Security Module v2.0. White Paper. April 2011
|
|
|
- Marcus Morris
- 8 years ago
- Views:
Transcription
1 Security Module v2.0 White Paper April 2011
2 Security Module: Comprehensive Security for CareFusion Products Overview CareFusion offers a comprehensive security technology solution for products running Microsoft Windows 2000 operating system or greater. Security Module is a complementary software offering that incorporates advanced security patch update mechanisms, virus protection tools, local reporting, and secure remote access through CareFusion Remote Support Services, which allows CareFusion to diagnose and potentially resolve security issues remotely. Features of Security Module v2.0 include: Industry-standard patch management using Microsoft Windows Server Update Services (WSUS v3.0 SP2). Virus protection with Symantec Endpoint Protection (SEP). Manage automatic updates of virus definitions for CareFusion products leveraging SEP v11.0. Rapid patch deployment through CareFusion Enterprise Security Services, allowing patches to be quickly and securely deployed to end devices upon certification. End-user Reports provide ability to view patch deployment status, compliance, and exception management. Deployment options allow Security Module v2.0 software to be deployed on customer-owned VMware infrastructure or on customer hardware that meets the minimum specification. Domain and Active Directory integration allow customer IT to effectively manage Security Module services. Secure Connectivity through CareFusion Remote Support Services. Benefits of Security Module v2.0 include: Improving patch deployment efficiency through simplification and automation of key aspects of the patch management process. With Security Module v2.0, manual patch distribution to each device is eliminated because patches are now automatically deployed through connectivity to CareFusion Enterprise Security Services. Promoting a timely, reliable, and consistent patch management solution across singleor multi-facility hospital environments. Local reporting capabilities provide easy access to critical compliance information. Security Module v2.0 provides extensive reporting capabilities that provide IT/Security personnel with the information necessary for adherence to security policies and HIPAA regulations that require a safeguard against security threats. CareFusion Page 2 of 6 April 4, 2011
3 Architecture The following figure shows the Security Module in relation to CareFusion services and devices. Relation of Security Module to CareFusion services and devices Windows Server Update Services (WSUS) 1. Every month, a list of approved patches is generated by CareFusion. This list is distributed to the field and can be communicated to customers who want to be notified of patches that have been released. 2. Approved patch metadata are deployed onto the CareFusion Enterprise Security Services servers. 3. On a predetermined schedule, Security Module servers located within the hospital firewall (local) request updates from the Enterprise servers. If new metadata exist, the data are downloaded to the local server. 4. Upon successful receipt, the local server requests the approved patches from the Microsoft Windows Update Services. 5. Upon successful download of the patches, the local server establishes connectivity to appropriate devices (for example, Pyxis MedStation system, Pyxis SupplyStation CareFusion Page 3 of 6 April 4, 2011
4 system, Pyxis Procar, and so on) and, based on the device settings, automatically deploys the appropriate patches and reboots the device (if required). NOTE: Because this release introduces automated patch delivery, it is critical that device configurations are agreed upon by the customer before installing Security Module v2.0. Symantec Endpoint Protection The Symantec Endpoint Protection (SEP) component of the Security Module is a completely automated process that does not require field or customer involvement. The Security Module server checks with Symantec LiveUpdate server every 4 hours for updated virus definitions. Clients are monitored by an AutoProtect system that checks every file as it is accessed, and clients are also configured to receive a full system scan once a week. If the facility uses a SEP Server, adding approved CareFusion products to the client s server in order to receive the updated definition files can be supported. Symantec is the only virus protection solution that is tested and verified for use with all Pyxis products. Security Module v2.0 patch cycle: In response to Microsoft security bulletins, and to subsequent security and critical updates, CareFusion has the following process to address the communication of vulnerabilities and security patch management of supported CareFusion products. Initialize Microsoft Security and Critical Updates are released on the second Tuesday of each month. Identification All updates as released by Microsoft are selected for installation on the WSUS server in the CareFusion testing facility, and their applicability to CareFusion products will be determined using the Windows Update Agent inherent with each device. Assessment and prioritization Once the results are obtained, CareFusion reviews the results for each product regarding applicability, severity, and likelihood of exploitation. The results determine if additional information or testing is necessary, or if any special mitigating circumstances need to be considered. The results are presented in the Security Bulletins that outline each of the vulnerabilities and the associated risks to the products. Testing and certifying patches Applicable updates are tested for integrity and system compatibility on CareFusion products by CareFusion to ensure that the patches do not break or alter the product functionality. Approval notification and distribution Upon approval of the patches, the appropriate Field Service teams are notified that patches have been approved and will be automatically deployed to customers with Security Module v2.0. Customers running Security Module v1.x will continue to execute the manual patch deployment and installation process. CareFusion Page 4 of 6 April 4, 2011
5 Customer requirements System requirements Customer VMware infrastructure - Processor: 2 vcpu (reservation not required) - Memory: 2 GB (reservation not required) - Storage: 150 GB (thick or thin provisioning) Customer hardware (bare metal) - Processor: 1 CPU (2 GHz) - Memory: 2 GB - Storage: 150 GB (RAID1 or RAID5) Environment requirements A preinstallation questionnaire was designed to help CareFusion obtain all necessary technical information and allow for proper planning and successful installation of the Security Module. The form helps ensure the availability of the following: Hospital-assigned static IP address, subnet mask, and gateway information. Hospital DNS primary and secondary IP addresses. WINS server addresses (optional). TCP ports 80, 443, and 8014 communications to all CareFusion devices. TCP ports 80 and 443 outbound to the Internet If a facility intends to share one Security Module among several sites, consider the following factors: Sufficient network bandwidth. Administrative infrastructure and ownership. A route between networks needs to be available if the branch offices of the IDN are on separate networks. Following the vendor specifications, a theoretical limit of 1,500 devices per server can be supported. For further information, contact your Account Executive or Customer Service Manager. CareFusion Professional Services provides this document for use as a general resource only. Anyone using this document should determine whether it is compatible with applicable state laws, regulations, professional practice guidelines, and accreditation standards. Use of this document should be at all times governed by professional judgment of the user. CareFusion Page 5 of 6 April 4, 2011
6 CareFusion, Pyxis, MedStation, SupplyStation and the CareFusion logo are trademarks or registered trademarks of CareFusion Corporation or one of its subsidiaries. All other trademarks are the property of their respective owners CareFusion Corporation or one of its subsidiaries. All rights reserved. CareFusion Page 6 of 6 April 4, 2011
