(IP Connection) Miami (54) (76) (21) (22) (51) (52) Application
|
|
|
- April Caldwell
- 8 years ago
- Views:
Transcription
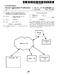
1 US Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/ A1 Henderson et al. (43) Pub. Date: Jan. 18, 2007 (54) (76) (21) (22) (51) (52) METHOD OF AND SYSTEM FOR BIOMETRIC-BASED ACCESS TO SECURE RESOURCES WITH DUAL AUTHENTICATION Inventors: James D. Henderson, Delray Beach, FL (US); Paul A. Windebank, Fort Lauderdale, FL (US) Correspondence Address: LAW OFFICE OF DAVID H. JUDSON DALLAS PARKWAY SUITE 225 DALLAS, TX (US) Appl. No.: 11/177,064 Filed: Jul. 8, 2005 Publication Classi?cation Int. Cl. H04L 9/00 ( ) US. Cl /169 (57) ABSTRACT A biometric-based access mechanism implements a dual authentication scheme. It is assumed that an authorized user has enrolled in the system by generating a set of biometric data from Which at least?rst and second templates have been generated and stored in an authentication server. When the user at a client later seeks to obtain access to a protected resource (e.g., a data?le, a database, an application, or the like) stored on an application server or other host, a new set of biometric data is generated at the client, together With new templates. The templates are generated using the same functions that Were used to generate the?rst and second templates during the enrollment process. The client main tains one of the two templates in-memory at a client While at least one other template is exported to the authentication server for matching. If the authentication server matches the template received from the client, the authentication server exports to the client a template that must then be matched With the template being held in-memory before authentica tion is complete and access to the protected resource at the application server or other host provided. This dual authen tication approach prevents a third party from spoo?ng the communications between the client and authentication server. Miami (IP Connection) SSL Enuypted Tramocllons SSL Encrypted Tlanuaiom Resource (?le. DB.?le system. auplicalion. etc. 100 Administration Console Enrollmznt, Rzpottinq, Slams Biometric Application HOSl Machine Application S erver
2 Patent Application Publication Jan. 18, 2007 Sheet 1 0f 3 US 2007/ A1 lntra / Internet {IP Connection) SSL Encrypted Tramoclions,~' ' ' \ {\ : Client SSL Encrypted Tlanuaiom / Sensor I06 I08 Autnentta?onserver mtiiéf frf?'?'e m2 Emgimmmgm_ Biometric Application Host Machine Application s erver Figure 1 Giant Authentication Server Client Manager 202 Server Manager 203 Authentication Matching Authentication Matching Routine 2134 Routine 210 Communications Communications DI'UCESS process Figure 2
3 Patent Application Publication Jan. 18, 2007 Sheet 2 0f 3 US 2007/ A1 rm Capture data 3'32 Create _- 304 templates Store TEMPLATE 306 STYLE A Forward TEMPLATE '308 STYLE 8 Send TEMPLATE STYLE 8 to the Authenticaucn Server 3m Retrieve HOST TEMPLATE, 312 STYLE 8 from DB l Provide TEMPLATES m MATCHER *3 31a 32IJ\ / 3'6 / MATCH? _ ForwardNOMATCH _ RETURN Retrieve copy of HOST, 322 TEMPLATE STYLE A r 329 \ Transmit to cliem machine " 325 Servlet decrypts, retrieves HOST TEMPLATE STYLE A, forward to MATCHER r, 33o Retrieve TEMPLATE STYLE A from memory YES / B 340 \ / PASS I \ 1 Generate NOMATCH _ Forwaru ]_ Send 1 Receive and store Figure 3
4 Patent Application Publication Jan. 18, 2007 Sheet 3 0f 3 US 2007/ A1 Fingerp Biometric Data Set 400 Function 1 Function 2 402a 402D Function n 4U2n Template 404a Template 404D Tempilate 404m Figure 4
5 US 2007/ A1 Jan. 18, 2007 METHOD OF AND SYSTEM FOR BIOMETRIC-BASED ACCESS TO SECURE RESOURCES WITH DUAL AUTHENTICATION [0001] BACKGROUND OF THE INVENTION 1. Technical Field [0002] The present invention relates generally to methods of and systems for managing access to protected resources by authorized users in a distributed computing environment. [0003] 2. Description of the Related Art [0004] Biometric-based access to secure resources over a computer network is a Well-de?ned art. Typically, a user desiring access to a secure resource is?rst enrolled in the system and assigned a usemame and password. Biometric based access is added through additional enrollment pro cesses. During such biometric enrollment, a biometric cap ture device (e.g., a?ngerprint reader, voice scan, or the like) obtains an image of the desired physical characteristic, Which is then processed into a template through one or more conventional data processing techniques, Which may be proprietary. The usemame, password and template are then stored in a database. When the user later desires access to a protected resource, he or she logs on (With the username/ password pair) and re-presents his or her physical charac teristic to the biometric device. If the user is authorized (through the username and password) and authenticated (by comparing the current template With the stored template), access to the protected resource is permitted. Such systems may also use the biometric mechanisms to facilitate frequent or access-based user password modi?cations for enhanced security. A representative system of this type is described in US. Pat. No. 6,636,973. [0005] While biometric-based access control Works Well, there remains a need in the art to enhance such systems, especially Where additional levels of security are desired or required for the particular resource. The present invention addresses this need. BRIEF SUMMARY OF THE INVENTION [0006] A biometric-based access mechanism of the present invention implements a dual authentication scheme. According to the present invention, it is assumed that an authorized user has enrolled in the system by generating a set of biometric data from Which at least?rst and second templates have been generated and stored in an authentica tion server. When the user at a client later seeks to obtain access to a protected resource (e.g., a data?le, a database, an application, or the like) stored on an application server (or other host), a new set of biometric data is generated at the client, together With new templates. The templates are generated using the same functions that Were used to gen erate the?rst and second templates during the enrollment process. The client maintains one of the two templates in-memory at a client While at least one other template is exported to the authentication server for matching. If the authentication server matches the template received from the client, the authentication server exports to the client a template that must then be matched With the template being held in-memory before authentication is complete and access to the protected resource at the application server provided. This dual authentication approach prevents a third party from spoo?ng the communications between the client and authentication server in a manner that might otherwise allow the third party to gain access to a template from Which a false authentication decision can be manufac tured. [0007] The foregoing has outlined some of the more pertinent features of the invention. These features should be construed to be merely illustrative. Many other bene?cial results can be attained by applying the disclosed invention in a different manner or by modifying the invention as Will be described. BRIEF DESCRIPTION OF THE DRAWINGS [0008] FIG. 1 is a block diagram illustrating a represen tative distributed computing environment in Which the present invention may be implemented; [0009] FIG. 2 illustrates a set of software components that facilitate the dual authentication scheme of the present invention; [0010] FIG. 3 is a process How illustrating a preferred embodiment of the present invention; and [0011] FIG. 4 illustrates how a biometric capture device and associated software generate?rst and second templates from a given data set generated by the capture device. DETAILED DESCRIPTION OF THE PREFERRED EMBODIMENT [0012] For purposes of illustration, the present invention is shown as being implemented in a distributed computer environment Within a given enterprise. The invention may be implemented as a product or a service. A representative system in Which the invention is implemented comprises an application server 102 (or any other host), a client machine 104, and an authentication server 108. The authentication server 108 has an associated administrative console 110. The machines are connected to one another over a network, such as Wide area network (WAN), local area network (LAN), protected network (e. g., VPN), a dedicated network, or some combination thereof. Communications among the various machines are assumed to be encrypted or otherwise pro tected, e. g., via SSL or the like. One or more of the machines preferably are located behind an enterprise?rewall. The application server (and there may be more than one) sup ports a given resource 100 (a?le, a database, a?le system, an application, a computer, a system, or the like) to Which a user of the client machine 104 desires to access. In one illustrated embodiment, the resource is a process executing on the application server 102. It is assumed that the user of the client machine has been authorized to access the resource (e.g., by an enterprise administrator or the like). The client machine has an associated biometric capture device 106. Biometric capture device 106 generates a bio metric data set for a given physical characteristic, such as?ngerprint, facial geometry, voice print, retinal scan, typing speed, or any other characteristic that distinguishes one person from another. Such devices include software routines for processing the biometric data set into a template, Which is a digital representation of the biometric data. The administrative console 110 may also include a biometric capture device 112. In a representative embodiment, the application server 102 and the authentication server 108 are
6 US 2007/ A1 Jan. 18, 2007 both IBM iseries machines running an operating system (e.g., IBM i5/os), and the client machine 104 is a Worksta tion having commodity hardware (e.g., Pentium class pro cessor(s)), operating system (Windows, Linux, or the like), application programs (e.g., Internet Explorer, and the like) and utilities. The authentication server 108 comprises a Web server 114 (e.g., Apache) and a database 116 (e.g., IBM DB2). A representative biometric capture device 106 or 112 is a?ngerprint sensor Model AES3500 (utilizing an RF electronic imaging mechanism called TruePrint technology) manufactured by AuthenTec, Inc. Of course, any other hardware, software, systems, devices and the like may be used. More generally, the present invention may be imple mented With any collection of autonomous computers (together With their associated software, systems, protocols and techniques) linked by a network or networks. [0013] As illustrated in FIG. 2, the present invention comprises a set of preferably software-based functions (e.g., applications, processes, execution threads, or the like) or?rmware-based functions that provide the dual authentica tion scheme. As shown in FIG. 2, these functions are provided in a set of components supported across the client machine and the authentication server. These components comprise, on the client machine, a client manager 202, an authentication matching routine 204, and Web servlet 206, and, on the authentication server, a server manager 208, an authentication matching routine 210, and Web servlet 212. These functions may be integrated into one set of code, but this is not a requirement. Neither the authentication match ing nor the communications functions are required to be native to the dual authentication codebase, as the matching function may be provided With the biometric capture device (e.g., as a software driver), and communications (e.g., through the servlet) may comprise part of an underlying application server framework. A representative application server is IBM WebSphere Application Server (WAS), such as Version 5.0 or greater, Which uses JV M (Java Virtual Machine) and is J2EE-compliant. Thus, according to the invention, each client and each authentication server include a manager process and template matching software. The manager process may be implemented in native code, as an execution thread, or in any other convenient manner depending on the client-server architecture, storage or pro cessing constraints, or the like. The particular hardware and software implementation details are not part of the present invention. [0014] As illustrated in FIG. 4, a biometric capture device generates a biometric data set 400 that, according to the present invention, is?rst processed by a set of two or more processing functions 402a-n into a set of two or more templates 404a-n. The processing functions 402 typically are proprietary algorithms created by the providers of the biometric devices, but one or more commercially available or open source techniques may be used. By Way of a simple example, one processing function generates a simple MD5 hash of a portion of the biometric data set While a second processing function generates a SHA-l hash of the portion. For purposes of the present invention, the particular pro cessing functions are not critical; rather, What is important is that at least?rst and second processing functions operate on the same biometric data set (or portions thereof) to generate the at least?rst and second templates, and that the same?rst and second processing functions be used during a user s enrollment process and When the user seeks to access a protected resource using the inventive dual authentication scheme. Generalizing, it is assumed that a given biometric data set processes at least two (2) biometric templates each With unique differentiating characteristics. In a