SAFAX. External Clients. TU/e Security Group
|
|
|
- Clarissa Hart
- 7 years ago
- Views:
Transcription
1 2016 SAFAX Policy Evaluation Deploy Policy TU/e Security Group
2 Table of Contents Introduction... 2 List of Acronyms and Definitions... 3 List of Acronyms... 3 List of Definitions... 3 General Steps... 4 Policy Evaluation... 5 Use a client code... 5 Use a username/password... 6 Deploy Policy... 7 Java Client Example Codes... 8 SFXClient.java... 8 SFXClientWithAuthorization.java... 8 PAPClient.java... 8 References Security Group TU/e
3 Introduction SAFAX [1] is an extensible authorization framework offered as a service. SAFAX provides a novel XACML-based architectural framework tailored to the development of extensible authorization services for distributed and collaborative systems. The key design principle underlying SAFAX is that all components are loosely coupled services, thus providing the flexibility, extensibility and scalability needed to manage authorizations in cloud environments. SAFAX s architecture allows users to: a) deploy their access control policies in a standard format; b) in a single location; and c) augment policy evaluation with information from user selectable external trust services. This document presents the steps to configure third-party software systems to access SAFAX programmatically. These software systems can also be considered clients of SAFAX as they consume SAFAX authorization service. To access SAFAX programmatically, we provide software clients that software systems can use to: Upload an XACML policy to an existing demo. Evaluate an XACML request using a client code. Evaluate an XACML request using username/password. Clients can be written in any programming language that supports creating web service clients. For testing purposes, we describe the realization of the clients in Java. 2 Security Group TU/e
4 List of Acronyms and Definitions List of Acronyms CH: Context Handler PAP: Policy Administration Point PEP: Policy Enforcement Point PIP: Policy Information Point SAFAX: extensible Authorization Framework As a Service UUID: Universally Unique IDentifier XACML: extensible Access Control Markup Language List of Definitions Administrator: a user who is responsible for the management of SAFAX. 3 Security Group TU/e
5 General Steps To access SAFAX programmatically, users need to register within SAFAX service. More specifically; - They need to obtain a username/password by visiting SAFAX website. Figure 1 SAFAX Registration GUI Menu - After login with the username/password users can create a project and a demo within this project. Figure 2 List of Demos in a Project - For each demo, SAFAX creates a PDP instance and a PDP code. Demos can be configured according to user preferences. Figure 3 PDP Code and PDP Settings 4 Security Group TU/e
6 Policy Evaluation A third-party software system asks SAFAX to evaluate a policy against an XACML request. There are two options to use SAFAX evaluate web service: 1. Use a client code 2. Use a username/password Use a client code A third-party software system consumes the following web service provided by SAFAX: The {pdpcode} refers to the demo with respect to which the request should be evaluated. The pdpcode can be found by selecting the appropriate demo and then navigating to the PDP Settings (see Figure 4). Figure 4 PDP Code The third-party software system also needs to provide the following parameters: clientcode: this is the key through which SAFAX authenticates client and is provided by SAFAX administrators. transactionid: an immutable universally unique identifier (UUID). A UUID represents a 128-bit value. The transactionid is provided by client and for example, can be obtained using the randomuuid() method of Java UUID class. request: an XACML request. In Java, this can be done by creating a Form object and attaching the three parameters to this object. Figure 5 Java Code Snippets Adding Form Parameters 5 Security Group TU/e
7 The client consumes the authorization service provided by SAFAX. SAFAX checks the client code provided by the client. If the code is valid, SAFAX evaluates the request and returns the XACML response to the third-party software system. Use a username/password A third-party software system consumes the following web service provided by SAFAX: The {pdpcode} refers to the demo with respect to which the request should be evaluated. The code can be found by choosing a demo and then navigating to the PDP Settings. Figure 6 PDP Code The third-party software system also needs to include the following form parameters: uname: this is the username provided by SAFAX. password: this is the password associated with a username. request_content: an XACML request. Figure 7 Java Code Snippets Adding Form Parameters The client consumes the authorization service provided by SAFAX. SAFAX checks the username and password provided by the client. SAFAX uses its own authorization service to check if the account associated with the client has the privilege to evaluate the request using the given PDP instance. If the account is allowed to evaluate the request against a policy contained in the given demo, SAFAX forwards the request to the PDP instance for evaluation and returns the XACML response to the client.. 6 Security Group TU/e
8 Deploy Policy A third-party software system can deploy a policy to an existing demo within SAFAX by consuming the following web service provided by SAFAX: The third-party software system needs to include the following form parameters: uname: this is the username. password: this is the password. policy_content: the content of the policy. Figure 8 Java Code Snippets Adding Form Parameters The client consumes the authorization service provided by SAFAX. In particular, the client sends a request to upload the given policy within a certain demo. SAFAX checks the username and password provided by the client. SAFAX uses its own authorization service to check if the account associated to the client is allowed to deploy the policy in the demo. If the account is authorized to deploy in the given demo, SAFAX forwards the request to the PAP service. SAFAX returns a notification to the client whether the policy is successfully deployed or not.. 7 Security Group TU/e
9 Java Client Example Codes The previous sections have presented the steps describing how to consume SAFAX authorization services without limitation to a particular programming language. In this section, we present some sample clients implemented in Java and how they can be configured. The example codes can be found in the SVN of the Security Group. We refer to the SAFAX Installation Guide [2] for the configuration of SVN and of the SAFAX project. Three Java client applications are available: 1. PAPClient.java 2. SFXClient.java 3. SFXClientWithAuthorization.java You can use Eclipse to open the project. Right-click any of the three client applications and choose Run As -> Java Application. SFXClient.java This client is used to evaluate an XACML request against the XACML policies defined in a given demo using a client code. The client requires the {pdpcode} corresponding to the demo to be used to evaluate the access request. Change the content of serviceurl at line 17 by using the appropriate {pdpcode}. This code can be obtained from the demo setting (see Figure 4). At line 20, a transactionid is automatically generated. At line 25, use the clientcode provided by SAFAX administrators. SFXClientWithAuthorization.java This client is used to evaluate an XACML request against the XACML policies defined in a given demo using a username/password. The client requires the {pdpcode} to use the service. Change the content of serviceurl at line 17 by using the {pdpcode} corresponding to the demo to be used. This code can be obtained from the demo setting (see Figure 4). At line 65 and 66 use your username and password provided by SAFAX. Figure 9 Username and Password Parameters PAPClient.java This client is used to upload a XACML policy to an existing demo in SAFAX. The client should specify the demoid based on actual need. In particular, the demoid indicates the demo in which a given XACML policy should be programmatically uploaded. This can be done by setting the content of the serviceurl variable at line Security Group TU/e
