Automating Releases in PeopleSoft using command line parameters
|
|
|
- Barnard Chase
- 10 years ago
- Views:
Transcription
1 Automating Releases in PeopleSoft using command line parameters White Paper By S.R.Raajesh Abstract This paper critically examines the benefits that can be accomplished by using the command line parameters in PSFT. A simulation study is done with the help of Visual Basic. The drawbacks of using these parameters are highlighted alongwith some innovative approaches towards overcoming the drawbacks and achieving complete automation. Automating releases in PeopleSoft using command line parameters 1
2 Introduction PeopleSoft offers command line parameters through which moving project files across environments can be achieved with some degree of automation. The amount of manual work involved in the process of release management can be considerably mitigated by the use of these command line parameters. This paper discusses the various command line parameters that are available in PSFT and the means to arrive at automation with these parameters. A simple simulation study result is presented and the drawbacks of this approach are also clearly described. Finally some innovative ways of using these utilities in attaining automation are discussed. Command line parameters- Introduction The executable file that invokes the application designer in PSFT is PSIDE.EXE. The available parameter for PSIDE.EXE falls into two categories 1. Parameters providing login information 2. Parameters setting general options. The general syntax followed for invoking the application in command line is PSIDE [-parameter value [-parameter value...]] Each parameter starts with a hyphen (-) or a forward slash (/). The value for each parameter follows the hyphen or slash, separated by zero or more spaces. In general, the value doesn't need to have quotation marks around it, even if it has internal spaces the system treats all text following the parameter as part of the value, up to the next parameter or the end of the command line. Some of the important command line parameters are listed below. For more detailed information, refer to [1]. Table 1 : Command line Parameters Parameter Value Description -CT Database type Type of database to which the user is connecting. Valid values are ORACLE, INFORMIX etc -CS Server Name The name of the database server to which the Automating releases in PeopleSoft using command line parameters 2
3 connection is made to -CD Database Name The name of the database to which the connection is made -CO User ID Peoplesoft login Id -CP Password Password for the specified user id. As an example the following statement starts the application designer and signs into ABC database as a VP1 user. PSIDE -CT ORACLE -CS ABC -CD ABC -CO VP1 -CP VP1 As per the 8.46 documentation of PSFT, following processes can be accomplished by using command line parameters. Copy a project from the source database to a flat file. Copy a project from the source database to a target database. Build a project present in a database Run a compare and report across two databases. Run datamover scripts in command line The above processes cover everything with respect to moving projects across environments in PSFT. Arriving at an automation Now that we have the list of parameters and their entitled functions, the task is to use them judiciously to arrive at a perfect automation. In a development environment, the developers submit their deliverables to the release manager who then takes care of the movement of the files across the environments for system testing and delivery. For a very high number of projects involving movement alone, a simple software program can be written to poll the source area for new submissions and accordingly connects to the target database and makes an automated movement. Assuming that the developers enter the project details once they are done into the GUI the automated program will do the following Scan for new submissions as and when they happen. Automating releases in PeopleSoft using command line parameters 3
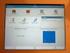
4 Trigger a command line program if there is a new entry and make the movement. A sample screen shot of the GUI used to achieve the movement is presented below. Copying to a flat file from a project was attempted. Screen shot of the generated log file is attached below The GUI is a memory resident one that does the basic movement across two databases by internally invoking the PSFT commands. The scope can be extended to support much more functionalities provided by PSFT. Not only for the project files, but also for migration SQLs and datamover scripts the same approach can be extended. If everything is perfectly placed, there is almost no need for a Automating releases in PeopleSoft using command line parameters 4
5 manual watch on movement of project files. It greatly simplifies the work of a release manager. Command line parameters- The other side The main advantage of using command line parameters is that we end up achieving some degree of automation. For each and every movement, a log file can also be generated which can be read back to report to the release manager in case of any issues. Hence, there are no alarms of objects getting missed out during the movement across environments. However, there is one shortcoming for this approach. If change control locking is enabled and if the objects are locked in the target database, then the movement will not be successful. In an ideal scenario, the probability for an object to be locked in an environment other than the development one is minimum. However, in reality it may so happen that some of the objects are locked up in the target. Though they can be traced back from the log files generated, there lies a manual intervention. Assuming that such an occurrence is rare, the automation is really beneficial. And an attempt is made to solve the above issue in the next section. Achieving perfect automation In this section, we will discuss a conceivable way to make a perfect movement even when change control locking is enabled. Change control locking in PSFT ensures that only one developer is in possession of an object at any point of time. It is controlled by two tables in PSFT i.e. pschgctlhist that stores the history of an object and pschgctllock which stores the lock related information on an object. Before making a movement to target database, insert all the rows present in the table pschgctllock to pschgctlhist and flush the pschgctllock table. This will update the history information and unlock the objects the way in which, unlocking the objects takes place through the application designer. The project file movement can then be made to the target database. Thus, even when change control locking is enabled and the objects are locked in the target database, we still end up moving the project file successfully. Conclusion Command line execution is the heart of the automation and it should be shielded enough by a perfect automation process, which manages the entire task of releasing projects across Automating releases in PeopleSoft using command line parameters 5
