Delphi-Windows Digital Signature Library Interface
|
|
|
- Aileen Stevenson
- 8 years ago
- Views:
Transcription
1 Delphi-Windows Digital Signature Library Interface Joseph Snyder SW Process Engineer Purpose The purpose of these three files is to provide the interface between Delphi executables and the built-in Windows security functions. The push to supplement the traditional sign-on with the usage of a Personal Identity Verification (PIV) card is rapidly gaining momentum. One major focus of using these PIV cards is to further secure the prescribing of controlled substances. There are already existing versions of these interface files which are available to the public. One version was released in the version 29 FOIA copy of the Computerized Patient Record System (CPRS) for the VistA EHR. However, it was determined that the license for those files, which was the Mozilla Public License, was incompatible with the license that the OSEHRA VistA uses for its repository. These files are released with the Apache 2.0 license to match the license for the OSEHRA VistA repository. The files contained here are written by blanking the three necessary files and filling in the function calls based upon what was missing during compilation time and testing. Code Walkthrough The interface consists of three separate files: XlfMime.pas Wcrypt2.pas WinSCard.pas Each file contains different functions corresponding to a different focus around acquiring and verifying the security certificate of the card holder. WinSCard.pas WinSCard.pas contains the constant values and function signatures necessary to connect to a Smart Card reader. Once a connection has been established to a local Smart Card reader, it is able to access the information about the certificate contained on a supplied card. These functions are all found in the Winscard.dll library. Wcrypt2.pas Once the user s certificate has been accessed from the PIV or Smart Card, the next step is to verify that the certificate is valid and corresponds to a trusted user. The functions found in Wcrypt2.pas are to be used to open a certificate store and perform various checks to verify that the user has the
2 correct identity and permissions. The functions in this file are called from one of two Windows DLLs: crypt32.dll or Advapi32.dll. XlfMime.pas The functions found in the XlfMime.pas file are used to encode information for transmission between two sites. This library encodes and decodes the information using a Base64/MIME encryption. The Delphi environment has a built-in library to accomplish this, named EncdDecd, to encode both strings and arbitrary streams of data External Interfaces/Dependencies The files in this submission were originally released with the CPRS code that corresponded to version 29 of the software. CPRSv29 corresponds to the OR*30*306 patch for the Order Entry Results Reporting package. If these files are placed into the source tree of an earlier version of CPRS, they should not have an effect on the compilation. To fully utilize the files, it is recommended that they be used to compile CPRSv29 or later. The files were rewritten by building the CPRS v29 code in the Delphi 2007 compiler. It was also tested with a different program using the Delphi XE3 compiler. Both of these compilation environments were run on Windows 7 SP 1 machines. These two compilers both showed no issue in compiling the submitted files. It is recommended that a Delphi compiler which is Delphi 2007 or more recent is used to compile the files. The testing code was verified using the NIST Test Personal Identity Verification (PIV) card set. More information about the NIST testing cards can be found here: As mentioned above, the development and testing was done on two Windows 7 Service Pack 1 computers. Of the three Windows DLLs that are used, none are specific to Windows 7. Therefore, there should be no dependence on the version of Windows environment necessary to build with these files. The versions used in development and testing are: crypt32.dll o Advapi32.dll o Winscard.dll o The values were found with by utilizing the sigcheck tool and entering the path to the C:\Windows\System32 version of each file.
3 Installation These files were created to replace files from the FOIA release of the CPRS executable, so there is already a designed path to include these files. Please be aware that these variables and options will only be shown on a system with the proper Delphi environment. To use these files with the OSEHRA VistA repository to build the CPRS executable, one would only need to set the BUILD_DELPHI_XuDigSig_DIR variable in the CMake GUI to the path to a directory with these files. An example is found in the image below: This information would then be propagated to the Delphi project file upon running the CMake configure and generate steps. These files are obviously not limited to just the CPRS application. To install the files into any other Delphi project, one would follow the standard method of including the files via the uses directive. The files should be placed into a directory and added to a uses subheading in the Delphi project file (*.dpr). Again, a small code snippet example follows: Uses ShareMem, Forms, WinHelpViewer, ORSystem, Wcrypt2 in 'C:/Users/joe.snyder/Work/OSEHRA/CPRSv29- XUDigSig\Wcrypt2.pas', WinSCard in 'C:/Users/joe.snyder/Work/OSEHRA/CPRSv29- XUDigSig\WinSCard.pas', XlfMime in 'C:/Users/joe.snyder/Work/OSEHRA/CPRSv29- XUDigSig\XlfMime.pas', <snip> How to Test There are DUnit tests written for the three files which included in this download: UTXlfMime.pas UTWcrypt2.pas UTWinSCard.pas
4 Note about testing: One of the Wcrypt2 tests has multiple pass conditions based upon the return of the function being tested. The TestCertVerifyRevocation function has two passing conditions: the CertVerifyRevocation function returns true and has no error expressed The CertVerifyRevocation function returns false and the dwerror value is set to This corresponds to a CRYPT_E_REVOCATION_OFFLINE error as expected. If the dwerror value is any other value, the test will fail. Due to the absence of a revocation server in the testing environment, there is no dashboard result with the test returning true with no errors. Integration of Testing OSEHRA VistA Repository These files, much like the source files, have a place in the OSEHRA VistA repository. To test the files with the CPRS build process, place the files into the Packages\Order Entry Results Reporting\CPRS\Testing\Tests directory. Then, you would add an entry for each file under the uses header to the CPRSTesting.dpr.in: uses UTXlfMime in '@SOURCE@\Tests\UTXlfMime.pas' {UTXuDsigS}, UTWcrypt2 in '@SOURCE@\Tests\UTWcrypt2.pas' {UTXuDsigS}, UTWinSCard in '@SOURCE@\Tests\UTWinSCard.pas'{UTXuDsigS}; After running a Configure, Generate, and make, you can execute all of the tests at once by running the executable or by using the CTest program. Running ctest n will show the available tests: C:\Users\joe.snyder\Work\OSEHRA\VistA-delphi-dev>ctest -N Test project C:/Users/joe.snyder/Work/OSEHRA/VistA-delphi-dev Test #1: DUnitUTSignonCnf Test #2: DUnitUTWcrypt2 Test #3: DUnitUTWinSCard Test #4: DUnitUTXlfMime Total Tests: 4 Then, the tests can be run together by executing ctest or individually with a command like ctest R Wcrypt2. The tests run will be determined by matching the test names against the string after the -R. Upon running the tests, all of the tests should pass. The output printed to the screen should look like this: C:\Users\joe.snyder\Work\OSEHRA\VistA-delphi-dev>ctest Test project C:/Users/joe.snyder/Work/OSEHRA/VistA-delphi-dev Start 1: DUnitUTSignonCnf 1/4 Test #1: DUnitUTSignonCnf... Passed 0.05 sec Start 2: DUnitUTWcrypt2 2/4 Test #2: DUnitUTWcrypt2... Passed sec Start 3: DUnitUTWinSCard 3/4 Test #3: DUnitUTWinSCard... Passed 0.20 sec Start 4: DUnitUTXlfMime 4/4 Test #4: DUnitUTXlfMime... Passed 0.05 sec
5 100% tests passed, 0 tests failed out of 4 Total Test time (real) = sec Be aware that running the tests will ask for a smart card to be inserted and accessed. An earlier attempt of the integration of the testing code can be found in the OSEHRA Gerrit instance: External project For testing with DUnit without using the OSEHRA VistA repository, the files can be included into any existing DUnit testing setup. If one does not exist, the OSEHRA version is a good example to see how to generate a separate testing executable to run. The Delphi project directory which generates the OSEHRA testing can be found in the Packages/Order Entry Results Reporting/CPRS/Testing directory. Coverage Calculations The testing of the code reports that 95% of the executable code is covered by the three test files. The coverage was calculated using the Delphi Code Coverage tool with the OSEHRA VistA testing setup. The coverage is calculated over the testing executable that is generated instead of the CPRS executable. The command used to generate the necessary HTML files for CTest to parse is: VistA-delphi-dev$ ~/Downloads/CodeCoverage_win32_1.0_RC9/CodeCoverage.exe -e ~/Work/OSEHRA/VistA-delphi-dev/CPRS/Testing/Bin/Debug/CPRSTesting.exe -html -u XlfMime WinSCard Wcrypt2 -sp ~/Work/OSEHRA/CPRSv29-XUDigSig/ An explanation of the flags for the function is below: -e o Path to the executable to run -html o Output the results of the coverage as HTML files -u o Names of the units to calculate coverage for -sp o Directory where the source for the targeted units can be found The generated HTML will report 100% coverage due to the fact that it can calculate which lines where hit, but not the total of executable lines. To demonstrate the correct calculation, run the Coverage capability of a CMake whose version is later than in the same directory that contains the output HTML of the previous step. An example run follows: VistA-delphi-dev$ ~/Work/cmake-build/bin/Debug/ctest.exe -M Experimental -T Coverage Site: TUCHANKA Build name: Win32- Performing coverage
6 Accumulating results (each. represents one file):... Covered LOC: 84 Not covered LOC: 4 Total LOC: 88 Percentage Coverage: 95.45% Future Work The future of these three files does have a clear path for additional development. The files do not contain the signatures for every possible Windows function. As a new functionality is developed for these Delphi libraries, calls to other Windows functions will become necessary. These functions and any necessary data structures will be included as needed.
