Security methods for livestock buildings including assessment aspects
|
|
|
- Milton Cain
- 10 years ago
- Views:
Transcription
1 Agronomy Research 13(1), , 2015 Security methods for livestock buildings including assessment aspects J. Hart 1,*, Z. Štěrbová 2 and V. Nídlová 3 1 Czech University of Life Sciences Prague (CULS), Faculty of Engineering, Department of Technological Equipment of Buildings, Kamýcká 129, Prague, Czech republic; * Correspondence: [email protected] 2 Czech University of Life Sciences Prague (CULS), Faculty of Engineering, Department of Mechanical Engineering, Kamýcká 129, Prague, Czech republic 3 Czech University of Life Sciences Prague (CULS), Faculty of Engineering, Department of Electrical Engineering and Automation, Kamýcká 129, Prague, Czech republic Abstract. The problem of security methods affects a large proportion of intrusion and hold-up alarm systems (I&HAS). In a time of increasing property crime, it is highly important for the security methods of livestock buildings to be able to achieve efficiency, reliability and faultlessness. In case it is proposed to place detectors, it is essential to determine the position of the detectors, the types of the detectors, but also to guarantee their capability of detection for use in livestock production buildings. The security proposals, which have been conducted, examine both the normal security methods in livestock production as well as cost and long-term financial expenses (investment in the communicator, private security guards etc.). These security proposals are important both from an informative perspective and also because of the possibility of using individual proposals in securing livestock production in practice. The aim was to compare the two kinds of security methods for a livestock building object. The compared values become the acquisition costs of security system. Key words: security risks, sabotage, intrusion and hold-up alarm systems, glass break detector. INTRODUCTION Intrusion and hold-up alarm systems serve primarily for the protection of buildings against unlawful conduct of third parties, and can be used as monitoring and control systems. Therefore, they are primarily a tool for ensuring a state of security. They operate in the material realm (physical protection of property, life and health) and in the emotional realm (providing a feeling of peace, safety and certain security). As a result, it is important for them not to malfunction and to be sufficiently resistant to attack. The procedure for the design of the placement of detectors in livestock buildings is a very relevant part that precedes the actual installation of the entire electrical security system, and it a part of the overall design of the security alarm and emergency systems (hereinafter SAES). This usually regards the part of security process which determines where individual detectors will be located. The process that we selected when designing the SAES will decide on how difficult the installation will be, and the price of the final system. 231
2 MATERIALS AND METHODS Nowadays, several methods are used that provide a sufficient level of the building s security (Staff & Honey, 1999; Uhlář, 2005; Křeček, 2006). However, only two methods comply with the applicable standards related to ČSN EN These are the method of perimeter procedure and the procedure using nodal points. The perimeter procedure is a frequently-used procedure in the process of securing a building. Detectors are installed around the perimeter of the building, thereby almost perfectly securing the building which cannot be entered without triggering an alarm. The closer to the centre of the building a detector is located, the less important it is for the correctness of the operation of the system see Fig. 1. Figure 1. Floor plan showing the perimeter security procedure. The procedure using nodal points is very different from the perimeter procedure. Here, the security of the perimeter of the building is not dealt with, but the most frequently used places, and places with the greatest probability of disturbing the building are selected and then secured see Fig. 2. During this procedure, it is necessary to be experienced and have a certain amount of imagination, as the security design becomes complicated in determining the nodal points. Like with the perimeter procedure, three degrees of security priorities are also defined for this method, but herein this priority is defined for every room (by points) and not for the perimeter. Figure 2. Floor plan showing the nodal points. 232
3 Nodal points are most often located in entrance areas and in all of the locations where the movement of an attacker is expected most probably. This mainly involves corridors, staircases to other floors, rooms that can be entered, etc. Compared to the standard security of family homes, the security of buildings for livestock production is a complicated matter. This is due to the movement of animals, which can cause false alarms in the building. However, it is possible to use various specific detectors that allow for even such complicated spaces to be guarded. The first alternative is to deploy infrared barriers and microwave barriers (Petruzzellis, 1993; Capel, 1999; Uhlář, 2005; Křeček, 2006). Although this alternative is efficient and effective, it is also costly, and it is relatively difficult to find a location where they can be placed in order to be usable. Another alternative is the use of dual detectors, or detectors with PET immunity. Dual detectors combine the properties of PIR (passive infra-red) detectors and usually one representative from active space detectors (Petruzzellis, 1993; Capel, 1999; Uhlář, 2005; Křeček, 2006). This alternative is acceptable, but in view of the fact that the detector may set off an alarm anyway when animals are untethered, it is gradually being waived. The alarm is caused by the movement of accumulated heat and its movement, which in principle works with the surrounding spaces in the same way as it does for heat exchangers (Šeďová et al., 2013; Neuberger et al., 2014). Thus, the only alternative for securing indoor spaces is the use of detectors with PET immunity. If these detectors are correctly selected and installed, they are able to accept the movements of animals whilst reliably detecting a human being. This is due to certain immunity to movement that occurs below a certain height level. These movements can also be limited by certain weight ranges that the detector can ignore up to a defined height level (Petruzzellis, 1993; Capel, 1999; Uhlář, 2005; Křeček, 2006). In order to compare the design of security via the perimeter procedure and the nodal points procedure, a building for stabling pigs at a pig farm near Jablonné nad Orlicí was selected. This is a classical smaller stable with several partition walls (Syrový et al., 2008). The wall is located in the centre of the building and it separates individual pens (See Fig. 3), and the exit is also separated from the building via a long corridor. Figure 3. Pig pens. 233
