Internet Security for Everyone. Mark Hasting
|
|
|
- MargaretMargaret Tate
- 3 years ago
- Views:
Transcription
1 Internet Security for Everyone by Mark Hasting
2 Keeping a computer up-to-date and safe on the Internet can be quite a chore. Not only do you have to watch out for Viruses, Trojans, Worms, and Spyware, but Spam, Phishing Scams, Identity Thieves and Hackers can also pose huge threats to the computer and the information stored there. Understanding how to secure your computer can be a daunting task for the average user. This guide will help you understand the basics of how to secure and protect your system along with some tools and knowledge to prevent future problems. Computer Updates The first line of defense in computer security involves updates. Keeping your computer up-to-date with the correct patches for the operating system, updates for your antivirus, and updates for anti-spyware is half the battle in preventing problems. Windows XP Updates Windows XP, although it s fairly easy to use, is very insecure without all the current updates. Because it s the most popular computer operating system, it s also the preferred target for hackers and others to attack. Making sure your computer has all the current critical updates for Windows XP is the highest priority. Follow the steps on the next page to check for updates and install them.
3 1) Open Control Panel, click on the Windows Update link in the left column Alternatively, you can open Internet Explorer and go to the following site 1) Click on the Express Button on the updates screen to allow the site to check for any critical updates that are not installed on your computer.
4 2) The site will check for any missing critical updates for your computer
5 3) If your computer has all the Windows critical updates installed, you should see the following screen. If there are updates to install, check them and install them. The computer will generally force you to reboot after installing them. You should regularly check for Windows updates at least once a month to maintain the security of Windows XP. Antivirus Updates Your antivirus is only as good as its last update. One of the most common problems I run across is an antivirus program with old, outdated virus signatures. Generally once an antivirus is installed it will update on its own as long as it can connect to the Internet. However, if the antivirus subscription has expired, the program will stop updating and can leave your computer vulnerable to new threats. For this reason, it s a good idea to check your antivirus program at least once a month to make sure its updating properly and protecting your system from virus, worm, and trojan threats. If you have Norton, McAfee, or Trend antivirus installed on your computer, you can visit the following page to learn how to update your antivirus and keep it protecting your computer. If you don t have a current antivirus program, you can download a free antivirus by visiting any of the following links Grisoft AVG Avast AntiVir
6 All three of the free antivirus programs are excellent alternatives to the more popular commercial programs. They are free for personal use, and have paid versions for business and commercial use. Be sure to check your antivirus once a month to make sure its properly updating. Anti-Spyware Updates Spyware and Adware not only can cause frustration because of pop-up advertisements and sluggish performance, but they can also install backdoor holes for spam, phishing schemes, and identity thieves. Running anti-spyware scans and keeping the signatures of the programs up-to-date is also an important step in securing your computer. Although you can purchase any number of programs to remove spyware and adware, in most cases the free anti-spyware software does an adequate if not better job of removing these pests than paid versions. It s also important to realize that each antispyware program will find different items on your computer so it s a good idea to run a couple different programs to thoroughly clean your system of these pests. I highly recommend the following programs to remove spyware and adware. Ad-Aware SE 1.06 by Lavasoft One of the first and still one of the best removal programs for adware, you can choose between a paid and a free version. Spybot Search and Destroy Another pioneer in the field of adware and spyware removal and always free. Microsoft Defender Microsoft purchased a company called Giant Software and morphed their antispyware program into what is now known as Windows Defender. With realtime protection and monitoring, this program helps to prevent spyware and adware from ever getting on your system Keeping your computer up-to-date is the easiest way to protect your computer from viruses, hackers, and other online issues. There are many programs to do this, and everyone has their personal favorite. The key is actually having these programs installed, up-to-date, and being used on a regular basis.
7 Home Networking When you are connected to the Internet, you are assigned a unique IP address. This IP address allows other computers on the Internet to find you properly. This IP address is called a public IP, it s sort of like a telephone number. The IP address is made up of 4 sets of numbers from 0 to 255 separated by periods ( ), this creates a total of over 4,228,250,625 possible addresses. Although not all of them are available for use. What happens if there are more than 4.2 billion computers that want to access the Internet, that s where private IP addresses are used. Three groups of IP address have been set aside for private networks, they are: to to to Private IPs allow you to connect multiple computers to the Internet using only 1 Public IP. The task of knowing which computer on the network gets what data is handled by a device called a router. Routers sort out information that comes from the Internet on a public IP and sends that information to the correct private IP address behind the router. The process of mapping the public IP to the private IP is called Network Address Translation or NAT for short. NAT is important in computer security because it provides a natural firewall between the outside world and your private network. Unless something is requested from your network, nothing will be able to get through. This creates a hardware firewall to protect your computer. The NAT firewall also has a second layer of security called stateful inspection. This means if the router receives data from a website, it looks at a list of the computers attached to it and determines which computer requested the data. If none of the computers behind the router asked for the data, the router discards it. In other words, unless a computer behind the router asked for the information, the router won t let it pass through. Firewalls Firewalls protect your computer from being accessed from the outside. There are two types of firewalls, hardware and software. Most broadband routers have NAT firewalls built into them to help, and many have more advanced firewall options to block intruders. A hardware firewall blocks data from entering your computer, while a software firewall like Windows XP Firewall, ZoneAlarm, or Kerio Personal Firewall, can stop data from coming in OR going out of your computer. If your computer
8 becomes infected with a virus, it could send data from your computer to another computer. A properly configured software firewall would prevent this action. When a software firewall is first installed, it has to learn which programs on the computer are allowed to gain access to the Internet, anytime the user opens a new application that needs internet access a screen will popup asking you to allow it permission to go online. These firewall rules allow the firewall to know what s good and what s bad. Unfortunately if during this time, you accidentally block a program like iexplore.exe, you will not be able to get online with Internet Explorer since iexplore.exe is the filename for Internet Explorer. You need be careful when these screens appear. Read them carefully and either accept or reject the request. If a program stops working shortly after a screen like this popped up, the chances are high that a firewall rule was set to block the application. In this case, you ll have to open the firewall and unblock it to continue. Firewalls are important and help prevent you from threats, however an improperly configured or corrupted firewall will cause your computer not to be able to get online. So please be careful when installing and configuring software firewalls. I recommend the following software firewalls for use: Windows XP SP2 Firewall An easy to turn on firewall, it silently does its job, and it doesn t slow down your computer system. However it only looks at traffic coming into your computer. Kerio Personal Firewall Kerio is an excellent two-way software firewall with a free and paid version. It even has the ability to block popup ads. ZoneLabs ZoneAlarm One of the most well known software firewalls and has been protecting computers since ZoneAlarm is recommended by countless experts as the best software firewall to use.
