Adapting Embedded Systems Framework to Provide Virtualization: the Hellfire Case Study
|
|
|
- Clementine Heath
- 10 years ago
- Views:
Transcription
1 Adapting Embedded Systems Framework to Provide Virtualization: the Hellfire Case Study Alexandra Aguiar, Sérgio J. Filho, Felipe G. Magalhães, Fabiano Hessel Faculty of Informatics PUCRS Av. Ipiranga 6681, Porto Alegre, Brazil {sergio.johann, Abstract In this paper, we present how it is possible to adapt existing development solutions to provide embedded virtualization advantages. To do so, we use the Hellfire Framework, which offers an integrated tool-flow in which design space exploration (DSE), OS customization and static and dynamic application mapping are highly automated. In this case, the designer can develop embedded sequential and parallel applications while evaluating how design decisions impact in the overall system behavior including analysis regarding whether virtualization usage presents benefits towards the non-virtualized solution. Keywords MPSoC, Embedded Systems Design, Embedded Virtualization I. INTRODUCTION Embedded systems, critical and non-critical, have increasingly become part of people s lives being present in day-by-day life issues, like health-care electronics, automotive industry and entertainment devices. Over the years, Multiprocessors Systemon-Chip (MPSoC) have become the most viable choice to implement them [1]. This trend combined with the growing complexity of real-time (RT) constrained embedded systems, has a major impact in the entire design and implementation of embedded systems. Additionally, characteristics present earlier only in generalpurpose systems are each more common in embedded systems, which affects directly their design. In this context, we can highlight their growing functionality as the greatest change, affecting dramatically their design and increasing the complexity of their software. Nowadays, it is even common to run general purpose applications in some embedded systems as well as to use applications written by developers that have little or no knowledge at all about the embedded systems constraints [2]. On the other hand, some typical embedded systems constraints persist and need to be considered. For example, timing constrained MPSoCs with short energy consumption budgets and strict time-to-market need software deployment and test on the target hardware architecture to be performed but this usually is a difficult and time consuming approach. Ergo, it is needed alternative methodologies where the final hardware prototype has equivalence of the code with system s hardware and software simulator and emulator. Aiming to improve the software design quality, we propose the use of embedded virtualization, which has gained attention over the last few years [3], [4], [5]. Thus, this paper presents adaption possibilities of the Hellfire Framework (HellfireFW) to allow embedded virtualization to be better explored. HellfireFW is an environment for the design of embedded systems applications which follows its own design flow where an MPSoC emulator is employed and over which a specific RTOS solution - the HellfireOS - is executed [6]. Still, HellfireFW improves the overall system quality, since it helps the designer to perform design space exploration through the customization and simulation of different HW/SW scenarios. The remainder of the paper is organized as it follows. The next section shows some related work. Section 3 shows virtualization concepts. Section 4 presents the Hellfire Framework followed by Section 5 where virtualization is considered in the framework. Then, Section 6 concludes the paper and presents some future work. II. RELATED WORK Design Related. Design space exploration can be achieved in several ways, including co-design based solutions which aim to create a suitable platform architecture [7]. It usually starts at system level, in which the final system division into hardware and software has not been completed yet. After the initial steps, the functional verification can be made through co-simulation mechanisms which help in both system s validation and refinement. Common embedded systems constraints, such as a tight time-to-market and the high complexity of current designs, lead to simulators in different abstraction levels, from Instruction Set Simulators (ISS) to system-level descriptions, usually implemented in SystemC or SpecC. In these simulators, usually both hardware and software models are executed in order to analyze the system behavior at an earlier development stage. In this context, several works [8], [9], [10] and [11] show some effort in modeling the RTOS at a higher level of abstraction. The main issue with this approach is that when the design is refined, although the RTOS model can be translated automatically into software services, usually a widely adopted RTOS is preferred, which prevents the results taken during the modeling to be accurate when the real hardware implementation is finished. [12] present the code equivalence problem, that is, if the code executed by the simulated system is different from the target hardware code, the system s behavior can be different from what was simulated. Still wrong design choices can be made. Moreover, when using high level simulation approaches, usually the system timing behavior is either not taken into account or is not completely accurate [13]. Simulators where timing of the target architecture is not accurately replicated are not allowed to precisely model critical and parallel embedded systems, as MP- SoCs.
2 These researches are valid since they help the designer to refine the HW/SW partition. Unfortunately, this validation is limited due to the code equivalence problem and restrictions of the assessment of the system timing properties. As opposed to some works shown previously, we use ISSs in our study. Although it represents a lower simulation speed, it allows the use of the same application code both in the simulation level and in the target architecture, thus dealing with the code equivalence problem. Virtualization Related. EmbeddedXEN Project. EmbeddedXEN is an academic project of the XEN.org research group where the main target concerns embedded real-time applications. Its hypervisor is executed in ARM cores and the EmbeddedXEN project provides to ARM developers a single multikernel binary image which includes XEN, Linux, minios and XenomaiRT extension adapted to run onto embedded systems. Virtualization and isolation mechanisms are fully relied on the XEN hypervisor for general purpose computers. The main goal of this project is to provide viability and performance evaluation of the embedded virtualization. It is an open-source project and it can be used in any device, although the Server Xen version is not open-source which can restrict its use [14]. OKL4. Implemented by OK Labs (Open Kernel Labs), it is an L4 family microkernel commercially distributed hypervisor with low overhead rates [3]. It has a high performance Inter- Process Communication (IPC) message exchange mechanism, which helps the low overheaded virtualization. A system call that causes a trap triggered by any virtual machine, calls the microkernel exception manager, converting this event into an IPC message to the guest OS. The client deals with this process as a normal system call and the answer is returned through another IPC message [3]. Wind River Hypervisor. It focuses on high performance, small footprint, determinism, low latency and high reliability. It is highly optimized for and integrated with VxWorks and Wind River Linux although it supports other operating systems. In terms of processor, supports single and multicore processors based on Intel and PowerPC architectures and its solution integrates with VxWorks and Wind River Linux. It also enables devices to be assigned to virtual boards as it provides device and memory protection between virtual boards [15]. VirtualLogix VLX. Hypervisor that decouples hardware management (intended for ARM and Intel architectures) and application environments (Android, Linux, proprietary, Symbian, Windows), thus enabling separation of design and functionality concerns. This allows OS/device independence and fault tolerance with minimal overhead, as well as improved performance for multimedia and gaming and enhanced device security through isolation [16]. Trango. It provides a thin layer of code that allows system designers greater flexibility when extending the functionality of an existing system or using multiple OSs. Only a single CPU is then needed to keep the OS and multiple environments separate, so the designer can create trusted areas where secure processes (such as key management or secure boot) can run without adding another CPU [17]. XtratuM. XtratuM is an open source hypervisor specially designed for embedded real-time systems available for x86, PowerPC, MIPS and recently for LEON2 (SPARC v8) processors. It is a hypervisor designed for embedded systems to meet safety critical real-time requirements and provides a framework to run several operating systems in a robust partitioned environment. XtratuM can be used to build a MILS (Multiple Independent Levels of Security) architecture [18]. Analysis. Many embedded hypervisors have emerged within the last few years. Although they have several qualities, our proposal aims to integrate a hypervisor intended for real-time MPSoCs in a well-structured design tool (Hellfire Framework) and it respects a design flow that helps to improve software quality. Also, it allows the use of simpler RISC processors, such as MIPS-based ones. III. VIRTUALIZATION BASIC CONCEPTS Virtualization allows a single physical computer to host multiple virtual machines, each being isolated from one another and it dates back more than 30 years [19]. Several advantages arise from its use, such as the possibility of running different operating systems in the same physical hardware. Still, if a virtual machine fails, the other ones can be kept safe at a reasonable cost [3]. Although it causes a single point of failure, since many servers can be placed at a unique hardware machine, one of the main uses of virtualization lies in enterprise IT. Still, virtualization is considered safer because most of service interrupts are caused by software failures, usually, by the operating system which tends to be big enough so that maintenance is harder [20]. So, the idea is to use simpler and more efficient kernel level software to avoid safety problems. The hypervisor - the main virtualization component - usually is at least two orders of magnitude smaller than general purpose OSs, therefore, it is less likely to have failures [20]. Commonly, two approaches are used to implement the hypervisor which is also known as Virtual Machine Monitor (VMM): In hypervisor type 1, also known as hardware level virtualization, the hypervisor itself can be considered as an operating system, since it is the only piece of software that works in kernel mode, like depicted in Figure 1. Its main task is to manage multiple copies of the real hardware - the virtual boards (virtual machines or domains) - just like an OS manages multitasking. Fig. 1. Hypervisor Type 1 Type 2 hypervisors, also known as operating system level virtualization, depicted in Figure 2, are implemented such that the hypervisor itself can be compared to another user application that simply interprets the guest machine ISS.