4 The security for the given building was designed according to the perimeter procedure (Fig. 1). The overall costs for the purchased material are shown in the following Table I. Table 1. Price calculation of the system resolved by the perimeter procedure pcs Price per item (EUR) Total price (EUR) Detector of opening Glass break detector PIR detector with PET immunity MainUnit +Keyboard Zone expander GSM communicator Cost of installation (approx) Total Total without GSM communicator and MainUnit Detectors of opening were designed for each pen and passage through the building. The glass break detectors were designed for the front of the building, as it has a glass surface. PIR detectors with PET immunity were designed for both sides of the passage serving as the entrance to building, and for both sides of both aisles with pens. The security for the given building was designed according to the procedure using nodal points (Fig. 2). The overall costs for the purchased material are shown in Table II. Table 2. Price calculation for the system resolved using nodal points pcs Price per item (EUR) Total price (EUR) Detector of opening Glass break detector PIR detector with PET immunity MainUnit +Keyboard Zone expander GSM communicator Cost of installation (approx) Total Total without GSM communicator and MainUnit With regard to nodal points, is was first necessary to mark the areas in the floor plan of the building where security is very important, followed by the areas that are important, and, finally, the areas that are unimportant in order for the system to operate correctly. The placement of nodal points follows the estimation of the designer, and is therefore not applicable for everyone who installs such a system. The floor plan marked in this way is shown in Fig. 2. The following nodal points were marked as very important: the access corridor (from both sides) and the top aisle between the pens (from both sides). These were selected due to the most probable entry by an intruder. The following nodal points were marked as important: the bottom aisle between the pens. The remaining spaces were selected as unimportant. 234
5 RESULTS AND DISCUSSION If we disregard the repeated costs for both security designs (MainUnit + keyboard and GSM communicator) and subtract them from the resulting comparison, the resulting price difference between individual designs is EUR see Table 3. Table 3. Comparison of the price of the system designed with the perimeter procedure and nodal points Price (EUR) Price (%) Perimeter procedure Nodal points Difference Using nodal points will save approx. 62% of the acquisition costs while the resulting degree of security will not be decreased. The long-term costs are the same for both proposals. Estimated useful lives of the systems are tens of years. Although the method of nodal points does not give great variability of settings, it saves on the cost of the system. The correct determination of nodal points in the building can decrease the costs for securing the building whilst maintaining the degree of security. Therefore, it is important not to refrain from this method, in particular in livestock production, where it is reasonable due to the efficiency of the security design, the fact that it can be assembled by on one s own or the resulting savings. As stated in Security Systems & Intruder Alarms (Capel, 1999), the security design is one of the most important parts of the entire installation. This can minimize false alarms and lower the costs of acquiring the system. The same is stated in Security: A Guide to Security System Design and Equipment Selection and Installation (Cumming, 1994), and that is why the author recommends primarily using the nodal points procedure. CONCLUSIONS Correct installation is one of the essential factors that can directly affect the security and functionality of the security system. It is necessary that the companies providing the installation of security systems always follow the manuals for the given system and pay attention to the correct installation procedure according to the relevant standards. If the installation company does not follow the manuals and standards, then no equipment installed by them will meet the parameters of security systems and it is not suitable to use them. In livestock production, the use of the perimeter procedure is not financially feasible. It is always important to concentrate on the building that needs to be secured, and not to proceed, with regard to all structures, in a manner that overdoes the security. Maximum security is not necessary for pig breeding, and it is important to focus rather on the development on new types of protection, specifically for livestock production. 235
6 In terms of the security design, financial calculations clearly showed that the perimeter procedure for small and simple installations can increase costs by up to 62% compared to the nodal point procedure and the nodal point method does not decrease the quality of security. The perimeter procedure may be able to perfectly secure a building, but this procedure is costly and increases the number of false alarms. Therefore, the question is whether or not to use the perimeter method. REFERENCES Capel, V Security Systems & Intruder Alarms. Elsevier Science, 301 p. Cumming, N Security: A Guide to Security System Design and Equipment Selection and Installation. Elsevier Science, 338p. Křeček, S Manual security equipment. Blatná: Circetus, 313 p. (in Czech) Petruzzellis, T Alarm Sensor and Security. McGraw-Hill Professional Publishing, 256 p. Staff, H., Honey, G Electronic Security Systems Pocket Book. Elsevier Science, 226 p. Syrový, O., Bauer, F., Gerndtova, I., Holubova, V., Hůla, J., Kovařiček, P., Krouhlik, M., Kumhala, F., Kviz, Z., Mašek, J., Pastorek, Z., Podpěra, V., Rybka, A., Sedlak, P., Skalicky, J., Šmerda, T Energy saving technologies in plant production, Research Institute of Agricultural Engineering, p.r.i. Prague, 101p. (in Czech) Šeďová, M., Adamovský, R., Neuberger, P Analysis of ground massif temperatures with horizontal heat exchanger. Research in Agricultural Engineering (Zemědělská technika), pp Neuberger, P., Adamovský, R., Šeďová, M Temperatures and Heat Flows in a Soil Enclosing a Slinky Horizontal Heat Exchanger. Energies, pp Uhlář, J Technical protection of objects, II. part, Electrical security systems II. Prague: PA ČR, 229 p. (in Czech) 236
Reliability of detection of sources of infrared radiation in security alarm and distress signal systems
 Agronomy Research 12(3), 949 954, 2014 Reliability of detection of sources of infrared radiation in security alarm and distress signal systems J. Hart *, V. Nídlová and M. Přikryl 1 Department of Technological
Agronomy Research 12(3), 949 954, 2014 Reliability of detection of sources of infrared radiation in security alarm and distress signal systems J. Hart *, V. Nídlová and M. Přikryl 1 Department of Technological
ABB Stotz-Kontakt GmbH ABB safe&smart Project planning of security systems
 ABB Stotz-Kontakt GmbH ABB safe&smart Project planning of security systems Content Introduction Preventing unauthorized access by perimeter surveillance Monitoring unauthorized access by indoor surveillance
ABB Stotz-Kontakt GmbH ABB safe&smart Project planning of security systems Content Introduction Preventing unauthorized access by perimeter surveillance Monitoring unauthorized access by indoor surveillance
Understanding Alarm Systems
 Understanding Alarm Systems A false alarm occurs when an alarm signal designed to elicit an immediate emergency Law Enforcement, Fire, or Medical response is activated, when in fact no emergency exists.
Understanding Alarm Systems A false alarm occurs when an alarm signal designed to elicit an immediate emergency Law Enforcement, Fire, or Medical response is activated, when in fact no emergency exists.
