(12) United States Patent (10) Patent N0.: US 8,176,126 B2 Da vi s et a]. 45 Date of Patent : Ma 8, 2012
|
|
|
- Bernard Simmons
- 8 years ago
- Views:
Transcription
1 ' US B2 (12) United States Patent (10) Patent N0.: US 8,176,126 B2 Da vi s et a]. 45 Date of Patent : Ma 8, 2012 (54) LIMIT SYSTEM, RATE METHOD OF TRANSFERRING AND PROGRAM TO 29513;, 7,117,358 B2 * 10/2006 Bandini arc 1... et ~~~~~~~~~~~~~~~~~~~~ al.... ~~ 713/153 MESSAGES FROM SUSPECTED SPAMMERS 7,203,749 B2 * 4/2007 Hiraga " 709/224 7,249,175 B1 * 7/2007 Donaldson /225 (75) Inventors: John Fred Davis, Durham, NC (U S); (Continued) Kevin David Himberger, Durham, NC DebshJfffriels; ( Chapel , FOREIGN PATENT DOCUMENTS ; arret osep eremia, NOrthYOrk (CA) JP A 4/2003 OTHER PUBLICATIONS (73) Asslgneez Internatlqnal Buslness Machmes Lisa 2002 Paper Spam Blocking With a Dynamically Updated Corporation Armonk NY (US) Firewall Ruleset Deeann M. M. Mikula, Christ Tracy, and Mike ( * ) Notice: Subject to any disclaimer, the term of this HoohngiTelemma Pubhc Access Internet pp' patent is extended or adjusted under 35 USC 1546)) by 2546 days Primary ExamineriDaVid England (74) Attorney, Agent, or Firm * Arthur J. SamodovitZ (22) Filed; Aug_ 26, 2004 A system, method and program product for managing s from a source suspected of sendmg spam. The s are (65) prior publication Date received determ1nat1on at' a?rewall is made or Whether router en a source route to has a mail sent an server. e-ma1l Us 2006/ A1 Mal 2, 2006 Which exhibits characteristics of spam. In response, subse quent s from the source destined for the mail server are (51) Int- Cl- rate-limiting at the?rewall or router such that the?rewall or G06F 15/16 ( ) router limits a rate at Which the subsequent s are for G06F 15/1 73 ( ) Warded from the?rewall or router to the mail server. The rate (52) US. Cl /206; 709/224 is predetermined and less than a maximum rate at Which the (58) Field of Classi?cation Search..... None?rewall or router can Physically forward e'ma?s to the mail See application?le for Complete Search history server absent the rate l1m1t. A determinatlon is made vvhether another source has sent another e-ma1l Wh1ch exh1b1ts more (56) References Cited characteristics of spam than the?rst said . In response, subsequent s from this other source are blocked at the U.S. PATENT DOCUMENTS?reWall or router. The rate limit can be a limit on a number of s per unit of time from the source that Will be forwarded 6,163,802 A 12/2000 Lin et al /217 6,189,035 B1 2/2001 Lockhart et al /229 from the?rewall or router to the mail server. 6,266,692 B1 7/2001 Greenstein /206 6,339,784 B1* 1/2002 Morris et al / Claims, 4 Drawing Sheets 121 NE RRIVES? EXTRACT SOURCE IF ADDRESS J04 DETERMINE LIKELIHOOD OF SPAM 306 LIKELIHOOD ABOVE UPPER THRESHOLD? LIKELIHOQD ELOW UPPER THRESHOLD BUT ABOVE LOWER THRESHOLD? NOTIFY MONITOR TO CREATE BLOCKING RULE FOR SOURCE IPADDRESS 310 DISCARD 312 NOTIFY MONITOR TO CREATE RATE-LIMITING RULE FOR SOURCE IP ADDRESS 330 OTIFY USER COMPUTER OF E-MAI 332
2 US 8,176,126 B2 Page 2 7,346,700 B2 * 2002/ A1* 2003/ A1* 2005/ A1* US. PATENT DOCUMENTS 3/2008 5/ /2003 6/2005 Gould et a /232 Morris et a /205 BenoWitZ et a /206 Thibadeau / / A1* 2005/ A1* 2006/ A1* 2007/ A1* * cited by examiner 7/2005 8/2005 3/2006 1/2007 Yu /206 Brown et a1. 709/206 Slater et a /206 Trupp et a /170
3 US. Patent May 8,2012 Sheet US 8,176,126 B2 mmov F2 1/ o2. rm:
4 US. Patent May 8,2012 Sheet US 8,176,126 B2 FIG EXTRACT SOURCE lp ADDRESS SOURCE YES BLOCK AND ADDRESS BLOCKED? DISCARD 196 SOURCE ADDRESS RATE-LIMITED? NO 206 CURRENT NO RATE ABOVE = LIMIT? FORWARD PACKET TO MAIL SERVER 204 SToRE 220 V WAIT FOR RETEST TIMER TO LAPSE 230
5 US. Patent May 8, 2012 Sheet US 8,176,126 B2 FIG EXTRACT SOURCE IP ADDRESS 304 DETERMINE LIKELIHOOD OF SPAM 306 NOTIFY MONITOR TO LIKELIHOOD YES CREATE BLOCKING ABOVE UPPER RULE FOR SOURCE THRESHOLD? IP ADDRESS 310 I DISCARD 312 LIKELIHOOD BELOW UPPER THRESHOLD BUT ABOVE LOWER THRESHOLD? END NOTIFY MONITOR TO CREATE RATE-LIMITING RULE FOR SOURCE IP ADDRESS 330 I NOTIFY USER COMPUTER OF 332
6 US. Patent May 8, 2012 Sheet 4 0f 4 US 8,176,126 B2 FIG. 4 RECEIVE NOTIFICATION OF SOURCE IP ADDRESS AND WHETHER TO BLOCK OR RATE-LIMIT FETCH CURRENT TIME FROM TIMER BLOCK REQUEST? YES ENTER RULE NAME, DURATION, TIMESTAMP AND "BLOCK" INDICATOR INTO ACTIONS DATABASE 512 I NOTIFY FIREWALL OR ROUTER OF NEW RULE IN ACTIONS DATABASE 520 PERIODICALLY EXAMINE RULES IN ACTIONS DATABASE 522 ENTER RULE NAME, DURATION, TIMESTAMP, RATE VALUE AND "RATE-LIMIT" INDICATOR INTO ACTIONS DATABASE 510 END EXPIRED RU LE? YES NO DELETE EXPIRED RULE AND NOTIFY FIREWALL OR ROUTER 524 END WAIT RETEST INTERVAL 526 I
7 1 SYSTEM, METHOD AND PROGRAM TO LIMIT RATE OF TRANSFERRING MESSAGES FROM SUSPECTED SPAMMERS FIELD OF THE INVENTION The invention relates generally to computer systems, and deals more particularly With a technique to reduce the impact of spam on a mail server. BACKGROUND OF THE INVENTION The Internet is Well known today, and comprises a vast number of user computers and servers interconnected via routers,?rewalls and networks. One role of the Internet is to provide a medium to exchange . A common problem today is spam, Where a source server sends commercial s via the Internet to numerous (thousands, even mil lions of) user computers via the user s mail servers. Each mail server provides an transfer function for multiple user computers. The spam clogs the Internet, mail servers and mail boxes of the user computers. Some mail servers may be so busy handling the spam, that they have little time to handle/ transfer legitimate . As a result, the legitimate is handled very slowly. It is known that an enterprise s intranet can be protected With a?rewall. The?reWall may be located between the enterprise s mail server and the Internet. The?reWall can be programmed to block from source IP addresses of likely spam servers. Spam detectors and?lters are Well known today such as Spam-Assassin (trademark of Apache Software Foundation) program. Typically, the spam detector and?lter are installed at an edge router or a?rewall for a mail server. The spam detector reviews incoming and cal culates a spam likelihood score for each based on its characteristics and the Weight of each characteristic. These characteristics include (a) key Words characteristic or mar keting material such as free and real-estate, etc. (b) Whether the is HTML type, (c) Whether the is malformed HTML type (Which is more characteristic of mar keting material than carefully Written HTML), (d) Whether the text omits the?rst or last name of the intended recipient, (e) Whether the subject line is blank or has certain Words characteristic of marketing, (f) Whether the identity listed in the from?eld matches the location of the source IP address, (g) Whether the includes colors, (h) Whether the has some text in larger font than ordinarily used for noncommercial , and (i) Whether the text is similar to or identical With other s from the same source. A known spam detector can also consider When multiple, similar s (ie the same or substantially the same text or the same subject) are addressed to multiple different recipients/ users and originate from the same source IP address. The spam detector Would ignore s sent from known, legiti mate sources, such as s from employees of the same corporation to Which the s are sent; these s are not considered to be spam. The legitimate sources may be found in a list supplied by a system administrator, and acces sible to the spam detector. If the spam likelihood score exceeds a predetermined upper threshold, then the is very likely to be spam. In such a case, the spam detector reads the IP address of the sender, and then blocks subsequent s from the same IP address and/or address by creating a corresponding spam?lter rule. Each spam?lter rule may specify a source IP address and/or address from Which Will not be accepted. The spam?lter rule is enforced at the?rewall or router, or a gateway server in the US 8,l76,126 B absence of a?rewall or router. The spam?lter rule may be in effect inde?nitely or for a predetermined amount of time, but can be periodically removed When there are too many?lters to e?iciently handle. A problem With the foregoing spam blocking technique is that some s are erroneously presumed to be spam based on their spam likelihood score or other factors. For example, a CEO or customer of a corporation may send an from an unrecognized computer to a large number of employees of the same corporation. In such a case, the known spam detector may presume the to be spam, and block it. An object of the present invention is to better manage suspected spam Which may actually be legitimate . SUMMARY The invention resides in a system, method and program product for managing s from a source suspected of sending spam. The s are received at a?rewall or router en route to a mail server. A determination is made Whether a source has sent an Which exhibits characteristics of spam. In response, subsequent s from the source des tined for the mail server are rate-limiting at the?rewall or router such that the?rewall or router limits a rate at Which the subsequent s are forwarded from the?rewall or router to the mail server. The rate is predetermined and less than a maximum rate at Which the?rewall or router can physically forward s to the mail server absent the rate limit. According to features of the present invention, a determi nation is made Whether another source has sent another Which exhibits more characteristics of spam than the?rst said . In response, subsequent s from this other source are blocked at the?rewall or router. The rate limit can be a limit on a number of s per unit of time from the source that Will be forwarded from the?rewall or router to the mail server. The characteristics of spam include one or more of the following characteristics: key Words characteristic of spam, Whether the is HTML type, Whether text in the omits a?rst or last name of an intended recipient, Whether a subject line of the is blank or includes Words characteristic of marketing, Whether an identity listed in a from?eld matches a location of a source IP address, Whether the includes colors, Whether the has some text in larger fonts than ordinarily used for noncommer cial , Whether multiple s With similar content are addressed to multiple different recipients and originate from a same source IP address, and Whether the text is similar to or identical With other s from a same source. BRIEF DESCRIPTION OF THE FIGURES FIG. 1 is a block diagram illustrating a computer system Which incorporates the present invention. FIG. 2 is a How chart of a spam management program Within a?rewall or router of the computer system of FIG. 1, according to the present invention. FIG. 3 is a How chart of a spam detector Within a mail server Within the computer system of FIG. 1, according to the present invention. FIG. 4 is a How chart of a monitor program Within the computer system of FIG. 1, according to the present inven tion. DETAILED DESCRIPTION OF THE PREFERRED EMBODIMENTS The present invention Will now be described in detail With reference to the?gures. FIG. 1 illustrates a distributed com