representa tive embodiment, the?ngerprint sensor is the AuthenTec AES3500 device (or equivalent) that has associated there With software (e.g., in the form of a dynamic link library, DLL) that implements the algorithms for generating the templates. Calls to the DLL may be implemented through an application programming interface (API). The templates are stored in a protected manner in the authentication server s database. Although not meant to be limiting, preferably the database server implements a database management scheme With a user s enrollment data indexed by a data identi?er. The identi?er is associated With a data record that is encrypted. Each?eld in the data record includes data asso ciated With a given one of the templates, and preferably a?eld level encryption scheme is applied across the data record for enhanced security. With the above as background, the dual authentication scheme is not described in detail using the process How diagram shown in FIG. 3. [0015] As described above, it is assumed that the authen tication server runs an AUTHENTICATION HOST process. The process begins at step 300 With enrollment. At this step an AUTHENTICATION HOST process of the authentica tion server receives and stores two (2) biometric templates With unique differentiating characteristics, as has been described above With respect to FIG. 2. The?rst template is the HOST TEMPLATE STYLE A and the second template is the HOST TEMPLATE STYLE B. Preferably, the authen tication stores these templates in an encrypted database, although this is not required. It is now assumed that a user desires to access a protected resource, such a resource 100 stored on the application server 102 shown in FIG. 1. For purposes of illustration, it is assumed that the user is making the access request from the client 104 having the biometric capture device 106, also as illustrated in FIG. 1. Of course, the user may enroll his or her biometrics at a?rst client and then request access to a protected resource from a second client. After the user logs in and is authorized in the usual manner (e.g., by entry and veri?cation of the user s user name and password), the routine continues at step 302. At this step, and When prompted for authentication, the user responds by providing the requested BIOMETRIC DATA via the capture device. At step 304, just as during the enrollment process, preferably two (2) sets of BIOMETRIC DATA, each With unique differentiating characteristics, are constructed, namely, TEMPLATE STYLE A and TEM PLATE STYLE B. Of course, any number of TEMPLATE STYLES may be generated, depending on the number generated during the enrollment process. Also, one of ordi nary skill in the art Will appreciate that the?rst and second processing functions used to generated the TEMPLATE STYLES A and B (and so on) must be the same processing functions used to generate the respective HOST TEM PLATE STYLES A and B (and so on). At step 306, TEM PLATE STYLE A is stored in-memory at the client and, at step 308, TEMPLATE STYLE B is sent to a communica tions (e.g., Web servlet) process executing on the client. Of course, here the nomenclature A and B is used for illustration only; it is only required that the particular version main tained in-memory or sent, as the case may be, be identi?able so that the authentication match can be performed at the authentication server 108 of FIG. 1.
7 US 2007/ A1 Jan. 18, 2007 [0016] At step 310, the client communications process transmits TEMPLATE STYLE B to the AUTHENTICA TION HOST process executing on the authentication server; preferably, this transmission occurs over a secure link. Alternatively, TEMPLATE STYLE B may be encrypted prior to being forwarded from the client to the authentication server. The routine then continues at the authentication server. At step 312, the authentication server communica tions process retrieves HOST TEMPLATE STYLE B from its associated database 110 of FIG. 1 and, at step 314, provides TEMPLATE STYLE B (received from the client) and HOST TEMPLATE STYLE B (retrieved from the local database) to a HOST AUTHENTICATION MATCHER process executing on the authentication server. Preferably, a MATCHER process is instantiated for each authentication request received at the authentication server. At step 316, the HOST AUTHENTICATION MATCHER tests to determine Whether TEMPLATE STYLE B matches HOST TEM PLATE STYLE B Within a given,?rst acceptance criteria. The particular criteria, of course, Will depend on the pro cessing function that Was used to generate the template. An administrator may establish one or more different acceptable thresholds, depending on the level(s) of security desired or required. If the outcome of the test at step 316 indicates that there is no match between TEMPLATE STYLE B and HOST TEMPLATE STYLE B, the routine branches to step 318, Wherein the authentication server forwards a NOMATCH message to the authentication server s commu nications process. At step 320, the authentication server s communications process returns the NOMATCH message to the requesting client and the authentication process termi nates. If, however, the outcome of the test at step 316 indicates that there is an acceptable match between TEM PLATE STYLE B and HOST TEMPLATE STYLE B, the routine continues at step 322 With the AUTHENTICATION HOST process of the authentication server retrieving a copy of HOST TEMPLATE STYLE A from its database, Which it then may encrypt. At step 324, the AUTHENTICATION HOST process provides the copy of HOST TEMPLATE STYLE A, together With an indication of the match, to the authentication server s communications process. At step 326, the authentication server s communications process sends this information to the requesting client s communi cations process. [0017] Processing then continues back at the client. At step 328, the client communications process decrypts the data, retrieves HOST TEMPLATE STYLE A and forwards it to a local MATCHER process. At step 330, the client Web servlet retrieves TEMPLATE STYLE A (Which to this point has been maintained in-memory at the client) and forwards it to the MATCHER process. At step 332, the client MATCHER process performs a test to compare TEMPLATE STYLE A and HOST TEMPLATE STYLE A, i.e., to deter mine Whether these templates match Within a given second, acceptance criteria. Once again, the particular acceptance criteria Will depend on the processing function that Was used to generate the template. An administrator may establish one or more different acceptable thresholds, depending on the level(s) of security desired or required. Also, the acceptable threshold may be varied as a function of the closeness in the TEMPLATE B biometric comparisons, or based on some other condition or occurrence. If the outcome of the test at step 332 indicates that there is a match between TEMPLATE STYLE A and HOST TEMPLATE STYLE A Within the given acceptance criteria, the routine continues at step 334, Which indicates a PASS. At this point, the user is provided access to the protected resource. If, however, the outcome of the test at step 332 is negative, the routine branches to step 336, Wherein a NOMATCH message is generated by the client MATCHER process. Continuing With this branch, at step 338, the NOMATCH message is provided to the client s communications process Which, at step 340, sends the NOMATCH message to the authentication server. At step 342, the authentication server communications process receives the NOMATCH message and forwards it to the authentication server, Which stores the indication in its associated database. This completes the processing. [0018] Thus, as can be seen, the present invention assumes that an authorized user has enrolled in the system by generating a set of biometric data from Which at least?rst and second templates have been generated and stored in an authentication server. When the user at a client later seeks to obtain access to a protected resource (e.g., a data?le, a database, an application, or the like) stored on an application server or other host, a new set of biometric data is generated at the client, together With new templates. The client main tains one of the two templates in-memory at a client While at least one other template is exported to an authentication server for matching. If the authentication server matches the template received from the client, it, the authentication server, exports to the client a template that must then be matched With the template being held in-memory before authentication is complete and access to the protected resource provided. This dual authentication approach pre vents a third party from spoo?ng the communications between the client and authentication server in a manner that might otherwise allow the third party to gain access to a template from Which a false authentication decision can be manufactured. [0019] The present invention provides scalable, enterprise biometric authentication in a manner that overcomes the de?ciencies of the prior art. The dual authentication scheme Works by associating biometric data With a user in a Way that cannot be spoofed, i.e., regenerated by other than from the biometric capture device used to enroll the authorized user and then being later used to access the protected resource. [0020] As previously noted, the hardware and software systems in Which the invention is illustrated are merely representative. The invention may be practiced, typically in software, on one or more machines. Generalizing, a machine typically comprises commodity hardware and software, stor age (e.g., disks, disk arrays, and the like) and memory (RAM, ROM, and the like). The particular machines used in the network are not a limitation of the present invention. A given machine includes network interfaces and software to connect the machine to a network in the usual manner. A machine typically includes a Web browser. An application server process may provide support for servlets and the like. [0021] A variation of the present invention Would be to create the?rst and second templates (either during enroll ment or in use to access a protected resource) using the same
8 US 2007/ A1 Jan. 18, 2007 codebase (e.g., a single processing function) applied to two distinct portions of the biometric data set. [0022] Having described our invention, what we now claim is set forth below. 1. A method to manage access to a given resource by an authorized user in a distributed computing system, the system including a client having an associated biometric capture device, and an authentication server in which are stored?rst and second templates derived from a given biometric characteristic of the authorized user by applying?rst and second functions to a biometric data set, the method comprising: upon a given request to access the given resource, gen erating, at the client, third and fourth templates by re-applying the respective?rst and second functions to a biometric data set that is generated at the client contemporaneously; forwarding the third template to the to the authentication server while maintaining the fourth template in-memory at the client; determining, at the authentication server, whether the third template matches the?rst template within a?rst acceptance criteria; if the third template matches the?rst template with the?rst acceptance criteria, forwarding an indication of the match and the second template from the authentication server to the client; determining, at the client, whether the second template forwarded from the authentication server matches, within a second acceptance criteria, the fourth template with then held in-memory; if the second template matches the fourth template within the second acceptance criteria, enabling access to the given resource by the authorized user. 2. The method as described in claim 1 further including the step of inhibiting access to the given resource if the third template does not match the?rst template within the?rst acceptance criteria, or if the second template does not match the fourth template within the second acceptance criteria. 3. The method as described in claim 1 wherein commu nications between the authentication server and the client are provided over a secure link. 4. The method as described in claim 4 wherein each communication is encrypted. 5. The method as described in claim 1 wherein the client and the authentication server communicate over a wide area network, local area network, or private network. 6. The method as described in claim 1 wherein the resource is stored on an application server or other machine distinct from the authentication server. 7. The method as described in claim 6 wherein the authentication server manages access requests from a set of authorized users in an enterprise. 8. A biometric-based access method operative in a dis tributed networking environment comprising a client machine having a biometric capture device, an authentica tion server, and an application server or other host having a protected resource, wherein at least?rst and second tem plates generated from a biometric data set have been stored in or in association with the authentication server, compris ing: upon an access request at the client machine, generating a new set of biometric data and associated third and fourth templates; maintaining the third template in-memory at the client machine while exporting the fourth template to the authentication server where it can be matched against the second template; upon any receipt at the client machine of the?rst tem plate, allowing access to the protected resource if the?rst template matches the third template. 9. The biometric-based access method as described in claim 8 wherein communications between the client machine and the authentication server occur over a secure link.
