FortiGate-620B Security Appliance Frequently Asked Questions
|
|
|
- Vivian Lucas
- 9 years ago
- Views:
Transcription
1 FortiGate-620B Security Appliance Frequently Asked Questions FAQ Hardware Questions Q: What is the FortiGate-620B? A: The FortiGate-620B is a new medium and large enterprise-class FortiGate with FortiASIC hardware acceleration for firewall/vpn. The FortiGate-620B offers twenty (20) 10/100/1000 Ethernet interfaces. Sixteen of these interfaces are accelerated by the FortiASIC NP2 network processor for wire-speed firewall throughput of 16 Gbps and IPSec VPN throughput of 12 Gbps. Intrusion prevention and antivirus throughput (1 Gbps and 250 Mbps, respectively) are accelerated via the FortiASIC content processor found in all FortiGate models. Optional Advanced Mezzanine Card (AMC) expansion options allow for an additional 4 Gigabit SFP-based Ethernet ports or local HDD capacity for log storage. The FortiGate-620B s increased firewall/vpn throughput and high port density relieves medium and large businesses of the restraints that have historically prevented internal network security segmentation. Q: What types of security features are available on the FG-620B? A: Fortinet s FortiGate-620B is a purpose-built appliances that provide comprehensive security capabilities including firewall, antivirus, antispyware, intrusion prevention, IPSec and SSL VPN, web content filtering, spam filtering, spyware/grayware filtering, and traffic management tools. The FG-620B is designed for medium to large enterprises and regional offices. This full-featured network security appliance offers comprehensive protection to distributed networks, meeting the needs for an array of mission critical applications such as , Web, VOIP, IM, and P2P with extensive network management, logging, and reporting capabilities. Q: What is different about the Fortinet FG-620B? A: The FG-620B is a disruptive new multi-threat security device that offers best in class throughput and port density by leveraging the power of FortiASIC network and content processors. Competitive advantages include: 3X greater FW/VPN throughput than any other product in its class Double the number ports of any other product in its class Optional AMC expansion capability (4 x NP accelerated SFP ports or HDD for local log and content archive) Best price/performance ratio of any product in its class Lowest price per port of any product in its class Lowest cost per Mbps of firewall throughput of any product in its class Backed by Fortinet s own FortiGuard Service Subscriptions which include: FortiGuard Antivirus and Antispyware Service FortiGuard Intrusion Prevention System Service FortiGuard Web Filtering Service FortiGuard Antispam Service Q: What is the advantage of having so many FortiASIC Network Processor-accelerated ports? A: Increasing newtork sizes, throughputs, and applications warrant internal network segmentation points for Gbps links in order to increase security layers and decrease security zone size. These drivers are requiring increased performance and interfaces within security infrastructure. Fortinet 1 August 2008
2 Q: Will fiber SFPs be supported by the FG-620B? A: The 20 ports available on a FG-620B base model are copper ports. However, the FG-620B does support AMC expansion module ASM-FB4, which offers four additional FortiASIC network processor-accelerated SFP ports which support fiber transceivers. Q: What happened to the older mid-range FortiGate products? A: Fortinet still sells most of these older models, however based on Moore s Law of increasing density of circuitry and performance over time with a decreasing price, Fortinet now offers the much higher performing FG-620B with a greatly improved price/performance ratio over older models. The FG-620B offers increased port density, security throughput, and modularity. Q: What is an AMC expansion slot? A: The Advanced Mezzanine Card (AMC) standard, also known as AdvancedMC, was developed by the PCI Industrial Computers Manufacturers Group (PICMG), which has over 100 companies building to the specification. AdvancedMC has been developed to meet the requirements for the next generation of carrier grade communications equipment. Q: What optional cards are supported by the FG-620B? A: The FG-620B supports two optional AMCs: 1. The ASM-FB4 AMC, which provides four additional FortiASIC network processor-accelerated SFP ports for an additional 4Gbps firewall and 3Gbps IPSec VPN throughput. 2. The ASM-SO8 AMC, which provides 80GB of disk-based storage for local logging and content archiving. The FortiGate does not boot from the disk drive, nor does it store configuration or operating system files on it. Q: What benefit does the ASM-SO8 hard drive AMC option provide? A: The hard drive option provides the added benefit of storing logs and quarantine files locally. This option would also allow customers to store traffic log data which is not available from a memory logging-only configuration. These added features are also available with an external FortiAnalyzer device which provides other benefits such as content logging, forensic analysis, as well as over 300 standard and customizable reports. Q: Is the FG-620B appliance rack mountable? A: Yes. All mid-range models come with rack mount ears and optional rubber feet to allow flexibility in any mounting environment. All models have built-in cooling fans. Each consumes only one rack unit of space in an industry standard 19-inch equipment rack. Q: Are there different models for countries with 220V vs. 110V power? A: All models have a built-in power supply that auto-senses between 100 to 240 VAC. Each unit comes with a regional power cord for most common worldwide power socket configurations. Simply add the proper two-digit suffix to the SKU when ordering to specify the desired power cord option, e.g. FG-620B-US or FG-620B-UK. Power cord choices include: -US (USA style), -UK (United Kingdom style), -EU (European style), -AU (Australian style). Q: Is the FG-620B RoHS compliant? A: Yes, the FG-620B is RoHS compliant. Software Questions Q: What is FortiOS? A: FortiOS is the multi-layered security software that runs on all FortiGate products. It is a proprietary securityhardened operating system that provides all of the multi-threat security functions. FortiOS provides the capability to manage FortiGate devices either via a secure GUI web-based user interface or a command line user interface. Q: What is the latest version of FortiOS? A: At the time of writing, Version 3.0 MR7 Patch 1 is the latest release of FortiOS. It was released to the public in October Q: What type of security modules does FortiOS offer? A: Fortinet's FortiGate systems provide the industry's broadest suite of best in class security protections in a single platform, inclusive of firewall, IPSec VPN, SSL VPN, antivirus, antispyware, intrusion detection/prevention system, web content filtering, antispam and traffic shaping functionality. Deployed as an integrated or standalone solution, Fortinet 2 August 2008
3 FortiGate systems detect and eliminate today's threats as well as emerging bended threats that cannot be detected and eliminated by competitive solutions. Q: Can I assign two ports as dual WAN interfaces for load balancing traffic? A: Yes you can. There are a couple of methods for doing this. One is to use the built-in Equal Cost Multi-Path (ECMP) routing mechanism offered in version 3.0 MR2 and above. This method uses a simple hash algorithm to automatically balance sessions between two or more equal cost routes. The other is to use policy-based routing rules (available since version 2.8) to manually send some traffic to one port and other traffic to a different port. You can route based on source or destination IP addresses or based on protocol type / TCP or UDP port numbers, or any combination of the above. Q: What happens to log messages if I don t have the hard drive AMC installed? A: Log messages can be sent to external logging and reporting devices such as a FortiAnalyzer, or can be forwarded to any syslog compatible server. Once sent to a FortiAnalyzer, log messages can be browsed directly from the FortiGate web GUI. Additionally each FortiGate reserves a small amount of memory for short term logging which can be uploaded or deleted as needed. Due to memory constraints FortiGate cannot perform detailed traffic or content logging to local memory. Multiple log output destinations are supported. The FortiGate can send logs to up to three syslog servers or FortiAnalyzers. Q: What types of high-availability features are offered? A: All mid-range FortiGate models support high-availability (HA) clustering. This includes both active-passive and active-active HA where the standby unit can also be used to load balance the traffic and in some cases provide additional processing power and overall throughput gains. The Fortinet HA clustering technique allows clustering of up to four units for increased reliability and performance. Various load-balancing algorithms are available such as round robin, least connections, and weighted round robin to take best advantage of different clustering configurations. However you can only combine like-models together in the same cluster. Security Subscription Services Q: What subscription services are available? A: All standard FortiGate product security subscription services are available on each FortiGate appliance. Security subscription services are inclusive of the FortiGuard Antivirus, IPS, Web Filtering, and Antispam services. Security subscription service bundles are also available to save cost over buying each service separately. No