3 In several aspects, the hypervisor can be considered similar to an operating system. So, some concepts regarding OSs implementation need to be highlighted. Classic studies of Popek and Goldberg [21] introduce a classification for the instructions of an ISA (Instruction Set Architecture) into three different groups: 1. privileged instructions: those that trap when used in user mode and do not trap if used in kernel mode; 2. control sensitive instructions: those that attempt to change the configuration of resources in the system, and; 3. behavior sensitive instructions: those whose behavior or result depends on the configuration of resources (the content of the relocation register or the processor s mode). Also, Popek and Goldberg declared that in order to virtualize a given machine, sensitive instructions must be a subset of the privileged instructions. Unfortunately, this is not a reality in many processors, such as Intel s x86 family and the common solution in this case, is to adopt processor s hardware support. Intel s support is named as VT (Virtualization Technology) and AMD s named as SVM (Secure Virtual Machine). In spite of it, hardware support is hard to be achieved for embedded systems yet, so other options have to be considered at the present time. In the remainder of the paper only hardware level (hypervisor type 1) is considered. In this type of virtualization, when no hardware support is available, the hypervisor is at charge of translating instructions whenever the virtual domain attempts to execute a privileged instruction (I/O request, memory write etc), which causes a trap into the hypervisor, being known as pure virtualization. This is often a very expensive way of dealing with virtual machines [22]. Still, an alternative known as impure virtualization can be used as it requires that sensitive instructions (those that require a trap into the hypervisor) are removed from the code executing in the virtual machine. This can be done either at compile time, by a technique called pre-virtualization or by binary code rewriting, where the executable code is scanned in order to replace such instructions. The main issue is that both approaches can cause huge performance losses. Finally, para-virtualization it a technique that replaces sensitive instructions of the original kernel code by explicit hypervisor calls (also known as hypercalls). The goal of paravirtualization is to reduce the problems encountered when dealing with different privilege levels. Usually, a scheme referred to as protection rings is used and it guarantees that the lower level rings (Ring 0, for instance) holds the highest privileges. So, most of OSs are executed in Ring 0, thus being able to interact directly with the physical hardware. In this case, when the hypervisor is adopted, it becomes the only piece of software to be executed in Ring 0, bringing severe consequences for the guest OSs: they are no longer executed in Ring 0, instead, run in Ring 1, with fewer privileges. This problem, known as ring de-privileging is depicted in Figure 3. Fig. 2. Hypervisor Type 2 Fig. 3. Ring de-privileging caused by the hypervisor IV. HELLFIRE SYSTEM The Hellfire System (HFS) is an academic project born at the Embedded Systems Group (GSE) of the Pontifical Catholic University (PUCRS), in Brazil. The project provides its own design flow that comprehends different abstraction levels, from C application development to FPGA prototyping. This design flow is supported by several tools and modules that compose the Hellfire Framework (HFFW). From a single processor point of view, the designer can develop the application C code and run it over the Hellfire Operating System (HellfireOS), which is a highly configurable realtime modular micro-kernel based OS. From the platform point of view, the designer can add up to 128 processors to the system, configure each one of them and, by using the HellfireOS API, develop parallel embedded applications which are able to exchange data and even able to migrate tasks. Currently, only MIPS based processors are allowed. A. HellfireOS The HellfireOS (HFOS) [6] is a real-time operating system (RTOS) developed in order to ensure maximum flexibility in its configuration and allow a high level platform customization. In order to allow such feature, HFOS was implemented in a modular way, where each module corresponds to some specific functionality. Figure 4 depicts the kernel modular organization. All hardware-specific functions are defined in the first layer, known as HAL (Hardware Abstraction Layer) and the ukernel lies just above it. The communication, migration, memory management and mutual exclusion drivers, as well the API are placed over the ukernel layer. The user applications belong to the top layer.
4 B. Hellfire Framework Fig. 4. HellfireOS Structure Due to its modular implementation, HellfireOS is easily portable to others architectures, requiring only the rewrite of hardware-dependent functions, such as the interrupt service, its initialization routine and the context switch. In order to decrease the kernel final size, allowing the HFOS usage even in architectures with severe memory limitations, parameters such as users tasks maximum number, stack and heap size and drivers usage, are configurable. The users applications are written using basic C programming language and the HellfireOS API. In Figure 5 a user task example that prints the CPU usage in the standard output of the system is shown. Fig. 5. Task Example Another configurable parameter is the activation bit used by the timing register, which determines the system tick size. The tick size corresponds to the minimum periodic timing unit of the system. This unit varies from 0.32ms to 83.88ms. Figure 6 shows the relation between the processor clock frequency rate and the activation bit. Fig. 6. Tick Time x Core Frequency The Hellfire Framework (HFFW) [6] allows a complete deployment and test of parallel embedded applications, defining the HW/SW architecture to be employed by the designer. The HFFW is divided in three modules as it follows, which are discussed throughout this section. HellfireOS, discussed previously in Section 4-A; N-MIPS MPSoC Simulator, and; architecture builder. The N-MIPS MPSoC Simulator is an Instruction-Set Simulator (ISS) based on MIPS-like [23] cores. It was also written in C and provides simulation of up to 128 processing cores. A very important feature is the possibility to prototype in FPGA the same resulting image file used during the simulation, which increases the chances of prototyping success after the simulation. The last highlighted module, named architecture builder is used to specify the target architecture and to configure all the HellfireOS parameters. The HellfireFW design flow is basically divided in three steps: the application design, the project creation and simulation/refinement, explained in the remainder of this section. Application Design. The first step of the design flow is the development of an application implemented in C language and manually divided into a set of tasks. These tasks are defined as n-uples (id i, r i, W CET i, D i, P i ) and the parameters stand for identification, release time, worst case execution time, deadline and period of each task respectively. HellfireFW Project Creation. After the application design, the designer must create a project in HFFW. This step corresponds to the architecture design and configuration. The designer must define the initial hardware architecture, specifying the number of processors and their frequencies and configuring the HellfireOS parameters, as presented in Section 4-A. After that, the mapping of the tasks along the processors must be performed. This mapping is done manually and is based on the designer s experience. As the output of this step, an MPSoC platform is expected, having a given number of processors, a personalized instance of HellfireOS on each processor and a static task mapping. Simulation and Refinement. When the designer triggers a simulation, the MPSoC ISS Simulator is activated. After the simulation is completed, several reports are presented to the designer both in textual and graphical way. The textual reports are the following: standard output of each processor; report with all Plasma instructions used, the number of times that each was used and an usage percentage of each group (logical, arithmetic, etc) of instructions; an energy consumption summary, based on [24]; report containing the main characteristics of the system, such as deadlines misses and CPU load, and; individual report of the cycle to cycle operation of each processors. All information contained on the system stack is shown in this report.