Installation and Deployment
 Installation and Deployment Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc. Installation and Deployment SmarterStats
Installation and Deployment Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc. Installation and Deployment SmarterStats
Yubico PIV Management Tools
 Yubico PIV Management Tools Active Directory Smart Card Logon using the YubiKey NEO or NEO-n Document Version 1.0 April 15, 2015 Yubico PIV Management Tools 2015 Yubico. All rights reserved. Page 1 of
Yubico PIV Management Tools Active Directory Smart Card Logon using the YubiKey NEO or NEO-n Document Version 1.0 April 15, 2015 Yubico PIV Management Tools 2015 Yubico. All rights reserved. Page 1 of
EventTracker: Configuring DLA Extension for AWStats Report AWStats Reports
 EventTracker: Configuring DLA Extension for AWStats Report AWStats Reports Publication Date: Oct 18, 2011 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com About This Guide Abstract
EventTracker: Configuring DLA Extension for AWStats Report AWStats Reports Publication Date: Oct 18, 2011 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com About This Guide Abstract
Department of Veterans Affairs. Open Source Electronic Health Record (EHR) Services
 Department of Veterans Affairs Open Source Electronic Health Record (EHR) Services Web Application Automated Testing Framework (WAATF) Software Design Document (SDD) Version 1.0 September 2013 Contract:
Department of Veterans Affairs Open Source Electronic Health Record (EHR) Services Web Application Automated Testing Framework (WAATF) Software Design Document (SDD) Version 1.0 September 2013 Contract:
EventTracker: Configuring DLA Extension for AWStats report AWStats Reports
 EventTracker: Configuring DLA Extension for AWStats report AWStats Reports Prism Microsystems Corporate Headquarter Date: October 18, 2011 8815 Centre Park Drive Columbia MD 21045 (+1) 410.953.6776 (+1)
EventTracker: Configuring DLA Extension for AWStats report AWStats Reports Prism Microsystems Corporate Headquarter Date: October 18, 2011 8815 Centre Park Drive Columbia MD 21045 (+1) 410.953.6776 (+1)
Shakambaree Technologies Pvt. Ltd.
 Welcome to Support Express by Shakambaree Technologies Pvt. Ltd. Introduction: This document is our sincere effort to put in some regular issues faced by a Digital Signature and USB Token user doing on
Welcome to Support Express by Shakambaree Technologies Pvt. Ltd. Introduction: This document is our sincere effort to put in some regular issues faced by a Digital Signature and USB Token user doing on
Document Digital Signature
 Supplier handbook Software Configuration for Digital Signature and Timestamp to certificate-based signature Document objectives and structure The document aims to support suppliers during the following
Supplier handbook Software Configuration for Digital Signature and Timestamp to certificate-based signature Document objectives and structure The document aims to support suppliers during the following
WrkSetup.exe Automated Installation (version 8.0.7)
 WrkSetup.exe Automated Installation (version 8.0.7) Revision: December 13, 2011 The workstation setup program allows you to set customize defaults, automatically select choices for the client workstation,
WrkSetup.exe Automated Installation (version 8.0.7) Revision: December 13, 2011 The workstation setup program allows you to set customize defaults, automatically select choices for the client workstation,
TZWorks Windows Event Log Viewer (evtx_view) Users Guide
 TZWorks Windows Event Log Viewer (evtx_view) Users Guide Abstract evtx_view is a standalone, GUI tool used to extract and parse Event Logs and display their internals. The tool allows one to export all
TZWorks Windows Event Log Viewer (evtx_view) Users Guide Abstract evtx_view is a standalone, GUI tool used to extract and parse Event Logs and display their internals. The tool allows one to export all
UNGASS CRIS 2008
 version 1.0 UNGASS DATA ENTRY SOFTWARE: GLOBAL REPORTING 2008 TROUBLESHOOTING GUIDE Prepared by UNAIDS Evidence, Monitoring, and Policy Department UNAIDS 20, Avenue Appia 1211 Geneva 27 Switzerland Tel.
version 1.0 UNGASS DATA ENTRY SOFTWARE: GLOBAL REPORTING 2008 TROUBLESHOOTING GUIDE Prepared by UNAIDS Evidence, Monitoring, and Policy Department UNAIDS 20, Avenue Appia 1211 Geneva 27 Switzerland Tel.
Tactics, Techniques, & Procedures (TTP) Dual Persona Personal Identity Verification (PIV) Authorization Certificate
 Tactics, Techniques, & Procedures (TTP) Dual Persona Personal Identity Verification (PIV) Authorization Certificate Version 3.0 23 Jan 2012 This document is not to be distributed or changed without express
Tactics, Techniques, & Procedures (TTP) Dual Persona Personal Identity Verification (PIV) Authorization Certificate Version 3.0 23 Jan 2012 This document is not to be distributed or changed without express
Microsoft Visual Studio Integration Guide
 Microsoft Visual Studio Integration Guide MKS provides a number of integrations for Integrated Development Environments (IDEs). IDE integrations allow you to access MKS Integrity s workflow and configuration
Microsoft Visual Studio Integration Guide MKS provides a number of integrations for Integrated Development Environments (IDEs). IDE integrations allow you to access MKS Integrity s workflow and configuration
SAIP 2012 Performance Engineering
 SAIP 2012 Performance Engineering Author: Jens Edlef Møller (jem@cs.au.dk) Instructions for installation, setup and use of tools. Introduction For the project assignment a number of tools will be used.
