Life on a University Network. An Architecture for Automatically Detecting, Isolating, and Cleaning Infected Hosts
|
|
|
- Mildred Casey
- 8 years ago
- Views:
Transcription
1 Life on a University Network An Architecture for Automatically Detecting, Isolating, and Cleaning Infected Hosts
2 Background Eric Gauthier Boston University Private University in downtown Boston, MA 17,682 undergraduate 11,367 graduate I m a Network Engineer, not: A security professional A windows programmer A lawyer Feb 2004 Eric Gauthier ~ Boston University 2
3 The BU Network 3-Tier hierarchical network with Multi-Gig backbone and w/10mbps port per student We handle layers 1 4 and ISP services (DNS, DHCP ) ~ 20,000 Systems ~ 2,000 Switches/routers ~ 200 Buildings and ~ 20 Staff members Variety of network devices, vendors, features Host OS diversity, though ~ 2 4 years old Not everything supports trunking Feb 2004 Eric Gauthier ~ Boston University 3
4 Facing the Abyss and not Flinching 12,000 students all showing up on Friday, all with at least one computer, and Classes Start Tuesday. Hosts: 90% Microsoft, 75% post Win98/NT. ~ 1 in 3 systems are vulnerable if not infected (I.e. 50% of post Win98/NT). The Solution is a Self-Help type system Its all Free except the labor Infrastructure and Host OS Independent Its not a Silver Bullet Feb 2004 Eric Gauthier ~ Boston University 4
5 The Team NetReg as known/unknown tracker Nessus to scan Cleaning tool Later IDS/Vulnerability Scans Quarantining Feb 2004 Eric Gauthier ~ Boston University 5
6 Thank You for Registering Mac Address Registration System/Database DHCP (un)known = host (un)registered DNS multiviews and and web virtual hosting tricks are used to present registration information Single subnet/multi-subnet vlans Quarantines = Host in the database but not known to the DHCP server AUP: you accept responsibility for the actions of this system. Feb 2004 Eric Gauthier ~ Boston University 6
7 What Does NetReg Use? DNS DHCP Web Server with NetReg backend CGI MySQL Vulnerability Scanner Feb 2004 Eric Gauthier ~ Boston University 7
8 Network Registration DHCP Server Nessus Server The Internet End User System DNS Server NetReg (Web) Feb 2004 Eric Gauthier ~ Boston University 8
9 Big Brother is Watching Nessus: Scan host for a particular/set of vulnerabilities Client/Server version Heavy client has list of scans to do Server performs scans and returns result details Client designed to run once for a range of hosts Client has list of all scans to perform NASL No Server needed Single Scan / single return code / no details We scanned for MS03-026, then MS Feb 2004 Eric Gauthier ~ Boston University 9
10 Nessus Scanning: DHCP Server Nessus Server The Internet End User System DNS Server NetReg (Web) Feb 2004 Eric Gauthier ~ Boston University 10
11 Fall Cleaning Single help desk tool (well 3 of them) Designed for NT/2000/XP/ME Wrapper written with SMS Installer Adds itself to the Run Once Verifies minimum Service Packs NT: SP5 Win2k: SP2 WinXP: SP1 Verifies certain Hotfixes MS or MS Load patches with wget Feb 2004 Eric Gauthier ~ Boston University 11
12 Check this, and this, and this Runs in the background with a notice window Stinger: NAI general cleaning tool (~20) FixWelch: Symantec Welchia Cleaner result generated Windows Update/AV Setup Messages Feb 2004 Eric Gauthier ~ Boston University 12
13 Oh, and Don t Forget Its an iterative process We run Microsoft Vulnerability Scans Correlate Hosts with Nessus Quarantine Hosts when found Working on automate un-quarantine Feb 2004 Eric Gauthier ~ Boston University 13
14 Oops - Issues and future plans Network Registration Where s the web browser on my Xbox? Apache ddos Spyware & HTTP-like things Can you handle the load Network Registration: Bypass Monitoring Automated Unquarantining Feb 2004 Eric Gauthier ~ Boston University 14
15 Oops - Issues and future plans Nessus Security model: failure goes to open state Nessus client vs. NASL: overhead vs. scan diversity IDS/Vulnerability scan integration feedback The one Linux oddball Feb 2004 Eric Gauthier ~ Boston University 15
16 Oops - Issues and future plans Cleaning SP1 Issues Language detection Illegal version keys Invasive Doesn t catch/clean everything Feb 2004 Eric Gauthier ~ Boston University 16
17 How Did We Do - Summary 90% Effective during Registration 90% Effective during Quarantine No one is trapped Reduced the cases to a manageable load Infection isn t spreading! 10% getting through is a decreasing number over time, not an exponentially increasing one Feb 2004 Eric Gauthier ~ Boston University 17
18 Special Thanks Boston University s Security and Help Desk teams Southwestern University for NetReg Anyone who ever made a tool and released it for free to the world Feb 2004 Eric Gauthier ~ Boston University 18
19 Helpful URLs ISC DHCP/DNS servers: Apache: NetReg: Nessus: Eric s brief write-up and some configuration examples: Feb 2004 Eric Gauthier ~ Boston University 19
20 More Helpful URLs Stinger: Fixwelch: er/venc/data/w32.welchia.worm.removal.tool. html SMS Installer: ds/20/tools/installer.asp MS03-026/MS Scanner: d=kb;en-us; Feb 2004 Eric Gauthier ~ Boston University 20
How To Manage Your Information Systems At Aerosoft.Com
 Your information systems are at the heart of your businesses daily operation. System down time costs businesses a significant amount of money each year. Most problems that cause down time can be prevented
Your information systems are at the heart of your businesses daily operation. System down time costs businesses a significant amount of money each year. Most problems that cause down time can be prevented
Bypassing Network Access Control Systems
 1 Bypassing Network Access Control Systems Ofir Arkin, CTO Blackhat USA 2006 ofir.arkin@insightix.com http://www.insightix.com 2 What this talk is about? Introduction to NAC The components of a NAC solution
1 Bypassing Network Access Control Systems Ofir Arkin, CTO Blackhat USA 2006 ofir.arkin@insightix.com http://www.insightix.com 2 What this talk is about? Introduction to NAC The components of a NAC solution
Network Virtualization Network Admission Control Deployment Guide
 Network Virtualization Network Admission Control Deployment Guide This document provides guidance for enterprises that want to deploy the Cisco Network Admission Control (NAC) Appliance for their campus
Network Virtualization Network Admission Control Deployment Guide This document provides guidance for enterprises that want to deploy the Cisco Network Admission Control (NAC) Appliance for their campus
Keeping Up To Date with Windows Server Update Services. Bob McCoy, CISSP, MCSE Technical Account Manager Microsoft Corporation
 Keeping Up To Date with Windows Server Update Services Bob McCoy, CISSP, MCSE Technical Account Manager Microsoft Corporation Business Risk Is High Up to 95% of breaches exploit vulnerabilities for which
Keeping Up To Date with Windows Server Update Services Bob McCoy, CISSP, MCSE Technical Account Manager Microsoft Corporation Business Risk Is High Up to 95% of breaches exploit vulnerabilities for which
The self-defending network a resilient network. By Steen Pedersen Ementor, Denmark
 The self-defending network a resilient network By Steen Pedersen Ementor, Denmark The self-defending network - a resilient network What is required of our internal networks? Available, robust, fast and
