Simple Tabletop Exercise, Cyber Security Breach Unusual Water Quality Scenario Scenario #3 Facilitator s Guide
|
|
|
- Polly Burke
- 8 years ago
- Views:
Transcription
1 Simple Tabletop Exercise, Cyber Security Breach Unusual Water Quality Scenario Scenario #3 Facilitator s Guide Scenario Summary Background: It is summer in Zenith City. The end of the city s fiscal year is approaching, and budgetary cutbacks within the city and the water department have resulted in several city employees being laid off. The Event: A water (or wastewater) utility worker, angry that he has lost his job, realizes that he is still able to dial-in to the Zenith City Water (or Wastewater) Treatment Plant s SCADA system. He decides to infect the SCADA system with a computer virus to cause system malfunctions. The Results: The SCADA system begins to issue alarms that inform operators that various systems in the treatment process are malfunctioning, and that water (or wastewater) leaving the treatment plant is not meeting water quality standards for drinking (or discharge). The SCADA system also reports malfunctions with the process flow routing and chemical feed rates. To the Facilitator: Because these alarms are computer virus-induced, they do not reflect the actual operation of the system. However, the exercise participants will not be aware of this fact until later in the exercise. This exercise is intended to generate discussion among the utilities represented regarding security procedures and protocols for SCADA systems and to gauge how confident personnel feel in operating their utilities without the aid of SCADA systems. This exercise may be run for either water or wastewater utility personnel, and appropriate suggestions for injects based on the exercise participants are included throughout this guide. In general, the terminology to be used for a wastewater audience can be found in parentheses immediately following the drinking water terminology. See the description for Inject #1 below for an example. Intended Participants: This exercise may be run for water supply, wastewater operators, public health, state drinking water primacy agencies, federal agencies such as EPA and Federal Bureau of Investigation (FBI), local law enforcement, and fire/emergency medical services (EMS) personnel. Page 1 of 8
2 You may wish to consider inviting: Water/Wastewater Utility Managers, Emergency Response Public Utilities: Team Members, Utility Operators, IT/SCADA Operators, Engineers, Sampling Staff, Administrative Staff Emergency Room staff, Physicians, Nurses and Nurse Hospital: Practitioners, Hospital Administrators, Medical Laboratory staff, Public Information Officer Health Officers, Epidemiologists, Technical Specialists, Public Health: Public Information Officer Fire Dept., HazMat and Fire Fighters, HazMat Team members, EMS workers, EMS: 911 Call Center workers Police: Police Officers, Counter-Terrorism Specialists Laboratory: Analysts / Technicians, Laboratory Administrators Mayor and Elected Officials, City Council Members, Local Local Officials: Emergency Planning Committee (LEPC) Members, Local Emergency Management Agency staff State Environmental Agency Staff, State Health Department Staff, State Drinking Water Primacy Agency, State State Officials: Emergency Management Agency, Governer's Office Representatives Federal Officials: EPA staff, FBI staff, FEMA staff, CDC staff, DHS staff Specifically, water and/or wastewater utility personnel, water and wastewater utility Information Technology (IT) personnel (if applicable), representative(s) from the utility s contracted IT firm or service (if applicable) should be included in this exercise. Running the Exercise Step 1: Decide on a facility, training date, training duration, and who to invite. Invite participants well in advance of your training date to ensure that you can achieve your attendance goal. Allow adequate time for planning and be sure to prepare all materials (digital and hard copy) ahead of time. Step 2: Depending on who is participating in this exercise, it may be a good idea to have the participants go around the table and introduce themselves (name, utility, and job title) so that everyone will understand where any particular individual is coming from during the ensuing discussions. Step 3: Explain to the participants that they are participating in a simple tabletop exercise, there is no time pressure, and that they are there as a group to discuss their roles and responses to an emergency incident. There are no right or wrong answers, but the group should be able to discuss problem or gray areas that may arise during the exercise. Let them know this is good, as the exercise should stimulate discussion that may lead to changes in the way the participants conduct their daily and emergency operations. Also inform the participants that, although the incident is set in fictional Page 2 of 8
3 Zenith City, it is okay to talk about the incident from their own experiences or in the context of their own protocols and procedures. It will make the exercise more beneficial for the participants if they exchange emergency response practices, protocols, and procedures that they may currently use. Step 4: Be sure to give the background PowerPoint presentation to introduce the participants to Zenith City and to set the stage for the incident. The exercise goals will also be presented as a part of this presentation. Step 5: Begin the exercise by delivering the first inject. Then, let the discussion evolve naturally on its own after giving the participants the first inject. If necessary, to get the discussion started, simply nudge the participants with a non-leading question such as: What would you do in this situation? You could direct this question to the group at large, or, in a group where no one is willing to break the ice, to a particular individual, preferably one that you know serves in a leadership role during the course of their daily activities. You can also refer to the discussion points in the Facilitator s Guide to help jump-start discussion. Step 6: Be sure to take notes during the discussions. These notes will form the basis of your after-action review. Note problem or gray areas that need more research prior to resolution and who will perform this research or any action items decided upon by the participants. The notes you take will ensure that a summary of the take-home points, action items or messages will not be forgotten or overlooked. You may wish to write these points, action items and messages on a flip chart at the end of the exercise. Step 7: Perform an after-action review. You may wish to give the participants a 10 to 15 minute break at the end of the exercise to give yourself time to compose your notes prior to conducting the review. Be sure to review the exercise objectives again to determine if the objectives were met by the exercise. Allow the participants to give their feedback on the exercise and the conclusions or decisions that they arrived at during the exercise. The entire tabletop exercise, including the after-action review, can typically be conducted in a two to four hour session. This time range is flexible and is dependant on the amount of discussion generated during the exercise. The pace of the exercise is controlled entirely by the facilitator, who manages the discussions and presents the injects. Page 3 of 8
4 Discussion Points Remember, this scenario begins after the end of the city s fiscal year, and budgetary cutbacks within the city and the water department have resulted in several city employees not being able to return to work. A water (or wastewater) utility worker, angry that he has lost his job, realizes that he is still able to dial-in to the Zenith City Water (or Wastewater) Treatment Plant s SCADA system. He decides to infect the SCADA system with a virus that will make it malfunction. Exercise participants are provided a map of Zenith City, a water supply distribution map, a wastewater distribution map, and other pertinent materials. If this exercise is to be customized, all these materials may be substituted with a utility s own maps and other materials. Use injects labeled with an a for a water utility audience and injects labeled with a b for a wastewater utility audience. Inject #1 (10:00 hrs., July 10, Material Code(s) SSc3-1a or SSc3-1b): The SCADA system alerts the operator that two high-lift pumps (or blowers if the exercise involves wastewater personnel) are not operational. The flow meter (or oxygen monitor) indicates that all is normal. Points that could be covered in the discussion of Inject #1 include: What is the procedure used to manually/visually inspect the pumps (or blower)? Where is this procedure or policy written and kept? Does anyone need to be notified? What do you do if the person you need to notify is out on vacation? Does it matter if this alarm occurs after business hours? Inject #2 (10:10 hrs., July 10, Material Code(s) SSc3-2a or SSc3-2b): A physical check of the high lift pumps (or blowers) shows that they are operational. Points that could be covered in the discussion of Inject #2 include: How do you know if the pumps (or blower) are operating at the correct rates? Do you assume that the flow meter (or oxygen monitor) is operating correctly? What is the appropriate evaluation and repair procedure for high-lift pump monitors within the SCADA system? Who is in charge of ensuring that the repair is made? Page 4 of 8
