SAFE HARBOR. unwanted popup ads, and block dangerous
|
|
|
- Aileen Morgan
- 8 years ago
- Views:
Transcription
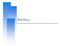
1 KNOW-HOW Squid proxy server Implementing a home proxy server with Squid SAFE HARBOR A proxy server provides safer and more efficient surfing. Although commercial proxy solutions are available, all you really need is Linux and an old PC in the attic. BY GEERT VAN PAMEL I have had a home network for several years. I started with a router using Windows XP with ICS (Internet Connection Sharing) and one multi-homed Ethernet card. The main disadvantages were instability, low performance, and a total lack of security. Troubleshooting was totally impossible. Firewall configuration was at the mercy of inexperienced users, who clicked randomly at security settings as if they were playing Russian roulette. I finally turned to Linux and set up an iptables firewall on a Pentium II computer acting as a router. The firewall system would keep the attackers off my network and log incoming and outgoing traffic. Along with the iptables firewall, I also set up a Squid proxy server to improve Internet performance, filter out unwanted popup ads, and block dangerous URLs. A Squid proxy server filters Web traffic and caches frequently accessed files. A proxy server limits Internet bandwidth usage, speeds up Web access, and lets you filter URLs. Centrally blocking advertisements and dangerous downloads is cost effective and transparent for the end user. Squid is a high performance implementation of a free Open- Source, full-featured proxy caching server. Squid provides extensive access controls and integrates easily with an iptables firewall. In my case, the Squid proxy server and the iptables firewall worked together to protect my network from intruders and dangerous HTML. You ll find many useful discussions of firewalls in books, magazines, and Websites. (See [1] and [2], for example.) The Squid proxy server, on the other hand, is not as Table 1: Recommended Hardware Necessary Components Specifics Intel Pentium II CPU, or higher - Why not a spare Alpha Server? 350 MHz MB memory minimum more is better 1 or more IDE disks (reuse 2 old disks: 1 GB system SW + swap & 3 GB for cache + /home disk) 4 GB minimum 2 Ethernet cards, minihub, fast Ethernet modem, 100 Mbit/ s if wireless router or hub possible CDROM, DVD reader software is mostly distributed via DVD Use only normal straight LAN cables [no need for modem and cross cables] minihub cross themselves! 48 ISSUE 60 NOVEMBER 2005 W W W. L I N U X- M A G A Z I N E. C O M
2 Squid proxy server KNOW-HOW well documented, especially for small home networks like mine. In this article, I will show you how to set up Squid. Getting Started The first step is to find the necessary hardware. Figure 1 depicts the network configuration of the Pentium II computer I used as a firewall and proxy server. This firewall system should operate with minimal human intervention, so after the system is configured, you ll want to disconnect the mouse, keyboard, and video screen. You may need to adjust the BIOS settings so that the computer will boot without a keyboard. The goal is to be able to put the whole system in the attic, where you won t hear it or trip over it. From the minihub shown in Figure 1, you can come downstairs to the home network using standard UTP cable or a wireless connection. Table 1 shows recommended hardware for the firewall machine. Assuming your firewall is working, the next step is to set up Squid. Squid is available from the Internet at [3] or one of its mirrors [4] as tar.gz (compile from sources). You can easily install it using one of the following commands: rpm -i /cdrom/redhat/rpms/u squid-2.4.stable7-4.i386.rpmu # Red Hat 8 rpm -i /cdrom/fedora/rpms/u squid-2.5.stable6-3.i386.rpm U # Fedora Core 3 rpm -i /cdrom//u squid-2.5.stable6-6.i586.rpmu # SuSE 9.2 At this writing, the current stable Squid version is 2.5. Configuring Squid Once Squid is installed, you ll need to configure it. Squid has one central configuration file. Every time this file changes, the configuration must be reloaded with the command /sbin/ init. d/ squid reload. You can edit the configuration file with a text editor. You ll find a detailed description of the settings inside the squid.conf file, although the discussion is sometimes very technical and difficult to understand. This section summarizes some of the important settings in the squid.conf file. First of all, you can prevent certain metadata related to your configuration from reaching the external world when you surf the Web: vi /etc/squid/squid.conf anonymize_headers deny U From Server Via User-Agent forwarded_for off strip_query_terms on Note that you cannot anonymize Referer and WWW-Authenticate because otherwise authentication and access control mechanisms won t work. forwarded_for off means that the IP address of the proxy server will not be sent externally. With strip_query_terms on, you do not log URL parameters after the?. When this parameter is set to off, the full URL is logged in the Squid log files. This feature can help with debugging the Squid filters, but it can also violate privacy rules. The next settings identify the Squid host, the (internal) domain where the machine is operating, and the username of whoever is responsible for the server. Note the dot in front of the domain. Further on, you find the name of the local DNS caching server, and the number of domain names to cache into the Squid server. visible_hostname squid append_domain.mshome.net Internet Figure 1: Ethernet basic LAN configuration. cache_mgr sysman dns_nameservers dns_testnames router.mshome.net fqdncache_size 1024 http_port 80 icp_port 0 http_port is the port used by the proxy server. You can choose anything, as long as the configuration does not conflict with other ports on your router. A common choice is 8080 or 80. The Squid default, 3128, is difficult to remember. We are not using cp_port, so we set it to 0. This setting synchronizes proxy servers. With log_mime_hdrs on, you can make mime headers visible in the access. log file. Avoid Disk Contention Squid needs to store its cache somewhere on the hard disk. The cache is a tree of directories. With the cache_dir option in the squid.conf file, you can specify configuration settings such as the following: disk I/ O mechanism aufs location of the squid cache on the disk /var/ cache/ squid amount of disk space that can be used by the proxy server 2.5 GB number of main directories 16 subdirectories 256 For instance: cache_dir aufs U /var/cache/squid Local Network W W W. L I N U X- M A G A Z I N E. C O M ISSUE 60 NOVEMBER
3 KNOW-HOW Squid proxy server The disk access method options are as follows: ufs classic disk access (too much I/ O can slow down the Squid server) aufs asynchronous UFS with threads, less risk of disk contention diskd diskd daemon, avoiding disk contention but using more memory UFS is the classic UNIX file system I/ O. We recommend using aufs to avoid I/ O bottlenecks. (When you use aufs, you have fewer processes.) # ls -ld /var/cache/squid lrwxrwxrwx 1 root rootu 19 Nov 22 00:42 U /var/cache/squid -> U /volset/cache/squid I suggest you keep the standard file location for the squid cache /var/ cache/ squid, then create a symbolic link to the real cache directory. If you move the cache to another disk for performance or capacity reasons, you only have to modify the symbolic link. The disk space is distributed among all directories. You would normally look for even distribution across all directories, but in practice, some variation in the distribution is acceptable. More complex setups using multiple disks are possible, but for home use, one directory structure is sufficient. maximum_object_sizeu _in_memory 2048 KB Log Format Specification You can choose between Squid log format and standard web server log format using the parameter emulate_httpd_log. When the parameter is set to on, standard web log format is used; if the parameter is set to off, you get more details with the Squid format. See [7] for more on analyzing Squid log files. Proxy Hierarchy The Squid proxy can work in a hierarchical way. If you want to avoid the parent proxy for some destinations, you can allow a direct lookup. The browser will still use your local proxy! acl direct-domain