10 At line 27 change the first parameter of the readfile() to reference to the policy file. Figure 10 Java Code Snippets serviceurl Variable At line 36 and 37 use your username and password provided by SAFAX. Figure 11 Username and Password Parameters 9 Security Group TU/e
11 References [1] S. P. Kaluvuri and A. I. Egner and J. den Hartog and N. Zannone. SAFAX -- an extensible authorization service for cloud environments. Frontiers in ICT 2(9), [2] SAFAX Installation Guide, Security Group TU/e
White Paper Cybercom & Axiomatics Joint Identity & Access Management (R)evolution
 White Paper Cybercom & Axiomatics Joint Identity & Access Management (R)evolution Federation and Attribute Based Access Control Page 2 Realization of the IAM (R)evolution Executive Summary Many organizations
White Paper Cybercom & Axiomatics Joint Identity & Access Management (R)evolution Federation and Attribute Based Access Control Page 2 Realization of the IAM (R)evolution Executive Summary Many organizations
Entitlements Access Management for Software Developers
 Entitlements Access Management for Software Developers Market Environment The use of fine grained entitlements and obligations control for access to sensitive information and services in software applications
Entitlements Access Management for Software Developers Market Environment The use of fine grained entitlements and obligations control for access to sensitive information and services in software applications
Redpaper Axel Buecker Craig Forster Sridhar Muppidi Borna Safabakhsh
 Redpaper Axel Buecker Craig Forster Sridhar Muppidi Borna Safabakhsh IBM Tivoli Security Policy Manager Introduction In a growing number of enterprises, policies are the key mechanism by which the capabilities
Redpaper Axel Buecker Craig Forster Sridhar Muppidi Borna Safabakhsh IBM Tivoli Security Policy Manager Introduction In a growing number of enterprises, policies are the key mechanism by which the capabilities
Integrating with IBM Tivoli TSOM
 Integration Notes Integrating with IBM Tivoli TSOM The Cascade Profiler integrates with the IBM Tivoli Security Operations Manager (TSOM) through the use of SNMP traps. It has been tested with TSOM Version
Integration Notes Integrating with IBM Tivoli TSOM The Cascade Profiler integrates with the IBM Tivoli Security Operations Manager (TSOM) through the use of SNMP traps. It has been tested with TSOM Version
The increasing popularity of mobile devices is rapidly changing how and where we
 Mobile Security BACKGROUND The increasing popularity of mobile devices is rapidly changing how and where we consume business related content. Mobile workforce expectations are forcing organizations to
Mobile Security BACKGROUND The increasing popularity of mobile devices is rapidly changing how and where we consume business related content. Mobile workforce expectations are forcing organizations to
Google App Engine f r o r J av a a v a (G ( AE A / E J / )
 Google App Engine for Java (GAE/J) What is Google App Engine? Google offers a cloud computing infrastructure calledgoogle App Engine(App Engine) for creating and running web applications. App Engine allows
Google App Engine for Java (GAE/J) What is Google App Engine? Google offers a cloud computing infrastructure calledgoogle App Engine(App Engine) for creating and running web applications. App Engine allows
Contents. Introduction. Prerequisites. Requirements. Components Used
 Contents Introduction Prerequisites Requirements Components Used Background Information Configure Step 1. Configure the Firepower User Agent for Single-Sign-On Step 2. Integrate the Firepower Management
Contents Introduction Prerequisites Requirements Components Used Background Information Configure Step 1. Configure the Firepower User Agent for Single-Sign-On Step 2. Integrate the Firepower Management
ClicktoFax Service Usage Manual
 ClicktoFax Service Usage Manual 1. Log in to Fax Service 2. Configure your account 3. Send a fax 4. Receive a fax/search for Faxes/View Faxes 5. Logout 6. Additional Support 1. Log into fax service: a.
ClicktoFax Service Usage Manual 1. Log in to Fax Service 2. Configure your account 3. Send a fax 4. Receive a fax/search for Faxes/View Faxes 5. Logout 6. Additional Support 1. Log into fax service: a.
http://docs.trendmicro.com
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the product, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the product, please review the readme files,
Bringing Cloud Security Down to Earth. Andreas M Antonopoulos Senior Vice President & Founding Partner www.nemertes.com
 Bringing Cloud Security Down to Earth Andreas M Antonopoulos Senior Vice President & Founding Partner www.nemertes.com Agenda About Nemertes Cloud Dynamics and Adoption Assessing Risk of Cloud Services
Bringing Cloud Security Down to Earth Andreas M Antonopoulos Senior Vice President & Founding Partner www.nemertes.com Agenda About Nemertes Cloud Dynamics and Adoption Assessing Risk of Cloud Services
Usage Control in Cloud Systems
 Usage Control in Cloud Systems Paolo Mori Istituto di Informatica e Telematica Consiglio Nazionale delle Ricerche Pisa Italy Agenda Examples of usage of Cloud services Usage Control Model Policy Language
Usage Control in Cloud Systems Paolo Mori Istituto di Informatica e Telematica Consiglio Nazionale delle Ricerche Pisa Italy Agenda Examples of usage of Cloud services Usage Control Model Policy Language
Installing the PA 100 VM in VMware Workstation 9.x
 Installing the PA 100 VM in VMware Workstation 9.x Johan Loos johan@accessdenied.be Version 1.0 Introduction The PA 100-VM is a virtual firewall delivered as a VMware OVF. This is a way to package and
Installing the PA 100 VM in VMware Workstation 9.x Johan Loos johan@accessdenied.be Version 1.0 Introduction The PA 100-VM is a virtual firewall delivered as a VMware OVF. This is a way to package and
XACML and Access Management. A Business Case for Fine-Grained Authorization and Centralized Policy Management
 A Business Case for Fine-Grained Authorization and Centralized Policy Management Dissolving Infrastructures A recent Roundtable with CIOs from a dozen multinational companies concurred that Identity &
A Business Case for Fine-Grained Authorization and Centralized Policy Management Dissolving Infrastructures A recent Roundtable with CIOs from a dozen multinational companies concurred that Identity &
SYSTEM DEVELOPMENT AND IMPLEMENTATION
 CHAPTER 6 SYSTEM DEVELOPMENT AND IMPLEMENTATION 6.0 Introduction This chapter discusses about the development and implementation process of EPUM web-based system. The process is based on the system design
CHAPTER 6 SYSTEM DEVELOPMENT AND IMPLEMENTATION 6.0 Introduction This chapter discusses about the development and implementation process of EPUM web-based system. The process is based on the system design
CORISECIO. Quick Installation Guide Open XML Gateway
 Quick Installation Guide Open XML Gateway Content 1 FIRST STEPS... 3 2 INSTALLATION... 3 3 ADMINCONSOLE... 4 3.1 Initial Login... 4 3.1.1 Derby Configuration... 5 3.1.2 Password Change... 6 3.2 Logout...
