Proteus, a hybrid Virtualization Platform for Embedded Systems
|
|
|
- Jemimah Hood
- 10 years ago
- Views:
Transcription
1 Proteus, a hybrid Virtualization Platform for Embedded Systems Dipl.-Inf. Daniel Baldin and Dipl.-Inf. Timo Kerstan Heinz-Nixdorf-Institute University of Paderborn Paderborn, Germany [email protected] [email protected] Abstract. By the use of virtualization the security of a system can be significantly increased and performance can be improved by sharing hardware resources while reducing the overall costs of the whole system. Nowadays virtualization also finds approval within the field of embedded systems. However, the currently available virtualization platforms designed for embedded systems only support para-virtualization trying to provide reasonable performance and support realtime applications only by the use of dedicated resources. Our approach introduces a hybrid configurable hypervisor architecture designed to support real-time applications. We do not restrict the set of applications which can be run virtualized on top of our hypervisor to para-virtualized applications but also allow applications to run unmodified or even partly para-virtualized while using state of the art methodologies to obtain high performance. Introduction In the last decade, embedded systems tended to become increasingly complex systems while retaining the requirements of security and robustness. This inherent problem has usually been faced by the use of redundancy in which the whole hardware and software system is replicated multiple times to compensate a broken system. Additionally, embedded systems applications also often serve completely unrelated purposes which raises the need of being isolated from each other. Virtualization offers a solution to all of these problems, allowing the coexistence of multiple virtual machines on one hardware platform. By the use of virtual resources, the security of a system can be significantly increased [Heiser, 2008] [Chen and Noble, 2001] [Smith and Nair, 2005] and performance can be gained by sharing hardware resources while reducing the overall costs of the whole system [Chen and Noble, 2001]. The rapid increasing performance of embedded system hardware and the increasing availability of memory protection mechanisms inside embedded system processors make virtualization inside embedded systems more and more attractive.
2 1 Related Work There already exist a few commercial virtualization platforms or hypervisors for a range of embedded processors with nearly all of them being proprietary systems. Trango [VmWare, 2009] and VirtualLogix [VirtualLogix, 2009] are two of those hypervisors allowing virtualization for a range of ARM and MIPS processors. Greenhills Integrity [Hills, 2009] and LynxSecure [LynuxWorks, 2009] are using virtualization to implement high security systems targeted for the military market and have been certified to fulfill the EAL7 standard. All of these available products only use para-virtualization trying to provide reasonable performance and support realtime applications only by the use of dedicated resources. Naturally, this limits the applicability of virtualization using these products to a subset of all possible scenarios. Especially, whenever there are applications that can not be para-virtualized since the source code is not available these applications can not be virtualized using the currently available virtualization products as this would require a binary analysis of the whole application which most often is not completely possible [Laune C. Harris, 2006] [Saumya Debray, 1998]. Our approach overcomes this problem by introducing a hybrid configurable hypervisor architecture designed and implemented for the PowerPC405 processor which allows the virtualization of unmodified applications as well as paravirtualized applications or a combination of both. Support for realtime applications was a major goal of our design which allows the integration of any kind of scheduling mechanism for virtual machines while being completely deterministic. Additionally, the high configurability allows the system to be optimized explicitly for the intended field of use. 2 Hybrid Architecture The basic requirements which the design of this virtualization platform faces are: Security Real-time capabilities High performance Configurability Minimal demand on memory and energy consumption In order to meet the requirements of high performance and configurability, the virtualization platform uses a hybrid architecture as depicted in figure 1. Therefore, it represents a hybrid hypervisor which uses full-virtualization as the basic virtualization technique with additional support for para-virtualization. Partially para-virtualized applications or self modifying applications are also supported by the use of a fallback feature which ensures the consistency while executing in and switching between both kind of states. The configurability of the hypervisor and the para-virtualization interface allows the system designer
3 Fig. 1. The virtual machine monitor allows the virtualized execution of any kind of guest application. Left: a unmodified application. Middle: a completely para-virtualized application. Right: a partially modified application. to create a system which is tailored for the particular field of application and saves as much memory as possible. In general, the design is based on the multiple independent levels of security (MILS) architecture [Systems, 2008]. As illustrated in figure 2, only the minimal set of components which are needed to implement the secure partitioning, scheduling and communication between virtual machines are part of the hypervisor running in privileged mode. All other components called Untrusted VMP Modules are placed inside a separate partition and are executed in user mode as this is one of the fundamental concepts of the MILS architecture. The communication between partitions is controlled by the Inter Partition Communication Manager (IPCM) who, on request, creates shared memory tunnels between two partitions which can be used for virtual machines to ease the communication between each other. Especially this feature allows formerly physically spread systems which had to use real-time capable bus systems (e.g. a CAN-bus) for communication to enhance the security, robustness and performance of the information flow between each other if they are virtualized and placed on top of the same hypervisor. The fundamental components of the whole system form the interrupt handler as seen in figure 2. Since the hypervisor executes the guest application in user mode, any interrupt occurring is first delegated to the hypervisor which then has to analyze the interrupt and forward it to the appropriate component or the virtual machine itself. Program interrupts raised amongst others by privileged instructions inside the guest application are forwarded to the emulation routine dispatcher which will determine the corresponding ISA emulation routine. Whenever the virtualization platform has been configured to support para-virtualization, applications running inside a virtual machine can use hypercalls to emulate privileged instructions, call the IPCM, use para-virtualized I/O drivers or call scheduler related functions. Especially the last component offers methods to set scheduler related parameters at runtime or the possibility
4 Problem Mode Full Virtualized Application Para-Virtualized Application Untrusted VMP Modules Hypercalls Supervisor Mode ISA Emulator Dispatcher Hypercall Handler IRQ Handler IPCM VM Scheduler Program IRQ Syscall IRQ PIT IRQ External IRQ Hardware Fig. 2. Information and control flow of the components used inside the virtualization platform. to yield the cpu directly in order to allow system designers to incorporate special scheduling mechanisms. 3 Concepts 3.1 Configurability Achieving only a small overhead as needed for the intended field of use was one of the major design goals of this system. This goal is met by the high flexibility offered through the possibility to configure a wide range of system components. Using the provided configuration files, the system designer is able to enable or disable features of the virtual machine monitor or specify which parts of the hypercall interface shall be supported. The principle workflow of the configuration is depicted in figure 3. The whole configuration workflow is based on the extensive usage of preprocessor statements. Based on the configuration files the preprocessor eliminates, adds or changes code segments inside the implementation files to create a source code which does not suffer from unneeded code parts any more. This is a very valuable feature if the platform is about to be deployed inside a very memory-limited environment. Our virtualization platform allows the system designer to explicitly define whether there is the need for full-virtualization or para-virtualization or even both. It is even possible to configure the support for special parts of the host ISA as e.g. support for virtual memory. The hypercall interface may explicitly