6 environments. It involves a careful engineering process which when done to perfection will end up providing fruitful results. References: PeopleSoft Peoplebooks- Application designer Automating releases in PeopleSoft using command line parameters 6
PATROL From a Database Administrator s Perspective
 PATROL From a Database Administrator s Perspective September 28, 2001 Author: Cindy Bean Senior Software Consultant BMC Software, Inc. 3/4/02 2 Table of Contents Introduction 5 Database Administrator Tasks
PATROL From a Database Administrator s Perspective September 28, 2001 Author: Cindy Bean Senior Software Consultant BMC Software, Inc. 3/4/02 2 Table of Contents Introduction 5 Database Administrator Tasks
Enterprise Job Scheduling: How Your Organization Can Benefit from Automation
 WHITE PAPER Enterprise Job Scheduling: How Your Organization Can Benefit from Automation By Pat Cameron Introduction Today's companies need automation solutions to attain the high levels of availability,
WHITE PAPER Enterprise Job Scheduling: How Your Organization Can Benefit from Automation By Pat Cameron Introduction Today's companies need automation solutions to attain the high levels of availability,
ITIL A guide to Event Management
 ITIL A guide to Event Management An event can be defined as any detectable or discernable occurrence that has significance for the management of the IT Infrastructure of the delivery of IT service and
ITIL A guide to Event Management An event can be defined as any detectable or discernable occurrence that has significance for the management of the IT Infrastructure of the delivery of IT service and
ITIL A guide to event management
 ITIL A guide to event management Event management process information Why have event management? An event can be defined as any detectable or discernable occurrence that has significance for the management
ITIL A guide to event management Event management process information Why have event management? An event can be defined as any detectable or discernable occurrence that has significance for the management
Representative Guide for Electronic Records Express Sending Individual Case Responses by Secure Website
 Representative Guide for Electronic Records Express Sending Individual Case Responses by Secure Website Office of Disability Adjudication and Review October 2011 Representative Guide for Electronic Records
Representative Guide for Electronic Records Express Sending Individual Case Responses by Secure Website Office of Disability Adjudication and Review October 2011 Representative Guide for Electronic Records
Load Testing with JMeter
 Load Testing with JMeter Presented by Matthew Stout - [email protected] JMeter Overview Java application for load testing and measuring performance Originally for web applications but has grown to support lots
Load Testing with JMeter Presented by Matthew Stout - [email protected] JMeter Overview Java application for load testing and measuring performance Originally for web applications but has grown to support lots
Simplify Your Migrations and Upgrades. Part 1: Avoiding risk, downtime and long hours
 Simplify Your Migrations and Upgrades Part 1: Avoiding risk, downtime and long hours Introduction You can say migrations and upgrades to a database administrator (DBA) or systems administrator. But what
Simplify Your Migrations and Upgrades Part 1: Avoiding risk, downtime and long hours Introduction You can say migrations and upgrades to a database administrator (DBA) or systems administrator. But what
Remote Access Password Tips
 Introduction: The following document was created to assist Remote Access users with password change and synchronization issues. IT&S has identified the following five (5) scenarios for remote access password
Introduction: The following document was created to assist Remote Access users with password change and synchronization issues. IT&S has identified the following five (5) scenarios for remote access password
Zero Downtime Deployments with Database Migrations. Bob Feldbauer twitter: @bobfeldbauer email: [email protected]
 Zero Downtime Deployments with Database Migrations Bob Feldbauer twitter: @bobfeldbauer email: [email protected] Deployments Two parts to deployment: Application code Database schema changes (migrations,
Zero Downtime Deployments with Database Migrations Bob Feldbauer twitter: @bobfeldbauer email: [email protected] Deployments Two parts to deployment: Application code Database schema changes (migrations,
Here you can see an example of the command results:
 CA Embedded Entitlements Manager (EEM) can be configured for Server failover which automatically routes requests to a secondary EEM Server when the primary EEM server is not available. However, for this
CA Embedded Entitlements Manager (EEM) can be configured for Server failover which automatically routes requests to a secondary EEM Server when the primary EEM server is not available. However, for this
MeetMe Conferencing. Quick Reference
 MeetMe Conferencing Quick Reference 2013 8156 S. Wadsworth Blvd, Suite E-354 Littleton, CO 80128 www.ipitimi.com [email protected] 1-855-IPITIMI (474-8464) MEET-ME CONFERENCIING Creating Conferences Access
MeetMe Conferencing Quick Reference 2013 8156 S. Wadsworth Blvd, Suite E-354 Littleton, CO 80128 www.ipitimi.com [email protected] 1-855-IPITIMI (474-8464) MEET-ME CONFERENCIING Creating Conferences Access
Security and Control Issues within Relational Databases
 Security and Control Issues within Relational Databases David C. Ogbolumani, CISA, CISSP, CIA, CISM Practice Manager Information Security Preview of Key Points The Database Environment Top Database Threats
Security and Control Issues within Relational Databases David C. Ogbolumani, CISA, CISSP, CIA, CISM Practice Manager Information Security Preview of Key Points The Database Environment Top Database Threats
Market Challenges Business Drivers
 VeriCentre 3.0 Market Challenges Business Drivers Inability to efficiently or effectively manage mass updates to install base High support costs associated with application rollouts Incomplete download
VeriCentre 3.0 Market Challenges Business Drivers Inability to efficiently or effectively manage mass updates to install base High support costs associated with application rollouts Incomplete download
WebSphere MQ Managed File Transfer. Parineeta Mattur
 WebSphere MQ Managed File Transfer Parineeta Mattur Agenda Basic FTP What is Managed File Transfer? WebSphere MQ File Transfer Edition The Three Key Components of FTE Integration with MQ Networks Data
WebSphere MQ Managed File Transfer Parineeta Mattur Agenda Basic FTP What is Managed File Transfer? WebSphere MQ File Transfer Edition The Three Key Components of FTE Integration with MQ Networks Data
Excel 2003, MS Access 2003, FileMaker Pro 8. Which One Should I Use?