Microsoft Software Update Services and Managed Symantec Anti-virus. Michael Satut TSS/Crown IT Support m-satut@northwestern.edu
 Microsoft Software Update Services and Managed Symantec Anti-virus Michael Satut TSS/Crown IT Support m-satut@northwestern.edu Introduction The recent increase in virus and worm activity has created the
Microsoft Software Update Services and Managed Symantec Anti-virus Michael Satut TSS/Crown IT Support m-satut@northwestern.edu Introduction The recent increase in virus and worm activity has created the
Barracuda Message Archiver Vx Deployment. Whitepaper
 Barracuda Message Archiver Vx Deployment Whitepaper Document Scope This document provides guidance on designing and deploying Barracuda Message Archiver Vx on VMware vsphere Document Scope, and Microsoft
Barracuda Message Archiver Vx Deployment Whitepaper Document Scope This document provides guidance on designing and deploying Barracuda Message Archiver Vx on VMware vsphere Document Scope, and Microsoft
Quick Install Guide. Lumension Endpoint Management and Security Suite 7.1
 Quick Install Guide Lumension Endpoint Management and Security Suite 7.1 Lumension Endpoint Management and Security Suite - 2 - Notices Version Information Lumension Endpoint Management and Security Suite
Quick Install Guide Lumension Endpoint Management and Security Suite 7.1 Lumension Endpoint Management and Security Suite - 2 - Notices Version Information Lumension Endpoint Management and Security Suite
Kaspersky Endpoint Security 10 for Windows. Deployment guide
 Kaspersky Endpoint Security 10 for Windows Deployment guide Introduction Typical Corporate Network Network servers Internet Gateway Workstations Mail servers Portable media Malware Intrusion Routes Viruses
Kaspersky Endpoint Security 10 for Windows Deployment guide Introduction Typical Corporate Network Network servers Internet Gateway Workstations Mail servers Portable media Malware Intrusion Routes Viruses
Barracuda Message Archiver Vx Deployment. Whitepaper
 Barracuda Message Archiver Vx Deployment Whitepaper Document Scope This document provides guidance on designing and deploying Barracuda Message Archiver Vx on VMware vsphere Document Scope, and Microsoft
Barracuda Message Archiver Vx Deployment Whitepaper Document Scope This document provides guidance on designing and deploying Barracuda Message Archiver Vx on VMware vsphere Document Scope, and Microsoft
System Management. What are my options for deploying System Management on remote computers?
 Getting Started, page 1 Managing Assets, page 2 Distributing Software, page 3 Distributing Patches, page 4 Backing Up Assets, page 5 Using Virus Protection, page 6 Security, page 7 Getting Started What
Getting Started, page 1 Managing Assets, page 2 Distributing Software, page 3 Distributing Patches, page 4 Backing Up Assets, page 5 Using Virus Protection, page 6 Security, page 7 Getting Started What
Virtual Appliance Setup Guide
 Virtual Appliance Setup Guide 2015 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property of their respective
Virtual Appliance Setup Guide 2015 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property of their respective
California Department of Technology, Office of Technology Services WINDOWS SERVER GUIDELINE
 Table of Contents 1.0 GENERAL... 2 1.1 SUMMARY...2 1.2 REFERENCES...2 1.3 SUBMITTALS...2 1.3.1 General...2 1.3.2 Service Request...3 1.4 EXPECTATIONS...3 1.4.1 OTech...3 1.4.2 Customer...3 1.5 SCHEDULING...4
Table of Contents 1.0 GENERAL... 2 1.1 SUMMARY...2 1.2 REFERENCES...2 1.3 SUBMITTALS...2 1.3.1 General...2 1.3.2 Service Request...3 1.4 EXPECTATIONS...3 1.4.1 OTech...3 1.4.2 Customer...3 1.5 SCHEDULING...4
Enterprise Cybersecurity Best Practices Part Number MAN-00363 Revision 006
 Enterprise Cybersecurity Best Practices Part Number MAN-00363 Revision 006 April 2013 Hologic and the Hologic Logo are trademarks or registered trademarks of Hologic, Inc. Microsoft, Active Directory,
Enterprise Cybersecurity Best Practices Part Number MAN-00363 Revision 006 April 2013 Hologic and the Hologic Logo are trademarks or registered trademarks of Hologic, Inc. Microsoft, Active Directory,
Cisco Advanced Services for Network Security
 Data Sheet Cisco Advanced Services for Network Security IP Communications networking the convergence of data, voice, and video onto a single network offers opportunities for reducing communication costs
Data Sheet Cisco Advanced Services for Network Security IP Communications networking the convergence of data, voice, and video onto a single network offers opportunities for reducing communication costs
Patch management with GFI LANguard and Microsoft WSUS
 A cost-effective and easy solution for network-wide patch management This white paper provides an overview of how to use GFI LANguard and Microsoft Windows Software Update Services (WSUS) to keep your
A cost-effective and easy solution for network-wide patch management This white paper provides an overview of how to use GFI LANguard and Microsoft Windows Software Update Services (WSUS) to keep your
W H I T E P A P E R : T E C H N I C A L. Understanding and Configuring Symantec Endpoint Protection Group Update Providers
 W H I T E P A P E R : T E C H N I C A L Understanding and Configuring Symantec Endpoint Protection Group Update Providers Martial Richard, Technical Field Enablement Manager Table of Contents Content Introduction...
W H I T E P A P E R : T E C H N I C A L Understanding and Configuring Symantec Endpoint Protection Group Update Providers Martial Richard, Technical Field Enablement Manager Table of Contents Content Introduction...
Symantec Endpoint Protection 11.0 Architecture, Sizing, and Performance Recommendations
 Symantec Endpoint Protection 11.0 Architecture, Sizing, and Performance Recommendations Technical Product Management Team Endpoint Security Copyright 2007 All Rights Reserved Revision 6 Introduction This
Symantec Endpoint Protection 11.0 Architecture, Sizing, and Performance Recommendations Technical Product Management Team Endpoint Security Copyright 2007 All Rights Reserved Revision 6 Introduction This
Virtual Appliance Setup Guide
 The Virtual Appliance includes the same powerful technology and simple Web based user interface found on the Barracuda Web Application Firewall hardware appliance. It is designed for easy deployment on
The Virtual Appliance includes the same powerful technology and simple Web based user interface found on the Barracuda Web Application Firewall hardware appliance. It is designed for easy deployment on
Patch and Vulnerability Management Program
 Patch and Vulnerability Management Program What is it? A security practice designed to proactively prevent the exploitation of IT vulnerabilities within an organization To reduce the time and money spent
Patch and Vulnerability Management Program What is it? A security practice designed to proactively prevent the exploitation of IT vulnerabilities within an organization To reduce the time and money spent
Core Protection for Virtual Machines 1
 Core Protection for Virtual Machines 1 Comprehensive Threat Protection for Virtual Environments. Installation Guide e Endpoint Security Trend Micro Incorporated reserves the right to make changes to this
Core Protection for Virtual Machines 1 Comprehensive Threat Protection for Virtual Environments. Installation Guide e Endpoint Security Trend Micro Incorporated reserves the right to make changes to this
F-Secure Internet Gatekeeper Virtual Appliance
 F-Secure Internet Gatekeeper Virtual Appliance F-Secure Internet Gatekeeper Virtual Appliance TOC 2 Contents Chapter 1: Welcome to F-Secure Internet Gatekeeper Virtual Appliance.3 Chapter 2: Deployment...4
F-Secure Internet Gatekeeper Virtual Appliance F-Secure Internet Gatekeeper Virtual Appliance TOC 2 Contents Chapter 1: Welcome to F-Secure Internet Gatekeeper Virtual Appliance.3 Chapter 2: Deployment...4
Network Detective. HIPAA Compliance Module. 2015 RapidFire Tools, Inc. All rights reserved V20150201
 Network Detective 2015 RapidFire Tools, Inc. All rights reserved V20150201 Contents Purpose of this Guide... 3 About Network Detective... 3 Overview... 4 Creating a Site... 5 Starting a HIPAA Assessment...