8 3 puter system generally designated 100. System 100 com prises a?rewall or router 110 and a mail server 112 coupled to the?rewall or router 110 via a subnet 103 (or other net work). System 100 also comprises a multiplicity of client/ user computers such as computer 114 coupled to mail server 112 via a Local Area Network (LAN) 105 (or other network). The?rewall or router 110 performs typical functions of known?rewalls and known spam blockers such as blocking s with a source address (i.e. the IP address of the sender of the known) known to be malicious. In addition, in accordance with the present invention,?rewall or router 110 rate-limits s from source addresses which have sent s that exhibit some characteristics of spam, but the characteristics are not suf?ciently de?nitive of spam to block the source altogether. Firewall or router 110 will not block s from these source IP addresses altogether, because the?rewall or router 110 is not reasonably certain that the s are spam. Rate-limiting means that the maximum rate at which the s from these IP addresses will be transferred from?rewall or router 110 to mail server 112 is less than the maximum rate at which these s could physically be transferred from?rewall or router 110 to mail server 112 (absent the rate-limit). Consequently, mail server 112 will not be overwhelmed or bogged down due to an abundance of s from these source IP addresses, and will have resources to quickly handle s from other IP addresses presumed to be legitimate. In the illustrated embodiment, a spam management pro gram 119 performs both the prior art function of blocking certain source IP addresses known to be sending spam and the new function of rate-limiting certain source IP address which exhibit some characteristics of spammers. Spam manage ment 119 is stored in a storage 210 for execution by CPU 163 under control of operating system 165. When each new is received, program 119 references a set of?lter rules 117 for respective source IP addresses to determine if the is subject to blocking or rate-limiting. Thus, if the IP address of the source of the matches one of the?lter rules (and the?lter rule is still in effect), then program 119 within the?rewall or router 110 blocks or rate-limits the depend ing on the nature of the?lter rule. The example of FIG. 1 illustrates six?lter rules - SA1, SA2, SA3, SA4, SAS and SA6, in?rewall or router Filter rules SA1, SA2, SA3 and SA4 are rules for rate-limiting s from four respective source IP addresses (or ranges of source IP addresses) for a?nite period of time. Filter rules SAS and SA6 are rules for blocking s from two respective source IP addresses (or ranges of source IP addresses) for a?nite period of time. The mail server 112 includes a message transfer agent ( MTA ) program 129, i.e. a program function which for wards received from the?rewall or router 110 to the intended recipient/user computer such as user computer 114. For example, MTA program 129 can be a Post?x (trademark of Post?x Corporation) mail transfer program. which is blocked altogether by the spam management program 119 in?rewall or router 110 is not forwarded to mail server 112, and so, cannot be not transferred from mail server 112 to the intended recipient. s which are rate limited by the spam management program 119 arrives at mail server 112, but at a?nite rate. Nevertheless, when the rate-limited is received by mail server 112, mail transfer program 129 for wards it rapidly to the intended recipient as if the originated from a source known to be legitimate. In other words, in the illustrated embodiment,?rewall or router 110 performs the rate-limiting, not the mail server 112. The server 112 also includes a known spam detector pro gram 121 such as Spam-Assassin spam detector program or US 8,176,126 B other spam detector program which evaluates characteristics of an and determines a spam likelihood score. The higher the spam likelihood score the more likely that the is spam. The spam detector program 121 may be part of the MTA program 129 or a separate program. Spam detec tor program 121 determines a spam likelihood score for each based on characteristics of the and the weight of each characteristic. These characteristics include (a) presence of key words characteristic or marketing material such as free and real-estate, etc. (b) whether the is HTML type, (c) whether the is malformed HTML type (which is more characteristic of marketing material than carefully written HTML), (d) whether the text omits the?rst or last name of the intended recipient, (e) whether the subject line is blank or has certain words characteristic of marketing, (f) whether the identity listed in the from?eld matches the location of the source IP address, (g) whether the includes colors, (h) whether the has some text in larger font than ordinarily used for noncommercial , and (i) whether the text is similar to or identical with other s from the same source. The spam detector program 121 can also consider whether multiple, similar s (i.e. the same or substantially the same text or the same subject) are addressed to multiple different recipients/users and originate from the same source IP address. The spam detector would ignore s sent from known, legitimate sources, such as s from employees of the same corporation to which the s are sent; these s are not considered to be spam. The legitimate sources may be found in a list supplied by a system administrator, and accessible to the spam detector program. If the spam likelihood score exceeds a predeter mined upper threshold, then the is very likely to be spam. If the spam likelihood score exceeds a predetermined lower threshold but is less than the predetermined upper threshold, then the may be spam, but the likelihood is not so certain. FIG. 2 is a?ow chart illustrating operation of spam man agement program 119 in more detail. In step 190, an incoming 125 is received by the?rewall or router 110. In response, the spam management program 119 extracts the source IP address of the incoming (step 192). Then, spam management program 119 determines if the source IP address of the matches the source IP address of an active?lter rule 117. As explained below, when a blocking or rate-limiting rule is created, it is assigned a start time (which is usually immediate upon creation) and a duration/period during which the blocking or rate-limiting rule is active, i.e. will be enforced. If the source IP address matches an active blocking rule, for example SAS or SA6 (decision 194, yes branch), then program 119 blocks and discards the , and does not forward it to mail server 112 (step 196). How ever, if the source IP address does not match an active block ing rule (decision 194, no branch), then program 119 deter mines if the source IP address matches an active rate-limiting rule (decision 202). If there is no active, rate-limiting rule (or blocking rule) which matches the source IP address of the current (decision 202, no branch), then program 119 in?rewall or router 110 forwards the packet to mail server 112 (step 204). However, if the source IP address matches an active rate limiting rule, for example, SA1, SA2, SA3 or SA4, then program 119 enforces the rate-limiting speci?ed in the rule such as follows. In one embodiment of the present invention, program 119 determines if the current incoming rate is above a predeter mined rate limit (step 206). For example, the permitted incoming rate may be set to ten s per minute from a respective source IP address. Every time an is
9 5 received, its time of arrival is recorded, and program 119 determines how many s Were received from this source IP address during the last minute. If there Were less than the predetermined rate limit, for example, less than or equal to ten s during the last minute, then the rate limit has not been exceeded, and program 119 forwards the to mail server 112 (step 204). HoWever, if there Were more than the prede termined limit during the last interval, for example, more than ten s during the last minute, then program 119 tempo rarily stores the current in storage 210 associated With?reWall or router 112 (step 220). Then, after a predetermined retest period elapses (step 230), for example,?ve minutes, program 119 again checks the current incoming rate, for example, the number of incoming s during the last minute (step 206). If the current rate has not been exceeded during the last interval (decision 206, no branch), for example, less than or equal to ten s during the last minute, then program 119 fetches the from storage 210 and forwards it to mail server 112 (step 204). HoWever, if the current rate limit has been exceeded decision 206, yes branch), for example, more than ten s during the last minute, then program 119 leaves the in storage until the next predetermined retest period elapses (steps 220 and 230). The foregoing process de?ned by steps is performed for each incoming . In another embodiment of the present invention, for each rate-limited source IP address, one , if any, per time period is transferred from?rewall or router 110 to mail server 112. For example, the time period can be six seconds. (This Will permit transfer of ten s per minute from a rate limited source IP address.) After each such time period, pro gram 119 checks storage 210 for any s from the respec tive source IP address that have not yet been transferred to mail server 112. If any such s exist in storage 210, then program 119 fetches one and transfers it to mail server 112. When a new arrives at?rewall or router 110 from this source IP address, program 119 checks if it has transferred another from this source IP address to mail server 112 in the current time period. If not, then program 119 transfers the current to mail server 112 (and records the time of transfer). If so, then program 119 stores the current in mail server 112 in a FIFO queue for this source IP address. (There is a separate FIFO queue for each source IP address.) In such a case, the oldest in the queue (for each source IP address) Will be transferred to mail server 112 at the end of the current unit of time. FIG. 3 illustrates processing by spam detector program 121 Within mail server 112 in more detail. Spain Detector pro gram 121 is stored in a storage 177 for execution by a CPU 173 under control of an operating system 175. Spam detector program 121 identi?es new sources of Which are very likely to be spam and then initiates creation of new, corre sponding source-address blocking rules for?rewall or router 110. Program 121 also identi?es new sources of Where have some lesser characteristics of spam and initiates creation of new, corresponding source-address rate-limiting rules for?rewall or router 110. In step 302, a new arrives at mail server 112 from?rewall or router 110. In response, program 121 extracts the source IP address of the (step 304). Then, program 121 determines the spam likelihood score indicating how likely the new is spam (step 306). If the new is very likely to be spam, i.e. the spam score exceeds the predetermined upper threshold (decision 3 08, yes branch), then program 121 noti?es a monitor program 130 as to the source IP address of this and that this source IP address should be blocked (step 310). Also, monitor program 130 discards the , so user computer 114 is not noti?ed US 8,176,126 B of the and the is not forwarded to user computer 114 (step 312). HoWever, if the new exhibits some lesser characteristics of spam, i.e. the spam score exceeds the predetermined lower threshold but is less than the predeter mined upper threshold (decision 308, no branch and decision 320, yes branch), then program 121 noti?es monitor program 130 as to the source IP address of this and that this source IP address should be rate-limited (step 330). Never theless, monitor program 130 Will still notify user computer 114 of the and allow transfer of the to user computer 114 (step 332). (Typically, the itself is not transferred until the user requests it from the user s mail box.) Referring again to decision 320, no branch, Where the spam likelihood score is less than the predetermined lower threshold, then program 121 noti?es user computer 114 of the , allows transfer of the to user computer 114 (step 332) and does not initiate creation of any blocking rule or rate-limiting rule. (Typically, the itself is not trans ferred until the user requests it from the user s mailbox.) FIG. 4 illustrates processing by the monitor program 130 for each source IP address identi?ed by spam detector pro gram 121 as a source IP address that should be blocked or rate-limited. The monitor program 130 can reside in server 112 or another server. When resident server 112, monitor program 130 is stored in storage 177 for execution by CPU 173 under control of operating system 175. In step 502, moni tor program 130 receives from the spam detector program 121 a noti?cation to block or rate-limit subsequent s from a speci?ed source IP address. In response, monitor program 130 determines the current time (step 504). If the noti?cation is to block the source IP address (decision 505, yes branch), then, the monitor program enters a rule name, current time, rule duration and block indicator into an actions database 132 (step 506). The initial duration of the rule is predeter mined, such as one minute. Subsequent blocking action of the same type on the same source address might be for a period at least as long as the initial period, such as 10 minutes. Refer ring again to decision 505, no branch, if the noti?cation is to rate-limit a source IP address (decision 507, yes branch), then the monitor program enters a rule name, current time, rule duration, rate value and a rate-limit indicator into the actions database 132 (step 510). The rate value is predeter mined, such as one percent of processing capacity on the link. Then, monitor program 132 noti?es the?rewall or router 110 that a new?lter rule has been added to the data base 132 (step 512). In response, the spam management program 119 copies the new?lter rule into its group of local?lter rules 117. Monitor program 130 periodically reviews the rules in the actions database to identify any rules that have expired (step 522). If any have expired (decision 523, yes branch), then monitor program 130 deletes them from the actions database 132 and noti?es spam management program 119 to delete the rule from its local data base 117 (step 524). After a predeter mined period elapses (step 526), monitor program 130 repeats steps Based on the foregoing, a spam rate-limiting system, method and program have been disclosed according to the present invention. HoWever, numerous modi?cations and substitutions can be made Without deviating from the scope of the present invention. For example, the foregoing rate-limit ing method and system can be applied to instant messaging spam (or SPIM), Where an enforcement module is used to rate-limit or block tra?ic to or from a particular address or subnet. Therefore, the present invention has been disclosed by Way of illustration and not limitation, and reference should be made to the following claims to determine the scope of the present invention.
