SIM, USIM/CSIM and ISIM Overview. James Ni 04/22/2013
|
|
|
- Brenda Rodgers
- 7 years ago
- Views:
Transcription
1 SIM, USIM/CSIM and ISIM Overview James Ni 04/22/2013 1
2 SIM Subscriber Identification Module (SIM) An integrated circuit that securely stores the international mobile subscriber identity (IMSI) and the related key used to identify and authenticate subscribers on mobile telephony devices Initially introduced in GSM (TS 11.11) Key Information Stored in SIM unique serial number (ICCID) up to 20 digits international mobile subscriber identity (IMSI) MCC + MNC + MSIN security authentication and ciphering information Authentication Key (Ki) bit unique key for each SIM, also stored in AuC/HSS temporary information related to the local network Local Area Identity (LAI) received from local carrier a list of the services the user has access to Operator-Specific Emergency Number SMSC (Short Message Service Center) number Service Provider Name (SPN) Service Dialing Numbers (SDN) Advice-Of-Charge parameters Value Added Service (VAS) applications two passwords: a personal identification number (PIN) for ordinary use and a personal unblocking code (PUK) for PIN unlocking 2
3 UMTS SIM Similar to GSM SIM USIM More capabilities allowing 3G UMTS services Stronger Authentication and Security capabilities Larger and securer phone book Key information stored similar to GSM SIM Additional information to support UMTS services 3
4 CSIM CDMA SIM Similar to GSM SIM runs on a UICC file structure derived from the R-UIM card For cdmaone/cdma2000 Key parameters Identifications MIN+ESN prior to introduction of IMSI, MIN for identifying the subscriber and MIN+ESN for registration and authentication IMSI (international mobile subscriber identifier). TMSI (temporary mobile subscriber identifier, for position security). UIMID (hardware identifier) - a pseudo value if EUIMID is in use. EUIMID Either short form (based on MEID) or long form (based on ICCID). ICCID Present even if it is not used as EUIMID MEID (hardware identifier). Encryption keys Phone Number List of services available Call Control SMS BCMCS Broadcast IP Location CDMA2000 Parameters Stats Misc. 4
5 ISIM IP Multimedia Service Identity Module (IMS SIM) An application residing on the UICC Contains parameters for identifying and authenticating the user to IMS ISIM can co-exist with (U)SIM and/or CSIM on the same UICC ISIM Application Dedicated File (ADF) Contains multiple Elementary Files (EFs) IST (ISIM Service Table): Lists available optional services: P-CSCF address Generic Bootstrapping Architecture (GBA), HTTP Digest GBA-based Local Key Establishment Mechanism, Support of P-CSCF discovery for IMS local break out DOMAIN (Home Network Domain Name) For 3GPP systems without ISMI, UE derives DOMAIN from IMSI IMPI (IMS Private User Identity) Every IMS user has one or more IMPIs assigned by the home network operator Used for Registration, Authorization, Administration and Accounting purposes an ISIM stores ONE IMPI not modifiable on UE Identifies the subscription, NOT the user Is used to identify the user s information (e.g. authentication info) stored in HSS (e.g. for Registration) HSS needs to store the IMPI S-CSCF needs to obtain and store the IMPI upon registration For 3GPP systems without ISIM, IMPI can be derived from IMSI 5
6 ISIM ISIM Application Dedicated File (ADF) Contains multiple Elementary Files (EFs) IMPU (IMS Public User Identity one or more) Every IMS user has one or more IMPUs IMPUs are used by users for requesting communications to other users IMPU takes the form of either SIP URI (RFC 3261): or TEL URI (RFC 3966): tel:<e.164 number> Both formats can be used to address users At least one IMPU is stored in ISIM cannot be modified on UE An IMPU must be registered (explicitly or implicitly) before use for IMS procedures Implicit registration allows registering a user with multiple IMPUs through one registration IMPUs are not authenticated during registration IMPUs MAY be used to identify the user s information in HSS (for mobile terminated sessions) Alias IMPUs can be grouped and used to identify the same user - stored in HSS IMPUs MAY be shared across multiple IMPIs within the same IMS subscription For 3GPP systems without ISIM, Temporary IMPU is derived from the IMSI AD (Administrative Data): UE operation mode normal or type approval) ARR (Access Rule Reference): access rules for files located under the ISIM ADF P-CSCF: P-CSCF Address (one or more) GBABP (GBA Bootstrapping parameters): RAND (AKA Random Challenge Bootstrapping Transaction Identifier (B-TID) associated to a GBA NAF derivation procedure NAFKCA (NAF Key Centre Address one or more) 6
7 MSISDN/MDN and MSRN/TLDN MSISDN/MDN are Public Mobile Telephone Numbers MSISDN: GSM/UMTS Networks MDN: CDMA Networks MSRN/TLDN are mobile routing numbers MSRN: GSM/UMTS Networks Calling party dials MSISDN of the called mobile station HLR maps MSISDN to IMSI VLR maps IMSI to MSRN MSRN is used to route the call to called mobile station TLDN: CDMA Networks Calling party dials MDN of the called mobile station In non-roaming case HLR returns registration status MDN is used to route the call In roaming case Serving MSC/VLR and HLR returns TLDN TLDN is used to route the call 7
8 CAVE Authentication CDMA Authentication HLR/AuC: (SSD RAND, ESN, A-key) SSD SSD RAND, MIN, ESN deliver to Serving MSC and Mobile Mobile Station: (SSD RAND, ESN, A-key) SSD Authentication Global challenge: to all mobile stations using a particular radio channel Unique challenge: to a individual mobile station Done at location updates time or service originating time Authentication results are compared at Either the serving MSC (when SSD is shared) Or the HLR/AuC (when SSD is not shared) 8
9 AKA Authentication IMS Authentication HSS: Generates and passes (RAND, AUTN, XRES, CK, IK) to S-CSCF via MAA S-CSCF: Relays (RAND, AUTN, CK, IK) to P-CSCF via 401(REGISTER), keeps XRES P-CSCF: Relays (RAND, AUTN) to Mobile Station via 401(REGISTER) Mobile Station: Calculates RES and send with REGISTER to IMS core S-CSCF: Compare RES and XRES to complete the authentication Notes: Random number (RAND) Authentication token (AUTN) Signed/expected result (XRES) Cipher key (CK) Integrity Key (IK) Result (RES) 9
10 IMS Registration(TS ) What are registered? Public User Identity: It shall be possible to register multiple public identities via single IMS registration It shall be possible to register a Public User Identity that is simultaneously shared across multiple contact addresses Registration of a Public User Identity shall not affect the status of already registered Public User Identity(s) When multiple UEs share the same public identity(s), each UE shall be able to register its contact address(es) with IMS. Private User Identity Home network domain name UE IP address Instance Identifier GRUU Support Indication 10