user licensing or user restrictions exist on any FortiGate model. Q: How often are these subscription services updated? A: Each FortiGuard service has constantly upgraded databases in order to keep your FortiGate units up to date to protect against recent cyber threats. The signature and vulnerability based Antivirus, Antispyware and Intrusion Prevention System services have the ability to automatically push real-time updates to registered and configured units at any time 24 hours a day. The real-time services inclusive of Antispam and Web Content Filtering are constantly upgraded databases that maintain the highest possible accuracy. Q: How does Fortinet subscription service response time compare to the industry? A: Fortinet s FortiGuard subscription services with Service Level Agreement and FortiGuard Distribution Network provides Fortinet customers with the highest responsiveness of security vendors in both response time of creating new signatures to new exploits and breadth of coverage for antivirus, antispyware, web content filtering, intrusion prevention and antispam. Security Deployment Scenarios Q: How do I determine what size FortiGate is needed for my deployment? A: Units are deployed based on throughput performance, not number of users. In fact, all FortiGate models have unlimited user licenses. Customers choose the proper model based on desired Firewall, or VPN, or content scanning performance needed. Customers should note that if they want to enable multiple security functions such as FW + VPN + AV they would use the lowest common performance factor as the denominator, which is usually the AV scanning performance. Contact your local Fortinet SE or Fortinet Value Added Reseller for assistance in FortiGate sizing. A sizing tool is also available on the Sales Intranet/Partner extranet site which will ask questions about users, throughput, and traffic requirements to help properly size the right model for customer requirements. Fortinet 3 August 2008
4 Q: How is the FG-620B positioned against the rest of the mid-range and high-end FortiGate models? A: The FG-620B is a replacement to the FG-800 product. It is the second new medium and large product introduction following the FG-310B. The price and performance of the FG-620B is roughly double that of the FG-310B, and is intended to continue raising the standard for mid-range security products by offering a high number of wire speed firewall ports. The new standard that Fortinet is setting for mid-range products and above is wire speed firewall ports on all models. Historically, firewall throughput has been the main metric used to determine product classification. Since all mid-range and high-end FortiGates will offer wire speed firewall, the new metric to determine classification is the full content inspection (i.e. IPS and AV). These are the performance metrics that distinguish mid-range products from high-end products. Other features of the high-end products (3000 series and 5000 series) may include switch-based form factors, stackability using multiple switch blades, extensive AMC modularity, dual power supplies, SFP ports, and, of course, increased IPS and AV throughput and content level metrics such as number of sessions, new sessions per second, number of policies, etc. Q: What security modules are recommended for MSSP (managed security service providers)? A: MSSPs typically need a flexible Customer Premise Equipment (CPE) platform that can be remotely managed and can have many security options available for menu-style security service offerings. All FortiGate models come with built-in remote management tools that allow centralized security policy management and remote event monitoring for control via a security operations center. Additional products available such as FortiManager and /or FortiAnalyzer provide the management tools to administer remote sites and scales from a multiple branch office network up to a global multi-domain operation. Q: What security modules are recommended for perimeter security? A: Perimeter networks generally require Firewall and VPN (IPSec and/or SSL) features and also will benefit from IPS and Antivirus protection. In some deployment scenarios where compliance requirements are in place that restrict access to specific web content, Web Content Filtering protection may be appropriate. Q: What security modules are recommended for secure messaging? A: A secure messaging system normally includes Antivirus and Antispam security and can also include Instant Messenger security if applicable. Q: What security modules are recommended for data center? A: Data Center security will normally require network and application security features including Firewall, IPS and Antivirus features. Antivirus protection will generally be used for specific application protocols used in the data center such as HTTP / FTP for web servers and SMTP / POP for servers. Performance & Throughput Q: Can I cluster these units together for better performance? A: Yes, with HA clustering in active-active mode customers can gain performance improvements, but only for certain types of traffic; including antivirus scanned sessions and TCP sessions only. Consult with your local Fortinet SE to find out more about implementing HA in your environment. Q: What are the key technical specifications and throughput measurements of the FG-620B? A: See performance metric chart below: Fortinet 4 August 2008
5 System Performance Firewall Throughput - Avg Size Packets (512 byte) Firewall Throughput - Small Size Packets (64 byte) IPSec VPN Throughput FortiGate-620B Base Model 16 Gbps 16 Gbps 12 Gbps FG-620B With Optional 4-Port AMC Module (ASM-FB4) 20 Gbps 20 Gbps 15 Gbps Antivirus Throughput IPS Throughput Dedicated IPSec VPN Tunnels Concurrent Sessions New Sessions/Sec Policies Unlimited User Licenses 250 Mbps 1Gbps 20, ,000 25, ,000 Yes Q: What are the performance assumptions for these metrics? A: The FortiGate-620B firewall throughput specification is based on benchmark results for 512-byte and 64-byte UDP packets processed while the FortiGate is operating in NAT mode. Antivirus performance is measured based on HTTP traffic with 32-Kbyte file attachments and IPS performance is measured based on UDP traffic with 512-byte packet size. Actual performance may vary depending on network traffic and environments. Copyright 2008 Fortinet, Inc. All rights reserved. No part of this publication including text, examples, diagrams or illustrations may be reproduced, transmitted, or translated in any form or by any means, electronic, mechanical, manual, optical or otherwise, for any purpose, without prior written permission of Fortinet Inc. Trademarks Products mentioned in this document are trademarks or registered trademarks of their respective holders. Disclaimer Although Fortinet has attempted to provide accurate information in these materials, Fortinet assumes no legal responsibility for the accuracy or completeness of the information. More specific information is available on request from Fortinet. Please note that Fortinet's product information does not constitute or contain any guarantee, warranty or legally binding representation, unless expressly identified as such in a duly signed writing. FG-620B-FAQ-R Fortinet 5 August 2008
Fortigate Features & Demo
 & Demo Prepared and Presented by: Georges Nassif Technical Manager Triple C Firewall Antivirus IPS Web Filtering AntiSpam Application Control DLP Client Reputation (cont d) Traffic Shaping IPSEC VPN SSL
& Demo Prepared and Presented by: Georges Nassif Technical Manager Triple C Firewall Antivirus IPS Web Filtering AntiSpam Application Control DLP Client Reputation (cont d) Traffic Shaping IPSEC VPN SSL
TECHNICAL NOTE. FortiGate Traffic Shaping Version 2.80. www.fortinet.com
 TECHNICAL NOTE FortiGate Traffic Shaping Version 2.80 www.fortinet.com FortiGate Traffic Shaping Technical Note Version 2.80 March 10, 2006 01-28000-0304-20060310 Copyright 2005 Fortinet, Inc. All rights
TECHNICAL NOTE FortiGate Traffic Shaping Version 2.80 www.fortinet.com FortiGate Traffic Shaping Technical Note Version 2.80 March 10, 2006 01-28000-0304-20060310 Copyright 2005 Fortinet, Inc. All rights
INTRODUCTION TO FIREWALL SECURITY
 INTRODUCTION TO FIREWALL SECURITY SESSION 1 Agenda Introduction to Firewalls Types of Firewalls Modes and Deployments Key Features in a Firewall Emerging Trends 2 Printed in USA. What Is a Firewall DMZ
INTRODUCTION TO FIREWALL SECURITY SESSION 1 Agenda Introduction to Firewalls Types of Firewalls Modes and Deployments Key Features in a Firewall Emerging Trends 2 Printed in USA. What Is a Firewall DMZ
Unified Threat Management Throughput Performance
 Unified Threat Management Throughput Performance Desktop Device Comparison DR150818C October 2015 Miercom www.miercom.com Contents Executive Summary... 3 Introduction... 4 Products Tested... 6 How We Did
Unified Threat Management Throughput Performance Desktop Device Comparison DR150818C October 2015 Miercom www.miercom.com Contents Executive Summary... 3 Introduction... 4 Products Tested... 6 How We Did
- Introduction to PIX/ASA Firewalls -
 1 Cisco Security Appliances - Introduction to PIX/ASA Firewalls - Both Cisco routers and multilayer switches support the IOS firewall set, which provides security functionality. Additionally, Cisco offers
1 Cisco Security Appliances - Introduction to PIX/ASA Firewalls - Both Cisco routers and multilayer switches support the IOS firewall set, which provides security functionality. Additionally, Cisco offers
QUESTION: 1 Which of the following are valid authentication user group types on a FortiGate unit? (Select all that apply.)