PASSIVE INFRARED INTRUSION DETECTOR PASSIVE INFRAROOD DETECTOR DETECTEUR D INTRUSION PASSIF INFRAROUGE
 MODEL HAA51 PASSIVE INFRARED INTRUSION DETECTOR PASSIVE INFRAROOD DETECTOR DETECTEUR D INTRUSION PASSIF INFRAROUGE OPERATING MANUAL HAA51 PASSIVE INFRARED INTRUDER DETECTOR INTRODUCTION HAA51 Passive Infrared
MODEL HAA51 PASSIVE INFRARED INTRUSION DETECTOR PASSIVE INFRAROOD DETECTOR DETECTEUR D INTRUSION PASSIF INFRAROUGE OPERATING MANUAL HAA51 PASSIVE INFRARED INTRUDER DETECTOR INTRODUCTION HAA51 Passive Infrared
Integration of Alarm Systems
 Integration of Alarm Systems Ing. Jan Valouch Tomas Bata University in Zlin, Faculty of Applied Informatics, Department of Security Engineering, Zlín, Czech Republic [email protected] Abstract Integrated
Integration of Alarm Systems Ing. Jan Valouch Tomas Bata University in Zlin, Faculty of Applied Informatics, Department of Security Engineering, Zlín, Czech Republic [email protected] Abstract Integrated
How To Make A Commercial Detector
 Detection delivered. Reliability assured. Commercial Series Motion Detectors Detection is the first step to protecting a home or business and the people and property within its walls. Instant responses
Detection delivered. Reliability assured. Commercial Series Motion Detectors Detection is the first step to protecting a home or business and the people and property within its walls. Instant responses
90 Degree PIR Wireless Security Sensor. Installation Instructions 5420/90F
 90 Degree PIR Wireless Security Sensor Installation Instructions 5420/90F Copyright Clipsal Australia P/L 2007. All rights reserved. Clipsal is a registered trademark of Clipsal Australia Pty Ltd. The
90 Degree PIR Wireless Security Sensor Installation Instructions 5420/90F Copyright Clipsal Australia P/L 2007. All rights reserved. Clipsal is a registered trademark of Clipsal Australia Pty Ltd. The
A Review of Security System for Smart Home Applications
 Journal of Computer Science 8 (7): 1165-1170, 2012 ISSN 1549-3636 2012 Science Publications A Review of Security System for Smart Home Applications Mohammad Syuhaimi Ab-Rahman and Mohd Ariff Razaly Department
Journal of Computer Science 8 (7): 1165-1170, 2012 ISSN 1549-3636 2012 Science Publications A Review of Security System for Smart Home Applications Mohammad Syuhaimi Ab-Rahman and Mohd Ariff Razaly Department
Fire Alarm system Installation Guide
 Fire Alarm system Installation Guide Fire Alarm System Categories Systems designed for Protection of Property only, fall into two classifications P1 or P2. but a manual system is also needed, then this
Fire Alarm system Installation Guide Fire Alarm System Categories Systems designed for Protection of Property only, fall into two classifications P1 or P2. but a manual system is also needed, then this
Overview. Components of an alarm system Technology behind the equipment Communication Platforms Industry Terminology False Alarm Tips DSC products
 Basic Security 101 Overview Components of an alarm system Technology behind the equipment Communication Platforms Industry Terminology False Alarm Tips DSC products Components of an Alarm System Main Control
Basic Security 101 Overview Components of an alarm system Technology behind the equipment Communication Platforms Industry Terminology False Alarm Tips DSC products Components of an Alarm System Main Control
BURGLAR ALARM SYSTEMS BURGLAR ALARM SYSTEMS BURGLAR ALARM SYSTEM EURO ALARM WIRELESS BURGLAR ALARM SYSTEM OASIS
 BURGLAR ALARM SYSTEMS BURGLAR ALARM SYSTEMS BURGLAR ALARM SYSTEM EURO ALARM WIRELESS BURGLAR ALARM SYSTEM OASIS BURGLAR ALARM SYSTEM EURO ALARM Six zones with the following connection capabilities: One
BURGLAR ALARM SYSTEMS BURGLAR ALARM SYSTEMS BURGLAR ALARM SYSTEM EURO ALARM WIRELESS BURGLAR ALARM SYSTEM OASIS BURGLAR ALARM SYSTEM EURO ALARM Six zones with the following connection capabilities: One
WHITE PAPER Professional Series Detectors Sensor Data Fusion February 2008
 WHITE PAPER Intrusion Professional Series Detectors Data Fusion February 2008 Introduction Bosch Security Systems, Inc. Professional Series detectors use a completely new form of processing called Data
WHITE PAPER Intrusion Professional Series Detectors Data Fusion February 2008 Introduction Bosch Security Systems, Inc. Professional Series detectors use a completely new form of processing called Data
INTRUSION ALARM SYSTEM
 INTRUSION ALARM SYSTEM Case studies reveal most burglars are deterred by the mere presence of an alarm system. Burglars attack unprotected premises considerably more often than ones protected by alarm
INTRUSION ALARM SYSTEM Case studies reveal most burglars are deterred by the mere presence of an alarm system. Burglars attack unprotected premises considerably more often than ones protected by alarm
Additional Instruction
 Additional Instruction Note: a. Please connect the camera with 2.4G WIFI router or Ethernet cable, can t support 5G router. b. For first time wifi connection, please put your mobile close to camera within
Additional Instruction Note: a. Please connect the camera with 2.4G WIFI router or Ethernet cable, can t support 5G router. b. For first time wifi connection, please put your mobile close to camera within
Crime Central Station Burglary Alarm Systems
 Page 1 of 10 Scope Crime Central Station Burglary Alarm Systems This criteria is intended to provide Loss Control Representatives with specific guidelines and information for evaluating central station
Page 1 of 10 Scope Crime Central Station Burglary Alarm Systems This criteria is intended to provide Loss Control Representatives with specific guidelines and information for evaluating central station
GSM ALARM SYSTEM USER MANUAL
 GSM ALARM SYSTEM USER MANUAL 1. Instruction The alarm system is based on GSM network. With a GSM SIM card, it can be used wherever you want and no need to connect any wire, which is convenient and easy
GSM ALARM SYSTEM USER MANUAL 1. Instruction The alarm system is based on GSM network. With a GSM SIM card, it can be used wherever you want and no need to connect any wire, which is convenient and easy
NX-10-V3 wireless system. To wire or not to wire?
