Agent Control. The World
|
|
|
- Marylou Collins
- 8 years ago
- Views:
Transcription
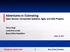
1 AFS and HAC: Domain-General Agent Simulation and Control Marc S. Atkin, David L. Westbrook, Paul R. Cohen and Gregory D. Jorstad Experimental Knowledge Systems Laboratory Department of Computer Science, LGRC, Box University of Massachusetts, Amherst, MA Abstract We present two systems for simulating and designing agents, respectively. The rst, the Abstract Force Simulator (AFS), is a domain-general simulator of agents applying forces many domains can be characterized in this way. The second, Hierarchical Agent Control (HAC), is a general toolkit for designing an action hierarchy. It supports action abstraction, a multilevel computational architecture, sensor integration, and planning. It is particularly well suited to controlling large numbers of agents in dynamic environments. Together, AFS and HAC provide a very general framework for designing and testing agents. Introduction We have set ourselves the goal of constructing a domaingeneral agent development toolkit. Regardless of the domain, agent designers must face the same kinds of problems: processing sensor information, reacting to a changing environment in a timely manner, integrating reactive and cognitive processes to achieve an abstract goal, interleaving planning and execution, distributed control, allowing code reuse within and across domains, and using computational resources eciently. The best possible solution to any of the above problems will depend to some extent on the domain. As a consequence, we wanted our toolkit to have enough exibility to allow any one of many solutions to be implemented. We provide the agent designer with dierent tools for dealing with a problem, but it is up to her to decide which tool to use. This paper will describe a general framework for controlling agents, called Hierarchical Agent Control (HAC). Complementing it is a general simulator of physical processes, the Abstract Force Simulator (AFS). AFS can be used to simulate many dierent domains, as will be described in the next section. HAC itselfisa general skeleton for controlling agents. It can work with many kinds of simulators or even real-life robots, as long as they adhere to a certain protocol. HAC provides the mechanics for sensor management, action scheduling, and message passing. The actual implementation of actions and sensors is provided by separate and interchangeable modules, as is the planner. Additional Action/Sensor Sets Planner Other Modules (language...) Agent Control The World AFS HAC Physics Model Robots Other Agents Figure 1: The AFS/HAC system modules and organization. modules might be task specic, such as the language generation module we have used. Figure 1 illustrates the system decomposition. AFS and HAC are written in Common Lisp. We will now describe AFS, which in many ways motivated the need for a general agent control architecture, before returning to HAC. The Abstract Force Simulator Physical Schemas It occurred to us some time ago that many ofthesimulators we had been writing really were just variations on a theme. Physical processes, military engagements, and games such as billiards are all about agents moving and applying force to one another (see, for example, (Tzu 1988) and (Karr 1981)). Even the somewhat abstract realm of diplomacy can viewed in these terms: One government might try to apply pressure to another for some purpose, or intend to contain a crisis before it spreads. Furthermore, it became clear that there is a common set of terms upon which all the above processes operate. Some examples are move, push, reduce, contain, block, orsurround. Collectively, we refer to these terms as physical schemas. If moving an army is conceptually no dierent than moving a robot, both
2 these processes can be represented with one move action in a simulator. We believe that people think and solve problems in terms of physical schemas. An example: A person notices his sink is leaking, and considers what to about it. He realizes that there are cracks in the sink. The way tosolve the problem is to plug the cracks. Now confront this person with a military problem: Hostile forces are moving across a mountain range into friendly territory. What should be done about it? If the person understands that military forces can behave like water, and that the cracks are passes in the mountain range, he can prevent the ow by making the passes untraversable. Based on these ideas, we have developed a simulator of physical schemas, the Abstract Force Simulator (AFS). It operates with a set of abstract agents, circular objects 1 called \blobs," which are described by a small set of physical features, including mass, velocity, friction, radius, attack strength, and so on. A blob is an abstract unit it could be an army, a soldier, a planet, or a political entity. Every blob has a small set of primitive actions it can perform, primarily move and apply-force. All other schemas are built from these actions. Simply by changing the physics of the simulator (how mass is aected by collisions, what the friction is for a blob moving over a certain type of surface, etc.), we can turn AFS from a simulator of billiard balls into one of unit movements in a military domain. Simulator Mechanics AFS is a simulator of physical processes. It is tickbased, but the ticks are small enough to accurately model the physical interactions between blobs. Although blobs themselves move continuously in 2D space, for reasons of eciency, the properties of this space, such as terrain attributes, are represented as a discrete grid of rectangular cells. Such a grid of cells is also used internally to bin spatially proximal blobs, making the time complexity of collision detection and blob sensor modeling no greater than linear in terms of the number of blobs in the simulator. AFS was designed from the outset to be able to simulate large numbers (on the order of hundreds or thousands) of blobs. The physics of the simulation are presently dened by the following parameters: Blob-specic attributes: maximum acceleration and deceleration friction of the blob on dierent surfaces viscosity and elasticity: do blobs pass through one another or bounce o? Global parameters: the eect of terrain on blobs 1 Eventually, blobs will be able to take any shape, and deform and redistribute their mass. Computing the physical interactions of arbitrarily-shaped objects is time-consuming as a rst pass, we intend to make blobs elliptical. the dierent types of blobs present in the simulation (such as blobs that need sustenance). the damage model: how blobs aect each others' masses by moving through each other or applying force. sustenance model: do blobs have to resupplied in order to prevent them from losing mass? AFS is an abstract simulator blobs are abstract entities that mayormay not haveinternal structure. AFS allows us to express a blob's internal structure by composing it from smaller blobs, much like anarmyiscomposed of smaller organizational units and ultimately individual soldiers. But we don't have totake the internal structure into account whensimulating, since at any level of abstraction, every blob is completely characterized by the physical attributes associated with it. Armies can move and apply force just like individual soldiers do. The physics of armies is dierent than the physics of soldiers, and the time and space scales are dierent, but the main idea behind AFS is that we can simulate at the \army" level if we so desire if we believe it is unnecessary or inecient tosimulate in more detail. Since AFS is basically just simulating physics, the top-level control loop of the simulator is quite straightforward: On each tick, loop over all blobs in the simulator and update each one based on the forces acting on it. If blobs interact, the physics of the world will specify what form their interaction will take. Then update the blob's low-level sensors, if it has any. Eachblob is assumed to have astate reector, a data structure that expresses the current state of the blob's sensory experience. It is the simulator's job to update this data structure. Hierarchical Agent Control Since AFS is such a general simulator, we require an appropriately general method for controlling the blobs within it. This control scheme is HAC (Hierarchical Agent Control). Whereas the physics modeled in AFS dene how an a blob's actions unfold in the world, HAC denes what the blob should do. One way tolookat HAC is as a toolset for designing a hierarchy of actions, goals, and sensors. Another way is as an execution module for the many actions that are running concurrently within a blob and across blobs. Although we have primarily been using HAC in conjunction with AFS, HAC isby no means tied to a specic simulator, and, unlike AFS, could be applied to domains that are not easily viewed as abstract physical processes. We are currently working on using HAC to control actual mobile robots (Pioneers). All HAC requires to work with any given agent isaninterface to the state reector for that agent (i.e., a way to access the low-level sensory data the agent collects) and an implementation of a set of low level action primitives, like turn, move, andpush.