11 IMS Registration(TS ) What is sent from S-CSCF to HSS Public User Identity Private User Identity S-CSCF name What is passed on from HSS to S-CSCF one or more names/addresses information which can be used to access the platform(s) used for service control while the user is registered at this S-CSCF. the names/addresses information, security information. etc. 11
12 MDN/MSISDN+IMSI as Temporary IMPU When ISIM is not available (for legacy non-ims access devices) IMSI + MDN/MSISDN is used as temporary IMPU for registration and authentication This is only for early IMS deployment and can only be a temporary solution The definition of IMPU can be carrier specific, MDN can be used in either one of the following IMPU format sip:mdn@network-domain tel: MDN 12
ETSI TS 131 103 V10.1.0 (2011-04) Technical Specification
 TS 131 103 V10.1.0 (2011-04) Technical Specification Digital cellular telecommunications system (Phase 2+); Universal Mobile Telecommunications System (UMTS); LTE; Characteristics of the IP Multimedia
TS 131 103 V10.1.0 (2011-04) Technical Specification Digital cellular telecommunications system (Phase 2+); Universal Mobile Telecommunications System (UMTS); LTE; Characteristics of the IP Multimedia
SIMalliance LTE UICC profile. This document is a collection of requirements for optimal support of LTE/EPS networks by UICC
 SIMalliance LTE UICC profile This document is a collection of requirements for optimal support of LTE/EPS networks by UICC Secure element architects for today s generation SIMalliance LTE UICC profile
SIMalliance LTE UICC profile This document is a collection of requirements for optimal support of LTE/EPS networks by UICC Secure element architects for today s generation SIMalliance LTE UICC profile
Operator-based Over-the-air M2M Wireless Sensor Network Security
 Operator-based Over-the-air M2M Wireless Sensor Network Security Sachin Agarwal Christoph Peylo Deutsche Telekom A.G., Laboratories Ernst-Reuter-Platz 7 10587 Berlin DE Email: {sachin.agarwal, christoph.peylo}@telekom.de
Operator-based Over-the-air M2M Wireless Sensor Network Security Sachin Agarwal Christoph Peylo Deutsche Telekom A.G., Laboratories Ernst-Reuter-Platz 7 10587 Berlin DE Email: {sachin.agarwal, christoph.peylo}@telekom.de
Global System for Mobile Communication Technology
 Global System for Mobile Communication Technology Mobile Device Investigations Program Technical Operations Division DHS - FLETC GSM Technology Global System for Mobile Communication or Groupe Special
Global System for Mobile Communication Technology Mobile Device Investigations Program Technical Operations Division DHS - FLETC GSM Technology Global System for Mobile Communication or Groupe Special
CIBER Records,MEID and EUIMID
 CIBER Records,MEID and EUIMID CDG International Roaming Team (IRT) Plenary Montego Bay, Jamaica 27-29 November, 2007 (r2 December, 2007) Bill Dahnke* David Crowe meid@cdg.org * On loan from Qualcomm to
CIBER Records,MEID and EUIMID CDG International Roaming Team (IRT) Plenary Montego Bay, Jamaica 27-29 November, 2007 (r2 December, 2007) Bill Dahnke* David Crowe meid@cdg.org * On loan from Qualcomm to
3GPP TS 33.220 V6.13.0 (2007-06)
 TS 33.220 V6.13.0 (2007-06) Technical Specification The present document has been developed within the 3 rd Generation Partnership Project ( TM ) and may be further elaborated for the purposes of. The
TS 33.220 V6.13.0 (2007-06) Technical Specification The present document has been developed within the 3 rd Generation Partnership Project ( TM ) and may be further elaborated for the purposes of. The
UMTS security. Helsinki University of Technology S-38.153 Security of Communication Protocols k-p.perttula@hut.fi 15.4.2003
 UMTS security Helsinki University of Technology S-38.153 Security of Communication Protocols k-p.perttula@hut.fi 15.4.2003 Contents UMTS Security objectives Problems with GSM security UMTS security mechanisms
UMTS security Helsinki University of Technology S-38.153 Security of Communication Protocols k-p.perttula@hut.fi 15.4.2003 Contents UMTS Security objectives Problems with GSM security UMTS security mechanisms
Mobile Services (ST 2010)
 Mobile Services (ST 2010) Chapter 3: Mobility Management Axel Küpper Service-centric Networking Deutsche Telekom Laboratories, TU Berlin 1 Mobile Services Summer Term 2010 3 Mobility Management 3.1 Handover
Mobile Services (ST 2010) Chapter 3: Mobility Management Axel Küpper Service-centric Networking Deutsche Telekom Laboratories, TU Berlin 1 Mobile Services Summer Term 2010 3 Mobility Management 3.1 Handover
9.1 Introduction. 9.2 Roaming
 9 Location Updating Objectives After this chapter the student will: be able to define the concepts of roaming and location updating. be able to name the different types of location updating and why they
9 Location Updating Objectives After this chapter the student will: be able to define the concepts of roaming and location updating. be able to name the different types of location updating and why they
1 Introduction. 2 Assumptions. Implementing roaming for OpenBTS
 Implementing roaming for OpenBTS 1 Introduction One of the main advantages of OpenBTS TM system architecture is absence of a legacy GSM core network. SIP is used for registering, call control and messaging.
Implementing roaming for OpenBTS 1 Introduction One of the main advantages of OpenBTS TM system architecture is absence of a legacy GSM core network. SIP is used for registering, call control and messaging.
ETSI TS 133 203 V5.1.0 (2002-03)
 TS 133 203 V5.1.0 (2002-03) Technical Specification Universal Mobile Telecommunications System (UMTS); 3G security; Access security for IP-based services (3GPP TS 33.203 version 5.1.0 Release 5) 1 TS 133
TS 133 203 V5.1.0 (2002-03) Technical Specification Universal Mobile Telecommunications System (UMTS); 3G security; Access security for IP-based services (3GPP TS 33.203 version 5.1.0 Release 5) 1 TS 133
3GPP TSG SA WG3 Security S3#20 S3-010580 27-30 November, 2001 Sophia Antipolis, France
 TSG SA WG3 Security S3#20 S3-010580 27-30 November, 2001 Sophia Antipolis, France Source : Subject : Gemplus ISIM Application The following document is a draft TS describing the ISIM characteristics. It
TSG SA WG3 Security S3#20 S3-010580 27-30 November, 2001 Sophia Antipolis, France Source : Subject : Gemplus ISIM Application The following document is a draft TS describing the ISIM characteristics. It
3GPP TSG CN Plenary Meeting #16 5 th - 7 th June 2002. Marco Island, USA. 3GPP TSG-CN1 Meeting #24 Tdoc N1-021455 Budapest, Hungary, 13. 17.