5 V. ADAPTING HELLFIREFW TO VIRTUALIZATION This section depicts the main changes in the Hellfire Framework design flow and the main advantages to use virtualization. We use the Virtual-Hellfire Hypervisor (VHH) architecture [5], based in the HellfireOS structure. The main advantages of VHH are: temporal and spatial isolation among domains (each domain contains its own OS); real-time scheduling policy for domain scheduling; deterministic hypervisor system calls (hypercalls). Figure 7 depicts the Virtual-Hellfire Hypervisor structure. In this figure, the hardware continues to provide the basic services as timer and interrupt but they are managed by the hypervisor, which provides hypercalls for the different domains, allowing them to perform privileged instructions. Fig. 7. Virtual-Hellfire Hypervisor Domain structure In terms of memory management, in MMU-less processors a possible choice is to implement a software virtual memory management, as proposed in [25]. Another viable strategy is to use a fixed partition memory scheme. In this case, the required amount of memory is allocated to each domain at boot (or load) time, meaning that its size cannot grow or shrink at run time. If the application code of the guest OS of a given domain requires dynamic memory (such as with malloc or free C primitives), the heap needs to be managed by the domain s code itself. For now, VHH uses this second option (fixed partition memory), as we can see in Figure 8, where each processor (Processing Element - PE, in the figure) of the MPSoC has its own Local Memory (LM). This memory is divided according to the amount of partitions that this processor will hold. The internal architecture of HellfireOS had to be modified to guarantee the use of virtualization. As a matter of fact, we kept some of the original features and took advantage of its highly modular implementation by adding the necessary modules to provide virtualization. Thus, Virtual-Hellfire Hypervisor is implemented based on the following layers: Hardware Abstraction Layer - HAL, responsible for implementing the set of drivers that manage the mandatory hardware, like processor, interrupts, clock, timers etc; Fig. 8. Virtual-Hellfire Hypervisor Memory Management Kernel API and Standard C Functions, which are not available to the partitions; Virtualization layer, which provides the services required to support virtualization and para-virtualization services. The hypercalls are implemented in this layer. In this new layer responsible for allowing virtualization to be used, there are some mandatory modules, such as: domain manager, responsible for domain creation, deletion, suspension etc; domain scheduler, responsible for scheduling domains in a single processor; interrupt manager, that handles hardware interrupts and traps. It is also in charge of triggering virtual interrupt and traps to domains; hypercall manager, responsible for handling calls made from domains, being analogous to the use of system calls in conventional operating systems; system clock provider, in which two clocks per domain are implemented: one that only advances while the domain is being executed (virtual) and a real, counted from the boot time. timer provider, similar to clock implementation, provides virtual and real timers, both accessible by hypercalls; memory manager, divided in virtual and physical management, according to the underlying hardware; system output facility, where all messages are queued and can be redirected to hardware peripherals, such as a serial port. A very interesting point of the VHH is the use of an MPSoC as underlying hardware. We assume the use of a Symmetric MultiProcessor (SMP) and the hypervisor acts as a MultiProcessor RTOS (MP-RTOS). The hypervisor is aware of the several domains and respects their own scheduling policies. Each processor has its ready task queue, which can contain tasks from different virtual domains. For each processor, the highest-priority task in the ready queue is executed. To avoid starvation of non real-time tasks (when allocated in the same processor of real-time tasks), it is possible to adopt a scheduling policy that guarantees the execution of best-effort tasks, such as R-EDF [26]. The mapping of virtual domains onto real processors is done at design time. For now, it is the designer s responsibility to associate virtual domains and real processors. In the future, we intend to use virtualization even as a load balancing solution, where, dynamically, virtual domains can migrate among the several processors of the MPSoC to improve a given measure, as performance or energy consumption. When more than one do-
6 main is mapped for a single processor, the scheduling among domains occurs according to a fixed priority scheduling. Then, domains are scheduled by the hypervisor considering its priority level. Since HellfireOS is integrated in the Hellfire Framework with several simulation facilities, VHH is also integrated in it and requires the designer to choose whether virtualization is enabled. In this case, although user-transparent, the design flow presented by Figure 9 is employed. This flow starts with the configuration of the VHH, where the number of domains is informed and the VHH core is generated. Following, each of the desired domains is configured in a very similar way Hellfire Framework used to do with non-virtual HellfireOS edition: application tasks were added and put together with the OS image. Finally, all system is assembled and executed by an ISS-like (Instruction Set Simulator) simulator. Fig. 9. VHH Integrated in the Hellfire Framework VI. CONCLUDING REMARKS AND FUTURE WORK Embedded systems are becoming more complex and new design solutions need to be investigated. In this paper the HellFire framework was presented. This framework helps to develop, validate and test embedded systems applications. The solution provides an easy way to develop and validate embedded software in a given platform and also to perform HW/SW design space exploration allowing the designer to combine different SW mapping possibilities onto several HW platform architectures, as well as several OS configurations to analyze different aspects of the system. Still, we discuss the use of a virtualization methodology. We demonstrate the usefulness of virtualization in embedded systems design and how it can be applied in current design flows. Future work includes measuring and getting comparison results for performance, area and energy consumption with nonvirtualized systems. Still, we want to measure precisely the overhead of the proposal besides improving the methodology itself, especially regarding memory and I/O management as well as to improve these features implementation quality. ACKNOWLEDGMENT The authors gratefully acknowledge the INCT-SEC support in the form of scholarships and grants. The authors acknowledge the support granted by CNPq and FAPESP to the INCT-SEC (National Institute of Science and Technology Embedded Critical Systems Brazil), processes / and 08/ REFERENCES [1] Ahmed Jerraya, Hannu Tenhunen, and Wayne Wolf, Multiprocessor systems-on-chips, Computer, vol. 38, no. Issue 7, pp , July [2] Y. Zorian and E. Marinissen, System chip test - how will it impact your design, in DAC Design Automation Conference, Las Vegas, EUA, Jun 2000, ACM Press. [3] G. Heiser, Hypervisors for consumer electronics, jan. 2009, pp [4] A. Aguiar and F. Hessel, Embedded systems virtualization: The next challenge?, in Rapid System Prototyping (RSP), st IEEE International Symposium on, 2010, pp [5] A. Aguiar and F. Hessel, Virtual hellfire hypervisor: Extending hellfire framework for embedded virtualization support, in To appear in Quality Electronic Design (ISQED), th International Symposium on, [6] A. Aguiar, S.J. Filho, F.G. Magalhaes, T.D. Casagrande, and F. Hessel, Hellfire: A design framework for critical embedded systems applications, in Quality Electronic Design (ISQED), th International Symposium on, 2010, pp [7] W. Wolf, A decade of hardware/software codesign, Computer, vol. 36, no. 4, pp , April [8] A. Gerstlauer, Haobo Yu, and D.D. Gajski, Rtos modeling for system level design, in Design, Automation and Test in Europe Conference and Exhibition, 2003, 2003, pp [9] R. Le Moigne, O. Pasquier, and J.-P. Calvez, A generic rtos model for real-time systems simulation with systemc, in Design, Automation and Test in Europe Conference and Exhibition, Proceedings, Feb. 2004, vol. 3, pp Vol.3. [10] H. Posadas, J. Adamez, P. Sanchez, E. Villar, and F. Blasco, Posix modeling in systemc, in Design Automation, Asia and South Pacific Conference on, Jan. 2006, pp. 6 pp.. [11] A. Shaout, K. Mattar, and A. Elkateeb, An ideal api for rtos modeling at the system abstraction level, in Mechatronics and Its Applications, ISMA th International Symposium on, May 2008, pp [12] S. Yoo, G. Nicolescu, L. Gauthier, and A. Jerraya, Automatic generation of fast timed simulation models for operating systems in soc design, in DATE 02: Proceedings of the conference on Design, automation and test in Europe, Washington, DC, USA, 2002, p. 620, IEEE Computer Society. [13] Gunar Schirner and Rainer Dömer, Introducing preemptive scheduling in abstract rtos models using result oriented modeling, in DATE 08: Proceedings of the conference on Design, automation and test in Europe, New York, NY, USA, 2008, pp , ACM. [14] XEN.org, Embedded xen project., Web, Available at Accessed at 10 ago., [15] Wind River, Wind river, Web, Available at Accessed at 2 oct., [16] VirtualLogix VLX, Real-time virtualization for connected devices, Web, Available at Accessed at 2 oct., [17] Trango, Trango hypervisor, Web, Available at Accessed at 2 oct., [18] XtratuM, Trango hypervisor, Web, Available at Accessed at 2 oct., [19] Robert P. Goldberg, Survey of virtual machine research, Computer, pp , [20] Andrew S. Tanenbaum, Modern Operating Systems, Prentice Hall Press, Upper Saddle River, NJ, USA, [21] Gerald J. Popek and Robert P. Goldberg, Formal requirements for virtualizable third generation architectures, Commun. ACM, vol. 17, no. 7, pp , [22] Carl A. Waldspurger, Memory resource management in vmware esx server, SIGOPS Oper. Syst. Rev., vol. 36, no. SI, pp , [23] Open Cores, Plasma most mips i(tm) opcodes, Accessed, September 2009, [24] Sergio Johann Filho, Alexandra Aguiar, César Augusto Missio Marcon, and Fabiano Passuelo Hessel, High-level estimation of execution time and energy consumption for fast homogeneous mpsocs prototyping, in RSP 08: Proceedings of the 2008 The 19th IEEE/IFIP International Symposium on Rapid System Prototyping, Washington, DC, USA, 2008, pp , IEEE Computer Society. [25] Siddharth Choudhuri and Tony Givargis, Software virtual memory management for mmu-less embedded systems, Tech. Rep., [26] Wanghong Yuan, K. Nahrstedt, and Kihun Kim, R-edf: a reservationbased edf scheduling algorithm for multiple multimedia task classes, 2001, pp