 Excel, MS Access, Pro 8 Which One Should I Use? This document is intended to show a comparison of Excel, Access, and along with general guidelines to help you decide when to use one versus the other. Excel
Excel, MS Access, Pro 8 Which One Should I Use? This document is intended to show a comparison of Excel, Access, and along with general guidelines to help you decide when to use one versus the other. Excel
White Paper. The Ten Features Your Web Application Monitoring Software Must Have. Executive Summary
 White Paper The Ten Features Your Web Application Monitoring Software Must Have Executive Summary It s hard to find an important business application that doesn t have a web-based version available and
White Paper The Ten Features Your Web Application Monitoring Software Must Have Executive Summary It s hard to find an important business application that doesn t have a web-based version available and
Oracle Discoverer EUL Command Line for Java Open Platform EUL Creation and Maintenance. An Oracle White Paper August 2003
 Oracle Discoverer EUL Command Line for Java Open Platform EUL Creation and Maintenance An Oracle White Paper August 2003 Oracle Discoverer EUL Command Line for Java EXECUTIVE OVERVIEW Oracle Application
Oracle Discoverer EUL Command Line for Java Open Platform EUL Creation and Maintenance An Oracle White Paper August 2003 Oracle Discoverer EUL Command Line for Java EXECUTIVE OVERVIEW Oracle Application
Workshop for WebLogic introduces new tools in support of Java EE 5.0 standards. The support for Java EE5 includes the following technologies:
 Oracle Workshop for WebLogic 10g R3 Hands on Labs Workshop for WebLogic extends Eclipse and Web Tools Platform for development of Web Services, Java, JavaEE, Object Relational Mapping, Spring, Beehive,
Oracle Workshop for WebLogic 10g R3 Hands on Labs Workshop for WebLogic extends Eclipse and Web Tools Platform for development of Web Services, Java, JavaEE, Object Relational Mapping, Spring, Beehive,
Access Control and Audit Trail Software
 Varian, Inc. 2700 Mitchell Drive Walnut Creek, CA 94598-1675/USA Access Control and Audit Trail Software Operation Manual Varian, Inc. 2002 03-914941-00:3 Table of Contents Introduction... 1 Access Control
Varian, Inc. 2700 Mitchell Drive Walnut Creek, CA 94598-1675/USA Access Control and Audit Trail Software Operation Manual Varian, Inc. 2002 03-914941-00:3 Table of Contents Introduction... 1 Access Control
Cigital. Paco Hope, Technical Manager [email protected]
 The Foundation for Security Paco Hope, Technical Manager [email protected] www.cigital.com [email protected] +1.703.404.9293 Cigital, Inc. All Rights Reserved. 2 Cigital Consulting firm of recognized software
The Foundation for Security Paco Hope, Technical Manager [email protected] www.cigital.com [email protected] +1.703.404.9293 Cigital, Inc. All Rights Reserved. 2 Cigital Consulting firm of recognized software
An Introduction to LoadRunner A Powerful Performance Testing Tool by HP. An Introduction to LoadRunner. A Powerful Performance Testing Tool by HP
 An Introduction to LoadRunner A Powerful Performance Testing Tool by HP Index Sr. Title Page 1 Introduction 2 2 LoadRunner Testing Process 4 3 Load test Planning 5 4 LoadRunner Controller at a Glance 7
An Introduction to LoadRunner A Powerful Performance Testing Tool by HP Index Sr. Title Page 1 Introduction 2 2 LoadRunner Testing Process 4 3 Load test Planning 5 4 LoadRunner Controller at a Glance 7
ADO and SQL Server Security
 ADO and SQL Server Security Security is a growing concern in the Internet/intranet development community. It is a constant trade off between access to services and data, and protection of those services
ADO and SQL Server Security Security is a growing concern in the Internet/intranet development community. It is a constant trade off between access to services and data, and protection of those services
Monitoring Windows Event Logs
 Monitoring Windows Event Logs Monitoring Windows Event Logs Using OpManager The Windows event logs are files serving as a placeholder of all occurrences on a Windows machine. This includes logs on specific
Monitoring Windows Event Logs Monitoring Windows Event Logs Using OpManager The Windows event logs are files serving as a placeholder of all occurrences on a Windows machine. This includes logs on specific
Using HP System Software Manager for the mass deployment of software updates to client PCs
 Using HP System Software Manager for the mass deployment of software updates to client PCs Introduction... 2 HP manageability solutions... 2 SSM overview... 3 Software updates... 3 Why not SSM-enabled?...
Using HP System Software Manager for the mass deployment of software updates to client PCs Introduction... 2 HP manageability solutions... 2 SSM overview... 3 Software updates... 3 Why not SSM-enabled?...
Making the Right Choice
 Tools & Automation Making the Right Choice The features you need in a GUI test automation tool by Elisabeth Hendrickson QUICK LOOK Factors to consider in choosing a GUI testing tool Treating GUI test automation
Tools & Automation Making the Right Choice The features you need in a GUI test automation tool by Elisabeth Hendrickson QUICK LOOK Factors to consider in choosing a GUI testing tool Treating GUI test automation
MyOra 3.0. User Guide. SQL Tool for Oracle. Jayam Systems, LLC
 MyOra 3.0 SQL Tool for Oracle User Guide Jayam Systems, LLC Contents Features... 4 Connecting to the Database... 5 Login... 5 Login History... 6 Connection Indicator... 6 Closing the Connection... 7 SQL
MyOra 3.0 SQL Tool for Oracle User Guide Jayam Systems, LLC Contents Features... 4 Connecting to the Database... 5 Login... 5 Login History... 6 Connection Indicator... 6 Closing the Connection... 7 SQL
Oracle. Brief Course Content This course can be done in modular form as per the detail below. ORA-1 Oracle Database 10g: SQL 4 Weeks 4000/-
 Oracle Objective: Oracle has many advantages and features that makes it popular and thereby makes it as the world's largest enterprise software company. Oracle is used for almost all large application
Oracle Objective: Oracle has many advantages and features that makes it popular and thereby makes it as the world's largest enterprise software company. Oracle is used for almost all large application
<Insert Picture Here> Oracle Database Security Overview
 Oracle Database Security Overview Tammy Bednar Sr. Principal Product Manager [email protected] Data Security Challenges What to secure? Sensitive Data: Confidential, PII, regulatory