Network Detective 2015 RapidFire Tools, Inc. All rights reserved V20150201 Contents Purpose of this Guide... 3 About Network Detective... 3 Overview... 4 Creating a Site... 5 Starting a HIPAA Assessment...
SILVER PEAK ACCELERATION WITH EMC VSPEX PRIVATE CLOUD WITH RECOVERPOINT FOR VMWARE VSPHERE
 VSPEX IMPLEMENTATION GUIDE SILVER PEAK ACCELERATION WITH EMC VSPEX PRIVATE CLOUD WITH RECOVERPOINT FOR VMWARE VSPHERE Silver Peak Abstract This Implementation Guide describes the deployment of Silver Peak
VSPEX IMPLEMENTATION GUIDE SILVER PEAK ACCELERATION WITH EMC VSPEX PRIVATE CLOUD WITH RECOVERPOINT FOR VMWARE VSPHERE Silver Peak Abstract This Implementation Guide describes the deployment of Silver Peak
Proactively Managing Servers with Dell KACE and Open Manage Essentials
 Proactively Managing Servers with Dell KACE and Open Manage Essentials A Dell Technical White Paper Dell KACE Dell Open Manage Essentials THIS WHITE PAPER IS FOR INFORMATIONAL PURPOSES ONLY, AND MAY CONTAIN
Proactively Managing Servers with Dell KACE and Open Manage Essentials A Dell Technical White Paper Dell KACE Dell Open Manage Essentials THIS WHITE PAPER IS FOR INFORMATIONAL PURPOSES ONLY, AND MAY CONTAIN
How To Set Up A Shared Insight Cache Server On A Pc Or Macbook With A Virtual Environment On A Virtual Computer (For A Virtual) (For Pc Or Ipa) ( For Macbook) (Or Macbook). (For Macbook
 SEP 12.1 Best Practices in a Virtual Environment The document is intended to capture the complete set of best practices for installation and configuration of SEP in a virtual environment. 1 Table of Contents
SEP 12.1 Best Practices in a Virtual Environment The document is intended to capture the complete set of best practices for installation and configuration of SEP in a virtual environment. 1 Table of Contents
Endpoint protection for physical and virtual desktops
 datasheet Trend Micro officescan Endpoint protection for physical and virtual desktops In the bring-your-own-device (BYOD) environment, protecting your endpoints against ever-evolving threats has become
datasheet Trend Micro officescan Endpoint protection for physical and virtual desktops In the bring-your-own-device (BYOD) environment, protecting your endpoints against ever-evolving threats has become
Virtual Appliances. Virtual Appliances: Setup Guide for Umbrella on VMWare and Hyper-V. Virtual Appliance Setup Guide for Umbrella Page 1
 Virtual Appliances Virtual Appliances: Setup Guide for Umbrella on VMWare and Hyper-V Virtual Appliance Setup Guide for Umbrella Page 1 Table of Contents Overview... 3 Prerequisites... 4 Virtualized Server
Virtual Appliances Virtual Appliances: Setup Guide for Umbrella on VMWare and Hyper-V Virtual Appliance Setup Guide for Umbrella Page 1 Table of Contents Overview... 3 Prerequisites... 4 Virtualized Server
Virtualization Guide. McAfee Vulnerability Manager Virtualization
 Virtualization Guide McAfee Vulnerability Manager Virtualization COPYRIGHT Copyright 2012 McAfee, Inc. Do not copy without permission. TRADEMARKS McAfee, the McAfee logo, McAfee Active Protection, McAfee
Virtualization Guide McAfee Vulnerability Manager Virtualization COPYRIGHT Copyright 2012 McAfee, Inc. Do not copy without permission. TRADEMARKS McAfee, the McAfee logo, McAfee Active Protection, McAfee
WHITE PAPER: BEST PRACTICES. Sizing and Scalability Recommendations for Symantec Endpoint Protection. Symantec Enterprise Security Solutions Group
 2 WHITE PAPER: BEST PRACTICES Sizing and Scalability Recommendations for Symantec Rev 2.3 Symantec Enterprise Security Solutions Group White Paper: Symantec Best Practices Contents Introduction... 4 The
2 WHITE PAPER: BEST PRACTICES Sizing and Scalability Recommendations for Symantec Rev 2.3 Symantec Enterprise Security Solutions Group White Paper: Symantec Best Practices Contents Introduction... 4 The
Hardware and Software Requirements for Server Applications
 Hardware and Software Requirements for Server Applications IVS Enterprise Server Version 11.3+ RMG Networks Holding Corporation All Rights Reserved. Rev 9/14 TABLE OF CONTENTS INTRODUCTION...3 Minimum
Hardware and Software Requirements for Server Applications IVS Enterprise Server Version 11.3+ RMG Networks Holding Corporation All Rights Reserved. Rev 9/14 TABLE OF CONTENTS INTRODUCTION...3 Minimum
Pearl Echo Installation Checklist
 Pearl Echo Installation Checklist Use this checklist to enter critical installation and setup information that will be required to install Pearl Echo in your network. For detailed deployment instructions
Pearl Echo Installation Checklist Use this checklist to enter critical installation and setup information that will be required to install Pearl Echo in your network. For detailed deployment instructions
F-Secure Messaging Security Gateway. Deployment Guide
 F-Secure Messaging Security Gateway Deployment Guide TOC F-Secure Messaging Security Gateway Contents Chapter 1: Deploying F-Secure Messaging Security Gateway...3 1.1 The typical product deployment model...4
F-Secure Messaging Security Gateway Deployment Guide TOC F-Secure Messaging Security Gateway Contents Chapter 1: Deploying F-Secure Messaging Security Gateway...3 1.1 The typical product deployment model...4
Installing and Configuring Windows Server 2008. Module Overview 14/05/2013. Lesson 1: Planning Windows Server 2008 Installation.