SAIP 2012 Performance Engineering Author: Jens Edlef Møller (jem@cs.au.dk) Instructions for installation, setup and use of tools. Introduction For the project assignment a number of tools will be used.
DEPLOYING EMC DOCUMENTUM BUSINESS ACTIVITY MONITOR SERVER ON IBM WEBSPHERE APPLICATION SERVER CLUSTER
 White Paper DEPLOYING EMC DOCUMENTUM BUSINESS ACTIVITY MONITOR SERVER ON IBM WEBSPHERE APPLICATION SERVER CLUSTER Abstract This white paper describes the process of deploying EMC Documentum Business Activity
White Paper DEPLOYING EMC DOCUMENTUM BUSINESS ACTIVITY MONITOR SERVER ON IBM WEBSPHERE APPLICATION SERVER CLUSTER Abstract This white paper describes the process of deploying EMC Documentum Business Activity
DEA e-prescribing Setup Installation and Configuration Guide (for Patches OR*3.0*218, PSD*3.0*76, and XU*8.0*580)
 DEA e-prescribing Setup Installation and Configuration Guide (for Patches OR*3.0*218, PSD*3.0*76, and XU*8.0*580) May 2013 Department of Veterans Affairs Office of Information & Technology (OI&T) Product
DEA e-prescribing Setup Installation and Configuration Guide (for Patches OR*3.0*218, PSD*3.0*76, and XU*8.0*580) May 2013 Department of Veterans Affairs Office of Information & Technology (OI&T) Product
PHP Integration Kit. Version 2.5.1. User Guide
 PHP Integration Kit Version 2.5.1 User Guide 2012 Ping Identity Corporation. All rights reserved. PingFederate PHP Integration Kit User Guide Version 2.5.1 December, 2012 Ping Identity Corporation 1001
PHP Integration Kit Version 2.5.1 User Guide 2012 Ping Identity Corporation. All rights reserved. PingFederate PHP Integration Kit User Guide Version 2.5.1 December, 2012 Ping Identity Corporation 1001
Access to Front Office services
 Electricity Transmission System Operator Access to Front Office services Supported Configuration Version 1.4, 2009-07-16 Page : 2/5 CONTENT 1. Purpose of the document 3 2. Operating systems supported for
Electricity Transmission System Operator Access to Front Office services Supported Configuration Version 1.4, 2009-07-16 Page : 2/5 CONTENT 1. Purpose of the document 3 2. Operating systems supported for
Jetico Central Manager. Administrator Guide
 Jetico Central Manager Administrator Guide Introduction Deployment, updating and control of client software can be a time consuming and expensive task for companies and organizations because of the number
Jetico Central Manager Administrator Guide Introduction Deployment, updating and control of client software can be a time consuming and expensive task for companies and organizations because of the number
IHS Emergency Department Dashboard
 RESOURCE AND PATIENT MANAGEMENT SYSTEM IHS Emergency Department Dashboard (BEDD) Version 1.0 Office of Information Technology Division of Information Resource Management Albuquerque, New Mexico Table of
RESOURCE AND PATIENT MANAGEMENT SYSTEM IHS Emergency Department Dashboard (BEDD) Version 1.0 Office of Information Technology Division of Information Resource Management Albuquerque, New Mexico Table of
Using CertAgent to Obtain Domain Controller and Smart Card Logon Certificates for Active Directory Authentication
 Using CertAgent to Obtain Domain Controller and Smart Card Logon Certificates for Active Directory Authentication Contents Domain Controller Certificates... 1 Enrollment for a Domain Controller Certificate...
Using CertAgent to Obtain Domain Controller and Smart Card Logon Certificates for Active Directory Authentication Contents Domain Controller Certificates... 1 Enrollment for a Domain Controller Certificate...
How To Install The Arcgis For Inspire Server Extension On A Microsoft Gis For Inspire Server Extension (For Microsoft) On A Pc Or Macbook Or Ipa (For Macbook)
 ArcGIS 10.2.1 for INSPIRE Server Extension Installation Guide Content 1 Introduction... 1 2 System Requirements... 1 3 Installation... 1 4 Software Authorization... 2 5 Changes to the System... 2 6 Performance
ArcGIS 10.2.1 for INSPIRE Server Extension Installation Guide Content 1 Introduction... 1 2 System Requirements... 1 3 Installation... 1 4 Software Authorization... 2 5 Changes to the System... 2 6 Performance
MySQL and Hadoop: Big Data Integration. Shubhangi Garg & Neha Kumari MySQL Engineering
 MySQL and Hadoop: Big Data Integration Shubhangi Garg & Neha Kumari MySQL Engineering 1Copyright 2013, Oracle and/or its affiliates. All rights reserved. Agenda Design rationale Implementation Installation
MySQL and Hadoop: Big Data Integration Shubhangi Garg & Neha Kumari MySQL Engineering 1Copyright 2013, Oracle and/or its affiliates. All rights reserved. Agenda Design rationale Implementation Installation
Mastering CMake. Sixth Edition. Bill Martin & Hoffman. Ken. Andy Cedilnik, David Cole, Marcus Hanwell, Julien Jomier, Brad King, Robert Maynard,
 Mastering CMake Sixth Edition Ken Bill Martin & Hoffman With contributions from: Andy Cedilnik, David Cole, Marcus Hanwell, Julien Jomier, Brad King, Robert Maynard, Alex Neundorf Published by Kitware
Mastering CMake Sixth Edition Ken Bill Martin & Hoffman With contributions from: Andy Cedilnik, David Cole, Marcus Hanwell, Julien Jomier, Brad King, Robert Maynard, Alex Neundorf Published by Kitware
1 Recommended Readings. 2 Resources Required. 3 Compiling and Running on Linux
 CSC 482/582 Assignment #2 Securing SimpleWebServer Due: September 29, 2015 The goal of this assignment is to learn how to validate input securely. To this purpose, students will add a feature to upload
CSC 482/582 Assignment #2 Securing SimpleWebServer Due: September 29, 2015 The goal of this assignment is to learn how to validate input securely. To this purpose, students will add a feature to upload
Technical Description. DigitalSign 3.1. State of the art legally valid electronic signature. The best, most secure and complete software for
 Technical Description DigitalSign 3.1 State of the art legally valid electronic signature The best, most secure and complete software for Adding digital signatures to any document, in conformance with
Technical Description DigitalSign 3.1 State of the art legally valid electronic signature The best, most secure and complete software for Adding digital signatures to any document, in conformance with
MS InfoPath 2003 MS InfoPath 2007 Microsoft Office InfoPath 2003 minimally runs on the following operating systems:
 8. PREPARING AND TRANSMITTING EDGARLITE SUBMISSIONS 8.1 Purpose EDGARLite is an application that uses intelligent forms to aid in the construction of filings to be submitted to EDGAR. Each EDGARLite form
8. PREPARING AND TRANSMITTING EDGARLITE SUBMISSIONS 8.1 Purpose EDGARLite is an application that uses intelligent forms to aid in the construction of filings to be submitted to EDGAR. Each EDGARLite form
WebSphere Application Server security auditing
 Copyright IBM Corporation 2008 All rights reserved IBM WebSphere Application Server V7 LAB EXERCISE WebSphere Application Server security auditing What this exercise is about... 1 Lab requirements... 1
Copyright IBM Corporation 2008 All rights reserved IBM WebSphere Application Server V7 LAB EXERCISE WebSphere Application Server security auditing What this exercise is about... 1 Lab requirements... 1
Jet Data Manager 2012 User Guide
 Jet Data Manager 2012 User Guide Welcome This documentation provides descriptions of the concepts and features of the Jet Data Manager and how to use with them. With the Jet Data Manager you can transform
Jet Data Manager 2012 User Guide Welcome This documentation provides descriptions of the concepts and features of the Jet Data Manager and how to use with them. With the Jet Data Manager you can transform
Customer Success Story: Dragon Medical 360 Network Edition with Microsoft Application Virtualization
 Customer Success Story: Dragon Medical 360 Network Edition with Microsoft Application Virtualization Contents Contents 2 Introduction 3 Hardware and Software Configurations 3 Dragon Medical 360 Network
Customer Success Story: Dragon Medical 360 Network Edition with Microsoft Application Virtualization Contents Contents 2 Introduction 3 Hardware and Software Configurations 3 Dragon Medical 360 Network
Exchange Server Backup and Restore
 WHITEPAPER BackupAssist Version 6 www.backupassist.com Cortex I.T. 2001-2007 2 Contents 1. Introduction... 3 1.1 Overview... 3 1.2 Requirements... 3 1.3 Requirements for remote backup of Exchange 2007...