Oracle Database Security Overview Tammy Bednar Sr. Principal Product Manager [email protected] Data Security Challenges What to secure? Sensitive Data: Confidential, PII, regulatory
AT&T Reservationless Service User Guide. April 16, 2007
 April 16, 2007 CHAPTER ONE...3 AT&T RESERVATIONLESS SERVICE INTRODUCTION..3 USER TYPES...3 ACCESS NUMBERS, PASSWORD, AND SECURITY CODE...3 PREPARING FOR A CONFERENCE CALL - PRE-CONFERENCE REQUIREMENTS...4
April 16, 2007 CHAPTER ONE...3 AT&T RESERVATIONLESS SERVICE INTRODUCTION..3 USER TYPES...3 ACCESS NUMBERS, PASSWORD, AND SECURITY CODE...3 PREPARING FOR A CONFERENCE CALL - PRE-CONFERENCE REQUIREMENTS...4
Integrated Migration Tool
 IceWarp Unified Communications Integrated Migration Tool Version 10.4 Printed on 16 April, 2012 Contents Integrated Migration Tool 1 How It Works... 2 Performing Migration... 3 Set up the Domain in IceWarp
IceWarp Unified Communications Integrated Migration Tool Version 10.4 Printed on 16 April, 2012 Contents Integrated Migration Tool 1 How It Works... 2 Performing Migration... 3 Set up the Domain in IceWarp
Troubleshooting problems with the PDMWorks Enterprise database server
 Troubleshooting problems with the PDMWorks Enterprise database server The PDMWorks Enterprise database server is a helper service that periodically polls any PDMWorks Enterprise databases on the SQL server
Troubleshooting problems with the PDMWorks Enterprise database server The PDMWorks Enterprise database server is a helper service that periodically polls any PDMWorks Enterprise databases on the SQL server
ImagineWorldClient Client Management Software. User s Manual. (Revision-2)
 ImagineWorldClient Client Management Software User s Manual (Revision-2) (888) 379-2666 US Toll Free (905) 336-9665 Phone (905) 336-9662 Fax www.videotransmitters.com 1 Contents 1. CMS SOFTWARE FEATURES...4
ImagineWorldClient Client Management Software User s Manual (Revision-2) (888) 379-2666 US Toll Free (905) 336-9665 Phone (905) 336-9662 Fax www.videotransmitters.com 1 Contents 1. CMS SOFTWARE FEATURES...4
DiskBoss. File & Disk Manager. Version 2.0. Dec 2011. Flexense Ltd. www.flexense.com [email protected]. File Integrity Monitor
 DiskBoss File & Disk Manager File Integrity Monitor Version 2.0 Dec 2011 www.flexense.com [email protected] 1 Product Overview DiskBoss is an automated, rule-based file and disk manager allowing one to
DiskBoss File & Disk Manager File Integrity Monitor Version 2.0 Dec 2011 www.flexense.com [email protected] 1 Product Overview DiskBoss is an automated, rule-based file and disk manager allowing one to
18.2 user guide No Magic, Inc. 2015
 18.2 user guide No Magic, Inc. 2015 All material contained here in is considered proprietary information owned by No Magic, Inc. and is not to be shared, copied, or reproduced by any means. All information
18.2 user guide No Magic, Inc. 2015 All material contained here in is considered proprietary information owned by No Magic, Inc. and is not to be shared, copied, or reproduced by any means. All information
Excel To Component Interface Utility
 Excel To Component Interface Utility Contents FAQ... 3 Coversheet... 4 Connection... 5 Example... 6 Template... 7 Toolbar Actions... 7 Template Properties... 8 Create a New Template... 9 Data Input...
Excel To Component Interface Utility Contents FAQ... 3 Coversheet... 4 Connection... 5 Example... 6 Template... 7 Toolbar Actions... 7 Template Properties... 8 Create a New Template... 9 Data Input...
news from Tom Bacon about Monday's lecture
 ECRIC news from Tom Bacon about Monday's lecture I won't be at the lecture on Monday due to the work swamp. The plan is still to try and get into the data centre in two weeks time and do the next migration,
ECRIC news from Tom Bacon about Monday's lecture I won't be at the lecture on Monday due to the work swamp. The plan is still to try and get into the data centre in two weeks time and do the next migration,
SQL Server Performance Tuning for DBAs
 ASPE IT Training SQL Server Performance Tuning for DBAs A WHITE PAPER PREPARED FOR ASPE BY TOM CARPENTER www.aspe-it.com toll-free: 877-800-5221 SQL Server Performance Tuning for DBAs DBAs are often tasked
ASPE IT Training SQL Server Performance Tuning for DBAs A WHITE PAPER PREPARED FOR ASPE BY TOM CARPENTER www.aspe-it.com toll-free: 877-800-5221 SQL Server Performance Tuning for DBAs DBAs are often tasked
Microsoft SQL Server for Oracle DBAs Course 40045; 4 Days, Instructor-led
 Microsoft SQL Server for Oracle DBAs Course 40045; 4 Days, Instructor-led Course Description This four-day instructor-led course provides students with the knowledge and skills to capitalize on their skills
Microsoft SQL Server for Oracle DBAs Course 40045; 4 Days, Instructor-led Course Description This four-day instructor-led course provides students with the knowledge and skills to capitalize on their skills
Identifying Problematic SQL in Sybase ASE. Abstract. Introduction
 Identifying Problematic SQL in Sybase ASE Written by Darren Mallette, Senior Technical Consultant, Dell Software Abstract Database administrators (DBAs), developers, quality assurance (QA) analysts and
Identifying Problematic SQL in Sybase ASE Written by Darren Mallette, Senior Technical Consultant, Dell Software Abstract Database administrators (DBAs), developers, quality assurance (QA) analysts and
Scheduling in SAS 9.4 Second Edition
 Scheduling in SAS 9.4 Second Edition SAS Documentation The correct bibliographic citation for this manual is as follows: SAS Institute Inc. 2015. Scheduling in SAS 9.4, Second Edition. Cary, NC: SAS Institute
Scheduling in SAS 9.4 Second Edition SAS Documentation The correct bibliographic citation for this manual is as follows: SAS Institute Inc. 2015. Scheduling in SAS 9.4, Second Edition. Cary, NC: SAS Institute
Implementation of PeopleSoft 8.9
 Implementation of PeopleSoft 8.9 Implementation of any ERP product is a huge effort considering the generic nature of the product and specific customer requirements. In addition the industry specific and
Implementation of PeopleSoft 8.9 Implementation of any ERP product is a huge effort considering the generic nature of the product and specific customer requirements. In addition the industry specific and
D83167 Oracle Data Integrator 12c: Integration and Administration
 D83167 Oracle Data Integrator 12c: Integration and Administration Learn To: Use Oracle Data Integrator to perform transformation of data among various platforms. Design ODI Mappings, Procedures, and Packages