 Installing and Configuring Windows Server 2008 Tom Brett Module Overview Planning Windows Server 2008 Installations Performing a Windows Server 2008 Installation Configuring Windows Server 2008 Following
Installing and Configuring Windows Server 2008 Tom Brett Module Overview Planning Windows Server 2008 Installations Performing a Windows Server 2008 Installation Configuring Windows Server 2008 Following
Securing the Microsoft Environment Using Desktop Patch Management
 Securing the Microsoft Environment Using Desktop Patch Management Published: February 2009 In an enterprise organization such as Microsoft, it's mission critical to maintain a secure environment by keeping
Securing the Microsoft Environment Using Desktop Patch Management Published: February 2009 In an enterprise organization such as Microsoft, it's mission critical to maintain a secure environment by keeping
NETGEAR ProSAFE WC9500 High Capacity Wireless Controller
 NETGEAR ProSAFE WC9500 High Capacity Wireless Controller Confi guring Microsoft DHCP for the Wireless LAN APPLICATION NOTES INTRODUCTION NETGEAR ProSAFE WC9500 High Capacity Wireless Controllers support
NETGEAR ProSAFE WC9500 High Capacity Wireless Controller Confi guring Microsoft DHCP for the Wireless LAN APPLICATION NOTES INTRODUCTION NETGEAR ProSAFE WC9500 High Capacity Wireless Controllers support
Abila MIP Mobile. System Requirements
 This is a publication of Abila, Inc. Version 1.x 2013 Abila, Inc. and its affiliated entities. All rights reserved. Abila, the Abila logos, and the Abila product and service names mentioned herein are
This is a publication of Abila, Inc. Version 1.x 2013 Abila, Inc. and its affiliated entities. All rights reserved. Abila, the Abila logos, and the Abila product and service names mentioned herein are
Altiris IT Analytics Solution 7.1 SP1 from Symantec User Guide
 Altiris IT Analytics Solution 7.1 SP1 from Symantec User Guide Altiris IT Analytics Solution 7.1 from Symantec User Guide The software described in this book is furnished under a license agreement and
Altiris IT Analytics Solution 7.1 SP1 from Symantec User Guide Altiris IT Analytics Solution 7.1 from Symantec User Guide The software described in this book is furnished under a license agreement and
EMC Data Domain Management Center
 EMC Data Domain Management Center Version 1.1 Initial Configuration Guide 302-000-071 REV 04 Copyright 2012-2015 EMC Corporation. All rights reserved. Published in USA. Published June, 2015 EMC believes
EMC Data Domain Management Center Version 1.1 Initial Configuration Guide 302-000-071 REV 04 Copyright 2012-2015 EMC Corporation. All rights reserved. Published in USA. Published June, 2015 EMC believes
Symantec Endpoint Protection Analyzer Report
 Symantec Endpoint Protection Analyzer Report For Symantec Customer Table of Contents Statement of Confidentiality... 3 1. Introduction... 4 2. Environmental Analysis Overview... 5 2.1 Findings Overview...
Symantec Endpoint Protection Analyzer Report For Symantec Customer Table of Contents Statement of Confidentiality... 3 1. Introduction... 4 2. Environmental Analysis Overview... 5 2.1 Findings Overview...
Goliath Performance Monitor Prerequisites v11.6
 v11.6 Are You Ready to Install? Use our pre-installation checklist below to make sure all items are in place before beginning the installation process. For further explanation, please read the official
v11.6 Are You Ready to Install? Use our pre-installation checklist below to make sure all items are in place before beginning the installation process. For further explanation, please read the official
Backup & Disaster Recovery Appliance User Guide
 Built on the Intel Hybrid Cloud Platform Backup & Disaster Recovery Appliance User Guide Order Number: G68664-001 Rev 1.0 June 22, 2012 Contents Registering the BDR Appliance... 4 Step 1: Register the
Built on the Intel Hybrid Cloud Platform Backup & Disaster Recovery Appliance User Guide Order Number: G68664-001 Rev 1.0 June 22, 2012 Contents Registering the BDR Appliance... 4 Step 1: Register the
Kaseya Server Instal ation User Guide June 6, 2008
 Kaseya Server Installation User Guide June 6, 2008 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations. Kaseya's
Kaseya Server Installation User Guide June 6, 2008 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations. Kaseya's
CLOUD SERVICE SCHEDULE Newcastle
 CLOUD SERVICE SCHEDULE Newcastle 1 DEFINITIONS Defined terms in the Standard Terms and Conditions have the same meaning in this Service Schedule unless expressed to the contrary. In this Service Schedule,
CLOUD SERVICE SCHEDULE Newcastle 1 DEFINITIONS Defined terms in the Standard Terms and Conditions have the same meaning in this Service Schedule unless expressed to the contrary. In this Service Schedule,
Product comparison. GFI LanGuard 2014 vs. Microsoft Windows Server Update Services 3.0 SP2
 Product comparison GFI LanGuard 2014 vs. Microsoft Windows Server Update Services 3.0 SP2 General features GFI LanGuard 2014 Microsoft WSUS 3.0 SP2 Scheduled scans Agent-less r Agent-based Integration
Product comparison GFI LanGuard 2014 vs. Microsoft Windows Server Update Services 3.0 SP2 General features GFI LanGuard 2014 Microsoft WSUS 3.0 SP2 Scheduled scans Agent-less r Agent-based Integration
System Compatibility. Enhancements. Email Security. SonicWALL Email Security 7.3.2 Appliance Release Notes
 Email Security SonicWALL Email Security 7.3.2 Appliance Release Notes System Compatibility SonicWALL Email Security 7.3.2 is supported on the following SonicWALL Email Security appliances: SonicWALL Email
Email Security SonicWALL Email Security 7.3.2 Appliance Release Notes System Compatibility SonicWALL Email Security 7.3.2 is supported on the following SonicWALL Email Security appliances: SonicWALL Email
Getting started. Symantec AntiVirus Corporate Edition. About Symantec AntiVirus. How to get started
 Getting started Symantec AntiVirus Corporate Edition Copyright 2004 Symantec Corporation. All rights reserved. Printed in the U.S.A. 03/04 10223881 Symantec and the Symantec logo are U.S. registered trademarks
Getting started Symantec AntiVirus Corporate Edition Copyright 2004 Symantec Corporation. All rights reserved. Printed in the U.S.A. 03/04 10223881 Symantec and the Symantec logo are U.S. registered trademarks
Endpoint protection for physical and virtual desktops
 datasheet Trend Micro officescan Endpoint protection for physical and virtual desktops In the bring-your-own-device (BYOD) environment, protecting your endpoints against ever-evolving threats has become
datasheet Trend Micro officescan Endpoint protection for physical and virtual desktops In the bring-your-own-device (BYOD) environment, protecting your endpoints against ever-evolving threats has become
