritime Transport Electronic Mail 1 Outline Introduction SMTP MIME Mail Access
Networking Dr. Ayman A. Abdel-Hamid College of Computing and Information Technology Arab Academy for Science & Technology and Maritime Transport Electronic Mail 1 Outline Introduction SMTP MIME Mail Access
Nokia for Business. Nokia and Nokia Connecting People are registered trademarks of Nokia Corporation
 Nokia for Business Nokia and Nokia Connecting People are registered trademarks of Nokia Corporation Nokia E50 Legal Notice Copyright Nokia 2006. All rights reserved. Reproduction, transfer, distribution
Nokia for Business Nokia and Nokia Connecting People are registered trademarks of Nokia Corporation Nokia E50 Legal Notice Copyright Nokia 2006. All rights reserved. Reproduction, transfer, distribution
Email Electronic Mail
 Email Electronic Mail Electronic mail paradigm Most heavily used application on any network Electronic version of paper-based office memo Quick, low-overhead written communication Dates back to time-sharing
Email Electronic Mail Electronic mail paradigm Most heavily used application on any network Electronic version of paper-based office memo Quick, low-overhead written communication Dates back to time-sharing
Internet Technology 2/13/2013
 Internet Technology 03r. Application layer protocols: email Email: Paul Krzyzanowski Rutgers University Spring 2013 1 2 Simple Mail Transfer Protocol () Defined in RFC 2821 (April 2001) Original definition
Internet Technology 03r. Application layer protocols: email Email: Paul Krzyzanowski Rutgers University Spring 2013 1 2 Simple Mail Transfer Protocol () Defined in RFC 2821 (April 2001) Original definition
2- Electronic Mail (SMTP), File Transfer (FTP), & Remote Logging (TELNET)
 2- Electronic Mail (SMTP), File Transfer (FTP), & Remote Logging (TELNET) There are three popular applications for exchanging information. Electronic mail exchanges information between people and file
2- Electronic Mail (SMTP), File Transfer (FTP), & Remote Logging (TELNET) There are three popular applications for exchanging information. Electronic mail exchanges information between people and file
Nokia E90 Communicator E-mail support
 Nokia E90 Communicator Nokia E90 Communicator Legal Notice Nokia, Nokia Connecting People, Eseries and E90 Communicator are trademarks or registered trademarks of Nokia Corporation. Other product and company
Nokia E90 Communicator Nokia E90 Communicator Legal Notice Nokia, Nokia Connecting People, Eseries and E90 Communicator are trademarks or registered trademarks of Nokia Corporation. Other product and company
Protocolo FTP. FTP: Active Mode. FTP: Active Mode. FTP: Active Mode. FTP: the file transfer protocol. Separate control, data connections
 : the file transfer protocol Protocolo at host interface local file system file transfer remote file system utilizes two ports: - a 'data' port (usually port 20...) - a 'command' port (port 21) SISTEMAS
: the file transfer protocol Protocolo at host interface local file system file transfer remote file system utilizes two ports: - a 'data' port (usually port 20...) - a 'command' port (port 21) SISTEMAS
Configuring your email client to connect to your Exchange mailbox
 Configuring your email client to connect to your Exchange mailbox Contents Use Outlook Web Access (OWA) to access your Exchange mailbox... 2 Use Outlook 2003 to connect to your Exchange mailbox... 3 Add
Configuring your email client to connect to your Exchange mailbox Contents Use Outlook Web Access (OWA) to access your Exchange mailbox... 2 Use Outlook 2003 to connect to your Exchange mailbox... 3 Add
CSCI-1680 SMTP Chen Avin
 CSCI-1680 Chen Avin Based on Computer Networking: A Top Down Approach - 6th edition Electronic Three major components: s s simple transfer protocol: User Agent a.k.a. reader composing, editing, reading
CSCI-1680 Chen Avin Based on Computer Networking: A Top Down Approach - 6th edition Electronic Three major components: s s simple transfer protocol: User Agent a.k.a. reader composing, editing, reading
MailEnable Connector for Microsoft Outlook
 MailEnable Connector for Microsoft Outlook Version 2.23 This guide describes the installation and functionality of the MailEnable Connector for Microsoft Outlook. Features The MailEnable Connector for
MailEnable Connector for Microsoft Outlook Version 2.23 This guide describes the installation and functionality of the MailEnable Connector for Microsoft Outlook. Features The MailEnable Connector for
FTP: the file transfer protocol
 File Transfer: FTP FTP: the file transfer protocol at host FTP interface FTP client local file system file transfer FTP remote file system transfer file to/from remote host client/ model client: side that
File Transfer: FTP FTP: the file transfer protocol at host FTP interface FTP client local file system file transfer FTP remote file system transfer file to/from remote host client/ model client: side that
Getting Started Guide
 Getting Started Guide Mulberry IMAP Internet Mail Client Versions 3.0 & 3.1 Cyrusoft International, Inc. Suite 780 The Design Center 5001 Baum Blvd. Pittsburgh PA 15213 USA Tel: +1 412 605 0499 Fax: +1
Getting Started Guide Mulberry IMAP Internet Mail Client Versions 3.0 & 3.1 Cyrusoft International, Inc. Suite 780 The Design Center 5001 Baum Blvd. Pittsburgh PA 15213 USA Tel: +1 412 605 0499 Fax: +1
MAPI Connector Overview
 The CommuniGate Pro Server can be used as a "service provider" for Microsoft Windows applications supporting the MAPI (Microsoft Messaging API). To use this service, a special Connector library (CommuniGate
The CommuniGate Pro Server can be used as a "service provider" for Microsoft Windows applications supporting the MAPI (Microsoft Messaging API). To use this service, a special Connector library (CommuniGate
isecuremail User Guide for iphone
 isecuremail User Guide for iphone Page 1 CONTENTS Chapter 1: Welcome... 4 Chapter 2: Getting Started... 5 Compatability... 5 Preliminary Steps... 5 Setting up a POP3 / IMAP4/ Exchange Email Account...
isecuremail User Guide for iphone Page 1 CONTENTS Chapter 1: Welcome... 4 Chapter 2: Getting Started... 5 Compatability... 5 Preliminary Steps... 5 Setting up a POP3 / IMAP4/ Exchange Email Account...