US 201203 03424Al (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2012/0303424 A1 Lundstrom (43) Pub. Date: NOV.
 US 201203 03424Al (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2012/0303424 A1 Lundstrom (43) Pub. Date: NOV. 29, 2012 (54) METHOD AND SOFTWARE FOR Publication Classi?cation
US 201203 03424Al (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2012/0303424 A1 Lundstrom (43) Pub. Date: NOV. 29, 2012 (54) METHOD AND SOFTWARE FOR Publication Classi?cation
US 20090157756Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2009/0157756 A1 Sanvido (43) Pub. Date: Jun.
 US 20090157756Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2009/0157756 A1 Sanvido (43) Pub. Date: Jun. 18, 2009 (54) FILE SYSTEM FOR STORING FILES IN Publication Classi?cation
US 20090157756Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2009/0157756 A1 Sanvido (43) Pub. Date: Jun. 18, 2009 (54) FILE SYSTEM FOR STORING FILES IN Publication Classi?cation
US 20070019798Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0019798 A1 Voight et al. SUBSCRIBER DATABASE.
 US 20070019798Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0019798 A1 Voight et al. (43) Pub. Date: Jan. 25, 2007 (54) METHOD AND APPARATUS FOR PROVIDING CUSTOMIZED
US 20070019798Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0019798 A1 Voight et al. (43) Pub. Date: Jan. 25, 2007 (54) METHOD AND APPARATUS FOR PROVIDING CUSTOMIZED
US 20140046812A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0046812 A1 FAN et al. (43) Pub. Date: Feb.
 US 20140046812A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0046812 A1 FAN et al. (43) Pub. Date: (54) EXPENSE REPORTS FOR PAYMENTS MADE (52) US. Cl. WITH A MOBILE DEVICE
US 20140046812A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0046812 A1 FAN et al. (43) Pub. Date: (54) EXPENSE REPORTS FOR PAYMENTS MADE (52) US. Cl. WITH A MOBILE DEVICE
Lookup CNAM / other database for calllng
 (19) United States US 20140003589Al (12) Patent Application Publication (10) Pub. No.: US 2014/0003589 A1 Martino et al. (43) Pub. Date: Jan. 2, 2014 (54) (71) (72) (73) (21) (22) (63) PROVIDING AUDIO
(19) United States US 20140003589Al (12) Patent Application Publication (10) Pub. No.: US 2014/0003589 A1 Martino et al. (43) Pub. Date: Jan. 2, 2014 (54) (71) (72) (73) (21) (22) (63) PROVIDING AUDIO
US 20050027827A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0027827 A1 Owhadi et al. (43) Pub. Date: Feb.
 US 20050027827A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0027827 A1 Owhadi et al. (43) Pub. Date: Feb. 3, 2005 (54) SYSTEM FOR PROVIDING SUPPORT FOR AN ELECTRONIC
US 20050027827A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0027827 A1 Owhadi et al. (43) Pub. Date: Feb. 3, 2005 (54) SYSTEM FOR PROVIDING SUPPORT FOR AN ELECTRONIC
NJ (US) (51) Int. Cl. H04L 9/00 (2006.01) Correspondence Address: (52) US. Cl... 380/278; 713/ 150 ALFRED C. ROTH (57) ABSTRACT
 . I. I. I US 20080187140A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2008/0187140 A1 McGillian et al. (43) Pub. Date: Aug. 7, 2008 (54) METHOD AND SYSTEM OF SECURELY Related
. I. I. I US 20080187140A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2008/0187140 A1 McGillian et al. (43) Pub. Date: Aug. 7, 2008 (54) METHOD AND SYSTEM OF SECURELY Related
ENCODED $30 CERT'F'CATE -+ DECODE CERTIFICATE
 US 20130346742A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0346742 A1 Tada et al. (43) Pub. Date: (54) METHOD AND SYSTEM FOR DEVICE Publication Classi?cation AUTHENTICATION
US 20130346742A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0346742 A1 Tada et al. (43) Pub. Date: (54) METHOD AND SYSTEM FOR DEVICE Publication Classi?cation AUTHENTICATION
US 20020072350A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0072350 A1 Fukuzato (43) Pub. Date: Jun.
 US 20020072350A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 20020072350 A1 Fukuzato (43) Pub. Date: Jun. 13, 2002 (54) BACKUP METHOD OF APPLICATIONS OF PORTABLE CELLULAR PHONE
US 20020072350A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 20020072350 A1 Fukuzato (43) Pub. Date: Jun. 13, 2002 (54) BACKUP METHOD OF APPLICATIONS OF PORTABLE CELLULAR PHONE
US 20070160058Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0160058 A1 Zhou et al. (43) Pub. Date: Jul.
 US 20070160058Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0160058 A1 Zhou et al. (43) Pub. Date: (54) METHOD AND SYSTEM FOR IMPLEMENTING BACKUP BASED ON SESSION BORDER
US 20070160058Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0160058 A1 Zhou et al. (43) Pub. Date: (54) METHOD AND SYSTEM FOR IMPLEMENTING BACKUP BASED ON SESSION BORDER
US 20020141557A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0141557 A1 STRANDBERG (43) Pub. Date: Oct.