 3GPP TSG CN Plenary Meeting #16 5 th - 7 th June 2002. Marco Island, USA. NP-020155 Title: Liaison Statement on 3GPP Network Domain Name usage for IMS Source: CN1 Agenda item: 5.1 Document for: INFORMATION
3GPP TSG CN Plenary Meeting #16 5 th - 7 th June 2002. Marco Island, USA. NP-020155 Title: Liaison Statement on 3GPP Network Domain Name usage for IMS Source: CN1 Agenda item: 5.1 Document for: INFORMATION
Security and Authentication Concepts
 Security and Authentication Concepts for UMTS/WLAN Convergence F. Fitzek M. Munari V. Pastesini S. Rossi L. Badia Dipartimento di Ingegneria, Università di Ferrara, via Saragat 1, 44100 Ferrara, Italy
Security and Authentication Concepts for UMTS/WLAN Convergence F. Fitzek M. Munari V. Pastesini S. Rossi L. Badia Dipartimento di Ingegneria, Università di Ferrara, via Saragat 1, 44100 Ferrara, Italy
Evolution of the SIM to esim
 Evolution of the SIM to esim Elaheh Vahidian Master of Telematics - Communication Networks and Networked Services (2 Submission date: Januar 2013 Supervisor: Van Thanh Do, ITEM Norwegian University of
Evolution of the SIM to esim Elaheh Vahidian Master of Telematics - Communication Networks and Networked Services (2 Submission date: Januar 2013 Supervisor: Van Thanh Do, ITEM Norwegian University of
3GPP TSG SA WG3 Security S3#25 S3-020572 8-11 October 2002 Munich, Germany
 3GPP TSG SA WG3 Security S3#25 S3-020572 8-11 October 2002 Munich, Germany Title: Response to: Source: To: Cc: Liaison on HTTP Security investigation within IMS LS S3-020475 (S2-022609) on Liaison on Security
3GPP TSG SA WG3 Security S3#25 S3-020572 8-11 October 2002 Munich, Germany Title: Response to: Source: To: Cc: Liaison on HTTP Security investigation within IMS LS S3-020475 (S2-022609) on Liaison on Security
Global System for Mobile Communications (GSM)
 Global System for Mobile Communications (GSM) Nguyen Thi Mai Trang LIP6/PHARE Thi-Mai-Trang.Nguyen@lip6.fr UPMC/PUF - M2 Networks - PTEL 1 Outline Principles of cellular networks GSM architecture Security
Global System for Mobile Communications (GSM) Nguyen Thi Mai Trang LIP6/PHARE Thi-Mai-Trang.Nguyen@lip6.fr UPMC/PUF - M2 Networks - PTEL 1 Outline Principles of cellular networks GSM architecture Security
Theory and Practice. IT-Security: GSM Location System Syslog XP 3.7. Mobile Communication. December 18, 2001. GSM Location System Syslog XP 3.
 Participant: Hack contacting... IT-Security: Theory and Practice Mobile Communication December 18, 2001 Uwe Jendricke uwe@iig.uni-freiburg.de Lecture Homepage: http://www.informatik.uni-freiburg.de/~softech/teaching/ws01/itsec/
Participant: Hack contacting... IT-Security: Theory and Practice Mobile Communication December 18, 2001 Uwe Jendricke uwe@iig.uni-freiburg.de Lecture Homepage: http://www.informatik.uni-freiburg.de/~softech/teaching/ws01/itsec/
Delivery of Voice and Text Messages over LTE
 Delivery of Voice and Text Messages over LTE 1. The Market for Voice and SMS! 2. Third Party Voice over IP! 3. The IP Multimedia Subsystem! 4. Circuit Switched Fallback! 5. VoLGA LTE was designed as a
Delivery of Voice and Text Messages over LTE 1. The Market for Voice and SMS! 2. Third Party Voice over IP! 3. The IP Multimedia Subsystem! 4. Circuit Switched Fallback! 5. VoLGA LTE was designed as a
Authentication and Secure Communication in GSM, GPRS, and UMTS Using Asymmetric Cryptography
 ISSN (Online): 1694-0784 ISSN (Print): 1694-0814 10 Authentication and Secure Communication in GSM, GPRS, and UMTS Using Asymmetric Cryptography Wilayat Khan 1 and Habib Ullah 2 1 Department of Electrical
ISSN (Online): 1694-0784 ISSN (Print): 1694-0814 10 Authentication and Secure Communication in GSM, GPRS, and UMTS Using Asymmetric Cryptography Wilayat Khan 1 and Habib Ullah 2 1 Department of Electrical
ARIB TR-T12-33.919 V7.2.0. 3G Security; Generic Authentication Architecture (GAA); System Description (Release 7)
 ARIB TR-T12-33.919 V7.2.0 3G Security; Generic Authentication Architecture (GAA); System Description (Release 7) Refer to Notice in the preface of ARIB TR-T12 for Copyrights. TR 33.919 V7.2.0 (2007-03)
ARIB TR-T12-33.919 V7.2.0 3G Security; Generic Authentication Architecture (GAA); System Description (Release 7) Refer to Notice in the preface of ARIB TR-T12 for Copyrights. TR 33.919 V7.2.0 (2007-03)
GAA/GBA: a new Architecture for single sign-on
 GAA/GBA: a new Architecture for single sign-on 2nd ETSI Security Workshop: Future Security 16-17 January 2007 Sophia- Antipolis (France) SER MÁS LÍDERES Wednesday, 17th January 2007 luisangel.galindosanchez@telefonica.es
GAA/GBA: a new Architecture for single sign-on 2nd ETSI Security Workshop: Future Security 16-17 January 2007 Sophia- Antipolis (France) SER MÁS LÍDERES Wednesday, 17th January 2007 luisangel.galindosanchez@telefonica.es
3GPP TR 33.804 V11.1.0 (2012-06)
 TR 33.804 V11.1.0 (2012-06) Technical Report 3rd Generation Partnership Project; Technical Specification Group Services and System Aspects; Single Sign On (SSO) application security for Common IP Multimedia
TR 33.804 V11.1.0 (2012-06) Technical Report 3rd Generation Partnership Project; Technical Specification Group Services and System Aspects; Single Sign On (SSO) application security for Common IP Multimedia
ETSI TS 184 002 V1.1.1 (2006-10)
 TS 184 002 V1.1.1 (2006-10) Technical Specification Telecommunications and Internet converged Services and Protocols for Advanced Networking (TISPAN); Identifiers (IDs) for NGN 2 TS 184 002 V1.1.1 (2006-10)
TS 184 002 V1.1.1 (2006-10) Technical Specification Telecommunications and Internet converged Services and Protocols for Advanced Networking (TISPAN); Identifiers (IDs) for NGN 2 TS 184 002 V1.1.1 (2006-10)
Security considerations for IMS access independence
 3GPP TSG SA WG3 Security S3#20 S3-010468 16-19 October, 2001 Sydney, Australia Source: Title: Document for: Agenda Item: Telia / independence Information Security Security considerations for access independence
3GPP TSG SA WG3 Security S3#20 S3-010468 16-19 October, 2001 Sydney, Australia Source: Title: Document for: Agenda Item: Telia / independence Information Security Security considerations for access independence
3GPP TS 31.103 V5.13.1 (2007-06)
 TS 31.103 V5.13.1 (2007-06) Technical Specification 3rd Generation Partnership Project; Technical Specification Group Core Network and Terminals; Characteristics of the IP Multimedia Services Identity
TS 31.103 V5.13.1 (2007-06) Technical Specification 3rd Generation Partnership Project; Technical Specification Group Core Network and Terminals; Characteristics of the IP Multimedia Services Identity
Voice and SMS in LTE White Paper
 Voice and SMS in LTE White Paper This white paper summarizes the technology options for supporting voice and short message service (SMS) in LTE, including circuit switched fallback (CSFB), SMS over SGs,
Voice and SMS in LTE White Paper This white paper summarizes the technology options for supporting voice and short message service (SMS) in LTE, including circuit switched fallback (CSFB), SMS over SGs,
GSM v. CDMA: Technical Comparison of M2M Technologies
 GSM v. CDMA: Technical Comparison of M2M Technologies Introduction Aeris provides network and data analytics services for Machine-to- Machine ( M2M ) and Internet of Things ( IoT ) applications using multiple
GSM v. CDMA: Technical Comparison of M2M Technologies Introduction Aeris provides network and data analytics services for Machine-to- Machine ( M2M ) and Internet of Things ( IoT ) applications using multiple
GSM Databases. Virginia Location Area HLR Vienna Cell Virginia BSC. Virginia MSC VLR
 Update ( Update Procedure) Network Mobiles Maryland Maryland Other Rockville Bethesda Maryland Mobile Mobile Cell Cell HLR Vienna Cell 12-Jun-14 22:48 (Page 1) This sequence diagram was generated with
Update ( Update Procedure) Network Mobiles Maryland Maryland Other Rockville Bethesda Maryland Mobile Mobile Cell Cell HLR Vienna Cell 12-Jun-14 22:48 (Page 1) This sequence diagram was generated with
GSM and UMTS security
 2007 Levente Buttyán Why is security more of a concern in wireless? no inherent physical protection physical connections between devices are replaced by logical associations sending and receiving messages
2007 Levente Buttyán Why is security more of a concern in wireless? no inherent physical protection physical connections between devices are replaced by logical associations sending and receiving messages
Advanced SIP Series: SIP and 3GPP
 Advanced SIP Series: SIP and 3GPP, Award Solutions, Inc Abstract The Session Initiation Protocol has been selected as the main signaling protocol of the Third Generation Partnership Projects IP Multimedia
Advanced SIP Series: SIP and 3GPP, Award Solutions, Inc Abstract The Session Initiation Protocol has been selected as the main signaling protocol of the Third Generation Partnership Projects IP Multimedia
Convergent data center for future network
 Convergent data center for future network Xia zhen hua (Lawrence Hsia) Huawei Technologies xiazhenhua@huawei.com Abstract In this article, we will analyze current issues and new challenges on user profile,
Convergent data center for future network Xia zhen hua (Lawrence Hsia) Huawei Technologies xiazhenhua@huawei.com Abstract In this article, we will analyze current issues and new challenges on user profile,
LTE Security How Good Is It?