Quick Installation Guide Open XML Gateway Content 1 FIRST STEPS... 3 2 INSTALLATION... 3 3 ADMINCONSOLE... 4 3.1 Initial Login... 4 3.1.1 Derby Configuration... 5 3.1.2 Password Change... 6 3.2 Logout...
CDOT Workflow ProjectWise Web Access Operations
 CDOT Workflow ProjectWise Web Access Operations ProjectWise offers a Web-based method for accessing project data from existing CDOT datasources. This document includes instructions for configuring Internet
CDOT Workflow ProjectWise Web Access Operations ProjectWise offers a Web-based method for accessing project data from existing CDOT datasources. This document includes instructions for configuring Internet
NS DISCOVER 4.0 ADMINISTRATOR S GUIDE. July, 2015. Version 4.0
 NS DISCOVER 4.0 ADMINISTRATOR S GUIDE July, 2015 Version 4.0 TABLE OF CONTENTS 1 General Information... 4 1.1 Objective... 4 1.2 New 4.0 Features Improvements... 4 1.3 Migrating from 3.x to 4.x... 5 2
NS DISCOVER 4.0 ADMINISTRATOR S GUIDE July, 2015 Version 4.0 TABLE OF CONTENTS 1 General Information... 4 1.1 Objective... 4 1.2 New 4.0 Features Improvements... 4 1.3 Migrating from 3.x to 4.x... 5 2
Ordering Offsite Backups
 Introduction The purpose of this Startup Guide is to familiarize you with Own Web Now's Offsite Backup offering and show you how to purchase, deploy and manage the service. Offsite Backup offering is an
Introduction The purpose of this Startup Guide is to familiarize you with Own Web Now's Offsite Backup offering and show you how to purchase, deploy and manage the service. Offsite Backup offering is an
Defender Configuring for Use with GrIDsure Tokens
 Defender Configuring for Use with GrIDsure Tokens Introduction The GrIDsure token can be used to protect any website hosted on Internet Information Server (IIS). This guide provides information for the
Defender Configuring for Use with GrIDsure Tokens Introduction The GrIDsure token can be used to protect any website hosted on Internet Information Server (IIS). This guide provides information for the
Configuration Guide. BES12 Cloud
 Configuration Guide BES12 Cloud Published: 2016-04-08 SWD-20160408113328879 Contents About this guide... 6 Getting started... 7 Configuring BES12 for the first time...7 Administrator permissions you need
Configuration Guide BES12 Cloud Published: 2016-04-08 SWD-20160408113328879 Contents About this guide... 6 Getting started... 7 Configuring BES12 for the first time...7 Administrator permissions you need
Securing Enterprise: Employability and HR
 1 Securing Enterprise: Employability and HR Federation and XACML as Security and Access Control Layer Open Standards Forum 2 Employability and HR Vertical Multiple Players - Excellent case for federation
1 Securing Enterprise: Employability and HR Federation and XACML as Security and Access Control Layer Open Standards Forum 2 Employability and HR Vertical Multiple Players - Excellent case for federation
goberlin a Trusted Cloud Marketplace for Governmental and Commercial Services
 goberlin a Trusted Cloud Marketplace for Governmental and Commercial Services Data Protection and Security Considerations in an egovernment Cloud in Germany Dr. Klaus-Peter Eckert Public Sector Cloud Forum
goberlin a Trusted Cloud Marketplace for Governmental and Commercial Services Data Protection and Security Considerations in an egovernment Cloud in Germany Dr. Klaus-Peter Eckert Public Sector Cloud Forum
The full setup includes the server itself, the server control panel, Firebird Database Server, and three sample applications with source code.
 Content Introduction... 2 Data Access Server Control Panel... 2 Running the Sample Client Applications... 4 Sample Applications Code... 7 Server Side Objects... 8 Sample Usage of Server Side Objects...
Content Introduction... 2 Data Access Server Control Panel... 2 Running the Sample Client Applications... 4 Sample Applications Code... 7 Server Side Objects... 8 Sample Usage of Server Side Objects...
Remote Storage Area (RSA) Basics
 Remote Storage Area (RSA) Basics Table of Contents Remote Storage Area Overview... 3 What is Remote Storage Area?... 3 Who has access to RSA?... 3 How much space is available?... 3 Basic RSA Use... 4 How
Remote Storage Area (RSA) Basics Table of Contents Remote Storage Area Overview... 3 What is Remote Storage Area?... 3 Who has access to RSA?... 3 How much space is available?... 3 Basic RSA Use... 4 How
Guidelines for new users of the Union Registry ECAS account, registration and enrolment
 Guidelines for new users of the Union Registry ECAS account, registration and enrolment An ECAS account and registration are required for a new user to be added as an account representative Before a new
Guidelines for new users of the Union Registry ECAS account, registration and enrolment An ECAS account and registration are required for a new user to be added as an account representative Before a new
IBM Bluemix Tutorial Connecting Eclipse to Bluemix v2.0
 IBM Bluemix http://ibm.biz/bluemixph A platform where developers can act like kids in a sandbox except this box is enterprise-grade. This laboratory exercise demonstrates how to connect Eclipse to Bluemix
IBM Bluemix http://ibm.biz/bluemixph A platform where developers can act like kids in a sandbox except this box is enterprise-grade. This laboratory exercise demonstrates how to connect Eclipse to Bluemix
Setting up and Automating a MS Dynamics AX Job in JAMS
 Setting up and Automating a MS Dynamics AX Job in JAMS Introduction... 1 Creating a User for the AX Job Execution... 2 Setting up the AX Job... 4 Create a New folder... 4 Adding a new Dynamics AX Job using
Setting up and Automating a MS Dynamics AX Job in JAMS Introduction... 1 Creating a User for the AX Job Execution... 2 Setting up the AX Job... 4 Create a New folder... 4 Adding a new Dynamics AX Job using
In this topic we will cover the security functionality provided with SAP Business One.