10 7 The invention claimed is: 1. A method for managing s, said s being received at a?rewall or router en route to a mail server, said method comprising the computer implemented steps of: determining a?rst score indicating an extent to which contents of a?rst sent by a?rst source exhibit characteristics of spam, and in response to said?rst score exceeding a lower threshold but not exceeding an upper threshold, said?rewall or router limiting a rate at which said?rewall or router forwards subsequent s from said?rst source to said mail server, the rate limit being predetermined, greater than Zero and less than a maximum rate at which said?rewall or router is able to forward said subsequent s from said?rst source to said mail server absent said rate limit; determining a second score indicating an extent to which contents of a second sent by a second source exhibit characteristics of spam, and in response to said second score exceeding said upper threshold, said?re wall or router not forwarding to said mail server subse quent s from said second source destined for said mail server; and determining a third score indicating an extent to which contents of a third sent by a third source exhibit characteristics of spam, and in response to said third score being less than said lower threshold, said?rewall or router forwarding sub sequent s from said third source to said mail server without blocking or rate limiting said subsequent s from said third source based on said contents of said third A method as set forth in claim 1 wherein scores below said lower threshold indicate that corresponding s are probably not spam, scores above said upper threshold indi cate that corresponding s are probably spam, and scores between said lower and upper thresholds indicate that corresponding s have an intermediate likelihood of being spam. 3. A method as set forth in claim 1 wherein said rate limit is a limit on a number of s per unit of time from said?rst source that will be forwarded from said?rewall or router to said mail server. 4. A method as set forth in claim 1 wherein said rate limit is in effect for a predetermined period, and then discontinued such that subsequent s from said?rst source are not rate-limited based on said contents of said?rst A method as set forth in claim 1 wherein said character istics of spam include three or more of the following charac teristics: key words characteristic of spam, whether the is HTML type, whether text in the omits a?rst or last name of an intended recipient, whether a subject line of the is blank or includes words characteristic of marketing, whether an identity listed in a from?eld matches a location of a source IP address, whether the includes colors, whether the has some text in larger fonts than ordinarily used for noncommercial , whether multiple s with similar content are addressed to multiple different recipients and origi nate from a same source IP address, and whether the text is similar or identical to other s from a same source. 6. A system for managing s, said s being received at a?rewall or router en route to a mail server, said system comprising: means for determining a?rst score indicating an extent to which contents of a?rst sent by a?rst source US 8,176,126 B exhibit characteristics of spam, and in response to said?rst score exceeding a lower threshold but not exceeding an upper threshold, limiting a rate at which said?rewall or router forwards said subsequent s from said?rst source to said mail server, the rate limit being predetermined, greater than Zero and less than a maximum rate at which said?rewall or router is able to forward s from said?rst source to said mail server absent said rate limit; means for determining a second score indicating an extent to which contents of a second sent by a second source exhibit characteristics of spam, and in response to said second score exceeding said upper threshold, caus ing said?rewall or router to block from said mail server subsequent s from said second source destined for said mail server; and means for determining a third score indicating an extent to which contents of a third sent by a third source exhibit characteristics of spam, and in response to said third score being less than said lower threshold, allowing said?rewall or router to forward subsequent s from said third source to said mail server without block ing or rate-limiting said subsequent s from said third source based on said contents of said third A system as set forth in claim 6 wherein scores below said lower threshold indicate that corresponding s are probably not spam, scores above said upper threshold indi cate that corresponding s are probably spam, and scores between said lower and upper thresholds indicate that corresponding s have an intermediate likelihood of being spam. 8. A system as set forth in claim 5 wherein said rate limit is a limit on a number of s per unit of time from said?rst source that will be forwarded from said?rewall or router to said mail server. 9. A system as set forth in claim 6 wherein said rate limit is in effect for a predetermined period, and then discontinued such that subsequent s from said?rst source are not rate-limited based on said contents of said?rst A system as set forth in claim 6 wherein said charac teristics of spam include three or more of the following char acteristics: key words characteristic of spam, whether the is HTML type, whether text in the omits a?rst or last name of an intended recipient, whether a subject line of the is blank or includes words characteristic of marketing, whether an identity listed in a from?eld matches a location of a source IP address, whether the includes colors, whether the has some text in larger fonts than ordinarily used for noncommercial , whether multiple s with similar content are addressed to multiple different recipients and origi nate from a same source IP address, and whether the text is similar to or identical with other s from a same source. 11. A computer program product for managing s, said s being received at a?rewall or router en route to a mail server, said computer program product comprising: one or more computer readable storage media;?rst program instructions to determine a?rst score indicat ing an extent to which contents of a?rst sent by a?rst source exhibit characteristics of spam, and in response to said?rst score exceeding a lower threshold but not exceeding an upper threshold, limit a rate at which said?rewall or router forwards subsequent s from said?rst source to said mail server, the rate limit being predetermined, greater than Zero and less
11 9 than a maximum rate at Which said?rewall or router is able to forward s from said?rst source to said mail server absent said rate limit; second program instructions to determine a second score indicating an extent to Which contents of a second sent by a second source exhibit characteristics of spam, and in response to said second score exceeding said upper threshold, cause said?rewall or router to block from said mail server subsequent s from said sec ond source destined for said mail server; and third program instructions to determine a third score indi cating an extent to Which contents of a third sent by a third source exhibit characteristics of spam, and in response to said third score being less than said lower threshold, allow said?rewall or router to forward sub sequent s from saidthird source to said mail server Without blocking or rate-limiting said subsequent s from said third source based on said contents of said third , and Wherein said?rst, second and third program instructions are recorded on said one or more computer readable storage media. 12. A computer program product as set forth in claim 11 Wherein scores below said lower threshold indicate that cor responding s are probably not spam, scores above said upper threshold indicate that corresponding s are prob ably spam, and scores between said lower and upper thresh olds indicate that corresponding s have an intermediate likelihood of being spam. US 8,176,126 B A computer program product as set forth in claim 11 Wherein said rate limit is a limit on a number of s per unit of time from said?rst source that Will be forwarded from said?rewall or router to said mail server. 14. A computer program product as set forth in claim 11 Wherein said rate limit is in effect for a predetermined period, and then discontinued such that subsequent s from said?rst source are not rate-limited based on said contents of said?rst A computer program product as set forth in claim 11 Wherein said characteristics of spam include three or more of the following characteristics: key Words characteristic of spam, Whether the is HTML type, Whether text in the omits a?rst or last name of an intended recipient, Whether a subject line of the is blank or includes Words characteristic of marketing, Whether an identity listed in a from?eld matches a location of a source IP address, Whether the includes colors, Whether the has some text in larger fonts than ordinarily used for noncommercial , Whether multiple s With similar content are addressed to multiple different recipients and origi nate from a same source IP address, and Whether the text is similar to or identical With other s from a same source.
Hay (43) Pub. Date: Oct. 17, 2002
 US 20020152322A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0152322 A1 Hay (43) Pub. Date: Oct. 17, 2002 (54) (76) (21) (22) (51) (52) METHOD AND APPARATUS FOR FACILITATING
US 20020152322A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0152322 A1 Hay (43) Pub. Date: Oct. 17, 2002 (54) (76) (21) (22) (51) (52) METHOD AND APPARATUS FOR FACILITATING
(54) RAPID NOTIFICATION SYSTEM (52) US. Cl... 709/206. (57) ABSTRACT (75) Inventors: Anand Rajasekar, San Jose, CA
 US 20120303720A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2012/0303720 A1 Rajasekar et a]. (43) Pub. Date: NOV. 29, 2012 (54) RAPID NOTIFICATION SYSTEM (52) US. Cl......
US 20120303720A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2012/0303720 A1 Rajasekar et a]. (43) Pub. Date: NOV. 29, 2012 (54) RAPID NOTIFICATION SYSTEM (52) US. Cl......
US 20070016324A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0016324 A1. Operating System. 106 q f 108.
 US 20070016324A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0016324 A1 Oddiraj u et al. (43) Pub. Date: Jan. 18, 2007 (54) SYSTEM BOOT OPTMZER (75) nventors: Chandar
US 20070016324A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0016324 A1 Oddiraj u et al. (43) Pub. Date: Jan. 18, 2007 (54) SYSTEM BOOT OPTMZER (75) nventors: Chandar
(12) United States Patent Halonen
 (12) United States Patent Halonen US006334053B1 () Patent N0.: (45) Date of Patent: Dec. 25, 2001 (54) PROCEDURE AND SYSTEM FOR PROVIDING AN ANSWERING SERVICE (75) Inventor: Mikko Halonen, Oulu (Fl) (73)
(12) United States Patent Halonen US006334053B1 () Patent N0.: (45) Date of Patent: Dec. 25, 2001 (54) PROCEDURE AND SYSTEM FOR PROVIDING AN ANSWERING SERVICE (75) Inventor: Mikko Halonen, Oulu (Fl) (73)
60 REDIRECTING THE PRINT PATH MANAGER 1
 US006788429B1 (12) United States Patent (10) Patent No.: US 6,788,429 B1 Clough et al. (45) Date of Patent: Sep. 7, 2004 (54) REMOTE PRINT QUEUE MANAGEMENT FOREIGN PATENT DOCUMENTS (75) Inventors: James
US006788429B1 (12) United States Patent (10) Patent No.: US 6,788,429 B1 Clough et al. (45) Date of Patent: Sep. 7, 2004 (54) REMOTE PRINT QUEUE MANAGEMENT FOREIGN PATENT DOCUMENTS (75) Inventors: James
(Us) (73) Assignee: Avaya Technology Corp. Je?' McElroy, Columbia, SC (US); (21) Appl. No.: 10/413,024. (22) Filed: Apr. 14, 2003 (57) ABSTRACT
 US 20040202300A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0202300 A1 Cooper et al. (43) Pub. Date: Oct. 14, 2004 (54) CALL HANDLING USING NON-SPEECH CUES VIA A PERSONAL
US 20040202300A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0202300 A1 Cooper et al. (43) Pub. Date: Oct. 14, 2004 (54) CALL HANDLING USING NON-SPEECH CUES VIA A PERSONAL
(12) United States Patent Edelen
 US008285799B2 (12) United States Patent Edelen (10) Patent N0.: (45) Date of Patent: Oct. 9, 2012 (54) QUOTA-BASED ARCHIVING (75) Inventor: James Edelen, Renton, WA (U S) (73) Assignee: Microsoft Corporation,
US008285799B2 (12) United States Patent Edelen (10) Patent N0.: (45) Date of Patent: Oct. 9, 2012 (54) QUOTA-BASED ARCHIVING (75) Inventor: James Edelen, Renton, WA (U S) (73) Assignee: Microsoft Corporation,
(12> Ulllted States Patent (10) Patent N0.: US 6,591,288 B1 Edwards et al. (45) Date of Patent: Jul. 8, 2003
 ' ' US006591288B1 (12> Ulllted States Patent (10) Patent N0.: Edwards et al. (45) Date of Patent: Jul. 8, 2003 (54) DATA NETWORK ACCELERATED ACCESS EP 0837584 4/1998..... H04L/29/06 SYSTEM W0 WO 96/34340
' ' US006591288B1 (12> Ulllted States Patent (10) Patent N0.: Edwards et al. (45) Date of Patent: Jul. 8, 2003 (54) DATA NETWORK ACCELERATED ACCESS EP 0837584 4/1998..... H04L/29/06 SYSTEM W0 WO 96/34340
US 20090157756Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2009/0157756 A1 Sanvido (43) Pub. Date: Jun.