 LTE Security How Good Is It? Michael Bartock IT Specialist (Security) National Institute of Standards & Technology Jeffrey Cichonski IT Specialist (Security) National Institute of Standards & Technology
LTE Security How Good Is It? Michael Bartock IT Specialist (Security) National Institute of Standards & Technology Jeffrey Cichonski IT Specialist (Security) National Institute of Standards & Technology
SOLUTIONS FOR ROAMING AND INTEROPERABILITY PROBLEMS BETWEEN LTE AND 2G OR 3G NETWORKS
 Review of the Air Force Academy No 2 (24) 2013 SOLUTIONS FOR ROAMING AND INTEROPERABILITY PROBLEMS BETWEEN LTE AND 2G OR 3G NETWORKS Radu CURPEN, Florin SANDU, Cosmin COSTACHE, Gabriel Mihail DANCIU Transilvania
Review of the Air Force Academy No 2 (24) 2013 SOLUTIONS FOR ROAMING AND INTEROPERABILITY PROBLEMS BETWEEN LTE AND 2G OR 3G NETWORKS Radu CURPEN, Florin SANDU, Cosmin COSTACHE, Gabriel Mihail DANCIU Transilvania
Removable User Identity Module for Spread Spectrum Systems
 GPP C.S00-C Version.0 Date: October, 00 Removable User Identity Module for Spread Spectrum Systems COPYRIGHT GPP and its Organizational Partners claim copyright in this document and individual Organizational
GPP C.S00-C Version.0 Date: October, 00 Removable User Identity Module for Spread Spectrum Systems COPYRIGHT GPP and its Organizational Partners claim copyright in this document and individual Organizational
!!! "# $ % & & # ' (! ) * +, -!!. / " 0! 1 (!!! ' &! & & & ' ( 2 3 0-4 ' 3 ' Giuseppe Bianchi
 !!! "# $ % & & # ' (! ) * +, -!!. / " 0! 1 (!!! ' &! & & & ' ( 2 3 0-4 ' 3 ' "#$!!% "&'! #&'!%! () *+,, 3 & 5 &,! #-!*! ' & '.! #%!* //!! & (0)/!&/, 6 5 /, "! First system: NMT-450 (Nordic Mobile Telephone)
!!! "# $ % & & # ' (! ) * +, -!!. / " 0! 1 (!!! ' &! & & & ' ( 2 3 0-4 ' 3 ' "#$!!% "&'! #&'!%! () *+,, 3 & 5 &,! #-!*! ' & '.! #%!* //!! & (0)/!&/, 6 5 /, "! First system: NMT-450 (Nordic Mobile Telephone)
Ch 2.3.3 GSM PENN. Magda El Zarki - Tcom 510 - Spring 98
 Ch 2.3.3 GSM In the early 80 s the European community decided to work together to define a cellular system that would permit full roaming in all countries and give the network providers freedom to provide
Ch 2.3.3 GSM In the early 80 s the European community decided to work together to define a cellular system that would permit full roaming in all countries and give the network providers freedom to provide
ETSI TS 123 251 V6.5.0 (2005-09)
 TS 123 251 V6.5.0 (2005-09) Technical Specification Universal Mobile Telecommunications System (UMTS); Network sharing; Architecture and functional description (3GPP TS 23.251 version 6.5.0 Release 6)
TS 123 251 V6.5.0 (2005-09) Technical Specification Universal Mobile Telecommunications System (UMTS); Network sharing; Architecture and functional description (3GPP TS 23.251 version 6.5.0 Release 6)
2 System introduction
 2 System introduction Objectives After this chapter the student will: be able to describe the different nodes in a GSM network. be able to describe geographical subdivision of a GSM network. be able to
2 System introduction Objectives After this chapter the student will: be able to describe the different nodes in a GSM network. be able to describe geographical subdivision of a GSM network. be able to
ETSI TR 133 919 V6.1.0 (2004-12)
 TR 133 919 V6.1.0 (2004-12) Technical Report Universal Mobile Telecommunications System (UMTS); Generic Authentication Architecture (GAA); System description (3GPP TR 33.919 version 6.1.0 Release 6) 1
TR 133 919 V6.1.0 (2004-12) Technical Report Universal Mobile Telecommunications System (UMTS); Generic Authentication Architecture (GAA); System description (3GPP TR 33.919 version 6.1.0 Release 6) 1
End-2-End QoS Provisioning in UMTS networks
 End-2-End QoS Provisioning in UMTS networks Haibo Wang Devendra Prasad October 28, 2004 Contents 1 QoS Support from end-to-end viewpoint 3 1.1 UMTS IP Multimedia Subsystem (IMS)................... 3 1.1.1
End-2-End QoS Provisioning in UMTS networks Haibo Wang Devendra Prasad October 28, 2004 Contents 1 QoS Support from end-to-end viewpoint 3 1.1 UMTS IP Multimedia Subsystem (IMS)................... 3 1.1.1
SIM Card Security. Sheng He 108005239797. Seminar Work. Chair for Communication Security Prof. Dr.-Ing. Christof Paar
 SIM Card Security Sheng He 108005239797 Seminar Work at Chair for Communication Security Prof. Dr.-Ing. Christof Paar advised through Thomas Eisenbarth 12.07.2007 Ruhr-University of Bochum Contents 1 Overview...3
SIM Card Security Sheng He 108005239797 Seminar Work at Chair for Communication Security Prof. Dr.-Ing. Christof Paar advised through Thomas Eisenbarth 12.07.2007 Ruhr-University of Bochum Contents 1 Overview...3
SIM/USIM cards. Samia Bouzefrane. samia.bouzefrane@cnam.fr. CEDRIC Lab CNAM http://cedric.cnam.fr/~bouzefra. samia.bouzefrane@cnam.