A hypervisor approach with real-time support to the MIPS M5150 processor
 ISQED Wednesday March 4, 2015 Session 5B A hypervisor approach with real-time support to the MIPS M5150 processor Authors: Samir Zampiva ([email protected]) Carlos Moratelli ([email protected])
ISQED Wednesday March 4, 2015 Session 5B A hypervisor approach with real-time support to the MIPS M5150 processor Authors: Samir Zampiva ([email protected]) Carlos Moratelli ([email protected])
How To Write A Virtual Hellfire Hypervisor For Embedded Systems
 SESSION 2C Tue, March 15, 2011 System Frameworks and Tools Virtual Hellfire Hypervisor: Extending Hellfire Framework for Embedded March 14-16, 2011 Hyatt Regency Hotel, Santa Clara, CA USA Alexandra Aguiar
SESSION 2C Tue, March 15, 2011 System Frameworks and Tools Virtual Hellfire Hypervisor: Extending Hellfire Framework for Embedded March 14-16, 2011 Hyatt Regency Hotel, Santa Clara, CA USA Alexandra Aguiar
Virtualization. Jukka K. Nurminen 23.9.2015
 Virtualization Jukka K. Nurminen 23.9.2015 Virtualization Virtualization refers to the act of creating a virtual (rather than actual) version of something, including virtual computer hardware platforms,
Virtualization Jukka K. Nurminen 23.9.2015 Virtualization Virtualization refers to the act of creating a virtual (rather than actual) version of something, including virtual computer hardware platforms,
Hypervisors. Introduction. Introduction. Introduction. Introduction. Introduction. Credits:
 Hypervisors Credits: P. Chaganti Xen Virtualization A practical handbook D. Chisnall The definitive guide to Xen Hypervisor G. Kesden Lect. 25 CS 15-440 G. Heiser UNSW/NICTA/OKL Virtualization is a technique
Hypervisors Credits: P. Chaganti Xen Virtualization A practical handbook D. Chisnall The definitive guide to Xen Hypervisor G. Kesden Lect. 25 CS 15-440 G. Heiser UNSW/NICTA/OKL Virtualization is a technique
Full and Para Virtualization
 Full and Para Virtualization Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF x86 Hardware Virtualization The x86 architecture offers four levels
Full and Para Virtualization Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF x86 Hardware Virtualization The x86 architecture offers four levels
Leveraging Thin Hypervisors for Security on Embedded Systems
 Leveraging Thin Hypervisors for Security on Embedded Systems Christian Gehrmann A part of Swedish ICT What is virtualization? Separation of a resource or request for a service from the underlying physical
Leveraging Thin Hypervisors for Security on Embedded Systems Christian Gehrmann A part of Swedish ICT What is virtualization? Separation of a resource or request for a service from the underlying physical
Proteus, a hybrid Virtualization Platform for Embedded Systems
 Proteus, a hybrid Virtualization Platform for Embedded Systems Dipl.-Inf. Daniel Baldin and Dipl.-Inf. Timo Kerstan Heinz-Nixdorf-Institute University of Paderborn 33102 Paderborn, Germany [email protected]
Proteus, a hybrid Virtualization Platform for Embedded Systems Dipl.-Inf. Daniel Baldin and Dipl.-Inf. Timo Kerstan Heinz-Nixdorf-Institute University of Paderborn 33102 Paderborn, Germany [email protected]
12. Introduction to Virtual Machines
 12. Introduction to Virtual Machines 12. Introduction to Virtual Machines Modern Applications Challenges of Virtual Machine Monitors Historical Perspective Classification 332 / 352 12. Introduction to
12. Introduction to Virtual Machines 12. Introduction to Virtual Machines Modern Applications Challenges of Virtual Machine Monitors Historical Perspective Classification 332 / 352 12. Introduction to
COS 318: Operating Systems. Virtual Machine Monitors
 COS 318: Operating Systems Virtual Machine Monitors Kai Li and Andy Bavier Computer Science Department Princeton University http://www.cs.princeton.edu/courses/archive/fall13/cos318/ Introduction u Have
COS 318: Operating Systems Virtual Machine Monitors Kai Li and Andy Bavier Computer Science Department Princeton University http://www.cs.princeton.edu/courses/archive/fall13/cos318/ Introduction u Have
Virtualization. Pradipta De [email protected]
 Virtualization Pradipta De [email protected] Today s Topic Virtualization Basics System Virtualization Techniques CSE506: Ext Filesystem 2 Virtualization? A virtual machine (VM) is an emulation
Virtualization Pradipta De [email protected] Today s Topic Virtualization Basics System Virtualization Techniques CSE506: Ext Filesystem 2 Virtualization? A virtual machine (VM) is an emulation
Virtualization. Types of Interfaces
 Virtualization Virtualization: extend or replace an existing interface to mimic the behavior of another system. Introduced in 1970s: run legacy software on newer mainframe hardware Handle platform diversity
Virtualization Virtualization: extend or replace an existing interface to mimic the behavior of another system. Introduced in 1970s: run legacy software on newer mainframe hardware Handle platform diversity
evm Virtualization Platform for Windows
 B A C K G R O U N D E R evm Virtualization Platform for Windows Host your Embedded OS and Windows on a Single Hardware Platform using Intel Virtualization Technology April, 2008 TenAsys Corporation 1400
B A C K G R O U N D E R evm Virtualization Platform for Windows Host your Embedded OS and Windows on a Single Hardware Platform using Intel Virtualization Technology April, 2008 TenAsys Corporation 1400
Hypervisors and Virtual Machines
 Hypervisors and Virtual Machines Implementation Insights on the x86 Architecture DON REVELLE Don is a performance engineer and Linux systems/kernel programmer, specializing in high-volume UNIX, Web, virtualization,
Hypervisors and Virtual Machines Implementation Insights on the x86 Architecture DON REVELLE Don is a performance engineer and Linux systems/kernel programmer, specializing in high-volume UNIX, Web, virtualization,
Cloud Computing #6 - Virtualization
 Cloud Computing #6 - Virtualization Main source: Smith & Nair, Virtual Machines, Morgan Kaufmann, 2005 Today What do we mean by virtualization? Why is it important to cloud? What is the penalty? Current
Cloud Computing #6 - Virtualization Main source: Smith & Nair, Virtual Machines, Morgan Kaufmann, 2005 Today What do we mean by virtualization? Why is it important to cloud? What is the penalty? Current
Virtualization. Dr. Yingwu Zhu
 Virtualization Dr. Yingwu Zhu What is virtualization? Virtualization allows one computer to do the job of multiple computers. Virtual environments let one computer host multiple operating systems at the
Virtualization Dr. Yingwu Zhu What is virtualization? Virtualization allows one computer to do the job of multiple computers. Virtual environments let one computer host multiple operating systems at the
GUEST OPERATING SYSTEM BASED PERFORMANCE COMPARISON OF VMWARE AND XEN HYPERVISOR
 GUEST OPERATING SYSTEM BASED PERFORMANCE COMPARISON OF VMWARE AND XEN HYPERVISOR ANKIT KUMAR, SAVITA SHIWANI 1 M. Tech Scholar, Software Engineering, Suresh Gyan Vihar University, Rajasthan, India, Email:
GUEST OPERATING SYSTEM BASED PERFORMANCE COMPARISON OF VMWARE AND XEN HYPERVISOR ANKIT KUMAR, SAVITA SHIWANI 1 M. Tech Scholar, Software Engineering, Suresh Gyan Vihar University, Rajasthan, India, Email:
Uses for Virtual Machines. Virtual Machines. There are several uses for virtual machines:
 Virtual Machines Uses for Virtual Machines Virtual machine technology, often just called virtualization, makes one computer behave as several computers by sharing the resources of a single computer between
Virtual Machines Uses for Virtual Machines Virtual machine technology, often just called virtualization, makes one computer behave as several computers by sharing the resources of a single computer between
Dynamic Load Balancing of Virtual Machines using QEMU-KVM
 Dynamic Load Balancing of Virtual Machines using QEMU-KVM Akshay Chandak Krishnakant Jaju Technology, College of Engineering, Pune. Maharashtra, India. Akshay Kanfade Pushkar Lohiya Technology, College
Dynamic Load Balancing of Virtual Machines using QEMU-KVM Akshay Chandak Krishnakant Jaju Technology, College of Engineering, Pune. Maharashtra, India. Akshay Kanfade Pushkar Lohiya Technology, College
Virtual Machine Monitors. Dr. Marc E. Fiuczynski Research Scholar Princeton University
 Virtual Machine Monitors Dr. Marc E. Fiuczynski Research Scholar Princeton University Introduction Have been around since 1960 s on mainframes used for multitasking Good example VM/370 Have resurfaced
Virtual Machine Monitors Dr. Marc E. Fiuczynski Research Scholar Princeton University Introduction Have been around since 1960 s on mainframes used for multitasking Good example VM/370 Have resurfaced
Microkernels, virtualization, exokernels. Tutorial 1 CSC469
 Microkernels, virtualization, exokernels Tutorial 1 CSC469 Monolithic kernel vs Microkernel Monolithic OS kernel Application VFS System call User mode What was the main idea? What were the problems? IPC,
Microkernels, virtualization, exokernels Tutorial 1 CSC469 Monolithic kernel vs Microkernel Monolithic OS kernel Application VFS System call User mode What was the main idea? What were the problems? IPC,
System Virtual Machines
 System Virtual Machines Introduction Key concepts Resource virtualization processors memory I/O devices Performance issues Applications 1 Introduction System virtual machine capable of supporting multiple
System Virtual Machines Introduction Key concepts Resource virtualization processors memory I/O devices Performance issues Applications 1 Introduction System virtual machine capable of supporting multiple
Parallels Virtuozzo Containers
 Parallels Virtuozzo Containers White Paper Top Ten Considerations For Choosing A Server Virtualization Technology www.parallels.com Version 1.0 Table of Contents Introduction... 3 Technology Overview...
Parallels Virtuozzo Containers White Paper Top Ten Considerations For Choosing A Server Virtualization Technology www.parallels.com Version 1.0 Table of Contents Introduction... 3 Technology Overview...