9 Once you have your computer up-to-date with your antivirus, spyware, firewall, and Windows updates, you should check to see how secure your connection is by visiting Steve Gibson s site Shields Up. Shields Up There are also a few other important security scanners on the Internet you may want to check out. Scanit Browser Security Test Windows Clipboard Test Security Test Symantec Security Test Wireless Networking and Encryption Wireless networks open a huge hole in your home network if they are left in their default settings. These open networks allow anyone with a wireless network device such as a notebook computer to connect to your network, browse the computers connected, look at your shared files and even print to a shared printer if the network allows. They work great for coffee shops, airports, and other convenience locations, but should be locked down using wireless encryption for home and business networks. To do this, you have to access your wireless routers administration interface by typing in the URL for it in your web browser. This is usually a private IP like or For the Actiontec modems that Qwest uses for DSL, the URL is Once there, click on the Wireless settings screen and you should see something similar to the following screenshot.
10 You ll notice at the bottom of the screen the Security feature, generally there are two basic encryption schemes WEP (Wired Equivalent Privacy) and WPA (Wi-Fi Protected Access). WEP is harder to setup because it involves setting up a 64 or 128 bit security key. A 64 bit security key uses 5 sets of hexadecimal numbers 0-9 and letters A-F, so a typical 64 bit key would look like the following: 01-5A-44-3C-8F A 128 bit security key comprises of 13 sets of hexadecimal numbers, so a typical 128 bit key would look similar to: E3-5F-93-2B-FF-6E CB-71-DB WPA encryption is easier to setup because it uses a passphrase to create a key. Its also a more secure encryption technique that WEP. For this reason, I would recommend using WPA encryption on your wireless network. The only thing you ll need to remember is the passphrase when you want to connect. MAC Address Filtering is another technique used to block access, it can be used along with wireless encryption to create a very secure network. Here s how MAC filtering works. Every networked device is assigned a MAC (Media Access Control) address. This address is a unique identifier for the hardware device, sort
11 of like an electronic fingerprint since no two MAC addresses are ever the same. You can enable MAC filtering in your router to thoroughly secure your network. You can find the MAC address for your network card in Windows XP by following these steps. 1) Click on the Start button, then choose RUN 2) Type CMD and click OK and a black DOS like box will appear 3) At the C:\> prompt type IPCONFIG /ALL and press Enter 4) Look for the Local Area Connection section and find the item called Physical Address. The hexadecimal code next to it is the MAC Address. 5) Type Exit at the prompt to return to Windows Extra Precautions for Wireless Networks 1) Change your router s default password 2) Change or hide your wireless network SSID (Service Set Identifier) 3) Be careful with File Sharing on your Network, only share the folders you need 4) Disable DHCP and assign IP addresses manually Privacy and Passwords Passwords should be used to protect your computer, especially the Administrator account in Windows XP. You should also use the Limited and Guest accounts to restrict access to your computer. Employees who don t need to install programs or make system changes on the computer should be assigned a Limited account. If you are not using the Guest account in Windows XP, turn it off to prevent access. By limiting access, you are also securing the computer if it becomes stolen or otherwise compromised.
12 Tip: Remember your password, don t put it on a Post-it Note and place on your monitor. Passwords only work if they are private. Here are some more great tips for keeping your privacy. 1) If you are using a password manager on your computer like Roboform to remember website logins, be sure to use a Master password to secure the software. 2) Use a program like CCleaner to clear cache, internet history, and most recently used lists from programs. 3) Password protect your program 4) Use a file shredder program like UltraWipe to delete sensitive data permanently. 5) Use a file protection program to hide files and folders from prying eyes. An excellent utility to do this is called Hide Folder and it can be freely downloaded from 6) Privatize your files. If you have multiple administrator accounts on your Windows XP machine, you can Share a folder and make the folder private. This will prevent anyone except that user from accessing the data stored there. 7) Use Data Encryption to encrypt sensitive files. If your computer is stolen, the intruders wont be able to get to your files unless they have the correct passwords. Unfortunately file encryption in Windows XP is rather extensive, for this reason if you would like to know more about how to encrypt your data and recover it, please read the following excellent tutorial on the subject.
13 8) Protect yourself from phishing scams by installing the Netcraft Anti- Phishing toolbar. The toolbar will assign a risk rating to each site you visit, so you can protect yourself from identity theft and online scams. The Netcraft toolbar can be downloaded from: Data Backups Using External Drives and USB Thumb Drives Backing up your vital data from a computer is an absolute must to protect from hard drive crash, virus attack, and other destruction. With the addition of external USB drives and small thumb drives, there is no reason NOT to backup your data. You can use free programs like Microsoft Synctoy or Karen s Replicator to backup your data on a daily basis, or use program like Symantec s Ghost or Acronis True Image to create an image of your computer s hard drive on CD or DVD. Microsoft Synctoy Karen s Replicator Symantec Ghost Acronis True Image
14 Offsite storage You should also store backups of your data and hard drive off site so in case of fire or other destruction, you can restore your data and get back to business. This can be done simply by taking a copy of your backup CDs, DVDs, or USB drive to an alternate location or you can opt for an online backup solution. Two of the more popular online solutions are Mozy XDrive Both are very cost effective and secure ways to store your data online, although I would not recommend storing your tax records there simply because its online. I would recommend taking backups of your CDs home or to another location and putting them in a safe and secured environment offsite. Conclusion I hope these tips will help you in securing your computer and network and keeping it clean of viruses, spyware, and other problems. If you are still having problems with your computer, I would suggest reading through more of the articles on PC Hell for solutions. If you are interested in a more thorough E-book on Internet Security I suggest you pick up a copy of The Hackers Nightmare, an excellent and extensive (over 400 pages) look at personal computer security and what the average person can do to make their computer safe. You can read more about The Hacker s Nightmare by visiting the following link: Thank you for your time. Mark Hasting PCHell.com
Preparing Your Personal Computer to Connect to the VPN
 Preparing Your Personal Computer to Connect to the VPN (Protecting Your Personal Computer Running Windows) Using the VPN to connect your computer to the campus network is the same as bringing your computer
Preparing Your Personal Computer to Connect to the VPN (Protecting Your Personal Computer Running Windows) Using the VPN to connect your computer to the campus network is the same as bringing your computer
Introduction to Computer Security Table of Contents
 Introduction to Computer Security Table of Contents Introduction... 2 1 - Viruses... 3 Virus Scanners... 3 2 - Spyware... 7 Spyware Scanners... 8 3 - Firewalls... 10 Windows Firewall... 10 4 - References...
Introduction to Computer Security Table of Contents Introduction... 2 1 - Viruses... 3 Virus Scanners... 3 2 - Spyware... 7 Spyware Scanners... 8 3 - Firewalls... 10 Windows Firewall... 10 4 - References...
