What does privacy mean to you?
|
|
|
- Mariah Bates
- 9 years ago
- Views:
Transcription
1 What does privacy mean to you? 1. What is your age in years? 1,004 answered question 1,004 skipped question 0 1 of 11
2 2. Do you typically do any of the following things? Select ALL that apply. Lock the bathroom door 54.2% 544 Change my social network privacy settings 65.7% 660 Close the blinds at home 78.1% 784 Limit who knows where I am or my family is 51.3% 515 Give out my address to websites 71.3% 716 Give out my phone number to websites 28.1% 282 Give out my credit card number to websites 52.5% 527 Search for my name on search engines 46.4% 466 Walk around naked in locker rooms 5.8% 58 Block online trackers while I browse 36.2% 363 Share my password 4.5% 45 Use loyalty cards when shopping 58.1% 583 answered question 1,004 skipped question 0 2 of 11
3 3. Are the following things part of your personal definition of privacy? Select all that apply. Locking the bathroom door 60.4% 606 Changing my social network privacy settings 73.4% 737 Closing the blinds at home 75.1% 754 Limiting who knows where I am or my family is 64.8% 651 Government or law enforcement surveillance and searches 44.9% 451 Controlling which websites have my 72.9% 732 Controlling which websites have my phone number 73.3% 736 Controlling which websites have my credit card number 79.4% 797 The ability to speak freely and be myself 57.8% 580 Online search results for my name 37.8% 380 Protecting my or my family s physical safety (e.g., from stalkers) 77.7% 780 Blocking online trackers from collecting my personal information while I browse 57.9% 581 The right to simply be left alone 82.7% 830 answered question 1,004 skipped question 0 3 of 11
4 4. Do you agree or disagree with the following statements? Agree Disagree Rating Online trackers that collect information about what websites I visit, what I read, and what I buy online are an invasion of my privacy. 83.1% (834) 16.9% (170) 1,004 Data collection sites or data brokers that publish personal information such as my home address, phone number, age, net worth, and family members names are an invasion of my privacy. 90.7% (911) 9.3% (93) 1,004 Websites requiring my address in order for me to access content or make a purchase are an invasion of my privacy. 40.0% (402) 60.0% (602) 1,004 Websites requiring me to log in with Facebook to access content are an invasion of my privacy. 76.8% (771) 23.2% (233) 1,004 Websites requiring my phone number in order for me to access content or make a purchase are an invasion of my privacy. 72.1% (724) 27.9% (280) 1,004 I feel my or my family s safety is threatened due to online privacy concerns. 34.8% (349) 65.2% (655) 1,004 I m concerned about companies losing, sharing, or selling my address. 73.0% (733) 27.0% (271) 1,004 I m concerned about companies losing, sharing, or selling my phone number. 78.4% (787) 21.6% (217) 1,004 I m concerned about companies losing, sharing, or selling my credit card number. 83.3% (836) 16.7% (168) 1,004 I m concerned about companies losing my login info (username and 61.7% (619) 38.3% (385) 1,004 4 of 11
5 password(s)). answered question 1,004 skipped question 0 5. Do you ever worry about your privacy? Yes, I worry about my privacy often. 22.0% 221 Yes, I worry about my privacy sometimes. 67.9% 682 No, I don t worry about my privacy. 10.1% 101 answered question 1,004 skipped question 0 6. Why does online privacy concern you? Select the one issue that's MOST important to you. Current or future employment 5.8% 52 I think I have a right to privacy 45.6% 406 My personal reputation 4.7% 42 My or my family s personal safety 17.4% 155 My or my family s financial safety 26.5% 236 answered question 891 skipped question of 11
6 7. Which of the following things is a privacy worry for you? Select all that apply: Online search results for my name 37.4% 333 Preventing people from spying on me in real life 51.6% 460 My personal contact information being easily available online (e.g., , phone number, home address 81.6% 727 The safety and security of my credit card when I shop online 84.6% 754 Photos of me online 51.2% 456 My social information (e.g., my friends, likes, Facebook posts, tweets, interests) 54.3% 484 Having to censor myself because I m worried that what I write might be used against me in the future 52.6% 469 Online trackers that collect my personal info as I browse 68.4% 609 answered question 891 skipped question of 11
7 8. Select the one piece of information below that you most DISLIKE giving out online. My phone number 15.7% 156 My address 2.0% 20 My home address 15.4% 153 My credit card number 60.9% 604 My age 0.6% 6 My name 5.2% 52 answered question 991 skipped question 13 7 of 11
8 9. Which one description below BEST sums up what online privacy means to you? I get to choose what personal information I give out and who gets it 23.3% 231 The right to be free from others watching me 4.4% 44 Easy access to all the personal information that companies have about me 1.8% 18 I should be able to use the Internet without having to trade away my personal information 14.5% 144 The on-demand ability to hide my real information 2.6% 26 Having complete control over what information is collected about me online 19.4% 192 Total anonymity 14.6% 145 Being able to delete anything about me online 5.4% 54 Having choice and control over my data 13.8% 137 answered question 991 skipped question 13 8 of 11
9 10. Have you taken any of the following actions to protect your online privacy? Select all that apply. Used private browsing mode or a Do Not Track feature in my browser 52.8% 523 Created multiple addresses (e.g., I use Hotmail for spam and Gmail for my real ) 73.8% 731 Given out a fake phone number 62.8% 622 Used PayPal to shop online instead of giving out my credit card number 59.2% 587 Used another payment method online (other than PayPal) to protect my credit card (e.g., a virtual credit card or one time use card) 29.8% 295 Created content to improve search results for my name 6.2% 61 Used a fake name or alias 59.8% 593 Avoided posting pictures of my face 37.9% 376 Used a proxy or a Virtual Private Network (VPN) 26.5% 263 Tried to get someone else to delete content about me (e.g., having a friend detag a Facebook picture, or getting a website to delete an article about me) 23.8% 236 Given a fake birthdate 53.8% 533 Adjusted social network privacy settings 69.2% of 11
10 Used a private search engine 20.9% 207 I don't do anything to protect my online privacy 2.8% 28 answered question 991 skipped question Would you ever pay for a product or service that gives you more privacy? As you answer this question, consider your definition of privacy from question 3 earlier in this survey. Yes, I would pay a significant amount (more than $100/year) 2.0% 20 Yes, I would pay a small amount ($10/year or less) 44.7% 443 No, I would not pay anything 49.3% 489 Yes, I already pay for privacy in some way. 3.9% 39 answered question 991 skipped question Last week, Facebook announced Facebook Home. Do you trust Facebook with your data? Yes 20.7% 196 No 79.3% 751 answered question 947 skipped question of 11
11 13. Optional: What does privacy mean to you? What specific things do you think of when you hear it? 339 answered question 339 skipped question of 11
To learn more about social networking, see the handout titled Know Social Networking.