3 One of the major issues in dening an action set for an agent, and, one might argue, one of the major issues in dening any kind of intelligent behavior, is the problem of forming abstractions. No agent designer will want to specify the solution to a given problem in terms of primitivelow-level actions and sensations. Instead, she will rst build more powerful abstract actions, which encode solutions to a range of problems, and use these actions when faced with a new problem. If a robot is supposed to retrieve an object, we don't want togiveit individual commands to move its wheels and its gripper we want togive it a \pick-up" command and have the robot gure out what it needs to do. HAC lets us abstract by providing the mechanisms to construct a hierarchy of actions. In the hierarchy, abstract actions are dened in terms of simpler ones, ultimately grounding out in the agent's eectors. Although actions are abstract at higher levels of the hierarchy, they are nonetheless executable. At the same time, the hierarchy implements a multilevel computational architecture, allowing us, for example, to have both cognitive and reactive actions within the same framework (George & Lansky 1987 Cohen et al. 1989). The main part of HAC's execution module is an action queue. Any scheduled action gets placed on the queue. The queue is sorted by the time at which the action will execute. Actions get taken o the queue and executed until there are no more actions that are scheduled to run at this time step. Actions can reschedule themselves, but in most cases, they will be rescheduled when woken up by messages from their children. An action is executed by calling its realize method. The realize method does not generally complete the action on its rst invocation it just does what needs to be done on this tick. In most cases, an action's realize method will be called many times before the action terminates. We will see an example of this later. The Action Hierarchy HAC is a supervenient architecture (Spector & Hendler 1994). This means that it abides by the principle that higher levels should provide goals and context for the lower levels, and lower levels provide sensory reports and messages to the higher levels (\goals down, knowledge up"). A higher level cannot overrule the sensory information provided by a lower level, nor can a lower level interfere with the control of a higher level. Supervenience structures the abstraction process it allows us to build modular, reusable actions. HAC goes a step further in the simplication of the action-writing process, by enforcing that every action's implementation take the following form: 1. React to messages coming in from children. 2. Update state. 3. Schedule new child actions if necessary. 4. Send messages up to parent. Let's assume we wanted to build an action that allows a blob to follow amoving target (see Figure 2). If we have amove-to-point action (which in turn uses the primitive move), writing such an action is fairly easy. We compute a direction that will cause us to intercept the target. Then we computeapoint a short distance along this vector, and schedule a child move-to-point action to move us there. We leave all the details of getting to this location, including such things as obstacle avoidance, up to the child. The child can send any kind of message up to its parent, including such things as status reports and errors. At thevery least it will send a completion message (failure or success). When the child completes, we compute a new direction vector and repeat the process, until we are successful or give up, in which casewe send a message to our parent. Domain Specific Actions Physical Schemas Primitive Actions Errors and Sensor Data Control Follow Move-To-Point Move Move Mobile Offense Harass Attack Apply Force Figure 2: Actions form a hierarchy control information is passed down, messages and sensor integration occurs bottom-up. Note that the implementation of an action is left completely up to the user she could decide to plan out all the movement steps in advance and simply schedule the next one when the move-to-point child completes. Or she could write a totally reactive implementation, as described above. Note also that every parent declares the set of messages it is interested in receiving. In some cases, a parent might only be interested in whether or not the child terminates. The parent can go to sleep while the child is executing. In other cases, the parent may request periodic status reports from the child, and run concurrently with the child in order to take corrective measures, such as interrupting the child. The very lowest level of the hierarchy consists of very primitive actions, things like the aforementioned move and apply-force. These actions are little more than low-level robotic eectors they set the blob's acceleration or attempt to do damage to a neighboring blob. Using these primitives, we build the layer of physical schemas, which consists of actions such as move-topoint, attack, and block. Above this layer we have domain-specic actions, if needed. It is interesting to
4 (defclass* swarm (level-n-action) (area swarm area (blobs nil) blobs involved in swarm storage (first-call t))) (defmethod handle-message ((game-state game-state) (action swarm) (message completion)) (redirect game-state action (blob (from message)))) (defmethod handle-message ((game-state game-state) (action swarm) (message afs-movement-message)) (interrupt-action game-state (from message)) (redirect game-state action (blob (from message)))) (defmethod redirect ((game-state game-state) (action swarm) blob) (start-new-child action game-state 'move-to-point :blob blob :destination-geom (make-destination-geom (random-location-in-geom (area action))) :messages-to-generate '(completion contact no-progress-in-movement) :speed nil :terminal-velocity nil)) (defmethod check-and-generate-message ((game-state game-state) (action swarm) (type (eql 'completion))) (values nil)) never completes (defmethod realize ((game-state game-state) (action swarm)) (when (first-call action) (setf (first-call action) nil) (loop for blob in (blobs action) do (redirect game-state action blob)))) Figure 3: Implementation of a multi-agent \swarm" behavior in HAC. note that as you go up the hierarchy, the actions tend to deal with larger time and space scales, and have more of a deliberative than a reactive character. But the transition to these cognitive actions is a smooth one no extra mechanism is needed to implement them. An Example Action Denition In the last section, we described in general terms how actions are dened within HAC. This section will elucidate the process using a concrete example and actual code. HAC provides a number of methods to make the process of writing actions easier. Across actions we must perform the same sort of tasks: generating messages for the parent, advancing the action, etc. In HAC, actions are classes each action denes a set of methods that address these tasks. Figure 3 shows the implementation of a multi-agent action, swarm. It is a simple action that causes a number of blobs to move around randomly within a circular region. We use the simpler action move-to-point to implement this it is invoked with the construct startnew-child. When the blobs bump or get stuck, they change direction. First, we dene the swarm action to be a level-n-action. This means it is non-primitiveand must handle messages from below aswell as pass messages up. We dene how we will react to messages from children using the handle-messages methods. Message handlers specialize on the type of message that a child might send. In the example, we redirect a blob to a new location when the move-to-point action controlling it completes. If the move-to-point reports any kind of error (all errors relating to movement are subclasses of afs-movement-message), such as contact with another blob, we simply interrupt it and redirect the blob somewhere else. These handle-messages methods are invoked whenever a message of the specied type is sent toswarm. When this happens, the realize method is also called. In our example, the realize method is only used for initialization: the rst time it is called, it sends all the blobs o to random locations. The set of check-and-generate methods dene the set of messages that this action can send up to its parents. When the realize message is called, the checkand-generate methods are invoked. We can specify if they should be called before or after the realize method. The swarm example never completes, and it doesn't report on its status, so it generates no messages. Note how simple it was to write a multi-agent action using the HAC methods. HAC is action-based, not blob-based. Writing an action for multiple blobs is no dierent from writing an action for a single blob that has to do several things at the same time (like turning and moving). Weenvision the dierent methods for implementing parts of actions as the beginnings of an action construction language, and we hopetomovehac in this direction. There would be constructs for combining actions, either sequentially or concurrently. There would be constructs specifying how resources should be used, whether or not something can be used by two agents at the same time, and so on.
5 Resources Resources are a very important part of agent control. There are many types of resources: the eectors of each individual agent, the objects in the world that agents use to fulll their tasks, and the agents themselves. Some resources can only be used by one agent at a time, some resources are scarce, and some resources emerge only in the process of performing some action. HAC provides mechanisms for managing resources and assigning resources to actions. HAC currently does not contain any general resource arbitration code, but instead assumes that a parent will arbitrate when its children are all vying for the same resources. Actions can return unused resources to their parent, who can then reassign them. Actions can also request more resources if they need them. The Sensor Hierarchy HAC not only supports a hierarchy of actions, but also a hierarchy of sensors. The sensor hierarchy is not yet fully implemented, so we will provide only a short description here. Just as a more complex action uses simpler ones to accomplish its goal, complex sensors use the values of simpler ones to compute their values. These are abstract sensors. They are not physical, since they don't sense anything directly from the world. They take the output of other sensors and integrate and re-interpret it. A low-level vision system (a physical sensor) produces a black and white pixel array. An abstract sensor might take this image and mark line segments in it. A higher level abstract sensor takes the line segments and determines whether or not there is a stretch of road ahead. A follow-road action can use this abstract sensor to compute where to go next. Since the lowest level sensors are associated with blobs moving around on the map, and higher level actions use abstract sensors that in turn use the values produced by these low level sensors, the structure of the sensor hierarchy will often mirror that of the action hierarchy. The two hierarchies cannot be merged, however. Suppose we have an abstract sensor that uses data from within a spatial region. This sensor uses all the data produced by blobs operating within this region, regardless of whether the blobs are all performing the same action. Thus, the two hierarchies might not correspond exactly. We are implementing a simple blackboard architecture that allows us to index sensor information based on location and type. We will still use the HAC's scheduling and message passing mechanism to organize sensors into a hierarchy, except that it is now sensor-update functions that are being scheduled, not actions, and sensor values that are being passed, not status reports and completion messages. Actions will use the blackboard to query sensors. An action can also ask to receive a message when a sensor achieves a certain value. Currently, actions do this checking themselves. These messages allow an action to be interrupted when a certain event occurs, enabling the action to take advantage of unexpected opportunities. The Planner As one of its modules, HAC includes a planner. How do goals and plans t into HAC's action hierarchy? Quite simply: Scheduling a child action can be viewed as posting a goal, and executing the child action that satises this goal. Planning is necessary when the goal is satis- ed by several actions and we have to decide between them. Simple goals, like moving to a location, are constrained enough that we can write out one good solution. All the actions we have seen so far were simple enough to require only one solution. But particularly as you get higher in the hierarchy, there will be more ambiguity with respect to how a goal should be achieved. Accordingly, goals might have multiple potential solutions. In HAC, we use the term \plan" to denote an action that satises a goal. We introduce a special child action, match-goal, that gets scheduled whenever an action posts a goal. Match-goal will check which plans can satisfy the goal, evaluate them, and choose the best one to execute. If no plan matches, match-goal reports failure back to the poster of the goal. Plans themselves may also contain sub-goals, which are satised using the same process. Plans are evaluated by a process of forward simulation: Instead of using some heuristic to pick the best plan, we actually use an even more abstract version of AFS to simulate what would happen if this plan were to execute. This process is made ecient by estimating the time at which something interesting will happen in the simulation, and advancing the simulation directly to these critical points. This type of planning, which uses stored solutions (plans) that are not fully elaborated, is known as partial hierarchical planning (George & Lansky 1986). Due to the exibility within the plans, it is particularly well suited to dealing with dynamic environments. In addition, the fact that we have pre-compiled solutions for certain types of problems cuts down enormously on the amount of search wewould otherwise have to do. Partial hierarchical planning meshes very well with the idea that people understand and reason about the world in terms of physical schemas. Viewed at the level of physical schemas, there really are only a few dierent ways to solve a problem. For example, if A and B are point masses, A can cause B to move by i) pushing it, ii) asking it to move (if it is an intentional agent), or iii) initiating movement in B. These separate solutions can be written down as plans that satisfy the goal \make Bmove". The exciting thing about planning at the physical schema level is that the plans you use are not limited to just one domain. If you can gure out what \move" and \push" mean in a domain, you can use your old plans.