Essentials of PC Security: Central Library Tech Center Evansville Vanderburgh Public Library
 Essentials of PC Security: Central Library Tech Center Evansville Vanderburgh Public Library Why should you be concerned? There are over 1 million known computer viruses. An unprotected computer on the
Essentials of PC Security: Central Library Tech Center Evansville Vanderburgh Public Library Why should you be concerned? There are over 1 million known computer viruses. An unprotected computer on the
Contents. McAfee Internet Security 3
 User Guide i Contents McAfee Internet Security 3 McAfee SecurityCenter... 5 SecurityCenter features... 6 Using SecurityCenter... 7 Fixing or ignoring protection problems... 16 Working with alerts... 21
User Guide i Contents McAfee Internet Security 3 McAfee SecurityCenter... 5 SecurityCenter features... 6 Using SecurityCenter... 7 Fixing or ignoring protection problems... 16 Working with alerts... 21
Computer Viruses: How to Avoid Infection
 Viruses From viruses to worms to Trojan Horses, the catchall term virus describes a threat that's been around almost as long as computers. These rogue programs exist for the simple reason to cause you
Viruses From viruses to worms to Trojan Horses, the catchall term virus describes a threat that's been around almost as long as computers. These rogue programs exist for the simple reason to cause you
Computer Security: Best Practices for Home Computing. Presented by Student Help Desk Merced Community College
 Computer Security: Best Practices for Home Computing Presented by Student Help Desk Merced Community College Defining the Problem Symantec documented 2,636 new vulnerabilities in 2003, an average of seven
Computer Security: Best Practices for Home Computing Presented by Student Help Desk Merced Community College Defining the Problem Symantec documented 2,636 new vulnerabilities in 2003, an average of seven
Computer Security Maintenance Information and Self-Check Activities
 Computer Security Maintenance Information and Self-Check Activities Overview Unlike what many people think, computers are not designed to be maintenance free. Just like cars they need routine maintenance.
Computer Security Maintenance Information and Self-Check Activities Overview Unlike what many people think, computers are not designed to be maintenance free. Just like cars they need routine maintenance.
Desktop and Laptop Security Policy
 Desktop and Laptop Security Policy Appendix A Examples of Desktop and Laptop standards and guidelines 1. Implement anti-virus software An anti-virus program is necessary to protect your computer from malicious
Desktop and Laptop Security Policy Appendix A Examples of Desktop and Laptop standards and guidelines 1. Implement anti-virus software An anti-virus program is necessary to protect your computer from malicious
When you listen to the news, you hear about many different forms of computer infection(s). The most common are:
 Access to information and entertainment, credit and financial services, products from every corner of the world even to your work is greater than ever. Thanks to the Internet, you can conduct your banking,
Access to information and entertainment, credit and financial services, products from every corner of the world even to your work is greater than ever. Thanks to the Internet, you can conduct your banking,
Quick Start. Installing the software. for Webroot Internet Security Complete, Version 7.0
 Quick Start for Webroot Internet Security Complete, Version 7.0 This Quick Start describes how to install and begin using the Webroot Internet Security Complete 2011 software. This integrated suite delivers
Quick Start for Webroot Internet Security Complete, Version 7.0 This Quick Start describes how to install and begin using the Webroot Internet Security Complete 2011 software. This integrated suite delivers
Spam, Spyware, Malware and You! Don't give up just yet! Presented by: Mervin Istace Provincial Library Saskatchewan Learning
 Spam, Spyware, Malware and You! Don't give up just yet! Presented by: Mervin Istace Provincial Library Saskatchewan Learning Lee Zelyck Network Administrator Regina Public Library Malware, Spyware, Trojans
Spam, Spyware, Malware and You! Don't give up just yet! Presented by: Mervin Istace Provincial Library Saskatchewan Learning Lee Zelyck Network Administrator Regina Public Library Malware, Spyware, Trojans
Malware & Botnets. Botnets
 - 2 - Malware & Botnets The Internet is a powerful and useful tool, but in the same way that you shouldn t drive without buckling your seat belt or ride a bike without a helmet, you shouldn t venture online
- 2 - Malware & Botnets The Internet is a powerful and useful tool, but in the same way that you shouldn t drive without buckling your seat belt or ride a bike without a helmet, you shouldn t venture online
McAfee Internet Security Suite Quick-Start Guide
 Enjoy a Worry Free Online Experience McAfee Internet Security Suite protects your PC, identity and online experience. It also includes PC and network tools, plus McAfee SiteAdvisor for safe surfing. Internet
Enjoy a Worry Free Online Experience McAfee Internet Security Suite protects your PC, identity and online experience. It also includes PC and network tools, plus McAfee SiteAdvisor for safe surfing. Internet
Why is a strong password important?
 Internet Security Why is a strong password important? Identity theft motives: To gain access to resources For the challenge/fun Personal reasons Theft methods Brute forcing and other script hacking methods
Internet Security Why is a strong password important? Identity theft motives: To gain access to resources For the challenge/fun Personal reasons Theft methods Brute forcing and other script hacking methods
Configuring Your Network s Security
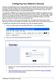 Configuring Your Network s Security Security is an important issue when using a wireless home network. Because radio waves are used to transfer information between your networked computers, it's possible
Configuring Your Network s Security Security is an important issue when using a wireless home network. Because radio waves are used to transfer information between your networked computers, it's possible
Secure and Safe Computing Primer Examples of Desktop and Laptop standards and guidelines
 Secure and Safe Computing Primer Examples of Desktop and Laptop standards and guidelines 1. Implement anti-virus software An anti-virus program is necessary to protect your computer from malicious programs,
Secure and Safe Computing Primer Examples of Desktop and Laptop standards and guidelines 1. Implement anti-virus software An anti-virus program is necessary to protect your computer from malicious programs,
Bookmarks for Desktop Self-Defense
 Basic Security Tips Bookmarks for Desktop Self-Defense Get Safe Online http://www.getsafeonline.org/ Get Safe Online will help you protect yourself against Internet threats. The site is sponsored by government
Basic Security Tips Bookmarks for Desktop Self-Defense Get Safe Online http://www.getsafeonline.org/ Get Safe Online will help you protect yourself against Internet threats. The site is sponsored by government
PC Security and Maintenance
 PC Security and Maintenance by IMRAN GHANI PC Maintenance and Security-Forecast. Major sources of danger. Important steps to protect your PC. PC Security Tools. PC Maintenance Tools. Tips. PC Security-
PC Security and Maintenance by IMRAN GHANI PC Maintenance and Security-Forecast. Major sources of danger. Important steps to protect your PC. PC Security Tools. PC Maintenance Tools. Tips. PC Security-
Ohio University Computer Services Center October, 2004 Spyware, Adware, and Virus Guide
 Ohio University Computer Services Center October, 2004 Spyware, Adware, and Virus Guide Definitions Malware is term meaning malicious software. Malware is software designed to disrupt a computer system.
Ohio University Computer Services Center October, 2004 Spyware, Adware, and Virus Guide Definitions Malware is term meaning malicious software. Malware is software designed to disrupt a computer system.
This guide will go through the common ways that a user can make their computer more secure.