Collax Mail Server. Howto. This howto describes the setup of a Collax server as mail server.
 Collax Mail Server Howto This howto describes the setup of a Collax server as mail server. Requirements Collax Business Server Collax Groupware Suite Collax Platform Server including Collax Communication
Collax Mail Server Howto This howto describes the setup of a Collax server as mail server. Requirements Collax Business Server Collax Groupware Suite Collax Platform Server including Collax Communication
Remote login (Telnet):
 SFWR 4C03: Computer Networks and Computer Security Feb 23-26 2004 Lecturer: Kartik Krishnan Lectures 19-21 Remote login (Telnet): Telnet permits a user to connect to an account on a remote machine. A client
SFWR 4C03: Computer Networks and Computer Security Feb 23-26 2004 Lecturer: Kartik Krishnan Lectures 19-21 Remote login (Telnet): Telnet permits a user to connect to an account on a remote machine. A client
Email, SNMP, Securing the Web: SSL
 Email, SNMP, Securing the Web: SSL 4 January 2015 Lecture 12 4 Jan 2015 SE 428: Advanced Computer Networks 1 Topics for Today Email (SMTP, POP) Network Management (SNMP) ASN.1 Secure Sockets Layer 4 Jan
Email, SNMP, Securing the Web: SSL 4 January 2015 Lecture 12 4 Jan 2015 SE 428: Advanced Computer Networks 1 Topics for Today Email (SMTP, POP) Network Management (SNMP) ASN.1 Secure Sockets Layer 4 Jan
Evolution of the WWW. Communication in the WWW. WWW, HTML, URL and HTTP. HTTP Abstract Message Format. The Client/Server model is used:
 Evolution of the WWW Communication in the WWW World Wide Web (WWW) Access to linked documents, which are distributed over several computers in the History of the WWW Origin 1989 in the nuclear research
Evolution of the WWW Communication in the WWW World Wide Web (WWW) Access to linked documents, which are distributed over several computers in the History of the WWW Origin 1989 in the nuclear research
Configuring Outlook to send mail via your Exchange mailbox using an alternative email address
 Configuring Outlook to send mail via your Exchange mailbox using an alternative email address This document is based on Exchange mailboxes and using Outlook 2007. The principles outlined are equally valid
Configuring Outlook to send mail via your Exchange mailbox using an alternative email address This document is based on Exchange mailboxes and using Outlook 2007. The principles outlined are equally valid
IceWarp Outlook Connector 4 User Guide
 IceWarp Unified Communications IceWarp Outlook Connector 4 User Guide Version 10.3 Printed on 23 February, 2011 Contents IceWarp Outlook Connector 4 1 Installing IceWarp Connector... 2 Pre-Installation
IceWarp Unified Communications IceWarp Outlook Connector 4 User Guide Version 10.3 Printed on 23 February, 2011 Contents IceWarp Outlook Connector 4 1 Installing IceWarp Connector... 2 Pre-Installation
Using the Web email service
 Using the Web email service This booklet describes the web based email service used by Sandwell schools. The web based email service was introduced in January 2005 to replace an earlier webmail system.
Using the Web email service This booklet describes the web based email service used by Sandwell schools. The web based email service was introduced in January 2005 to replace an earlier webmail system.
Sonian Getting Started Guide October 2008
 Sonian Getting Started Guide October 2008 Sonian, Inc. For Authorized Use Only 1 Create your new archiving account 3 Configure your firewall for IMAP collections 4 (Skip this step if you will be using
Sonian Getting Started Guide October 2008 Sonian, Inc. For Authorized Use Only 1 Create your new archiving account 3 Configure your firewall for IMAP collections 4 (Skip this step if you will be using
PrinterOn Enterprise Administration Support Guide
 PrinterOn Enterprise Administration Support Guide Version 2.5 Doc Rev: 1.1 Table of Contents 1. Overview...4 2. Hardware and Operating System Requirements...5 2.1. Hardware Requirements...5 2.2. Software
PrinterOn Enterprise Administration Support Guide Version 2.5 Doc Rev: 1.1 Table of Contents 1. Overview...4 2. Hardware and Operating System Requirements...5 2.1. Hardware Requirements...5 2.2. Software
Using Avaya Aura Messaging
 Using Avaya Aura Messaging Release 6.3.2 Issue 1 December 2014 Contents Chapter 1: Getting Started... 4 Messaging overview... 4 Prerequisites... 4 Accessing your mailbox from any phone... 4 Accessing the
Using Avaya Aura Messaging Release 6.3.2 Issue 1 December 2014 Contents Chapter 1: Getting Started... 4 Messaging overview... 4 Prerequisites... 4 Accessing your mailbox from any phone... 4 Accessing the
2- Electronic Mail (SMTP), File Transfer (FTP), & Remote Logging (TELNET)
 2- Electronic Mail (SMTP), File Transfer (FTP), & Remote Logging (TELNET) There are three popular applications for exchanging information. Electronic mail exchanges information between people and file
2- Electronic Mail (SMTP), File Transfer (FTP), & Remote Logging (TELNET) There are three popular applications for exchanging information. Electronic mail exchanges information between people and file
User Guide. Time Warner Cable Business Class Cloud Solutions Control Panel. Hosted Microsoft Exchange 2007 Hosted Microsoft SharePoint 2007
 Chapter Title Time Warner Cable Business Class Cloud Solutions Control Panel User Guide Hosted Microsoft Exchange 2007 Hosted Microsoft SharePoint 2007 Version 1.1 Table of Contents Table of Contents...