 US 20090157756Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2009/0157756 A1 Sanvido (43) Pub. Date: Jun. 18, 2009 (54) FILE SYSTEM FOR STORING FILES IN Publication Classi?cation
US 20090157756Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2009/0157756 A1 Sanvido (43) Pub. Date: Jun. 18, 2009 (54) FILE SYSTEM FOR STORING FILES IN Publication Classi?cation
\ \ \ connection connection connection interface interface interface
 US 20140122910A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 20140122910 A1 Chiu et al. (43) Pub. Date: May 1, 2014 (54) RACK SERVER SYSTEM AND OPERATION Publication Classi?cation
US 20140122910A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 20140122910 A1 Chiu et al. (43) Pub. Date: May 1, 2014 (54) RACK SERVER SYSTEM AND OPERATION Publication Classi?cation
222252 211222 1111;111:131... ~~~~~~~~~~~~~~~~~~~ 2221522 [73] Assigneez Rockwell Semiconductor Systems 5,754,639 5/1998 Flockhart et al...
![222252 211222 1111;111:131... ~~~~~~~~~~~~~~~~~~~ 2221522 [73] Assigneez Rockwell Semiconductor Systems 5,754,639 5/1998 Flockhart et al... 222252 211222 1111;111:131... ~~~~~~~~~~~~~~~~~~~ 2221522 [73] Assigneez Rockwell Semiconductor Systems 5,754,639 5/1998 Flockhart et al...](/thumbs/31/14952948.jpg) I I US0059012A Ulllted States Patent [19] [11] Patent Number: Dez0nn0 [] Date of Patent: * May 4, 1999 [54] APPARATUS AND METHOD FOR 5,526,416 6/1996 DeZonno et al...... 379/266 IDENTIFYING RECORDS ()1?
I I US0059012A Ulllted States Patent [19] [11] Patent Number: Dez0nn0 [] Date of Patent: * May 4, 1999 [54] APPARATUS AND METHOD FOR 5,526,416 6/1996 DeZonno et al...... 379/266 IDENTIFYING RECORDS ()1?
US 20120222106Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0222106 A1 Kuehl (43) Pub. Date: Aug.
 US 20120222106Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0222106 A1 Kuehl (43) Pub. Date: (54) AUTOMATED HYBRID CONNECTIONS (52) US. Cl...... 726/11 BETWEEN MULTIPLE
US 20120222106Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0222106 A1 Kuehl (43) Pub. Date: (54) AUTOMATED HYBRID CONNECTIONS (52) US. Cl...... 726/11 BETWEEN MULTIPLE
US 20130007621A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0007621 A1 Warren (43) Pub. Date: Jan.
 US 20130007621A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0007621 A1 Warren (43) Pub. Date: Jan. 3, 2013 (54) (76) (21) (22) (51) (52) SYSTEM FOR LEARNING NAMES OF
US 20130007621A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0007621 A1 Warren (43) Pub. Date: Jan. 3, 2013 (54) (76) (21) (22) (51) (52) SYSTEM FOR LEARNING NAMES OF
Ulllted States Patent [19] [11] Patent Number: 5,943,406
![Ulllted States Patent [19] [11] Patent Number: 5,943,406 Ulllted States Patent [19] [11] Patent Number: 5,943,406](/thumbs/30/14188909.jpg) US005943406A Ulllted States Patent [19] [11] Patent Number: 5,943,406 Leta et al. [45] Date of Patent: Aug. 24, 1999 [54] TELEPHONE CALL TRACKING AND 4,813,065 3/1989 Segala..... 379/112 BILLING SYSTEM
US005943406A Ulllted States Patent [19] [11] Patent Number: 5,943,406 Leta et al. [45] Date of Patent: Aug. 24, 1999 [54] TELEPHONE CALL TRACKING AND 4,813,065 3/1989 Segala..... 379/112 BILLING SYSTEM
software, and perform automatic dialing according to the /*~102
 US 20140105199A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0105199 A1 Tian (43) Pub. Date: (54) METHOD AND APPARATUS FOR AUTOMATIC DIALING ACCESS POINTS (71) Applicant:
US 20140105199A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0105199 A1 Tian (43) Pub. Date: (54) METHOD AND APPARATUS FOR AUTOMATIC DIALING ACCESS POINTS (71) Applicant:
(12) United States Patent (16) Patent N6.= US 6,198,814 B1 Gill (45) Date of Patent: Mar. 6, 2001
 US006198814B1 (12) United States Patent (16) Patent N6.= Gill (45) Date of Patent: Mar. 6, 2001 (54) SYSTEM AND METHOD FOR ENTERING 5,621,790 * 4/1997 Grossman 6161...... 379/266 CALL OUTCOME RECORDS IN
US006198814B1 (12) United States Patent (16) Patent N6.= Gill (45) Date of Patent: Mar. 6, 2001 (54) SYSTEM AND METHOD FOR ENTERING 5,621,790 * 4/1997 Grossman 6161...... 379/266 CALL OUTCOME RECORDS IN
US 201203 03424Al (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2012/0303424 A1 Lundstrom (43) Pub. Date: NOV.
 US 201203 03424Al (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2012/0303424 A1 Lundstrom (43) Pub. Date: NOV. 29, 2012 (54) METHOD AND SOFTWARE FOR Publication Classi?cation
US 201203 03424Al (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2012/0303424 A1 Lundstrom (43) Pub. Date: NOV. 29, 2012 (54) METHOD AND SOFTWARE FOR Publication Classi?cation
Patent Application Publication Sep. 30, 2004 Sheet 1 0f 2. Hierarchical Query. Contact Ow FIG. 1
 US 20040193595A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0193595 A1 Kaminsky et al. (43) Pub. Date: Sep. 30, 2004 (54) NEAREST KNOWN PERSON DIRECTORY FUNCTION (75)
US 20040193595A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0193595 A1 Kaminsky et al. (43) Pub. Date: Sep. 30, 2004 (54) NEAREST KNOWN PERSON DIRECTORY FUNCTION (75)
llllllllllllllillllllllllllllllllllllllllllllllllllllllllllllllllllllllllll
 llllllllllllllillllllllllllllllllllllllllllllllllllllllllllllllllllllllllll USOO5535162A United States Patent [19] [11] Patent Number: 5,535,162 Uenoyama [45] Date of Patent: Jul. 9, 1996 [54] ELECTRICALLY
llllllllllllllillllllllllllllllllllllllllllllllllllllllllllllllllllllllllll USOO5535162A United States Patent [19] [11] Patent Number: 5,535,162 Uenoyama [45] Date of Patent: Jul. 9, 1996 [54] ELECTRICALLY
(12) United States Patent (10) Patent No.: US 8,253,226 B2 Oguri (45) Date of Patent: Aug. 28, 2012
 US008253226B2 (12) United States Patent (10) Patent No.: US 8,253,226 B2 Oguri (45) Date of Patent: Aug. 28, 2012 (54) ELECTRONIC PARTS, AND METHOD FOR (56) References Cited ARRANGING SHIELDING CASE AND
US008253226B2 (12) United States Patent (10) Patent No.: US 8,253,226 B2 Oguri (45) Date of Patent: Aug. 28, 2012 (54) ELECTRONIC PARTS, AND METHOD FOR (56) References Cited ARRANGING SHIELDING CASE AND
US 20120215907A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0215907 A1 Chung (43) Pub. Date: Aug.
 US 20120215907A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0215907 A1 Chung (43) Pub. Date: (54) SYSTEMS AND METHODS FOR (52) US. Cl...... 709/224 SELF-ADJUSTING LOGGING
US 20120215907A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0215907 A1 Chung (43) Pub. Date: (54) SYSTEMS AND METHODS FOR (52) US. Cl...... 709/224 SELF-ADJUSTING LOGGING
(12) Ulllted States Patent (10) Patent N0.: US 8,028,070 B2 Boyd et al. (45) Date of Patent: Sep. 27, 2011
 US008028070B2 (12) Ulllted States Patent (10) Patent N0.: Boyd et al. (45) Date of Patent: Sep. 27, 2011 (54) SYNCHRONIZING TASKS BETWEEN 2002/0065926 A1 * 5/2002 Hackney et al...... 709/231 SERVERS 2004/0221323
US008028070B2 (12) Ulllted States Patent (10) Patent N0.: Boyd et al. (45) Date of Patent: Sep. 27, 2011 (54) SYNCHRONIZING TASKS BETWEEN 2002/0065926 A1 * 5/2002 Hackney et al...... 709/231 SERVERS 2004/0221323
(30) Foreign Application Priority Data
 US 20040015727A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0015727 A1 Lahti et al. (43) Pub. Date: Jan. 22, 2004 (54) SYNCHRONIZATION METHOD (76) Inventors: Jerry Lahti,
US 20040015727A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0015727 A1 Lahti et al. (43) Pub. Date: Jan. 22, 2004 (54) SYNCHRONIZATION METHOD (76) Inventors: Jerry Lahti,
US 20020072350A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0072350 A1 Fukuzato (43) Pub. Date: Jun.
 US 20020072350A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 20020072350 A1 Fukuzato (43) Pub. Date: Jun. 13, 2002 (54) BACKUP METHOD OF APPLICATIONS OF PORTABLE CELLULAR PHONE
US 20020072350A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 20020072350 A1 Fukuzato (43) Pub. Date: Jun. 13, 2002 (54) BACKUP METHOD OF APPLICATIONS OF PORTABLE CELLULAR PHONE
(12) United States Patent (16) Patent N6.= US 6,611,861 B1 Schairer et al. (45) Date of Patent: Aug. 26, 2003
 US006611861B1 (12) United States Patent (16) Patent N6.= Schairer et al. () Date of Patent: Aug. 26, 2003 (54) INTERNET HOSTING AND ACCESS SYSTEM Primary Examiner AyaZ Sheikh AND METHOD Assistant Examiner
US006611861B1 (12) United States Patent (16) Patent N6.= Schairer et al. () Date of Patent: Aug. 26, 2003 (54) INTERNET HOSTING AND ACCESS SYSTEM Primary Examiner AyaZ Sheikh AND METHOD Assistant Examiner
US 20140046812A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0046812 A1 FAN et al. (43) Pub. Date: Feb.