WHITEPAPER BackupAssist Version 6 www.backupassist.com Cortex I.T. 2001-2007 2 Contents 1. Introduction... 3 1.1 Overview... 3 1.2 Requirements... 3 1.3 Requirements for remote backup of Exchange 2007...
Encrypting and signing e-mail
 Encrypting and signing e-mail V1.0 Developed by Gunnar Kreitz at CSC, KTH. V2.0 Developed by Pehr Söderman at ICT, KTH (Pehrs@kth.se) V3.0 Includes experiences from the 2009 course V3.1 Adaptation for
Encrypting and signing e-mail V1.0 Developed by Gunnar Kreitz at CSC, KTH. V2.0 Developed by Pehr Söderman at ICT, KTH (Pehrs@kth.se) V3.0 Includes experiences from the 2009 course V3.1 Adaptation for
RMS FTP PUBLIC. FTP Recommendations for Meter Data Retrieval. Issue 4.0 IMP_GDE_0085. Provides the three approaches to FTP as recommended by IESO.
 PUBLIC IMP_GDE_0085 RMS FTP FTP Recommendations for Meter Data Retrieval Issue 4.0 Provides the three approaches to FTP as recommended by IESO. Public Disclaimer The posting of documents on this Web site
PUBLIC IMP_GDE_0085 RMS FTP FTP Recommendations for Meter Data Retrieval Issue 4.0 Provides the three approaches to FTP as recommended by IESO. Public Disclaimer The posting of documents on this Web site
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de
 Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Configuring the Forefront TMG HTTP Filter Abstract In this article I will show you how to configure
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Configuring the Forefront TMG HTTP Filter Abstract In this article I will show you how to configure
1. When will an IP process drop a datagram? 2. When will an IP process fragment a datagram? 3. When will a TCP process drop a segment?
 Questions 1. When will an IP process drop a datagram? 2. When will an IP process fragment a datagram? 3. When will a TCP process drop a segment? 4. When will a TCP process resend a segment? CP476 Internet
Questions 1. When will an IP process drop a datagram? 2. When will an IP process fragment a datagram? 3. When will a TCP process drop a segment? 4. When will a TCP process resend a segment? CP476 Internet
Enabling Single Signon with IBM Cognos 8 BI MR1 and SAP Enterprise Portal
 Guideline Enabling Single Signon with IBM Cognos 8 BI MR1 and SAP Enterprise Portal Product: IBM Cognos 8 BI Area of Interest: Security 2 Copyright Copyright 2008 Cognos ULC (formerly Cognos Incorporated).
Guideline Enabling Single Signon with IBM Cognos 8 BI MR1 and SAP Enterprise Portal Product: IBM Cognos 8 BI Area of Interest: Security 2 Copyright Copyright 2008 Cognos ULC (formerly Cognos Incorporated).
YubiKey PIV Deployment Guide
 YubiKey PIV Deployment Guide Best Practices and Basic Setup YubiKey 4, YubiKey 4 Nano, YubiKey NEO, YubiKey NEO-n YubiKey PIV Deployment Guide 2016 Yubico. All rights reserved. Page 1 of 27 Copyright 2016
YubiKey PIV Deployment Guide Best Practices and Basic Setup YubiKey 4, YubiKey 4 Nano, YubiKey NEO, YubiKey NEO-n YubiKey PIV Deployment Guide 2016 Yubico. All rights reserved. Page 1 of 27 Copyright 2016
Continuous Integration on System z
 Continuous Integration on System z A Proof of Concept at Generali Deutschland Informatik Services GmbH Enterprise Modernization GSE Frankfurt, 14th October 2013 Markus Holzem, GDIS-AS mailto: markus.holzem@generali.de
Continuous Integration on System z A Proof of Concept at Generali Deutschland Informatik Services GmbH Enterprise Modernization GSE Frankfurt, 14th October 2013 Markus Holzem, GDIS-AS mailto: markus.holzem@generali.de
SAP HANA Big Data Intelligence rapiddeployment
 SAP HANA 1.0 November 2015 English SAP HANA Big Data Intelligence rapiddeployment solution: Software and Delivery Requirements SAP SE Dietmar-Hopp-Allee 16 69190 Walldorf Germany Document Revisions 0 1
SAP HANA 1.0 November 2015 English SAP HANA Big Data Intelligence rapiddeployment solution: Software and Delivery Requirements SAP SE Dietmar-Hopp-Allee 16 69190 Walldorf Germany Document Revisions 0 1
Bitrix Site Manager ASP.NET. Installation Guide
 Bitrix Site Manager ASP.NET Installation Guide Contents Introduction... 4 Chapter 1. Checking for IIS Installation... 5 Chapter 2. Using An Archive File to Install Bitrix Site Manager ASP.NET... 7 Preliminary
Bitrix Site Manager ASP.NET Installation Guide Contents Introduction... 4 Chapter 1. Checking for IIS Installation... 5 Chapter 2. Using An Archive File to Install Bitrix Site Manager ASP.NET... 7 Preliminary
Telelogic DASHBOARD Installation Guide Release 3.6
 Telelogic DASHBOARD Installation Guide Release 3.6 1 This edition applies to 3.6.0, Telelogic Dashboard and to all subsequent releases and modifications until otherwise indicated in new editions. Copyright
Telelogic DASHBOARD Installation Guide Release 3.6 1 This edition applies to 3.6.0, Telelogic Dashboard and to all subsequent releases and modifications until otherwise indicated in new editions. Copyright
Foxit Reader Deployment and Configuration
 Copyright 2004-2015 Foxit Software Incorporated. All Rights Reserved. No part of this document can be reproduced, transferred, distributed or stored in any format without the prior written permission of
Copyright 2004-2015 Foxit Software Incorporated. All Rights Reserved. No part of this document can be reproduced, transferred, distributed or stored in any format without the prior written permission of
Enabling Single Signon with IBM Cognos ReportNet and SAP Enterprise Portal
 Guideline Enabling Single Signon with IBM Cognos ReportNet and SAP Enterprise Portal Product(s): IBM Cognos ReportNet Area of Interest: Security 2 Copyright Copyright 2008 Cognos ULC (formerly Cognos Incorporated).