The self-defending network a resilient network By Steen Pedersen Ementor, Denmark The self-defending network - a resilient network What is required of our internal networks? Available, robust, fast and
Nessus scanning on Windows Domain
 Nessus scanning on Windows Domain A little inside information and Nessus can go a long way By Sunil Vakharia sunilv@phreaker.net Version 1.0 4 November 2003 About this paper This paper is not a tutorial
Nessus scanning on Windows Domain A little inside information and Nessus can go a long way By Sunil Vakharia sunilv@phreaker.net Version 1.0 4 November 2003 About this paper This paper is not a tutorial
Transferring Your Internet Services
 Page 1 of 6 Transferring Your Internet Services Below you will find the instructions necessary to move your web hosting, email, and DNS services to NuVox. The Basics Transferring your domain name Preparing
Page 1 of 6 Transferring Your Internet Services Below you will find the instructions necessary to move your web hosting, email, and DNS services to NuVox. The Basics Transferring your domain name Preparing
DNS ROUND ROBIN HIGH-AVAILABILITY LOAD SHARING
 PolyServe High-Availability Server Clustering for E-Business 918 Parker Street Berkeley, California 94710 (510) 665-2929 wwwpolyservecom Number 990903 WHITE PAPER DNS ROUND ROBIN HIGH-AVAILABILITY LOAD
PolyServe High-Availability Server Clustering for E-Business 918 Parker Street Berkeley, California 94710 (510) 665-2929 wwwpolyservecom Number 990903 WHITE PAPER DNS ROUND ROBIN HIGH-AVAILABILITY LOAD
ResNet Computer Consultant Job Description
 ResNet Computer Consultant Job Description Description: ResNet is the Internet Service Provider within the Residence Halls and Family and Graduate Housing at Montana State University. In addition to providing
ResNet Computer Consultant Job Description Description: ResNet is the Internet Service Provider within the Residence Halls and Family and Graduate Housing at Montana State University. In addition to providing
Comprehensive Malware Detection with SecurityCenter Continuous View and Nessus. February 3, 2015 (Revision 4)
 Comprehensive Malware Detection with SecurityCenter Continuous View and Nessus February 3, 2015 (Revision 4) Table of Contents Overview... 3 Malware, Botnet Detection, and Anti-Virus Auditing... 3 Malware
Comprehensive Malware Detection with SecurityCenter Continuous View and Nessus February 3, 2015 (Revision 4) Table of Contents Overview... 3 Malware, Botnet Detection, and Anti-Virus Auditing... 3 Malware
BIND 10 the next BIG thing
 BIND 10 the next BIG thing What is it? BIND10 will be the next step in the evolution of DNS & DHCP More evolution than revolution in the code sense More revolution than evolution in the UI sense Product
BIND 10 the next BIG thing What is it? BIND10 will be the next step in the evolution of DNS & DHCP More evolution than revolution in the code sense More revolution than evolution in the UI sense Product
Vulnerability Assessment Using Nessus
 Vulnerability Assessment Using Nessus Paul Asadoorian, GCIA, GCIH Network Security Engineer Brown University Paul_Asadoorian@brown.edu Overview Introduction to Nessus Nessus Architecture Nessus in Action
Vulnerability Assessment Using Nessus Paul Asadoorian, GCIA, GCIH Network Security Engineer Brown University Paul_Asadoorian@brown.edu Overview Introduction to Nessus Nessus Architecture Nessus in Action
White Paper How to Remotely Access Ethernet I/O Over the Internet
 White Paper How to Remotely Access Ethernet I/O Over the Internet ACROMAG INCORPORATED Tel: (248) 295-0880 30765 South Wixom Road Fax: (248) 624-9234 P.O. BOX 437 Wixom, MI 48393-7037 U.S.A. Copyright
White Paper How to Remotely Access Ethernet I/O Over the Internet ACROMAG INCORPORATED Tel: (248) 295-0880 30765 South Wixom Road Fax: (248) 624-9234 P.O. BOX 437 Wixom, MI 48393-7037 U.S.A. Copyright
1 Scope of Assessment
 CIT 380 Project Network Security Assessment Due: April 30, 2014 This project is a security assessment of a small group of systems. In this assessment, students will apply security tools and resources learned
CIT 380 Project Network Security Assessment Due: April 30, 2014 This project is a security assessment of a small group of systems. In this assessment, students will apply security tools and resources learned
inforouter V8.0 Server & Client Requirements
 inforouter V8.0 Server & Client Requirements Please review this document thoroughly before proceeding with the installation of inforouter Version 8. This document describes the minimum and recommended
inforouter V8.0 Server & Client Requirements Please review this document thoroughly before proceeding with the installation of inforouter Version 8. This document describes the minimum and recommended
Web Application Threats and Vulnerabilities Web Server Hacking and Web Application Vulnerability
 Web Application Threats and Vulnerabilities Web Server Hacking and Web Application Vulnerability WWW Based upon HTTP and HTML Runs in TCP s application layer Runs on top of the Internet Used to exchange
Web Application Threats and Vulnerabilities Web Server Hacking and Web Application Vulnerability WWW Based upon HTTP and HTML Runs in TCP s application layer Runs on top of the Internet Used to exchange
IntraVUE Plug Scanner/Recorder Installation and Start-Up
 IntraVUE Plug Scanner/Recorder Installation and Start-Up The IntraVUE Plug is a complete IntraVUE Hardware/Software solution that can plug directly into any network to continually scan and record details
IntraVUE Plug Scanner/Recorder Installation and Start-Up The IntraVUE Plug is a complete IntraVUE Hardware/Software solution that can plug directly into any network to continually scan and record details
SCHOOL DISTRICT OF ESCAMBIA COUNTY
 SCHOOL DISTRICT OF ESCAMBIA COUNTY JOB DESCRIPTION Programmer Analyst I Web Technologies PROGRAMMER ANALYST I WEB TECHNOLOGIES QUALIFICATIONS: (1) Bachelor s Degree from an accredited educational institution
SCHOOL DISTRICT OF ESCAMBIA COUNTY JOB DESCRIPTION Programmer Analyst I Web Technologies PROGRAMMER ANALYST I WEB TECHNOLOGIES QUALIFICATIONS: (1) Bachelor s Degree from an accredited educational institution
SNOW LICENSE MANAGER (8.X)... 4
 SYSTEM REQUIREMENTS Products Snow License Manager Snow Automation Platform Snow Device Manager Snow Inventory Server, IDR, IDP Mobile Information Server Client for Windows Client for Unix Client for OS
SYSTEM REQUIREMENTS Products Snow License Manager Snow Automation Platform Snow Device Manager Snow Inventory Server, IDR, IDP Mobile Information Server Client for Windows Client for Unix Client for OS
Bypassing Network Access Control Systems
 Bypassing Network Access Control Systems Ofir Arkin Chief Technology Officer Insightix Ltd. September 2006 United States International 945 Concord Street 13 Hasadna Street Framingham, MA 01701 Ra'anana,
Bypassing Network Access Control Systems Ofir Arkin Chief Technology Officer Insightix Ltd. September 2006 United States International 945 Concord Street 13 Hasadna Street Framingham, MA 01701 Ra'anana,
SNOW LICENSE MANAGER (7.X)... 3
 SYSTEM REQUIREMENTS Products Snow License Manager Snow Automation Platform Snow Device Manager Snow Inventory Server, IDR, IDP Mobile Information Server Client for Windows Client for Linux Client for Unix
SYSTEM REQUIREMENTS Products Snow License Manager Snow Automation Platform Snow Device Manager Snow Inventory Server, IDR, IDP Mobile Information Server Client for Windows Client for Linux Client for Unix
Lecture 2. Internet: who talks with whom?