 ---- US 20020141557A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0141557 A1 STRANDBERG (43) Pub. Date: (54) SYSTEM AND METHOD FOR PROVIDING AN AUTOMATIC TELEPHONE CALL
---- US 20020141557A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0141557 A1 STRANDBERG (43) Pub. Date: (54) SYSTEM AND METHOD FOR PROVIDING AN AUTOMATIC TELEPHONE CALL
Ulllted States Patent [19] [11] Patent Number: 5,943,406
![Ulllted States Patent [19] [11] Patent Number: 5,943,406 Ulllted States Patent [19] [11] Patent Number: 5,943,406](/thumbs/30/14188909.jpg) US005943406A Ulllted States Patent [19] [11] Patent Number: 5,943,406 Leta et al. [45] Date of Patent: Aug. 24, 1999 [54] TELEPHONE CALL TRACKING AND 4,813,065 3/1989 Segala..... 379/112 BILLING SYSTEM
US005943406A Ulllted States Patent [19] [11] Patent Number: 5,943,406 Leta et al. [45] Date of Patent: Aug. 24, 1999 [54] TELEPHONE CALL TRACKING AND 4,813,065 3/1989 Segala..... 379/112 BILLING SYSTEM
/ \33 40 \ / \\ \ \ M / 32. 28f 1. (19) United States (12) Patent Application Publication Lawser et al. NETWORK \ 36. SERVlCE 'NTERNET SERVICE
 (19) United States (12) Patent Application Publication Lawser et al. US 20130336314A1 (10) Pub. N0.: US 2013/0336314 A1 (43) Pub. Date: Dec. 19, 2013 (54) (71) (72) (73) (21) (22) (63) METHOD FOR COMPLETING
(19) United States (12) Patent Application Publication Lawser et al. US 20130336314A1 (10) Pub. N0.: US 2013/0336314 A1 (43) Pub. Date: Dec. 19, 2013 (54) (71) (72) (73) (21) (22) (63) METHOD FOR COMPLETING
(Us) (73) Assignee: Avaya Technology Corp. Je?' McElroy, Columbia, SC (US); (21) Appl. No.: 10/413,024. (22) Filed: Apr. 14, 2003 (57) ABSTRACT
 US 20040202300A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0202300 A1 Cooper et al. (43) Pub. Date: Oct. 14, 2004 (54) CALL HANDLING USING NON-SPEECH CUES VIA A PERSONAL
US 20040202300A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0202300 A1 Cooper et al. (43) Pub. Date: Oct. 14, 2004 (54) CALL HANDLING USING NON-SPEECH CUES VIA A PERSONAL
(12) Patent Application Publication (10) Pub. No.: US 2003/0035525 A1 Wu et al. (43) Pub. Date: Feb. 20, 2003
 (19) United States US 20030035525A1 (12) Patent Application Publication (10) Pub. No.: US 2003/0035525 A1 Wu et al. (43) Pub. Date: (54) (76) (21) (22) SYSTEM AND METHOD FOR DISTINGUISHING TELEPHONE NUMBER
(19) United States US 20030035525A1 (12) Patent Application Publication (10) Pub. No.: US 2003/0035525 A1 Wu et al. (43) Pub. Date: (54) (76) (21) (22) SYSTEM AND METHOD FOR DISTINGUISHING TELEPHONE NUMBER
software, and perform automatic dialing according to the /*~102
 US 20140105199A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0105199 A1 Tian (43) Pub. Date: (54) METHOD AND APPARATUS FOR AUTOMATIC DIALING ACCESS POINTS (71) Applicant:
US 20140105199A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0105199 A1 Tian (43) Pub. Date: (54) METHOD AND APPARATUS FOR AUTOMATIC DIALING ACCESS POINTS (71) Applicant:
(12) United States Patent (10) Patent N0.: US 8,282,471 B1 Korner (45) Date of Patent: Oct. 9, 2012
 US008282471B1 (12) United States Patent (10) Patent N0.: US 8,282,471 B1 Korner (45) Date of Patent: Oct. 9, 2012 (54) COMPUTER-IMPLEMENTED SPORTS 2011/0003634 A1* 1/2011 Manteris..... 463/25 WAGERING
US008282471B1 (12) United States Patent (10) Patent N0.: US 8,282,471 B1 Korner (45) Date of Patent: Oct. 9, 2012 (54) COMPUTER-IMPLEMENTED SPORTS 2011/0003634 A1* 1/2011 Manteris..... 463/25 WAGERING
US 20030110248A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2003/0110248 A1 Ritchc (43) Pub. Date: Jun.
 US 20030110248A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2003/0110248 A1 Ritchc (43) Pub. Date: (54) (76) (21) (22) (51) (52) AUTOMATED SERVICE SUPPORT OF SOFTWARE DISTRIBUTION
US 20030110248A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2003/0110248 A1 Ritchc (43) Pub. Date: (54) (76) (21) (22) (51) (52) AUTOMATED SERVICE SUPPORT OF SOFTWARE DISTRIBUTION
US 20070203917A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0203917 A1 Du et al. (43) Pub. Date: Aug.
 ' i.. 2. Y. US 20070203917A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0203917 A1 Du et al. (43) Pub. Date: (54) COMMUNICATION SYSTEM AND METHOD FOR IMPLEMENTING ONLINE
' i.. 2. Y. US 20070203917A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0203917 A1 Du et al. (43) Pub. Date: (54) COMMUNICATION SYSTEM AND METHOD FOR IMPLEMENTING ONLINE
60 REDIRECTING THE PRINT PATH MANAGER 1
 US006788429B1 (12) United States Patent (10) Patent No.: US 6,788,429 B1 Clough et al. (45) Date of Patent: Sep. 7, 2004 (54) REMOTE PRINT QUEUE MANAGEMENT FOREIGN PATENT DOCUMENTS (75) Inventors: James
US006788429B1 (12) United States Patent (10) Patent No.: US 6,788,429 B1 Clough et al. (45) Date of Patent: Sep. 7, 2004 (54) REMOTE PRINT QUEUE MANAGEMENT FOREIGN PATENT DOCUMENTS (75) Inventors: James
US 20070016324A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0016324 A1. Operating System. 106 q f 108.
 US 20070016324A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0016324 A1 Oddiraj u et al. (43) Pub. Date: Jan. 18, 2007 (54) SYSTEM BOOT OPTMZER (75) nventors: Chandar
US 20070016324A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0016324 A1 Oddiraj u et al. (43) Pub. Date: Jan. 18, 2007 (54) SYSTEM BOOT OPTMZER (75) nventors: Chandar
Hay (43) Pub. Date: Oct. 17, 2002
 US 20020152322A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0152322 A1 Hay (43) Pub. Date: Oct. 17, 2002 (54) (76) (21) (22) (51) (52) METHOD AND APPARATUS FOR FACILITATING
US 20020152322A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0152322 A1 Hay (43) Pub. Date: Oct. 17, 2002 (54) (76) (21) (22) (51) (52) METHOD AND APPARATUS FOR FACILITATING
Cunneciiun to credit cards dltabase. The system analyzes all credit cards aeecums.
 US 20050137949A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0137949 A1 Rittman et al. (43) Pub. Date: Jun. 23, 2005 (54) AUTOMATIC, CHARACTERIZED AND PRIORITIZED TRANSACTIONS
US 20050137949A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0137949 A1 Rittman et al. (43) Pub. Date: Jun. 23, 2005 (54) AUTOMATIC, CHARACTERIZED AND PRIORITIZED TRANSACTIONS
Patent Application Publication Sep. 30, 2004 Sheet 1 0f 2. Hierarchical Query. Contact Ow FIG. 1
 US 20040193595A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0193595 A1 Kaminsky et al. (43) Pub. Date: Sep. 30, 2004 (54) NEAREST KNOWN PERSON DIRECTORY FUNCTION (75)
US 20040193595A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0193595 A1 Kaminsky et al. (43) Pub. Date: Sep. 30, 2004 (54) NEAREST KNOWN PERSON DIRECTORY FUNCTION (75)
(71) Applicant: SPEAKWRITE, LLC,Austin, TX (US)
 US 20130304465Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0304465 A1 Henry et al. (43) Pub. Date: NOV. 14, 2013 (54) METHOD AND SYSTEM FOR AUDIO-VIDEO (52) US. Cl.
US 20130304465Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0304465 A1 Henry et al. (43) Pub. Date: NOV. 14, 2013 (54) METHOD AND SYSTEM FOR AUDIO-VIDEO (52) US. Cl.
US 20120215907A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0215907 A1 Chung (43) Pub. Date: Aug.
 US 20120215907A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0215907 A1 Chung (43) Pub. Date: (54) SYSTEMS AND METHODS FOR (52) US. Cl...... 709/224 SELF-ADJUSTING LOGGING
US 20120215907A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0215907 A1 Chung (43) Pub. Date: (54) SYSTEMS AND METHODS FOR (52) US. Cl...... 709/224 SELF-ADJUSTING LOGGING
222252 211222 1111;111:131... ~~~~~~~~~~~~~~~~~~~ 2221522 [73] Assigneez Rockwell Semiconductor Systems 5,754,639 5/1998 Flockhart et al...
![222252 211222 1111;111:131... ~~~~~~~~~~~~~~~~~~~ 2221522 [73] Assigneez Rockwell Semiconductor Systems 5,754,639 5/1998 Flockhart et al... 222252 211222 1111;111:131... ~~~~~~~~~~~~~~~~~~~ 2221522 [73] Assigneez Rockwell Semiconductor Systems 5,754,639 5/1998 Flockhart et al...](/thumbs/31/14952948.jpg) I I US0059012A Ulllted States Patent [19] [11] Patent Number: Dez0nn0 [] Date of Patent: * May 4, 1999 [54] APPARATUS AND METHOD FOR 5,526,416 6/1996 DeZonno et al...... 379/266 IDENTIFYING RECORDS ()1?
I I US0059012A Ulllted States Patent [19] [11] Patent Number: Dez0nn0 [] Date of Patent: * May 4, 1999 [54] APPARATUS AND METHOD FOR 5,526,416 6/1996 DeZonno et al...... 379/266 IDENTIFYING RECORDS ()1?
DigitalPersona Pro Enterprise
 DigitalPersona Pro Enterprise Version 5.3 Frequently Asked Questions 2012 DigitalPersona, Inc. All Rights Reserved. All intellectual property rights in the DigitalPersona software, firmware, hardware and
DigitalPersona Pro Enterprise Version 5.3 Frequently Asked Questions 2012 DigitalPersona, Inc. All Rights Reserved. All intellectual property rights in the DigitalPersona software, firmware, hardware and
Telephone Dressing Systems - Advantages and Disadvantages
 I US 20030185352A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2003/0185352 A1 Savage et al. (43) Pub. Date: (54) AUTOMATED MESSAGE BROADCAST SYSTEM WITH DUAL MESSAGE SOURCES
I US 20030185352A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2003/0185352 A1 Savage et al. (43) Pub. Date: (54) AUTOMATED MESSAGE BROADCAST SYSTEM WITH DUAL MESSAGE SOURCES
(30) Foreign Application Priority Data
 US 20040015727A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0015727 A1 Lahti et al. (43) Pub. Date: Jan. 22, 2004 (54) SYNCHRONIZATION METHOD (76) Inventors: Jerry Lahti,
US 20040015727A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0015727 A1 Lahti et al. (43) Pub. Date: Jan. 22, 2004 (54) SYNCHRONIZATION METHOD (76) Inventors: Jerry Lahti,
US 20020174380A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2002/0174380 A1. Mannarsamy (43) Pub. Date: NOV.