Guideline Enabling Single Signon with IBM Cognos ReportNet and SAP Enterprise Portal Product(s): IBM Cognos ReportNet Area of Interest: Security 2 Copyright Copyright 2008 Cognos ULC (formerly Cognos Incorporated).
Enterprise Service Bus
 We tested: Talend ESB 5.2.1 Enterprise Service Bus Dr. Götz Güttich Talend Enterprise Service Bus 5.2.1 is an open source, modular solution that allows enterprises to integrate existing or new applications
We tested: Talend ESB 5.2.1 Enterprise Service Bus Dr. Götz Güttich Talend Enterprise Service Bus 5.2.1 is an open source, modular solution that allows enterprises to integrate existing or new applications
DIGIPASS CertiID. Getting Started 3.1.0
 DIGIPASS CertiID Getting Started 3.1.0 Disclaimer Disclaimer of Warranties and Limitations of Liabilities The Product is provided on an 'as is' basis, without any other warranties, or conditions, express
DIGIPASS CertiID Getting Started 3.1.0 Disclaimer Disclaimer of Warranties and Limitations of Liabilities The Product is provided on an 'as is' basis, without any other warranties, or conditions, express
Avira Exchange Security 11 Release Notes
 Release Notes General Information The Avira Exchange Security, version 11.1 will replace the previous Avira AntiVir Exchange, version 9.2. The new Avira Exchange Security is available for download on the
Release Notes General Information The Avira Exchange Security, version 11.1 will replace the previous Avira AntiVir Exchange, version 9.2. The new Avira Exchange Security is available for download on the
G/On Release Note. The latest information regarding the G/On software. G/On Version: 5.3 Document revision: 6
 G/On Release Note The latest information regarding the G/On software G/On Version: 5.3 Document revision: 6 G/On Release Note About this document Version 5.3 About this document This document provides
G/On Release Note The latest information regarding the G/On software G/On Version: 5.3 Document revision: 6 G/On Release Note About this document Version 5.3 About this document This document provides
FTP Client Engine Library for Visual dbase. Programmer's Manual
 FTP Client Engine Library for Visual dbase Programmer's Manual (FCE4DB) Version 3.3 May 6, 2014 This software is provided as-is. There are no warranties, expressed or implied. MarshallSoft Computing, Inc.
FTP Client Engine Library for Visual dbase Programmer's Manual (FCE4DB) Version 3.3 May 6, 2014 This software is provided as-is. There are no warranties, expressed or implied. MarshallSoft Computing, Inc.
OpenLDAP Oracle Enterprise Gateway Integration Guide
 An Oracle White Paper June 2011 OpenLDAP Oracle Enterprise Gateway Integration Guide 1 / 29 Disclaimer The following is intended to outline our general product direction. It is intended for information
An Oracle White Paper June 2011 OpenLDAP Oracle Enterprise Gateway Integration Guide 1 / 29 Disclaimer The following is intended to outline our general product direction. It is intended for information
How to resolve Root Certificate Expiry Issue for Enterprise Manager - Database Control (10.2.0.4)
 PURPOSE 14 th June, 2011 This paper demonstrates how to resolve the Oracle Enterprise Manager Database Control configuration errors in Oracle Database versions 10.2.0.4 or 10.2.0.5, arising due to the
PURPOSE 14 th June, 2011 This paper demonstrates how to resolve the Oracle Enterprise Manager Database Control configuration errors in Oracle Database versions 10.2.0.4 or 10.2.0.5, arising due to the
Feature and Technical
 BlackBerry Enterprise Server for Microsoft Exchange Version: 5.0 Service Pack: 4 Feature and Technical Overview Published: 2013-11-07 SWD-20131107160132924 Contents 1 Document revision history...6 2 What's
BlackBerry Enterprise Server for Microsoft Exchange Version: 5.0 Service Pack: 4 Feature and Technical Overview Published: 2013-11-07 SWD-20131107160132924 Contents 1 Document revision history...6 2 What's
[The BSD License] Copyright (c) 2004-2011 Jaroslaw Kowalski jaak@jkowalski.net
![[The BSD License] Copyright (c) 2004-2011 Jaroslaw Kowalski jaak@jkowalski.net [The BSD License] Copyright (c) 2004-2011 Jaroslaw Kowalski jaak@jkowalski.net](/thumbs/20/970627.jpg) Software used by portions of this application require the following license statement: [The BSD License] Copyright (c) 2004-2011 Jaroslaw Kowalski jaak@jkowalski.net All rights reserved. Redistribution
Software used by portions of this application require the following license statement: [The BSD License] Copyright (c) 2004-2011 Jaroslaw Kowalski jaak@jkowalski.net All rights reserved. Redistribution
ICE Trade Vault. Public User & Technology Guide June 6, 2014
 ICE Trade Vault Public User & Technology Guide June 6, 2014 This material may not be reproduced or redistributed in whole or in part without the express, prior written consent of IntercontinentalExchange,
ICE Trade Vault Public User & Technology Guide June 6, 2014 This material may not be reproduced or redistributed in whole or in part without the express, prior written consent of IntercontinentalExchange,
Integrity 10. Curriculum Guide
 Integrity 10 Curriculum Guide Live Classroom Curriculum Guide Integrity 10 Workflows and Documents Administration Training Integrity 10 SCM Administration Training Integrity 10 SCM Basic User Training
Integrity 10 Curriculum Guide Live Classroom Curriculum Guide Integrity 10 Workflows and Documents Administration Training Integrity 10 SCM Administration Training Integrity 10 SCM Basic User Training
Windows Intune Walkthrough: Windows Phone 8 Management
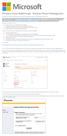 Windows Intune Walkthrough: Windows Phone 8 Management This document will review all the necessary steps to setup and manage Windows Phone 8 using the Windows Intune service. Note: If you want to test
Windows Intune Walkthrough: Windows Phone 8 Management This document will review all the necessary steps to setup and manage Windows Phone 8 using the Windows Intune service. Note: If you want to test
Microsoft Corporation. Project Server 2010 Installation Guide
 Microsoft Corporation Project Server 2010 Installation Guide Office Asia Team 11/4/2010 Table of Contents 1. Prepare the Server... 2 1.1 Install KB979917 on Windows Server... 2 1.2 Creating users and groups
Microsoft Corporation Project Server 2010 Installation Guide Office Asia Team 11/4/2010 Table of Contents 1. Prepare the Server... 2 1.1 Install KB979917 on Windows Server... 2 1.2 Creating users and groups
Installing OpenVSP on Windows 7
 ASDL, Georgia Institue of Technology August 2012 Table of Contents 1. Introduction... 1 2. Setting up Windows Line-Mode... 1 3. Preparation for OpenVSP... 2 3.1. Create an OpenVSP Folder... 2 3.2. Install
ASDL, Georgia Institue of Technology August 2012 Table of Contents 1. Introduction... 1 2. Setting up Windows Line-Mode... 1 3. Preparation for OpenVSP... 2 3.1. Create an OpenVSP Folder... 2 3.2. Install
Novell ZENworks 10 Configuration Management SP3
 AUTHORIZED DOCUMENTATION Software Distribution Reference Novell ZENworks 10 Configuration Management SP3 10.3 November 17, 2011 www.novell.com Legal Notices Novell, Inc., makes no representations or warranties
AUTHORIZED DOCUMENTATION Software Distribution Reference Novell ZENworks 10 Configuration Management SP3 10.3 November 17, 2011 www.novell.com Legal Notices Novell, Inc., makes no representations or warranties