 A beginners guide in how to make a Laptop/PC more secure. This guide will go through the common ways that a user can make their computer more secure. Here are the key points covered: 1) Device Password
A beginners guide in how to make a Laptop/PC more secure. This guide will go through the common ways that a user can make their computer more secure. Here are the key points covered: 1) Device Password
Willem Wiechers 3 rd March 2015
 Willem Wiechers 3 rd March 2015 1 Why do we want Malware & Virus Protection? To make our computers save Wish to keep our data private Wish to have a safe environment to do our online banking, shopping,
Willem Wiechers 3 rd March 2015 1 Why do we want Malware & Virus Protection? To make our computers save Wish to keep our data private Wish to have a safe environment to do our online banking, shopping,
Frequently Asked Questions
 FAQs Frequently Asked Questions Connecting your Linksys router to the Internet 1 What computer operating systems does my Linksys router support? 1 Why can t I connect my computer or device to my router?
FAQs Frequently Asked Questions Connecting your Linksys router to the Internet 1 What computer operating systems does my Linksys router support? 1 Why can t I connect my computer or device to my router?
Airtel PC Secure Trouble Shooting Guide
 Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
HomeNet. Gateway User Guide
 HomeNet Gateway User Guide Gateway User Guide Table of Contents HomeNet Gateway User Guide Gateway User Guide Table of Contents... 2 Introduction... 3 What is the HomeNet Gateway (Gateway)?... 3 How do
HomeNet Gateway User Guide Gateway User Guide Table of Contents HomeNet Gateway User Guide Gateway User Guide Table of Contents... 2 Introduction... 3 What is the HomeNet Gateway (Gateway)?... 3 How do
Frequently Asked Questions
 Frequently Asked Questions 1) What does SkyBest Internet Guardian do? Prevents e-mail and image spam from reaching your inbox Halts access to dangerous Web pages Stops Web sites from installing dangerous
Frequently Asked Questions 1) What does SkyBest Internet Guardian do? Prevents e-mail and image spam from reaching your inbox Halts access to dangerous Web pages Stops Web sites from installing dangerous
What's the difference between spyware and a virus? What is Scareware?
 What's the difference between spyware and a virus? What is Scareware? Spyware and viruses are both forms of unwanted or malicious software, sometimes called "malware." You can use Microsoft Security Essentials
What's the difference between spyware and a virus? What is Scareware? Spyware and viruses are both forms of unwanted or malicious software, sometimes called "malware." You can use Microsoft Security Essentials
SecuritySecuritySecurity!
 SecuritySecuritySecurity! It was the best of times and the worst of times... I suspect Dickens would be quite surprised to learn how prophetic his words would be over 150 years after he penned them. THE
SecuritySecuritySecurity! It was the best of times and the worst of times... I suspect Dickens would be quite surprised to learn how prophetic his words would be over 150 years after he penned them. THE
ViRobot Desktop 5.5. User s Guide
 ViRobot Desktop 5.5 User s Guide ViRobot Desktop 5.5 User s Guide Copyright Notice Copyright 2007 by HAURI Inc. All rights reserved worldwide. No part of this publication or software may be reproduced,
ViRobot Desktop 5.5 User s Guide ViRobot Desktop 5.5 User s Guide Copyright Notice Copyright 2007 by HAURI Inc. All rights reserved worldwide. No part of this publication or software may be reproduced,
Ad-Aware Antivirus Overview
 Contents Ad-Aware Antivirus Overview... 3 What is Ad-Aware Antivirus?... 3 Ad-Aware Antivirus Features... 4 System Requirements... 6 Getting Started... 7 Ad-Aware Install... 7 Using Ad-Aware Free 30 day
Contents Ad-Aware Antivirus Overview... 3 What is Ad-Aware Antivirus?... 3 Ad-Aware Antivirus Features... 4 System Requirements... 6 Getting Started... 7 Ad-Aware Install... 7 Using Ad-Aware Free 30 day
What you need to know to keep your computer safe on the Internet
 What you need to know to keep your computer safe on the Internet Tip 1: Always install Operating System updates The most important steps for any computer user is to always install updates, especially security
What you need to know to keep your computer safe on the Internet Tip 1: Always install Operating System updates The most important steps for any computer user is to always install updates, especially security
Cyber Security Awareness
 Cyber Security Awareness User IDs and Passwords Home Computer Protection Protecting your Information Firewalls Malicious Code Protection Mobile Computing Security Wireless Security Patching Possible Symptoms
Cyber Security Awareness User IDs and Passwords Home Computer Protection Protecting your Information Firewalls Malicious Code Protection Mobile Computing Security Wireless Security Patching Possible Symptoms
Antivirus. Quick Start Guide. Antivirus
 Antivirus 2007 Antivirus plus I Firewall Quick Start Guide Helpful Information on Installation and Set-Up STOPS and Removes Viruses DELIVERS Proactive Firewall Protection EASY to Set Up and Use FREE Upgrades
Antivirus 2007 Antivirus plus I Firewall Quick Start Guide Helpful Information on Installation and Set-Up STOPS and Removes Viruses DELIVERS Proactive Firewall Protection EASY to Set Up and Use FREE Upgrades
Laura Royer, Extension Faculty, University of Florida/IFAS Osceola County Extension Services
 Consumer Choices: Computer Security Software Prepared by: Dave Palmer, Instructional Media Faculty, University of Florida/IFAS Extension, South Central Extension District Laura Royer, Extension Faculty,
Consumer Choices: Computer Security Software Prepared by: Dave Palmer, Instructional Media Faculty, University of Florida/IFAS Extension, South Central Extension District Laura Royer, Extension Faculty,
Securing Your Windows Laptop
 Securing Your Windows Laptop Arindam Mandal (arindam.mandal@paladion.net) Paladion Networks (http://www.paladion.net) May 2004 Now-a-days laptops are part of our life. We carry laptops almost everywhere
Securing Your Windows Laptop Arindam Mandal (arindam.mandal@paladion.net) Paladion Networks (http://www.paladion.net) May 2004 Now-a-days laptops are part of our life. We carry laptops almost everywhere
Online Banking Fraud Prevention Recommendations and Best Practices
 Online Banking Fraud Prevention Recommendations and Best Practices This document provides you with fraud prevention best practices that every employee at Continental National Bank of Miami needs to know
Online Banking Fraud Prevention Recommendations and Best Practices This document provides you with fraud prevention best practices that every employee at Continental National Bank of Miami needs to know
LAW OFFICE SECURITY for Small Firms and Sole Practitioners. Prepared by Andrew Mason, Scott Phelps & Mason, Saskatoon Saskatchewan
 LAW OFFICE SECURITY for Small Firms and Sole Practitioners Prepared by Andrew Mason, Scott Phelps & Mason, Saskatoon Saskatchewan 1. Introduction CONTENTS 2. Security Consciousness Having a Firm Security
LAW OFFICE SECURITY for Small Firms and Sole Practitioners Prepared by Andrew Mason, Scott Phelps & Mason, Saskatoon Saskatchewan 1. Introduction CONTENTS 2. Security Consciousness Having a Firm Security
STEP III: Enable the Wireless Network Card. STEP IV: Print out the Printer Settings pages to determine the IP Address
 Title: How do I configure the wireless printer without a network cable and install the printer driver in Windows? NOTE: For successful wireless setup, you MUST know your network security settings. STEP