 US 20140046812A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0046812 A1 FAN et al. (43) Pub. Date: (54) EXPENSE REPORTS FOR PAYMENTS MADE (52) US. Cl. WITH A MOBILE DEVICE
US 20140046812A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0046812 A1 FAN et al. (43) Pub. Date: (54) EXPENSE REPORTS FOR PAYMENTS MADE (52) US. Cl. WITH A MOBILE DEVICE
United States Patent [191
 United States Patent [191 Fancy [54] REDUNDANT SIGNAL CIRCUIT [75] Inventor: Thomas A. Fancy, Westminster, Mass. [73] Assignee: General Electric Company, Schenectady, NY. [211 Appl. No.: 854,973 [22] Filed:
United States Patent [191 Fancy [54] REDUNDANT SIGNAL CIRCUIT [75] Inventor: Thomas A. Fancy, Westminster, Mass. [73] Assignee: General Electric Company, Schenectady, NY. [211 Appl. No.: 854,973 [22] Filed:
US 20020116467A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0116467 A1 Boyer et al. (43) Pub. Date: Aug.
 US 20020116467A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0116467 A1 Boyer et al. (43) Pub. Date: Aug. 22, 2002 (54) METHOD AND APPARATUS FOR Publication Classi?cation
US 20020116467A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0116467 A1 Boyer et al. (43) Pub. Date: Aug. 22, 2002 (54) METHOD AND APPARATUS FOR Publication Classi?cation
/ \33 40 \ / \\ \ \ M / 32. 28f 1. (19) United States (12) Patent Application Publication Lawser et al. NETWORK \ 36. SERVlCE 'NTERNET SERVICE
 (19) United States (12) Patent Application Publication Lawser et al. US 20130336314A1 (10) Pub. N0.: US 2013/0336314 A1 (43) Pub. Date: Dec. 19, 2013 (54) (71) (72) (73) (21) (22) (63) METHOD FOR COMPLETING
(19) United States (12) Patent Application Publication Lawser et al. US 20130336314A1 (10) Pub. N0.: US 2013/0336314 A1 (43) Pub. Date: Dec. 19, 2013 (54) (71) (72) (73) (21) (22) (63) METHOD FOR COMPLETING
US 20090055802A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2009/0055802 A1 CROSBY (43) Pub. Date: Feb.
 US 20090055802A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2009/0055802 A1 CROSBY (43) Pub. Date: (54) SELECTIVE MONITORING OF SOFTWARE Publication Classi?cation APPLICATIONS
US 20090055802A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2009/0055802 A1 CROSBY (43) Pub. Date: (54) SELECTIVE MONITORING OF SOFTWARE Publication Classi?cation APPLICATIONS
(54) RETARGETING RELATED TECHNIQUES (52) US. Cl... 705/1453 AND OFFERINGS. (75) Inventors: Ayrnan Farahat, San Francisco, (57) ABSTRACT
 US 20120271714Al (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2012/0271714 A1 Farahat et a]. (43) Pub. Date: Oct. 25, 2012 (54) RETARGETING RELATED TECHNIQUES (52) US. Cl......
US 20120271714Al (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2012/0271714 A1 Farahat et a]. (43) Pub. Date: Oct. 25, 2012 (54) RETARGETING RELATED TECHNIQUES (52) US. Cl......
US 20020141557A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0141557 A1 STRANDBERG (43) Pub. Date: Oct.
 ---- US 20020141557A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0141557 A1 STRANDBERG (43) Pub. Date: (54) SYSTEM AND METHOD FOR PROVIDING AN AUTOMATIC TELEPHONE CALL
---- US 20020141557A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0141557 A1 STRANDBERG (43) Pub. Date: (54) SYSTEM AND METHOD FOR PROVIDING AN AUTOMATIC TELEPHONE CALL
Telephone Dressing Systems - Advantages and Disadvantages
 I US 20030185352A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2003/0185352 A1 Savage et al. (43) Pub. Date: (54) AUTOMATED MESSAGE BROADCAST SYSTEM WITH DUAL MESSAGE SOURCES
I US 20030185352A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2003/0185352 A1 Savage et al. (43) Pub. Date: (54) AUTOMATED MESSAGE BROADCAST SYSTEM WITH DUAL MESSAGE SOURCES
MAIN COMPUTER MONlTOR. INPUT/ OUTPUT ClRCUlT. 4,748,566 May 31, 1988. United States Patent [191. [11] Patent Number: [45] Date of Patent:
![MAIN COMPUTER MONlTOR. INPUT/ OUTPUT ClRCUlT. 4,748,566 May 31, 1988. United States Patent [191. [11] Patent Number: [45] Date of Patent: MAIN COMPUTER MONlTOR. INPUT/ OUTPUT ClRCUlT. 4,748,566 May 31, 1988. United States Patent [191. [11] Patent Number: [45] Date of Patent:](/thumbs/29/13384343.jpg) United States Patent [191 Sasaki et al. [11] Patent Number: [45] Date of Patent: May 31, 1988 [54] ENGINE CONTROL APPARATUS [75] Inventors: Shoji Sasaki; Kenji Tabuchi, both of Katsuta, Japan [73] Assignee:
United States Patent [191 Sasaki et al. [11] Patent Number: [45] Date of Patent: May 31, 1988 [54] ENGINE CONTROL APPARATUS [75] Inventors: Shoji Sasaki; Kenji Tabuchi, both of Katsuta, Japan [73] Assignee:
(54) LOTTERY METHOD Publication Classi?cation
 US 20130231987A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0231987 A1 Veverka et al. (43) Pub. Date: Sep. 5, 2013 (54) LOTTERY METHOD Publication Classi?cation (71)
US 20130231987A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0231987 A1 Veverka et al. (43) Pub. Date: Sep. 5, 2013 (54) LOTTERY METHOD Publication Classi?cation (71)
(12) Patent Application Publication (10) Pub. No.: US 2003/0035525 A1 Wu et al. (43) Pub. Date: Feb. 20, 2003
 (19) United States US 20030035525A1 (12) Patent Application Publication (10) Pub. No.: US 2003/0035525 A1 Wu et al. (43) Pub. Date: (54) (76) (21) (22) SYSTEM AND METHOD FOR DISTINGUISHING TELEPHONE NUMBER
(19) United States US 20030035525A1 (12) Patent Application Publication (10) Pub. No.: US 2003/0035525 A1 Wu et al. (43) Pub. Date: (54) (76) (21) (22) SYSTEM AND METHOD FOR DISTINGUISHING TELEPHONE NUMBER
NETWORK BOUNDARY PRIVATE NETWORK PUBLIC _1 NETWORK
 US 20050177647A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0177647 A1 Anantha et al. (43) Pub. Date: (54) (75) (73) (21) (22) (51) MOBILE IP EXTENSION TO SUPPORT PRIVATE
US 20050177647A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0177647 A1 Anantha et al. (43) Pub. Date: (54) (75) (73) (21) (22) (51) MOBILE IP EXTENSION TO SUPPORT PRIVATE
Back up information data by blocks, and generate backup data of each block
 US 20140046903A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0046903 A1 Ylll (43) Pub. Date: (54) DATA BACKUP AND RECOVERY METHOD Publication Classi?cation FOR MOBILE
US 20140046903A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0046903 A1 Ylll (43) Pub. Date: (54) DATA BACKUP AND RECOVERY METHOD Publication Classi?cation FOR MOBILE
Lookup CNAM / other database for calllng
 (19) United States US 20140003589Al (12) Patent Application Publication (10) Pub. No.: US 2014/0003589 A1 Martino et al. (43) Pub. Date: Jan. 2, 2014 (54) (71) (72) (73) (21) (22) (63) PROVIDING AUDIO
(19) United States US 20140003589Al (12) Patent Application Publication (10) Pub. No.: US 2014/0003589 A1 Martino et al. (43) Pub. Date: Jan. 2, 2014 (54) (71) (72) (73) (21) (22) (63) PROVIDING AUDIO
US 20130254326Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0254326 A1 Weng et al. (43) Pub. Date: Sep.
 1 l US 20130254326Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0254326 A1 Weng et al. (43) Pub. Date: Sep. 26, 2013 (54) ELECTRONIC DEVICE, CLOUD STORAGE Publication
1 l US 20130254326Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0254326 A1 Weng et al. (43) Pub. Date: Sep. 26, 2013 (54) ELECTRONIC DEVICE, CLOUD STORAGE Publication
(12) United States Patent (10) Patent N0.: US 7,068,424 B1 Jennings et al. (45) Date of Patent: Jun. 27, 2006
 US007068424B1 (12) United States Patent (10) Patent N0.: US 7,068,424 B1 Jennings et al. (45) Date of Patent: Jun. 27, 2006 (54) MULTIPLE PULSE GENERATION 6,141,127 A * 10/2000 Boivin et a1...... 398/92
US007068424B1 (12) United States Patent (10) Patent N0.: US 7,068,424 B1 Jennings et al. (45) Date of Patent: Jun. 27, 2006 (54) MULTIPLE PULSE GENERATION 6,141,127 A * 10/2000 Boivin et a1...... 398/92
(12) United States Patent Wen et a].
![(12) United States Patent Wen et a]. (12) United States Patent Wen et a].](/thumbs/27/10120921.jpg) ' US008719918B2 (12) United States Patent Wen et a]. (10) Patent N0.: () Date of Patent: May 6, 14 (54) (75) (73) (21) (22) (86) (87) () () (51) (52) (58) METHOD AND DEVICE FOR DISTRIBUTED SECURITY CONTROL
' US008719918B2 (12) United States Patent Wen et a]. (10) Patent N0.: () Date of Patent: May 6, 14 (54) (75) (73) (21) (22) (86) (87) () () (51) (52) (58) METHOD AND DEVICE FOR DISTRIBUTED SECURITY CONTROL
(54) Applicant: (71) (72) Assignee: (73) (21) (22) (60)
 US 20140373140A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0373140 A1 Waters, JR. et al. (43) Pub. Date: Dec. 18, 2014 (54) (71) (72) (73) (21) (22) (60) DATA CENTER
US 20140373140A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0373140 A1 Waters, JR. et al. (43) Pub. Date: Dec. 18, 2014 (54) (71) (72) (73) (21) (22) (60) DATA CENTER
POTENTIAL. SC DA Il'JA N INTERFACE m. (21) Appl. No.: 11/037,604
 US 20050125439A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0125439 A1 Nourbakhsh et al. (43) Pub. Date: Jun. 9, 2005 (54) METHOD AND APPARATUS FOR MULTI-CONTACT SCHEDULING
US 20050125439A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0125439 A1 Nourbakhsh et al. (43) Pub. Date: Jun. 9, 2005 (54) METHOD AND APPARATUS FOR MULTI-CONTACT SCHEDULING
(43) Pub. Date: Feb. 16, 2012
 US 20120041897A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0041897 A1 Teague et al. (43) Pub. Date: (54) (75) (73) (21) (22) (63) MARKET INDICATOR PROCESS AND METHOD
US 20120041897A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0041897 A1 Teague et al. (43) Pub. Date: (54) (75) (73) (21) (22) (63) MARKET INDICATOR PROCESS AND METHOD
US 20050027827A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0027827 A1 Owhadi et al. (43) Pub. Date: Feb.