 1 Fortinet - FCNSA Fortinet Certified Network Security Administrator QUESTION: 1 Which of the following are valid authentication user group types on a FortiGate unit? (Select all that apply.) A. Firewall
1 Fortinet - FCNSA Fortinet Certified Network Security Administrator QUESTION: 1 Which of the following are valid authentication user group types on a FortiGate unit? (Select all that apply.) A. Firewall
Feature Brief. FortiGate TM Multi-Threat Security System v3.00 MR5 Rev. 1.1 July 20, 2007
 Feature Brief FortiGate TM Multi-Threat Security System v3.00 MR5 Rev. 1.1 July 20, 2007 Revision History Revision Change Description 1.0 Initial Release. 1.1 Removed sectoin on Content Archive and AV
Feature Brief FortiGate TM Multi-Threat Security System v3.00 MR5 Rev. 1.1 July 20, 2007 Revision History Revision Change Description 1.0 Initial Release. 1.1 Removed sectoin on Content Archive and AV
HA OVERVIEW. FortiGate FortiOS v3.0 MR5. www.fortinet.com
 HA OVERVIEW FortiGate FortiOS v3.0 MR5 www.fortinet.com FortiGate HA Overview FortiOS v3.0 MR5 1 October 2007 01-30005-0351-20071001 Copyright 2007 Fortinet, Inc. All rights reserved. No part of this publication
HA OVERVIEW FortiGate FortiOS v3.0 MR5 www.fortinet.com FortiGate HA Overview FortiOS v3.0 MR5 1 October 2007 01-30005-0351-20071001 Copyright 2007 Fortinet, Inc. All rights reserved. No part of this publication
FortiGate 100D Series
 DATA SHEET FortiGate 100D Series Integrated Security for Small and Medium Enterprises FortiGate 100D Series FortiGate 100D, 140D, 140D-POE and 140D-POE-T1 In order to comply with legislation and secure
DATA SHEET FortiGate 100D Series Integrated Security for Small and Medium Enterprises FortiGate 100D Series FortiGate 100D, 140D, 140D-POE and 140D-POE-T1 In order to comply with legislation and secure
High Availability. FortiOS Handbook v3 for FortiOS 4.0 MR3
 High Availability FortiOS Handbook v3 for FortiOS 4.0 MR3 FortiOS Handbook High Availability v3 2 May 2014 01-431-99686-20140502 Copyright 2014 Fortinet, Inc. All rights reserved. Fortinet, FortiGate,
High Availability FortiOS Handbook v3 for FortiOS 4.0 MR3 FortiOS Handbook High Availability v3 2 May 2014 01-431-99686-20140502 Copyright 2014 Fortinet, Inc. All rights reserved. Fortinet, FortiGate,
Nokia IP Security Platforms Technical Specifications Guide Nokia Enterprise Solutions
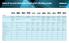 Nokia IP Security Platforms Technical Specifications Guide Nokia Enterprise Solutions Positioning Enterprise ROBO 8, 16, 32 and Unlimited Work extender, telecommuter, small office FW or VPN Medium businesses
Nokia IP Security Platforms Technical Specifications Guide Nokia Enterprise Solutions Positioning Enterprise ROBO 8, 16, 32 and Unlimited Work extender, telecommuter, small office FW or VPN Medium businesses
FortiGate/FortiWiFi -60C Series Integrated Threat Management for Small Networks
 FortiGate/FortiWiFi -60C Series Integrated Threat Management for Small Networks The FortiGate/FortiWiFi-60C Series are compact, all-in-one security appliances that deliver Fortinet s Connected UTM. Ideal
FortiGate/FortiWiFi -60C Series Integrated Threat Management for Small Networks The FortiGate/FortiWiFi-60C Series are compact, all-in-one security appliances that deliver Fortinet s Connected UTM. Ideal
High performance security for low-latency networks
 High performance security for low-latency networks Fortinet solutions for the financial services sector Financial Services Fortinet solutions protect your network and proprietary data without compromising
High performance security for low-latency networks Fortinet solutions for the financial services sector Financial Services Fortinet solutions protect your network and proprietary data without compromising
Fortinet Certified Network Security Administrator
 Fortigate 1 Fortinet Certified Network Security Administrator Objectives The Fortinet Certified Network Security Administratordesignation certifies that individuals have the expertise necessary to manage
Fortigate 1 Fortinet Certified Network Security Administrator Objectives The Fortinet Certified Network Security Administratordesignation certifies that individuals have the expertise necessary to manage
FortiOS Handbook WAN Optimization, Web Cache, Explicit Proxy, and WCCP for FortiOS 5.0
 FortiOS Handbook WAN Optimization, Web Cache, Explicit Proxy, and WCCP for FortiOS 5.0 FortiOS Handbook WAN Optimization, Web Cache, Explicit Proxy, and WCCP for FortiOS 5.0 June 10, 2014 01-500-96996-20140610
FortiOS Handbook WAN Optimization, Web Cache, Explicit Proxy, and WCCP for FortiOS 5.0 FortiOS Handbook WAN Optimization, Web Cache, Explicit Proxy, and WCCP for FortiOS 5.0 June 10, 2014 01-500-96996-20140610
1Fortinet. 2How Logtrust. Firewall technologies from Fortinet offer integrated, As your business grows and volumes of data increase,
 Fortinet 1Fortinet Firewall technologies from Fortinet offer integrated, high-performance protection against today s wide range of threats targeting applications, data and users. Fortinet s firewall technology
Fortinet 1Fortinet Firewall technologies from Fortinet offer integrated, high-performance protection against today s wide range of threats targeting applications, data and users. Fortinet s firewall technology
Cyberoam Perspective BFSI Security Guidelines. Overview
 Overview The term BFSI stands for Banking, Financial Services and Insurance (BFSI). This term is widely used to address those companies which provide an array of financial products or services. Financial
Overview The term BFSI stands for Banking, Financial Services and Insurance (BFSI). This term is widely used to address those companies which provide an array of financial products or services. Financial
TECHNICAL NOTE. FortiGate Support for SIP FortiOS v3.0 MR5. www.fortinet.com
 TECHNICAL NOTE FortiGate Support for SIP FortiOS v3.0 MR5 www.fortinet.com FortiGate Support for SIP Technical Note FortiOS v3.0 MR5 22 August 2007 01-30005-0232-20070822 Copyright 2007 Fortinet, Inc.