 Lecture 2. Internet: who talks with whom? An application layer view, with particular attention to the World Wide Web Basic scenario Internet Client (local PC) Server (remote host) Client wants to retrieve
Lecture 2. Internet: who talks with whom? An application layer view, with particular attention to the World Wide Web Basic scenario Internet Client (local PC) Server (remote host) Client wants to retrieve
Internet Information TE Services 5.0. Training Division, NIC New Delhi
 Internet Information TE Services 5.0 Training Division, NIC New Delhi Understanding the Web Technology IIS 5.0 Architecture IIS 5.0 Installation IIS 5.0 Administration IIS 5.0 Security Understanding The
Internet Information TE Services 5.0 Training Division, NIC New Delhi Understanding the Web Technology IIS 5.0 Architecture IIS 5.0 Installation IIS 5.0 Administration IIS 5.0 Security Understanding The
McAfee SECURE Technical White Paper
 Protect what you value. VERSION #1 093008 McAfee SECURE Technical White Paper Table of Contents Contnuous Security Auditing....................................................................... 2 Vulnerability
Protect what you value. VERSION #1 093008 McAfee SECURE Technical White Paper Table of Contents Contnuous Security Auditing....................................................................... 2 Vulnerability
SNOW LICENSE MANAGER (7.X)... 3
 SYSTEM REQUIREMENTS Products Snow License Manager Software Store Option Snow Inventory Server, IDR, IDP Client for Windows Client for Linux Client for Unix Client for OS X Oracle Scanner Snow Integration
SYSTEM REQUIREMENTS Products Snow License Manager Software Store Option Snow Inventory Server, IDR, IDP Client for Windows Client for Linux Client for Unix Client for OS X Oracle Scanner Snow Integration
Securing Your Network Environment. Software Distribution & Patch Management
 Securing Your Network Environment Software Distribution & Patch Management Ken Conrad Chief Strategist Microsoft Infrastructure Solutions Analysts International Overview Microsoft s s Patch Management
Securing Your Network Environment Software Distribution & Patch Management Ken Conrad Chief Strategist Microsoft Infrastructure Solutions Analysts International Overview Microsoft s s Patch Management
Nessus Cloud User Registration
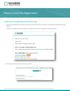 Nessus Cloud User Registration Create Your Tenable Nessus Cloud Account 1. Click on the provided URL to create your account. If the link does not work, please cut and paste the entire URL into your browser.
Nessus Cloud User Registration Create Your Tenable Nessus Cloud Account 1. Click on the provided URL to create your account. If the link does not work, please cut and paste the entire URL into your browser.
Reasons to choose Refresh Web Hosting
 Reasons to choose Refresh Web Hosting We believe that web hosting is more than just providing web space and FTP access. Our aim is to provide individuals and businesses with everything they need to express
Reasons to choose Refresh Web Hosting We believe that web hosting is more than just providing web space and FTP access. Our aim is to provide individuals and businesses with everything they need to express
2. Installing GFI LANguard Network Security Scanner
 2. Installing GFI LANguard Network Security Scanner System requirements Install GFI LANguard N.S.S on a computer that meets the following requirements: Windows 2000 (SP4), XP (SP2), 2003, 2008, VISTA (SP1),
2. Installing GFI LANguard Network Security Scanner System requirements Install GFI LANguard N.S.S on a computer that meets the following requirements: Windows 2000 (SP4), XP (SP2), 2003, 2008, VISTA (SP1),
Nessus Agents. October 2015
 Nessus Agents October 2015 Table of Contents Introduction... 3 What Are Nessus Agents?... 3 Scanning... 4 Results... 6 Conclusion... 6 About Tenable Network Security... 6 2 Introduction Today s changing
Nessus Agents October 2015 Table of Contents Introduction... 3 What Are Nessus Agents?... 3 Scanning... 4 Results... 6 Conclusion... 6 About Tenable Network Security... 6 2 Introduction Today s changing
Automated Patching. Paul Asadoorian IT Security Specialist Brown University
 Automated Patching Paul Asadoorian IT Security Specialist Brown University Outline Automated Patching Introduction Tools from Microsoft Microsoft SUS Microsoft SMS Others HFNetCheck Pro (Shavlik) Novell
Automated Patching Paul Asadoorian IT Security Specialist Brown University Outline Automated Patching Introduction Tools from Microsoft Microsoft SUS Microsoft SMS Others HFNetCheck Pro (Shavlik) Novell
Basic IPv6 WAN and LAN Configuration
 Basic IPv6 WAN and LAN Configuration This quick start guide provides basic IPv6 WAN and LAN configuration information for the ProSafe Wireless-N 8-Port Gigabit VPN Firewall FVS318N. For complete IPv6 configuration
Basic IPv6 WAN and LAN Configuration This quick start guide provides basic IPv6 WAN and LAN configuration information for the ProSafe Wireless-N 8-Port Gigabit VPN Firewall FVS318N. For complete IPv6 configuration
Medical Device Security Health Imaging Digital Capture. Security Assessment Report for the Kodak Medical Image Manager (MIM) Version 6.1.