 Know facebook Objectives Identify different social networks Identify common features of a social network Understand social networking etiquette Sign up for a Facebook account Create a profile in Facebook
Know facebook Objectives Identify different social networks Identify common features of a social network Understand social networking etiquette Sign up for a Facebook account Create a profile in Facebook
Internet basics 2.3 Protecting your computer
 Basics Use this document with the glossary Beginner s guide to Internet basics 2.3 Protecting your computer How can I protect my computer? This activity will show you how to protect your computer from
Basics Use this document with the glossary Beginner s guide to Internet basics 2.3 Protecting your computer How can I protect my computer? This activity will show you how to protect your computer from
HO-6: Shopcreator Set-up the build process (Logging On: Administration/Store)
 Shopcreator HO-Exercises: What to do Work thorough the hands-on exercises in the order they are presented: Any point marked like this indicates outcomes (what you should be able to do by the end of the
Shopcreator HO-Exercises: What to do Work thorough the hands-on exercises in the order they are presented: Any point marked like this indicates outcomes (what you should be able to do by the end of the
This document has been produced following a request from the Hft National Speak Out Group for help with staying safe when using the internet.
 This document has been produced following a request from the Hft National Speak Out Group for help with staying safe when using the internet. Hft Safeguarding Group commissioned a member of Hft National
This document has been produced following a request from the Hft National Speak Out Group for help with staying safe when using the internet. Hft Safeguarding Group commissioned a member of Hft National
Internet basics 2.2 Staying safe online. Beginner s guide to. Basics
 Basics Beginner s guide to Internet basics 2.2 Staying safe online Use this document with the glossary A helper should take you through this guide This activity will help you register safely online and
Basics Beginner s guide to Internet basics 2.2 Staying safe online Use this document with the glossary A helper should take you through this guide This activity will help you register safely online and
DIGITAL LIFE E-GUIDE How to Protect your Smartphone
 A DIGITAL LIFE E-GUIDE How to Protect your Smartphone It s been said that information is the new currency. 1 Carrying a smartphone nowadays is like having a second wallet. Instead of containing money
A DIGITAL LIFE E-GUIDE How to Protect your Smartphone It s been said that information is the new currency. 1 Carrying a smartphone nowadays is like having a second wallet. Instead of containing money
Google 2 factor authentication User Guide
 Information Technology Services Centre Google 2 factor authentication User Guide Description: This guide describes how to setup Two factor authentication for your Google account. Version: 1.0 Link: Effective
Information Technology Services Centre Google 2 factor authentication User Guide Description: This guide describes how to setup Two factor authentication for your Google account. Version: 1.0 Link: Effective
Single Property Website Quickstart Guide
 Single Property Website Quickstart Guide Win More Listings. Attract More Buyers. Sell More Homes. TABLE OF CONTENTS Getting Started... 3 First Time Registration...3 Existing Account...6 Administration
Single Property Website Quickstart Guide Win More Listings. Attract More Buyers. Sell More Homes. TABLE OF CONTENTS Getting Started... 3 First Time Registration...3 Existing Account...6 Administration
Online Trading User s Manual
 Online Trading User s Manual October, 2015 Version 3.0 Securities and Investment Company UAE Important Notice: This manual has been prepared only to assist the client how to interact with the Online Trading
Online Trading User s Manual October, 2015 Version 3.0 Securities and Investment Company UAE Important Notice: This manual has been prepared only to assist the client how to interact with the Online Trading
Review VIDEO WORKSHEET. Your Digital Identity A Permanent Step #300005. Name: Hour:
 #300005 Name: Hour: VIDEO WORKSHEET Review Directions: After watching Digital Footprint: Watch Where You Step, answer the following questions. Your Digital Identity A Permanent Step 1. What is a digital
#300005 Name: Hour: VIDEO WORKSHEET Review Directions: After watching Digital Footprint: Watch Where You Step, answer the following questions. Your Digital Identity A Permanent Step 1. What is a digital
one Managing your PBX Administrator ACCESSING YOUR PBX ACCOUNT CHECKING ACCOUNT ACTIVITY
 one Managing your PBX Administrator ACCESSING YOUR PBX ACCOUNT Navigate to https://portal.priorityonenet.com/ and log in to the PriorityOne portal account. If you would like your web browser to keep you
one Managing your PBX Administrator ACCESSING YOUR PBX ACCOUNT Navigate to https://portal.priorityonenet.com/ and log in to the PriorityOne portal account. If you would like your web browser to keep you
DISCOUNT DEALER PROGRAM