CPET 581 Cloud Computing: Technologies and Enterprise IT Strategies. Virtualization of Clusters and Data Centers
 CPET 581 Cloud Computing: Technologies and Enterprise IT Strategies Lecture 4 Virtualization of Clusters and Data Centers Text Book: Distributed and Cloud Computing, by K. Hwang, G C. Fox, and J.J. Dongarra,
CPET 581 Cloud Computing: Technologies and Enterprise IT Strategies Lecture 4 Virtualization of Clusters and Data Centers Text Book: Distributed and Cloud Computing, by K. Hwang, G C. Fox, and J.J. Dongarra,
Knut Omang Ifi/Oracle 19 Oct, 2015
 Software and hardware support for Network Virtualization Knut Omang Ifi/Oracle 19 Oct, 2015 Motivation Goal: Introduction to challenges in providing fast networking to virtual machines Prerequisites: What
Software and hardware support for Network Virtualization Knut Omang Ifi/Oracle 19 Oct, 2015 Motivation Goal: Introduction to challenges in providing fast networking to virtual machines Prerequisites: What
Design and Implementation of the Heterogeneous Multikernel Operating System
 223 Design and Implementation of the Heterogeneous Multikernel Operating System Yauhen KLIMIANKOU Department of Computer Systems and Networks, Belarusian State University of Informatics and Radioelectronics,
223 Design and Implementation of the Heterogeneous Multikernel Operating System Yauhen KLIMIANKOU Department of Computer Systems and Networks, Belarusian State University of Informatics and Radioelectronics,
Chapter 2 Addendum (More on Virtualization)
 Chapter 2 Addendum (More on Virtualization) Roch Glitho, PhD Associate Professor and Canada Research Chair My URL - http://users.encs.concordia.ca/~glitho/ More on Systems Virtualization Type I (bare metal)
Chapter 2 Addendum (More on Virtualization) Roch Glitho, PhD Associate Professor and Canada Research Chair My URL - http://users.encs.concordia.ca/~glitho/ More on Systems Virtualization Type I (bare metal)
Virtualization. Jia Rao Assistant Professor in CS http://cs.uccs.edu/~jrao/
 Virtualization Jia Rao Assistant Professor in CS http://cs.uccs.edu/~jrao/ What is Virtualization? Virtualization is the simulation of the software and/ or hardware upon which other software runs. This
Virtualization Jia Rao Assistant Professor in CS http://cs.uccs.edu/~jrao/ What is Virtualization? Virtualization is the simulation of the software and/ or hardware upon which other software runs. This
COS 318: Operating Systems. Virtual Machine Monitors
 COS 318: Operating Systems Virtual Machine Monitors Andy Bavier Computer Science Department Princeton University http://www.cs.princeton.edu/courses/archive/fall10/cos318/ Introduction Have been around
COS 318: Operating Systems Virtual Machine Monitors Andy Bavier Computer Science Department Princeton University http://www.cs.princeton.edu/courses/archive/fall10/cos318/ Introduction Have been around
Virtualization Technologies (ENCS 691K Chapter 3)
 Virtualization Technologies (ENCS 691K Chapter 3) Roch Glitho, PhD Associate Professor and Canada Research Chair My URL - http://users.encs.concordia.ca/~glitho/ The Key Technologies on Which Cloud Computing
Virtualization Technologies (ENCS 691K Chapter 3) Roch Glitho, PhD Associate Professor and Canada Research Chair My URL - http://users.encs.concordia.ca/~glitho/ The Key Technologies on Which Cloud Computing
Embedded Systems. 6. Real-Time Operating Systems
 Embedded Systems 6. Real-Time Operating Systems Lothar Thiele 6-1 Contents of Course 1. Embedded Systems Introduction 2. Software Introduction 7. System Components 10. Models 3. Real-Time Models 4. Periodic/Aperiodic
Embedded Systems 6. Real-Time Operating Systems Lothar Thiele 6-1 Contents of Course 1. Embedded Systems Introduction 2. Software Introduction 7. System Components 10. Models 3. Real-Time Models 4. Periodic/Aperiodic
The Microsoft Windows Hypervisor High Level Architecture
 The Microsoft Windows Hypervisor High Level Architecture September 21, 2007 Abstract The Microsoft Windows hypervisor brings new virtualization capabilities to the Windows Server operating system. Its
The Microsoft Windows Hypervisor High Level Architecture September 21, 2007 Abstract The Microsoft Windows hypervisor brings new virtualization capabilities to the Windows Server operating system. Its
The MIPS architecture and virtualization
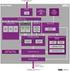 The MIPS architecture and virtualization Simply put, virtualization makes one physical device appear as one or more virtual devices. Virtualization can be implemented at the processor level (e.g. CPU or
The MIPS architecture and virtualization Simply put, virtualization makes one physical device appear as one or more virtual devices. Virtualization can be implemented at the processor level (e.g. CPU or
VxWorks Guest OS Programmer's Guide for Hypervisor 1.1, 6.8. VxWorks GUEST OS PROGRAMMER'S GUIDE FOR HYPERVISOR 1.1 6.8
 VxWorks Guest OS Programmer's Guide for Hypervisor 1.1, 6.8 VxWorks GUEST OS PROGRAMMER'S GUIDE FOR HYPERVISOR 1.1 6.8 Copyright 2009 Wind River Systems, Inc. All rights reserved. No part of this publication
VxWorks Guest OS Programmer's Guide for Hypervisor 1.1, 6.8 VxWorks GUEST OS PROGRAMMER'S GUIDE FOR HYPERVISOR 1.1 6.8 Copyright 2009 Wind River Systems, Inc. All rights reserved. No part of this publication
Basics in Energy Information (& Communication) Systems Virtualization / Virtual Machines
 Basics in Energy Information (& Communication) Systems Virtualization / Virtual Machines Dr. Johann Pohany, Virtualization Virtualization deals with extending or replacing an existing interface so as to
Basics in Energy Information (& Communication) Systems Virtualization / Virtual Machines Dr. Johann Pohany, Virtualization Virtualization deals with extending or replacing an existing interface so as to
PikeOS: Multi-Core RTOS for IMA. Dr. Sergey Tverdyshev SYSGO AG 29.10.2012, Moscow
 PikeOS: Multi-Core RTOS for IMA Dr. Sergey Tverdyshev SYSGO AG 29.10.2012, Moscow Contents Multi Core Overview Hardware Considerations Multi Core Software Design Certification Consideratins PikeOS Multi-Core
PikeOS: Multi-Core RTOS for IMA Dr. Sergey Tverdyshev SYSGO AG 29.10.2012, Moscow Contents Multi Core Overview Hardware Considerations Multi Core Software Design Certification Consideratins PikeOS Multi-Core
Virtual Machines. COMP 3361: Operating Systems I Winter 2015 http://www.cs.du.edu/3361
 s COMP 3361: Operating Systems I Winter 2015 http://www.cs.du.edu/3361 1 Virtualization! Create illusion of multiple machines on the same physical hardware! Single computer hosts multiple virtual machines
s COMP 3361: Operating Systems I Winter 2015 http://www.cs.du.edu/3361 1 Virtualization! Create illusion of multiple machines on the same physical hardware! Single computer hosts multiple virtual machines
VMware Server 2.0 Essentials. Virtualization Deployment and Management
 VMware Server 2.0 Essentials Virtualization Deployment and Management . This PDF is provided for personal use only. Unauthorized use, reproduction and/or distribution strictly prohibited. All rights reserved.
VMware Server 2.0 Essentials Virtualization Deployment and Management . This PDF is provided for personal use only. Unauthorized use, reproduction and/or distribution strictly prohibited. All rights reserved.