6 Figure 4: The Capture the Flag domain. Since match-goal is a child action, just like any other, interleaving planning and execution is a straightforward process. Let's assume match-goal takes a certain amount of time, t, to nish evaluating all the plans that match. All this means is that it will take t time units before a plan starts executing. All other actions that the parent scheduled during this time interval will continue to execute normally. And since every action must be written to respond to failures or unexpected events in its children, so must a goal poster respond to the failure of one the matched plans. This is how replanning is initiated. An Example Domain: Capture the Flag We have been developing a dynamic and adversarial domain in which to test AFS, HAC, and the planner. This domain is based on the game of \Capture the Flag." There are two teams, red and blue. Some of the blobs on each team are of a special type, \ag" they cannot move. The objective for both teams is to capture all the opponent's ags. Figure 4 shows one of the randomly generated starting positions for this domain. Notice that we use dierent types of terrain. Some of the terrain, such as mountains and water, cannot be traversed by blobs,which gives us the opportunity to reason about such physical schemas as \blocked" and \constriction." We have constructed an action hierarchy based on the primitives move and apply-force that allows us to move to a location, attack a target, and defend a blob. We can also block passes or intercept hostile blobs. The top-level actions are more domain-specic and concern
7 themselves primarily with the allocation of resources. They generate a list of tasks, such as \attack anspecic enemy" or \defend a ag," and then construct a list of physical schemas that achieve these tasks. Each task mightbeachieved by more than one physical schema (a ag could be defended by placing blobs around it or by intercepting the blobs that are threatening it, for example). Depending on how tasks are weighted and what physical schemas are chosen to achieve these tasks, one arrives at dierent high-level solutions to the ultimate goal of capturing the opponent's ags. If attack tasks are weighted more strongly than defense, one mightend up with a more aggressive strategy. The dierent strategies correspond to dierent plans for achieving the goal \win-capture-the-ag." They are evaluated within match-goal by forward simulation. Forward simulation also takes into account howtheop- ponent might respond. The best plan, determined by a static evaluation function of the resulting map and placementofblobs,ischosen and executed. Our goal for this domain is to show how one can reason with physical schemas, and how this reasoning ts in with our general HAC architecture. Beating the computer is already non-trivial, and as our plans become more rened, it will only get harder. Furthermore, the actions we use and a lot of the reasoning we do during planning is not specic to the Capture the Flag domain. In fact, since we already had implementations of move-to-point and attack from other domains, it took us only two weeks to implement this scenario and a rst version of the plans that solve it. This speaks for the power and exibility ofhac. Summary and Discussion This paper has introduced AFS as a general simulator for any domain that can be described as agents moving and applying force to one another, and HAC as toolset for controlling such agents. We set out not to build a domain-specic agent design tool, but to only provide a general framework that helps the designer, and leaves the actual implementation up to her. These are the issues we believe HAC addresses well: Reactive and cognitive processes are integrated seamlessly. Agent control, action execution, planning, and sensing are all part of the same framework HAC is a modular system it can be used to control agents in simulation or real robots. Supervenience enables us build re-usable action modules. Ecient multi-agent control and simulation. Planning in continuous domains. Easy transference of knowledge across domains through the use of physical schemas. These are the issues we believe still need work: Communication between agents in the hierarchy, without going through a parent. An automatic domain to physics mapper. A fully implemented agent sensor model. A specication of an action construction language. Acknowledgements This research is supported by DARPA/USAF under contract numbers N C-8504, F , and F The U.S. Governmentis authorized to reproduce and distribute reprints for governmental purposes notwithstanding any copyright notation hereon. The views and conclusions contained herein are those of the authors and should not be interpreted as necessarily representing the ocial policies or endorsements either expressed or implied, of the Defense Advanced Research Projects Agency/Air Force Materiel Command or the U.S. Government. References Cohen, P. R. Greenberg, M. L. Hart, D. M. and Howe, A. E Trial by re: Understanding the design requirements for agents in complex environments. AI Magazine 10(3):32{48. George, M. P., and Lansky, A. L Procedural knowledge. IEEE Special Issue on Knowledge Representation 74(10):1383{1398. George, M. P., and Lansky, A. L Reactive reasoning and planning. In AAAI 87, 677{682. MIT Press. Karr, A. F Lanchester attrition processes and theater-level combat models. Technical report, Institute for Defense Analyses, Program Analysis Division, Arlington, VA. Spector, L., and Hendler, J The use of supervenience in dynamic-world planning. In Hammond, K., ed., Proceedings of The Second International Conference on Articial Intelligence Planning Systems, 158{ 163. Tzu, S The Art of War. Shambhala Publications.
 A Componentware Methodology based on Process Patterns Klaus Bergner, Andreas Rausch Marc Sihling, Alexander Vilbig Institut fur Informatik Technische Universitat Munchen D-80290 Munchen http://www4.informatik.tu-muenchen.de
A Componentware Methodology based on Process Patterns Klaus Bergner, Andreas Rausch Marc Sihling, Alexander Vilbig Institut fur Informatik Technische Universitat Munchen D-80290 Munchen http://www4.informatik.tu-muenchen.de
Envelopes as a Vehicle for Improving. David M. Hart, Scott D. Anderson, Paul R. Cohen. University of Massachusetts. Amherst, MA 01003.
 Envelopes as a Vehicle for Improving the Eciency of Plan Execution David M. Hart, Scott D. Anderson, Paul R. Cohen COINS Technical Report 90-21 Experimental Knowledge Systems Laboratory Department of Computer
Envelopes as a Vehicle for Improving the Eciency of Plan Execution David M. Hart, Scott D. Anderson, Paul R. Cohen COINS Technical Report 90-21 Experimental Knowledge Systems Laboratory Department of Computer
A Cognitive Approach to Vision for a Mobile Robot
 A Cognitive Approach to Vision for a Mobile Robot D. Paul Benjamin Christopher Funk Pace University, 1 Pace Plaza, New York, New York 10038, 212-346-1012 benjamin@pace.edu Damian Lyons Fordham University,
A Cognitive Approach to Vision for a Mobile Robot D. Paul Benjamin Christopher Funk Pace University, 1 Pace Plaza, New York, New York 10038, 212-346-1012 benjamin@pace.edu Damian Lyons Fordham University,
Reactive Agent Technology for Real-Time, Multisensor Target Tracking
 Reactive Agent Technology for Real-Time, Multisensor Target Tracking COSTAS TSATSOULIS AND EDWARD KOMP Department of Electrical Engineering and Computer Science Information and Telecommunication Technology
Reactive Agent Technology for Real-Time, Multisensor Target Tracking COSTAS TSATSOULIS AND EDWARD KOMP Department of Electrical Engineering and Computer Science Information and Telecommunication Technology
Developing an Artificial Intelligence Engine
 Introduction Developing an Artificial Intelligence Engine Michael van Lent and John Laird Artificial Intelligence Lab University of Michigan 1101 Beal Ave. Ann Arbor, MI 48109-2110 {vanlent,laird}@umich.edu
Introduction Developing an Artificial Intelligence Engine Michael van Lent and John Laird Artificial Intelligence Lab University of Michigan 1101 Beal Ave. Ann Arbor, MI 48109-2110 {vanlent,laird}@umich.edu
Blender Notes. Introduction to Digital Modelling and Animation in Design Blender Tutorial - week 9 The Game Engine
 Blender Notes Introduction to Digital Modelling and Animation in Design Blender Tutorial - week 9 The Game Engine The Blender Game Engine This week we will have an introduction to the Game Engine build
Blender Notes Introduction to Digital Modelling and Animation in Design Blender Tutorial - week 9 The Game Engine The Blender Game Engine This week we will have an introduction to the Game Engine build
 Repairing Plans On-the-y Brian Drabble, Je Dalton & Austin Tate Articial Intelligence Applications Institute University of Edinburgh 80 South Bridge Edinburgh EH1 1HN United Kingdom Tel: (+44) 131 650
Repairing Plans On-the-y Brian Drabble, Je Dalton & Austin Tate Articial Intelligence Applications Institute University of Edinburgh 80 South Bridge Edinburgh EH1 1HN United Kingdom Tel: (+44) 131 650
Intelligent Agents. Based on An Introduction to MultiAgent Systems and slides by Michael Wooldridge
 Intelligent Agents Based on An Introduction to MultiAgent Systems and slides by Michael Wooldridge Denition of an Agent An agent is a computer system capable of autonomous action in some environment, in
Intelligent Agents Based on An Introduction to MultiAgent Systems and slides by Michael Wooldridge Denition of an Agent An agent is a computer system capable of autonomous action in some environment, in
Managing large sound databases using Mpeg7
 Max Jacob 1 1 Institut de Recherche et Coordination Acoustique/Musique (IRCAM), place Igor Stravinsky 1, 75003, Paris, France Correspondence should be addressed to Max Jacob (max.jacob@ircam.fr) ABSTRACT
Max Jacob 1 1 Institut de Recherche et Coordination Acoustique/Musique (IRCAM), place Igor Stravinsky 1, 75003, Paris, France Correspondence should be addressed to Max Jacob (max.jacob@ircam.fr) ABSTRACT
picture of patterns in a dataset. useful results. Choosing appropriate operations hard for a human analyst to do alone, but because it
 Evaluation of a Semi-Autonomous Assistant for Exploratory Data Analysis Robert St. Amant Department of Computer Science North Carolina State University Box 8206 Raleigh, NC 27695-8206 stamant@csc.ncsu.edu
Evaluation of a Semi-Autonomous Assistant for Exploratory Data Analysis Robert St. Amant Department of Computer Science North Carolina State University Box 8206 Raleigh, NC 27695-8206 stamant@csc.ncsu.edu
How To Develop Software
 Software Engineering Prof. N.L. Sarda Computer Science & Engineering Indian Institute of Technology, Bombay Lecture-4 Overview of Phases (Part - II) We studied the problem definition phase, with which
Software Engineering Prof. N.L. Sarda Computer Science & Engineering Indian Institute of Technology, Bombay Lecture-4 Overview of Phases (Part - II) We studied the problem definition phase, with which
A Multi-Layer Distributed Development. Abstract. complex devices which may be dicult to model from an abstract point of view.