 DISCOUNT DEALER PROGRAM U.S. Cooler offers dealers the opportunity to purchase and sell walk-ins online through our Discount Dealer Program. The following outlines the step-by-step process. We also offer
DISCOUNT DEALER PROGRAM U.S. Cooler offers dealers the opportunity to purchase and sell walk-ins online through our Discount Dealer Program. The following outlines the step-by-step process. We also offer
What is the Cloud? Computer Basics Web Apps and the Cloud. Page 1
 Computer Basics Web Apps and the Cloud What is the Cloud? You may have heard people using terms like the cloud, cloud computing, or cloud storage. But what exactly is the cloud? Basically, the cloud is
Computer Basics Web Apps and the Cloud What is the Cloud? You may have heard people using terms like the cloud, cloud computing, or cloud storage. But what exactly is the cloud? Basically, the cloud is
Page 18. Using Software To Make More Money With Surveys. Visit us on the web at: www.takesurveysforcash.com
 Page 18 Page 1 Using Software To Make More Money With Surveys by Jason White Page 2 Introduction So you re off and running with making money by taking surveys online, good for you! The problem, as you
Page 18 Page 1 Using Software To Make More Money With Surveys by Jason White Page 2 Introduction So you re off and running with making money by taking surveys online, good for you! The problem, as you
Player & Parent Handbook
 Player & Parent Handbook Your GotSoccer player account has many features. This handbook is designed to help you understand the capabilities of our system. Contents Creating a Player Account... 2 Login
Player & Parent Handbook Your GotSoccer player account has many features. This handbook is designed to help you understand the capabilities of our system. Contents Creating a Player Account... 2 Login
How to train your Browser Controller
 How to train your Browser Controller Table of Contents ABOUT 3 TOP BAR SETTINGS 3 CHILD LOCK 3 SPYDERWEB 3 PERSONAL PRIVACY EXPOSURE 4 KEY & STATS 4 GRAPH VIEW 4 AUTO-REFRESH 5 DOMAIN GEO-LOCATION INFO
How to train your Browser Controller Table of Contents ABOUT 3 TOP BAR SETTINGS 3 CHILD LOCK 3 SPYDERWEB 3 PERSONAL PRIVACY EXPOSURE 4 KEY & STATS 4 GRAPH VIEW 4 AUTO-REFRESH 5 DOMAIN GEO-LOCATION INFO
Preparing your Domain to transfer from Go Daddy
 Preparing your Domain to transfer from Go Daddy Before you can transfer a domain: Getting Started Disable domain privacy. If the privacy service forwards incoming email, check the ʻforward toʼ contact
Preparing your Domain to transfer from Go Daddy Before you can transfer a domain: Getting Started Disable domain privacy. If the privacy service forwards incoming email, check the ʻforward toʼ contact
NAVY COMMAND PRINCIPAL SECURITY ADVISOR RECOMMENDED FACEBOOK SECURITY SETTINGS
 NAVY COMMAND PRINCIPAL SECURITY ADVISOR RECOMMENDED FACEBOOK SECURITY SETTINGS NC PSyA Recommended Facebook Settings - October 2014 1 Introduction 3 Privacy Shortcuts 3 Privacy Settings and Tools 6 General
NAVY COMMAND PRINCIPAL SECURITY ADVISOR RECOMMENDED FACEBOOK SECURITY SETTINGS NC PSyA Recommended Facebook Settings - October 2014 1 Introduction 3 Privacy Shortcuts 3 Privacy Settings and Tools 6 General
Telephone Users Guide
 Telephone Users Guide T A B L E O F C O N T E N T S 1 WELCOME TO ARMSTRONG TELEPHONE 2 Our Commitment to You Identifying Our Employees Dialing 911 - Your Safety Is Important 3 HOW TO MAKE CALLS Domestic
Telephone Users Guide T A B L E O F C O N T E N T S 1 WELCOME TO ARMSTRONG TELEPHONE 2 Our Commitment to You Identifying Our Employees Dialing 911 - Your Safety Is Important 3 HOW TO MAKE CALLS Domestic
EVENT REGISTRATION. Introduction. Feature Availability. Requirements. Table of Contents. Version 7/22/2012
 EVENT REGISTRATION Version 7/22/2012 SOAR Scouting Online Affordable & Reliable Introduction This Guide will walk you through the basics of using the SOAR Event Signup feature for event registration. The
EVENT REGISTRATION Version 7/22/2012 SOAR Scouting Online Affordable & Reliable Introduction This Guide will walk you through the basics of using the SOAR Event Signup feature for event registration. The
Understand What s Going On
 Internet Safety Tips For Dummies In This Book Recognizing how online risks occur Staying safer with technology Taking care with shared photos Understanding how crooks collect information Reporting fraud
Internet Safety Tips For Dummies In This Book Recognizing how online risks occur Staying safer with technology Taking care with shared photos Understanding how crooks collect information Reporting fraud
How to Open,Verify and Fund Accessible PayPal Account In Any Unsupported Country
 Michael Nwanator's PayPal Solution PayPal Solution How to Open,Verify and Fund Accessible PayPal Account In Any Unsupported Country By Michael Nwanator www.4lucrativebiz.com Important: Free Giveaway Rights
Michael Nwanator's PayPal Solution PayPal Solution How to Open,Verify and Fund Accessible PayPal Account In Any Unsupported Country By Michael Nwanator www.4lucrativebiz.com Important: Free Giveaway Rights
WHAT INFORMATION IS COLLECTED AT MOTOROLA.COM.VN AND/OR MOTOROLA.VN AND HOW IS IT PROCESSED AND USED?