ESE566 REPORT3. Design Methodologies for Core-based System-on-Chip HUA TANG OVIDIU CARNU
 ESE566 REPORT3 Design Methodologies for Core-based System-on-Chip HUA TANG OVIDIU CARNU Nov 19th, 2002 ABSTRACT: In this report, we discuss several recent published papers on design methodologies of core-based
ESE566 REPORT3 Design Methodologies for Core-based System-on-Chip HUA TANG OVIDIU CARNU Nov 19th, 2002 ABSTRACT: In this report, we discuss several recent published papers on design methodologies of core-based
Virtualization for Cloud Computing
 Virtualization for Cloud Computing Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF CLOUD COMPUTING On demand provision of computational resources
Virtualization for Cloud Computing Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF CLOUD COMPUTING On demand provision of computational resources
MODULE 3 VIRTUALIZED DATA CENTER COMPUTE
 MODULE 3 VIRTUALIZED DATA CENTER COMPUTE Module 3: Virtualized Data Center Compute Upon completion of this module, you should be able to: Describe compute virtualization Discuss the compute virtualization
MODULE 3 VIRTUALIZED DATA CENTER COMPUTE Module 3: Virtualized Data Center Compute Upon completion of this module, you should be able to: Describe compute virtualization Discuss the compute virtualization
VMware and CPU Virtualization Technology. Jack Lo Sr. Director, R&D
 ware and CPU Virtualization Technology Jack Lo Sr. Director, R&D This presentation may contain ware confidential information. Copyright 2005 ware, Inc. All rights reserved. All other marks and names mentioned
ware and CPU Virtualization Technology Jack Lo Sr. Director, R&D This presentation may contain ware confidential information. Copyright 2005 ware, Inc. All rights reserved. All other marks and names mentioned
Virtual Machines. www.viplavkambli.com
 1 Virtual Machines A virtual machine (VM) is a "completely isolated guest operating system installation within a normal host operating system". Modern virtual machines are implemented with either software
1 Virtual Machines A virtual machine (VM) is a "completely isolated guest operating system installation within a normal host operating system". Modern virtual machines are implemented with either software
Distributed and Cloud Computing
 Distributed and Cloud Computing K. Hwang, G. Fox and J. Dongarra Chapter 3: Virtual Machines and Virtualization of Clusters and datacenters Adapted from Kai Hwang University of Southern California March
Distributed and Cloud Computing K. Hwang, G. Fox and J. Dongarra Chapter 3: Virtual Machines and Virtualization of Clusters and datacenters Adapted from Kai Hwang University of Southern California March
Virtualization for Hard Real-Time Applications Partition where you can Virtualize where you have to
 Virtualization for Hard Real-Time Applications Partition where you can Virtualize where you have to Hanspeter Vogel Triadem Solutions AG Real-Time Systems GmbH Gartenstrasse 33 D-88212 Ravensburg Germany
Virtualization for Hard Real-Time Applications Partition where you can Virtualize where you have to Hanspeter Vogel Triadem Solutions AG Real-Time Systems GmbH Gartenstrasse 33 D-88212 Ravensburg Germany
How do Users and Processes interact with the Operating System? Services for Processes. OS Structure with Services. Services for the OS Itself
 How do Users and Processes interact with the Operating System? Users interact indirectly through a collection of system programs that make up the operating system interface. The interface could be: A GUI,
How do Users and Processes interact with the Operating System? Users interact indirectly through a collection of system programs that make up the operating system interface. The interface could be: A GUI,
Basics of Virtualisation
 Basics of Virtualisation Volker Büge Institut für Experimentelle Kernphysik Universität Karlsruhe Die Kooperation von The x86 Architecture Why do we need virtualisation? x86 based operating systems are
Basics of Virtualisation Volker Büge Institut für Experimentelle Kernphysik Universität Karlsruhe Die Kooperation von The x86 Architecture Why do we need virtualisation? x86 based operating systems are
Virtualization in the ARMv7 Architecture Lecture for the Embedded Systems Course CSD, University of Crete (May 20, 2014)
 Virtualization in the ARMv7 Architecture Lecture for the Embedded Systems Course CSD, University of Crete (May 20, 2014) ManolisMarazakis ([email protected]) Institute of Computer Science (ICS) Foundation
Virtualization in the ARMv7 Architecture Lecture for the Embedded Systems Course CSD, University of Crete (May 20, 2014) ManolisMarazakis ([email protected]) Institute of Computer Science (ICS) Foundation
KVM in Embedded Requirements, Experiences, Open Challenges
 Corporate Technology KVM in Embedded Requirements, Experiences, Open Challenges Jan Kiszka, Siemens AG Corporate Competence Center Embedded Linux [email protected] Copyright Siemens AG 2009. All rights
Corporate Technology KVM in Embedded Requirements, Experiences, Open Challenges Jan Kiszka, Siemens AG Corporate Competence Center Embedded Linux [email protected] Copyright Siemens AG 2009. All rights
VtRES 2013. Towards Hardware Embedded Virtualization Technology: Architectural Enhancements to an ARM SoC. ESRG Embedded Systems Research Group
 Towards Hardware Embedded Virtualization Technology: Architectural Enhancements to an ARM SoC VtRES 2013 P. Garcia, T. Gomes, F. Salgado, J. Monteiro, A. Tavares Summary 1. Current landscape in 2. Embedded
Towards Hardware Embedded Virtualization Technology: Architectural Enhancements to an ARM SoC VtRES 2013 P. Garcia, T. Gomes, F. Salgado, J. Monteiro, A. Tavares Summary 1. Current landscape in 2. Embedded
COM 444 Cloud Computing
 COM 444 Cloud Computing Lec 3: Virtual Machines and Virtualization of Clusters and Datacenters Prof. Dr. Halûk Gümüşkaya [email protected] [email protected] http://www.gumuskaya.com Virtual
COM 444 Cloud Computing Lec 3: Virtual Machines and Virtualization of Clusters and Datacenters Prof. Dr. Halûk Gümüşkaya [email protected] [email protected] http://www.gumuskaya.com Virtual
Virtualization. Clothing the Wolf in Wool. Wednesday, April 17, 13
 Virtualization Clothing the Wolf in Wool Virtual Machines Began in 1960s with IBM and MIT Project MAC Also called open shop operating systems Present user with the view of a bare machine Execute most instructions
Virtualization Clothing the Wolf in Wool Virtual Machines Began in 1960s with IBM and MIT Project MAC Also called open shop operating systems Present user with the view of a bare machine Execute most instructions
10.04.2008. Thomas Fahrig Senior Developer Hypervisor Team. Hypervisor Architecture Terminology Goals Basics Details
 Thomas Fahrig Senior Developer Hypervisor Team Hypervisor Architecture Terminology Goals Basics Details Scheduling Interval External Interrupt Handling Reserves, Weights and Caps Context Switch Waiting
Thomas Fahrig Senior Developer Hypervisor Team Hypervisor Architecture Terminology Goals Basics Details Scheduling Interval External Interrupt Handling Reserves, Weights and Caps Context Switch Waiting
Virtual machines and operating systems
 V i r t u a l m a c h i n e s a n d o p e r a t i n g s y s t e m s Virtual machines and operating systems Krzysztof Lichota [email protected] A g e n d a Virtual machines and operating systems interactions
V i r t u a l m a c h i n e s a n d o p e r a t i n g s y s t e m s Virtual machines and operating systems Krzysztof Lichota [email protected] A g e n d a Virtual machines and operating systems interactions
XtratuM hypervisor redesign for LEON4 multicore processor
 XtratuM hypervisor redesign for LEON4 multicore processor E.Carrascosa, M.Masmano, P.Balbastre and A.Crespo Universidad Politécnica de Valencia, Spain Outline Motivation/Introduction XtratuM hypervisor
XtratuM hypervisor redesign for LEON4 multicore processor E.Carrascosa, M.Masmano, P.Balbastre and A.Crespo Universidad Politécnica de Valencia, Spain Outline Motivation/Introduction XtratuM hypervisor
Virtualization. Explain how today s virtualization movement is actually a reinvention
 Virtualization Learning Objectives Explain how today s virtualization movement is actually a reinvention of the past. Explain how virtualization works. Discuss the technical challenges to virtualization.
Virtualization Learning Objectives Explain how today s virtualization movement is actually a reinvention of the past. Explain how virtualization works. Discuss the technical challenges to virtualization.