5 Fig. 3. Configuration flow of the virtualization platform. be configured by defining whether para-virtualized drivers are supported, inter partition communication is needed and which scheduler has to be used. Each of the components can then be configured as well to allow the platform to match the needs of the target system to a maximum amount. 3.2 Innocuous Register File Mapping Virtualizing the processor is one of the main tasks of the virtual machine monitor. Every virtual machine gets its own set of virtual registers stored inside the Register File as depicted in figure 4a. Whenever the virtual machine is activated, the registers are copied into the registers of the physical processor. During the execution the virtual machine has unrestricted access to the user space registers of the processor. Registers that need to be accessed by the use of privileged instructions will trap to the virtual machine monitor which then emulates the behaviour of that instruction on the virtual register inside the register file. However, there exist registers which can be accessed without having immediate influence on the state or behaviour of the virtual machine. An example is given by the Save Restore Registers (SRR) of the PowerPC Processor. The value of these registers will only be used whenever the processor executes the privileged recover from interrupt (rfi) instruction. In order to speed up the access to this kind of registers, Proteus uses a technique we call Innocuous Register File Mapping (IRFM) which allows virtual registers to be mapped to memory pages inside the virtual machines accessible memory area as illustrated in figure 4b. Virtual registers, which may be read directly without the need of any emulation, are mapped into a read-only memory page. Registers, that can be either read or written without immediate influence, are made accessible inside a readable and writable memory page whose address can be configured to conform to the systems memory map. Therefore, access to these registers is possible by using load and store commands instead of trapping to the virtual machine monitor which speeds up the virtualized execution of a program dramatically. A similar approach has been
6 Fig. 4. a) Processor Virtualization by using Register Files. b) Innocuous Register File Mapping. Temporarily innocuous register are mapped into pages inside the VM memory space. used inside the ia64 port of the Xen hypervisor [Barham et al., 2003] for desktop systems to speedup the information flow between the hypervisor and the virtual machines. However, the approach has not been applied completely to all possible registers of the ISA as this virtualization platform does. Since the IRFM feature can only be used by para-virtualized applications, partially modified applications may still use privileged instructions to access the virtual registers. In order to ensure the consistency of the mapped registers and the virtual registers inside the register file, the virtual machine monitor updates the mapped registers whenever a value is written to the register file. This feature is called the Innocuous Register File Mapping Fallback Feature and may be enabled if the system designer is unsure whether all privileged instructions are para-virtualized or not. Especially for systems using third party libraries without access to the source code this is a very valuable feature. 3.3 Pre-Virtualization Support As some features like the IRFM are only accessible for para-virtualized applications, our virtualization platform supports a technique called Pre-Virtualization [LeVasseur et al., 2006] which is based on the principle of binary replacement. The technique is based on the idea to append no operation (nop) instructions to every privileged instruction inside the guests applications source code in order to create space for a later replacement of these instructions by hypercall instructions to the virtual machine monitor. The overall process is illustrated exemplarily in figure 5. We developed a python script which first parses the source
7 Fig. 5. Pre-Virtualization illustrated. a) Base source code. b) Pre-Virtualized source code and Pre-Virtualization table. c) The final para-virtualized code. code of an application for privileged instructions. Whenever a privileged instruction is found, its address is stored inside a pre-virtualization table together with the binary code of the hypercall instructions. The code itself is only modified by appending nop instructions to the privileged instructions found. Therefore the intermediate pre-virtualized code can still be executed natively. At loadtime, the virtual machine monitor finally para-virtualizes the pre-virtualized applications by the use of the pre-virtualization table which is stored within the applications data area. 3.4 Programming Concept A substantial part of the virtual machine monitor is comprised of the interrupt handler. Since a significant amount of time is spent inside these routines, most of the components called by the handlers and the handler themselves are directly written in assembly language. By using this methodology it was possible to create source code without the usual overhead induced by higher level languages like C oder C++ and EABI overheads like saving/restoring stack frames. Actually the implemented virtual machine monitor operates without using a stack as often as possible. The amount of registers used by the interrupt handler and emulation routines has been minimized as well to reduce the amount of time needed for a context switch between the virtual machine and the emulation software. Only if higher level activities are processed as e.g. calling the VM scheduler or triggering a driver, the whole context of the virtual machine needs to be saved. Additionally every operation of the virtual machine monitor has been implemented to behave deterministically in order to allow the calculation of an upper bound for the execution time of these operations.
8 native full-virt para-virt Overhead ORCOS + CTask 10, , , ,88% ORCOS + FFTTask 5094, , ,936 0,45% SimpleFFT 294, , ,564 0,00% Table 1. Execution in ms measured for a set of application scenarios and the corresponding percental lengthening of the execution time for the best case compared to the native execution time. 4 Performance Figures The performance overhead introduced by the virtualization software has been measured for a set of application scenarios. We used the real-time operating system ORCOS [University of Paderborn, 2009] running on a PowerPC405 processor to measure the overhead for two application scenarios. The first scenario used a simple periodic real-time task with the only purpose to count a variable to a specific value. The execution time was measured for an interval of two hundred repetitions to get a reasonable measurement. The overhead produced here was about 60% compared to the native execution time. The high overhead in this scenario can be easily explained by the fact that the amount of time spent inside the operating system compared to the amount of time spent inside the real-time task was really high. Thus the relative amount of privileged instructions used by the operating system which needed to be emulated was high as well leading to this kind of overhead. A more realistic scenario was given by another real-time task which had to calculate a Fast Fourier Transformation for a set of input values for a fixed amount of repetitions. Since the relative amount of time spent for this calculation was much higher compared to the amount of emulation routines called the overhead reduced to less then one percent if the application was executed paravirtualized. It is also possible to see that running the unmodified application in full-virtualization mode is only slightly slower. The overhead increased by 0.56% in that case. Considering embedded control systems, which often consist of a comparable amount of calculations, this makes the usage of full-virtualization extremely interesting. Additionally, this observation gives reason to believe that the execution time of applications that could not be para-virtualized completely, since e.g. a part of the application has been linked against static libraries, will not suffer much by running inside our virtual machine. Applications using only the user ISA, as given by the third example application SimpleFFT which calculated a Fast Fourier Transformation without using the support of an operating system, can be executed with native performance because no instruction needs to be emulated by the virtual machine monitor.