5 Inject #3 (10:23 hrs., July 10, Material Code(s) SSc3-3a or SSc3-3b): The SCADA system alerts the operator that the chlorinator is not working properly, which may lead to out-of-compliance water quality standards. The residual analyzer indicates that nothing is wrong. Points that could be covered in the discussion of Inject #3 include: What is the procedure used to inspect the chlorinator? How often are personnel trained in this procedure? Is there a checklist to take personnel through this procedure? How often are personnel trained in any procedure involving troubleshooting the SCADA system? What is the back-up plan if the person who knows the SCADA system best is out of town or otherwise not available? Inject #4 (10:30 hrs., July 10, Material Code(s) SSc3-4a or SSc3-4b): A physical check of the chlorinator shows that it is operational. Points that could be covered in the discussion of Inject #4 include: How do you know that the chlorinator is feeding the right amount of chlorine? How much do you trust the residual monitor and the entire SCADA system after the occurrence of what appear to be two false alarms? When would sampling be performed to independently verify what the SCADA system is telling you? Inject # 5 (10:37 hrs., July 10, Material Code(s) SSc3-5a or SSc3-5b): Results of grab water sample (indicating that chlorine residual level is within normal range). Points that could be covered in the discussion of Inject # 5 include: Is this enough information to assume that the SCADA system is giving false alarms? Who would be notified at this point? If there is not a full-time Information Technology (IT) staff member, how quickly could the contractor respond to examine the SCADA system? What exactly would be done at this point? Page 5 of 8
6 Inject #6 (10:47 hrs., July 10, Material Code(s) SSc3-6a or SSc3-6b): The SCADA system alerts the operator again that the chlorinator is not feeding properly, raising the risk for a second time (within a matter of minutes) that water may be exiting the plant that does not meet water quality standards. Points that could be covered in the discussion of Inject #6 include: Why might the SCADA system be alerting the operator yet again that the chlorine feed is not operating properly? What do the plant s policies or guidelines say to do in this situation? Is water quality sampling being performed to ensure that water leaving the plant meets water quality and/or permit guidelines? Are sampling points pre-determined? If not, how do you decide where to sample? Inject #7 (11:00 hrs., July 10, Material Code(s) SSc3-7a or SSc3-7b): A physical check of the chlorinator shows that it appears to be operational. Points that could be covered in the discussion of Inject #7 include: Would you sample again for chlorine residual (this was just done 20 minutes ago)? When is the call made to not use the SCADA system and to go to manual control? How often does the utility train to operate the system manually? What is the procedure to shift to manual control? Unplug the SCADA? Are there any back-up systems that may be employed independent of the SCADA system? When do you ask for help from Information Technology (IT)? Do you begin to consider that an intentional disruption of the SCADA system is possible? What types of information would you need to gather to make that determination? Page 6 of 8
7 Inject #8 (11:15 hrs., July 10, Material Code(s) SSc3-8a or SSc3-8b): The utility s IT person or IT contractor has discovered that Eric Harwood, a young utility employee recently laid off due to budget cutbacks, accessed the SCADA system remotely after his layoff. Points that could be covered in the discussion of Inject #8 include: Who has access to the SCADA system and at what security levels may they access the system? Is there a written policy governing SCADA access? What are the utility s security procedures and protocols governing SCADA systems? Have they been updated since 9/11? Have they been updated within the context of the new National Response Plan (NRP) and National Incident Management System (NIMS)? Why or why not? What are the in and out-processing requirements when a new employee is hired or leaves, whether it is a voluntary or non-voluntary separation? Are passwords, log-ins, and accounts cancelled and reassigned? Does the fact that the SCADA system was accessed remotely by a former employee lead you to deem this threat credible? What types of information would you need to confirm this threat? Inject #9 (11:48 hrs., July 10, Material Code(s) SSc3-9a or SSc3-9b): The utility s IT person or contractor cannot pinpoint any definitive problem with the SCADA s systems software. In the meantime, the SCADA system has warned of another high-lift pump (or blower) failure. A virus is suspected. Points that could be covered in the discussion of Inject #9 include: Based on the knowledge that Eric Harwood was laid off, that he accessed the SCADA system after being laid off, he was upset about his layoff, and the bizarre behavior of the SCADA system which the IT professional says could be a virus, is it time to notify law enforcement? (Note: As a facilitator, you may wish to reemphasize with the participants that it is now a federal crime to threaten or tamper with a public drinking water system.) In light of this new information, what would your immediate response actions be? With a suspected virus, is it just better and safer to run the entire operation manually? Is this possible? What pros and cons need to be balanced in terms of making a decision to operate completely manually versus continuing to use the SCADA and risking the virus affecting some previously unaffected utility component, some other interconnected system or water or effluent quality? Can the participating utilities run their system manually? How many times has this been trained? Is a written procedure or checklist in place to do this? Page 7 of 8
8 Inject #10 (13:00 hrs., July 10, Material Code(s) SSc3-10a or SSc3-10b): Eric Harwood s former supervisor, upon hearing that the problems with the SCADA system may be virus-related and connected to Eric, steps forward to let the water or wastewater superintendent know that he isn t sure if Eric returned his keys to anyone when he left. Points that could be covered in the discussion of Inject #10 include: What is the utility s key control policy? Can keys be easily copied? How often are locks changed? Is it possible that Eric did more than just plant a virus within the SCADA system? Should a physical check of all major plant processes and chemicals be undertaken? Who s in charge of inactivating user names and passwords as personnel changes occur? Inject # 11 (15:27 hrs., July 10, Material Code(s) SSc3-11a or SSc3-11b): The police, who are looking for Eric for questioning, notify the water or wastewater superintendent that Eric has a criminal record. Points that could be covered in the discussion of Inject #11 include: How does this change the utility s view of the situation in terms of urgency and seriousness? Do the participating utilities have a requirement for a criminal background check of their employees or are they considering instituting such a requirement? Page 8 of 8
Simple Tabletop Exercise, Interdependency Natural Disaster Scenario Scenario #8 Facilitator s Guide
 Simple Tabletop Exercise, Interdependency Natural Disaster Scenario Scenario #8 Facilitator s Guide Scenario Summary Background: It is March in Zenith City and the residents are experiencing a cold spring.
Simple Tabletop Exercise, Interdependency Natural Disaster Scenario Scenario #8 Facilitator s Guide Scenario Summary Background: It is March in Zenith City and the residents are experiencing a cold spring.