 In this topic we will cover the security functionality provided with SAP Business One. 1 After completing this topic, you will be able to: Describe the security functions provided by the System Landscape
In this topic we will cover the security functionality provided with SAP Business One. 1 After completing this topic, you will be able to: Describe the security functions provided by the System Landscape
Soft Solutions, Inc. 4-Sight FAX 7.5. Getting Started. Soft Solutions, Inc. http://www.4sightfax.com/
 4-Sight FAX 7.5 Getting Started Soft Solutions, Inc. http://www.4sightfax.com/ Introduction Thank you for your interest in 4-Sight FAX version 7.5. This guide documents the general configuration for using
4-Sight FAX 7.5 Getting Started Soft Solutions, Inc. http://www.4sightfax.com/ Introduction Thank you for your interest in 4-Sight FAX version 7.5. This guide documents the general configuration for using
http://docs.trendmicro.com
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the product, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the product, please review the readme files,
Using Microsoft Windows Authentication for Microsoft SQL Server Connections in Data Archive
 Using Microsoft Windows Authentication for Microsoft SQL Server Connections in Data Archive 2014 Informatica Corporation. No part of this document may be reproduced or transmitted in any form, by any means
Using Microsoft Windows Authentication for Microsoft SQL Server Connections in Data Archive 2014 Informatica Corporation. No part of this document may be reproduced or transmitted in any form, by any means
Step by Step. Use the Cloud Login Website
 Step by Step HOW TO Use the Cloud Login Website This How To article will show you how to use the Cloud Login Website to upload and download your files from the cloud. For a complete list of available How
Step by Step HOW TO Use the Cloud Login Website This How To article will show you how to use the Cloud Login Website to upload and download your files from the cloud. For a complete list of available How
VPN-1 VE Evaluation Guide
 VPN-1 VE Evaluation Guide This document is intended for users who are new to Check Point VPN-1 products and would like to evaluate and review VPN-1 VE. We recommend reading the VPN-1 VE Administration
VPN-1 VE Evaluation Guide This document is intended for users who are new to Check Point VPN-1 products and would like to evaluate and review VPN-1 VE. We recommend reading the VPN-1 VE Administration
Smart Business Architecture for Midsize Networks Network Management Deployment Guide
 Smart Business Architecture for Midsize Networks Network Management Deployment Guide Introduction: Smart Business Architecture for Mid-sized Networks, Network Management Deployment Guide With the Smart
Smart Business Architecture for Midsize Networks Network Management Deployment Guide Introduction: Smart Business Architecture for Mid-sized Networks, Network Management Deployment Guide With the Smart
Working in Park City Group s Extranet
 Working in Park City Group s Extranet This is a guide to working in the Park City Group (PCG) Extranet. The Extranet is your portal into seeking support from our trained professionals, enabling timely
Working in Park City Group s Extranet This is a guide to working in the Park City Group (PCG) Extranet. The Extranet is your portal into seeking support from our trained professionals, enabling timely
VERALAB LDAP Configuration Guide
 VERALAB LDAP Configuration Guide VeraLab Suite is a client-server application and has two main components: a web-based application and a client software agent. Web-based application provides access to
VERALAB LDAP Configuration Guide VeraLab Suite is a client-server application and has two main components: a web-based application and a client software agent. Web-based application provides access to
Secret Server Installation Windows Server 2008 R2
 Table of Contents Introduction... 2 ASP.NET Website... 2 SQL Server Database... 2 Administrative Access... 2 Prerequisites... 2 System Requirements Overview... 2 Additional Recommendations... 3 Beginning
Table of Contents Introduction... 2 ASP.NET Website... 2 SQL Server Database... 2 Administrative Access... 2 Prerequisites... 2 System Requirements Overview... 2 Additional Recommendations... 3 Beginning
GMC Connect User Guide v1.1
 GMC Connect User Guide v1.1 CONTENTS 1 INTRODUCTION...3 2 ACCESSING GMC CONNECT...4 2.1 User Registration...4 2.2 Logging In...5 3 THE HOME PAGE...6 4 DOCUMENT FOLDERS...7 4.1 About Document Folders...7
GMC Connect User Guide v1.1 CONTENTS 1 INTRODUCTION...3 2 ACCESSING GMC CONNECT...4 2.1 User Registration...4 2.2 Logging In...5 3 THE HOME PAGE...6 4 DOCUMENT FOLDERS...7 4.1 About Document Folders...7
QUANTIFY INSTALLATION GUIDE
 QUANTIFY INSTALLATION GUIDE Thank you for putting your trust in Avontus! This guide reviews the process of installing Quantify software. For Quantify system requirement information, please refer to the
QUANTIFY INSTALLATION GUIDE Thank you for putting your trust in Avontus! This guide reviews the process of installing Quantify software. For Quantify system requirement information, please refer to the
Customize Mobile Apps with MicroStrategy SDK: Custom Security, Plugins, and Extensions
 Customize Mobile Apps with MicroStrategy SDK: Custom Security, Plugins, and Extensions MicroStrategy Mobile SDK 1 Agenda MicroStrategy Mobile SDK Overview Requirements & Setup Custom App Delegate Custom
Customize Mobile Apps with MicroStrategy SDK: Custom Security, Plugins, and Extensions MicroStrategy Mobile SDK 1 Agenda MicroStrategy Mobile SDK Overview Requirements & Setup Custom App Delegate Custom
i2b2: Security Baseline
 i2b2: Security Baseline Contents Introduction... 3 CentOS Security Configuration... 4 SSL Configuration... 5 Database Configuration Files... 6 Revision History... 11 2 Introduction This document outlines
i2b2: Security Baseline Contents Introduction... 3 CentOS Security Configuration... 4 SSL Configuration... 5 Database Configuration Files... 6 Revision History... 11 2 Introduction This document outlines
Windows Clients and GoPrint Print Queues
 Windows Clients and GoPrint Print Queues Overview The following tasks demonstrate how to configure shared network printers on Windows client machines in a Windows Active Directory Domain and Workgroup
Windows Clients and GoPrint Print Queues Overview The following tasks demonstrate how to configure shared network printers on Windows client machines in a Windows Active Directory Domain and Workgroup
Superior Court of Orange County 08/13/2010 700 Civic Center Drive West Santa Ana, CA 92701
 1 Contents 1 DOCUMENT DESCRIPTION... 2 1.1 DISCLAIMER... 2 1.2 GLOSSARY... 2 1.3 OVERVIEW... 3 1.4 OBJECTIVES... 5 1.5 IDENTITY PROVIDER... 6 1.5.1 Colon Issues... 6 1.6 ARCHITECTURAL OVERVIEW... 7 1.7