Hands-On Lab. Web Development in Visual Studio 2010. Lab version: 1.0.0. Last updated: 12/10/2010. Page 1
 Hands-On Lab Web Development in Visual Studio 2010 Lab version: 1.0.0 Last updated: 12/10/2010 Page 1 CONTENTS OVERVIEW... 3 EXERCISE 1: USING HTML CODE SNIPPETS IN VISUAL STUDIO 2010... 6 Task 1 Adding
Hands-On Lab Web Development in Visual Studio 2010 Lab version: 1.0.0 Last updated: 12/10/2010 Page 1 CONTENTS OVERVIEW... 3 EXERCISE 1: USING HTML CODE SNIPPETS IN VISUAL STUDIO 2010... 6 Task 1 Adding
Kaspersky Endpoint Security 10 for Windows. Deployment guide
 Kaspersky Endpoint Security 10 for Windows Deployment guide Introduction Typical Corporate Network Network servers Internet Gateway Workstations Mail servers Portable media Malware Intrusion Routes Viruses
Kaspersky Endpoint Security 10 for Windows Deployment guide Introduction Typical Corporate Network Network servers Internet Gateway Workstations Mail servers Portable media Malware Intrusion Routes Viruses
Reporting Installation Checklist
 This checklist is designed to help you before and during your Websense Enterprise Reporting installation. Print this checklist for reference as you prepare for and perform the installation, especially
This checklist is designed to help you before and during your Websense Enterprise Reporting installation. Print this checklist for reference as you prepare for and perform the installation, especially
2007 Microsoft Office System Document Encryption
 2007 Microsoft Office System Document Encryption June 2007 Table of Contents Introduction 1 Benefits of Document Encryption 2 Microsoft 2007 Office system Document Encryption Improvements 5 End-User Microsoft
2007 Microsoft Office System Document Encryption June 2007 Table of Contents Introduction 1 Benefits of Document Encryption 2 Microsoft 2007 Office system Document Encryption Improvements 5 End-User Microsoft
FreeForm Designer. Phone: +972-9-8309999 Fax: +972-9-8309998 POB 8792, Natanya, 42505 Israel www.autofont.com. Document2
 FreeForm Designer FreeForm Designer enables designing smart forms based on industry-standard MS Word editing features. FreeForm Designer does not require any knowledge of or training in programming languages
FreeForm Designer FreeForm Designer enables designing smart forms based on industry-standard MS Word editing features. FreeForm Designer does not require any knowledge of or training in programming languages
NetIQ Identity Manager Setup Guide
 NetIQ Identity Manager Setup Guide July 2015 www.netiq.com/documentation Legal Notice THIS DOCUMENT AND THE SOFTWARE DESCRIBED IN THIS DOCUMENT ARE FURNISHED UNDER AND ARE SUBJECT TO THE TERMS OF A LICENSE
NetIQ Identity Manager Setup Guide July 2015 www.netiq.com/documentation Legal Notice THIS DOCUMENT AND THE SOFTWARE DESCRIBED IN THIS DOCUMENT ARE FURNISHED UNDER AND ARE SUBJECT TO THE TERMS OF A LICENSE
BI xpress Product Overview
 BI xpress Product Overview Develop and manage SSIS packages with ease! Key Features Create a robust auditing and notification framework for SSIS Speed BI development with SSAS calculations and SSIS package
BI xpress Product Overview Develop and manage SSIS packages with ease! Key Features Create a robust auditing and notification framework for SSIS Speed BI development with SSAS calculations and SSIS package
DVBLink For IPTV. Installation and configuration manual
 DVBLink For IPTV Installation and configuration manual DVBLogic 2010 Table of contents Table of contents... 2 Introduction... 4 Installation types... 4 DVBLink for IPTV local installation... 4 DVBLink
DVBLink For IPTV Installation and configuration manual DVBLogic 2010 Table of contents Table of contents... 2 Introduction... 4 Installation types... 4 DVBLink for IPTV local installation... 4 DVBLink
What is An Introduction
 What is? An Introduction GenICam_Introduction.doc Page 1 of 14 Table of Contents 1 SCOPE OF THIS DOCUMENT... 4 2 GENICAM'S KEY IDEA... 4 3 GENICAM USE CASES... 5 3.1 CONFIGURING THE CAMERA... 5 3.2 GRABBING
What is? An Introduction GenICam_Introduction.doc Page 1 of 14 Table of Contents 1 SCOPE OF THIS DOCUMENT... 4 2 GENICAM'S KEY IDEA... 4 3 GENICAM USE CASES... 5 3.1 CONFIGURING THE CAMERA... 5 3.2 GRABBING
AddLocalUser AddLocalGroup AddLocalUserToLocalGroup AddDomainUserToLocalGroup AddDomainGroupToLocalGroup
 Written by Rob Zylowski Originally developed for Unidesk and posted on www.unidesk.com Sr. Solutions Architect, Unidesk Corporation rzylowski@unidesk.com Managing User or Group Permissions on Virtual Desktops
Written by Rob Zylowski Originally developed for Unidesk and posted on www.unidesk.com Sr. Solutions Architect, Unidesk Corporation rzylowski@unidesk.com Managing User or Group Permissions on Virtual Desktops
Win8 Networking FinishLynx with Meet Management Technical Support Guide
 FINISHLYNX NETWORKING WIN 8 LYNX SYSTEM DEVELOPERS, INC. Win8 Networking FinishLynx with Meet Management Technical Support Guide Sections 1 and 2 should be completed on both FinishLynx and Meet Management
FINISHLYNX NETWORKING WIN 8 LYNX SYSTEM DEVELOPERS, INC. Win8 Networking FinishLynx with Meet Management Technical Support Guide Sections 1 and 2 should be completed on both FinishLynx and Meet Management
MassTransit 6.0 Enterprise Web Configuration For Windows
 MassTransit 6.0 Enterprise Web Configuration For Windows November 7, 2008 Group Logic, Inc. 1100 North Glebe Road, Suite 800 Arlington, VA 22201 Phone: 703-528-1555 Fax: 703-528-3296 E-mail: info@grouplogic.com
MassTransit 6.0 Enterprise Web Configuration For Windows November 7, 2008 Group Logic, Inc. 1100 North Glebe Road, Suite 800 Arlington, VA 22201 Phone: 703-528-1555 Fax: 703-528-3296 E-mail: info@grouplogic.com
32-Bit Workload Automation 5 for Windows on 64-Bit Windows Systems
 32-Bit Workload Automation 5 for Windows on 64-Bit Windows Systems Overview 64-bit Windows Systems Modifying the Working Folder for Universal Server Components Applications Installed in the Windows System
32-Bit Workload Automation 5 for Windows on 64-Bit Windows Systems Overview 64-bit Windows Systems Modifying the Working Folder for Universal Server Components Applications Installed in the Windows System
Desktop Authority and Group Policy Preferences
 Desktop Authority and Group Policy Preferences A ScriptLogic Product Positioning Paper 1.800.813.6415 www.scriptlogic.com Desktop Authority and Group Policy Preferences Introduction Group Policy Preferences
Desktop Authority and Group Policy Preferences A ScriptLogic Product Positioning Paper 1.800.813.6415 www.scriptlogic.com Desktop Authority and Group Policy Preferences Introduction Group Policy Preferences
Phoronix Test Suite v5.8.0 (Belev)
 (Belev) Phoromatic User Manual Phoronix Test Suite Phoromatic Phoromatic Server Introduction Phoromatic is a remote management system for the Phoronix Test Suite. Phoromatic allows the automatic (hence
(Belev) Phoromatic User Manual Phoronix Test Suite Phoromatic Phoromatic Server Introduction Phoromatic is a remote management system for the Phoronix Test Suite. Phoromatic allows the automatic (hence
ncipher Modules Integration Guide for Axway Validation Authority Server 4.11 (Responder) www.thales-esecurity.com
 ncipher Modules Integration Guide for Axway Validation Authority Server 4.11 (Responder) www.thales-esecurity.com Version: 1.0 Date: 30 May 2012 Copyright 2012 Thales e-security Limited. All rights reserved.