Eaton NetWatch v5.0 NetWatch on Microsoft Hyper-V server 2008 Installation and configuration guide
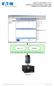 Eaton NetWatch v5.0 NetWatch on Microsoft Hyper-V server 2008 Installation and configuration guide Hyper-V 6.0 NetWatch Main operating system: 2008 Enterprise x64 (hosting Hyper-V) Eaton UPS Eaton NetWatch
Eaton NetWatch v5.0 NetWatch on Microsoft Hyper-V server 2008 Installation and configuration guide Hyper-V 6.0 NetWatch Main operating system: 2008 Enterprise x64 (hosting Hyper-V) Eaton UPS Eaton NetWatch
1. Server 2008 - Microsoft FEP 2010 - Instalation
 1. Server 2008 - Microsoft FEP 2010 - Instalation 1 2. Windows XP x86 (32bit) - Microsoft FEP 2010 Instalation 2 3 2.1. 4 System Requirements Microsoft Forefront Endpoint Protection 2010 1 System Requirements
1. Server 2008 - Microsoft FEP 2010 - Instalation 1 2. Windows XP x86 (32bit) - Microsoft FEP 2010 Instalation 2 3 2.1. 4 System Requirements Microsoft Forefront Endpoint Protection 2010 1 System Requirements
Remote PC Guide Series - Volume 1
 Introduction and Planning for Remote PC Implementation with NETLAB+ Document Version: 2016-02-01 What is a remote PC and how does it work with NETLAB+? This educational guide will introduce the concepts
Introduction and Planning for Remote PC Implementation with NETLAB+ Document Version: 2016-02-01 What is a remote PC and how does it work with NETLAB+? This educational guide will introduce the concepts
Deploying F5 BIG-IP Virtual Editions in a Hyper-Converged Infrastructure
 Deploying F5 BIG-IP Virtual Editions in a Hyper-Converged Infrastructure Justin Venezia Senior Solution Architect Paul Pindell Senior Solution Architect Contents The Challenge 3 What is a hyper-converged
Deploying F5 BIG-IP Virtual Editions in a Hyper-Converged Infrastructure Justin Venezia Senior Solution Architect Paul Pindell Senior Solution Architect Contents The Challenge 3 What is a hyper-converged
Getting Started. Symantec Client Security. About Symantec Client Security. How to get started
 Getting Started Symantec Client Security About Security Security provides scalable, cross-platform firewall, intrusion prevention, and antivirus protection for workstations and antivirus protection for
Getting Started Symantec Client Security About Security Security provides scalable, cross-platform firewall, intrusion prevention, and antivirus protection for workstations and antivirus protection for
ACI ON DEMAND DELIVERS PEACE OF MIND
 DELIVERS PEACE OF MIND SERVICE LINE FLYER ACI ON DEMAND ACCESS TO THE LATEST RELEASES OF FEATURE-RICH SOFTWARE AND SYSTEMS, INCLUDING INTEGRATION WITH VALUE- ADDED THIRD PARTIES IMPLEMENTATION CONFIGURED
DELIVERS PEACE OF MIND SERVICE LINE FLYER ACI ON DEMAND ACCESS TO THE LATEST RELEASES OF FEATURE-RICH SOFTWARE AND SYSTEMS, INCLUDING INTEGRATION WITH VALUE- ADDED THIRD PARTIES IMPLEMENTATION CONFIGURED
MANAGED FIREWALL SERVICE. Service definition
 MANAGED FIREWALL SERVICE Service definition Page 1 of 4 Version 1.2 (03/02/2015) NSMS Managed Firewalls Service Definition Understanding of a firewall service The function of any firewall service is to
MANAGED FIREWALL SERVICE Service definition Page 1 of 4 Version 1.2 (03/02/2015) NSMS Managed Firewalls Service Definition Understanding of a firewall service The function of any firewall service is to
Product Support Notice
 PSN # PSN004098u Product Support Notice Original publication date: 8-Nov-13. This is Issue #06, Published date: 21-Feb-14. 2014 Avaya Inc. All Rights Reserved. Severity/risk level High Urgency Complete
PSN # PSN004098u Product Support Notice Original publication date: 8-Nov-13. This is Issue #06, Published date: 21-Feb-14. 2014 Avaya Inc. All Rights Reserved. Severity/risk level High Urgency Complete
Getting started. Symantec AntiVirus Business Pack. About Symantec AntiVirus. Where to find information
 Getting started Symantec AntiVirus Business Pack Copyright 2004 Symantec Corporation. All rights reserved. Printed in the U.S.A. 03/04 Symantec and the Symantec logo are U.S. registered trademarks of Symantec
Getting started Symantec AntiVirus Business Pack Copyright 2004 Symantec Corporation. All rights reserved. Printed in the U.S.A. 03/04 Symantec and the Symantec logo are U.S. registered trademarks of Symantec
Backup Exec System Recovery Management Solution 2010 FAQ
 Backup Exec System Recovery Management Solution 2010 FAQ Contents Overview... 1 Supported Backup Exec System Recovery Versions and Configurations... 6 Backup Exec System Recovery Management Solution Installation
Backup Exec System Recovery Management Solution 2010 FAQ Contents Overview... 1 Supported Backup Exec System Recovery Versions and Configurations... 6 Backup Exec System Recovery Management Solution Installation
Windows 7, Enterprise Desktop Support Technician
 Course 50331D: Windows 7, Enterprise Desktop Support Technician Page 1 of 11 Windows 7, Enterprise Desktop Support Technician Course 50331D: 4 days; Instructor-Led Introduction This four-day instructor-ledcourse
Course 50331D: Windows 7, Enterprise Desktop Support Technician Page 1 of 11 Windows 7, Enterprise Desktop Support Technician Course 50331D: 4 days; Instructor-Led Introduction This four-day instructor-ledcourse
Minimum Requirements for Cencon 4 with Microsoft R SQL 2008 R2 Express
 Minimum Requirements for Cencon 4 with Microsoft R SQL 2008 R2 Express SQL 2008 R2 Express Restrictions 1 CPU 1 GB Ram Use Limit 10 GB Database Size High Availability Options None (No Database Mirroring,
Minimum Requirements for Cencon 4 with Microsoft R SQL 2008 R2 Express SQL 2008 R2 Express Restrictions 1 CPU 1 GB Ram Use Limit 10 GB Database Size High Availability Options None (No Database Mirroring,
WatchGuard XCSv Setup Guide
 WatchGuard XCSv Setup Guide All XCSv Editions Copyright and Patent Information Copyright 2010 2013 WatchGuard Technologies, Inc. All rights reserved. WatchGuard, the WatchGuard logo, LiveSecurity, and
WatchGuard XCSv Setup Guide All XCSv Editions Copyright and Patent Information Copyright 2010 2013 WatchGuard Technologies, Inc. All rights reserved. WatchGuard, the WatchGuard logo, LiveSecurity, and
Planning and Administering Windows Server 2008 Servers
 Planning and Administering Windows Server 2008 Servers Course 6430 Five days Instructor-led Introduction Elements of this syllabus are subject to change. This five-day instructor-led course provides students
Planning and Administering Windows Server 2008 Servers Course 6430 Five days Instructor-led Introduction Elements of this syllabus are subject to change. This five-day instructor-led course provides students
Patch Management Integration