9 .text.data Basis System Para-Virtualization Support IRFM Support IRFM Fallback Support Pre-Virtualization Support TLB Virtualization Support Driver Support IPCM Support Table 2. Binary and memory footprint of the virtualization platform in bytes for a set of configurable components for the PowerPC405 processor (32 Bit Architecture). 5 Footprint In order to be deployed on small scale nodes, the memory overhead introduced by the virtual machine monitor needs to be as small as possible. Since Proteus is completely configurable, the amount of binary and memory footprint occupied by the virtual machine monitor strongly depends on the features used by the target system. The basis system, which already supports full-virtualization of the ISA and which is able to emulate a fairly complete set of privileged instructions needs about 4.4 Kb for the binary and about 2.5 Kb for the data structures whereas about 2.4 Kb of the data area, together with the whole text area, may be placed inside the ROM of the host platform. The biggest fraction of the data area is used for dispatching purposes of the ISA emulation dispatcher. Adding Para-Virtualization support, including the whole IRFM feature set, increases the footprint by additional 1.5 Kb. The whole system (with all its features) has a footprint of under 11 Kb with 10 Kb being read-only data or executable code respectively which could be placed inside the ROM memory area of the platform. The sizes listed above do not include the required space for the register files of the virtual machines. Depending on how many virtual machines the hypervisor shall support, additional 304 bytes need to be reserved for every virtual machine for our target processor the PowerPC405. If the TLB needs to be virtualized as well, in order to allow the virtual machines to use virtual memory, the reserved bytes per virtual machine increases by Conclusion and Future Work In this work we presented the first hybrid configurable virtualization platform which supports full-virtualization and para-virtualization as well as a mixture of both as needed. The high configurability allows the system designer to adapt the platform for its dedicated field of use. This feature allows the system to be very small and efficient as the maximum memory overhead induced by the virtual
10 machine monitor is below 11Kb which lets Proteus compete with current State of the Art virtualization platforms like Trango or VirtualLogix. The system combines state of the art features like the IRFM feature and Pre-Virtualization while being implemented directly in assembler to minimize the overhead. Our newly introduced IRFM Fallback feature ensures the consistency while switching between full and para-virtualization. It is designed and implemented to support real-time applications and offers an interface to add deterministic real-time capable hierarchical scheduling mechanisms as e.g. described in [Lipari and Bini, 2005] in the future. We are currently working on further measurements demonstrating the realtime capabilities of the system. Additionally we are working on dynamic selfoptimizing features that shall be integrated into the system in the future. References [Barham et al., 2003] Barham, P., Dragovic, B., Fraser, K., Hand, S., Harris, T., Ho, A., Neugebauery, R., Pratt, I., and Warfield, A. (2003). Xen and the Art of Virtualization. ACM. [Chen and Noble, 2001] Chen, P. M. and Noble, B. D. (2001). When virtual is better than real. In HOTOS 01: Proceedings of the Eighth Workshop on Hot Topics in Operating Systems, page 133, Washington, DC, USA. IEEE Computer Society. [Heiser, 2008] Heiser, G. (2008). The role of virtualization in embedded systems. In IIES 08: Proceedings of the 1st workshop on Isolation and integration in embedded systems, pages 11 16, New York, NY, USA. ACM. [Hills, 2009] Hills, G. (2009). Real-Time Operating Systems (RTOS), Embedded Development Tools, Optimizing Compilers, IDE tools, Debuggers - Green Hills Software. Website. [Laune C. Harris, 2006] Laune C. Harris, B. P. M. (2006). Practical Analysis of Stripped Binary Code. Technical report, Computer Sciences Department, University of Wisconsin. [LeVasseur et al., 2006] LeVasseur, J., Uhlig, V., Chapman, M., Chubb, P., Leslie, B., and Heiser, G. (2006). Pre-virtualization: soft layering for virtual machines. Technical Report , Fakultät für Informatik, Universität Karlsruhe (TH). [Lipari and Bini, 2005] Lipari, G. and Bini, E. (2005). A methodology for designing hierarchical scheduling systems. J. Embedded Comput., 1(2): [LynuxWorks, 2009] LynuxWorks (2009). Embedded Hypervisor and Separation Kernel for Operating-system Virtualization: LynxSecure. Website. [Saumya Debray, 1998] Saumya Debray, Robert Muth, M. W. (1998). Alias Analysis of Executable Code. Technical report, Department of Computer Science, University of Arizona. [Smith and Nair, 2005] Smith, J. and Nair, R. (2005). The architecture of virtual machines. Computer, 38(5): [Systems, 2008] Systems, O. I. (2008). MILS Technical Primer. Website. [University of Paderborn, 2009] University of Paderborn (2009). ORCOS. Website.
11 [VirtualLogix, 2009] VirtualLogix (2009). VirtualLogix - Real-time Virtualization for Connected Devices :: Products - VLX for Embedded Systems:. Website. [VmWare, 2009] VmWare (2009). TRANGO Virtual Prozessors: Scalable security for embedded devices. Website.
COS 318: Operating Systems. Virtual Machine Monitors
 COS 318: Operating Systems Virtual Machine Monitors Kai Li and Andy Bavier Computer Science Department Princeton University http://www.cs.princeton.edu/courses/archive/fall13/cos318/ Introduction u Have
COS 318: Operating Systems Virtual Machine Monitors Kai Li and Andy Bavier Computer Science Department Princeton University http://www.cs.princeton.edu/courses/archive/fall13/cos318/ Introduction u Have
Full and Para Virtualization
 Full and Para Virtualization Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF x86 Hardware Virtualization The x86 architecture offers four levels
Full and Para Virtualization Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF x86 Hardware Virtualization The x86 architecture offers four levels
Virtualization. Pradipta De [email protected]
 Virtualization Pradipta De [email protected] Today s Topic Virtualization Basics System Virtualization Techniques CSE506: Ext Filesystem 2 Virtualization? A virtual machine (VM) is an emulation
Virtualization Pradipta De [email protected] Today s Topic Virtualization Basics System Virtualization Techniques CSE506: Ext Filesystem 2 Virtualization? A virtual machine (VM) is an emulation
KVM: A Hypervisor for All Seasons. Avi Kivity [email protected]
 KVM: A Hypervisor for All Seasons Avi Kivity [email protected] November 2007 Virtualization Simulation of computer system in software Components Processor: register state, instructions, exceptions Memory
KVM: A Hypervisor for All Seasons Avi Kivity [email protected] November 2007 Virtualization Simulation of computer system in software Components Processor: register state, instructions, exceptions Memory
A hypervisor approach with real-time support to the MIPS M5150 processor
 ISQED Wednesday March 4, 2015 Session 5B A hypervisor approach with real-time support to the MIPS M5150 processor Authors: Samir Zampiva ([email protected]) Carlos Moratelli ([email protected])
ISQED Wednesday March 4, 2015 Session 5B A hypervisor approach with real-time support to the MIPS M5150 processor Authors: Samir Zampiva ([email protected]) Carlos Moratelli ([email protected])
Virtualization. Explain how today s virtualization movement is actually a reinvention
 Virtualization Learning Objectives Explain how today s virtualization movement is actually a reinvention of the past. Explain how virtualization works. Discuss the technical challenges to virtualization.
Virtualization Learning Objectives Explain how today s virtualization movement is actually a reinvention of the past. Explain how virtualization works. Discuss the technical challenges to virtualization.
EECatalog SPECIAL FEATURE
 Type Zero Hypervisor the New Frontier in Embedded Virtualization The hypervisor s full control over the hardware platform and ability to virtualize hardware platforms are beneficial in environments that
Type Zero Hypervisor the New Frontier in Embedded Virtualization The hypervisor s full control over the hardware platform and ability to virtualize hardware platforms are beneficial in environments that
Virtual Machine Monitors. Dr. Marc E. Fiuczynski Research Scholar Princeton University
 Virtual Machine Monitors Dr. Marc E. Fiuczynski Research Scholar Princeton University Introduction Have been around since 1960 s on mainframes used for multitasking Good example VM/370 Have resurfaced
Virtual Machine Monitors Dr. Marc E. Fiuczynski Research Scholar Princeton University Introduction Have been around since 1960 s on mainframes used for multitasking Good example VM/370 Have resurfaced
Uses for Virtual Machines. Virtual Machines. There are several uses for virtual machines:
 Virtual Machines Uses for Virtual Machines Virtual machine technology, often just called virtualization, makes one computer behave as several computers by sharing the resources of a single computer between
Virtual Machines Uses for Virtual Machines Virtual machine technology, often just called virtualization, makes one computer behave as several computers by sharing the resources of a single computer between
Chapter 5 Cloud Resource Virtualization
 Chapter 5 Cloud Resource Virtualization Contents Virtualization. Layering and virtualization. Virtual machine monitor. Virtual machine. Performance and security isolation. Architectural support for virtualization.
Chapter 5 Cloud Resource Virtualization Contents Virtualization. Layering and virtualization. Virtual machine monitor. Virtual machine. Performance and security isolation. Architectural support for virtualization.
Microkernels, virtualization, exokernels. Tutorial 1 CSC469
 Microkernels, virtualization, exokernels Tutorial 1 CSC469 Monolithic kernel vs Microkernel Monolithic OS kernel Application VFS System call User mode What was the main idea? What were the problems? IPC,
Microkernels, virtualization, exokernels Tutorial 1 CSC469 Monolithic kernel vs Microkernel Monolithic OS kernel Application VFS System call User mode What was the main idea? What were the problems? IPC,
VMware Server 2.0 Essentials. Virtualization Deployment and Management
 VMware Server 2.0 Essentials Virtualization Deployment and Management . This PDF is provided for personal use only. Unauthorized use, reproduction and/or distribution strictly prohibited. All rights reserved.
VMware Server 2.0 Essentials Virtualization Deployment and Management . This PDF is provided for personal use only. Unauthorized use, reproduction and/or distribution strictly prohibited. All rights reserved.