 MOTOROLA PRIVACY POLICY This Privacy Statement ( Policy ) is subject to change at Motorola s discretion. If we decide to change this Policy, we will post the amended Policy on this website so you will
MOTOROLA PRIVACY POLICY This Privacy Statement ( Policy ) is subject to change at Motorola s discretion. If we decide to change this Policy, we will post the amended Policy on this website so you will
The Lynx A Step by Step guide
 The Lynx A Step by Step guide Section 1: Updating your organization and recruiting tips (pg.1) Section 2: For page managers (pg. 5) Section 3: Club Sports specific tasks (pg. 12) Section 4: New Users and
The Lynx A Step by Step guide Section 1: Updating your organization and recruiting tips (pg.1) Section 2: For page managers (pg. 5) Section 3: Club Sports specific tasks (pg. 12) Section 4: New Users and
STOP. THINK. CONNECT. Online Safety Quiz
 STOP. THINK. CONNECT. Online Safety Quiz Round 1: Safety and Security Kristina is on Facebook and receives a friend request from a boy she doesn t know. What should she do? A. Accept the friend request.
STOP. THINK. CONNECT. Online Safety Quiz Round 1: Safety and Security Kristina is on Facebook and receives a friend request from a boy she doesn t know. What should she do? A. Accept the friend request.
Could you spot a scammer?
 Could you spot a scammer? Keeping you safe and secure Fraud can affect anyone whatever your background, age or experience And attempts can come in all shapes and sizes over the phone, on the internet or
Could you spot a scammer? Keeping you safe and secure Fraud can affect anyone whatever your background, age or experience And attempts can come in all shapes and sizes over the phone, on the internet or
Contents. Introduction. Creating a list. Growing your list. Managing unsubscribes. Handling spam complaints. Managing bounces
 Managing your data Contents 01 02 03 04 05 06 07 08 09 10 11 Introduction Creating a list Growing your list Managing unsubscribes Handling spam complaints Managing bounces Dealing with Out of Office notifications
Managing your data Contents 01 02 03 04 05 06 07 08 09 10 11 Introduction Creating a list Growing your list Managing unsubscribes Handling spam complaints Managing bounces Dealing with Out of Office notifications
Shentel (Shentel.net)
 Shentel (Shentel.net) Email Quick Start Guide Your new webmail is now powered by Contents If you are forwarding your Shentel.net email to a third party address...2 If you use an email program other than
Shentel (Shentel.net) Email Quick Start Guide Your new webmail is now powered by Contents If you are forwarding your Shentel.net email to a third party address...2 If you use an email program other than
Frequently Asked Questions for logging in to Online Banking
 Frequently Asked Questions for logging in to Online Banking Why don t I recognize any of the phone numbers on the Secure Code page? I can t remember my password; can I reset it myself? I know I have the
Frequently Asked Questions for logging in to Online Banking Why don t I recognize any of the phone numbers on the Secure Code page? I can t remember my password; can I reset it myself? I know I have the
In the Cloud. Scoville Memorial Library February, 2013 [email protected]
 In the Cloud Scoville Memorial Library February, 2013 [email protected] What is the Cloud? You may have heard people using terms like the cloud, cloud computing, or cloud storage. But what exactly is the
In the Cloud Scoville Memorial Library February, 2013 [email protected] What is the Cloud? You may have heard people using terms like the cloud, cloud computing, or cloud storage. But what exactly is the
Website Privacy Policy Statement. 1519 York Rd Lutherville, MD 21093. We may be reached via email at [email protected].
 Website Privacy Policy Statement This website juliereisler.com is operated by Empowered Living, LLC and this policy applies to all websites owned, operated, controlled and otherwise made available by Company,
Website Privacy Policy Statement This website juliereisler.com is operated by Empowered Living, LLC and this policy applies to all websites owned, operated, controlled and otherwise made available by Company,
A quick guide to setting up your new website
 A quick guide to setting up your new website Hi there. Welcome to MrSite we re really happy you chose to build your brand new website with us and look forward to seeing what you create! We re sure you
A quick guide to setting up your new website Hi there. Welcome to MrSite we re really happy you chose to build your brand new website with us and look forward to seeing what you create! We re sure you
Website Privacy Policy Statement
 Website Privacy Policy Statement This website ( CRSF Website ) is operated by Cal Ripken, Sr. Foundation, Inc. ( Company ) and this policy applies to all websites owned, operated, controlled and otherwise
Website Privacy Policy Statement This website ( CRSF Website ) is operated by Cal Ripken, Sr. Foundation, Inc. ( Company ) and this policy applies to all websites owned, operated, controlled and otherwise
TweetAttacks Pro. User Manual
 TweetAttacks Pro User Manual The ultimate twitter auto follower, auto unfollower, tweet scraper, reply generator, auto retweeter, tweet spinner, mass retweeter and tweet scheduler with socialoomph integration.
TweetAttacks Pro User Manual The ultimate twitter auto follower, auto unfollower, tweet scraper, reply generator, auto retweeter, tweet spinner, mass retweeter and tweet scheduler with socialoomph integration.