 A Multi-Layer Distributed Development Environment for Mobile Robotics Gregory Dudek Research Centre for Intelligent Machines McGill University Montreal, Quebec, Canada Michael Jenkin Department of Computer
A Multi-Layer Distributed Development Environment for Mobile Robotics Gregory Dudek Research Centre for Intelligent Machines McGill University Montreal, Quebec, Canada Michael Jenkin Department of Computer
DEALMAKER: An Agent for Selecting Sources of Supply To Fill Orders
 DEALMAKER: An Agent for Selecting Sources of Supply To Fill Orders Pedro Szekely, Bob Neches, David Benjamin, Jinbo Chen and Craig Milo Rogers USC/Information Sciences Institute Marina del Rey, CA 90292
DEALMAKER: An Agent for Selecting Sources of Supply To Fill Orders Pedro Szekely, Bob Neches, David Benjamin, Jinbo Chen and Craig Milo Rogers USC/Information Sciences Institute Marina del Rey, CA 90292
Software Quality Factors OOA, OOD, and OOP Object-oriented techniques enhance key external and internal software quality factors, e.g., 1. External (v
 Object-Oriented Design and Programming Deja Vu? In the past: Structured = Good Overview of Object-Oriented Design Principles and Techniques Today: Object-Oriented = Good e.g., Douglas C. Schmidt www.cs.wustl.edu/schmidt/
Object-Oriented Design and Programming Deja Vu? In the past: Structured = Good Overview of Object-Oriented Design Principles and Techniques Today: Object-Oriented = Good e.g., Douglas C. Schmidt www.cs.wustl.edu/schmidt/
PS engine. Execution
 A Model-Based Approach to the Verication of Program Supervision Systems Mar Marcos 1 y, Sabine Moisan z and Angel P. del Pobil y y Universitat Jaume I, Dept. of Computer Science Campus de Penyeta Roja,
A Model-Based Approach to the Verication of Program Supervision Systems Mar Marcos 1 y, Sabine Moisan z and Angel P. del Pobil y y Universitat Jaume I, Dept. of Computer Science Campus de Penyeta Roja,
Architecture bits. (Chromosome) (Evolved chromosome) Downloading. Downloading PLD. GA operation Architecture bits
 A Pattern Recognition System Using Evolvable Hardware Masaya Iwata 1 Isamu Kajitani 2 Hitoshi Yamada 2 Hitoshi Iba 1 Tetsuya Higuchi 1 1 1-1-4,Umezono,Tsukuba,Ibaraki,305,Japan Electrotechnical Laboratory
A Pattern Recognition System Using Evolvable Hardware Masaya Iwata 1 Isamu Kajitani 2 Hitoshi Yamada 2 Hitoshi Iba 1 Tetsuya Higuchi 1 1 1-1-4,Umezono,Tsukuba,Ibaraki,305,Japan Electrotechnical Laboratory
Distributed Database for Environmental Data Integration
 Distributed Database for Environmental Data Integration A. Amato', V. Di Lecce2, and V. Piuri 3 II Engineering Faculty of Politecnico di Bari - Italy 2 DIASS, Politecnico di Bari, Italy 3Dept Information
Distributed Database for Environmental Data Integration A. Amato', V. Di Lecce2, and V. Piuri 3 II Engineering Faculty of Politecnico di Bari - Italy 2 DIASS, Politecnico di Bari, Italy 3Dept Information
Levels of Analysis and ACT-R
 1 Levels of Analysis and ACT-R LaLoCo, Fall 2013 Adrian Brasoveanu, Karl DeVries [based on slides by Sharon Goldwater & Frank Keller] 2 David Marr: levels of analysis Background Levels of Analysis John
1 Levels of Analysis and ACT-R LaLoCo, Fall 2013 Adrian Brasoveanu, Karl DeVries [based on slides by Sharon Goldwater & Frank Keller] 2 David Marr: levels of analysis Background Levels of Analysis John
SYSTEMS AND SOFTWARE REQUIREMENTS SPECIFICATION (SSRS) TEMPLATE. Version A.4, January 2014 FOREWORD DOCUMENT CONVENTIONS
 SYSTEMS AND SOFTWARE REQUIREMENTS SPECIFICATION (SSRS) TEMPLATE Version A.4, January 2014 FOREWORD This document was written to provide software development projects with a template for generating a System
SYSTEMS AND SOFTWARE REQUIREMENTS SPECIFICATION (SSRS) TEMPLATE Version A.4, January 2014 FOREWORD This document was written to provide software development projects with a template for generating a System
The Generalized Railroad Crossing: A Case Study in Formal. Abstract
 The Generalized Railroad Crossing: A Case Study in Formal Verication of Real-Time Systems Constance Heitmeyer Nancy Lynch y Abstract A new solution to the Generalized Railroad Crossing problem, based on
The Generalized Railroad Crossing: A Case Study in Formal Verication of Real-Time Systems Constance Heitmeyer Nancy Lynch y Abstract A new solution to the Generalized Railroad Crossing problem, based on
Intelligent Flexible Automation
 Intelligent Flexible Automation David Peters Chief Executive Officer Universal Robotics February 20-22, 2013 Orlando World Marriott Center Orlando, Florida USA Trends in AI and Computing Power Convergence
Intelligent Flexible Automation David Peters Chief Executive Officer Universal Robotics February 20-22, 2013 Orlando World Marriott Center Orlando, Florida USA Trends in AI and Computing Power Convergence
Topology-based network security
 Topology-based network security Tiit Pikma Supervised by Vitaly Skachek Research Seminar in Cryptography University of Tartu, Spring 2013 1 Introduction In both wired and wireless networks, there is the
Topology-based network security Tiit Pikma Supervised by Vitaly Skachek Research Seminar in Cryptography University of Tartu, Spring 2013 1 Introduction In both wired and wireless networks, there is the
Memory Systems. Static Random Access Memory (SRAM) Cell
 Memory Systems This chapter begins the discussion of memory systems from the implementation of a single bit. The architecture of memory chips is then constructed using arrays of bit implementations coupled
Memory Systems This chapter begins the discussion of memory systems from the implementation of a single bit. The architecture of memory chips is then constructed using arrays of bit implementations coupled
Optimization Problems in Infrastructure Security
 Evangelos Kranakis, School of Computer Science, Carleton University, Ottawa 1 Optimization Problems in Infrastructure Security Evangelos Kranakis Carleton University School of Computer Science Ottawa,
Evangelos Kranakis, School of Computer Science, Carleton University, Ottawa 1 Optimization Problems in Infrastructure Security Evangelos Kranakis Carleton University School of Computer Science Ottawa,
DYNAMIC RANGE IMPROVEMENT THROUGH MULTIPLE EXPOSURES. Mark A. Robertson, Sean Borman, and Robert L. Stevenson
 c 1999 IEEE. Personal use of this material is permitted. However, permission to reprint/republish this material for advertising or promotional purposes or for creating new collective works for resale or
c 1999 IEEE. Personal use of this material is permitted. However, permission to reprint/republish this material for advertising or promotional purposes or for creating new collective works for resale or
Introduction to programming moway
 moway Contents Contents... 1 Introduction... 2 Flowcharts... 2 Movement blocks... 5 Conditionals... 6 Loops... 7 AND/OR Operators... 8 Setting flowcharts in order... 10 www.moway-robot.com 1 Introduction
moway Contents Contents... 1 Introduction... 2 Flowcharts... 2 Movement blocks... 5 Conditionals... 6 Loops... 7 AND/OR Operators... 8 Setting flowcharts in order... 10 www.moway-robot.com 1 Introduction
New Generation of Software Development
 New Generation of Software Development Terry Hon University of British Columbia 201-2366 Main Mall Vancouver B.C. V6T 1Z4 tyehon@cs.ubc.ca ABSTRACT In this paper, I present a picture of what software development
New Generation of Software Development Terry Hon University of British Columbia 201-2366 Main Mall Vancouver B.C. V6T 1Z4 tyehon@cs.ubc.ca ABSTRACT In this paper, I present a picture of what software development
Security Issues with the Military Use of Cellular Technology Brad Long, Director of Engineering, IFONE, Inc.