TECHNICAL NOTE FortiGate Support for SIP FortiOS v3.0 MR5 www.fortinet.com FortiGate Support for SIP Technical Note FortiOS v3.0 MR5 22 August 2007 01-30005-0232-20070822 Copyright 2007 Fortinet, Inc.
Sophos SG Series Appliances
 Unleash the full potential of your network With bandwidth requirements constantly increasing, network security appliances need to do more than ever before. The Sophos SG Series appliances are built to
Unleash the full potential of your network With bandwidth requirements constantly increasing, network security appliances need to do more than ever before. The Sophos SG Series appliances are built to
FortiGate/FortiWiFi -90D Series Enterprise-Grade Protection for Smaller Networks
 FortiGate/FortiWiFi -90D Series Enterprise-Grade Protection for Smaller Networks FortiGate/FortiWiFi-90D Series consolidated security appliances deliver comprehensive enterprise-class protection for remote
FortiGate/FortiWiFi -90D Series Enterprise-Grade Protection for Smaller Networks FortiGate/FortiWiFi-90D Series consolidated security appliances deliver comprehensive enterprise-class protection for remote
Sophos SG Series Appliances
 Unleash the full potential of your network With bandwidth requirements constantly increasing, network security appliances need to do more than ever before. The Sophos SG Series appliances are built to
Unleash the full potential of your network With bandwidth requirements constantly increasing, network security appliances need to do more than ever before. The Sophos SG Series appliances are built to
FortiGate High Availability Overview Technical Note
 FortiGate High Availability Overview Technical Note FortiGate High Availability Overview Technical Note Document Version: 2 Publication Date: 21 October, 2005 Description: This document provides an overview
FortiGate High Availability Overview Technical Note FortiGate High Availability Overview Technical Note Document Version: 2 Publication Date: 21 October, 2005 Description: This document provides an overview
Supported Upgrade Paths for FortiOS Firmware VERSION 5.0.12
 Supported Upgrade Paths for FortiOS Firmware VERSION 5.0.12 FORTINET DOCUMENT LIBRARY http://docs.fortinet.com FORTINET VIDEO GUIDE http://video.fortinet.com FORTINET BLOG https://blog.fortinet.com CUSTOMER
Supported Upgrade Paths for FortiOS Firmware VERSION 5.0.12 FORTINET DOCUMENT LIBRARY http://docs.fortinet.com FORTINET VIDEO GUIDE http://video.fortinet.com FORTINET BLOG https://blog.fortinet.com CUSTOMER
Astaro Gateway Software Applications
 Astaro Overview Astaro Products - Astaro Security Gateway - Astaro Web Gateway - Astaro Mail Gateway - Astaro Command Center - Astaro Report Manager Astaro Gateway Software Applications - Network Security
Astaro Overview Astaro Products - Astaro Security Gateway - Astaro Web Gateway - Astaro Mail Gateway - Astaro Command Center - Astaro Report Manager Astaro Gateway Software Applications - Network Security
FortiGate /FortiWiFi -80 Series Enterprise-Class Protection for Branch Offices
 DATASHEET FortiGate /FortiWiFi -80 Series Enterprise-Class Protection for Branch Offices Proven Security for Remote Offices, Retail, and Customer Premise Equipment FortiGate/FortiWiFi-80 Series consolidated
DATASHEET FortiGate /FortiWiFi -80 Series Enterprise-Class Protection for Branch Offices Proven Security for Remote Offices, Retail, and Customer Premise Equipment FortiGate/FortiWiFi-80 Series consolidated
WAN Optimization, Web Cache, Explicit Proxy, and WCCP. FortiOS Handbook v3 for FortiOS 4.0 MR3
 WAN Optimization, Web Cache, Explicit Proxy, and WCCP FortiOS Handbook v3 for FortiOS 4.0 MR3 FortiOS Handbook WAN Optimization, Web Cache, Explicit Proxy, and WCCP v3 13 January 2012 01-433-96996-20120113
WAN Optimization, Web Cache, Explicit Proxy, and WCCP FortiOS Handbook v3 for FortiOS 4.0 MR3 FortiOS Handbook WAN Optimization, Web Cache, Explicit Proxy, and WCCP v3 13 January 2012 01-433-96996-20120113
Networking for Caribbean Development
 Networking for Caribbean Development BELIZE NOV 2 NOV 6, 2015 w w w. c a r i b n o g. o r g N E T W O R K I N G F O R C A R I B B E A N D E V E L O P M E N T BELIZE NOV 2 NOV 6, 2015 w w w. c a r i b n
Networking for Caribbean Development BELIZE NOV 2 NOV 6, 2015 w w w. c a r i b n o g. o r g N E T W O R K I N G F O R C A R I B B E A N D E V E L O P M E N T BELIZE NOV 2 NOV 6, 2015 w w w. c a r i b n
LotWan Appliance User Guide USER GUIDE
 LotWan Appliance User Guide USER GUIDE Copyright Information Copyright 2014, Beijing AppEx Networks Corporation The description, illustrations, pictures, methods and other information contain in this document
LotWan Appliance User Guide USER GUIDE Copyright Information Copyright 2014, Beijing AppEx Networks Corporation The description, illustrations, pictures, methods and other information contain in this document
PERFORMANCE VALIDATION OF JUNIPER NETWORKS SRX5800 SERVICES GATEWAY
 APPLICATION NOTE PERFORMANCE VALIDATION OF JUNIPER NETWORKS SRX5800 SERVICES GATEWAY Copyright 2010, Juniper Networks, Inc. Table of Contents Introduction........................................................................................
APPLICATION NOTE PERFORMANCE VALIDATION OF JUNIPER NETWORKS SRX5800 SERVICES GATEWAY Copyright 2010, Juniper Networks, Inc. Table of Contents Introduction........................................................................................
NetScreen-5GT Announcement Frequently Asked Questions (FAQ)
 Announcement Frequently Asked Questions (FAQ) Q: What is the? A: The is a high performance network security appliance targeted to small or remote offices in distributed enterprises, including telecommuters,
Announcement Frequently Asked Questions (FAQ) Q: What is the? A: The is a high performance network security appliance targeted to small or remote offices in distributed enterprises, including telecommuters,
MANAGED FIREWALL SERVICE. Service definition
 MANAGED FIREWALL SERVICE Service definition Page 1 of 4 Version 1.2 (03/02/2015) NSMS Managed Firewalls Service Definition Understanding of a firewall service The function of any firewall service is to
MANAGED FIREWALL SERVICE Service definition Page 1 of 4 Version 1.2 (03/02/2015) NSMS Managed Firewalls Service Definition Understanding of a firewall service The function of any firewall service is to
How To Configure The Fortigate Cluster Protocol In A Cluster Of Three (Fcfc) On A Microsoft Ipo (For A Powerpoint) On An Ipo 2.5 (For An Ipos 2.2.5)
 FortiGate High Availability Guide FortiGate High Availability Guide Document Version: 5 Publication Date: March 10, 2005 Description: This document describes FortiGate FortiOS v2.80 High Availability.
FortiGate High Availability Guide FortiGate High Availability Guide Document Version: 5 Publication Date: March 10, 2005 Description: This document describes FortiGate FortiOS v2.80 High Availability.