D83167 Oracle Data Integrator 12c: Integration and Administration Learn To: Use Oracle Data Integrator to perform transformation of data among various platforms. Design ODI Mappings, Procedures, and Packages
Test Plan Online Book Store Phase-II. Vamsi Krishna Mummaneni
 Test Plan Online Book Store Phase-II Submitted in partial fulfillment of the requirements of the degree of Master of Software Engineering Vamsi Krishna Mummaneni CIS 895 MSE Project Kansas State University
Test Plan Online Book Store Phase-II Submitted in partial fulfillment of the requirements of the degree of Master of Software Engineering Vamsi Krishna Mummaneni CIS 895 MSE Project Kansas State University
DIRECT DATA FLOW CHANNEL (SECURE FILE TRANSFER)/ IBM CONNECT:DIRECT GUIDE
 DIRECT DATA FLOW CHANNEL (SECURE FILE TRANSFER)/ IBM CONNECT:DIRECT GUIDE DIRECT DATA FLOW CHANNEL (SECURE FILE TRANSFER) / IBM CONNECT:DIRECT GUIDE JANUARY 2012 1 1. PURPOSE The purpose of this guide
DIRECT DATA FLOW CHANNEL (SECURE FILE TRANSFER)/ IBM CONNECT:DIRECT GUIDE DIRECT DATA FLOW CHANNEL (SECURE FILE TRANSFER) / IBM CONNECT:DIRECT GUIDE JANUARY 2012 1 1. PURPOSE The purpose of this guide
<Insert Picture Here> PeopleTools Security, What's New in PeopleTools 8.50
 PeopleTools Security, What's New in PeopleTools 8.50 Tom Lenz & Sushma Patel Principal Support Engineer Oracle PeopleTools Global Customer Support The following is intended to outline
PeopleTools Security, What's New in PeopleTools 8.50 Tom Lenz & Sushma Patel Principal Support Engineer Oracle PeopleTools Global Customer Support The following is intended to outline
How Do I Sign Up? For more information call (866)-337-9011 or contact us at [email protected]
 How Do I Sign Up? Simply visit our website at www.newpeoplesbank.com and click on the Register link underneath Online Banking. Once there, you will submit a form via our secure servers to our Online Banking
How Do I Sign Up? Simply visit our website at www.newpeoplesbank.com and click on the Register link underneath Online Banking. Once there, you will submit a form via our secure servers to our Online Banking
identity management in Linux and UNIX environments
 Whitepaper identity management in Linux and UNIX environments EXECUTIVE SUMMARY In today s IT environments everything is growing, especially the number of users, systems, services, applications, and virtual
Whitepaper identity management in Linux and UNIX environments EXECUTIVE SUMMARY In today s IT environments everything is growing, especially the number of users, systems, services, applications, and virtual
Web Presentation Layer Architecture
 Chapter 4 Web Presentation Layer Architecture In this chapter we provide a discussion of important current approaches to web interface programming based on the Model 2 architecture [59]. From the results
Chapter 4 Web Presentation Layer Architecture In this chapter we provide a discussion of important current approaches to web interface programming based on the Model 2 architecture [59]. From the results
CPM 5.2.1 5.6 release notes
 1 (18) CPM 5.2.1 5.6 release notes Aditro Oy, 2014 CPM Release Notes Page 1 of 18 2 (18) Contents Fakta version 5.2.1. version 1.2.1... 3 Fakta version 5.2.1.1038 sp1 version 1.2.1.300 sp1... 4 Fakta version
1 (18) CPM 5.2.1 5.6 release notes Aditro Oy, 2014 CPM Release Notes Page 1 of 18 2 (18) Contents Fakta version 5.2.1. version 1.2.1... 3 Fakta version 5.2.1.1038 sp1 version 1.2.1.300 sp1... 4 Fakta version
TouchBase Pro. Users Guide
 TouchBase Pro Automated Emailing System Users Guide Z-Micro Technologies, Inc. Copyright 2005. Z-Micro Technologies, Inc. All Rights Reserved 2 Table of Contents Chapter 1: Overview & Installation Features
TouchBase Pro Automated Emailing System Users Guide Z-Micro Technologies, Inc. Copyright 2005. Z-Micro Technologies, Inc. All Rights Reserved 2 Table of Contents Chapter 1: Overview & Installation Features
LockoutGuard v1.2 Documentation
 LockoutGuard v1.2 Documentation (The following graphics are screen shots from Microsoft ISA Server and Threat Management Gateway which are the property of Microsoft Corp. and are included here for instructive
LockoutGuard v1.2 Documentation (The following graphics are screen shots from Microsoft ISA Server and Threat Management Gateway which are the property of Microsoft Corp. and are included here for instructive
www.excellium.ca Tel. : 514.798.8899 Fax. : 514.798.8898 Toll Free : 1.888.381.2457 Equipmentperfect Controlperfect IDperfect Keyperfect Reportperfect
 Controlperfect Equipmentperfect With its unique approach, Controlperfect is the first software suite to integrate, in a complete and interactive whole, the numerous daily tasks related to the management
Controlperfect Equipmentperfect With its unique approach, Controlperfect is the first software suite to integrate, in a complete and interactive whole, the numerous daily tasks related to the management
ICAB4136B Use structured query language to create database structures and manipulate data
 ICAB4136B Use structured query language to create database structures and manipulate data Release: 1 ICAB4136B Use structured query language to create database structures and manipulate data Modification
ICAB4136B Use structured query language to create database structures and manipulate data Release: 1 ICAB4136B Use structured query language to create database structures and manipulate data Modification
Oracle Database 11 g Performance Tuning. Recipes. Sam R. Alapati Darl Kuhn Bill Padfield. Apress*
 Oracle Database 11 g Performance Tuning Recipes Sam R. Alapati Darl Kuhn Bill Padfield Apress* Contents About the Authors About the Technical Reviewer Acknowledgments xvi xvii xviii Chapter 1: Optimizing
Oracle Database 11 g Performance Tuning Recipes Sam R. Alapati Darl Kuhn Bill Padfield Apress* Contents About the Authors About the Technical Reviewer Acknowledgments xvi xvii xviii Chapter 1: Optimizing
A Scheme for Automation of Telecom Data Processing for Business Application
 A Scheme for Automation of Telecom Data Processing for Business Application 1 T.R.Gopalakrishnan Nair, 2 Vithal. J. Sampagar, 3 Suma V, 4 Ezhilarasan Maharajan 1, 3 Research and Industry Incubation Center,
A Scheme for Automation of Telecom Data Processing for Business Application 1 T.R.Gopalakrishnan Nair, 2 Vithal. J. Sampagar, 3 Suma V, 4 Ezhilarasan Maharajan 1, 3 Research and Industry Incubation Center,
Bazaarvoice for Magento Extension Implementation Guide v6.3.4
 Bazaarvoice Bazaarvoice for Magento Extension Implementation Guide v6.3.4 Version 6.3.4 Bazaarvoice Inc. 03/25/2016 Introduction Bazaarvoice maintains a pre-built integration into the Magento platform.