Title: How do I configure the wireless printer without a network cable and install the printer driver in Windows? NOTE: For successful wireless setup, you MUST know your network security settings. STEP
7 Steps to Safer Computing
 7 Steps to Safer Computing These are the seven essentials: - Use a firewall. - Keep your software up to date. - Use an up to date antivirus program. - Use an up to date anti-spyware program. - Only download
7 Steps to Safer Computing These are the seven essentials: - Use a firewall. - Keep your software up to date. - Use an up to date antivirus program. - Use an up to date anti-spyware program. - Only download
Welcome To The L.R.F.H.S. Computer Group Wednesday 27 th November 2013
 Welcome To The L.R.F.H.S. Computer Group Wednesday 27 th November 2013 BACKUP SECURITY AND THE CLOUD BACK UP ALWAYS BACK UP TO AN EXTERNAL DEVICE OR REMOVAL MEDIA- NEVER DIRECTLY ON TO YOUR COMPUTER IF
Welcome To The L.R.F.H.S. Computer Group Wednesday 27 th November 2013 BACKUP SECURITY AND THE CLOUD BACK UP ALWAYS BACK UP TO AN EXTERNAL DEVICE OR REMOVAL MEDIA- NEVER DIRECTLY ON TO YOUR COMPUTER IF
OCT Training & Technology Solutions Training@qc.cuny.edu (718) 997-4875
 OCT Training & Technology Solutions Training@qc.cuny.edu (718) 997-4875 Understanding Information Security Information Security Information security refers to safeguarding information from misuse and theft,
OCT Training & Technology Solutions Training@qc.cuny.edu (718) 997-4875 Understanding Information Security Information Security Information security refers to safeguarding information from misuse and theft,
How to Use Windows Firewall With User Account Control (UAC)
 Keeping Windows 8.1 safe and secure 14 IN THIS CHAPTER, YOU WILL LEARN HOW TO Work with the User Account Control. Use Windows Firewall. Use Windows Defender. Enhance the security of your passwords. Security
Keeping Windows 8.1 safe and secure 14 IN THIS CHAPTER, YOU WILL LEARN HOW TO Work with the User Account Control. Use Windows Firewall. Use Windows Defender. Enhance the security of your passwords. Security
Remote Desktop Part II. AHS Computing
 Remote Desktop Part II AHS Computing Overview How to become connected at home How to be secure when connecting from home Hazards of home computing How to work from home Troubleshooting issues from home
Remote Desktop Part II AHS Computing Overview How to become connected at home How to be secure when connecting from home Hazards of home computing How to work from home Troubleshooting issues from home
MN-700 Base Station Configuration Guide
 MN-700 Base Station Configuration Guide Contents pen the Base Station Management Tool...3 Log ff the Base Station Management Tool...3 Navigate the Base Station Management Tool...4 Current Base Station
MN-700 Base Station Configuration Guide Contents pen the Base Station Management Tool...3 Log ff the Base Station Management Tool...3 Navigate the Base Station Management Tool...4 Current Base Station
Infocomm Sec rity is incomplete without U Be aware,
 Infocomm Sec rity is incomplete without U Be aware, responsible secure! HACKER Smack that What you can do with these five online security measures... ANTI-VIRUS SCAMS UPDATE FIREWALL PASSWORD [ 2 ] FASTEN
Infocomm Sec rity is incomplete without U Be aware, responsible secure! HACKER Smack that What you can do with these five online security measures... ANTI-VIRUS SCAMS UPDATE FIREWALL PASSWORD [ 2 ] FASTEN
Reliance Bank Fraud Prevention Best Practices
 Reliance Bank Fraud Prevention Best Practices May 2013 User ID and Password Guidelines Create a strong password with at least 8 characters that includes a combination of mixed case letters and numbers.
Reliance Bank Fraud Prevention Best Practices May 2013 User ID and Password Guidelines Create a strong password with at least 8 characters that includes a combination of mixed case letters and numbers.
ITSC Training Courses Student IT Competence Programme SIIS1 Information Security
 ITSC Training Courses Student IT Competence Programme SI1 2012 2013 Prof. Chan Yuen Yan, Rosanna Department of Engineering The Chinese University of Hong Kong SI1-1 Course Outline What you should know
ITSC Training Courses Student IT Competence Programme SI1 2012 2013 Prof. Chan Yuen Yan, Rosanna Department of Engineering The Chinese University of Hong Kong SI1-1 Course Outline What you should know
Statistical Analysis of Internet Security Threats. Daniel G. James
 Statistical Analysis of Internet Security Threats Daniel G. James ABSTRACT The purpose of this paper is to analyze the statistics surrounding the most common security threats faced by Internet users. There
Statistical Analysis of Internet Security Threats Daniel G. James ABSTRACT The purpose of this paper is to analyze the statistics surrounding the most common security threats faced by Internet users. There
Welcome to Part 2 of the online course, Spyware and Adware What s in Your Computer?
 Welcome to Part 2 of the online course, Spyware and Adware What s in Your Computer? 1 2 This is the second part of a two-part course on spyware and adware. In this portion of the course we will: Review
Welcome to Part 2 of the online course, Spyware and Adware What s in Your Computer? 1 2 This is the second part of a two-part course on spyware and adware. In this portion of the course we will: Review
High Speed Internet - User Guide. Welcome to. your world.
 High Speed Internet - User Guide Welcome to your world. 1 Welcome to your world :) Thank you for choosing Cogeco High Speed Internet. Welcome to your new High Speed Internet service. When it comes to a
High Speed Internet - User Guide Welcome to your world. 1 Welcome to your world :) Thank you for choosing Cogeco High Speed Internet. Welcome to your new High Speed Internet service. When it comes to a
Email Security. 01-15-09 Fort Mac
 Email Security 01-15-09 Fort Mac Most Common Mistakes in Email Security Email Security 1. Using just one email account. 2. Holding onto spammed-out accounts too long. 3. Not closing the browser after logging
Email Security 01-15-09 Fort Mac Most Common Mistakes in Email Security Email Security 1. Using just one email account. 2. Holding onto spammed-out accounts too long. 3. Not closing the browser after logging
Why you need. McAfee. Multi Acess PARTNER SERVICES
 Why you need McAfee Multi Acess PARTNER SERVICES McAfee Multi Access is an online security app that protects all types of devices. All at once. The simple monthly subscription covers up to five devices
Why you need McAfee Multi Acess PARTNER SERVICES McAfee Multi Access is an online security app that protects all types of devices. All at once. The simple monthly subscription covers up to five devices
How to Install Windows 7 software
 Connecting Windows 7 to the network This document outlines the procedure for setting up Windows 7 to use the College and University network. It assumes that the computer is set up and working correctly
Connecting Windows 7 to the network This document outlines the procedure for setting up Windows 7 to use the College and University network. It assumes that the computer is set up and working correctly
Installing a Westell USB Network Adapter
 Installing a Westell USB Network Adapter Before You Begin Before you begin installing your Westell USB Network adapter: 1. Make sure the computer with the USB adapter meets the minimum system requirements
Installing a Westell USB Network Adapter Before You Begin Before you begin installing your Westell USB Network adapter: 1. Make sure the computer with the USB adapter meets the minimum system requirements
Go Wireless. Open up new possibilities for work and play
 Go Wireless Open up new possibilities for work and play Start with 3 pieces A typical home or small-office wireless LAN requires only 3 pieces of hardware. With these 3 pieces, you re ready to get started!