 US 20050027827A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0027827 A1 Owhadi et al. (43) Pub. Date: Feb. 3, 2005 (54) SYSTEM FOR PROVIDING SUPPORT FOR AN ELECTRONIC
US 20050027827A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0027827 A1 Owhadi et al. (43) Pub. Date: Feb. 3, 2005 (54) SYSTEM FOR PROVIDING SUPPORT FOR AN ELECTRONIC
(IP Connection) Miami (54) (76) (21) (22) (51) (52) Application
 US 20070016777Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0016777 A1 Henderson et al. (43) Pub. Date: Jan. 18, 2007 (54) (76) (21) (22) (51) (52) METHOD OF AND SYSTEM
US 20070016777Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0016777 A1 Henderson et al. (43) Pub. Date: Jan. 18, 2007 (54) (76) (21) (22) (51) (52) METHOD OF AND SYSTEM
(71) Applicant: SPEAKWRITE, LLC,Austin, TX (US)
 US 20130304465Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0304465 A1 Henry et al. (43) Pub. Date: NOV. 14, 2013 (54) METHOD AND SYSTEM FOR AUDIO-VIDEO (52) US. Cl.
US 20130304465Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0304465 A1 Henry et al. (43) Pub. Date: NOV. 14, 2013 (54) METHOD AND SYSTEM FOR AUDIO-VIDEO (52) US. Cl.
US 20130325834A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2013/0325834 A1 Simburg (43) Pub. Date: Dec.
 US 20130325834A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2013/0325834 A1 Simburg (43) Pub. Date: Dec. 5, 2013 (54) LINK ALLOCATION FOR SEARCH ENGINE (52) US. Cl. OPTIMIZATION
US 20130325834A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2013/0325834 A1 Simburg (43) Pub. Date: Dec. 5, 2013 (54) LINK ALLOCATION FOR SEARCH ENGINE (52) US. Cl. OPTIMIZATION
5,793,972 Aug. 11, 1998
 United States Patent [19] Shane USOO5793972A [11] Patent Number: [45] Date of Patent: 5,793,972 Aug. 11, 1998 [54] SYSTEM AND METHOD PROVIDING AN INTERACTIVE RESPONSE TO DIRECT MAIL BY CREATING PERSONALIZED
United States Patent [19] Shane USOO5793972A [11] Patent Number: [45] Date of Patent: 5,793,972 Aug. 11, 1998 [54] SYSTEM AND METHOD PROVIDING AN INTERACTIVE RESPONSE TO DIRECT MAIL BY CREATING PERSONALIZED
(12) United States Patent Petralia
 US007676410B2 (12) United States Patent Petralia (10) Patent N0.: (45) Date of Patent: Mar. 9, 2010 (54) (75) (73) (*) (21) (22) (65) (51) (52) (58) COMBINED DEBT CONSOLIDATION AND SETTLEMENT PROGRAM Inventor:
US007676410B2 (12) United States Patent Petralia (10) Patent N0.: (45) Date of Patent: Mar. 9, 2010 (54) (75) (73) (*) (21) (22) (65) (51) (52) (58) COMBINED DEBT CONSOLIDATION AND SETTLEMENT PROGRAM Inventor:
(12) United States Patent Munshi et al.
 US008806190B1 (12) United States Patent Munshi et al. (10) Patent N0.: () Date of Patent: Aug. 12, 14 (54) METHOD OF TRANSMISSION OF ENCRYPTED DOCUMENTS FROM AN EMAIL APPLICATION (76) Inventors: Amaani
US008806190B1 (12) United States Patent Munshi et al. (10) Patent N0.: () Date of Patent: Aug. 12, 14 (54) METHOD OF TRANSMISSION OF ENCRYPTED DOCUMENTS FROM AN EMAIL APPLICATION (76) Inventors: Amaani
US 20030108052A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2003/0108052 A1 Inoue et al. (43) Pub. Date: Jun.
 US 20030108052A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2003/0108052 A1 Inoue et al. (43) Pub. Date: Jun. 12, 2003 (54) SERVER LOAD SHARING SYSTEM (76) Inventors: Rumiko
US 20030108052A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2003/0108052 A1 Inoue et al. (43) Pub. Date: Jun. 12, 2003 (54) SERVER LOAD SHARING SYSTEM (76) Inventors: Rumiko
GATEWAY ' 8 8 8 o o o
 US 20130102274A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0102274 A1 Lauwaert (43) Pub. Date: Apr. 25, 2013 (54) SYSTEMS AND METHODS FOR MOBILE Publication Classi?cation
US 20130102274A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0102274 A1 Lauwaert (43) Pub. Date: Apr. 25, 2013 (54) SYSTEMS AND METHODS FOR MOBILE Publication Classi?cation
(51) Int Cl.: H04L 29/06 (2006.01) H04L 12/24 (2006.01)
 (19) (12) EUROPEAN PATENT SPECIFICATION (11) EP 1 231 74 B1 (4) Date of publication and mention of the grant of the patent: 16.03.11 Bulletin 11/11 (1) Int Cl.: H04L 29/06 (06.01) H04L 12/24 (06.01) (21)
(19) (12) EUROPEAN PATENT SPECIFICATION (11) EP 1 231 74 B1 (4) Date of publication and mention of the grant of the patent: 16.03.11 Bulletin 11/11 (1) Int Cl.: H04L 29/06 (06.01) H04L 12/24 (06.01) (21)
Srimuang (43) Pub. Date: Mar. 27, 2003
 US 20030061087A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2003/0061087 A1 Srimuang (43) Pub. Date: Mar. 27, 2003 (54) CALENDAR SCHEDULING OF MULTIPLE PERSONS RESOURCES AND
US 20030061087A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2003/0061087 A1 Srimuang (43) Pub. Date: Mar. 27, 2003 (54) CALENDAR SCHEDULING OF MULTIPLE PERSONS RESOURCES AND
(12) United States Patent Armenio et a].
![(12) United States Patent Armenio et a]. (12) United States Patent Armenio et a].](/thumbs/40/20558097.jpg) US008425210B2 (12) United States Patent Armenio et a]. (10) Patent N0.: (45) Date of Patent: Apr. 23, 2013 (54) TWO-SETTINGVARIABLE-ECCENTRICITY VANE PUMP (75) Inventors: Giacomo Armenio, Livorno (IT);
US008425210B2 (12) United States Patent Armenio et a]. (10) Patent N0.: (45) Date of Patent: Apr. 23, 2013 (54) TWO-SETTINGVARIABLE-ECCENTRICITY VANE PUMP (75) Inventors: Giacomo Armenio, Livorno (IT);
US 20070139188A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0139188 A1 Ollis et al. HOME PROCESSOR /\ J\ NETWORK
 US 20070139188A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0139188 A1 Ollis et al. (43) Pub. Date: Jun. 21, 2007 (54) (75) (73) (21) (22) METHOD AND APPARATUS FOR COMMUNICATING
US 20070139188A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0139188 A1 Ollis et al. (43) Pub. Date: Jun. 21, 2007 (54) (75) (73) (21) (22) METHOD AND APPARATUS FOR COMMUNICATING
1 JOURNAL SYSTEM 16 / 10w T 12 8\ EMAIL ARCHIVE STORAGE ARCHIVE. STORAGE l 6 USER METADATA \ MA'LBOX T : DATABASE ARCHIVING (54) (75) Assignee: (73)
 US 20120259817Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0259817 A1 Baessler et al. (43) Pub. Date: (54) (75) (73) (21) (22) (63) UTLZNG METADATA TO OPTMZE EFFCENCY
US 20120259817Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0259817 A1 Baessler et al. (43) Pub. Date: (54) (75) (73) (21) (22) (63) UTLZNG METADATA TO OPTMZE EFFCENCY
(12) (10) Patent N0.: US 7,069,466 B2 Trimmer et a]. (45) Date of Patent: Jun. 27, 2006
![(12) (10) Patent N0.: US 7,069,466 B2 Trimmer et a]. (45) Date of Patent: Jun. 27, 2006 (12) (10) Patent N0.: US 7,069,466 B2 Trimmer et a]. (45) Date of Patent: Jun. 27, 2006](/thumbs/33/15766535.jpg) United States Patent US007069466B2 (12) (10) Patent N0.: US 7,069,466 B2 Trimmer et a]. (45) Date of Patent: Jun. 27, 2006 (54) METHOD AND SYSTEM FOR COPYING 5,963,971 A 10/1999 Fosler et a1. BACKUP DATA
United States Patent US007069466B2 (12) (10) Patent N0.: US 7,069,466 B2 Trimmer et a]. (45) Date of Patent: Jun. 27, 2006 (54) METHOD AND SYSTEM FOR COPYING 5,963,971 A 10/1999 Fosler et a1. BACKUP DATA
US 20060209260A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2006/0209260 A1 Clegg (43) Pub. Date: Sep.
 US 20060209260A1 (19) United States (12) Patent Application Publication (10) Pub. No.: Clegg (43) Pub. Date: Sep. 21, 2006 (54) SCROLLING PICTURE CHANGER (52) US. Cl...... 352/98 (76) Inventor: Timothy
US 20060209260A1 (19) United States (12) Patent Application Publication (10) Pub. No.: Clegg (43) Pub. Date: Sep. 21, 2006 (54) SCROLLING PICTURE CHANGER (52) US. Cl...... 352/98 (76) Inventor: Timothy
(54) METHOD FOR AUTOMATED HANDLING OF Publication Classi?cation OUTBOUND CONTACTS REQUIRING ASSURED CONNECTION TO A LIVE AGENT (51) Int- Cl
 US 20140044256A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0044256 A1 Zgardovski et al. (43) Pub. Date: (54) METHOD FOR AUTOMATED HANDLING OF Publication Classi?cation
US 20140044256A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0044256 A1 Zgardovski et al. (43) Pub. Date: (54) METHOD FOR AUTOMATED HANDLING OF Publication Classi?cation
(12) United States Patent (10) Patent N0.: US 8,282,471 B1 Korner (45) Date of Patent: Oct. 9, 2012
 US008282471B1 (12) United States Patent (10) Patent N0.: US 8,282,471 B1 Korner (45) Date of Patent: Oct. 9, 2012 (54) COMPUTER-IMPLEMENTED SPORTS 2011/0003634 A1* 1/2011 Manteris..... 463/25 WAGERING
US008282471B1 (12) United States Patent (10) Patent N0.: US 8,282,471 B1 Korner (45) Date of Patent: Oct. 9, 2012 (54) COMPUTER-IMPLEMENTED SPORTS 2011/0003634 A1* 1/2011 Manteris..... 463/25 WAGERING
(12) United States Patent
 US008914855B2 (12) United States Patent Whitmyer, Jr. (10) Patent N0.: (45) Date of Patent: US 8,914,855 B2 Dec. 16, 2014 (54) PORTABLE PASSWORD KEEPER WITH INTERNET STORAGE AND RESTORE (75) Inventor:
US008914855B2 (12) United States Patent Whitmyer, Jr. (10) Patent N0.: (45) Date of Patent: US 8,914,855 B2 Dec. 16, 2014 (54) PORTABLE PASSWORD KEEPER WITH INTERNET STORAGE AND RESTORE (75) Inventor:
US 20050015455A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2005/0015455 A1 Liu (43) Pub. Date: Jan.