GUIDANCE FOR WATER UTILITY RESPONSE, RECOVERY & REMEDIATION ACTIONS FOR MAN-MADE AND/OR TECHNOLOGICAL EMERGENCIES
 Office of Water (4601M) EPA 810-R-02-001 www.epa.gov/safewater April 2002 GUIDANCE FOR WATER UTILITY RESPONSE, RECOVERY & REMEDIATION FOR MAN-MADE AND/OR TECHNOLOGICAL EMERGENCIES DISCLAIMER The statements
Office of Water (4601M) EPA 810-R-02-001 www.epa.gov/safewater April 2002 GUIDANCE FOR WATER UTILITY RESPONSE, RECOVERY & REMEDIATION FOR MAN-MADE AND/OR TECHNOLOGICAL EMERGENCIES DISCLAIMER The statements
Missouri Department of Natural Resources Public Drinking Water Branch 1-800-361-4827 or (573) 751-5331
 Missouri Department of Natural Resources Public Drinking Water Branch 1-800-361-4827 or (573) 751-5331 U.S. Environmental Protection Agency s Water Security Handbook: Planning for and Responding to Drinking
Missouri Department of Natural Resources Public Drinking Water Branch 1-800-361-4827 or (573) 751-5331 U.S. Environmental Protection Agency s Water Security Handbook: Planning for and Responding to Drinking
A Water Security Handbook: Planning for and Responding to Drinking Water Contamination Threats and Incidents
 A : Planning for and Responding to Drinking Water Contamination Threats and Incidents Water Security Incidents Threats Printed on Recycled Paper Note to Readers: The U.S. Environmental Protection Agency
A : Planning for and Responding to Drinking Water Contamination Threats and Incidents Water Security Incidents Threats Printed on Recycled Paper Note to Readers: The U.S. Environmental Protection Agency
Site Attendance Guidelines for Automated/Unattended Monitoring and Process Controlled Facilities
 Site Attendance Guidelines for Automated/Unattended Monitoring and Process Controlled Facilities June 2015 EPB #428 The guidelines will be revised and updated as new information warrants change. Please
Site Attendance Guidelines for Automated/Unattended Monitoring and Process Controlled Facilities June 2015 EPB #428 The guidelines will be revised and updated as new information warrants change. Please
Module 14 Handling Emergency Situations
 Handling Emergency Situations The Shift Lead protects the team, customers and restaurant by monitoring safety. However, you cannot always prevent problems. Sometimes, things happen that you were not expecting
Handling Emergency Situations The Shift Lead protects the team, customers and restaurant by monitoring safety. However, you cannot always prevent problems. Sometimes, things happen that you were not expecting
SAFETY GUIDANCE MATERIAL
 SAFETY GUIDANCE MATERIAL SAFETY MANAGEMENT MONDAY MARCH 23,GUIDANCE 2015 This safety resource was written for the scrap industry by the scrap industry and was developed to assist you in making your scrap
SAFETY GUIDANCE MATERIAL SAFETY MANAGEMENT MONDAY MARCH 23,GUIDANCE 2015 This safety resource was written for the scrap industry by the scrap industry and was developed to assist you in making your scrap
APPENDIX G-Emergency Response Plan Template
 APPENDIX G-Emergency Response Plan Template BSDW-ERP Template 10/04 EMERGENCY RESPONSE PLAN WATER SECTOR Public Water System Name: PWSID No: Physical Address: City: State: Zip Code: General Phone Number:
APPENDIX G-Emergency Response Plan Template BSDW-ERP Template 10/04 EMERGENCY RESPONSE PLAN WATER SECTOR Public Water System Name: PWSID No: Physical Address: City: State: Zip Code: General Phone Number:
NEW HAMPSHIRE. Downloaded January 2011 HE P 803.08 NURSING HOME REQUIREMENTS FOR ORGANIZATIONAL CHANGES.
 NEW HAMPSHIRE Downloaded January 2011 HE P 803.08 NURSING HOME REQUIREMENTS FOR ORGANIZATIONAL CHANGES. (a) The nursing home shall provide the department with written notice at least 30 days prior to changes
NEW HAMPSHIRE Downloaded January 2011 HE P 803.08 NURSING HOME REQUIREMENTS FOR ORGANIZATIONAL CHANGES. (a) The nursing home shall provide the department with written notice at least 30 days prior to changes
RED FLAGS RULE. Identifying, Detecting, & Mitigating Possible Identity Theft
 RED FLAGS RULE Identifying, Detecting, & Mitigating Possible Identity Theft What is the Red Flag Rule? The Federal Trade Commission (FTC), along with federal bank regulators and the National Credit Union
RED FLAGS RULE Identifying, Detecting, & Mitigating Possible Identity Theft What is the Red Flag Rule? The Federal Trade Commission (FTC), along with federal bank regulators and the National Credit Union
Lessons Learned from a Basic Vulnerability Assessment and Emergency Response Plan Update Project in Greensboro
 Lessons Learned from a Basic Vulnerability Assessment and Emergency Response Plan Update Project in Greensboro Steve Drew, Director, Greensboro Water Resources Department Jack Moyer, Carolinas / Tennessee
Lessons Learned from a Basic Vulnerability Assessment and Emergency Response Plan Update Project in Greensboro Steve Drew, Director, Greensboro Water Resources Department Jack Moyer, Carolinas / Tennessee
Security Guidelines for. Agricultural distributors
 Security Guidelines for Agricultural distributors SECURITY GUIDELINES FOR AGRICULTURAL DISTRIBUTORS As a result of global uncertainties the security of agricultural retail facilities has taken on a whole
Security Guidelines for Agricultural distributors SECURITY GUIDELINES FOR AGRICULTURAL DISTRIBUTORS As a result of global uncertainties the security of agricultural retail facilities has taken on a whole
Child and Adult Care Food Program Sponsoring Organization
 BIOSECURITY / SECURITY CHECKLIST For the Food Service Director Child and Adult Care Food Program Sponsoring Organization Biosecurity and security are part of an all-hazards approach to Food Safety. BE
BIOSECURITY / SECURITY CHECKLIST For the Food Service Director Child and Adult Care Food Program Sponsoring Organization Biosecurity and security are part of an all-hazards approach to Food Safety. BE
WATER RESOURCES MANAGEMENT MASTER PROGRAM Water Utility Administration and Management Course LECTURE 13
 WATER RESOURCES MANAGEMENT MASTER PROGRAM Water Utility Administration and Management Course LECTURE 13 Water Service Crises and Emergency Management Dr. Nahed Ghbn, Eng. Rebhi El-Shiekh Palestinian Water
WATER RESOURCES MANAGEMENT MASTER PROGRAM Water Utility Administration and Management Course LECTURE 13 Water Service Crises and Emergency Management Dr. Nahed Ghbn, Eng. Rebhi El-Shiekh Palestinian Water
State of Iowa Juvenile Fire Intervention Program Program Delivery SOG
 PURPOSE: State of Iowa Juvenile Fire Intervention Program Date: January 2012 Page 1 of 13 This regulation establishes the responsibilities of the State of Iowa s Juvenile Fire Intervention Program and
PURPOSE: State of Iowa Juvenile Fire Intervention Program Date: January 2012 Page 1 of 13 This regulation establishes the responsibilities of the State of Iowa s Juvenile Fire Intervention Program and
Contingency Plan. Facility Name
 Contingency Plan Facility Name This plan is reviewed annually and amended whenever changes occur that will significantly affect the ability of this facility to respond to an emergency situation. This includes
Contingency Plan Facility Name This plan is reviewed annually and amended whenever changes occur that will significantly affect the ability of this facility to respond to an emergency situation. This includes
Office of Human Resources A Shared Service of DHS and OHA
 Office of Human Resources A Shared Service of DHS and OHA Policy Policy Title: Workplace Incident Response Policy Policy Number: 080-013 Version: 1.0 Effective Date: Upon Approval Approved for DHS by Jim
Office of Human Resources A Shared Service of DHS and OHA Policy Policy Title: Workplace Incident Response Policy Policy Number: 080-013 Version: 1.0 Effective Date: Upon Approval Approved for DHS by Jim
"DOT IN-DEPTH HAZMAT SECURITY TRAINING"
 PRESENTER'S GUIDE "DOT IN-DEPTH HAZMAT SECURITY TRAINING" For the Department of Transportation's 49 CFR 172.700 Subpart H Training Requirements Quality Safety and Health Products, for Today...and Tomorrow
PRESENTER'S GUIDE "DOT IN-DEPTH HAZMAT SECURITY TRAINING" For the Department of Transportation's 49 CFR 172.700 Subpart H Training Requirements Quality Safety and Health Products, for Today...and Tomorrow
Business Continuity Exercise: Electricity Supply Failure Appendix 4.4
 1 Business Continuity Exercise: Electricity Supply Failure Appendix 4.4 2 Housekeeping Fire safety Breaks and refreshments Toilets Mobiles and pagers 3 Introduction Respect each others contributions What
1 Business Continuity Exercise: Electricity Supply Failure Appendix 4.4 2 Housekeeping Fire safety Breaks and refreshments Toilets Mobiles and pagers 3 Introduction Respect each others contributions What