 Medical Device Security Health Imaging Digital Capture Security Assessment Report for the Kodak Medical Image Manager (MIM) Version 6.1.1 Part Number 1G0119 Version 1.0 Eastman Kodak Company, Health Group
Medical Device Security Health Imaging Digital Capture Security Assessment Report for the Kodak Medical Image Manager (MIM) Version 6.1.1 Part Number 1G0119 Version 1.0 Eastman Kodak Company, Health Group
WiNG5 CAPTIVE PORTAL DESIGN GUIDE
 WiNG5 DESIGN GUIDE By Sriram Venkiteswaran WiNG5 CAPTIVE PORTAL DESIGN GUIDE June, 2011 TABLE OF CONTENTS HEADING STYLE Introduction To Captive Portal... 1 Overview... 1 Common Applications... 1 Authenticated
WiNG5 DESIGN GUIDE By Sriram Venkiteswaran WiNG5 CAPTIVE PORTAL DESIGN GUIDE June, 2011 TABLE OF CONTENTS HEADING STYLE Introduction To Captive Portal... 1 Overview... 1 Common Applications... 1 Authenticated
End-user Security Analytics Strengthens Protection with ArcSight
 Case Study for XY Bank End-user Security Analytics Strengthens Protection with ArcSight INTRODUCTION Detect and respond to advanced persistent threats (APT) in real-time with Nexthink End-user Security
Case Study for XY Bank End-user Security Analytics Strengthens Protection with ArcSight INTRODUCTION Detect and respond to advanced persistent threats (APT) in real-time with Nexthink End-user Security
6 reasons to choose us for your web hosting
 Web Hosting We believe that web hosting is more than just providing web space and FTP access. Our aim is to provide individuals and businesses with everything they need to express themselves on the internet,
Web Hosting We believe that web hosting is more than just providing web space and FTP access. Our aim is to provide individuals and businesses with everything they need to express themselves on the internet,
AVeS Cloud Security powered by SYMANTEC TM
 Protecting your business from online threats should be simple, yet powerful and effective. A solution that secures your laptops, desktops, and servers without slowing down your systems and distracting
Protecting your business from online threats should be simple, yet powerful and effective. A solution that secures your laptops, desktops, and servers without slowing down your systems and distracting
Red Hat Network: Monitoring Module Overview
 Red Hat Network: Monitoring Module Overview Red Hat has built the next generation of systems management software presenting both highgrowth businesses and service providers with a simple, scalable and
Red Hat Network: Monitoring Module Overview Red Hat has built the next generation of systems management software presenting both highgrowth businesses and service providers with a simple, scalable and
OPEN FOR EDUCATION. CampusNet - Managed Hosting services for Higher Education
 OPEN FOR EDUCATION CampusNet - Managed services for Higher Education The partnership with CampusNet provides ForeFront Education with a fullservice hosting environment complete with staff who have product
OPEN FOR EDUCATION CampusNet - Managed services for Higher Education The partnership with CampusNet provides ForeFront Education with a fullservice hosting environment complete with staff who have product
Vulnerability Assessment. A. Open Vulnerability Assessment (OpenVAS)
 Vulnerability Assessment After target discovery and enumeration, the next step is identifying critical security vulnerabilities in the target systems. Vulnerability assessment depends on the type and OS
Vulnerability Assessment After target discovery and enumeration, the next step is identifying critical security vulnerabilities in the target systems. Vulnerability assessment depends on the type and OS
Patch Management Marvin Christensen /CIAC
 Patch Management Marvin Christensen /CIAC US DOE Cyber Security Group 2004 Training Conference May 26, 2004 Management Track 11:00 am 11:45 pm UCRL-CONF-204220 CIAC 04-099 This work was performed under
Patch Management Marvin Christensen /CIAC US DOE Cyber Security Group 2004 Training Conference May 26, 2004 Management Track 11:00 am 11:45 pm UCRL-CONF-204220 CIAC 04-099 This work was performed under
Connecticut Justice Information System Security Compliance Assessment Form
 The Connecticut Justice Information System (CJIS-2) is used as a mechanism for municipalities, State and Federal agencies to assess their compliance with the CJIS Security Requirements & Recommendations
The Connecticut Justice Information System (CJIS-2) is used as a mechanism for municipalities, State and Federal agencies to assess their compliance with the CJIS Security Requirements & Recommendations
Modified Reverse Proxy Website Vulnerability Test Results
 Modified Reverse Proxy Website Vulnerability Test Results Vincent Berk and Marion Bates Institute for Security Technology Studies Dartmouth College September 10, 2001 Contents 1 Introduction 1 2 Preparation
Modified Reverse Proxy Website Vulnerability Test Results Vincent Berk and Marion Bates Institute for Security Technology Studies Dartmouth College September 10, 2001 Contents 1 Introduction 1 2 Preparation
Web Application Vulnerability Testing with Nessus
 The OWASP Foundation http://www.owasp.org Web Application Vulnerability Testing with Nessus Rïk A. Jones, CISSP rikjones@computer.org Rïk A. Jones Web developer since 1995 (16+ years) Involved with information
The OWASP Foundation http://www.owasp.org Web Application Vulnerability Testing with Nessus Rïk A. Jones, CISSP rikjones@computer.org Rïk A. Jones Web developer since 1995 (16+ years) Involved with information
E-Commerce for IT Advanced. Louis Aguila & Matt Burt
 Advanced Louis Aguila & Matt Burt Class Objectives To explore Microsoft Internet Information Services (IIS) use and troubleshooting Basic E-Commerce site setup in IIS Use of Application Pools and settings
Advanced Louis Aguila & Matt Burt Class Objectives To explore Microsoft Internet Information Services (IIS) use and troubleshooting Basic E-Commerce site setup in IIS Use of Application Pools and settings
Managed Services Agreement. Hilliard Office Solutions, Ltd. PO Box 52510 Phone: 432-617-4677 Midland, Texas 79710 Fax: 432-617-3043
 Managed Services Agreement Hilliard Office Solutions, Ltd. PO Box 52510 Phone: 432-617-4677 Midland, Texas 79710 Fax: 432-617-3043 SERVICE DESCRIPTIONS By purchasing these Services from Hilliard Office
Managed Services Agreement Hilliard Office Solutions, Ltd. PO Box 52510 Phone: 432-617-4677 Midland, Texas 79710 Fax: 432-617-3043 SERVICE DESCRIPTIONS By purchasing these Services from Hilliard Office
Medical Device Security Health Imaging Digital Capture. Security Assessment Report for the Kodak DryView 8150 Imager Release 1.0.