Bazaarvoice Bazaarvoice for Magento Extension Implementation Guide v6.3.4 Version 6.3.4 Bazaarvoice Inc. 03/25/2016 Introduction Bazaarvoice maintains a pre-built integration into the Magento platform.
Threat Modeling. Categorizing the nature and severity of system vulnerabilities. John B. Dickson, CISSP
 Threat Modeling Categorizing the nature and severity of system vulnerabilities John B. Dickson, CISSP What is Threat Modeling? Structured approach to identifying, quantifying, and addressing threats. Threat
Threat Modeling Categorizing the nature and severity of system vulnerabilities John B. Dickson, CISSP What is Threat Modeling? Structured approach to identifying, quantifying, and addressing threats. Threat
<Insert Picture Here> When to Automate Your Testing (and When Not To)
 When to Automate Your Testing (and When Not To) Joe Fernandes (Oracle) Alex Di Fonzo (Synchronoss Technologies) Three Myths of Automated Testing 1. Automated testing always results
When to Automate Your Testing (and When Not To) Joe Fernandes (Oracle) Alex Di Fonzo (Synchronoss Technologies) Three Myths of Automated Testing 1. Automated testing always results
Security and Your SAP System When Working with Winshuttle Products
 Security and Your SAP System When Working with Winshuttle Products 2014 Winshuttle, LLC. All rights reserved. 2/14 www.winshuttle.com Background Companies running SAP systems are accustomed to configuring
Security and Your SAP System When Working with Winshuttle Products 2014 Winshuttle, LLC. All rights reserved. 2/14 www.winshuttle.com Background Companies running SAP systems are accustomed to configuring
NonStop SQL Database Management
 NonStop SQL Database Management I have always been, and always will be, what has been referred to as a command line cowboy. I go through keyboards faster than most people go through mobile phones. I know
NonStop SQL Database Management I have always been, and always will be, what has been referred to as a command line cowboy. I go through keyboards faster than most people go through mobile phones. I know
EAE-MS SCCAPI based Version Control System
 EAE-MS SCCAPI based Version Control System This document is an implementation guide to use the EAE-MS SCCAPI based Version Control System as an alternative to the existing EAE Version Control System. The
EAE-MS SCCAPI based Version Control System This document is an implementation guide to use the EAE-MS SCCAPI based Version Control System as an alternative to the existing EAE Version Control System. The
Toad for Oracle 8.6 SQL Tuning
 Quick User Guide for Toad for Oracle 8.6 SQL Tuning SQL Tuning Version 6.1.1 SQL Tuning definitively solves SQL bottlenecks through a unique methodology that scans code, without executing programs, to
Quick User Guide for Toad for Oracle 8.6 SQL Tuning SQL Tuning Version 6.1.1 SQL Tuning definitively solves SQL bottlenecks through a unique methodology that scans code, without executing programs, to
Security Testing & Load Testing for Online Document Management system
 1 Security Testing & Load Testing for Online Document Management system Abstract The client is a leading provider of online technical documentation solutions in UK, they wanted to protect their documents
1 Security Testing & Load Testing for Online Document Management system Abstract The client is a leading provider of online technical documentation solutions in UK, they wanted to protect their documents
How to leverage SAP NetWeaver Identity Management and SAP Access Control combined solutions
 How to leverage SAP NetWeaver Identity Management and SAP Access Control combined solutions Introduction This paper provides an overview of the integrated solution and a summary of implementation options
How to leverage SAP NetWeaver Identity Management and SAP Access Control combined solutions Introduction This paper provides an overview of the integrated solution and a summary of implementation options
EBERSPÄCHER ELECTRONICS automotive bus systems. solutions for network analysis
 EBERSPÄCHER ELECTRONICS automotive bus systems solutions for network analysis DRIVING THE MOBILITY OF TOMORROW 2 AUTOmotive bus systems System Overview Analyzing Networks in all Development Phases Control
EBERSPÄCHER ELECTRONICS automotive bus systems solutions for network analysis DRIVING THE MOBILITY OF TOMORROW 2 AUTOmotive bus systems System Overview Analyzing Networks in all Development Phases Control
Binding an OS X computer to Active Directory at NEIU (Existing User)
 Binding an OS X computer to Active Directory at NEIU (Existing User) The instructions in this guide assume that a local Administrator account is available on the Macintosh computer. These instructions
Binding an OS X computer to Active Directory at NEIU (Existing User) The instructions in this guide assume that a local Administrator account is available on the Macintosh computer. These instructions
SQL Server Performance Intelligence
 WHITE PAPER SQL Server Performance Intelligence MARCH 2009 Confio Software www.confio.com +1-303-938-8282 By: Consortio Services & Confio Software Performance Intelligence is Confio Software s method of
WHITE PAPER SQL Server Performance Intelligence MARCH 2009 Confio Software www.confio.com +1-303-938-8282 By: Consortio Services & Confio Software Performance Intelligence is Confio Software s method of
Migration Best Practices for OpenSSO 8 and SAM 7.1 deployments O R A C L E W H I T E P A P E R M A R C H 2015
 Migration Best Practices for OpenSSO 8 and SAM 7.1 deployments O R A C L E W H I T E P A P E R M A R C H 2015 Disclaimer The following is intended to outline our general product direction. It is intended
Migration Best Practices for OpenSSO 8 and SAM 7.1 deployments O R A C L E W H I T E P A P E R M A R C H 2015 Disclaimer The following is intended to outline our general product direction. It is intended
Collaborate.ets.org Password Setup & Recovery Guide. Table of Contents
 MyPassword is a self-service password management tool. Collaborate.ets.org Password Setup & Recovery Guide https://mypassword.ets.org/ Table of Contents Create/Edit Your Profile (First time use)... I Change
MyPassword is a self-service password management tool. Collaborate.ets.org Password Setup & Recovery Guide https://mypassword.ets.org/ Table of Contents Create/Edit Your Profile (First time use)... I Change
ORACLE DATABASE SECURITY. Keywords: data security, password administration, Oracle HTTP Server, OracleAS, access control.