 NX-10-V3 wireless system To wire or not to wire? Now your security goes where you go Our NX-10-V3 system is fully wireless with a keypad in a designer housing. The hybrid series goes where no security
NX-10-V3 wireless system To wire or not to wire? Now your security goes where you go Our NX-10-V3 system is fully wireless with a keypad in a designer housing. The hybrid series goes where no security
COMITÉ EUROPÉEN DES ASSURANCES
 COMITÉ EUROPÉEN DES ASSURANCES SECRETARIAT GENERAL 3bis, rue de la Chaussée d'antin F 75009 Paris Tél. : +33 1 44 83 11 73 Fax : +33 1 44 83 11 85 Web : cea.assur.org DELEGATION A BRUXELLES Square de Meeûs,
COMITÉ EUROPÉEN DES ASSURANCES SECRETARIAT GENERAL 3bis, rue de la Chaussée d'antin F 75009 Paris Tél. : +33 1 44 83 11 73 Fax : +33 1 44 83 11 85 Web : cea.assur.org DELEGATION A BRUXELLES Square de Meeûs,
Solution 16 plus Security at your fingertips
 Solution 16 plus Security at your fingertips Keeping your home and family safe doesn t need to be complicated. That s why we ve made the Bosch Solution 16 plus security system code pad just like an ATM
Solution 16 plus Security at your fingertips Keeping your home and family safe doesn t need to be complicated. That s why we ve made the Bosch Solution 16 plus security system code pad just like an ATM
Restaurant & café guide
 'Helping our customers stay in business by reducing risk' NZI Risk Solutions TM About NZI Risk Solutions NZI has extensive experience in providing expert risk management advice to help our commercial customers
'Helping our customers stay in business by reducing risk' NZI Risk Solutions TM About NZI Risk Solutions NZI has extensive experience in providing expert risk management advice to help our commercial customers
Why home security is important. Contents
 Why home security is important Although property crime is falling it still accounted for 70% of all police recorded crimes in England and Wales in 2013/14, so it s important to do all you can to keep your
Why home security is important Although property crime is falling it still accounted for 70% of all police recorded crimes in England and Wales in 2013/14, so it s important to do all you can to keep your
AN ESTIMATION OF A PASSIVE INFRA-RED SENSOR'S PROBABILITY OF DETECTION
 Proceedings of the 7 th Conference on Nuclear and Particle Physics, 11-15 Nov. 2009, Sharm El-Sheikh, Egypt AN ESTIMATION OF A PASSIVE INFRA-RED SENSOR'S PROBABILITY OF DETECTION E.A. Osman¹, M.I. El-Gazar¹,
Proceedings of the 7 th Conference on Nuclear and Particle Physics, 11-15 Nov. 2009, Sharm El-Sheikh, Egypt AN ESTIMATION OF A PASSIVE INFRA-RED SENSOR'S PROBABILITY OF DETECTION E.A. Osman¹, M.I. El-Gazar¹,
The Buhl Electric Secure Home. Brought to you by Buhl Electric. Security Packages and Options
 The Buhl Electric Secure Home Brought to you by Buhl Electric Security Packages and Options Contents Why do I Need a Security System... 4 What Are the Advantages of a Hard-Wired Security System... 4 Security
The Buhl Electric Secure Home Brought to you by Buhl Electric Security Packages and Options Contents Why do I Need a Security System... 4 What Are the Advantages of a Hard-Wired Security System... 4 Security
View. Select View Managed Video Services ADT
 monitoring Access Control Video Surveillance Intrusion Detection Fire & life safety Commercial Solutions ADT SM Select View Managed Video Services Leverage your existing investment in video surveillance
monitoring Access Control Video Surveillance Intrusion Detection Fire & life safety Commercial Solutions ADT SM Select View Managed Video Services Leverage your existing investment in video surveillance
the new wireless home alarm system
 the new wireless home alarm system ANDROMEDA s wireless solution offers maximum installation flexibility even where wiring cannot be handled The advantages of Andromeda s wireless system: installation
the new wireless home alarm system ANDROMEDA s wireless solution offers maximum installation flexibility even where wiring cannot be handled The advantages of Andromeda s wireless system: installation
INFORMATION ON STANDARDS FOR ELECTRONIC SECURITY SYSTEMS
 INFORMATION ON STANDARDS FOR ELECTRONIC SECURITY SYSTEMS This is an uncontrolled document. The purpose of this document is to list the primary technical standards that NACOSS Gold and Systems Silver approved
INFORMATION ON STANDARDS FOR ELECTRONIC SECURITY SYSTEMS This is an uncontrolled document. The purpose of this document is to list the primary technical standards that NACOSS Gold and Systems Silver approved
Security. Alarm central unit. Ref.-No. KNX Alarm central unit EAM 4000
 Security Alarm Central Unit 3 4 Technical KNX Alarm central unit EAM 4000 ETS-product family: Alarm system Product type: Alarm central unit The alarm central unit is a modern alarm system using the KNX
Security Alarm Central Unit 3 4 Technical KNX Alarm central unit EAM 4000 ETS-product family: Alarm system Product type: Alarm central unit The alarm central unit is a modern alarm system using the KNX
Fire. The Fire Installers Mate. A guide to fire alarm systems design
 Fire The Fire Installers Mate A guide to fire alarm systems design BS 5839 Part 1:2002 A guide to BS 5839 Part 1:2002 Disclaimer This booklet is not intended to be a comprehensive guide to all aspects
Fire The Fire Installers Mate A guide to fire alarm systems design BS 5839 Part 1:2002 A guide to BS 5839 Part 1:2002 Disclaimer This booklet is not intended to be a comprehensive guide to all aspects
AIR STREAMS IN BUILDING FOR BROILERS
 AIR STREAMS IN BUILDING FOR BROILERS PAVEL KIC - MILAN ZAJÍČEK ABSTRACT The Fluent CFD software is used to do numerical analysis of existing poultry house during the summer and winter periods. Principal
AIR STREAMS IN BUILDING FOR BROILERS PAVEL KIC - MILAN ZAJÍČEK ABSTRACT The Fluent CFD software is used to do numerical analysis of existing poultry house during the summer and winter periods. Principal
Fire Safety In High Rise Building
 Fire Safety In High Rise Building CLASSIFICATION OF BUILDINGS AS PER NATIONAL BUILDING CODE 1. GROUPING. Group A - Residential : Lodgings, Dwellings, Dormitories, Flats, Hotels. Group B Group C - Educational
Fire Safety In High Rise Building CLASSIFICATION OF BUILDINGS AS PER NATIONAL BUILDING CODE 1. GROUPING. Group A - Residential : Lodgings, Dwellings, Dormitories, Flats, Hotels. Group B Group C - Educational
Security Barriers in the Physical Protection Concept of Nuclear Facilities In Switzerland
 Security Barriers in the Physical Protection Concept of Nuclear Facilities In Switzerland B. Wieland Swiss Federal Office of Energy, CH 3003 Berne, Switzerland ABSTRACT: The presentation describes the
Security Barriers in the Physical Protection Concept of Nuclear Facilities In Switzerland B. Wieland Swiss Federal Office of Energy, CH 3003 Berne, Switzerland ABSTRACT: The presentation describes the
Security Alarm Monitoring Protocol
 Security Protocol TABLE OF CONTENTS 1.0 PURPOSE. Page 1 2.0 SCOPE.. Page 1 3.0 DEFINITIONS... Page 1 4.0 PROTOCOL 4.1 General.. Page 4 4.2 of Buildings Perimeter Page 5 4.3 of Buildings Interior Room or
Security Protocol TABLE OF CONTENTS 1.0 PURPOSE. Page 1 2.0 SCOPE.. Page 1 3.0 DEFINITIONS... Page 1 4.0 PROTOCOL 4.1 General.. Page 4 4.2 of Buildings Perimeter Page 5 4.3 of Buildings Interior Room or
Alarm Systems. The purpose of an intruder alarm system is: Commonly utilised detection devices include:
 Alarm Systems An intruder alarm system is designed to detect intruder presence at your premises. When detected, a siren will activate and communicate an alarm signal to one of our highly sophisticated
Alarm Systems An intruder alarm system is designed to detect intruder presence at your premises. When detected, a siren will activate and communicate an alarm signal to one of our highly sophisticated
Restaurant and Café Risk Management Guide. Don t Risk It!
 property & liability Restaurant and Café Risk Management Guide Don t Risk It! About Lumley Insurance Lumley Insurance has extensive experience in restaurant insurance and risk management. This experience
property & liability Restaurant and Café Risk Management Guide Don t Risk It! About Lumley Insurance Lumley Insurance has extensive experience in restaurant insurance and risk management. This experience
Our data centres have been awarded with ISO 27001:2005 standard for security management and ISO 9001:2008 standard for business quality management.