Go Wireless Open up new possibilities for work and play Start with 3 pieces A typical home or small-office wireless LAN requires only 3 pieces of hardware. With these 3 pieces, you re ready to get started!
Keeping you and your computer safe in the digital world.
 Keeping you and your computer safe in the digital world. After completing this class, you should be able to: Explain the terms security and privacy as applied to the digital world Identify digital threats
Keeping you and your computer safe in the digital world. After completing this class, you should be able to: Explain the terms security and privacy as applied to the digital world Identify digital threats
Internet Security for Windows XP and Vista
 Welcome Windows XP and Vista Users Welcome to Alliance Internet. You have joined one of the fastest growing Internet providers in the area. This information will help you understand how your Internet works.
Welcome Windows XP and Vista Users Welcome to Alliance Internet. You have joined one of the fastest growing Internet providers in the area. This information will help you understand how your Internet works.
Best Practices Guide to Electronic Banking
 Best Practices Guide to Electronic Banking City Bank & Trust Company offers a variety of services to our customers. As these services have evolved over time, a much higher percentage of customers have
Best Practices Guide to Electronic Banking City Bank & Trust Company offers a variety of services to our customers. As these services have evolved over time, a much higher percentage of customers have
Software. Webroot. Spy Sweeper. User Guide. for. Webroot Software, Inc. PO Box 19816 Boulder, CO 80308 www.webroot.com. Version 6.
 Webroot Software User Guide for Spy Sweeper Webroot Software, Inc. PO Box 19816 Boulder, CO 80308 www.webroot.com Version 6.1 Webroot Software User Guide Version 6.1 2003 2009 Webroot Software, Inc. All
Webroot Software User Guide for Spy Sweeper Webroot Software, Inc. PO Box 19816 Boulder, CO 80308 www.webroot.com Version 6.1 Webroot Software User Guide Version 6.1 2003 2009 Webroot Software, Inc. All
Cyber Security Awareness
 Cyber Security Awareness William F. Pelgrin Chair Page 1 Introduction Information is a critical asset. Therefore, it must be protected from unauthorized modification, destruction and disclosure. This brochure
Cyber Security Awareness William F. Pelgrin Chair Page 1 Introduction Information is a critical asset. Therefore, it must be protected from unauthorized modification, destruction and disclosure. This brochure
Business Internet Banking / Cash Management Fraud Prevention Best Practices
 Business Internet Banking / Cash Management Fraud Prevention Best Practices This document provides fraud prevention best practices that can be used as a training tool to educate new Users within your organization
Business Internet Banking / Cash Management Fraud Prevention Best Practices This document provides fraud prevention best practices that can be used as a training tool to educate new Users within your organization
A6210 WiFi USB Adapter 802.11ac USB 3.0 Dual Band User Manual
 802.11ac USB 3.0 Dual Band User Manual August 2014 202-11373-01 350 East Plumeria Drive San Jose, CA 95134 USA Support Thank you for selecting NETGEAR products. After installing your device, locate the
802.11ac USB 3.0 Dual Band User Manual August 2014 202-11373-01 350 East Plumeria Drive San Jose, CA 95134 USA Support Thank you for selecting NETGEAR products. After installing your device, locate the
NBG2105. User s Guide. Quick Start Guide. Wireless Mini Travel Router. Default Login Details. Version 1.00 Edition 1, 11/2012
 NBG2105 Wireless Mini Travel Router Version 1.00 Edition 1, 11/2012 Quick Start Guide User s Guide LAN IP Address Default Login Details 192.168.1.1 (Router Mode) 192.168.1.2 (Other Modes) Passwordwww.zyxel.com
NBG2105 Wireless Mini Travel Router Version 1.00 Edition 1, 11/2012 Quick Start Guide User s Guide LAN IP Address Default Login Details 192.168.1.1 (Router Mode) 192.168.1.2 (Other Modes) Passwordwww.zyxel.com
Business ebanking Fraud Prevention Best Practices
 Business ebanking Fraud Prevention Best Practices User ID and Password Guidelines Create a strong password with at least 8 characters that includes a combination of mixed case letters, numbers, and special
Business ebanking Fraud Prevention Best Practices User ID and Password Guidelines Create a strong password with at least 8 characters that includes a combination of mixed case letters, numbers, and special
Manually Add Programs to Your Firewall or Anti-Virus Programs Trusted List. ZoneAlarm
 Manually Add Programs to Your Firewall or Anti-Virus Programs Trusted List ZoneAlarm AVG Open the AVG Anti-Virus plus Firewall. Double-click the Firewall button to configure the Firewall. Add the programs
Manually Add Programs to Your Firewall or Anti-Virus Programs Trusted List ZoneAlarm AVG Open the AVG Anti-Virus plus Firewall. Double-click the Firewall button to configure the Firewall. Add the programs
Security Practices Essentials. Viruses McAfee Virus Software Critical Windows Updates Network Settings. Spyware Adaware Spybot Windows Defender
 Security Practices Essentials Viruses McAfee Virus Software Critical Windows Updates Network Settings Spyware Adaware Spybot Windows Defender Security Practices Essentials: All computer passwords should
Security Practices Essentials Viruses McAfee Virus Software Critical Windows Updates Network Settings Spyware Adaware Spybot Windows Defender Security Practices Essentials: All computer passwords should
Contact details For contacting ENISA or for general enquiries on information security awareness matters, please use the following details:
 Malicious software About ENISA The European Network and Information Security Agency (ENISA) is an EU agency created to advance the functioning of the internal market. ENISA is a centre of excellence for
Malicious software About ENISA The European Network and Information Security Agency (ENISA) is an EU agency created to advance the functioning of the internal market. ENISA is a centre of excellence for
Step-by-Step Configuration
 Step-by-Step Configuration Kerio Technologies C 2001-2003 Kerio Technologies. All Rights Reserved. Printing Date: December 17, 2003 This guide provides detailed description on configuration of the local
Step-by-Step Configuration Kerio Technologies C 2001-2003 Kerio Technologies. All Rights Reserved. Printing Date: December 17, 2003 This guide provides detailed description on configuration of the local
Cyber Security: Beginners Guide to Firewalls
 Cyber Security: Beginners Guide to Firewalls A Non-Technical Guide Essential for Business Managers Office Managers Operations Managers This appendix is a supplement to the Cyber Security: Getting Started
Cyber Security: Beginners Guide to Firewalls A Non-Technical Guide Essential for Business Managers Office Managers Operations Managers This appendix is a supplement to the Cyber Security: Getting Started
PROTECT YOUR COMPUTER AND YOUR PRIVACY!