Chapter 14 Virtual Machines
 Operating Systems: Internals and Design Principles Chapter 14 Virtual Machines Eighth Edition By William Stallings Virtual Machines (VM) Virtualization technology enables a single PC or server to simultaneously
Operating Systems: Internals and Design Principles Chapter 14 Virtual Machines Eighth Edition By William Stallings Virtual Machines (VM) Virtualization technology enables a single PC or server to simultaneously
Introduction to the NI Real-Time Hypervisor
 Introduction to the NI Real-Time Hypervisor 1 Agenda 1) NI Real-Time Hypervisor overview 2) Basics of virtualization technology 3) Configuring and using Real-Time Hypervisor systems 4) Performance and
Introduction to the NI Real-Time Hypervisor 1 Agenda 1) NI Real-Time Hypervisor overview 2) Basics of virtualization technology 3) Configuring and using Real-Time Hypervisor systems 4) Performance and
Virtual Machines. Virtualization
 Virtual Machines Marie Roch Tanenbaum 8.3 contains slides from: Tanenbaum 3 rd ed. 2008 1 Virtualization Started with the IBM System/360 in the 1960s Basic concept simulate multiple copies of the underlying
Virtual Machines Marie Roch Tanenbaum 8.3 contains slides from: Tanenbaum 3 rd ed. 2008 1 Virtualization Started with the IBM System/360 in the 1960s Basic concept simulate multiple copies of the underlying
XtratuM: a Hypervisor for Safety Critical Embedded Systems
 XtratuM: a Hypervisor for Safety Critical Embedded Systems M. Masmano, I. Ripoll, and A. Crespo Instituto de Informática Industrial, Universidad Politécnica de Valencia (Spain) {mmasmano, iripoll, alfons}@ai2.upv.es
XtratuM: a Hypervisor for Safety Critical Embedded Systems M. Masmano, I. Ripoll, and A. Crespo Instituto de Informática Industrial, Universidad Politécnica de Valencia (Spain) {mmasmano, iripoll, alfons}@ai2.upv.es
ELEC 5260/6260/6266 Embedded Computing Systems
 ELEC 5260/6260/6266 Embedded Computing Systems Spring 2016 Victor P. Nelson Text: Computers as Components, 3 rd Edition Prof. Marilyn Wolf (Georgia Tech) Course Topics Embedded system design & modeling
ELEC 5260/6260/6266 Embedded Computing Systems Spring 2016 Victor P. Nelson Text: Computers as Components, 3 rd Edition Prof. Marilyn Wolf (Georgia Tech) Course Topics Embedded system design & modeling
Deeply Embedded Real-Time Hypervisors for the Automotive Domain Dr. Gary Morgan, ETAS/ESC
 Deeply Embedded Real-Time Hypervisors for the Automotive Domain Dr. Gary Morgan, ETAS/ESC 1 Public ETAS/ESC 2014-02-20 ETAS GmbH 2014. All rights reserved, also regarding any disposal, exploitation, reproduction,
Deeply Embedded Real-Time Hypervisors for the Automotive Domain Dr. Gary Morgan, ETAS/ESC 1 Public ETAS/ESC 2014-02-20 ETAS GmbH 2014. All rights reserved, also regarding any disposal, exploitation, reproduction,
Distributed Systems. Virtualization. Paul Krzyzanowski [email protected]
 Distributed Systems Virtualization Paul Krzyzanowski [email protected] Except as otherwise noted, the content of this presentation is licensed under the Creative Commons Attribution 2.5 License. Virtualization
Distributed Systems Virtualization Paul Krzyzanowski [email protected] Except as otherwise noted, the content of this presentation is licensed under the Creative Commons Attribution 2.5 License. Virtualization
Virtualization. ! Physical Hardware. ! Software. ! Isolation. ! Software Abstraction. ! Encapsulation. ! Virtualization Layer. !
 Starting Point: A Physical Machine Virtualization Based on materials from: Introduction to Virtual Machines by Carl Waldspurger Understanding Intel Virtualization Technology (VT) by N. B. Sahgal and D.
Starting Point: A Physical Machine Virtualization Based on materials from: Introduction to Virtual Machines by Carl Waldspurger Understanding Intel Virtualization Technology (VT) by N. B. Sahgal and D.
Implementation of a Purely Hardware-assisted VMM for x86 Architecture
 Implementation of a Purely Hardware-assisted VMM for x86 Architecture Saidalavi Kalady, Dileep P G, Krishanu Sikdar, Sreejith B S, Vinaya Surya, Ezudheen P Abstract Virtualization is a technique for efficient
Implementation of a Purely Hardware-assisted VMM for x86 Architecture Saidalavi Kalady, Dileep P G, Krishanu Sikdar, Sreejith B S, Vinaya Surya, Ezudheen P Abstract Virtualization is a technique for efficient
Virtualization: Hypervisors for Embedded and Safe Systems. Hanspeter Vogel Triadem Solutions AG
 1 Virtualization: Hypervisors for Embedded and Safe Systems Hanspeter Vogel Triadem Solutions AG 2 Agenda Use cases for virtualization Terminology Hypervisor Solutions Realtime System Hypervisor Features
1 Virtualization: Hypervisors for Embedded and Safe Systems Hanspeter Vogel Triadem Solutions AG 2 Agenda Use cases for virtualization Terminology Hypervisor Solutions Realtime System Hypervisor Features
Virtualization. Michael Tsai 2015/06/08
 Virtualization Michael Tsai 2015/06/08 What is virtualization? Let s first look at a video from VMware http://bcove.me/x9zhalcl Problems? Low utilization Different needs DNS DHCP Web mail 5% 5% 15% 8%
Virtualization Michael Tsai 2015/06/08 What is virtualization? Let s first look at a video from VMware http://bcove.me/x9zhalcl Problems? Low utilization Different needs DNS DHCP Web mail 5% 5% 15% 8%
Architectures and Platforms
 Hardware/Software Codesign Arch&Platf. - 1 Architectures and Platforms 1. Architecture Selection: The Basic Trade-Offs 2. General Purpose vs. Application-Specific Processors 3. Processor Specialisation
Hardware/Software Codesign Arch&Platf. - 1 Architectures and Platforms 1. Architecture Selection: The Basic Trade-Offs 2. General Purpose vs. Application-Specific Processors 3. Processor Specialisation
nanohub.org An Overview of Virtualization Techniques
 An Overview of Virtualization Techniques Renato Figueiredo Advanced Computing and Information Systems (ACIS) Electrical and Computer Engineering University of Florida NCN/NMI Team 2/3/2006 1 Outline Resource
An Overview of Virtualization Techniques Renato Figueiredo Advanced Computing and Information Systems (ACIS) Electrical and Computer Engineering University of Florida NCN/NMI Team 2/3/2006 1 Outline Resource
Title: XtratuM: a Hypervisor for Safety Critical Embedded Systems. Authors:M. Masmano, I. Ripoll, A. Crespo and J.J. Metge
 Title: XtratuM: a Hypervisor for Safety Critical Embedded Systems. Authors:M. Masmano, I. Ripoll, A. Crespo and J.J. Metge Affiliation: Instituto de Informática Industrial, Universidad Politécnica de Valencia,
Title: XtratuM: a Hypervisor for Safety Critical Embedded Systems. Authors:M. Masmano, I. Ripoll, A. Crespo and J.J. Metge Affiliation: Instituto de Informática Industrial, Universidad Politécnica de Valencia,
x86 ISA Modifications to support Virtual Machines
 x86 ISA Modifications to support Virtual Machines Douglas Beal Ashish Kumar Gupta CSE 548 Project Outline of the talk Review of Virtual Machines What complicates Virtualization Technique for Virtualization
x86 ISA Modifications to support Virtual Machines Douglas Beal Ashish Kumar Gupta CSE 548 Project Outline of the talk Review of Virtual Machines What complicates Virtualization Technique for Virtualization
Special FEATURE. By Heinrich Munz
 Special FEATURE By Heinrich Munz Heinrich Munz of KUKA Roboter discusses in this article how to bring Microsoft Windows CE and WindowsXP together on the same PC. He discusses system and application requirements,
Special FEATURE By Heinrich Munz Heinrich Munz of KUKA Roboter discusses in this article how to bring Microsoft Windows CE and WindowsXP together on the same PC. He discusses system and application requirements,
Virtualization Technologies and Blackboard: The Future of Blackboard Software on Multi-Core Technologies
 Virtualization Technologies and Blackboard: The Future of Blackboard Software on Multi-Core Technologies Kurt Klemperer, Principal System Performance Engineer [email protected] Agenda Session Length:
Virtualization Technologies and Blackboard: The Future of Blackboard Software on Multi-Core Technologies Kurt Klemperer, Principal System Performance Engineer [email protected] Agenda Session Length:
Virtualization. P. A. Wilsey. The text highlighted in green in these slides contain external hyperlinks. 1 / 16
 Virtualization P. A. Wilsey The text highlighted in green in these slides contain external hyperlinks. 1 / 16 Conventional System Viewed as Layers This illustration is a common presentation of the application/operating
Virtualization P. A. Wilsey The text highlighted in green in these slides contain external hyperlinks. 1 / 16 Conventional System Viewed as Layers This illustration is a common presentation of the application/operating
MultiPARTES. Virtualization on Heterogeneous Multicore Platforms. 2012/7/18 Slides by TU Wien, UPV, fentiss, UPM
 MultiPARTES Virtualization on Heterogeneous Multicore Platforms 2012/7/18 Slides by TU Wien, UPV, fentiss, UPM Contents Analysis of scheduling approaches Virtualization of devices Dealing with heterogeneous
MultiPARTES Virtualization on Heterogeneous Multicore Platforms 2012/7/18 Slides by TU Wien, UPV, fentiss, UPM Contents Analysis of scheduling approaches Virtualization of devices Dealing with heterogeneous
Real-Time Operating Systems for MPSoCs
 Real-Time Operating Systems for MPSoCs Hiroyuki Tomiyama Graduate School of Information Science Nagoya University http://member.acm.org/~hiroyuki MPSoC 2009 1 Contributors Hiroaki Takada Director and Professor
Real-Time Operating Systems for MPSoCs Hiroyuki Tomiyama Graduate School of Information Science Nagoya University http://member.acm.org/~hiroyuki MPSoC 2009 1 Contributors Hiroaki Takada Director and Professor
Virtualization is set to become a key requirement
 Xen, the virtual machine monitor The art of virtualization Moshe Bar Virtualization is set to become a key requirement for every server in the data center. This trend is a direct consequence of an industrywide
Xen, the virtual machine monitor The art of virtualization Moshe Bar Virtualization is set to become a key requirement for every server in the data center. This trend is a direct consequence of an industrywide
The Art of Virtualization with Free Software
 Master on Free Software 2009/2010 {mvidal,jfcastro}@libresoft.es GSyC/Libresoft URJC April 24th, 2010 (cc) 2010. Some rights reserved. This work is licensed under a Creative Commons Attribution-Share Alike
Master on Free Software 2009/2010 {mvidal,jfcastro}@libresoft.es GSyC/Libresoft URJC April 24th, 2010 (cc) 2010. Some rights reserved. This work is licensed under a Creative Commons Attribution-Share Alike
Outline. Introduction. Multiprocessor Systems on Chip. A MPSoC Example: Nexperia DVP. A New Paradigm: Network on Chip
 Outline Modeling, simulation and optimization of Multi-Processor SoCs (MPSoCs) Università of Verona Dipartimento di Informatica MPSoCs: Multi-Processor Systems on Chip A simulation platform for a MPSoC
Outline Modeling, simulation and optimization of Multi-Processor SoCs (MPSoCs) Università of Verona Dipartimento di Informatica MPSoCs: Multi-Processor Systems on Chip A simulation platform for a MPSoC
Outline. Outline. Why virtualization? Why not virtualize? Today s data center. Cloud computing. Virtual resource pool
 Outline CS 6V81-05: System Security and Malicious Code Analysis Overview of System ization: The most powerful platform for program analysis and system security Zhiqiang Lin Department of Computer Science
Outline CS 6V81-05: System Security and Malicious Code Analysis Overview of System ization: The most powerful platform for program analysis and system security Zhiqiang Lin Department of Computer Science
Chapter 5 Cloud Resource Virtualization
 Chapter 5 Cloud Resource Virtualization Contents Virtualization. Layering and virtualization. Virtual machine monitor. Virtual machine. Performance and security isolation. Architectural support for virtualization.