 AIMS is Malaysia and South East Asia s leading carrier neutral data centre operator and managed services provider. We provide international class data storage and ancillary services, augmented by an unrivaled
AIMS is Malaysia and South East Asia s leading carrier neutral data centre operator and managed services provider. We provide international class data storage and ancillary services, augmented by an unrivaled
Solution Ultima ICP-CC488 Home security you can rely on
 Solution Ultima ICP-CC488 Home security you can rely on Keeping your home and family safe doesn t need to be complicated. That s why we ve made the Ultima security system so easy to use all it takes is
Solution Ultima ICP-CC488 Home security you can rely on Keeping your home and family safe doesn t need to be complicated. That s why we ve made the Ultima security system so easy to use all it takes is
ICP-CP500. User's Guide ICP-CP500 Codepads
 ICP-CP500 EN User's Guide ICP-CP500 Codepads ICP-CP500 User's Guide 1.0 ICP-CP500 Series Codepads Overview EN 2 1.0 ICP-CP500 Series Codepads Overview The codepad is the communications interface between
ICP-CP500 EN User's Guide ICP-CP500 Codepads ICP-CP500 User's Guide 1.0 ICP-CP500 Series Codepads Overview EN 2 1.0 ICP-CP500 Series Codepads Overview The codepad is the communications interface between
Building Technologies
 Building Technologies Passive infrared detectors: Safe detection of unwanted visitors. Efficient security systems by Siemens. Many demands are made on the protection of people and property against burglary,
Building Technologies Passive infrared detectors: Safe detection of unwanted visitors. Efficient security systems by Siemens. Many demands are made on the protection of people and property against burglary,
The SwannCloud Mobile App
 QSCLOUD150113E Swann 2014 The SwannCloud Mobile App Have a Smartphone or Tablet? With the free SwannCloud app, you can turn your ios or Android mobile device into a monitoring centre for your camera. Have
QSCLOUD150113E Swann 2014 The SwannCloud Mobile App Have a Smartphone or Tablet? With the free SwannCloud app, you can turn your ios or Android mobile device into a monitoring centre for your camera. Have
Passive Infrared Motion Detector 5420/90. Installation Instructions
 Passive Infrared Motion Detector Installation Instructions 5420/90 The 5420/90 Passive Infrared Motion Detector provides reliable, high performance detection at an affordable price. The Detector features
Passive Infrared Motion Detector Installation Instructions 5420/90 The 5420/90 Passive Infrared Motion Detector provides reliable, high performance detection at an affordable price. The Detector features
Security Service de Services sécurité. Security Alarm Monitoring Protocol
 Security Service de Services sécurité TABLE OF CONTENTS 1.0 PURPOSE. Page 1 2.0 SCOPE.. Page 1 3.0 DEFINITIONS Page 1 4.0 PROTOCOL 4.1 General.. Page 4 4.2 of Buildings Perimeter Page 5 4.3 of Buildings
Security Service de Services sécurité TABLE OF CONTENTS 1.0 PURPOSE. Page 1 2.0 SCOPE.. Page 1 3.0 DEFINITIONS Page 1 4.0 PROTOCOL 4.1 General.. Page 4 4.2 of Buildings Perimeter Page 5 4.3 of Buildings
Intruder Alarm Advice for Domestic Properties
 Intruder Alarm Advice for Properties Burglars want easy pickings and will avoid effective security. Government statistics have shown that approximately 60% of burglaries on homes fitted with burglar alarms
Intruder Alarm Advice for Properties Burglars want easy pickings and will avoid effective security. Government statistics have shown that approximately 60% of burglaries on homes fitted with burglar alarms
City of Temple Burglar Alarm Permit Process Information Sheet
 City of Temple Burglar Alarm Permit Process Information Sheet Initial Permit FREE Renewal Permit Fee $ 10.00 -EVERY TWO YEARS Make checks / money orders payable to: The City of Temple, FARP Mail to: Temple
City of Temple Burglar Alarm Permit Process Information Sheet Initial Permit FREE Renewal Permit Fee $ 10.00 -EVERY TWO YEARS Make checks / money orders payable to: The City of Temple, FARP Mail to: Temple
Advanced Fencing and Security Technologies Ltd
 G.M. Advanced Fencing and Security Technologies Ltd P.O. Box 2327 Kfar Sava Industrial Area 44425, Israel Tel +972-9-7662965 Fax + 972-9-7662964 E-mail: [email protected] Website: www.gmsecurity.com
G.M. Advanced Fencing and Security Technologies Ltd P.O. Box 2327 Kfar Sava Industrial Area 44425, Israel Tel +972-9-7662965 Fax + 972-9-7662964 E-mail: [email protected] Website: www.gmsecurity.com
MONITORING OF DROUGHT ON THE CHMI WEBSITE
 MONITORING OF DROUGHT ON THE CHMI WEBSITE Richterová D. 1, 2, Kohut M. 3 1 Department of Applied and Land scape Ecology, Faculty of Agronomy, Mendel University in Brno, Zemedelska 1, 613 00 Brno, Czech
MONITORING OF DROUGHT ON THE CHMI WEBSITE Richterová D. 1, 2, Kohut M. 3 1 Department of Applied and Land scape Ecology, Faculty of Agronomy, Mendel University in Brno, Zemedelska 1, 613 00 Brno, Czech
SPECIAL APPLICATIONS
 Page 1 SPECIAL APPLICATIONS The protection of microelectronics clean rooms using aspirating smoke detection systems requires special consideration. The physical configuration of the room(s) and the direction
Page 1 SPECIAL APPLICATIONS The protection of microelectronics clean rooms using aspirating smoke detection systems requires special consideration. The physical configuration of the room(s) and the direction
SERIES ͲΝΒΣΞ ΒΟΘΖ Swann 2013
 SERIES Swann 2013 Home Protection that s Advanced & Easy Doorways Windows Garages Sheds Potential Entry Points Blind Spots ALARM SENSOR A typical home layout with suggested mounting points for alarms www.swann.com
SERIES Swann 2013 Home Protection that s Advanced & Easy Doorways Windows Garages Sheds Potential Entry Points Blind Spots ALARM SENSOR A typical home layout with suggested mounting points for alarms www.swann.com
Intrusion. IC60 security meets design. Answers for infrastructure.