 US 20020174380A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2002/0174380 A1 Mannarsamy (43) Pub. Date: NOV. 21, 2002 (54) HELPDESK SYSTEM AND METHOD (52) US. Cl...... 714/25
US 20020174380A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2002/0174380 A1 Mannarsamy (43) Pub. Date: NOV. 21, 2002 (54) HELPDESK SYSTEM AND METHOD (52) US. Cl...... 714/25
i Load balancer relays request to selected node
 US 20040243709A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0243709 A1 Kalyanavarathan et al. (43) Pub. Date: Dec. 2, 2004 (54) SYSTEM AND METHOD FOR CLUSTER-SENSITIVE
US 20040243709A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0243709 A1 Kalyanavarathan et al. (43) Pub. Date: Dec. 2, 2004 (54) SYSTEM AND METHOD FOR CLUSTER-SENSITIVE
US 20090055802A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2009/0055802 A1 CROSBY (43) Pub. Date: Feb.
 US 20090055802A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2009/0055802 A1 CROSBY (43) Pub. Date: (54) SELECTIVE MONITORING OF SOFTWARE Publication Classi?cation APPLICATIONS
US 20090055802A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2009/0055802 A1 CROSBY (43) Pub. Date: (54) SELECTIVE MONITORING OF SOFTWARE Publication Classi?cation APPLICATIONS
remote backup central communications and storage facility
 US 20040122914A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0122914 A1 Williams (43) Pub. Date: (54) SECURE DATA BACKUP (52) US. Cl...... 709/217; 711/162 COMMUNICATIONS
US 20040122914A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0122914 A1 Williams (43) Pub. Date: (54) SECURE DATA BACKUP (52) US. Cl...... 709/217; 711/162 COMMUNICATIONS
US 20130138449A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2013/0138449 A1 Pi0t (43) Pub. Date: May 30, 2013
 US 20130138449A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2013/0138449 A1 Pi0t (43) Pub. Date: May 30, 2013 (54) SYSTEM AND METHOD FOR SCHEDULING (52) us. c1. HoME VISITS
US 20130138449A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2013/0138449 A1 Pi0t (43) Pub. Date: May 30, 2013 (54) SYSTEM AND METHOD FOR SCHEDULING (52) us. c1. HoME VISITS
l / Normal End, client 1 granted access to " System 1
 US 20110252465A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2011/0252465 A1 MILLER et al. (43) Pub. Date: Oct. 13, 2011 (54) (75) (73) (21) (22) (63) (60) SYSTEM AND METHOD
US 20110252465A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2011/0252465 A1 MILLER et al. (43) Pub. Date: Oct. 13, 2011 (54) (75) (73) (21) (22) (63) (60) SYSTEM AND METHOD
United States Patent [191
 United States Patent [191 Fancy [54] REDUNDANT SIGNAL CIRCUIT [75] Inventor: Thomas A. Fancy, Westminster, Mass. [73] Assignee: General Electric Company, Schenectady, NY. [211 Appl. No.: 854,973 [22] Filed:
United States Patent [191 Fancy [54] REDUNDANT SIGNAL CIRCUIT [75] Inventor: Thomas A. Fancy, Westminster, Mass. [73] Assignee: General Electric Company, Schenectady, NY. [211 Appl. No.: 854,973 [22] Filed:
US 20120222106Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0222106 A1 Kuehl (43) Pub. Date: Aug.
 US 20120222106Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0222106 A1 Kuehl (43) Pub. Date: (54) AUTOMATED HYBRID CONNECTIONS (52) US. Cl...... 726/11 BETWEEN MULTIPLE
US 20120222106Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0222106 A1 Kuehl (43) Pub. Date: (54) AUTOMATED HYBRID CONNECTIONS (52) US. Cl...... 726/11 BETWEEN MULTIPLE
US 20020116467A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0116467 A1 Boyer et al. (43) Pub. Date: Aug.
 US 20020116467A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0116467 A1 Boyer et al. (43) Pub. Date: Aug. 22, 2002 (54) METHOD AND APPARATUS FOR Publication Classi?cation
US 20020116467A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0116467 A1 Boyer et al. (43) Pub. Date: Aug. 22, 2002 (54) METHOD AND APPARATUS FOR Publication Classi?cation
llllllllllllllillllllllllllllllllllllllllllllllllllllllllllllllllllllllllll
 llllllllllllllillllllllllllllllllllllllllllllllllllllllllllllllllllllllllll USOO5535162A United States Patent [19] [11] Patent Number: 5,535,162 Uenoyama [45] Date of Patent: Jul. 9, 1996 [54] ELECTRICALLY
llllllllllllllillllllllllllllllllllllllllllllllllllllllllllllllllllllllllll USOO5535162A United States Patent [19] [11] Patent Number: 5,535,162 Uenoyama [45] Date of Patent: Jul. 9, 1996 [54] ELECTRICALLY
(12) United States Patent Wen et a].
![(12) United States Patent Wen et a]. (12) United States Patent Wen et a].](/thumbs/27/10120921.jpg) ' US008719918B2 (12) United States Patent Wen et a]. (10) Patent N0.: () Date of Patent: May 6, 14 (54) (75) (73) (21) (22) (86) (87) () () (51) (52) (58) METHOD AND DEVICE FOR DISTRIBUTED SECURITY CONTROL
' US008719918B2 (12) United States Patent Wen et a]. (10) Patent N0.: () Date of Patent: May 6, 14 (54) (75) (73) (21) (22) (86) (87) () () (51) (52) (58) METHOD AND DEVICE FOR DISTRIBUTED SECURITY CONTROL
US 20070139188A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0139188 A1 Ollis et al. HOME PROCESSOR /\ J\ NETWORK
 US 20070139188A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0139188 A1 Ollis et al. (43) Pub. Date: Jun. 21, 2007 (54) (75) (73) (21) (22) METHOD AND APPARATUS FOR COMMUNICATING
US 20070139188A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0139188 A1 Ollis et al. (43) Pub. Date: Jun. 21, 2007 (54) (75) (73) (21) (22) METHOD AND APPARATUS FOR COMMUNICATING
(54) RAPID NOTIFICATION SYSTEM (52) US. Cl... 709/206. (57) ABSTRACT (75) Inventors: Anand Rajasekar, San Jose, CA
 US 20120303720A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2012/0303720 A1 Rajasekar et a]. (43) Pub. Date: NOV. 29, 2012 (54) RAPID NOTIFICATION SYSTEM (52) US. Cl......
US 20120303720A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2012/0303720 A1 Rajasekar et a]. (43) Pub. Date: NOV. 29, 2012 (54) RAPID NOTIFICATION SYSTEM (52) US. Cl......
(54) Applicant: (71) (72) Assignee: (73) (21) (22) (60)
 US 20140373140A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0373140 A1 Waters, JR. et al. (43) Pub. Date: Dec. 18, 2014 (54) (71) (72) (73) (21) (22) (60) DATA CENTER
US 20140373140A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0373140 A1 Waters, JR. et al. (43) Pub. Date: Dec. 18, 2014 (54) (71) (72) (73) (21) (22) (60) DATA CENTER
(54) SYSTEM AND METHOD FOR PROXYING Publication Classi?cation FEDERATED AUTHENTICATION PROTOCOLS (51) Int. Cl.
 US 20140245389A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0245389 A1 Oberheide et al. (43) Pub. Date: Aug. 28, 2014 (54) SYSTEM AND METHOD FOR PROXYING Publication
US 20140245389A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0245389 A1 Oberheide et al. (43) Pub. Date: Aug. 28, 2014 (54) SYSTEM AND METHOD FOR PROXYING Publication
US 20120066004A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0066004 A1 Lee (43) Pub. Date: Mar.
 US 212664A1 (19) United States (12) Patent Application Publication (1) Pub. o.: US 212/664 A1 Lee (43) Pub. Date: Mar. 15, 212 (54) (76) (21) (22) (6) METHOD AD SYSTEM FOR PERSOAL ISURACE COMPARISO AD
US 212664A1 (19) United States (12) Patent Application Publication (1) Pub. o.: US 212/664 A1 Lee (43) Pub. Date: Mar. 15, 212 (54) (76) (21) (22) (6) METHOD AD SYSTEM FOR PERSOAL ISURACE COMPARISO AD
US 20130300867A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0300867 A1 Yoder (43) Pub. Date: NOV.
 US 20130300867A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0300867 A1 Yoder (43) Pub. Date: NOV. 14, 2013 (54) METHOD AND APPARATUS FOR Publication Classi?cation INTERACTIVE
US 20130300867A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0300867 A1 Yoder (43) Pub. Date: NOV. 14, 2013 (54) METHOD AND APPARATUS FOR Publication Classi?cation INTERACTIVE
US 20100025463A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2010/0025463 A1 Daroga (43) Pub. Date: Feb.
 US 20100025463A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2010/0025463 A1 Daroga (43) Pub. Date: (54) DIGITAL TRANSMISSION SYSTEM (DTS) Publication Classi?cation FOR BANK
US 20100025463A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2010/0025463 A1 Daroga (43) Pub. Date: (54) DIGITAL TRANSMISSION SYSTEM (DTS) Publication Classi?cation FOR BANK
US 20130007621A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0007621 A1 Warren (43) Pub. Date: Jan.