Red Flag Policy and Procedures for Alexander Orthopaedic Associates
 Red Flag Policy and Procedures for Alexander Orthopaedic Associates The Identify Theft Prevention Program developed by Alexander Medical Group LLC dba Alexander Orthopaedic Associates referred throughout
Red Flag Policy and Procedures for Alexander Orthopaedic Associates The Identify Theft Prevention Program developed by Alexander Medical Group LLC dba Alexander Orthopaedic Associates referred throughout
POINT UNIVERSITY CAMPUS SECURITY Emergency Response Plan
 POINT UNIVERSITY CAMPUS SECURITY Emergency Response Plan Introduction The Point University Emergency Response Plan establishes guidelines for campus-wide communication, service coordination and safety
POINT UNIVERSITY CAMPUS SECURITY Emergency Response Plan Introduction The Point University Emergency Response Plan establishes guidelines for campus-wide communication, service coordination and safety
Water Treatment Operator. Water Treatment Operator I - 30000146
 Water Treatment Operator FLSA Status: Bargaining Unit: Covered District Council of Trade Unions (DCTU) General Summary Positions in this broad class control and adjust water flow and chemical treatment
Water Treatment Operator FLSA Status: Bargaining Unit: Covered District Council of Trade Unions (DCTU) General Summary Positions in this broad class control and adjust water flow and chemical treatment
United States Environmental Protection Agency
 United States Environmental Protection Agency Emergency Response Plan Guidance for Small and Medium Community Water Systems to Comply with the Public Health Security and Bioterrorism Preparedness and Response
United States Environmental Protection Agency Emergency Response Plan Guidance for Small and Medium Community Water Systems to Comply with the Public Health Security and Bioterrorism Preparedness and Response
Select Agent Program Workshop November 16, 2012. Agricultural Select Agent Program (USDA/APHIS) CDC Select Agent Program (HHS/CDC)
 Select Agent Program Workshop November 16, 2012 Agricultural Select Agent Program (USDA/APHIS) CDC Select Agent Program (HHS/CDC) Revisions to Regulations 11 (a) through 11 (c)(7): (b) and (c)(2) changed
Select Agent Program Workshop November 16, 2012 Agricultural Select Agent Program (USDA/APHIS) CDC Select Agent Program (HHS/CDC) Revisions to Regulations 11 (a) through 11 (c)(7): (b) and (c)(2) changed
For the purpose of this chapter the following definitions shall apply:
 CHAPTER 110. ALARM SYSTEMS GENERAL PROVISIONS Sec. 110.01. Definitions. Secs. 110.02 110.14. Reserved. Sec. 110.01. - Definitions. For the purpose of this chapter the following definitions shall apply:
CHAPTER 110. ALARM SYSTEMS GENERAL PROVISIONS Sec. 110.01. Definitions. Secs. 110.02 110.14. Reserved. Sec. 110.01. - Definitions. For the purpose of this chapter the following definitions shall apply:
On-Site Risk Management Audit Checklist for Program Level 3 Process
 On-Site Risk Management Audit Checklist for Program Level 3 Process Auditor name: Date: I. Facility Information: Facility name: Facility location: County: Contact name: RMP Facility I.D. Phone Number:
On-Site Risk Management Audit Checklist for Program Level 3 Process Auditor name: Date: I. Facility Information: Facility name: Facility location: County: Contact name: RMP Facility I.D. Phone Number:
Fire Safety PROCEDURES January 2011
 Fire Safety PROCEDURES January 2011 firesafety@uwo.ca Campus Phones EMERGENCY Dial 911 Fire Safety Service is the focal point for the coordinated administration of the University Fire Safety program and
Fire Safety PROCEDURES January 2011 firesafety@uwo.ca Campus Phones EMERGENCY Dial 911 Fire Safety Service is the focal point for the coordinated administration of the University Fire Safety program and
Evacuation Procedures
 Evacuation Procedures CONTENTS Evacuation Procedures... 1 When Alarm Sounds... 2 Evacuation Routes... 2 Accounting for Employees/Visitors after Evacuation... 3 Emergency Contact Information... 3 Advanced
Evacuation Procedures CONTENTS Evacuation Procedures... 1 When Alarm Sounds... 2 Evacuation Routes... 2 Accounting for Employees/Visitors after Evacuation... 3 Emergency Contact Information... 3 Advanced
Inspection, Testing and Maintenance
 Page 18 ABOUT CODE CORNER CCFS would like to remind you to check with your local Authority Having Jurisdiction (AHJ) for questions and opinions concerning your local Fire and Building Codes. The information
Page 18 ABOUT CODE CORNER CCFS would like to remind you to check with your local Authority Having Jurisdiction (AHJ) for questions and opinions concerning your local Fire and Building Codes. The information
Emergencies and Incident Investigation FOR SCHOOLS
 Emergencies and Incident Investigation FOR SCHOOLS When an emergency occurs it is too late to decide who will do what, and what equipment you need. With your staff, plan how you will manage emergencies
Emergencies and Incident Investigation FOR SCHOOLS When an emergency occurs it is too late to decide who will do what, and what equipment you need. With your staff, plan how you will manage emergencies
Emergency Response Plan
 Emergency Response Plan Third revised version placed in the Public Document Repository on July 1, 2011 I certify under penalty of law that this document and all attachments were prepared under my direction
Emergency Response Plan Third revised version placed in the Public Document Repository on July 1, 2011 I certify under penalty of law that this document and all attachments were prepared under my direction
CITY OF BOULDER *** POLICIES AND PROCEDURES
 CITY OF BOULDER *** POLICIES AND PROCEDURES CONNECTED PARTNER EFFECTIVE DATE: SECURITY POLICY LAST REVISED: 12/2006 CHRISS PUCCIO, CITY IT DIRECTOR CONNECTED PARTNER SECURITY POLICY PAGE 1 OF 9 Table of
CITY OF BOULDER *** POLICIES AND PROCEDURES CONNECTED PARTNER EFFECTIVE DATE: SECURITY POLICY LAST REVISED: 12/2006 CHRISS PUCCIO, CITY IT DIRECTOR CONNECTED PARTNER SECURITY POLICY PAGE 1 OF 9 Table of
Emergency Response Plans. More than a phone tree Less than an encyclopedia Doing it just right
 Emergency Response Plans More than a phone tree Less than an encyclopedia Doing it just right Background For systems over 3,300 population (1,000 connections) an Emergency Response Plan (ERP) is required
Emergency Response Plans More than a phone tree Less than an encyclopedia Doing it just right Background For systems over 3,300 population (1,000 connections) an Emergency Response Plan (ERP) is required
Sam Houston State University
 Sam Houston State University Lowman Student Center EMERGENCY PROCEDURES July 2007 Emergency Procedures Found in this Document General Information for any Emergency Situation in the LSC...... 2 Vandalism,
Sam Houston State University Lowman Student Center EMERGENCY PROCEDURES July 2007 Emergency Procedures Found in this Document General Information for any Emergency Situation in the LSC...... 2 Vandalism,
Security Vulnerability Self-Assessment Guide for Small Drinking Water Systems
 Security Vulnerability Self-Assessment Guide for Small Drinking Water Systems Association of State Drinking Water Administrators National Rural Water Association May 30, 2002 A Note about Security for
Security Vulnerability Self-Assessment Guide for Small Drinking Water Systems Association of State Drinking Water Administrators National Rural Water Association May 30, 2002 A Note about Security for
This document contains the text of Secretary of the State regulations concerning
 1 This document contains the text of Secretary of the State regulations concerning Emergency Contingency Model Plan for Elections (Sections 9-174a-1 to 9-174a-34) This document was created by the Office
1 This document contains the text of Secretary of the State regulations concerning Emergency Contingency Model Plan for Elections (Sections 9-174a-1 to 9-174a-34) This document was created by the Office
GEARS Cyber-Security Services
 Florida Department of Management Services Division of State Purchasing Table of Contents Introduction... 1 About GEARS... 2 1. Pre-Incident Services... 3 1.1 Incident Response Agreements... 3 1.2 Assessments
Florida Department of Management Services Division of State Purchasing Table of Contents Introduction... 1 About GEARS... 2 1. Pre-Incident Services... 3 1.1 Incident Response Agreements... 3 1.2 Assessments
NCS 330. Information Assurance Policies, Ethics and Disaster Recovery. NYC University Polices and Standards 4/15/15.