High Performance NGFW Extended
 High Performance NGFW Extended Enrique Millán Country Manager Colombia [email protected] 1 Copyright 2013 Fortinet Inc. All rights reserved. D I S C L A I M E R This document contains confidential material
High Performance NGFW Extended Enrique Millán Country Manager Colombia [email protected] 1 Copyright 2013 Fortinet Inc. All rights reserved. D I S C L A I M E R This document contains confidential material
Virtualized Security: The Next Generation of Consolidation
 Virtualization. Consolidation. Simplification. Choice. WHITE PAPER Virtualized Security: The Next Generation of Consolidation Virtualized Security: The Next Generation of Consolidation As we approach the
Virtualization. Consolidation. Simplification. Choice. WHITE PAPER Virtualized Security: The Next Generation of Consolidation Virtualized Security: The Next Generation of Consolidation As we approach the
Implementing Cisco IOS Network Security
 Implementing Cisco IOS Network Security IINS v3.0; 5 Days, Instructor-led Course Description Implementing Cisco Network Security (IINS) v3.0 is a 5-day instructor-led course focusing on security principles
Implementing Cisco IOS Network Security IINS v3.0; 5 Days, Instructor-led Course Description Implementing Cisco Network Security (IINS) v3.0 is a 5-day instructor-led course focusing on security principles
Total Cost of Ownership: Benefits of Comprehensive, Real-Time Gateway Security
 Total Cost of Ownership: Benefits of Comprehensive, Real-Time Gateway Security White Paper September 2003 Abstract The network security landscape has changed dramatically over the past several years. Until
Total Cost of Ownership: Benefits of Comprehensive, Real-Time Gateway Security White Paper September 2003 Abstract The network security landscape has changed dramatically over the past several years. Until
Network Intrusion Prevention Systems (IPS) Frequently Asked Questions FAQ
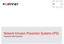 Network Intrusion Prevention Systems (IPS) Frequently Asked Questions FAQ FORTINET Network Intrusion Prevention Systems (IPS) PAGE 2 Introduction Deploying updates and patches to devices and servers in
Network Intrusion Prevention Systems (IPS) Frequently Asked Questions FAQ FORTINET Network Intrusion Prevention Systems (IPS) PAGE 2 Introduction Deploying updates and patches to devices and servers in
Unified Threat Management, Managed Security, and the Cloud Services Model
 Unified Threat Management, Managed Security, and the Cloud Services Model Kurtis E. Minder CISSP Global Account Manager - Service Provider Group Fortinet, Inc. Introduction Kurtis E. Minder, Technical
Unified Threat Management, Managed Security, and the Cloud Services Model Kurtis E. Minder CISSP Global Account Manager - Service Provider Group Fortinet, Inc. Introduction Kurtis E. Minder, Technical
Configuration Example
 Configuration Example FortiGate Enterprise Version 3.0 MR5 www.fortinet.com FortiGate Enterprise Configuration Example Version 3.0 MR5 August 28, 2007 01-30005-0315-20070828 Copyright 2007 Fortinet, Inc.
Configuration Example FortiGate Enterprise Version 3.0 MR5 www.fortinet.com FortiGate Enterprise Configuration Example Version 3.0 MR5 August 28, 2007 01-30005-0315-20070828 Copyright 2007 Fortinet, Inc.
FortiCarrier Systems Specialized Security for Service Providers
 DATASHEET FortiCarrier Systems Specialized Security for Service Providers As the communications industry continues its convergence toward an all-ip model, service providers of all types are challenged
DATASHEET FortiCarrier Systems Specialized Security for Service Providers As the communications industry continues its convergence toward an all-ip model, service providers of all types are challenged
FortiMail VM (Microsoft Hyper-V) Install Guide
 FortiMail VM (Microsoft Hyper-V) Install Guide FortiMail VM (Microsoft Hyper-V) Install Guide August 20, 2014 1st Edition Copyright 2014 Fortinet, Inc. All rights reserved. Fortinet, FortiGate, FortiCare
FortiMail VM (Microsoft Hyper-V) Install Guide FortiMail VM (Microsoft Hyper-V) Install Guide August 20, 2014 1st Edition Copyright 2014 Fortinet, Inc. All rights reserved. Fortinet, FortiGate, FortiCare
ANNEXURE TO TENDER NO. MRPU/IGCAR/COMP/5239
 ANNEXURE TO TENDER NO. MRPU/IGCAR/COMP/5239 Check Point Firewall Software and Management Software I. Description of the Item Up gradation, installation and commissioning of Checkpoint security gateway
ANNEXURE TO TENDER NO. MRPU/IGCAR/COMP/5239 Check Point Firewall Software and Management Software I. Description of the Item Up gradation, installation and commissioning of Checkpoint security gateway
FortiWeb 5.0, Web Application Firewall Course #251
 FortiWeb 5.0, Web Application Firewall Course #251 Course Overview Through this 1-day instructor-led classroom or online virtual training, participants learn the basic configuration and administration
FortiWeb 5.0, Web Application Firewall Course #251 Course Overview Through this 1-day instructor-led classroom or online virtual training, participants learn the basic configuration and administration
Deployment Guide: Transparent Mode
 Deployment Guide: Transparent Mode March 15, 2007 Deployment and Task Overview Description Follow the tasks in this guide to deploy the appliance as a transparent-firewall device on your network. This
Deployment Guide: Transparent Mode March 15, 2007 Deployment and Task Overview Description Follow the tasks in this guide to deploy the appliance as a transparent-firewall device on your network. This
Barracuda Link Balancer
 Barracuda Networks Technical Documentation Barracuda Link Balancer Administrator s Guide Version 2.2 RECLAIM YOUR NETWORK Copyright Notice Copyright 2004-2011, Barracuda Networks www.barracuda.com v2.2-110503-01-0503
Barracuda Networks Technical Documentation Barracuda Link Balancer Administrator s Guide Version 2.2 RECLAIM YOUR NETWORK Copyright Notice Copyright 2004-2011, Barracuda Networks www.barracuda.com v2.2-110503-01-0503
FortiGate 200D Series
 DATA SHEET FortiGate 200D Series Secure Protection for the Campus Perimeter and Branch Office FortiGate 200D Series FortiGate 200D, 200D-, 240D, 240D- and 280D- The FortiGate 200D series delivers high-speed
DATA SHEET FortiGate 200D Series Secure Protection for the Campus Perimeter and Branch Office FortiGate 200D Series FortiGate 200D, 200D-, 240D, 240D- and 280D- The FortiGate 200D series delivers high-speed
Introducing FortiDDoS. Mar, 2013
 Introducing FortiDDoS Mar, 2013 Introducing FortiDDoS Hardware Accelerated DDoS Defense Intent Based Protection Uses the newest member of the FortiASIC family, FortiASIC-TP TM Rate Based Detection Inline
Introducing FortiDDoS Mar, 2013 Introducing FortiDDoS Hardware Accelerated DDoS Defense Intent Based Protection Uses the newest member of the FortiASIC family, FortiASIC-TP TM Rate Based Detection Inline
FortiGuard Web Content Filtering versus Websense March 2005
 FortiGuard Web Content Filtering versus Websense March 2005 FortiGuard Web Filtering offers schools and enterprises a cost effective and easy to deploy solution to enforce safe and acceptable web usage
FortiGuard Web Content Filtering versus Websense March 2005 FortiGuard Web Filtering offers schools and enterprises a cost effective and easy to deploy solution to enforce safe and acceptable web usage
Firewall. FortiOS Handbook v3 for FortiOS 4.0 MR3
 Firewall FortiOS Handbook v3 for FortiOS 4.0 MR3 FortiOS Handbook Firewall v3 24 January 2012 01-432-148222-20120124 Copyright 2012 Fortinet, Inc. All rights reserved. Contents and terms are subject to
Firewall FortiOS Handbook v3 for FortiOS 4.0 MR3 FortiOS Handbook Firewall v3 24 January 2012 01-432-148222-20120124 Copyright 2012 Fortinet, Inc. All rights reserved. Contents and terms are subject to
SonicWALL Clean VPN. Protect applications with granular access control based on user identity and device identity/integrity
 SSL-VPN Combined With Network Security Introducing A popular feature of the SonicWALL Aventail SSL VPN appliances is called End Point Control (EPC). This allows the administrator to define specific criteria
SSL-VPN Combined With Network Security Introducing A popular feature of the SonicWALL Aventail SSL VPN appliances is called End Point Control (EPC). This allows the administrator to define specific criteria
Check Point taps the power of virtualization to simplify security for private clouds
 Datasheet: Check Point Virtual Systems Check Point taps the power of virtualization to simplify security for private clouds Looking for ways to reduce complexity and simplify network security in your private
Datasheet: Check Point Virtual Systems Check Point taps the power of virtualization to simplify security for private clouds Looking for ways to reduce complexity and simplify network security in your private
Scalable. Reliable. Flexible. High Performance Architecture. Fault Tolerant System Design. Expansion Options for Unique Business Needs
 Protecting the Data That Drives Business SecureSphere Appliances Scalable. Reliable. Flexible. Imperva SecureSphere appliances provide superior performance and resiliency for demanding network environments.