Chapter Title Time Warner Cable Business Class Cloud Solutions Control Panel User Guide Hosted Microsoft Exchange 2007 Hosted Microsoft SharePoint 2007 Version 1.1 Table of Contents Table of Contents...
Cloud. Hosted Exchange Administration Manual
 Cloud Hosted Exchange Administration Manual Table of Contents Table of Contents... 1 Table of Figures... 4 1 Preface... 6 2 Telesystem Hosted Exchange Administrative Portal... 7 3 Hosted Exchange Service...
Cloud Hosted Exchange Administration Manual Table of Contents Table of Contents... 1 Table of Figures... 4 1 Preface... 6 2 Telesystem Hosted Exchange Administrative Portal... 7 3 Hosted Exchange Service...
Merak Outlook Connector User Guide
 IceWarp Server Merak Outlook Connector User Guide Version 9.0 Printed on 21 August, 2007 i Contents Introduction 1 Installation 2 Pre-requisites... 2 Running the install... 2 Add Account Wizard... 6 Finalizing
IceWarp Server Merak Outlook Connector User Guide Version 9.0 Printed on 21 August, 2007 i Contents Introduction 1 Installation 2 Pre-requisites... 2 Running the install... 2 Add Account Wizard... 6 Finalizing
IxLoad Data Mail (SMTP, POP3, IMAP) Features
 IxLoad Data Mail (SMTP, POP3, IMAP) Features Aptixia IxLoad can test the performance of email delivery systems and devices by emulating various email clients, servers and associated protocols. SMTP, POP3
IxLoad Data Mail (SMTP, POP3, IMAP) Features Aptixia IxLoad can test the performance of email delivery systems and devices by emulating various email clients, servers and associated protocols. SMTP, POP3
Reading mail via the Web on Mail.uh.edu
 Reading mail via the Web on Mail.uh.edu Connecting to mail via the Web Once you have obtained your userid and password, go to the Web Site http://mail.uh.edu You will see the following screen: Click Log
Reading mail via the Web on Mail.uh.edu Connecting to mail via the Web Once you have obtained your userid and password, go to the Web Site http://mail.uh.edu You will see the following screen: Click Log
USING YOUR GMAIL ACCOUNT FOR SCRUBBING YOUR REGULAR EMAIL OF SPAM Beginners Kaffee Klatch Presented by Bill Wilkinson
 USING YOUR GMAIL ACCOUNT FOR SCRUBBING YOUR REGULAR EMAIL OF SPAM Beginners Kaffee Klatch Presented by Bill Wilkinson The Gmail spam filter is highly acclaimed by many experts in the security and privacy
USING YOUR GMAIL ACCOUNT FOR SCRUBBING YOUR REGULAR EMAIL OF SPAM Beginners Kaffee Klatch Presented by Bill Wilkinson The Gmail spam filter is highly acclaimed by many experts in the security and privacy
MailStore Server 7 Technical Specifications
 MailStore Server 7 Technical Specifications MailStore Server The Standard in Email Archiving Businesses of all sizes can benefit from the legal, technical, and financial advantages of modern and secure
MailStore Server 7 Technical Specifications MailStore Server The Standard in Email Archiving Businesses of all sizes can benefit from the legal, technical, and financial advantages of modern and secure
Linux Network Administration
 Linux Network Administration Sendmail Evolution of Email The birth of electronic mail (email) occurred in the early 1960s The mailbox was a file in a user's home directory that was readable only by that
Linux Network Administration Sendmail Evolution of Email The birth of electronic mail (email) occurred in the early 1960s The mailbox was a file in a user's home directory that was readable only by that
THUNDERBIRD SETUP (STEP-BY-STEP)
 Jim McKnight www.jimopi.net Thunderbird_Setup.lwp revised 12-11-2013 (Note1: Not all sections have been updated for the latest version of Thunderbird available at the time I verified that Section. Each
Jim McKnight www.jimopi.net Thunderbird_Setup.lwp revised 12-11-2013 (Note1: Not all sections have been updated for the latest version of Thunderbird available at the time I verified that Section. Each
Netwrix Auditor for Exchange
 Netwrix Auditor for Exchange Quick-Start Guide Version: 8.0 4/22/2016 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from Netwrix
Netwrix Auditor for Exchange Quick-Start Guide Version: 8.0 4/22/2016 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from Netwrix
1 Introduction: Network Applications
 1 Introduction: Network Applications Some Network Apps E-mail Web Instant messaging Remote login P2P file sharing Multi-user network games Streaming stored video clips Internet telephone Real-time video
1 Introduction: Network Applications Some Network Apps E-mail Web Instant messaging Remote login P2P file sharing Multi-user network games Streaming stored video clips Internet telephone Real-time video
Email Management CSCU9B2 CSCU9B2 1
 Email Management CSCU9B2 CSCU9B2 1 Contents Email clients choosing and using Email message header and content Emailing to lists of people In and out message management Mime attachments and HTML email SMTP,
Email Management CSCU9B2 CSCU9B2 1 Contents Email clients choosing and using Email message header and content Emailing to lists of people In and out message management Mime attachments and HTML email SMTP,
CPSC 360 - Network Programming. Email, FTP, and NAT. http://www.cs.clemson.edu/~mweigle/courses/cpsc360
 CPSC 360 - Network Programming E, FTP, and NAT Michele Weigle Department of Computer Science Clemson University mweigle@cs.clemson.edu April 18, 2005 http://www.cs.clemson.edu/~mweigle/courses/cpsc360
CPSC 360 - Network Programming E, FTP, and NAT Michele Weigle Department of Computer Science Clemson University mweigle@cs.clemson.edu April 18, 2005 http://www.cs.clemson.edu/~mweigle/courses/cpsc360
Secure Email Frequently Asked Questions