 NCS 330 Information Assurance Policies, Ethics and Disaster Recovery NYC University Polices and Standards 4/15/15 Jess Yanarella Table of Contents: Introduction: Part One: Risk Analysis Threats Vulnerabilities
NCS 330 Information Assurance Policies, Ethics and Disaster Recovery NYC University Polices and Standards 4/15/15 Jess Yanarella Table of Contents: Introduction: Part One: Risk Analysis Threats Vulnerabilities
utilities helping utilities MI WARN Michigan Water/Wastewater Agency Response Network Water and Wastewater Agency Response Network: An Update
 utilities helping utilities MI WARN Michigan Water/Wastewater Agency Response Network Water and Wastewater Agency Response Network: An Update MI WARN Website Home Mutual Aid Agreement MIWARN Regions Links/Downloads
utilities helping utilities MI WARN Michigan Water/Wastewater Agency Response Network Water and Wastewater Agency Response Network: An Update MI WARN Website Home Mutual Aid Agreement MIWARN Regions Links/Downloads
SECURITY IN TRUCKING
 SECURITY IN TRUCKING A CHECKLIST FOR FLEET OPERATORS SECURITY IN TRUCKING A CHECKLIST FOR FLEET OPERATORS This checklist for fleet security has been compiled by the Private Motor Truck Council of Canada
SECURITY IN TRUCKING A CHECKLIST FOR FLEET OPERATORS SECURITY IN TRUCKING A CHECKLIST FOR FLEET OPERATORS This checklist for fleet security has been compiled by the Private Motor Truck Council of Canada
SMITH COLLEGE EMERGENCY PLANNING SUMMER PROGRAMS EMERGENCY PLAN
 T (413) 585-2669 F (413) 585-6990 SMITH COLLEGE EMERGENCY PLANNING Overview Smith College currently has in place an Emergency Response Plan, an Emergency Response Team, and a Crisis Management Team. Campus
T (413) 585-2669 F (413) 585-6990 SMITH COLLEGE EMERGENCY PLANNING Overview Smith College currently has in place an Emergency Response Plan, an Emergency Response Team, and a Crisis Management Team. Campus
THE UNIVERSITY OF TEXAS AT AUSTIN HANDBOOK OF OPERATING PROCEDURES SECURITY SYSTEMS ALARM POLICY
 THE UNIVERSITY OF TEXAS AT AUSTIN HANDBOOK OF OPERATING PROCEDURES Section I. General Policy Guidelines A. Policy Statement SECURITY SYSTEMS ALARM POLICY Part 2. Campus Services Section A. General Campus
THE UNIVERSITY OF TEXAS AT AUSTIN HANDBOOK OF OPERATING PROCEDURES Section I. General Policy Guidelines A. Policy Statement SECURITY SYSTEMS ALARM POLICY Part 2. Campus Services Section A. General Campus
University of St Andrews Out of Hours Protocol Appendices: A- CCTV Code of Practice B- Service Level Statement
 University of St Andrews Out of Hours Protocol Appendices: A- CCTV Code of Practice B- Service Level Statement 1. Context The University security service provides night and weekend cover throughout the
University of St Andrews Out of Hours Protocol Appendices: A- CCTV Code of Practice B- Service Level Statement 1. Context The University security service provides night and weekend cover throughout the
Section 1: Definitions
 ARTICLE XIV: REGISTRATION AND ENFORCEMENT OF ALARM SYSTEMS Section 1: Definitions A. Alarm Company is a person or business that sells, provides, monitors, maintains, services, repairs, alters, replaces,
ARTICLE XIV: REGISTRATION AND ENFORCEMENT OF ALARM SYSTEMS Section 1: Definitions A. Alarm Company is a person or business that sells, provides, monitors, maintains, services, repairs, alters, replaces,
Working for business. Workplace Safety Discount Application With employees
 Working for business Workplace Safety Discount Application With employees What is the Workplace Safety Discount? Workplace Safety Discount provides a framework for building successful and sustainable workplace
Working for business Workplace Safety Discount Application With employees What is the Workplace Safety Discount? Workplace Safety Discount provides a framework for building successful and sustainable workplace
HIPAA Privacy and Security. Rochelle Steimel, HIPAA Privacy Official Judy Smith, Staff Development January 2012
 HIPAA Privacy and Security Rochelle Steimel, HIPAA Privacy Official Judy Smith, Staff Development January 2012 Goals and Objectives Course Goal: To introduce the staff of Munson Healthcare to the concepts
HIPAA Privacy and Security Rochelle Steimel, HIPAA Privacy Official Judy Smith, Staff Development January 2012 Goals and Objectives Course Goal: To introduce the staff of Munson Healthcare to the concepts
HIPAA Security Alert
 Shipman & Goodwin LLP HIPAA Security Alert July 2008 EXECUTIVE GUIDANCE HIPAA SECURITY COMPLIANCE How would your organization s senior management respond to CMS or OIG inquiries about health information
Shipman & Goodwin LLP HIPAA Security Alert July 2008 EXECUTIVE GUIDANCE HIPAA SECURITY COMPLIANCE How would your organization s senior management respond to CMS or OIG inquiries about health information
How To Understand Cyber Security
 Law Enforcement Perceptions of Cyber Security International Association of Chiefs of Police Canadian Association of Chiefs of Police May 2013 This study made possible through financial and program support
Law Enforcement Perceptions of Cyber Security International Association of Chiefs of Police Canadian Association of Chiefs of Police May 2013 This study made possible through financial and program support
Health and Safety Policy
 Health and Safety Policy Document Control Title : Health and Safety Policy Applicable to : All Staff and Executive Officers Date last reviewed : July 2015 Procedure Owner : People and Organisational Development
Health and Safety Policy Document Control Title : Health and Safety Policy Applicable to : All Staff and Executive Officers Date last reviewed : July 2015 Procedure Owner : People and Organisational Development
A practical guide to IT security
 Data protection A practical guide to IT security Ideal for the small business The Data Protection Act states that appropriate technical and organisational measures shall be taken against unauthorised or
Data protection A practical guide to IT security Ideal for the small business The Data Protection Act states that appropriate technical and organisational measures shall be taken against unauthorised or
Feel Secure Your Guide to Home Safety
 Feel Secure Your Guide to Home Safety Master Licences: VIC No. 65201491P WA No. SA36517 SA No. ISL152299 NSW No. 405187443 ACT No. 17501009 QLD No. 3258669 Pic contents Watching over you and your home
Feel Secure Your Guide to Home Safety Master Licences: VIC No. 65201491P WA No. SA36517 SA No. ISL152299 NSW No. 405187443 ACT No. 17501009 QLD No. 3258669 Pic contents Watching over you and your home
Emergency Preparedness: Learning Objectives. Minimizing and Controlling Future Disasters. SHRM Disaster Preparedness Survey 3.