U dstdomain.turboline.be always_direct allow U direct-domain acl direct-path urlpath_regexu -i "/etc/squid/direct-path.reg" always_direct allow direct-path Some ISPs allow you to use their proxy server to visit their own pages even if you are not a customer. This can help you speed up your visits to their pages. The closer the proxy to the original Table 2: ACL Guidelines the order of the rules is important first list all the deny rules the first matching rule is executed the rest of the rules are ignored the last rule should be an allow all pages, the more likely the page is to be cached. Because your own ISP is more remote, the ISP is less likely to be caching its competitor s contents cache_peer proxy.tiscali.beu parent U no-query default cache_peer_domain U proxy.tiscali.be.tiscali.be no-query means that you do not use, or cannot use, ICP (the Internet Caching Protocol), see [8]. You can obtain the same functionality using regular expressions, but this gives you more freedom. cache_peer proxy.tiscali.beu parent U no-query default acl tiscali-proxy U dstdom_regex -i U \.tiscali\.be$ cache_peer_access U proxy.tiscali.be allow U tiscali-proxy Cache Replacement The proxy server uses an LRU (Least Recently Used) algorithm. Detailed studies by HP Laboratories [6] have revealed that an LRU algorithm is not always an intelligent choice. The GDSF setting keeps small popular objects in cache, while removing bigger and lesser used objects, thus increasing the overall efficiency. cache_replacement_policyu heap GDSF memory_replacement_policyu heap GDSF Big objects requested only once can flush out a lot of smaller objects, therefore you d better limit the maximum object size for the cache: cache_mem 20 MB maximum_object_sizeu KB Listing 1: Blocking Unwanted Pages 01 acl block-ip dst "/etc/squid/block-ip.reg" 02 deny_info filter_spam block-ip 03 http_access deny block-ip acl block-hosts dstdom_regex -i "/etc/squid/block-hosts.reg" 06 deny_info filter_spam block-hosts 07 http_access deny block-hosts acl noblock-url url_regex -i "/etc/squid/noblock-url.reg" 10 http_access allow noblock-url Safe_ports acl block-path urlpath_regex -i "/etc/squid/block-path.reg" 13 deny_info filter_spam block-path 14 http_access deny block-path acl block-url url_regex -i "/etc/squid/block-url.reg" 17 deny_info filter_spam block-url 18 http_access deny block-url 50 ISSUE 60 NOVEMBER 2005 W W W. L I N U X- M A G A Z I N E. C O M
4 Squid proxy server KNOW-HOW 01 vi /etc/squid/errors/filter_spam 02 Listing 2: Making a Page Invisible 03 <script language="javascript" type="text/javascript"> 04 <!-- 05 window.status="filter " + document.location; //.pathname; 06 // --> 07 </script> 08 <noscript><plaintext><!-- The ACL could also include a regular expression (regex for short) with the URL using an url_regex construct. For Squid, regular expressions can be specified immediately, or they can be in a file name between double quotes, in which case the file should contain one regex expression per line no empty lines. The -i (ignore case) means that case-insensitive comparisons are used. If you are configuring a system with multiple proxies, you can specify a round-robin to speed up page lookups and minimize the delay when one of the servers is not available. Remember that most browsers issue parallel connections when obtaining all the elements from a single page. If you use multiple proxy servers to obtain these elements, your response time might be better. cache_peer U parent U no-query round-robin cache_peer U parent U no-query round-robin cache_peer U parent U no-query round-robin FTP files are normally downloaded just once, so will not normally want to cache them, except when downloading repeatedly. Also, local pages are not normally cached, since they already reside on your network :.mshome.net always_direct allow U local-domain acl localnet-dst dst U /24 always_direct allow U localnet-dst Filtering with Squid The preceding sections introduced some important Squid configuration settings. You have already learned earlier in this article that ACLs (Access Control Lists) can be used for allowing direct access to pages without using the parent proxy. In this section, I ll show you how to use ACLs for more fine-grained access control. Table 2 provides some guidelines for creating ACL lists. It is a very good idea to only allow what-you-see-is-what-youget (WYSIWYG) surfing. If you do not want to see certain pages or frames, then you can automatically block the corresponding URLs for those pages on the proxy server. You can filter on: domains of client or server IP subnets of client or server URL path Full URL including parameters keywords ports protocols: HTTP, FTP methods: GET, POST, HEAD, CON- NECT 01 vi /etc/squid/block-hosts.reg ^a\. 04 ^ad\. 05 ^adfarm\. 06 ^ads\. 07 ^ads1\. 08 ^al\. 09 ^as\. 10 \.msads\.net$ 11 ^ss\. day & hour browser type username Listing 1 shows examples of commands that block unwanted pages. The script in Listing 2 will make unwanted pages invisible: Whenever Squid executes the deny_ info tag, it sends the file /etc/ squid/ errors/ filter_spam to the browser instead of the real Web page effectively filtering away the unwanted object. The trailing <!-- hides any other Squid error messages in the body of the text. Squid allows you to block content by IP subnet. For instance, you can block sites with explicit sexual content; you could use whois [9] to help you identify the subnets, then enter the subnets in the /etc/ squid/ block-ip.reg file: vi /etc/squid/block-ip.reg / / / / / /18 To block advertisements or sex sites by domain name, you can list regular expressions describing the sites in the file /etc/ squid/ block-hosts.reg, as shown in Listing 3. It is also a good idea to block certain file types. For instance, you do not want to allow.exe files, since these are some- Listing 3: Blocking by Domain Name 15 ^tracking\. 16 adserver.adtech.de \.belstat\.be$ 19 \.doubleclick\.net$ 20 \.insites\.be$ 21 ^metrics\. 22 \.metriweb\$ 23 \.metriweb\.$ \.playboy\.com$ acl FTP proto FTP always_direct allow FTP acl local-domain dstdomain U 12 ^sa\. 13 ^sc\. 14 ^sm6\. 26 \.hln\.be$ 27 side W W W. L I N U X- M A G A Z I N E. C O M ISSUE 60 NOVEMBER
5 KNOW-HOW Squid proxy server Listing 4: Blocking by Path or Extension 01 vi /etc/squid/block-path.reg \.ad[ep](\?.*)?$ 04 \.ba[st](\?.*)?$ 05 \.chm(\?.*)?$ 06 \.cmd(\?.*)?$ 07 \.com(\?.*)?$ 08 \.cpl(\?.*)?$ 09 \.crt(\?.*)?$ 10 \.dbx(\?.*)?$ 11 \.hlp(\?.*)?$ 12 \.hta(\?.*)?$ 13 \.in[fs](\?.*)?$ 14 \.isp(\?.*)?$ 15 \.lnk(\?.*)?$ 16 \.md[abetwz](\?.*)? 17 \.ms[cpt](\?.*)?$ 18 \.nch(\?.*)?$ 19 \.ops(\?.*)?$ 20 \.pcd(\?.*)?$ 21 \.p[ir]f(\?.*)?$ 22 \.reg(\?.*)?$ 23 \.sc[frt](\?.*)?$ 24 \.sh[bs](\?.*)?$ 25 \.url(\?.*)?$ 26 \.vb([e])?(\?.*)?$ 27 \.vir(\?.*)?$ 28 \.wm[sz](\?.*)?$ 29 \.ws[cfh](\?.*)?$ INFO [1] Presentation for the HP-Interex user group in Belgium on 17/ 03/ 2005 about Implementing a home Router, Firewall, Proxy server, and DNS Caching Server using Linux users. belgacombusiness. net/ linuxug/ pub/ router/ linux-router-firewall-proxy. zip [2] Firewalls: www. linux-magazine. com/ issue/ 40/ Checkpoint_FW1_Firewall_Builder. pdf www. linux-magazine. com/ issue/ 34/ IPtables_Firewalling. pdf [3] About Squid in general: www. squid-cache. org squid-docs. sourceforge. net/ latest/ book-full. html#aen www. squid-cache. org/ FAQ/ FAQ-10. html [4] Squid mirror sites: www1. de. squid-cache. org www1. fr. squid-cache. org www1. nl. squid-cache. org www1. uk. squid-cache. org [5] Suse 9.2 Professional DVD software distribution www. linux-magazine. com/ issue/ 54/ Linux_Magazine_ DVD. pdf [6] For more information about the GDSF and LFUDA cache replacement policies see: www. hpl. hp. com/ techreports/ 1999/ HPL html fog. hpl. external. hp. com/ techreports/ 98/ HPL html [7] Reporting and analysing Squid log files: www. linux-magazine. com/ issue/ 36/ Charly_Column. pdf [8] ICP Internet Caching Protocol: en. wikipedia. org/ wiki/ Internet_Cache_ Protocol [9] The whois database: www. ripe. net/ db/ other-whois. html [10] About Regular Expressions: www. python. org/ doc/ current/ lib/ module-re. html [11] Example configuration files for Squid: members. lycos. nl/ geertivp/ pub/ squid times executable zip files that install software. Squid lets you block files by path, filename, or file extension, as shown in Listing 4. Squid also lets you filter for regular expressions used in the URL. Of course, your filter may occasionally turn up a false positive. You can add regular expressions for URLs you specifically don t want to block to /etc/ squid/ noblock-url.reg. vi /etc/squid/noblock-url.reg ^ You can find an up-to-date version of those configuration files at [11] Protect your Ports For security reasons, you should disable all ports and only allow well known web ports using the syntax shown in Listing 5. The same can be done for connected ports. You can allow SSL ports when connected, and deny them otherwise. Remember that the normal HTTP protocol is not connected. The client and the browser always establish a new connection for every page visit. 