 US 20130007621A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0007621 A1 Warren (43) Pub. Date: Jan. 3, 2013 (54) (76) (21) (22) (51) (52) SYSTEM FOR LEARNING NAMES OF
US 20130007621A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0007621 A1 Warren (43) Pub. Date: Jan. 3, 2013 (54) (76) (21) (22) (51) (52) SYSTEM FOR LEARNING NAMES OF
(12) United States Patent Halonen
 (12) United States Patent Halonen US006334053B1 () Patent N0.: (45) Date of Patent: Dec. 25, 2001 (54) PROCEDURE AND SYSTEM FOR PROVIDING AN ANSWERING SERVICE (75) Inventor: Mikko Halonen, Oulu (Fl) (73)
(12) United States Patent Halonen US006334053B1 () Patent N0.: (45) Date of Patent: Dec. 25, 2001 (54) PROCEDURE AND SYSTEM FOR PROVIDING AN ANSWERING SERVICE (75) Inventor: Mikko Halonen, Oulu (Fl) (73)
\ \ \ connection connection connection interface interface interface
 US 20140122910A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 20140122910 A1 Chiu et al. (43) Pub. Date: May 1, 2014 (54) RACK SERVER SYSTEM AND OPERATION Publication Classi?cation
US 20140122910A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 20140122910 A1 Chiu et al. (43) Pub. Date: May 1, 2014 (54) RACK SERVER SYSTEM AND OPERATION Publication Classi?cation
(12) United States Patent Munshi et al.
 US008806190B1 (12) United States Patent Munshi et al. (10) Patent N0.: () Date of Patent: Aug. 12, 14 (54) METHOD OF TRANSMISSION OF ENCRYPTED DOCUMENTS FROM AN EMAIL APPLICATION (76) Inventors: Amaani
US008806190B1 (12) United States Patent Munshi et al. (10) Patent N0.: () Date of Patent: Aug. 12, 14 (54) METHOD OF TRANSMISSION OF ENCRYPTED DOCUMENTS FROM AN EMAIL APPLICATION (76) Inventors: Amaani
US 20130254326Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0254326 A1 Weng et al. (43) Pub. Date: Sep.
 1 l US 20130254326Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0254326 A1 Weng et al. (43) Pub. Date: Sep. 26, 2013 (54) ELECTRONIC DEVICE, CLOUD STORAGE Publication
1 l US 20130254326Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0254326 A1 Weng et al. (43) Pub. Date: Sep. 26, 2013 (54) ELECTRONIC DEVICE, CLOUD STORAGE Publication
i VlRTUAL SERVER 1 \ VIRTUAL SERVER 2, _ 7
 US 20110225267A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2011/0225267 A1 OHASHI (43) Pub. Date: Sep. 15, 2011 (54) SERVER SYSTEM FOR VIEWING IN-HOUSE INFORMATION, AND METHOD
US 20110225267A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2011/0225267 A1 OHASHI (43) Pub. Date: Sep. 15, 2011 (54) SERVER SYSTEM FOR VIEWING IN-HOUSE INFORMATION, AND METHOD
US 201403 80094A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0380094 A1 Kota et al. (43) Pub. Date: Dec.
 US 201403 80094A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0380094 A1 Kota et al. (43) Pub. Date: (54) AVOIDING RESTART ON ERROR IN DATA (52) US. Cl. INTEGRATION CPC.....
US 201403 80094A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0380094 A1 Kota et al. (43) Pub. Date: (54) AVOIDING RESTART ON ERROR IN DATA (52) US. Cl. INTEGRATION CPC.....
(12) United States Patent Edelen
 US008285799B2 (12) United States Patent Edelen (10) Patent N0.: (45) Date of Patent: Oct. 9, 2012 (54) QUOTA-BASED ARCHIVING (75) Inventor: James Edelen, Renton, WA (U S) (73) Assignee: Microsoft Corporation,
US008285799B2 (12) United States Patent Edelen (10) Patent N0.: (45) Date of Patent: Oct. 9, 2012 (54) QUOTA-BASED ARCHIVING (75) Inventor: James Edelen, Renton, WA (U S) (73) Assignee: Microsoft Corporation,
(12> Ulllted States Patent (10) Patent N0.: US 6,591,288 B1 Edwards et al. (45) Date of Patent: Jul. 8, 2003
 ' ' US006591288B1 (12> Ulllted States Patent (10) Patent N0.: Edwards et al. (45) Date of Patent: Jul. 8, 2003 (54) DATA NETWORK ACCELERATED ACCESS EP 0837584 4/1998..... H04L/29/06 SYSTEM W0 WO 96/34340
' ' US006591288B1 (12> Ulllted States Patent (10) Patent N0.: Edwards et al. (45) Date of Patent: Jul. 8, 2003 (54) DATA NETWORK ACCELERATED ACCESS EP 0837584 4/1998..... H04L/29/06 SYSTEM W0 WO 96/34340
PINsafe Multifactor Authentication Solution. Technical White Paper
 PINsafe Multifactor Authentication Solution Technical White Paper Abstract PINsafe is a flexible authentication solution that offers a wide range of authentication models. The use of the patented one-time
PINsafe Multifactor Authentication Solution Technical White Paper Abstract PINsafe is a flexible authentication solution that offers a wide range of authentication models. The use of the patented one-time
US 20030108052A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2003/0108052 A1 Inoue et al. (43) Pub. Date: Jun.
 US 20030108052A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2003/0108052 A1 Inoue et al. (43) Pub. Date: Jun. 12, 2003 (54) SERVER LOAD SHARING SYSTEM (76) Inventors: Rumiko
US 20030108052A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2003/0108052 A1 Inoue et al. (43) Pub. Date: Jun. 12, 2003 (54) SERVER LOAD SHARING SYSTEM (76) Inventors: Rumiko
GATEWAY ' 8 8 8 o o o
 US 20130102274A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0102274 A1 Lauwaert (43) Pub. Date: Apr. 25, 2013 (54) SYSTEMS AND METHODS FOR MOBILE Publication Classi?cation
US 20130102274A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0102274 A1 Lauwaert (43) Pub. Date: Apr. 25, 2013 (54) SYSTEMS AND METHODS FOR MOBILE Publication Classi?cation
(12) United States Patent
 US008914855B2 (12) United States Patent Whitmyer, Jr. (10) Patent N0.: (45) Date of Patent: US 8,914,855 B2 Dec. 16, 2014 (54) PORTABLE PASSWORD KEEPER WITH INTERNET STORAGE AND RESTORE (75) Inventor:
US008914855B2 (12) United States Patent Whitmyer, Jr. (10) Patent N0.: (45) Date of Patent: US 8,914,855 B2 Dec. 16, 2014 (54) PORTABLE PASSWORD KEEPER WITH INTERNET STORAGE AND RESTORE (75) Inventor:
Levy Processing System 1_Q
 US 20130332350A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0332350 A1 Polk (43) Pub. Date: Dec. 12, 2013 (54) SYSTEMS AND METHODS FOR (52) US. Cl. PROCESSINIG LEIES
US 20130332350A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0332350 A1 Polk (43) Pub. Date: Dec. 12, 2013 (54) SYSTEMS AND METHODS FOR (52) US. Cl. PROCESSINIG LEIES
Back up information data by blocks, and generate backup data of each block
 US 20140046903A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0046903 A1 Ylll (43) Pub. Date: (54) DATA BACKUP AND RECOVERY METHOD Publication Classi?cation FOR MOBILE
US 20140046903A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0046903 A1 Ylll (43) Pub. Date: (54) DATA BACKUP AND RECOVERY METHOD Publication Classi?cation FOR MOBILE
Provisional application No. 61/082,685,?led on Jul. 22, 2008. the non-member private key are not generated. 116 Registered Log Archive
 US 20100023757Al (19) United States (12) Patent Application Publication (10) Pub. N0.2 US 2010/0023757 A1 Nguyen-Huu et al. (43) Pub. Date: (54) (75) (73) (21) (22) (60) METHODS AND SYSTEMS FOR SENDING
US 20100023757Al (19) United States (12) Patent Application Publication (10) Pub. N0.2 US 2010/0023757 A1 Nguyen-Huu et al. (43) Pub. Date: (54) (75) (73) (21) (22) (60) METHODS AND SYSTEMS FOR SENDING
US006282278B1 (12) United States Patent. (10) Patent N0.: US 6,282,278 B1 D0ganata et al. (45) Date 0f Patent: Aug. 28, 2001
 US006282278B1 (12) United States Patent (10) Patent N0.: US 6,282,278 B1 D0ganata et al. (45) Date 0f Patent: Aug. 28, 2001 (54) UNIVERSAL CONFERENCE CONTROL 5,758,281 * 5/1998 Emery et a1...... 455/428
US006282278B1 (12) United States Patent (10) Patent N0.: US 6,282,278 B1 D0ganata et al. (45) Date 0f Patent: Aug. 28, 2001 (54) UNIVERSAL CONFERENCE CONTROL 5,758,281 * 5/1998 Emery et a1...... 455/428
Ulllted States Patent [19] [11] Patent Number: 6,141,545
![Ulllted States Patent [19] [11] Patent Number: 6,141,545 Ulllted States Patent [19] [11] Patent Number: 6,141,545](/thumbs/27/11642488.jpg) US0061445A Ulllted States Patent [19] [11] Patent Number: Begeja et al. [45] Date of Patent: *Oct. 31, 2000 [54] METHOD AND SYSTEM FOR REMOTE 5,440,614 8/1995 Sonberg et a1...... 455/414 CALL FORWARDING
US0061445A Ulllted States Patent [19] [11] Patent Number: Begeja et al. [45] Date of Patent: *Oct. 31, 2000 [54] METHOD AND SYSTEM FOR REMOTE 5,440,614 8/1995 Sonberg et a1...... 455/414 CALL FORWARDING
United States. (12) Patent Application Publication (10) Pub. No.: US 2013/0268350 A1 Koonce et al. (43) Pub. Date: Oct. 10, 2013 (19) (54) (71) (72)
 (19) United States US 20130268350A1 (12) Patent Application Publication (10) Pub. No.: US 2013/0268350 A1 Koonce et al. (43) Pub. Date: Oct. 10, 2013 (54) (71) (72) (21) (22) (63) SYSTEM AND METHOD FOR
(19) United States US 20130268350A1 (12) Patent Application Publication (10) Pub. No.: US 2013/0268350 A1 Koonce et al. (43) Pub. Date: Oct. 10, 2013 (54) (71) (72) (21) (22) (63) SYSTEM AND METHOD FOR
USOOS 90761 1A Ulllted States Patent [19] [11 Patent Number: 5 907 611. 9 9 Dezonno et al. [45] Date of Patent: *May 25, 1999
![USOOS 90761 1A Ulllted States Patent [19] [11 Patent Number: 5 907 611. 9 9 Dezonno et al. [45] Date of Patent: *May 25, 1999 USOOS 90761 1A Ulllted States Patent [19] [11 Patent Number: 5 907 611. 9 9 Dezonno et al. [45] Date of Patent: *May 25, 1999](/thumbs/31/15320422.jpg) USOOS 90761 1A Ulllted States Patent [19] [11 Patent Number: 5 907 611 9 9 Dezonno et al. [45] Date of Patent: *May 25, 1999 [54] APPARATUS AND METHOD FOR 5,526,416 6/1996 Dezonno et al...... 379/266 IDENTIFYING
USOOS 90761 1A Ulllted States Patent [19] [11 Patent Number: 5 907 611 9 9 Dezonno et al. [45] Date of Patent: *May 25, 1999 [54] APPARATUS AND METHOD FOR 5,526,416 6/1996 Dezonno et al...... 379/266 IDENTIFYING
wanagamem transformation and management
 US 20120150919Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0150919 A1 Brown et al. (43) Pub. Date: Jun. 14, 2012 (54) (76) (21) (22) (60) (51) AGENCY MANAGEMENT SYSTEM
US 20120150919Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0150919 A1 Brown et al. (43) Pub. Date: Jun. 14, 2012 (54) (76) (21) (22) (60) (51) AGENCY MANAGEMENT SYSTEM
US 20130325834A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2013/0325834 A1 Simburg (43) Pub. Date: Dec.