Hypervisors. Introduction. Introduction. Introduction. Introduction. Introduction. Credits:
 Hypervisors Credits: P. Chaganti Xen Virtualization A practical handbook D. Chisnall The definitive guide to Xen Hypervisor G. Kesden Lect. 25 CS 15-440 G. Heiser UNSW/NICTA/OKL Virtualization is a technique
Hypervisors Credits: P. Chaganti Xen Virtualization A practical handbook D. Chisnall The definitive guide to Xen Hypervisor G. Kesden Lect. 25 CS 15-440 G. Heiser UNSW/NICTA/OKL Virtualization is a technique
Virtual machines and operating systems
 V i r t u a l m a c h i n e s a n d o p e r a t i n g s y s t e m s Virtual machines and operating systems Krzysztof Lichota [email protected] A g e n d a Virtual machines and operating systems interactions
V i r t u a l m a c h i n e s a n d o p e r a t i n g s y s t e m s Virtual machines and operating systems Krzysztof Lichota [email protected] A g e n d a Virtual machines and operating systems interactions
Virtualization. Dr. Yingwu Zhu
 Virtualization Dr. Yingwu Zhu What is virtualization? Virtualization allows one computer to do the job of multiple computers. Virtual environments let one computer host multiple operating systems at the
Virtualization Dr. Yingwu Zhu What is virtualization? Virtualization allows one computer to do the job of multiple computers. Virtual environments let one computer host multiple operating systems at the
Models For Modeling and Measuring the Performance of a Xen Virtual Server
 Measuring and Modeling the Performance of the Xen VMM Jie Lu, Lev Makhlis, Jianjiun Chen BMC Software Inc. Waltham, MA 2451 Server virtualization technology provides an alternative for server consolidation
Measuring and Modeling the Performance of the Xen VMM Jie Lu, Lev Makhlis, Jianjiun Chen BMC Software Inc. Waltham, MA 2451 Server virtualization technology provides an alternative for server consolidation
Basics of Virtualisation
 Basics of Virtualisation Volker Büge Institut für Experimentelle Kernphysik Universität Karlsruhe Die Kooperation von The x86 Architecture Why do we need virtualisation? x86 based operating systems are
Basics of Virtualisation Volker Büge Institut für Experimentelle Kernphysik Universität Karlsruhe Die Kooperation von The x86 Architecture Why do we need virtualisation? x86 based operating systems are
Xen and the Art of. Virtualization. Ian Pratt
 Xen and the Art of Virtualization Ian Pratt Keir Fraser, Steve Hand, Christian Limpach, Dan Magenheimer (HP), Mike Wray (HP), R Neugebauer (Intel), M Williamson (Intel) Computer Laboratory Outline Virtualization
Xen and the Art of Virtualization Ian Pratt Keir Fraser, Steve Hand, Christian Limpach, Dan Magenheimer (HP), Mike Wray (HP), R Neugebauer (Intel), M Williamson (Intel) Computer Laboratory Outline Virtualization
12. Introduction to Virtual Machines
 12. Introduction to Virtual Machines 12. Introduction to Virtual Machines Modern Applications Challenges of Virtual Machine Monitors Historical Perspective Classification 332 / 352 12. Introduction to
12. Introduction to Virtual Machines 12. Introduction to Virtual Machines Modern Applications Challenges of Virtual Machine Monitors Historical Perspective Classification 332 / 352 12. Introduction to
Virtualization in the ARMv7 Architecture Lecture for the Embedded Systems Course CSD, University of Crete (May 20, 2014)
 Virtualization in the ARMv7 Architecture Lecture for the Embedded Systems Course CSD, University of Crete (May 20, 2014) ManolisMarazakis ([email protected]) Institute of Computer Science (ICS) Foundation
Virtualization in the ARMv7 Architecture Lecture for the Embedded Systems Course CSD, University of Crete (May 20, 2014) ManolisMarazakis ([email protected]) Institute of Computer Science (ICS) Foundation
VxWorks Guest OS Programmer's Guide for Hypervisor 1.1, 6.8. VxWorks GUEST OS PROGRAMMER'S GUIDE FOR HYPERVISOR 1.1 6.8
 VxWorks Guest OS Programmer's Guide for Hypervisor 1.1, 6.8 VxWorks GUEST OS PROGRAMMER'S GUIDE FOR HYPERVISOR 1.1 6.8 Copyright 2009 Wind River Systems, Inc. All rights reserved. No part of this publication
VxWorks Guest OS Programmer's Guide for Hypervisor 1.1, 6.8 VxWorks GUEST OS PROGRAMMER'S GUIDE FOR HYPERVISOR 1.1 6.8 Copyright 2009 Wind River Systems, Inc. All rights reserved. No part of this publication
Virtualization Technologies (ENCS 691K Chapter 3)
 Virtualization Technologies (ENCS 691K Chapter 3) Roch Glitho, PhD Associate Professor and Canada Research Chair My URL - http://users.encs.concordia.ca/~glitho/ The Key Technologies on Which Cloud Computing
Virtualization Technologies (ENCS 691K Chapter 3) Roch Glitho, PhD Associate Professor and Canada Research Chair My URL - http://users.encs.concordia.ca/~glitho/ The Key Technologies on Which Cloud Computing
evm Virtualization Platform for Windows
 B A C K G R O U N D E R evm Virtualization Platform for Windows Host your Embedded OS and Windows on a Single Hardware Platform using Intel Virtualization Technology April, 2008 TenAsys Corporation 1400
B A C K G R O U N D E R evm Virtualization Platform for Windows Host your Embedded OS and Windows on a Single Hardware Platform using Intel Virtualization Technology April, 2008 TenAsys Corporation 1400
System Virtual Machines
 System Virtual Machines Introduction Key concepts Resource virtualization processors memory I/O devices Performance issues Applications 1 Introduction System virtual machine capable of supporting multiple
System Virtual Machines Introduction Key concepts Resource virtualization processors memory I/O devices Performance issues Applications 1 Introduction System virtual machine capable of supporting multiple
Virtualization for Cloud Computing
 Virtualization for Cloud Computing Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF CLOUD COMPUTING On demand provision of computational resources
Virtualization for Cloud Computing Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF CLOUD COMPUTING On demand provision of computational resources
Virtualization Technology. Zhiming Shen
 Virtualization Technology Zhiming Shen Virtualization: rejuvenation 1960 s: first track of virtualization Time and resource sharing on expensive mainframes IBM VM/370 Late 1970 s and early 1980 s: became
Virtualization Technology Zhiming Shen Virtualization: rejuvenation 1960 s: first track of virtualization Time and resource sharing on expensive mainframes IBM VM/370 Late 1970 s and early 1980 s: became
Chapter 2 Addendum (More on Virtualization)
 Chapter 2 Addendum (More on Virtualization) Roch Glitho, PhD Associate Professor and Canada Research Chair My URL - http://users.encs.concordia.ca/~glitho/ More on Systems Virtualization Type I (bare metal)
Chapter 2 Addendum (More on Virtualization) Roch Glitho, PhD Associate Professor and Canada Research Chair My URL - http://users.encs.concordia.ca/~glitho/ More on Systems Virtualization Type I (bare metal)
COS 318: Operating Systems. Virtual Machine Monitors
 COS 318: Operating Systems Virtual Machine Monitors Andy Bavier Computer Science Department Princeton University http://www.cs.princeton.edu/courses/archive/fall10/cos318/ Introduction Have been around
COS 318: Operating Systems Virtual Machine Monitors Andy Bavier Computer Science Department Princeton University http://www.cs.princeton.edu/courses/archive/fall10/cos318/ Introduction Have been around
Performance Comparison of VMware and Xen Hypervisor on Guest OS
 ISSN: 2393-8528 Contents lists available at www.ijicse.in International Journal of Innovative Computer Science & Engineering Volume 2 Issue 3; July-August-2015; Page No. 56-60 Performance Comparison of
ISSN: 2393-8528 Contents lists available at www.ijicse.in International Journal of Innovative Computer Science & Engineering Volume 2 Issue 3; July-August-2015; Page No. 56-60 Performance Comparison of
Architecture of the Kernel-based Virtual Machine (KVM)
 Corporate Technology Architecture of the Kernel-based Virtual Machine (KVM) Jan Kiszka, Siemens AG, CT T DE IT 1 Corporate Competence Center Embedded Linux [email protected] Copyright Siemens AG 2010.