 SIM/USIM cards Samia Bouzefrane CEDRIC Lab CNAM http://cedric.cnam.fr/~bouzefra 1 Agenda - Introduction to GSM network - Introduction to SIM cards - SIM card services -Security - File systems of SIM cards
SIM/USIM cards Samia Bouzefrane CEDRIC Lab CNAM http://cedric.cnam.fr/~bouzefra 1 Agenda - Introduction to GSM network - Introduction to SIM cards - SIM card services -Security - File systems of SIM cards
PacketCable 2.0. HSS Technical Report PKT-TR-HSS-V01-060914 RELEASED. Notice
 PacketCable 2.0 HSS Technical Report RELEASED Notice This PacketCable technical report is a cooperative effort undertaken at the direction of Cable Television Laboratories, Inc. (CableLabs ) for the benefit
PacketCable 2.0 HSS Technical Report RELEASED Notice This PacketCable technical report is a cooperative effort undertaken at the direction of Cable Television Laboratories, Inc. (CableLabs ) for the benefit
TELECOMMUNICATIONS REGULATORY AUTHORITY BAHRAIN. Bahrain Number Portability Implementation Routing and Charging specification
 TELECOMMUNICATIONS REGULATORY AUTHORITY BAHRAIN Bahrain Number Portability Implementation Routing and Charging specification Version: 0.4 Status: draft Date: 4-0-00 Modification History Issue Date Modification
TELECOMMUNICATIONS REGULATORY AUTHORITY BAHRAIN Bahrain Number Portability Implementation Routing and Charging specification Version: 0.4 Status: draft Date: 4-0-00 Modification History Issue Date Modification
The GSM and GPRS network T-110.300/301
 The GSM and GPRS network T-110.300/301 History The successful analog 1:st generation mobile telephone systems proved that there is a market for mobile telephones ARP (AutoRadioPuhelin) in Finland NMT (Nordic
The GSM and GPRS network T-110.300/301 History The successful analog 1:st generation mobile telephone systems proved that there is a market for mobile telephones ARP (AutoRadioPuhelin) in Finland NMT (Nordic
Mobile Office Security Requirements for the Mobile Office
 Mobile Office Security Requirements for the Mobile Office S.Rupp@alcatel.de Alcatel SEL AG 20./21.06.2001 Overview Security Concepts in Mobile Networks Applications in Mobile Networks Mobile Terminal used
Mobile Office Security Requirements for the Mobile Office S.Rupp@alcatel.de Alcatel SEL AG 20./21.06.2001 Overview Security Concepts in Mobile Networks Applications in Mobile Networks Mobile Terminal used
Security Architecture in UMTS Third Generation Cellular Networks Tomás Balderas-Contreras René A. Cumplido-Parra
 Security Architecture in UMTS Third Generation Cellular Networks Tomás Balderas-Contreras René A. Cumplido-Parra Reporte Técnico No. CCC-04-002 27 de febrero de 2004 Coordinación de Ciencias Computacionales
Security Architecture in UMTS Third Generation Cellular Networks Tomás Balderas-Contreras René A. Cumplido-Parra Reporte Técnico No. CCC-04-002 27 de febrero de 2004 Coordinación de Ciencias Computacionales
SIP Roaming Server Product Overview. Mobile Convergence Technology
 SIP Roaming Server Product Overview Mobile Convergence Technology CONNECTING NETW ORKS Roam, Talk and Text (without a Mobile Network) By interworking with existing communications infrastructures, Session
SIP Roaming Server Product Overview Mobile Convergence Technology CONNECTING NETW ORKS Roam, Talk and Text (without a Mobile Network) By interworking with existing communications infrastructures, Session
Security Evaluation of CDMA2000
 Security Evaluation of CDMA2000 L. Ertaul 1, S. Natte 2, and G. Saldamli 3 1 Mathematics and Computer Science, CSU East Bay, Hayward, CA, USA 2 Mathematics and Computer Science, CSU East Bay, Hayward,
Security Evaluation of CDMA2000 L. Ertaul 1, S. Natte 2, and G. Saldamli 3 1 Mathematics and Computer Science, CSU East Bay, Hayward, CA, USA 2 Mathematics and Computer Science, CSU East Bay, Hayward,
Advanced SIP Series: SIP and 3GPP Operations
 Advanced S Series: S and 3GPP Operations, Award Solutions, Inc Abstract The Session Initiation Protocol has been chosen by the 3GPP for establishing multimedia sessions in UMTS Release 5 (R5) networks.
Advanced S Series: S and 3GPP Operations, Award Solutions, Inc Abstract The Session Initiation Protocol has been chosen by the 3GPP for establishing multimedia sessions in UMTS Release 5 (R5) networks.
Mobile Communications
 October 21, 2009 Agenda Topic 2: Case Study: The GSM Network 1 GSM System General Architecture 2 GSM Access network. 3 Traffic Models for the Air interface 4 Models for the BSS design. 5 UMTS and the path
October 21, 2009 Agenda Topic 2: Case Study: The GSM Network 1 GSM System General Architecture 2 GSM Access network. 3 Traffic Models for the Air interface 4 Models for the BSS design. 5 UMTS and the path
EAP-SIM Authentication using Interlink Networks RAD-Series RADIUS Server
 Application Note EAP-SIM Authentication using Interlink Networks RAD-Series RADIUS Server Introduction The demand for wireless LAN (WLAN) access to the public IP network is growing rapidly. It is only
Application Note EAP-SIM Authentication using Interlink Networks RAD-Series RADIUS Server Introduction The demand for wireless LAN (WLAN) access to the public IP network is growing rapidly. It is only
HRPD Support for Emergency Services
 GPP X.S000-0 Version.0 Date: July 00 HRPD Support for Emergency Services COPYRIGHT GPP and its Organizational Partners claim copyright in this document and individual Organizational Partners may copyright
GPP X.S000-0 Version.0 Date: July 00 HRPD Support for Emergency Services COPYRIGHT GPP and its Organizational Partners claim copyright in this document and individual Organizational Partners may copyright
Worldwide attacks on SS7 network
 Worldwide attacks on SS7 network P1 Security Hackito Ergo Sum 26 th April 2014 Pierre-Olivier Vauboin (po@p1sec.com) Alexandre De Oliveira (alex@p1sec.com) Agenda Overall telecom architecture Architecture
Worldwide attacks on SS7 network P1 Security Hackito Ergo Sum 26 th April 2014 Pierre-Olivier Vauboin (po@p1sec.com) Alexandre De Oliveira (alex@p1sec.com) Agenda Overall telecom architecture Architecture
IMSI Catcher. Daehyun Strobel. 13.Juli 2007. Seminararbeit Ruhr-Universität Bochum. Chair for Communication Security Prof. Dr.-Ing.