Privacy Policy Version 1.0, 1 st of May 2016
 Privacy Policy Version 1.0, 1 st of May 2016 THIS PRIVACY POLICY APPLIES TO PERSONAL INFORMATION COLLECTED BY GOCIETY SOLUTIONS FROM USERS OF THE GOCIETY SOLUTIONS APPLICATIONS (GoLivePhone and GoLiveAssist)
Privacy Policy Version 1.0, 1 st of May 2016 THIS PRIVACY POLICY APPLIES TO PERSONAL INFORMATION COLLECTED BY GOCIETY SOLUTIONS FROM USERS OF THE GOCIETY SOLUTIONS APPLICATIONS (GoLivePhone and GoLiveAssist)
Order a Transcript/Enrollment Verification as a Current Student
 Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Order a Transcript/Enrollment Verification as a Current Overview With the University s Transcript/Enrollment Verification Ordering service,
Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Order a Transcript/Enrollment Verification as a Current Overview With the University s Transcript/Enrollment Verification Ordering service,
How To Send Your Email Newsletter
 How To Send Your Email Newsletter You can manage email contacts and send your email newsletter through our proprietary email system called the ONLINE MARKETING CENTER. On the next few pages of this guide
How To Send Your Email Newsletter You can manage email contacts and send your email newsletter through our proprietary email system called the ONLINE MARKETING CENTER. On the next few pages of this guide
How to minimize SPAM in your CBPref.com Inbox
 How to minimize SPAM in your CBPref.com Inbox By Jason K. Serafin As I travel through our Coldwell Banker Preferred branch offices, I hear many agents ask me the same question over and over: What can we
How to minimize SPAM in your CBPref.com Inbox By Jason K. Serafin As I travel through our Coldwell Banker Preferred branch offices, I hear many agents ask me the same question over and over: What can we
Frequently Asked Questions: Cisco Jabber 9.x for Android
 Frequently Asked Questions Frequently Asked Questions: Cisco Jabber 9.x for Android Frequently Asked Questions (FAQs) 2 Setup 2 Basics 4 Connectivity 8 Calls 9 Contacts and Directory Search 14 Voicemail
Frequently Asked Questions Frequently Asked Questions: Cisco Jabber 9.x for Android Frequently Asked Questions (FAQs) 2 Setup 2 Basics 4 Connectivity 8 Calls 9 Contacts and Directory Search 14 Voicemail
Taylor & Francis Online Mobile FAQs
 Taylor & Francis Online Mobile FAQs ACCESS Q. How do I access Taylor & Francis Online Mobile? A. Open the browser on your mobile device and enter the URL www.tandfonline.com. As you are accessing the site
Taylor & Francis Online Mobile FAQs ACCESS Q. How do I access Taylor & Francis Online Mobile? A. Open the browser on your mobile device and enter the URL www.tandfonline.com. As you are accessing the site
Protect yourself online
 Protect yourself online Advice from Nottinghamshire Police s Pre Crime Unit Get daily updates: www.nottinghamshire.police.uk www.twitter.com/nottspolice www.facebook.com/nottspolice www.youtube.com/nottinghampolice
Protect yourself online Advice from Nottinghamshire Police s Pre Crime Unit Get daily updates: www.nottinghamshire.police.uk www.twitter.com/nottspolice www.facebook.com/nottspolice www.youtube.com/nottinghampolice
Create your portal account, and connect to your medical records.
 Create your portal account, and connect to your medical records. Follow these steps if you have not received an email invitation to register. Any questions, please email us at [email protected]
Create your portal account, and connect to your medical records. Follow these steps if you have not received an email invitation to register. Any questions, please email us at [email protected]
IntelliPay Billpay Application Documentation
 IntelliPay Billpay Application Documentation Contents Billpay Introduction First Time Payment (With username and password) First Time Payment (Without username and password) Returning Customer Introduction:
IntelliPay Billpay Application Documentation Contents Billpay Introduction First Time Payment (With username and password) First Time Payment (Without username and password) Returning Customer Introduction:
Social Media and Cyber Safety
 Social Media and Cyber Safety Presented to the National Association of REALTORS by Andrew Wooten Safety and Security Consultant [email protected] Social Media and Cyber Safety Our instructor today
Social Media and Cyber Safety Presented to the National Association of REALTORS by Andrew Wooten Safety and Security Consultant [email protected] Social Media and Cyber Safety Our instructor today
Defense Media Activity Guide To Keeping Your Social Media Accounts Secure
 Guide To Keeping Your Social Media Accounts Secure Social media is an integral part of the strategic communications and public affairs missions of the Department of Defense. Like any asset, it is something
Guide To Keeping Your Social Media Accounts Secure Social media is an integral part of the strategic communications and public affairs missions of the Department of Defense. Like any asset, it is something
MathXL Getting Started Guide for Students
 MathXL Getting Started Guide for Students Copyright Notice Copyright 2013 by Pearson Education. All rights reserved. No part of the contents of this book may be reproduced or transmitted in any form or
MathXL Getting Started Guide for Students Copyright Notice Copyright 2013 by Pearson Education. All rights reserved. No part of the contents of this book may be reproduced or transmitted in any form or
Email and Security. U3A Radlett Computer Group Meeting 6-Oct-2014 V1.1
 Email and Security U3A Radlett Computer Group Meeting 6-Oct-2014 V1.1 Agenda Introduction Email Security Q&A Introduction Gary Harding email:- [email protected] Spent more than 40 years working in the
Email and Security U3A Radlett Computer Group Meeting 6-Oct-2014 V1.1 Agenda Introduction Email Security Q&A Introduction Gary Harding email:- [email protected] Spent more than 40 years working in the
User Guide. Copyright 2003 Networks Associates Technology, Inc. All Rights Reserved.