 US 20050015455A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2005/0015455 A1 Liu (43) Pub. Date: Jan. 20, 2005 (54) SPAM PROCESSING SYSTEM AND METHODS INCLUDING SHARED INFORMATION
US 20050015455A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2005/0015455 A1 Liu (43) Pub. Date: Jan. 20, 2005 (54) SPAM PROCESSING SYSTEM AND METHODS INCLUDING SHARED INFORMATION
US 20020174380A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2002/0174380 A1. Mannarsamy (43) Pub. Date: NOV.
 US 20020174380A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2002/0174380 A1 Mannarsamy (43) Pub. Date: NOV. 21, 2002 (54) HELPDESK SYSTEM AND METHOD (52) US. Cl...... 714/25
US 20020174380A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2002/0174380 A1 Mannarsamy (43) Pub. Date: NOV. 21, 2002 (54) HELPDESK SYSTEM AND METHOD (52) US. Cl...... 714/25
I SEARCH DATABASE l/ VISIT WEBSITE k ( UPDATE RECORDS Y (54) (75) (73) (21) (22) (63) (60) (US); Gary Stephen Shuster, Oakland, SELECT SUB-DOMAIN NAME
 US 20060293973Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2006/0293973 A1 Shuster et al. (43) Pub. Date: Dec. 28, 2006 (54) (75) (73) (21) (22) (63) (60) METHOD AND APPARATUS
US 20060293973Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2006/0293973 A1 Shuster et al. (43) Pub. Date: Dec. 28, 2006 (54) (75) (73) (21) (22) (63) (60) METHOD AND APPARATUS
US 20070019798Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0019798 A1 Voight et al. SUBSCRIBER DATABASE.
 US 20070019798Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0019798 A1 Voight et al. (43) Pub. Date: Jan. 25, 2007 (54) METHOD AND APPARATUS FOR PROVIDING CUSTOMIZED
US 20070019798Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0019798 A1 Voight et al. (43) Pub. Date: Jan. 25, 2007 (54) METHOD AND APPARATUS FOR PROVIDING CUSTOMIZED
(54) METHODS AND SYSTEMS FOR FINDING Publication Classi?cation CONNECTIONS AMONG SUBSCRIBERS TO AN EMAIL CAMPAIGN (51) Int- Cl
 US 201403 79420A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0379420 A1 Chestnut et al. (43) Pub. Date: Dec. 25, 2014 (54) METHODS AND SYSTEMS FOR FINDING Publication
US 201403 79420A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0379420 A1 Chestnut et al. (43) Pub. Date: Dec. 25, 2014 (54) METHODS AND SYSTEMS FOR FINDING Publication
US 201403 80094A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0380094 A1 Kota et al. (43) Pub. Date: Dec.
 US 201403 80094A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0380094 A1 Kota et al. (43) Pub. Date: (54) AVOIDING RESTART ON ERROR IN DATA (52) US. Cl. INTEGRATION CPC.....
US 201403 80094A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0380094 A1 Kota et al. (43) Pub. Date: (54) AVOIDING RESTART ON ERROR IN DATA (52) US. Cl. INTEGRATION CPC.....
Provisional application No. 61/082,685,?led on Jul. 22, 2008. the non-member private key are not generated. 116 Registered Log Archive
 US 20100023757Al (19) United States (12) Patent Application Publication (10) Pub. N0.2 US 2010/0023757 A1 Nguyen-Huu et al. (43) Pub. Date: (54) (75) (73) (21) (22) (60) METHODS AND SYSTEMS FOR SENDING
US 20100023757Al (19) United States (12) Patent Application Publication (10) Pub. N0.2 US 2010/0023757 A1 Nguyen-Huu et al. (43) Pub. Date: (54) (75) (73) (21) (22) (60) METHODS AND SYSTEMS FOR SENDING
(12) (10) Patent N0.: US 6,614,314 B2 d Haene et al. 45 Date 0f Patent: Se. 2 2003 (54) NON-LINEAR PHASE DETECTOR FOREIGN PATENT DOCUMENTS
 United States Patent US006614314B2 (12) (10) Patent N0.: US 6,614,314 B2 d Haene et al. 45 Date 0f Patent: Se. 2 2003 a (54) NON-LINEAR PHASE DETECTOR FOREIGN PATENT DOCUMENTS (75) Inventors: Wesley Calvin
United States Patent US006614314B2 (12) (10) Patent N0.: US 6,614,314 B2 d Haene et al. 45 Date 0f Patent: Se. 2 2003 a (54) NON-LINEAR PHASE DETECTOR FOREIGN PATENT DOCUMENTS (75) Inventors: Wesley Calvin
NJ (US) (51) Int. Cl. H04L 9/00 (2006.01) Correspondence Address: (52) US. Cl... 380/278; 713/ 150 ALFRED C. ROTH (57) ABSTRACT
 . I. I. I US 20080187140A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2008/0187140 A1 McGillian et al. (43) Pub. Date: Aug. 7, 2008 (54) METHOD AND SYSTEM OF SECURELY Related
. I. I. I US 20080187140A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2008/0187140 A1 McGillian et al. (43) Pub. Date: Aug. 7, 2008 (54) METHOD AND SYSTEM OF SECURELY Related
Vignet (43) Pub. Date: Nov. 24, 2005
 US 20050262425A1 (19) United States (12) Patent Application Publication (10) Pub. No.: Vignet (43) Pub. Date: Nov. 24, 2005 (54) (76) (21) (22) METHOD AND SYSTEM FOR JAVA GANTT/BAR CHART RENDERING Inventor:
US 20050262425A1 (19) United States (12) Patent Application Publication (10) Pub. No.: Vignet (43) Pub. Date: Nov. 24, 2005 (54) (76) (21) (22) METHOD AND SYSTEM FOR JAVA GANTT/BAR CHART RENDERING Inventor:
US 20030110248A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2003/0110248 A1 Ritchc (43) Pub. Date: Jun.
 US 20030110248A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2003/0110248 A1 Ritchc (43) Pub. Date: (54) (76) (21) (22) (51) (52) AUTOMATED SERVICE SUPPORT OF SOFTWARE DISTRIBUTION
US 20030110248A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2003/0110248 A1 Ritchc (43) Pub. Date: (54) (76) (21) (22) (51) (52) AUTOMATED SERVICE SUPPORT OF SOFTWARE DISTRIBUTION
United States Patent [191 [11] Patent Number: 4,895,256
![United States Patent [191 [11] Patent Number: 4,895,256 United States Patent [191 [11] Patent Number: 4,895,256](/thumbs/29/13744178.jpg) I United States Patent [191 [11] Patent Number: 4,895,256 Johnston [45] Date of Patent: Jan. 23, 1990 [54] AIR CONDITIONING SUPPLY CARRIER 3,392,874 7/1968 3,627,122 12/1971 [76] Inventor: James E. Johnston,
I United States Patent [191 [11] Patent Number: 4,895,256 Johnston [45] Date of Patent: Jan. 23, 1990 [54] AIR CONDITIONING SUPPLY CARRIER 3,392,874 7/1968 3,627,122 12/1971 [76] Inventor: James E. Johnston,
USOO5469362A United States Patent [191 [11] Patent Number: 5,469,362. Hunt et al. [45] Date of Patent: Nov. 21, 1995
![USOO5469362A United States Patent [191 [11] Patent Number: 5,469,362. Hunt et al. [45] Date of Patent: Nov. 21, 1995 USOO5469362A United States Patent [191 [11] Patent Number: 5,469,362. Hunt et al. [45] Date of Patent: Nov. 21, 1995](/thumbs/30/14713887.jpg) llllllllllllllllllllllllllllllllllllllllll l llllllllllllllllllllllll USOO5469362A United States Patent [191 [11] Patent Number: 5,469,362 Hunt et al. [45] Date of Patent: Nov. 21, 1995 [54] DISPATCHING
llllllllllllllllllllllllllllllllllllllllll l llllllllllllllllllllllll USOO5469362A United States Patent [191 [11] Patent Number: 5,469,362 Hunt et al. [45] Date of Patent: Nov. 21, 1995 [54] DISPATCHING
USOOS 90761 1A Ulllted States Patent [19] [11 Patent Number: 5 907 611. 9 9 Dezonno et al. [45] Date of Patent: *May 25, 1999
![USOOS 90761 1A Ulllted States Patent [19] [11 Patent Number: 5 907 611. 9 9 Dezonno et al. [45] Date of Patent: *May 25, 1999 USOOS 90761 1A Ulllted States Patent [19] [11 Patent Number: 5 907 611. 9 9 Dezonno et al. [45] Date of Patent: *May 25, 1999](/thumbs/31/15320422.jpg) USOOS 90761 1A Ulllted States Patent [19] [11 Patent Number: 5 907 611 9 9 Dezonno et al. [45] Date of Patent: *May 25, 1999 [54] APPARATUS AND METHOD FOR 5,526,416 6/1996 Dezonno et al...... 379/266 IDENTIFYING
USOOS 90761 1A Ulllted States Patent [19] [11 Patent Number: 5 907 611 9 9 Dezonno et al. [45] Date of Patent: *May 25, 1999 [54] APPARATUS AND METHOD FOR 5,526,416 6/1996 Dezonno et al...... 379/266 IDENTIFYING
United States Patent [19] [11] Patent Number: 5,347,302
![United States Patent [19] [11] Patent Number: 5,347,302 United States Patent [19] [11] Patent Number: 5,347,302](/thumbs/30/14645079.jpg) USO05347302A United States Patent [19] [11] Patent Number: 5,347,302 Simonoff [45] Date of Patent: Sep. 13, 1994, [54] METHOD FOR MICR ENCODING 0F [57] ABSTRACT 8S3 ; An improved method for accurately
USO05347302A United States Patent [19] [11] Patent Number: 5,347,302 Simonoff [45] Date of Patent: Sep. 13, 1994, [54] METHOD FOR MICR ENCODING 0F [57] ABSTRACT 8S3 ; An improved method for accurately
i VlRTUAL SERVER 1 \ VIRTUAL SERVER 2, _ 7
 US 20110225267A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2011/0225267 A1 OHASHI (43) Pub. Date: Sep. 15, 2011 (54) SERVER SYSTEM FOR VIEWING IN-HOUSE INFORMATION, AND METHOD
US 20110225267A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2011/0225267 A1 OHASHI (43) Pub. Date: Sep. 15, 2011 (54) SERVER SYSTEM FOR VIEWING IN-HOUSE INFORMATION, AND METHOD
US 20130138449A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2013/0138449 A1 Pi0t (43) Pub. Date: May 30, 2013
 US 20130138449A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2013/0138449 A1 Pi0t (43) Pub. Date: May 30, 2013 (54) SYSTEM AND METHOD FOR SCHEDULING (52) us. c1. HoME VISITS
US 20130138449A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2013/0138449 A1 Pi0t (43) Pub. Date: May 30, 2013 (54) SYSTEM AND METHOD FOR SCHEDULING (52) us. c1. HoME VISITS
4,670,900 Jun. 2, 1987
 United States Patent [19] Waldman [11] Patent Number: [45] Date of Patent: 4,670,900 Jun. 2, 1987 [54] SINGLE LINE TELEPHONE CALL FORWARDING DEVICE [76] Inventor: Herbert H. Waldman, 1739 52nd St., Brooklyn,