 IMSI Catcher Daehyun Strobel 13.Juli 2007 Seminararbeit Ruhr-Universität Bochum Chair for Communication Security Prof. Dr.-Ing. Christof Paar Contents 1 Introduction 1 2 GSM (Global System for Mobile
IMSI Catcher Daehyun Strobel 13.Juli 2007 Seminararbeit Ruhr-Universität Bochum Chair for Communication Security Prof. Dr.-Ing. Christof Paar Contents 1 Introduction 1 2 GSM (Global System for Mobile
II. Service deployment
 BULGARIAN ACADEMY OF SCIENCES CYBERNETICS AND INFORMATION TECHNOLOGIES Volume 9, No 3 Sofia 2009 Integration of Services Implemented on Different Service Platforms Evelina Pencheva, Ivaylo Atanasov Technical
BULGARIAN ACADEMY OF SCIENCES CYBERNETICS AND INFORMATION TECHNOLOGIES Volume 9, No 3 Sofia 2009 Integration of Services Implemented on Different Service Platforms Evelina Pencheva, Ivaylo Atanasov Technical
ETSI TS 131 104 V11.1.0 (2012-10)
 TS 131 104 V11.1.0 (2012-10) Technical Specification Universal Mobile Telecommunications System (UMTS); LTE; Characteristics of the Hosting Party Subscription Identity Module (HPSIM) application (3GPP
TS 131 104 V11.1.0 (2012-10) Technical Specification Universal Mobile Telecommunications System (UMTS); LTE; Characteristics of the Hosting Party Subscription Identity Module (HPSIM) application (3GPP
WHITE PAPER. August, 2002. Contacts: Christopher Wingert Mullaguru Naidu
 C D M A 1 X R T T S E C U R I T Y WHITE PAPER O V E R V I E W August, 2002 Contacts: Christopher Wingert Mullaguru Naidu T A B L E O F C O N T E N T S 1. Executive Summary 2 2. Security CDMA Networks 3
C D M A 1 X R T T S E C U R I T Y WHITE PAPER O V E R V I E W August, 2002 Contacts: Christopher Wingert Mullaguru Naidu T A B L E O F C O N T E N T S 1. Executive Summary 2 2. Security CDMA Networks 3
Security features include Authentication and encryption to protect data and prevent eavesdropping.
 What is a SIM card? A SIM card, also known as a subscriber identity module, is a subscriber identity module application on a smartcard that stores data for GSM/CDMA Cellular telephone subscribers. Such
What is a SIM card? A SIM card, also known as a subscriber identity module, is a subscriber identity module application on a smartcard that stores data for GSM/CDMA Cellular telephone subscribers. Such
White Paper ON Dual Mode Phone (GSM & Wi-Fi)
 White Paper ON Dual Mode Phone (GSM & Wi-Fi) Author: N Group 1.0 Abstract Dual Mode Handset is in demand for converged Network, Access, Billing, and Operation environment. Dual mode handsets provide cost
White Paper ON Dual Mode Phone (GSM & Wi-Fi) Author: N Group 1.0 Abstract Dual Mode Handset is in demand for converged Network, Access, Billing, and Operation environment. Dual mode handsets provide cost
ETSI TS 133 102 V3.6.0 (2000-10)
 TS 133 102 V3.6.0 (2000-10) Technical Specification Universal Mobile Telecommunications System (UMTS); 3G Security; Security Architecture (3GPP TS 33.102 version 3.6.0 Release 1999) 1 TS 133 102 V3.6.0
TS 133 102 V3.6.0 (2000-10) Technical Specification Universal Mobile Telecommunications System (UMTS); 3G Security; Security Architecture (3GPP TS 33.102 version 3.6.0 Release 1999) 1 TS 133 102 V3.6.0
White Paper. IMS Architecture. The LTE User Equipment Perspective. www.spirent.com
 White Paper IMS Architecture The LTE User Equipment Perspective www.spirent.com SPIRENT IMS Architecture The LTE User Equipment Perspective TABLE OF CONTENTS 1. Executive Summary 3 2. Introduction 3 3.
White Paper IMS Architecture The LTE User Equipment Perspective www.spirent.com SPIRENT IMS Architecture The LTE User Equipment Perspective TABLE OF CONTENTS 1. Executive Summary 3 2. Introduction 3 3.
Authentication and Security in IP based Multi Hop Networks
 7TH WWRF MEETING IN EINDHOVEN, THE NETHERLANDS 3RD - 4TH DECEMBER 2002 1 Authentication and Security in IP based Multi Hop Networks Frank Fitzek, Andreas Köpsel, Patrick Seeling Abstract Network security
7TH WWRF MEETING IN EINDHOVEN, THE NETHERLANDS 3RD - 4TH DECEMBER 2002 1 Authentication and Security in IP based Multi Hop Networks Frank Fitzek, Andreas Köpsel, Patrick Seeling Abstract Network security
Long-Term Evolution. Mobile Telecommunications Networks WMNet Lab
 Long-Term Evolution Mobile Telecommunications Networks WMNet Lab Background Long-Term Evolution Define a new packet-only wideband radio with flat architecture as part of 3GPP radio technology family 2004:
Long-Term Evolution Mobile Telecommunications Networks WMNet Lab Background Long-Term Evolution Define a new packet-only wideband radio with flat architecture as part of 3GPP radio technology family 2004:
PM ASSIGNMENT. Security in Mobile Telephony and Voice over IP
 PM ASSIGNMENT Security in Mobile Telephony and Voice over IP Christian Wallin Christian.wallin.7513@student.uu.se Danlu Fu danlu.fu.6095@student.uu.se David Alfonso david.alfonso.5823@student.uu.se 1.
PM ASSIGNMENT Security in Mobile Telephony and Voice over IP Christian Wallin Christian.wallin.7513@student.uu.se Danlu Fu danlu.fu.6095@student.uu.se David Alfonso david.alfonso.5823@student.uu.se 1.
Network Access Security in Mobile 4G LTE. Huang Zheng Xiong Jiaxi An Sihua 2013.07
 Network Access Security in Mobile 4G LTE Huang Zheng Xiong Jiaxi An Sihua 2013.07 Outline Mobile Evolution About LTE Overview of LTE System LTE Network Access Security Conclusion Mobile Evolution Improvements
Network Access Security in Mobile 4G LTE Huang Zheng Xiong Jiaxi An Sihua 2013.07 Outline Mobile Evolution About LTE Overview of LTE System LTE Network Access Security Conclusion Mobile Evolution Improvements
Using an approximated One-Time Pad to Secure Short Messaging Service (SMS)
 Using an approximated One-Time Pad to Secure Short Messaging Service (SMS) N.J Croft and M.S Olivier Information and Computer Security Architectures (ICSA) Research Group Department of Computer Science
Using an approximated One-Time Pad to Secure Short Messaging Service (SMS) N.J Croft and M.S Olivier Information and Computer Security Architectures (ICSA) Research Group Department of Computer Science
LTE and the Evolution to 4G Wireless
 LTE and the Evolution to 4G Wireless Design and Measurement Challenges Bonus Material: Security in the LTE-SAE Network www.agilent.com/find/lte Introduction Security in the LTE-SAE Network This overview
LTE and the Evolution to 4G Wireless Design and Measurement Challenges Bonus Material: Security in the LTE-SAE Network www.agilent.com/find/lte Introduction Security in the LTE-SAE Network This overview
Mobile Computing. Basic Call Calling terminal Network Called terminal 10/25/14. Public Switched Telephone Network - PSTN. CSE 40814/60814 Fall 2014
 Mobile Computing CSE 40814/60814 Fall 2014 Public Switched Telephone Network - PSTN Transit switch Transit switch Long distance network Transit switch Local switch Outgoing call Incoming call Local switch
Mobile Computing CSE 40814/60814 Fall 2014 Public Switched Telephone Network - PSTN Transit switch Transit switch Long distance network Transit switch Local switch Outgoing call Incoming call Local switch
Mobility and cellular networks
 Mobility and cellular s Wireless WANs Cellular radio and PCS s Wireless data s Satellite links and s Mobility, etc.- 2 Cellular s First generation: initially debuted in Japan in 1979, analog transmission
Mobility and cellular s Wireless WANs Cellular radio and PCS s Wireless data s Satellite links and s Mobility, etc.- 2 Cellular s First generation: initially debuted in Japan in 1979, analog transmission
of the existing VoLTE roaming and interconnection architecture. This article compares existing circuit-switched models with the earlier