 PROTECT YOUR COMPUTER AND YOUR PRIVACY! Fraud comes in many shapes simple: the loss of both money protecting your computer and Take action and get peace of and sizes, but the outcome is and time. That
PROTECT YOUR COMPUTER AND YOUR PRIVACY! Fraud comes in many shapes simple: the loss of both money protecting your computer and Take action and get peace of and sizes, but the outcome is and time. That
The answers vary widely, but there are five components to every spyware definition:
 What's spyware? The answers vary widely, but there are five components to every spyware definition: Users don't knowingly request spyware. Spyware applications operate on the user's computer and have not
What's spyware? The answers vary widely, but there are five components to every spyware definition: Users don't knowingly request spyware. Spyware applications operate on the user's computer and have not
Contents of this tutorial. Virus Protection under windows
 Contents of this tutorial?? Virus protection under Windows?? Printing under windows?? Connecting to Rice wireless network?? List of useful software Virus Protection under windows Let s face it, some people
Contents of this tutorial?? Virus protection under Windows?? Printing under windows?? Connecting to Rice wireless network?? List of useful software Virus Protection under windows Let s face it, some people
C&G FLUX MARKET Internet Safety
 Internet Safety Introduction Viruses, Trojan horses, worms, and spyware are all threats that can damage our computer systems. We know we need to protect our computers, but with so many antivirus programs
Internet Safety Introduction Viruses, Trojan horses, worms, and spyware are all threats that can damage our computer systems. We know we need to protect our computers, but with so many antivirus programs
Stable and Secure Network Infrastructure Benchmarks
 Last updated: March 4, 2014 Stable and Secure Network Infrastructure Benchmarks 501 Commons has developed a list of key benchmarks for maintaining a stable and secure IT Infrastructure for conducting day-to-day
Last updated: March 4, 2014 Stable and Secure Network Infrastructure Benchmarks 501 Commons has developed a list of key benchmarks for maintaining a stable and secure IT Infrastructure for conducting day-to-day
How To Use Secureanything On A Mac Or Ipad (For A Mac)
 User Guide for Mac OS X Copyright Webroot SecureAnywhere User Guide for Mac OS X March, 2013 2012-2013 Webroot Software, Inc. All rights reserved. Webroot is a registered trademark and SecureAnywhere is
User Guide for Mac OS X Copyright Webroot SecureAnywhere User Guide for Mac OS X March, 2013 2012-2013 Webroot Software, Inc. All rights reserved. Webroot is a registered trademark and SecureAnywhere is
Securing Your Wireless Network
 Choosing A Wireless Router You might already have a wireless router provided to you by your Internet Service Provider. Otherwise, if you are intending to get one or decide to upgrade your old router, look
Choosing A Wireless Router You might already have a wireless router provided to you by your Internet Service Provider. Otherwise, if you are intending to get one or decide to upgrade your old router, look
CYBER-SAFETY BASICS. A computer security tutorial for UC Davis students, faculty and staff
 CYBER-SAFETY BASICS A computer security tutorial for UC Davis students, faculty and staff INTRODUCTION This tutorial provides some basic information and practical suggestions for protecting your personal
CYBER-SAFETY BASICS A computer security tutorial for UC Davis students, faculty and staff INTRODUCTION This tutorial provides some basic information and practical suggestions for protecting your personal
October Is National Cyber Security Awareness Month!
 (0 West Virginia Executive Branch Privacy Tip October Is National Cyber Security Awareness Month! In recognition of National Cyber Security Month, we are supplying tips to keep you safe in your work life
(0 West Virginia Executive Branch Privacy Tip October Is National Cyber Security Awareness Month! In recognition of National Cyber Security Month, we are supplying tips to keep you safe in your work life
How to easily clean an infected computer (Malware Removal Guide)
 How to easily clean an infected computer (Malware Removal Guide) Malware, short for malicious (or malevolent) software, is software used or programmed by attackers to disrupt computer operation, gather
How to easily clean an infected computer (Malware Removal Guide) Malware, short for malicious (or malevolent) software, is software used or programmed by attackers to disrupt computer operation, gather
INSTALLATION AND CONFIGURATION GUIDE (THIS DOCUMENT RELATES TO MDAEMON v15.5.0 ONWARDS)
 Web: Overview INSTALLATION AND CONFIGURATION GUIDE (THIS DOCUMENT RELATES TO MDAEMON v15.5.0 ONWARDS) This document provides an installation and configuration guide for MDaemon Messaging Server along with
Web: Overview INSTALLATION AND CONFIGURATION GUIDE (THIS DOCUMENT RELATES TO MDAEMON v15.5.0 ONWARDS) This document provides an installation and configuration guide for MDaemon Messaging Server along with
Basic PC Maintenance. Instructors. Action Center
 Basic PC Maintenance The St. Edward's University workshop "Basic PC Maintenance" addresses best practices for maintaining your (Windows 7) PC at home. This document includes notes and recommendations for
Basic PC Maintenance The St. Edward's University workshop "Basic PC Maintenance" addresses best practices for maintaining your (Windows 7) PC at home. This document includes notes and recommendations for
Certified Secure Computer User
 Certified Secure Computer User Course Outline Module 01: Foundations of Security Essential Terminologies Computer Security Why Security? Potential Losses Due to Security Attacks Elements of Security The
Certified Secure Computer User Course Outline Module 01: Foundations of Security Essential Terminologies Computer Security Why Security? Potential Losses Due to Security Attacks Elements of Security The
1. Any email requesting personal information, or asking you to verify an account, is usually a scam... even if it looks authentic.
 Your identity is one of the most valuable things you own. It s important to keep your identity from being stolen by someone who can potentially harm your good name and financial well-being. Identity theft
Your identity is one of the most valuable things you own. It s important to keep your identity from being stolen by someone who can potentially harm your good name and financial well-being. Identity theft
10 Simple Computer Maintenance Tips For The Laptop
 Greenspring Computer Club April 2015 No matter how savvy you are, there are certain things every one of us has to deal with when using a computer and we don t always deal with them in the most efficient
Greenspring Computer Club April 2015 No matter how savvy you are, there are certain things every one of us has to deal with when using a computer and we don t always deal with them in the most efficient
BCS IT User Syllabus IT Security for Users Level 2. Version 1.0
 BCS IT User Syllabus IT for Users Level 2 Version 1.0 June 2009 ITS2.1 System Performance ITS2.1.1 Unwanted messages ITS2.1.2 Malicious ITS2.1.1.1 ITS2.1.1.2 ITS2.1.2.1 ITS2.1.2.2 ITS2.1.2.3 ITS2.1.2.4
BCS IT User Syllabus IT for Users Level 2 Version 1.0 June 2009 ITS2.1 System Performance ITS2.1.1 Unwanted messages ITS2.1.2 Malicious ITS2.1.1.1 ITS2.1.1.2 ITS2.1.2.1 ITS2.1.2.2 ITS2.1.2.3 ITS2.1.2.4
9 Simple steps to secure your Wi-Fi Network.
 9 Simple steps to secure your Wi-Fi Network. Step 1: Change the Default Password of Modem / Router After opening modem page click on management - access control password. Select username, confirm old password
9 Simple steps to secure your Wi-Fi Network. Step 1: Change the Default Password of Modem / Router After opening modem page click on management - access control password. Select username, confirm old password
Prepared by Computer Troubleshooters Local Service Global Strength Guaranteed!