Protecting the Data That Drives Business SecureSphere Appliances Scalable. Reliable. Flexible. Imperva SecureSphere appliances provide superior performance and resiliency for demanding network environments.
Appliance Comparison Chart
 Security Gateway Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark - version R77 and later) Security 2 2 230 405 673 Firewall (Gbps).4.4 2.2 3.4
Security Gateway Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark - version R77 and later) Security 2 2 230 405 673 Firewall (Gbps).4.4 2.2 3.4
Intel Network Builders: Lanner and Intel Building the Best Network Security Platforms
 Solution Brief Intel Xeon Processors Lanner Intel Network Builders: Lanner and Intel Building the Best Network Security Platforms Internet usage continues to rapidly expand and evolve, and with it network
Solution Brief Intel Xeon Processors Lanner Intel Network Builders: Lanner and Intel Building the Best Network Security Platforms Internet usage continues to rapidly expand and evolve, and with it network
Overview and Deployment Guide. Sophos UTM on AWS
 Overview and Deployment Guide Sophos UTM on AWS Overview and Deployment Guide Document date: November 2014 1 Sophos UTM and AWS Contents 1 Amazon Web Services... 4 1.1 AMI (Amazon Machine Image)... 4 1.2
Overview and Deployment Guide Sophos UTM on AWS Overview and Deployment Guide Document date: November 2014 1 Sophos UTM and AWS Contents 1 Amazon Web Services... 4 1.1 AMI (Amazon Machine Image)... 4 1.2
Managing a FortiSwitch unit with a FortiGate Administration Guide
 Managing a FortiSwitch unit with a FortiGate Administration Guide Managing a FortiSwitch unit with a FortiGate April 30, 2014. Copyright 2014 Fortinet, Inc. All rights reserved. Fortinet, FortiGate, FortiCare
Managing a FortiSwitch unit with a FortiGate Administration Guide Managing a FortiSwitch unit with a FortiGate April 30, 2014. Copyright 2014 Fortinet, Inc. All rights reserved. Fortinet, FortiGate, FortiCare
The Fortinet Secure Health Architecture
 The Fortinet Secure Health Architecture Providing Next Generation Secure Healthcare for The Healthcare Industry Authored by: Mark Hanson U.S. Director Fortinet, Inc. - Healthcare Introduction Healthcare
The Fortinet Secure Health Architecture Providing Next Generation Secure Healthcare for The Healthcare Industry Authored by: Mark Hanson U.S. Director Fortinet, Inc. - Healthcare Introduction Healthcare
Configuring PA Firewalls for a Layer 3 Deployment
 Configuring PA Firewalls for a Layer 3 Deployment Configuring PAN Firewalls for a Layer 3 Deployment Configuration Guide January 2009 Introduction The following document provides detailed step-by-step
Configuring PA Firewalls for a Layer 3 Deployment Configuring PAN Firewalls for a Layer 3 Deployment Configuration Guide January 2009 Introduction The following document provides detailed step-by-step
Mobile Configuration Profiles for ios Devices Technical Note
 Mobile Configuration Profiles for ios Devices Technical Note Mobile Configuration Profiles for ios Devices Technical Note December 10, 2013 04-502-197517-20131210 Copyright 2013 Fortinet, Inc. All rights
Mobile Configuration Profiles for ios Devices Technical Note Mobile Configuration Profiles for ios Devices Technical Note December 10, 2013 04-502-197517-20131210 Copyright 2013 Fortinet, Inc. All rights
FortiGate Multi-Threat Security Systems I Administration, Content Inspection and SSL VPN Course #201
 FortiGate Multi-Threat Security Systems I Administration, Content Inspection and SSL VPN Course #201 Course Overview Through this 2-day instructor-led classroom or online virtual training, participants
FortiGate Multi-Threat Security Systems I Administration, Content Inspection and SSL VPN Course #201 Course Overview Through this 2-day instructor-led classroom or online virtual training, participants
Appliance Comparison Chart
 Security Gateway Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark - version R77 and later) Security 2 2 230 405 673 Firewall (Gbps).4.4 2.2 3.4
Security Gateway Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark - version R77 and later) Security 2 2 230 405 673 Firewall (Gbps).4.4 2.2 3.4
Sizing Guideline. Sophos UTM 9.2 - SG Series Appliances. Sophos UTM 9.2 Sizing Guide for SG Series appliances
 Sizing Guideline Sophos UTM 9.2 - SG Series Appliances Three steps to specifying the right appliance model This document provides a guideline for choosing the right Sophos SG Series appliance for your
Sizing Guideline Sophos UTM 9.2 - SG Series Appliances Three steps to specifying the right appliance model This document provides a guideline for choosing the right Sophos SG Series appliance for your
NETASQ MIGRATING FROM V8 TO V9
 UTM Firewall version 9 NETASQ MIGRATING FROM V8 TO V9 Document version: 1.1 Reference: naentno_migration-v8-to-v9 INTRODUCTION 3 Upgrading on a production site... 3 Compatibility... 3 Requirements... 4
UTM Firewall version 9 NETASQ MIGRATING FROM V8 TO V9 Document version: 1.1 Reference: naentno_migration-v8-to-v9 INTRODUCTION 3 Upgrading on a production site... 3 Compatibility... 3 Requirements... 4
Sizing Guideline. Sophos UTM 9.1
 Sizing Guideline Sophos UTM 9.1 Three steps to specifying the right appliance model This document provides a guideline for choosing the right Sophos UTM appliance for your customer. Specifying the right
Sizing Guideline Sophos UTM 9.1 Three steps to specifying the right appliance model This document provides a guideline for choosing the right Sophos UTM appliance for your customer. Specifying the right
Appliance Comparison Chart
 202 Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark) Security 4 4 223 374 623 Firewall (Gbps).4.4 2.2 3.4 5.8 Firewall and IPS (Mbps) 50 50
202 Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark) Security 4 4 223 374 623 Firewall (Gbps).4.4 2.2 3.4 5.8 Firewall and IPS (Mbps) 50 50
FortiGate -3040B/3140B 10-GbE Consolidated Security Appliances
 DATASHEET FortiGate -3040B/3140B 10-GbE Consolidated Security Appliances FortiGate-3040B and FortiGate-3140B consolidated security appliances offer exceptional levels of performance, deployment flexibility,
DATASHEET FortiGate -3040B/3140B 10-GbE Consolidated Security Appliances FortiGate-3040B and FortiGate-3140B consolidated security appliances offer exceptional levels of performance, deployment flexibility,
FortiGate -3700D High Performance Data Center Firewall
 FortiGate -3700D High Performance Data Center Firewall Data centers, cloud providers, carriers and service providers need a high-speed, high-capacity firewall to stay ahead of ever-increasing network performance
FortiGate -3700D High Performance Data Center Firewall Data centers, cloud providers, carriers and service providers need a high-speed, high-capacity firewall to stay ahead of ever-increasing network performance
Scalable. Reliable. Flexible. High Performance Architecture. Fault Tolerant System Design. Expansion Options for Unique Business Needs
 Protecting the Data That Drives Business SecureSphere Appliances Scalable. Reliable. Flexible. Imperva SecureSphere appliances provide superior performance and resiliency for demanding network environments.