 VoLTE 3GPP Roaming Further Development of LTE/LTE-Advanced LTE Release 10/11 Standardization Trends VoLTE Roaming and ion Standard Technology In 3GPP Release 11, the VoLTE roaming and interconnection architecture
VoLTE 3GPP Roaming Further Development of LTE/LTE-Advanced LTE Release 10/11 Standardization Trends VoLTE Roaming and ion Standard Technology In 3GPP Release 11, the VoLTE roaming and interconnection architecture
End Device Support for AAA in SIP Conferencing
 End Device Support for AAA in SIP Conferencing Antti Poikela Helsinki University of Technology aspoikel@cc.hut.fi Abstract This study is a literature survey of current problems and solutions for authentication,
End Device Support for AAA in SIP Conferencing Antti Poikela Helsinki University of Technology aspoikel@cc.hut.fi Abstract This study is a literature survey of current problems and solutions for authentication,
Toolkit for vulnerability assessment in 3G networks. Kameswari Kotapati The Pennsylvania State University University Park PA 16802
 Toolkit for vulnerability assessment in 3G networks Kameswari Kotapati The Pennsylvania State University University Park PA 16802 Contents Motivation Solution Overview Methodology Overview 3G Attack Graph
Toolkit for vulnerability assessment in 3G networks Kameswari Kotapati The Pennsylvania State University University Park PA 16802 Contents Motivation Solution Overview Methodology Overview 3G Attack Graph
How To Understand The Gsm And Mts Mobile Network Evolution
 Mobile Network Evolution Part 1 GSM and UMTS GSM Cell layout Architecture Call setup Mobility management Security GPRS Architecture Protocols QoS EDGE UMTS Architecture Integrated Communication Systems
Mobile Network Evolution Part 1 GSM and UMTS GSM Cell layout Architecture Call setup Mobility management Security GPRS Architecture Protocols QoS EDGE UMTS Architecture Integrated Communication Systems
Mobile Devices Security: Evolving Threat Profile of Mobile Networks
 Mobile Devices Security: Evolving Threat Profile of Mobile Networks SESSION ID: MBS-T07 Anand R. Prasad, Dr.,ir., Selim Aissi, PhD Objectives Introduction Mobile Network Security Cybersecurity Implications
Mobile Devices Security: Evolving Threat Profile of Mobile Networks SESSION ID: MBS-T07 Anand R. Prasad, Dr.,ir., Selim Aissi, PhD Objectives Introduction Mobile Network Security Cybersecurity Implications
LTE Overview October 6, 2011
 LTE Overview October 6, 2011 Robert Barringer Enterprise Architect AT&T Proprietary (Internal Use Only) Not for use or disclosure outside the AT&T companies except under written agreement LTE Long Term
LTE Overview October 6, 2011 Robert Barringer Enterprise Architect AT&T Proprietary (Internal Use Only) Not for use or disclosure outside the AT&T companies except under written agreement LTE Long Term
3GPP TR 23.912 V3.1.0 (2001-12)
 TR 23.912 V3.1.0 (2001-12) Technical Specification 3rd Generation Partnership Project; Technical Specification Group Core Network; Technical report on Super-Charger (Release 1999) The present document
TR 23.912 V3.1.0 (2001-12) Technical Specification 3rd Generation Partnership Project; Technical Specification Group Core Network; Technical report on Super-Charger (Release 1999) The present document
IMS Release 10 Tutorial
 IMS Release 10 Tutorial Silvia Scalisi University of Trento 1 Introduction The IP Multimedia Subsystem (IMS) is a network architecture that delivers services based upon the Internet protocols to mobile
IMS Release 10 Tutorial Silvia Scalisi University of Trento 1 Introduction The IP Multimedia Subsystem (IMS) is a network architecture that delivers services based upon the Internet protocols to mobile
Mobile@Home GSM services over wireless LAN
 Mobile@Home GSM services over wireless LAN Martin Bäckström, Andreas Havdrup, Tomas Nylander, Jari Vikberg and Peter Öhman What do you get when you combine mobile telephony with voice over IP (VoIP)? Mobile@Home.
Mobile@Home GSM services over wireless LAN Martin Bäckström, Andreas Havdrup, Tomas Nylander, Jari Vikberg and Peter Öhman What do you get when you combine mobile telephony with voice over IP (VoIP)? Mobile@Home.
ETSI TS 121 111 V8.0.1 (2008-01) Technical Specification
 TS 121 111 V8.0.1 (2008-01) Technical Specification Universal Mobile Telecommunications System (UMTS); USIM and IC card requirements (3GPP TS 21.111 version 8.0.1 Release 8) 1 TS 121 111 V8.0.1 (2008-01)
TS 121 111 V8.0.1 (2008-01) Technical Specification Universal Mobile Telecommunications System (UMTS); USIM and IC card requirements (3GPP TS 21.111 version 8.0.1 Release 8) 1 TS 121 111 V8.0.1 (2008-01)
2G/3G Mobile Communication Systems
 2G/3G Mobile Communication Systems Winter 2012/13 Integrated Communication Systems Group Ilmenau University of Technology Outline 2G Review: GSM Services Architecture Protocols Call setup Mobility management
2G/3G Mobile Communication Systems Winter 2012/13 Integrated Communication Systems Group Ilmenau University of Technology Outline 2G Review: GSM Services Architecture Protocols Call setup Mobility management
Reprogrammable SIMs:
 Reprogrammable SIMs: Technology, Evolution and Implications Final Report Prepared for: Prepared by: CSMG Descartes House 8 Gate Street London WC2A 3HP United Kingdom www.csmg-global.com 25 September 2012
Reprogrammable SIMs: Technology, Evolution and Implications Final Report Prepared for: Prepared by: CSMG Descartes House 8 Gate Street London WC2A 3HP United Kingdom www.csmg-global.com 25 September 2012
(U)SimMonitor: A Mobile Application for Security Evaluation of Cellular Networks
 (U)SimMonitor: A Mobile Application for Security Evaluation of Cellular Networks Christos Xenakis, Christoforos Ntantogian, Orestis Panos Department of Digital Systems, University of Piraeus Piraeus, Greece
(U)SimMonitor: A Mobile Application for Security Evaluation of Cellular Networks Christos Xenakis, Christoforos Ntantogian, Orestis Panos Department of Digital Systems, University of Piraeus Piraeus, Greece
3GPP Femtocells: Architecture and Protocols. by Gavin Horn
 3GPP Femtocells: Architecture and Protocols by Gavin Horn QUALCOMM Incorporated 5775 Morehouse Drive San Diego, CA 92121-1714 U.S.A. 3GPP Femtocells: Architecture and Protocols September 2010-2 - Contents
3GPP Femtocells: Architecture and Protocols by Gavin Horn QUALCOMM Incorporated 5775 Morehouse Drive San Diego, CA 92121-1714 U.S.A. 3GPP Femtocells: Architecture and Protocols September 2010-2 - Contents
MAP/C SEND ROUTING INFO FOR SM. Destination Mobile Number. Obtain the SS7 address of the MSC VLR currently serving the specified Mobile Number
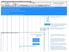 In this call flow we will look at how a terminating SMS is handled in GSM. Setting up a terminating SMS session is a multi-step process. (1) Interrogate the MSC to locate the subscriber (2)Setting SMS
In this call flow we will look at how a terminating SMS is handled in GSM. Setting up a terminating SMS session is a multi-step process. (1) Interrogate the MSC to locate the subscriber (2)Setting SMS
Network Security. Chapter 14. Security Aspects of Mobile Communications
 Network Security Chapter 14 Security Aspects of Mobile Communications Network Security (WS 2002): 14 Security Aspects of Mobile Communications 1 Security Aspects of Mobile Communication Mobile communication
Network Security Chapter 14 Security Aspects of Mobile Communications Network Security (WS 2002): 14 Security Aspects of Mobile Communications 1 Security Aspects of Mobile Communication Mobile communication
Mobile Phone Security. Hoang Vo Billy Ngo
 Mobile Phone Security Hoang Vo Billy Ngo Table of Content 1. Introduction Page 2 1.1 Analog Network Page 2 1.2 Digital Network Page 2 2. Security Protocols Page 4 2.1 Analog Page 4 2.2 Digital Page 5 3.