 Medical Device Security Health Imaging Digital Capture Security Assessment Report for the Kodak DryView 8150 Imager Release 1.0 Page 1 of 9 Table of Contents Table of Contents... 2 Executive Summary...
Medical Device Security Health Imaging Digital Capture Security Assessment Report for the Kodak DryView 8150 Imager Release 1.0 Page 1 of 9 Table of Contents Table of Contents... 2 Executive Summary...
University Systems Desktop Support Service Level Commitment
 University Systems Desktop Support Service Level Commitment The Purpose of this Service Level Commitment (SLC) is to formally define the level of service University Systems will provide to UVic faculty,
University Systems Desktop Support Service Level Commitment The Purpose of this Service Level Commitment (SLC) is to formally define the level of service University Systems will provide to UVic faculty,
Vulnerability management lifecycle: defining vulnerability management
 Framework for building a vulnerability management lifecycle program http://searchsecurity.techtarget.com/magazinecontent/framework-for-building-avulnerability-management-lifecycle-program August 2011 By
Framework for building a vulnerability management lifecycle program http://searchsecurity.techtarget.com/magazinecontent/framework-for-building-avulnerability-management-lifecycle-program August 2011 By
Choosing the Right Web Host
 out of this world guide to: Web Hosting We believe that web hosting is more than just providing web space and FTP access. Our aim is to provide individuals and businesses with everything they need to express
out of this world guide to: Web Hosting We believe that web hosting is more than just providing web space and FTP access. Our aim is to provide individuals and businesses with everything they need to express
Medical Device Security Health Imaging Digital Capture. Security Assessment Report for the Kodak DR V2.0
 Medical Device Security Health Imaging Digital Capture Security Assessment Report for the Kodak DR V2.0 Version 1.0 Eastman Kodak Company, Health Imaging Group Page 1 Table of Contents Table of Contents
Medical Device Security Health Imaging Digital Capture Security Assessment Report for the Kodak DR V2.0 Version 1.0 Eastman Kodak Company, Health Imaging Group Page 1 Table of Contents Table of Contents
8 Steps for Network Security Protection
 8 Steps for Network Security Protection cognoscape.com 8 Steps for Network Security Protection Many small and medium sized businesses make the mistake of thinking they won t be the target of hackers because
8 Steps for Network Security Protection cognoscape.com 8 Steps for Network Security Protection Many small and medium sized businesses make the mistake of thinking they won t be the target of hackers because
ANNEXURE-1 TO THE TENDER ENQUIRY NO.: DPS/AMPU/MIC/1896. Network Security Software Nessus- Technical Details
 Sub: Supply, Installation, setup and testing of Tenable Network Security Nessus vulnerability scanner professional version 6 or latest for scanning the LAN, VLAN, VPN and IPs with 3 years License/Subscription
Sub: Supply, Installation, setup and testing of Tenable Network Security Nessus vulnerability scanner professional version 6 or latest for scanning the LAN, VLAN, VPN and IPs with 3 years License/Subscription
8 Steps For Network Security Protection
 8 Steps For Network Security Protection 8 Steps For Network Security Protection Many small and medium sized businesses make the mistake of thinking they won t be the target of hackers because of their
8 Steps For Network Security Protection 8 Steps For Network Security Protection Many small and medium sized businesses make the mistake of thinking they won t be the target of hackers because of their
Windows Security. Introduction. Topics. Loughborough University. Janet Web Cache Service. Matthew Cook http://escarpment.net/
 Windows Security Matthew Cook http://escarpment.net/ Introduction Loughborough University http://www.lboro.ac.uk/computing/ Janet Web Cache Service http://wwwcache.ja.net/ Bandwidth Management Advisory
Windows Security Matthew Cook http://escarpment.net/ Introduction Loughborough University http://www.lboro.ac.uk/computing/ Janet Web Cache Service http://wwwcache.ja.net/ Bandwidth Management Advisory
Component Details Notes Tested. The virtualization host is a windows 2008 R2 Hyper-V server. Yes
 We will be reviewing Microsoft s Remote Desktop Services (RDS), which has undergone significant reworking since it was released as Windows 2008 Terminal Services. In the original release of Microsoft Windows
We will be reviewing Microsoft s Remote Desktop Services (RDS), which has undergone significant reworking since it was released as Windows 2008 Terminal Services. In the original release of Microsoft Windows
Security Consultant Scenario INFO 517-900 Term Project. Brad S. Brady. Drexel University
 Security Consultant Scenario INFO 517-900 Term Project Drexel University Author Note This paper was prepared for INFO-517-900 taught by Dr. Scott White. Table of Contents ABSTRACT.1 THE INTERVIEW...2 THE
Security Consultant Scenario INFO 517-900 Term Project Drexel University Author Note This paper was prepared for INFO-517-900 taught by Dr. Scott White. Table of Contents ABSTRACT.1 THE INTERVIEW...2 THE
eeye Digital Security Product Training
 eeye Digital Security Product Training Retina CS for System Administration (4MD) This hands-on instructor led course provides security system administration/analysts with the skills and knowledge necessary
eeye Digital Security Product Training Retina CS for System Administration (4MD) This hands-on instructor led course provides security system administration/analysts with the skills and knowledge necessary
A Network Administrator s Guide to Web App Security
 A Network Administrator s Guide to Web App Security Speaker: Orion Cassetto, Product Marketing Manager, Incapsula Moderator: Rich Nass, OpenSystems Media Agenda Housekeeping Presentation Questions and
A Network Administrator s Guide to Web App Security Speaker: Orion Cassetto, Product Marketing Manager, Incapsula Moderator: Rich Nass, OpenSystems Media Agenda Housekeeping Presentation Questions and
Internet. User guide
 Internet User guide 2014-2015 1 TM Contents 1 2 3 4 5 6 7 8 9 10 11 Setting up your Internet Connecting Ethernet setup Wireless setup Registering Adding a device that has a Web browser Adding a device
Internet User guide 2014-2015 1 TM Contents 1 2 3 4 5 6 7 8 9 10 11 Setting up your Internet Connecting Ethernet setup Wireless setup Registering Adding a device that has a Web browser Adding a device
60467 Project 1. Net Vulnerabilities scans and attacks. Chun Li
 60467 Project 1 Net Vulnerabilities scans and attacks Chun Li Hardware used: Desktop PC: Windows Vista service pack Service Pack 2 v113 Intel Core 2 Duo 3GHz CPU, 4GB Ram, D-Link DWA-552 XtremeN Desktop
60467 Project 1 Net Vulnerabilities scans and attacks Chun Li Hardware used: Desktop PC: Windows Vista service pack Service Pack 2 v113 Intel Core 2 Duo 3GHz CPU, 4GB Ram, D-Link DWA-552 XtremeN Desktop
A Windows Desktop Security Primer
 A Windows Desktop Security Primer ITSS Technical Briefing Jay Stamps, ITSS, jstamps@stanford.edu, 723-0018 Turing Auditorium, May 20, 2005 Topics for the Afternoon Windows XP Professional Security Setting
A Windows Desktop Security Primer ITSS Technical Briefing Jay Stamps, ITSS, jstamps@stanford.edu, 723-0018 Turing Auditorium, May 20, 2005 Topics for the Afternoon Windows XP Professional Security Setting
White Paper. McAfee Web Security Service Technical White Paper
 McAfee Web Security Service Technical White Paper Effective Management of Anti-Virus and Security Solutions for Smaller Businesses Continaul Security Auditing Vulnerability Knowledge Base Vulnerability
McAfee Web Security Service Technical White Paper Effective Management of Anti-Virus and Security Solutions for Smaller Businesses Continaul Security Auditing Vulnerability Knowledge Base Vulnerability
Penetration Testing. NTS330 Unit 1 Penetration V1.0. February 20, 2011. Juan Ortega. Juan Ortega, juaorteg@uat.edu. 1 Juan Ortega, juaorteg@uat.