 Secure Email Frequently Asked Questions Frequently Asked Questions Contents General Secure Email Questions and Answers Forced TLS Questions and Answers SecureMail Questions and Answers Glossary Support
Secure Email Frequently Asked Questions Frequently Asked Questions Contents General Secure Email Questions and Answers Forced TLS Questions and Answers SecureMail Questions and Answers Glossary Support
Internet Architecture
 Internet Architecture Lecture 10: How Email Work Assistant Teacher Samraa Adnan Al-Asadi 1 How Email Works Electronic mail, or email, might be the most heavily used feature of the Internet. You can use
Internet Architecture Lecture 10: How Email Work Assistant Teacher Samraa Adnan Al-Asadi 1 How Email Works Electronic mail, or email, might be the most heavily used feature of the Internet. You can use
Sending an Encrypted/Unencrypted Message. Let's Begin: Log In and Set Up Security Questions. Create Additional ProMailSource Accounts:
 Let's Begin: Log In and Set Up Security Questions To start, you can log in from the ProMailSource home page. Sending an Encrypted/Unencrypted Message Every message you send through ProMailSource is automatically
Let's Begin: Log In and Set Up Security Questions To start, you can log in from the ProMailSource home page. Sending an Encrypted/Unencrypted Message Every message you send through ProMailSource is automatically
Published : 2013-12-02 License : None
 K9 1 2 Published : 2013-12-02 License : None INTRODUCTION K-9 Mail is an email application (app) for Android phones or tablets. K-9 supports multiple mailboxes, each independently configurable. T his ability
K9 1 2 Published : 2013-12-02 License : None INTRODUCTION K-9 Mail is an email application (app) for Android phones or tablets. K-9 supports multiple mailboxes, each independently configurable. T his ability
IBM WebSphere Adapter for Email 7.0.0.0. Quick Start Tutorials
 IBM WebSphere Adapter for Email 7.0.0.0 Quick Start Tutorials Note: Before using this information and the product it supports, read the information in "Notices" on page 182. This edition applies to version
IBM WebSphere Adapter for Email 7.0.0.0 Quick Start Tutorials Note: Before using this information and the product it supports, read the information in "Notices" on page 182. This edition applies to version
MailStore Server 5.0 Documentation
 MailStore Server 5.0 Documentation 2010 deepinvent Software GmbH 24. May 2011 Products that are referred to in this document may be either trademarks and/or registered trademarks of the respective owners.
MailStore Server 5.0 Documentation 2010 deepinvent Software GmbH 24. May 2011 Products that are referred to in this document may be either trademarks and/or registered trademarks of the respective owners.
Clearswift Information Governance
 Clearswift Information Governance Implementing the CLEARSWIFT SECURE Encryption Portal on the CLEARSWIFT SECURE Email Gateway Version 1.10 02/09/13 Contents 1 Introduction... 3 2 How it Works... 4 3 Configuration
Clearswift Information Governance Implementing the CLEARSWIFT SECURE Encryption Portal on the CLEARSWIFT SECURE Email Gateway Version 1.10 02/09/13 Contents 1 Introduction... 3 2 How it Works... 4 3 Configuration
Before starting to use the new system you will need to know the password to your e-wire email account.
 Contents E-Wire Email Configuration and Migration... 2 Webmail... 2 Migration Process... 2 POP Accounts... 3 Checking Current POP Configuration... 3 POP Migration Process... 5 IMAP Accounts... 6 IMAP Migration
Contents E-Wire Email Configuration and Migration... 2 Webmail... 2 Migration Process... 2 POP Accounts... 3 Checking Current POP Configuration... 3 POP Migration Process... 5 IMAP Accounts... 6 IMAP Migration
Evolution of the WWW. Communication in the WWW. WWW, HTML, URL and HTTP. HTTP - Message Format. The Client/Server model is used:
 Evolution of the WWW Communication in the WWW World Wide Web (WWW) Access to linked documents, which are distributed over several computers in the History of the WWW Origin 1989 in the nuclear research
Evolution of the WWW Communication in the WWW World Wide Web (WWW) Access to linked documents, which are distributed over several computers in the History of the WWW Origin 1989 in the nuclear research
9236245 Issue 2EN. Nokia and Nokia Connecting People are registered trademarks of Nokia Corporation
 9236245 Issue 2EN Nokia and Nokia Connecting People are registered trademarks of Nokia Corporation Nokia 9300 Configuring connection settings Legal Notice Copyright Nokia 2005. All rights reserved. Reproduction,
9236245 Issue 2EN Nokia and Nokia Connecting People are registered trademarks of Nokia Corporation Nokia 9300 Configuring connection settings Legal Notice Copyright Nokia 2005. All rights reserved. Reproduction,
How To Set Up Your Email
 How To Set Up Your Email Contents Page Microsoft Outlook 1 Outlook Express 6 7 Webmail (this is for those who do not use an email programme) 12 Windows Live Mail 22 Mozilla Thunderbird 26 Windows Mail
How To Set Up Your Email Contents Page Microsoft Outlook 1 Outlook Express 6 7 Webmail (this is for those who do not use an email programme) 12 Windows Live Mail 22 Mozilla Thunderbird 26 Windows Mail
Using email over FleetBroadband
 Using email over FleetBroadband Version 01 20 October 2007 inmarsat.com/fleetbroadband Whilst the information has been prepared by Inmarsat in good faith, and all reasonable efforts have been made to ensure
Using email over FleetBroadband Version 01 20 October 2007 inmarsat.com/fleetbroadband Whilst the information has been prepared by Inmarsat in good faith, and all reasonable efforts have been made to ensure
After you've enabled POP/IMAP access in i.mail, you need to configure your email client to download i.mail messages.