 Security Issues with the Military Use of Cellular Technology Brad Long, Director of Engineering, IFONE, Inc. Executive Summary IFONE provides securable private cellular networks. It presents this paper
Security Issues with the Military Use of Cellular Technology Brad Long, Director of Engineering, IFONE, Inc. Executive Summary IFONE provides securable private cellular networks. It presents this paper
Oscillations of the Sending Window in Compound TCP
 Oscillations of the Sending Window in Compound TCP Alberto Blanc 1, Denis Collange 1, and Konstantin Avrachenkov 2 1 Orange Labs, 905 rue Albert Einstein, 06921 Sophia Antipolis, France 2 I.N.R.I.A. 2004
Oscillations of the Sending Window in Compound TCP Alberto Blanc 1, Denis Collange 1, and Konstantin Avrachenkov 2 1 Orange Labs, 905 rue Albert Einstein, 06921 Sophia Antipolis, France 2 I.N.R.I.A. 2004
Outline. 1 Denitions. 2 Principles. 4 Implementation and Evaluation. 5 Debugging. 6 References
 Outline Computer Science 331 Introduction to Testing of Programs Mike Jacobson Department of Computer Science University of Calgary Lecture #3-4 1 Denitions 2 3 4 Implementation and Evaluation 5 Debugging
Outline Computer Science 331 Introduction to Testing of Programs Mike Jacobson Department of Computer Science University of Calgary Lecture #3-4 1 Denitions 2 3 4 Implementation and Evaluation 5 Debugging
Toward a Plan Steering Agent: Experiments with Schedule Maintenance
 Toward a Plan Steering Agent: Experiments with Schedule Maintenance Tim Oates and Paul R. Cohen Computer Science Department, LGRC University of Massachusetts Box 34610 Amherst, MA 01003-4610 oatesqcs.umass.edu,
Toward a Plan Steering Agent: Experiments with Schedule Maintenance Tim Oates and Paul R. Cohen Computer Science Department, LGRC University of Massachusetts Box 34610 Amherst, MA 01003-4610 oatesqcs.umass.edu,
Thesis work and research project
 Thesis work and research project Hélia Pouyllau, INRIA of Rennes, Campus Beaulieu 35042 Rennes, helia.pouyllau@irisa.fr July 16, 2007 1 Thesis work on Distributed algorithms for endto-end QoS contract
Thesis work and research project Hélia Pouyllau, INRIA of Rennes, Campus Beaulieu 35042 Rennes, helia.pouyllau@irisa.fr July 16, 2007 1 Thesis work on Distributed algorithms for endto-end QoS contract
Software development process
 OpenStax-CNX module: m14619 1 Software development process Trung Hung VO This work is produced by OpenStax-CNX and licensed under the Creative Commons Attribution License 2.0 Abstract A software development
OpenStax-CNX module: m14619 1 Software development process Trung Hung VO This work is produced by OpenStax-CNX and licensed under the Creative Commons Attribution License 2.0 Abstract A software development
The Scientific Data Mining Process
 Chapter 4 The Scientific Data Mining Process When I use a word, Humpty Dumpty said, in rather a scornful tone, it means just what I choose it to mean neither more nor less. Lewis Carroll [87, p. 214] In
Chapter 4 The Scientific Data Mining Process When I use a word, Humpty Dumpty said, in rather a scornful tone, it means just what I choose it to mean neither more nor less. Lewis Carroll [87, p. 214] In
Options with exceptions
 Options with exceptions Munu Sairamesh and Balaraman Ravindran Indian Institute Of Technology Madras, India Abstract. An option is a policy fragment that represents a solution to a frequent subproblem
Options with exceptions Munu Sairamesh and Balaraman Ravindran Indian Institute Of Technology Madras, India Abstract. An option is a policy fragment that represents a solution to a frequent subproblem
Developing an Inventory Management System for Second Life
 Developing an Inventory Management System for Second Life Abstract Anthony Rosequist Workflow For the progress report a month ago, I set the goal to have a basic, functional inventory management system
Developing an Inventory Management System for Second Life Abstract Anthony Rosequist Workflow For the progress report a month ago, I set the goal to have a basic, functional inventory management system
2013 International Symposium on Green Manufacturing and Applications Honolulu, Hawaii
 Green Robotics, Automation, and Machine Intelligence; a new Engineering Course in Sustainable Design Joseph T. Wunderlich, PhD College, PA, USA 2013 International Symposium on Green Manufacturing and Applications
Green Robotics, Automation, and Machine Intelligence; a new Engineering Course in Sustainable Design Joseph T. Wunderlich, PhD College, PA, USA 2013 International Symposium on Green Manufacturing and Applications
A STRATEGIC PLANNER FOR ROBOT EXCAVATION' by Humberto Romero-Lois, Research Assistant, Department of Civil Engineering
 A STRATEGIC PLANNER FOR ROBOT EXCAVATION' by Humberto Romero-Lois, Research Assistant, Department of Civil Engineering Chris Hendrickson, Professor, Department of Civil Engineering, and Irving Oppenheim,
A STRATEGIC PLANNER FOR ROBOT EXCAVATION' by Humberto Romero-Lois, Research Assistant, Department of Civil Engineering Chris Hendrickson, Professor, Department of Civil Engineering, and Irving Oppenheim,
An Intelligent Assistant for Computer-Aided Design Extended Abstract
 From: AAAI Technical Report SS-00-04. Compilation copyright 2000, AAAI (www.aaai.org). All rights reserved. An Intelligent Assistant for Computer-Aided Design Extended Abstract Olivier St-Cyr, Yves Lespérance,
From: AAAI Technical Report SS-00-04. Compilation copyright 2000, AAAI (www.aaai.org). All rights reserved. An Intelligent Assistant for Computer-Aided Design Extended Abstract Olivier St-Cyr, Yves Lespérance,
Experiment 7 ~ Conservation of Linear Momentum
 Experiment 7 ~ Conservation of Linear Momentum Purpose: The purpose of this experiment is to reproduce a simple experiment demonstrating the Conservation of Linear Momentum. Theory: The momentum p of an
Experiment 7 ~ Conservation of Linear Momentum Purpose: The purpose of this experiment is to reproduce a simple experiment demonstrating the Conservation of Linear Momentum. Theory: The momentum p of an
3.2 Roulette and Markov Chains
 238 CHAPTER 3. DISCRETE DYNAMICAL SYSTEMS WITH MANY VARIABLES 3.2 Roulette and Markov Chains In this section we will be discussing an application of systems of recursion equations called Markov Chains.
238 CHAPTER 3. DISCRETE DYNAMICAL SYSTEMS WITH MANY VARIABLES 3.2 Roulette and Markov Chains In this section we will be discussing an application of systems of recursion equations called Markov Chains.