 Copyright 2003 Networks Associates Technology, Inc. All Rights Reserved. Table of Contents Getting Started... 4 New Features... 4 System Requirements... 4 Configuring Microsoft Internet Explorer... 4 Configuring
Copyright 2003 Networks Associates Technology, Inc. All Rights Reserved. Table of Contents Getting Started... 4 New Features... 4 System Requirements... 4 Configuring Microsoft Internet Explorer... 4 Configuring
Follow these easy instructions to list your business on the BEC Australia National Business Directory.
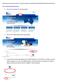 Follow these easy instructions to list your business on the BEC Australia National Business Directory. Go to www.becaustralia.org.au 1. Click on the Directory tab (see below) 2. Click on the Add listing
Follow these easy instructions to list your business on the BEC Australia National Business Directory. Go to www.becaustralia.org.au 1. Click on the Directory tab (see below) 2. Click on the Add listing
Grand Blanc Community Schools
 Mailbox Quotas August 1, 2012 Grand Blanc Community Schools The District s Exchange server is in need of software updates in order to maximize server performance. There is not enough space on the server
Mailbox Quotas August 1, 2012 Grand Blanc Community Schools The District s Exchange server is in need of software updates in order to maximize server performance. There is not enough space on the server
THE LITTLE BIG BOOK OF BADNESS
 THE LITTLE BIG BOOK OF BADNESS How to stay safe on the Internet a guidebook for students and parents USE THIS BOOK TO FIND OUT HOW YOU AND YOUR COMPUTER CAN STAY AWAY FROM BAD THINGS 2 CONTENTS Why you
THE LITTLE BIG BOOK OF BADNESS How to stay safe on the Internet a guidebook for students and parents USE THIS BOOK TO FIND OUT HOW YOU AND YOUR COMPUTER CAN STAY AWAY FROM BAD THINGS 2 CONTENTS Why you
Privacy Policy. If you have questions or complaints regarding our Privacy Policy or practices, please see Contact Us. Introduction
 Privacy Policy This Privacy Policy will be effective from September 1 st, 2014. Please read Pelican Technologies Privacy Policy before using Pelican Technologies services because it will tell you how we
Privacy Policy This Privacy Policy will be effective from September 1 st, 2014. Please read Pelican Technologies Privacy Policy before using Pelican Technologies services because it will tell you how we
General Security Best Practices
 General Security Best Practices 1. One of the strongest physical security measures for a computer or server is a locked door. 2. Whenever you step away from your workstation, get into the habit of locking
General Security Best Practices 1. One of the strongest physical security measures for a computer or server is a locked door. 2. Whenever you step away from your workstation, get into the habit of locking
Online Safety for Middle and High School
 Online Safety for Middle and High School Presented by Warren County Schools Technology Department 2010-2011 Internet & Technology Safety The purpose of this presentation is to TEACH YOU about INTERNET
Online Safety for Middle and High School Presented by Warren County Schools Technology Department 2010-2011 Internet & Technology Safety The purpose of this presentation is to TEACH YOU about INTERNET
Annual HIPAA Security & Information Security Competency
 Annual HIPAA Security & Information Security Competency 1 General Information FISO- What is a FISO? Facility Information Security Officer Responsible for the physical protection and recovery of all electronic
Annual HIPAA Security & Information Security Competency 1 General Information FISO- What is a FISO? Facility Information Security Officer Responsible for the physical protection and recovery of all electronic
HOMEBANKING ISSUE WITH INTERNET EXPLORER
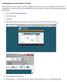 HOMEBANKING ISSUE WITH INTERNET EXPLORER Internet Explorer has made a change in their latest upgrade that has caused an issue when viewing balances and histories in Homebanking. If you are able to log
HOMEBANKING ISSUE WITH INTERNET EXPLORER Internet Explorer has made a change in their latest upgrade that has caused an issue when viewing balances and histories in Homebanking. If you are able to log
How to get started with Microsoft SkyDrive
 How to get started with Microsoft SkyDrive Blog Post Date: August 27, 2012 Category: Technology made easy Author: Ulrika Hedlund Source: http://www.businessproductivity.com/how-to-get-started-with-microsoft-skydrive
How to get started with Microsoft SkyDrive Blog Post Date: August 27, 2012 Category: Technology made easy Author: Ulrika Hedlund Source: http://www.businessproductivity.com/how-to-get-started-with-microsoft-skydrive
Website in a box 2.0 Users Guide. Contact: [email protected] Website: www.healthwatch.co.uk/website-in-a-box
 Website in a box 2.0 Users Guide Contact: [email protected] Website: www.healthwatch.co.uk/website-in-a-box Welcome to the new website in a box. We ve created a new, lighter, fresher and more
Website in a box 2.0 Users Guide Contact: [email protected] Website: www.healthwatch.co.uk/website-in-a-box Welcome to the new website in a box. We ve created a new, lighter, fresher and more
At the most basic level you need two things, namely: You need an IMAP email account and you need an authorized email source.