Corporate Technology Architecture of the Kernel-based Virtual Machine (KVM) Jan Kiszka, Siemens AG, CT T DE IT 1 Corporate Competence Center Embedded Linux [email protected] Copyright Siemens AG 2010.
Virtualization. Jukka K. Nurminen 23.9.2015
 Virtualization Jukka K. Nurminen 23.9.2015 Virtualization Virtualization refers to the act of creating a virtual (rather than actual) version of something, including virtual computer hardware platforms,
Virtualization Jukka K. Nurminen 23.9.2015 Virtualization Virtualization refers to the act of creating a virtual (rather than actual) version of something, including virtual computer hardware platforms,
x86 ISA Modifications to support Virtual Machines
 x86 ISA Modifications to support Virtual Machines Douglas Beal Ashish Kumar Gupta CSE 548 Project Outline of the talk Review of Virtual Machines What complicates Virtualization Technique for Virtualization
x86 ISA Modifications to support Virtual Machines Douglas Beal Ashish Kumar Gupta CSE 548 Project Outline of the talk Review of Virtual Machines What complicates Virtualization Technique for Virtualization
Outline. Outline. Why virtualization? Why not virtualize? Today s data center. Cloud computing. Virtual resource pool
 Outline CS 6V81-05: System Security and Malicious Code Analysis Overview of System ization: The most powerful platform for program analysis and system security Zhiqiang Lin Department of Computer Science
Outline CS 6V81-05: System Security and Malicious Code Analysis Overview of System ization: The most powerful platform for program analysis and system security Zhiqiang Lin Department of Computer Science
VIRTUALIZATION, The next step for online services
 Scientific Bulletin of the Petru Maior University of Tîrgu Mureş Vol. 10 (XXVII) no. 1, 2013 ISSN-L 1841-9267 (Print), ISSN 2285-438X (Online), ISSN 2286-3184 (CD-ROM) VIRTUALIZATION, The next step for
Scientific Bulletin of the Petru Maior University of Tîrgu Mureş Vol. 10 (XXVII) no. 1, 2013 ISSN-L 1841-9267 (Print), ISSN 2285-438X (Online), ISSN 2286-3184 (CD-ROM) VIRTUALIZATION, The next step for
Leveraging Thin Hypervisors for Security on Embedded Systems
 Leveraging Thin Hypervisors for Security on Embedded Systems Christian Gehrmann A part of Swedish ICT What is virtualization? Separation of a resource or request for a service from the underlying physical
Leveraging Thin Hypervisors for Security on Embedded Systems Christian Gehrmann A part of Swedish ICT What is virtualization? Separation of a resource or request for a service from the underlying physical
How To Compare Performance Of A Router On A Hypervisor On A Linux Virtualbox 2.5 (Xen) To A Virtualbox 3.5.2 (Xeen) 2.2.5-Xen-Virtualization (X
 Performance Evaluation of Virtual Routers in Para-virtual Environment 1. Abhishek Bajaj [email protected] 2. Anargha Biswas [email protected] 3. Ambarish Kumar [email protected] 4.
Performance Evaluation of Virtual Routers in Para-virtual Environment 1. Abhishek Bajaj [email protected] 2. Anargha Biswas [email protected] 3. Ambarish Kumar [email protected] 4.
VMkit A lightweight hypervisor library for Barrelfish
 Masters Thesis VMkit A lightweight hypervisor library for Barrelfish by Raffaele Sandrini Due date 2 September 2009 Advisors: Simon Peter, Andrew Baumann, and Timothy Roscoe ETH Zurich, Systems Group Department
Masters Thesis VMkit A lightweight hypervisor library for Barrelfish by Raffaele Sandrini Due date 2 September 2009 Advisors: Simon Peter, Andrew Baumann, and Timothy Roscoe ETH Zurich, Systems Group Department
Hybrid Virtualization The Next Generation of XenLinux
 Hybrid Virtualization The Next Generation of XenLinux Jun Nakajima Principal Engineer Intel Open Source Technology Center Legal Disclaimer INFORMATION IN THIS DOCUMENT IS PROVIDED IN CONNECTION WITH INTEL
Hybrid Virtualization The Next Generation of XenLinux Jun Nakajima Principal Engineer Intel Open Source Technology Center Legal Disclaimer INFORMATION IN THIS DOCUMENT IS PROVIDED IN CONNECTION WITH INTEL
The Xen of Virtualization
 The Xen of Virtualization Assignment for CLC-MIRI Amin Khan Universitat Politècnica de Catalunya March 4, 2013 Amin Khan (UPC) Xen Hypervisor March 4, 2013 1 / 19 Outline 1 Introduction 2 Architecture
The Xen of Virtualization Assignment for CLC-MIRI Amin Khan Universitat Politècnica de Catalunya March 4, 2013 Amin Khan (UPC) Xen Hypervisor March 4, 2013 1 / 19 Outline 1 Introduction 2 Architecture
Virtualization. Jia Rao Assistant Professor in CS http://cs.uccs.edu/~jrao/
 Virtualization Jia Rao Assistant Professor in CS http://cs.uccs.edu/~jrao/ What is Virtualization? Virtualization is the simulation of the software and/ or hardware upon which other software runs. This
Virtualization Jia Rao Assistant Professor in CS http://cs.uccs.edu/~jrao/ What is Virtualization? Virtualization is the simulation of the software and/ or hardware upon which other software runs. This
Virtualization: Hypervisors for Embedded and Safe Systems. Hanspeter Vogel Triadem Solutions AG
 1 Virtualization: Hypervisors for Embedded and Safe Systems Hanspeter Vogel Triadem Solutions AG 2 Agenda Use cases for virtualization Terminology Hypervisor Solutions Realtime System Hypervisor Features
1 Virtualization: Hypervisors for Embedded and Safe Systems Hanspeter Vogel Triadem Solutions AG 2 Agenda Use cases for virtualization Terminology Hypervisor Solutions Realtime System Hypervisor Features
Virtualization. Types of Interfaces
 Virtualization Virtualization: extend or replace an existing interface to mimic the behavior of another system. Introduced in 1970s: run legacy software on newer mainframe hardware Handle platform diversity
Virtualization Virtualization: extend or replace an existing interface to mimic the behavior of another system. Introduced in 1970s: run legacy software on newer mainframe hardware Handle platform diversity
Virtual Machines. www.viplavkambli.com
 1 Virtual Machines A virtual machine (VM) is a "completely isolated guest operating system installation within a normal host operating system". Modern virtual machines are implemented with either software
1 Virtual Machines A virtual machine (VM) is a "completely isolated guest operating system installation within a normal host operating system". Modern virtual machines are implemented with either software
Parallels Virtuozzo Containers
 Parallels Virtuozzo Containers White Paper Top Ten Considerations For Choosing A Server Virtualization Technology www.parallels.com Version 1.0 Table of Contents Introduction... 3 Technology Overview...