8. KNOWLEDGE BASED SYSTEMS IN MANUFACTURING SIMULATION
 - 1-8. KNOWLEDGE BASED SYSTEMS IN MANUFACTURING SIMULATION 8.1 Introduction 8.1.1 Summary introduction The first part of this section gives a brief overview of some of the different uses of expert systems
- 1-8. KNOWLEDGE BASED SYSTEMS IN MANUFACTURING SIMULATION 8.1 Introduction 8.1.1 Summary introduction The first part of this section gives a brief overview of some of the different uses of expert systems
How To Model Data For Business Intelligence (Bi)
 WHITE PAPER: THE BENEFITS OF DATA MODELING IN BUSINESS INTELLIGENCE The Benefits of Data Modeling in Business Intelligence DECEMBER 2008 Table of Contents Executive Summary 1 SECTION 1 2 Introduction 2
WHITE PAPER: THE BENEFITS OF DATA MODELING IN BUSINESS INTELLIGENCE The Benefits of Data Modeling in Business Intelligence DECEMBER 2008 Table of Contents Executive Summary 1 SECTION 1 2 Introduction 2
22C:22 (CS:2820) Object-Oriented Software Development
 The University of Iowa 22C:22 (CS:2820) Object-Oriented Software Development Fall 2012 Software Complexity by Cesare Tinelli Complexity Software systems are complex artifacts Failure to master this complexity
The University of Iowa 22C:22 (CS:2820) Object-Oriented Software Development Fall 2012 Software Complexity by Cesare Tinelli Complexity Software systems are complex artifacts Failure to master this complexity
Grid Computing for Artificial Intelligence
 Grid Computing for Artificial Intelligence J.M.P. van Waveren May 25th 2007 2007, Id Software, Inc. Abstract To show intelligent behavior in a First Person Shooter (FPS) game an Artificial Intelligence
Grid Computing for Artificial Intelligence J.M.P. van Waveren May 25th 2007 2007, Id Software, Inc. Abstract To show intelligent behavior in a First Person Shooter (FPS) game an Artificial Intelligence
Software Engineering
 Software Engineering Lecture 06: Design an Overview Peter Thiemann University of Freiburg, Germany SS 2013 Peter Thiemann (Univ. Freiburg) Software Engineering SWT 1 / 35 The Design Phase Programming in
Software Engineering Lecture 06: Design an Overview Peter Thiemann University of Freiburg, Germany SS 2013 Peter Thiemann (Univ. Freiburg) Software Engineering SWT 1 / 35 The Design Phase Programming in
The Trip Scheduling Problem
 The Trip Scheduling Problem Claudia Archetti Department of Quantitative Methods, University of Brescia Contrada Santa Chiara 50, 25122 Brescia, Italy Martin Savelsbergh School of Industrial and Systems
The Trip Scheduling Problem Claudia Archetti Department of Quantitative Methods, University of Brescia Contrada Santa Chiara 50, 25122 Brescia, Italy Martin Savelsbergh School of Industrial and Systems
A Business Process Driven Approach for Generating Software Modules
 A Business Process Driven Approach for Generating Software Modules Xulin Zhao, Ying Zou Dept. of Electrical and Computer Engineering, Queen s University, Kingston, ON, Canada SUMMARY Business processes
A Business Process Driven Approach for Generating Software Modules Xulin Zhao, Ying Zou Dept. of Electrical and Computer Engineering, Queen s University, Kingston, ON, Canada SUMMARY Business processes
Artificial Intelligence Approaches to Spacecraft Scheduling
 Artificial Intelligence Approaches to Spacecraft Scheduling Mark D. Johnston Space Telescope Science Institute/Space Telescope-European Coordinating Facility Summary: The problem of optimal spacecraft
Artificial Intelligence Approaches to Spacecraft Scheduling Mark D. Johnston Space Telescope Science Institute/Space Telescope-European Coordinating Facility Summary: The problem of optimal spacecraft
A refined architecture for DRM
 A refined architecture for DRM Koen Buyens Sam Michiels Wouter Joosen Report CW 450, June 2006 nkatholieke Universiteit Leuven Department of Computer Science Celestijnenlaan 200A B-3001 Heverlee (Belgium)
A refined architecture for DRM Koen Buyens Sam Michiels Wouter Joosen Report CW 450, June 2006 nkatholieke Universiteit Leuven Department of Computer Science Celestijnenlaan 200A B-3001 Heverlee (Belgium)
Introduction. Chapter 1
 1 Chapter 1 Introduction Robotics and automation have undergone an outstanding development in the manufacturing industry over the last decades owing to the increasing demand for higher levels of productivity
1 Chapter 1 Introduction Robotics and automation have undergone an outstanding development in the manufacturing industry over the last decades owing to the increasing demand for higher levels of productivity
RS MDM. Integration Guide. Riversand
 RS MDM 2009 Integration Guide This document provides the details about RS MDMCenter integration module and provides details about the overall architecture and principles of integration with the system.
RS MDM 2009 Integration Guide This document provides the details about RS MDMCenter integration module and provides details about the overall architecture and principles of integration with the system.
Implementing GIS in Optical Fiber. Communication
 KING FAHD UNIVERSITY OF PETROLEUM AND MINERALS COLLEGE OF ENVIRONMENTAL DESIGN CITY & RIGINAL PLANNING DEPARTMENT TERM ROJECT Implementing GIS in Optical Fiber Communication By Ahmed Saeed Bagazi ID# 201102590
KING FAHD UNIVERSITY OF PETROLEUM AND MINERALS COLLEGE OF ENVIRONMENTAL DESIGN CITY & RIGINAL PLANNING DEPARTMENT TERM ROJECT Implementing GIS in Optical Fiber Communication By Ahmed Saeed Bagazi ID# 201102590
Visualization Quick Guide
 Visualization Quick Guide A best practice guide to help you find the right visualization for your data WHAT IS DOMO? Domo is a new form of business intelligence (BI) unlike anything before an executive
Visualization Quick Guide A best practice guide to help you find the right visualization for your data WHAT IS DOMO? Domo is a new form of business intelligence (BI) unlike anything before an executive
RoCKIn@Work Innovation in Industrial Mobile Manipulation
 Robot Competitions Kick Innovation in Cognitive Systems and Robotics FP7-ICT-601012 RoCKIn@Work Innovation in Industrial Mobile Manipulation I: RoCKIn@Work in a Nutshell Revision: Date: Editors: Contributors:
Robot Competitions Kick Innovation in Cognitive Systems and Robotics FP7-ICT-601012 RoCKIn@Work Innovation in Industrial Mobile Manipulation I: RoCKIn@Work in a Nutshell Revision: Date: Editors: Contributors:
Service Oriented Architecture
 Service Oriented Architecture Service Oriented Analysis and Design (SOAD) in Practice Part 4 Adomas Svirskas Vilnius University October 2005 Agenda Service identification and definition Business process
Service Oriented Architecture Service Oriented Analysis and Design (SOAD) in Practice Part 4 Adomas Svirskas Vilnius University October 2005 Agenda Service identification and definition Business process
Using the TASKING Software Platform for AURIX
 Using the TASKING Software Platform for AURIX MA160-869 (v1.0rb3) June 19, 2015 Copyright 2015 Altium BV. All rights reserved. You are permitted to print this document provided that (1) the use of such
Using the TASKING Software Platform for AURIX MA160-869 (v1.0rb3) June 19, 2015 Copyright 2015 Altium BV. All rights reserved. You are permitted to print this document provided that (1) the use of such
The Benefits of Data Modeling in Business Intelligence
 WHITE PAPER: THE BENEFITS OF DATA MODELING IN BUSINESS INTELLIGENCE The Benefits of Data Modeling in Business Intelligence DECEMBER 2008 Table of Contents Executive Summary 1 SECTION 1 2 Introduction 2
WHITE PAPER: THE BENEFITS OF DATA MODELING IN BUSINESS INTELLIGENCE The Benefits of Data Modeling in Business Intelligence DECEMBER 2008 Table of Contents Executive Summary 1 SECTION 1 2 Introduction 2
INTRUSION PREVENTION AND EXPERT SYSTEMS
 INTRUSION PREVENTION AND EXPERT SYSTEMS By Avi Chesla avic@v-secure.com Introduction Over the past few years, the market has developed new expectations from the security industry, especially from the intrusion
INTRUSION PREVENTION AND EXPERT SYSTEMS By Avi Chesla avic@v-secure.com Introduction Over the past few years, the market has developed new expectations from the security industry, especially from the intrusion
Journal of Information Technology Management SIGNS OF IT SOLUTIONS FAILURE: REASONS AND A PROPOSED SOLUTION ABSTRACT
 Journal of Information Technology Management ISSN #1042-1319 A Publication of the Association of Management SIGNS OF IT SOLUTIONS FAILURE: REASONS AND A PROPOSED SOLUTION MAJED ABUSAFIYA NEW MEXICO TECH
Journal of Information Technology Management ISSN #1042-1319 A Publication of the Association of Management SIGNS OF IT SOLUTIONS FAILURE: REASONS AND A PROPOSED SOLUTION MAJED ABUSAFIYA NEW MEXICO TECH
Design of Intelligent Robotics. René van de Molengraft December, 6th, 2010
 Design of Intelligent Robotics René van de Molengraft December, 6th, 2010 Theme Health: Care and Cure 11-12-2009 PAGE 2 Mission Help elderly people to stay in their homes Improve quality of surgery for
Design of Intelligent Robotics René van de Molengraft December, 6th, 2010 Theme Health: Care and Cure 11-12-2009 PAGE 2 Mission Help elderly people to stay in their homes Improve quality of surgery for
How to Design and Maintain a Secure ICS Network
 Whitepaper How to Design and Maintain a Secure ICS Network Support IEC 62443 Compliance with SilentDefense ICS Authors Daniel Trivellato, PhD - Product Manager Industrial Line Dennis Murphy, MSc - Senior
Whitepaper How to Design and Maintain a Secure ICS Network Support IEC 62443 Compliance with SilentDefense ICS Authors Daniel Trivellato, PhD - Product Manager Industrial Line Dennis Murphy, MSc - Senior
Cognitive Robotics: High-Level Robot Programming Inspired by Cognitive Science
 Cognitive Robotics: High-Level Robot Programming Inspired by Cognitive Science David S. Touretzky Ethan Tira-Thompson Computer Science Department Carnegie Mellon University Pittsburgh, PA 15213-3891 July
Cognitive Robotics: High-Level Robot Programming Inspired by Cognitive Science David S. Touretzky Ethan Tira-Thompson Computer Science Department Carnegie Mellon University Pittsburgh, PA 15213-3891 July
Architectural Patterns. Layers: Pattern. Architectural Pattern Examples. Layer 3. Component 3.1. Layer 2. Component 2.1 Component 2.2.