01 acl Safe_ports port 80 # http 02 acl Safe_ports port 21 # ftp 03 acl Safe_ports port 2020 # BeOne Radio 04 acl Safe_ports port 2002 # Local server 05 acl Safe_ports port 8044 # Tiscali acl SSL_ports port acl SSL_ports port 1863 U # Microsoft Messenger acl SSL_ports port U # Limewire http_access allow U CONNECT SSL_ports http_access deny U CONNECT 06 acl Safe_ports port 8080 # Turboline port scan 07 acl Safe_ports port 8081 # Prentice Hall # Deny requests to unknown ports 10 http_access deny!safe_ports Do not allow others to misuse your cache! You only want your cache to be used by your own intranet. Users on the external Internet should not be able to access your cache: acl localhost src U / acl localnet-src src U /24 Listing 5: Protecting Ports http_access deny!localnet-src Allowing All the Rest To allow only the protocols and the methods that you want: acl allow-proto proto HTTP http_access deny!allow-proto 52 ISSUE 60 NOVEMBER 2005 W W W. L I N U X- M A G A Z I N E. C O M
6 Squid proxy server KNOW-HOW acl allow-method U method GET POST http_access deny U!allow-method The last rule should be an allow-all, since the previous rule was a deny http_access allow all Remember after changing parameters to always restart the Squid server with the following command: /sbin/init.d/squid reload For SuSE the /sbin/ init.d folder is standard. For Fedora, create a symbolic link: You should configure your iptables firewall so that it blocks all outgoing HTTP traffic unless the proxy server is used. Since the proxy server is on the local network, it allows all incoming requests from local browser clients. Any attempt to bypass the Squid filters is blocked by the FORWARD firewall rule cd /sbin ln -s /etc/init.d When you have finished the configuration, use setup (Fedora), yast2 (SuSE), or an equivalent tool to activate the Squid service. Remember to reload the server when you change a file. /sbin/init.d/squid reload If anything does not work as expected, you can look for a reason in the cache log file /var/ log/ squid/ cache.log. Conclusions This article is the result of a presentation for the Belgium HP-Interex organization. Enforce Parental Control and Block Spyware blocking HTTP outgoing traffic. Spyware programs mostly use the HTTP protocol (remember: port 80) for outgoing connections, but it seems that Spyware hardly ever uses the proxy (because Spyware authors are too lazy to inspect the rconfiguration). Spyware is thus blocked by the firewall rules. Slides are available from [1] giving more details about the setup of the iptables firewall, the router, the DNS caching server, the DHCP server, and the NTP server. If you are looking for better performance, safer surfing, and a way to block access to dangerous Web content, try putting a Squid proxy server in your attic. For the cost conscious among you: a Pentium II router consumes about 11 kwh/ week. You should balance this expense against the increased security and reduced headaches of operating your own firewall with Squid proxy caching. THE AUTHOR Geert Van Pamel has worked as a project manager at Belgacom in Belgium since He has been a member of DECUS since 1985 and a board member of HP-Interex since He learned UNIX on a PDP system in 1982, and he currently works with Linux in a mixed environment with other servers such as Tru64 UNIX, HP-UX, OpenVMS, NonStop Tandem, SUN, and NCR Teradata. ADVERTISEMENT W W W. L I N U X- M A G A Z I N E. C O M ISSUE 60 NOVEMBER
Linux Squid Proxy Server
 Linux Squid Proxy Server Descriptions and Purpose of Lab Exercise Squid is caching proxy server, which improves the bandwidth and the reponse time by caching the recently requested web pages. Now a days
Linux Squid Proxy Server Descriptions and Purpose of Lab Exercise Squid is caching proxy server, which improves the bandwidth and the reponse time by caching the recently requested web pages. Now a days
Setting up a Squid-Proxy Server
 LinuxFocus article number 235 http://linuxfocus.org Setting up a Squid-Proxy Server by D.S. Oberoi About the author: D.S. Oberoi lives in Jammu, India and has currently problems
LinuxFocus article number 235 http://linuxfocus.org Setting up a Squid-Proxy Server by D.S. Oberoi About the author: D.S. Oberoi lives in Jammu, India and has currently problems
1. What is this? Why would I want it?
 HOWTO - Jeanne, redirector for Squid Reverse Proxy Vincent Berk (c)2001 vberk@ists.dartmouth.edu GNU/GPL Marion Bates (c) 2001 mbates@ists.dartmouth.edu Installation Guide with Examples (ALPHA distribution)
HOWTO - Jeanne, redirector for Squid Reverse Proxy Vincent Berk (c)2001 vberk@ists.dartmouth.edu GNU/GPL Marion Bates (c) 2001 mbates@ists.dartmouth.edu Installation Guide with Examples (ALPHA distribution)
Reverse Web Hosting - A Quick Guide
 HOWTO v.2 - Jeanne, redirector for Squid Reverse Proxy Vincent Berk (c)2001 vberk@ists.dartmouth.edu GNU/GPL Marion Bates (c) 2003 mbates@ists.dartmouth.edu Installation Guide with Examples 1. What is
HOWTO v.2 - Jeanne, redirector for Squid Reverse Proxy Vincent Berk (c)2001 vberk@ists.dartmouth.edu GNU/GPL Marion Bates (c) 2003 mbates@ists.dartmouth.edu Installation Guide with Examples 1. What is
EZblue BusinessServer The All - In - One Server For Your Home And Business
 EZblue BusinessServer The All - In - One Server For Your Home And Business Quick Start Guide Version 3.8 1 2 3 EZblue Server Overview EZblue Server Installation EZblue Server Configuration 4 EZblue Magellan
EZblue BusinessServer The All - In - One Server For Your Home And Business Quick Start Guide Version 3.8 1 2 3 EZblue Server Overview EZblue Server Installation EZblue Server Configuration 4 EZblue Magellan
Implementing Reverse Proxy Using Squid. Prepared By Visolve Squid Team
 Implementing Reverse Proxy Using Squid Prepared By Visolve Squid Team Introduction What is Reverse Proxy Cache About Squid How Reverse Proxy Cache work Configuring Squid as Reverse Proxy Configuring Squid
Implementing Reverse Proxy Using Squid Prepared By Visolve Squid Team Introduction What is Reverse Proxy Cache About Squid How Reverse Proxy Cache work Configuring Squid as Reverse Proxy Configuring Squid
EZblue BusinessServer The All - In - One Server For Your Home And Business
 EZblue BusinessServer The All - In - One Server For Your Home And Business Quick Start Guide Version 3.11 1 2 3 EZblue Server Overview EZblue Server Installation EZblue Server Configuration 4 EZblue Magellan
EZblue BusinessServer The All - In - One Server For Your Home And Business Quick Start Guide Version 3.11 1 2 3 EZblue Server Overview EZblue Server Installation EZblue Server Configuration 4 EZblue Magellan
ZENworks 11 Support Pack 4 HTTP Proxy Reference. May 2016
 ZENworks 11 Support Pack 4 HTTP Proxy Reference May 2016 Legal Notices For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government rights,
ZENworks 11 Support Pack 4 HTTP Proxy Reference May 2016 Legal Notices For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government rights,
Web Security Deployment. Deployment Guide for Client Site Proxy and Remote Connect
 Web Security Deployment Deployment Guide for Client Site Proxy and Remote Connect Client Site Proxy and Remote Connect Deployment Guide Documentation version: 1.0 Legal Notice Legal Notice Copyright 2013
Web Security Deployment Deployment Guide for Client Site Proxy and Remote Connect Client Site Proxy and Remote Connect Deployment Guide Documentation version: 1.0 Legal Notice Legal Notice Copyright 2013
Proxy. Proxy. Computer Center, CS, NCTU. Proxy. A proxy server is a server which services the requests of its clients by: Goals: Server.