 Emergency Preparedness: 1 Minimizing and Controlling Future Disasters October 7-8, 2013 Presenter: Marna Hayden, SPHR Hayden Resources Inc. www.haydenhr.com Learning Objectives How to develop emergency
Emergency Preparedness: 1 Minimizing and Controlling Future Disasters October 7-8, 2013 Presenter: Marna Hayden, SPHR Hayden Resources Inc. www.haydenhr.com Learning Objectives How to develop emergency
Business Continuity Plan Guidance and Template to support Small Businesses
 Business Continuity Plan Guidance and Template to support Small Businesses Disclaimer This template and guidance is provided as general information about Business Continuity Planning. It is not intended
Business Continuity Plan Guidance and Template to support Small Businesses Disclaimer This template and guidance is provided as general information about Business Continuity Planning. It is not intended
ORDINANCE RELATIVE TO FALSE ALARMS
 ORDINANCE RELATIVE TO FALSE ALARMS BE IT ORDAINED by the Municipal Council of the City of Attleboro as follows: That Section 15-3 Alarm Regulations of Chapter 15 Police, of the Revised Ordinances of the
ORDINANCE RELATIVE TO FALSE ALARMS BE IT ORDAINED by the Municipal Council of the City of Attleboro as follows: That Section 15-3 Alarm Regulations of Chapter 15 Police, of the Revised Ordinances of the
Emergency Response Planning Template for Public Drinking Water Systems
 Emergency Response Planning Template for Public Drinking Water Systems Rural Community Assistance Corporation www.rcac.org Produced for the Rural Community Assistance Partnership (RCAP) National Network
Emergency Response Planning Template for Public Drinking Water Systems Rural Community Assistance Corporation www.rcac.org Produced for the Rural Community Assistance Partnership (RCAP) National Network
EMERGENCY PREPAREDNESS PLAN
 EMERGENCY PREPAREDNESS PLAN Promontory Charter School ----------------Emergency 911--------------------- INTRODUCTION The purpose of this Emergency Preparedness Plan for Promontory Charter School is to
EMERGENCY PREPAREDNESS PLAN Promontory Charter School ----------------Emergency 911--------------------- INTRODUCTION The purpose of this Emergency Preparedness Plan for Promontory Charter School is to
6 Tech-savvy Ideas that will enhance (and simplify) Client Care
 6 Tech-savvy Ideas that will enhance (and simplify) Client Care Human services and community living organizations all share the same mission - to better the lives of those in our communities who need assistance.
6 Tech-savvy Ideas that will enhance (and simplify) Client Care Human services and community living organizations all share the same mission - to better the lives of those in our communities who need assistance.
Crisis Communications Plan
 Crisis Communications Plan Cleveland Metropolitan School District External Affairs Department January 13, 2009 1 Table of Contents 1. Purpose 1.1 Why do we need this plan? 5 1.2 What are the objectives?
Crisis Communications Plan Cleveland Metropolitan School District External Affairs Department January 13, 2009 1 Table of Contents 1. Purpose 1.1 Why do we need this plan? 5 1.2 What are the objectives?
CYBERSECURITY BEST PRACTICES FOR SMALL AND MEDIUM PENNSYLVANIA UTILITIES
 CYBERSECURITY BEST PRACTICES FOR SMALL AND MEDIUM PENNSYLVANIA UTILITIES The information provided in this document is presented as a courtesy to be used for informational purposes only. This information
CYBERSECURITY BEST PRACTICES FOR SMALL AND MEDIUM PENNSYLVANIA UTILITIES The information provided in this document is presented as a courtesy to be used for informational purposes only. This information
DOT HAZMAT SECURITY AWARENESS TRAINING
 ERI Safety Videos DVDs, Digital Media & Custom Production 1319 DOT HAZMAT SECURITY AWARENESS TRAINING Leader s Guide Safety Source Productions DOT HAZMAT SECURITY AWARENESS TRAINING This easy-to-use Leader
ERI Safety Videos DVDs, Digital Media & Custom Production 1319 DOT HAZMAT SECURITY AWARENESS TRAINING Leader s Guide Safety Source Productions DOT HAZMAT SECURITY AWARENESS TRAINING This easy-to-use Leader
DATE APPROVED: DATE EFFECTIVE: Date of Approval. REFERENCE NO. MOH/04 PAGE: 1 of 7
 SOURCE: Ministry of Health DATE APPROVED: DATE EFFECTIVE: Date of Approval REPLACESPOLICY DATED: 1 POLICY TITLE: Incident/Accident Reporting REFERENCE NO. MOH/04 PAGE: 1 of 7 REVISION DATE(s): Ministry
SOURCE: Ministry of Health DATE APPROVED: DATE EFFECTIVE: Date of Approval REPLACESPOLICY DATED: 1 POLICY TITLE: Incident/Accident Reporting REFERENCE NO. MOH/04 PAGE: 1 of 7 REVISION DATE(s): Ministry
OH&S Management Systems Audit Checklist (NAT, E3)
 3.1.2 3.1.1 Introduction OH&S Management Systems Audit Checklist (NAT, E3) This audit checklist is based on Element 3 (Implementation) of the National Self-Insurers OHS Audit Tool. For a full copy of the
3.1.2 3.1.1 Introduction OH&S Management Systems Audit Checklist (NAT, E3) This audit checklist is based on Element 3 (Implementation) of the National Self-Insurers OHS Audit Tool. For a full copy of the
Identity Theft Repair Kit
 Identity Theft Repair Kit The Identity Theft Repair Kit contains a resolution checklist and resolution worksheets. The checklist will help you keep track of the companies and organizations you should contact
Identity Theft Repair Kit The Identity Theft Repair Kit contains a resolution checklist and resolution worksheets. The checklist will help you keep track of the companies and organizations you should contact
ALARM SYSTEM USER: Any person, firm, partnership, cooperation or other entity which uses an Alarm System at its Alarm Site.
 Article XIII. Alarm Systems November 16, 1991, May 5, 2012 Section 1. Title and Purpose This bylaw shall be known as the Alarm System Bylaw. The purposes of this bylaw are to encourage alarm users to maintain
Article XIII. Alarm Systems November 16, 1991, May 5, 2012 Section 1. Title and Purpose This bylaw shall be known as the Alarm System Bylaw. The purposes of this bylaw are to encourage alarm users to maintain
Information Security
 Information Security A staff guide to the University's Information Systems Security Policy Issued by the IT Security Group on behalf of the University. Information Systems Security Guidelines for Staff
Information Security A staff guide to the University's Information Systems Security Policy Issued by the IT Security Group on behalf of the University. Information Systems Security Guidelines for Staff
Water Security Issues: The Federal Perspective. J. Alan Roberson, P.E. Director of Security and Regulatory Affairs AWWA Washington, DC
 Water Security Issues: The Federal Perspective J. Alan Roberson, P.E. Director of Security and Regulatory Affairs AWWA Washington, DC Outline The Overall Concept for Water Security What s Important in
Water Security Issues: The Federal Perspective J. Alan Roberson, P.E. Director of Security and Regulatory Affairs AWWA Washington, DC Outline The Overall Concept for Water Security What s Important in
Update on Anthem Cyber Attack General Information for Clients and Brokers
 Update on Anthem Cyber Attack General Information for Clients and Brokers February 20, 2015 What happened? Anthem, Inc. was the victim of a cyber attack. Anthem discovered that one of its database warehouses