Parallels Virtuozzo Containers White Paper Top Ten Considerations For Choosing A Server Virtualization Technology www.parallels.com Version 1.0 Table of Contents Introduction... 3 Technology Overview...
Security Overview of the Integrity Virtual Machines Architecture
 Security Overview of the Integrity Virtual Machines Architecture Introduction... 2 Integrity Virtual Machines Architecture... 2 Virtual Machine Host System... 2 Virtual Machine Control... 2 Scheduling
Security Overview of the Integrity Virtual Machines Architecture Introduction... 2 Integrity Virtual Machines Architecture... 2 Virtual Machine Host System... 2 Virtual Machine Control... 2 Scheduling
OS Virtualization Frank Hofmann
 OS Virtualization Frank Hofmann OP/N1 Released Products Engineering Sun Microsystems UK Overview Different approaches to virtualization > Compartmentalization > System Personalities > Virtual Machines
OS Virtualization Frank Hofmann OP/N1 Released Products Engineering Sun Microsystems UK Overview Different approaches to virtualization > Compartmentalization > System Personalities > Virtual Machines
How do Users and Processes interact with the Operating System? Services for Processes. OS Structure with Services. Services for the OS Itself
 How do Users and Processes interact with the Operating System? Users interact indirectly through a collection of system programs that make up the operating system interface. The interface could be: A GUI,
How do Users and Processes interact with the Operating System? Users interact indirectly through a collection of system programs that make up the operating system interface. The interface could be: A GUI,
Virtualization and the U2 Databases
 Virtualization and the U2 Databases Brian Kupzyk Senior Technical Support Engineer for Rocket U2 Nik Kesic Lead Technical Support for Rocket U2 Opening Procedure Orange arrow allows you to manipulate the
Virtualization and the U2 Databases Brian Kupzyk Senior Technical Support Engineer for Rocket U2 Nik Kesic Lead Technical Support for Rocket U2 Opening Procedure Orange arrow allows you to manipulate the
The MIPS architecture and virtualization
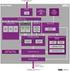 The MIPS architecture and virtualization Simply put, virtualization makes one physical device appear as one or more virtual devices. Virtualization can be implemented at the processor level (e.g. CPU or
The MIPS architecture and virtualization Simply put, virtualization makes one physical device appear as one or more virtual devices. Virtualization can be implemented at the processor level (e.g. CPU or
Virtualization. Clothing the Wolf in Wool. Wednesday, April 17, 13
 Virtualization Clothing the Wolf in Wool Virtual Machines Began in 1960s with IBM and MIT Project MAC Also called open shop operating systems Present user with the view of a bare machine Execute most instructions
Virtualization Clothing the Wolf in Wool Virtual Machines Began in 1960s with IBM and MIT Project MAC Also called open shop operating systems Present user with the view of a bare machine Execute most instructions
Virtual Hosting & Virtual Machines
 & Virtual Machines Coleman Kane [email protected] September 2, 2014 Cyber Defense Overview / Machines 1 / 17 Similar to the network partitioning schemes described previously, there exist a menu of options
& Virtual Machines Coleman Kane [email protected] September 2, 2014 Cyber Defense Overview / Machines 1 / 17 Similar to the network partitioning schemes described previously, there exist a menu of options
Virtualization and Other Tricks.
 Virtualization and Other Tricks. Pavel Parízek, Tomáš Kalibera, Peter Libič DEPARTMENT OF DISTRIBUTED AND DEPENDABLE SYSTEMS http://d3s.mff.cuni.cz CHARLES UNIVERSITY PRAGUE Faculty of Mathematics and
Virtualization and Other Tricks. Pavel Parízek, Tomáš Kalibera, Peter Libič DEPARTMENT OF DISTRIBUTED AND DEPENDABLE SYSTEMS http://d3s.mff.cuni.cz CHARLES UNIVERSITY PRAGUE Faculty of Mathematics and
Cloud Computing #6 - Virtualization
 Cloud Computing #6 - Virtualization Main source: Smith & Nair, Virtual Machines, Morgan Kaufmann, 2005 Today What do we mean by virtualization? Why is it important to cloud? What is the penalty? Current
Cloud Computing #6 - Virtualization Main source: Smith & Nair, Virtual Machines, Morgan Kaufmann, 2005 Today What do we mean by virtualization? Why is it important to cloud? What is the penalty? Current
Virtual Computing and VMWare. Module 4
 Virtual Computing and VMWare Module 4 Virtual Computing Cyber Defense program depends on virtual computing We will use it for hands-on learning Cyber defense competition will be hosted on a virtual computing
Virtual Computing and VMWare Module 4 Virtual Computing Cyber Defense program depends on virtual computing We will use it for hands-on learning Cyber defense competition will be hosted on a virtual computing
DIABLO TECHNOLOGIES MEMORY CHANNEL STORAGE AND VMWARE VIRTUAL SAN : VDI ACCELERATION
 DIABLO TECHNOLOGIES MEMORY CHANNEL STORAGE AND VMWARE VIRTUAL SAN : VDI ACCELERATION A DIABLO WHITE PAPER AUGUST 2014 Ricky Trigalo Director of Business Development Virtualization, Diablo Technologies
DIABLO TECHNOLOGIES MEMORY CHANNEL STORAGE AND VMWARE VIRTUAL SAN : VDI ACCELERATION A DIABLO WHITE PAPER AUGUST 2014 Ricky Trigalo Director of Business Development Virtualization, Diablo Technologies
Virtual Machines. Virtualization
 Virtual Machines Marie Roch Tanenbaum 8.3 contains slides from: Tanenbaum 3 rd ed. 2008 1 Virtualization Started with the IBM System/360 in the 1960s Basic concept simulate multiple copies of the underlying
Virtual Machines Marie Roch Tanenbaum 8.3 contains slides from: Tanenbaum 3 rd ed. 2008 1 Virtualization Started with the IBM System/360 in the 1960s Basic concept simulate multiple copies of the underlying
Xen and the Art of Virtualization
 Xen and the Art of Virtualization Paul Barham, Boris Dragovic, Keir Fraser, Steven Hand, Tim Harris, Alex Ho, Rolf Neugebauery, Ian Pratt, Andrew Warfield University of Cambridge Computer Laboratory, SOSP
Xen and the Art of Virtualization Paul Barham, Boris Dragovic, Keir Fraser, Steven Hand, Tim Harris, Alex Ho, Rolf Neugebauery, Ian Pratt, Andrew Warfield University of Cambridge Computer Laboratory, SOSP
MobiVMM: a Virtual Machine Monitor for Mobile Phones
 MobiVMM: a Virtual Machine Monitor for Mobile Phones Seehwan Yoo [email protected] Chuck Yoo [email protected] Yunxin Liu Shanghai Jiaotong University Microsoft Research Asia, China [email protected]
MobiVMM: a Virtual Machine Monitor for Mobile Phones Seehwan Yoo [email protected] Chuck Yoo [email protected] Yunxin Liu Shanghai Jiaotong University Microsoft Research Asia, China [email protected]
www.see-grid-sci.eu Regional SEE-GRID-SCI Training for Site Administrators Institute of Physics Belgrade March 5-6, 2009
 SEE-GRID-SCI Virtualization and Grid Computing with XEN www.see-grid-sci.eu Regional SEE-GRID-SCI Training for Site Administrators Institute of Physics Belgrade March 5-6, 2009 Milan Potocnik University
SEE-GRID-SCI Virtualization and Grid Computing with XEN www.see-grid-sci.eu Regional SEE-GRID-SCI Training for Site Administrators Institute of Physics Belgrade March 5-6, 2009 Milan Potocnik University
Operating System Organization. Purpose of an OS