 Web A proxy server is a server which services the requests of its clients by: Making requests to other servers Caching some results for further same requests Goals: Performance Stability Central Control
Web A proxy server is a server which services the requests of its clients by: Making requests to other servers Caching some results for further same requests Goals: Performance Stability Central Control
Third Party Integration
 APPENDIXG This appendix contains the following sections: Overview, page G-1 BlackBerry Enterprise Server, page G-1 Blue Coat, page G-2 Check Point, page G-3 Firebox, page G-4 ISA Server/Forefront TMG,
APPENDIXG This appendix contains the following sections: Overview, page G-1 BlackBerry Enterprise Server, page G-1 Blue Coat, page G-2 Check Point, page G-3 Firebox, page G-4 ISA Server/Forefront TMG,
How To Use 1Bay 1Bay From Awn.Net On A Pc Or Mac Or Ipad (For Pc Or Ipa) With A Network Box (For Mac) With An Ipad Or Ipod (For Ipad) With The
 1-bay NAS User Guide INDEX Index... 1 Log in... 2 Basic - Quick Setup... 3 Wizard... 3 Add User... 6 Add Group... 7 Add Share... 9 Control Panel... 11 Control Panel - User and groups... 12 Group Management...
1-bay NAS User Guide INDEX Index... 1 Log in... 2 Basic - Quick Setup... 3 Wizard... 3 Add User... 6 Add Group... 7 Add Share... 9 Control Panel... 11 Control Panel - User and groups... 12 Group Management...
LOCKSS on LINUX. CentOS6 Installation Manual 08/22/2013
 LOCKSS on LINUX CentOS6 Installation Manual 08/22/2013 1 Table of Contents Overview... 3 LOCKSS Hardware... 5 Installation Checklist... 6 BIOS Settings... 9 Installation... 10 Firewall Configuration...
LOCKSS on LINUX CentOS6 Installation Manual 08/22/2013 1 Table of Contents Overview... 3 LOCKSS Hardware... 5 Installation Checklist... 6 BIOS Settings... 9 Installation... 10 Firewall Configuration...
Multi-Homing Dual WAN Firewall Router
 Multi-Homing Dual WAN Firewall Router Quick Installation Guide M73-APO09-400 Multi-Homing Dual WAN Firewall Router Overview The Multi-Homing Dual WAN Firewall Router provides three 10/100Mbit Ethernet
Multi-Homing Dual WAN Firewall Router Quick Installation Guide M73-APO09-400 Multi-Homing Dual WAN Firewall Router Overview The Multi-Homing Dual WAN Firewall Router provides three 10/100Mbit Ethernet
CMPT 471 Networking II
 CMPT 471 Networking II Firewalls Janice Regan, 2006-2013 1 Security When is a computer secure When the data and software on the computer are available on demand only to those people who should have access
CMPT 471 Networking II Firewalls Janice Regan, 2006-2013 1 Security When is a computer secure When the data and software on the computer are available on demand only to those people who should have access
Windows Client/Server Local Area Network (LAN) System Security Lab 2 Time allocation 3 hours
 Windows Client/Server Local Area Network (LAN) System Security Lab 2 Time allocation 3 hours Introduction The following lab allows the trainee to obtain a more in depth knowledge of network security and
Windows Client/Server Local Area Network (LAN) System Security Lab 2 Time allocation 3 hours Introduction The following lab allows the trainee to obtain a more in depth knowledge of network security and
LOCKSS on LINUX. Installation Manual and the OpenBSD Transition 02/17/2011
 LOCKSS on LINUX Installation Manual and the OpenBSD Transition 02/17/2011 1 Table of Contents Overview... 3 LOCKSS Hardware... 5 Installation Checklist... 7 BIOS Settings... 10 Installation... 11 Firewall
LOCKSS on LINUX Installation Manual and the OpenBSD Transition 02/17/2011 1 Table of Contents Overview... 3 LOCKSS Hardware... 5 Installation Checklist... 7 BIOS Settings... 10 Installation... 11 Firewall
Internet Content Distribution
 Internet Content Distribution Chapter 2: Server-Side Techniques (TUD Student Use Only) Chapter Outline Server-side techniques for content distribution Goals Mirrors Server farms Surrogates DNS load balancing
Internet Content Distribution Chapter 2: Server-Side Techniques (TUD Student Use Only) Chapter Outline Server-side techniques for content distribution Goals Mirrors Server farms Surrogates DNS load balancing
HOMEROOM SERVER INSTALLATION & NETWORK CONFIGURATION GUIDE
 HOMEROOM SERVER INSTALLATION & NETWORK CONFIGURATION GUIDE Level 1, 61 Davey St Hobart, TAS 7000 T (03) 6165 1555 www.getbusi.com Table of Contents ABOUT THIS MANUAL! 1 SYSTEM REQUIREMENTS! 2 Hardware
HOMEROOM SERVER INSTALLATION & NETWORK CONFIGURATION GUIDE Level 1, 61 Davey St Hobart, TAS 7000 T (03) 6165 1555 www.getbusi.com Table of Contents ABOUT THIS MANUAL! 1 SYSTEM REQUIREMENTS! 2 Hardware
Chapter 9 Monitoring System Performance
 Chapter 9 Monitoring System Performance This chapter describes the full set of system monitoring features of your ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN. You can be alerted to important
Chapter 9 Monitoring System Performance This chapter describes the full set of system monitoring features of your ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN. You can be alerted to important
Ultra Thin Client TC-401 TC-402. Users s Guide
 Ultra Thin Client TC-401 TC-402 Users s Guide CONTENT 1. OVERVIEW... 3 1.1 HARDWARE SPECIFICATION... 3 1.2 SOFTWARE OVERVIEW... 4 1.3 HARDWARE OVERVIEW...5 1.4 NETWORK CONNECTION... 7 2. INSTALLING THE
Ultra Thin Client TC-401 TC-402 Users s Guide CONTENT 1. OVERVIEW... 3 1.1 HARDWARE SPECIFICATION... 3 1.2 SOFTWARE OVERVIEW... 4 1.3 HARDWARE OVERVIEW...5 1.4 NETWORK CONNECTION... 7 2. INSTALLING THE
AdminToys Suite. Installation & Setup Guide
 AdminToys Suite Installation & Setup Guide Copyright 2008-2009 Lovelysoft. All Rights Reserved. Information in this document is subject to change without prior notice. Certain names of program products
AdminToys Suite Installation & Setup Guide Copyright 2008-2009 Lovelysoft. All Rights Reserved. Information in this document is subject to change without prior notice. Certain names of program products
SuperLumin Nemesis. Administration Guide. February 2011
 SuperLumin Nemesis Administration Guide February 2011 SuperLumin Nemesis Legal Notices Information contained in this document is believed to be accurate and reliable. However, SuperLumin assumes no responsibility
SuperLumin Nemesis Administration Guide February 2011 SuperLumin Nemesis Legal Notices Information contained in this document is believed to be accurate and reliable. However, SuperLumin assumes no responsibility
Firewall VPN Router. Quick Installation Guide M73-APO09-380
 Firewall VPN Router Quick Installation Guide M73-APO09-380 Firewall VPN Router Overview The Firewall VPN Router provides three 10/100Mbit Ethernet network interface ports which are the Internal/LAN, External/WAN,
Firewall VPN Router Quick Installation Guide M73-APO09-380 Firewall VPN Router Overview The Firewall VPN Router provides three 10/100Mbit Ethernet network interface ports which are the Internal/LAN, External/WAN,
Chapter 15: Advanced Networks
 Chapter 15: Advanced Networks IT Essentials: PC Hardware and Software v4.0 1 Determine a Network Topology A site survey is a physical inspection of the building that will help determine a basic logical
Chapter 15: Advanced Networks IT Essentials: PC Hardware and Software v4.0 1 Determine a Network Topology A site survey is a physical inspection of the building that will help determine a basic logical
McAfee Web Gateway 7.4.1
 Release Notes Revision B McAfee Web Gateway 7.4.1 Contents About this release New features and enhancements Resolved issues Installation instructions Known issues Find product documentation About this
Release Notes Revision B McAfee Web Gateway 7.4.1 Contents About this release New features and enhancements Resolved issues Installation instructions Known issues Find product documentation About this
Configuration Manual English version
 Configuration Manual English version Frama F-Link Configuration Manual (EN) All rights reserved. Frama Group. The right to make changes in this Installation Guide is reserved. Frama Ltd also reserves the