 User Guide- i.mail enhancement Configure POP/IMAP access using Outlook and Windows Mail Firstly, you need to enable POP/IMAP on your i.mail account: 1. Log into your i.mail account via web 2. Click Mail
User Guide- i.mail enhancement Configure POP/IMAP access using Outlook and Windows Mail Firstly, you need to enable POP/IMAP on your i.mail account: 1. Log into your i.mail account via web 2. Click Mail
Email Archiving Service Finding Your Own Messages Guide
 Email Archiving Service Finding Your Own Messages Guide This guide is for end-users. It explains how to search for your own messages within the email archive using Outlook and Outlook Web Access (OWA).
Email Archiving Service Finding Your Own Messages Guide This guide is for end-users. It explains how to search for your own messages within the email archive using Outlook and Outlook Web Access (OWA).
Astaro Mail Archiving Getting Started Guide
 Connect With Confidence Astaro Mail Archiving Getting Started Guide About this Getting Started Guide The Astaro Mail Archiving Service is an archiving platform in the form of a fully hosted service. E-mails
Connect With Confidence Astaro Mail Archiving Getting Started Guide About this Getting Started Guide The Astaro Mail Archiving Service is an archiving platform in the form of a fully hosted service. E-mails
How To Synchronize With Gmail For Business On Shoretel
 Voice Mail Synchronization with Gmail for Business Voice Mail Synchronization with Gmail for Business The Synchronization with Gmail for Business feature automatically synchronizes the state of a ShoreTel
Voice Mail Synchronization with Gmail for Business Voice Mail Synchronization with Gmail for Business The Synchronization with Gmail for Business feature automatically synchronizes the state of a ShoreTel
How To Use Gfi Mailarchiver On A Pc Or Macbook With Gfi Email From A Windows 7.5 (Windows 7) On A Microsoft Mail Server On A Gfi Server On An Ipod Or Gfi.Org (
 GFI MailArchiver for Exchange 4 Manual By GFI Software http://www.gfi.com Email: info@gfi.com Information in this document is subject to change without notice. Companies, names, and data used in examples
GFI MailArchiver for Exchange 4 Manual By GFI Software http://www.gfi.com Email: info@gfi.com Information in this document is subject to change without notice. Companies, names, and data used in examples
WEBROOT EMAIL ARCHIVING SERVICE. Getting Started Guide North America. The best security in an unsecured world. TM
 WEBROOT EMAIL ARCHIVING SERVICE Getting Started Guide North America Webroot Software, Inc. World Headquarters 2560 55th Street Boulder CO 80301 USA www.webroot.com 800.870.8102 Table of Contents Create
WEBROOT EMAIL ARCHIVING SERVICE Getting Started Guide North America Webroot Software, Inc. World Headquarters 2560 55th Street Boulder CO 80301 USA www.webroot.com 800.870.8102 Table of Contents Create
MailEnable Scalability White Paper Version 1.2
 MailEnable Scalability White Paper Version 1.2 Table of Contents 1 Overview...2 2 Core architecture...3 2.1 Configuration repository...3 2.2 Storage repository...3 2.3 Connectors...3 2.3.1 SMTP Connector...3
MailEnable Scalability White Paper Version 1.2 Table of Contents 1 Overview...2 2 Core architecture...3 2.1 Configuration repository...3 2.2 Storage repository...3 2.3 Connectors...3 2.3.1 SMTP Connector...3
20.12. smtplib SMTP protocol client
 20.12. smtplib SMTP protocol client The smtplib module defines an SMTP client session object that can be used to send mail to any Internet machine with an SMTP or ESMTP listener daemon. For details of
20.12. smtplib SMTP protocol client The smtplib module defines an SMTP client session object that can be used to send mail to any Internet machine with an SMTP or ESMTP listener daemon. For details of
OpenProtocols Connector for Microsoft Outlook Version 2.00 ARPDev Pty. Ltd. Overview. Features. Requirements
 OpenProtocols Connector for Microsoft Outlook Version 2.00 ARPDev Pty. Ltd Overview This guide describes the installation and functionality of the OpenProtocols for Microsoft Outlook. The OpenProtocols
OpenProtocols Connector for Microsoft Outlook Version 2.00 ARPDev Pty. Ltd Overview This guide describes the installation and functionality of the OpenProtocols for Microsoft Outlook. The OpenProtocols
e- storage Mail Archive
 e- storage Mail Archive 1 TABLE OF CONTENTS 1.0 OVERVIEW 3 1.1 INTRODUCTION... 3 1.2 REQUIREMENT. 4 2.0 SETUP AND CONFIGURATION. 6 2.1 CREATE NEW ARCHIVE PROFILE. 6 2.1.1 Gmail Account.. 8 2.1.2 Hotmail
e- storage Mail Archive 1 TABLE OF CONTENTS 1.0 OVERVIEW 3 1.1 INTRODUCTION... 3 1.2 REQUIREMENT. 4 2.0 SETUP AND CONFIGURATION. 6 2.1 CREATE NEW ARCHIVE PROFILE. 6 2.1.1 Gmail Account.. 8 2.1.2 Hotmail
SUPPORT GUIDE FOR EMAIL SETTINGS IN NOKIA 6600 IMAGING PHONE
 SUPPORT GUIDE FOR EMAIL SETTINGS IN NOKIA 6600 IMAGING PHONE Contents 1. INTRODUCTION...1 2. EMAIL ACCOUNT SETTINGS ON PHONE...1 3. EMAIL ACCOUNT SETTINGS WITH PC SUITE...4 Legal Notice Copyright 2003
SUPPORT GUIDE FOR EMAIL SETTINGS IN NOKIA 6600 IMAGING PHONE Contents 1. INTRODUCTION...1 2. EMAIL ACCOUNT SETTINGS ON PHONE...1 3. EMAIL ACCOUNT SETTINGS WITH PC SUITE...4 Legal Notice Copyright 2003