 1 Penetration Testing NTS330 Unit 1 Penetration V1.0 February 20, 2011 Juan Ortega Juan Ortega, juaorteg@uat.edu 1 Juan Ortega, juaorteg@uat.edu 2 Document Properties Title Version V1.0 Author Pen-testers
1 Penetration Testing NTS330 Unit 1 Penetration V1.0 February 20, 2011 Juan Ortega Juan Ortega, juaorteg@uat.edu 1 Juan Ortega, juaorteg@uat.edu 2 Document Properties Title Version V1.0 Author Pen-testers
Tenable Tools for Security Compliance The Antivirus Challenge
 Tenable Tools for Security Compliance The Antivirus Challenge January 20, 2005 (Updated February 7, 2007) Nicolas Pouvesl e / John Lampe Table of Contents TABLE OF CONTENTS... 2 INTRODUCTION... 3 WHAT
Tenable Tools for Security Compliance The Antivirus Challenge January 20, 2005 (Updated February 7, 2007) Nicolas Pouvesl e / John Lampe Table of Contents TABLE OF CONTENTS... 2 INTRODUCTION... 3 WHAT
Course: Information Security Management in e-governance. Day 1. Session 5: Securing Data and Operating systems
 Course: Information Security Management in e-governance Day 1 Session 5: Securing Data and Operating systems Agenda Introduction to information, data and database systems Information security risks surrounding
Course: Information Security Management in e-governance Day 1 Session 5: Securing Data and Operating systems Agenda Introduction to information, data and database systems Information security risks surrounding
ITEC 495 Capstone Project Ideas
 ITEC 495 Capstone Project Ideas Open Source Content Filtering OpenDNS A 25 person architectural firm with one single location needs to implement a low cost, secure, easy to deploy and administer web content
ITEC 495 Capstone Project Ideas Open Source Content Filtering OpenDNS A 25 person architectural firm with one single location needs to implement a low cost, secure, easy to deploy and administer web content
Avira Endpoint and Email Security. HowTo
 Avira Endpoint and Email Security HowTo Table of contents 1. Introduction... 3 2. Product Information... 3 2.1 Operation mode... 3 2.2 Scope of services... 3 2.3 Optimum protection. Fast updates. Efficient
Avira Endpoint and Email Security HowTo Table of contents 1. Introduction... 3 2. Product Information... 3 2.1 Operation mode... 3 2.2 Scope of services... 3 2.3 Optimum protection. Fast updates. Efficient
CLEARPASS ONGUARD CONFIGURATION GUIDE
 CONFIGURATION GUIDE REVISION HISTORY Revised By Date Changes Dennis Boas July 2015 Version 1 initial release TABLE OF CONTENTS... 1 INTRODUCTION... 3 CONFIGURATION WORKFLOW... 4 CONFIGURE POSTURE POLICIES...
CONFIGURATION GUIDE REVISION HISTORY Revised By Date Changes Dennis Boas July 2015 Version 1 initial release TABLE OF CONTENTS... 1 INTRODUCTION... 3 CONFIGURATION WORKFLOW... 4 CONFIGURE POSTURE POLICIES...
Medical Device Security Health Imaging Digital Capture. Security Assessment Report for the Kodak Capture Link Server V1.00
 Medical Device Security Health Imaging Digital Capture Security Assessment Report for the Kodak Capture Link Server V1.00 Version 1.0 Eastman Kodak Company, Health Imaging Group Page 1 Table of Contents
Medical Device Security Health Imaging Digital Capture Security Assessment Report for the Kodak Capture Link Server V1.00 Version 1.0 Eastman Kodak Company, Health Imaging Group Page 1 Table of Contents
How to Set Up Automatic Subnet Scan Using SolarWinds IP Address Manager. Share:
 How to Set Up Automatic Subnet Scan Using SolarWinds IP Address Manager Share: How to Set Up Automatic Subnet Scan Using SolarWinds IPAM? SolarWinds IP Address Manager (IPAM) allows you to perform scheduled
How to Set Up Automatic Subnet Scan Using SolarWinds IP Address Manager Share: How to Set Up Automatic Subnet Scan Using SolarWinds IPAM? SolarWinds IP Address Manager (IPAM) allows you to perform scheduled
VULNERABILITY ASSESSMENT WHITEPAPER INTRODUCTION, IMPLEMENTATION AND TECHNOLOGY DISCUSSION
 VULNERABILITY ASSESSMENT WHITEPAPER INTRODUCTION, IMPLEMENTATION AND TECHNOLOGY DISCUSSION copyright 2003 securitymetrics Security Vulnerabilities of Computers & Servers Security Risks Change Daily New
VULNERABILITY ASSESSMENT WHITEPAPER INTRODUCTION, IMPLEMENTATION AND TECHNOLOGY DISCUSSION copyright 2003 securitymetrics Security Vulnerabilities of Computers & Servers Security Risks Change Daily New
Security Module v2.0. White Paper. April 2011
 Security Module v2.0 White Paper April 2011 Security Module: Comprehensive Security for CareFusion Products Overview CareFusion offers a comprehensive security technology solution for products running
Security Module v2.0 White Paper April 2011 Security Module: Comprehensive Security for CareFusion Products Overview CareFusion offers a comprehensive security technology solution for products running
Medical Device Security Health Imaging Digital Capture. Security Assessment Report for the Kodak CR V4.1
 Medical Device Security Health Imaging Digital Capture Security Assessment Report for the Kodak CR V4.1 Version 1.0 Eastman Kodak Company, Health Imaging Group Page 1 Table of Contents Table of Contents
Medical Device Security Health Imaging Digital Capture Security Assessment Report for the Kodak CR V4.1 Version 1.0 Eastman Kodak Company, Health Imaging Group Page 1 Table of Contents Table of Contents
Countermeasures against Bots
 Countermeasures against Bots Are you sure your computer is not infected with Bot? Information-technology Promotion Agency IT Security Center http://www.ipa.go.jp/security/ 1. What is a Bot? Bot is a computer
Countermeasures against Bots Are you sure your computer is not infected with Bot? Information-technology Promotion Agency IT Security Center http://www.ipa.go.jp/security/ 1. What is a Bot? Bot is a computer
Using Nessus In Web Application Vulnerability Assessments