 Intrusion IC60 security meets design Answers for infrastructure. 1 Welcome home There is no better feeling than knowing your loved ones and your home are safe. Now imagine if you could improve both your
Intrusion IC60 security meets design Answers for infrastructure. 1 Welcome home There is no better feeling than knowing your loved ones and your home are safe. Now imagine if you could improve both your
Administrative Procedure
 Administrative Procedure Effective: 12/21/2012 Supersedes: N/A Page: 1 of 5 Subject: SECURITY ALARMS 1.0. PURPOSE: The purpose of this procedure is to coordinate and control the installation, monitoring,
Administrative Procedure Effective: 12/21/2012 Supersedes: N/A Page: 1 of 5 Subject: SECURITY ALARMS 1.0. PURPOSE: The purpose of this procedure is to coordinate and control the installation, monitoring,
How to Solve the Most Persistent Problem in Perimeter Security Systems
 How to Solve the Most Persistent Problem in Perimeter Security Systems Duane Thompson General Manager of Fiber SenSys Carrondo, Antonio Commercial Manager, Teleprinta Perimeter Security Challenging!! More
How to Solve the Most Persistent Problem in Perimeter Security Systems Duane Thompson General Manager of Fiber SenSys Carrondo, Antonio Commercial Manager, Teleprinta Perimeter Security Challenging!! More
LYNX Touch Small Business Solutions DYNAMIC, FULL COLOR SELF-CONTAINED BUSINESS CONTROL SYSTEM. Your Connected Business
 LYNX Touch Small Business Solutions DYNAMIC, FULL COLOR SELF-CONTAINED BUSINESS CONTROL SYSTEM Your Connected Business LYNX Touch Protected and Connected Honeywell s LYNX Touch self-contained business
LYNX Touch Small Business Solutions DYNAMIC, FULL COLOR SELF-CONTAINED BUSINESS CONTROL SYSTEM Your Connected Business LYNX Touch Protected and Connected Honeywell s LYNX Touch self-contained business
Wireless Alarm system s manual
 MOUNTVIEW TECH AUSTRALIA PTY LTD Wireless Alarm system s manual ADS A180 Series ADS Security 1/11/2011 1. Before You Begin For your safety and the safety of others, and to ensure that you get the most
MOUNTVIEW TECH AUSTRALIA PTY LTD Wireless Alarm system s manual ADS A180 Series ADS Security 1/11/2011 1. Before You Begin For your safety and the safety of others, and to ensure that you get the most
Adaptive strategies for office spaces in the UK climate
 International Conference Passive and Low Energy Cooling 631 Adaptive strategies for office spaces in the UK climate I. Gallou Environment & Energy Studies Programme, Architectural Association Graduate
International Conference Passive and Low Energy Cooling 631 Adaptive strategies for office spaces in the UK climate I. Gallou Environment & Energy Studies Programme, Architectural Association Graduate
Energy efficient Smart home based on Wireless Sensor Network using LabVIEW
 American Journal of Engineering Research (AJER) e-issn : 2320-0847 p-issn : 2320-0936 Volume-02, Issue-12, pp-409-413 www.ajer.org Research Paper Open Access Energy efficient Smart home based on Wireless
American Journal of Engineering Research (AJER) e-issn : 2320-0847 p-issn : 2320-0936 Volume-02, Issue-12, pp-409-413 www.ajer.org Research Paper Open Access Energy efficient Smart home based on Wireless
Area of Rescue Assistance Communication System ADA Code Applicable excerpts:
 Area of Rescue Assistance Communication System ADA Code Applicable excerpts: CONTENTS (Guidelines and Definitions) Page 1 Area of Rescue Assistance Requirements Page 2 Emergency Communication Equipment
Area of Rescue Assistance Communication System ADA Code Applicable excerpts: CONTENTS (Guidelines and Definitions) Page 1 Area of Rescue Assistance Requirements Page 2 Emergency Communication Equipment
Solution Ultima ICP-CC488 Home security you can rely on
 Solution Ultima ICP-CC488 Home security you can rely on Keeping your home and family safe doesn t need to be complicated. That s why we ve made the Ultima security system so easy to use all it takes is
Solution Ultima ICP-CC488 Home security you can rely on Keeping your home and family safe doesn t need to be complicated. That s why we ve made the Ultima security system so easy to use all it takes is
Appendix G. Security management plan
 Appendix G Security management plan Security Management Plan Prepared by: Kann Finch Group Project Energy Australia Belmore Park Zone 1- Sub-station component General Design Requirements The perimeter
Appendix G Security management plan Security Management Plan Prepared by: Kann Finch Group Project Energy Australia Belmore Park Zone 1- Sub-station component General Design Requirements The perimeter
Hills wireless security alarm DIY range
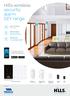 Hills wireless security alarm DIY range EASY TO INSTALL DIY system PEACE OF MIND Receive SMS/calls when alarm is armed INTERACTIVE Arm and disarm by SMS or via smartphone app Control your alarm via smart
Hills wireless security alarm DIY range EASY TO INSTALL DIY system PEACE OF MIND Receive SMS/calls when alarm is armed INTERACTIVE Arm and disarm by SMS or via smartphone app Control your alarm via smart
S I E R R A PRODUCT INFORMATION GUIDE FOR HOME SECURITY. SIERRA Page 1
 S I E R R A PRODUCT INFORMATION GUIDE FOR HOME SECURITY SIERRA Page 1 C O N T E N T S USING YOUR SIERRA SYSTEM: Turning On/Off Home Arming Instant Home Arming Quick Exit Mode Chime Mode SPECIAL FUNCTIONS:
S I E R R A PRODUCT INFORMATION GUIDE FOR HOME SECURITY SIERRA Page 1 C O N T E N T S USING YOUR SIERRA SYSTEM: Turning On/Off Home Arming Instant Home Arming Quick Exit Mode Chime Mode SPECIAL FUNCTIONS:
Jewellers Block Insurance and the Pre- Risk Survey
 Jewellers Block Insurance and the Pre- Risk Survey What is Jewellers Block and who might purchase this insurance? Jewellers Block Insurance relates to insurance cover provided for the following: Retailers
Jewellers Block Insurance and the Pre- Risk Survey What is Jewellers Block and who might purchase this insurance? Jewellers Block Insurance relates to insurance cover provided for the following: Retailers
Designing Out Crime Assessment
 Designing Out Crime Assessment New Flats (Affordable Housing) Yew Tree Road Moreton Wirral CH46 8UA Construction of flats complex. For Bernard Taylor Partnership Ltd [email protected] Tel 0161 443
Designing Out Crime Assessment New Flats (Affordable Housing) Yew Tree Road Moreton Wirral CH46 8UA Construction of flats complex. For Bernard Taylor Partnership Ltd [email protected] Tel 0161 443
Solution 880 Operators Manual ISSUE 1.10
 Solution 880 Operators Manual ISSUE 1.10 Solution 880 Operators Manual Copyright 2001 by, SYDNEY, AUSTRALIA Document Part Number MA408O DOCUMENT ISSUE 1.10 Printed 25 May 2001 This documentation is provided
Solution 880 Operators Manual ISSUE 1.10 Solution 880 Operators Manual Copyright 2001 by, SYDNEY, AUSTRALIA Document Part Number MA408O DOCUMENT ISSUE 1.10 Printed 25 May 2001 This documentation is provided
Home Security. What you absolutely must know before purchasing a security system
 Home Security What you absolutely must know before purchasing a security system 1 As founder and owner of SHIELD Security Systems, I ve answered hundreds, if not thousands, of questions from homeowners
Home Security What you absolutely must know before purchasing a security system 1 As founder and owner of SHIELD Security Systems, I ve answered hundreds, if not thousands, of questions from homeowners
ALARM SYSTEM INSTALLATION GUIDE
 ALARM SYSTEM INSTALLATION GUIDE Congratulations on the purchase of your Egardia alarm system. Egardia's website www.egardia.com Customer services Please visit www.egardia.com if you would like further
ALARM SYSTEM INSTALLATION GUIDE Congratulations on the purchase of your Egardia alarm system. Egardia's website www.egardia.com Customer services Please visit www.egardia.com if you would like further
3.0 Nonsystem Based Design Descriptions and ITAAC
 3.0 Nonsystem Based Design Descriptions and ITAAC 3.1 Security 3.1.1 Design Features The physical security system provides physical features to detect, delay, assist response to, and defend against the
3.0 Nonsystem Based Design Descriptions and ITAAC 3.1 Security 3.1.1 Design Features The physical security system provides physical features to detect, delay, assist response to, and defend against the
Using Your. Security System With Icon Keypad S5020, S5021, S5022
 Using Your Security System With Icon Keypad S5020, S5021, S5022 Contents 1 Overview Your Security System... 1 How Your Security System Works... 2 Your System's Programming... 3 Getting Used to Your System...