 Architectural Patterns Architectural Patterns Dr. James A. Bednar jbednar@inf.ed.ac.uk http://homepages.inf.ed.ac.uk/jbednar Dr. David Robertson dr@inf.ed.ac.uk http://www.inf.ed.ac.uk/ssp/members/dave.htm
Architectural Patterns Architectural Patterns Dr. James A. Bednar jbednar@inf.ed.ac.uk http://homepages.inf.ed.ac.uk/jbednar Dr. David Robertson dr@inf.ed.ac.uk http://www.inf.ed.ac.uk/ssp/members/dave.htm
The 2014 Bottleneck Report on Enterprise Mobile
 The 2014 Bottleneck Report on Enterprise Mobile What s the big bottleneck for enterprise mobile app development this year, and how do you get past it? 1 / 32 The 2014 Bottleneck Report on Enterprise Mobile
The 2014 Bottleneck Report on Enterprise Mobile What s the big bottleneck for enterprise mobile app development this year, and how do you get past it? 1 / 32 The 2014 Bottleneck Report on Enterprise Mobile
Event Management Proposal for Distribution Data Service Standard
 Event Management Proposal for Distribution Service Standard José-Luis Poza-Luján, Juan-Luis Posadas-Yagüe and José-Enrique Simó-Ten University Institute of Control Systems and Industrial Computing (ai2).
Event Management Proposal for Distribution Service Standard José-Luis Poza-Luján, Juan-Luis Posadas-Yagüe and José-Enrique Simó-Ten University Institute of Control Systems and Industrial Computing (ai2).
Agent Simulation of Hull s Drive Theory
 Agent Simulation of Hull s Drive Theory Nick Schmansky Department of Cognitive and Neural Systems Boston University March 7, 4 Abstract A computer simulation was conducted of an agent attempting to survive
Agent Simulation of Hull s Drive Theory Nick Schmansky Department of Cognitive and Neural Systems Boston University March 7, 4 Abstract A computer simulation was conducted of an agent attempting to survive
Explore 3: Crash Test Dummies
 Explore : Crash Test Dummies Type of Lesson: Learning Goal & Instructiona l Objectives Content with Process: Focus on constructing knowledge through active learning. Students investigate Newton s first
Explore : Crash Test Dummies Type of Lesson: Learning Goal & Instructiona l Objectives Content with Process: Focus on constructing knowledge through active learning. Students investigate Newton s first
Malay A. Dalal Madhav Erraguntla Perakath Benjamin. Knowledge Based Systems, Inc. (KBSI) College Station, TX 77840, U.S.A.
 AN INTRODUCTION TO USING PROSIM FOR BUSINESS PROCESS SIMULATION AND ANALYSIS Malay A. Dalal Madhav Erraguntla Perakath Benjamin Knowledge Based Systems, Inc. (KBSI) College Station, TX 77840, U.S.A. ABSTRACT
AN INTRODUCTION TO USING PROSIM FOR BUSINESS PROCESS SIMULATION AND ANALYSIS Malay A. Dalal Madhav Erraguntla Perakath Benjamin Knowledge Based Systems, Inc. (KBSI) College Station, TX 77840, U.S.A. ABSTRACT
2.5 Physically-based Animation
 2.5 Physically-based Animation 320491: Advanced Graphics - Chapter 2 74 Physically-based animation Morphing allowed us to animate between two known states. Typically, only one state of an object is known.
2.5 Physically-based Animation 320491: Advanced Graphics - Chapter 2 74 Physically-based animation Morphing allowed us to animate between two known states. Typically, only one state of an object is known.
Sophisticated Indicators for the Modern Threat Landscape: An Introduction to OpenIOC
 WHITE PAPER Sophisticated Indicators for the Modern Threat Landscape: An Introduction to OpenIOC www.openioc.org OpenIOC 1 Table of Contents Introduction... 3 IOCs & OpenIOC... 4 IOC Functionality... 5
WHITE PAPER Sophisticated Indicators for the Modern Threat Landscape: An Introduction to OpenIOC www.openioc.org OpenIOC 1 Table of Contents Introduction... 3 IOCs & OpenIOC... 4 IOC Functionality... 5
A MODEL OF HUMAN COGNITIVE BEHAVIOR IN WRITING CODE FOR COMPUTER PROGRAMS
 A MODEL OF HUMAN COGNITIVE BEHAVIOR IN WRITING CODE FOR COMPUTER PROGRAMS Ruven Brooke Department of Information and Computer Science University of California - Irvine Irvine, CA 92664 U.S.A. Section 12:
A MODEL OF HUMAN COGNITIVE BEHAVIOR IN WRITING CODE FOR COMPUTER PROGRAMS Ruven Brooke Department of Information and Computer Science University of California - Irvine Irvine, CA 92664 U.S.A. Section 12:
EVALUATION. WA1844 WebSphere Process Server 7.0 Programming Using WebSphere Integration COPY. Developer
 WA1844 WebSphere Process Server 7.0 Programming Using WebSphere Integration Developer Web Age Solutions Inc. USA: 1-877-517-6540 Canada: 1-866-206-4644 Web: http://www.webagesolutions.com Chapter 6 - Introduction
WA1844 WebSphere Process Server 7.0 Programming Using WebSphere Integration Developer Web Age Solutions Inc. USA: 1-877-517-6540 Canada: 1-866-206-4644 Web: http://www.webagesolutions.com Chapter 6 - Introduction
Sensory-motor control scheme based on Kohonen Maps and AVITE model
 Sensory-motor control scheme based on Kohonen Maps and AVITE model Juan L. Pedreño-Molina, Antonio Guerrero-González, Oscar A. Florez-Giraldo, J. Molina-Vilaplana Technical University of Cartagena Department
Sensory-motor control scheme based on Kohonen Maps and AVITE model Juan L. Pedreño-Molina, Antonio Guerrero-González, Oscar A. Florez-Giraldo, J. Molina-Vilaplana Technical University of Cartagena Department
Report Data Management in the Cloud: Limitations and Opportunities
 Report Data Management in the Cloud: Limitations and Opportunities Article by Daniel J. Abadi [1] Report by Lukas Probst January 4, 2013 In this report I want to summarize Daniel J. Abadi's article [1]
Report Data Management in the Cloud: Limitations and Opportunities Article by Daniel J. Abadi [1] Report by Lukas Probst January 4, 2013 In this report I want to summarize Daniel J. Abadi's article [1]
The Top FIVE Metrics. For Revenue Generation Marketers
 The Top FIVE Metrics For Revenue Generation Marketers Introduction It s an old cliché but true: you manage what you measure. One implication is that when a business changes, measures should change as well.
The Top FIVE Metrics For Revenue Generation Marketers Introduction It s an old cliché but true: you manage what you measure. One implication is that when a business changes, measures should change as well.
GOAL-BASED INTELLIGENT AGENTS
 International Journal of Information Technology, Vol. 9 No. 1 GOAL-BASED INTELLIGENT AGENTS Zhiqi Shen, Robert Gay and Xuehong Tao ICIS, School of EEE, Nanyang Technological University, Singapore 639798
International Journal of Information Technology, Vol. 9 No. 1 GOAL-BASED INTELLIGENT AGENTS Zhiqi Shen, Robert Gay and Xuehong Tao ICIS, School of EEE, Nanyang Technological University, Singapore 639798
Obstacles and opportunities for model-based testing. in an industrial software environment
 Obstacles and opportunities for model-based testing in an industrial software environment Harry Robinson Test Architect, Enterprise Management Division Microsoft Corporation harryr@microsoft.com Abstract
Obstacles and opportunities for model-based testing in an industrial software environment Harry Robinson Test Architect, Enterprise Management Division Microsoft Corporation harryr@microsoft.com Abstract
Aspect-Oriented Programming
 Aspect-Oriented Programming An Introduction to Aspect-Oriented Programming and AspectJ Niklas Påhlsson Department of Technology University of Kalmar S 391 82 Kalmar SWEDEN Topic Report for Software Engineering
Aspect-Oriented Programming An Introduction to Aspect-Oriented Programming and AspectJ Niklas Påhlsson Department of Technology University of Kalmar S 391 82 Kalmar SWEDEN Topic Report for Software Engineering
Ontology and automatic code generation on modeling and simulation
 Ontology and automatic code generation on modeling and simulation Youcef Gheraibia Computing Department University Md Messadia Souk Ahras, 41000, Algeria youcef.gheraibia@gmail.com Abdelhabib Bourouis
Ontology and automatic code generation on modeling and simulation Youcef Gheraibia Computing Department University Md Messadia Souk Ahras, 41000, Algeria youcef.gheraibia@gmail.com Abdelhabib Bourouis
MAPS USER. Global Planner. Local Planner. actuators TR+ TREES ENVIRONMENT. sensors GLOBAL PLANNING LOCAL PLANNING
 DRAFT SUBMITTED TO IEEE TRANSACTIONS ROBOTICS & AUTOMATION, 1998 1 SPOTT: A Predictable and Scalable Architecture for Autonomous Mobile Robot Control John S. Zelek and Martin D. Levine Abstract A robot
DRAFT SUBMITTED TO IEEE TRANSACTIONS ROBOTICS & AUTOMATION, 1998 1 SPOTT: A Predictable and Scalable Architecture for Autonomous Mobile Robot Control John S. Zelek and Martin D. Levine Abstract A robot
The Benefits of Data Modeling in Business Intelligence. www.erwin.com
 The Benefits of Data Modeling in Business Intelligence Table of Contents Executive Summary...... 3 Introduction.... 3 Why Data Modeling for BI Is Unique...... 4 Understanding the Meaning of Information.....