 Submit Social Updates via Email For Those In a Hurry, Here Are The Basic Setup Instructions At the most basic level you need two things, namely: You need an IMAP email account and you need an authorized
Submit Social Updates via Email For Those In a Hurry, Here Are The Basic Setup Instructions At the most basic level you need two things, namely: You need an IMAP email account and you need an authorized
User Guide for Kelani Mail
 User Guide for Kelani Mail Table of Contents Log in to Kelani Mail 1 Using Kelani Mail 1 Changing Password 2 Using Mail Application 3 Using email system folders 3 Managing Your Mail 4 Using your Junk folder
User Guide for Kelani Mail Table of Contents Log in to Kelani Mail 1 Using Kelani Mail 1 Changing Password 2 Using Mail Application 3 Using email system folders 3 Managing Your Mail 4 Using your Junk folder
Anonymity on the Internet Over Proxy Servers
 Anonymity on the Internet Over Proxy Servers Final Product Fábio Rodrigues [email protected] Matej Bulić [email protected] Introduction user always leaves digital sign need for security and anonymity Proxy
Anonymity on the Internet Over Proxy Servers Final Product Fábio Rodrigues [email protected] Matej Bulić [email protected] Introduction user always leaves digital sign need for security and anonymity Proxy
2015 Janrain Consumer Research UK, France, and Germany Consumer Identity and Mistargeting. Identity-Driven Marketing
 2015 Janrain Consumer Research UK, France, and Germany Consumer Identity and Mistargeting Identity-Driven Marketing Mistargeting continues to be ubiquitous and drives disengagement. DESPITE A MANTRA OF
2015 Janrain Consumer Research UK, France, and Germany Consumer Identity and Mistargeting Identity-Driven Marketing Mistargeting continues to be ubiquitous and drives disengagement. DESPITE A MANTRA OF
Today s mobile ecosystem means shared responsibility
 It seems just about everybody has a mobile phone now, including more than three-quarters of U.S. teens and a rapidly growing number of younger kids. For young people as well as adults, the technology has
It seems just about everybody has a mobile phone now, including more than three-quarters of U.S. teens and a rapidly growing number of younger kids. For young people as well as adults, the technology has
ABC PRIVACY POLICY. The ABC is strongly committed to protecting your privacy when you interact with us, our content, products and services.
 ABC PRIVACY POLICY The ABC is strongly committed to protecting your privacy when you interact with us, our content, products and services. Our goal is to provide you and your family with media experiences
ABC PRIVACY POLICY The ABC is strongly committed to protecting your privacy when you interact with us, our content, products and services. Our goal is to provide you and your family with media experiences
Chapter 15: Computer Security and Privacy
 Understanding Computers Today and Tomorrow 12 th Edition Chapter 15: Computer Security and Privacy Learning Objectives Explain why all computer users should be concerned about computer security. List some
Understanding Computers Today and Tomorrow 12 th Edition Chapter 15: Computer Security and Privacy Learning Objectives Explain why all computer users should be concerned about computer security. List some
Mtivity Client Support System. Quick start guide
 Mtivity Client Support System Quick start guide Mtivity Client Support System We are very pleased to announce the launch of a new Client Support System for Mtivity. The new Client Support System will provide
Mtivity Client Support System Quick start guide Mtivity Client Support System We are very pleased to announce the launch of a new Client Support System for Mtivity. The new Client Support System will provide
1. Open up your Internet browser and go to https://hootsuite.com
 HootSuite Tutorial HootSuite is an excellent social media management website. Through HootSuite you can track things like when your Twitter account (called a handle ) is mentioned by another Twitter user,
HootSuite Tutorial HootSuite is an excellent social media management website. Through HootSuite you can track things like when your Twitter account (called a handle ) is mentioned by another Twitter user,
EVENT MANAGEMENT CENTER GUIDE
 American Cancer Society How To: EMC Guide EVENT MANAGEMENT CENTER GUIDE Welcome to the American Cancer Society s Comprehensive Website Management Guide. This Guide is broken out into two main parts the
American Cancer Society How To: EMC Guide EVENT MANAGEMENT CENTER GUIDE Welcome to the American Cancer Society s Comprehensive Website Management Guide. This Guide is broken out into two main parts the
School Bullying Survey
 School Bullying Survey This survey is not required for your class. If you choose not to complete this survey, your grade in the class will not be affected in any way. If this is your decision, just leave
School Bullying Survey This survey is not required for your class. If you choose not to complete this survey, your grade in the class will not be affected in any way. If this is your decision, just leave
HITC elearning Modules Quickstart Guide
 HITC elearning Modules Quickstart Guide This Quickstart Guide has been designed to help you access the Hamad International Training Center (HITC) elearning platform and course content. The Online Learning
HITC elearning Modules Quickstart Guide This Quickstart Guide has been designed to help you access the Hamad International Training Center (HITC) elearning platform and course content. The Online Learning
Do I need anything special to use it? All you need to use Twitter is an Internet connection or a mobile phone with Internet capability.
 Twitter Guide What is Twitter? Twitter is a real-time communication platform that allows you to quickly share thoughts, opinions, and interesting links with friends, family, and the general public. People
Twitter Guide What is Twitter? Twitter is a real-time communication platform that allows you to quickly share thoughts, opinions, and interesting links with friends, family, and the general public. People
THE 10 MOST POWERFUL CHANGES THAT WILL INCREASE SALES IN YOUR COMPANY IMMEDIATELY!