Protecting the Data That Drives Business SecureSphere Appliances Scalable. Reliable. Flexible. Imperva SecureSphere appliances provide superior performance and resiliency for demanding network environments.
Chapter 9 Firewalls and Intrusion Prevention Systems
 Chapter 9 Firewalls and Intrusion Prevention Systems connectivity is essential However it creates a threat Effective means of protecting LANs Inserted between the premises network and the to establish
Chapter 9 Firewalls and Intrusion Prevention Systems connectivity is essential However it creates a threat Effective means of protecting LANs Inserted between the premises network and the to establish
Appliance Comparison Chart
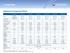 Appliance Comparison Chart Models Edge 10 270 570 1070 2070 070 Edge X, Edge W, Edge X ADSL, Edge W ADSL 12 16 272 276 572 576 107 1076 207 2076 07 076 Software Edition Embedded NGX R65, R70 R65, R70 R65,
Appliance Comparison Chart Models Edge 10 270 570 1070 2070 070 Edge X, Edge W, Edge X ADSL, Edge W ADSL 12 16 272 276 572 576 107 1076 207 2076 07 076 Software Edition Embedded NGX R65, R70 R65, R70 R65,
Emerson Smart Firewall
 DeltaV TM Distributed Control System Product Data Sheet Emerson Smart Firewall The Emerson Smart Firewall protects the DeltaV system with an easy to use perimeter defense solution. Purpose built for easy
DeltaV TM Distributed Control System Product Data Sheet Emerson Smart Firewall The Emerson Smart Firewall protects the DeltaV system with an easy to use perimeter defense solution. Purpose built for easy
Fortinet Network Security NSE4 test questions and answers:http://www.it-tests.com/NSE4.html
 IT-TESTs.com IT Certification Guaranteed, The Easy Way! \ http://www.it-tests.com We offer free update service for one year Exam : NSE4 Title : Fortinet Network Security Expert 4 Written Exam (400) Vendor
IT-TESTs.com IT Certification Guaranteed, The Easy Way! \ http://www.it-tests.com We offer free update service for one year Exam : NSE4 Title : Fortinet Network Security Expert 4 Written Exam (400) Vendor
Load Balance Router R258V
 Load Balance Router R258V Specification Hardware Interface WAN - 5 * 10/100M bps Ethernet LAN - 8 * 10/100M bps Switch Reset Switch LED Indicator Power - Push to load factory default value or back to latest
Load Balance Router R258V Specification Hardware Interface WAN - 5 * 10/100M bps Ethernet LAN - 8 * 10/100M bps Switch Reset Switch LED Indicator Power - Push to load factory default value or back to latest
Cisco Small Business ISA500 Series Integrated Security Appliances
 Q & A Cisco Small Business ISA500 Series Integrated Security Appliances Q. What is the Cisco Small Business ISA500 Series Integrated Security Appliance? A. The Cisco Small Business ISA500 Series Integrated
Q & A Cisco Small Business ISA500 Series Integrated Security Appliances Q. What is the Cisco Small Business ISA500 Series Integrated Security Appliance? A. The Cisco Small Business ISA500 Series Integrated
Check Point 2200 Appliance
 Datasheet: Check Point 2200 Appliance 2200 Branch & Small Office Solution Enterprise security in a desktop package Check Point 2200 Appliance Today the Internet gateway is more than a firewall. It is a
Datasheet: Check Point 2200 Appliance 2200 Branch & Small Office Solution Enterprise security in a desktop package Check Point 2200 Appliance Today the Internet gateway is more than a firewall. It is a
Solution Brief FortiMail for Service Providers. Nathalie Rivat
 Solution Brief FortiMail for Service Providers Nathalie Rivat Agenda FortiMail for Internet Service Providers Outbound antispam to prevent blacklisting MMS routing for Mobile Operators Inbound antispam
Solution Brief FortiMail for Service Providers Nathalie Rivat Agenda FortiMail for Internet Service Providers Outbound antispam to prevent blacklisting MMS routing for Mobile Operators Inbound antispam
FortiOS Handbook - FortiView VERSION 5.2.3
 FortiOS Handbook - FortiView VERSION 5.2.3 FORTINET DOCUMENT LIBRARY http://docs.fortinet.com FORTINET VIDEO GUIDE http://video.fortinet.com FORTINET BLOG https://blog.fortinet.com CUSTOMER SERVICE & SUPPORT
FortiOS Handbook - FortiView VERSION 5.2.3 FORTINET DOCUMENT LIBRARY http://docs.fortinet.com FORTINET VIDEO GUIDE http://video.fortinet.com FORTINET BLOG https://blog.fortinet.com CUSTOMER SERVICE & SUPPORT
IREBOX X. Firebox X Family of Security Products. Comprehensive Unified Threat Management Solutions That Scale With Your Business
 IREBOX X IREBOX X Firebox X Family of Security Products Comprehensive Unified Threat Management Solutions That Scale With Your Business Family of Security Products Comprehensive unified threat management
IREBOX X IREBOX X Firebox X Family of Security Products Comprehensive Unified Threat Management Solutions That Scale With Your Business Family of Security Products Comprehensive unified threat management
Network Security Market in India CY 2014
 Network Security Market in India CY 2014 Advanced, Sophisticated, and Targeted Attacks Lead to High Adoption of Network Security Solutions July 2015 Contents Section Slide Number Executive Summary 3 Market
Network Security Market in India CY 2014 Advanced, Sophisticated, and Targeted Attacks Lead to High Adoption of Network Security Solutions July 2015 Contents Section Slide Number Executive Summary 3 Market
Classic IOS Firewall using CBACs. 2012 Cisco and/or its affiliates. All rights reserved. 1
 Classic IOS Firewall using CBACs 2012 Cisco and/or its affiliates. All rights reserved. 1 Although CBAC serves as a good foundation for understanding the revolutionary path toward modern zone based firewalls,
Classic IOS Firewall using CBACs 2012 Cisco and/or its affiliates. All rights reserved. 1 Although CBAC serves as a good foundation for understanding the revolutionary path toward modern zone based firewalls,
White Paper. Accelerating VMware vsphere Replication with Silver Peak
 Accelerating VMware vsphere Replication with Silver Peak Accelerating VMware vsphere Replication with Silver Peak Contents Overview...3 The Challenge of Replicating Over Distance...3 VMware vsphere Replication
Accelerating VMware vsphere Replication with Silver Peak Accelerating VMware vsphere Replication with Silver Peak Contents Overview...3 The Challenge of Replicating Over Distance...3 VMware vsphere Replication
FortiGate 1500D. The Fortinet Enterprise Firewall Solution. One Enterprise Firewall Solution across the Extended Enterprise. Highlights. forti.