1. The Web: HTTP; file transfer: FTP; remote login: Telnet; Network News: NNTP; e-mail: SMTP.
 Chapter 2 Review Questions 1. The Web: HTTP; file transfer: FTP; remote login: Telnet; Network News: NNTP; e-mail: SMTP. 2. Network architecture refers to the organization of the communication process
Chapter 2 Review Questions 1. The Web: HTTP; file transfer: FTP; remote login: Telnet; Network News: NNTP; e-mail: SMTP. 2. Network architecture refers to the organization of the communication process
Version 1.7. Inbound Email Integration (POP3 and IMAP) Installation, Configuration and User Guide. Last updated October 2011
 Version 1.7 Inbound Email Integration (POP3 and IMAP) Installation, Configuration and User Guide Last updated October 2011 1 Introduction and Overview... 1 2 The Case for Email monitoring... 2 3 Installation
Version 1.7 Inbound Email Integration (POP3 and IMAP) Installation, Configuration and User Guide Last updated October 2011 1 Introduction and Overview... 1 2 The Case for Email monitoring... 2 3 Installation
Migration Quick Reference Guide for Administrators
 Migration Quick Reference Guide for Administrators 10 Easy Steps for Migration Maximize Performance with Easy Settings Changes Communicating with Your Users Reporting Spam Resources Page 1 10 Easy Steps
Migration Quick Reference Guide for Administrators 10 Easy Steps for Migration Maximize Performance with Easy Settings Changes Communicating with Your Users Reporting Spam Resources Page 1 10 Easy Steps
1. Open Thunderbird. If the Import Wizard window opens, select Don t import anything and click Next and go to step 3.
 Thunderbird The changes that need to be made in the email programs will be the following: Incoming mail server: newmail.one-eleven.net Outgoing mail server (SMTP): newmail.one-eleven.net You will also
Thunderbird The changes that need to be made in the email programs will be the following: Incoming mail server: newmail.one-eleven.net Outgoing mail server (SMTP): newmail.one-eleven.net You will also
MailStore Server 7 Documentation
 MailStore Server 7 Documentation 2012 MailStore Software GmbH 11. May 2012 Products that are referred to in this document may be either trademarks and/or registered trademarks of the respective owners.
MailStore Server 7 Documentation 2012 MailStore Software GmbH 11. May 2012 Products that are referred to in this document may be either trademarks and/or registered trademarks of the respective owners.
Advanced Settings. Help Documentation
 Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc. Advanced Settings Abuse Detection SmarterMail has several methods
Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc. Advanced Settings Abuse Detection SmarterMail has several methods
Outlook Express POP Instructions - Bloomsburg University Students
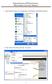 1. Open Outlook Express by clicking Start, All Programs, and Outlook Express. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add Mail 4. Enter your name and click Next. 2 5. Enter your full
1. Open Outlook Express by clicking Start, All Programs, and Outlook Express. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add Mail 4. Enter your name and click Next. 2 5. Enter your full
Getting Started Guide
 Getting Started Guide Mulberry Internet Email/Calendar Client Version 4.0 Cyrus Daboo Pittsburgh PA USA mailto:mulberry@mulberrymail.com http://www.mulberrymail.com/ Information in this document is subject
Getting Started Guide Mulberry Internet Email/Calendar Client Version 4.0 Cyrus Daboo Pittsburgh PA USA mailto:mulberry@mulberrymail.com http://www.mulberrymail.com/ Information in this document is subject
Introduction. Friday, June 21, 2002
 This article is intended to give you a general understanding how ArGoSoft Mail Server Pro, and en Email, in general, works. It does not give you step-by-step instructions; it does not walk you through
This article is intended to give you a general understanding how ArGoSoft Mail Server Pro, and en Email, in general, works. It does not give you step-by-step instructions; it does not walk you through
S-Doc User Guide. Instructions on using the Secure Document Online Courier with the CAAT Pension Plan. September 2012
 S-Doc User Guide Instructions on using the Secure Document Online Courier with the CAAT Pension Plan Secure solution provided by Accellion September 2012 S E C U R E C O L L A B O R A T I O N U S E R G
S-Doc User Guide Instructions on using the Secure Document Online Courier with the CAAT Pension Plan Secure solution provided by Accellion September 2012 S E C U R E C O L L A B O R A T I O N U S E R G
1 Accessing E-mail accounts on the Axxess Mail Server
 1 Accessing E-mail accounts on the Axxess Mail Server The Axxess Mail Server provides users with access to their e-mail folders through POP3, and IMAP protocols, or OpenWebMail browser interface. The server
1 Accessing E-mail accounts on the Axxess Mail Server The Axxess Mail Server provides users with access to their e-mail folders through POP3, and IMAP protocols, or OpenWebMail browser interface. The server
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Interwise Connect. Working with Reverse Proxy Version 7.x
 Working with Reverse Proxy Version 7.x Table of Contents BACKGROUND...3 Single Sign On (SSO)... 3 Interwise Connect... 3 INTERWISE CONNECT WORKING WITH REVERSE PROXY...4 Architecture... 4 Interwise Web
Working with Reverse Proxy Version 7.x Table of Contents BACKGROUND...3 Single Sign On (SSO)... 3 Interwise Connect... 3 INTERWISE CONNECT WORKING WITH REVERSE PROXY...4 Architecture... 4 Interwise Web