 Patch Management Integration January 10, 2012 (Revision 5) Copyright 2002-2012 Tenable Network Security, Inc. Tenable Network Security, Nessus and ProfessionalFeed are registered trademarks of Tenable
Patch Management Integration January 10, 2012 (Revision 5) Copyright 2002-2012 Tenable Network Security, Inc. Tenable Network Security, Nessus and ProfessionalFeed are registered trademarks of Tenable
EMC Integrated Infrastructure for VMware
 EMC Integrated Infrastructure for VMware Enabled by EMC Celerra NS-120 Reference Architecture EMC Global Solutions Centers EMC Corporation Corporate Headquarters Hopkinton MA 01748-9103 1.508.435.1000
EMC Integrated Infrastructure for VMware Enabled by EMC Celerra NS-120 Reference Architecture EMC Global Solutions Centers EMC Corporation Corporate Headquarters Hopkinton MA 01748-9103 1.508.435.1000
Windows 7, Enterprise Desktop Support Technician Course 50331: 5 days; Instructor-led
 Lincoln Land Community College Capital City Training Center 130 West Mason Springfield, IL 62702 217-782-7436 www.llcc.edu/cctc Windows 7, Enterprise Desktop Support Technician Course 50331: 5 days; Instructor-led
Lincoln Land Community College Capital City Training Center 130 West Mason Springfield, IL 62702 217-782-7436 www.llcc.edu/cctc Windows 7, Enterprise Desktop Support Technician Course 50331: 5 days; Instructor-led
Getting started. Symantec AntiVirus Corporate Edition. About Symantec AntiVirus. How to get started
 Getting started Corporate Edition Copyright 2005 Corporation. All rights reserved. Printed in the U.S.A. 03/05 PN: 10362873 and the logo are U.S. registered trademarks of Corporation. is a trademark of
Getting started Corporate Edition Copyright 2005 Corporation. All rights reserved. Printed in the U.S.A. 03/05 PN: 10362873 and the logo are U.S. registered trademarks of Corporation. is a trademark of
Fundamentals of Windows Server 2008 Network and Applications Infrastructure
 Fundamentals of Windows Server 2008 Network and Applications Infrastructure MOC6420 About this Course This five-day instructor-led course introduces students to network and applications infrastructure
Fundamentals of Windows Server 2008 Network and Applications Infrastructure MOC6420 About this Course This five-day instructor-led course introduces students to network and applications infrastructure
VMware vcenter Log Insight Getting Started Guide
 VMware vcenter Log Insight Getting Started Guide vcenter Log Insight 1.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
VMware vcenter Log Insight Getting Started Guide vcenter Log Insight 1.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
Electoral Commission. Auction # 10220759. Patch Management Solution
 Electoral Commission Auction # 10220759 Patch Management Solution IMPORTANT NOTICE Failure to comply with the completion of the auction conditions and the required information (i.e. Make, model and size
Electoral Commission Auction # 10220759 Patch Management Solution IMPORTANT NOTICE Failure to comply with the completion of the auction conditions and the required information (i.e. Make, model and size
Best Practices & Deployment SurfControl Mobile Filter v 5.0.2.60
 Best Practices & Deployment SurfControl Mobile Filter v 5.0.2.60 rev2.1, January 2006 Pre-Installation Guide Notice 2006 SurfControl. All rights reserved. SurfControl, SurfControl E-mail Filter, SurfControl
Best Practices & Deployment SurfControl Mobile Filter v 5.0.2.60 rev2.1, January 2006 Pre-Installation Guide Notice 2006 SurfControl. All rights reserved. SurfControl, SurfControl E-mail Filter, SurfControl
Getting Started. Version 9.1
 Getting Started Version 9.1 Contents About this Guide 4 Other Resources 4 Product Documentation 4 Online Training Program 4 Daily Online Q & A sessions 4 Prepare Your Customer's Network 5 Create a Probe
Getting Started Version 9.1 Contents About this Guide 4 Other Resources 4 Product Documentation 4 Online Training Program 4 Daily Online Q & A sessions 4 Prepare Your Customer's Network 5 Create a Probe
Mitel Communication Service & Phone Manager Installation Guide OCTOBER 2014 DOCUMENT RELEASE 4.1 INSTALLATION GUIDE
 Mitel Communication Service & Phone Manager Installation Guide OCTOBER 2014 DOCUMENT RELEASE 4.1 INSTALLATION GUIDE NOTICE The information contained in this document is believed to be accurate in all respects
Mitel Communication Service & Phone Manager Installation Guide OCTOBER 2014 DOCUMENT RELEASE 4.1 INSTALLATION GUIDE NOTICE The information contained in this document is believed to be accurate in all respects
VMware vsphere: Install, Configure, Manage [V5.0]
![VMware vsphere: Install, Configure, Manage [V5.0] VMware vsphere: Install, Configure, Manage [V5.0]](/thumbs/18/878042.jpg) VMware vsphere: Install, Configure, Manage [V5.0] Gain hands-on experience using VMware ESXi 5.0 and vcenter Server 5.0. In this hands-on, VMware -authorized course based on ESXi 5.0 and vcenter Server
VMware vsphere: Install, Configure, Manage [V5.0] Gain hands-on experience using VMware ESXi 5.0 and vcenter Server 5.0. In this hands-on, VMware -authorized course based on ESXi 5.0 and vcenter Server
Microsoft Dynamics CRM 2011 Guide to features and requirements
 Guide to features and requirements New or existing Dynamics CRM Users, here s what you need to know about CRM 2011! This guide explains what new features are available and what hardware and software requirements
Guide to features and requirements New or existing Dynamics CRM Users, here s what you need to know about CRM 2011! This guide explains what new features are available and what hardware and software requirements
HP ProLiant Essentials Vulnerability and Patch Management Pack Planning Guide
 HP ProLiant Essentials Vulnerability and Patch Management Pack Planning Guide Product overview... 3 Vulnerability scanning components... 3 Vulnerability fix and patch components... 3 Checklist... 4 Pre-installation
HP ProLiant Essentials Vulnerability and Patch Management Pack Planning Guide Product overview... 3 Vulnerability scanning components... 3 Vulnerability fix and patch components... 3 Checklist... 4 Pre-installation
Understand Troubleshooting Methodology
 Understand Troubleshooting Methodology Lesson Overview In this lesson, you will learn about: Troubleshooting procedures Event Viewer Logging Resource Monitor Anticipatory Set If the workstation service
Understand Troubleshooting Methodology Lesson Overview In this lesson, you will learn about: Troubleshooting procedures Event Viewer Logging Resource Monitor Anticipatory Set If the workstation service
Course Syllabus. Planning and Administering Windows Server 2008 Servers. Key Data. Audience. At Course Completion. Prerequisites. Recommended Courses