 Using Nessus In Web Application Vulnerability Assessments Paul Asadoorian Product Evangelist Tenable Network Security pasadoorian@tenablesecurity.com About Tenable Nessus vulnerability scanner, ProfessionalFeed
Using Nessus In Web Application Vulnerability Assessments Paul Asadoorian Product Evangelist Tenable Network Security pasadoorian@tenablesecurity.com About Tenable Nessus vulnerability scanner, ProfessionalFeed
TIME TO LIVE ON THE NETWORK
 TIME TO LIVE ON THE NETWORK Executive Summary This experiment tests to see how well commonly used computer platforms withstand Internet attacks in the wild. The experiment quantifies the amount of time
TIME TO LIVE ON THE NETWORK Executive Summary This experiment tests to see how well commonly used computer platforms withstand Internet attacks in the wild. The experiment quantifies the amount of time
Application Security Best Practices. Wally LEE <wally.lee@scs.com.sg> Principal Consultant
 Application Security Best Practices Wally LEE Principal Consultant 17/18 March 2009 Speaker Profile Wally LEE CISSP BS7799 Lead Auditor Certified Ultimate Hacking Instructor Certified
Application Security Best Practices Wally LEE Principal Consultant 17/18 March 2009 Speaker Profile Wally LEE CISSP BS7799 Lead Auditor Certified Ultimate Hacking Instructor Certified
Installing The SysAidTM Server Locally
 Installing The SysAidTM Server Locally Document Updated: 17 October 2010 Introduction SysAid is available in two editions: a fully on-demand ASP solution and an installed, in-house solution for your server.
Installing The SysAidTM Server Locally Document Updated: 17 October 2010 Introduction SysAid is available in two editions: a fully on-demand ASP solution and an installed, in-house solution for your server.
SNOW LICENSE MANAGER (7.X)... 3
 SYSTEM REQUIREMENTS Products Snow License Manager Snow Inventory Server, IDR, IDP Client for Windows Client for Linux Client for Unix Client for OS X Oracle Scanner External Data Provider Snow Distribution
SYSTEM REQUIREMENTS Products Snow License Manager Snow Inventory Server, IDR, IDP Client for Windows Client for Linux Client for Unix Client for OS X Oracle Scanner External Data Provider Snow Distribution
Secret Server Qualys Integration Guide
 Secret Server Qualys Integration Guide Table of Contents Secret Server and Qualys Cloud Platform... 2 Authenticated vs. Unauthenticated Scanning... 2 What are the Advantages?... 2 Integrating Secret Server
Secret Server Qualys Integration Guide Table of Contents Secret Server and Qualys Cloud Platform... 2 Authenticated vs. Unauthenticated Scanning... 2 What are the Advantages?... 2 Integrating Secret Server
Deep Security Vulnerability Protection Summary
 Deep Security Vulnerability Protection Summary Trend Micro, Incorporated This documents outlines the process behind rules creation and answers common questions about vulnerability coverage for Deep Security
Deep Security Vulnerability Protection Summary Trend Micro, Incorporated This documents outlines the process behind rules creation and answers common questions about vulnerability coverage for Deep Security
Case Study. SaaS Based Multi-Store Market Place. www.brainvire.com 2013 Brainvire Infotech Pvt. Ltd Page 1 of 5
 Case Study SaaS Based Multi-Store Market Place Page 1 of 5 Client Requirement Magento Multi-Store Ecommerce Management is a web based virtual mall. It s an e- commerce virtual mall cum SaaS based model
Case Study SaaS Based Multi-Store Market Place Page 1 of 5 Client Requirement Magento Multi-Store Ecommerce Management is a web based virtual mall. It s an e- commerce virtual mall cum SaaS based model
Network Access Security It's Broke, Now What? June 15, 2010
 Network Access Security It's Broke, Now What? June 15, 2010 Jeffrey L Carrell Network Security Consultant Network Conversions SHARKFEST 10 Stanford University June 14-17, 2010 Network Access Security It's
Network Access Security It's Broke, Now What? June 15, 2010 Jeffrey L Carrell Network Security Consultant Network Conversions SHARKFEST 10 Stanford University June 14-17, 2010 Network Access Security It's
TECHNICAL VULNERABILITY & PATCH MANAGEMENT
 INFORMATION SECURITY POLICY TECHNICAL VULNERABILITY & PATCH MANAGEMENT ISO 27002 12.6.1 Author: Owner: Organisation: Document No: Chris Stone Ruskwig TruePersona Ltd SP-12.6.1 Version No: 1.1 Date: 1 st
INFORMATION SECURITY POLICY TECHNICAL VULNERABILITY & PATCH MANAGEMENT ISO 27002 12.6.1 Author: Owner: Organisation: Document No: Chris Stone Ruskwig TruePersona Ltd SP-12.6.1 Version No: 1.1 Date: 1 st
PRICE LIST. Purchasing Initial License Additional Licenses. Subscription
 PRICE LIST as of 1 st January 2011 all prices are subject to VAT @ 20% Purchasing Initial License Additional Licenses COv4 Startup Edition 150 n/a COv4 Professional Edition 450 150 COv4 Server Edition
PRICE LIST as of 1 st January 2011 all prices are subject to VAT @ 20% Purchasing Initial License Additional Licenses COv4 Startup Edition 150 n/a COv4 Professional Edition 450 150 COv4 Server Edition
Towards End-to-End Security
 Towards End-to-End Security Thomas M. Chen Dept. of Electrical Engineering Southern Methodist University PO Box 750338 Dallas, TX 75275-0338 USA Tel: 214-768-8541 Fax: 214-768-3573 Email: tchen@engr.smu.edu
Towards End-to-End Security Thomas M. Chen Dept. of Electrical Engineering Southern Methodist University PO Box 750338 Dallas, TX 75275-0338 USA Tel: 214-768-8541 Fax: 214-768-3573 Email: tchen@engr.smu.edu
Agilent Technologies Electronic Measurements Group Computer Virus Control Program
 Agilent Technologies Electronic Measurements Group Computer Virus Control Program Agilent Technologies Electronic Measurements Group (EMG) recognizes the potential risk of computer virus infection that