United States Patent [19] Waldman [11] Patent Number: [45] Date of Patent: 4,670,900 Jun. 2, 1987 [54] SINGLE LINE TELEPHONE CALL FORWARDING DEVICE [76] Inventor: Herbert H. Waldman, 1739 52nd St., Brooklyn,
Ulllted States Patent [19] [11] Patent Number: 6,141,545
![Ulllted States Patent [19] [11] Patent Number: 6,141,545 Ulllted States Patent [19] [11] Patent Number: 6,141,545](/thumbs/27/11642488.jpg) US0061445A Ulllted States Patent [19] [11] Patent Number: Begeja et al. [45] Date of Patent: *Oct. 31, 2000 [54] METHOD AND SYSTEM FOR REMOTE 5,440,614 8/1995 Sonberg et a1...... 455/414 CALL FORWARDING
US0061445A Ulllted States Patent [19] [11] Patent Number: Begeja et al. [45] Date of Patent: *Oct. 31, 2000 [54] METHOD AND SYSTEM FOR REMOTE 5,440,614 8/1995 Sonberg et a1...... 455/414 CALL FORWARDING
Using the Barracuda to Filter Your Emails
 Using the Barracuda to Filter Your Emails The following describes how end users interact with the Barracuda to check their quarantined messages, classify messages as spam and not spam, and modify their
Using the Barracuda to Filter Your Emails The following describes how end users interact with the Barracuda to check their quarantined messages, classify messages as spam and not spam, and modify their
US006282278B1 (12) United States Patent. (10) Patent N0.: US 6,282,278 B1 D0ganata et al. (45) Date 0f Patent: Aug. 28, 2001
 US006282278B1 (12) United States Patent (10) Patent N0.: US 6,282,278 B1 D0ganata et al. (45) Date 0f Patent: Aug. 28, 2001 (54) UNIVERSAL CONFERENCE CONTROL 5,758,281 * 5/1998 Emery et a1...... 455/428
US006282278B1 (12) United States Patent (10) Patent N0.: US 6,282,278 B1 D0ganata et al. (45) Date 0f Patent: Aug. 28, 2001 (54) UNIVERSAL CONFERENCE CONTROL 5,758,281 * 5/1998 Emery et a1...... 455/428
Ff'if ~ _ INVISIWALL. Shively (43) Pub. Date: NOV. 28, 2002 . LOCAL ONSITE. (Us) (21) Appl. No.: 09/865,377
 US 20020178378A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0178378 A1 Shively (43) Pub. Date: NOV. 28, 2002 (54) SECURE NTRUSON DETECTON SYSTEM (76) nventor: Geo?'rey
US 20020178378A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0178378 A1 Shively (43) Pub. Date: NOV. 28, 2002 (54) SECURE NTRUSON DETECTON SYSTEM (76) nventor: Geo?'rey
(12) United States Patent (10) Patent N0.: US 8,626,119 B2 Leemet et a]. (45) Date of Patent: *Jan. 7, 2014
![(12) United States Patent (10) Patent N0.: US 8,626,119 B2 Leemet et a]. (45) Date of Patent: *Jan. 7, 2014 (12) United States Patent (10) Patent N0.: US 8,626,119 B2 Leemet et a]. (45) Date of Patent: *Jan. 7, 2014](/thumbs/29/13301505.jpg) US008626119B2 (12) United States Patent (10) Patent N0.: US 8,626,119 B2 Leemet et a]. (45) Date of Patent: *Jan. 7, 2014 (54) SYSTEM AND METHOD FOR MANAGINGA (51) Int. Cl. MOBILE DEVICE H04M 11/00 (2006.01)
US008626119B2 (12) United States Patent (10) Patent N0.: US 8,626,119 B2 Leemet et a]. (45) Date of Patent: *Jan. 7, 2014 (54) SYSTEM AND METHOD FOR MANAGINGA (51) Int. Cl. MOBILE DEVICE H04M 11/00 (2006.01)
(43) Pub. Date: Jan. 24, 2008
 US 20080022336A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2008/0022336 A1 Howcroft et al. (43) Pub. Date: Jan. 24, 2008 (54) SET-TOP BOX NETWORK DIAGNOSTICS (75) (73) (21)
US 20080022336A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2008/0022336 A1 Howcroft et al. (43) Pub. Date: Jan. 24, 2008 (54) SET-TOP BOX NETWORK DIAGNOSTICS (75) (73) (21)
US 20070160058Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0160058 A1 Zhou et al. (43) Pub. Date: Jul.
 US 20070160058Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0160058 A1 Zhou et al. (43) Pub. Date: (54) METHOD AND SYSTEM FOR IMPLEMENTING BACKUP BASED ON SESSION BORDER
US 20070160058Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0160058 A1 Zhou et al. (43) Pub. Date: (54) METHOD AND SYSTEM FOR IMPLEMENTING BACKUP BASED ON SESSION BORDER
Title: Spam Filter Active / Spam Filter Active : CAB Page 1 of 5
 Friday, April 18, 2008 11:24:8 AM Title: Spam Filter Active / Spam Filter Active : CAB Page 1 of 5 Name: Author: Subject: Spam Filter Active CAB Administrator Spam Filter Active Keywords: Category: The
Friday, April 18, 2008 11:24:8 AM Title: Spam Filter Active / Spam Filter Active : CAB Page 1 of 5 Name: Author: Subject: Spam Filter Active CAB Administrator Spam Filter Active Keywords: Category: The
(12) Unlted States Patent (10) Patent N0.2 US 7,428,664 B2 Sirbu (45) Date of Patent: Sep. 23, 2008
 US007428664B2 (12) Unlted States Patent (10) Patent N0.2 Sirbu (45) Date of Patent: Sep. 23, 2008 (54) PROTOCOL REPLAY SYSTEM 5,287,506 A * 2/1994 Whiteside..... 714/39 6,708,292 B1 * 3/2004 Mangasarian..
US007428664B2 (12) Unlted States Patent (10) Patent N0.2 Sirbu (45) Date of Patent: Sep. 23, 2008 (54) PROTOCOL REPLAY SYSTEM 5,287,506 A * 2/1994 Whiteside..... 714/39 6,708,292 B1 * 3/2004 Mangasarian..
How To Make A Programmable Logic Network From A Program To A Program
 Àug.19,19694 c. CHEMLA :TAL ' 3,462,738. _ POLYPHASE PRIORITY DETERMINING SYSTEM Filed May 19, 1966 s sheets-*sheet x l I I I ` ` i i tu t1 t2 t3 t1. t5 te t7 te ts îlo tu t1: ha tu. BY mventors. clauos
Àug.19,19694 c. CHEMLA :TAL ' 3,462,738. _ POLYPHASE PRIORITY DETERMINING SYSTEM Filed May 19, 1966 s sheets-*sheet x l I I I ` ` i i tu t1 t2 t3 t1. t5 te t7 te ts îlo tu t1: ha tu. BY mventors. clauos
Psychic Psychic Psychic Psychic Psychic
 US 20070274495Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0274495 A1 Youd et al. (43) Pub. Date: NOV. 29, 2007 (54) SYSTEMS AND METHODS FOR EXPERT Publication Classi?cation
US 20070274495Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0274495 A1 Youd et al. (43) Pub. Date: NOV. 29, 2007 (54) SYSTEMS AND METHODS FOR EXPERT Publication Classi?cation
US 20120066004A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0066004 A1 Lee (43) Pub. Date: Mar.
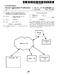 US 212664A1 (19) United States (12) Patent Application Publication (1) Pub. o.: US 212/664 A1 Lee (43) Pub. Date: Mar. 15, 212 (54) (76) (21) (22) (6) METHOD AD SYSTEM FOR PERSOAL ISURACE COMPARISO AD
US 212664A1 (19) United States (12) Patent Application Publication (1) Pub. o.: US 212/664 A1 Lee (43) Pub. Date: Mar. 15, 212 (54) (76) (21) (22) (6) METHOD AD SYSTEM FOR PERSOAL ISURACE COMPARISO AD
Libra Esva. Whitepaper. Glossary. How Email Really Works. Email Security Virtual Appliance. May, 2010. It's So Simple...or Is It?
 Libra Esva Email Security Virtual Appliance Whitepaper May, 2010 How Email Really Works Glossary 1 2 SMTP is a protocol for sending email messages between servers. DNS (Domain Name System) is an internet
Libra Esva Email Security Virtual Appliance Whitepaper May, 2010 How Email Really Works Glossary 1 2 SMTP is a protocol for sending email messages between servers. DNS (Domain Name System) is an internet
US 20130169877A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2013/0169877 A1 DANG (43) Pub. Date: Jul.
 US 20130169877A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2013/0169877 A1 DANG (43) Pub. Date: Jul. 4, 2013 (54) SUPPLEMENTAL AUDIO AND VISUAL (52) US. Cl. SYSTEM FORA VIDEO
US 20130169877A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2013/0169877 A1 DANG (43) Pub. Date: Jul. 4, 2013 (54) SUPPLEMENTAL AUDIO AND VISUAL (52) US. Cl. SYSTEM FORA VIDEO
1,5 F., n M 3 My MM, 3 2. M5, ' 120 1. (21) App1.N0.: 13/789,334 M/WMWW W ~ 3> ( I INTERNET < 114. (71) ApplicantszRobert Monster, Sammamish, WA
 v US 2013023 8496A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0238496 A1 Monster et al. (43) Pub. Date: Sep. 12, 2013 (54) SYSTEM AND METHOD FOR DOMAN LEASNG, ACQUSTON
v US 2013023 8496A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0238496 A1 Monster et al. (43) Pub. Date: Sep. 12, 2013 (54) SYSTEM AND METHOD FOR DOMAN LEASNG, ACQUSTON
Cunneciiun to credit cards dltabase. The system analyzes all credit cards aeecums.
 US 20050137949A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0137949 A1 Rittman et al. (43) Pub. Date: Jun. 23, 2005 (54) AUTOMATIC, CHARACTERIZED AND PRIORITIZED TRANSACTIONS
US 20050137949A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0137949 A1 Rittman et al. (43) Pub. Date: Jun. 23, 2005 (54) AUTOMATIC, CHARACTERIZED AND PRIORITIZED TRANSACTIONS
check is encoded for causing it to b; oplerable with a, predetermined metering device. In t e a ternative em
 12/23/82 Unlted States XF? LHBI'I'QOES Patent [19] [11] 4,317,028 Simjian [] Feb. 23, 1982 [54] SUBSCRIBER CHECK ACCEPTING AND check adapted to operate a metering device comprises ISSUING APPARATUS means
12/23/82 Unlted States XF? LHBI'I'QOES Patent [19] [11] 4,317,028 Simjian [] Feb. 23, 1982 [54] SUBSCRIBER CHECK ACCEPTING AND check adapted to operate a metering device comprises ISSUING APPARATUS means
(54) MANAGEMENT OF QUEUES IN CONTACT Publication Classi?cation CENTRES (51) Int. Cl.
 l US 20110283000A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2011/0283000 A1 McCormack et al. (43) Pub. Date: NOV. 17, 201 1 (54) MANAGEMENT OF QUEUES IN CONTACT Publication
l US 20110283000A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2011/0283000 A1 McCormack et al. (43) Pub. Date: NOV. 17, 201 1 (54) MANAGEMENT OF QUEUES IN CONTACT Publication