 5 Most Common Computer Problems Affecting Business Owners Today and What To Do about Them Prepared by Computer Troubleshooters Local Service Global Strength Guaranteed! Introduction Computer Troubleshooters
5 Most Common Computer Problems Affecting Business Owners Today and What To Do about Them Prepared by Computer Troubleshooters Local Service Global Strength Guaranteed! Introduction Computer Troubleshooters
Securing Your Technology Infrastructure Five security areas of focus for small to medium businesses.
 Securing Your Technology Infrastructure Five security areas of focus for small to medium businesses. Anthony Suda Network Manager marketing + technology 701.235.5525 888.9.sundog fax: 701.235.8941 2000
Securing Your Technology Infrastructure Five security areas of focus for small to medium businesses. Anthony Suda Network Manager marketing + technology 701.235.5525 888.9.sundog fax: 701.235.8941 2000
CYBER-SAFETY. A computer security tutorial for UC Davis students, faculty and staff
 CYBER-SAFETY BASICS A computer security tutorial for UC Davis students, faculty and staff I N T R O D U C T I O N This tutorial provides some basic information and practical suggestions for protecting
CYBER-SAFETY BASICS A computer security tutorial for UC Davis students, faculty and staff I N T R O D U C T I O N This tutorial provides some basic information and practical suggestions for protecting
How Spyware and Anti-Spyware Work
 22 PART 1 INTERNET SECURITY CHAPTER 3 How Spyware and Anti-Spyware Work 23 THESE days, the biggest danger you face when you go onto the Internet might be spyware a type of malicious software that can invade
22 PART 1 INTERNET SECURITY CHAPTER 3 How Spyware and Anti-Spyware Work 23 THESE days, the biggest danger you face when you go onto the Internet might be spyware a type of malicious software that can invade
F-Secure Anti-Virus for Mac 2015
 F-Secure Anti-Virus for Mac 2015 TOC F-Secure Anti-Virus for Mac 2015 Contents Chapter 1: Getting started...3 1.1 Manage subscription...4 1.2 How to make sure that my computer is protected...4 1.2.1 Protection
F-Secure Anti-Virus for Mac 2015 TOC F-Secure Anti-Virus for Mac 2015 Contents Chapter 1: Getting started...3 1.1 Manage subscription...4 1.2 How to make sure that my computer is protected...4 1.2.1 Protection
Computer Security. Uses Zip disks that hold up to 750 MB of data. Must buy and hook up the drive.
 Basic Computer Security Practices Make backups of important files. Apply patches to the operating system. Use anti-virus software, update definitions very frequently, and run a full virus scan at least
Basic Computer Security Practices Make backups of important files. Apply patches to the operating system. Use anti-virus software, update definitions very frequently, and run a full virus scan at least
Get Started Guide - PC Tools Internet Security
 Get Started Guide - PC Tools Internet Security Table of Contents PC Tools Internet Security... 1 Getting Started with PC Tools Internet Security... 1 Installing... 1 Getting Started... 2 iii PC Tools
Get Started Guide - PC Tools Internet Security Table of Contents PC Tools Internet Security... 1 Getting Started with PC Tools Internet Security... 1 Installing... 1 Getting Started... 2 iii PC Tools
Lectures 9 Advanced Operating Systems Fundamental Security. Computer Systems Administration TE2003
 Lectures 9 Advanced Operating Systems Fundamental Security Computer Systems Administration TE2003 Lecture overview At the end of lecture 9 students can identify, describe and discuss: Main factors while
Lectures 9 Advanced Operating Systems Fundamental Security Computer Systems Administration TE2003 Lecture overview At the end of lecture 9 students can identify, describe and discuss: Main factors while
Chapter 3 Safeguarding Your Network
 Chapter 3 Safeguarding Your Network The RangeMax NEXT Wireless Router WNR834B provides highly effective security features which are covered in detail in this chapter. This chapter includes: Choosing Appropriate
Chapter 3 Safeguarding Your Network The RangeMax NEXT Wireless Router WNR834B provides highly effective security features which are covered in detail in this chapter. This chapter includes: Choosing Appropriate
Configuring Routers and Their Settings
 Configuring Routers and Their Settings When installing a router on your home network the routers settings are usually defaulted to automatically protect your home, and simplify setup. This is done because
Configuring Routers and Their Settings When installing a router on your home network the routers settings are usually defaulted to automatically protect your home, and simplify setup. This is done because
Basic Computer Security Part 2
 Basic Computer Security Part 2 Presenter David Schaefer, MBA OCC Manager of Desktop Support Adjunct Security Instructor: Walsh College, Oakland Community College, Lawrence Technology University Welcome
Basic Computer Security Part 2 Presenter David Schaefer, MBA OCC Manager of Desktop Support Adjunct Security Instructor: Walsh College, Oakland Community College, Lawrence Technology University Welcome
What is a Virus? What is a Worm? What is a Trojan Horse? How do worms and other viruses spread? Viruses on the Network. Reducing your virus Risk.
 C/W MARS INC. What is a Virus? What is a Worm? What is a Trojan Horse? How do worms and other viruses spread? Viruses on the Network. Reducing your virus Risk. Prevent Future Infections. Non-Booting System!
C/W MARS INC. What is a Virus? What is a Worm? What is a Trojan Horse? How do worms and other viruses spread? Viruses on the Network. Reducing your virus Risk. Prevent Future Infections. Non-Booting System!
Online Security Awareness - UAE Exchange - Foreign Exchange Send Money UAE Exchange
 The responsibility of safeguarding your personal information starts with you. Your information is critical and it must be protected from unauthorised disclosure, modification or destruction. Here we are
The responsibility of safeguarding your personal information starts with you. Your information is critical and it must be protected from unauthorised disclosure, modification or destruction. Here we are
References NYS Office of Cyber Security and Critical Infrastructure Coordination Best Practices and Assessment Tools for the Household
 This appendix is a supplement to the Cyber Security: Getting Started Guide, a non-technical reference essential for business managers, office managers, and operations managers. This appendix is one of
This appendix is a supplement to the Cyber Security: Getting Started Guide, a non-technical reference essential for business managers, office managers, and operations managers. This appendix is one of
How To Build A Network Security Firewall
 Ethical Hacking and Countermeasures Version 6 Module LX Firewall Technologies News Source: http://www.internetnews.com/ Module Objective This module will familiarize i you with: Firewalls Hardware Firewalls
Ethical Hacking and Countermeasures Version 6 Module LX Firewall Technologies News Source: http://www.internetnews.com/ Module Objective This module will familiarize i you with: Firewalls Hardware Firewalls