Update on Anthem Cyber Attack General Information for Clients and Brokers February 20, 2015 What happened? Anthem, Inc. was the victim of a cyber attack. Anthem discovered that one of its database warehouses
ALARM COMPANIES, FIRE PROTECTION, FIRE EXTINGUISHING SYSTEM INSTALLATION, SERVICE, & REPAIR
 Salt Lake City Area Office 8722 S. Harrison St. Sandy, UT 84070 P.O. Box 4439 Sandy, UT 84091 800-257-5590 Fax 877-452-6910 Chicago Office 303 W. Madison Street Suite 2075 Chicago, IL 60606 800-456-4576
Salt Lake City Area Office 8722 S. Harrison St. Sandy, UT 84070 P.O. Box 4439 Sandy, UT 84091 800-257-5590 Fax 877-452-6910 Chicago Office 303 W. Madison Street Suite 2075 Chicago, IL 60606 800-456-4576
Standard: Information Security Incident Management
 Standard: Information Security Incident Management Page 1 Executive Summary California State University Information Security Policy 8075.00 states security incidents involving loss, damage or misuse of
Standard: Information Security Incident Management Page 1 Executive Summary California State University Information Security Policy 8075.00 states security incidents involving loss, damage or misuse of
Accreditation Program: Hospital. Emergency Management
 ccreditation Program: Hospital Emergency Management ccreditation of Healthcare Organizations ccreditation Program: Hospital Chapter: Emergency Management Standard EM.01.01.01 The [organization] engages
ccreditation Program: Hospital Emergency Management ccreditation of Healthcare Organizations ccreditation Program: Hospital Chapter: Emergency Management Standard EM.01.01.01 The [organization] engages
Consumer Information Sheet 16 October 2013
 First Aid For Medical Identity Theft Tips for Consumers Consumer Information Sheet 16 October 201 When another person uses your personal information to get medical services or goods, or to gain financially,
First Aid For Medical Identity Theft Tips for Consumers Consumer Information Sheet 16 October 201 When another person uses your personal information to get medical services or goods, or to gain financially,
Key Work Process 1.0 Manage After-Hours Emergency Response NEED KPI 1.1 TRANSFER PHONES KPI 1.2 CALL ANSWERING SERVICE PO&M CALL TREE
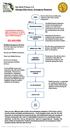 Key Work Process 1.0 Manage After-Hours Emergency Response Any School Board employee or public safety agency is to call the BPS Emergency phone number to report a facility emergency. 321-633-3600 KPI 1.1
Key Work Process 1.0 Manage After-Hours Emergency Response Any School Board employee or public safety agency is to call the BPS Emergency phone number to report a facility emergency. 321-633-3600 KPI 1.1
HIPAA and Health Information Privacy and Security
 HIPAA and Health Information Privacy and Security Revised 7/2014 What Is HIPAA? H Health I Insurance P Portability & A Accountability A - Act HIPAA Privacy and Security Rules were passed to protect patient
HIPAA and Health Information Privacy and Security Revised 7/2014 What Is HIPAA? H Health I Insurance P Portability & A Accountability A - Act HIPAA Privacy and Security Rules were passed to protect patient
HIPAA Audit Risk Assessment - Risk Factors
 I II Compliance Compliance I Compliance II SECTION ONE COVERED ENTITY RESPONSIBILITIES AREA ONE Notice of Privacy Practices 1 Is your full notice of privacy practices given to every new patient in your
I II Compliance Compliance I Compliance II SECTION ONE COVERED ENTITY RESPONSIBILITIES AREA ONE Notice of Privacy Practices 1 Is your full notice of privacy practices given to every new patient in your
ORDINANCE NO. 08-129
 ORDINANCE NO. 08-129 AN ORDINANCE REPEALING AND REORDAINING PART 4 (ALARM LICENSES AND REGISTRATION) OF ARTICLE 3 (SALES OF GOODS AND SERVICES) OF CHAPTER 2 (BUSINESS LICENSES, LIQUOR REGULATION AND TAXATION),
ORDINANCE NO. 08-129 AN ORDINANCE REPEALING AND REORDAINING PART 4 (ALARM LICENSES AND REGISTRATION) OF ARTICLE 3 (SALES OF GOODS AND SERVICES) OF CHAPTER 2 (BUSINESS LICENSES, LIQUOR REGULATION AND TAXATION),
OCPS Tech Centers Orlando Campus. Annual Security Report
 OCPS Tech Centers Orlando Campus Annual Security Report 2015 2016 1. Current campus policies regarding procedures for students and others to report criminal actions or other emergencies occurring on campus.
OCPS Tech Centers Orlando Campus Annual Security Report 2015 2016 1. Current campus policies regarding procedures for students and others to report criminal actions or other emergencies occurring on campus.
Security Vulnerability Self-Assessment Guide for Mississippi s Public Water Systems
 Security Vulnerability Self-Assessment Guide for Mississippi s Public Water Systems NAME OF PUBLIC WATER SYSTEM PWS ID NUMBER(S) Date Completed Date Last Updated (should be updated annually) MISSISSIPPI
Security Vulnerability Self-Assessment Guide for Mississippi s Public Water Systems NAME OF PUBLIC WATER SYSTEM PWS ID NUMBER(S) Date Completed Date Last Updated (should be updated annually) MISSISSIPPI
STOKER OILFIELD SERVICE EMPLOYMENT APPLICATION
 STOKER OILFIELD SERVICE EMPLOYMENT APPLICATION Applicant Full Name Home Phone Cell Phone Email Address Current Address: Number and street City State & Zip How were you referred to Company?: Employment
STOKER OILFIELD SERVICE EMPLOYMENT APPLICATION Applicant Full Name Home Phone Cell Phone Email Address Current Address: Number and street City State & Zip How were you referred to Company?: Employment
RESPONSIBLE CARE SECURITY CODE OF MANAGEMENT PRACTICES
 RESPONSIBLE CARE SECURITY CODE OF MANAGEMENT PRACTICES Purpose and Scope The purpose of the Security Code of Management Practices is to help protect people, property, products, processes, information and
RESPONSIBLE CARE SECURITY CODE OF MANAGEMENT PRACTICES Purpose and Scope The purpose of the Security Code of Management Practices is to help protect people, property, products, processes, information and
WHAT ARE THE BENEFITS OF OUTSOURCING NETWORK SECURITY?
 WHAT ARE THE BENEFITS OF OUTSOURCING NETWORK SECURITY? Contents Introduction.... 3 What Types of Network Security Services are Available?... 4 Penetration Testing and Vulnerability Assessment... 4 Cyber
WHAT ARE THE BENEFITS OF OUTSOURCING NETWORK SECURITY? Contents Introduction.... 3 What Types of Network Security Services are Available?... 4 Penetration Testing and Vulnerability Assessment... 4 Cyber
Security Solutions to Meet NERC-CIP Requirements. Kevin Staggs, Honeywell Process Solutions
 Kevin Staggs, Honeywell Process Solutions Table of Contents Introduction...3 Nerc Standards and Implications...3 How to Meet the New Requirements...4 Protecting Your System...4 Cyber Security...5 A Sample
Kevin Staggs, Honeywell Process Solutions Table of Contents Introduction...3 Nerc Standards and Implications...3 How to Meet the New Requirements...4 Protecting Your System...4 Cyber Security...5 A Sample
Protecting your business from fraud
 Protecting your business from fraud KEY TAKEAWAYS > Understand the most common types of fraud and how to identify them. > What to do if you uncover fraudulent activity or suspect you are a victim of fraud.
Protecting your business from fraud KEY TAKEAWAYS > Understand the most common types of fraud and how to identify them. > What to do if you uncover fraudulent activity or suspect you are a victim of fraud.