The Benefits of Data Modeling in Business Intelligence Table of Contents Executive Summary...... 3 Introduction.... 3 Why Data Modeling for BI Is Unique...... 4 Understanding the Meaning of Information.....
Expanding the CASEsim Framework to Facilitate Load Balancing of Social Network Simulations
 Expanding the CASEsim Framework to Facilitate Load Balancing of Social Network Simulations Amara Keller, Martin Kelly, Aaron Todd 4 June 2010 Abstract This research has two components, both involving the
Expanding the CASEsim Framework to Facilitate Load Balancing of Social Network Simulations Amara Keller, Martin Kelly, Aaron Todd 4 June 2010 Abstract This research has two components, both involving the
Vector storage and access; algorithms in GIS. This is lecture 6
 Vector storage and access; algorithms in GIS This is lecture 6 Vector data storage and access Vectors are built from points, line and areas. (x,y) Surface: (x,y,z) Vector data access Access to vector
Vector storage and access; algorithms in GIS This is lecture 6 Vector data storage and access Vectors are built from points, line and areas. (x,y) Surface: (x,y,z) Vector data access Access to vector
CA Workload Automation Agents Operating System, ERP, Database, Application Services and Web Services
 PRODUCT SHEET CA Workload Automation Agents CA Workload Automation Agents Operating System, ERP, Database, Application Services and Web Services CA Workload Automation Agents extend the automation capabilities
PRODUCT SHEET CA Workload Automation Agents CA Workload Automation Agents Operating System, ERP, Database, Application Services and Web Services CA Workload Automation Agents extend the automation capabilities
A METHODOLOGY FOR KNOWLEDGE DISCOVERY AND CLASSIFICATION. University of Massachusetts Amherst, MA 01003-2210. 15021 21 Drive, SE Mill Creek WA, 98012
 A METHODOLOGY FOR KNOWLEDGE DISCOVERY AND CLASSIFICATION Janis Terpenny 1, Stephen Strong 2, Jiachuan Wang 1 1 Department of Mechanical and Industrial Engineering University of Massachusetts Amherst, MA
A METHODOLOGY FOR KNOWLEDGE DISCOVERY AND CLASSIFICATION Janis Terpenny 1, Stephen Strong 2, Jiachuan Wang 1 1 Department of Mechanical and Industrial Engineering University of Massachusetts Amherst, MA
The Encryption Anywhere Data Protection Platform
 The Encryption Anywhere Data Protection Platform A Technical White Paper 5 December 2005 475 Brannan Street, Suite 400, San Francisco CA 94107-5421 800-440-0419 415-683-2200 Fax 415-683-2349 For more information,
The Encryption Anywhere Data Protection Platform A Technical White Paper 5 December 2005 475 Brannan Street, Suite 400, San Francisco CA 94107-5421 800-440-0419 415-683-2200 Fax 415-683-2349 For more information,
(Refer Slide Time: 02:39)
 Computer Architecture Prof. Anshul Kumar Department of Computer Science and Engineering, Indian Institute of Technology, Delhi Lecture - 1 Introduction Welcome to this course on computer architecture.
Computer Architecture Prof. Anshul Kumar Department of Computer Science and Engineering, Indian Institute of Technology, Delhi Lecture - 1 Introduction Welcome to this course on computer architecture.
Adventures in Estimating Open Source, Component Systems, Agile, and SOA Projects
 Open Source, Component Systems, Agile, and SOA Projects Terry Vogt Lead Associate Booz Allen Hamilton Sept 13, 2011 Ready for what s next 1 Booz Allen Hamilton 1 Agenda Background Open Source Component
Open Source, Component Systems, Agile, and SOA Projects Terry Vogt Lead Associate Booz Allen Hamilton Sept 13, 2011 Ready for what s next 1 Booz Allen Hamilton 1 Agenda Background Open Source Component
A Model of Distraction using new Architectural Mechanisms to Manage Multiple Goals
 A Model of Distraction using new Architectural Mechanisms to Manage Multiple Goals Niels A. Taatgen (n.a.taatgen@rug.nl), Ioanna Katidioti (i.katidioti@rug.nl), Jelmer Borst (j.p.borst@rug.nl) & Marieke
A Model of Distraction using new Architectural Mechanisms to Manage Multiple Goals Niels A. Taatgen (n.a.taatgen@rug.nl), Ioanna Katidioti (i.katidioti@rug.nl), Jelmer Borst (j.p.borst@rug.nl) & Marieke
A very short history of networking
 A New vision for network architecture David Clark M.I.T. Laboratory for Computer Science September, 2002 V3.0 Abstract This is a proposal for a long-term program in network research, consistent with the
A New vision for network architecture David Clark M.I.T. Laboratory for Computer Science September, 2002 V3.0 Abstract This is a proposal for a long-term program in network research, consistent with the
Advantages of Auto-tuning for Servo-motors
 Advantages of for Servo-motors Executive summary The same way that 2 years ago computer science introduced plug and play, where devices would selfadjust to existing system hardware, industrial motion control
Advantages of for Servo-motors Executive summary The same way that 2 years ago computer science introduced plug and play, where devices would selfadjust to existing system hardware, industrial motion control
Development of a Network Configuration Management System Using Artificial Neural Networks
 Development of a Network Configuration Management System Using Artificial Neural Networks R. Ramiah*, E. Gemikonakli, and O. Gemikonakli** *MSc Computer Network Management, **Tutor and Head of Department
Development of a Network Configuration Management System Using Artificial Neural Networks R. Ramiah*, E. Gemikonakli, and O. Gemikonakli** *MSc Computer Network Management, **Tutor and Head of Department
Euler: A System for Numerical Optimization of Programs
 Euler: A System for Numerical Optimization of Programs Swarat Chaudhuri 1 and Armando Solar-Lezama 2 1 Rice University 2 MIT Abstract. We give a tutorial introduction to Euler, a system for solving difficult
Euler: A System for Numerical Optimization of Programs Swarat Chaudhuri 1 and Armando Solar-Lezama 2 1 Rice University 2 MIT Abstract. We give a tutorial introduction to Euler, a system for solving difficult
?kt. An Unconventional Method for Load Balancing. w = C ( t m a z - ti) = p(tmaz - 0i=l. 1 Introduction. R. Alan McCoy,*
 ENL-62052 An Unconventional Method for Load Balancing Yuefan Deng,* R. Alan McCoy,* Robert B. Marr,t Ronald F. Peierlst Abstract A new method of load balancing is introduced based on the idea of dynamically
ENL-62052 An Unconventional Method for Load Balancing Yuefan Deng,* R. Alan McCoy,* Robert B. Marr,t Ronald F. Peierlst Abstract A new method of load balancing is introduced based on the idea of dynamically
Department of Computer and Information Science, Ohio State University. In Section 3, the concepts and structure of signature
 Proceedings of the 2nd International Computer Science Conference, Hong Kong, Dec. 1992, 616-622. 616 SIGNATURE FILE METHODS FOR INDEXING OBJECT-ORIENTED DATABASE SYSTEMS Wang-chien Lee and Dik L. Lee Department
Proceedings of the 2nd International Computer Science Conference, Hong Kong, Dec. 1992, 616-622. 616 SIGNATURE FILE METHODS FOR INDEXING OBJECT-ORIENTED DATABASE SYSTEMS Wang-chien Lee and Dik L. Lee Department
1 Example of Time Series Analysis by SSA 1
 1 Example of Time Series Analysis by SSA 1 Let us illustrate the 'Caterpillar'-SSA technique [1] by the example of time series analysis. Consider the time series FORT (monthly volumes of fortied wine sales
1 Example of Time Series Analysis by SSA 1 Let us illustrate the 'Caterpillar'-SSA technique [1] by the example of time series analysis. Consider the time series FORT (monthly volumes of fortied wine sales
Environments. Peri Tarr. Lori A. Clarke. Software Development Laboratory. University of Massachusetts
 Pleiades: An Object Management System for Software Engineering Environments Peri Tarr Lori A. Clarke Software Development Laboratory Department of Computer Science University of Massachusetts Amherst,
Pleiades: An Object Management System for Software Engineering Environments Peri Tarr Lori A. Clarke Software Development Laboratory Department of Computer Science University of Massachusetts Amherst,
Patent Application Publication Sep. 30, 2004 Sheet 1 0f 2. Hierarchical Query. Contact Ow FIG. 1
 US 20040193595A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0193595 A1 Kaminsky et al. (43) Pub. Date: Sep. 30, 2004 (54) NEAREST KNOWN PERSON DIRECTORY FUNCTION (75)
US 20040193595A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2004/0193595 A1 Kaminsky et al. (43) Pub. Date: Sep. 30, 2004 (54) NEAREST KNOWN PERSON DIRECTORY FUNCTION (75)
Chapter 1: Key Concepts of Programming and Software Engineering
 Chapter 1: Key Concepts of Programming and Software Engineering Software Engineering Coding without a solution design increases debugging time - known fact! A team of programmers for a large software development
Chapter 1: Key Concepts of Programming and Software Engineering Software Engineering Coding without a solution design increases debugging time - known fact! A team of programmers for a large software development