1 Contents 1 DOCUMENT DESCRIPTION... 2 1.1 DISCLAIMER... 2 1.2 GLOSSARY... 2 1.3 OVERVIEW... 3 1.4 OBJECTIVES... 5 1.5 IDENTITY PROVIDER... 6 1.5.1 Colon Issues... 6 1.6 ARCHITECTURAL OVERVIEW... 7 1.7
Accessing the Media General SSL VPN
 Launching Applications and Mapping Drives Remote Desktop Outlook Launching Web Applications Full Access VPN Note: To access the Media General VPN, anti-virus software must be installed and running on your
Launching Applications and Mapping Drives Remote Desktop Outlook Launching Web Applications Full Access VPN Note: To access the Media General VPN, anti-virus software must be installed and running on your
Access Management Analysis of some available solutions
 Access Management Analysis of some available solutions Enterprise Security & Risk Management May 2015 Authors: Yogesh Kumar Sharma, Kinshuk De, Dr. Sundeep Oberoi Access Management - Analysis of some available
Access Management Analysis of some available solutions Enterprise Security & Risk Management May 2015 Authors: Yogesh Kumar Sharma, Kinshuk De, Dr. Sundeep Oberoi Access Management - Analysis of some available
Receiving Secure Emails
 Receiving Secure Emails This document explains how you can access emails that have been sent to you through CyberArk s Secure Email system in several simple steps. When you receive a secure email, you
Receiving Secure Emails This document explains how you can access emails that have been sent to you through CyberArk s Secure Email system in several simple steps. When you receive a secure email, you
A Model for Access Control Management in Distributed Networks
 A Model for Access Control Management in Distributed Networks Master of Science Thesis Azadeh Bararsani Supervisor/Examiner: Dr. Johan Montelius Royal Institute of Technology (KTH), Stockholm, Sweden,
A Model for Access Control Management in Distributed Networks Master of Science Thesis Azadeh Bararsani Supervisor/Examiner: Dr. Johan Montelius Royal Institute of Technology (KTH), Stockholm, Sweden,
Configure Cisco Unified Customer Voice Portal
 Cisco Unified Customer Voice Portal Configuration, page 1 Configure Gateways, page 1 Transfer Unified CVP Scripts and Media Files, page 2 Unified Customer Voice Portal Licenses, page 2 Configure SNMP,
Cisco Unified Customer Voice Portal Configuration, page 1 Configure Gateways, page 1 Transfer Unified CVP Scripts and Media Files, page 2 Unified Customer Voice Portal Licenses, page 2 Configure SNMP,
System Center 2012 R2 SP1 Configuration Manager & Microsoft Intune
 2015 System Center 2012 R2 SP1 Configuration Manager & Microsoft Intune DEPLOYING MICROSOFT OFFICE 365 PROFESSIONAL PLUS RONNI PEDERSEN & HANS CHRISTIAN ANDERSEN RONNIPEDERSEN.COM Microsoft MVP: Enterprise
2015 System Center 2012 R2 SP1 Configuration Manager & Microsoft Intune DEPLOYING MICROSOFT OFFICE 365 PROFESSIONAL PLUS RONNI PEDERSEN & HANS CHRISTIAN ANDERSEN RONNIPEDERSEN.COM Microsoft MVP: Enterprise
Dynamic Access Control Infrastructure for On-demand Provisioned Cloud Services
 Dynamic Access Control Infrastructure for On-demand Provisioned Cloud Services Canh Ngo SNE Group, University of Amsterdam OGF-ISOD 33 September 19-21, 2011 Lyon, 2011 Agenda Introduction Scenario Motivation
Dynamic Access Control Infrastructure for On-demand Provisioned Cloud Services Canh Ngo SNE Group, University of Amsterdam OGF-ISOD 33 September 19-21, 2011 Lyon, 2011 Agenda Introduction Scenario Motivation
User s Guide For Department of Facility Services
 Doc s File Server User s Guide For Department of Facility Services For Ver : 7.2.88.1020 Rev : 1_05-27-2011 Created by : Elliott Jeyaseelan 2 Table of Contents SERVER LOGIN & AUTHENTICATION REQUIREMENTS
Doc s File Server User s Guide For Department of Facility Services For Ver : 7.2.88.1020 Rev : 1_05-27-2011 Created by : Elliott Jeyaseelan 2 Table of Contents SERVER LOGIN & AUTHENTICATION REQUIREMENTS
Edexcel Online FS ICT On Demand Download of Papers
 Edexcel Online FS ICT On Demand Download of Papers For further information visit our support page: www.pearsonwbl.edexcel.com/our-support 1 Contents Please note clicking on any of the individual sections
Edexcel Online FS ICT On Demand Download of Papers For further information visit our support page: www.pearsonwbl.edexcel.com/our-support 1 Contents Please note clicking on any of the individual sections
Personal Computer and Mobile Printing
 Personal Computer and Mobile Printing IT Services now offers students, faculty, and staff the ability to print from personal laptops and Apple ios devices on the Fort Wayne campus without having access
Personal Computer and Mobile Printing IT Services now offers students, faculty, and staff the ability to print from personal laptops and Apple ios devices on the Fort Wayne campus without having access
Using the Content Distribution Manager GUI
 CHAPTER 3 Using the Content Distribution Manager GUI The Content Distribution Manager is the central location from which much of the work of creating and managing ACNS networks and hosted content can be
CHAPTER 3 Using the Content Distribution Manager GUI The Content Distribution Manager is the central location from which much of the work of creating and managing ACNS networks and hosted content can be
Creating and Issuing the Workstation Authentication Certificate Template on the Certification Authority
 In this post we will see the steps for deploying the client certificate for windows computers. This post is a part of Deploy PKI Certificates for SCCM 2012 R2 Step by Step Guide. In the previous post we
In this post we will see the steps for deploying the client certificate for windows computers. This post is a part of Deploy PKI Certificates for SCCM 2012 R2 Step by Step Guide. In the previous post we
Tips for Web Filers. Tips for Web Filers. New Company Registration Page
 Please read all information and instructions prior to entering the data. The instructions provide important details about completing the form and will help make your web experience a positive one. 1. How
Please read all information and instructions prior to entering the data. The instructions provide important details about completing the form and will help make your web experience a positive one. 1. How
Oracle Database Express Edition
 Oracle Database Express Edition Getting Started Guide 11g Release 2 (11.2) E18585-05 May 2014 Welcome to Oracle Database Express Edition (Oracle Database XE). This guide gets you quickly up and running
Oracle Database Express Edition Getting Started Guide 11g Release 2 (11.2) E18585-05 May 2014 Welcome to Oracle Database Express Edition (Oracle Database XE). This guide gets you quickly up and running
Volume FIRST WALKTHROUGH. The 10-Minute Guide to Using Newsletter Services. First Walkthrough: the 10-Minute Guide