 Slide 3-1 Operating System Organization Purpose of an OS Slide 3-2 es Coordinate Use of the Abstractions he Abstractions Create the Abstractions 1 OS Requirements Slide 3-3 Provide resource abstractions
Slide 3-1 Operating System Organization Purpose of an OS Slide 3-2 es Coordinate Use of the Abstractions he Abstractions Create the Abstractions 1 OS Requirements Slide 3-3 Provide resource abstractions
Operating Systems. Lecture 03. February 11, 2013
 Operating Systems Lecture 03 February 11, 2013 Goals for Today Interrupts, traps and signals Hardware Protection System Calls Interrupts, Traps, and Signals The occurrence of an event is usually signaled
Operating Systems Lecture 03 February 11, 2013 Goals for Today Interrupts, traps and signals Hardware Protection System Calls Interrupts, Traps, and Signals The occurrence of an event is usually signaled
Analysis on Virtualization Technologies in Cloud
 Analysis on Virtualization Technologies in Cloud 1 V RaviTeja Kanakala, V.Krishna Reddy, K.Thirupathi Rao 1 Research Scholar, Department of CSE, KL University, Vaddeswaram, India I. Abstract Virtualization
Analysis on Virtualization Technologies in Cloud 1 V RaviTeja Kanakala, V.Krishna Reddy, K.Thirupathi Rao 1 Research Scholar, Department of CSE, KL University, Vaddeswaram, India I. Abstract Virtualization
Nested Virtualization
 Nested Virtualization Dongxiao Xu, Xiantao Zhang, Yang Zhang May 9, 2013 Agenda Nested Virtualization Overview Dive into Nested Virtualization Details Nested CPU Virtualization Nested MMU Virtualization
Nested Virtualization Dongxiao Xu, Xiantao Zhang, Yang Zhang May 9, 2013 Agenda Nested Virtualization Overview Dive into Nested Virtualization Details Nested CPU Virtualization Nested MMU Virtualization
A Survey on Virtual Machine Security
 A Survey on Virtual Machine Security Jenni Susan Reuben Helsinki University of Technology [email protected] Abstract Virtualization plays a major role in helping the organizations to reduce the operational
A Survey on Virtual Machine Security Jenni Susan Reuben Helsinki University of Technology [email protected] Abstract Virtualization plays a major role in helping the organizations to reduce the operational
Xen Live Migration. Networks and Distributed Systems Seminar, 24 April 2006. Matúš Harvan Xen Live Migration 1
 Xen Live Migration Matúš Harvan Networks and Distributed Systems Seminar, 24 April 2006 Matúš Harvan Xen Live Migration 1 Outline 1 Xen Overview 2 Live migration General Memory, Network, Storage Migration
Xen Live Migration Matúš Harvan Networks and Distributed Systems Seminar, 24 April 2006 Matúš Harvan Xen Live Migration 1 Outline 1 Xen Overview 2 Live migration General Memory, Network, Storage Migration
XtratuM: a Hypervisor for Safety Critical Embedded Systems
 XtratuM: a Hypervisor for Safety Critical Embedded Systems M. Masmano, I. Ripoll, and A. Crespo Instituto de Informática Industrial, Universidad Politécnica de Valencia (Spain) {mmasmano, iripoll, alfons}@ai2.upv.es
XtratuM: a Hypervisor for Safety Critical Embedded Systems M. Masmano, I. Ripoll, and A. Crespo Instituto de Informática Industrial, Universidad Politécnica de Valencia (Spain) {mmasmano, iripoll, alfons}@ai2.upv.es
Virtualization: What does it mean for SAS? Karl Fisher and Clarke Thacher, SAS Institute Inc., Cary, NC
 Paper 347-2009 Virtualization: What does it mean for SAS? Karl Fisher and Clarke Thacher, SAS Institute Inc., Cary, NC ABSTRACT SAS groups virtualization into four categories: Hardware Virtualization,
Paper 347-2009 Virtualization: What does it mean for SAS? Karl Fisher and Clarke Thacher, SAS Institute Inc., Cary, NC ABSTRACT SAS groups virtualization into four categories: Hardware Virtualization,
PERFORMANCE ANALYSIS OF KERNEL-BASED VIRTUAL MACHINE
 PERFORMANCE ANALYSIS OF KERNEL-BASED VIRTUAL MACHINE Sudha M 1, Harish G M 2, Nandan A 3, Usha J 4 1 Department of MCA, R V College of Engineering, Bangalore : 560059, India [email protected] 2 Department
PERFORMANCE ANALYSIS OF KERNEL-BASED VIRTUAL MACHINE Sudha M 1, Harish G M 2, Nandan A 3, Usha J 4 1 Department of MCA, R V College of Engineering, Bangalore : 560059, India [email protected] 2 Department
Performance tuning Xen
 Performance tuning Xen Roger Pau Monné [email protected] Madrid 8th of November, 2013 Xen Architecture Control Domain NetBSD or Linux device model (qemu) Hardware Drivers toolstack netback blkback Paravirtualized
Performance tuning Xen Roger Pau Monné [email protected] Madrid 8th of November, 2013 Xen Architecture Control Domain NetBSD or Linux device model (qemu) Hardware Drivers toolstack netback blkback Paravirtualized
Distributed and Cloud Computing
 Distributed and Cloud Computing K. Hwang, G. Fox and J. Dongarra Chapter 3: Virtual Machines and Virtualization of Clusters and datacenters Adapted from Kai Hwang University of Southern California March
Distributed and Cloud Computing K. Hwang, G. Fox and J. Dongarra Chapter 3: Virtual Machines and Virtualization of Clusters and datacenters Adapted from Kai Hwang University of Southern California March
Introduction to Virtual Machines
 Introduction to Virtual Machines Introduction Abstraction and interfaces Virtualization Computer system architecture Process virtual machines System virtual machines 1 Abstraction Mechanism to manage complexity
Introduction to Virtual Machines Introduction Abstraction and interfaces Virtualization Computer system architecture Process virtual machines System virtual machines 1 Abstraction Mechanism to manage complexity
Virtualization. Michael Tsai 2015/06/08
 Virtualization Michael Tsai 2015/06/08 What is virtualization? Let s first look at a video from VMware http://bcove.me/x9zhalcl Problems? Low utilization Different needs DNS DHCP Web mail 5% 5% 15% 8%
Virtualization Michael Tsai 2015/06/08 What is virtualization? Let s first look at a video from VMware http://bcove.me/x9zhalcl Problems? Low utilization Different needs DNS DHCP Web mail 5% 5% 15% 8%
Cloud Computing. Up until now
 Cloud Computing Lecture 11 Virtualization 2011-2012 Up until now Introduction. Definition of Cloud Computing Grid Computing Content Distribution Networks Map Reduce Cycle-Sharing 1 Process Virtual Machines
Cloud Computing Lecture 11 Virtualization 2011-2012 Up until now Introduction. Definition of Cloud Computing Grid Computing Content Distribution Networks Map Reduce Cycle-Sharing 1 Process Virtual Machines
White Paper. Real-time Capabilities for Linux SGI REACT Real-Time for Linux
 White Paper Real-time Capabilities for Linux SGI REACT Real-Time for Linux Abstract This white paper describes the real-time capabilities provided by SGI REACT Real-Time for Linux. software. REACT enables
White Paper Real-time Capabilities for Linux SGI REACT Real-Time for Linux Abstract This white paper describes the real-time capabilities provided by SGI REACT Real-Time for Linux. software. REACT enables
Virtualization. P. A. Wilsey. The text highlighted in green in these slides contain external hyperlinks. 1 / 16
 Virtualization P. A. Wilsey The text highlighted in green in these slides contain external hyperlinks. 1 / 16 Conventional System Viewed as Layers This illustration is a common presentation of the application/operating
Virtualization P. A. Wilsey The text highlighted in green in these slides contain external hyperlinks. 1 / 16 Conventional System Viewed as Layers This illustration is a common presentation of the application/operating