Chapter 5 Cloud Resource Virtualization Contents Virtualization. Layering and virtualization. Virtual machine monitor. Virtual machine. Performance and security isolation. Architectural support for virtualization.
Multilevel Load Balancing in NUMA Computers
 FACULDADE DE INFORMÁTICA PUCRS - Brazil http://www.pucrs.br/inf/pos/ Multilevel Load Balancing in NUMA Computers M. Corrêa, R. Chanin, A. Sales, R. Scheer, A. Zorzo Technical Report Series Number 049 July,
FACULDADE DE INFORMÁTICA PUCRS - Brazil http://www.pucrs.br/inf/pos/ Multilevel Load Balancing in NUMA Computers M. Corrêa, R. Chanin, A. Sales, R. Scheer, A. Zorzo Technical Report Series Number 049 July,
Embedded & Real-time Operating Systems
 Universität Dortmund 12 Embedded & Real-time Operating Systems Peter Marwedel, Informatik 12 Germany Application Knowledge Structure of this course New clustering 3: Embedded System HW 2: Specifications
Universität Dortmund 12 Embedded & Real-time Operating Systems Peter Marwedel, Informatik 12 Germany Application Knowledge Structure of this course New clustering 3: Embedded System HW 2: Specifications
Virtual Servers. Virtual machines. Virtualization. Design of IBM s VM. Virtual machine systems can give everyone the OS (and hardware) that they want.
 Virtual machines Virtual machine systems can give everyone the OS (and hardware) that they want. IBM s VM provided an exact copy of the hardware to the user. Virtual Servers Virtual machines are very widespread.
Virtual machines Virtual machine systems can give everyone the OS (and hardware) that they want. IBM s VM provided an exact copy of the hardware to the user. Virtual Servers Virtual machines are very widespread.
Virtualization and Other Tricks.
 Virtualization and Other Tricks. Pavel Parízek, Tomáš Kalibera, Peter Libič DEPARTMENT OF DISTRIBUTED AND DEPENDABLE SYSTEMS http://d3s.mff.cuni.cz CHARLES UNIVERSITY PRAGUE Faculty of Mathematics and
Virtualization and Other Tricks. Pavel Parízek, Tomáš Kalibera, Peter Libič DEPARTMENT OF DISTRIBUTED AND DEPENDABLE SYSTEMS http://d3s.mff.cuni.cz CHARLES UNIVERSITY PRAGUE Faculty of Mathematics and
OS Virtualization. CSC 456 Final Presentation Brandon D. Shroyer
 OS Virtualization CSC 456 Final Presentation Brandon D. Shroyer Introduction Virtualization: Providing an interface to software that maps to some underlying system. A one-to-one mapping between a guest
OS Virtualization CSC 456 Final Presentation Brandon D. Shroyer Introduction Virtualization: Providing an interface to software that maps to some underlying system. A one-to-one mapping between a guest
Enterprise-Class Virtualization with Open Source Technologies
 Enterprise-Class Virtualization with Open Source Technologies Alex Vasilevsky CTO & Founder Virtual Iron Software June 14, 2006 Virtualization Overview Traditional x86 Architecture Each server runs single
Enterprise-Class Virtualization with Open Source Technologies Alex Vasilevsky CTO & Founder Virtual Iron Software June 14, 2006 Virtualization Overview Traditional x86 Architecture Each server runs single
Building Embedded Systems
 All Rights Reserved. The contents of this document cannot be reproduced without prior permission of the authors. Building Embedded Systems Chapter 2: Building Operating Systems Andreas Knirsch [email protected]
All Rights Reserved. The contents of this document cannot be reproduced without prior permission of the authors. Building Embedded Systems Chapter 2: Building Operating Systems Andreas Knirsch [email protected]
Virtualization: Concepts, Applications, and Performance Modeling
 Virtualization: Concepts, s, and Performance Modeling Daniel A. Menascé, Ph.D. The Volgenau School of Information Technology and Engineering Department of Computer Science George Mason University www.cs.gmu.edu/faculty/menasce.html
Virtualization: Concepts, s, and Performance Modeling Daniel A. Menascé, Ph.D. The Volgenau School of Information Technology and Engineering Department of Computer Science George Mason University www.cs.gmu.edu/faculty/menasce.html
A Unified View of Virtual Machines
 A Unified View of Virtual Machines First ACM/USENIX Conference on Virtual Execution Environments J. E. Smith June 2005 Introduction Why are virtual machines interesting? They allow transcending of interfaces
A Unified View of Virtual Machines First ACM/USENIX Conference on Virtual Execution Environments J. E. Smith June 2005 Introduction Why are virtual machines interesting? They allow transcending of interfaces
Hardware accelerated Virtualization in the ARM Cortex Processors
 Hardware accelerated Virtualization in the ARM Cortex Processors John Goodacre Director, Program Management ARM Processor Division ARM Ltd. Cambridge UK 2nd November 2010 Sponsored by: & & New Capabilities
Hardware accelerated Virtualization in the ARM Cortex Processors John Goodacre Director, Program Management ARM Processor Division ARM Ltd. Cambridge UK 2nd November 2010 Sponsored by: & & New Capabilities
Cloud Computing CS 15-319
 Cloud Computing CS 15-319 Virtualization Case Studies : Xen and VMware Lecture 20 Majd F. Sakr, Mohammad Hammoud and Suhail Rehman 1 Today Last session Resource Virtualization Today s session Virtualization
Cloud Computing CS 15-319 Virtualization Case Studies : Xen and VMware Lecture 20 Majd F. Sakr, Mohammad Hammoud and Suhail Rehman 1 Today Last session Resource Virtualization Today s session Virtualization
Virtualization Technology. Zhiming Shen
 Virtualization Technology Zhiming Shen Virtualization: rejuvenation 1960 s: first track of virtualization Time and resource sharing on expensive mainframes IBM VM/370 Late 1970 s and early 1980 s: became
Virtualization Technology Zhiming Shen Virtualization: rejuvenation 1960 s: first track of virtualization Time and resource sharing on expensive mainframes IBM VM/370 Late 1970 s and early 1980 s: became
x86 Virtualization Hardware Support Pla$orm Virtualiza.on
 x86 Virtualization Hardware Support Pla$orm Virtualiza.on Hide the physical characteris.cs of computer resources from the applica.ons Not a new idea: IBM s CP- 40 1967, CP/CMS, VM Full Virtualiza.on Simulate
x86 Virtualization Hardware Support Pla$orm Virtualiza.on Hide the physical characteris.cs of computer resources from the applica.ons Not a new idea: IBM s CP- 40 1967, CP/CMS, VM Full Virtualiza.on Simulate
GEDAE TM - A Graphical Programming and Autocode Generation Tool for Signal Processor Applications
 GEDAE TM - A Graphical Programming and Autocode Generation Tool for Signal Processor Applications Harris Z. Zebrowitz Lockheed Martin Advanced Technology Laboratories 1 Federal Street Camden, NJ 08102
GEDAE TM - A Graphical Programming and Autocode Generation Tool for Signal Processor Applications Harris Z. Zebrowitz Lockheed Martin Advanced Technology Laboratories 1 Federal Street Camden, NJ 08102