ncipher Modules Integration Guide for Axway Validation Authority Server 4.11 (Responder) www.thales-esecurity.com Version: 1.0 Date: 30 May 2012 Copyright 2012 Thales e-security Limited. All rights reserved.
SafeNet KMIP and Google Cloud Storage Integration Guide
 SafeNet KMIP and Google Cloud Storage Integration Guide Documentation Version: 20130719 Table of Contents CHAPTER 1 GOOGLE CLOUD STORAGE................................. 2 Introduction...............................................................
SafeNet KMIP and Google Cloud Storage Integration Guide Documentation Version: 20130719 Table of Contents CHAPTER 1 GOOGLE CLOUD STORAGE................................. 2 Introduction...............................................................
Presents. WITSML Solutions For Your Business
 Presents WITSML Solutions For Your Business WHAT IS WITSML? WITSML (Wellsite Information Transfer Standard Markup Language) is a petroleum industry standard way of sharing drilling and completions related
Presents WITSML Solutions For Your Business WHAT IS WITSML? WITSML (Wellsite Information Transfer Standard Markup Language) is a petroleum industry standard way of sharing drilling and completions related
C HAPTER E IGHTEEN T HE PGP, MAIL, AND CGI LIBRARIES. PGP Interface Library
 C HAPTER E IGHTEEN T HE PGP, MAIL, AND CGI LIBRARIES The PGP (pgp-lib.pl), mail (mail-lib.pl), and CGI (cgi-lib.pl) libraries are general libraries that support Web-store-specific functions. For example,
C HAPTER E IGHTEEN T HE PGP, MAIL, AND CGI LIBRARIES The PGP (pgp-lib.pl), mail (mail-lib.pl), and CGI (cgi-lib.pl) libraries are general libraries that support Web-store-specific functions. For example,
A Binary Tree SMART Migration Webinar. SMART Solutions for Notes- to- Exchange Migrations
 A Binary Tree SMART Migration Webinar SMART Solutions for Notes- to- Exchange Migrations Critical Success Factors of Enterprise Migrations from Notes/Domino to Exchange Secure integration of mail systems
A Binary Tree SMART Migration Webinar SMART Solutions for Notes- to- Exchange Migrations Critical Success Factors of Enterprise Migrations from Notes/Domino to Exchange Secure integration of mail systems
NIST/ITL CSD Biometric Conformance Test Software on Apache Hadoop. September 2014. National Institute of Standards and Technology (NIST)
 NIST/ITL CSD Biometric Conformance Test Software on Apache Hadoop September 2014 Dylan Yaga NIST/ITL CSD Lead Software Designer Fernando Podio NIST/ITL CSD Project Manager National Institute of Standards
NIST/ITL CSD Biometric Conformance Test Software on Apache Hadoop September 2014 Dylan Yaga NIST/ITL CSD Lead Software Designer Fernando Podio NIST/ITL CSD Project Manager National Institute of Standards
About This Document 3. Integration and Automation Capabilities 4. Command-Line Interface (CLI) 8. API RPC Protocol 9.
 Parallels Panel Contents About This Document 3 Integration and Automation Capabilities 4 Command-Line Interface (CLI) 8 API RPC Protocol 9 Event Handlers 11 Panel Notifications 13 APS Packages 14 C H A
Parallels Panel Contents About This Document 3 Integration and Automation Capabilities 4 Command-Line Interface (CLI) 8 API RPC Protocol 9 Event Handlers 11 Panel Notifications 13 APS Packages 14 C H A
DESLock+ Basic Setup Guide Version 1.20, rev: June 9th 2014
 DESLock+ Basic Setup Guide Version 1.20, rev: June 9th 2014 Contents Overview... 2 System requirements:... 2 Before installing... 3 Download and installation... 3 Configure DESLock+ Enterprise Server...
DESLock+ Basic Setup Guide Version 1.20, rev: June 9th 2014 Contents Overview... 2 System requirements:... 2 Before installing... 3 Download and installation... 3 Configure DESLock+ Enterprise Server...
FEATURE COMPARISON BETWEEN WINDOWS SERVER UPDATE SERVICES AND SHAVLIK HFNETCHKPRO
 FEATURE COMPARISON BETWEEN WINDOWS SERVER UPDATE SERVICES AND SHAVLIK HFNETCHKPRO Copyright 2005 Shavlik Technologies. All rights reserved. No part of this document may be reproduced or retransmitted in
FEATURE COMPARISON BETWEEN WINDOWS SERVER UPDATE SERVICES AND SHAVLIK HFNETCHKPRO Copyright 2005 Shavlik Technologies. All rights reserved. No part of this document may be reproduced or retransmitted in
Administration Guide ActivClient for Windows 6.2
 Administration Guide ActivClient for Windows 6.2 ActivClient for Windows Administration Guide P 2 Table of Contents Chapter 1: Introduction....................................................................12
Administration Guide ActivClient for Windows 6.2 ActivClient for Windows Administration Guide P 2 Table of Contents Chapter 1: Introduction....................................................................12
Extending Remote Desktop for Large Installations. Distributed Package Installs
 Extending Remote Desktop for Large Installations This article describes four ways Remote Desktop can be extended for large installations. The four ways are: Distributed Package Installs, List Sharing,
Extending Remote Desktop for Large Installations This article describes four ways Remote Desktop can be extended for large installations. The four ways are: Distributed Package Installs, List Sharing,
Tuskar UI Documentation
 Tuskar UI Documentation Release Juno Tuskar Team May 05, 2015 Contents 1 Tuskar UI 3 1.1 High-Level Overview.......................................... 3 1.2 Installation Guide............................................
Tuskar UI Documentation Release Juno Tuskar Team May 05, 2015 Contents 1 Tuskar UI 3 1.1 High-Level Overview.......................................... 3 1.2 Installation Guide............................................