 US 20130325834A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2013/0325834 A1 Simburg (43) Pub. Date: Dec. 5, 2013 (54) LINK ALLOCATION FOR SEARCH ENGINE (52) US. Cl. OPTIMIZATION
US 20130325834A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2013/0325834 A1 Simburg (43) Pub. Date: Dec. 5, 2013 (54) LINK ALLOCATION FOR SEARCH ENGINE (52) US. Cl. OPTIMIZATION
ID Director for Windows
 2016 ID Director for Windows FINGERPRINT AUTHENTICATION FOR MICROSOFT NETWORKS BIO-key International www.bio-key.com Introduction Fingerprint biometrics are commonly deployed by organizations seeking to
2016 ID Director for Windows FINGERPRINT AUTHENTICATION FOR MICROSOFT NETWORKS BIO-key International www.bio-key.com Introduction Fingerprint biometrics are commonly deployed by organizations seeking to
US 20130169877A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2013/0169877 A1 DANG (43) Pub. Date: Jul.
 US 20130169877A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2013/0169877 A1 DANG (43) Pub. Date: Jul. 4, 2013 (54) SUPPLEMENTAL AUDIO AND VISUAL (52) US. Cl. SYSTEM FORA VIDEO
US 20130169877A1 (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2013/0169877 A1 DANG (43) Pub. Date: Jul. 4, 2013 (54) SUPPLEMENTAL AUDIO AND VISUAL (52) US. Cl. SYSTEM FORA VIDEO
BlackBerry Enterprise Service 10. Secure Work Space for ios and Android Version: 10.1.1. Security Note
 BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
Access List: my-fw-rule
 US 200701573 02Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0157302 A1 Ottamalika et al. (43) Pub. Date: Jul. 5, 2007 (54) METHODS AND SYSTEMS FOR Publication Classi?cation
US 200701573 02Al (19) United States (12) Patent Application Publication (10) Pub. No.: US 2007/0157302 A1 Ottamalika et al. (43) Pub. Date: Jul. 5, 2007 (54) METHODS AND SYSTEMS FOR Publication Classi?cation
US 20050026694A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0026694 A1 Kelly et al. (43) Pub. Date: Feb.
 US 20050026694A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 20050026694 A1 Kelly et al. (43) Pub. Date: Feb. 3, 2005 (54) PRIZE REDEMPTION SYSTEM FOR GAMES EXECUTED OVER A
US 20050026694A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 20050026694 A1 Kelly et al. (43) Pub. Date: Feb. 3, 2005 (54) PRIZE REDEMPTION SYSTEM FOR GAMES EXECUTED OVER A
(54) RETARGETING RELATED TECHNIQUES (52) US. Cl... 705/1453 AND OFFERINGS. (75) Inventors: Ayrnan Farahat, San Francisco, (57) ABSTRACT
 US 20120271714Al (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2012/0271714 A1 Farahat et a]. (43) Pub. Date: Oct. 25, 2012 (54) RETARGETING RELATED TECHNIQUES (52) US. Cl......
US 20120271714Al (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2012/0271714 A1 Farahat et a]. (43) Pub. Date: Oct. 25, 2012 (54) RETARGETING RELATED TECHNIQUES (52) US. Cl......
(12) United States Patent Schlossman et al.
 (12) United States Patent Schlossman et al. US006320944B1 () Patent N0.: (45) Date of Patent: *Nov. 20, 2001 (54) (75) (73) (*) (21) (22) (63) (51) (52) (58) NTELLGENT CONFGURATON SERVER nventors: David
(12) United States Patent Schlossman et al. US006320944B1 () Patent N0.: (45) Date of Patent: *Nov. 20, 2001 (54) (75) (73) (*) (21) (22) (63) (51) (52) (58) NTELLGENT CONFGURATON SERVER nventors: David
(12) United States Patent (10) Patent N0.2 US 8,566,608 B2 Pemmaraju (45) Date of Patent: Oct. 22, 2013
 US008566608B2 (12) United States Patent (10) Patent N0.2 US 8,566,608 B2 Pemmaraju (45) Date o Patent: Oct. 22, 2013 (54) METHODS AND APPARATUS FOR (56) Reerences Cited SECURING KEYSTROKES FROM BEING INTERCEPTED
US008566608B2 (12) United States Patent (10) Patent N0.2 US 8,566,608 B2 Pemmaraju (45) Date o Patent: Oct. 22, 2013 (54) METHODS AND APPARATUS FOR (56) Reerences Cited SECURING KEYSTROKES FROM BEING INTERCEPTED
MaaS360 Mobile Enterprise Gateway
 MaaS360 Mobile Enterprise Gateway Administrator Guide Copyright 2014 Fiberlink, an IBM Company. All rights reserved. Information in this document is subject to change without notice. The software described
MaaS360 Mobile Enterprise Gateway Administrator Guide Copyright 2014 Fiberlink, an IBM Company. All rights reserved. Information in this document is subject to change without notice. The software described
(12) United States Patent (10) Patent No.: US 7,142,661 B2 Erhart et al. (45) Date of Patent: Nov. 28, 2006
 US007142661B2 (12) United States Patent (10) Patent No.: US 7,142,661 B2 Erhart et al. (45) Date of Patent: Nov. 28, 2006 (54) METHOD AND APPARATUS FOR 2003/0061029 A1* 3/2003 Shaket..... 704/9 INTERACTIVE
US007142661B2 (12) United States Patent (10) Patent No.: US 7,142,661 B2 Erhart et al. (45) Date of Patent: Nov. 28, 2006 (54) METHOD AND APPARATUS FOR 2003/0061029 A1* 3/2003 Shaket..... 704/9 INTERACTIVE
(73) Assignee: Realovation Holdings, LLC d/b/a/ systems methods and Software? for improving Communic?