Agilent Technologies Electronic Measurements Group Computer Virus Control Program Agilent Technologies Electronic Measurements Group (EMG) recognizes the potential risk of computer virus infection that
Sygate Secure Enterprise and Alcatel
 Sygate Secure Enterprise and Alcatel Sygate Secure Enterprise eliminates the damage or loss of information, cost of recovery, and regulatory violation due to rogue corporate computers, applications, and
Sygate Secure Enterprise and Alcatel Sygate Secure Enterprise eliminates the damage or loss of information, cost of recovery, and regulatory violation due to rogue corporate computers, applications, and
THREAT VISIBILITY & VULNERABILITY ASSESSMENT
 THREAT VISIBILITY & VULNERABILITY ASSESSMENT Date: April 15, 2015 IKANOW Analysts: Casey Pence IKANOW Platform Build: 1.34 11921 Freedom Drive, Reston, VA 20190 IKANOW.com TABLE OF CONTENTS 1 Key Findings
THREAT VISIBILITY & VULNERABILITY ASSESSMENT Date: April 15, 2015 IKANOW Analysts: Casey Pence IKANOW Platform Build: 1.34 11921 Freedom Drive, Reston, VA 20190 IKANOW.com TABLE OF CONTENTS 1 Key Findings
Contact details For contacting ENISA or for general enquiries on information security awareness matters, please use the following details:
 Malicious software About ENISA The European Network and Information Security Agency (ENISA) is an EU agency created to advance the functioning of the internal market. ENISA is a centre of excellence for
Malicious software About ENISA The European Network and Information Security Agency (ENISA) is an EU agency created to advance the functioning of the internal market. ENISA is a centre of excellence for
E-MAIL AND SERVER SECURITY
 E-MAIL AND SERVER SECURITY DEPLOYMENT GUIDE 1 E-MAIL AND SERVER SECURITY Deployment Guide 2 CONTENTS 1. Overview 3 1.1 How the product works 3 1.2 Product contents 4 2. Deployment scenarios 5 2.1 Stand-alone
E-MAIL AND SERVER SECURITY DEPLOYMENT GUIDE 1 E-MAIL AND SERVER SECURITY Deployment Guide 2 CONTENTS 1. Overview 3 1.1 How the product works 3 1.2 Product contents 4 2. Deployment scenarios 5 2.1 Stand-alone
E-MAIL AND SERVER SECURITY
 E-MAIL AND SERVER SECURITY DEPLOYMENT GUIDE 1 E-MAIL AND SERVER SECURITY Deployment Guide 2 CONTENTS 1. Overview 3 2. Deployment scenarios 5 2.1 Stand-alone server 5 2.2 Deploying the product with F-Secure
E-MAIL AND SERVER SECURITY DEPLOYMENT GUIDE 1 E-MAIL AND SERVER SECURITY Deployment Guide 2 CONTENTS 1. Overview 3 2. Deployment scenarios 5 2.1 Stand-alone server 5 2.2 Deploying the product with F-Secure
Self Service Penetration Testing
 Self Service Penetration Testing Matthew Cook http://escarpment.net/ Introduction Matthew Cook Senior IT Security Specialist Loughborough University Computing Services http://escarpment.net/ Self Service
Self Service Penetration Testing Matthew Cook http://escarpment.net/ Introduction Matthew Cook Senior IT Security Specialist Loughborough University Computing Services http://escarpment.net/ Self Service
ALTIRIS Patch Management Solution 6.2 for Windows Help
 ALTIRIS Patch Management Solution 6.2 for Windows Help Notice Altiris Patch Management Solution 6.2 2001-2006 Altiris, Inc. All rights reserved. Document Date: February 13, 2007 Protected by one or more
ALTIRIS Patch Management Solution 6.2 for Windows Help Notice Altiris Patch Management Solution 6.2 2001-2006 Altiris, Inc. All rights reserved. Document Date: February 13, 2007 Protected by one or more
ZENworks 11 Support Pack 4 Management Zone Settings Reference. May 2016
 ZENworks 11 Support Pack 4 Management Zone Settings Reference May 2016 Legal Notices For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government
ZENworks 11 Support Pack 4 Management Zone Settings Reference May 2016 Legal Notices For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government
Customer Tips. Configuration and Use of the MeterAssistant Option. for the user. Purpose. Xerox Device Configuration. Xerox Multifunction Devices
 Xerox Multifunction Devices Customer Tips June 21, 2006 This document applies to the Xerox products This indicated document in the applies table to below. these For Xerox some products: products, it is
Xerox Multifunction Devices Customer Tips June 21, 2006 This document applies to the Xerox products This indicated document in the applies table to below. these For Xerox some products: products, it is
Vulnerability analysis
 Vulnerability analysis License This work by Z. Cliffe Schreuders at Leeds Metropolitan University is licensed under a Creative Commons Attribution-ShareAlike 3.0 Unported License. Contents License Contents
Vulnerability analysis License This work by Z. Cliffe Schreuders at Leeds Metropolitan University is licensed under a Creative Commons Attribution-ShareAlike 3.0 Unported License. Contents License Contents
Microsoft Windows Apple Mac OS X
 Products Snow License Manager Snow Inventory Server, IDP, IDR Client for Windows Client for OS X Client for Linux Client for Unix Oracle Scanner External Data Provider Snow Distribution Date 2014-04-02
Products Snow License Manager Snow Inventory Server, IDP, IDR Client for Windows Client for OS X Client for Linux Client for Unix Oracle Scanner External Data Provider Snow Distribution Date 2014-04-02
How to scan/exploit a ssl based webserver. by xxradar. http://www.radarhack.com mailto:xxradar@radarhack.com. Version 1.
 How to scan/exploit a ssl based webserver. by xxradar. http://www.radarhack.com mailto:xxradar@radarhack.com. Version 1.0 21-09-2003 1. Introduction Sometimes late at night, playing with openssl and connecting
How to scan/exploit a ssl based webserver. by xxradar. http://www.radarhack.com mailto:xxradar@radarhack.com. Version 1.0 21-09-2003 1. Introduction Sometimes late at night, playing with openssl and connecting