 ORACLE DATABASE SECURITY Cristina-Maria Titrade 1 Abstract This paper presents some security issues, namely security database system level, data level security, user-level security, user management, resource
ORACLE DATABASE SECURITY Cristina-Maria Titrade 1 Abstract This paper presents some security issues, namely security database system level, data level security, user-level security, user management, resource
Lenovo Partner Access - Overview
 Table of Contents: Lenovo Partner Access Overview How to Access the Lenovo Partner Access Portal Registration Process and Account Activation First time login Accepting the T s & C s and Selecting Challenge
Table of Contents: Lenovo Partner Access Overview How to Access the Lenovo Partner Access Portal Registration Process and Account Activation First time login Accepting the T s & C s and Selecting Challenge
Cognos Event Studio. Deliver By : Amit Sharma Presented By : Amit Sharma
 Cognos Event Studio Deliver By : Amit Sharma Presented By : Amit Sharma An Introduction Cognos Event Studio to notify decision-makers of events as they happen, so that they can make timely and effective
Cognos Event Studio Deliver By : Amit Sharma Presented By : Amit Sharma An Introduction Cognos Event Studio to notify decision-makers of events as they happen, so that they can make timely and effective
SEEM3490 Information Systems Management Lecture 01 Introduction to ISM
 SEEM3490 Information Systems Management Lecture 01 Introduction to ISM Terminologies! Two very similar terms:! Information Systems Management (ISM)! Management Information Systems (MIS)! Are there any
SEEM3490 Information Systems Management Lecture 01 Introduction to ISM Terminologies! Two very similar terms:! Information Systems Management (ISM)! Management Information Systems (MIS)! Are there any
The safer, easier way to help you pass any IT exams. Exam : C_HANASUP_1. SAP Certified Support Associate - SAP HANA 1.0.
 Exam : C_HANASUP_1 Title : SAP Certified Support Associate - SAP HANA 1.0 Version : DEMO 1 / 4 1.In the SAP HANA studio, which of the following SQL thread details can you monitor by using the Threads subtab
Exam : C_HANASUP_1 Title : SAP Certified Support Associate - SAP HANA 1.0 Version : DEMO 1 / 4 1.In the SAP HANA studio, which of the following SQL thread details can you monitor by using the Threads subtab
2 SQL in iseries Navigator
 2 SQL in iseries Navigator In V4R4, IBM added an SQL scripting tool to the standard features included within iseries Navigator and has continued enhancing it in subsequent releases. Because standard features
2 SQL in iseries Navigator In V4R4, IBM added an SQL scripting tool to the standard features included within iseries Navigator and has continued enhancing it in subsequent releases. Because standard features
Meet Me Conferencing. Document Date: 05/15/2015 Document Version: 1.0d
 Meet Me Conferencing Document Date: 05/15/2015 Document Version: 1.0d Creating Conferences Access You have access to Conferencing features if you have been assigned to a Meet-Me conference bridge. Go to
Meet Me Conferencing Document Date: 05/15/2015 Document Version: 1.0d Creating Conferences Access You have access to Conferencing features if you have been assigned to a Meet-Me conference bridge. Go to
Configuring NXT Hardware with Mercury Inside into Doors.NET TM Application Note
 1.0 Installing the Mercury SCP Gateway The MSC/SCP gateway must be installed to interface with Mercury hardware. This gateway must be chosen during the installation of the software, or it can be added
1.0 Installing the Mercury SCP Gateway The MSC/SCP gateway must be installed to interface with Mercury hardware. This gateway must be chosen during the installation of the software, or it can be added
Oracle Database Development Standards For DNR Staff and Contractors. Table of Contents
 Oracle Database Development Standards For DNR Staff and Contractors Table of Contents INTRODUCTION...2 DATABASE ORGANIZATION...2 DATABASE PROCEDURES...3 Development...3 Testing...3 Production Release...4
Oracle Database Development Standards For DNR Staff and Contractors Table of Contents INTRODUCTION...2 DATABASE ORGANIZATION...2 DATABASE PROCEDURES...3 Development...3 Testing...3 Production Release...4
Provider Express Obtaining Login Access. Information for Network Providers
 Provider Express Obtaining Login Access Information for Network Providers November 2013 Objectives This presentation will review the following features: How to Log in to Provider Express Retrieve a forgotten
Provider Express Obtaining Login Access Information for Network Providers November 2013 Objectives This presentation will review the following features: How to Log in to Provider Express Retrieve a forgotten
Using MS-SQL Server with Visual DataFlex March, 2009
 Using MS-SQL Server with Visual DataFlex March, 2009 All rights reserved. Target Audience It is assumed that the reader of this white paper has general knowledge of the Visual DataFlex development environment.
Using MS-SQL Server with Visual DataFlex March, 2009 All rights reserved. Target Audience It is assumed that the reader of this white paper has general knowledge of the Visual DataFlex development environment.