Using Your Security System With Icon Keypad S5020, S5021, S5022 Contents 1 Overview Your Security System... 1 How Your Security System Works... 2 Your System's Programming... 3 Getting Used to Your System...
Preventing arson in buildings
 Preventing arson in buildings More than half of fires in commercial buildings are started deliberately. These maliciously started fires can be particularly dangerous because they often develop quickly,
Preventing arson in buildings More than half of fires in commercial buildings are started deliberately. These maliciously started fires can be particularly dangerous because they often develop quickly,
PSTN Home Alarm System
 PSTN Home Alarm System User Manual Model: PST-TEL99E Please read this user guide carefully before operation and installation. Contents 1. Product Overview... - 3-2. Main Function & Features... - 3-3. For
PSTN Home Alarm System User Manual Model: PST-TEL99E Please read this user guide carefully before operation and installation. Contents 1. Product Overview... - 3-2. Main Function & Features... - 3-3. For
How To Protect Yourself With Securtek
 Protect What Matters Most to You For more information please contact our Customer Care Centre at 1-877-777-7590 or visit us online at securtek.com SMS27-06/08/5M Why Choose SecurTek? Providing Peace of
Protect What Matters Most to You For more information please contact our Customer Care Centre at 1-877-777-7590 or visit us online at securtek.com SMS27-06/08/5M Why Choose SecurTek? Providing Peace of
THE QUICK START QUICK START GUIDE
 THE QUICK START QUICK START GUIDE www.frontpointsecurity.com/support-overview WELCOME FRONTPOINT TO Thank you for choosing Frontpoint for your security needs! We re delighted to have you as a new customer
THE QUICK START QUICK START GUIDE www.frontpointsecurity.com/support-overview WELCOME FRONTPOINT TO Thank you for choosing Frontpoint for your security needs! We re delighted to have you as a new customer
A REMOTE HOME SECURITY SYSTEM BASED ON WIRELESS SENSOR NETWORK AND GSM TECHNOLOGY
 A REMOTE HOME SECURITY SYSTEM BASED ON WIRELESS SENSOR NETWORK AND GSM TECHNOLOGY AIM: The main aim of this project is to implement Remote Home Security System Based on Wireless Sensor Network and GSM
A REMOTE HOME SECURITY SYSTEM BASED ON WIRELESS SENSOR NETWORK AND GSM TECHNOLOGY AIM: The main aim of this project is to implement Remote Home Security System Based on Wireless Sensor Network and GSM
BS5839 Part 1:2002 Overview
 BS5839 Part 1:2002 Overview 1 Contents Introduction So why is the current standard being revised? The brief for the new standard Changes to structure of current Standard Enhanced certification of Fire
BS5839 Part 1:2002 Overview 1 Contents Introduction So why is the current standard being revised? The brief for the new standard Changes to structure of current Standard Enhanced certification of Fire
Doc 10. UTM Standards: Card Access Security System
 Doc 10 UTM Standards: Card Access Security System 1. GENERAL... 2 1.1. GENERAL REQUIREMENTS.... 2 1.2. SUMMARY OF WORK INCLUDED... 2 1.3. OVERVIEW... 2 1.4. MANDATORY REQUIREMENTS... 3 1.5. ACCESS CONTROL
Doc 10 UTM Standards: Card Access Security System 1. GENERAL... 2 1.1. GENERAL REQUIREMENTS.... 2 1.2. SUMMARY OF WORK INCLUDED... 2 1.3. OVERVIEW... 2 1.4. MANDATORY REQUIREMENTS... 3 1.5. ACCESS CONTROL
5W LED Energy Saver PIR Bulkhead
 5W LED Energy Saver PIR Bulkhead Model: LED88PIR Black I n s t a l l a t i o n & Ope r a t i n g I n s t r u c t i o n s 1. General information: The unit utilises passive infrared technology to detect
5W LED Energy Saver PIR Bulkhead Model: LED88PIR Black I n s t a l l a t i o n & Ope r a t i n g I n s t r u c t i o n s 1. General information: The unit utilises passive infrared technology to detect
Cooling a hot issue? MINKELS COLD CORRIDOR TM SOLUTION
 Cooling a hot issue? MINKELS COLD CORRIDOR TM SOLUTION The heat load in data centers is increasing rapidly, the adaptation of a cooling strategy is often necessary. Many data centers and server rooms use
Cooling a hot issue? MINKELS COLD CORRIDOR TM SOLUTION The heat load in data centers is increasing rapidly, the adaptation of a cooling strategy is often necessary. Many data centers and server rooms use
Florida Building Code 2004 SECTION 1009 STAIRWAYS AND HANDRAILS
 Florida Building Code 2004 SECTION 1009 STAIRWAYS AND HANDRAILS 1009.1 Stairway width. The width of stairways shall be determined as specified in Section 1005.1, but such width shall not be less than 44
Florida Building Code 2004 SECTION 1009 STAIRWAYS AND HANDRAILS 1009.1 Stairway width. The width of stairways shall be determined as specified in Section 1005.1, but such width shall not be less than 44
Totally Wireless Video Security
 Traditional Video Surveillance ($50,000+) vs. Event-Based Videofied Solution ($2,500) Executive Summary: Totally Wireless Video Security has been effective but cost and complexity has limited deployment
Traditional Video Surveillance ($50,000+) vs. Event-Based Videofied Solution ($2,500) Executive Summary: Totally Wireless Video Security has been effective but cost and complexity has limited deployment
What is an intruder alarm?