 Volume 1 FIRST WALKTHROUGH The 10-Minute Guide to Using Newsletter Services First Walkthrough: the 10-Minute Guide Table of Contents Step - 1... 3 Sign-up for an account... 3 Step 2... 4 Authenticate your
Volume 1 FIRST WALKTHROUGH The 10-Minute Guide to Using Newsletter Services First Walkthrough: the 10-Minute Guide Table of Contents Step - 1... 3 Sign-up for an account... 3 Step 2... 4 Authenticate your
Marcum LLP MFT Guide
 MFT Guide Contents 1. Logging In...3 2. Installing the Upload Wizard...4 3. Uploading Files Using the Upload Wizard...5 4. Downloading Files Using the Upload Wizard...8 5. Frequently Asked Questions...9
MFT Guide Contents 1. Logging In...3 2. Installing the Upload Wizard...4 3. Uploading Files Using the Upload Wizard...5 4. Downloading Files Using the Upload Wizard...8 5. Frequently Asked Questions...9
Encryption Key Best Practices Nasuni Corporation Natick, MA
 Nasuni Corporation Natick, MA Summary of Best Practices Recommendations The best practices for managing encryption keys for the Nasuni Filer include the following: If your enterprise has existing OpenPGP-compatible
Nasuni Corporation Natick, MA Summary of Best Practices Recommendations The best practices for managing encryption keys for the Nasuni Filer include the following: If your enterprise has existing OpenPGP-compatible
Setting up a Scheduled task to upload pupil records to ParentPay
 Setting up a Scheduled task to upload pupil records to ParentPay To ensure that your setup goes ahead without any issues please first check that you are setting the scheduled task up on the SIMS server
Setting up a Scheduled task to upload pupil records to ParentPay To ensure that your setup goes ahead without any issues please first check that you are setting the scheduled task up on the SIMS server
Information Technology Services
 Uploading Videos to the Streaming Service **NOTE: Please ensure you have acquired the rights required to video stream any copyrighted material. For guidance on College practices regarding copyright please
Uploading Videos to the Streaming Service **NOTE: Please ensure you have acquired the rights required to video stream any copyrighted material. For guidance on College practices regarding copyright please
INTEGRATION GUIDE. DIGIPASS Authentication for Google Apps using IDENTIKEY Federation Server
 INTEGRATION GUIDE DIGIPASS Authentication for Google Apps using IDENTIKEY Federation Server Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document
INTEGRATION GUIDE DIGIPASS Authentication for Google Apps using IDENTIKEY Federation Server Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document
New Help Desk Ticketing System
 New Help Desk Ticketing System Starting Monday, November 30, 2009 at 6 am the University will be going live with their new help desk ticketing system. The website to access the new ticketing system is
New Help Desk Ticketing System Starting Monday, November 30, 2009 at 6 am the University will be going live with their new help desk ticketing system. The website to access the new ticketing system is
LabView Package and Driver Installation Tutorial for ENGR 190
 LabView Package and Driver Installation Tutorial for ENGR 190 Student will need to install following software and drivers to use LabView, NI Multisim and MyDAQ for ENGR 190. It is advised to follow all
LabView Package and Driver Installation Tutorial for ENGR 190 Student will need to install following software and drivers to use LabView, NI Multisim and MyDAQ for ENGR 190. It is advised to follow all
On XACML, role-based access control, and health grids
 On XACML, role-based access control, and health grids 01 On XACML, role-based access control, and health grids D. Power, M. Slaymaker, E. Politou and A. Simpson On XACML, role-based access control, and
On XACML, role-based access control, and health grids 01 On XACML, role-based access control, and health grids D. Power, M. Slaymaker, E. Politou and A. Simpson On XACML, role-based access control, and
SpringCM Integration Guide. for Salesforce
 SpringCM Integration Guide for Salesforce January 2013 Introduction You are minutes away from fully integrating SpringCM into your Salesforce account. The SpringCM Open Cloud Connector will allow you to
SpringCM Integration Guide for Salesforce January 2013 Introduction You are minutes away from fully integrating SpringCM into your Salesforce account. The SpringCM Open Cloud Connector will allow you to
Configuration Manual for Lime Domains
 Email Accounts Configuration Manual for Lime Domains Table of Contents Introduction:... 2 To configure your Outlook Express client:... 3 To configure your Microsoft Outlook client:... 12 To configure your
Email Accounts Configuration Manual for Lime Domains Table of Contents Introduction:... 2 To configure your Outlook Express client:... 3 To configure your Microsoft Outlook client:... 12 To configure your
Integration Guide. SafeNet Authentication Client. Using SAC CBA for Check Point Security Gateway
 SafeNet Authentication Client Integration Guide Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet, Inc. All rights reserved. 1 Document Information Document
SafeNet Authentication Client Integration Guide Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet, Inc. All rights reserved. 1 Document Information Document
White Paper The Identity & Access Management (R)evolution
 White Paper The Identity & Access Management (R)evolution Federation and Attribute Based Access Control Page 2 A New Perspective on Identity & Access Management Executive Summary Identity & Access Management
White Paper The Identity & Access Management (R)evolution Federation and Attribute Based Access Control Page 2 A New Perspective on Identity & Access Management Executive Summary Identity & Access Management
1. Please login to the Own Web Now Support Portal (https://support.ownwebnow.com) with your email address and a password.
 Offsite Backups Introduction The purpose of this Startup Guide is to familiarize you with Own Web Now's Offsite Backup offering and show you how to purchase, deploy and manage the service. Offsite Backup
Offsite Backups Introduction The purpose of this Startup Guide is to familiarize you with Own Web Now's Offsite Backup offering and show you how to purchase, deploy and manage the service. Offsite Backup
OUTLOOK WEB APP (OWA): MAIL
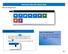 Office 365 Navigation Pane: Navigating in Office 365 Click the App Launcher and then choose the application (i.e. Outlook, Calendar, People, etc.). To modify your personal account settings, click the Logon
Office 365 Navigation Pane: Navigating in Office 365 Click the App Launcher and then choose the application (i.e. Outlook, Calendar, People, etc.). To modify your personal account settings, click the Logon
To enable an application to use external usernames and passwords, you need to first configure CA EEM to use external directories.