 Course Syllabus Planning and Administering Windows Server 2008 Servers This five-day instructor-led course provides students with the knowledge and skills to implement, monitor, and maintain Windows Server
Course Syllabus Planning and Administering Windows Server 2008 Servers This five-day instructor-led course provides students with the knowledge and skills to implement, monitor, and maintain Windows Server
Installing and Configuring Websense Content Gateway
 Installing and Configuring Websense Content Gateway Websense Support Webinar - September 2009 web security data security email security Support Webinars 2009 Websense, Inc. All rights reserved. Webinar
Installing and Configuring Websense Content Gateway Websense Support Webinar - September 2009 web security data security email security Support Webinars 2009 Websense, Inc. All rights reserved. Webinar
Information Technology
 Information Technology Symantec Endpoint Protection Download and Installation The packages on the web include virus and spyware protection for 32 and 64 bit Microsoft Windows systems. Minimum system requirements:
Information Technology Symantec Endpoint Protection Download and Installation The packages on the web include virus and spyware protection for 32 and 64 bit Microsoft Windows systems. Minimum system requirements:
Symantec Endpoint Protection 12.1.5 Sizing and Scalability Best Practices White Paper
 Symantec Endpoint Protection 12.1.5 Sizing and Scalability Best Practices White Paper Symantec Endpoint Protection Sizing and Scalability Best Practices White Paper Product version: 12.1.5 Documentation
Symantec Endpoint Protection 12.1.5 Sizing and Scalability Best Practices White Paper Symantec Endpoint Protection Sizing and Scalability Best Practices White Paper Product version: 12.1.5 Documentation
Release Version 4.1 The 2X Software Server Based Computing Guide
 Release Version 4.1 The 2X Software Server Based Computing Guide Information in this document is subject to change without notice. Companies, names, and data used in examples herein are fictitious unless
Release Version 4.1 The 2X Software Server Based Computing Guide Information in this document is subject to change without notice. Companies, names, and data used in examples herein are fictitious unless
Hardware and Software Requirements for Server Applications
 Hardware and Software Requirements for Server Applications IVS Enterprise Server Version 11.3+ RMG Enterprise Solutions, Inc. All Rights Reserved. Rev 7/14 TABLE OF CONTENTS INTRODUCTION...3 Minimum Hardware
Hardware and Software Requirements for Server Applications IVS Enterprise Server Version 11.3+ RMG Enterprise Solutions, Inc. All Rights Reserved. Rev 7/14 TABLE OF CONTENTS INTRODUCTION...3 Minimum Hardware
VIA COLLAGE Deployment Guide
 VIA COLLAGE Deployment Guide www.true-collaboration.com Infinite Ways to Collaborate CONTENTS Introduction... 3 User Experience... 3 Pre-Deployment Planning... 3 Connectivity... 3 Network Addressing...
VIA COLLAGE Deployment Guide www.true-collaboration.com Infinite Ways to Collaborate CONTENTS Introduction... 3 User Experience... 3 Pre-Deployment Planning... 3 Connectivity... 3 Network Addressing...
F-SECURE MESSAGING SECURITY GATEWAY
 F-SECURE MESSAGING SECURITY GATEWAY DEFAULT SETUP GUIDE This guide describes how to set up and configure the F-Secure Messaging Security Gateway appliance in a basic e-mail server environment. AN EXAMPLE
F-SECURE MESSAGING SECURITY GATEWAY DEFAULT SETUP GUIDE This guide describes how to set up and configure the F-Secure Messaging Security Gateway appliance in a basic e-mail server environment. AN EXAMPLE
Wyse Device Manager TM
 Wyse Device Manager TM Secure, flexible and effective thin client management software All youneed toknow.here. An introduction to Wyse Device Manager TM Minimize your desktop support costs. Maximize desktop
Wyse Device Manager TM Secure, flexible and effective thin client management software All youneed toknow.here. An introduction to Wyse Device Manager TM Minimize your desktop support costs. Maximize desktop
REDCENTRIC MANAGED SERVER SERVICE DEFINITION
 REDCENTRIC MANAGED SERVER SERVICE DEFINITION SD062 V1.4 Issue Date 01 July 2014 1) OVERVIEW The Managed Server service (MSS) provides access to Redcentric s 24x7 support capability, technical skills and
REDCENTRIC MANAGED SERVER SERVICE DEFINITION SD062 V1.4 Issue Date 01 July 2014 1) OVERVIEW The Managed Server service (MSS) provides access to Redcentric s 24x7 support capability, technical skills and
Hyper-V Server 2008 Setup and Configuration Tool Guide
 Hyper-V Server 2008 Setup and Configuration Tool Guide Microsoft Corporation Published: October 2008 Author: Cynthia Nottingham Abstract This guide will help you set up and configure Microsoft Hyper-V
Hyper-V Server 2008 Setup and Configuration Tool Guide Microsoft Corporation Published: October 2008 Author: Cynthia Nottingham Abstract This guide will help you set up and configure Microsoft Hyper-V
TANDBERG MANAGEMENT SUITE 10.0
 TANDBERG MANAGEMENT SUITE 10.0 Installation Manual Getting Started D12786 Rev.16 This document is not to be reproduced in whole or in part without permission in writing from: Contents INTRODUCTION 3 REQUIREMENTS
TANDBERG MANAGEMENT SUITE 10.0 Installation Manual Getting Started D12786 Rev.16 This document is not to be reproduced in whole or in part without permission in writing from: Contents INTRODUCTION 3 REQUIREMENTS
Interworks. Interworks Cloud Platform Installation Guide
 Interworks Interworks Cloud Platform Installation Guide Published: March, 2014 This document contains information proprietary to Interworks and its receipt or possession does not convey any rights to reproduce,
Interworks Interworks Cloud Platform Installation Guide Published: March, 2014 This document contains information proprietary to Interworks and its receipt or possession does not convey any rights to reproduce,
"Charting the Course... ... to Your Success!" MOC 50331 D Windows 7 Enterprise Desktop Support Technician Course Summary
 Description Course Summary This course provides students with the knowledge and skills needed to isolate, document and resolve problems on a Windows 7 desktop or laptop computer. It will also help test
Description Course Summary This course provides students with the knowledge and skills needed to isolate, document and resolve problems on a Windows 7 desktop or laptop computer. It will also help test
INFRASTRUCTURE AS A SERVICE (IAAS) SERVICE SCHEDULE Australia
 INFRASTRUCTURE AS A SERVICE (IAAS) SERVICE SCHEDULE Australia 1 DEFINITIONS Capitalised terms in this Service Schedule not otherwise defined here have the meaning given in the Standard Terms and Conditions:
INFRASTRUCTURE AS A SERVICE (IAAS) SERVICE SCHEDULE Australia 1 DEFINITIONS Capitalised terms in this Service Schedule not otherwise defined here have the meaning given in the Standard Terms and Conditions:
Design and Implementation Guide. Apple iphone Compatibility
 Design and Implementation Guide Apple iphone Compatibility Introduction Security in wireless LANs has long been a concern for network administrators. While securing laptop devices is well understood, new
Design and Implementation Guide Apple iphone Compatibility Introduction Security in wireless LANs has long been a concern for network administrators. While securing laptop devices is well understood, new
Virtualized Disaster Recovery (VDR) Overview... 2. Detailed Description... 3
 Service Description Virtualized Disaster Recovery (VDR) Terremark's Virtualized Disaster Recovery (VDR) service is a fully managed replication and Disaster Recovery (DR) service, where Terremark provides
Service Description Virtualized Disaster Recovery (VDR) Terremark's Virtualized Disaster Recovery (VDR) service is a fully managed replication and Disaster Recovery (DR) service, where Terremark provides
SENIOR SYSTEMS ANALYST
 CITY OF MONTEBELLO 109 DEFINITION Under general administrative direction of the City Administrator, provides advanced professional support to departments with very complex computer systems, programs and
CITY OF MONTEBELLO 109 DEFINITION Under general administrative direction of the City Administrator, provides advanced professional support to departments with very complex computer systems, programs and
Planning and Administering Windows Server 2008 Servers
 Planning and Administering Windows Server 2008 Servers MOC6430 About this Course Elements of this syllabus are subject to change. This five-day instructor-led course provides students with the knowledge
Planning and Administering Windows Server 2008 Servers MOC6430 About this Course Elements of this syllabus are subject to change. This five-day instructor-led course provides students with the knowledge
Delphi 2015 SP1-AP1 System Requirements
 Delphi 2015 SP1-AP1 System Requirements Revision 1.2 Newmarket International Inc. July 24,2015 newmarketinc.com Copyright 2015 Newmarket International, Inc., an Amadeus company. All rights reserved. This
Delphi 2015 SP1-AP1 System Requirements Revision 1.2 Newmarket International Inc. July 24,2015 newmarketinc.com Copyright 2015 Newmarket International, Inc., an Amadeus company. All rights reserved. This
Securing the Microsoft Platform on Amazon Web Services
 Securing the Microsoft Platform on Amazon Web Services Tom Stickle August 2012 (Please consult http://aws.amazon.com/whitepapers/ for the latest version of this paper) Page 1 of 22 Abstract Deploying Microsoft
Securing the Microsoft Platform on Amazon Web Services Tom Stickle August 2012 (Please consult http://aws.amazon.com/whitepapers/ for the latest version of this paper) Page 1 of 22 Abstract Deploying Microsoft
How To Run A Hosted Physical Server On A Server At Redcentric
 REDCENTRIC HOSTED PHYSICAL SERVER SERVICE DEFINITION SD027 V1.6 Issue Date 01 July 2014 1) OVERVIEW The Hosted Physical Server service (HPS) offers dedicated off-site server resource located within an
REDCENTRIC HOSTED PHYSICAL SERVER SERVICE DEFINITION SD027 V1.6 Issue Date 01 July 2014 1) OVERVIEW The Hosted Physical Server service (HPS) offers dedicated off-site server resource located within an
McAfee Endpoint Security 10.0.0 Software
 Installation Guide McAfee Endpoint Security 10.0.0 Software For use with epolicy Orchestrator 5.1.1 5.2.0 software and the McAfee SecurityCenter COPYRIGHT Copyright 2014 McAfee, Inc. Do not copy without
Installation Guide McAfee Endpoint Security 10.0.0 Software For use with epolicy Orchestrator 5.1.1 5.2.0 software and the McAfee SecurityCenter COPYRIGHT Copyright 2014 McAfee, Inc. Do not copy without
SolarWinds Network Performance Monitor
 SolarWinds Network Performance Monitor powerful network fault & availabilty management Fully Functional for 30 Days SolarWinds Network Performance Monitor (NPM) makes it easy to quickly detect, diagnose,
SolarWinds Network Performance Monitor powerful network fault & availabilty management Fully Functional for 30 Days SolarWinds Network Performance Monitor (NPM) makes it easy to quickly detect, diagnose,
NetWrix USB Blocker Version 3.6 Quick Start Guide
 NetWrix USB Blocker Version 3.6 Quick Start Guide Table of Contents 1. Introduction...3 1.1. What is NetWrix USB Blocker?...3 1.2. Product Architecture...3 2. Licensing...4 3. Getting Started...5 3.1.
NetWrix USB Blocker Version 3.6 Quick Start Guide Table of Contents 1. Introduction...3 1.1. What is NetWrix USB Blocker?...3 1.2. Product Architecture...3 2. Licensing...4 3. Getting Started...5 3.1.
Data Sheet: Endpoint Security Symantec Endpoint Protection The next generation of antivirus technology from Symantec
 The next generation of antivirus technology from Symantec Overview Advanced threat protection combines Symantec AntiVirus with advanced threat prevention to deliver an unmatched defense against malware
The next generation of antivirus technology from Symantec Overview Advanced threat protection combines Symantec AntiVirus with advanced threat prevention to deliver an unmatched defense against malware
Planning and Maintaining a Microsoft Windows Server Network Infrastructure
 Unit 27: Planning and Maintaining a Microsoft Windows Server Network Infrastructure Learning outcomes A candidate following a programme of learning leading to this unit will be able to: Configure security
Unit 27: Planning and Maintaining a Microsoft Windows Server Network Infrastructure Learning outcomes A candidate following a programme of learning leading to this unit will be able to: Configure security
Installing and Administering VMware vsphere Update Manager
 Installing and Administering VMware vsphere Update Manager Update 1 vsphere Update Manager 5.1 This document supports the version of each product listed and supports all subsequent versions until the document
Installing and Administering VMware vsphere Update Manager Update 1 vsphere Update Manager 5.1 This document supports the version of each product listed and supports all subsequent versions until the document
SolarWinds Network Performance Monitor powerful network fault & availabilty management
 SolarWinds Network Performance Monitor powerful network fault & availabilty management Fully Functional for 30 Days SolarWinds Network Performance Monitor (NPM) is powerful and affordable network monitoring
SolarWinds Network Performance Monitor powerful network fault & availabilty management Fully Functional for 30 Days SolarWinds Network Performance Monitor (NPM) is powerful and affordable network monitoring