 How to Plan and install an Intruder Alarm PART 1 PART 1 August 009 What is an intruder alarm? An intruder alarm system monitors and detects unauthorised entry to properties homes and businesses alike -
How to Plan and install an Intruder Alarm PART 1 PART 1 August 009 What is an intruder alarm? An intruder alarm system monitors and detects unauthorised entry to properties homes and businesses alike -
Our data centres have been awarded with ISO 27001:2005 standard for security management and ISO 9001:2008 standard for business quality management.
 AIMS is Malaysia and South East Asia s leading carrier neutral data centre operator and managed services provider. We provide international class data storage and ancillary services, augmented by an unrivaled
AIMS is Malaysia and South East Asia s leading carrier neutral data centre operator and managed services provider. We provide international class data storage and ancillary services, augmented by an unrivaled
IMS [Integrated Management System] Surveillance Solution Segment Focus: Gaming Industry
![IMS [Integrated Management System] Surveillance Solution Segment Focus: Gaming Industry IMS [Integrated Management System] Surveillance Solution Segment Focus: Gaming Industry](/thumbs/24/3135702.jpg) IMS [Integrated Management System] Surveillance Solution Segment Focus: Gaming Industry Needs analysis Reduce disputes over payouts Eliminate theft Detect misconduct and record it for use as evidence in
IMS [Integrated Management System] Surveillance Solution Segment Focus: Gaming Industry Needs analysis Reduce disputes over payouts Eliminate theft Detect misconduct and record it for use as evidence in
... ... Why All Data Centers are Not Created Equal
 ... Las Vegas SuperNAP INFOSHEET... Why All Data Centers are Not Created Equal The Las Vegas SuperNap Auto-Graphics Data Center of Choice Auto-Graphics (A-G) offers its customers absolute flexibility when
... Las Vegas SuperNAP INFOSHEET... Why All Data Centers are Not Created Equal The Las Vegas SuperNap Auto-Graphics Data Center of Choice Auto-Graphics (A-G) offers its customers absolute flexibility when
Current as of 11/10/08 1 of 1
 BEST PRACTICES STANDARDS FOR SCHOOLS UNDER CONSTRUCTION OR BEING PLANNED FOR CONSTRUCTION I. Site Layout A. School buildings shall be provided with a securable perimeter. A securable perimeter means that
BEST PRACTICES STANDARDS FOR SCHOOLS UNDER CONSTRUCTION OR BEING PLANNED FOR CONSTRUCTION I. Site Layout A. School buildings shall be provided with a securable perimeter. A securable perimeter means that
A Beginner s Guide to Home Security Systems
 Systems An introduction to the basic concepts and arguments for owning a home security system. By Intruder Prevention Page 2 of 22 Legal Information: This is a reference guide and is to be used for informational
Systems An introduction to the basic concepts and arguments for owning a home security system. By Intruder Prevention Page 2 of 22 Legal Information: This is a reference guide and is to be used for informational
Professional Monitoring
 Mark Twain Communications Alarm & Security Systems Video Surveillance Self Monitoring Professional Monitoring Page 2 SERVING THE COUNTIES OF: Adair - Clark - Knox - Lewis - Macon - Marion Monroe - Scotland
Mark Twain Communications Alarm & Security Systems Video Surveillance Self Monitoring Professional Monitoring Page 2 SERVING THE COUNTIES OF: Adair - Clark - Knox - Lewis - Macon - Marion Monroe - Scotland
Keys to understanding your alarm system
 Keys to understanding your alarm system This section is designed to allow you to familiarize yourself with most of the security system devices that may be installed or proposed to be installed in your
Keys to understanding your alarm system This section is designed to allow you to familiarize yourself with most of the security system devices that may be installed or proposed to be installed in your
SECURITY VULNERABILITY CHECKLIST FOR ACADEMIC AND SMALL CHEMICAL LABORATORY FACILITIES
 SECURITY VULNERABILITY CHECKLIST FOR ACADEMIC AND SMALL CHEMICAL LABORATORY FACILITIES by the American Chemical Society, Committee on Chemical Safety, Safe Practices Subcommittee Introduction Terrorism
SECURITY VULNERABILITY CHECKLIST FOR ACADEMIC AND SMALL CHEMICAL LABORATORY FACILITIES by the American Chemical Society, Committee on Chemical Safety, Safe Practices Subcommittee Introduction Terrorism
CHAPTER 8. Village of Caledonia Alarm Systems Ordinance (2013-11 07/01/13)
 CHAPTER 8 Village of Caledonia Alarm Systems Ordinance (2013-11 07/01/13) Section Title Number 5-8-1 Title 5-8-2 Declaration of Purpose 5-8-3 Definitions 5-8-4 Administrative Rules 5-8-5 Supervised Fire
CHAPTER 8 Village of Caledonia Alarm Systems Ordinance (2013-11 07/01/13) Section Title Number 5-8-1 Title 5-8-2 Declaration of Purpose 5-8-3 Definitions 5-8-4 Administrative Rules 5-8-5 Supervised Fire
BARNSTABLE POLICE DEPARTMENT
 BARNSTABLE POLICE DEPARTMENT ALARM REGULATIONS Effective Date: January 2011 Per the Authority of: Paul B. MacDonald, Chief of Police Introduction Pursuant to Chapter 17 of the General Ordinances of the
BARNSTABLE POLICE DEPARTMENT ALARM REGULATIONS Effective Date: January 2011 Per the Authority of: Paul B. MacDonald, Chief of Police Introduction Pursuant to Chapter 17 of the General Ordinances of the
Quick Setup Guide LifeShield Broadband
 Quick Setup Guide LifeShield Broadband 1 Important Information login.lifeshield.com How To Contact Us [email protected] 877-464-7437 lifeshield.com/support-center login.lifeshield.com 1 Get Started
Quick Setup Guide LifeShield Broadband 1 Important Information login.lifeshield.com How To Contact Us [email protected] 877-464-7437 lifeshield.com/support-center login.lifeshield.com 1 Get Started
Welcome to Bell Aliant NextGen Home Security
 Quick Start Guide Welcome to Bell Aliant NextGen Home Security Congratulations! Your home is now protected by the most advanced security technology available. This guide is intended to familiarize you
Quick Start Guide Welcome to Bell Aliant NextGen Home Security Congratulations! Your home is now protected by the most advanced security technology available. This guide is intended to familiarize you