Idera SQL Diagnostic Manager Management Pack Guide for System Center Operations Manager. Install Guide. Idera Inc., Published: April 2013
 Idera SQL Diagnostic Manager Management Pack Guide for System Center Operations Manager Install Guide Idera Inc., Published: April 2013 Contents Introduction to the Idera SQL Diagnostic Manager Management
Idera SQL Diagnostic Manager Management Pack Guide for System Center Operations Manager Install Guide Idera Inc., Published: April 2013 Contents Introduction to the Idera SQL Diagnostic Manager Management
Ipswitch Client Installation Guide
 IPSWITCH TECHNICAL BRIEF Ipswitch Client Installation Guide In This Document Installing on a Single Computer... 1 Installing to Multiple End User Computers... 5 Silent Install... 5 Active Directory Group
IPSWITCH TECHNICAL BRIEF Ipswitch Client Installation Guide In This Document Installing on a Single Computer... 1 Installing to Multiple End User Computers... 5 Silent Install... 5 Active Directory Group
Troubleshooting smart card logon authentication on active directory
 Troubleshooting smart card logon authentication on active directory Version 1.0 Prepared by: "Vincent Le Toux" Date: 2014-06-11 1 Table of Contents Table of Contents Revision History Error messages The
Troubleshooting smart card logon authentication on active directory Version 1.0 Prepared by: "Vincent Le Toux" Date: 2014-06-11 1 Table of Contents Table of Contents Revision History Error messages The
DiskBoss. File & Disk Manager. Version 2.0. Dec 2011. Flexense Ltd. www.flexense.com info@flexense.com. File Integrity Monitor
 DiskBoss File & Disk Manager File Integrity Monitor Version 2.0 Dec 2011 www.flexense.com info@flexense.com 1 Product Overview DiskBoss is an automated, rule-based file and disk manager allowing one to
DiskBoss File & Disk Manager File Integrity Monitor Version 2.0 Dec 2011 www.flexense.com info@flexense.com 1 Product Overview DiskBoss is an automated, rule-based file and disk manager allowing one to
FrontDesk. (Server Software Installation) Ver. 1.0.1. www.frontdeskhealth.com
 FrontDesk (Server Software Installation) Ver. 1.0.1 www.frontdeskhealth.com This document is the installation manual for installing the FrontDesk Server, Kiosk/Touch Screen, and License Management Tool
FrontDesk (Server Software Installation) Ver. 1.0.1 www.frontdeskhealth.com This document is the installation manual for installing the FrontDesk Server, Kiosk/Touch Screen, and License Management Tool
Internet Information Services Integration Kit. Version 2.4. User Guide
 Internet Information Services Integration Kit Version 2.4 User Guide 2014 Ping Identity Corporation. All rights reserved. PingFederate Internet Information Services User Guide Version 2.4 June, 2014 Ping
Internet Information Services Integration Kit Version 2.4 User Guide 2014 Ping Identity Corporation. All rights reserved. PingFederate Internet Information Services User Guide Version 2.4 June, 2014 Ping
6. Is it mandatory to have the digital certificate issued from NICCA?...3. 7. Is it mandatory for the sender and receiver to have a NIC email id?...
 FAQ FOR S/MIME 1. What is S/MIME?...2 2. What is digital certificate?...2 3. What is an encrypted email?...2 4. Is it mandatory to use this service?...2 5. What I need to do to start using S/MIME service?...2
FAQ FOR S/MIME 1. What is S/MIME?...2 2. What is digital certificate?...2 3. What is an encrypted email?...2 4. Is it mandatory to use this service?...2 5. What I need to do to start using S/MIME service?...2
Executable Integrity Verification
 Executable Integrity Verification Abstract Background Determining if a given executable has been trojaned is a tedious task. It is beyond the capabilities of the average end user and even many network
Executable Integrity Verification Abstract Background Determining if a given executable has been trojaned is a tedious task. It is beyond the capabilities of the average end user and even many network
INSTALL NOTES Elements Environments Windows 95 Users
 NEURON DATA INSTALL NOTES Elements Environments Windows 95 Users Modifying Environment Variables You must modify the environment variables of your system to be able to compile and run Elements Environment
NEURON DATA INSTALL NOTES Elements Environments Windows 95 Users Modifying Environment Variables You must modify the environment variables of your system to be able to compile and run Elements Environment
Drupal CMS for marketing sites
 Drupal CMS for marketing sites Intro Sample sites: End to End flow Folder Structure Project setup Content Folder Data Store (Drupal CMS) Importing/Exporting Content Database Migrations Backend Config Unit
Drupal CMS for marketing sites Intro Sample sites: End to End flow Folder Structure Project setup Content Folder Data Store (Drupal CMS) Importing/Exporting Content Database Migrations Backend Config Unit
StreamServe Persuasion SP5 Supported platforms and software
 StreamServe Persuasion SP5 Supported platforms and software Reference Guide Rev A StreamServe Persuasion SP5 Reference Guide Rev A 2001-2010 STREAMSERVE, INC. ALL RIGHTS RESERVED United States patent #7,127,520
StreamServe Persuasion SP5 Supported platforms and software Reference Guide Rev A StreamServe Persuasion SP5 Reference Guide Rev A 2001-2010 STREAMSERVE, INC. ALL RIGHTS RESERVED United States patent #7,127,520
Nebraska Insurance Reporting Guide
 Nebraska Insurance Reporting Guide Nebraska Department of Motor Vehicles Driver and Vehicle Records Division 301 Centennial Mall South P.O. Box 94789 Lincoln, NE 68509-4789 www.dmv.nebraska.gov Table of
Nebraska Insurance Reporting Guide Nebraska Department of Motor Vehicles Driver and Vehicle Records Division 301 Centennial Mall South P.O. Box 94789 Lincoln, NE 68509-4789 www.dmv.nebraska.gov Table of
Application Note Windows 2008 and IBM Tape Diagnostic Tool (ITDT-GE)
 Application Note Windows 2008 and IBM Tape Diagnostic Tool (ITDT-GE) PREFACE This document describes how to install and use IBM Tape Diagnostic Tool GUI Edition (ITDT-GE) on a Windows 2008 x 64 server
Application Note Windows 2008 and IBM Tape Diagnostic Tool (ITDT-GE) PREFACE This document describes how to install and use IBM Tape Diagnostic Tool GUI Edition (ITDT-GE) on a Windows 2008 x 64 server
Installation Guide for Pulse on Windows Server 2008R2
 MadCap Software Installation Guide for Pulse on Windows Server 2008R2 Pulse Copyright 2014 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software
MadCap Software Installation Guide for Pulse on Windows Server 2008R2 Pulse Copyright 2014 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software
GP REPORTS VIEWER USER GUIDE
 GP Reports Viewer Dynamics GP Reporting Made Easy GP REPORTS VIEWER USER GUIDE For Dynamics GP Version 2015 (Build 5) Dynamics GP Version 2013 (Build 14) Dynamics GP Version 2010 (Build 65) Last updated
GP Reports Viewer Dynamics GP Reporting Made Easy GP REPORTS VIEWER USER GUIDE For Dynamics GP Version 2015 (Build 5) Dynamics GP Version 2013 (Build 14) Dynamics GP Version 2010 (Build 65) Last updated
Supplement I.B: Installing and Configuring JDK 1.6
 Supplement I.B: Installing and Configuring JDK 1.6 For Introduction to Java Programming Y. Daniel Liang This supplement covers the following topics: Downloading JDK 1.6 ( 1.2) Installing JDK 1.6 ( 1.3)
Supplement I.B: Installing and Configuring JDK 1.6 For Introduction to Java Programming Y. Daniel Liang This supplement covers the following topics: Downloading JDK 1.6 ( 1.2) Installing JDK 1.6 ( 1.3)