 Most clients utilize an external directory tool, such as Microsoft Active Directory, to provide authentication. CA Embedded Entitlements Manager (EEM) can be configured to integrate with the same external
Most clients utilize an external directory tool, such as Microsoft Active Directory, to provide authentication. CA Embedded Entitlements Manager (EEM) can be configured to integrate with the same external
Two-Factor Authentication
 Two-Factor Authentication This document describes SonicWALL s implementation of two-factor authentication for SonicWALL SSL-VPN appliances. This document contains the following sections: Feature Overview
Two-Factor Authentication This document describes SonicWALL s implementation of two-factor authentication for SonicWALL SSL-VPN appliances. This document contains the following sections: Feature Overview
Fax User Guide 07/31/2014 USER GUIDE
 Fax User Guide 07/31/2014 USER GUIDE Contents: Access Fusion Fax Service 3 Search Tab 3 View Tab 5 To E-mail From View Page 5 Send Tab 7 Recipient Info Section 7 Attachments Section 7 Preview Fax Section
Fax User Guide 07/31/2014 USER GUIDE Contents: Access Fusion Fax Service 3 Search Tab 3 View Tab 5 To E-mail From View Page 5 Send Tab 7 Recipient Info Section 7 Attachments Section 7 Preview Fax Section
INTEGRATION GUIDE. DIGIPASS Authentication for Salesforce using IDENTIKEY Federation Server
 INTEGRATION GUIDE DIGIPASS Authentication for Salesforce using IDENTIKEY Federation Server Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document is
INTEGRATION GUIDE DIGIPASS Authentication for Salesforce using IDENTIKEY Federation Server Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document is
The Cancer Institute NSW Grants Management System User Guide
 The Cancer Institute NSW Grants Management User Guide Version 1.1 12 February 2016 Contents 1. Registration 2 2. Login to the Institute s GMS 3 3. Forgot password 3 4. The home page 4 5. Creating a profile
The Cancer Institute NSW Grants Management User Guide Version 1.1 12 February 2016 Contents 1. Registration 2 2. Login to the Institute s GMS 3 3. Forgot password 3 4. The home page 4 5. Creating a profile
Sitecore Ecommerce Enterprise Edition Installation Guide Installation guide for administrators and developers
 Installation guide for administrators and developers Table of Contents Chapter 1 Introduction... 2 1.1 Preparing to Install Sitecore Ecommerce Enterprise Edition... 2 1.2 Required Installation Components...
Installation guide for administrators and developers Table of Contents Chapter 1 Introduction... 2 1.1 Preparing to Install Sitecore Ecommerce Enterprise Edition... 2 1.2 Required Installation Components...
Working with the ERP Integration Service of EMC Documentum Process Services for SAP
 Working with the ERP Integration Service of EMC Documentum Process Services for SAP Applied Technology Abstract EMC Documentum Process Services for SAP is a new product that integrates with EMC Documentum
Working with the ERP Integration Service of EMC Documentum Process Services for SAP Applied Technology Abstract EMC Documentum Process Services for SAP is a new product that integrates with EMC Documentum
Preparing for GO!Enterprise MDM On-Demand Service
 Preparing for GO!Enterprise MDM On-Demand Service This guide provides information on...... An overview of GO!Enterprise MDM... Preparing your environment for GO!Enterprise MDM On-Demand... Firewall rules
Preparing for GO!Enterprise MDM On-Demand Service This guide provides information on...... An overview of GO!Enterprise MDM... Preparing your environment for GO!Enterprise MDM On-Demand... Firewall rules
PigCHAMP Knowledge Software. Enterprise Edition Installation Guide
 PigCHAMP Knowledge Software Enterprise Edition Installation Guide Enterprise Edition Installation Guide MARCH 2012 EDITION PigCHAMP Knowledge Software 1531 Airport Rd Suite 101 Ames, IA 50010 Phone (515)
PigCHAMP Knowledge Software Enterprise Edition Installation Guide Enterprise Edition Installation Guide MARCH 2012 EDITION PigCHAMP Knowledge Software 1531 Airport Rd Suite 101 Ames, IA 50010 Phone (515)
Broker Registration Guide for TrustFunds Authentication A- B- C Registration Steps 1-2- 3-4
 Broker Registration Guide for TrustFunds Authentication A- B- C Registration Steps 1-2- 3-4 Broker Authentication 1. From the TrustFunds website homepage, click Get Started Now to begin your Authentication
Broker Registration Guide for TrustFunds Authentication A- B- C Registration Steps 1-2- 3-4 Broker Authentication 1. From the TrustFunds website homepage, click Get Started Now to begin your Authentication
525 South 29 th Street. Harrisburg, PA 17104. Learning Management System User s Guide
 525 South 29 th Street Harrisburg, PA 17104 Learning Management System User s Guide July 2015 1 Table of Contents User Accounts Overview 3 Changing your Email address 3 Changing your Password 3 Changing
525 South 29 th Street Harrisburg, PA 17104 Learning Management System User s Guide July 2015 1 Table of Contents User Accounts Overview 3 Changing your Email address 3 Changing your Password 3 Changing
DOCQN. Account. CA Departm. Version 2.0
 DOCQN NET Project Account Creation & Maintenancee CA Departm ment of Business Oversight Version 2.0 (6/18/2014) Table of Contents 1. Overview... 3 2. Account Management... 4 2.1 How to Create a New Account...
DOCQN NET Project Account Creation & Maintenancee CA Departm ment of Business Oversight Version 2.0 (6/18/2014) Table of Contents 1. Overview... 3 2. Account Management... 4 2.1 How to Create a New Account...
www.novell.com/documentation Server Installation ZENworks Mobile Management 2.7.x August 2013
 www.novell.com/documentation Server Installation ZENworks Mobile Management 2.7.x August 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of this
www.novell.com/documentation Server Installation ZENworks Mobile Management 2.7.x August 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of this
Configuring Devices for Use with Cisco Configuration Professional (CCP) 2.5
 Configuring Devices for Use with Cisco Configuration Professional (CCP) 2.5 Objectives Part 1: Configure CCP Access for Routers Enable HTTP/HTTPS server. Create a user account with privilege level 15.
Configuring Devices for Use with Cisco Configuration Professional (CCP) 2.5 Objectives Part 1: Configure CCP Access for Routers Enable HTTP/HTTPS server. Create a user account with privilege level 15.