Enterprise Email Archive Managed Archiving & ediscovery Services User Manual
 Enterprise Email Archive Managed Archiving & ediscovery Services User Manual Copyright (C) 2012 MessageSolution Inc. All Rights Reserved Table of Contents Chapter 1: Introduction... 3 1.1 About MessageSolution
Enterprise Email Archive Managed Archiving & ediscovery Services User Manual Copyright (C) 2012 MessageSolution Inc. All Rights Reserved Table of Contents Chapter 1: Introduction... 3 1.1 About MessageSolution
Honeywell Secure Email External User Guide August 2013
 Honeywell Secure Email External User Guide August 2013 PAGE: 1 of 14 Chapter No Table of Content Page No 1 Introduction 3 2 Using the Honeywell Secure Email Interface 3 3 Sending an Encrypted Email to
Honeywell Secure Email External User Guide August 2013 PAGE: 1 of 14 Chapter No Table of Content Page No 1 Introduction 3 2 Using the Honeywell Secure Email Interface 3 3 Sending an Encrypted Email to
Securemail User Guide
 Securemail User Guide Created: 2009-02-17 Updated: 2013-07-05 - New links and Address Book instructions Updated: 2014-04-23 - http://dhhs.ne.gov/documents/dhhs-securemail-userguide.pdf 1 INDEX: How Securemail
Securemail User Guide Created: 2009-02-17 Updated: 2013-07-05 - New links and Address Book instructions Updated: 2014-04-23 - http://dhhs.ne.gov/documents/dhhs-securemail-userguide.pdf 1 INDEX: How Securemail
Request Manager Installation and Configuration Guide
 Request Manager Installation and Configuration Guide vcloud Request Manager 1.0.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced
Request Manager Installation and Configuration Guide vcloud Request Manager 1.0.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced
Webmail Using the Hush Encryption Engine
 Webmail Using the Hush Encryption Engine Introduction...2 Terms in this Document...2 Requirements...3 Architecture...3 Authentication...4 The Role of the Session...4 Steps...5 Private Key Retrieval...5
Webmail Using the Hush Encryption Engine Introduction...2 Terms in this Document...2 Requirements...3 Architecture...3 Authentication...4 The Role of the Session...4 Steps...5 Private Key Retrieval...5
Live@edu User Guide. Please visit the Helpdesk website for more information: http://www.smu.edu.sg/iits/helpdesk_support/index.asp
 IITS Main Office SINGAPORE MANAGEMENT UNIVERSITY Administration Building, Level 11 81, Victoria Street Singapore 188065 Phone: 65-6828 1930 Email: iits@smu.edu.sg Please visit the Helpdesk website for
IITS Main Office SINGAPORE MANAGEMENT UNIVERSITY Administration Building, Level 11 81, Victoria Street Singapore 188065 Phone: 65-6828 1930 Email: iits@smu.edu.sg Please visit the Helpdesk website for
DATA COMMUNICATOIN NETWORKING
 DATA COMMUNICATOIN NETWORKING Instructor: Ouldooz Baghban Karimi Course Book: Computer Networking, A Top-Down Approach By: Kurose, Ross Introduction Course Overview Basics of Computer Networks Internet
DATA COMMUNICATOIN NETWORKING Instructor: Ouldooz Baghban Karimi Course Book: Computer Networking, A Top-Down Approach By: Kurose, Ross Introduction Course Overview Basics of Computer Networks Internet
Start Thunderbird and follow its prompts to configure it for your Yale Central email account.
 e/ Yale Software Library http://www.yale.edu/its/software/ For assistance contact the ITS Help Desk 203-432-9000, helpdesk@yale.edu Thunderbird Before you begin Download and install a current version of
e/ Yale Software Library http://www.yale.edu/its/software/ For assistance contact the ITS Help Desk 203-432-9000, helpdesk@yale.edu Thunderbird Before you begin Download and install a current version of
Feature and Technical
 BlackBerry Enterprise Server for Microsoft Exchange Version: 5.0 Service Pack: 4 Feature and Technical Overview Published: 2013-11-07 SWD-20131107160132924 Contents 1 Document revision history...6 2 What's
BlackBerry Enterprise Server for Microsoft Exchange Version: 5.0 Service Pack: 4 Feature and Technical Overview Published: 2013-11-07 SWD-20131107160132924 Contents 1 Document revision history...6 2 What's
Ciphermail for BlackBerry Quick Start Guide
 CIPHERMAIL EMAIL ENCRYPTION Ciphermail for BlackBerry Quick Start Guide June 19, 2014, Rev: 8975 Copyright 2010-2014, ciphermail.com. Introduction This guide will explain how to setup and configure a Ciphermail
CIPHERMAIL EMAIL ENCRYPTION Ciphermail for BlackBerry Quick Start Guide June 19, 2014, Rev: 8975 Copyright 2010-2014, ciphermail.com. Introduction This guide will explain how to setup and configure a Ciphermail
NETWRIX EVENT LOG MANAGER
 NETWRIX EVENT LOG MANAGER QUICK-START GUIDE FOR THE ENTERPRISE EDITION Product Version: 4.0 July/2012. Legal Notice The information in this publication is furnished for information use only, and does not
NETWRIX EVENT LOG MANAGER QUICK-START GUIDE FOR THE ENTERPRISE EDITION Product Version: 4.0 July/2012. Legal Notice The information in this publication is furnished for information use only, and does not
Product Guide Revision A. McAfee Secure Web Mail Client 7.0.0 Software
 Product Guide Revision A McAfee Secure Web Mail Client 7.0.0 Software COPYRIGHT Copyright 2011 McAfee, Inc. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed,
Product Guide Revision A McAfee Secure Web Mail Client 7.0.0 Software COPYRIGHT Copyright 2011 McAfee, Inc. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed,
Architecture. The DMZ is a portion of a network that separates a purely internal network from an external network.