Configuration Manual English version Frama F-Link Configuration Manual (EN) All rights reserved. Frama Group. The right to make changes in this Installation Guide is reserved. Frama Ltd also reserves the
Chapter 8 Router and Network Management
 Chapter 8 Router and Network Management This chapter describes how to use the network management features of your ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN. These features can be found by
Chapter 8 Router and Network Management This chapter describes how to use the network management features of your ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN. These features can be found by
Network Agent Quick Start
 Network Agent Quick Start Topic 50500 Network Agent Quick Start Updated 17-Sep-2013 Applies To: Web Filter, Web Security, Web Security Gateway, and Web Security Gateway Anywhere, v7.7 and 7.8 Websense
Network Agent Quick Start Topic 50500 Network Agent Quick Start Updated 17-Sep-2013 Applies To: Web Filter, Web Security, Web Security Gateway, and Web Security Gateway Anywhere, v7.7 and 7.8 Websense
Quick Note 052. Connecting to Digi Remote Manager SM Through Web Proxy
 Quick Note 052 Connecting to Digi Remote Manager SM Through Web Proxy Digi Product Management August 2015 Contents 1 Document Version...2 2 Abstract...3 3 Introduction...3 4 Web Proxy Configuration...4
Quick Note 052 Connecting to Digi Remote Manager SM Through Web Proxy Digi Product Management August 2015 Contents 1 Document Version...2 2 Abstract...3 3 Introduction...3 4 Web Proxy Configuration...4
How to Configure edgebox as a Web Server
 intelligence at the edge of the network www.critical-links.com edgebox V4.5 Introduction: The Web Server panel allows the simple creation of multiple web sites using the Apache web server. Each website
intelligence at the edge of the network www.critical-links.com edgebox V4.5 Introduction: The Web Server panel allows the simple creation of multiple web sites using the Apache web server. Each website
Installing, Uninstalling, and Upgrading Service Monitor
 CHAPTER 2 Installing, Uninstalling, and Upgrading Service Monitor This section contains the following topics: Preparing to Install Service Monitor, page 2-1 Installing Cisco Unified Service Monitor, page
CHAPTER 2 Installing, Uninstalling, and Upgrading Service Monitor This section contains the following topics: Preparing to Install Service Monitor, page 2-1 Installing Cisco Unified Service Monitor, page
Websense Content Gateway v7.x: Troubleshooting
 Websense Content Gateway v7.x: Troubleshooting Topic 60042 Content Gateway Troubleshooting Updated: 28-October-2013 Dropped HTTPS connections Websites that have difficulty transiting Content Gateway Low
Websense Content Gateway v7.x: Troubleshooting Topic 60042 Content Gateway Troubleshooting Updated: 28-October-2013 Dropped HTTPS connections Websites that have difficulty transiting Content Gateway Low
CYAN SECURE WEB APPLIANCE. User interface manual
 CYAN SECURE WEB APPLIANCE User interface manual Jun. 13, 2008 Applies to: CYAN Secure Web 1.4 and above Contents 1 Log in...3 2 Status...3 2.1 Status / System...3 2.2 Status / Network...4 Status / Network
CYAN SECURE WEB APPLIANCE User interface manual Jun. 13, 2008 Applies to: CYAN Secure Web 1.4 and above Contents 1 Log in...3 2 Status...3 2.1 Status / System...3 2.2 Status / Network...4 Status / Network
RemotelyAnywhere Getting Started Guide
 April 2007 About RemotelyAnywhere... 2 About RemotelyAnywhere... 2 About this Guide... 2 Installation of RemotelyAnywhere... 2 Software Activation...3 Accessing RemotelyAnywhere... 4 About Dynamic IP Addresses...
April 2007 About RemotelyAnywhere... 2 About RemotelyAnywhere... 2 About this Guide... 2 Installation of RemotelyAnywhere... 2 Software Activation...3 Accessing RemotelyAnywhere... 4 About Dynamic IP Addresses...
Student Halls Network. Connection Guide
 Student Halls Network Connection Guide Contents: Page 3 Page 4 Page 6 Page 10 Page 17 Page 18 Page 19 Page 20 Introduction Network Connection Policy Connecting to the Student Halls Network Connecting to
Student Halls Network Connection Guide Contents: Page 3 Page 4 Page 6 Page 10 Page 17 Page 18 Page 19 Page 20 Introduction Network Connection Policy Connecting to the Student Halls Network Connecting to
CONNECTING TO DEPARTMENT OF COMPUTER SCIENCE SERVERS BOTH FROM ON AND OFF CAMPUS USING TUNNELING, PuTTY, AND VNC Client Utilities
 CONNECTING TO DEPARTMENT OF COMPUTER SCIENCE SERVERS BOTH FROM ON AND OFF CAMPUS USING TUNNELING, PuTTY, AND VNC Client Utilities DNS name: turing.cs.montclair.edu -This server is the Departmental Server
CONNECTING TO DEPARTMENT OF COMPUTER SCIENCE SERVERS BOTH FROM ON AND OFF CAMPUS USING TUNNELING, PuTTY, AND VNC Client Utilities DNS name: turing.cs.montclair.edu -This server is the Departmental Server
Load Balancing for esafe Gateway 3.0 when using Alteon s AD2 or AD3
 Load Balancing for esafe Gateway 3.0 when using Alteon s AD2 or AD3 page 3 Load Balancing for esafe Gateway 3.0 when using Alteon s AD2 or AD3 This document describes how to setup and configure Alteon
Load Balancing for esafe Gateway 3.0 when using Alteon s AD2 or AD3 page 3 Load Balancing for esafe Gateway 3.0 when using Alteon s AD2 or AD3 This document describes how to setup and configure Alteon
W3Perl A free logfile analyzer
 W3Perl A free logfile analyzer Features Works on Unix / Windows / Mac View last entries based on Perl scripts Web / FTP / Squid / Email servers Session tracking Others log format can be added easily Detailed
W3Perl A free logfile analyzer Features Works on Unix / Windows / Mac View last entries based on Perl scripts Web / FTP / Squid / Email servers Session tracking Others log format can be added easily Detailed
Barracuda Link Balancer
 Barracuda Networks Technical Documentation Barracuda Link Balancer Administrator s Guide Version 2.2 RECLAIM YOUR NETWORK Copyright Notice Copyright 2004-2011, Barracuda Networks www.barracuda.com v2.2-110503-01-0503
Barracuda Networks Technical Documentation Barracuda Link Balancer Administrator s Guide Version 2.2 RECLAIM YOUR NETWORK Copyright Notice Copyright 2004-2011, Barracuda Networks www.barracuda.com v2.2-110503-01-0503
Proctor Caching User Guide
 Proctor Caching User Guide Copyright 2014, Pearson Education, Inc. Published March 5, 2014 Proctor Caching User Guide 1 Proctor Caching User Guide Revision History What is Proctor Caching? Hardware and
Proctor Caching User Guide Copyright 2014, Pearson Education, Inc. Published March 5, 2014 Proctor Caching User Guide 1 Proctor Caching User Guide Revision History What is Proctor Caching? Hardware and
Barracuda Link Balancer Administrator s Guide
 Barracuda Link Balancer Administrator s Guide Version 1.0 Barracuda Networks Inc. 3175 S. Winchester Blvd. Campbell, CA 95008 http://www.barracuda.com Copyright Notice Copyright 2008, Barracuda Networks
Barracuda Link Balancer Administrator s Guide Version 1.0 Barracuda Networks Inc. 3175 S. Winchester Blvd. Campbell, CA 95008 http://www.barracuda.com Copyright Notice Copyright 2008, Barracuda Networks
Perimeter Firewalls. Brandon Napier Rick Archibald Pete Jamison HAL PC & HLUG 09/22/2007. brought to you by: in association with
 Perimeter Firewalls 09/22/2007 brought to you by: Brandon Napier Rick Archibald Pete Jamison in association with HAL PC & HLUG Who am I? Brandon Napier Got interested in computers in 1992, in high school
Perimeter Firewalls 09/22/2007 brought to you by: Brandon Napier Rick Archibald Pete Jamison in association with HAL PC & HLUG Who am I? Brandon Napier Got interested in computers in 1992, in high school
WebSpy Vantage Ultimate 2.2 Web Module Administrators Guide
 WebSpy Vantage Ultimate 2.2 Web Module Administrators Guide This document is intended to help you get started using WebSpy Vantage Ultimate and the Web Module. For more detailed information, please see
WebSpy Vantage Ultimate 2.2 Web Module Administrators Guide This document is intended to help you get started using WebSpy Vantage Ultimate and the Web Module. For more detailed information, please see