FSIS Security Guidelines for Food Processors
 United States Department of Agriculture Food Safety and Inspection Service FSIS Security Guidelines for Food Processors Food Security Plan Management Dear Establishment Owner/Operator: The Food Safety
United States Department of Agriculture Food Safety and Inspection Service FSIS Security Guidelines for Food Processors Food Security Plan Management Dear Establishment Owner/Operator: The Food Safety
HIPAA. New Breach Notification Risk Assessment and Sanctions Policy. Incident Management Policy. Focus on: For breaches affecting 1 3 individuals
 HIPAA New Breach Notification Risk Assessment and Sanctions Policy Incident Management Policy For breaches affecting 1 3 individuals +25 individuals + 500 individuals Focus on: analysis documentation PHI
HIPAA New Breach Notification Risk Assessment and Sanctions Policy Incident Management Policy For breaches affecting 1 3 individuals +25 individuals + 500 individuals Focus on: analysis documentation PHI
PCI Data Security Standard 3.0
 SECURELY ENABLING BUSINESS PCI Data Security Standard 3.0 Training Strategies That Work Presented by Doug Hall May 20, 2014 AGENDA PCI DSS 3.0 Training Strategies That Work PCI DSS 3.0 Overview PCI Training
SECURELY ENABLING BUSINESS PCI Data Security Standard 3.0 Training Strategies That Work Presented by Doug Hall May 20, 2014 AGENDA PCI DSS 3.0 Training Strategies That Work PCI DSS 3.0 Overview PCI Training
History of the SPCC Rule
 2010 SPCC Training SPCC Rule History of the SPCC Rule The SPCC plan is a document required under the clean water act (CWA) It became effective in 1972 and has changed little in 32 years. The rule was formally
2010 SPCC Training SPCC Rule History of the SPCC Rule The SPCC plan is a document required under the clean water act (CWA) It became effective in 1972 and has changed little in 32 years. The rule was formally
Enhanced Security Monitoring Primer For Water Quality Surveillance and Response Systems
 United States Environmental Protection Agency Enhanced Security Monitoring Primer For Water Quality Surveillance and Response Systems Office of Water (M 140) EPA 817-B-15-002B May 2015 Introduction A Water
United States Environmental Protection Agency Enhanced Security Monitoring Primer For Water Quality Surveillance and Response Systems Office of Water (M 140) EPA 817-B-15-002B May 2015 Introduction A Water
Rockwell Software Online Demo System
 Rockwell Software Online Demo System Table of Contents TABLE OF CONTENTS 1 ROCKWELL SOFTWARE ONLINE DEMO SYSTEM 3 ABOUT THIS SCRIPT 3 HOW TO USE THIS SCRIPT 3 BEFORE YOU BEGIN 4 NAVIGATION 5 DEMO WATER
Rockwell Software Online Demo System Table of Contents TABLE OF CONTENTS 1 ROCKWELL SOFTWARE ONLINE DEMO SYSTEM 3 ABOUT THIS SCRIPT 3 HOW TO USE THIS SCRIPT 3 BEFORE YOU BEGIN 4 NAVIGATION 5 DEMO WATER
Contents. Introduction. Basic use... pg 3. App settings: Main Menu... pg 6. App settings: Profile Sub-menu... pg 7
 USER GUIDE PanicGuard 2014 2 Contents Basic use... pg 3 How and when to use PanicGuard App settings: Main Menu... pg 6 A brief guide to contacts, wallpapers and other customisable settings App settings:
USER GUIDE PanicGuard 2014 2 Contents Basic use... pg 3 How and when to use PanicGuard App settings: Main Menu... pg 6 A brief guide to contacts, wallpapers and other customisable settings App settings:
Security Breaches. There are unscrupulous individuals, like identity thieves, who want your information to commit fraud.
 IDENTITY THEFT Security Breaches Our economy generates an enormous amount of data. Most users of that information are from honest businesses - getting and giving legitimate information. Despite the benefits
IDENTITY THEFT Security Breaches Our economy generates an enormous amount of data. Most users of that information are from honest businesses - getting and giving legitimate information. Despite the benefits
Table of Contents ESF-3-1 034-00-13
 Table of Contents Primary Coordinating Agency... 2 Local Supporting Agencies... 2 State, Regional, and Federal Agencies and Organizations... 3 Purpose... 3 Situations and Assumptions... 4 Direction and
Table of Contents Primary Coordinating Agency... 2 Local Supporting Agencies... 2 State, Regional, and Federal Agencies and Organizations... 3 Purpose... 3 Situations and Assumptions... 4 Direction and
Emergency Response Network in Your Community. Paul Haley Emergency Management Coordinator City of Trenton
 Emergency Response Network in Your Community Paul Haley Emergency Management Coordinator City of Trenton Your Local Emergency Management Support What we are going to cover Objectives Questions anytime
Emergency Response Network in Your Community Paul Haley Emergency Management Coordinator City of Trenton Your Local Emergency Management Support What we are going to cover Objectives Questions anytime
Sanitary Sewer Overflow Response Plan Working Committee SANITARY SEWER OVERFLOW RESPONSE PLAN
 Sanitary Sewer Overflow Response Plan Working Committee SANITARY SEWER OVERFLOW RESPONSE PLAN I. PURPOSE The Municipality / Authority has structured this Sanitary Sewer Overflow Response Plan to satisfy
Sanitary Sewer Overflow Response Plan Working Committee SANITARY SEWER OVERFLOW RESPONSE PLAN I. PURPOSE The Municipality / Authority has structured this Sanitary Sewer Overflow Response Plan to satisfy
Cyber Security Initiatives and Issues
 Cyber Security Initiatives and Issues NARUC Summer Committee Meetings Robert Schreiber, CISSP, CISA Director, Client Services and Security Operations ITS July 19, 2009 Water Utility History of SCADA Yesterday
Cyber Security Initiatives and Issues NARUC Summer Committee Meetings Robert Schreiber, CISSP, CISA Director, Client Services and Security Operations ITS July 19, 2009 Water Utility History of SCADA Yesterday
Bioterrorism & Emergency Readiness
 Bioterrorism & Emergency Readiness COMPETENCIES FOR ALL PUBLIC HEALTH WORKERS A Message from the Centers for Disease Control and Prevention Dear Public Health Colleague, A prepared workforce is an essential
Bioterrorism & Emergency Readiness COMPETENCIES FOR ALL PUBLIC HEALTH WORKERS A Message from the Centers for Disease Control and Prevention Dear Public Health Colleague, A prepared workforce is an essential
CYBER SECURITY POLICY For Managers of Drinking Water Systems
 CYBER SECURITY POLICY For Managers of Drinking Water Systems Excerpt from Cyber Security Assessment and Recommended Approach, Final Report STATE OF DELAWARE DRINKING WATER SYSTEMS February 206 Kash Srinivasan
CYBER SECURITY POLICY For Managers of Drinking Water Systems Excerpt from Cyber Security Assessment and Recommended Approach, Final Report STATE OF DELAWARE DRINKING WATER SYSTEMS February 206 Kash Srinivasan
PCI DSS Security Awareness Training for University of Tennessee Credit Card Merchants. UT System Administration Information Security Office
 PCI DSS Security Awareness Training for University of Tennessee Credit Card Merchants UT System Administration Information Security Office Agenda Overview of PCI DSS Compliance versus Non-Compliance PCI
PCI DSS Security Awareness Training for University of Tennessee Credit Card Merchants UT System Administration Information Security Office Agenda Overview of PCI DSS Compliance versus Non-Compliance PCI
National Cyber Security Month 2015: Daily Security Awareness Tips
 National Cyber Security Month 2015: Daily Security Awareness Tips October 1 New Threats Are Constantly Being Developed. Protect Your Home Computer and Personal Devices by Automatically Installing OS Updates.
National Cyber Security Month 2015: Daily Security Awareness Tips October 1 New Threats Are Constantly Being Developed. Protect Your Home Computer and Personal Devices by Automatically Installing OS Updates.
Administrative Procedure
 Administrative Procedure Effective: 12/21/2012 Supersedes: N/A Page: 1 of 5 Subject: SECURITY ALARMS 1.0. PURPOSE: The purpose of this procedure is to coordinate and control the installation, monitoring,
Administrative Procedure Effective: 12/21/2012 Supersedes: N/A Page: 1 of 5 Subject: SECURITY ALARMS 1.0. PURPOSE: The purpose of this procedure is to coordinate and control the installation, monitoring,
TOWN OF BLACKFALDS BYLAW 1191/15
 A BYLAW OF THE TOWN OF BLACKFALDS, IN THE PROVINCE OF ALBERTA, TO CONTROL SECURITY ALARM SYSTEMS SO AS TO REDUCE FALSE ALARMS REQUIRING RCMP OR FIRE DEPARTMENT RESPONSE WHEREAS Council of the Town of Blackfalds
A BYLAW OF THE TOWN OF BLACKFALDS, IN THE PROVINCE OF ALBERTA, TO CONTROL SECURITY ALARM SYSTEMS SO AS TO REDUCE FALSE ALARMS REQUIRING RCMP OR FIRE DEPARTMENT RESPONSE WHEREAS Council of the Town of Blackfalds