 DATA SHEET FortiGate 1500D Next Generation Firewall Internal Segmentation Firewall Data Center Firewall FortiGate 1500D FortiGate 1500D, 1500D-DC and 1500DT The Fortinet Enterprise Firewall Solution The
DATA SHEET FortiGate 1500D Next Generation Firewall Internal Segmentation Firewall Data Center Firewall FortiGate 1500D FortiGate 1500D, 1500D-DC and 1500DT The Fortinet Enterprise Firewall Solution The
Preventing credit card numbers from escaping your network
 Preventing credit card numbers from escaping your network The following recipe describes how to configure your FortiGate to use DLP (Data Loss Prevention) so that credit card numbers cannot be sent out
Preventing credit card numbers from escaping your network The following recipe describes how to configure your FortiGate to use DLP (Data Loss Prevention) so that credit card numbers cannot be sent out
Virtual Private Networks Secured Connectivity for the Distributed Organization
 Virtual Private Networks Secured Connectivity for the Distributed Organization FORTINET VIRTUAL PRIVATE NETWORKS PAGE 2 Introduction A Virtual Private Network (VPN) allows organizations to securely connect
Virtual Private Networks Secured Connectivity for the Distributed Organization FORTINET VIRTUAL PRIVATE NETWORKS PAGE 2 Introduction A Virtual Private Network (VPN) allows organizations to securely connect
The All-in-one Guest Access Solution of
 The All-in-one Guest Access Solution of Redefining Networking Integration Tomorrow, Delivered Today Application Guide Series Series Application Guide Providing access in hospitality venues is not the same
The All-in-one Guest Access Solution of Redefining Networking Integration Tomorrow, Delivered Today Application Guide Series Series Application Guide Providing access in hospitality venues is not the same
Cisco PIX vs. Checkpoint Firewall
 Cisco PIX vs. Checkpoint Firewall Introduction Firewall technology ranges from packet filtering to application-layer proxies, to Stateful inspection; each technique gleaning the benefits from its predecessor.
Cisco PIX vs. Checkpoint Firewall Introduction Firewall technology ranges from packet filtering to application-layer proxies, to Stateful inspection; each technique gleaning the benefits from its predecessor.
Table of Contents. 1 Overview 1-1 Introduction 1-1 Product Design 1-1 Appearance 1-2
 Table of Contents 1 Overview 1-1 Introduction 1-1 Product Design 1-1 Appearance 1-2 2 Features and Benefits 2-1 Key Features 2-1 Support for the Browser/Server Resource Access Model 2-1 Support for Client/Server
Table of Contents 1 Overview 1-1 Introduction 1-1 Product Design 1-1 Appearance 1-2 2 Features and Benefits 2-1 Key Features 2-1 Support for the Browser/Server Resource Access Model 2-1 Support for Client/Server
Network Security. Protective and Dependable. 52 Network Security. UTM Content Security Gateway CS-2000
 Network Security Protective and Dependable With the growth of the Internet threats, network security becomes the fundamental concerns of family network and enterprise network. To enhance your business
Network Security Protective and Dependable With the growth of the Internet threats, network security becomes the fundamental concerns of family network and enterprise network. To enhance your business
Protecting the Infrastructure: Symantec Web Gateway
 Protecting the Infrastructure: Symantec Web Gateway 1 Why Symantec for Web Security? Flexibility and Choice Best in class hosted service, appliance, and virtual appliance (upcoming) deployment options
Protecting the Infrastructure: Symantec Web Gateway 1 Why Symantec for Web Security? Flexibility and Choice Best in class hosted service, appliance, and virtual appliance (upcoming) deployment options
FortiClient 5.2.3 Administration Guide
 FortiClient 5.2.3 Administration Guide FortiClient 5.2.3 Administration Guide January 29, 2015 04-523-225910-20150129 Copyright 2015 Fortinet, Inc. All rights reserved. Fortinet, FortiGate, FortiCare and
FortiClient 5.2.3 Administration Guide FortiClient 5.2.3 Administration Guide January 29, 2015 04-523-225910-20150129 Copyright 2015 Fortinet, Inc. All rights reserved. Fortinet, FortiGate, FortiCare and
User Manual. Page 2 of 38
 DSL1215FUN(L) Page 2 of 38 Contents About the Device...4 Minimum System Requirements...5 Package Contents...5 Device Overview...6 Front Panel...6 Side Panel...6 Back Panel...7 Hardware Setup Diagram...8
DSL1215FUN(L) Page 2 of 38 Contents About the Device...4 Minimum System Requirements...5 Package Contents...5 Device Overview...6 Front Panel...6 Side Panel...6 Back Panel...7 Hardware Setup Diagram...8
FortiGate 3700D. The Fortinet Enterprise Firewall Solution. One Enterprise Firewall Solution across the Extended Enterprise. Highlights. forti.
 DATA SHEET FortiGate 700D Next Generation Firewall Internal Segmentation Firewall Data Center Firewall Carrier-Class Firewall FortiGate 700D FortiGate 700D, 700D-NEBS, 700D-DC and 700D-DC-NEBS The Fortinet
DATA SHEET FortiGate 700D Next Generation Firewall Internal Segmentation Firewall Data Center Firewall Carrier-Class Firewall FortiGate 700D FortiGate 700D, 700D-NEBS, 700D-DC and 700D-DC-NEBS The Fortinet
74% 96 Action Items. Compliance
 Compliance Report PCI DSS 2.0 Generated by Check Point Compliance Blade, on July 02, 2013 11:12 AM 1 74% Compliance 96 Action Items Upcoming 0 items About PCI DSS 2.0 PCI-DSS is a legal obligation mandated
Compliance Report PCI DSS 2.0 Generated by Check Point Compliance Blade, on July 02, 2013 11:12 AM 1 74% Compliance 96 Action Items Upcoming 0 items About PCI DSS 2.0 PCI-DSS is a legal obligation mandated
SonicWALL Team Nordic Recommendations for safe Unified Threat Management (UTM) Deployments*
 SonicWALL Team Nordic Recommendations for safe Unified Threat Management () Deployments* [email protected] tel: +46 8 410 71 700 TZ100/100W 01-SSC-8739 01-SSC-8739 01-SSC-8723 $470/$536W 128Mb RAM 5FE
SonicWALL Team Nordic Recommendations for safe Unified Threat Management () Deployments* [email protected] tel: +46 8 410 71 700 TZ100/100W 01-SSC-8739 01-SSC-8739 01-SSC-8723 $470/$536W 128Mb RAM 5FE
Please report errors or omissions in this or any Fortinet technical document to [email protected].
 The FortiGate Cookbook 5.0.7 (Expanded Version) Essential Recipes for Success with your FortiGate April 23, 2014 Copyright 2014 Fortinet, Inc. All rights reserved. Fortinet, FortiGate, FortiCare and FortiGuard,
The FortiGate Cookbook 5.0.7 (Expanded Version) Essential Recipes for Success with your FortiGate April 23, 2014 Copyright 2014 Fortinet, Inc. All rights reserved. Fortinet, FortiGate, FortiCare and FortiGuard,
Considerations In Developing Firewall Selection Criteria. Adeptech Systems, Inc.
 Considerations In Developing Firewall Selection Criteria Adeptech Systems, Inc. Table of Contents Introduction... 1 Firewall s Function...1 Firewall Selection Considerations... 1 Firewall Types... 2 Packet
Considerations In Developing Firewall Selection Criteria Adeptech Systems, Inc. Table of Contents Introduction... 1 Firewall s Function...1 Firewall Selection Considerations... 1 Firewall Types... 2 Packet