Proxy Servers. Building and Deploying System Improvement and Protection. Elvin Smith & Jose Robles
 Proxy Servers Building and Deploying System Improvement and Protection Elvin Smith & Jose Robles IT 4444 Capstone Spring 2013 Outline Topic: Proxy Server 1. Introduction a. Technical definition of a proxy
Proxy Servers Building and Deploying System Improvement and Protection Elvin Smith & Jose Robles IT 4444 Capstone Spring 2013 Outline Topic: Proxy Server 1. Introduction a. Technical definition of a proxy
Troubleshooting / FAQ
 Troubleshooting / FAQ Routers / Firewalls I can't connect to my server from outside of my internal network. The server's IP is 10.0.1.23, but I can't use that IP from a friend's computer. How do I get
Troubleshooting / FAQ Routers / Firewalls I can't connect to my server from outside of my internal network. The server's IP is 10.0.1.23, but I can't use that IP from a friend's computer. How do I get
Smart Connect. Deployment Guide
 Smart Connect Deployment Guide Smart Connect Deployment Guide Documentation version: 1.0 Legal Notice Legal Notice Copyright 2013 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo,
Smart Connect Deployment Guide Smart Connect Deployment Guide Documentation version: 1.0 Legal Notice Legal Notice Copyright 2013 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo,
MN-700 Base Station Configuration Guide
 MN-700 Base Station Configuration Guide Contents pen the Base Station Management Tool...3 Log ff the Base Station Management Tool...3 Navigate the Base Station Management Tool...4 Current Base Station
MN-700 Base Station Configuration Guide Contents pen the Base Station Management Tool...3 Log ff the Base Station Management Tool...3 Navigate the Base Station Management Tool...4 Current Base Station
Core Protection for Virtual Machines 1
 Core Protection for Virtual Machines 1 Comprehensive Threat Protection for Virtual Environments. Installation Guide e Endpoint Security Trend Micro Incorporated reserves the right to make changes to this
Core Protection for Virtual Machines 1 Comprehensive Threat Protection for Virtual Environments. Installation Guide e Endpoint Security Trend Micro Incorporated reserves the right to make changes to this
FileMaker Server 7. Administrator s Guide. For Windows and Mac OS
 FileMaker Server 7 Administrator s Guide For Windows and Mac OS 1994-2004, FileMaker, Inc. All Rights Reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker is a trademark
FileMaker Server 7 Administrator s Guide For Windows and Mac OS 1994-2004, FileMaker, Inc. All Rights Reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker is a trademark
Creating client-server setup with multiple clients
 Creating client-server setup with multiple clients Coffalyser.Net uses a SQL client server database model to store all project/experiment- related data. The client-server model has one main application
Creating client-server setup with multiple clients Coffalyser.Net uses a SQL client server database model to store all project/experiment- related data. The client-server model has one main application
FortKnox Personal Firewall
 FortKnox Personal Firewall User Manual Document version 1.4 EN ( 15. 9. 2009 ) Copyright (c) 2007-2009 NETGATE Technologies s.r.o. All rights reserved. This product uses compression library zlib Copyright
FortKnox Personal Firewall User Manual Document version 1.4 EN ( 15. 9. 2009 ) Copyright (c) 2007-2009 NETGATE Technologies s.r.o. All rights reserved. This product uses compression library zlib Copyright
NetIQ Sentinel 7.0.1 Quick Start Guide
 NetIQ Sentinel 7.0.1 Quick Start Guide April 2012 Getting Started Use the following information to get Sentinel installed and running quickly. Meeting System Requirements on page 1 Installing Sentinel
NetIQ Sentinel 7.0.1 Quick Start Guide April 2012 Getting Started Use the following information to get Sentinel installed and running quickly. Meeting System Requirements on page 1 Installing Sentinel
Network Probe User Guide
 Network Probe User Guide Network Probe User Guide Table of Contents 1. Introduction...1 2. Installation...2 Windows installation...2 Linux installation...3 Mac installation...4 License key...5 Deployment...5
Network Probe User Guide Network Probe User Guide Table of Contents 1. Introduction...1 2. Installation...2 Windows installation...2 Linux installation...3 Mac installation...4 License key...5 Deployment...5
v.5.5.2 Installation Guide for Websense Enterprise v.5.5.2 Embedded on Cisco Content Engine with ACNS v.5.4
 v.5.5.2 Installation Guide for Websense Enterprise v.5.5.2 Embedded on Cisco Content Engine with ACNS v.5.4 Websense Enterprise Installation Guide 1996 2004, Websense, Inc. All rights reserved. 10240 Sorrento
v.5.5.2 Installation Guide for Websense Enterprise v.5.5.2 Embedded on Cisco Content Engine with ACNS v.5.4 Websense Enterprise Installation Guide 1996 2004, Websense, Inc. All rights reserved. 10240 Sorrento
PFSENSE Load Balance with Fail Over From Version Beta3
 PFSENSE Load Balance with Fail Over From Version Beta3 Following are the Installation instructions of PFSense beginning at first Login to setup Load Balance and Fail over procedures for outbound Internet
PFSENSE Load Balance with Fail Over From Version Beta3 Following are the Installation instructions of PFSense beginning at first Login to setup Load Balance and Fail over procedures for outbound Internet
VMware vcenter Support Assistant 5.1.1
 VMware vcenter.ga September 25, 2013 GA Last updated: September 24, 2013 Check for additions and updates to these release notes. RELEASE NOTES What s in the Release Notes The release notes cover the following
VMware vcenter.ga September 25, 2013 GA Last updated: September 24, 2013 Check for additions and updates to these release notes. RELEASE NOTES What s in the Release Notes The release notes cover the following
GoToMyPC Corporate Advanced Firewall Support Features
 F A C T S H E E T GoToMyPC Corporate Advanced Firewall Support Features Citrix GoToMyPC Corporate features Citrix Online s advanced connectivity technology. We support all of the common firewall and proxy
F A C T S H E E T GoToMyPC Corporate Advanced Firewall Support Features Citrix GoToMyPC Corporate features Citrix Online s advanced connectivity technology. We support all of the common firewall and proxy
Avira Update Manager User Manual
 Avira Update Manager User Manual Table of contents Table of contents 1. Product information........................................... 4 1.1 Functionality................................................................
Avira Update Manager User Manual Table of contents Table of contents 1. Product information........................................... 4 1.1 Functionality................................................................
Getting Started with PRTG Network Monitor 2012 Paessler AG
 Getting Started with PRTG Network Monitor 2012 Paessler AG All rights reserved. No parts of this work may be reproduced in any form or by any means graphic, electronic, or mechanical, including photocopying,
Getting Started with PRTG Network Monitor 2012 Paessler AG All rights reserved. No parts of this work may be reproduced in any form or by any means graphic, electronic, or mechanical, including photocopying,
F-Secure Internet Gatekeeper
 F-Secure Internet Gatekeeper TOC F-Secure Internet Gatekeeper Contents Chapter 1: Welcome to F-Secure Internet Gatekeeper...5 1.1 Features...6 Chapter 2: Deployment...8 2.1 System requirements...9 2.2
F-Secure Internet Gatekeeper TOC F-Secure Internet Gatekeeper Contents Chapter 1: Welcome to F-Secure Internet Gatekeeper...5 1.1 Features...6 Chapter 2: Deployment...8 2.1 System requirements...9 2.2
DigiDelivery Client Quick Start
 DigiDelivery Client Quick Start Installing the DigiDelivery Client To download and install the DigiDelivery client software: 1 Launch your Web browser and navigate to www.digidesign.com/digidelivery/clients.