 Architecture The policy discussed suggests that the network be partitioned into several parts with guards between the various parts to prevent information from leaking from one part to another. One part
Architecture The policy discussed suggests that the network be partitioned into several parts with guards between the various parts to prevent information from leaking from one part to another. One part
Implementing MDaemon as an Email Security Gateway to Exchange Server
 Implementing MDaemon as an Email Security Gateway to Exchange Server Introduction MDaemon is widely deployed as a very effective antispam/antivirus gateway to Exchange. For optimum performance, we recommend
Implementing MDaemon as an Email Security Gateway to Exchange Server Introduction MDaemon is widely deployed as a very effective antispam/antivirus gateway to Exchange. For optimum performance, we recommend
Configuring TCP/IP Port & Firewall Monitoring With Sentry-go Quick & Plus! monitors
 Configuring TCP/IP Port & Firewall Monitoring With Sentry-go Quick & Plus! monitors 3Ds (UK) Limited, November, 2013 http://www.sentry-go.com Be Proactive, Not Reactive! TCP/IP Port Monitoring TCP/IP ports
Configuring TCP/IP Port & Firewall Monitoring With Sentry-go Quick & Plus! monitors 3Ds (UK) Limited, November, 2013 http://www.sentry-go.com Be Proactive, Not Reactive! TCP/IP Port Monitoring TCP/IP ports
NetWrix Account Lockout Examiner Version 4.0 Administrator Guide
 NetWrix Account Lockout Examiner Version 4.0 Administrator Guide Table of Contents Concepts... 1 Product Architecture... 1 Product Settings... 2 List of Managed Domains and Domain Controllers... 2 Email
NetWrix Account Lockout Examiner Version 4.0 Administrator Guide Table of Contents Concepts... 1 Product Architecture... 1 Product Settings... 2 List of Managed Domains and Domain Controllers... 2 Email
Secure Messaging Quick Reference Guide
 Secure Messaging Quick Reference Guide Overview The SHARE Secure Messaging feature allows a SHARE registered user to securely send health information to another SHARE registered user. The Secure Messaging
Secure Messaging Quick Reference Guide Overview The SHARE Secure Messaging feature allows a SHARE registered user to securely send health information to another SHARE registered user. The Secure Messaging
Netwrix Auditor for SQL Server
 Netwrix Auditor for SQL Server Quick-Start Guide Version: 8.0 4/22/2016 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from
Netwrix Auditor for SQL Server Quick-Start Guide Version: 8.0 4/22/2016 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from
Deploying the BIG-IP LTM system and Microsoft Windows Server 2003 Terminal Services
 Deployment Guide Deploying the BIG-IP System with Microsoft Windows Server 2003 Terminal Services Deploying the BIG-IP LTM system and Microsoft Windows Server 2003 Terminal Services Welcome to the BIG-IP
Deployment Guide Deploying the BIG-IP System with Microsoft Windows Server 2003 Terminal Services Deploying the BIG-IP LTM system and Microsoft Windows Server 2003 Terminal Services Welcome to the BIG-IP
Procedure to Save Email to the Projects Folder
 Capital Projects and Construction Post Office Box 751 Portland, Oregon 97207-0751 503-725-3738 tel 503-725-4329 fax www.fap.pdx.edu Effective Date: November 20, 2013 (Procedure checked using Mozilla Thunderbird
Capital Projects and Construction Post Office Box 751 Portland, Oregon 97207-0751 503-725-3738 tel 503-725-4329 fax www.fap.pdx.edu Effective Date: November 20, 2013 (Procedure checked using Mozilla Thunderbird
MSP/ISP Multi-Tenant Archiving Platform Online Deployment Customer Activation 10-Step Quick Guide
 MSP/ISP Multi-Tenant Archiving Platform Online Deployment Customer Activation 10-Step Quick Guide Copyright (C) 2011 MessageSolution Inc. All Rights Reserved 1 Table of Contents Pre-Implementation... 3
MSP/ISP Multi-Tenant Archiving Platform Online Deployment Customer Activation 10-Step Quick Guide Copyright (C) 2011 MessageSolution Inc. All Rights Reserved 1 Table of Contents Pre-Implementation... 3
Tutorial Details Product Demonstrated: X-301 Estimated Completion Time: 15 minutes
 How to Setup Email Notifications on ControlByWeb products Tutorial Details Product Demonstrated: X-301 Estimated Completion Time: 15 minutes Getting the Message ControlByWeb products can generate email
How to Setup Email Notifications on ControlByWeb products Tutorial Details Product Demonstrated: X-301 Estimated Completion Time: 15 minutes Getting the Message ControlByWeb products can generate email
PineApp Archive-Secure Quick Installation Guide:
 PineApp Archive-Secure Quick Installation Guide: The following guide provides setup instructions for Archive-SeCure s quick implementation for your network environment. For further detailing and other
PineApp Archive-Secure Quick Installation Guide: The following guide provides setup instructions for Archive-SeCure s quick implementation for your network environment. For further detailing and other