Hypervisors and Virtual Machines
 Hypervisors and Virtual Machines Implementation Insights on the x86 Architecture DON REVELLE Don is a performance engineer and Linux systems/kernel programmer, specializing in high-volume UNIX, Web, virtualization,
Hypervisors and Virtual Machines Implementation Insights on the x86 Architecture DON REVELLE Don is a performance engineer and Linux systems/kernel programmer, specializing in high-volume UNIX, Web, virtualization,
CS 695 Topics in Virtualization and Cloud Computing. More Introduction + Processor Virtualization
 CS 695 Topics in Virtualization and Cloud Computing More Introduction + Processor Virtualization (source for all images: Virtual Machines: Versatile Platforms for Systems and Processes Morgan Kaufmann;
CS 695 Topics in Virtualization and Cloud Computing More Introduction + Processor Virtualization (source for all images: Virtual Machines: Versatile Platforms for Systems and Processes Morgan Kaufmann;
Distributed Systems. Virtualization. Paul Krzyzanowski [email protected]
 Distributed Systems Virtualization Paul Krzyzanowski [email protected] Except as otherwise noted, the content of this presentation is licensed under the Creative Commons Attribution 2.5 License. Virtualization
Distributed Systems Virtualization Paul Krzyzanowski [email protected] Except as otherwise noted, the content of this presentation is licensed under the Creative Commons Attribution 2.5 License. Virtualization
Arwed Tschoeke, Systems Architect [email protected] IBM Systems and Technology Group
 Virtualization in a Nutshell Arwed Tschoeke, Systems Architect [email protected] and Technology Group Virtualization Say What? Virtual Resources Proxies for real resources: same interfaces/functions,
Virtualization in a Nutshell Arwed Tschoeke, Systems Architect [email protected] and Technology Group Virtualization Say What? Virtual Resources Proxies for real resources: same interfaces/functions,
Enterprise-Class Virtualization with Open Source Technologies
 Enterprise-Class Virtualization with Open Source Technologies Alex Vasilevsky CTO & Founder Virtual Iron Software June 14, 2006 Virtualization Overview Traditional x86 Architecture Each server runs single
Enterprise-Class Virtualization with Open Source Technologies Alex Vasilevsky CTO & Founder Virtual Iron Software June 14, 2006 Virtualization Overview Traditional x86 Architecture Each server runs single
Cloud^H^H^H^H^H Virtualization Technology. Andrew Jones ([email protected]) May 2011
 Cloud^H^H^H^H^H Virtualization Technology Andrew Jones ([email protected]) May 2011 Outline Promise to not use the word Cloud again...but still give a couple use cases for Virtualization Emulation it's
Cloud^H^H^H^H^H Virtualization Technology Andrew Jones ([email protected]) May 2011 Outline Promise to not use the word Cloud again...but still give a couple use cases for Virtualization Emulation it's
Virtual Machines. COMP 3361: Operating Systems I Winter 2015 http://www.cs.du.edu/3361
 s COMP 3361: Operating Systems I Winter 2015 http://www.cs.du.edu/3361 1 Virtualization! Create illusion of multiple machines on the same physical hardware! Single computer hosts multiple virtual machines
s COMP 3361: Operating Systems I Winter 2015 http://www.cs.du.edu/3361 1 Virtualization! Create illusion of multiple machines on the same physical hardware! Single computer hosts multiple virtual machines
Hardware accelerated Virtualization in the ARM Cortex Processors
 Hardware accelerated Virtualization in the ARM Cortex Processors John Goodacre Director, Program Management ARM Processor Division ARM Ltd. Cambridge UK 2nd November 2010 Sponsored by: & & New Capabilities
Hardware accelerated Virtualization in the ARM Cortex Processors John Goodacre Director, Program Management ARM Processor Division ARM Ltd. Cambridge UK 2nd November 2010 Sponsored by: & & New Capabilities
GUEST OPERATING SYSTEM BASED PERFORMANCE COMPARISON OF VMWARE AND XEN HYPERVISOR
 GUEST OPERATING SYSTEM BASED PERFORMANCE COMPARISON OF VMWARE AND XEN HYPERVISOR ANKIT KUMAR, SAVITA SHIWANI 1 M. Tech Scholar, Software Engineering, Suresh Gyan Vihar University, Rajasthan, India, Email:
GUEST OPERATING SYSTEM BASED PERFORMANCE COMPARISON OF VMWARE AND XEN HYPERVISOR ANKIT KUMAR, SAVITA SHIWANI 1 M. Tech Scholar, Software Engineering, Suresh Gyan Vihar University, Rajasthan, India, Email:
OS Virtualization. CSC 456 Final Presentation Brandon D. Shroyer
 OS Virtualization CSC 456 Final Presentation Brandon D. Shroyer Introduction Virtualization: Providing an interface to software that maps to some underlying system. A one-to-one mapping between a guest
OS Virtualization CSC 456 Final Presentation Brandon D. Shroyer Introduction Virtualization: Providing an interface to software that maps to some underlying system. A one-to-one mapping between a guest
CS5460: Operating Systems. Lecture: Virtualization 2. Anton Burtsev March, 2013
 CS5460: Operating Systems Lecture: Virtualization 2 Anton Burtsev March, 2013 Paravirtualization: Xen Full virtualization Complete illusion of physical hardware Trap _all_ sensitive instructions Virtualized
CS5460: Operating Systems Lecture: Virtualization 2 Anton Burtsev March, 2013 Paravirtualization: Xen Full virtualization Complete illusion of physical hardware Trap _all_ sensitive instructions Virtualized
Dynamic resource management for energy saving in the cloud computing environment
 Dynamic resource management for energy saving in the cloud computing environment Liang-Teh Lee, Kang-Yuan Liu, and Hui-Yang Huang Department of Computer Science and Engineering, Tatung University, Taiwan
Dynamic resource management for energy saving in the cloud computing environment Liang-Teh Lee, Kang-Yuan Liu, and Hui-Yang Huang Department of Computer Science and Engineering, Tatung University, Taiwan
Multi-core Programming System Overview
 Multi-core Programming System Overview Based on slides from Intel Software College and Multi-Core Programming increasing performance through software multi-threading by Shameem Akhter and Jason Roberts,
Multi-core Programming System Overview Based on slides from Intel Software College and Multi-Core Programming increasing performance through software multi-threading by Shameem Akhter and Jason Roberts,
How To Understand The Power Of A Virtual Machine Monitor (Vm) In A Linux Computer System (Or A Virtualized Computer)
 KVM - The kernel-based virtual machine Timo Hirt [email protected] 13. Februar 2010 Abstract Virtualization has been introduced in the 1960s, when computing systems were large and expensive to operate. It
KVM - The kernel-based virtual machine Timo Hirt [email protected] 13. Februar 2010 Abstract Virtualization has been introduced in the 1960s, when computing systems were large and expensive to operate. It
INFO5010 Advanced Topics in IT: Cloud Computing
 INFO5010 Advanced Topics in IT: Cloud Computing Week 2: Data Center and Virtualization Technology Dr. Uwe Röhm School of Information Technologies This Week s Agenda! Data Centers: Infrastructure of Scale!
INFO5010 Advanced Topics in IT: Cloud Computing Week 2: Data Center and Virtualization Technology Dr. Uwe Röhm School of Information Technologies This Week s Agenda! Data Centers: Infrastructure of Scale!