DigiDelivery Client Quick Start Installing the DigiDelivery Client To download and install the DigiDelivery client software: 1 Launch your Web browser and navigate to www.digidesign.com/digidelivery/clients.
Chapter 6 Virtual Private Networking Using SSL Connections
 Chapter 6 Virtual Private Networking Using SSL Connections The FVS336G ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN provides a hardwarebased SSL VPN solution designed specifically to provide
Chapter 6 Virtual Private Networking Using SSL Connections The FVS336G ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN provides a hardwarebased SSL VPN solution designed specifically to provide
Security Correlation Server Quick Installation Guide
 orrelogtm Security Correlation Server Quick Installation Guide This guide provides brief information on how to install the CorreLog Server system on a Microsoft Windows platform. This information can also
orrelogtm Security Correlation Server Quick Installation Guide This guide provides brief information on how to install the CorreLog Server system on a Microsoft Windows platform. This information can also
User Guide. Version 3.2. Copyright 2002-2009 Snow Software AB. All rights reserved.
 Version 3.2 User Guide Copyright 2002-2009 Snow Software AB. All rights reserved. This manual and computer program is protected by copyright law and international treaties. Unauthorized reproduction or
Version 3.2 User Guide Copyright 2002-2009 Snow Software AB. All rights reserved. This manual and computer program is protected by copyright law and international treaties. Unauthorized reproduction or
NEFSIS DEDICATED SERVER
 NEFSIS TRAINING SERIES Nefsis Dedicated Server version 5.2.0.XXX (DRAFT Document) Requirements and Implementation Guide (Rev5-113009) REQUIREMENTS AND INSTALLATION OF THE NEFSIS DEDICATED SERVER Nefsis
NEFSIS TRAINING SERIES Nefsis Dedicated Server version 5.2.0.XXX (DRAFT Document) Requirements and Implementation Guide (Rev5-113009) REQUIREMENTS AND INSTALLATION OF THE NEFSIS DEDICATED SERVER Nefsis
Getting Started. Symantec Client Security. About Symantec Client Security. How to get started
 Getting Started Symantec Client Security About Security Security provides scalable, cross-platform firewall, intrusion prevention, and antivirus protection for workstations and antivirus protection for
Getting Started Symantec Client Security About Security Security provides scalable, cross-platform firewall, intrusion prevention, and antivirus protection for workstations and antivirus protection for
N-CAP Users Guide Everything You Need to Know About Using the Internet! How Firewalls Work
 N-CAP Users Guide Everything You Need to Know About Using the Internet! How Firewalls Work How Firewalls Work By: Jeff Tyson If you have been using the internet for any length of time, and especially if
N-CAP Users Guide Everything You Need to Know About Using the Internet! How Firewalls Work How Firewalls Work By: Jeff Tyson If you have been using the internet for any length of time, and especially if
FTP Service Reference
 IceWarp Server FTP Service Reference Version 10 Printed on 12 August, 2009 i Contents FTP Service 1 V10 New Features... 2 FTP Access Mode... 2 FTP Synchronization... 2 FTP Service Node... 3 FTP Service
IceWarp Server FTP Service Reference Version 10 Printed on 12 August, 2009 i Contents FTP Service 1 V10 New Features... 2 FTP Access Mode... 2 FTP Synchronization... 2 FTP Service Node... 3 FTP Service
Chapter 7. Firewalls http://www.redhat.com/docs/manuals/enterprise/rhel-4-manual/security-guide/ch-fw.html
 Red Hat Docs > Manuals > Red Hat Enterprise Linux Manuals > Red Hat Enterprise Linux 4: Security Guide Chapter 7. Firewalls http://www.redhat.com/docs/manuals/enterprise/rhel-4-manual/security-guide/ch-fw.html
Red Hat Docs > Manuals > Red Hat Enterprise Linux Manuals > Red Hat Enterprise Linux 4: Security Guide Chapter 7. Firewalls http://www.redhat.com/docs/manuals/enterprise/rhel-4-manual/security-guide/ch-fw.html
Konica Minolta s Optimised Print Services (OPS)
 Konica Minolta s Optimised Print Services (OPS) Document Collection Agent (DCA) Detailed Installation Guide V1.6 Page 1 of 43 Table of Contents Notes... 4 Requirements... 5 Network requirements... 5 System
Konica Minolta s Optimised Print Services (OPS) Document Collection Agent (DCA) Detailed Installation Guide V1.6 Page 1 of 43 Table of Contents Notes... 4 Requirements... 5 Network requirements... 5 System
Step-by-Step Configuration
 Step-by-Step Configuration Kerio Technologies C 2001-2003 Kerio Technologies. All Rights Reserved. Printing Date: December 17, 2003 This guide provides detailed description on configuration of the local
Step-by-Step Configuration Kerio Technologies C 2001-2003 Kerio Technologies. All Rights Reserved. Printing Date: December 17, 2003 This guide provides detailed description on configuration of the local
Remote Console Installation & Setup Guide. November 2009
 Remote Console Installation & Setup Guide November 2009 Legal Information All rights reserved. No part of this document shall be reproduced or transmitted by any means or otherwise, without written permission
Remote Console Installation & Setup Guide November 2009 Legal Information All rights reserved. No part of this document shall be reproduced or transmitted by any means or otherwise, without written permission
This document is intended to make you familiar with the ServersCheck Monitoring Appliance
 ServersCheck Monitoring Appliance Quick Overview This document is intended to make you familiar with the ServersCheck Monitoring Appliance Although it is possible, we highly recommend not to install other
ServersCheck Monitoring Appliance Quick Overview This document is intended to make you familiar with the ServersCheck Monitoring Appliance Although it is possible, we highly recommend not to install other
Installing and Configuring Websense Content Gateway
 Installing and Configuring Websense Content Gateway Websense Support Webinar - September 2009 web security data security email security Support Webinars 2009 Websense, Inc. All rights reserved. Webinar
Installing and Configuring Websense Content Gateway Websense Support Webinar - September 2009 web security data security email security Support Webinars 2009 Websense, Inc. All rights reserved. Webinar
Savvius Insight Initial Configuration
 The configuration utility on Savvius Insight lets you configure device, network, and time settings. Additionally, if you are forwarding your data from Savvius Insight to a Splunk server, You can configure
The configuration utility on Savvius Insight lets you configure device, network, and time settings. Additionally, if you are forwarding your data from Savvius Insight to a Splunk server, You can configure
Amahi Instruction Manual
 History of Amahi Chapter 1 Installing fedora 12 and Amahi Home Digital Assistant (HDA) Chapter 2 Your DHCP/DNS options Chapter 3 Network Troubleshooting Chapter 4 Getting Started Appendix: Advanced Hard
History of Amahi Chapter 1 Installing fedora 12 and Amahi Home Digital Assistant (HDA) Chapter 2 Your DHCP/DNS options Chapter 3 Network Troubleshooting Chapter 4 Getting Started Appendix: Advanced Hard
PasserellesNumeriquesCambodia (PNC)
 PasserellesNumeriquesCambodia (PNC) Table of Contents I. Configure DHCP Relay... 3 1. Use client to testing with connection... 4 II. IPTABLES On SUSE... 5 1. Variable and allow client ping... 5 2. Allow
PasserellesNumeriquesCambodia (PNC) Table of Contents I. Configure DHCP Relay... 3 1. Use client to testing with connection... 4 II. IPTABLES On SUSE... 5 1. Variable and allow client ping... 5 2. Allow
Lab 8.4.2 Configuring Access Policies and DMZ Settings
 Lab 8.4.2 Configuring Access Policies and DMZ Settings Objectives Log in to a multi-function device and view security settings. Set up Internet access policies based on IP address and application. Set
Lab 8.4.2 Configuring Access Policies and DMZ Settings Objectives Log in to a multi-function device and view security settings. Set up Internet access policies based on IP address and application. Set
National Fire Incident Reporting System (NFIRS 5.0) Configuration Tool User's Guide
 National Fire Incident Reporting System (NFIRS 5.0) Configuration Tool User's Guide NFIRS 5.0 Software Version 5.6 1/7/2009 Department of Homeland Security Federal Emergency Management Agency United States
National Fire Incident Reporting System (NFIRS 5.0) Configuration Tool User's Guide NFIRS 5.0 Software Version 5.6 1/7/2009 Department of Homeland Security Federal Emergency Management Agency United States