Managing User Security: Roles and Scopes
 CHAPTER 10 These topics describe how Cisco ANA implements a two-dimensional security engine combining a role-based security mechanism with scopes (groups of NEs) that are granted to users. In addition,
CHAPTER 10 These topics describe how Cisco ANA implements a two-dimensional security engine combining a role-based security mechanism with scopes (groups of NEs) that are granted to users. In addition,
Law Conferencing uses the Webinterpoint 8.2 web conferencing platform. This service is completely reservationless and available 24/7.
 Law Conferencing uses the Webinterpoint 8.2 web conferencing platform. This service is completely reservationless and available 24/7. This document contains detailed instructions on all features. Table
Law Conferencing uses the Webinterpoint 8.2 web conferencing platform. This service is completely reservationless and available 24/7. This document contains detailed instructions on all features. Table
System Build 2 Test Plan
 System Build 2 Test Plan Version 1.0 System Build 2 Test Plan Author s Signature Your signature indicates that this document has been prepared with input from content experts and is in compliance with
System Build 2 Test Plan Version 1.0 System Build 2 Test Plan Author s Signature Your signature indicates that this document has been prepared with input from content experts and is in compliance with
12 SPS DATABASE ADMINISTRATION
 Chapter 12 SPS DATABASE ADMINISTRATION Table of Contents Chapter 12... 1 SPS DATABASE ADMINISTRATION... 1 Table of Contents... 1 12-1 Manually dumping a database... 1 12-2 Logging in to Sybase Central
Chapter 12 SPS DATABASE ADMINISTRATION Table of Contents Chapter 12... 1 SPS DATABASE ADMINISTRATION... 1 Table of Contents... 1 12-1 Manually dumping a database... 1 12-2 Logging in to Sybase Central
Oracle EXAM - 1Z0-528. Oracle Database 11g Security Essentials. Buy Full Product. http://www.examskey.com/1z0-528.html
 Oracle EXAM - 1Z0-528 Oracle Database 11g Security Essentials Buy Full Product http://www.examskey.com/1z0-528.html Examskey Oracle 1Z0-528 exam demo product is here for you to test the quality of the
Oracle EXAM - 1Z0-528 Oracle Database 11g Security Essentials Buy Full Product http://www.examskey.com/1z0-528.html Examskey Oracle 1Z0-528 exam demo product is here for you to test the quality of the
Notification messages
 AXIS P8221 Network I/O Audio Module TECHNICAL NOTE Notification messages How to integrate AXIS P8221 Updated: August 19, 2011 Rev: 1.1 TABLE OF CONTENTS 1 INTRODUCTION 3 1.1 HTTP and TCP 3 1.2 VAPIX 3
AXIS P8221 Network I/O Audio Module TECHNICAL NOTE Notification messages How to integrate AXIS P8221 Updated: August 19, 2011 Rev: 1.1 TABLE OF CONTENTS 1 INTRODUCTION 3 1.1 HTTP and TCP 3 1.2 VAPIX 3
DATABASE SECURITY MECHANISMS AND IMPLEMENTATIONS
 DATABASE SECURITY MECHANISMS AND IMPLEMENTATIONS Manying Qiu, Virginia State University, [email protected] Steve Davis, Clemson University, [email protected] ABSTRACT People considering improvements in database
DATABASE SECURITY MECHANISMS AND IMPLEMENTATIONS Manying Qiu, Virginia State University, [email protected] Steve Davis, Clemson University, [email protected] ABSTRACT People considering improvements in database
AREA RICERCA Ufficio Dottorati di Ricerca Nazionali ed Internazionali
 REGISTRATION Note: former students can skip the registration process and log in using their account (id123456) 1.1 HOW TO REGISTER: please, go to web page www.univr.it/applicationphd2015 and select the
REGISTRATION Note: former students can skip the registration process and log in using their account (id123456) 1.1 HOW TO REGISTER: please, go to web page www.univr.it/applicationphd2015 and select the
WebSphere MQ Managed File Transfer
 WebSphere MQ Managed File Transfer Geoff Judd WebSphere MQ Development IBM 1 2009 IBM Agenda Common problems transferring file data Introduction to MQ Managed File Transfer IBM s Managed File Transfer
WebSphere MQ Managed File Transfer Geoff Judd WebSphere MQ Development IBM 1 2009 IBM Agenda Common problems transferring file data Introduction to MQ Managed File Transfer IBM s Managed File Transfer
Secure network guest access with the Avaya Identity Engines portfolio
 Secure network guest access with the Avaya Identity Engines portfolio Table of Contents Executive summary... 1 Overview... 1 The solution... 2 Key solution features... 2 Guest Access Administration...
Secure network guest access with the Avaya Identity Engines portfolio Table of Contents Executive summary... 1 Overview... 1 The solution... 2 Key solution features... 2 Guest Access Administration...
MS-40074: Microsoft SQL Server 2014 for Oracle DBAs
 MS-40074: Microsoft SQL Server 2014 for Oracle DBAs Description This four-day instructor-led course provides students with the knowledge and skills to capitalize on their skills and experience as an Oracle
MS-40074: Microsoft SQL Server 2014 for Oracle DBAs Description This four-day instructor-led course provides students with the knowledge and skills to capitalize on their skills and experience as an Oracle
Loading Excel Data Securely into SAP ERP Systems
 Loading Excel Data Securely into SAP ERP Systems SUMMARY When organizations make the strategic decision to invest in an ERP system with the goal of making the business run better, data becomes paramount
Loading Excel Data Securely into SAP ERP Systems SUMMARY When organizations make the strategic decision to invest in an ERP system with the goal of making the business run better, data becomes paramount
Warehouse R x Inventory Management Software. Technical Overview
 Warehouse R x Inventory Management Software Technical Overview January 19, 2009 System Overview Warehouse R X is the latest version of Daifuku America s Warehouse Control System (WCS) software. It provides
Warehouse R x Inventory Management Software Technical Overview January 19, 2009 System Overview Warehouse R X is the latest version of Daifuku America s Warehouse Control System (WCS) software. It provides