Mobile Phone Security Hoang Vo Billy Ngo Table of Content 1. Introduction Page 2 1.1 Analog Network Page 2 1.2 Digital Network Page 2 2. Security Protocols Page 4 2.1 Analog Page 4 2.2 Digital Page 5 3.
Study Paper on Security Accreditation Scheme for SIM
 May 2014 MOBILE Study Paper on Security Accreditation Scheme for SIM TEC TELECOMMUNICATION ENGINEERING CENTRE KHURSHID LAL BHAWAN, JANPATH NEW DELHI - 110001 INDIA 1 Introduction... 4 2 Security Threats...
May 2014 MOBILE Study Paper on Security Accreditation Scheme for SIM TEC TELECOMMUNICATION ENGINEERING CENTRE KHURSHID LAL BHAWAN, JANPATH NEW DELHI - 110001 INDIA 1 Introduction... 4 2 Security Threats...
Provides a communication link between MS and MSC; Manages DB for MS location. Controls user connection. Transmission.
 Provides a communication link between MS and MSC; Manages DB for MS location Controls user connection CM MM RR Transmission Several RR functions considered in previous part!"# Surprise! handover is part
Provides a communication link between MS and MSC; Manages DB for MS location Controls user connection CM MM RR Transmission Several RR functions considered in previous part!"# Surprise! handover is part
3GPP TS 23.003 V5.11.0 (2006-06)
 TS 23.003 V5.11.0 (2006-06) Technical Specification 3rd Generation Partnership Project; Technical Specification Group Core Network; Numbering, addressing and identification (Release 5) GLOBAL SYSTEM FOR
TS 23.003 V5.11.0 (2006-06) Technical Specification 3rd Generation Partnership Project; Technical Specification Group Core Network; Numbering, addressing and identification (Release 5) GLOBAL SYSTEM FOR
CS Fallback Function for Combined LTE and 3G Circuit Switched Services
 EPC Voice over Circuit Switched Services Special Articles on SAE Standardization Technology CS Fallback Function for Combined and Circuit Switched Services The PP, an international standardization body
EPC Voice over Circuit Switched Services Special Articles on SAE Standardization Technology CS Fallback Function for Combined and Circuit Switched Services The PP, an international standardization body
ETSI TS 123 003 V10.5.0 (2012-04)
 TS 123 003 V10.5.0 (2012-04) Technical Specification Digital cellular telecommunications system (Phase 2+); Universal Mobile Telecommunications System (UMTS); Numbering, addressing and identification (3GPP
TS 123 003 V10.5.0 (2012-04) Technical Specification Digital cellular telecommunications system (Phase 2+); Universal Mobile Telecommunications System (UMTS); Numbering, addressing and identification (3GPP
Virtual SIM A Feasibility Study
 i Master s Thesis The Virtual SIM A Feasibility Study By Marc Richarme In collaboration with: Copenhagen, 21 April 2008 ii Preface Preface This Master s thesis has been prepared at the Department for Informatics
i Master s Thesis The Virtual SIM A Feasibility Study By Marc Richarme In collaboration with: Copenhagen, 21 April 2008 ii Preface Preface This Master s thesis has been prepared at the Department for Informatics
Review of Cell Phone Technology
 Review of Cell Phone Technology Types of Cell Technology - CDMA - GSM - iden - TDMA CDMA Code Division Multiple Access (CDMA) CDMA Code Division Multiple Access. In reality it is cdmaone (2G) or CDMA2000
Review of Cell Phone Technology Types of Cell Technology - CDMA - GSM - iden - TDMA CDMA Code Division Multiple Access (CDMA) CDMA Code Division Multiple Access. In reality it is cdmaone (2G) or CDMA2000
Overview Smartcards and Related Application Infrastructures. Smartcards. Smartcards
 Overview Smartcards and Related Application Infrastructures Lecture 8 Smartcards and Related Application Infrastructures Smartcards Introduction Subscriber Identity Module (SIM) WAP Identity Module (WIM)
Overview Smartcards and Related Application Infrastructures Lecture 8 Smartcards and Related Application Infrastructures Smartcards Introduction Subscriber Identity Module (SIM) WAP Identity Module (WIM)
MOBILE COMPUTING AND M- COMMERCE SECURITY ISSUES
 MOBILE COMPUTING AND M- COMMERCE SECURITY ISSUES Krishna Prakash 1 and Balachandra 2 1,2 Department of Information and Communication Technology, MIT Manipal 1 kkp_prakash@yahoo.com, 2 bala_muniyal@yahoo.com
MOBILE COMPUTING AND M- COMMERCE SECURITY ISSUES Krishna Prakash 1 and Balachandra 2 1,2 Department of Information and Communication Technology, MIT Manipal 1 kkp_prakash@yahoo.com, 2 bala_muniyal@yahoo.com
Co-existence of Wireless LAN and Cellular Henry Haverinen Senior Specialist Nokia Enterprise Solutions
 Co-existence of Wireless LAN and Cellular Henry Haverinen Senior Specialist Nokia Enterprise Solutions 1 2005 Nokia city_wlan_2005_haverinen.ppt / 2005-08-19 / HH Outline Key use cases of integrating Wireless
Co-existence of Wireless LAN and Cellular Henry Haverinen Senior Specialist Nokia Enterprise Solutions 1 2005 Nokia city_wlan_2005_haverinen.ppt / 2005-08-19 / HH Outline Key use cases of integrating Wireless
GSM BASICS GSM HISTORY:
 GSM BASICS GSM HISTORY: In 1982 the Nordic PTTs sent a proposal to CEPT (Conference of European Postal & telegraph Administration) to study and to improve digital cellular technology by forming a team
GSM BASICS GSM HISTORY: In 1982 the Nordic PTTs sent a proposal to CEPT (Conference of European Postal & telegraph Administration) to study and to improve digital cellular technology by forming a team
Security Analysis of LTE Access Network
 Security Analysis of LTE Access Network Cristina-Elena Vintilă, Victor-Valeriu Patriciu, Ion Bica Computer Science Department Military Technical Academy - Bucharest, ROMANIA cristina.vintila@gmail.com,
Security Analysis of LTE Access Network Cristina-Elena Vintilă, Victor-Valeriu Patriciu, Ion Bica Computer Science Department Military Technical Academy - Bucharest, ROMANIA cristina.vintila@gmail.com,