Step-by-Step Configuration
 Step-by-Step Configuration Kerio Technologies Kerio Technologies. All Rights Reserved. Printing Date: August 15, 2007 This guide provides detailed description on configuration of the local network which
Step-by-Step Configuration Kerio Technologies Kerio Technologies. All Rights Reserved. Printing Date: August 15, 2007 This guide provides detailed description on configuration of the local network which
Reference and Troubleshooting: FTP, IIS, and Firewall Information
 APPENDIXC Reference and Troubleshooting: FTP, IIS, and Firewall Information Although Cisco VXC Manager automatically installs and configures everything you need for use with respect to FTP, IIS, and the
APPENDIXC Reference and Troubleshooting: FTP, IIS, and Firewall Information Although Cisco VXC Manager automatically installs and configures everything you need for use with respect to FTP, IIS, and the
Lesson 7 - Website Administration
 Lesson 7 - Website Administration If you are hired as a web designer, your client will most likely expect you do more than just create their website. They will expect you to also know how to get their
Lesson 7 - Website Administration If you are hired as a web designer, your client will most likely expect you do more than just create their website. They will expect you to also know how to get their
Introduction to Network Security Lab 1 - Wireshark
 Introduction to Network Security Lab 1 - Wireshark Bridges To Computing 1 Introduction: In our last lecture we discussed the Internet the World Wide Web and the Protocols that are used to facilitate communication
Introduction to Network Security Lab 1 - Wireshark Bridges To Computing 1 Introduction: In our last lecture we discussed the Internet the World Wide Web and the Protocols that are used to facilitate communication
The PostBase Connectivity Wizard
 The PostBase Connectivity Wizard The PostBase Connectivity Wizard allows you to easily set up your PostBase postage machine to suit your organization s arrangements. This document will guide you through
The PostBase Connectivity Wizard The PostBase Connectivity Wizard allows you to easily set up your PostBase postage machine to suit your organization s arrangements. This document will guide you through
Basic computer security
 Mag. iur. Dr. techn. Michael Sonntag Basic computer security E-Mail: sonntag@fim.uni-linz.ac.at http://www.fim.uni-linz.ac.at/staff/sonntag.htm Institute for Information Processing and Microprocessor Technology
Mag. iur. Dr. techn. Michael Sonntag Basic computer security E-Mail: sonntag@fim.uni-linz.ac.at http://www.fim.uni-linz.ac.at/staff/sonntag.htm Institute for Information Processing and Microprocessor Technology
Getting Started Guide. Getting Started With Your Dedicated Server. Setting up and hosting a domain on your Linux Dedicated Server using Plesk 8.0.
 Getting Started Guide Getting Started With Your Dedicated Server Setting up and hosting a domain on your Linux Dedicated Server using Plesk 8.0. Getting Started with Your Dedicated Server Plesk 8.0 Version
Getting Started Guide Getting Started With Your Dedicated Server Setting up and hosting a domain on your Linux Dedicated Server using Plesk 8.0. Getting Started with Your Dedicated Server Plesk 8.0 Version
Online Backup Client User Manual
 Online Backup Client User Manual Software version 3.21 For Linux distributions January 2011 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have
Online Backup Client User Manual Software version 3.21 For Linux distributions January 2011 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have
 1 I have forgotten the administrator username and/or password. To reset the administrator username and password, Press and hold down the RESET BUTTON for 5 seconds. Release the power button and the username
1 I have forgotten the administrator username and/or password. To reset the administrator username and password, Press and hold down the RESET BUTTON for 5 seconds. Release the power button and the username
7 6.2 Windows Vista / Windows 7. 10 8.2 IP Address Syntax. 12 9.2 Mobile Port. 13 10.2 Windows Vista / Windows 7. 17 13.2 Apply Rules To Your Device
 TABLE OF CONTENTS ADDRESS CHECKLIST 3 INTRODUCTION 4 WHAT IS PORT FORWARDING? 4 PROCEDURE OVERVIEW 5 PHYSICAL CONNECTION 6 FIND YOUR ROUTER S LOCAL NETWORK IP ADDRESS 7 6.1 Windows XP 7 6.2 Windows Vista
TABLE OF CONTENTS ADDRESS CHECKLIST 3 INTRODUCTION 4 WHAT IS PORT FORWARDING? 4 PROCEDURE OVERVIEW 5 PHYSICAL CONNECTION 6 FIND YOUR ROUTER S LOCAL NETWORK IP ADDRESS 7 6.1 Windows XP 7 6.2 Windows Vista
Getting started. Symantec AntiVirus Corporate Edition. About Symantec AntiVirus. How to get started
 Getting started Corporate Edition Copyright 2005 Corporation. All rights reserved. Printed in the U.S.A. 03/05 PN: 10362873 and the logo are U.S. registered trademarks of Corporation. is a trademark of
Getting started Corporate Edition Copyright 2005 Corporation. All rights reserved. Printed in the U.S.A. 03/05 PN: 10362873 and the logo are U.S. registered trademarks of Corporation. is a trademark of
Chapter 8: Installing Linux The Complete Guide To Linux System Administration Modified by M. L. Malone, 11/05
 Chapter 8: Installing Linux The Complete Guide To Linux System Administration Modified by M. L. Malone, 11/05 At the end of this chapter the successful student will be able to Describe the main hardware
Chapter 8: Installing Linux The Complete Guide To Linux System Administration Modified by M. L. Malone, 11/05 At the end of this chapter the successful student will be able to Describe the main hardware
StruxureWare Data Center Expert 7.2.4 Release Notes
 StruxureWare Data Center Expert 7.2.4 Release Notes Table of Contents Page # Part Numbers Affected...... 1 Minimum System Requirements... 1 New Features........ 1 Issues Fixed....3 Known Issues...3 Upgrade
StruxureWare Data Center Expert 7.2.4 Release Notes Table of Contents Page # Part Numbers Affected...... 1 Minimum System Requirements... 1 New Features........ 1 Issues Fixed....3 Known Issues...3 Upgrade
Proxy Server, Network Address Translator, Firewall. Proxy Server
 Proxy Server, Network Address Translator, Firewall 1 Proxy Server 2 1 Introduction What is a proxy server? Acts on behalf of other clients, and presents requests from other clients to a server. Acts as
Proxy Server, Network Address Translator, Firewall 1 Proxy Server 2 1 Introduction What is a proxy server? Acts on behalf of other clients, and presents requests from other clients to a server. Acts as
Installation Guide. Wyse Device Manager Release 4.8.5. Issue: 042511 PN: 883886-01 Rev. L
 Installation Guide Wyse Device Manager Release 4.8.5 Issue: 042511 PN: 883886-01 Rev. L Copyright Notices 2011, Wyse Technology Inc. All rights reserved. This manual and the software and firmware described
Installation Guide Wyse Device Manager Release 4.8.5 Issue: 042511 PN: 883886-01 Rev. L Copyright Notices 2011, Wyse Technology Inc. All rights reserved. This manual and the software and firmware described
Contents. Preparation/SetUp...2
 LAN Control Utility User Manual (for MH850U) Contents Preparation/SetUp... Preparation before using the network function... Connection...3 Installation...3 Setting the IP address of the projector...5 When
LAN Control Utility User Manual (for MH850U) Contents Preparation/SetUp... Preparation before using the network function... Connection...3 Installation...3 Setting the IP address of the projector...5 When
Hillstone StoneOS User Manual Hillstone Unified Intelligence Firewall Installation Manual
 Hillstone StoneOS User Manual Hillstone Unified Intelligence Firewall Installation Manual www.hillstonenet.com Preface Conventions Content This document follows the conventions below: CLI Tip: provides
Hillstone StoneOS User Manual Hillstone Unified Intelligence Firewall Installation Manual www.hillstonenet.com Preface Conventions Content This document follows the conventions below: CLI Tip: provides
User Guide. Cloud Gateway Software Device
 User Guide Cloud Gateway Software Device This document is designed to provide information about the first time configuration and administrator use of the Cloud Gateway (web filtering device software).
User Guide Cloud Gateway Software Device This document is designed to provide information about the first time configuration and administrator use of the Cloud Gateway (web filtering device software).