 THE 10 MOST POWERFUL CHANGES THAT WILL INCREASE SALES IN YOUR COMPANY IMMEDIATELY! LEADS X CONVERSIONS = SALES Most companies put all their efforts into generating more leads to generate more sales. In
THE 10 MOST POWERFUL CHANGES THAT WILL INCREASE SALES IN YOUR COMPANY IMMEDIATELY! LEADS X CONVERSIONS = SALES Most companies put all their efforts into generating more leads to generate more sales. In
Anonymity, Privacy, and Security Online
 www.pewresearch.org SEPTEMBER 5, 2013 Anonymity, Privacy, and Security Online 86% of adult internet users have taken steps from time to time to avoid surveillance by other people or organizations when
www.pewresearch.org SEPTEMBER 5, 2013 Anonymity, Privacy, and Security Online 86% of adult internet users have taken steps from time to time to avoid surveillance by other people or organizations when
A Publication of the GCPS Information Management Division
 GCPS A Publication of the GCPS Information Management Division Gwinnett County Public Schools is committed to providing information related to student technology use in a manner that is clear, concise,
GCPS A Publication of the GCPS Information Management Division Gwinnett County Public Schools is committed to providing information related to student technology use in a manner that is clear, concise,
Using the My HUgo Portal
 Using the My HUgo Portal Before you log in It is important that your browser is set to allow cookies from Hodges, otherwise you will not be able to log in to My HUgo. In Internet Explorer, go to the Tools
Using the My HUgo Portal Before you log in It is important that your browser is set to allow cookies from Hodges, otherwise you will not be able to log in to My HUgo. In Internet Explorer, go to the Tools
BlackBerry World Storefront. Version: 4.3. User Guide
 BlackBerry World Storefront Version: 4.3 User Guide Published: 2013-02-21 SWD-20130221142618627 Contents About BlackBerry World... 5 New features and enhancements... 6 Browsing and searching... 7 Search
BlackBerry World Storefront Version: 4.3 User Guide Published: 2013-02-21 SWD-20130221142618627 Contents About BlackBerry World... 5 New features and enhancements... 6 Browsing and searching... 7 Search
How do I share a file with a friend or trusted associate?
 Sharing Information How do I share a file with a friend or trusted associate? Sharing a file in InformationSAFE is easy. The share utility in InformationSAFE allows you to securely share your information
Sharing Information How do I share a file with a friend or trusted associate? Sharing a file in InformationSAFE is easy. The share utility in InformationSAFE allows you to securely share your information
Why Your Local Business Needs a Website
 Why Your Local Business Needs a Website Let's face it; times have changed and the way people look for new products and services has changed. Think about it when was the last time you picked up a phone
Why Your Local Business Needs a Website Let's face it; times have changed and the way people look for new products and services has changed. Think about it when was the last time you picked up a phone
girlsdrivebetter.com is a trading style of Policywise Ltd, a limited liability company registered in England and Wales number 8107294.
 COOKIE POLICY In this section you will find information on what cookies may be set when you visit our website and how to reject or delete those cookies. When we provide services, we want to make them easy,
COOKIE POLICY In this section you will find information on what cookies may be set when you visit our website and how to reject or delete those cookies. When we provide services, we want to make them easy,
Privacy Policy Last Updated September 10, 2015
 Privacy Policy Last Updated September 10, 2015 Tanger Properties Limited Partnership d/b/a Tanger Outlets or Tanger Outlet Centers ("Tanger," "we" or us ), which includes affiliated companies owned or
Privacy Policy Last Updated September 10, 2015 Tanger Properties Limited Partnership d/b/a Tanger Outlets or Tanger Outlet Centers ("Tanger," "we" or us ), which includes affiliated companies owned or
SCRIPT: Security Training
 SCRIPT: Security Training Slide Name Introduction Overview 1 Overview 2 Overview 3 Text Welcome to the MN WIC Program Security Training Module for all MN WIC Program staff provided by the MN Department
SCRIPT: Security Training Slide Name Introduction Overview 1 Overview 2 Overview 3 Text Welcome to the MN WIC Program Security Training Module for all MN WIC Program staff provided by the MN Department
MEETINGONE ONLINE ACCOUNT MANAGEMENT PORTAL ACCOUNT ADMIN USER GUIDE
 MEETINGONE ONLINE ACCOUNT MANAGEMENT PORTAL ACCOUNT ADMIN USER GUIDE CONTENTS Description of Roles... 4 How to Login... 4 Select a Role... 5 Overview of Tabs... 6 Home Tab... 7 Account Profile Tab... 7
MEETINGONE ONLINE ACCOUNT MANAGEMENT PORTAL ACCOUNT ADMIN USER GUIDE CONTENTS Description of Roles... 4 How to Login... 4 Select a Role... 5 Overview of Tabs... 6 Home Tab... 7 Account Profile Tab... 7
nctv.com Email Quick Start Guide
 nctv.com Email Quick Start Guide Your new webmail is now powered by Contents If you are forwarding your nctv.com email to a third party address...2 If you use an email program other than Webmail from nctv.com..5
nctv.com Email Quick Start Guide Your new webmail is now powered by Contents If you are forwarding your nctv.com email to a third party address...2 If you use an email program other than Webmail from nctv.com..5
The Digital Divide: How the Online Behavior of Teens is Getting Past Parents
 June 2012 The Digital Divide: How the Online Behavior of Teens is Getting Past Parents Parent Disconnect Despite the obvious disconnect between teens online behaviors and parents knowledge of them, parents
June 2012 The Digital Divide: How the Online Behavior of Teens is Getting Past Parents Parent Disconnect Despite the obvious disconnect between teens online behaviors and parents knowledge of them, parents