AxiomONE vsphere Plug-In. Please Review Create Datastores Topics
 AxiomONE vsphere Plug-In Please Review Create Datastores Topics Table of Contents Create a Datastore Mapped to an Existing LUN.... 3 Create a Datastore Mapped to a New LUN.... 5 Index.... 7 2 Create a
AxiomONE vsphere Plug-In Please Review Create Datastores Topics Table of Contents Create a Datastore Mapped to an Existing LUN.... 3 Create a Datastore Mapped to a New LUN.... 5 Index.... 7 2 Create a
Quareo ICM Server Software
 The Quareo Infrastructure Configuration Manager (ICM) is a server software application designed to document and administer both passive and active network connectivity infrastructure. ICM enables management
The Quareo Infrastructure Configuration Manager (ICM) is a server software application designed to document and administer both passive and active network connectivity infrastructure. ICM enables management
Contents Release Notes... ... 3 System Requirements... ... 4 Administering Jive for Office... ... 5
 Jive for Office TOC 2 Contents Release Notes...3 System Requirements... 4 Administering Jive for Office... 5 Getting Set Up...5 Installing the Extended API JAR File... 5 Updating Client Binaries...5 Client
Jive for Office TOC 2 Contents Release Notes...3 System Requirements... 4 Administering Jive for Office... 5 Getting Set Up...5 Installing the Extended API JAR File... 5 Updating Client Binaries...5 Client
Qlik Sense Cloud. Qlik Sense 2.0.4 Copyright 1993-2015 QlikTech International AB. All rights reserved.
 Qlik Sense Cloud Qlik Sense 2.0.4 Copyright 1993-2015 QlikTech International AB. All rights reserved. Copyright 1993-2015 QlikTech International AB. All rights reserved. Qlik, QlikTech, Qlik Sense, QlikView,
Qlik Sense Cloud Qlik Sense 2.0.4 Copyright 1993-2015 QlikTech International AB. All rights reserved. Copyright 1993-2015 QlikTech International AB. All rights reserved. Qlik, QlikTech, Qlik Sense, QlikView,
FortyCloud Installation Guide. Installing FortyCloud Gateways Using AMIs (AWS Billing)
 FortyCloud Installation Guide Installing FortyCloud Gateways Using AMIs (AWS Billing) Date Version Changes 9/29/2015 2.0 2015 FortyCloud Ltd. 15 Berkshire Road Mansfield, MA 02048 USA 1 P a g e Introduction
FortyCloud Installation Guide Installing FortyCloud Gateways Using AMIs (AWS Billing) Date Version Changes 9/29/2015 2.0 2015 FortyCloud Ltd. 15 Berkshire Road Mansfield, MA 02048 USA 1 P a g e Introduction
MS SQL Server Backup - User Guide
 MS SQL Server Backup - User Guide TABLE OF CONTENTS Introduction... 1 Features... 1 System Requirements... 1 MS SQL Server Backup... 2 Accessing SQL Server Backup... 2 MS SQL Server Restore... 6 Accessing
MS SQL Server Backup - User Guide TABLE OF CONTENTS Introduction... 1 Features... 1 System Requirements... 1 MS SQL Server Backup... 2 Accessing SQL Server Backup... 2 MS SQL Server Restore... 6 Accessing
COX BUSINESS ONLINE BACKUP
 COX BUSINESS ONLINE BACKUP Quick start Guide www.cox.com Services and features not available in all areas and package options vary by market. Rates and speeds vary by market. Number of users and network
COX BUSINESS ONLINE BACKUP Quick start Guide www.cox.com Services and features not available in all areas and package options vary by market. Rates and speeds vary by market. Number of users and network
SETUP AND OPERATION GUIDE CLOUD PRINT. Version 1.0. January 2015. 2015 KYOCERA Document Solutions UK
 SETUP AND OPERATION GUIDE CLOUD PRINT Version 1.0 January 2015 2015 KYOCERA Document Solutions UK HyPAS TM and TASKalfa TM are trademarks of the KYOCERA Companies. Other company names in this guide may
SETUP AND OPERATION GUIDE CLOUD PRINT Version 1.0 January 2015 2015 KYOCERA Document Solutions UK HyPAS TM and TASKalfa TM are trademarks of the KYOCERA Companies. Other company names in this guide may
SAML 2.0 SSO Deployment with Okta
 SAML 2.0 SSO Deployment with Okta Simplify Network Authentication by Using Thunder ADC as an Authentication Proxy DEPLOYMENT GUIDE Table of Contents Overview...3 The A10 Networks SAML 2.0 SSO Deployment
SAML 2.0 SSO Deployment with Okta Simplify Network Authentication by Using Thunder ADC as an Authentication Proxy DEPLOYMENT GUIDE Table of Contents Overview...3 The A10 Networks SAML 2.0 SSO Deployment
SonicWALL SRA Virtual Appliance Getting Started Guide
 COMPREHENSIVE INTERNET SECURITY SonicWALL Secure Remote Access Appliances SonicWALL SRA Virtual Appliance Getting Started Guide SonicWALL SRA Virtual Appliance5.0 Getting Started Guide This Getting Started
COMPREHENSIVE INTERNET SECURITY SonicWALL Secure Remote Access Appliances SonicWALL SRA Virtual Appliance Getting Started Guide SonicWALL SRA Virtual Appliance5.0 Getting Started Guide This Getting Started
TIB 2.0 Administration Functions Overview
 TIB 2.0 Administration Functions Overview Table of Contents 1. INTRODUCTION 4 1.1. Purpose/Background 4 1.2. Definitions, Acronyms and Abbreviations 4 2. OVERVIEW 5 2.1. Overall Process Map 5 3. ADMINISTRATOR
TIB 2.0 Administration Functions Overview Table of Contents 1. INTRODUCTION 4 1.1. Purpose/Background 4 1.2. Definitions, Acronyms and Abbreviations 4 2. OVERVIEW 5 2.1. Overall Process Map 5 3. ADMINISTRATOR
And be taken to the Update My Information page (See Updating your My Information on page 2)
 AUTHOR LOGIN AND UPDATING MY INFORMATION Please do not print this document as it is subject to continuous revision. The latest version will always be available here: Please submit any feedback to John.Day@rcni.com
AUTHOR LOGIN AND UPDATING MY INFORMATION Please do not print this document as it is subject to continuous revision. The latest version will always be available here: Please submit any feedback to John.Day@rcni.com
STEPS TO REGISTER YOUR PROFILE AND BOOK THE COUPON
 STEPS TO REGISTER YOUR PROFILE AND BOOK THE COUPON 1. Registering with Sabarimala Virtual Q Portal A user can register into the site after a few easy steps. A user needs to register with the site to be
STEPS TO REGISTER YOUR PROFILE AND BOOK THE COUPON 1. Registering with Sabarimala Virtual Q Portal A user can register into the site after a few easy steps. A user needs to register with the site to be
Virtual Code Authentication User s Guide. June 25, 2015
 Virtual Code Authentication User s Guide June 25, 2015 Virtual Code Authentication User s Guide Overview of New Security Modern technologies call for higher security standards as practiced among many other
Virtual Code Authentication User s Guide June 25, 2015 Virtual Code Authentication User s Guide Overview of New Security Modern technologies call for higher security standards as practiced among many other