 US 20130297442A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0297442 A1 Simons et al. (43) Pub. Date: NOV. 7, 2013 (54) SYSTEM AND METHOD FOR ROUTING AND Publication Classi?cation
US 20130297442A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0297442 A1 Simons et al. (43) Pub. Date: NOV. 7, 2013 (54) SYSTEM AND METHOD FOR ROUTING AND Publication Classi?cation
(54) METHODS AND SYSTEMS FOR FINDING Publication Classi?cation CONNECTIONS AMONG SUBSCRIBERS TO AN EMAIL CAMPAIGN (51) Int- Cl
 US 201403 79420A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0379420 A1 Chestnut et al. (43) Pub. Date: Dec. 25, 2014 (54) METHODS AND SYSTEMS FOR FINDING Publication
US 201403 79420A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0379420 A1 Chestnut et al. (43) Pub. Date: Dec. 25, 2014 (54) METHODS AND SYSTEMS FOR FINDING Publication
US 20030093692A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2003/0093692 A1. Porras (43) Pub. Date: May 15, 2003
 l ll l l US 20030093692A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2003/0093692 A1 Porras (43) Pub. Date: (54) GLOBAL DEPLOYMENT OF HOST-BASED Publication Classi?cation
l ll l l US 20030093692A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2003/0093692 A1 Porras (43) Pub. Date: (54) GLOBAL DEPLOYMENT OF HOST-BASED Publication Classi?cation
POTENTIAL. SC DA Il'JA N INTERFACE m. (21) Appl. No.: 11/037,604
 US 20050125439A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0125439 A1 Nourbakhsh et al. (43) Pub. Date: Jun. 9, 2005 (54) METHOD AND APPARATUS FOR MULTI-CONTACT SCHEDULING
US 20050125439A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0125439 A1 Nourbakhsh et al. (43) Pub. Date: Jun. 9, 2005 (54) METHOD AND APPARATUS FOR MULTI-CONTACT SCHEDULING
(12) United States Patent (10) Patent N0.: US 8,326,445 B2 Baak et al. (45) Date of Patent: Dec. 4, 2012
 US008326445B2 (12) United States Patent (10) Patent N0.: Baak et al. (45) Date of Patent: Dec. 4, 2012 (54) MESSAGE STRING CORRESPONDENCE 2003/0046160 A1 * 3/2003 PaZ-Pujalt et al...... 705/14 2003/0120726
US008326445B2 (12) United States Patent (10) Patent N0.: Baak et al. (45) Date of Patent: Dec. 4, 2012 (54) MESSAGE STRING CORRESPONDENCE 2003/0046160 A1 * 3/2003 PaZ-Pujalt et al...... 705/14 2003/0120726
disclosed. The method mcludes recervmg information corre
 US 20140039935A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0039935 A1 RIVERA (43) Pub. Date: Feb. 6, 2014 (54) INSURANCE VERIFICATION SYSTEM Publication Classi?cation
US 20140039935A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0039935 A1 RIVERA (43) Pub. Date: Feb. 6, 2014 (54) INSURANCE VERIFICATION SYSTEM Publication Classi?cation
US 20070268144Al (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2007/0268144 A1 D0b0sz (43) Pub. Date: NOV.
 US 20070268144Al (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2007/0268144 A1 D0b0sz (43) Pub. Date: NOV. 22, 2007 (54) WRISTBAND READER APPARATUS FOR (52) US. Cl...... 340/572.8;
US 20070268144Al (19) United States (12) Patent Application Publication (10) Pub. N0.: US 2007/0268144 A1 D0b0sz (43) Pub. Date: NOV. 22, 2007 (54) WRISTBAND READER APPARATUS FOR (52) US. Cl...... 340/572.8;
Content Provider Artist?zgiputer Rgcord L1a4t6e
 US 20050154608A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0154608 A1 Paulson et al. (43) Pub. Date: Jul. 14, 2005 (54) DIGITAL MEDIA DISTRIBUTION AND TRADING SYSTEM
US 20050154608A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2005/0154608 A1 Paulson et al. (43) Pub. Date: Jul. 14, 2005 (54) DIGITAL MEDIA DISTRIBUTION AND TRADING SYSTEM
Secure Network Communications FIPS 140 2 Non Proprietary Security Policy
 Secure Network Communications FIPS 140 2 Non Proprietary Security Policy 21 June 2010 Table of Contents Introduction Module Specification Ports and Interfaces Approved Algorithms Test Environment Roles
Secure Network Communications FIPS 140 2 Non Proprietary Security Policy 21 June 2010 Table of Contents Introduction Module Specification Ports and Interfaces Approved Algorithms Test Environment Roles
T0 THE USER EE JEQE, THE REWRWTEN CQNTENT includeng A REFERENCE N132
 US 20130091305A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0091305 A1 Freeman et al. (43) Pub. Date: Apr. 11, 2013 (54) IDENTIFYING USERS THROUGH A PROXY (52) US. Cl.
US 20130091305A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0091305 A1 Freeman et al. (43) Pub. Date: Apr. 11, 2013 (54) IDENTIFYING USERS THROUGH A PROXY (52) US. Cl.
(54) SYSTEM AND METHOD FOR REAL-TIME Publication Classi?cation TRANSACTIONAL DATA OBFUSCATION (51) Int Cl
 US 20120030165A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0030165 A1 Guirguis et al. (43) Pub. Date: Feb. 2, 2012 (54) SYSTEM AND METHOD FOR REAL-TIME Publication Classi?cation
US 20120030165A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2012/0030165 A1 Guirguis et al. (43) Pub. Date: Feb. 2, 2012 (54) SYSTEM AND METHOD FOR REAL-TIME Publication Classi?cation
7714 Evaluation 7 logic
 US 20140229045A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0229045 A1 Borchers et al. (43) Pub. Date: Aug. 14, 2014 (54) (75) (73) (21) (22) (86) (30) METHOD FOR OPERATING
US 20140229045A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2014/0229045 A1 Borchers et al. (43) Pub. Date: Aug. 14, 2014 (54) (75) (73) (21) (22) (86) (30) METHOD FOR OPERATING
McGary (43) Pub. Date: Jun. 14, 2007
 US 20070133525Al (19) United States (12) Patent Application Publication (10) Pub. No.: McGary (43) Pub. Date: Jun. 14, 2007 (54) SYSTEM AND METHOD FOR Publication Classi?cation FACILITATING VOIP COMMUNICATIONS
US 20070133525Al (19) United States (12) Patent Application Publication (10) Pub. No.: McGary (43) Pub. Date: Jun. 14, 2007 (54) SYSTEM AND METHOD FOR Publication Classi?cation FACILITATING VOIP COMMUNICATIONS
US 2011023 8247A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2011/0238247 A1 Yen et al. (43) Pub. Date: Sep.
 US 2011023 8247A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2011/0238247 A1 Yen et al. (43) Pub. Date: Sep. 29, 2011 (54) PERSONAL, GREEN-ENERGY, Publication Classi?cation
US 2011023 8247A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2011/0238247 A1 Yen et al. (43) Pub. Date: Sep. 29, 2011 (54) PERSONAL, GREEN-ENERGY, Publication Classi?cation
US 20130073440A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0073440 A1 Chen (57)
 US 20130073440A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0073440 A1 Chen (43) Pub. Date: Mar. 21, 2013 (54) PAYROLL SYSTEM AND METHOD Publication Classi?cation (76)
US 20130073440A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2013/0073440 A1 Chen (43) Pub. Date: Mar. 21, 2013 (54) PAYROLL SYSTEM AND METHOD Publication Classi?cation (76)
(12) United States Patent (10) Patent N0.: US 6,192,121 B1 Atkinson et al. (45) Date of Patent: Feb. 20, 2001
 US006192121B1 (12) United States Patent (10) Patent N0.: US 6,192,121 B1 Atkinson et al. (45) Date of Patent: Feb. 20, 2001 (54) TELEPHONY SERVER APPLICATION 5,101,425 3/1992 Darland et a1...... 379/34
US006192121B1 (12) United States Patent (10) Patent N0.: US 6,192,121 B1 Atkinson et al. (45) Date of Patent: Feb. 20, 2001 (54) TELEPHONY SERVER APPLICATION 5,101,425 3/1992 Darland et a1...... 379/34
Ulllted States Patent [19] [11] Patent Number: 5,859,416
![Ulllted States Patent [19] [11] Patent Number: 5,859,416 Ulllted States Patent [19] [11] Patent Number: 5,859,416](/thumbs/30/14417385.jpg) US005859416A. Ulllted States Patent [19] [11] Patent Number: Gatto [] Date of Patent: *Jan. 12, 1999 [54] FUEL PUMP SYSTEM WITH AUTOMATED 5,144,1 9/1992 Yoshida..... 2/379 TRANSACTION PROCESSING 5,175,416
US005859416A. Ulllted States Patent [19] [11] Patent Number: Gatto [] Date of Patent: *Jan. 12, 1999 [54] FUEL PUMP SYSTEM WITH AUTOMATED 5,144,1 9/1992 Yoshida..... 2/379 TRANSACTION PROCESSING 5,175,416
llllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllilll
 llllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllilll USOO5l8l239A United States Patent 19 [11] Patent Number: 5 9181 9239 J olissaint [45] Date of Patent: Jan. 19, 1993 [54] CALL
llllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllllilll USOO5l8l239A United States Patent 19 [11] Patent Number: 5 9181 9239 J olissaint [45] Date of Patent: Jan. 19, 1993 [54] CALL
(12) Ulllted States Patent (10) Patent N0.: US 8,028,070 B2 Boyd et al. (45) Date of Patent: Sep. 27, 2011
 US008028070B2 (12) Ulllted States Patent (10) Patent N0.: Boyd et al. (45) Date of Patent: Sep. 27, 2011 (54) SYNCHRONIZING TASKS BETWEEN 2002/0065926 A1 * 5/2002 Hackney et al...... 709/231 SERVERS 2004/0221323
US008028070B2 (12) Ulllted States Patent (10) Patent N0.: Boyd et al. (45) Date of Patent: Sep. 27, 2011 (54) SYNCHRONIZING TASKS BETWEEN 2002/0065926 A1 * 5/2002 Hackney et al...... 709/231 SERVERS 2004/0221323
/12 [-16. U CIUUU Cl UUCIEI U CICIUU. (12) Patent Application Publication (10) Pub. No.: US 2002/0193094 A1 Lawless et al.
 (19) United States US 20020193094A1 (12) Patent Application Publication (10) Pub. No.: US 2002/0193094 A1 Lawless et al. (43) Pub. Date: (54) METHOD AND SYSTEM FOR DOWNLOADNG SOFTWARE PRODUCTS DRECTLY
(19) United States US 20020193094A1 (12) Patent Application Publication (10) Pub. No.: US 2002/0193094 A1 Lawless et al. (43) Pub. Date: (54) METHOD AND SYSTEM FOR DOWNLOADNG SOFTWARE PRODUCTS DRECTLY
